Patents
Literature
266 results about "Computer methods" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method (computer programming) A method in object-oriented programming (OOP) is a procedure associated with a message and an object. An object consists of data and behavior.
Dynamic load balancing of a network of client and server computer
InactiveUS20030126200A1Program synchronisationMultiple digital computer combinationsDynamic load balancingClient-side
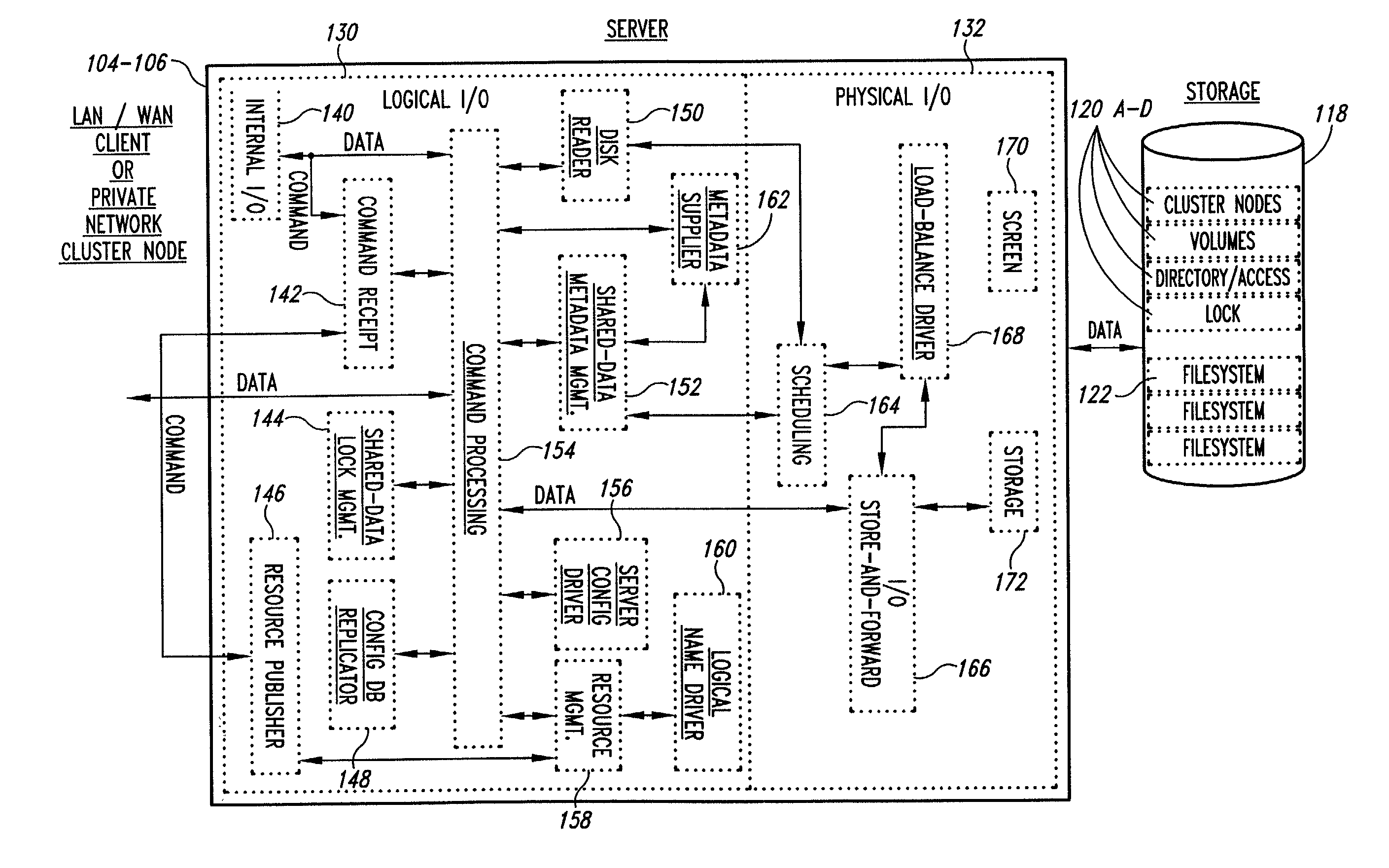
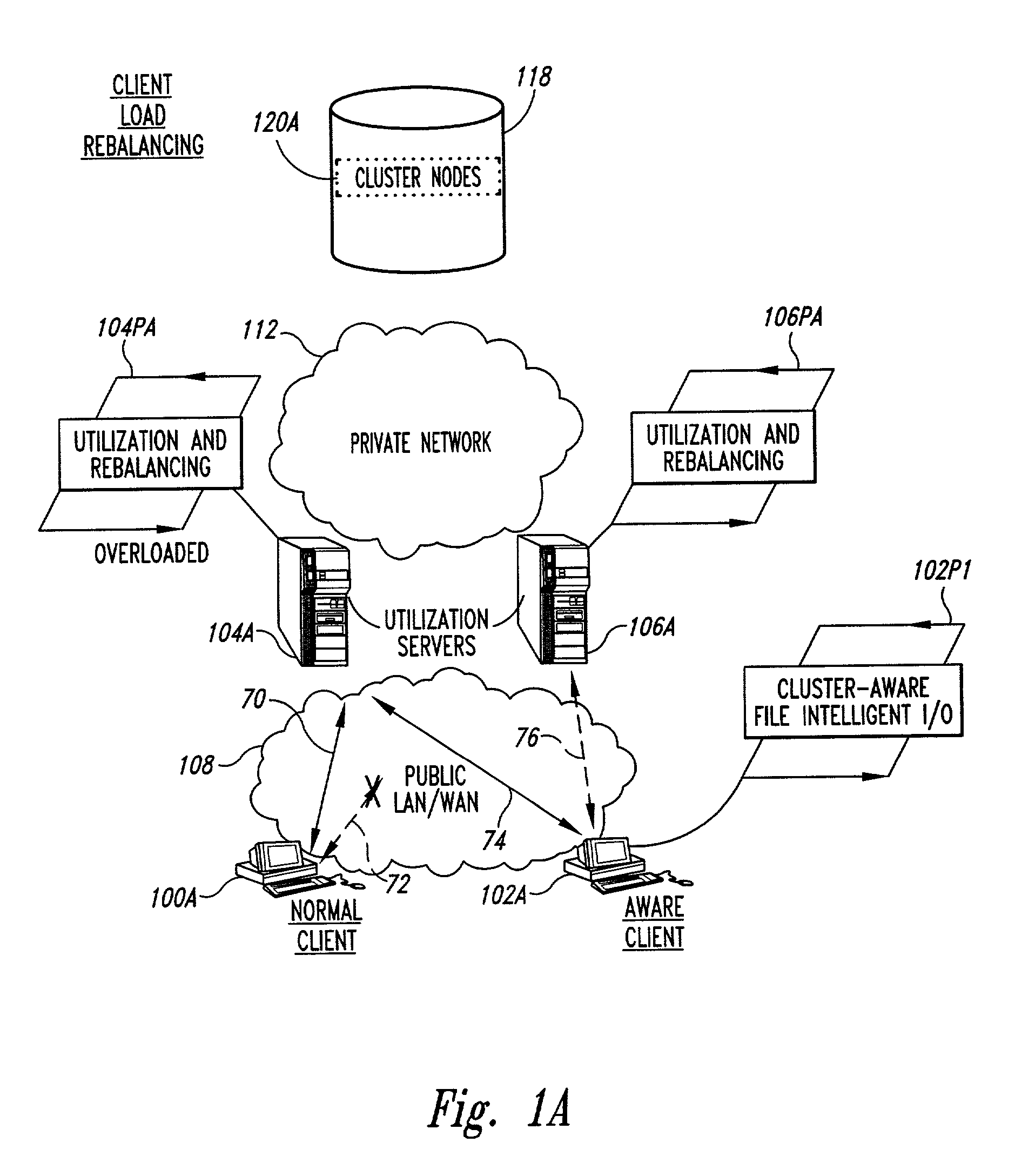
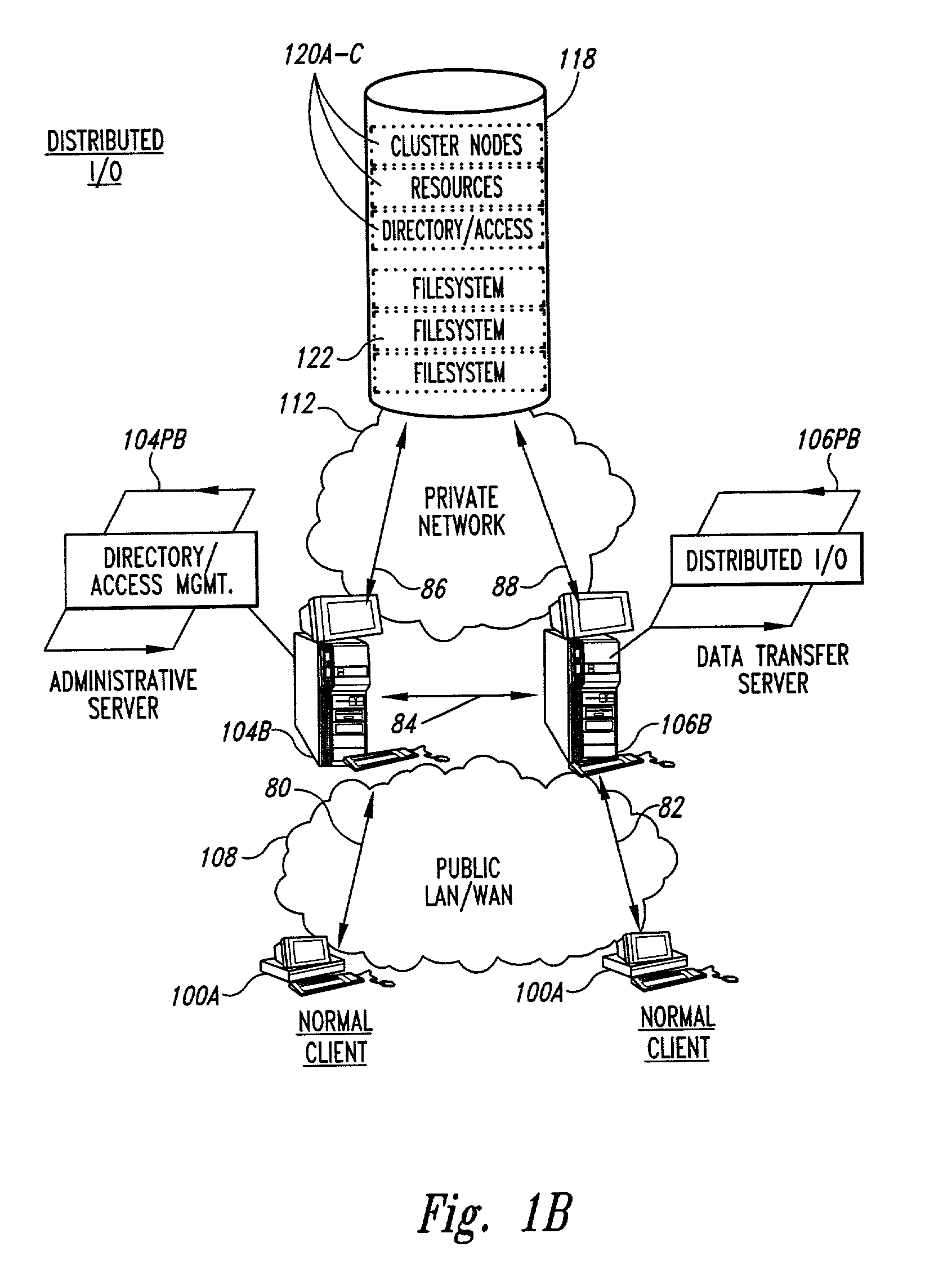
Methods for load rebalancing by clients in a network are disclosed. Client load rebalancing allows the clients to optimize throughput between themselves and the resources accessed by the nodes. A network which implements this embodiment of the invention can dynamically rebalance itself to optimize throughput by migrating client I / O requests from overutilized pathways to underutilized pathways. Client load rebalancing refers to the ability of a client enabled with processes in accordance with the current invention to remap a path through a plurality of nodes to a resource. The remapping may take place in response to a redirection command emanating from an overloaded node, e.g. server. These embodiments disclosed allow more efficient, robust communication between a plurality of clients and a plurality of resources via a plurality of nodes. In an embodiment of the invention a method for load balancing on a network is disclosed. The network includes at least one client node coupled to a plurality of server nodes, and at least one resource coupled to at least a first and a second server node of the plurality of server nodes. The method comprises the acts of: receiving at a first server node among the plurality of server nodes a request for the at least one resource; determining a utilization condition of the first server node; and re-directing subsequent requests for the at least one resource to a second server node among the plurality of server nodes in response to the determining act. In another embodiment of the invention the method comprises the acts of: sending an I / O request from the at least one client to the first server node for the at least one resource; determining an I / O failure of the first server node; and re-directing subsequent requests from the at least one client for the at least one resource to an other among the plurality of server nodes in response to the determining act.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
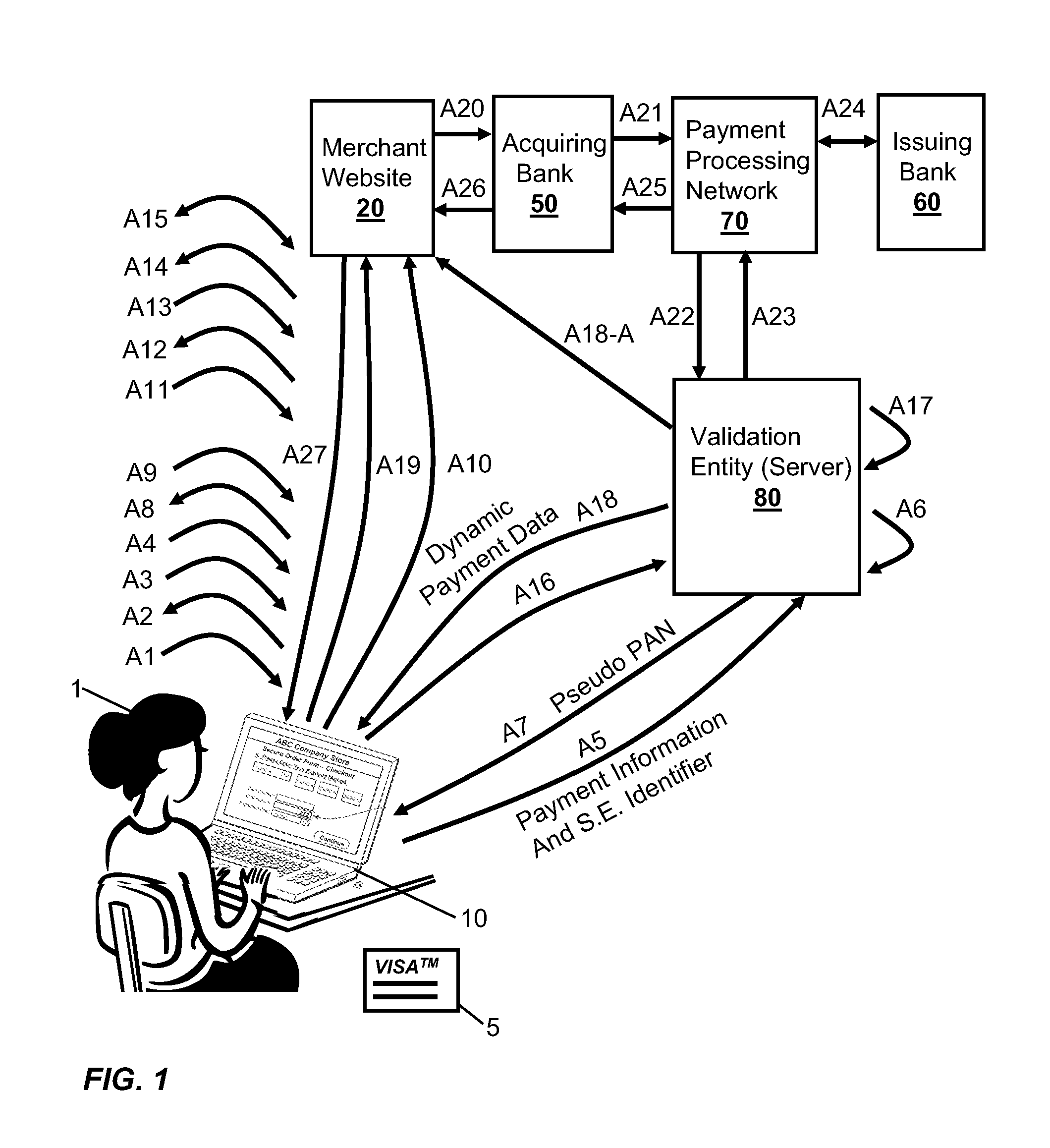
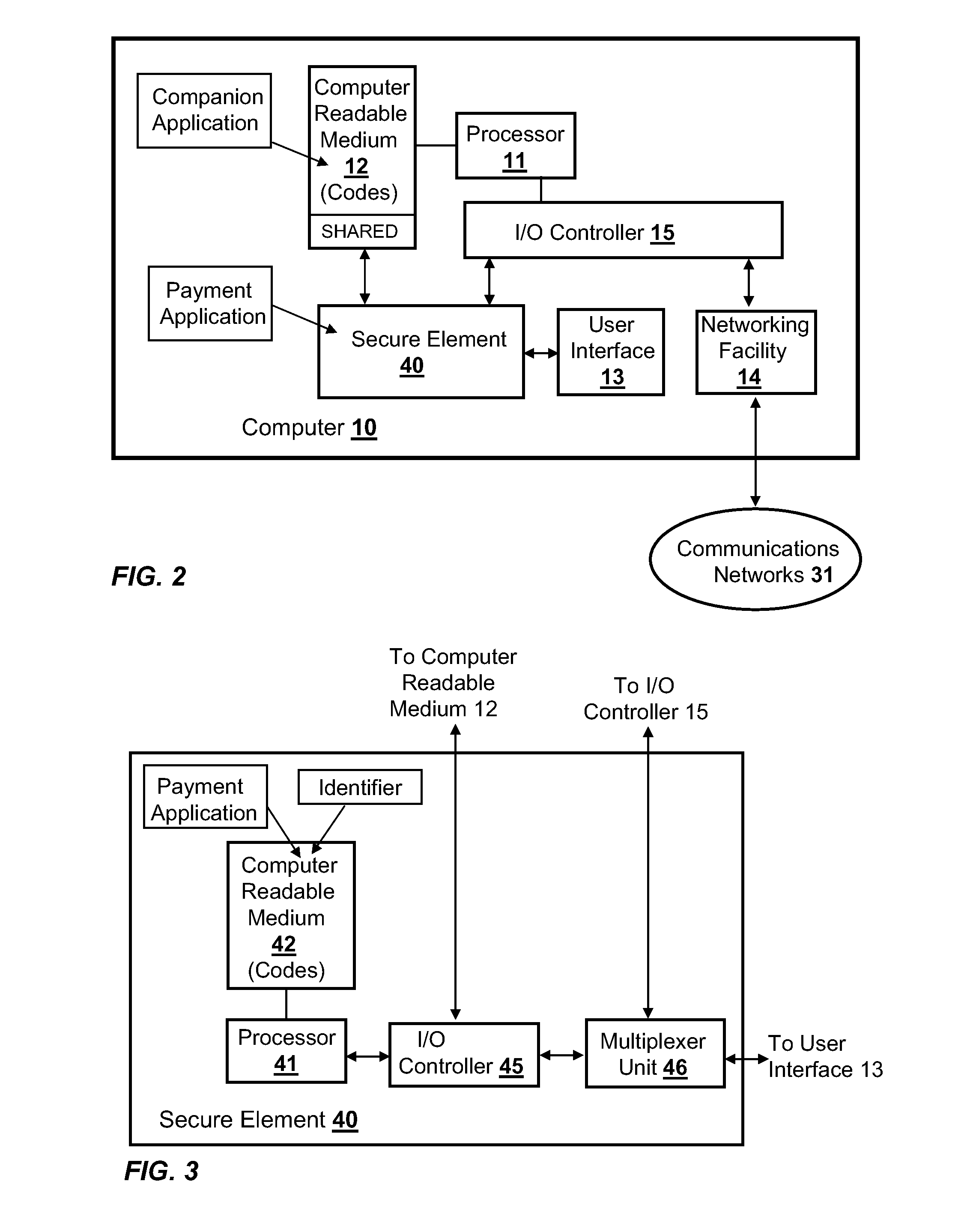
Integration of Payment Capability into Secure Elements of Computers
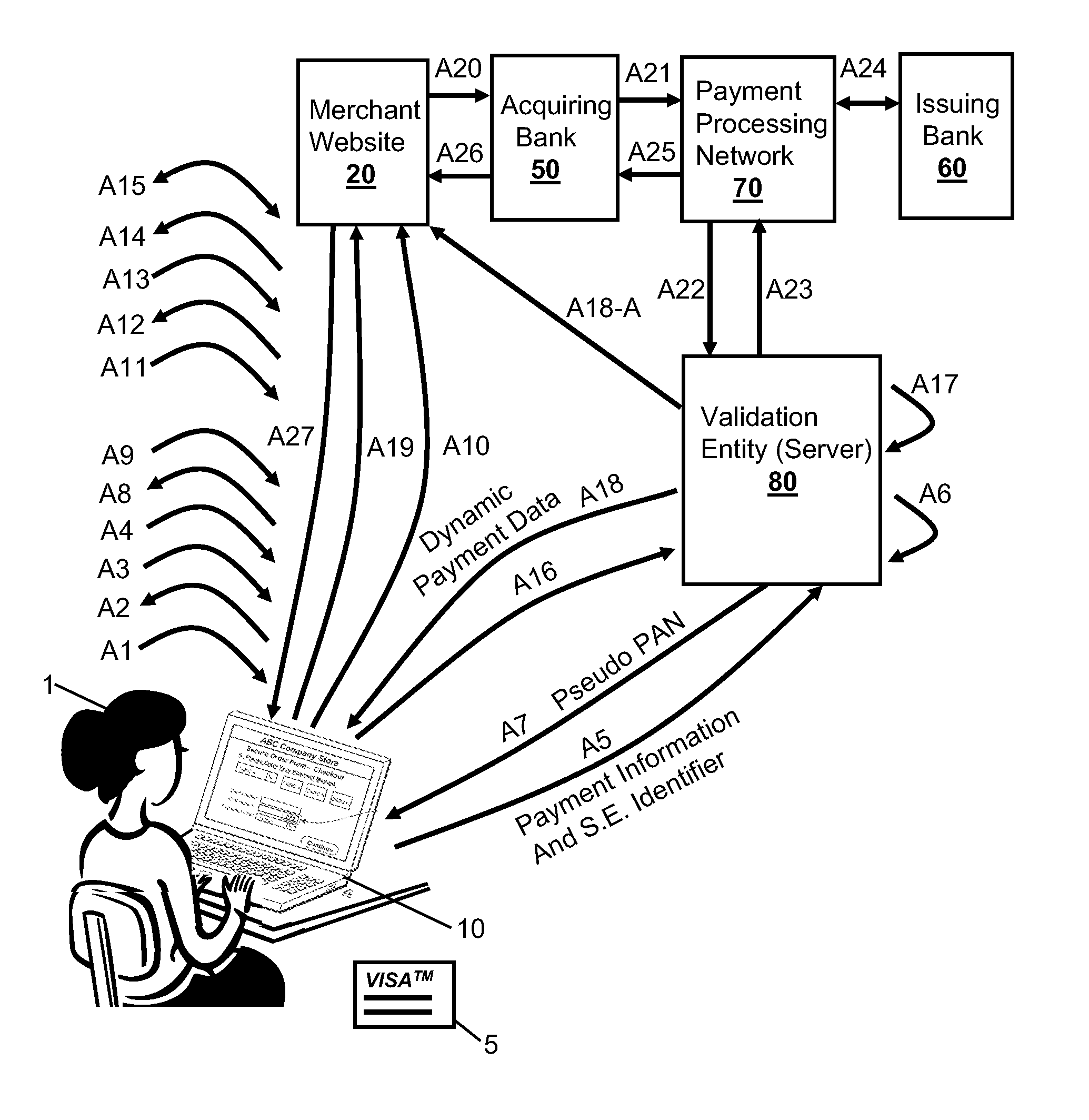
Methods, secure elements, validation entities, and computer program products for effecting secure communication of payment information to merchants for Internet-based purchases. Payment information for a user's real payment information is installed in a secure element of a computer, the payment information may comprise a pseudo PAN number for the portable consumer device provided by a validation entity. The secure element is shielded from the computer's operating system to thwart hacker attacks. The user accesses the secure element to make a purchase. In response, the secure element contacts the validation entity with the pseudo account number, and in response obtains dynamic payment information that the secure element can used to effect the payment. The dynamic payment information comprises an account number that is different from the pseudo PAN, and which has at least one difference which respect to the user's real payment information.
