Patents
Literature
235 results about "Security layer" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
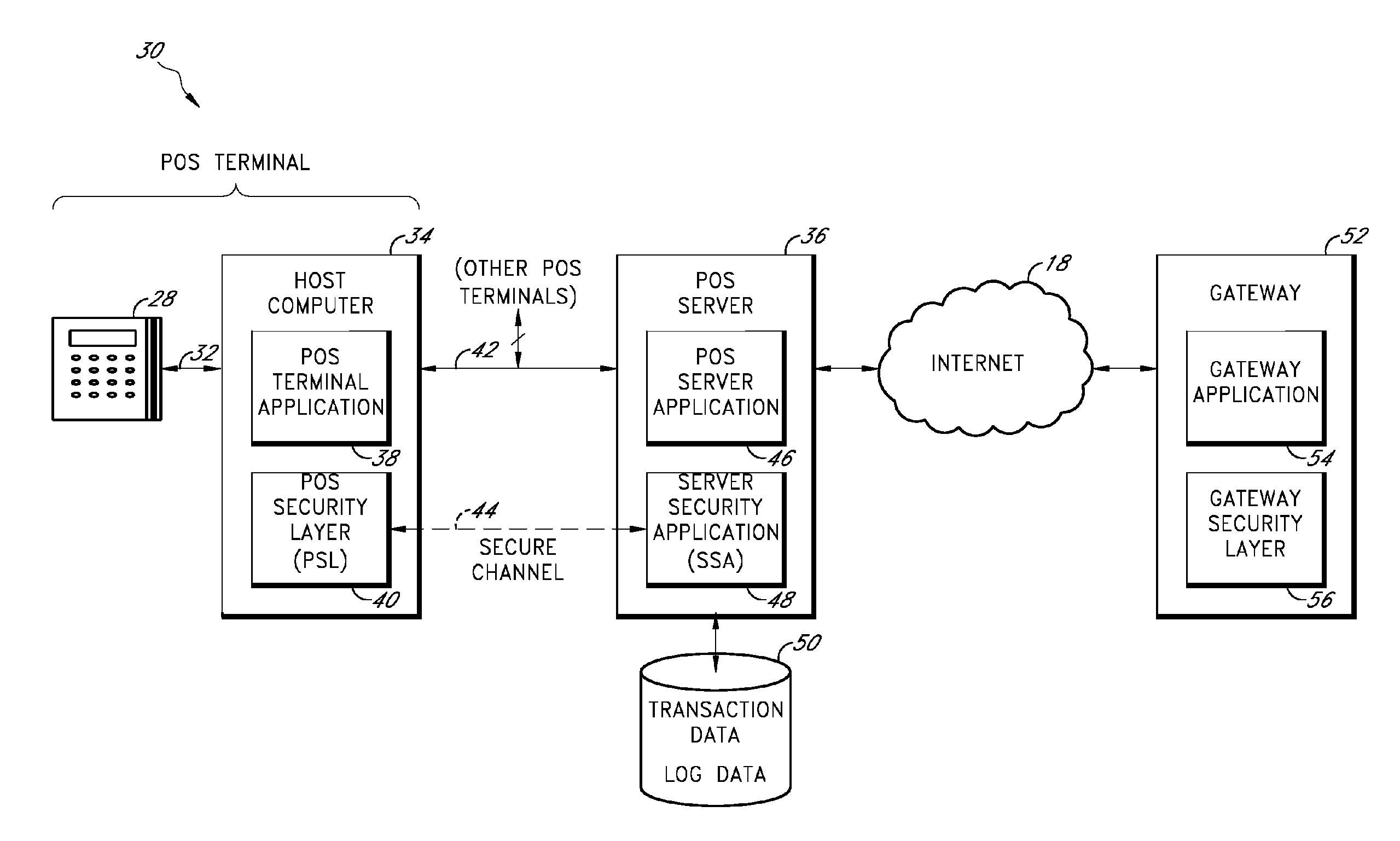
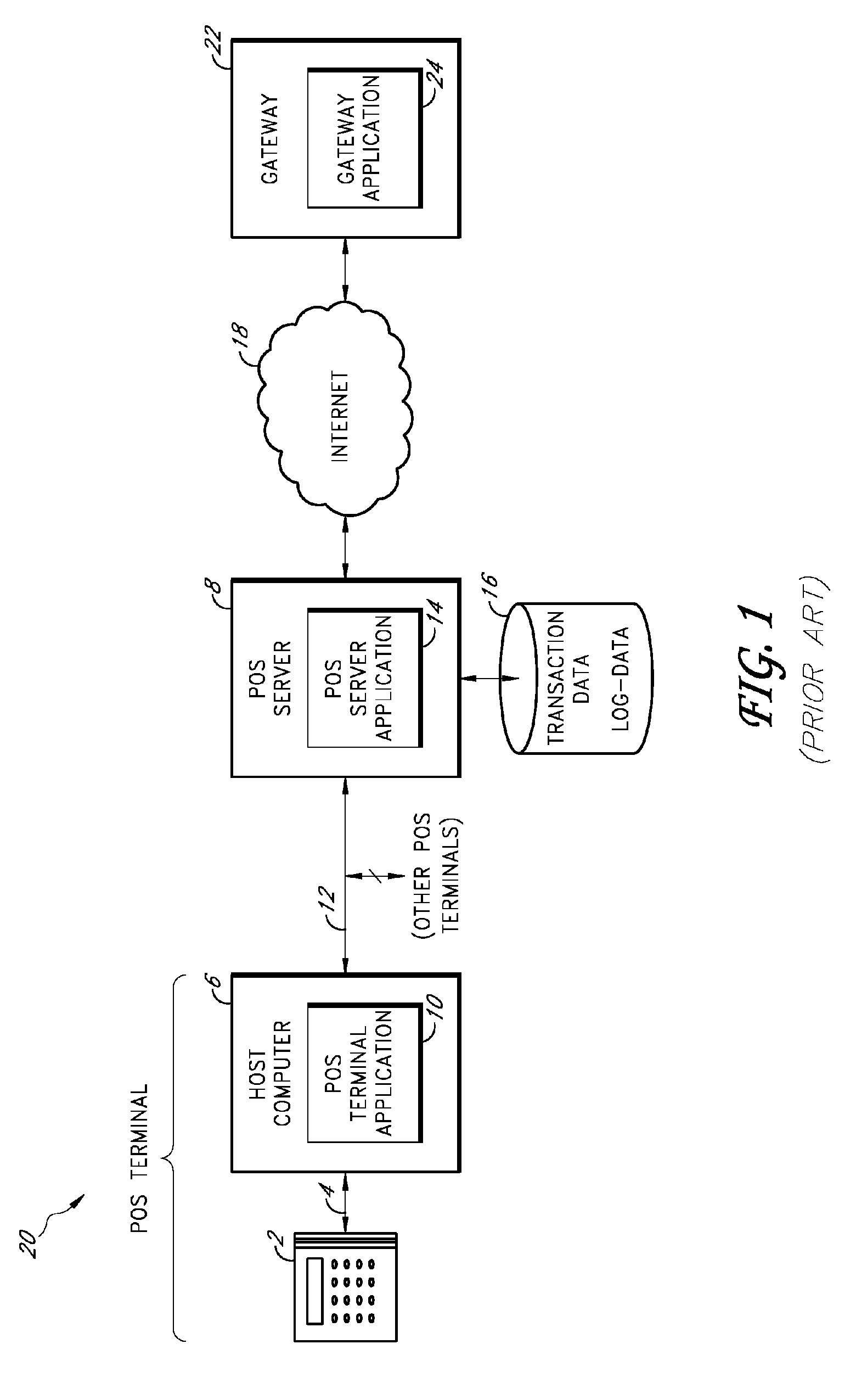
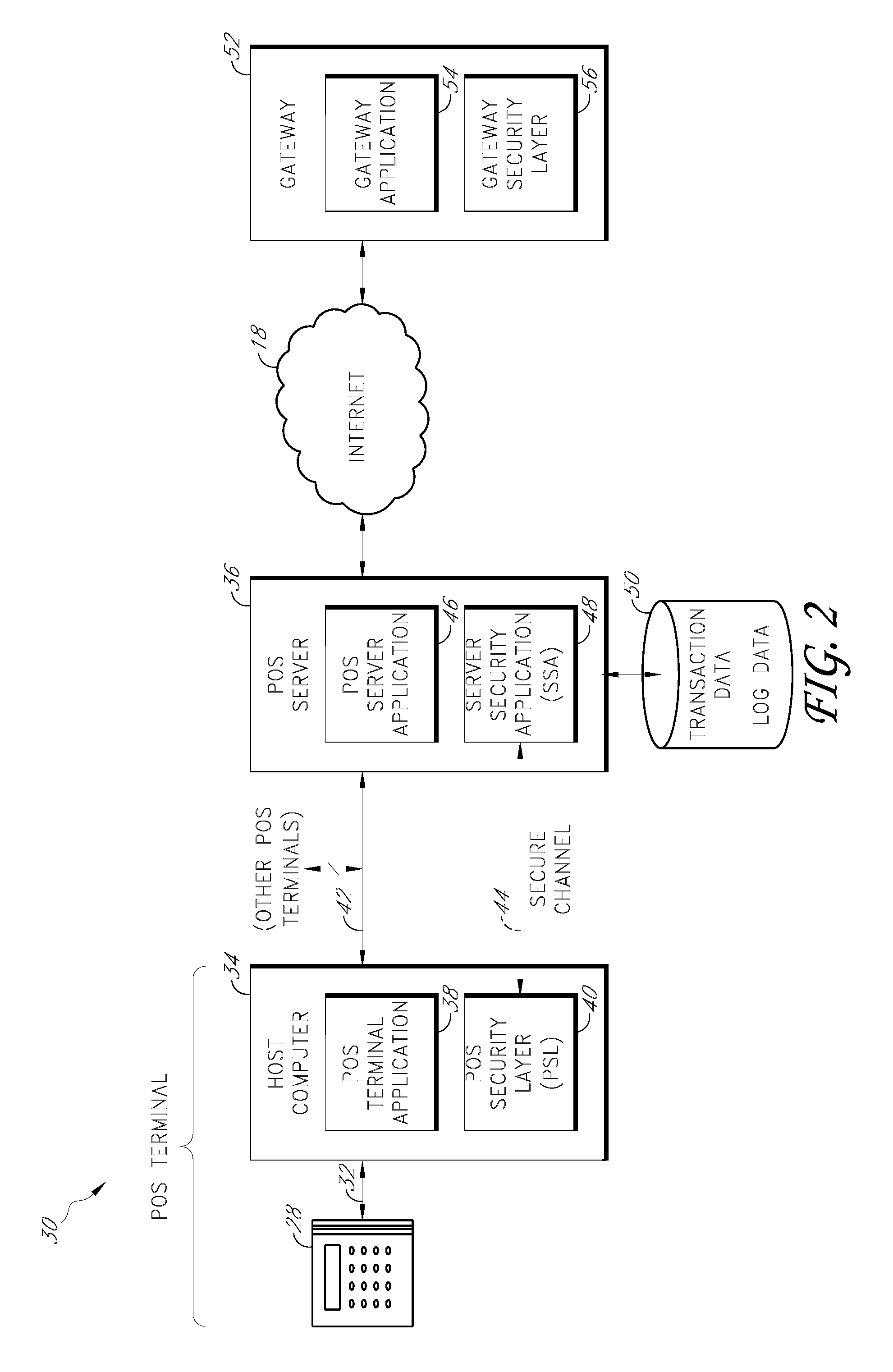
Secure payment card transactions
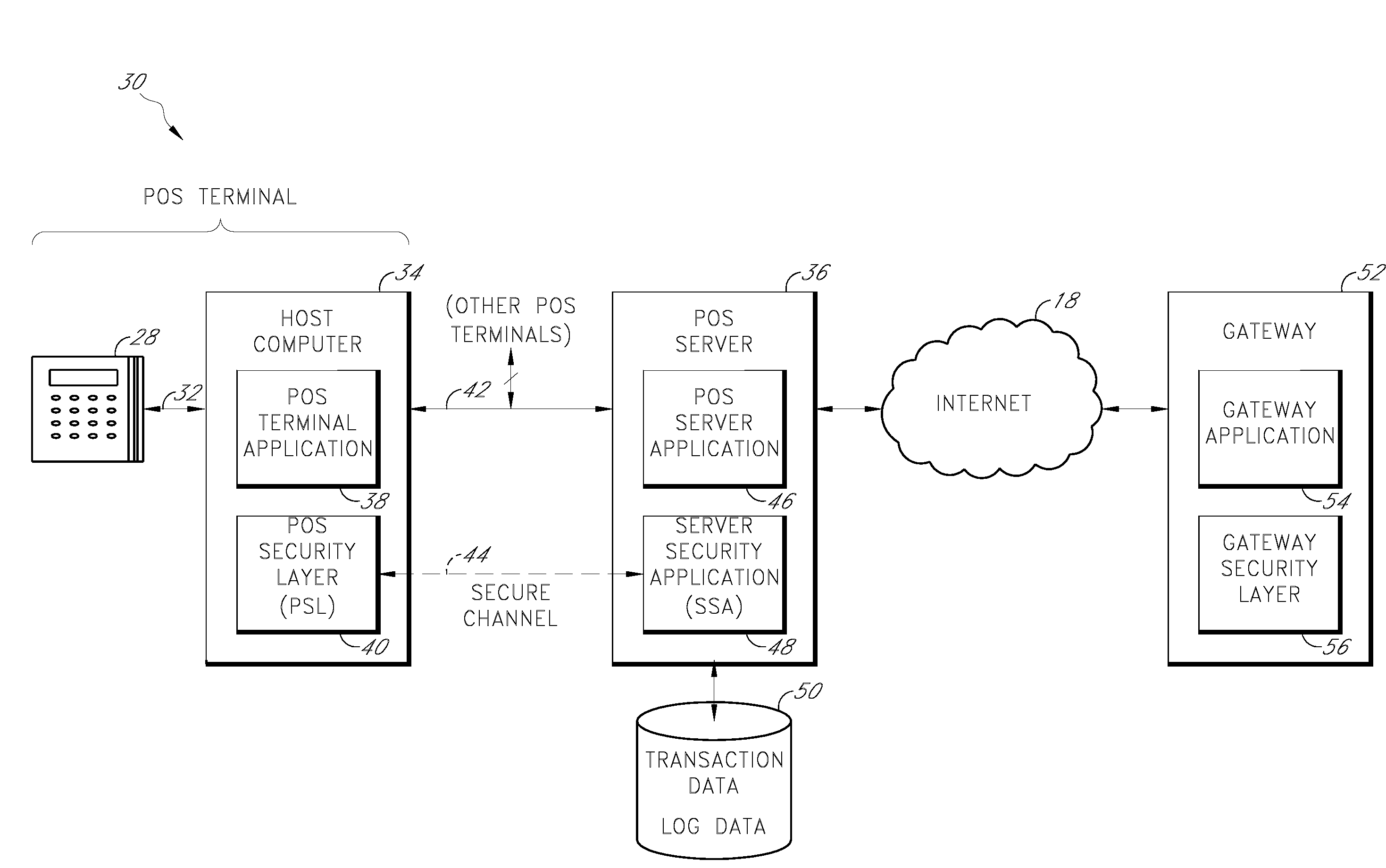
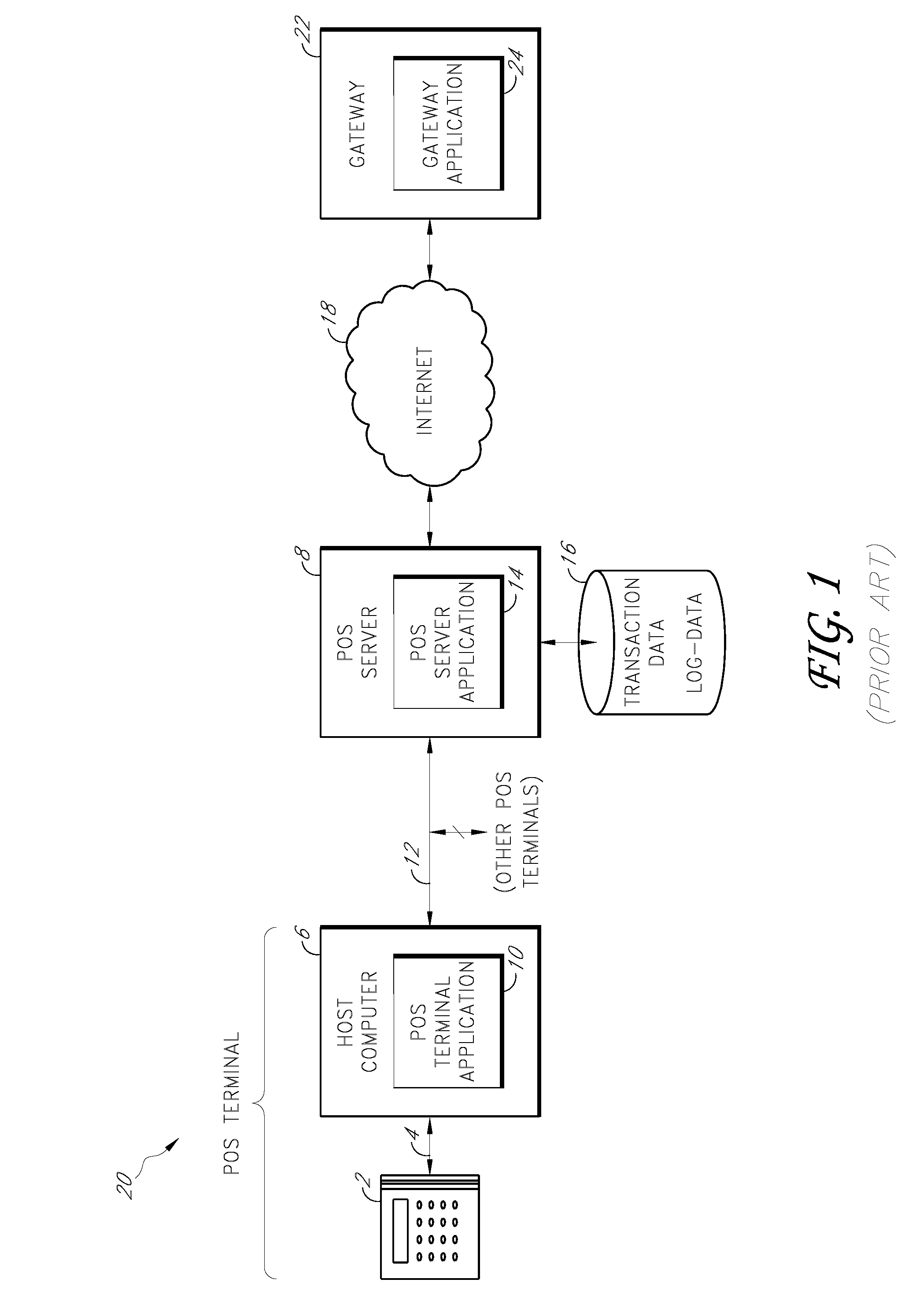
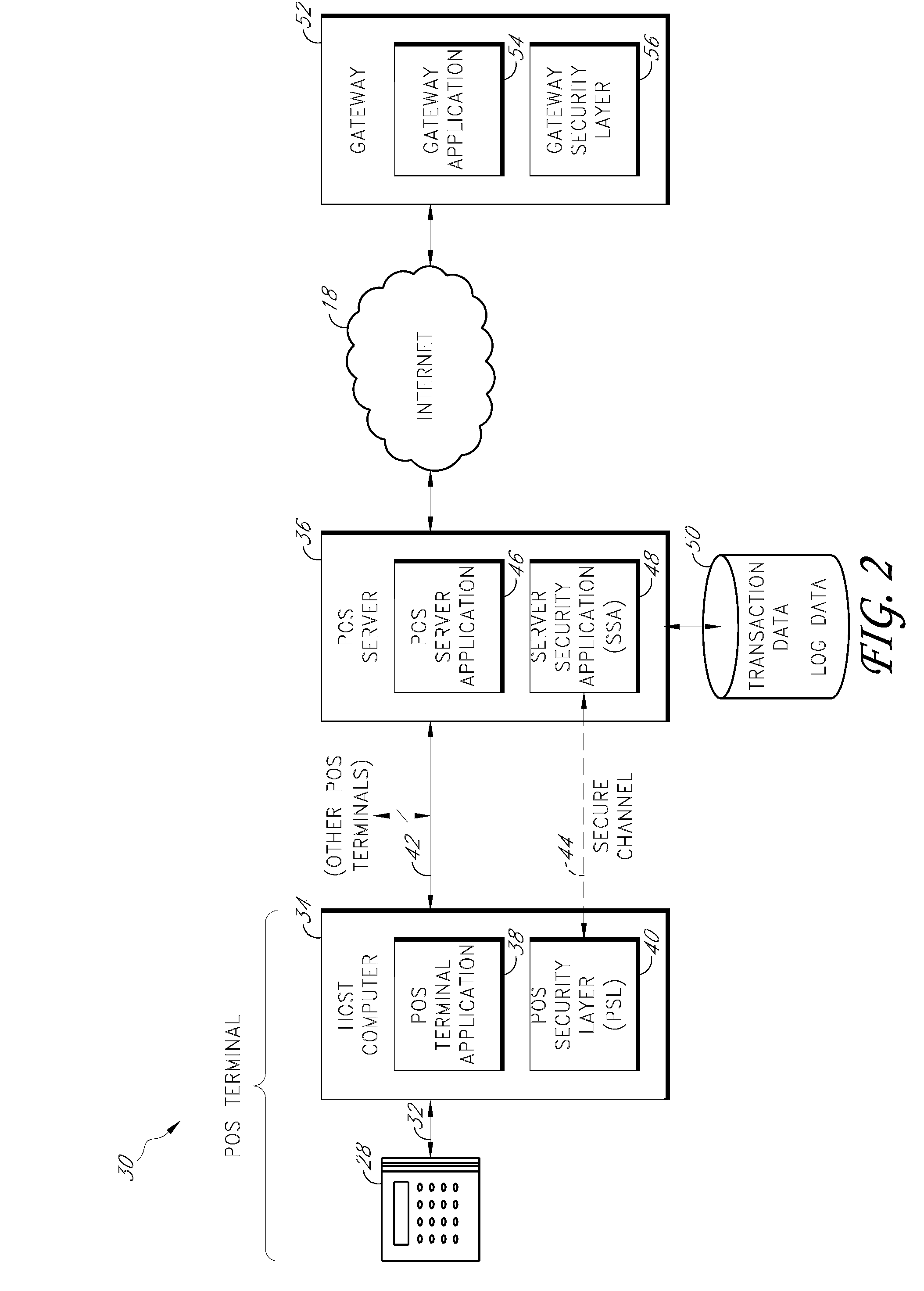
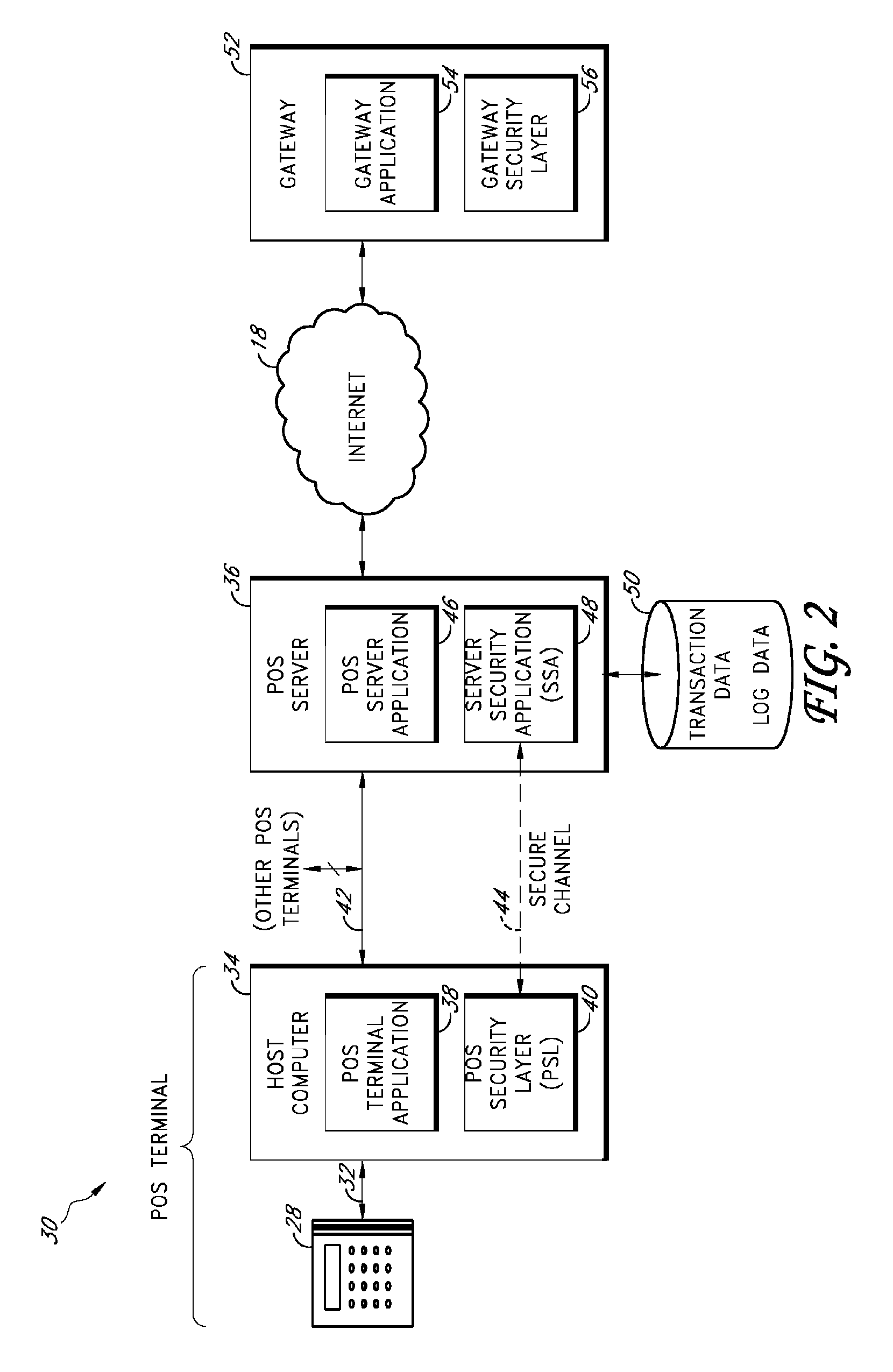
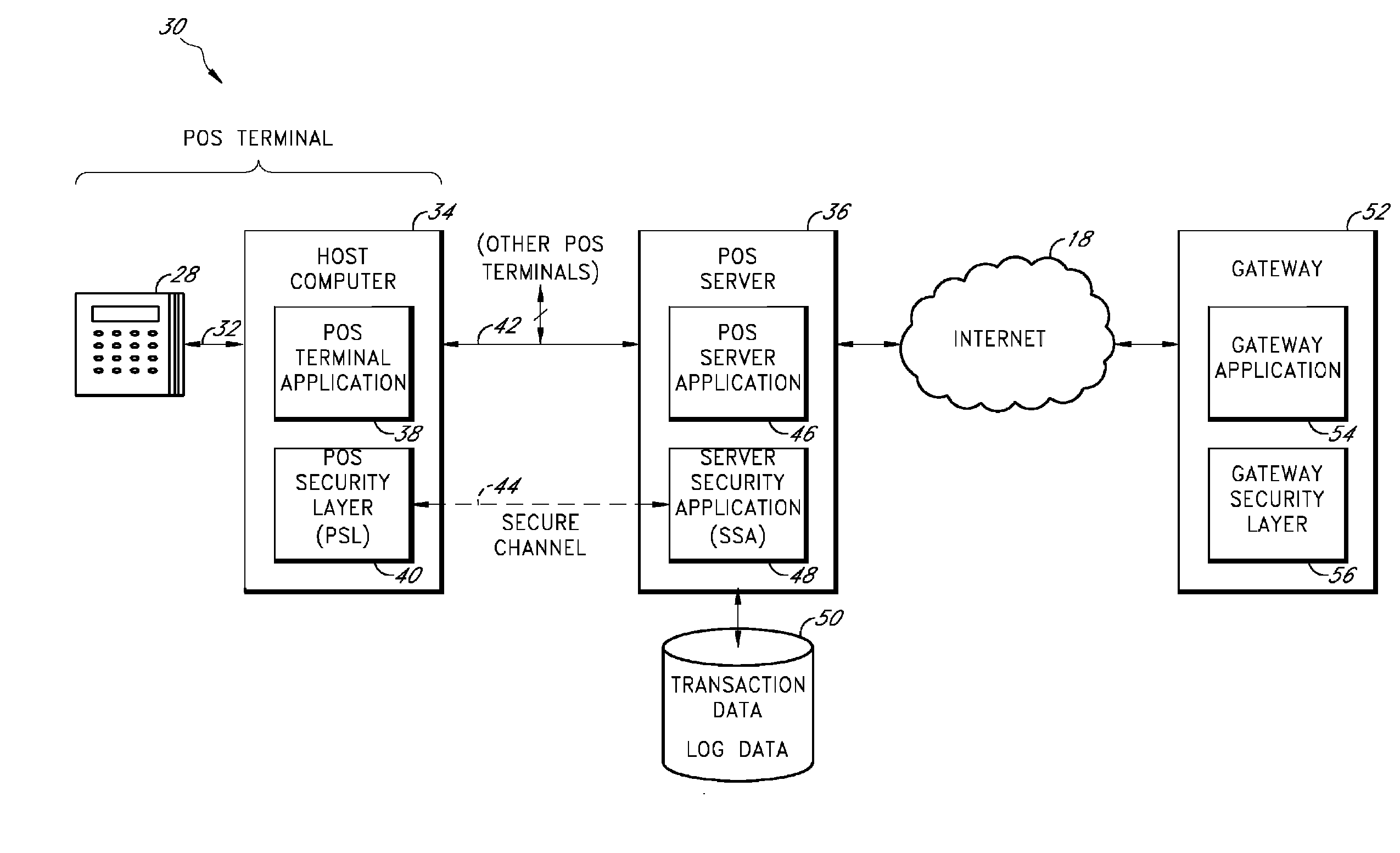
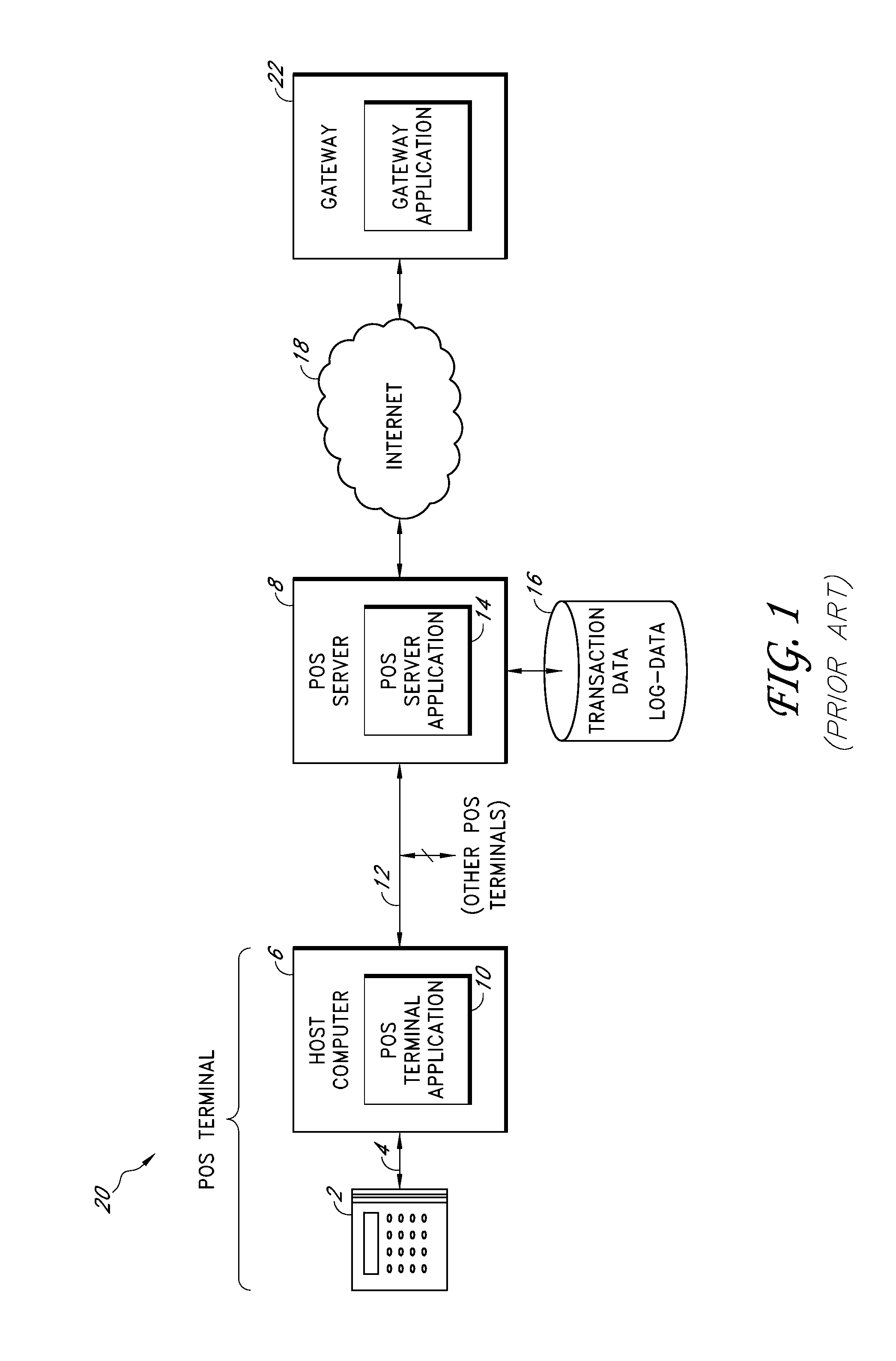
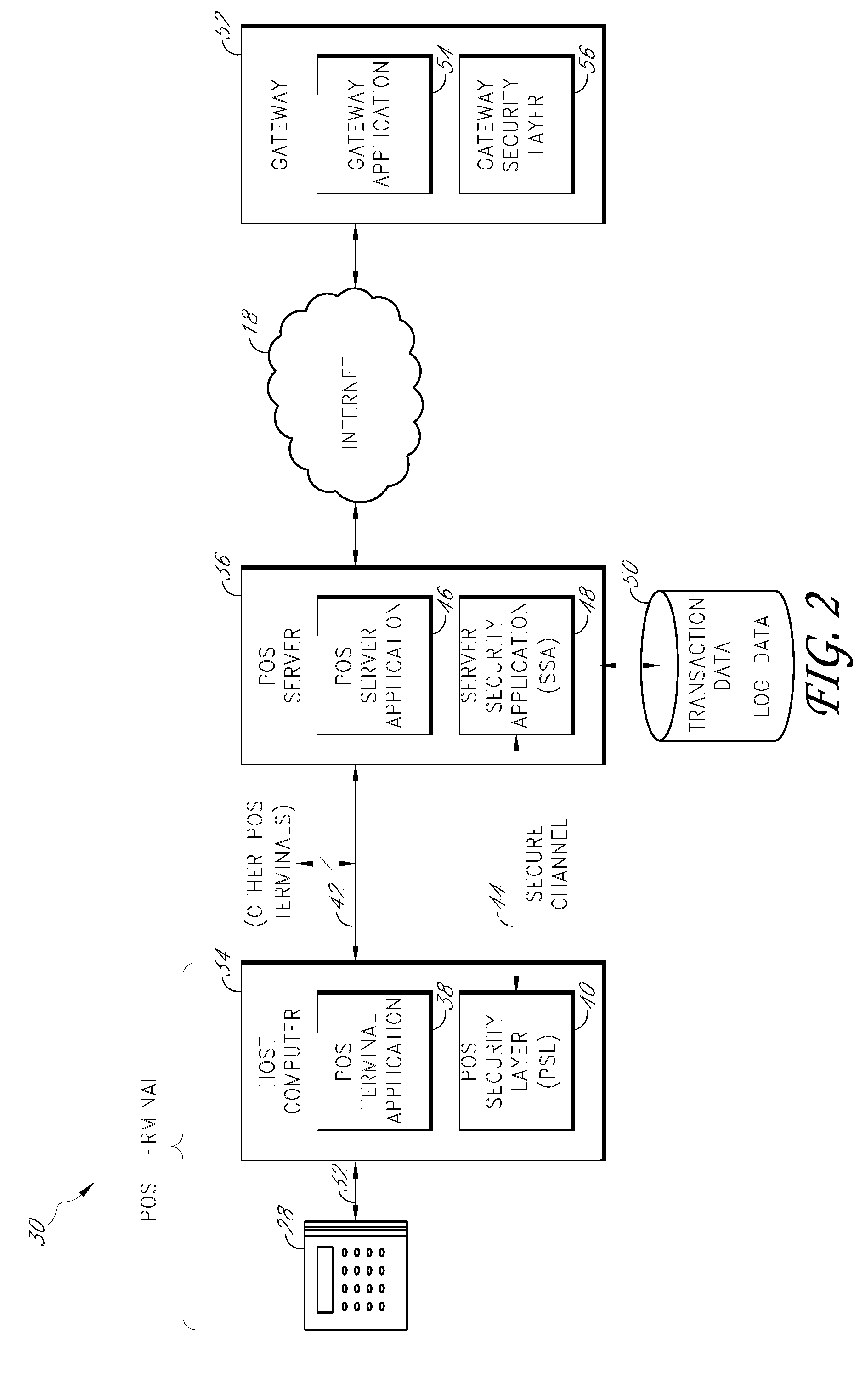
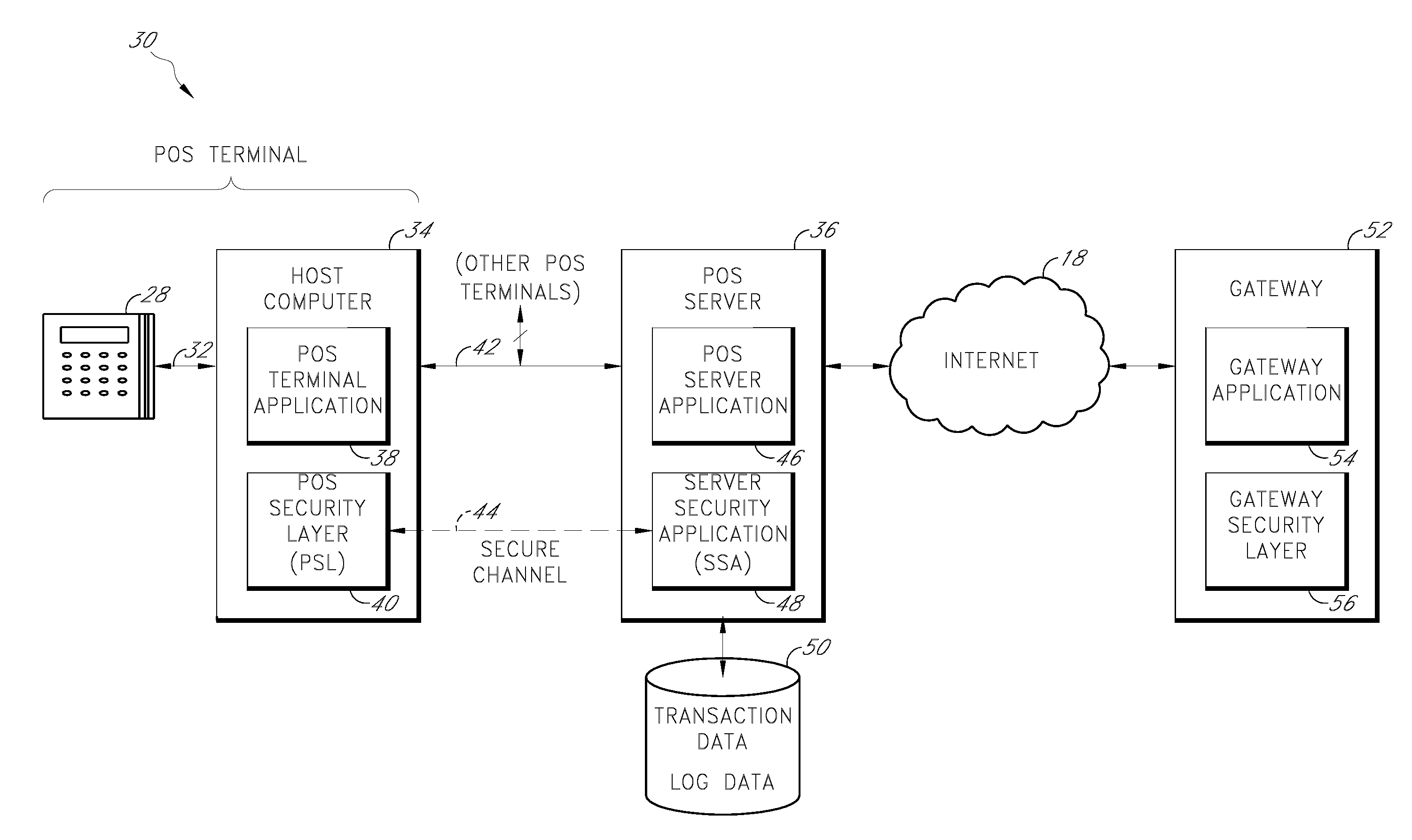
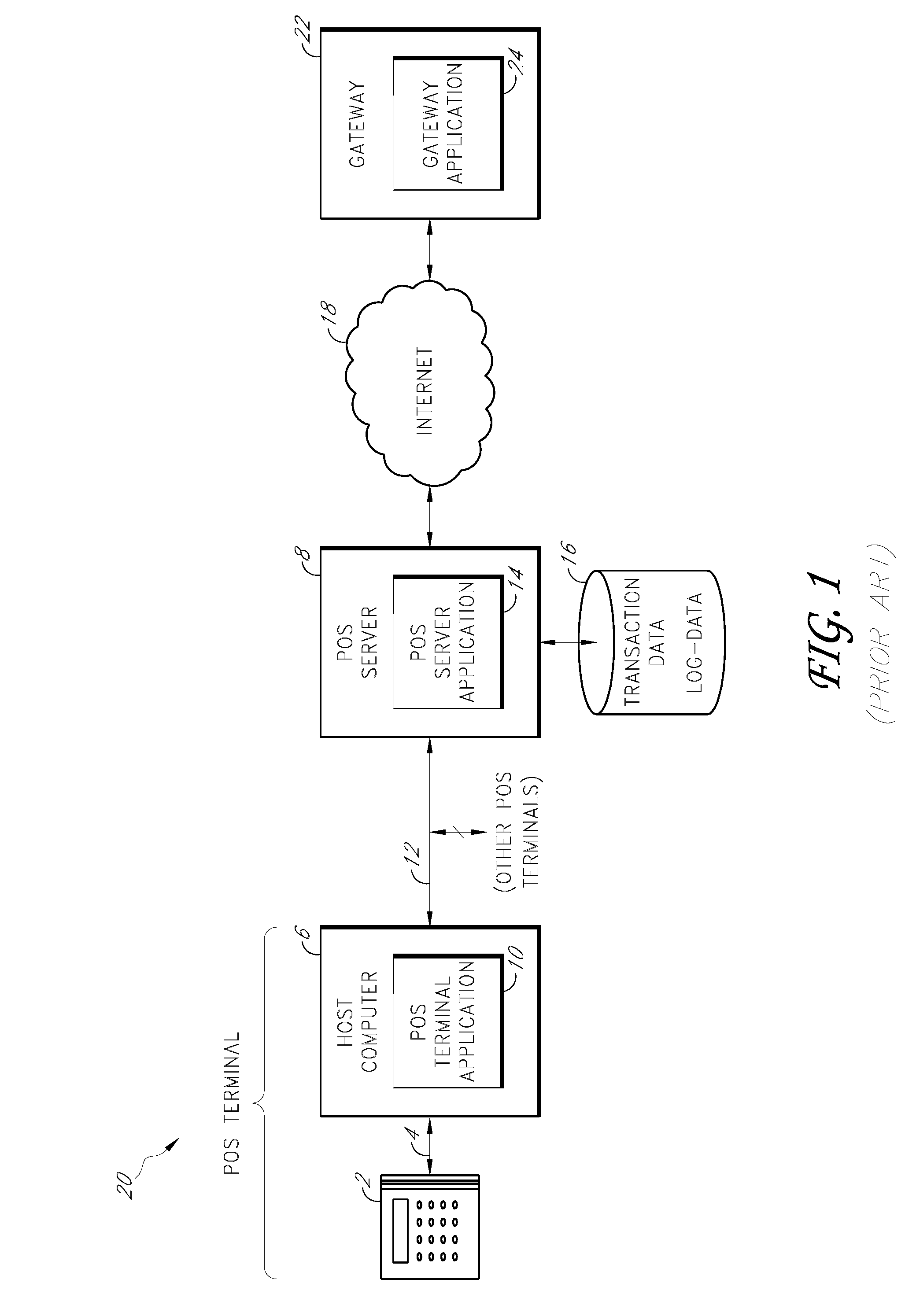
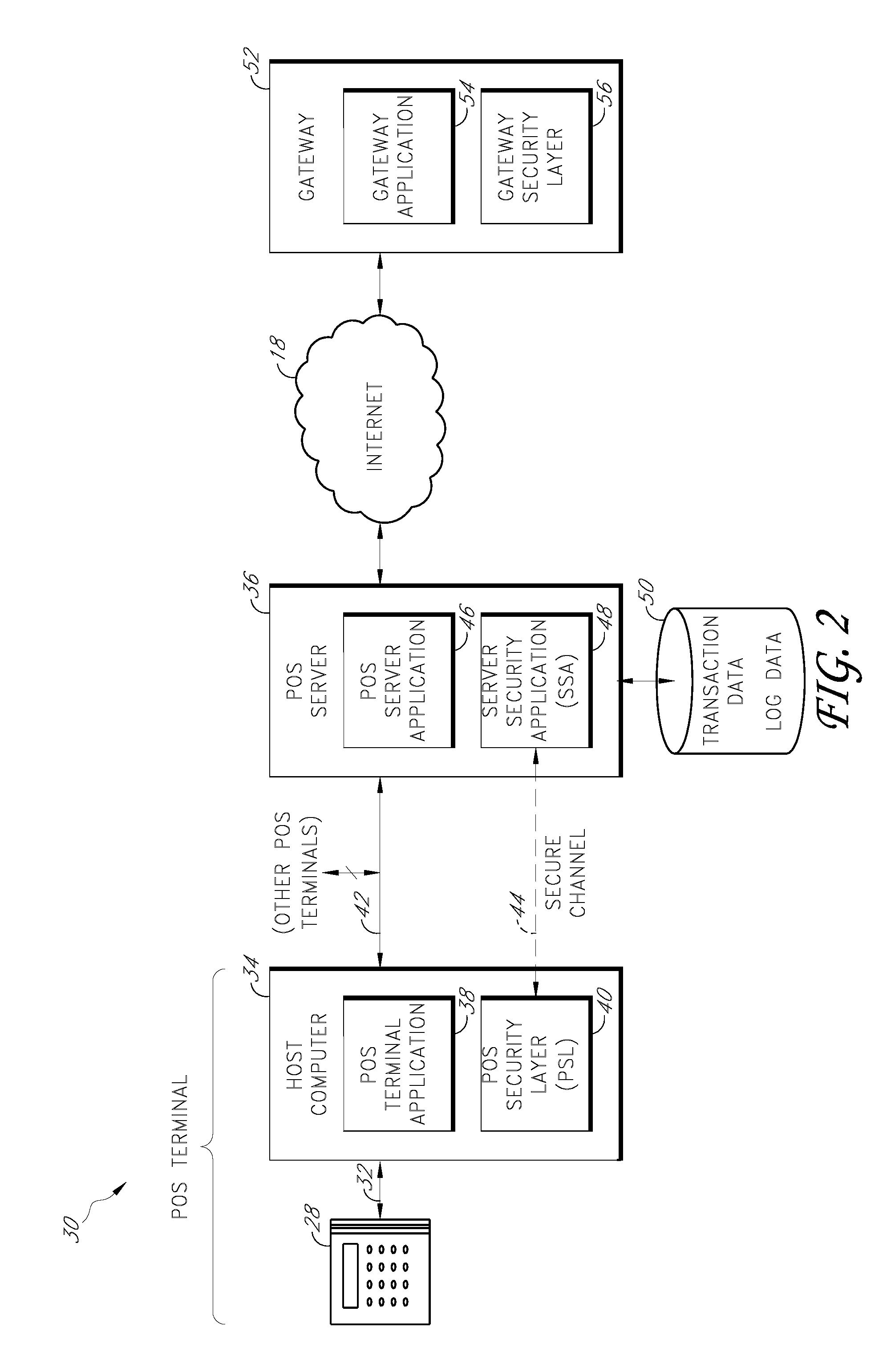
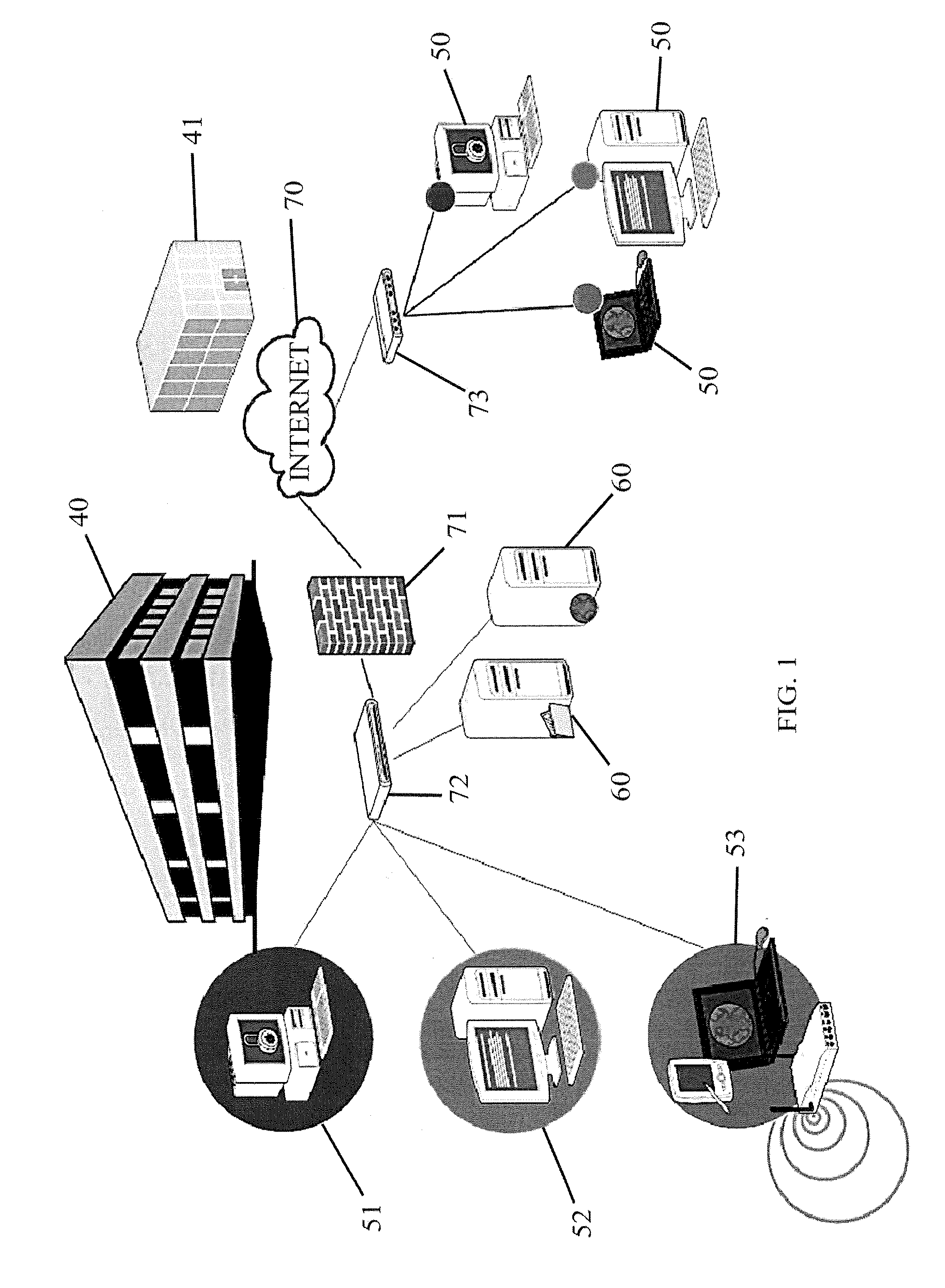
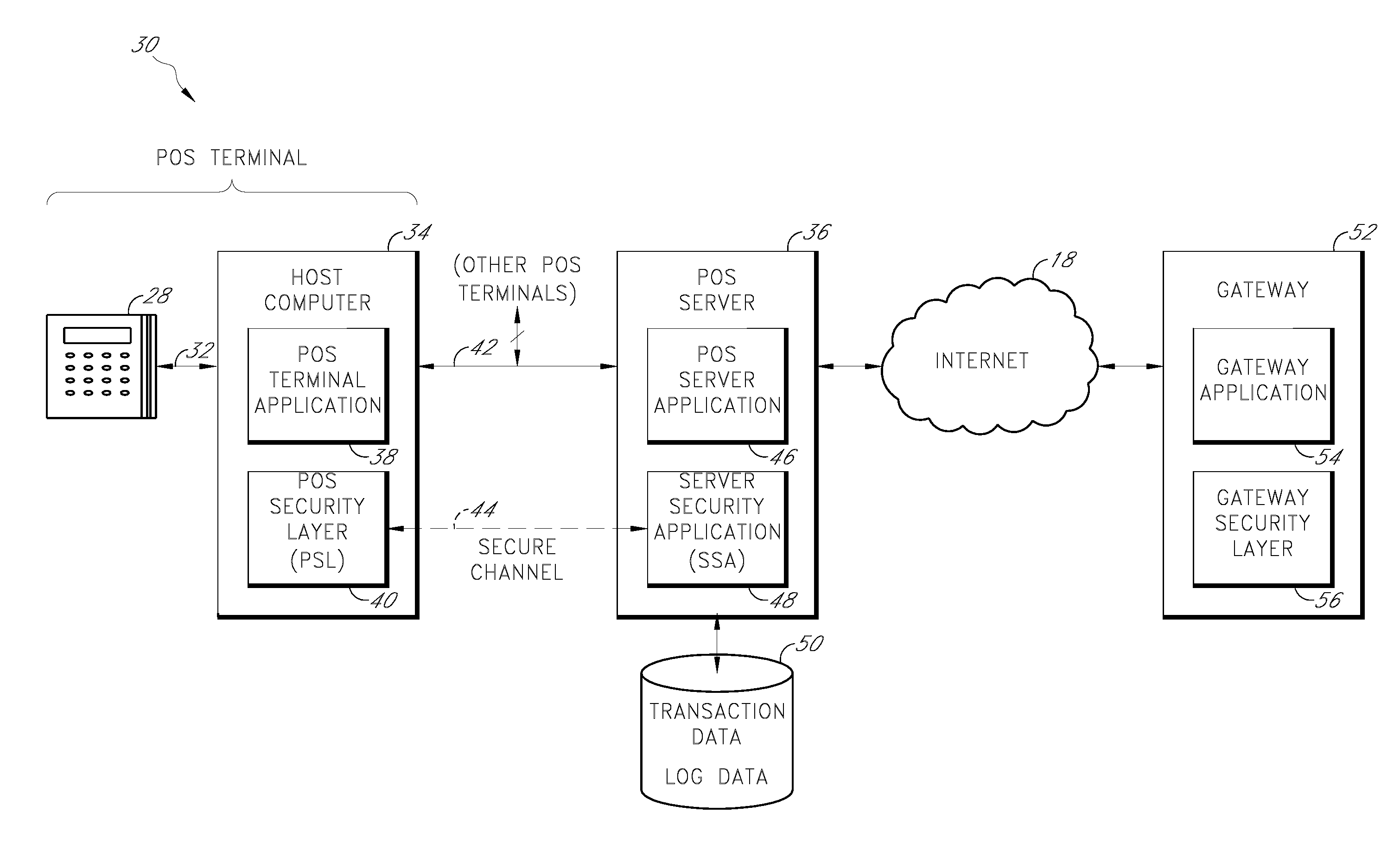
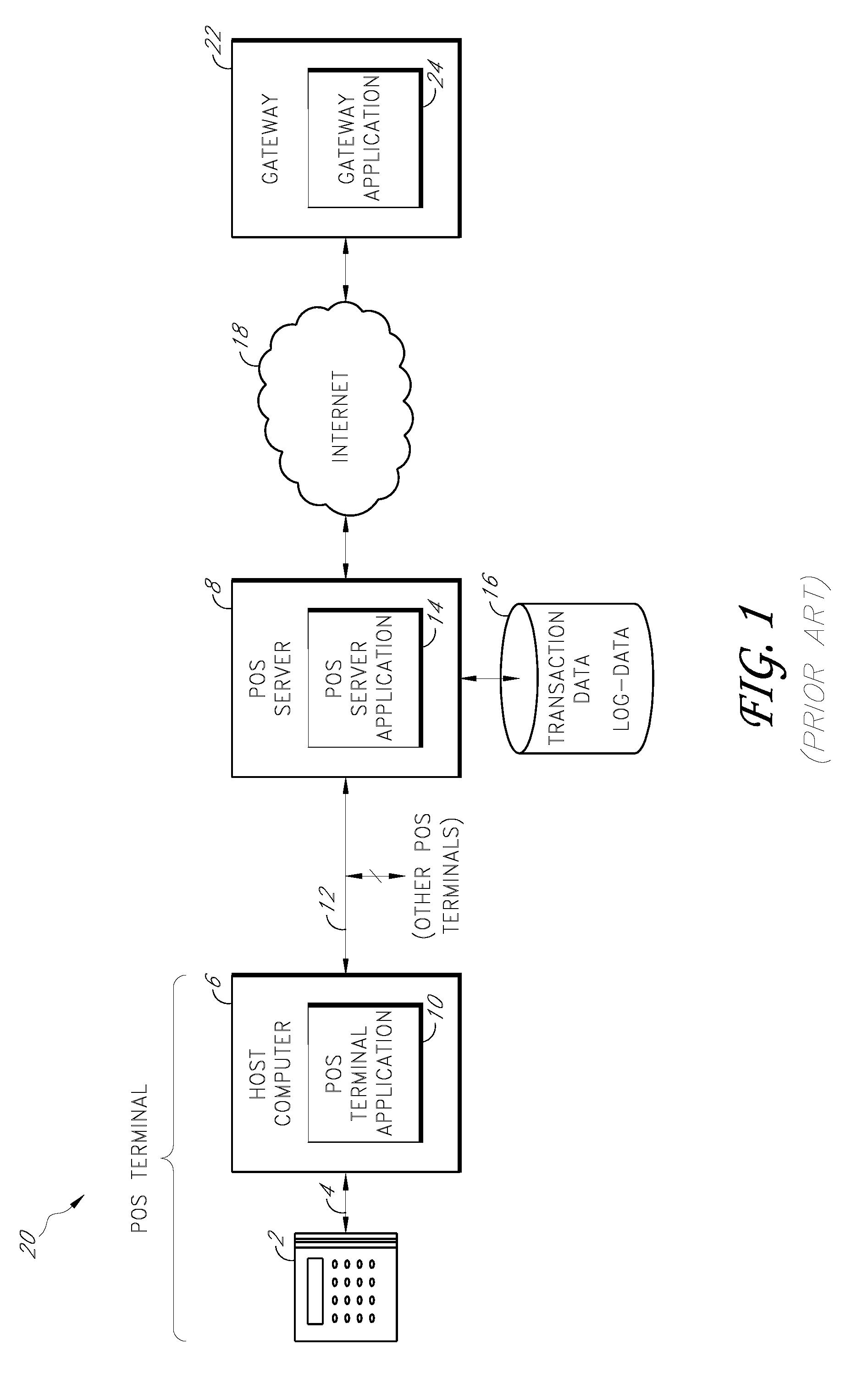
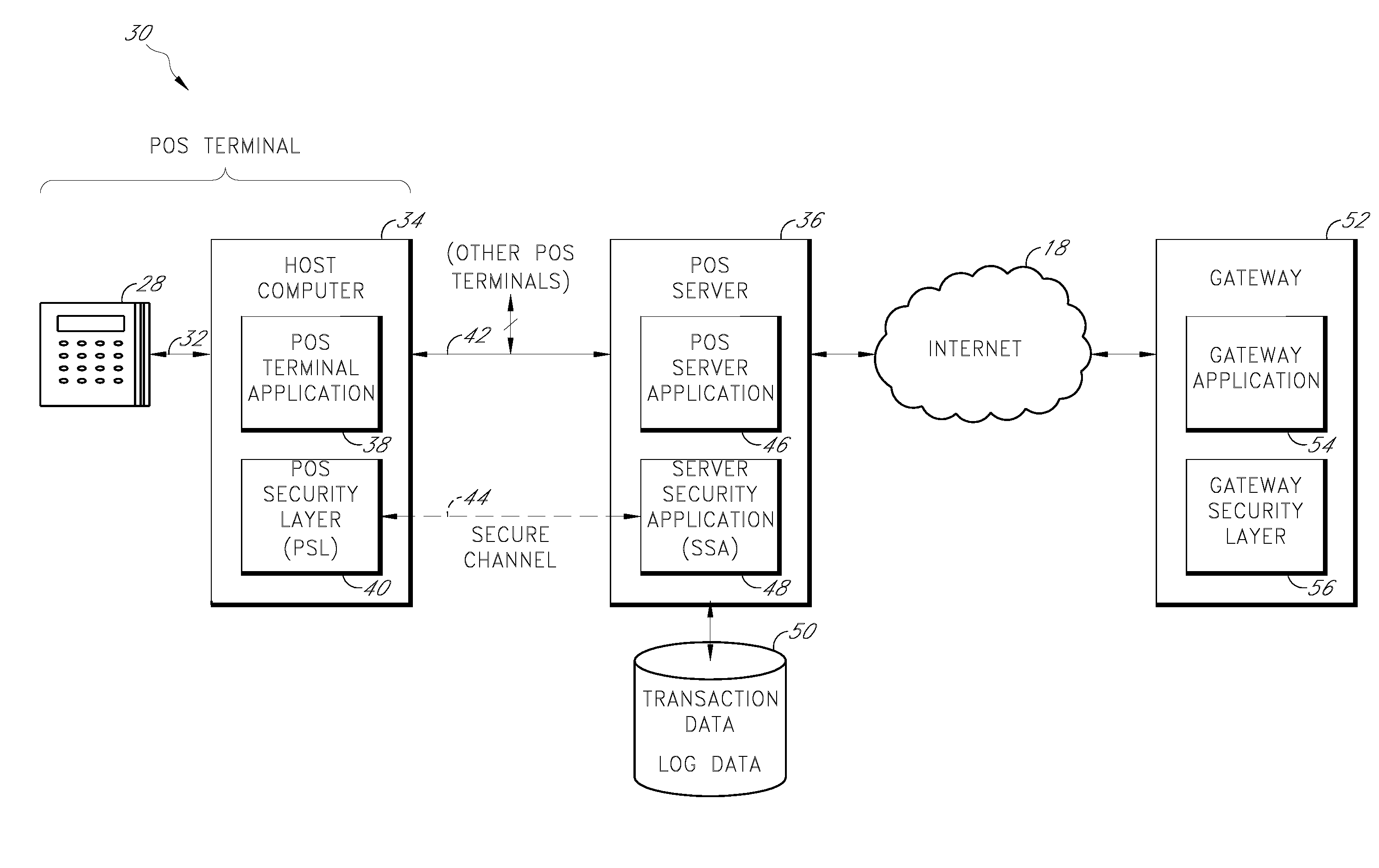
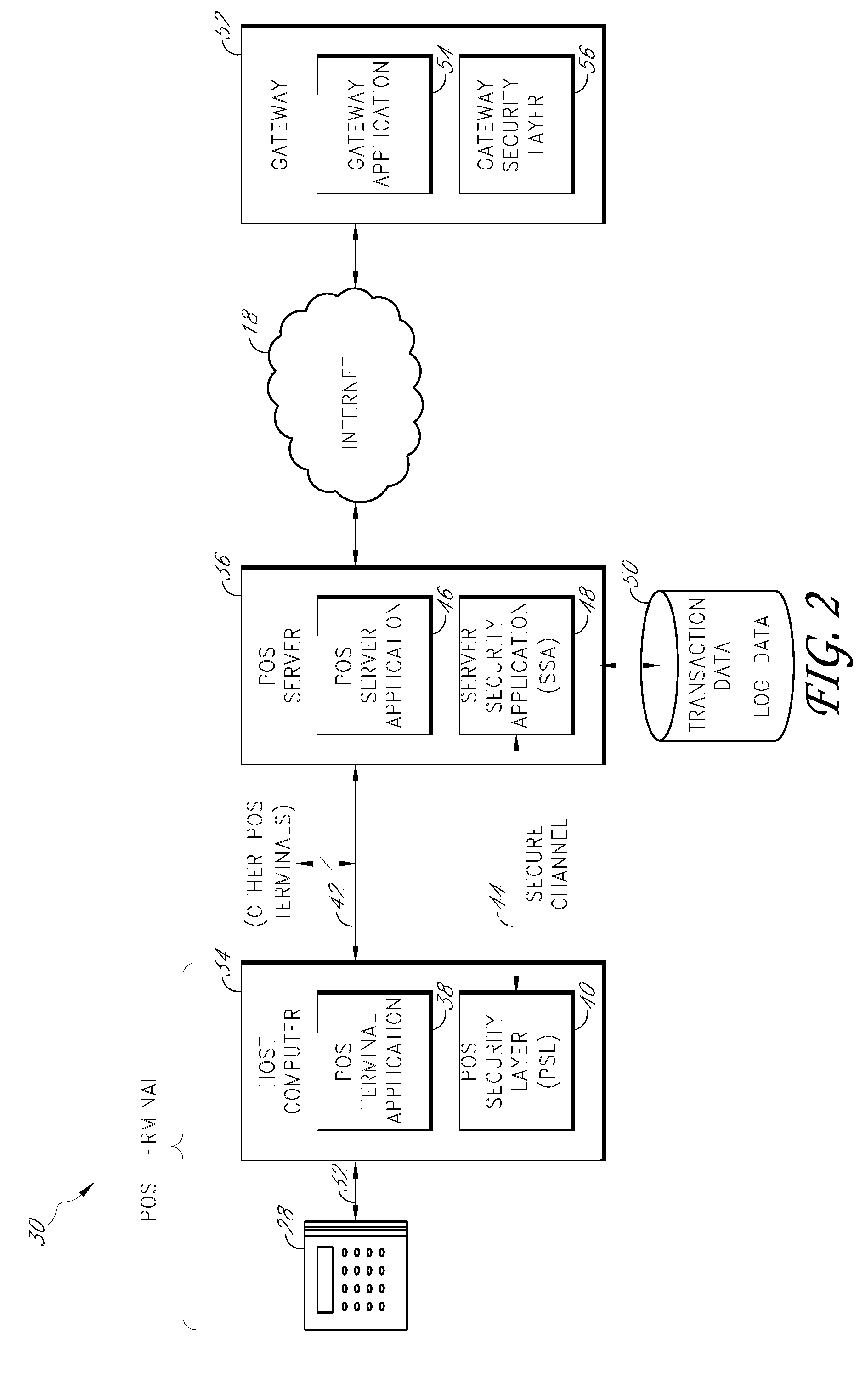
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
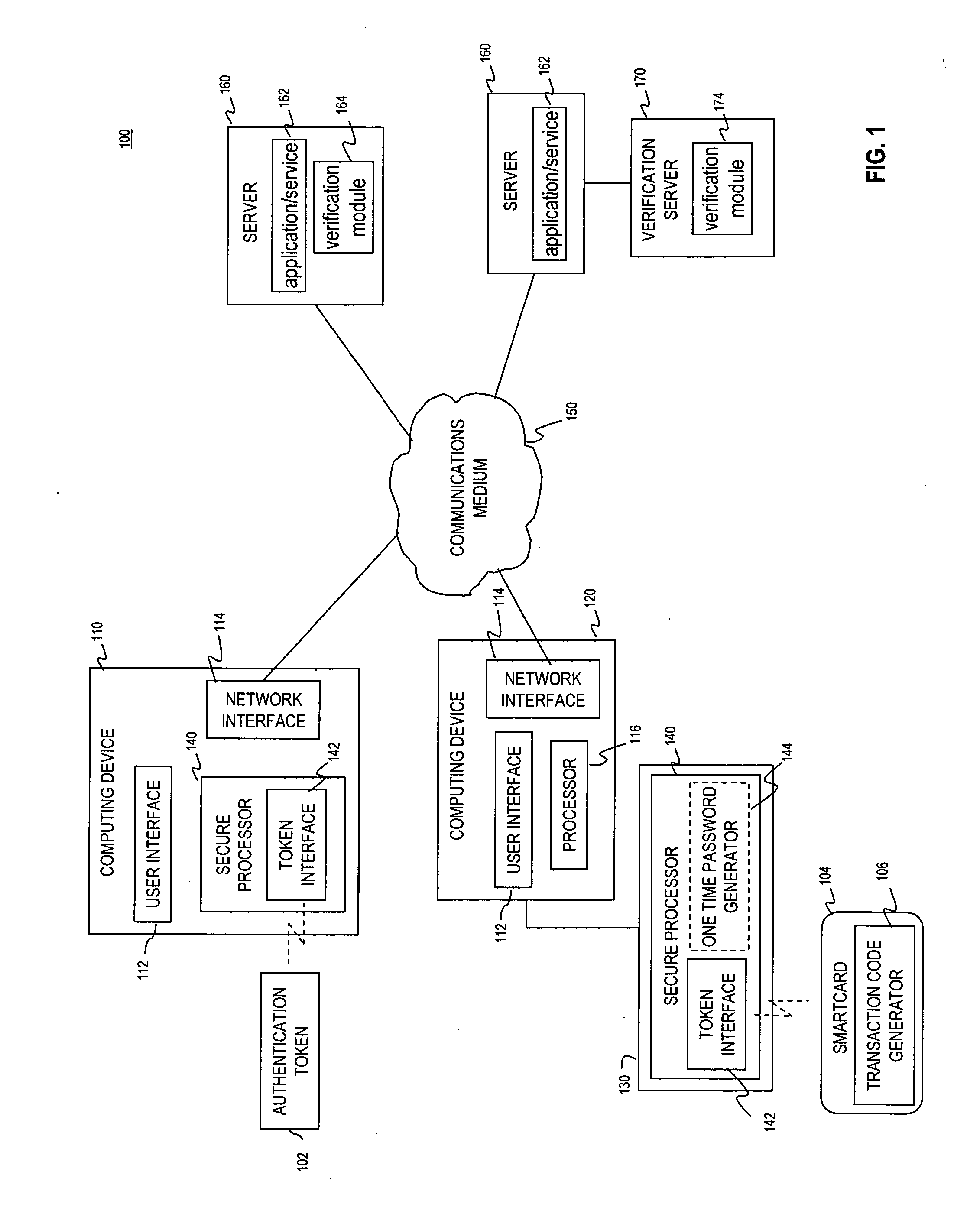
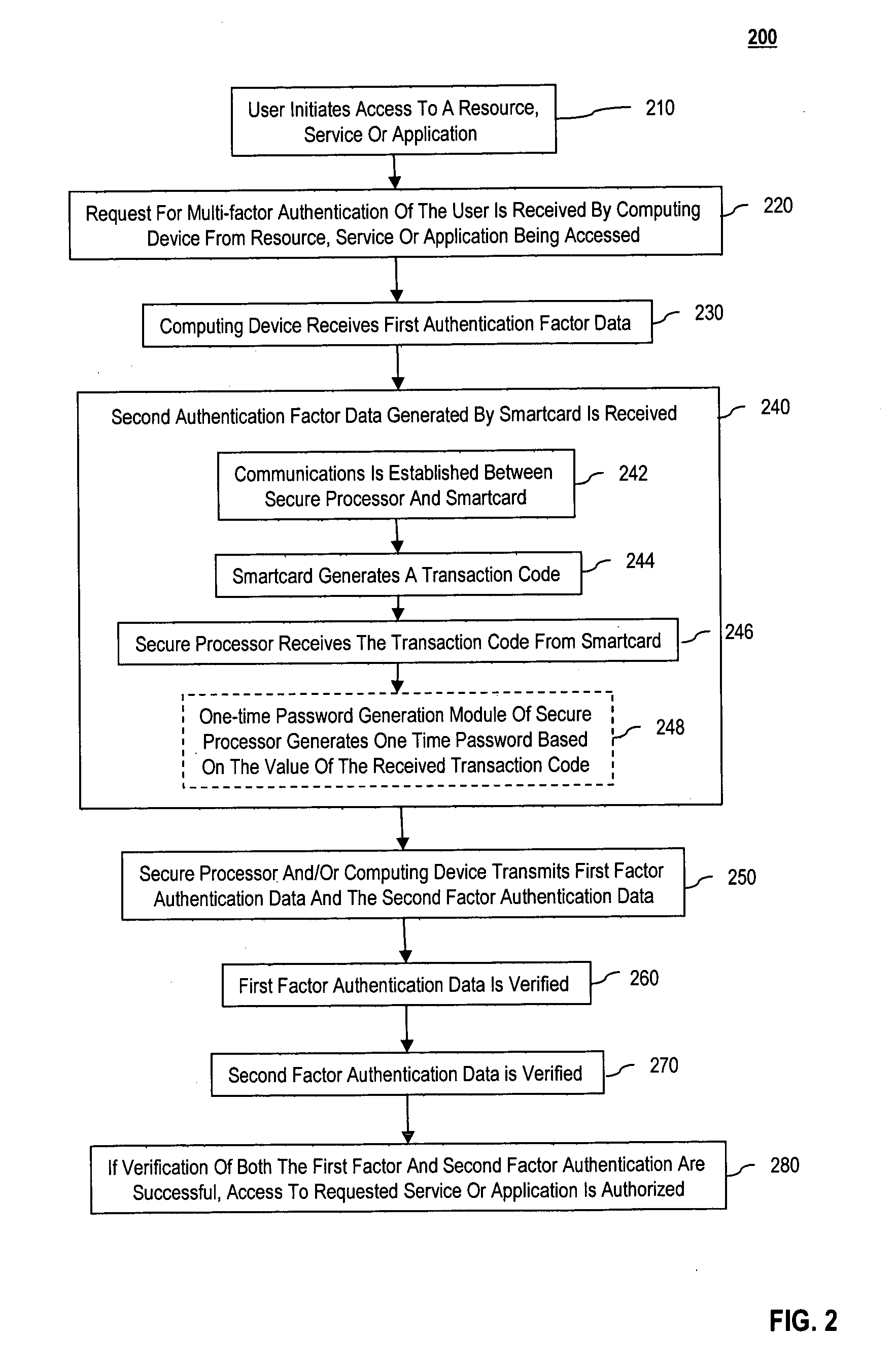
