Key exchanging method for end-to-end VoIP encryption communication
A technology of encrypted communication and key exchange, which is applied in the field of key exchange of end-to-end VoIP encrypted communication
Inactive Publication Date: 2017-06-13
INST OF INFORMATION ENG CAS
View PDF4 Cites 3 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
The invention proposes a method for exchanging session keys for encrypted VoIP call applications based on the
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
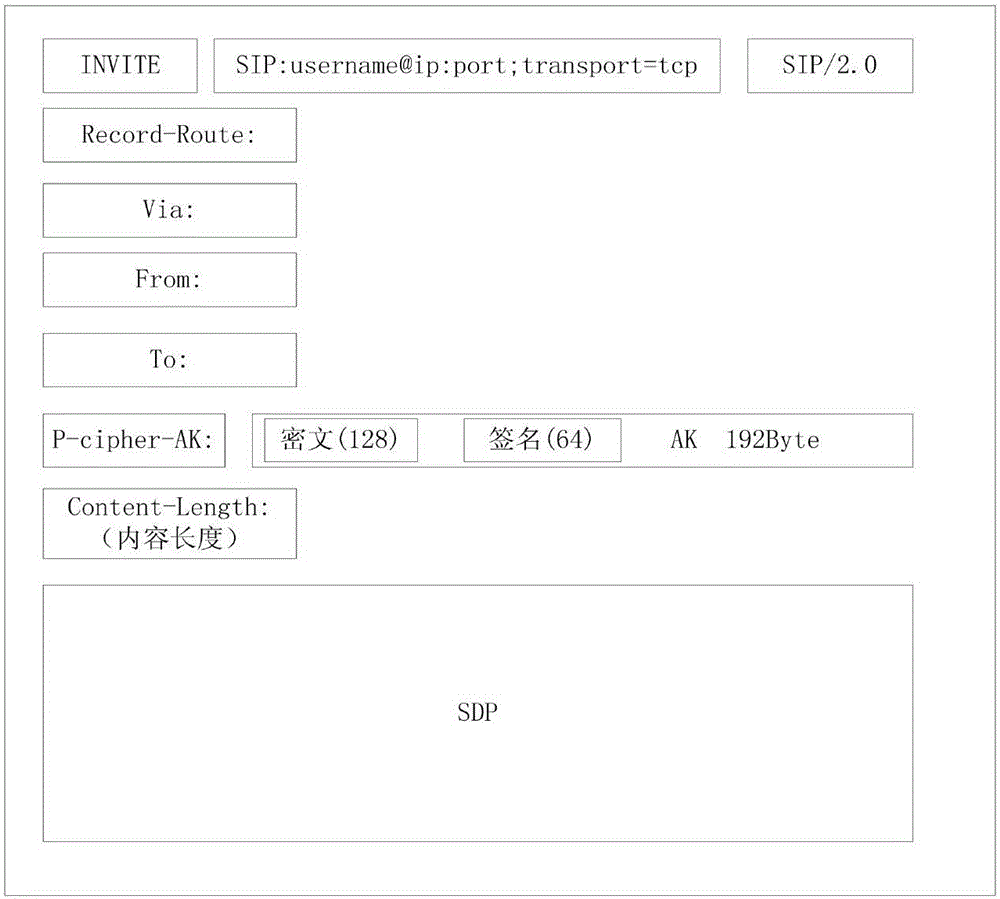
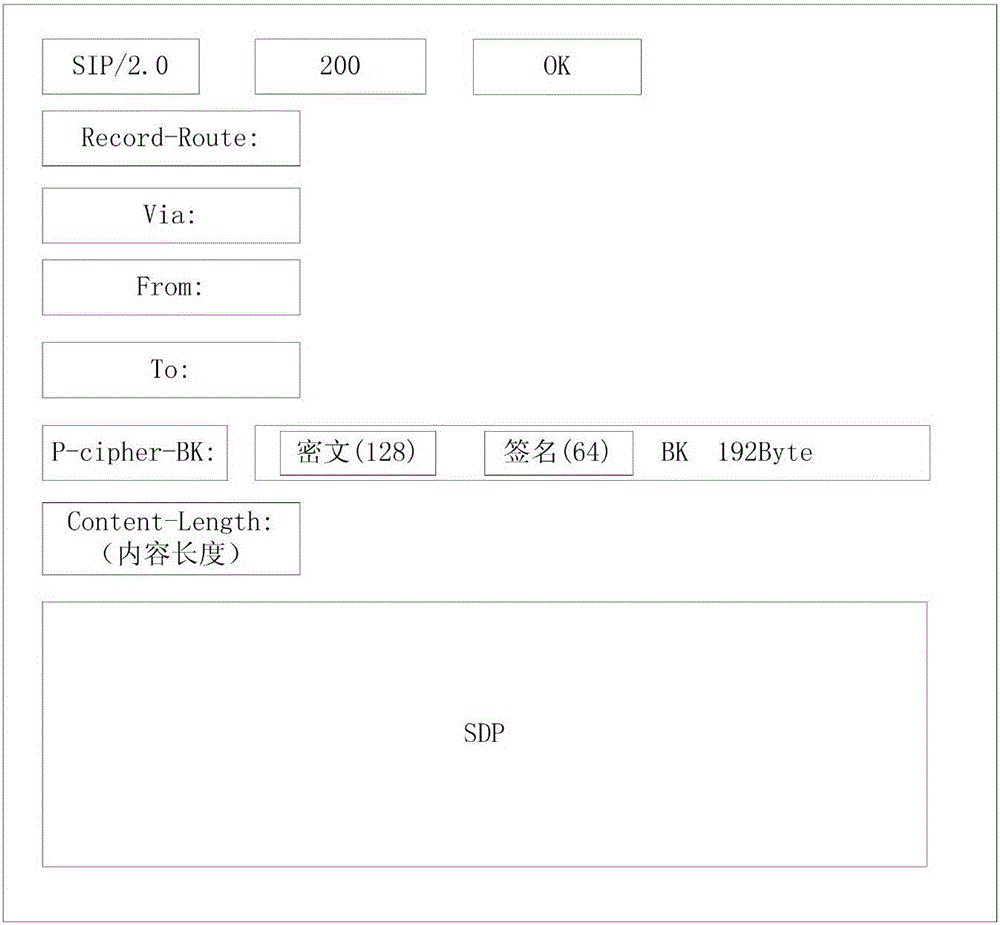
The invention discloses a key exchanging method for end-to-end VoIP encryption communication. The method comprises the steps that 1), a session initiator generates a session key AK and encrypts the AK through utilization of a public key of a target receiver; 2), an AK ciphertext is added to an INVITE message and the INVITE message is sent to the target receiver; 3), the target receiver decrypts the AK ciphertext through utilization of a private key, thereby obtaining the AK, generates the session key BK and generates a key C as a negotiation key according to the AK and the BK; and 4), after encrypting the BK through utilization of the public key of the initiator, the target receiver sends a BK ciphertext to the initiator through utilization of a 200 OK message, and the initiator decrypts the BK ciphertext through utilization of the private key, thereby obtaining the BK and then generates the key C as the negotiation key according to the AK and the BK. The method is simple and practicable, the influence on a protocol is low, and the key negotiation efficiency is greatly improved.
Description
technical field [0001] The invention belongs to the technical field of network communication security, and relates to a key exchange method in IP domain VoIP, in particular to a key exchange method for end-to-end VoIP encrypted communication. Background technique [0002] The rapid development and wide application of mobile communication technology has brought great convenience to people's life, but it also brings many security risks, and illegal communication monitoring often occurs. For this reason, the present invention proposes a method for end-to-end encrypted communication in the IP domain, thereby protecting the security of conversations. [0003] Because symmetric encryption is faster than asymmetric encryption, the delay of encryption and decryption is very short, and the security can be guaranteed enough. At present, symmetric encryption is generally used for encryption and decryption of real-time application data such as voice and multimedia communication. Such a...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06H04M7/00
CPCH04L63/0442H04L63/061H04M7/0078H04L65/1104
Inventor 周卫华单旭
Owner INST OF INFORMATION ENG CAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com