Owner:VISA INT SERVICE ASSOC
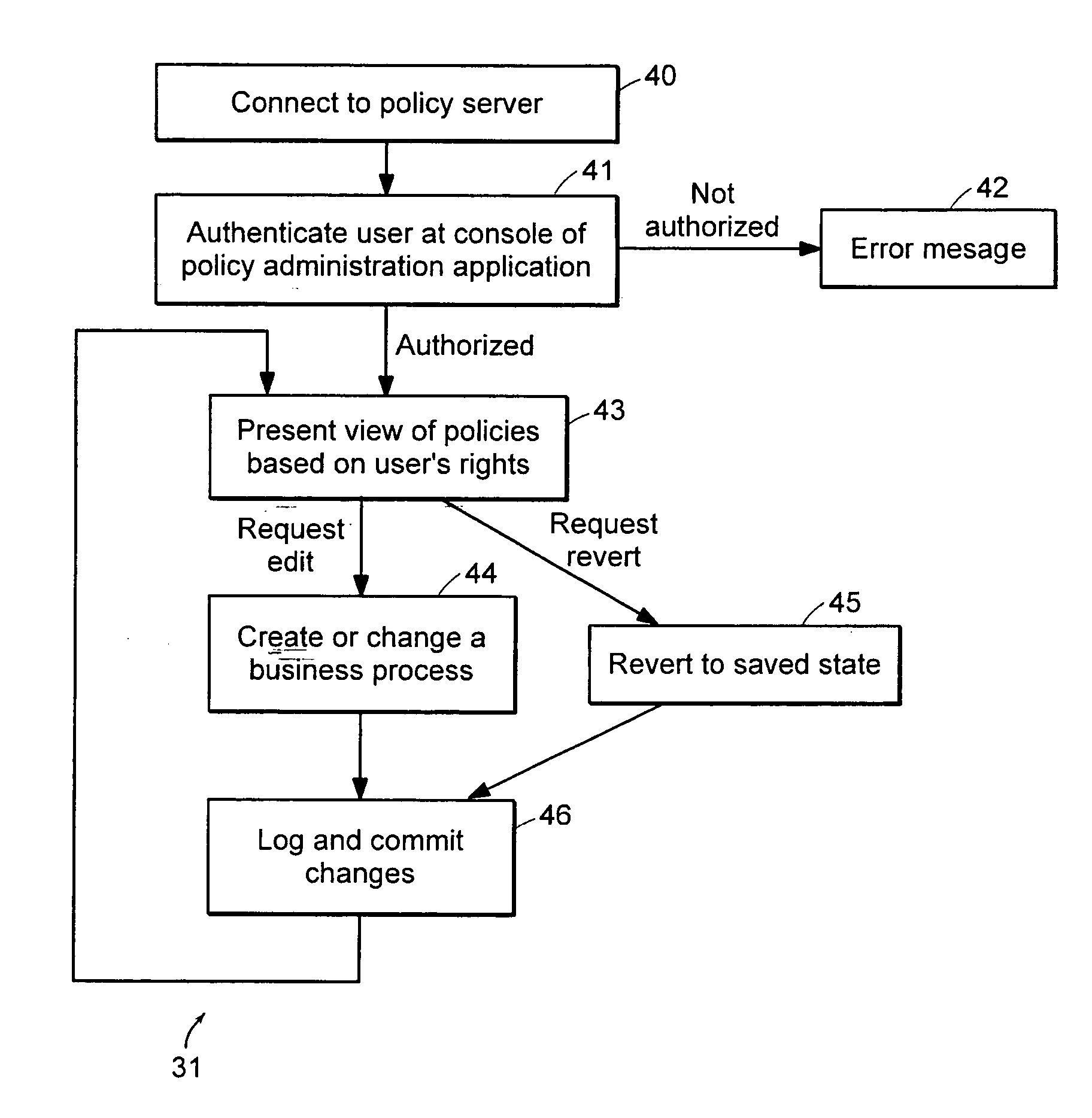
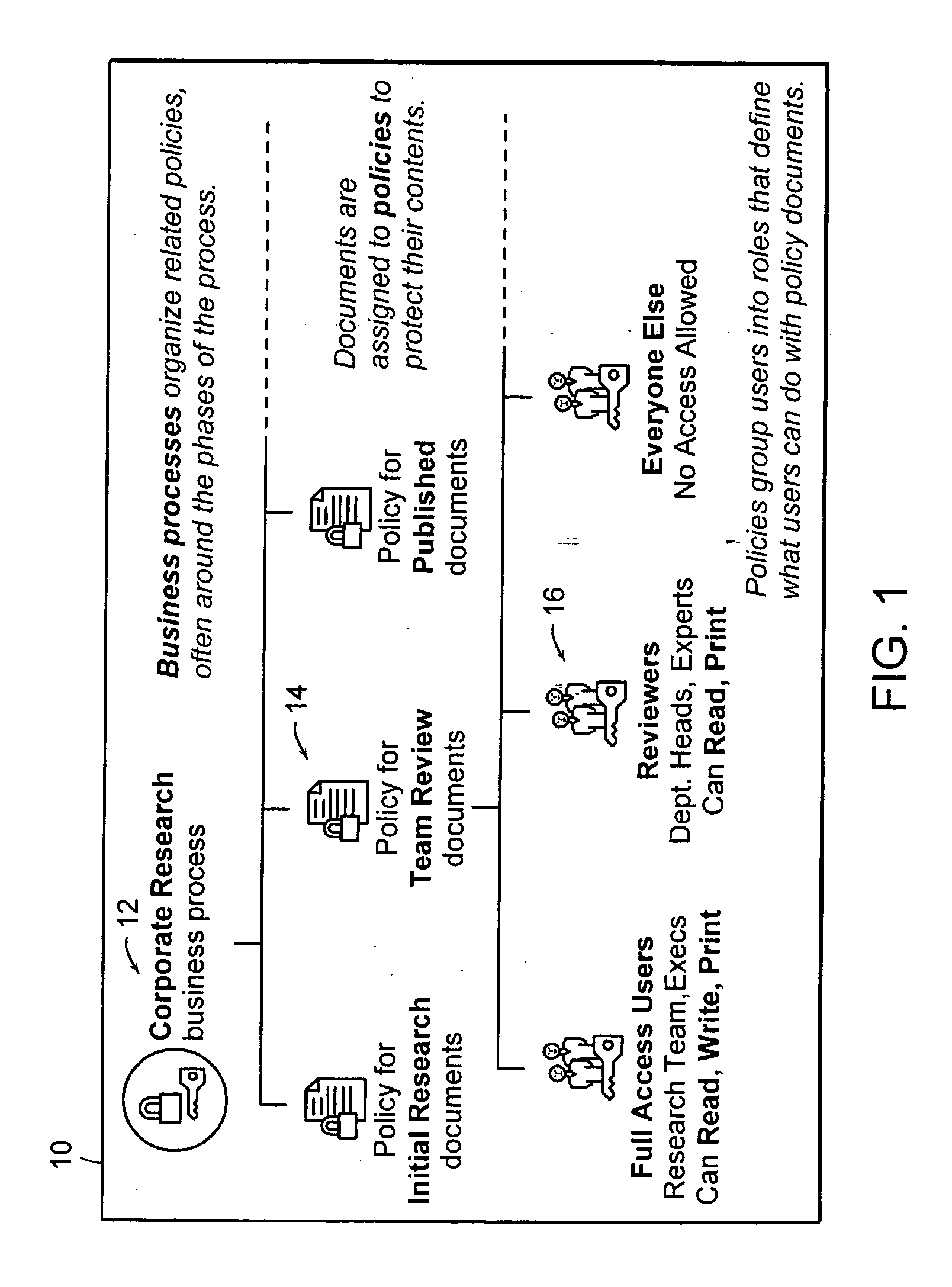
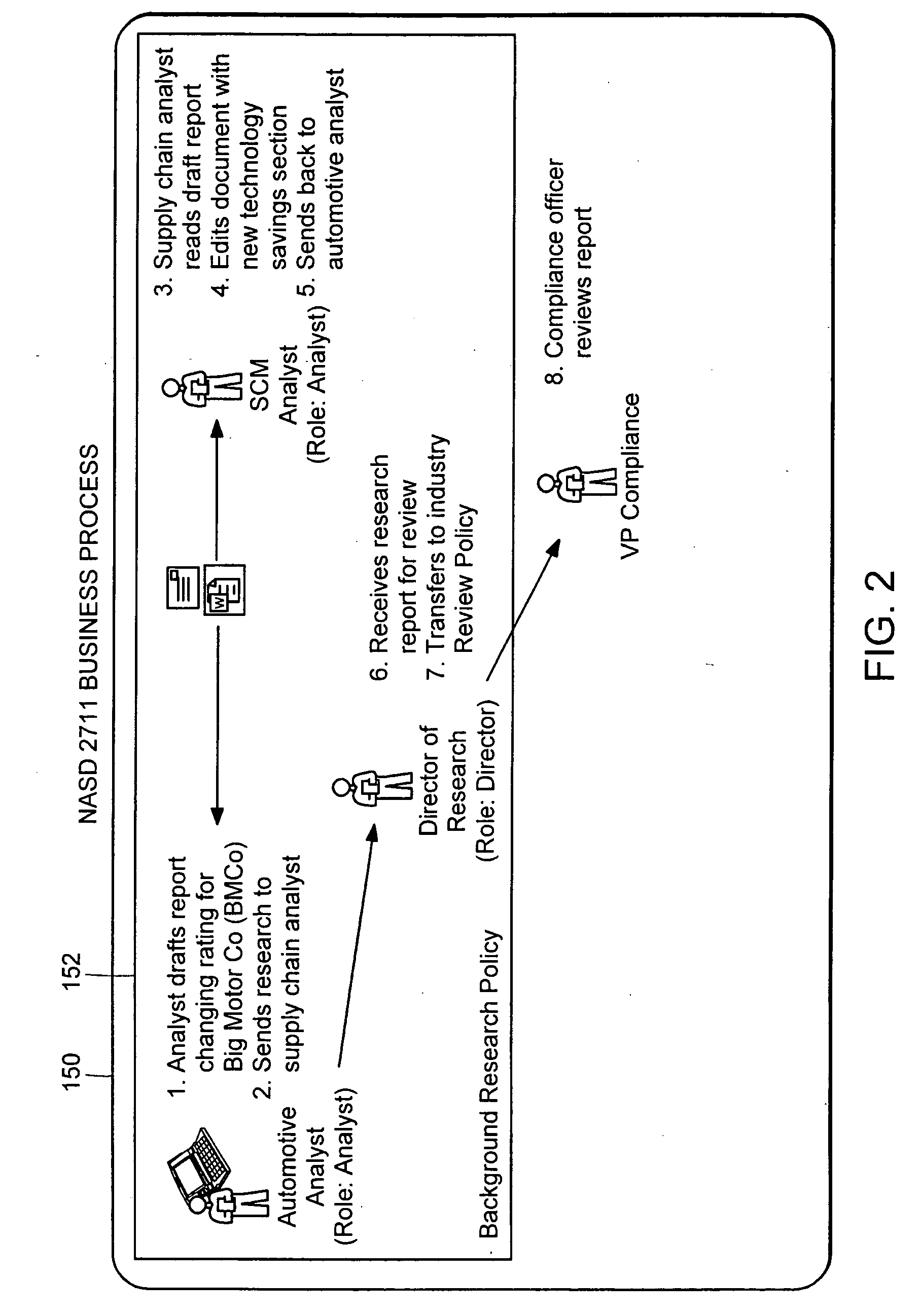
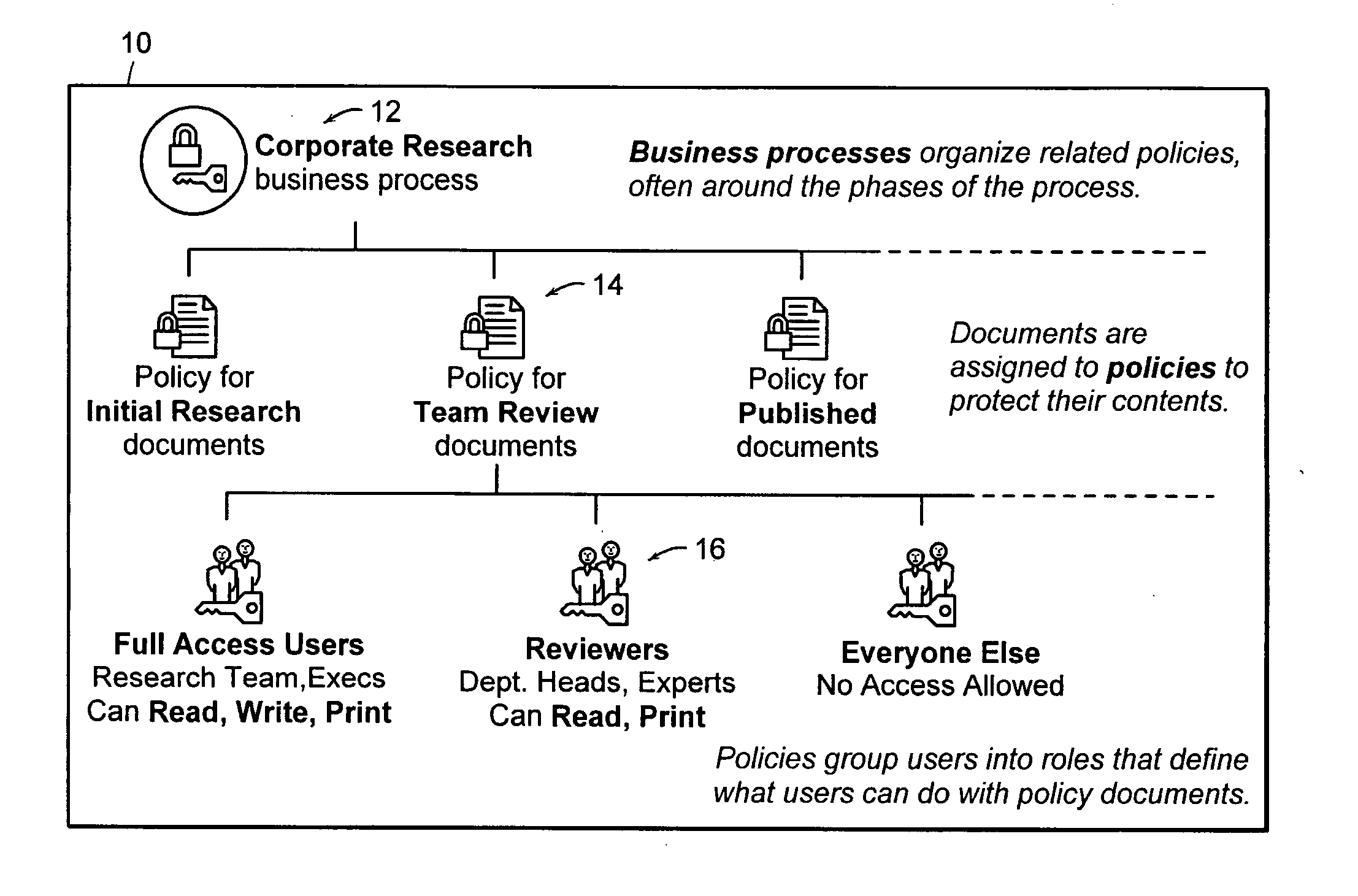
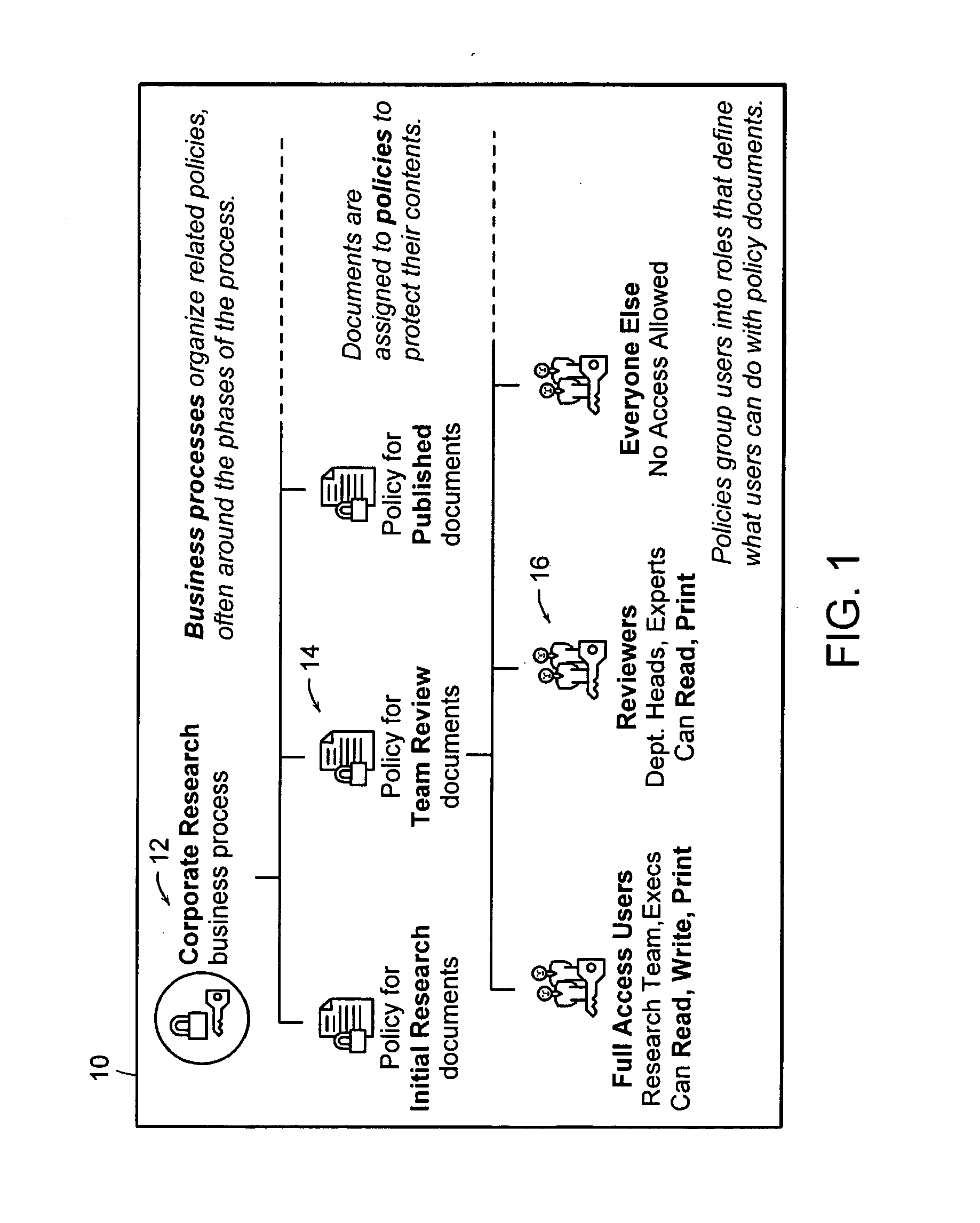
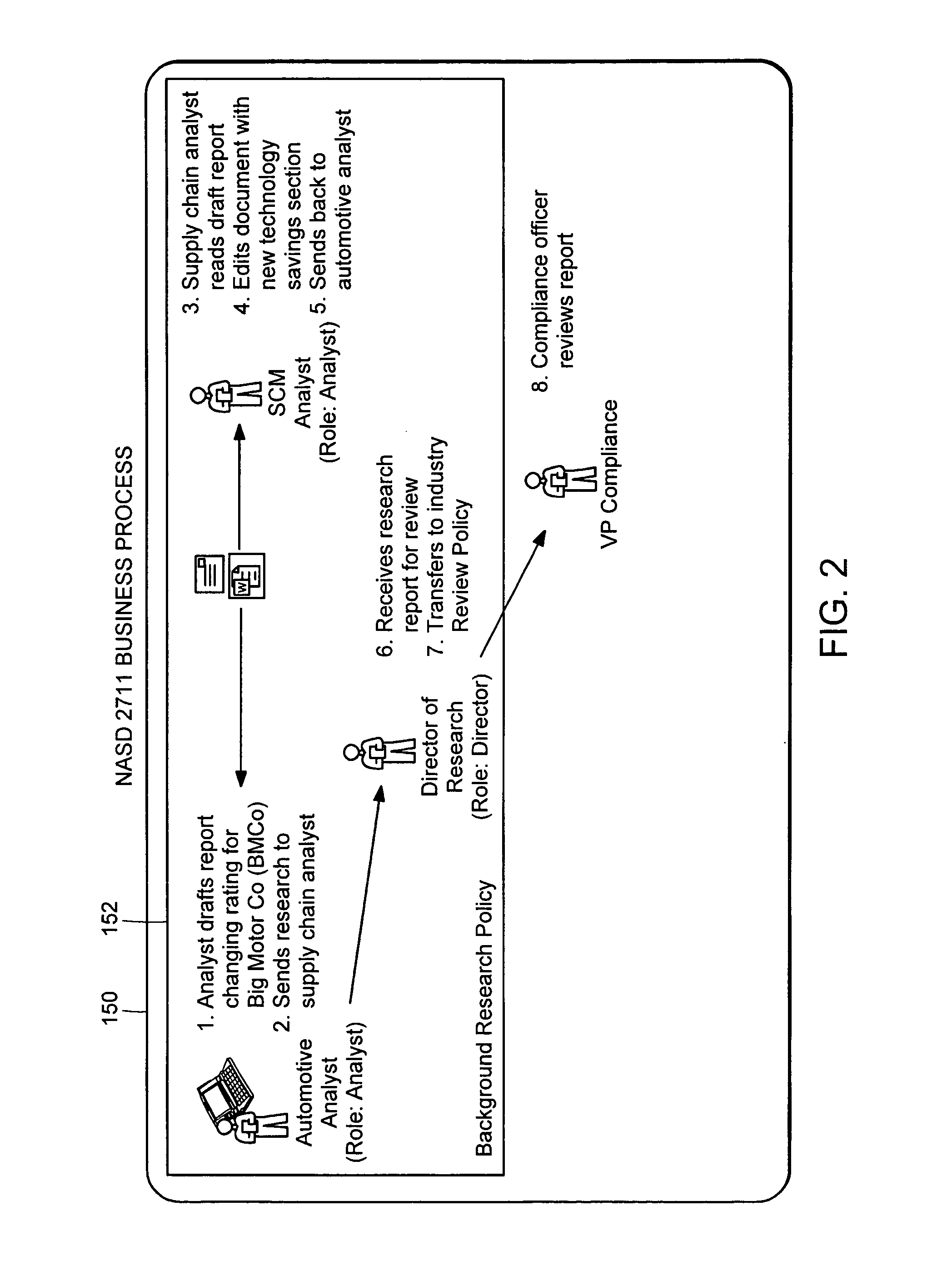
Computer method and apparatus for managing data objects in a distributed context
ActiveUS20050028006A1Obtaining visibility into a business processLimited historyKey distribution for secure communicationDigital data processing detailsDerivative workComputer methods
In a network of intermittently-connected computers, a method and apparatus for maintaining and managing control over data objects authored, accessed, and altered by users in dynamic, distributed, and collaborative contexts. The invention method and apparatus attach to each data object an identification of a respective control policy. Each control policy comprises at least an indication of a subset of the users who may access the data object, an indication of the privileges granted to each subset of users able to access the data object, and an indication of a subset of users who may define or edit the control policy. The invention method and apparatus separate the management of the control policies of data objects from the creation and use of the data objects. The invention method and apparatus automate common policy changes, distribution of policy changes to the enforcement agents, and propagation of control policies to derivative works.
Owner:LIQUID MACHINES
Computer method and apparatus for securely managing data objects in a distributed context
InactiveUS20050008163A1Obtaining visibility into a business processLimited historyKey distribution for secure communicationUnauthorized memory use protectionDerivative workComputer methods