Multi-factor authentication using a smartcard
ActiveUS20070118745A1Digital data processing detailsUser identity/authority verificationSecure communicationThe Internet
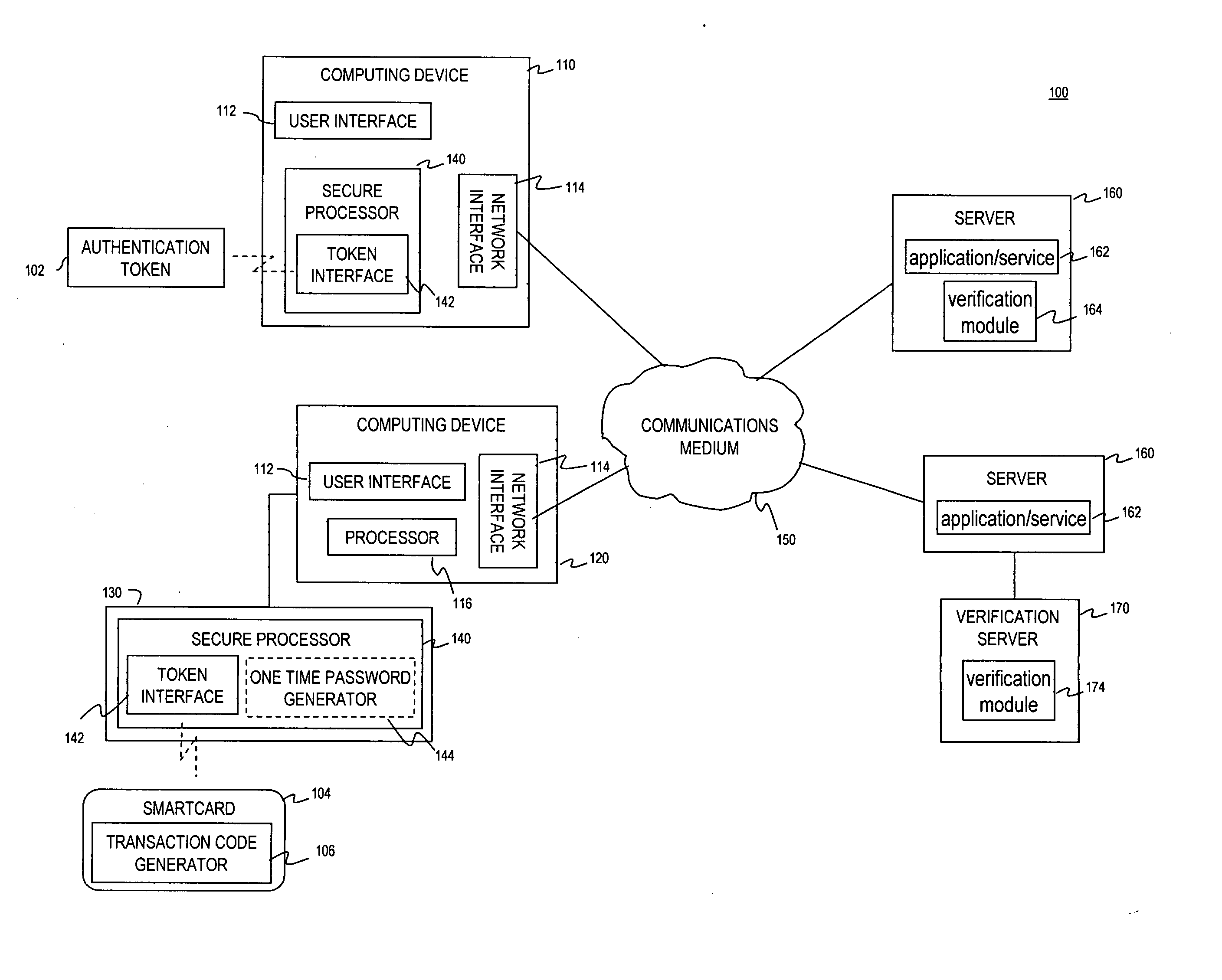
Methods and systems are provided for non-cryptographic capabilities of a token such as a smartcard to be used as an additional authentication factor when multi-factor authentication is required. Smartcards are configured to generate a transaction code each time a transaction is attempted by the smartcard. The transaction code is dynamic, changing with each transaction, and therefore is used as a one-time password. When a user attempts to access a service or application requiring at least two authentication factors, a secure processor is used to read transaction code from the smartcard. The secure processor establishes a secure communication with the remote computer hosting the service or application. The transaction code can then be encrypted prior to transmission over the public Internet, providing an additional layer of security.
