Secure transmission method using time-varying incidental information flow as key information
A technology for secure transmission and incidental information, applied in the field of data security transmission, it can solve the problems that subsequent information cannot be decrypted and affect the normal exchange of data, and achieve the effect of reducing the number of handshakes, enhancing security, and improving communication efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
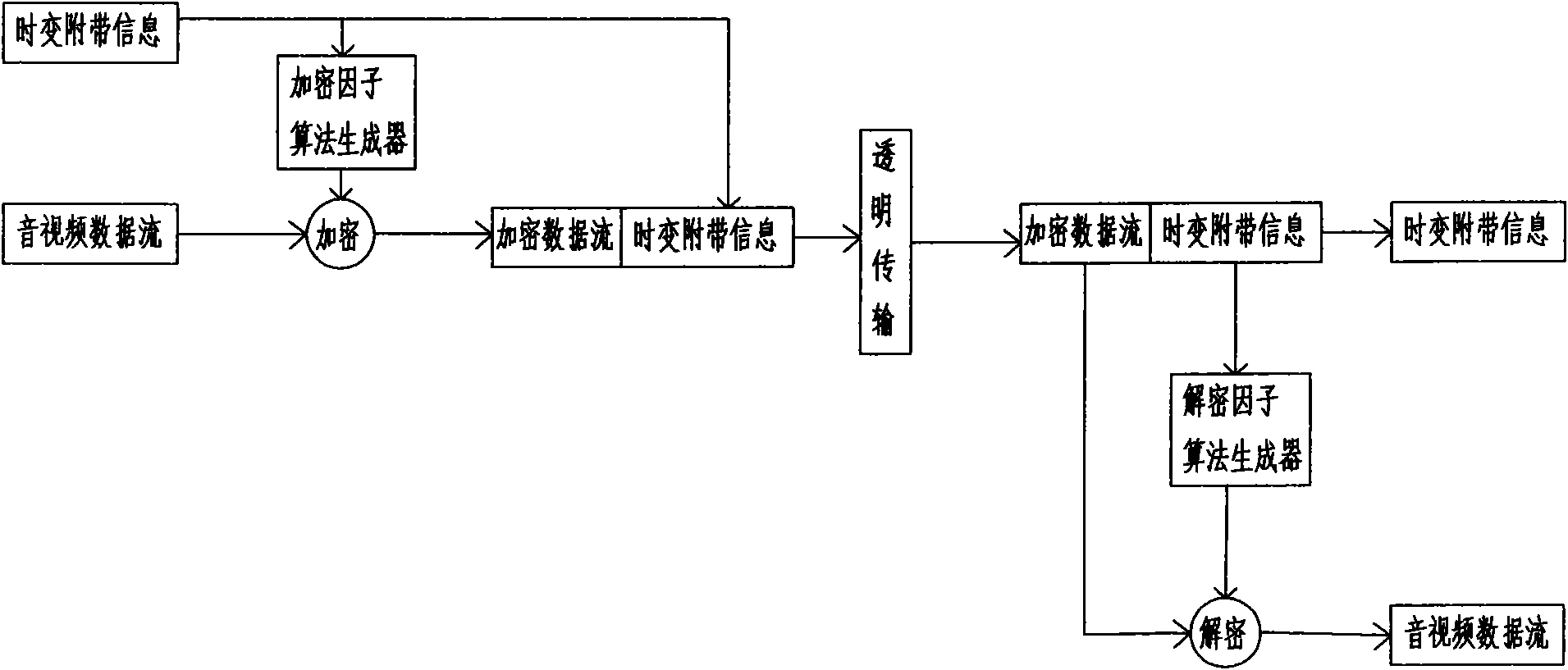
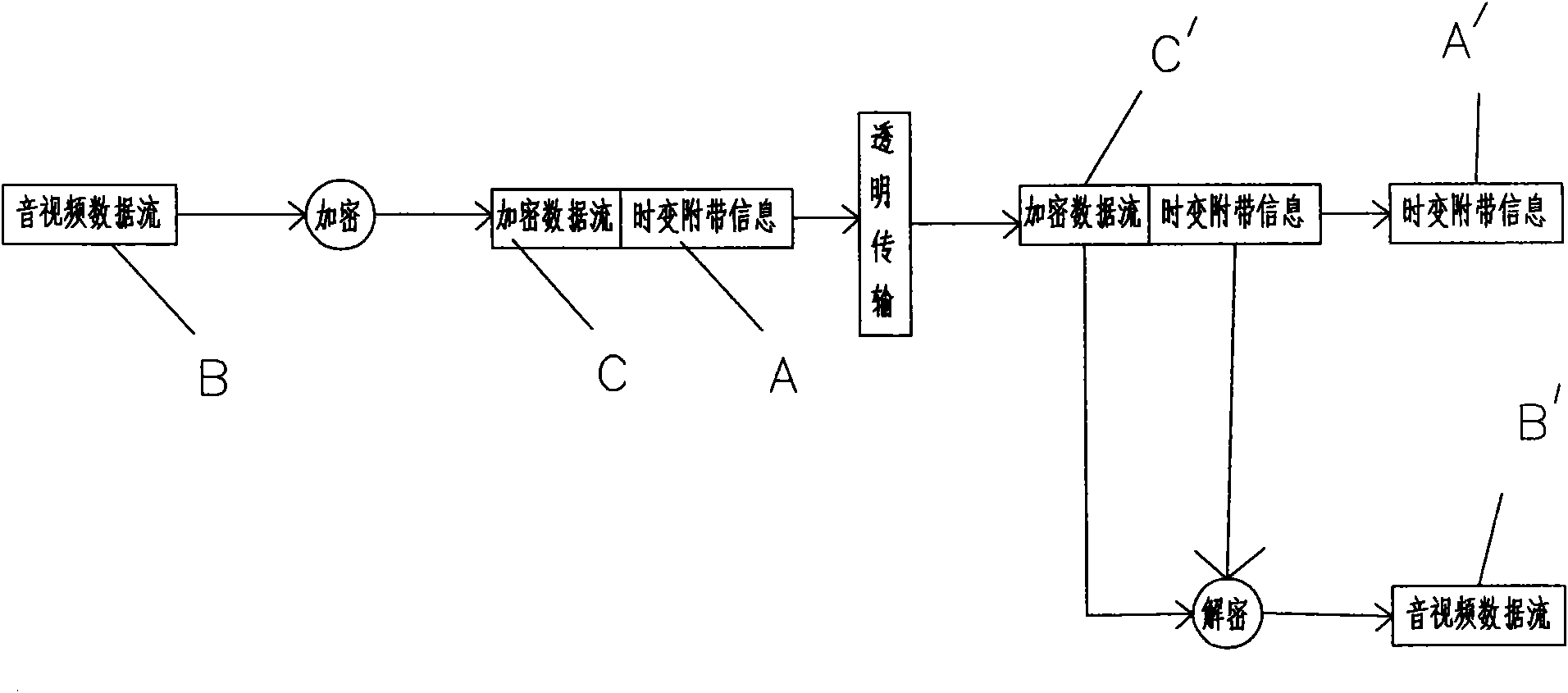
[0019] Such as figure 1 As shown, the time-varying incidental information stream described in this embodiment is a secure transmission method of key information, which uses binary coding to transmit the data stream. Its characteristics are: (1) During the data processing process of the sender, the algorithm generator uses the time-varying The incidental information generates a time-varying encryption factor, the time-varying encryption factor is logically operated with the original data stream to be sent to generate an encrypted data stream, and the encrypted data stream is combined with the time-varying incidental information in a specific way to form an information data stream and sent; (2) The receiver receives the information data stream, detects the time-varying incidental information in the information data stream and separates it from the encrypted data stream, and uses an algorithm generator to generate the time-varying incidental information based on the time-varying inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com