In a network of intermittently-connected computers, a method and apparatus for maintaining and managing control over data objects authored, accessed, and altered by users in dynamic, distributed, and collaborative contexts. The invention method and apparatus attach to each data object an identification of a respective control policy. Each control policy comprises at least an indication of a subset of the users who may access the data object, an indication of the privileges granted to each subset of users able to access the data object, and an indication of a subset of users who may define or edit the control policy. The invention method and apparatus separate the management of the control policies of data objects from the creation and use of the data objects. The invention method and apparatus automate common policy changes, distribution of policy changes to the enforcement agents, and propagation of control policies to derivative works.
Owner:LIQUID MACHINES
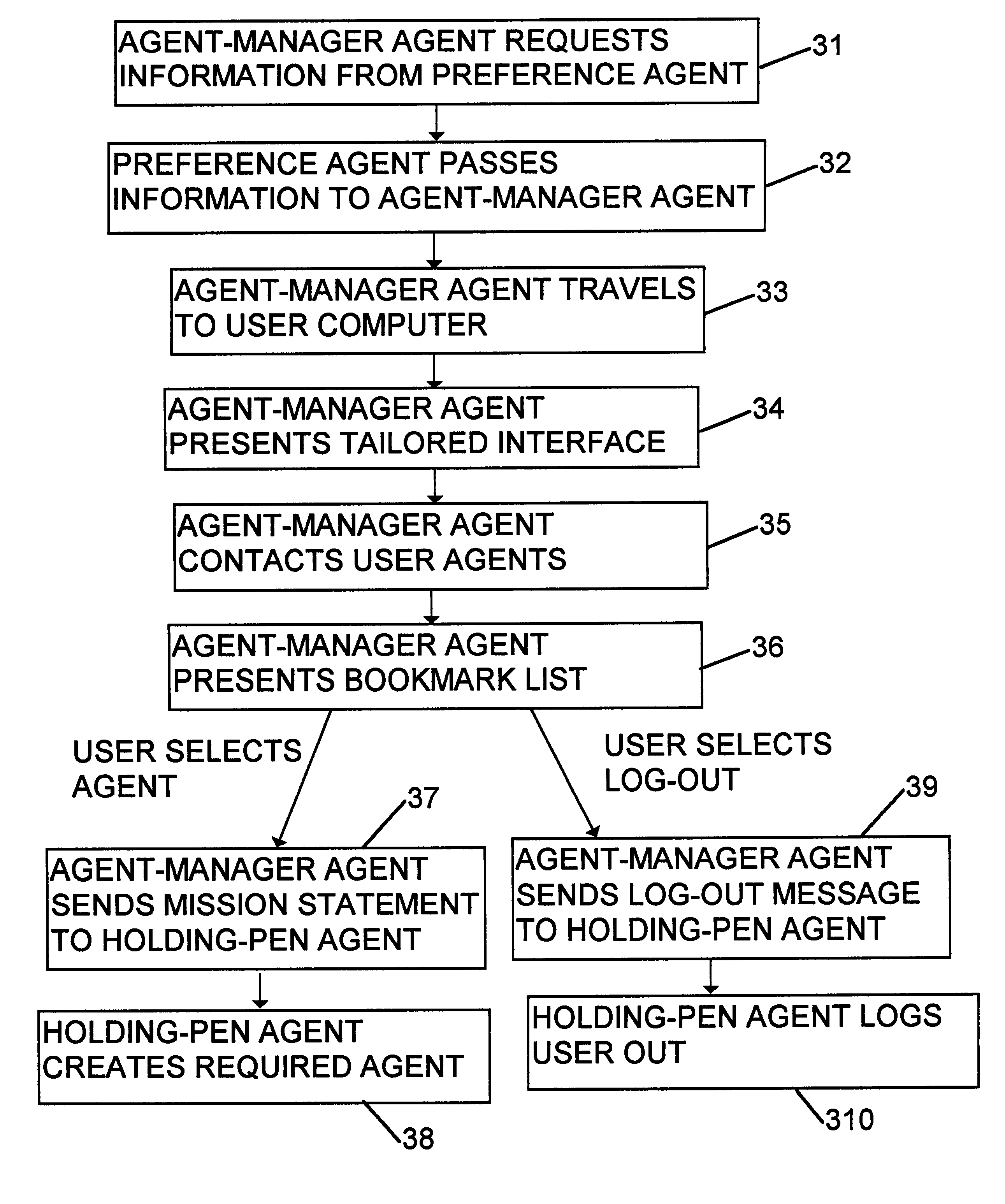
Computer method for delivery of financial services
A computer system is provided for delivery of financial services, such as banking, general insurance, life assurance, pensions and investments, loans and mortgages, and financial planning and advisory services. The system comprises a number of user computers connected to a plurality of server computers by way of a network, such as the Internet. The system creates at least one mobile agent which obtains details of a user's requirements, obtains financial information from the server computers on behalf of the user in the light of the user's requirements, and then transports itself to the user's computer to deliver the financial information to the user.