Owner:AVAGO TECH INT SALES PTE LTD
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
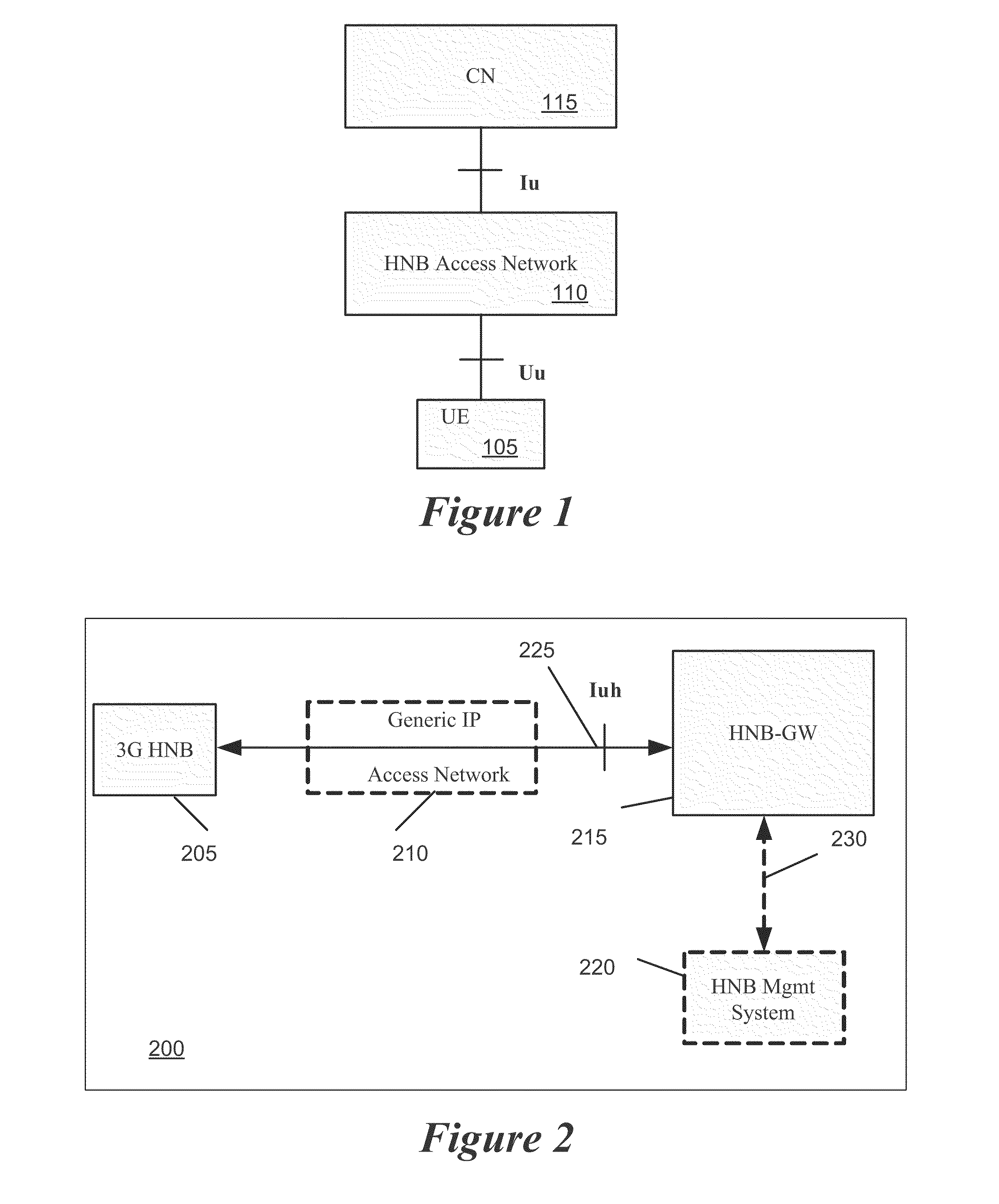
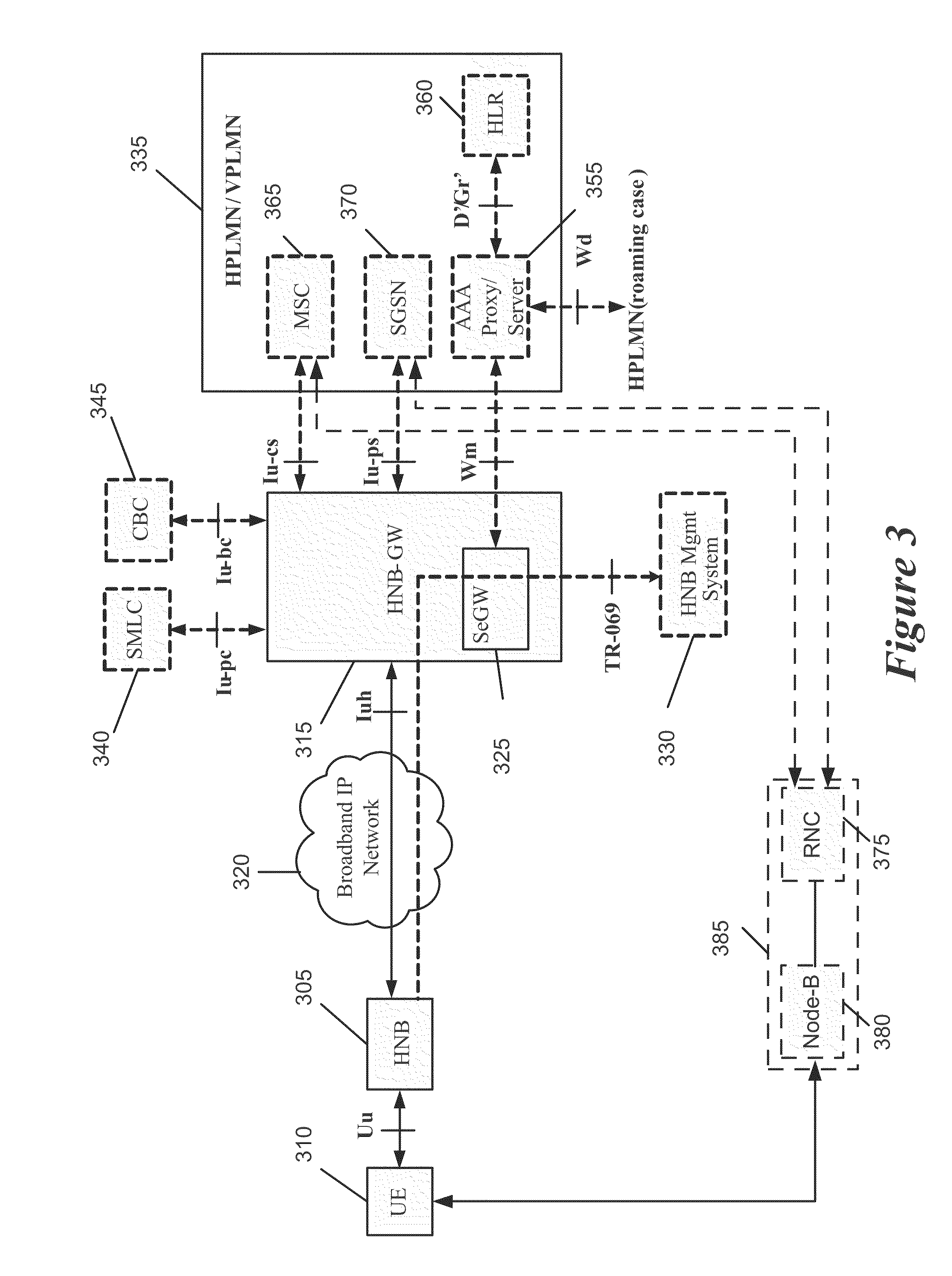
Home Node B System Architecture with Support for RANAP User Adaptation Protocol
InactiveUS20090265543A1Lower deployment costsSpeed andAssess restrictionNetwork topologiesHome Node BTransport layer
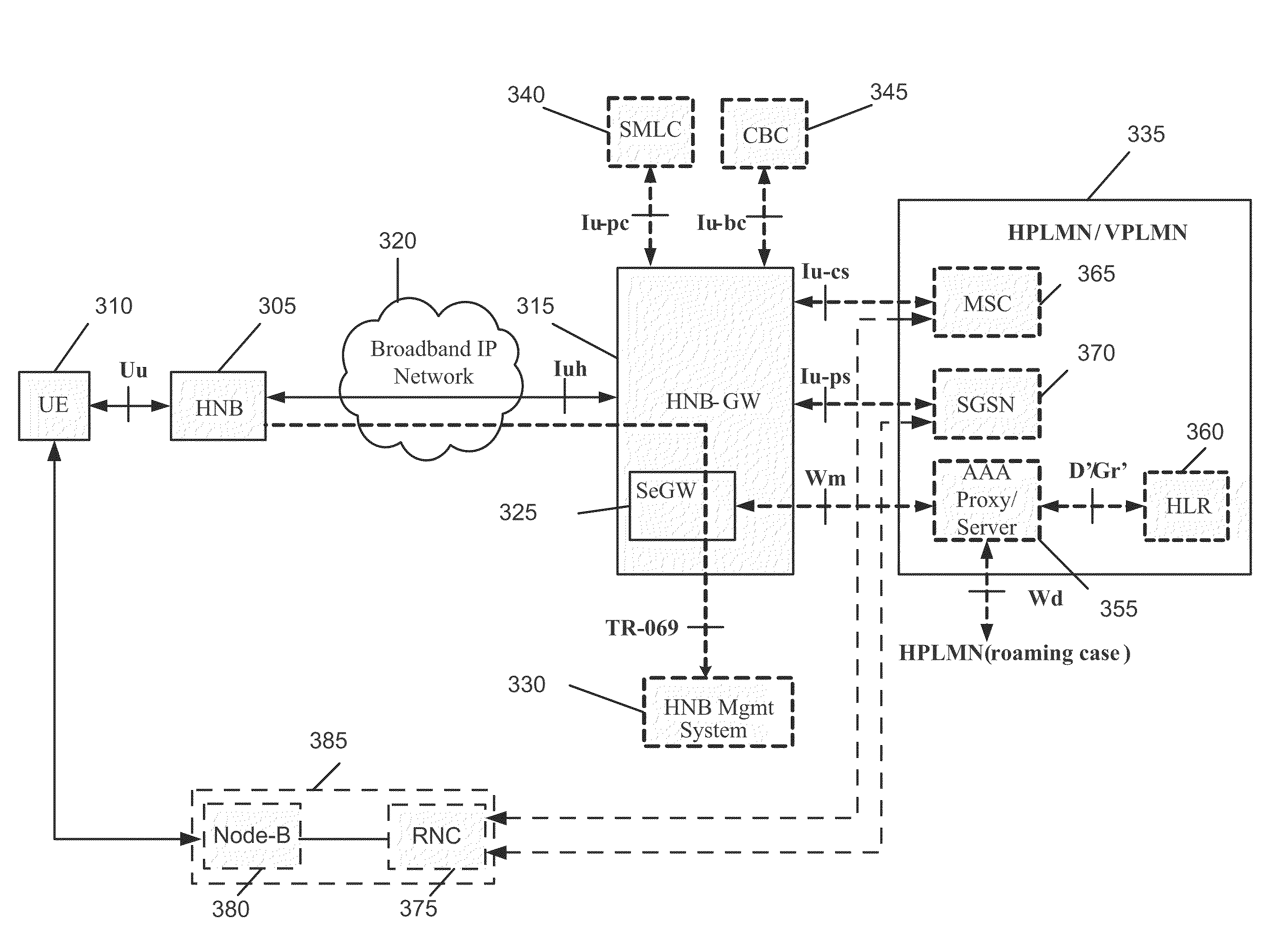
Some embodiments are implemented in a communication system that includes a first communication system comprised of a licensed wireless radio access network and a core network, and a second communication system comprising a plurality of user hosted access points and a network controller. In some embodiments, each access point operates using short range licensed wireless frequencies to establish a service region. In some embodiments, the network controller communicatively couples the core network to the plurality of access points. The method uses three sets of protocol layers: a security layer, a transport layer, and a layer for transferring Radio Access Network Application Part (RANAP) messages, to communicate between the network controller and one of the access points. The method also uses the Iuh interface for the transport of messages across the three sets of protocol layers.
Owner:KINETO WIRELESS
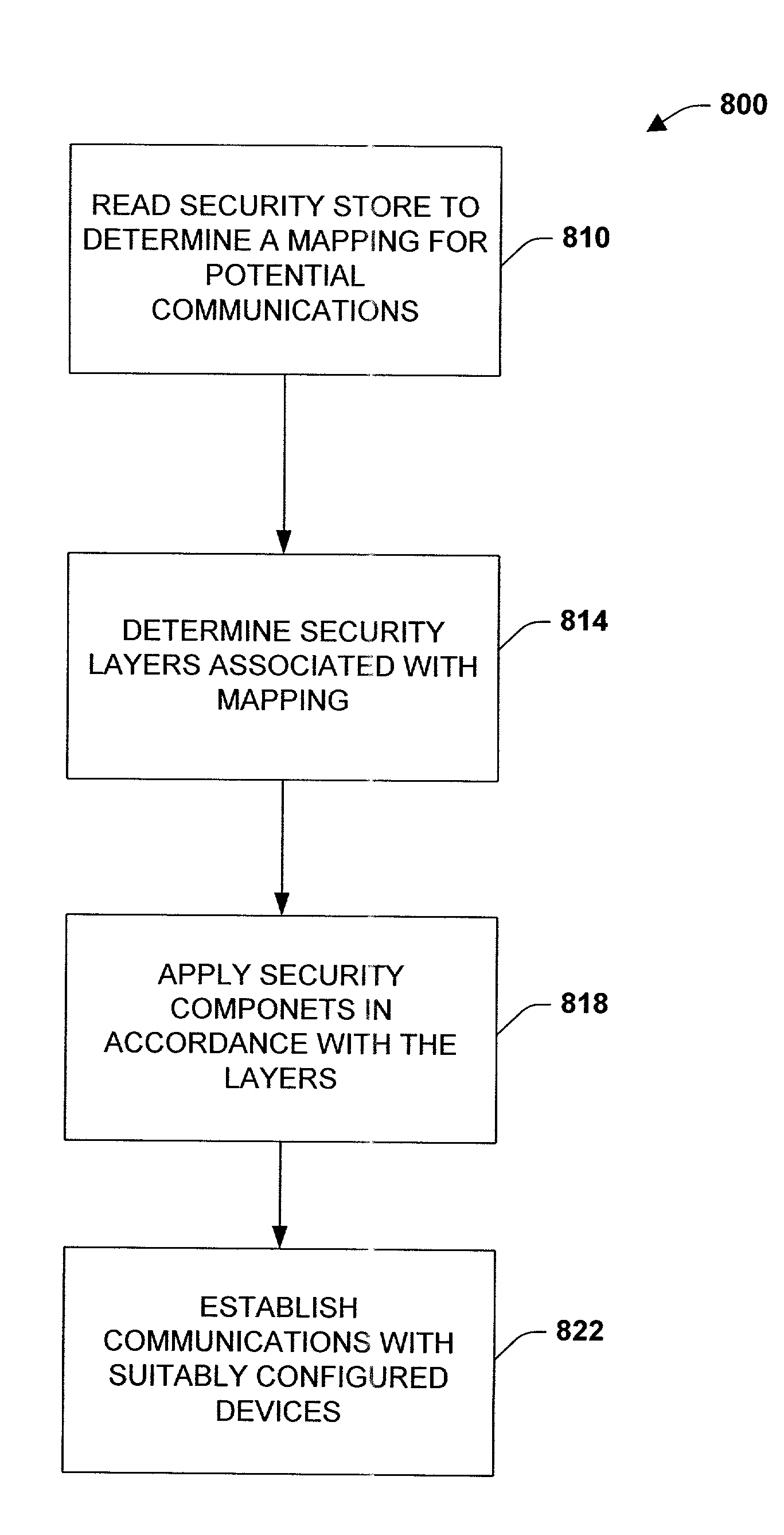
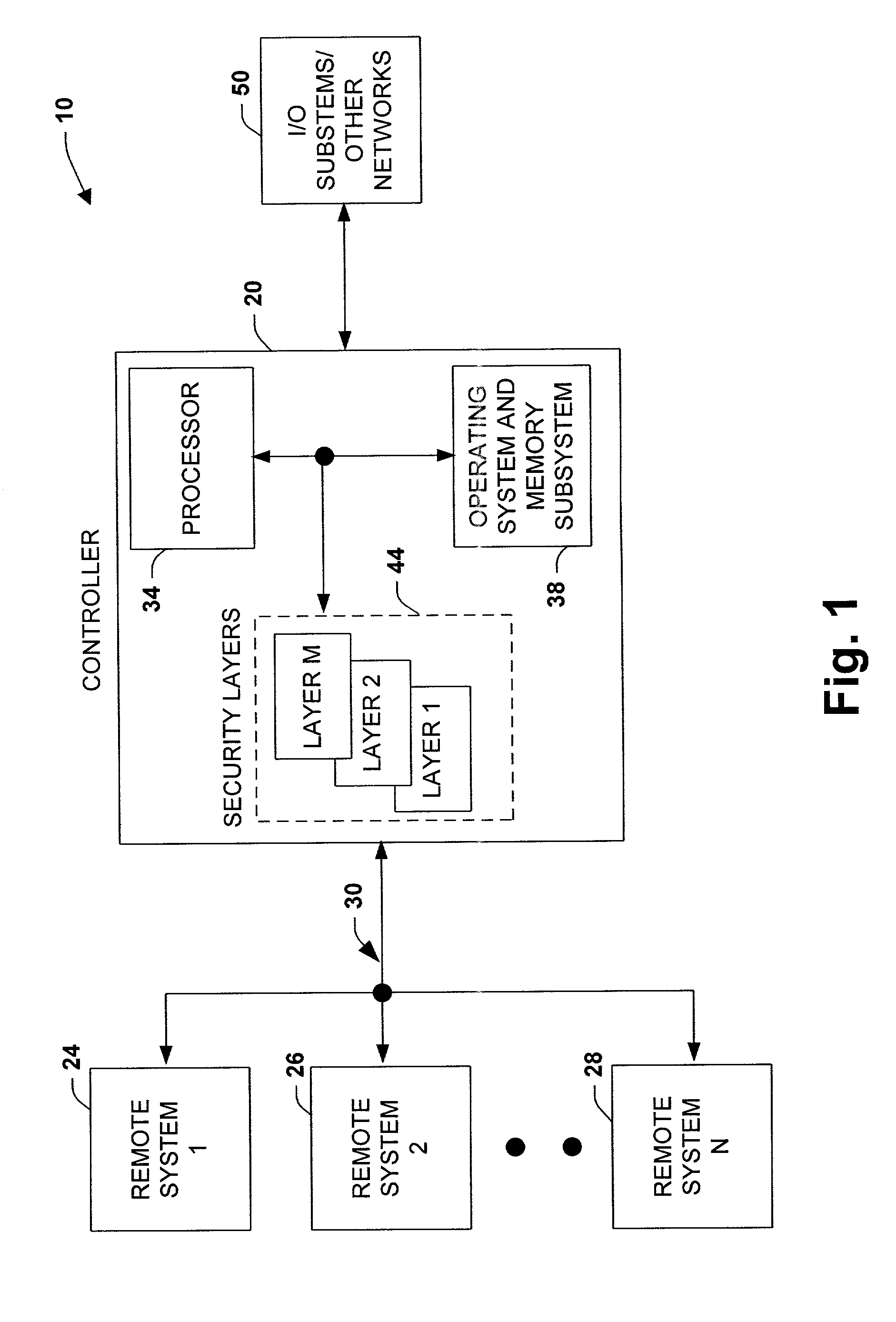
System and methodology providing multi-tier-security for network data exchange with industrial control components
ActiveUS7536548B1Well formedMitigates unauthorized data accessDigital data processing detailsUser identity/authority verificationOperational systemData access
The present invention relates to a system and methodology facilitating network security and data access in an industrial control environment. An industrial control system is provided that includes an industrial controller to communicate with a network. At least one security layer can be configured in the industrial controller, wherein the security layer can be associated with one or more security components to control and / or restrict data access to the controller. An operating system manages the security layer in accordance with a processor to limit or mitigate communications from the network based upon the configured security layer or layers.
Owner:ROCKWELL AUTOMATION TECH
Method and system for managing security tiers
InactiveUS6889210B1Fold preciselyKey distribution for secure communicationUser identity/authority verificationSecurity parameterControllability
Techniques for reorganizing security levels without implicating accessibility to secured files classified in accordance to one of the security levels are disclosed. In a case of adding a new security level, the controllability or restrictiveness of the new security level is determined with respect to the most restrictive security level or the least security level in a set of existing security levels. A set of proper security parameters are then generated for the new security level and subsequently the existing security levels are reorganized to accommodate the new security level. In a case of removing a security level from the existing security levels, the security parameters for the security level to be deleted are either folded up or down to an immediate next security level, depending on implementation. As a result, the security parameters for the immediate next security level are updated to include those for the security level to be deleted such that the secured files classified at the security level to be deleted can still be accessed by those with proper clearance levels.
Owner:GUARDIAN DATA STORAGE
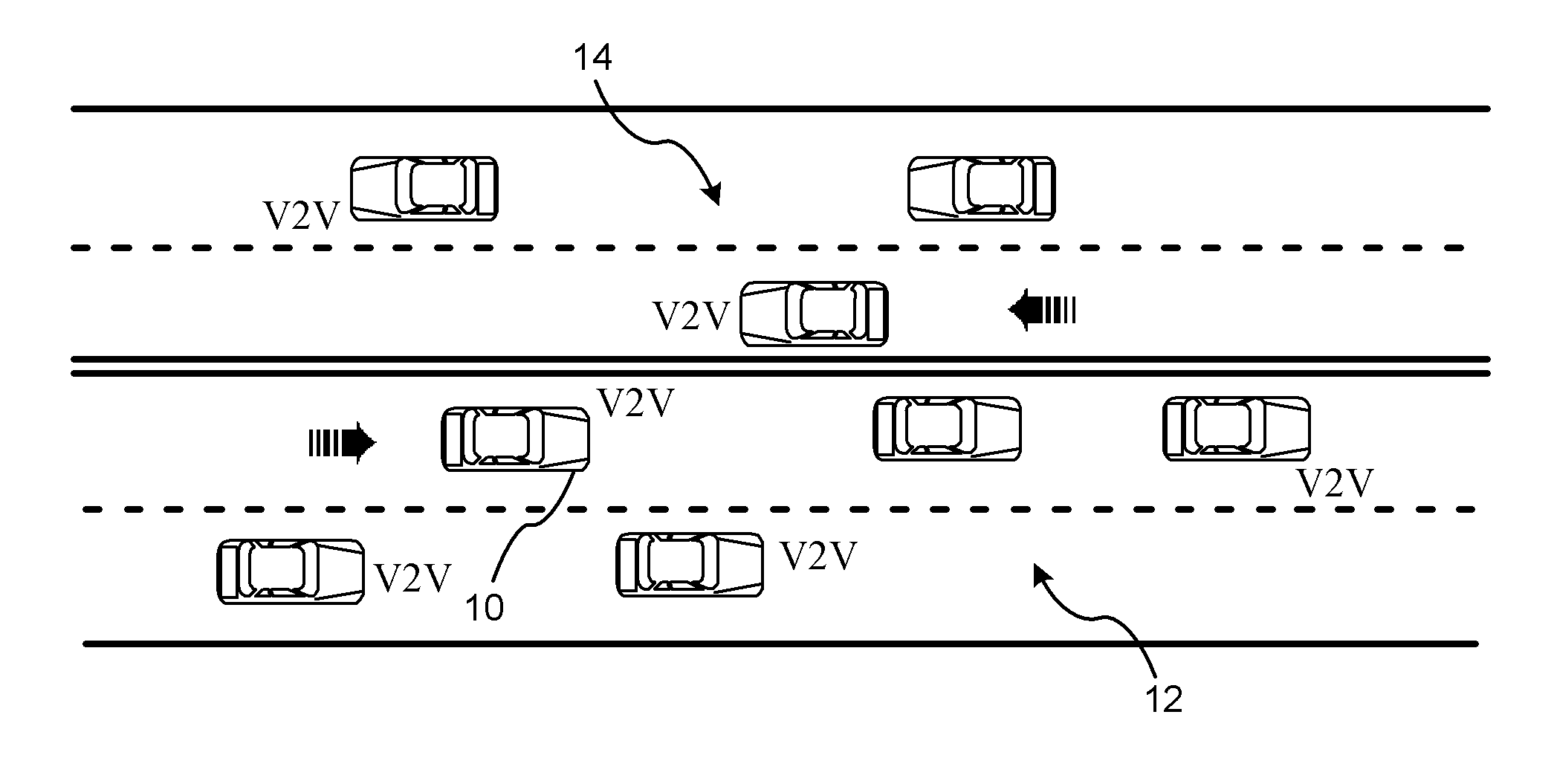
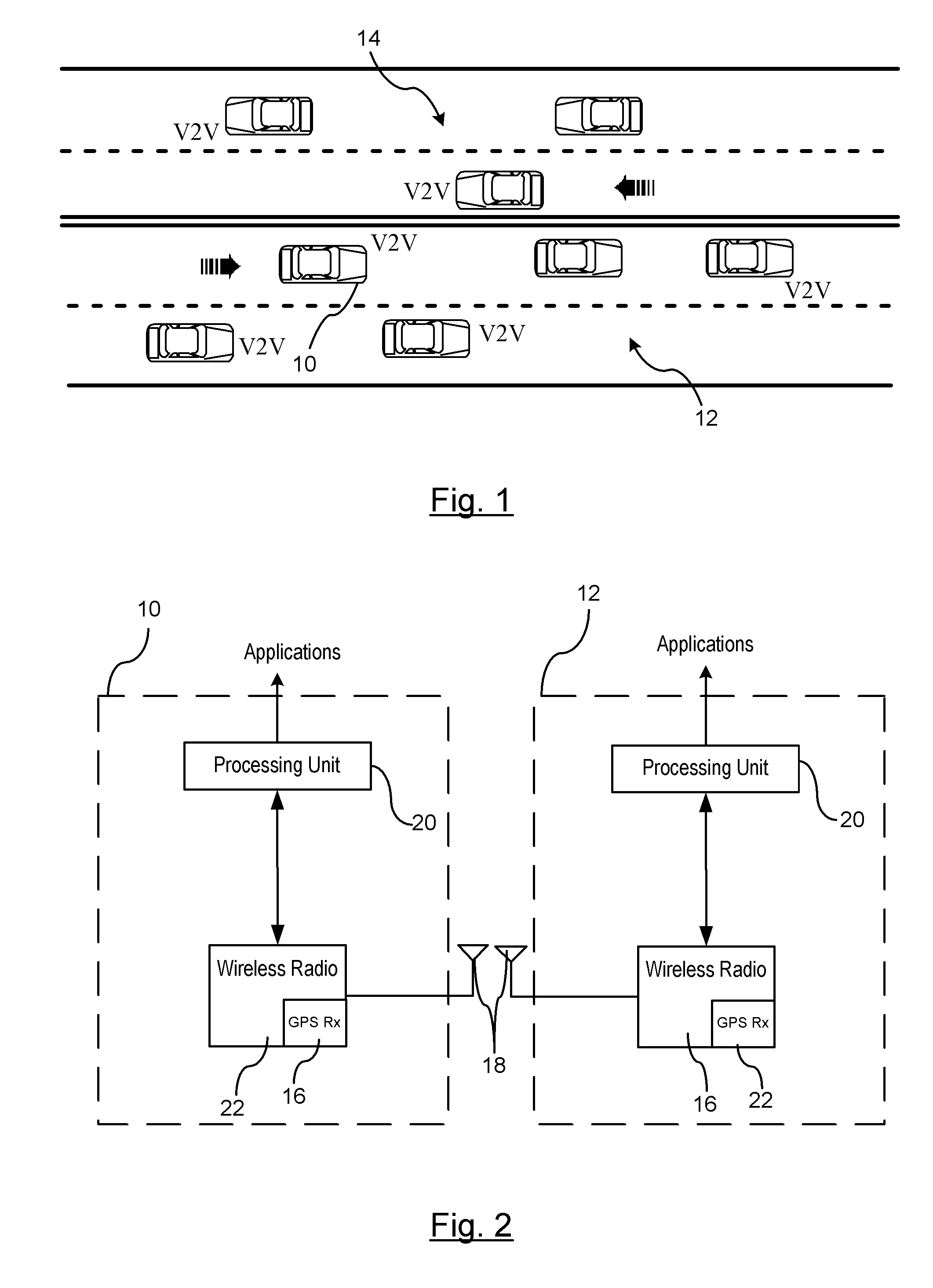
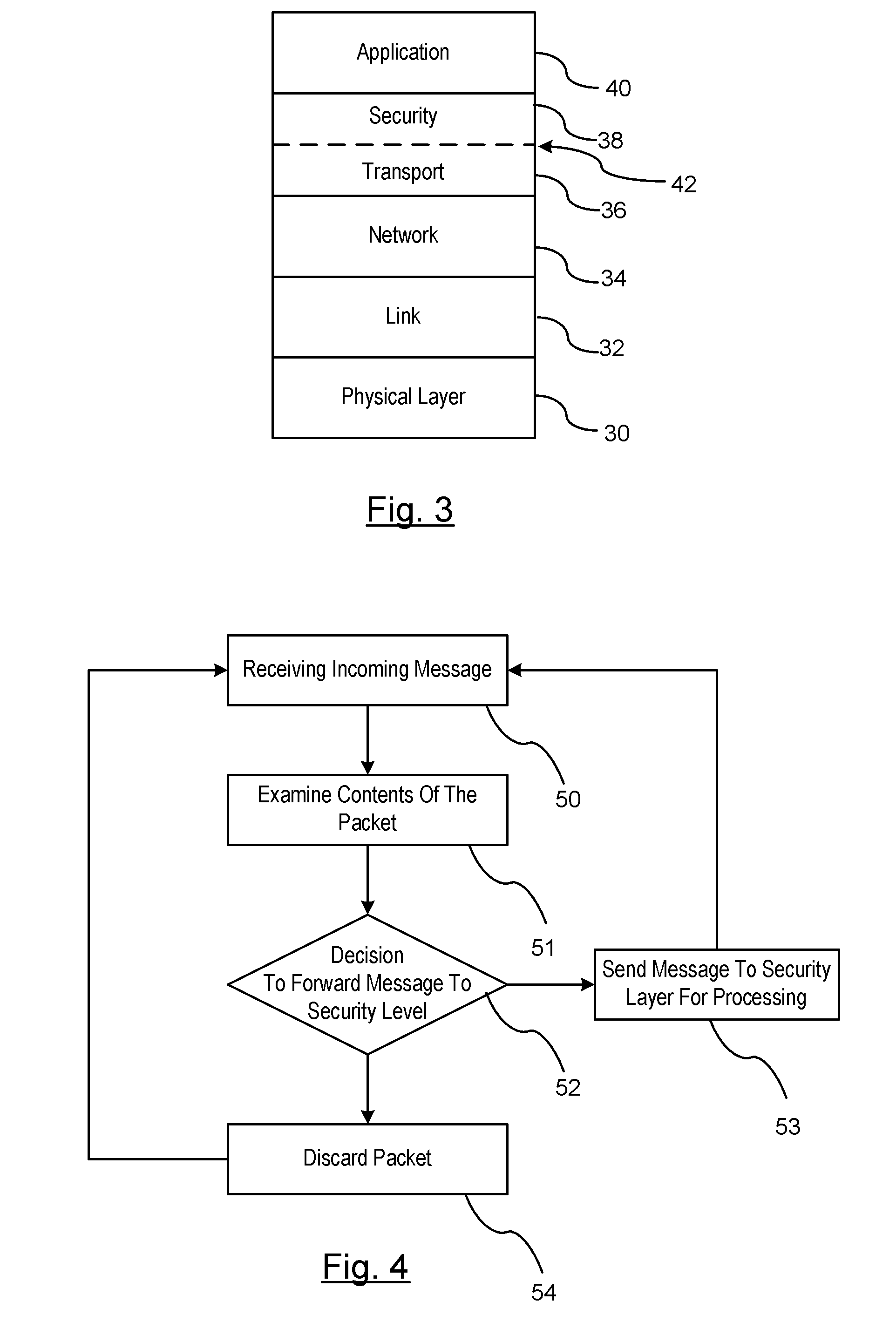
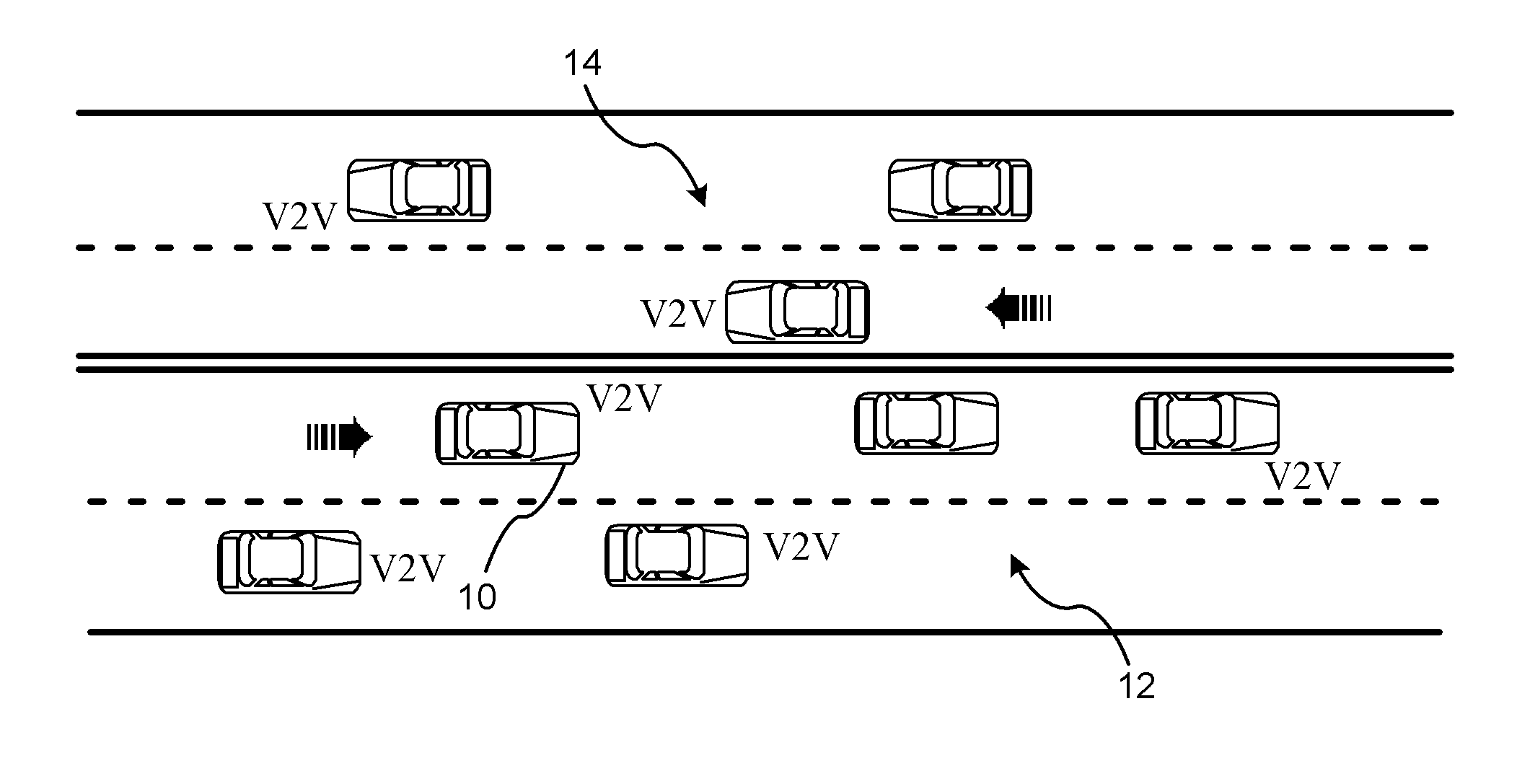
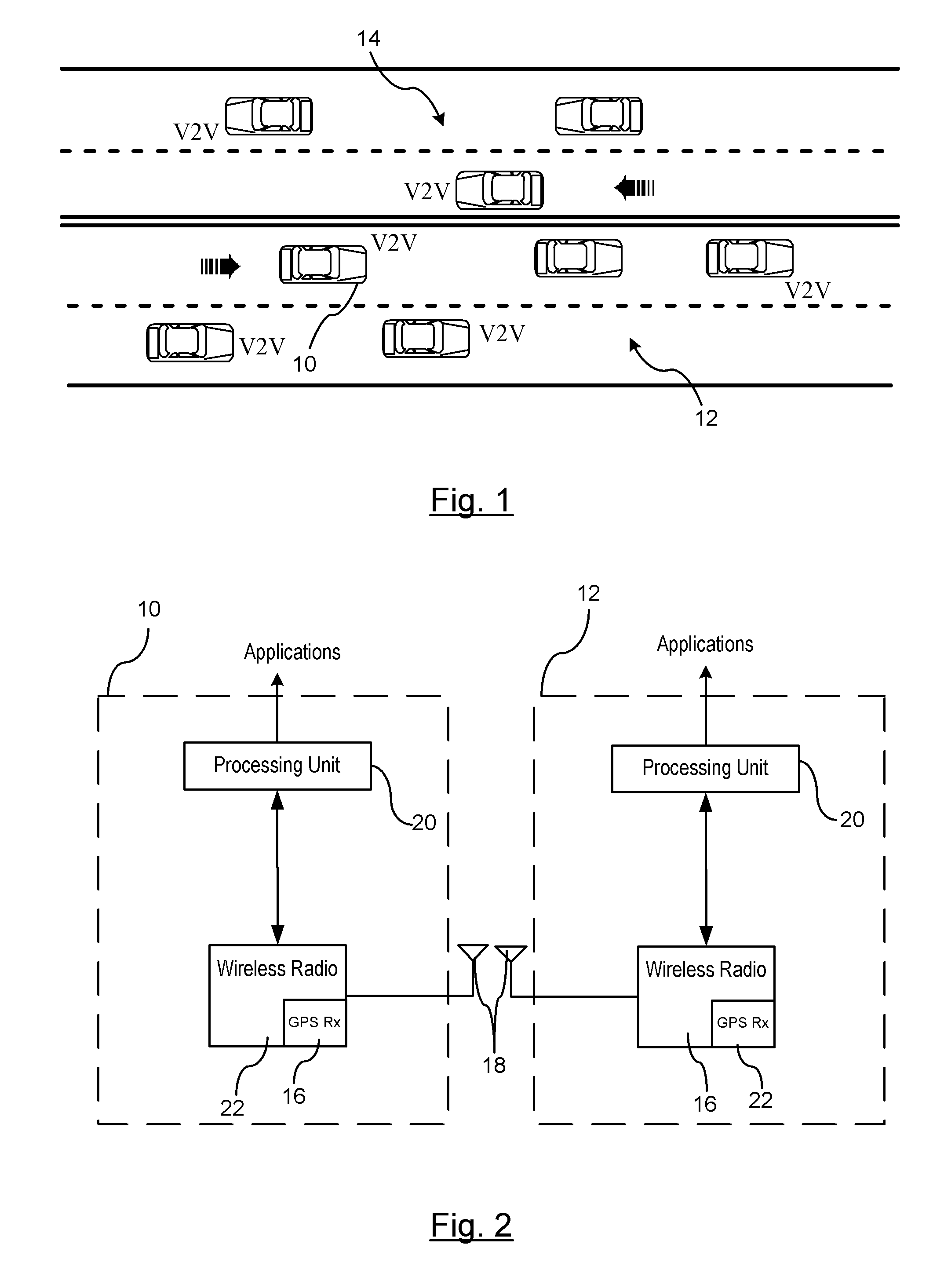
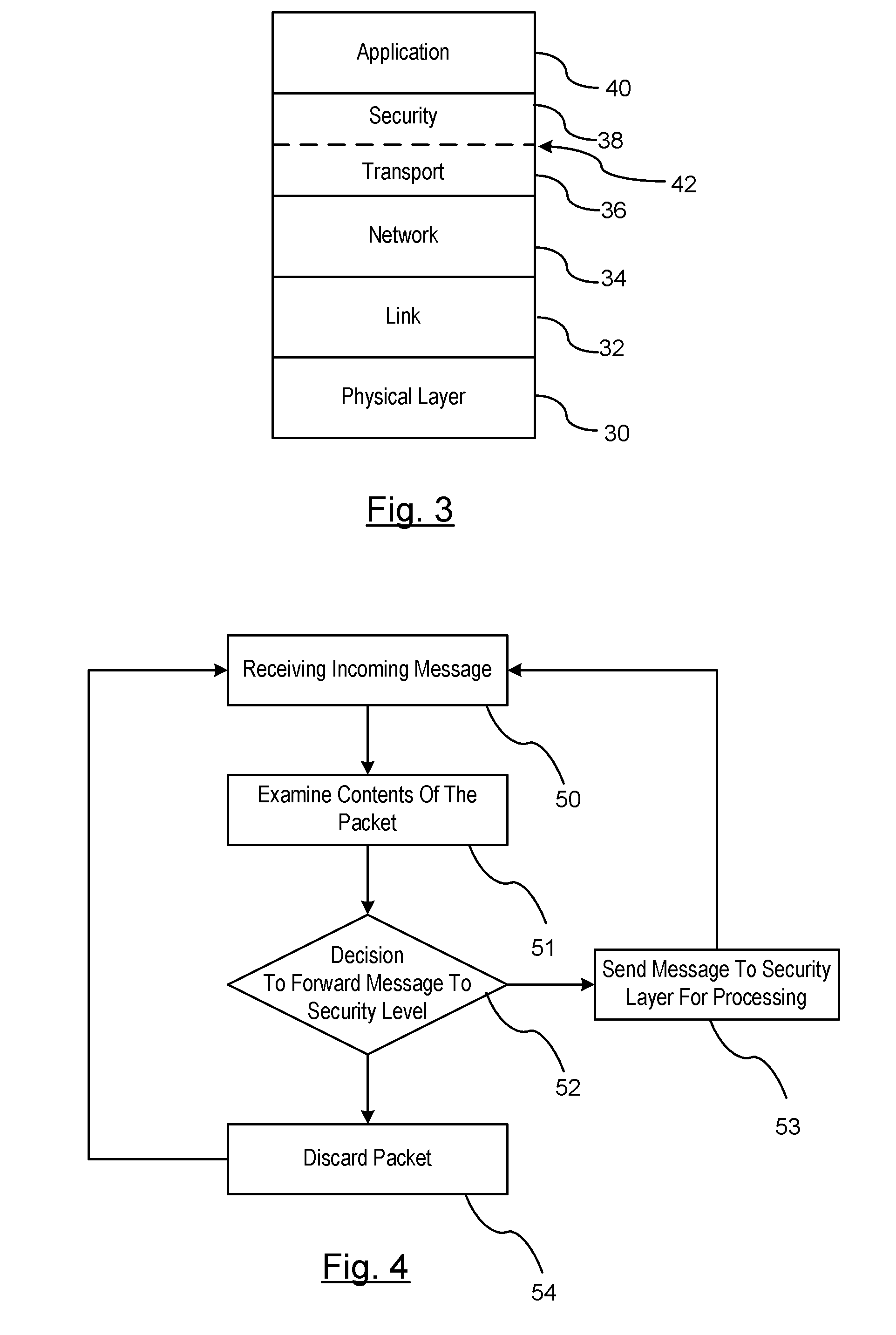
Reducing the Computational Load on Processors by Selectively Discarding Data in Vehicular Networks
ActiveUS20110080302A1Efficient processingReduce computing loadService provisioningParticular environment based servicesCommunications systemProtocol stack
A method is provided for efficiently processing messages staged for authentication in a security layer of a protocol stack in a wireless vehicle-to-vehicle communication system. The vehicle-to-vehicle communication system includes a host vehicle receiver for receiving messages transmitted by one or more remote vehicles. The host receiver is configured to authenticate received messages in a security layer of a protocol stack. A wireless message broadcast by a remote vehicle is received. The wireless message contains characteristic data of the remote vehicle. The characteristic data is analyzed for determining whether the wireless message is in compliance with a predetermined parameter of the host vehicle. The wireless message is discarded prior to a transfer of the wireless message to the security layer in response to a determination that the wireless message is not in compliance with the predetermined parameter of the host vehicle. Otherwise, the wireless message is transferred to the security layer.
Owner:GM GLOBAL TECH OPERATIONS LLC
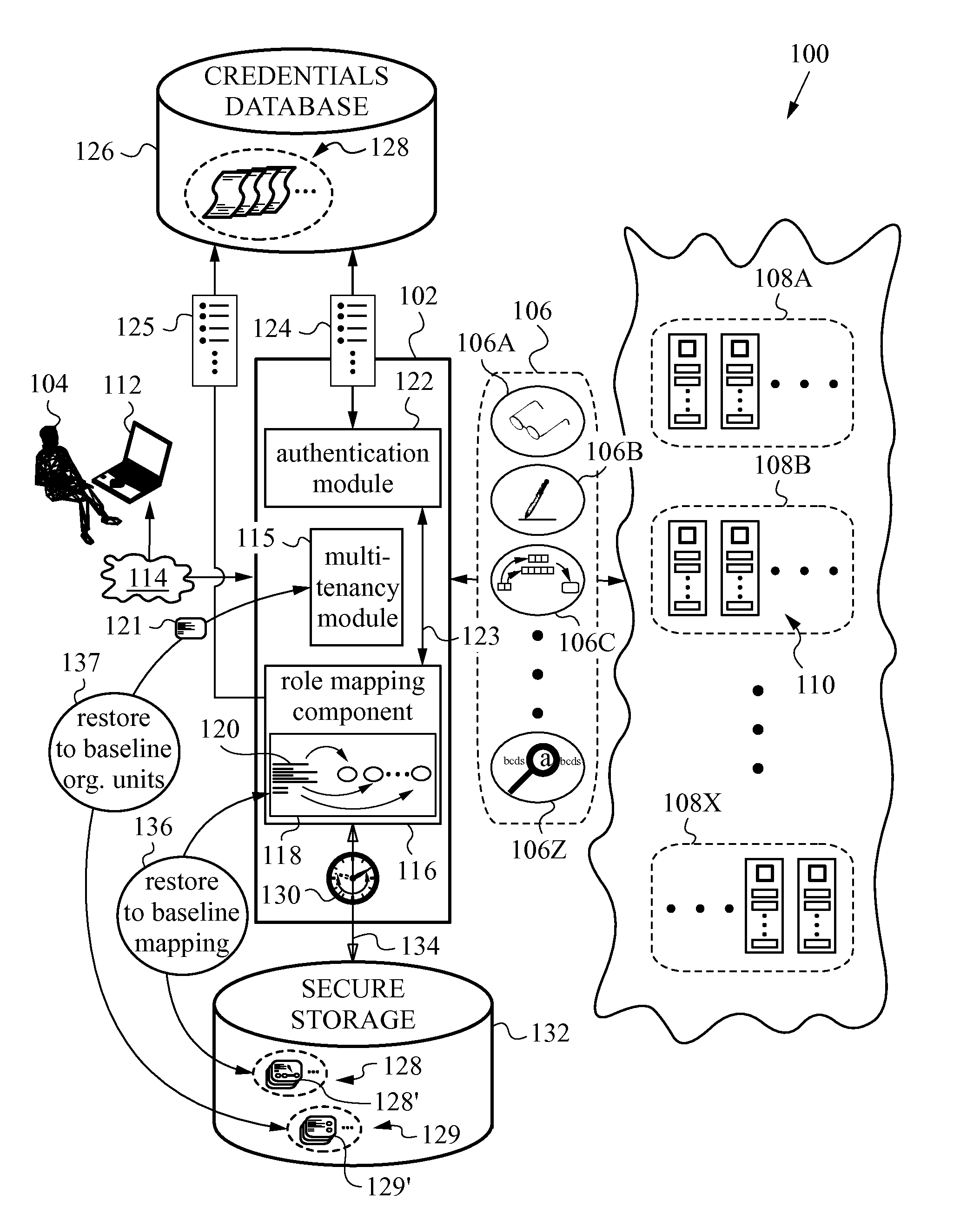
Monitoring of Authorization-Exceeding Activity in Distributed Networks
ActiveUS20140196115A1Minimal disruptionProvide supportDigital data processing detailsComputer security arrangementsUser authenticationOnline identity
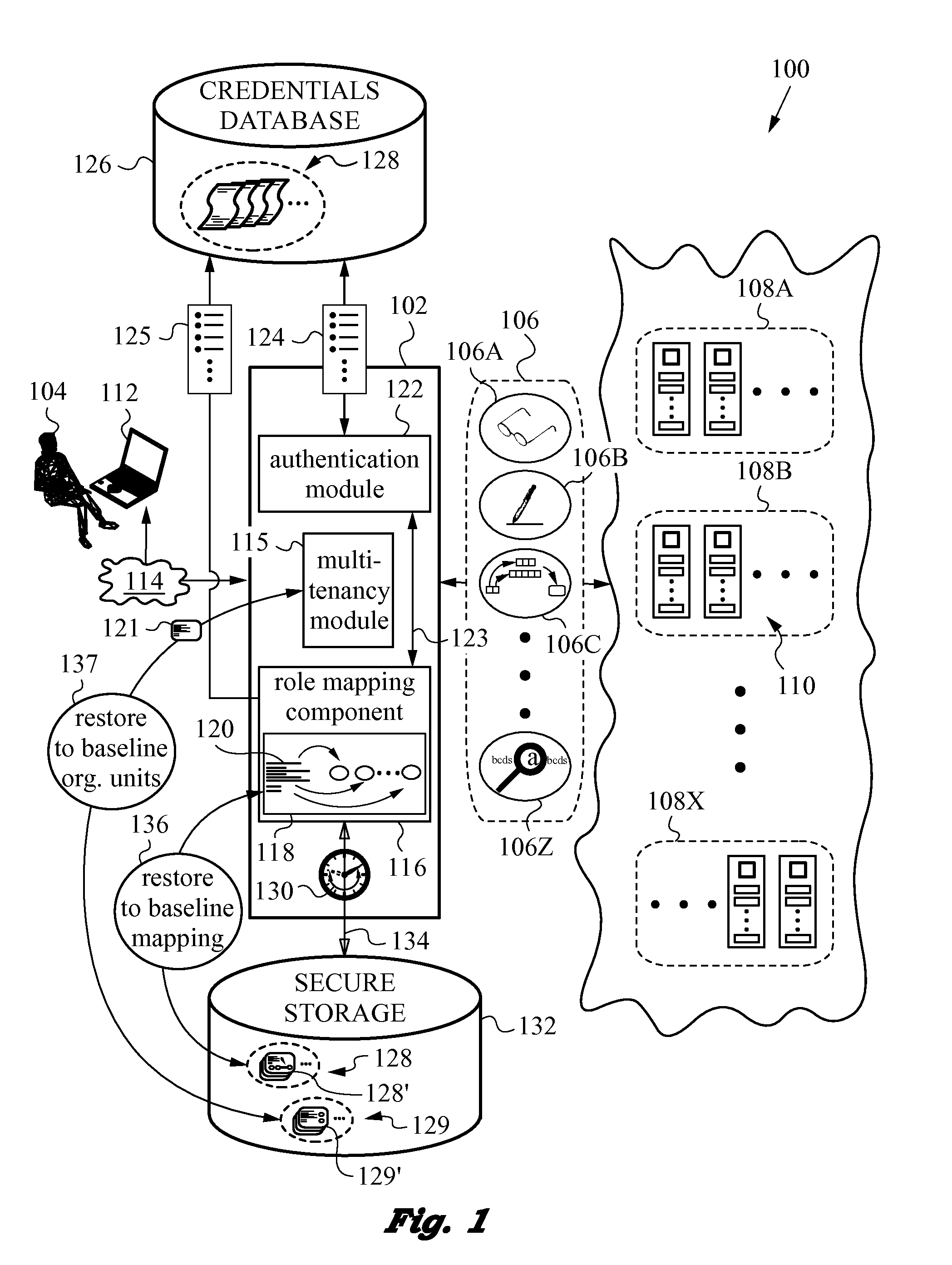
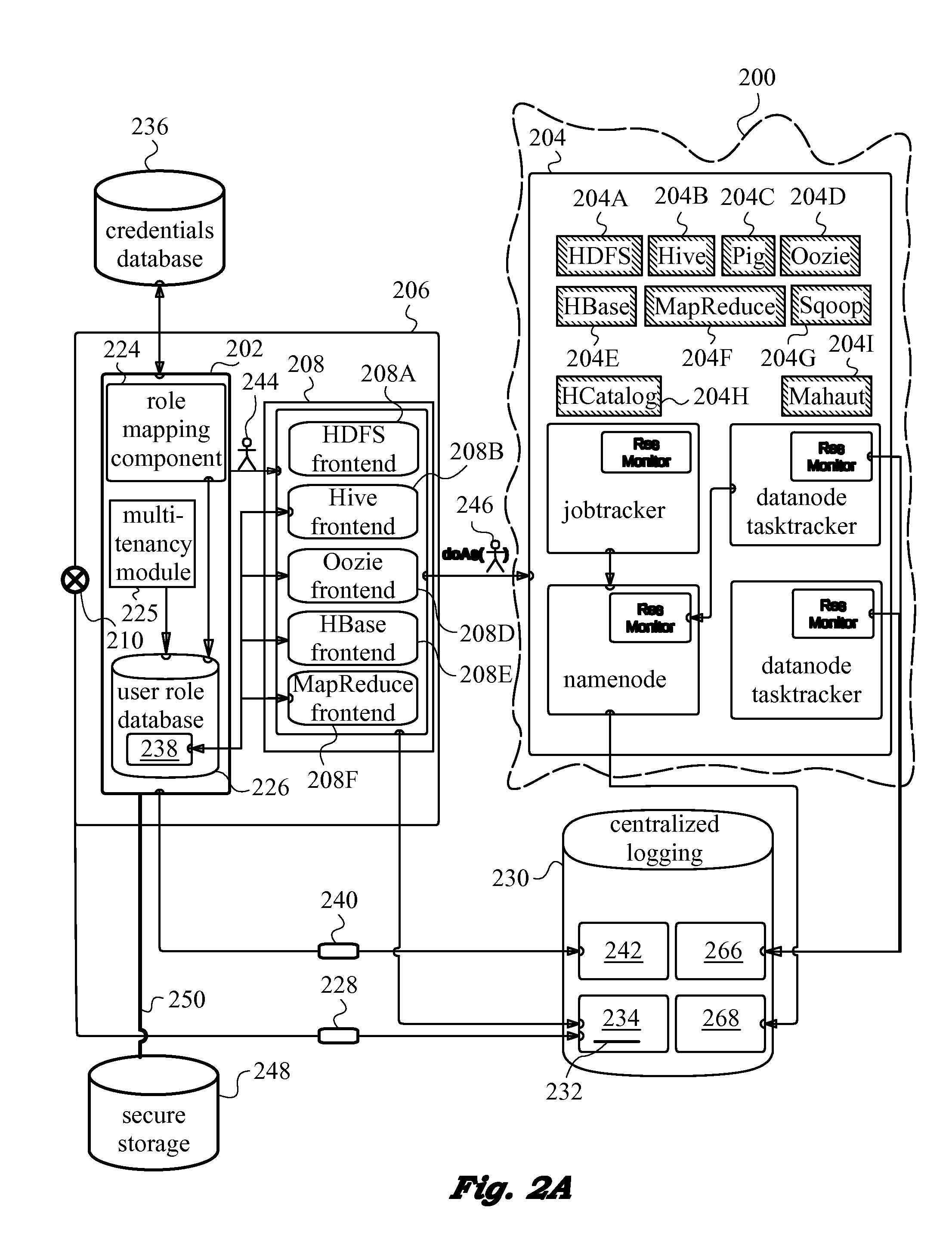
A network security layer with a role mapping component with a current role mapping between services and access permissions is provided between a user and the services. A multi-tenancy module with current membership mapping is also provided. The security layer has a network authentication protocol for user authentication at log-in. Snapshots of a baseline role mapping between services and permissions are taken at certain times. The role mapping component verifies snapshots at set intervals, and when the user performs certain actions, the current role mapping is compared with the baseline role mapping. Upon discrepancy, the role mapping component executes a set of rules, including forceful log-out to prevent system intrusion. Comparison of current membership mapping with a baseline membership mapping can also be applied. The security layer can thus monitor authorization-exceeding modifications to baseline policies attempted by logged-in and initially authorized users.
Owner:ZETTASET
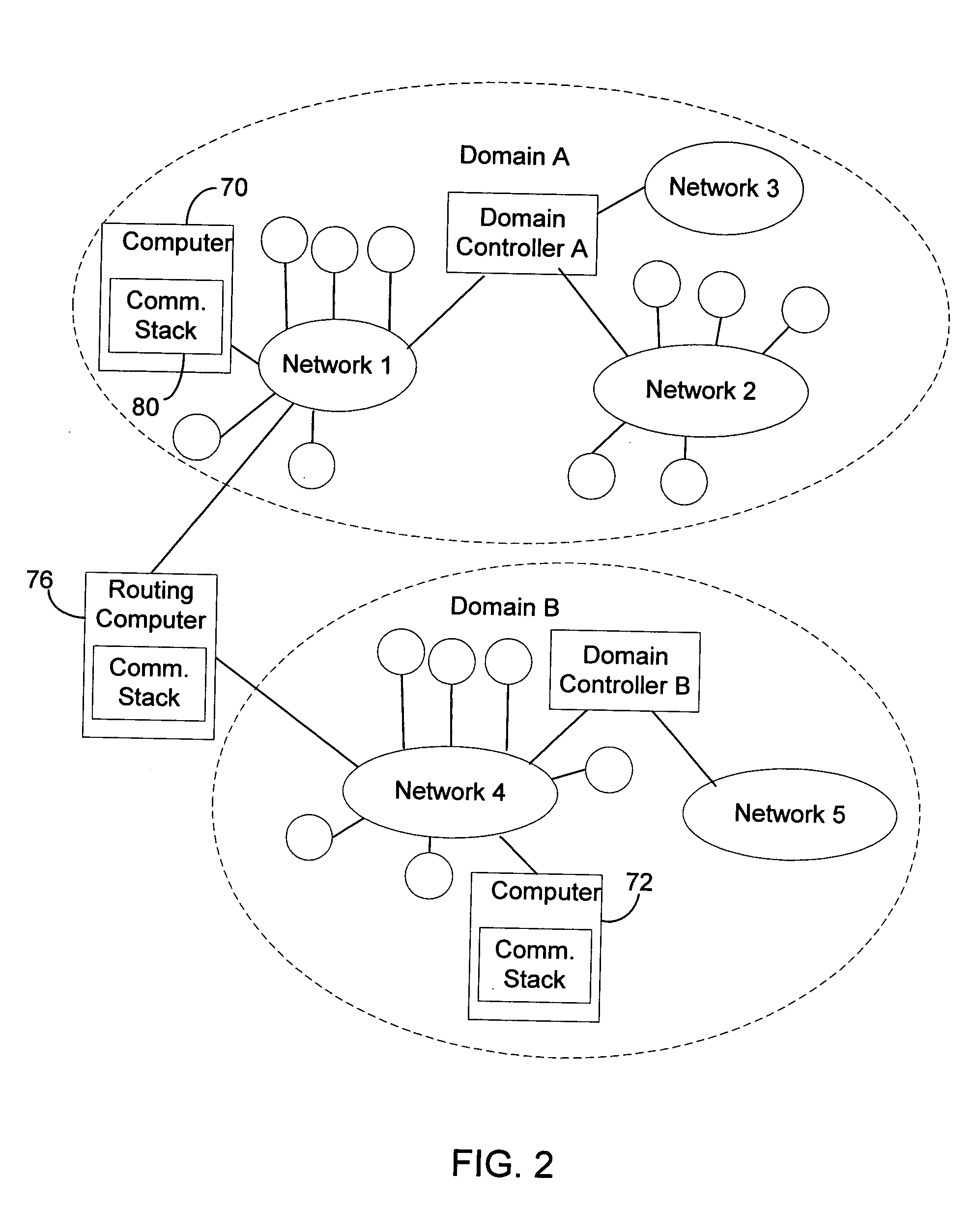
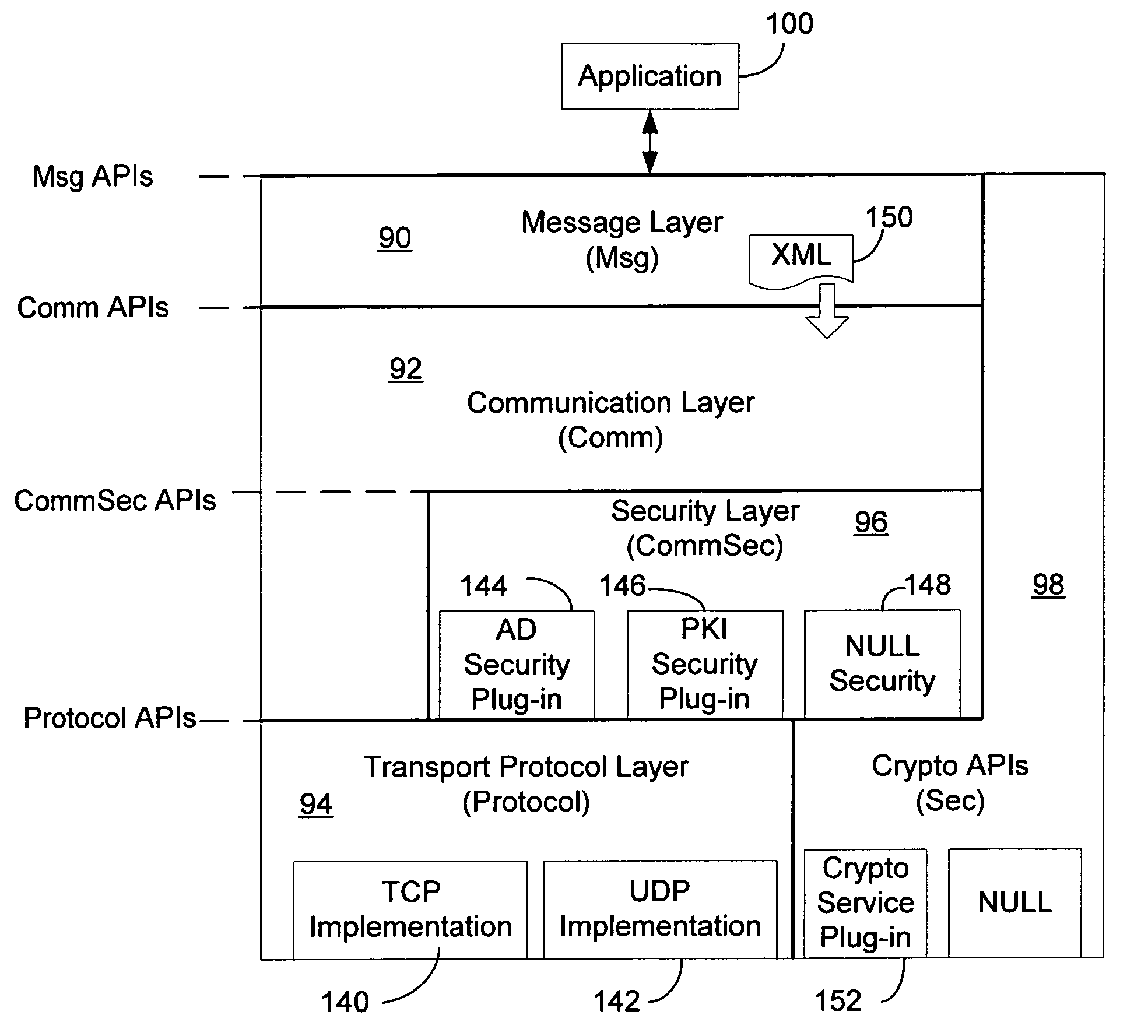
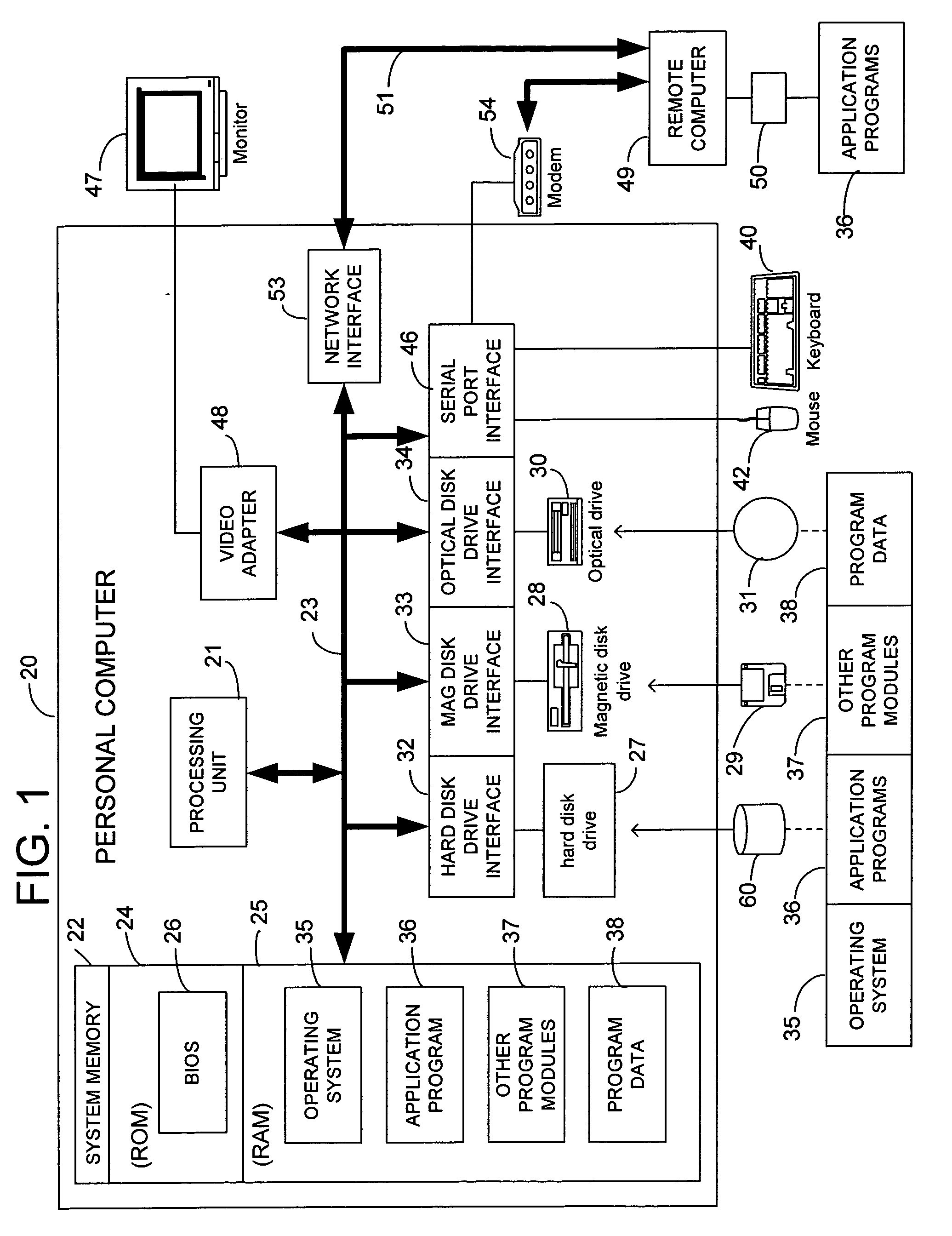
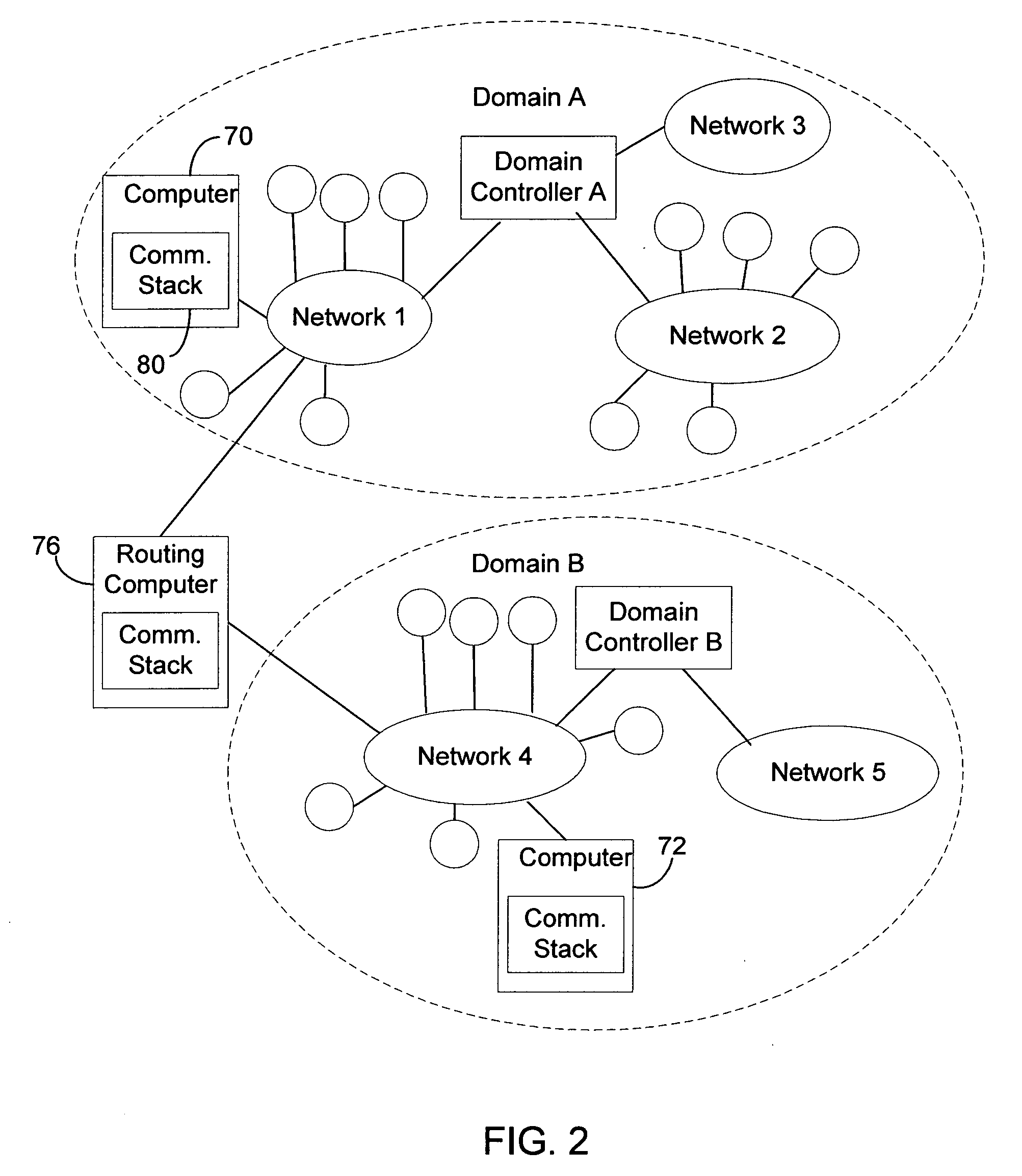
Communication stack for network communication and routing
ActiveUS7191248B2Imparts flexibilityImparts extensibilityMultiple digital computer combinationsSecuring communicationTransmission protocolCryptographic protocol
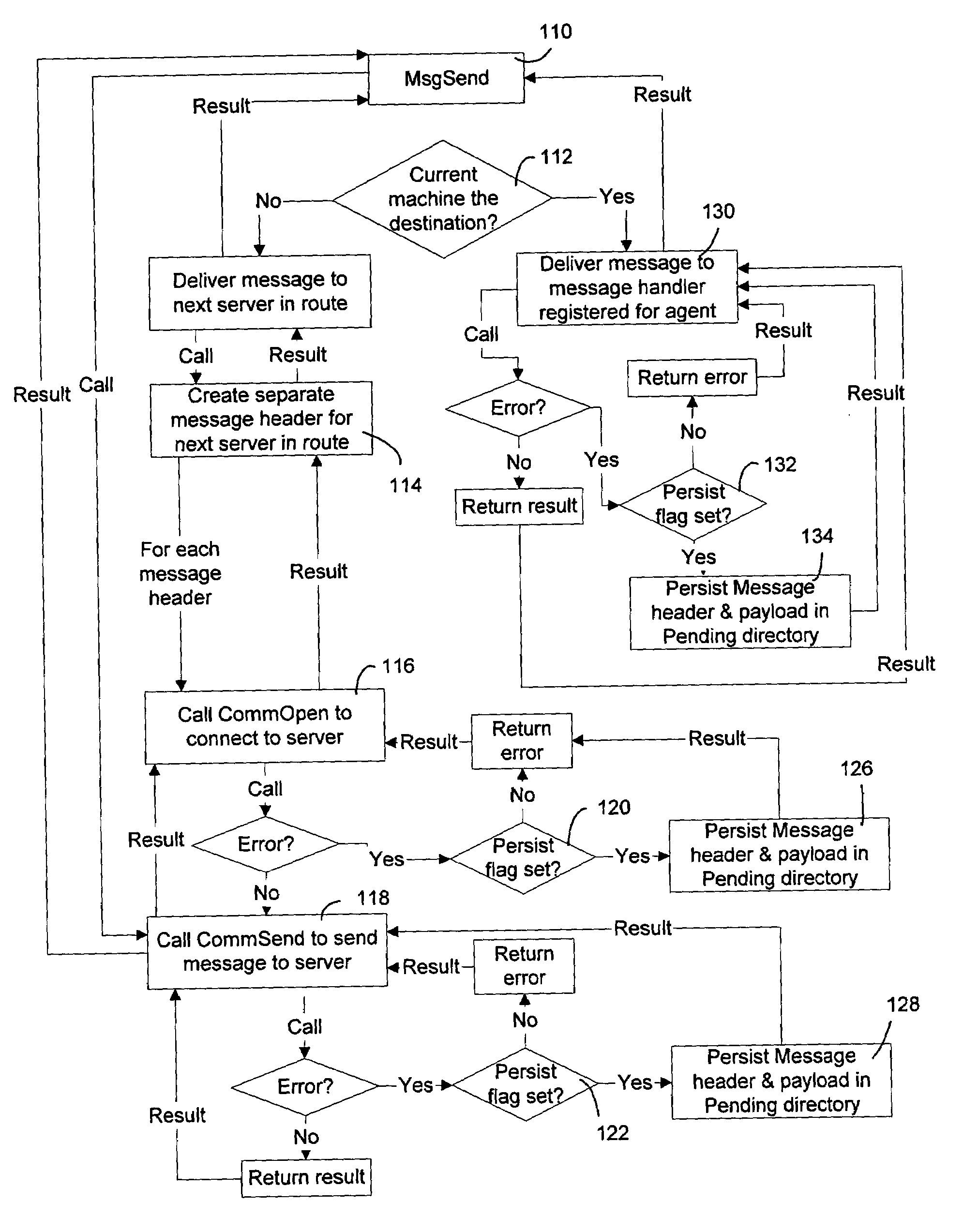
A communication stack enables computers implementing it to send, receive, or route network communications. The communication stack includes a message layer, a communication layer, a security layer, and a transport protocol layer, with plug-in transport protocol modules and plug-in security protocol modules. Each of the origin computer, target computer, and routing computers involved in delivering a message implements the communication stack. An application on the origin computer calls the message layer of the computer to send messages to a target computer and identifies routing computers on the route for delivering the message to the target computer. The message layer calls the communication layer to establish a connection to the target computer. The communication layer uses the transport protocol layer to establish an initial connection with the target computer, and uses the security layer to negotiate security parameters and to handle secured communications between the origin and target computers.