Owner:INT COMP LTD
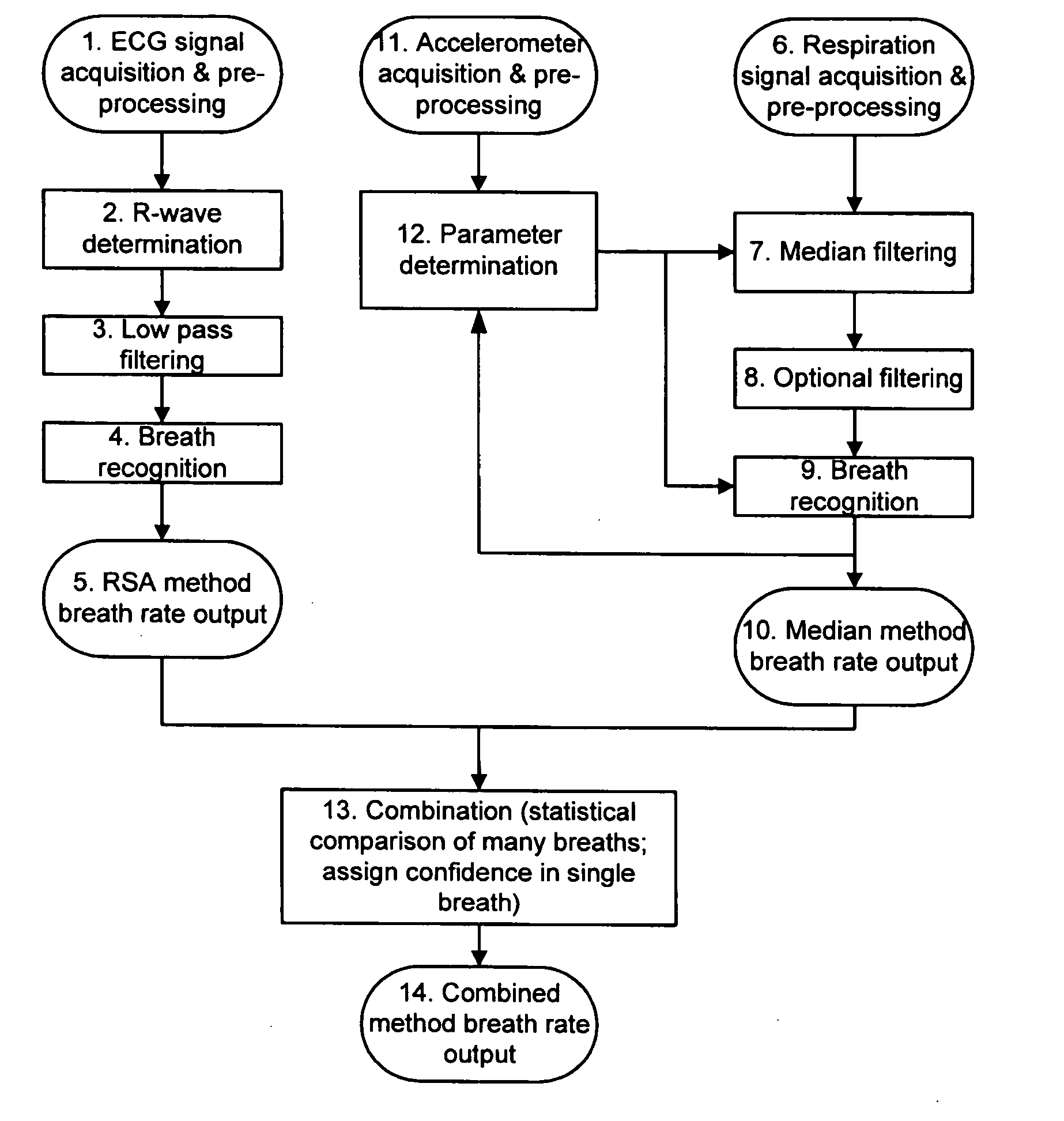
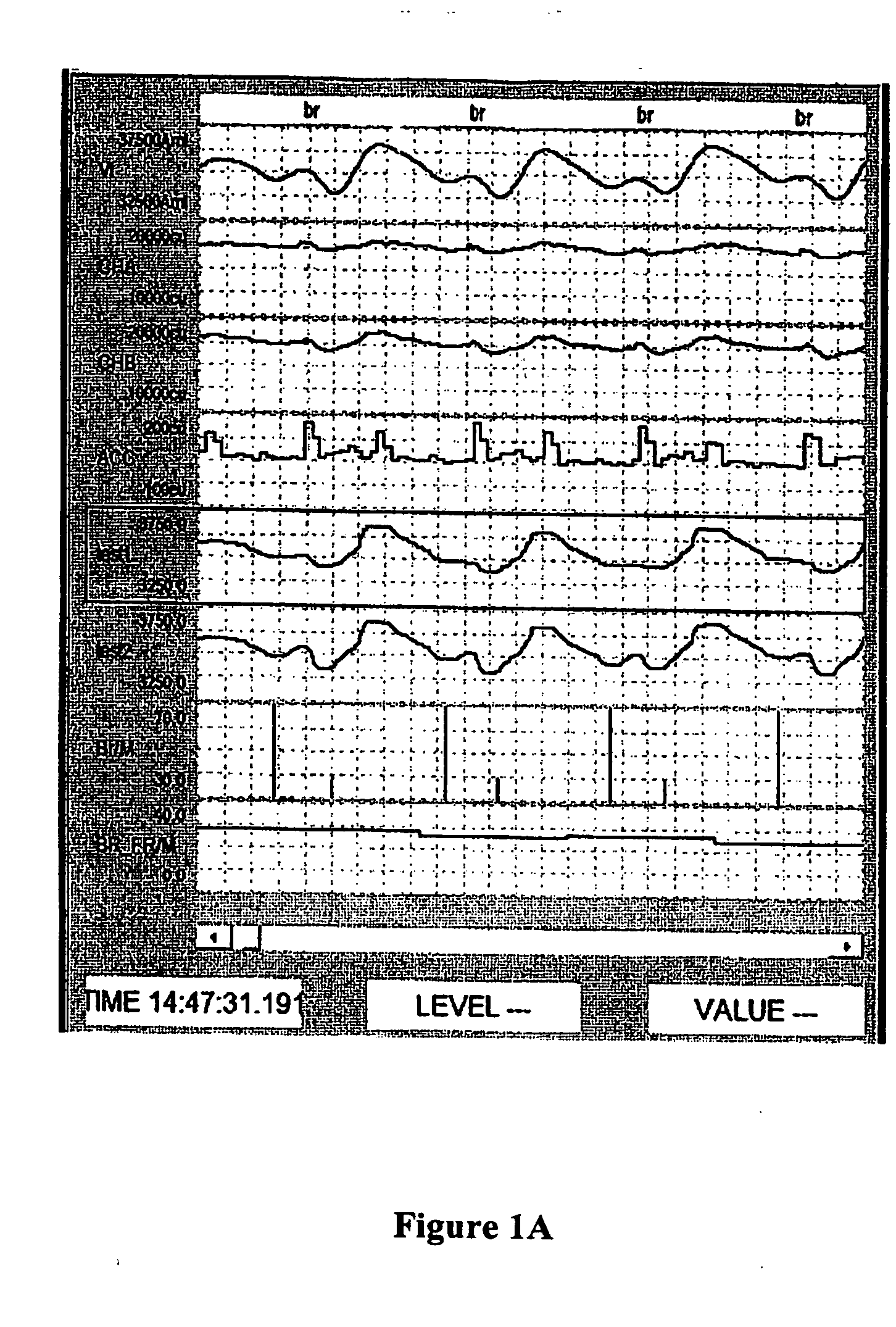
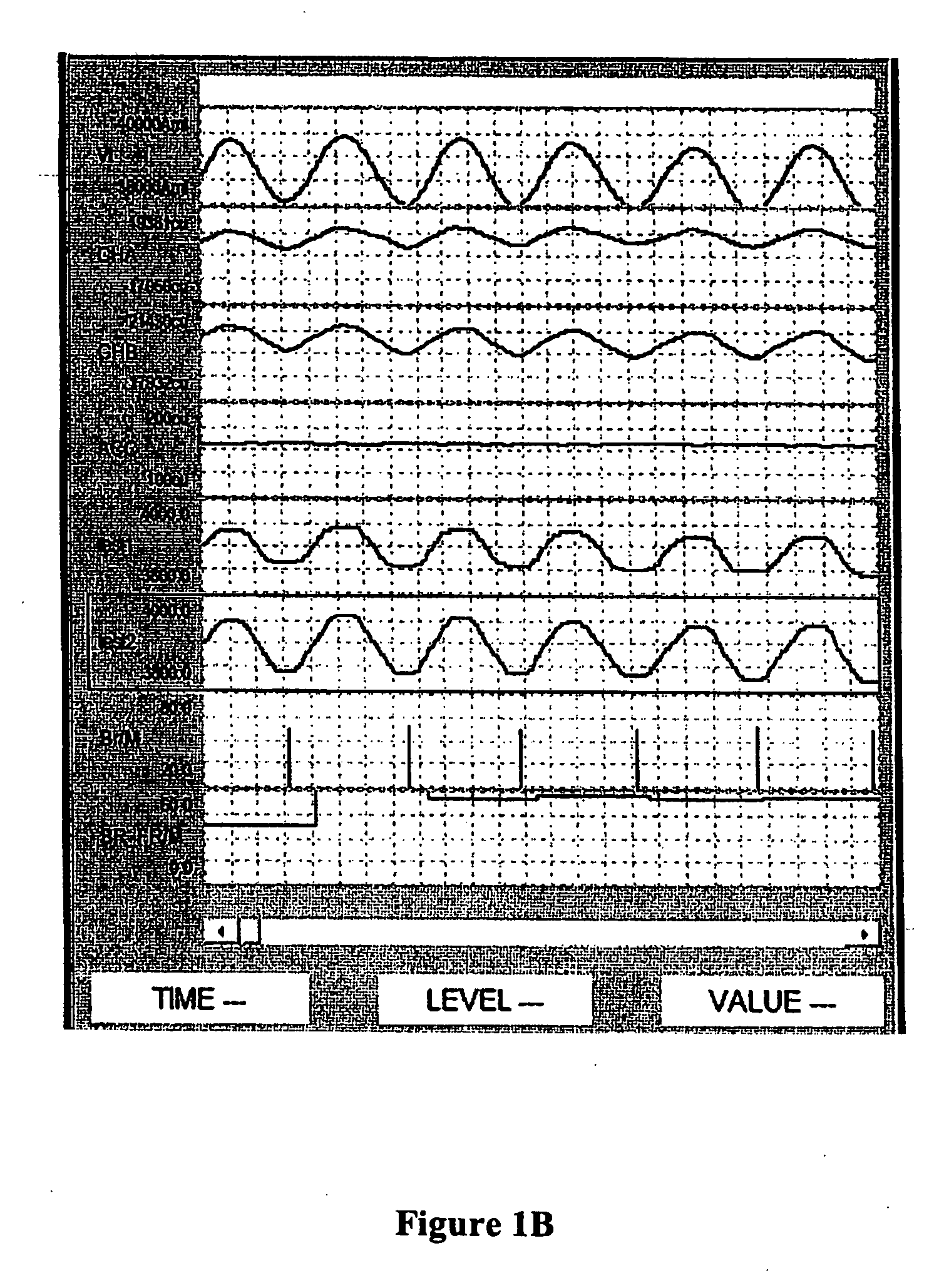
Methods and systems for real time breath rate determination with limited processor resources
InactiveUS20060178591A1Less durationElectrocardiographyInertial sensorsTidal volumeMonitoring system
A method for recognizing occurrences of breaths in respiratory signals. The method includes receiving digitized respiratory signals that includes tidal volume signals, filtering the received respiratory signals to limit artifacts having a duration less than a selected duration, and recognizing breaths in the filtered respiratory signals. A breath is recognized when amplitude deviations in filtered tidal volume signals exceed a selected fraction of an average of previously determined breaths. This invention also include methods for recognizing breathes from electrocardiogram R-waves; computer methods having code for performing the methods of this invention; monitoring systems that monitor a subject and include local or remote computers or other devices that perform the methods of this invention.
Owner:VIVOMETRICS INC
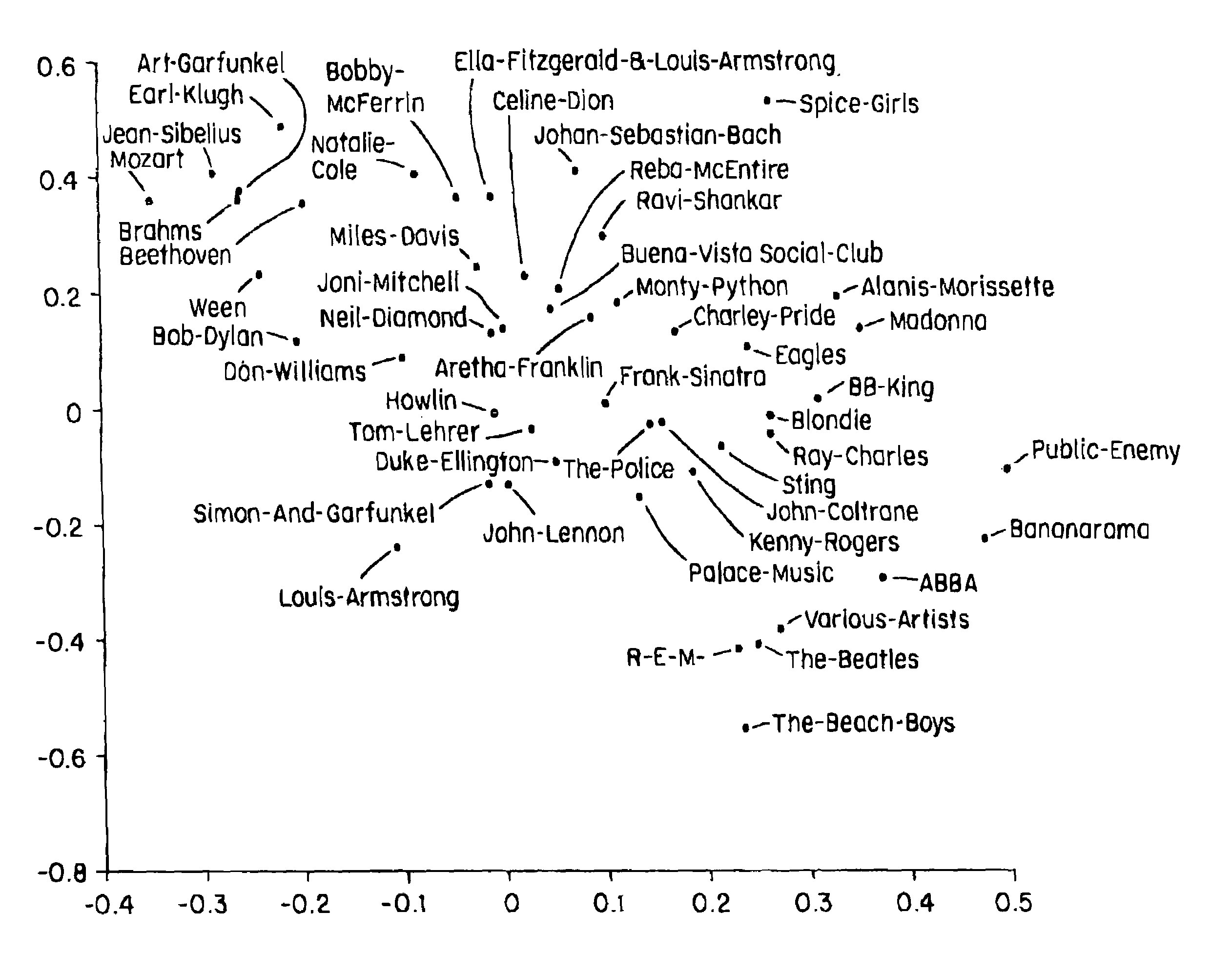
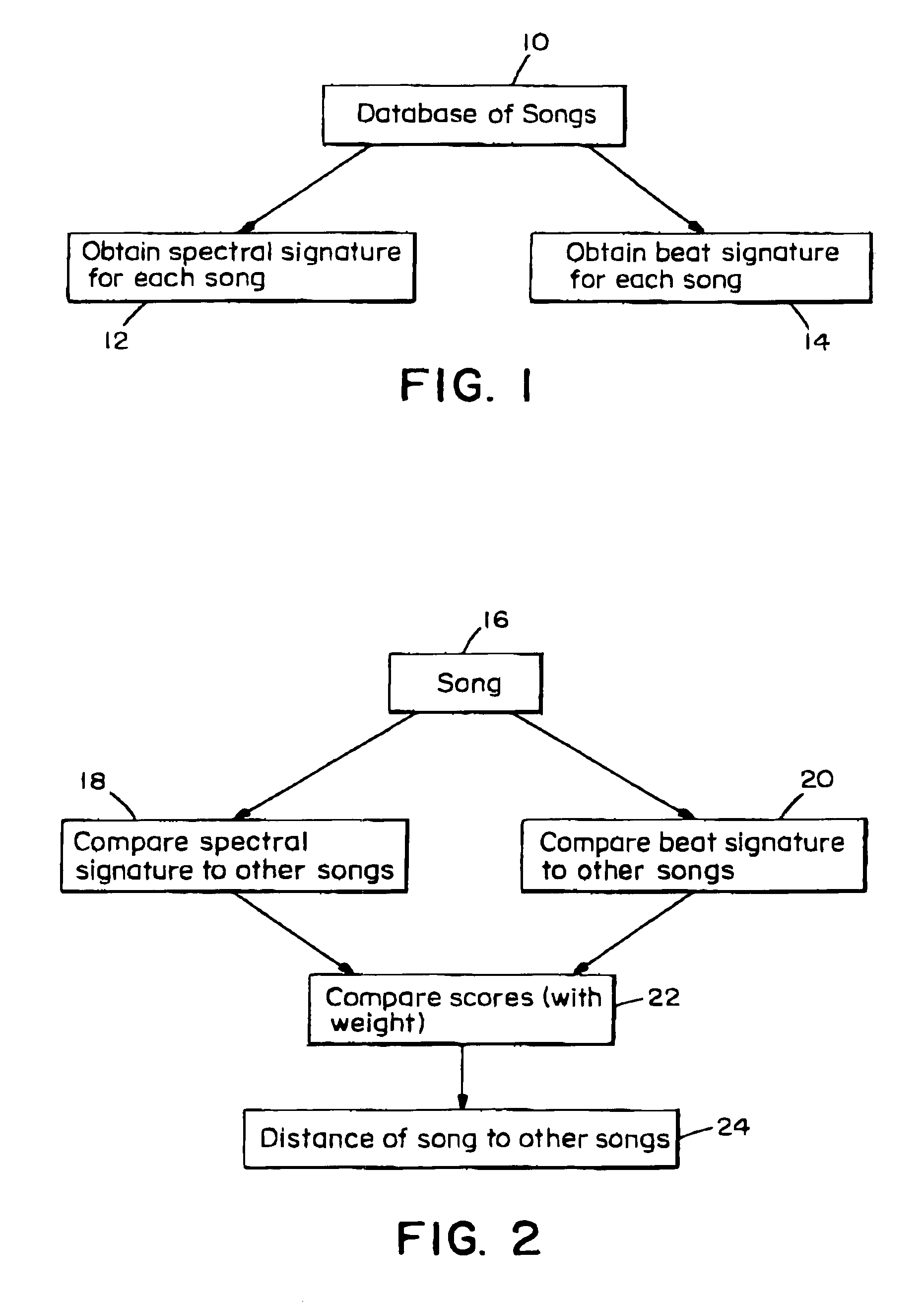
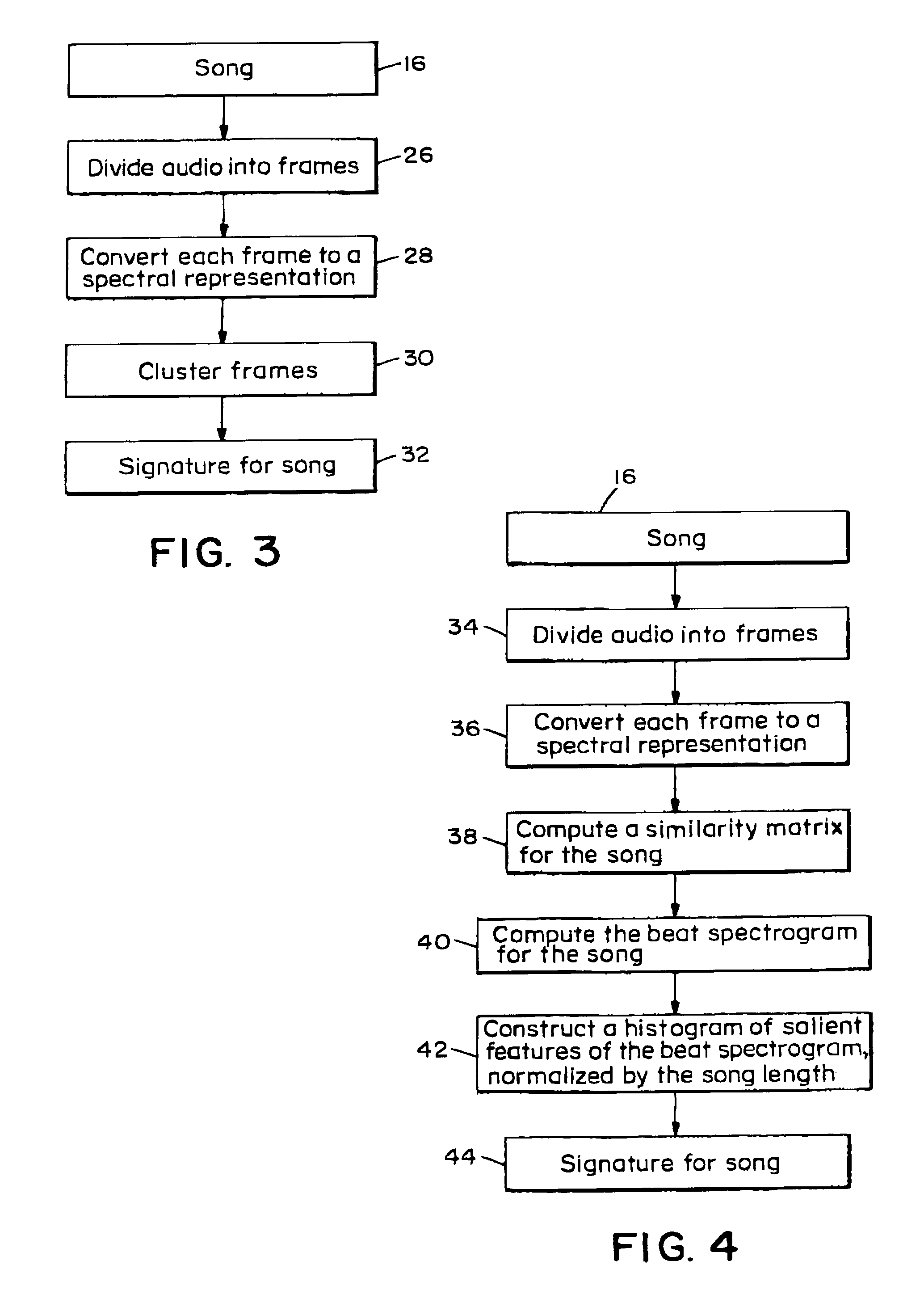
Music similarity function based on signal analysis
InactiveUS7031980B2Television system detailsData processing applicationsComputer methodsDistance measurement
The present invention computer method and apparatus determines music similarity by generating a K-means (instead of Gaussian) cluster signature and a beat signature for each piece of music. The beat of the music is included in the subsequent distance measurement.