Owner:MICROSOFT TECH LICENSING LLC
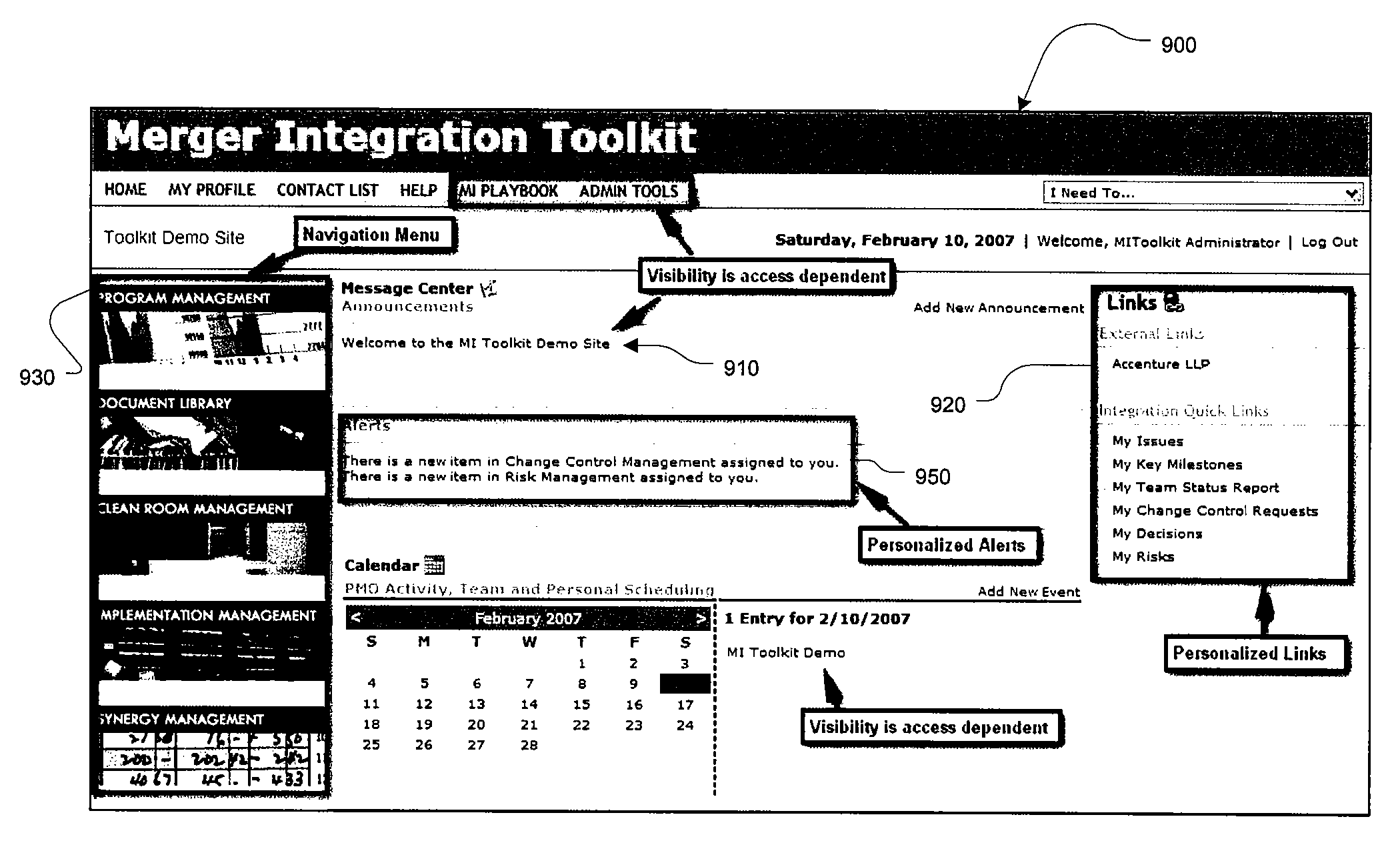
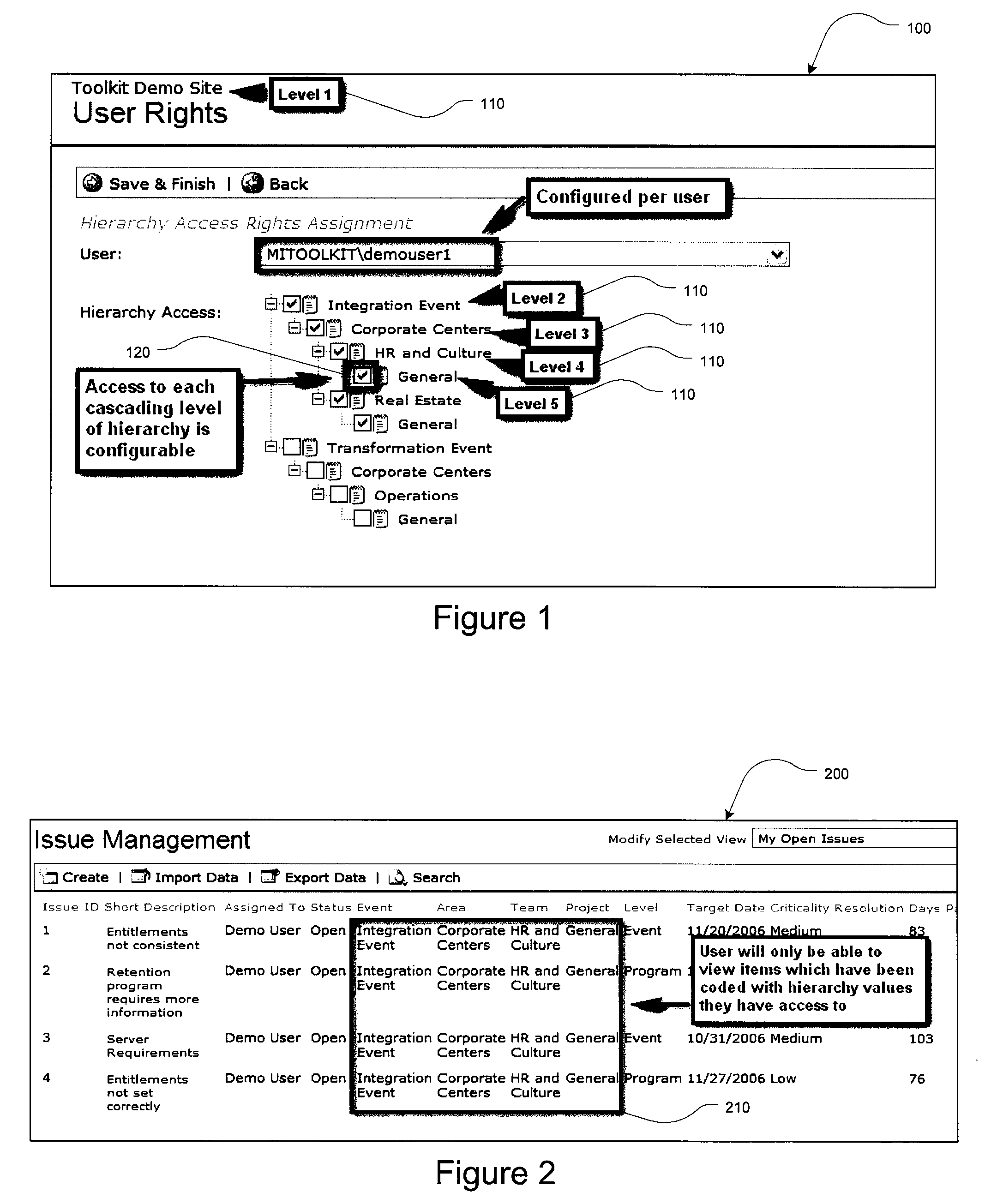
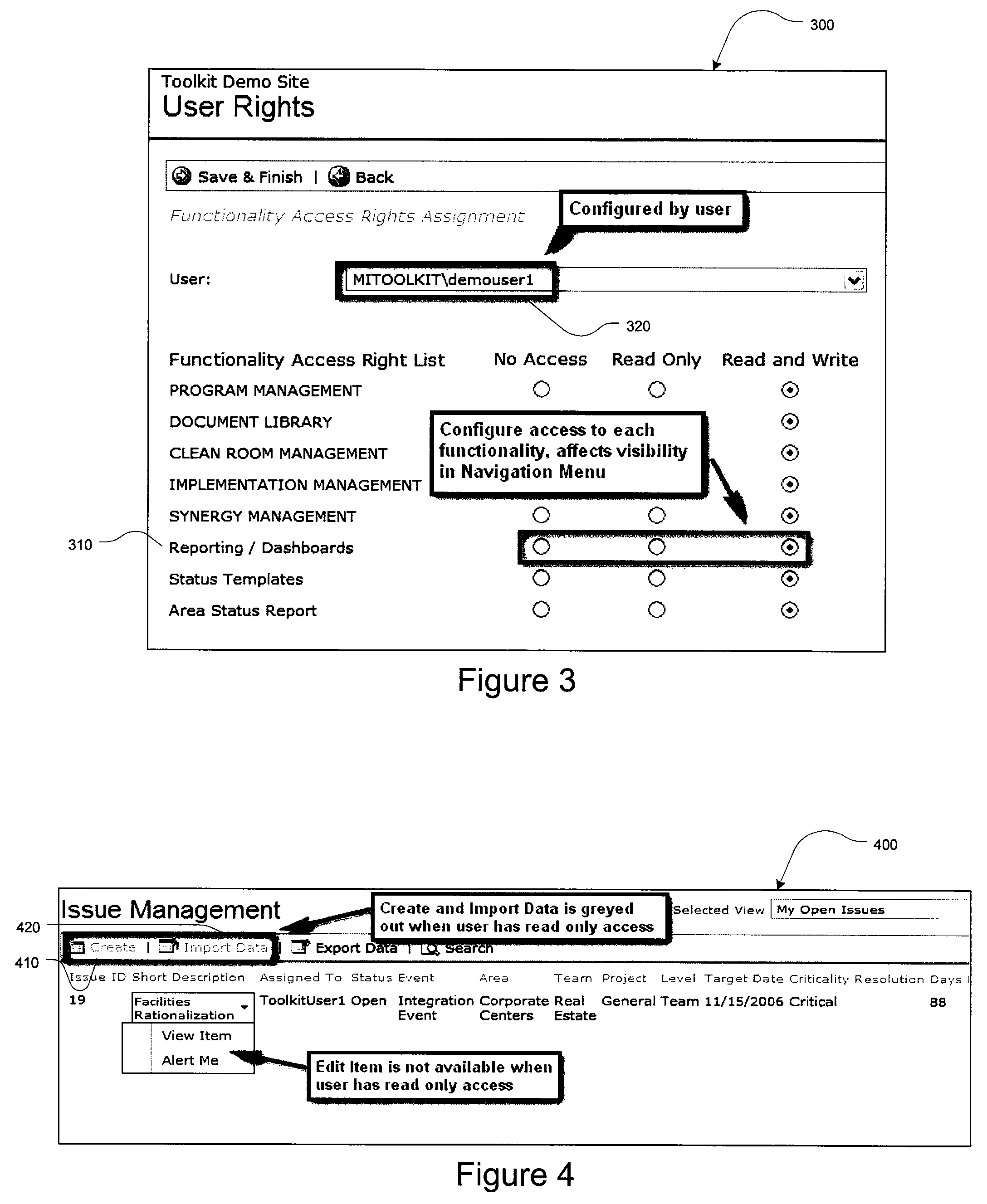
Merger integration toolkit system and method for secure navigation hierarchy and workflow functionality
InactiveUS20080040173A1Provide functionalityProvide securityResourcesSpecific program execution arrangementsVisibilityEnterprise integration
The present invention provides for a method and a computer system for electronically managing and supporting a merger integration of businesses. In one aspect, the invention provides program-level hierarchy and security with a collaboration environment computer program for assisting a group of individuals performing the integration, such that the collaboration environment is an electronic tool configured to provide administrative controls and communication among the group of individuals performing the integration. A management and security layer is established for the collaboration environment computer program. The management and security layer is configurable to control access to content in the collaboration environment computer program independently for each of the individuals, and access to the content is controlled with a plurality of hierarchy levels that are defined and applied to designate the portions of the content to which each individual has access. An individual interfaces with the management and security layer such that the individual's access or visibility of the content is controlled based on the plurality of hierarchy levels. In other aspects of the invention, the method and computer system for an integration of businesses provides a user portal and customizable workflow.
Owner:ACCENTURE GLOBAL SERVICES LTD
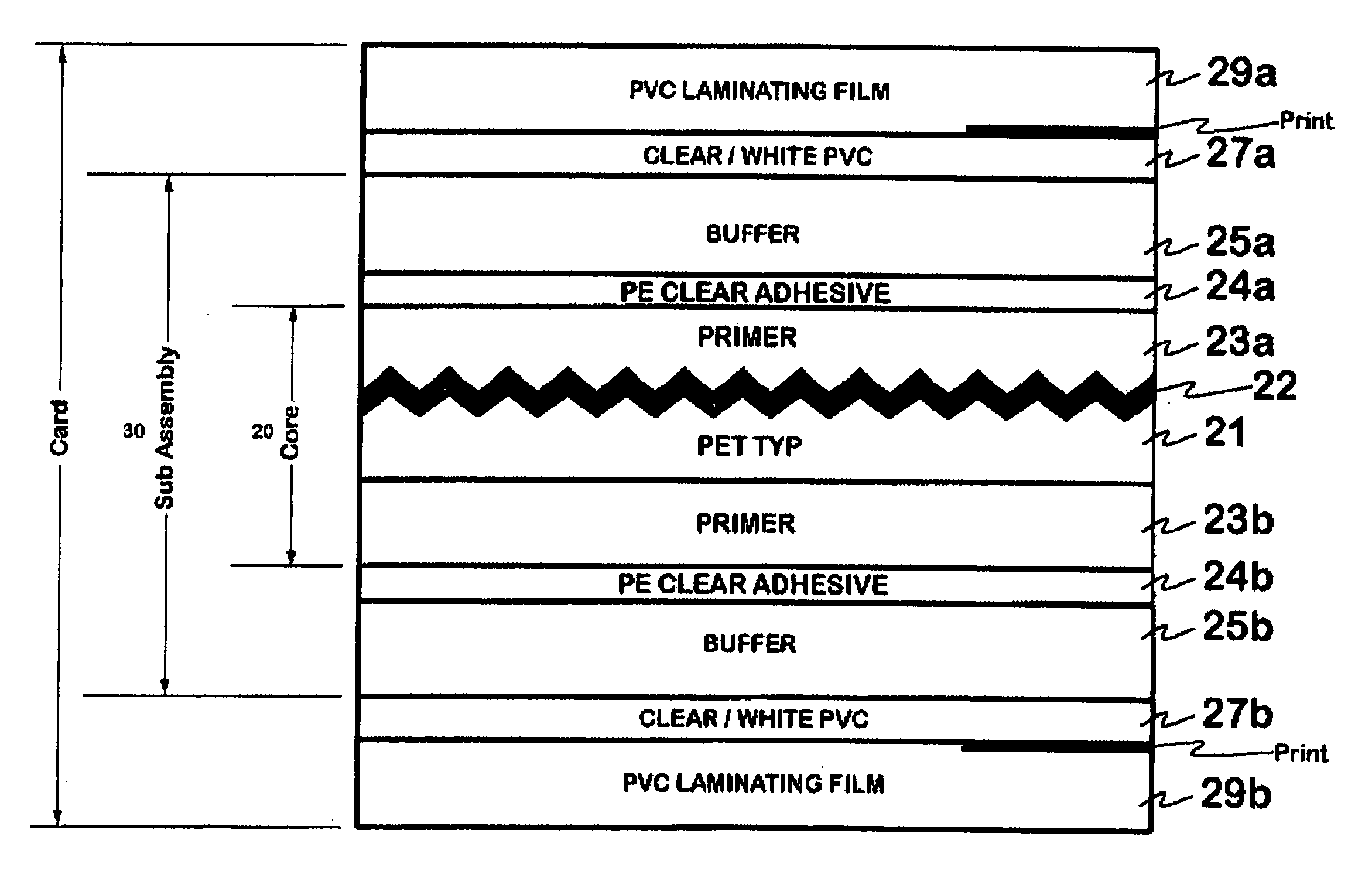
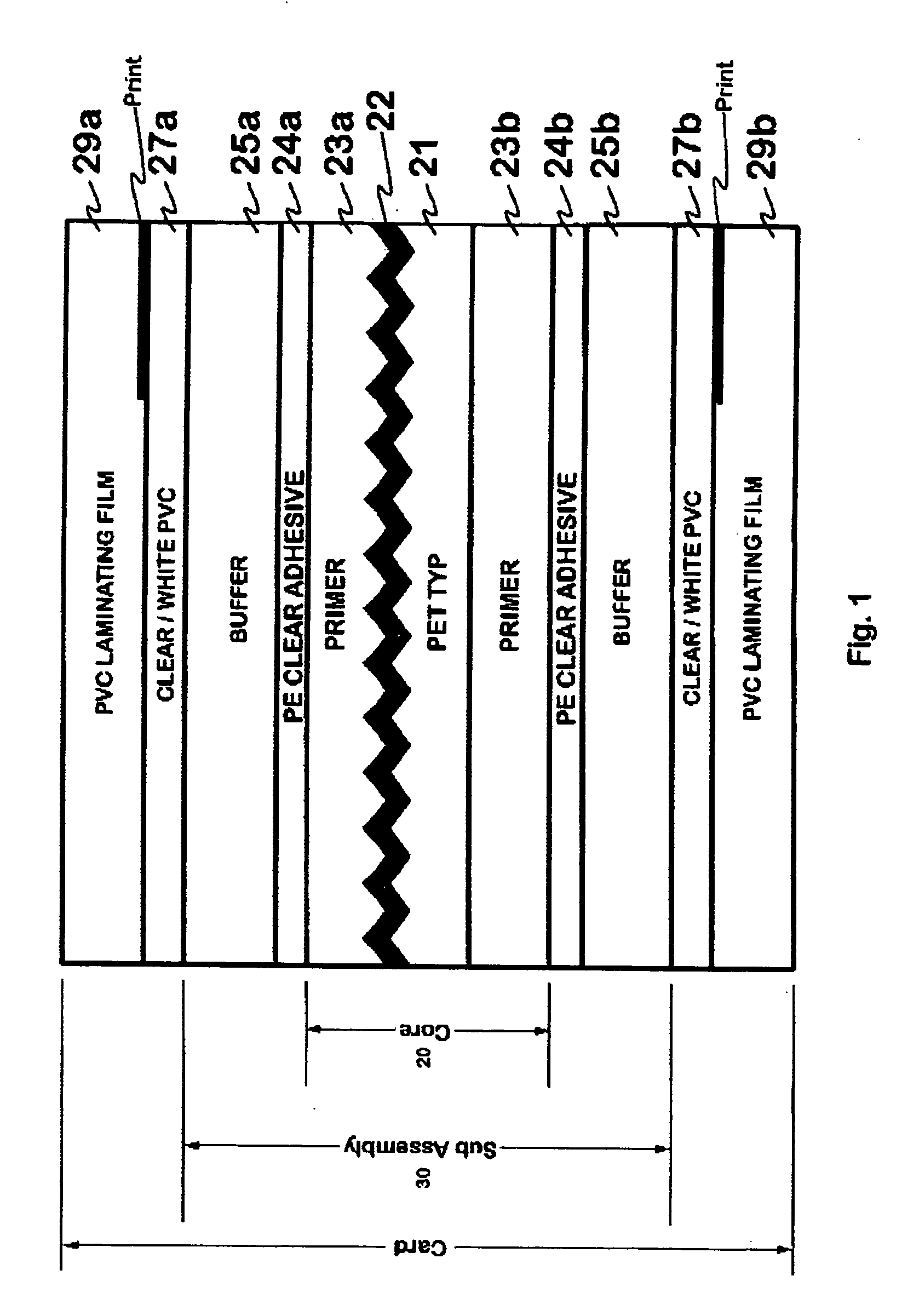
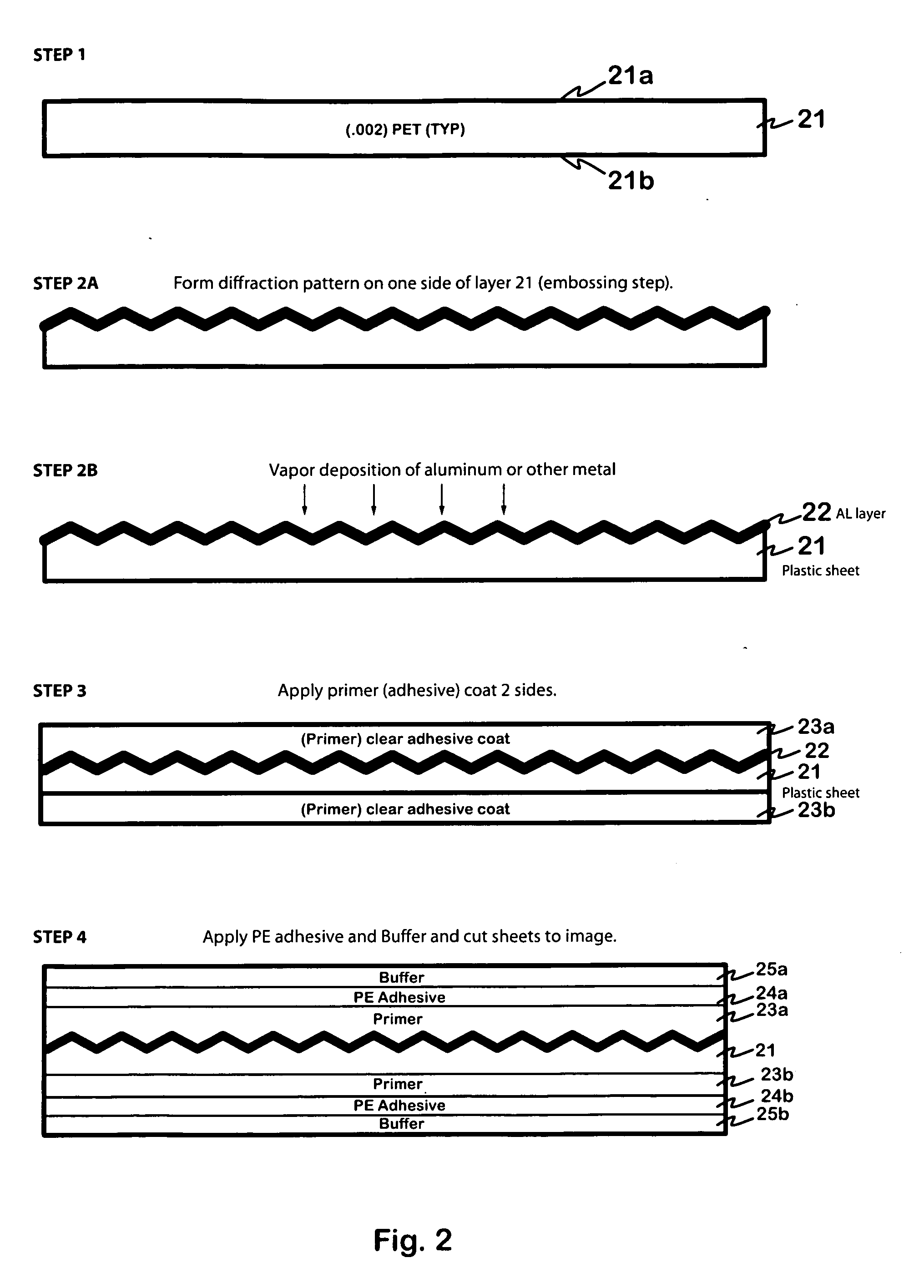
Foil composite card
Composite cards formed in accordance with the invention include a security layer comprising a hologram or diffraction grating formed at, or in, the center, or core layer, of the card. The hologram may be formed by embossing a designated area of the core layer with a diffraction pattern and depositing a thin layer of metal on the embossed layer. Additional layers may be selectively and symmetrically attached to the top and bottom surfaces of the core layer. A laser may be used to remove selected portions of the metal formed on the embossed layer, at selected stages of forming the card, to impart a selected pattern or information to the holographic region. The cards may be “lasered” when the cards being processed are attached to, and part of, a large sheet of material, whereby the “lasering” of all the cards on the sheet can be done at the same time and relatively inexpensively. Alternatively, each card may be individually “lasered” to produce desired alpha numeric information, bar codes information or a graphic image, after the sheets are die-cut into cards.
Owner:COMPOSECURE LLC
Multiple security layers for time-based network admission control
InactiveUS20100043066A1Reduce energy consumptionOptimize networkDigital data processing detailsUser identity/authority verificationComputer methodsNetwork Access Control
Embodiments of the present invention include a computer method of controlling access to a computer-based network comprising: (i) receiving an indication of an attempt to gain access to a computer-based network; (ii) applying a respective network access control policy to determine whether to allow the attempt to gain access to the computer-based network at each of multiple security layers; and (iii) allowing or blocking the attempt to gain access through the security layer to the computer-based network based on the application of the respective network access control policy at each security layer. Other embodiments include a computer method of controlling access to a computer-based network comprising: (a) scanning a host computer for viruses; (b) temporarily disabling a firewall of the host computer during an audit; and (c) shutting down high risk services running on the host computer.
Owner:NETCLARITY
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
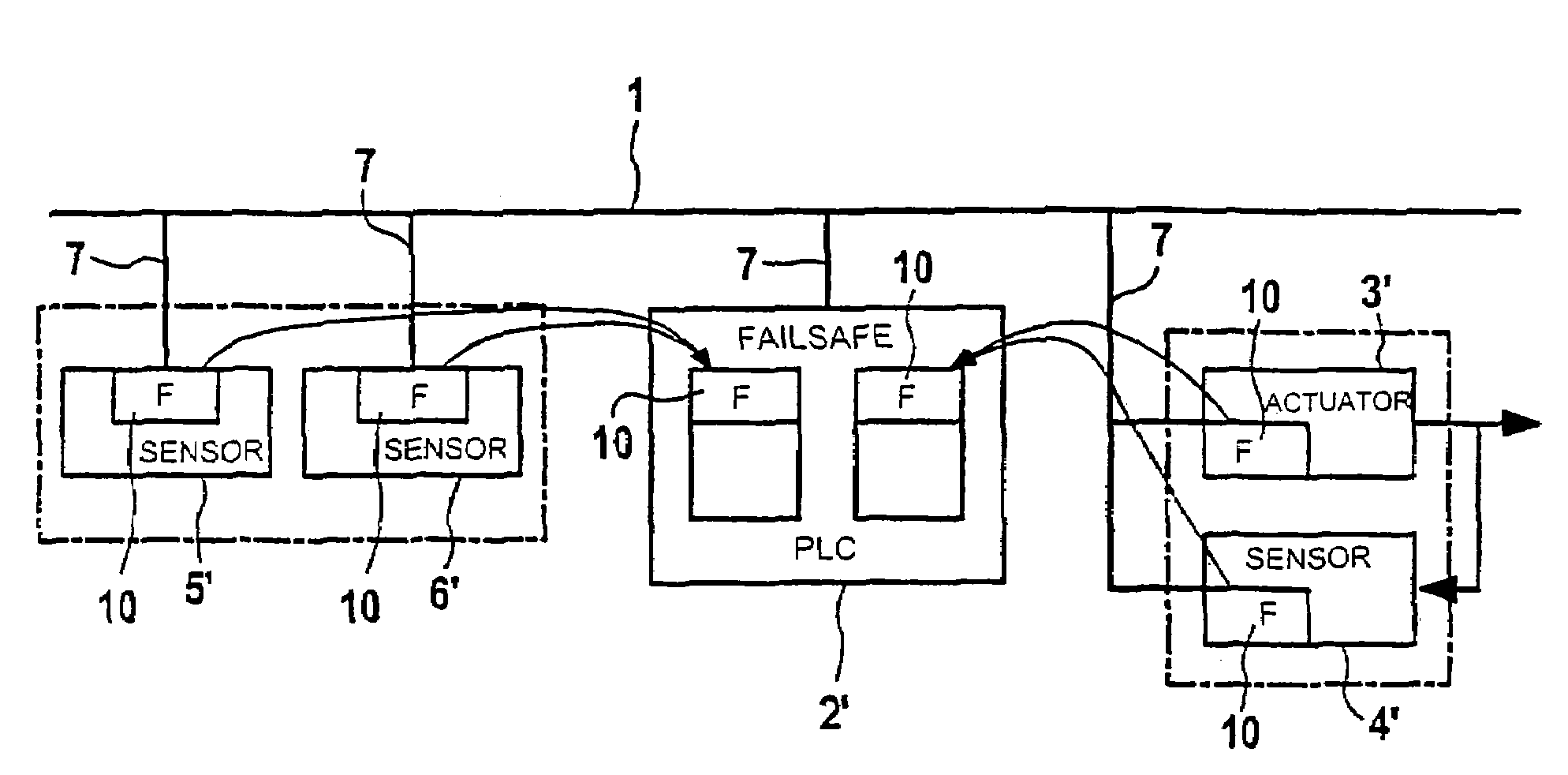
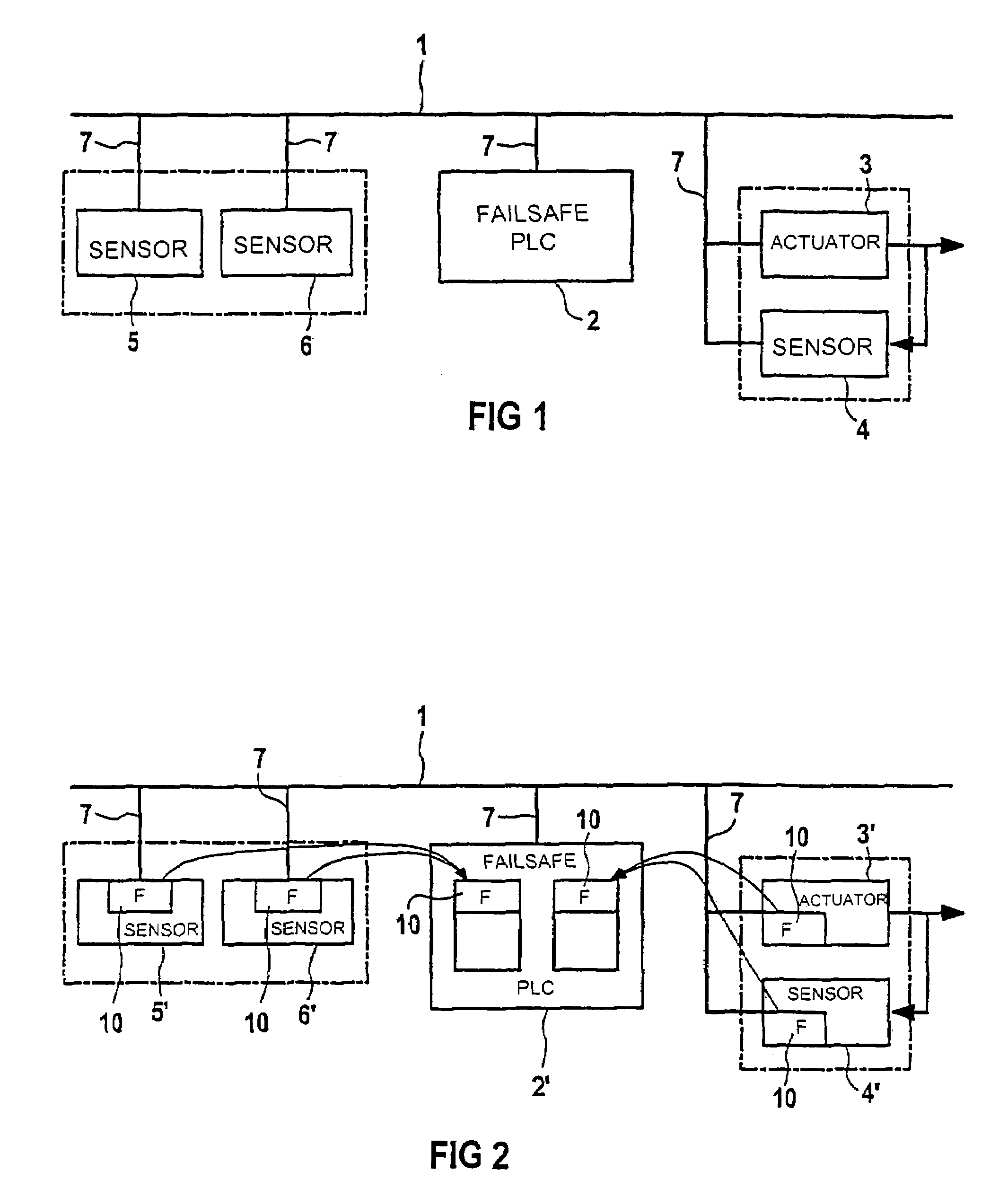
Microprocessor-controlled field device for connection to a field bus system
InactiveUS7337369B2Low costIntegration of a safety layer is relatively simpleError detection/correctionTotal factory controlActuatorSecurity validation
A microprocessor-controlled standard field device, such as a measuring sensor or an actuator, is connected to a field bus system that, in turn, is connected to, for example, a freely programmable controller. The field device is equipped with a security layer for carrying out a security proven communication. A secure and simultaneously cost-effective communication with a control device via a field bus system is made possible by implementing a security layer in, e.g., a conventional operationally proven or redundant standard field device.