Owner:HEWLETT PACKARD DEV CO LP
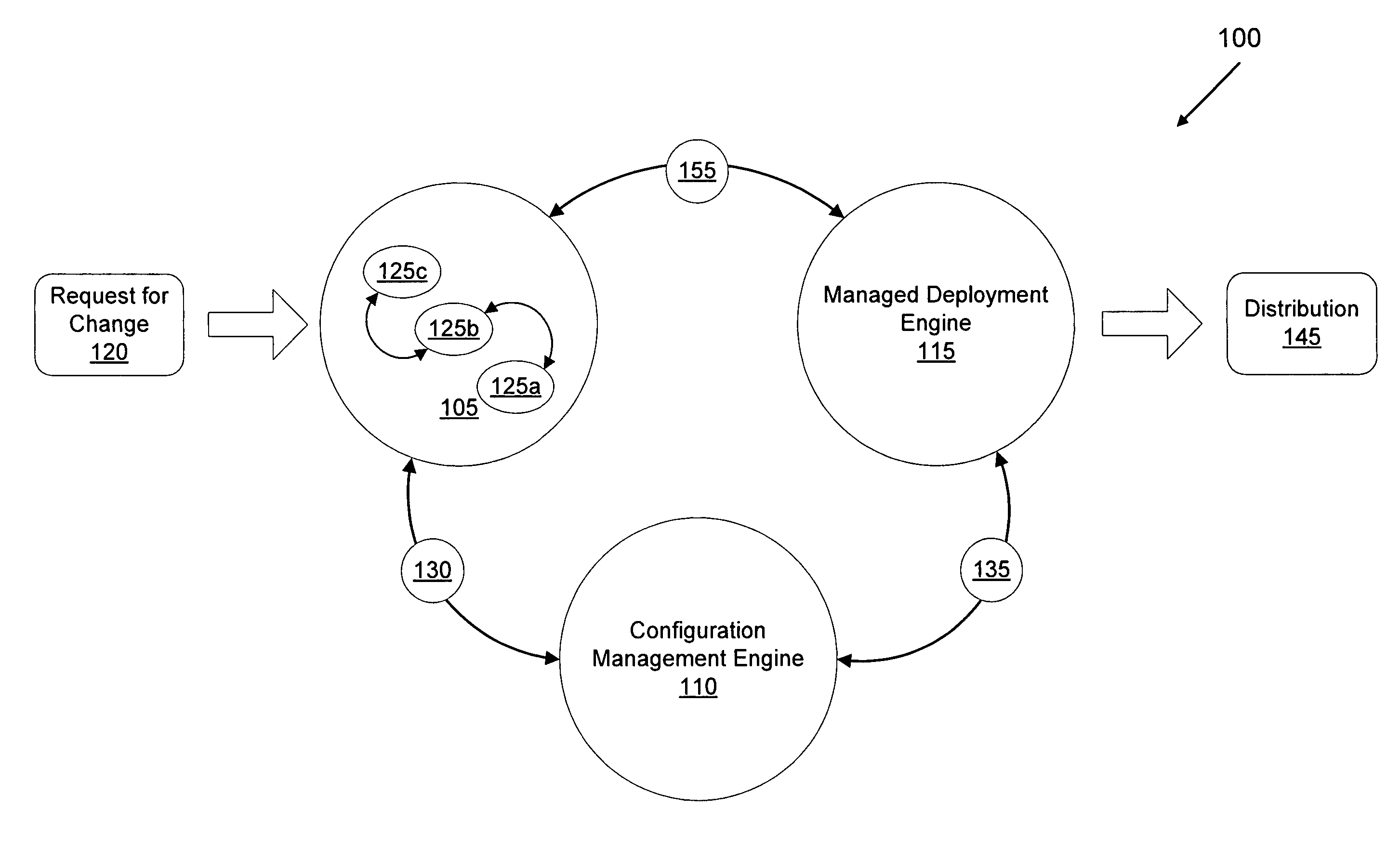
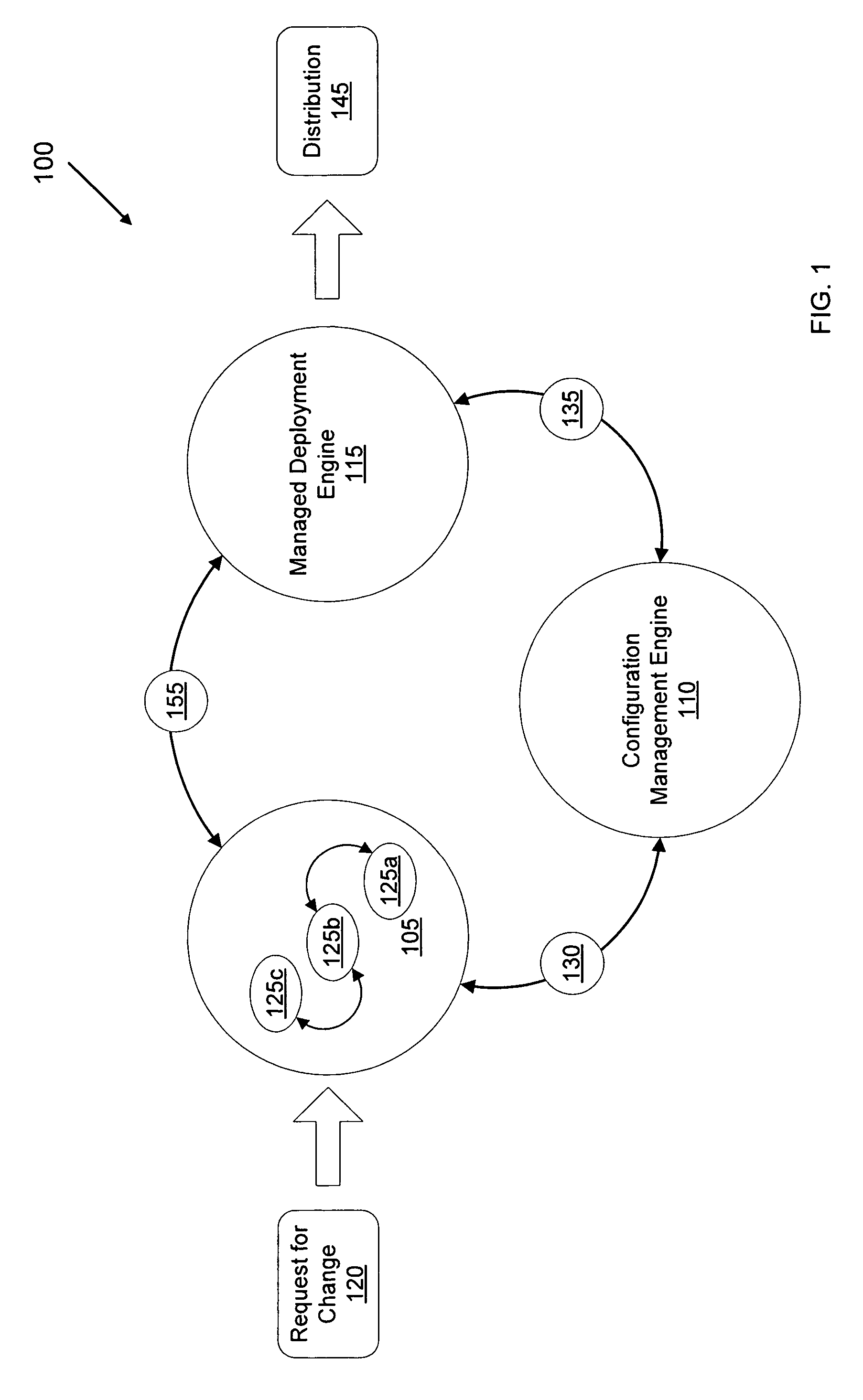
Computer method and system for integrating software development and deployment
InactiveUS20070006122A1TransmissionSpecific program execution arrangementsSoftware developmentIntegrated software
A computer implemented method and system for software auditability and bidirectional traceability in a software development lifecycle is provided. The lifecycle having at least development and deployment phases is bridged with a configurable workflow engine, a configuration management engine, and a managed deployment engine, interconnected with one or more representations of work to be performed or of work performed. Additionally, auditability and bidirectional traceability is provided by linking a development asset in the development phase to a deployment asset in the deployment phase so that: the development asset can be determined from the deployment asset; a deploying entity deploying the deployment asset can be determined from the development asset; a development request for developing the development asset can be determined from the deployment asset deployed; and a deployment environment where the deployment asset is being deployed can be determined from the development asset.
Owner:LINKEDIN
Computer system and method of using presence visualizations of avatars as persistable virtual contact objects
Owner:ACTIVISION PUBLISHING
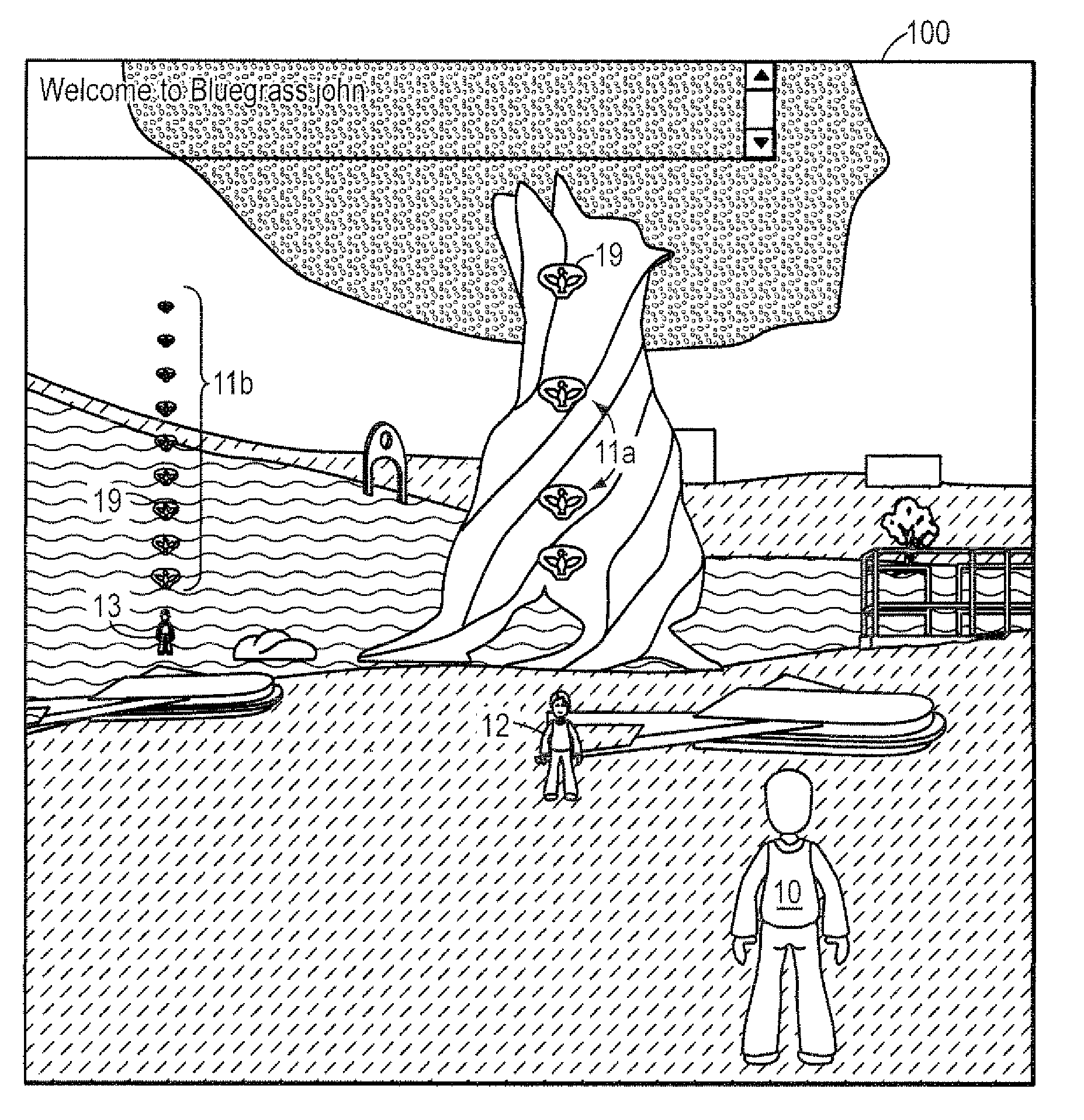
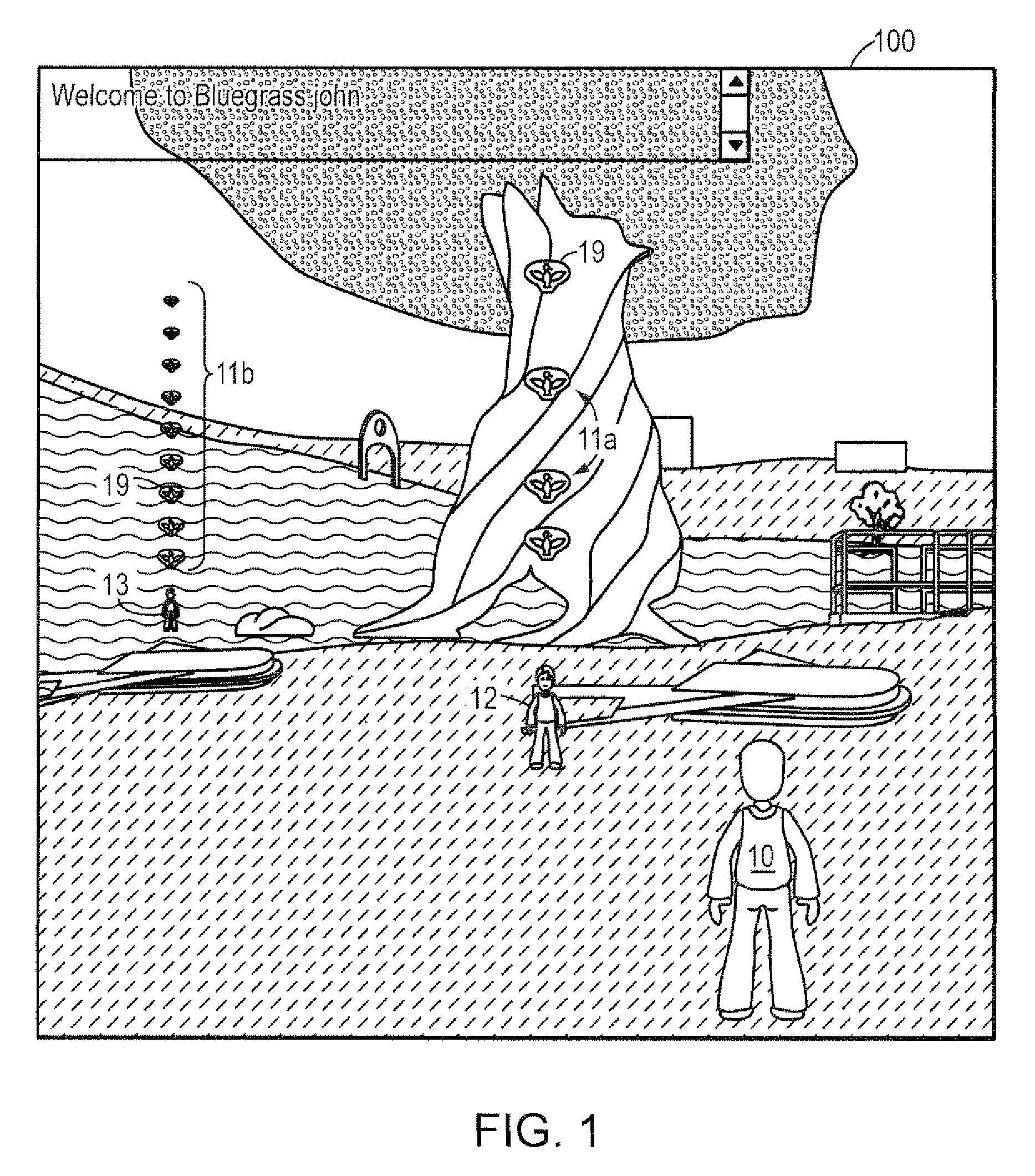
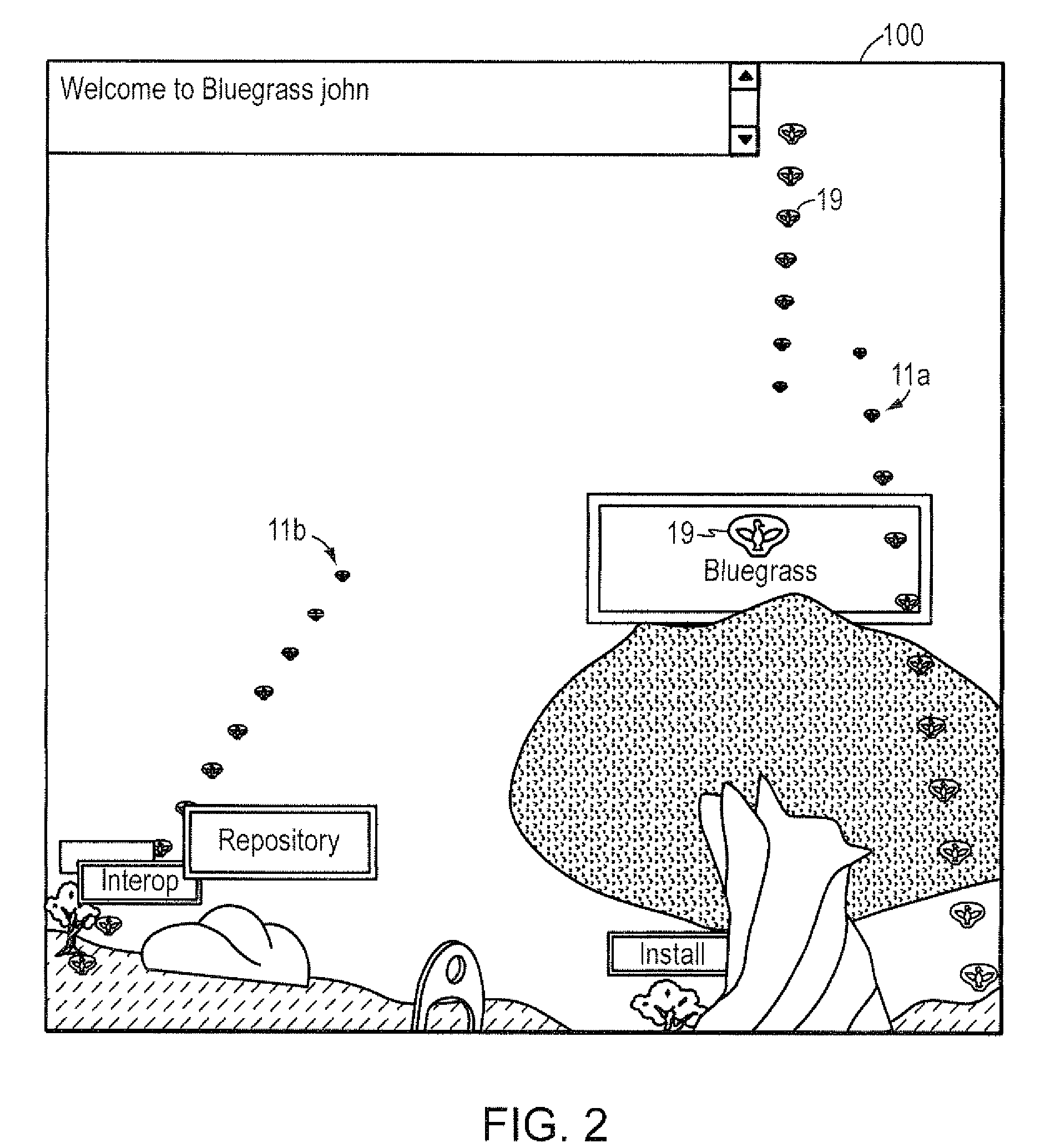
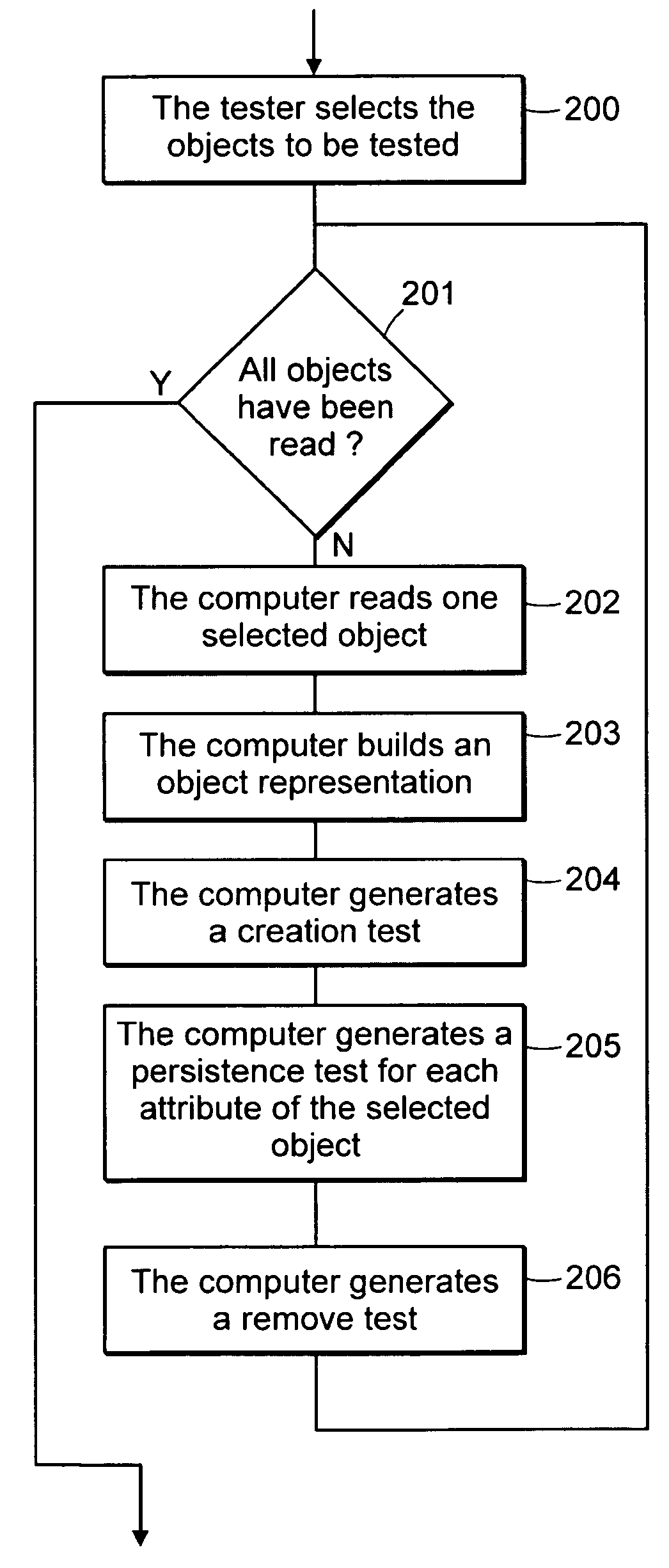
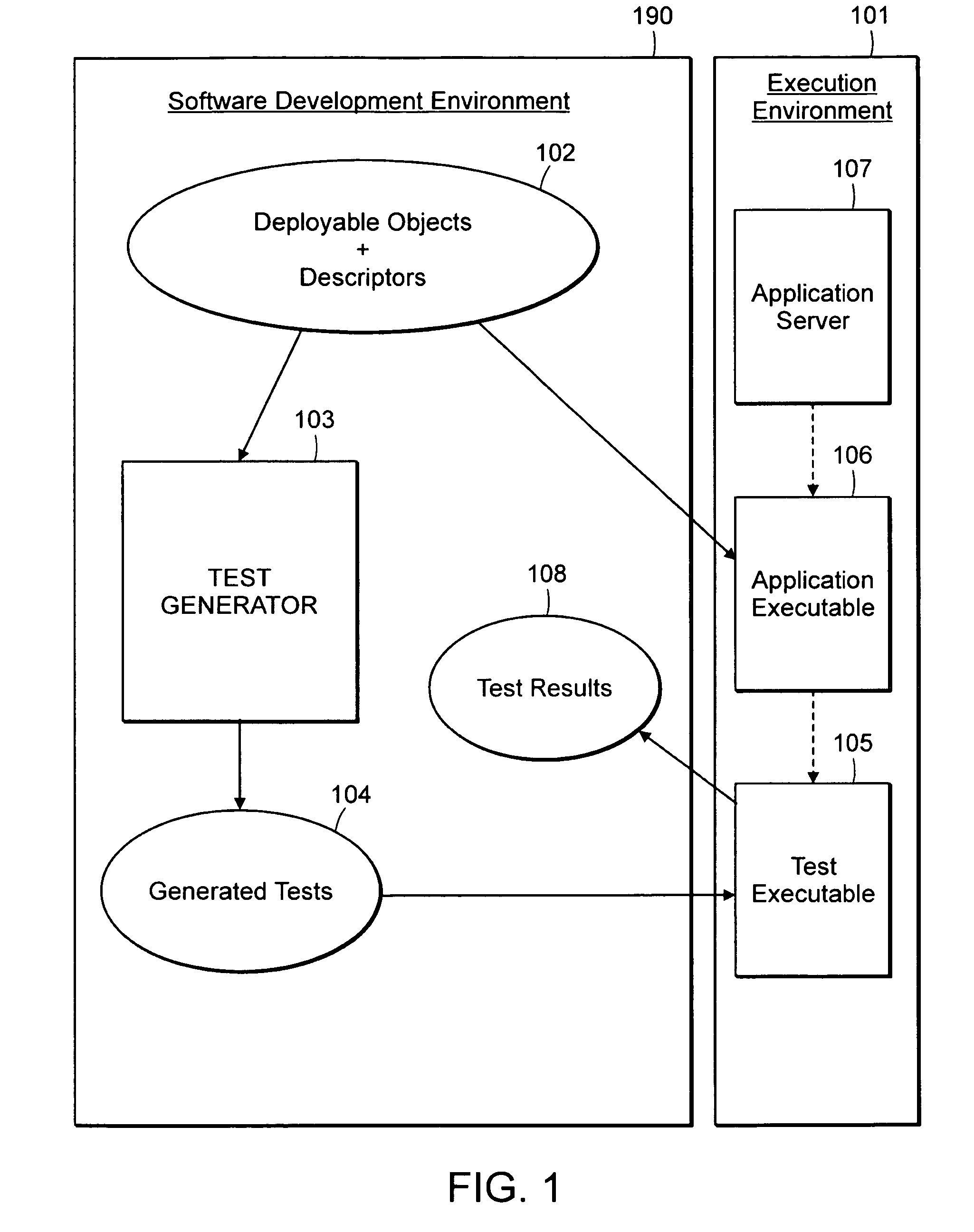
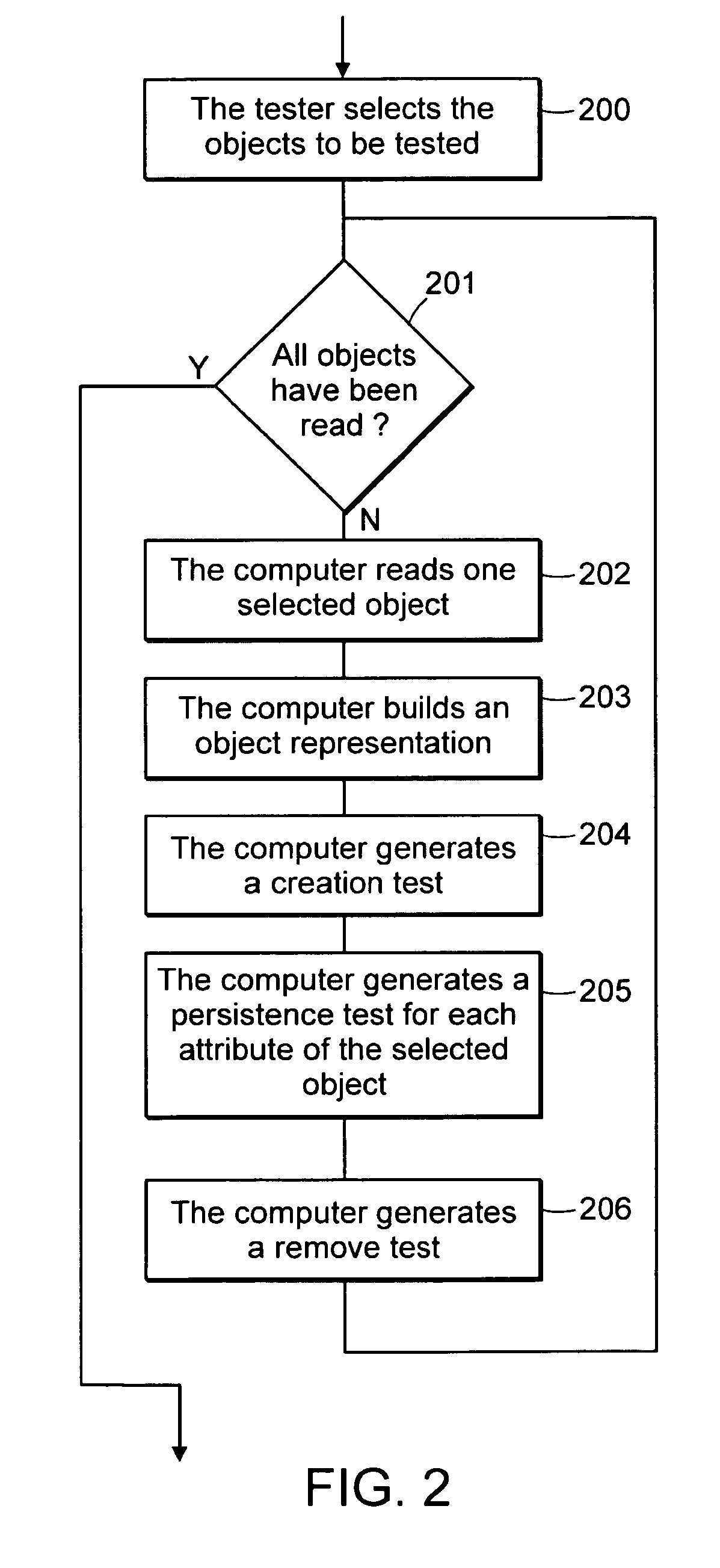
Computer method and system for automatically creating tests for checking software
InactiveUS7707553B2Error detection/correctionSoftware engineeringComputerized systemApplication software
Computer system and method automatically generates a test source code for checking validity of an application written in an object oriented language. The application includes objects accessible through an interface implementing programming rules and object behavior rules. For each object, the invention extracts object methods and attributes of the object interface which are impacted by the object behavior rules and extracts the object identification. The invention fills the variable fields of a source code template with the extracted information. The template non variable source code is in conformance with the programming rules and implements a scenario for checking a set of object behavior rules; thus the filled template forms a generated test source code. For distributed applications, the specifications may be EJB or CORBA and the Test Generator uses templates for checking the life-cycle (creation, persistency, removal) of deployed objects.
Owner:INT BUSINESS MASCH CORP
Multiple security layers for time-based network admission control
InactiveUS20100043066A1Reduce energy consumptionOptimize networkDigital data processing detailsUser identity/authority verificationComputer methodsNetwork Access Control
Embodiments of the present invention include a computer method of controlling access to a computer-based network comprising: (i) receiving an indication of an attempt to gain access to a computer-based network; (ii) applying a respective network access control policy to determine whether to allow the attempt to gain access to the computer-based network at each of multiple security layers; and (iii) allowing or blocking the attempt to gain access through the security layer to the computer-based network based on the application of the respective network access control policy at each security layer. Other embodiments include a computer method of controlling access to a computer-based network comprising: (a) scanning a host computer for viruses; (b) temporarily disabling a firewall of the host computer during an audit; and (c) shutting down high risk services running on the host computer.
Owner:NETCLARITY
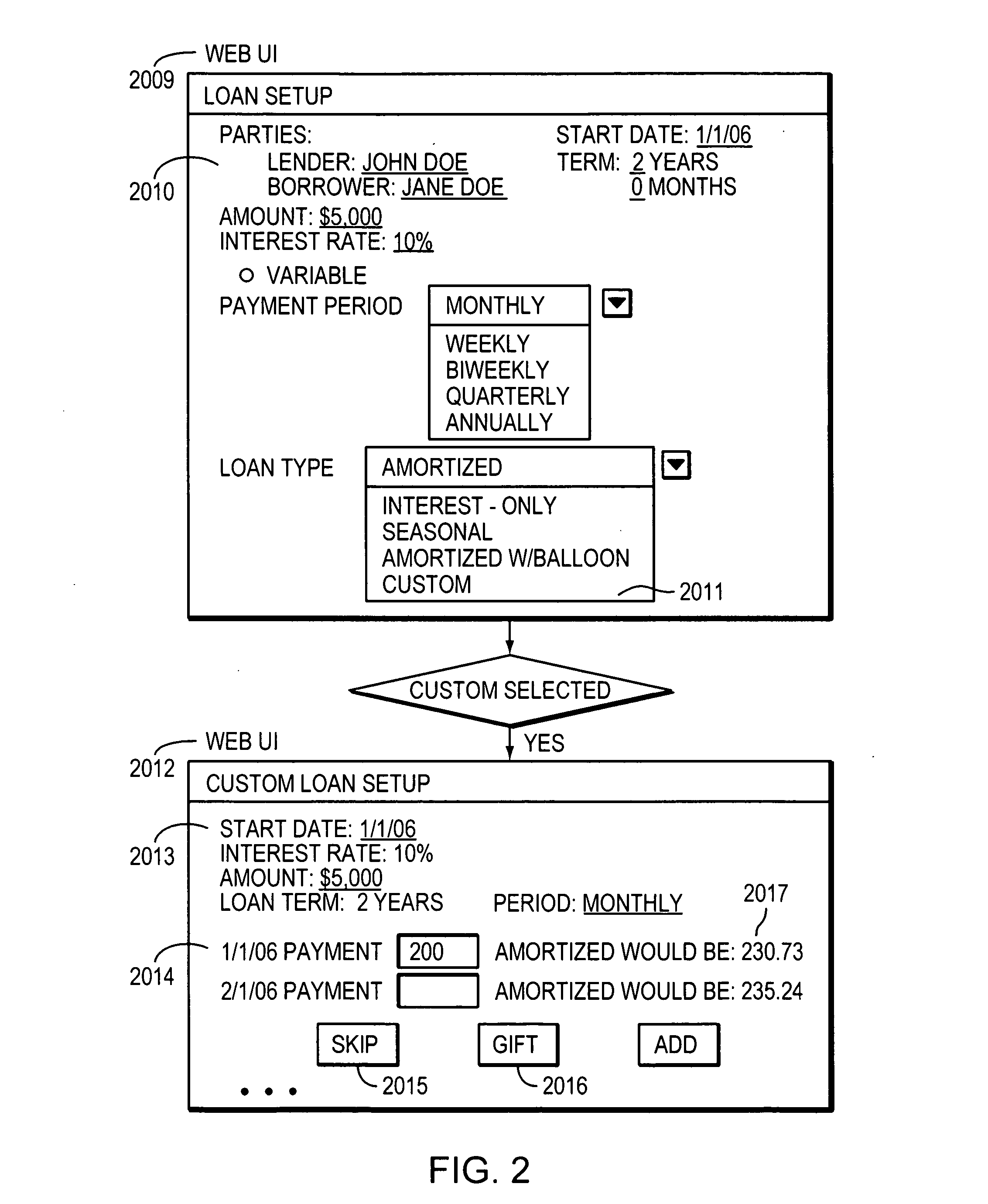
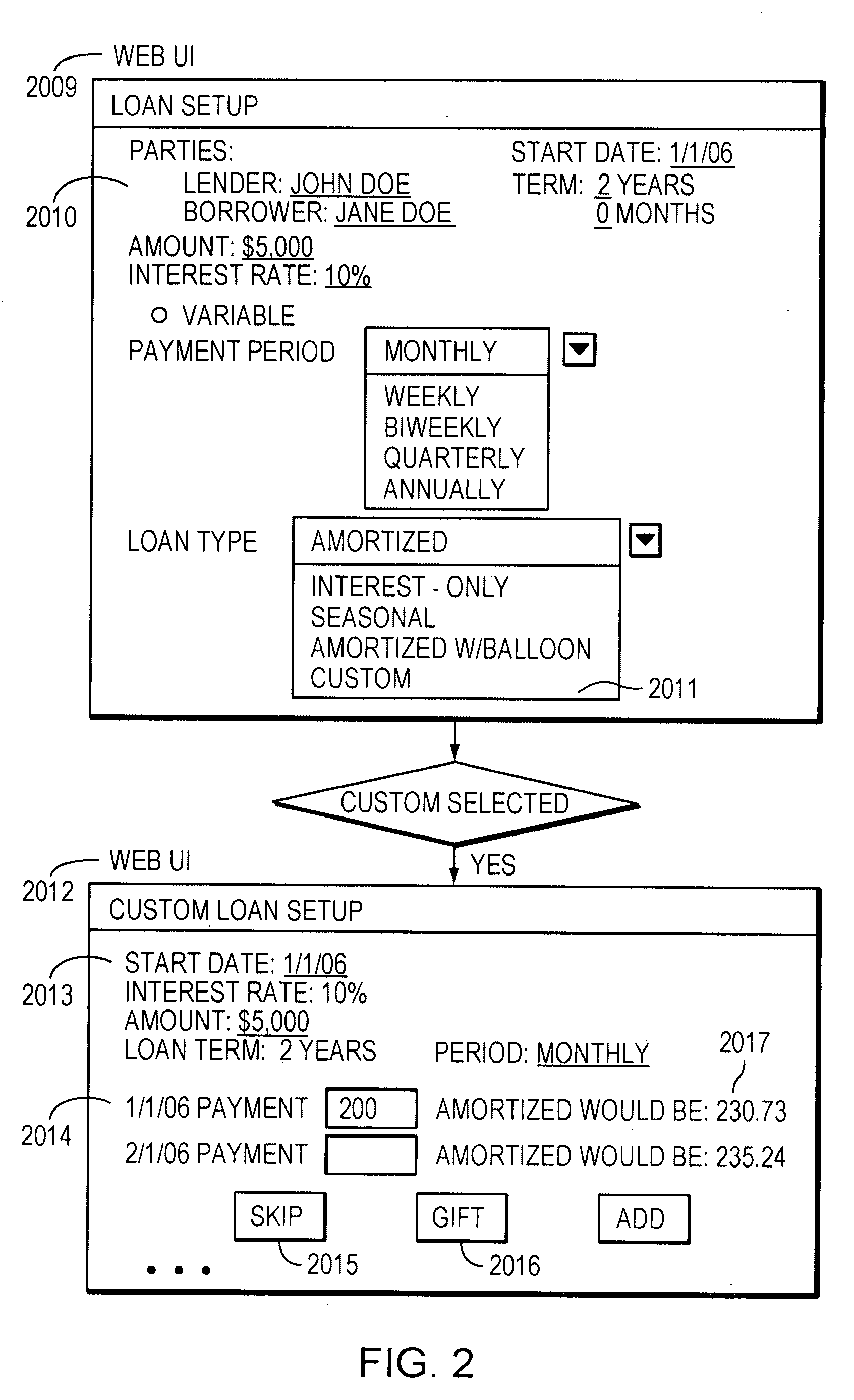
System and method for automated flexible person-to-person lending
A computer method for automating person-to-person lending comprises receiving from a user over a computer network at least one custom periodic payment amount for a loan period of a person-to-person loan; generating a custom loan schedule based on the custom amount; and transmitting the custom loan schedule over the computer network to the user. A further method comprises receiving from a first user over a computer network a request to modify at least one specific periodic payment amount for a loan period of a pre-existing person-to-person loan; receiving from a second user a consent to the first user's request; and generating a revised loan schedule for the loan based on the request to modify the payment amount. Another method comprises retrieving from a database loan history data for a person-to-person loan; and transmitting the loan history data to a credit reporting agency over a computer network.