Owner:SIEMENS AG
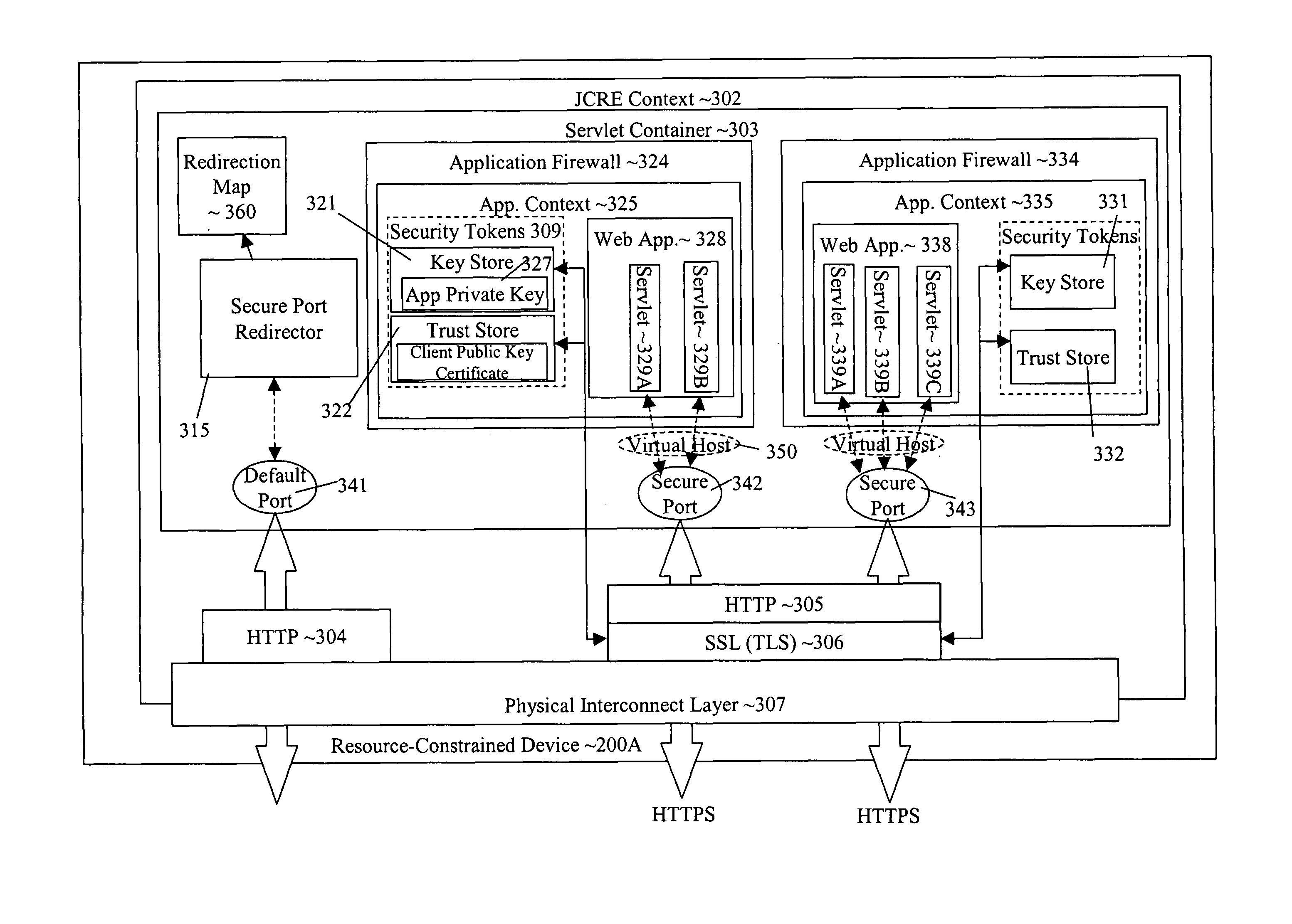
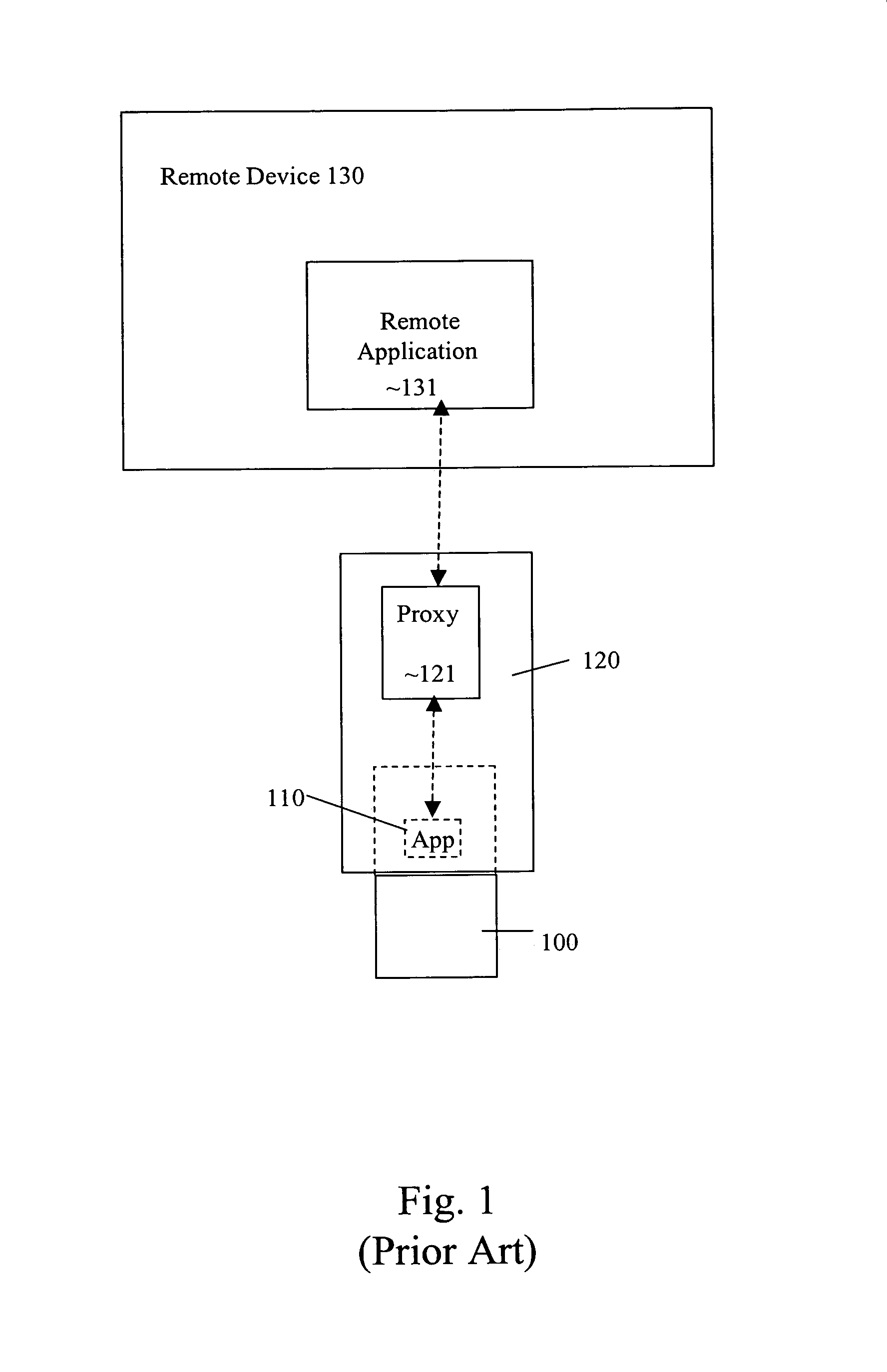
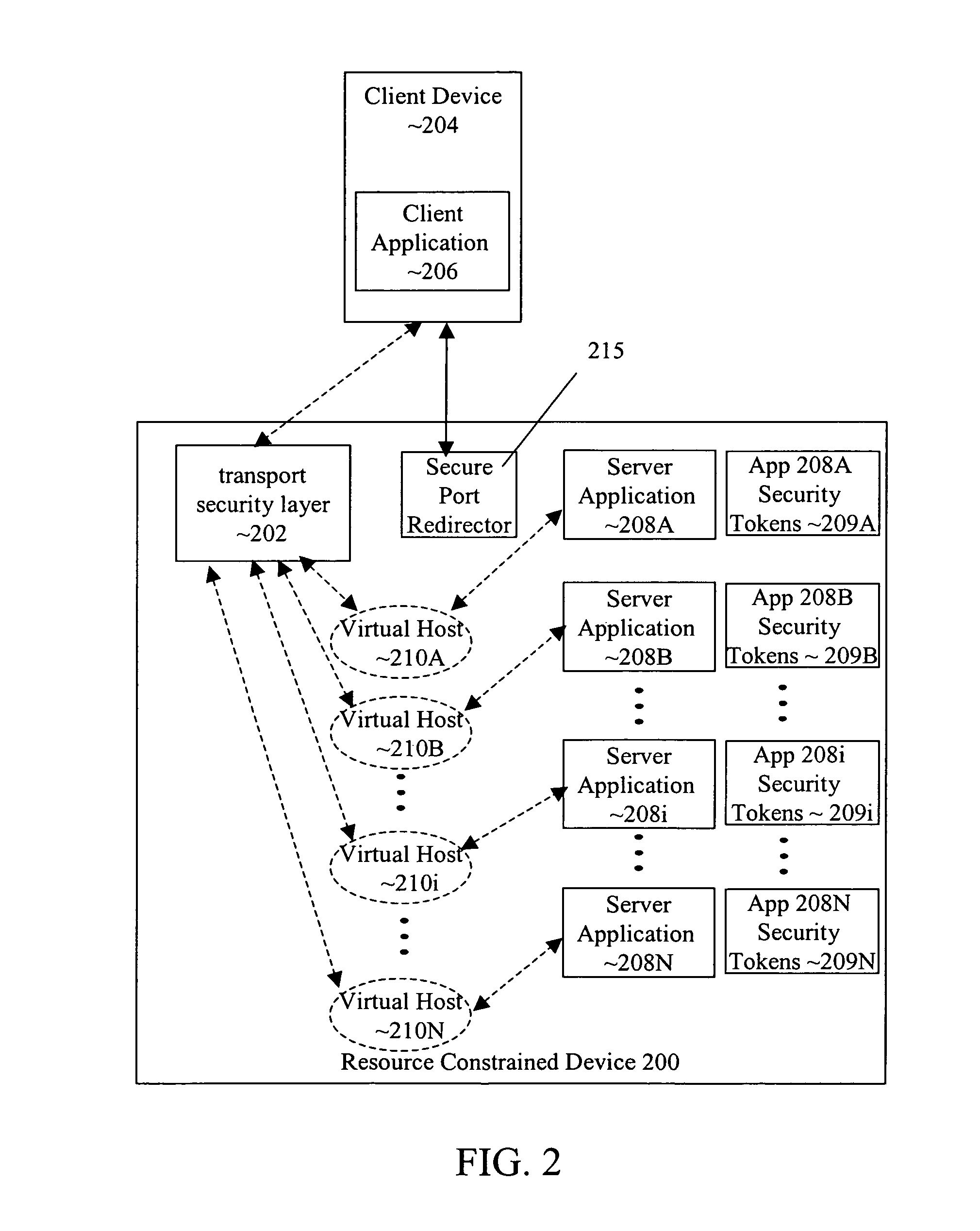
Transport-level web application security on a resource-constrained device
ActiveUS8245285B1Facilitates secure communicationFacilitate communicationDigital data processing detailsMultiple digital computer combinationsSecure communicationClient-side
A system and method is provided to facilitate secure communications for a server-application executing on a resource-constrained device. A request, from a client application executing on a client device to access a server application executing on the resource-constrained device is received on an application-specific secure port of a resource-constrained device. The request is authenticated using a security token stored in an application context of the server application. The authentication is performed by a transport security layer protocol executing within the application context of the server application. The security token is specific for the server application. A secure connection is established directly between the secure port and the client application upon the authentication being successful.
Owner:ORACLE INT CORP
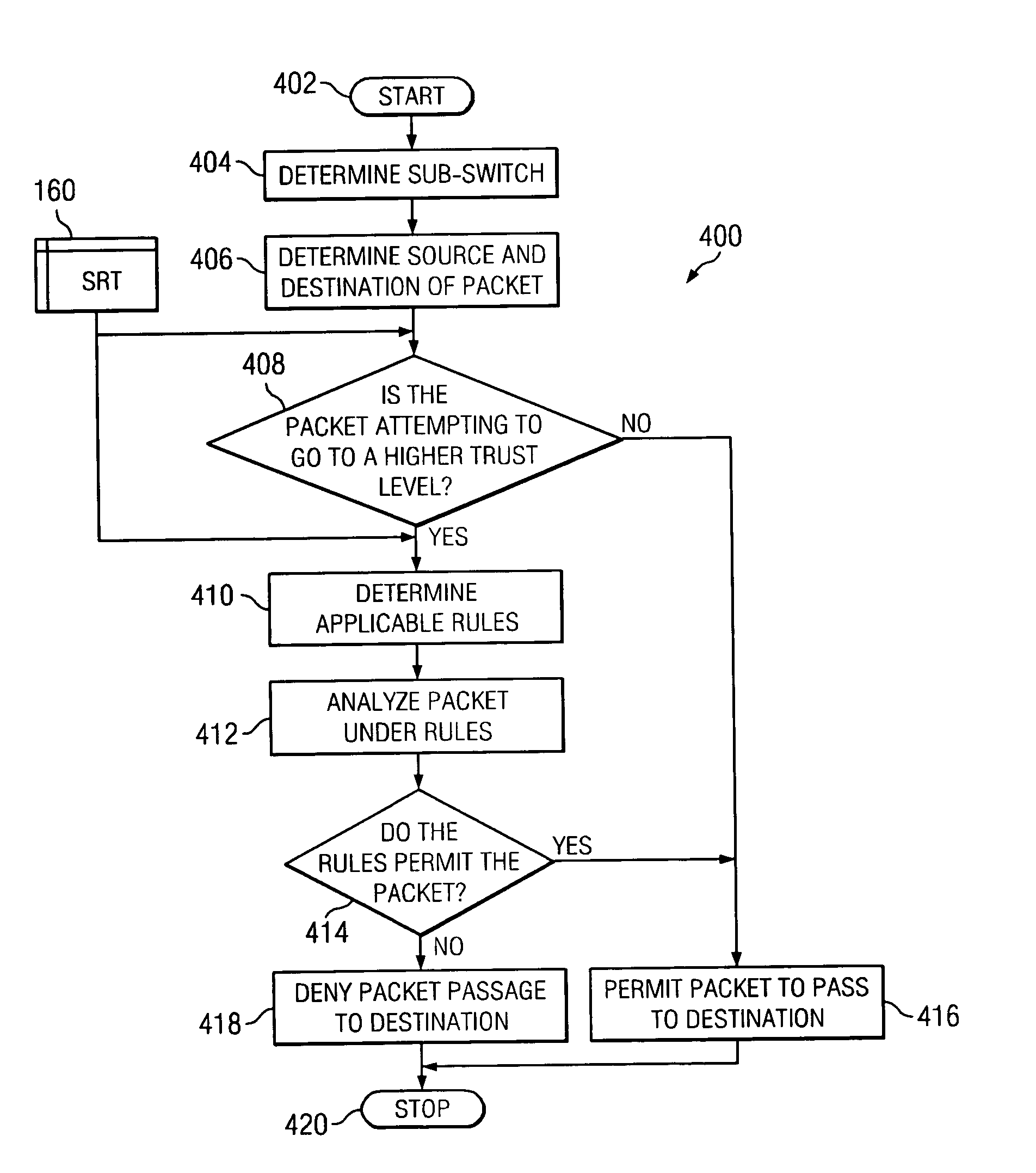
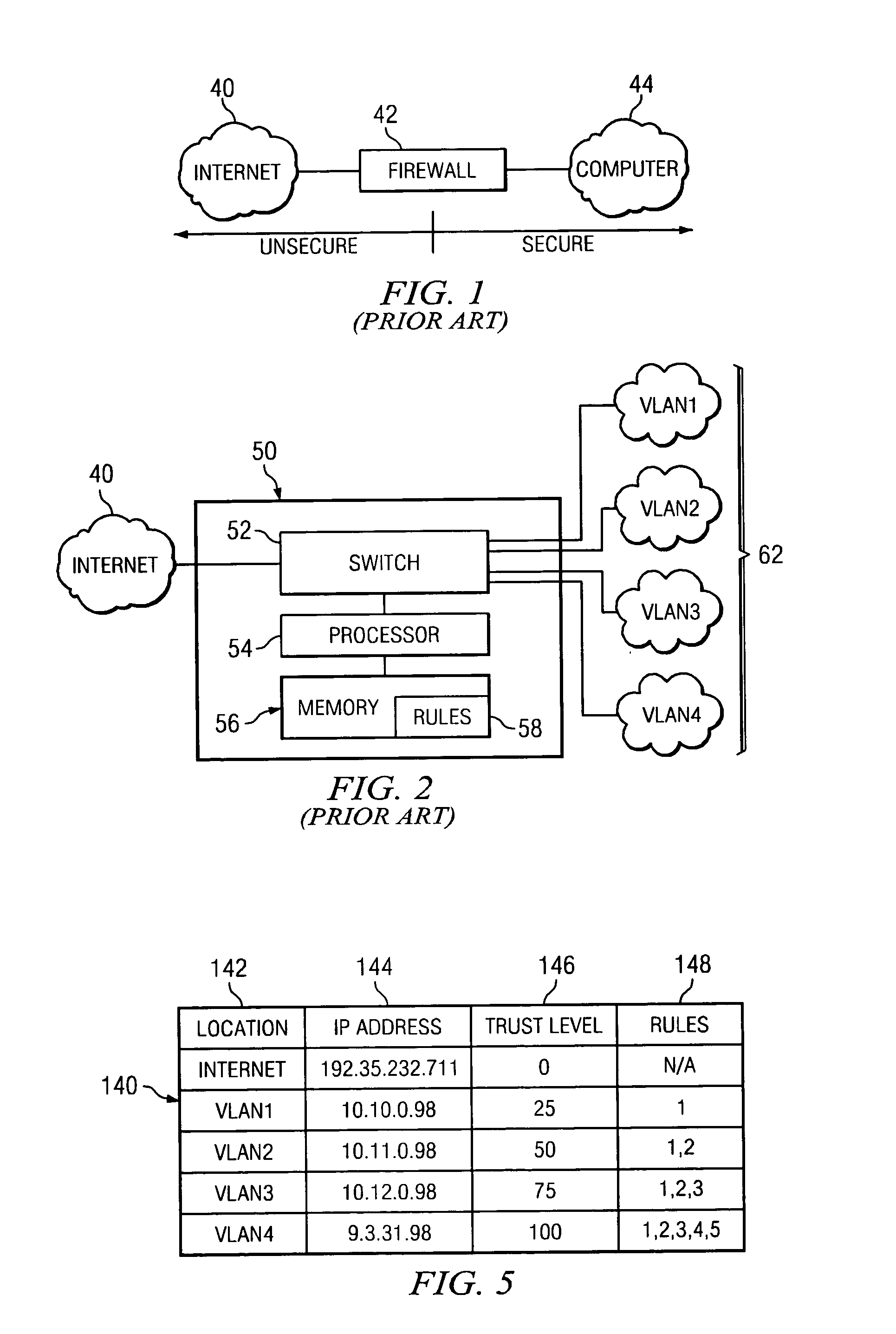
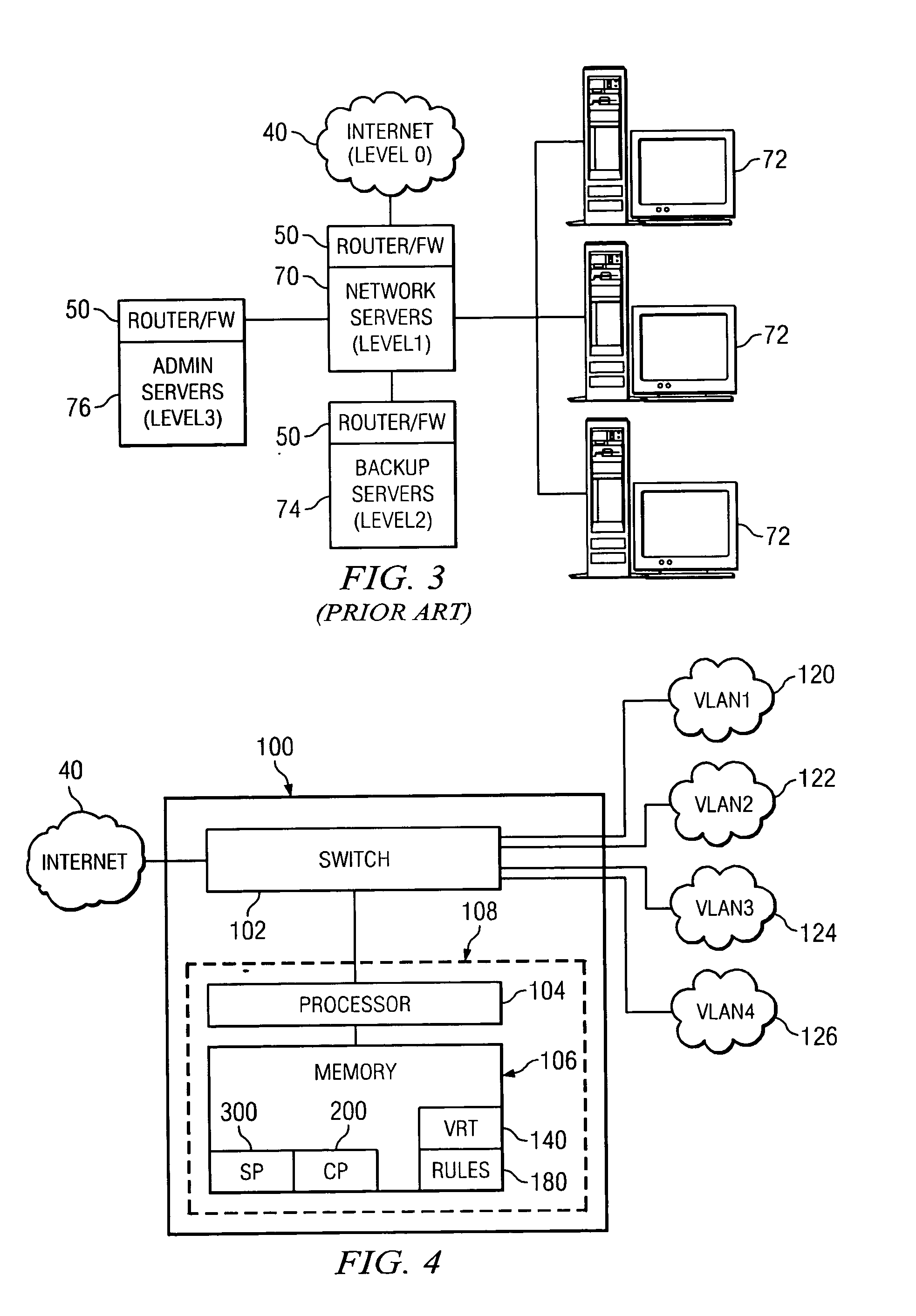
VLAN router with firewall supporting multiple security layers
InactiveUS20050081058A1Eliminates redundant ruleShorten comparison timeDigital data processing detailsMultiple digital computer combinationsVirtual LANTrust level
A router containing a firewall capable of supporting a plurality of different security levels. The router of the present invention creates a plurality of Virtual Local Area Networks (VLANs) using a network switch. The VLAN Rules Table (VRT) allows a network administrator to designate a trust level for each VLAN. The trust level may be different for every VLAN and the administrator may designate different rules for each VLAN. The Security Program (SP) analyzes each packet passing through the firewall and determines if the packet is permitted under the rules for the VLAN trust level. An alterative embodiment in which the switch in the router is divided into a plurality of sub-switches is also disclosed. In the alternative embodiment, the firewall need only compare the packet to rules which were not applied in the lower trust levels, eliminating the redundant rules from the comparison process.
Owner:TREND MICRO INC
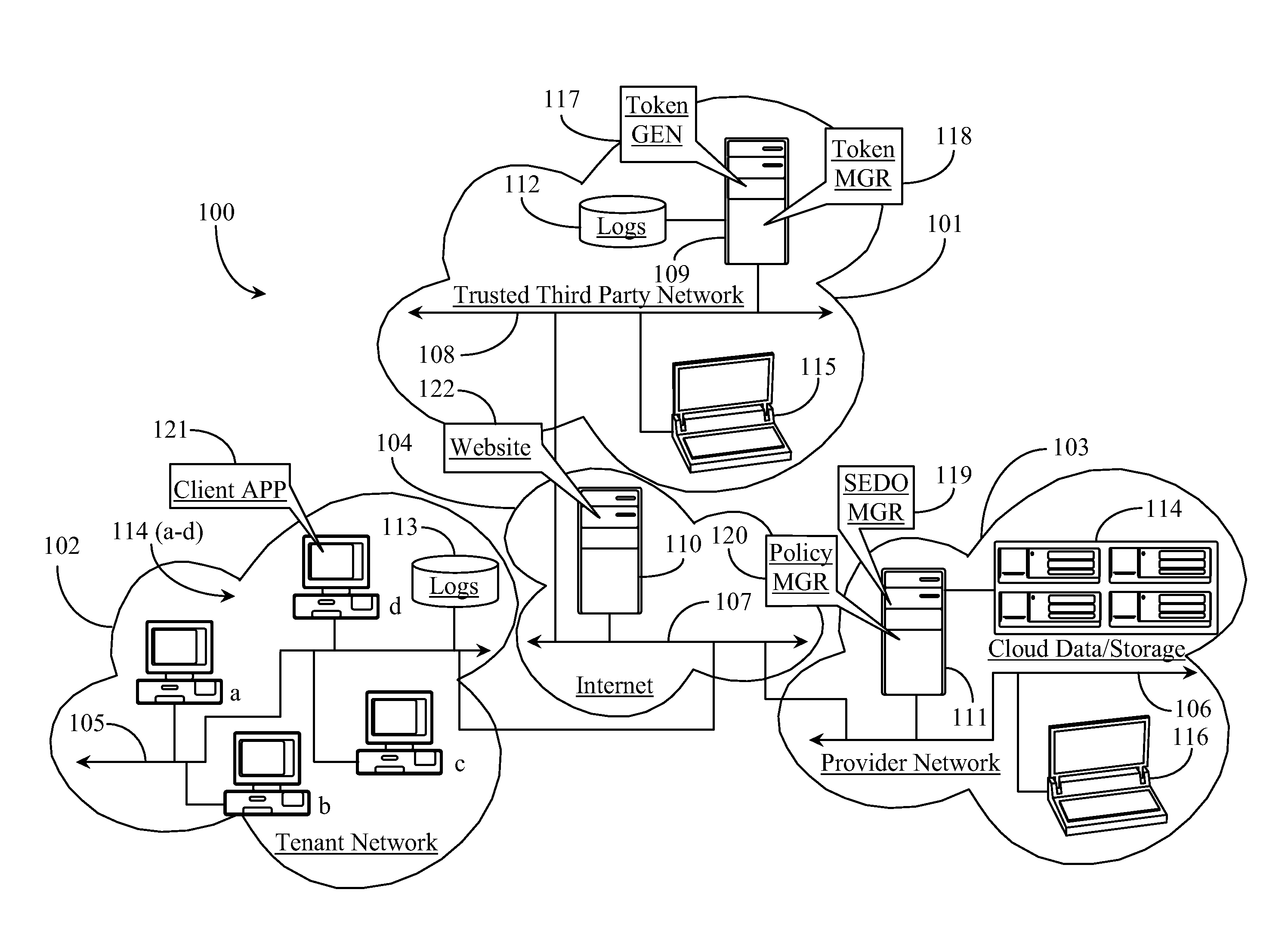
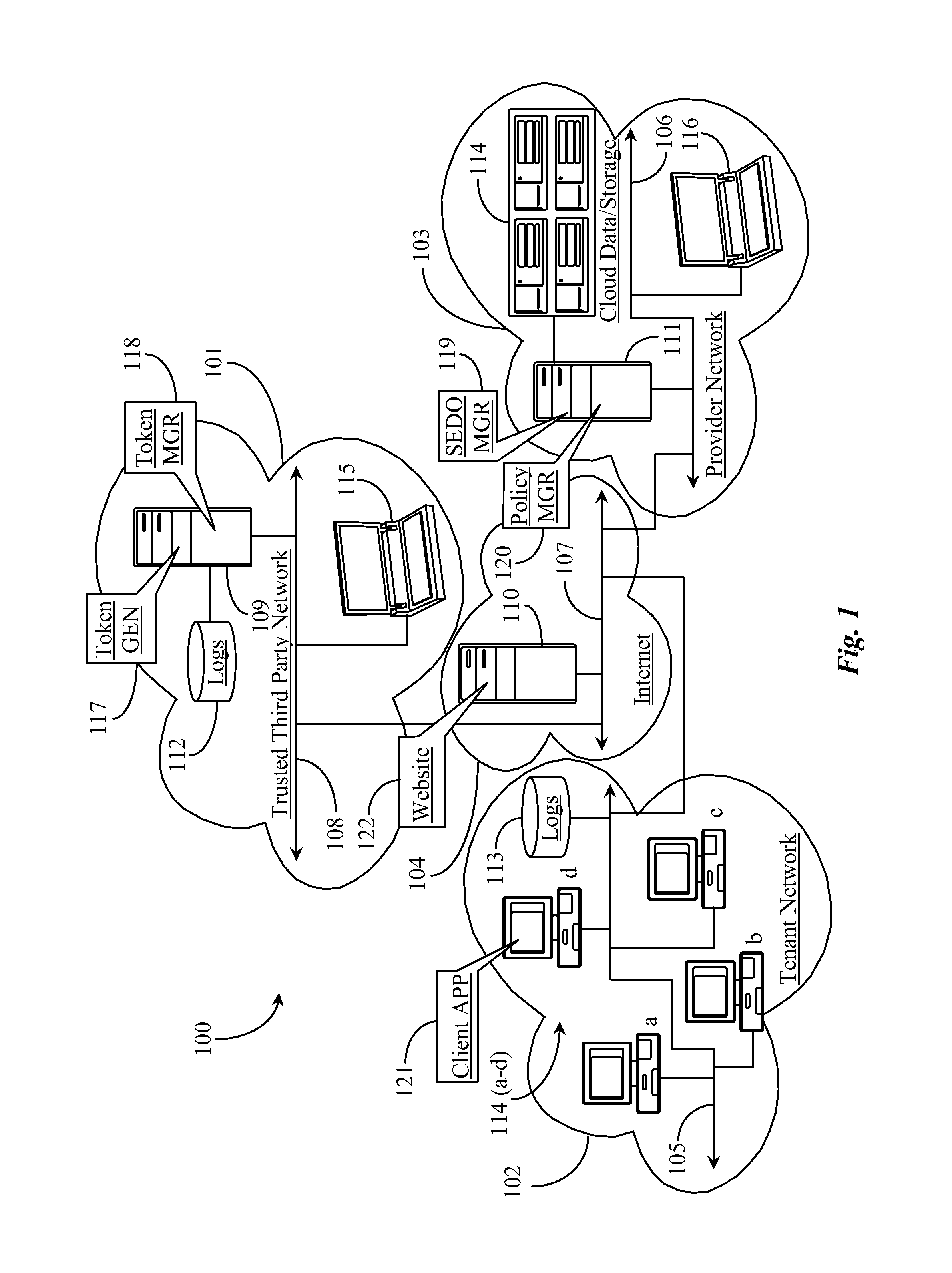
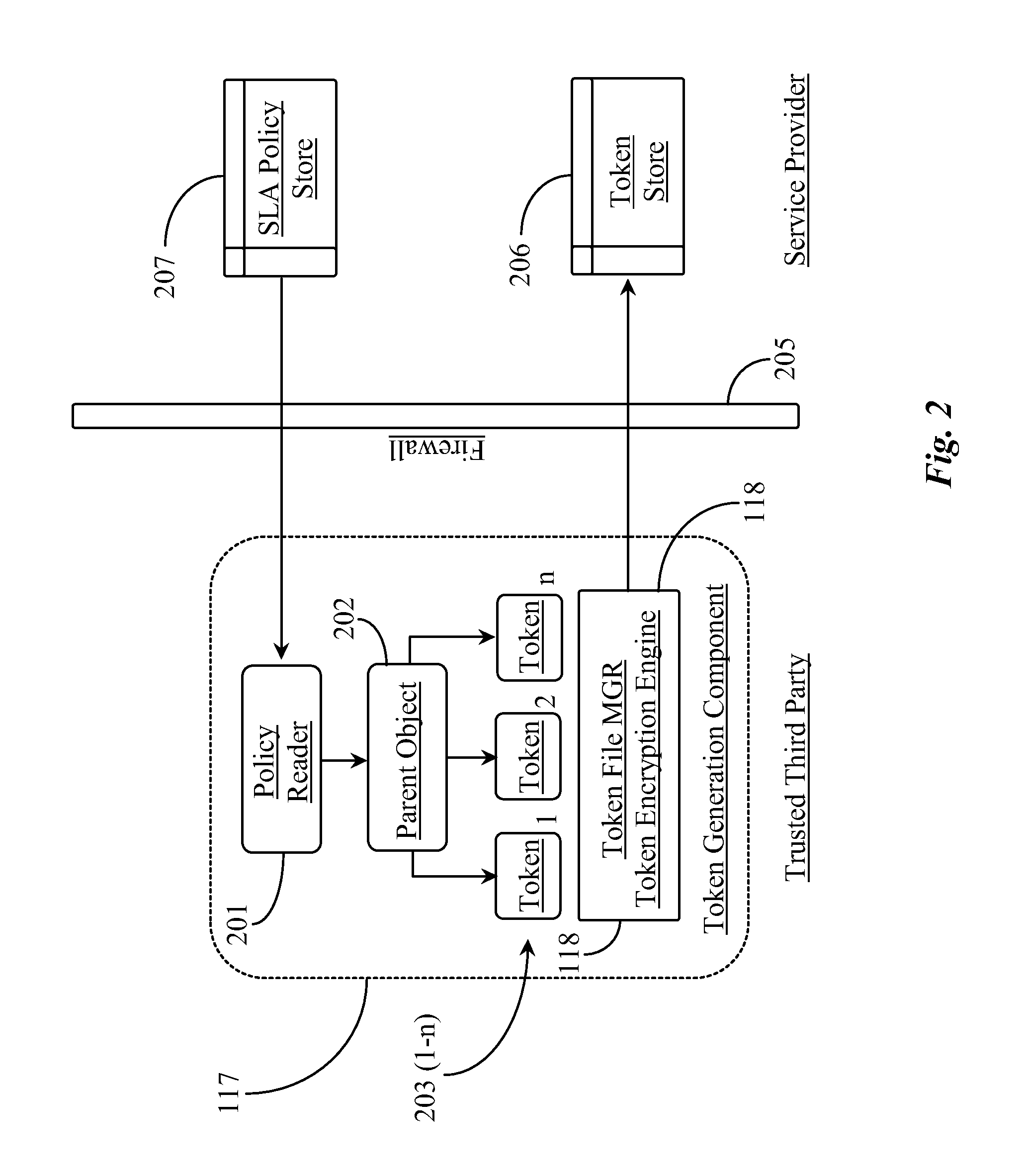
Security Layer and Methods for Protecting Tenant Data in a Cloud-Mediated Computing Network
ActiveUS20140075568A1Improve securityDigital data processing detailsAnalogue secracy/subscription systemsData operationsThe Internet
A system for protecting data managed in a cloud-computing network from malicious data operations includes an Internet-connected server and software executing on the server from a non-transitory physical medium, the software providing a first function for generating one or more security tokens that validate one or more computing operations to be performed on the data, a second function for generating a hash for each token generated, the hash detailing, in a secure fashion, the operation type or types permitted by the one or more tokens, a third function for brokering two-party signature of the one or more tokens, and a fourth function for dynamically activating the one or more signed tokens for a specific time window required to perform the operations permitted by the token.
Owner:AMRITA VISHWA VIDYAPEETHAM
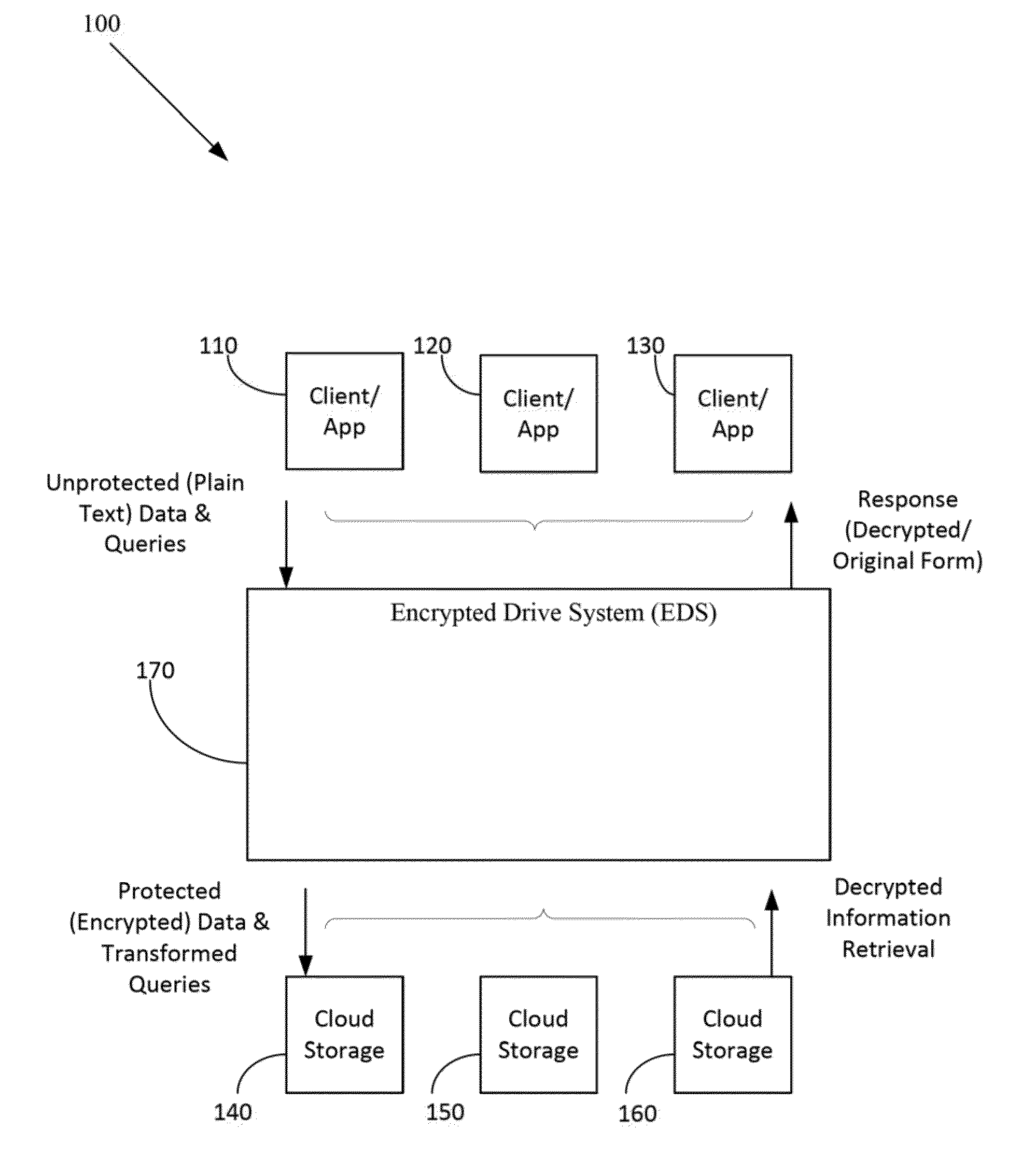
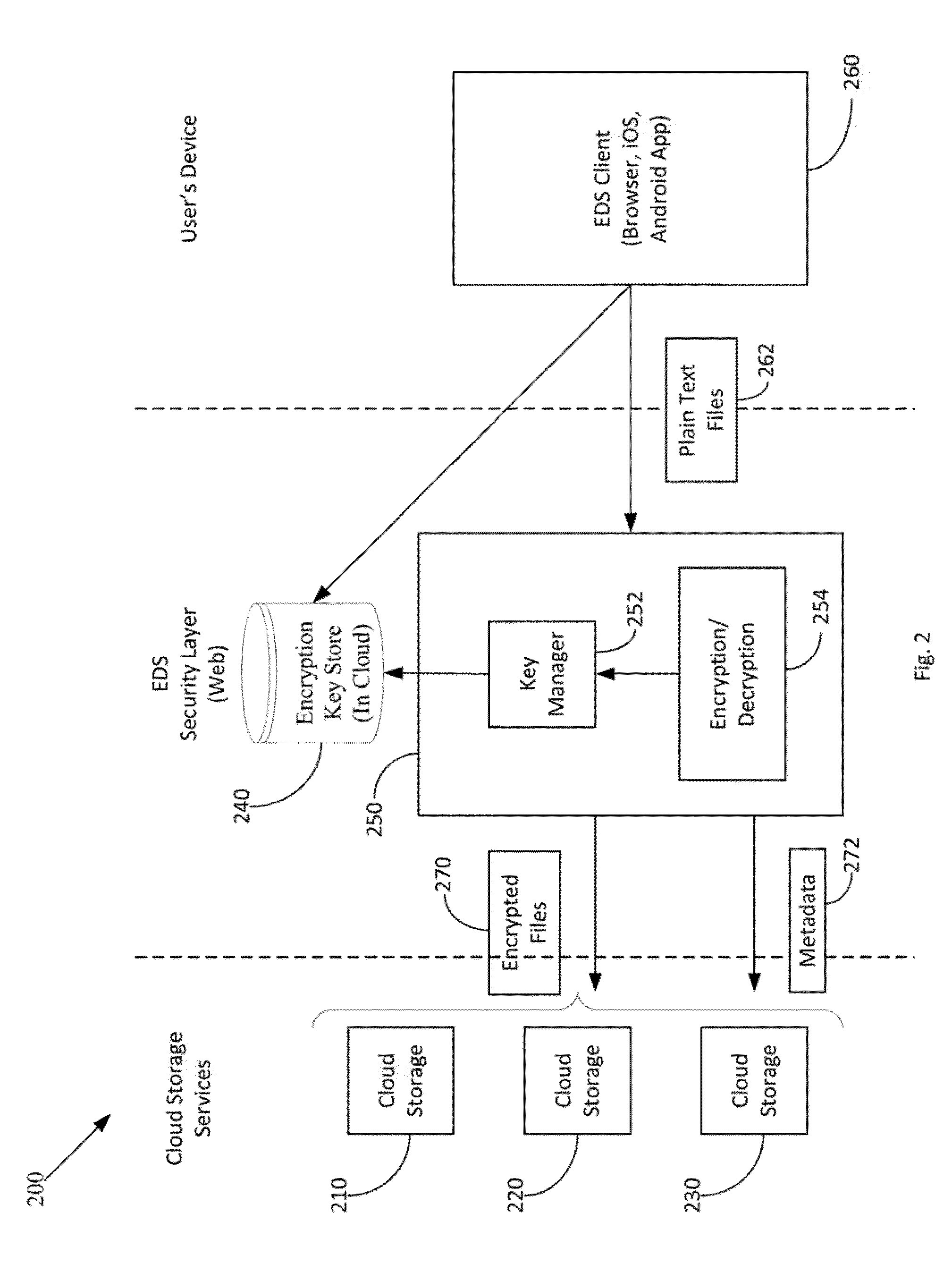
Method and apparatus for securing sensitive data in a cloud storage system
ActiveUS20150365385A1Protection attackImprove security levelEncryption apparatus with shift registers/memoriesSecurity indexData file
In one aspect, relates to a system and method of seamlessly encrypting data files before uploading them to a public cloud storage system by providing an encrypted drive system (EDS) that forms a security layer around existing cloud storage services to provide enhanced protection to data. The EDS also provides a convenient interface to specify data protection policies across connected cloud storage applications. The EDS implements standard functionalities like accessing, search and sharing directly on the encrypted data using secure indexing and querying of encrypted data. The EDS is able to guarantee a much higher level of security for data in the cloud without the user having to compromise on the features of the various applications.