Owner:VIRGIN MONEY HLDG USA
System and method for automated flexible person-to-person lending
A computer method for automating person-to-person lending comprises receiving from a user over a computer network at least one custom periodic payment amount for a loan period of a person-to-person loan; generating a custom loan schedule based on the custom amount; and transmitting the custom loan schedule over the computer network to the user. A further method comprises receiving from a first user over a computer network a request to modify at least one specific periodic payment amount for a loan period of a pre-existing person-to-person loan; receiving from a second user a consent to the first user's request; and generating a revised loan schedule for the loan based on the request to modify the payment amount. Another method comprises retrieving from a database loan history data for a person-to-person loan; and transmitting the loan history data to a credit reporting agency over a computer network.
Owner:VIRGIN MONEY HLDG USA
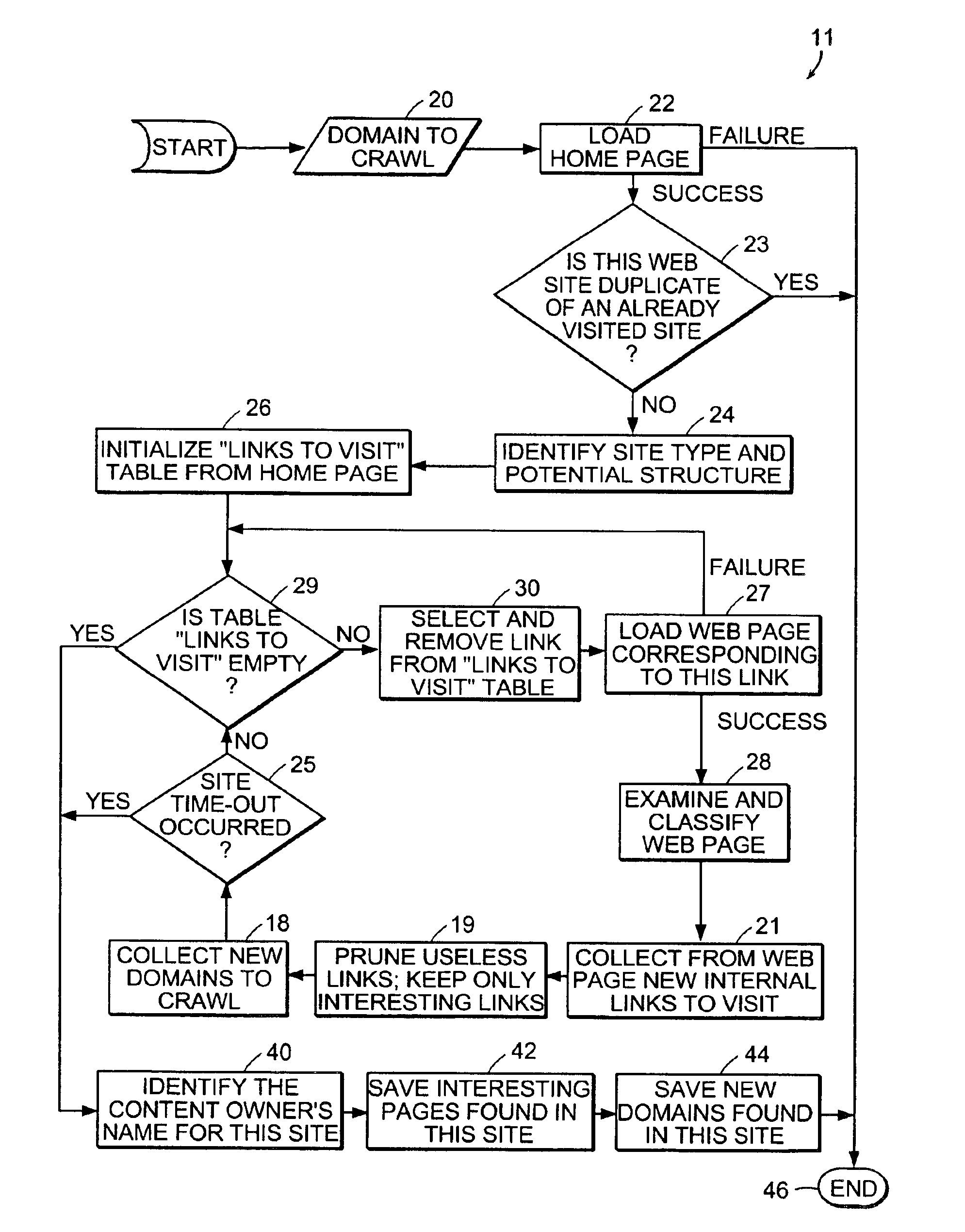
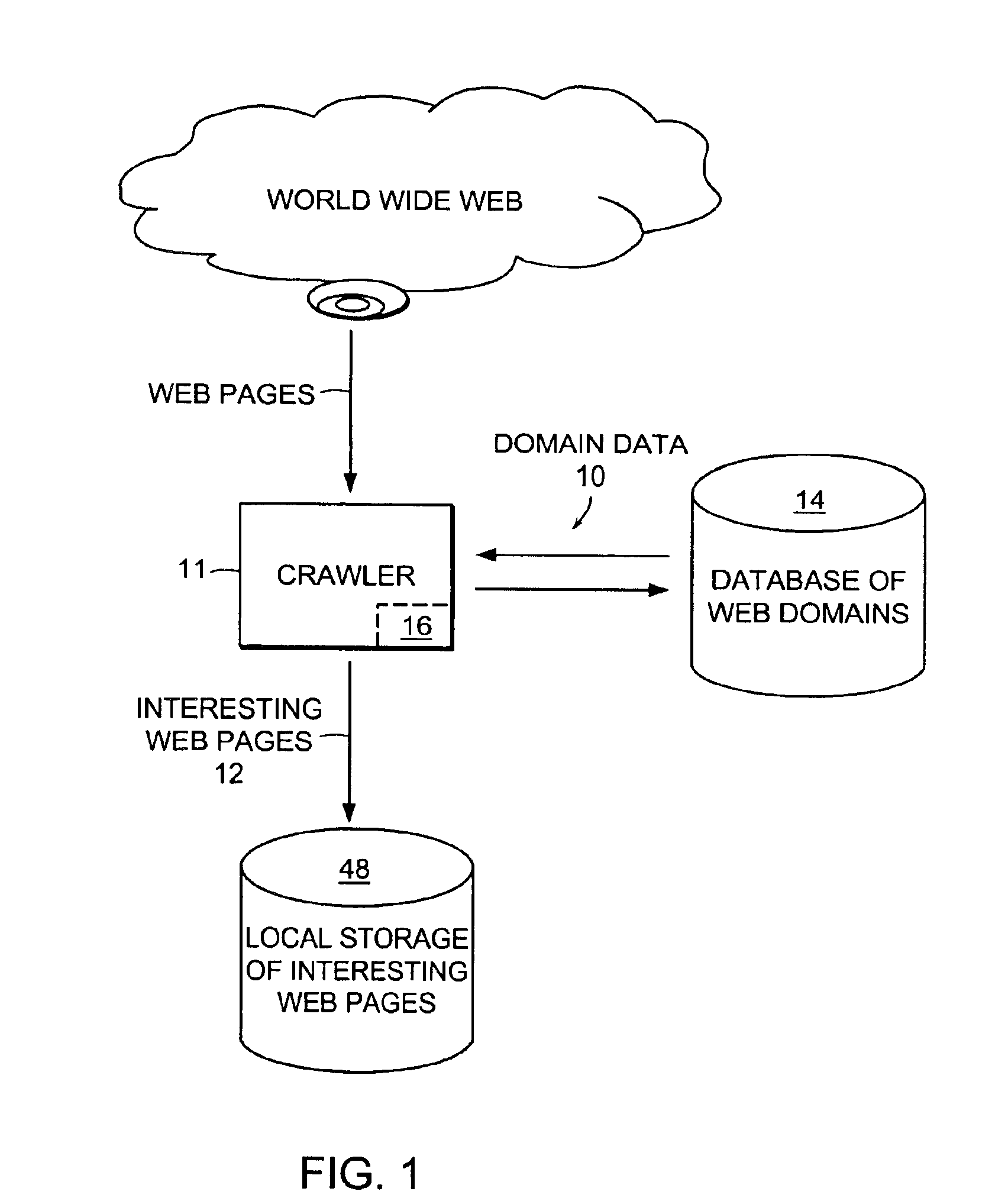
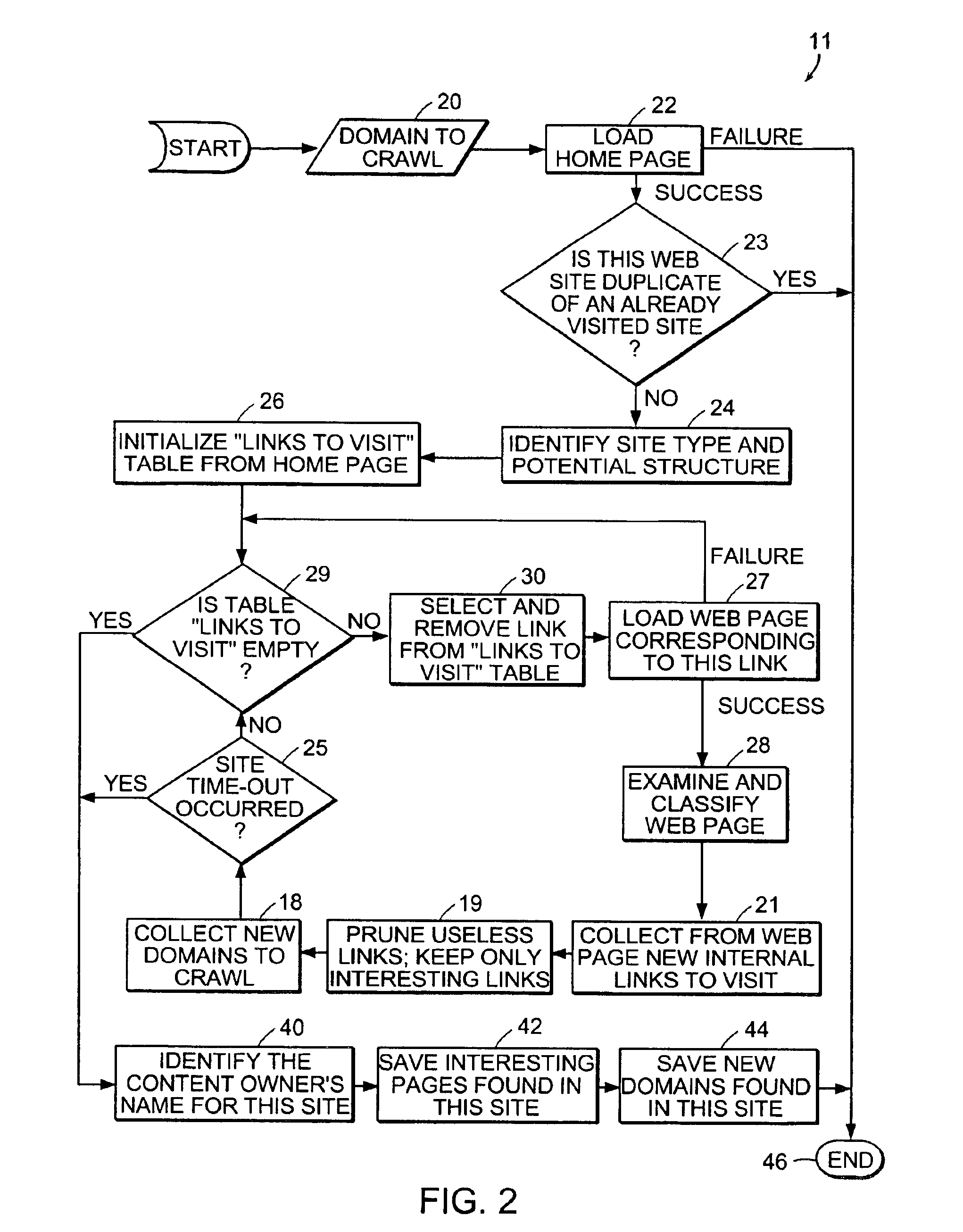
Computer method and apparatus for collecting people and organization information from Web sites
ActiveUS6983282B2Efficient and accurate in its taskData processing applicationsWeb data indexingWeb siteUnique identifier
Computer processing method and apparatus for searching and retrieving Web pages to collect people and organization information are disclosed. A Web site of potential interest is accessed. A subset of Web pages from the accessed site are determined for processing. According to types of contents found on a subject Web page, extraction of people and organization information is enabled. Internal links of a Web site are collected and recorded in a links-to-visit table. To avoid duplicate processing of Web sites, unique identifiers or Web site signatures are utilized. Respective time thresholds (time-outs) for processing a Web site and for processing a Web page are employed. A database is maintained for storing indications of domain URLs, names of respective owners of the URLs as identified from the corresponding Web sites, type of each Web site, processing frequencies, dates of last processings, outcomes of last processings, size of each domain and number of data items found in the last processing of each Web site.
Owner:ELIYON TECH CORP
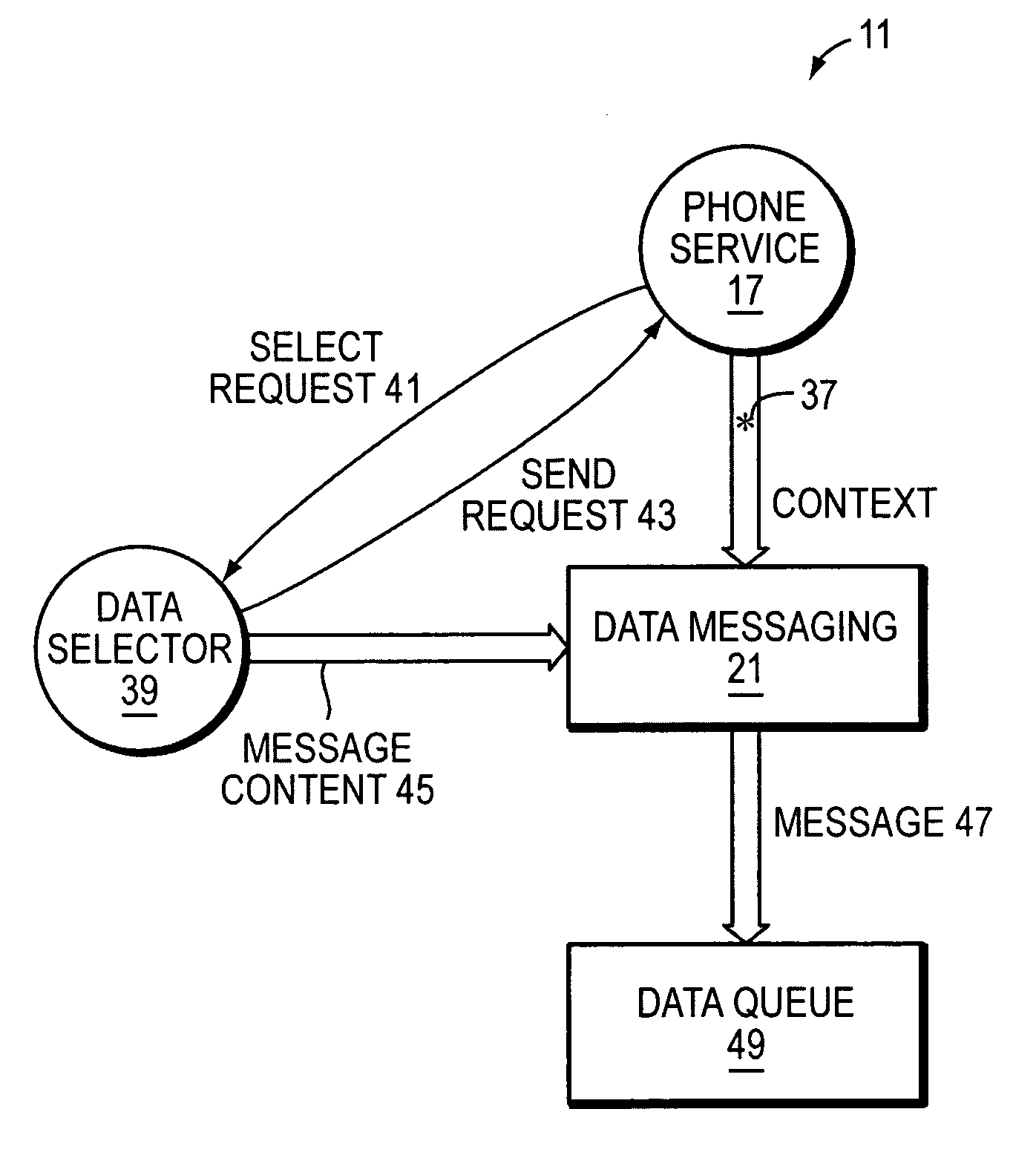
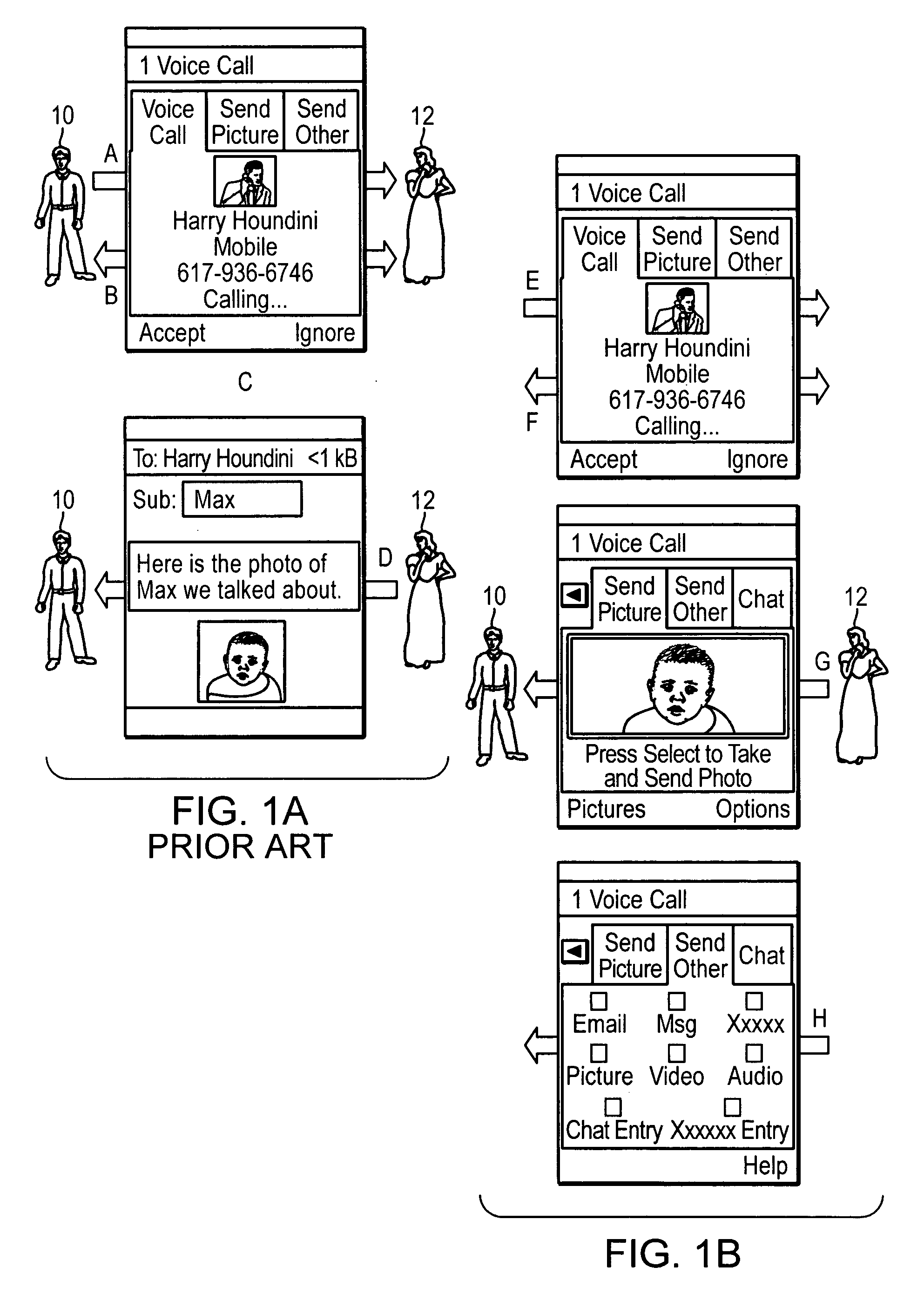
Method and apparatus for augmenting voice data on a mobile device call
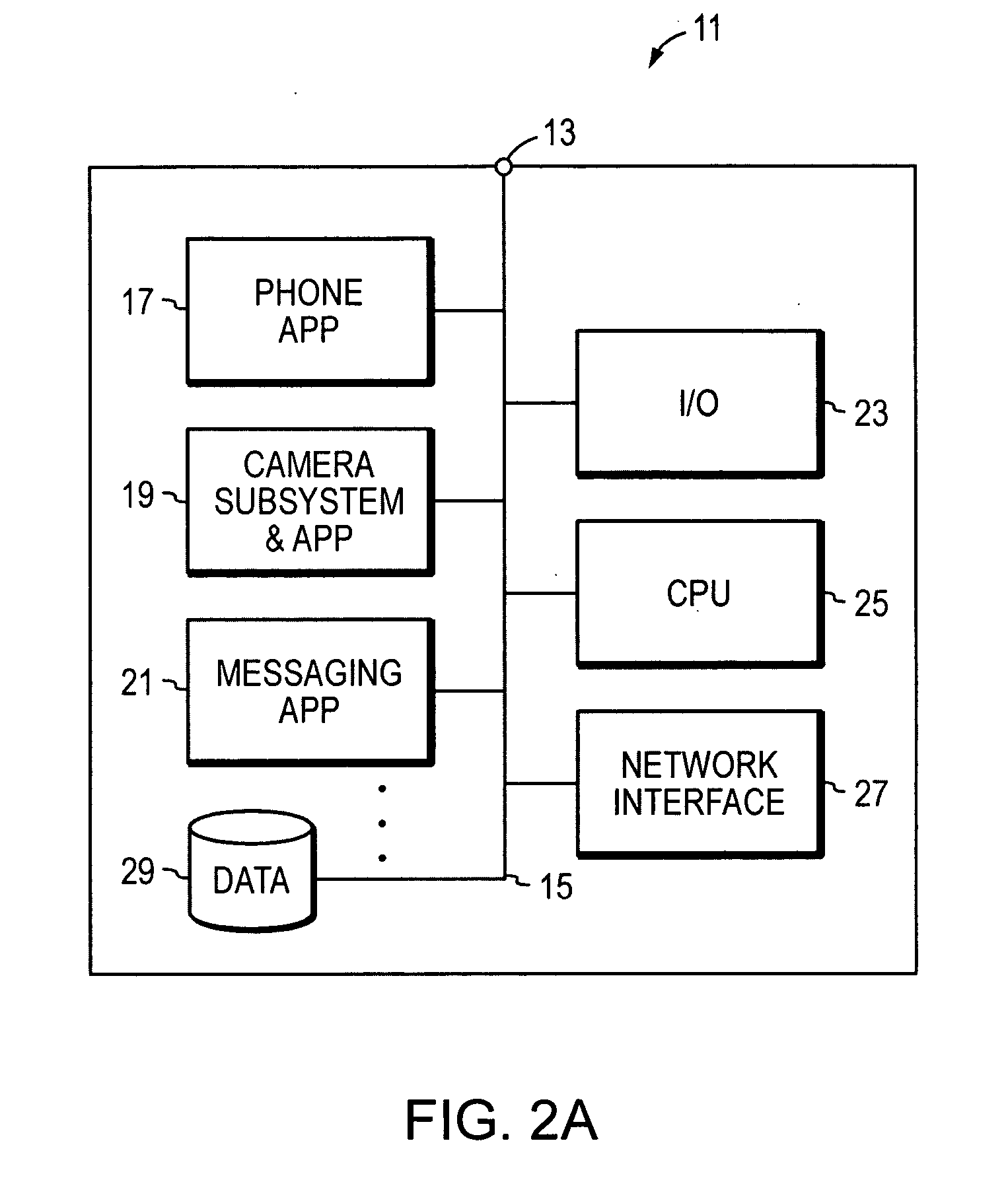
InactiveUS20060193448A1Automatic call-answering/message-recording/conversation-recordingMessaging/mailboxes/announcementsData elementComputer methods
A computer method and system for portable phone devices enable a user to compose and send a data message (e.g., a photo / image) during a voice call. The data message includes any of image data, audio (music) packette, an electronic calendar entry / event, contact information, HTML, text-based data, video data, multimedia and the like. During a voice call session between a user and a recipient, the user using a subject phone device obtains at least one data element. The subject phone device automatically forms and transmits a data message, including the at least one data element, to the recipient of the voice call session. The subject phone device maintains and continues the voice call session with voice data indicative of verbal conversation between the recipient and user. The subject phone device may be a PDA, mobile / cellular phone or other wireless communication and data device.