Owner:GARBLECLOUD INC
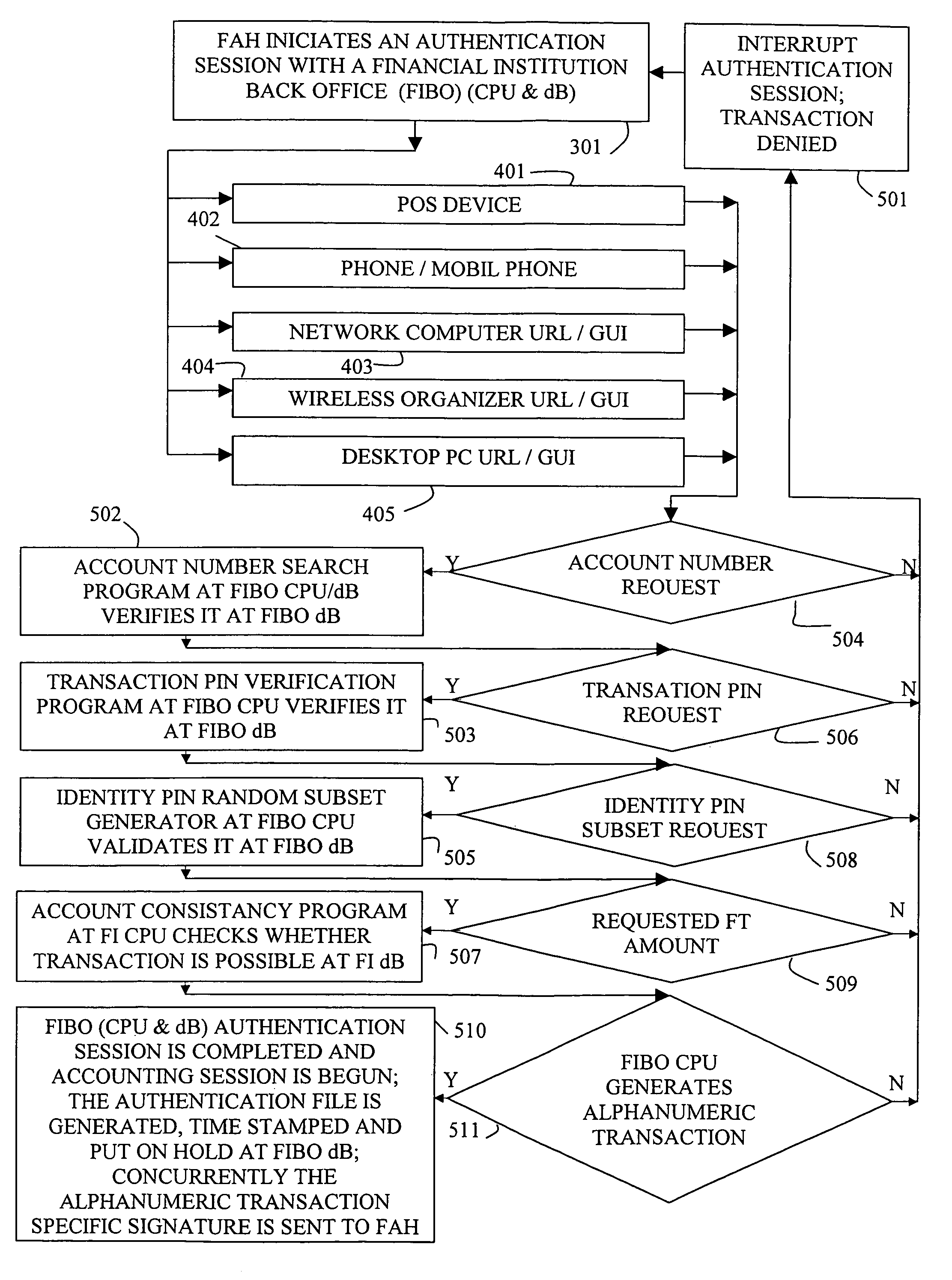
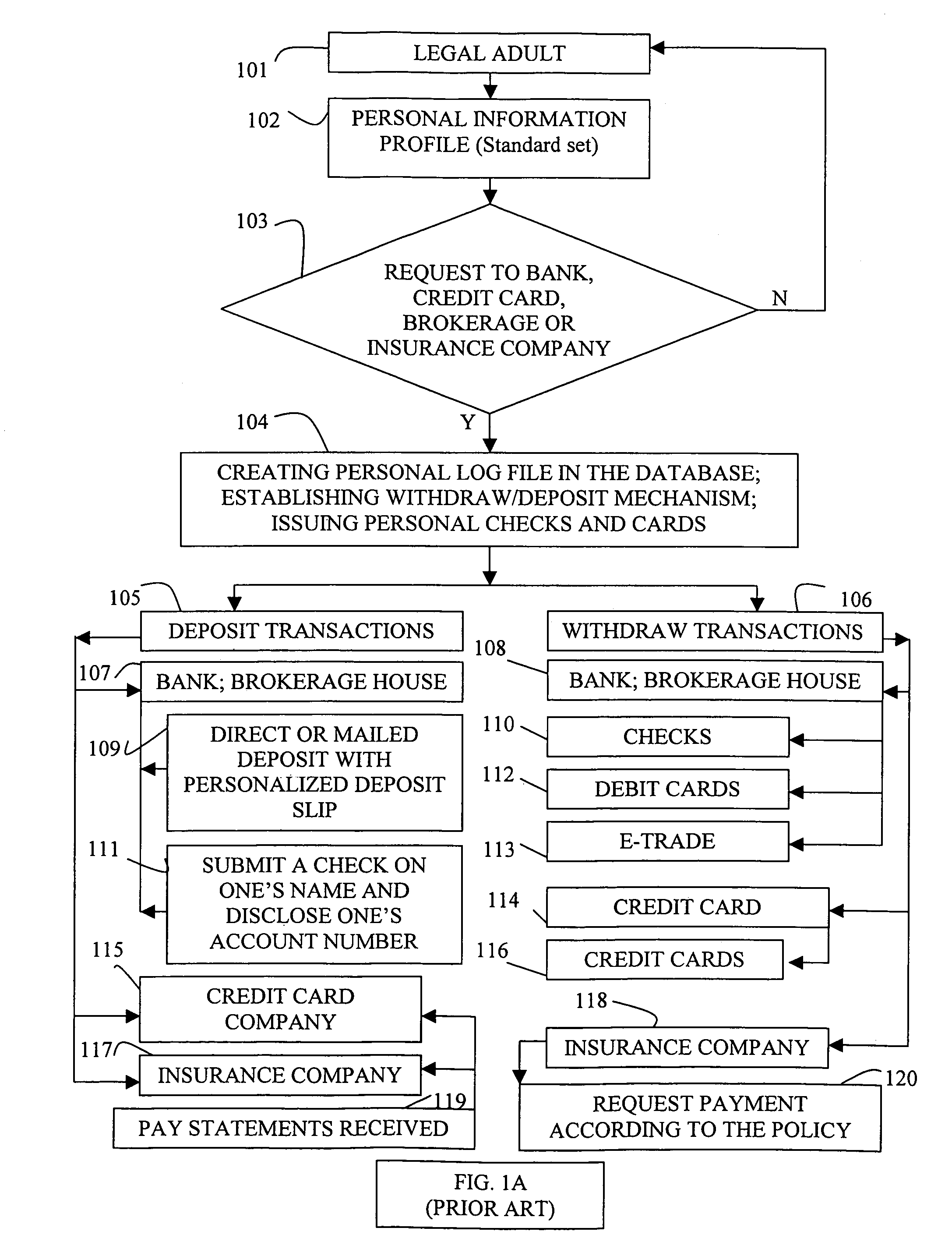
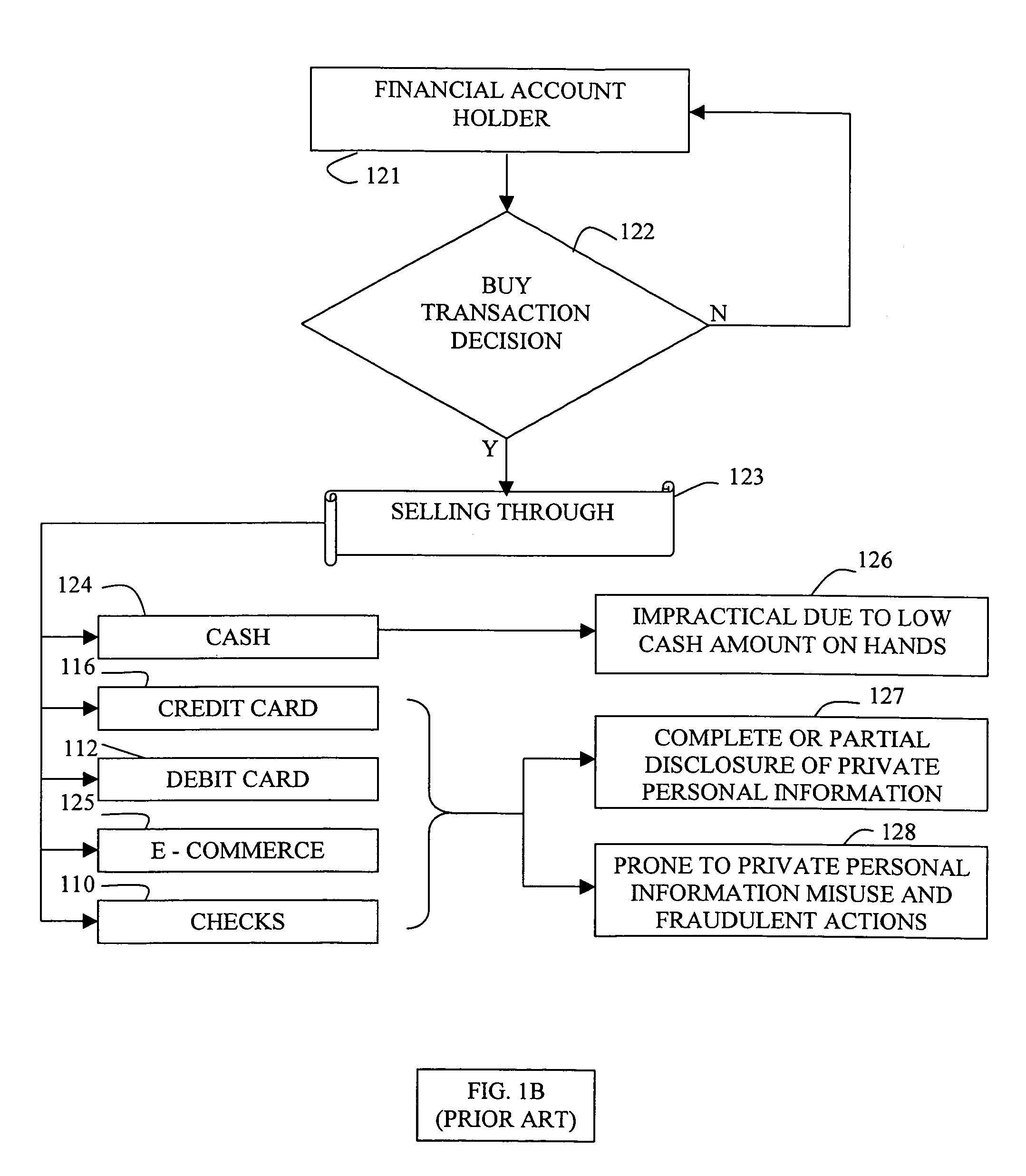
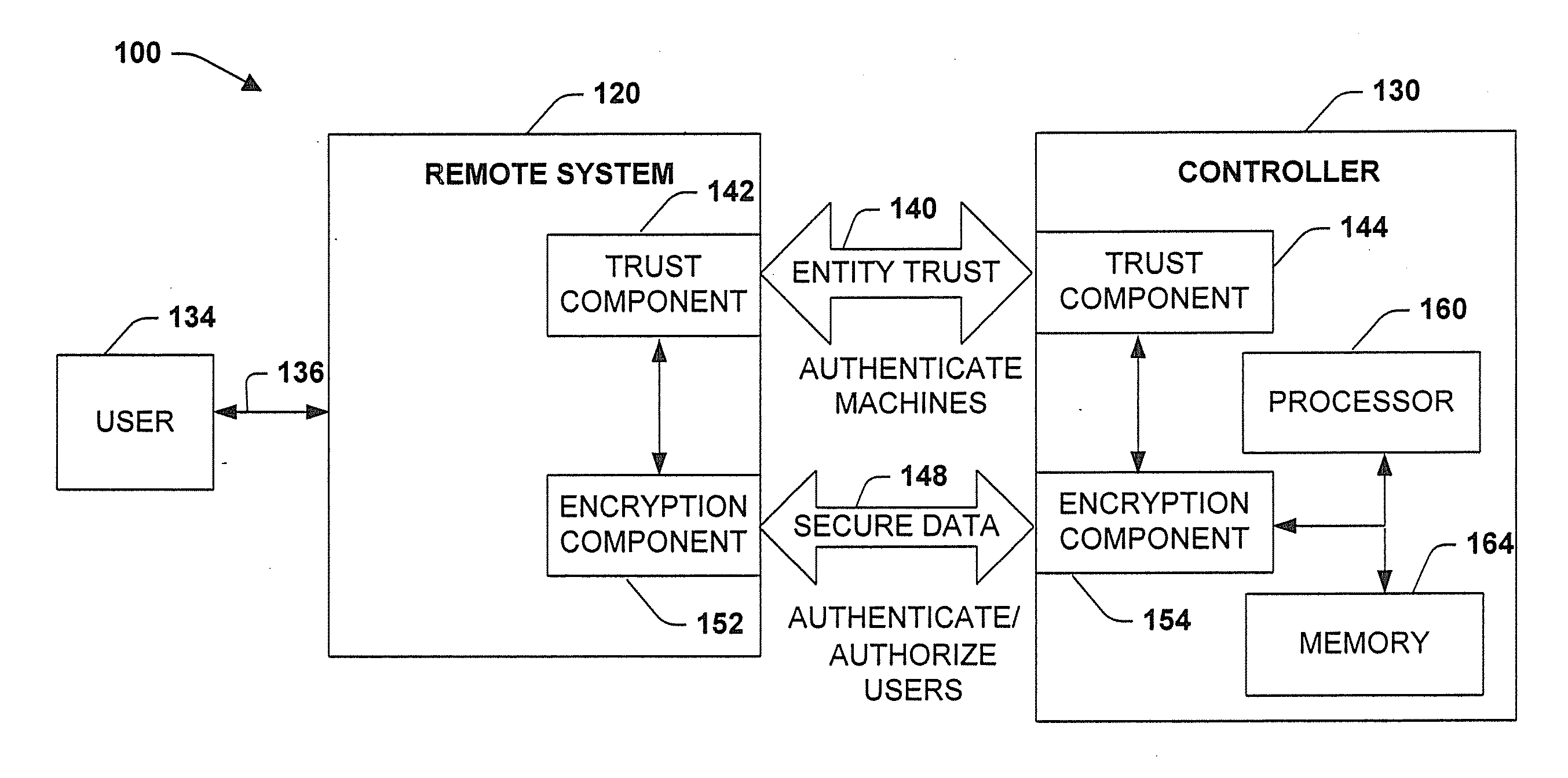
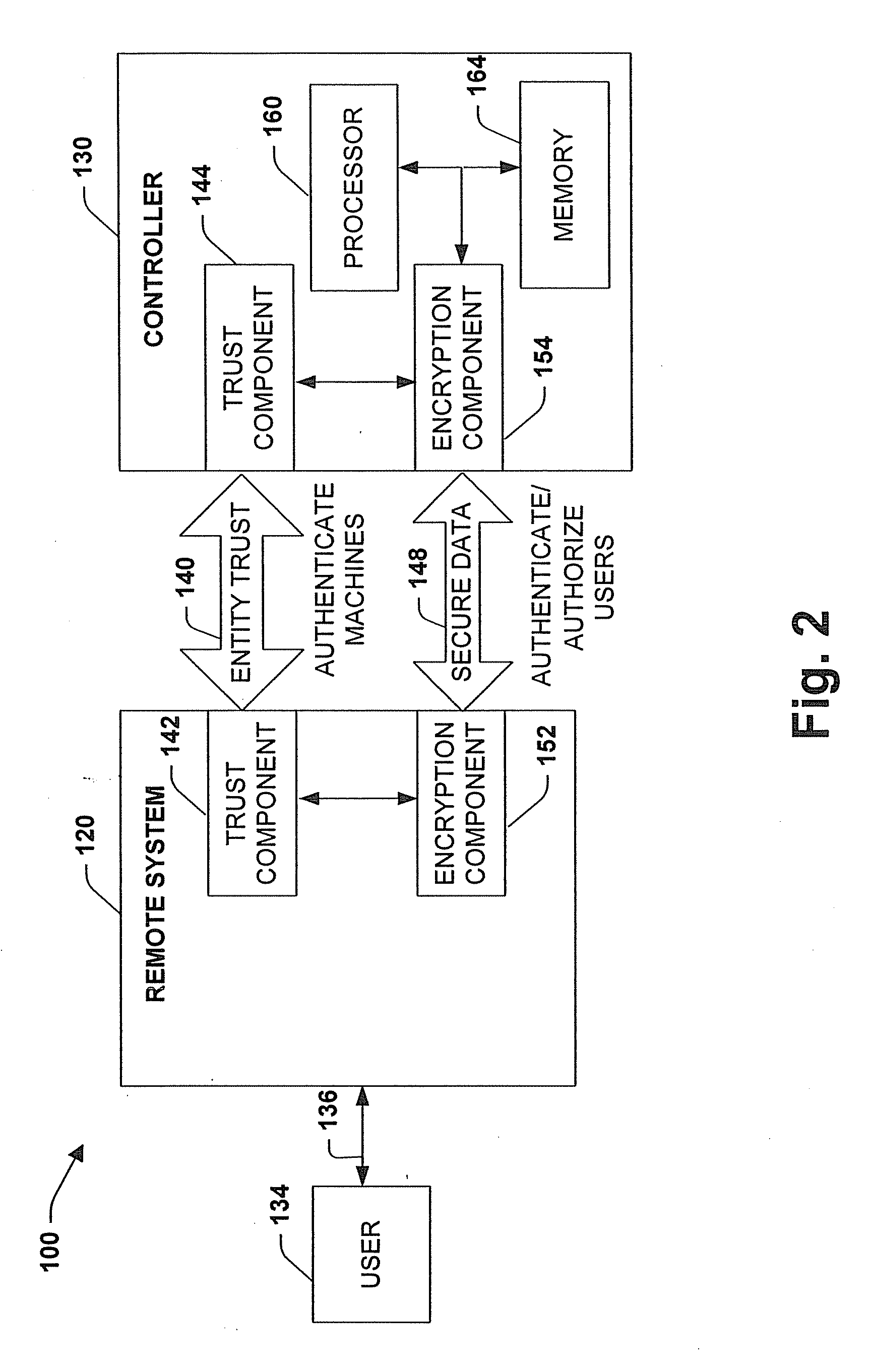
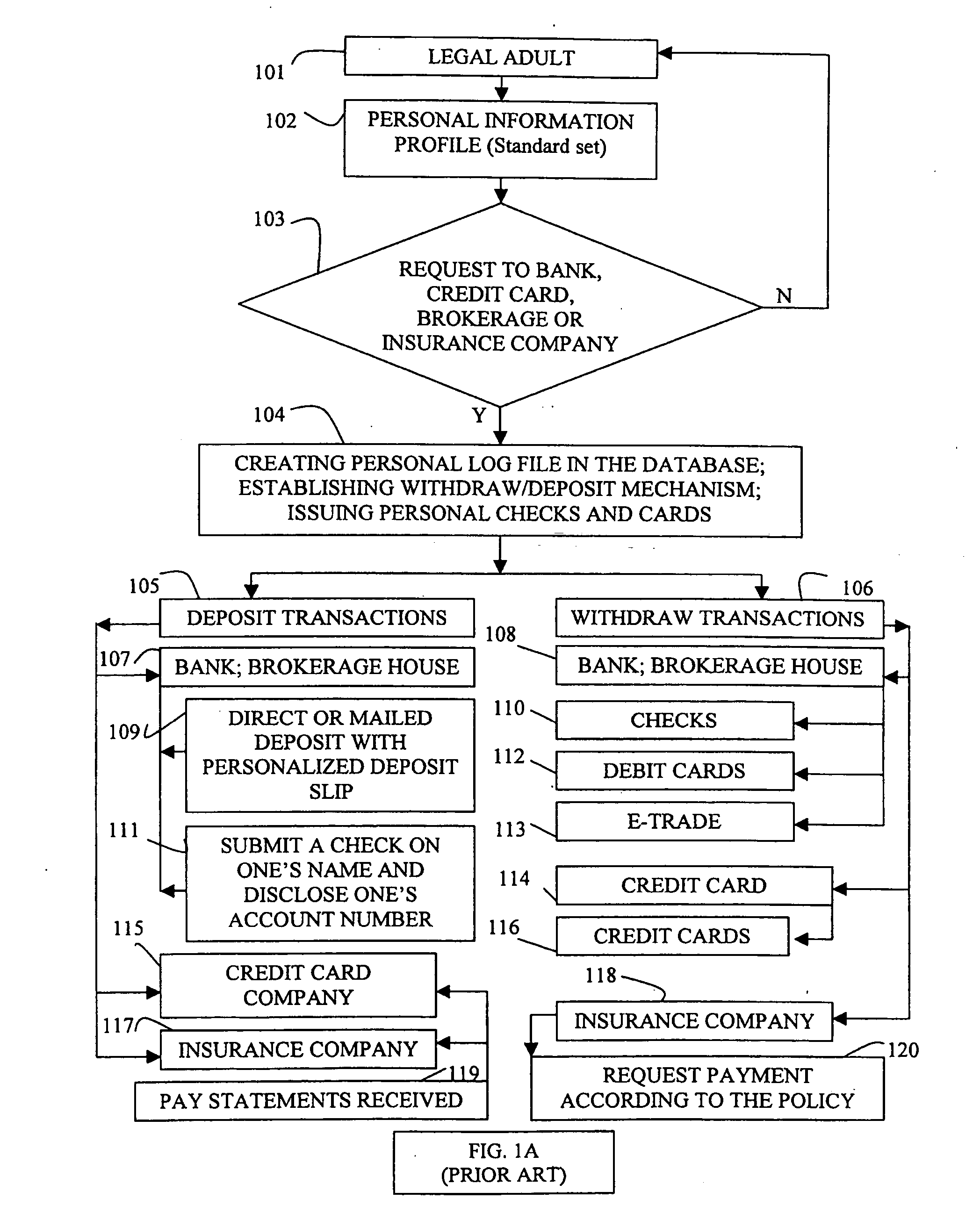
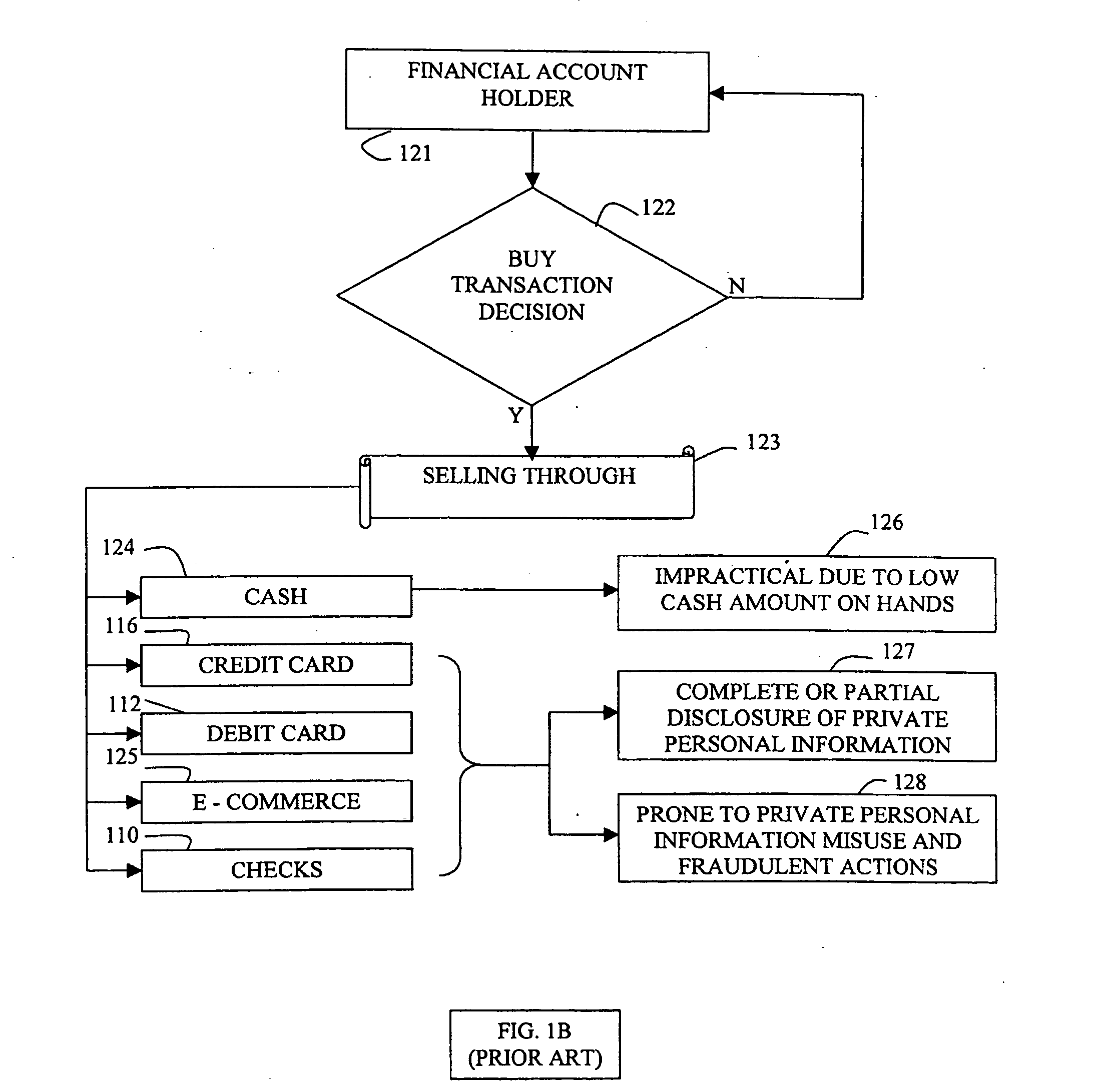
System and method for private secure financial transactions
A clocked authentication, authorization and accounting (CAAA) system and method offers private and secure credit / debit card online and offline financial transactions (FT) including an embedded privacy and security layer (EPSL) architecture. EPSL includes an authentication stage prior to the authorization stage that is automated and enabled through a back office, and enhanced by associating the authentication stage with projected timing, security and accounting parameters. It enables legal financial account holders to perform buy / sell or withdraw / deposit transactions without disclosing private personal information to the transaction counterparts, while preserving highly elevated and enhanced security and fraud protection as compared with conventional methods. The CAAA method enables efficient mass user EPSL implementation at back offices utilizing high frequency synchronized global clocking of EPSL logic blocks.
Owner:AUTHERNATIVE INC
Peer-to-peer communication method for near field communication
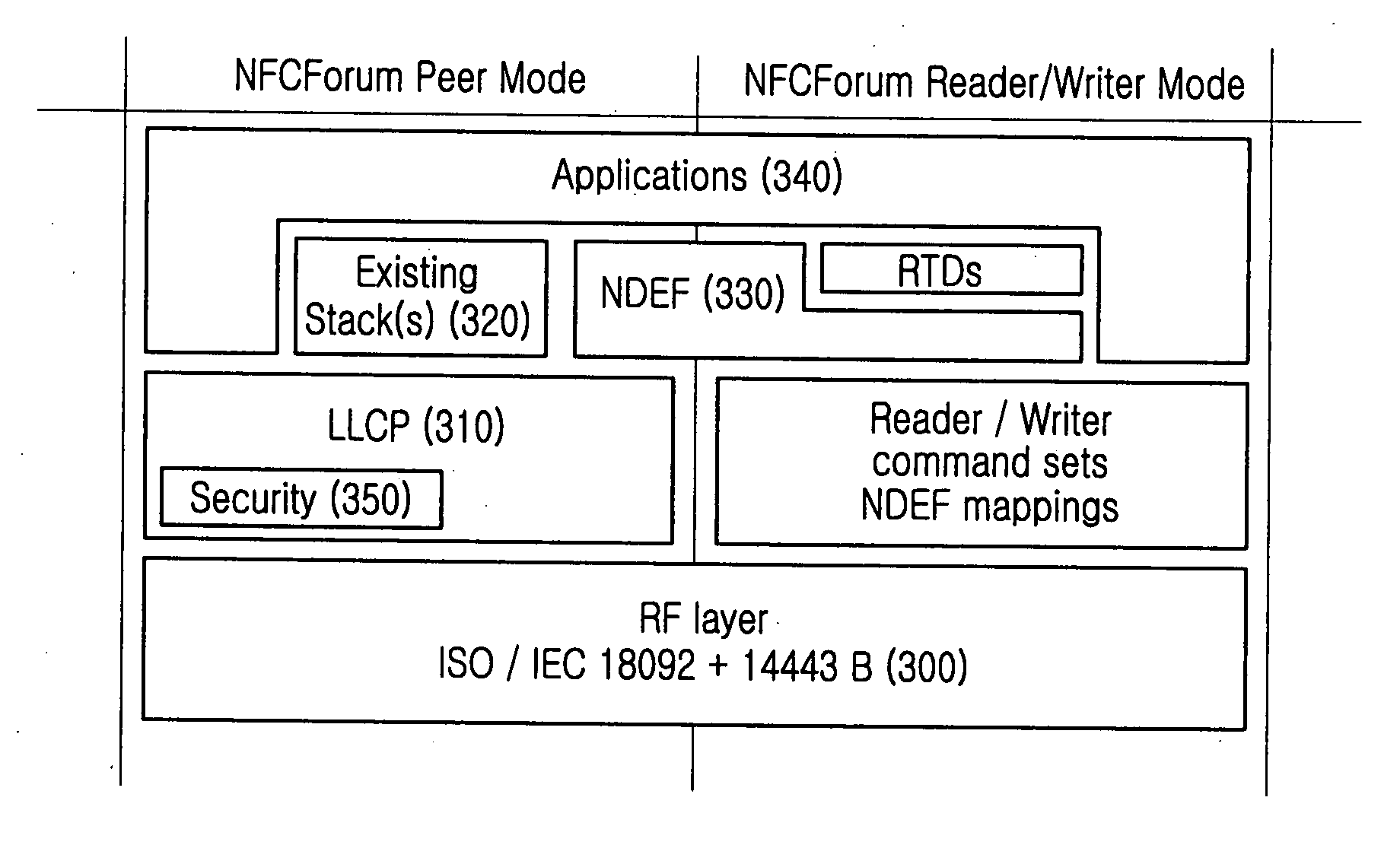
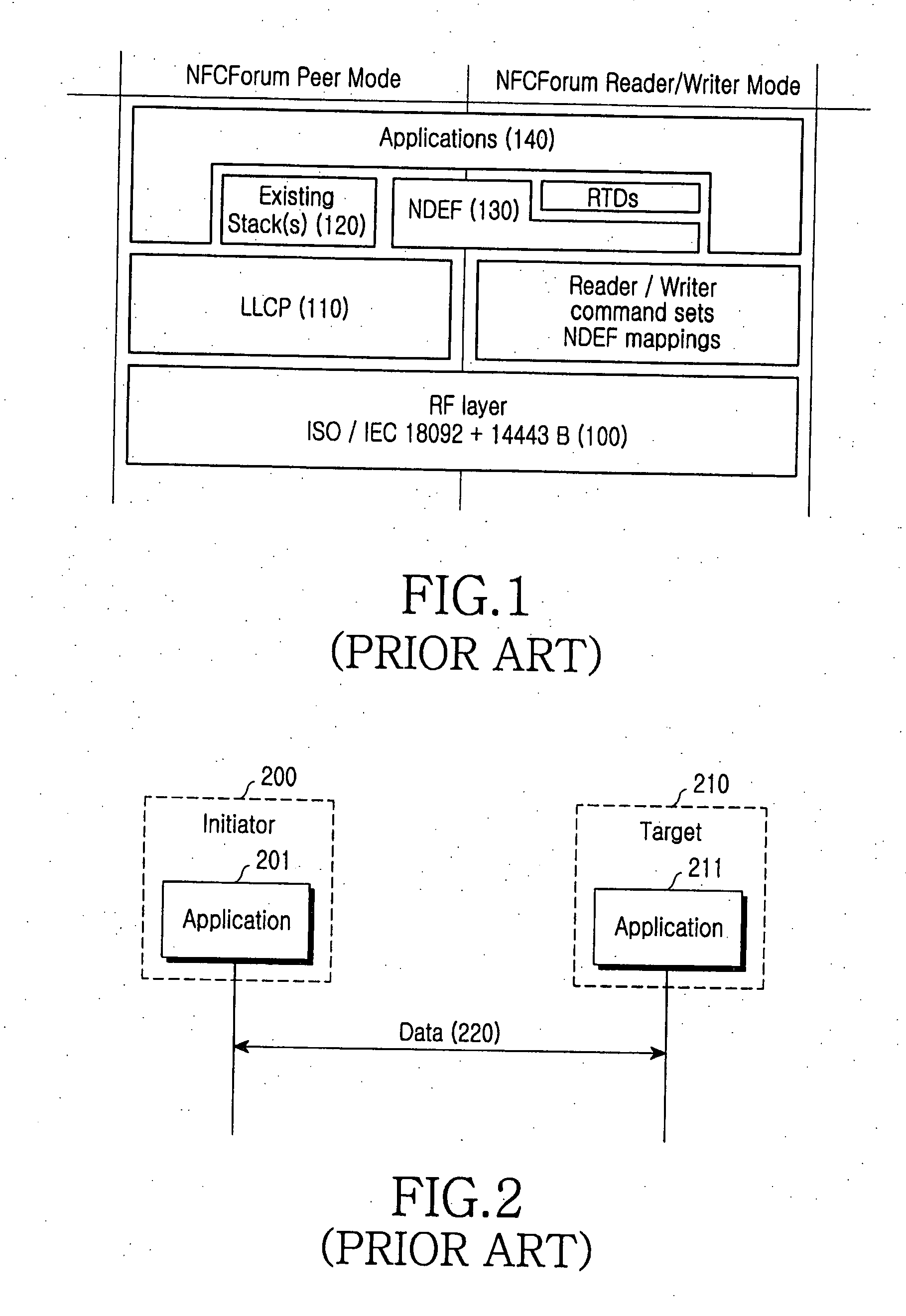
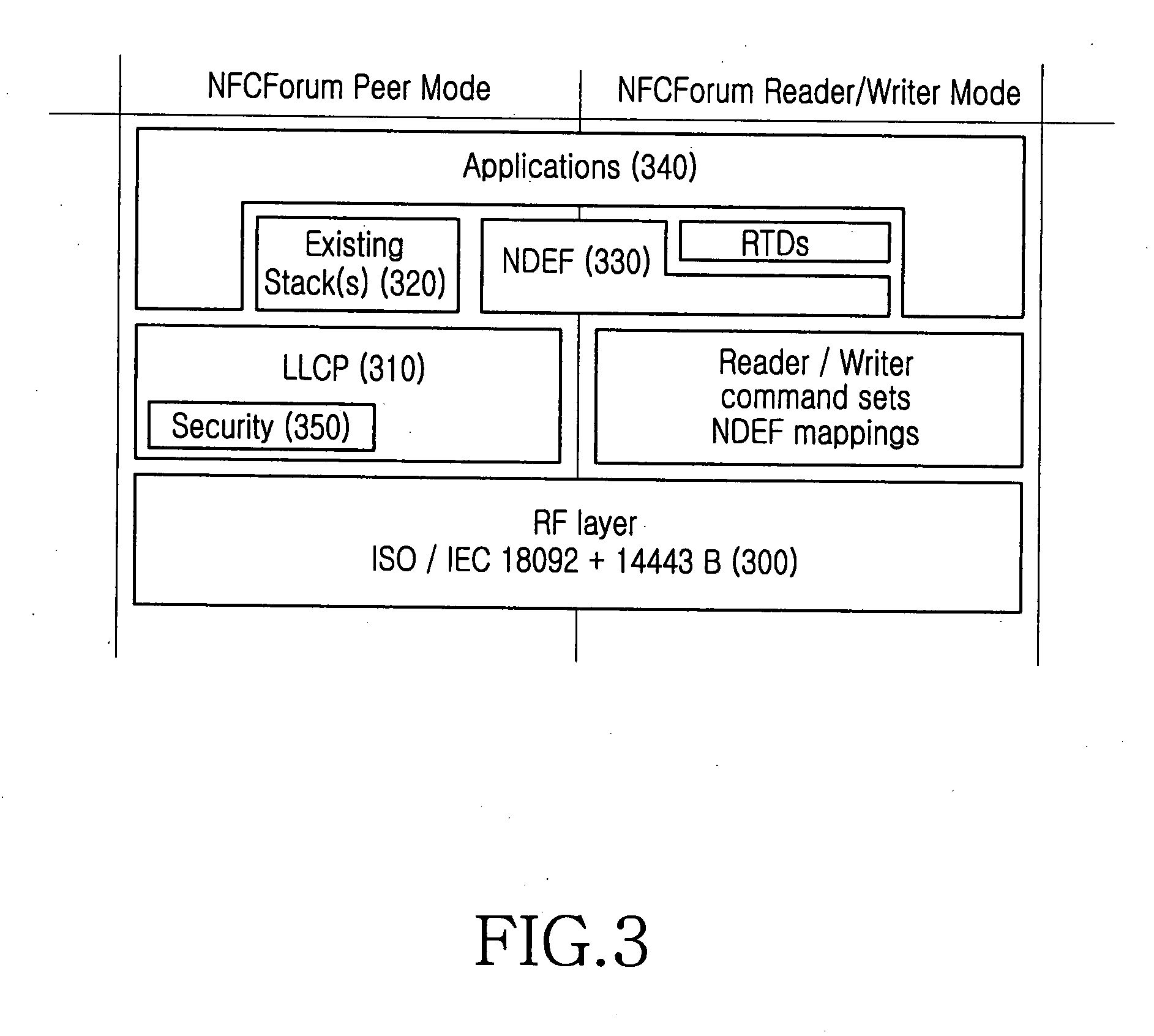
ActiveUS20080065877A1Stricter securityNear-field transmissionRadio transmissionPeer-to-peerPeer communication
A peer-to-peer communication method for NFC is provided. A link-level security is started by exchanging a link-level security request and a link-level security response between an initiator terminal and a target terminal, then transmission data are encrypted at link-level security layers of the initiator terminal and the target terminal, and the encrypted data are exchanged between the initiator terminal and the target terminal. The link-level security is released by exchanging a link-level security release request and a link-level security release response between the initiator terminal and the target terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
System and methodology providing multi-tier security for network data with industrial control components
The present invention relates to a system and methodology facilitating network security and data access in an industrial control environment. An industrial control system is provided that includes an industrial controller to communicate with a network. At least one security layer can be configured in the industrial controller, wherein the security layer can be associated with one or more security components to control and / or restrict data access to the controller. An operating system manages the security layer in accordance with a processor to limit or mitigate communications from the network based upon the configured security layer or layers.
Owner:ROCKWELL AUTOMATION TECH
Reducing the computational load on processors by selectively discarding data in vehicular networks
ActiveUS8314718B2Reduce computing loadReduce bottlenecksService provisioningParticular environment based servicesCommunications systemComputer science
Owner:GM GLOBAL TECH OPERATIONS LLC
Communication stack for network communication and routing
InactiveUS20050216727A1Imparts flexibilityImparts extensibilitySecuring communicationNetwork communicationSecurity parameter
A communication stack enables computers implementing it to send, receive, or route network communications. The communication stack includes a message layer, a communication layer, a security layer, and a transport protocol layer, with plug-in transport protocol modules and plug-in security protocol modules. Each of the origin computer, target computer, and routing computers involved in delivering a message implements the communication stack. An application on the origin computer calls the message layer of the computer to send messages to a target computer and identifies routing computers on the route for delivering the message to the target computer. The message layer calls the communication layer to establish a connection to the target computer. The communication layer uses the transport protocol layer to establish an initial connection with the target computer, and uses the security layer to negotiate security parameters and to handle secured communications between the origin and target computers.
Owner:MICROSOFT TECH LICENSING LLC
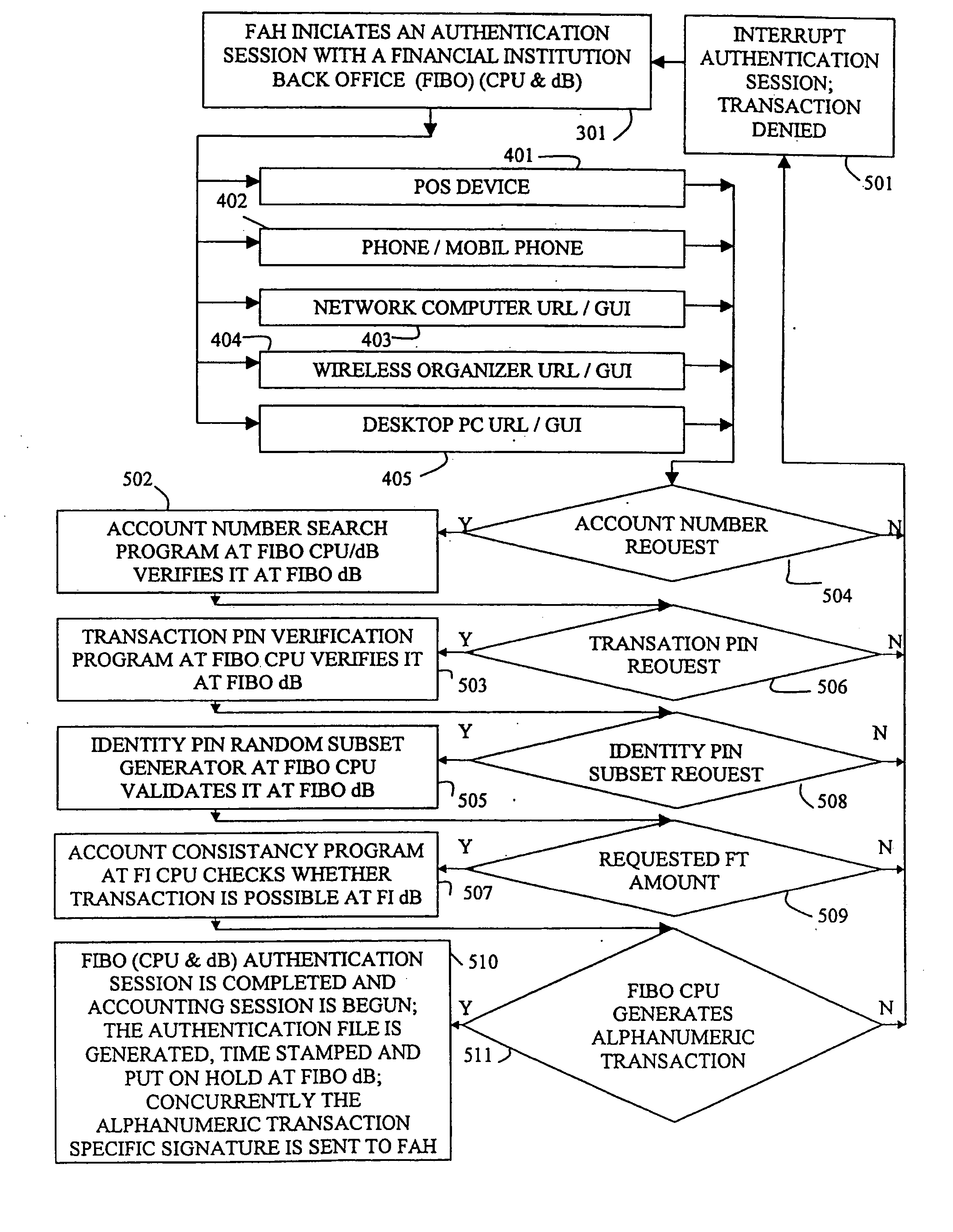
Method of one time authentication response to a session-specific challenge indicating a random subset of password or PIN character positions
InactiveUS20060136317A1Highly elevated and enhanced securityEfficient deploymentComplete banking machinesFinancePasswordRecognition algorithm
Financial institution back office computerized transaction-processing system with embedded privacy and security layer (EPSL) enables strong transaction authentication prior to a merchant or vendor contact, based on a user account number, transaction conditions like anticipated transaction time and money, user two-factor authentication with a static transaction PIN and a transaction session-specific random partial password or PIN recognition algorithm. User enters the user name and then, challenged by server with a random session-specific subset of a password or PIN character's consecutive position numbers, enters based on cognitive association a one time authentication response. The authentication session is interactive, transaction session-specific, and followed by either a transaction denial or an alphanumeric transaction signature generated by EPSL for this specific transaction. Then, the user submits her request to a transaction counterpart along with the transaction signature. The merchant or vendor requests an authorization session with EPSL.
Owner:AUTHERNATIVE INC
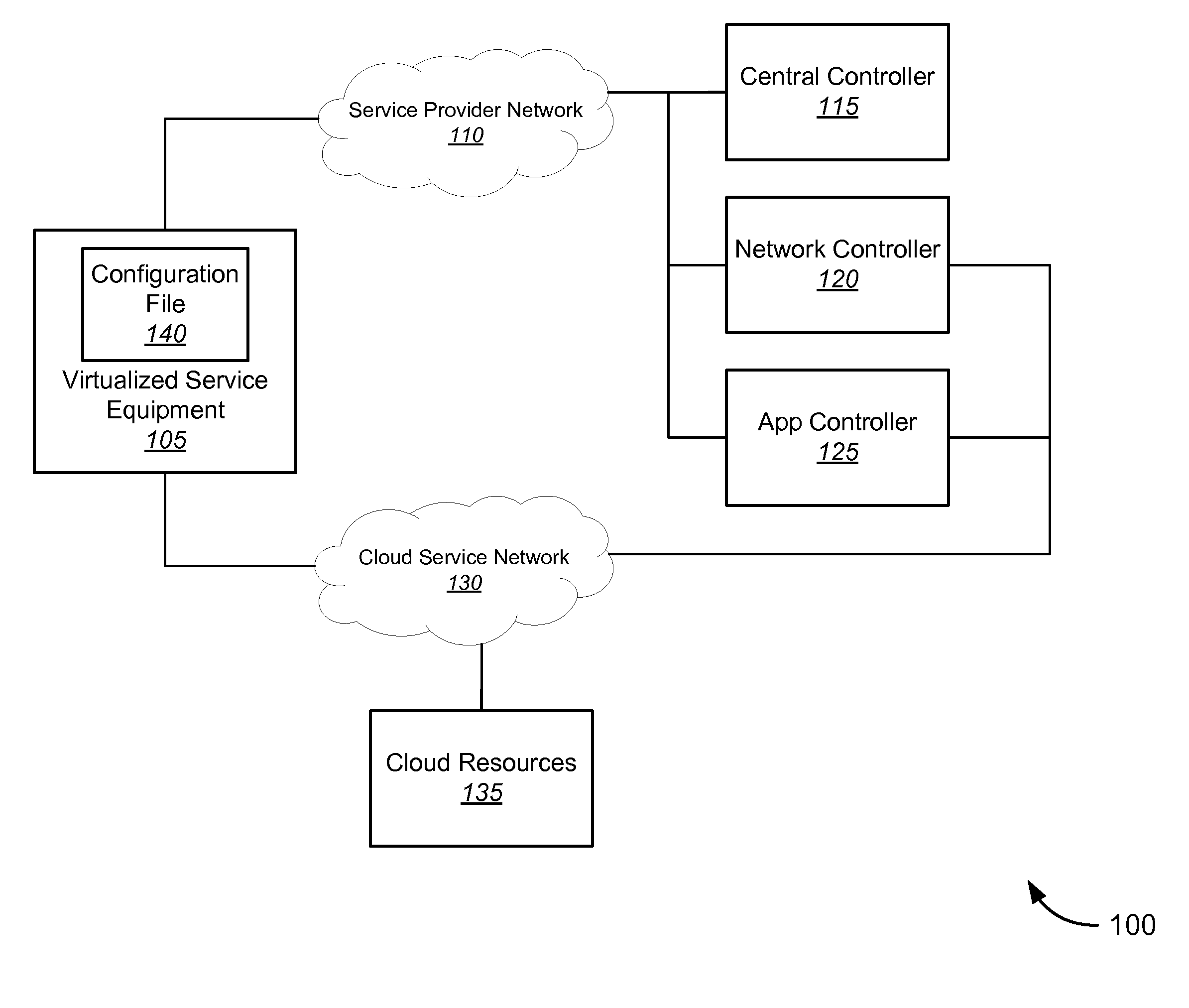
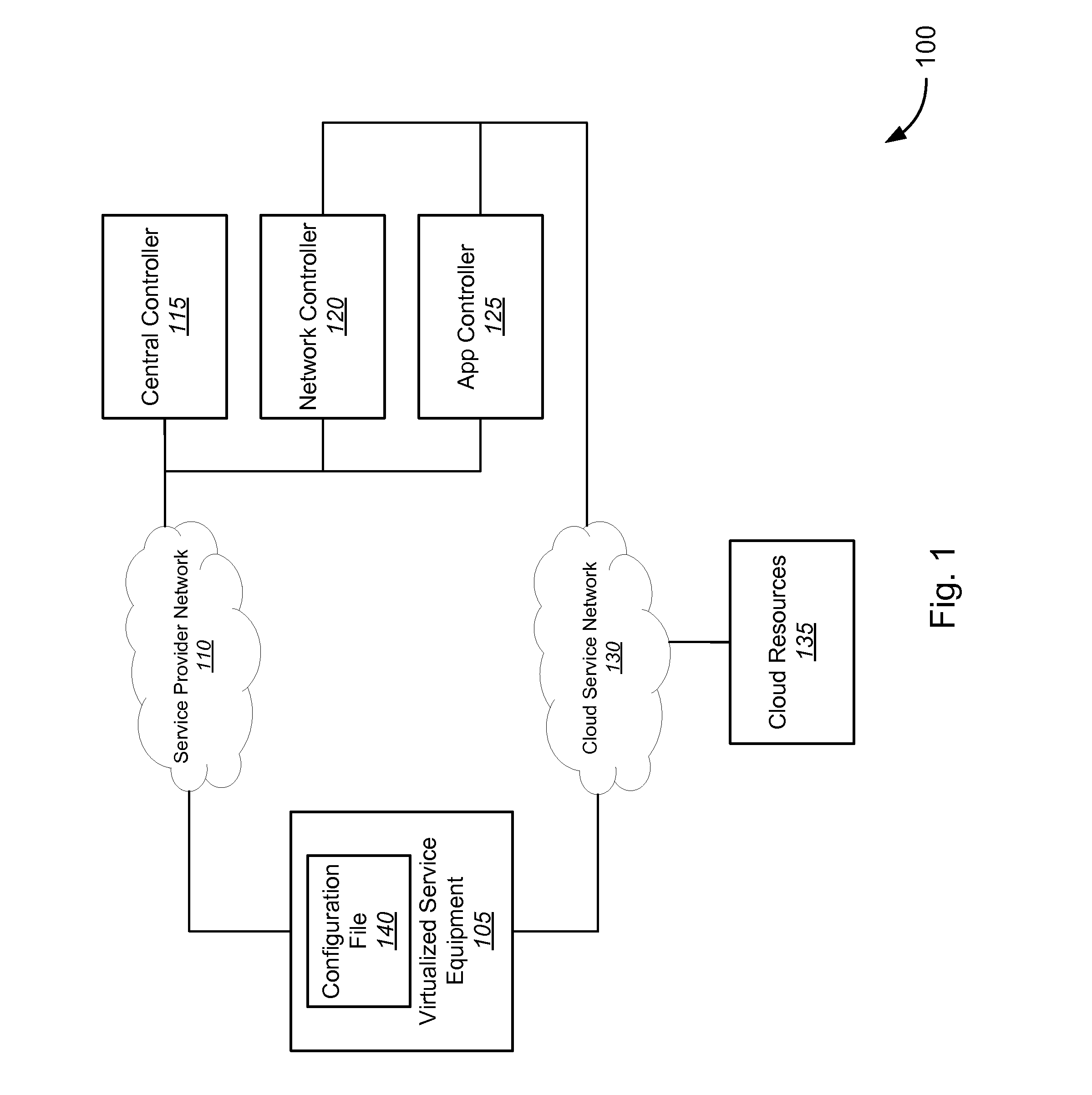
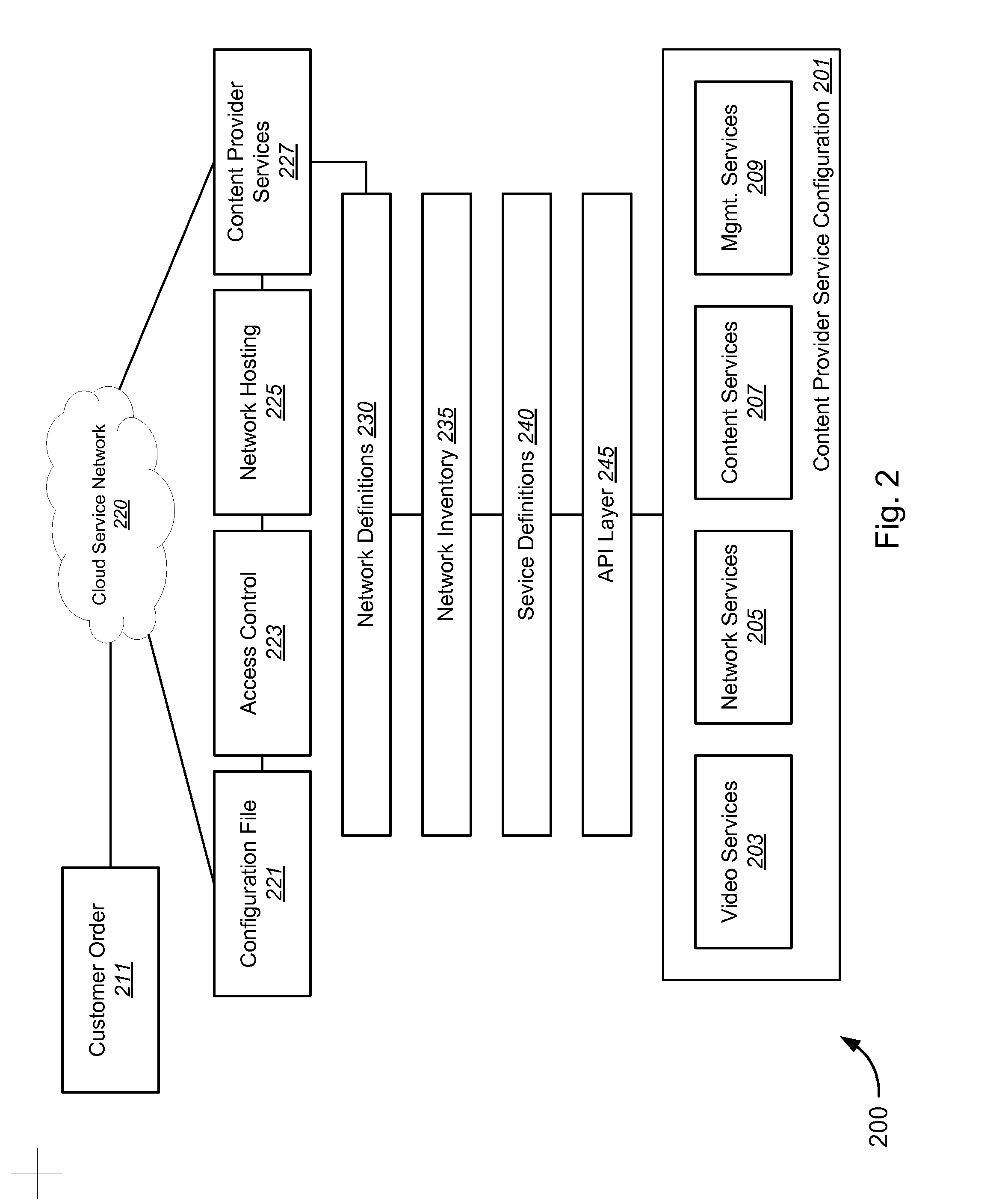
Network Services API
Novel tools and techniques are provided for invoking virtualized network functions. In some embodiments, a programmable service backbone might comprise at least one virtualized network function, and might provide virtualized network functions required to provision a service offering. In some cases, at least one application programming interface might be configured to invoke the at least one virtualized network function of the programmable service backbone. An application programming interface gateway might be configured to manage access to the at least one application programming interface, and the application programming interface gateway might comprise a security layer. Virtualized service equipment, which might be in communication with the application programming interface gateway, might provide authentication indicative of selected virtualized network functions associated with the service offering, and the security layer might release an authorized subset of virtualized network functions of the at least one virtualized network function based on the authentication.
Owner:CENTURYLINK INTPROP
Secure payment card transactions
Payment card transactions at a point of sale (POS) are secured in certain embodiments by intercepting, with a POS security layer installed on a POS terminal, payment data from the POS terminal, transmitting the payment data from the POS security layer to a server security application installed on a POS server, and providing false payment data from the POS security layer to a POS terminal application installed on the POS terminal. The false payment data in various embodiments is processed as if it were the payment data, such that the POS terminal transmits an authorization request to the POS server using the false payment data. In addition, the authorization request may be transmitted from the POS server to a payment gateway.
Owner:SHIFT4 CORP
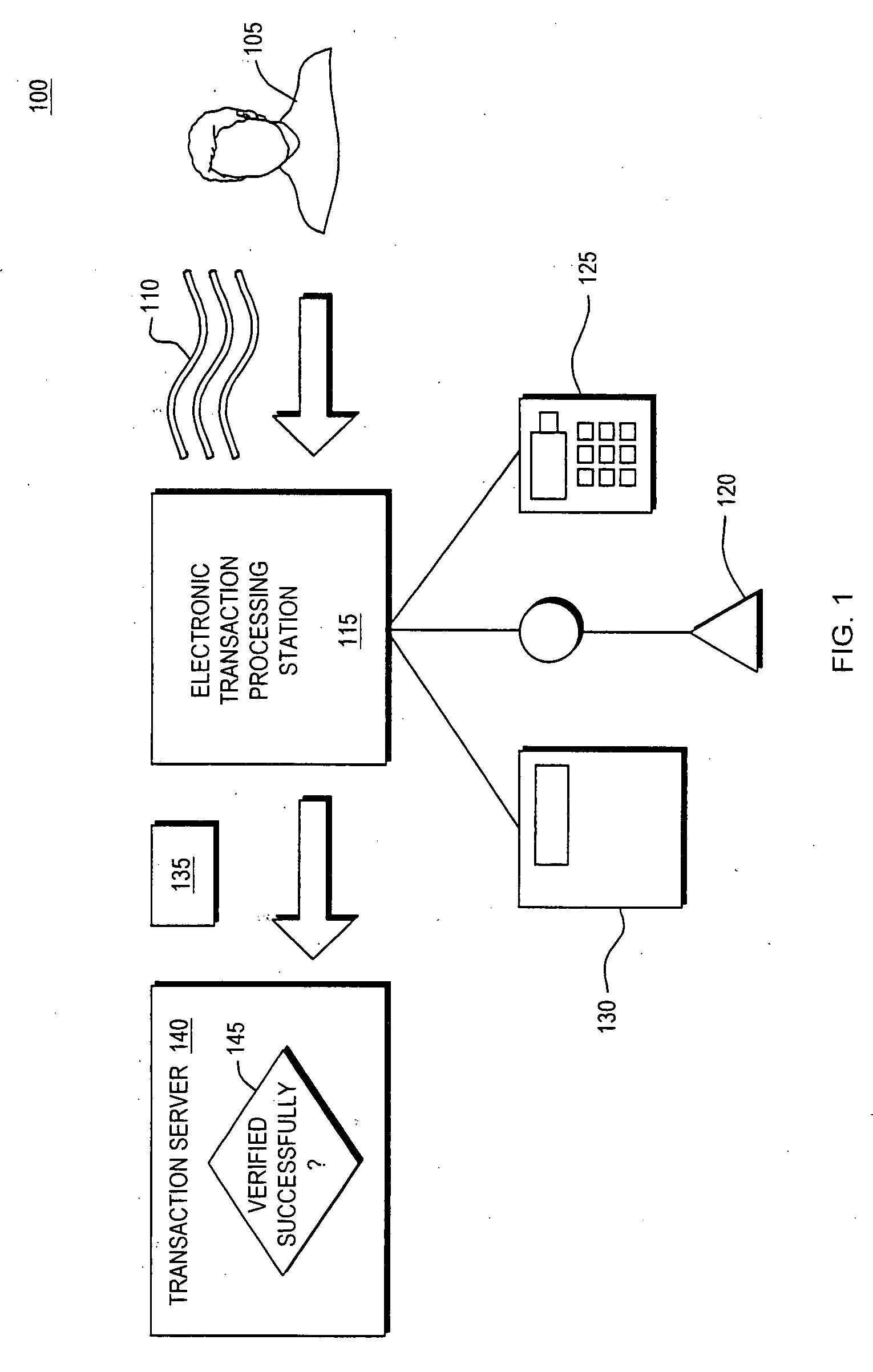
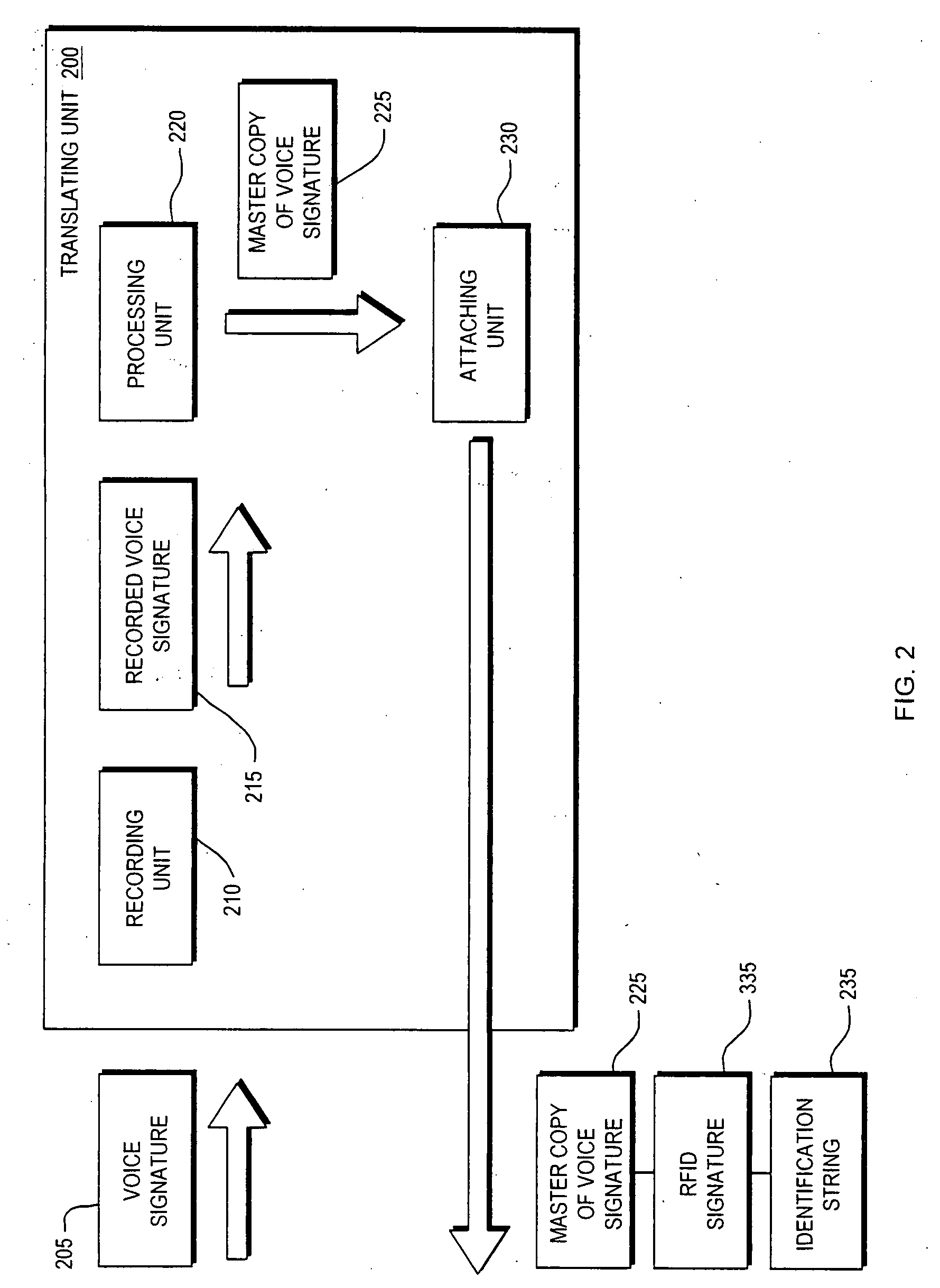
System and Method for Radio Frequency Identifier Voice Signature
ActiveUS20080169903A1Increase flexibilityImprove securityElectric signal transmission systemsDigital data processing detailsUser devicePersonal identification number
Conventional techniques for logging and using a user's signature are insecure and inflexible. A system and method are provided which: i) translate a user's first signature, such as a user's voice signature, into a user's second signature, such as a radio frequency identifier signature; and ii) deploy the user's second signature. By translating the user's first signature into the user's second signature and deploying the user's second signature, the provided technique assures the authenticity of the user. Furthermore, the provided system and method enable additional authentication factors, such as a user's personal identification number, to be used with the user's first and second signatures in multiple combinations and sequences to assure the authenticity of the user. As such, the invention provides a security layer offering added security and added flexibility previously unavailable, and which may be applied in a variety of contexts, such as a user device or a retail transaction.
Owner:CUFER ASSET LTD LLC
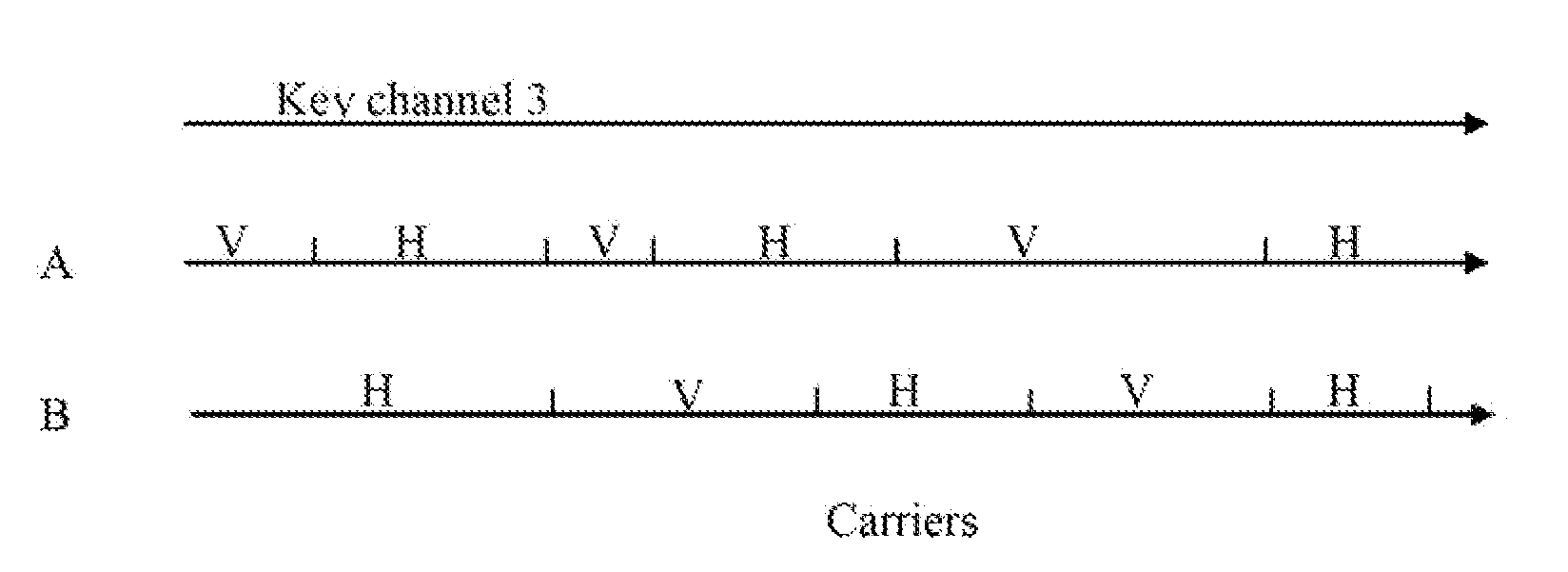
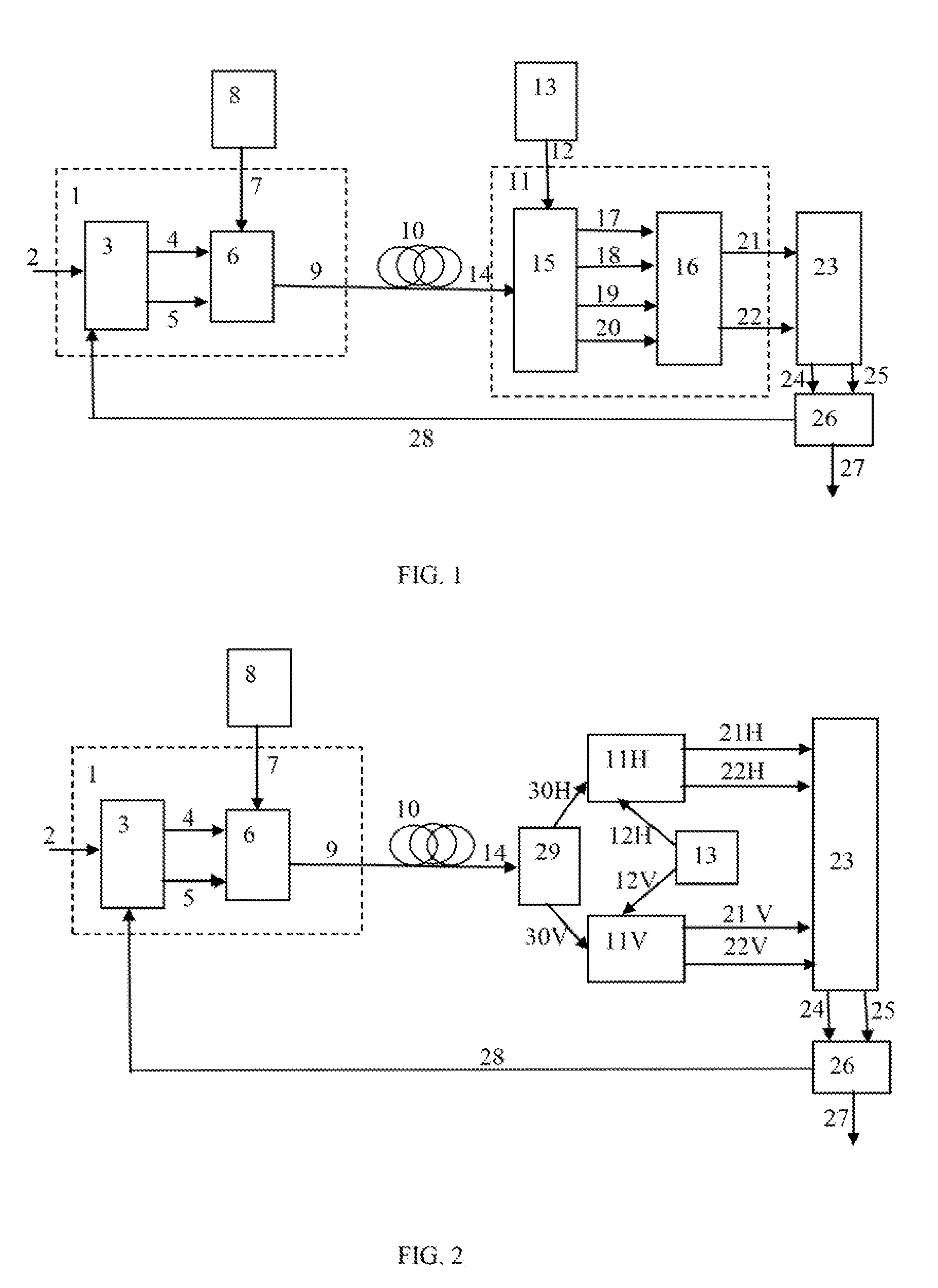
Secure orthogonal frequency multiplexed optical communications
InactiveUS20110170690A1Improve securityMultiple modulation transmitter/receiver arrangementsPolarisation multiplex systemsDigital signal processingOptical communication
The invention provides a system and method for secure communication that involve encoding and transmitting an optical orthogonal frequency division multiplexed (OFDM) signal. Each subcarrier of an optical carrier in OFDM transmission is modulated with data individually, and a variety of data format are used, such as QPSK, OOK, QAM, etc. The data format of each subcarrier may change in time according to a predetermined pattern. An optical receiver uncovers the data transmitted via an optical link. It is based on a coherent optical receiver and a digital signal processing (DSP) unit. A key to the data mapping and change is transmitted via the same optical link or by a separate channel. In one embodiment, the key is transmitted using quantum encryption technique. Besides subcarrier modulation encoding, the system may provide additional layers of security: optical carrier frequency hopping and polarization scrambling.
Owner:CELIGHT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com