Owner:SUN MICROSYSTEMS INC
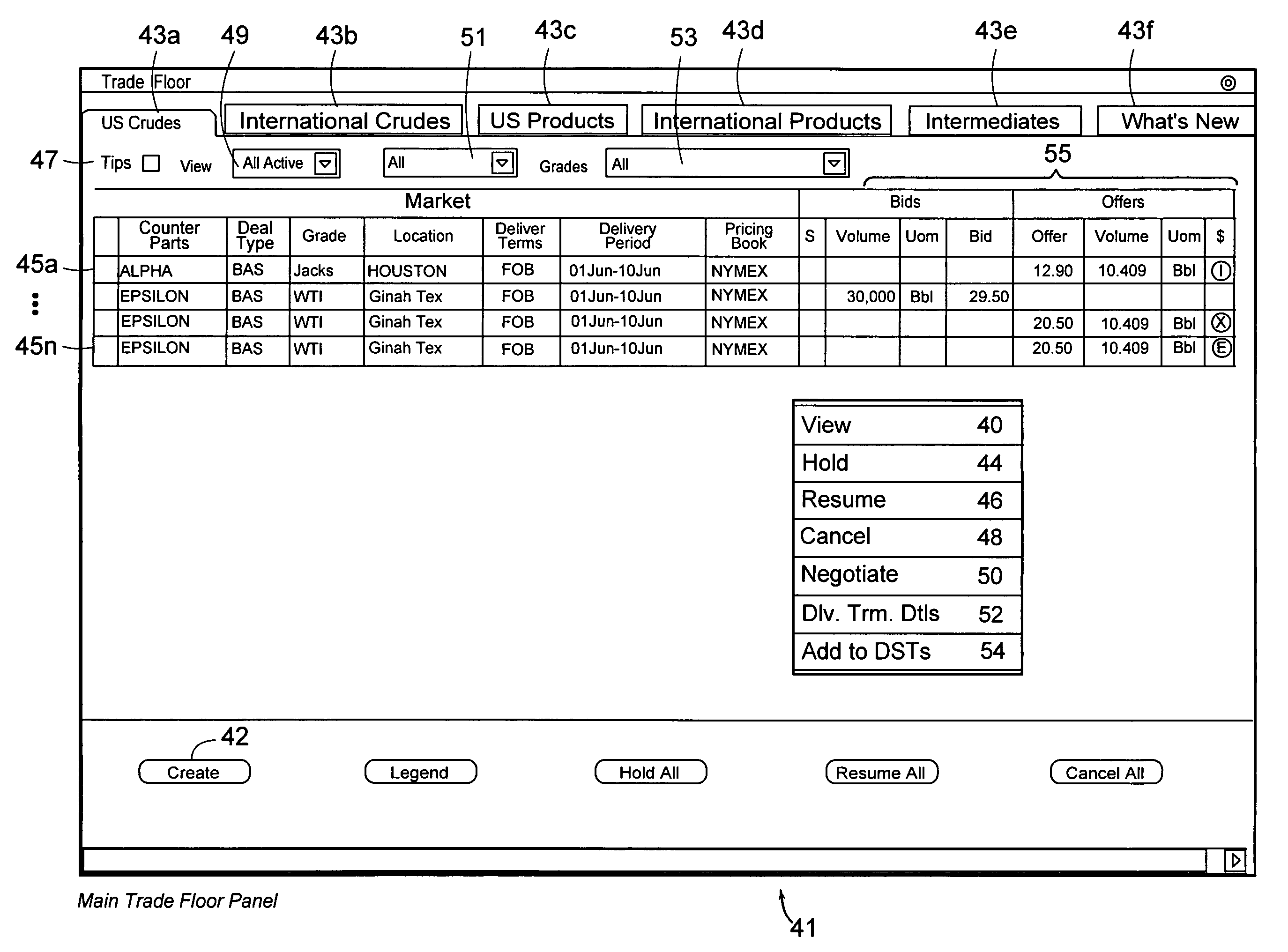
Computer method and apparatus for vessel selection and optimization
InactiveUS6983186B2Accurate dataFew typographical errorFinanceOffice automationLogistics managementComputer methods
Owner:ASPENTECH CORP
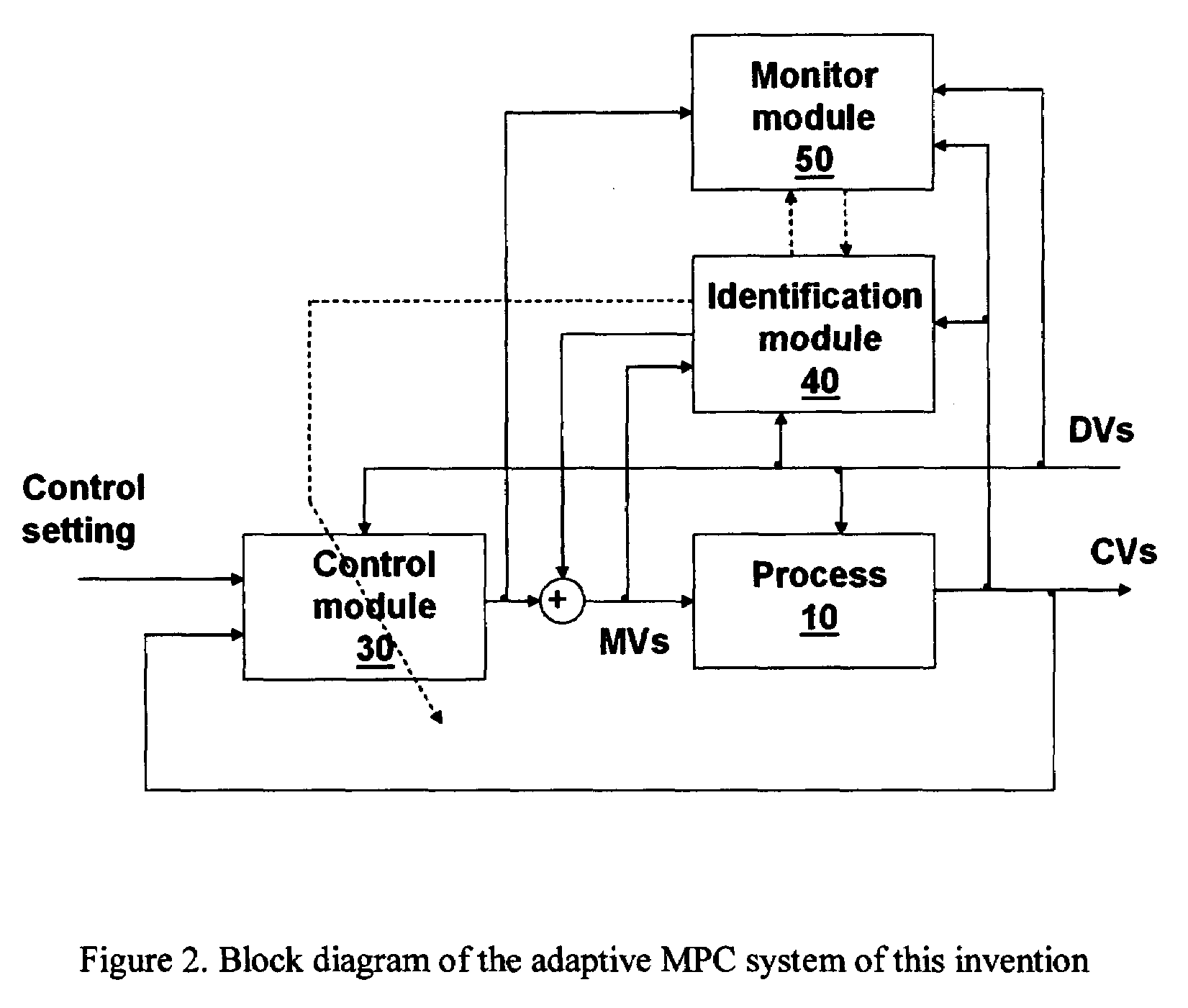
Computer method and apparatus for adaptive model predictive control
InactiveUS20070225835A1Automatically efficiently performLow costAdaptive controlControl engineeringModel quality
A computer method and apparatus for adaptive model predictive control (MPC) of multivariable processes is disclosed. The adaptive MPC system can perform automatic implementation for a new MPC controller, and, for an existing MPC controller, it can perform automatic maintenance when necessary. The adaptive MPC system consists of three modules: an MPC control module, an online identification module and a control monitor module. In MPC implementation, the online identification module and the MPC control module work together and perform various steps in MPC implementation automatically and efficiently. When the MPC controller is online, the control monitor module continuously monitors the MPC performance and model quality. When control performance becomes poor and considerable model degradation is detected, monitor module will start the maintenance by activating the online identification module. The identification module will re-identify the model and replace the old model. For strongly nonlinear process units, multiple models are identified and used in control.
Owner:ZHU YUCAI
Computer method and apparatus for processing image data
InactiveUS20100008424A1Precise cuttingIncrease the compression ratioColor television with pulse code modulationColor television with bandwidth reductionPattern recognitionData compression
A method and apparatus for image data compression includes detecting a portion of an image signal that uses a disproportionate amount of bandwidth compared to other portions of the image signal. The detected portion of the image signal result in determined components of interest. Relative to certain variance, the method and apparatus normalize the determined components of interest to generate an intermediate form of the components of interest. The intermediate form represents the components of interest reduced in complexity by the certain variance and enables a compressed form of the image signal where the determined components of interest maintain saliency. In one embodiment, the video signal is a sequence of video frames. The step of detecting includes any of: (i) analyzing image gradients across one or more frames where image gradient is a first derivative model and gradient flow is a second derivative, (ii) integrating finite differences of pels temporally or spatially to form a derivative model, (iii) analyzing an illumination field across one or more frames, and (iv) predictive analysis, to determine bandwidth consumption. The determined bandwidth consumption is then used to determine the components of interest.
Owner:EUCLID DISCOVERIES LLC
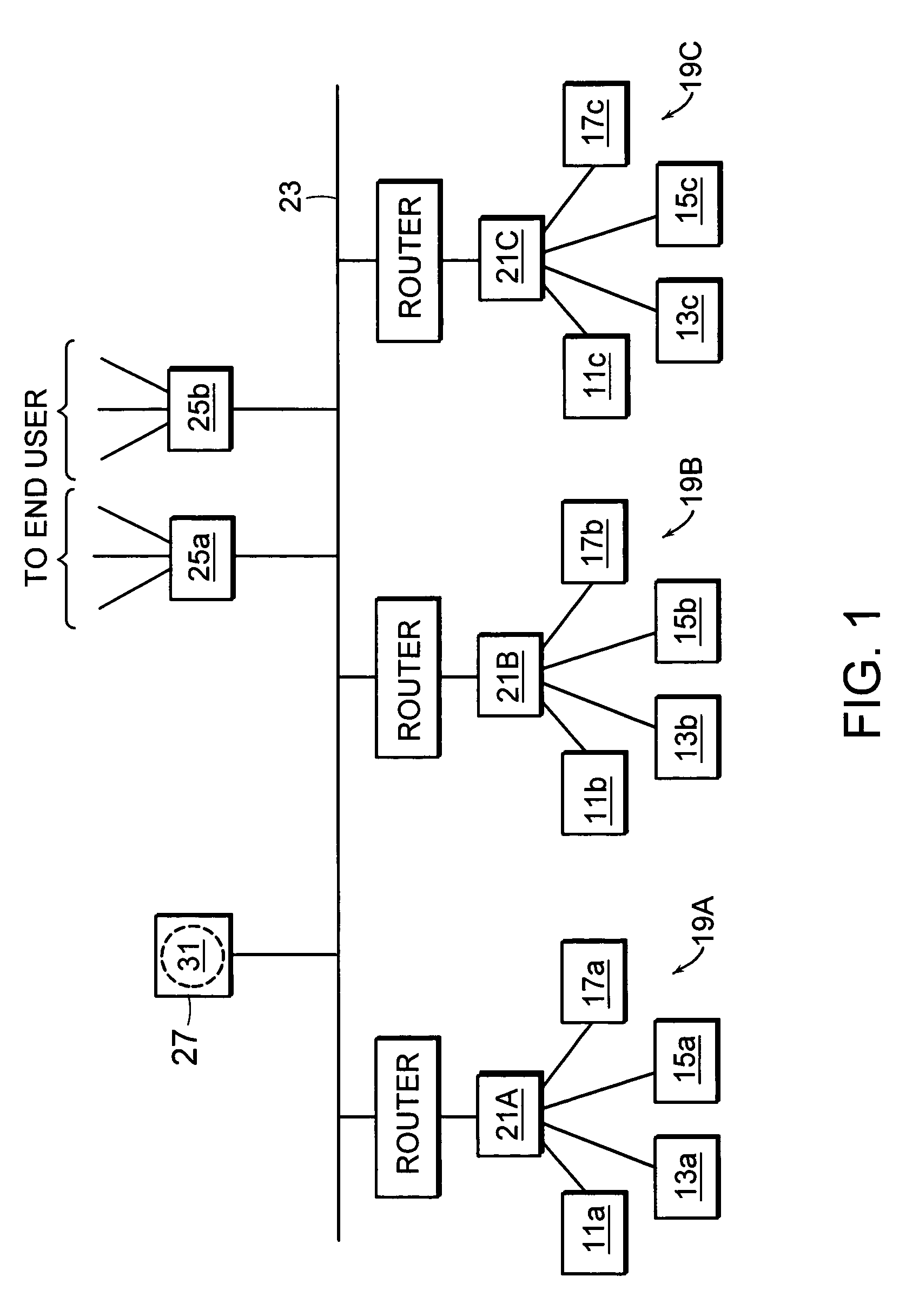
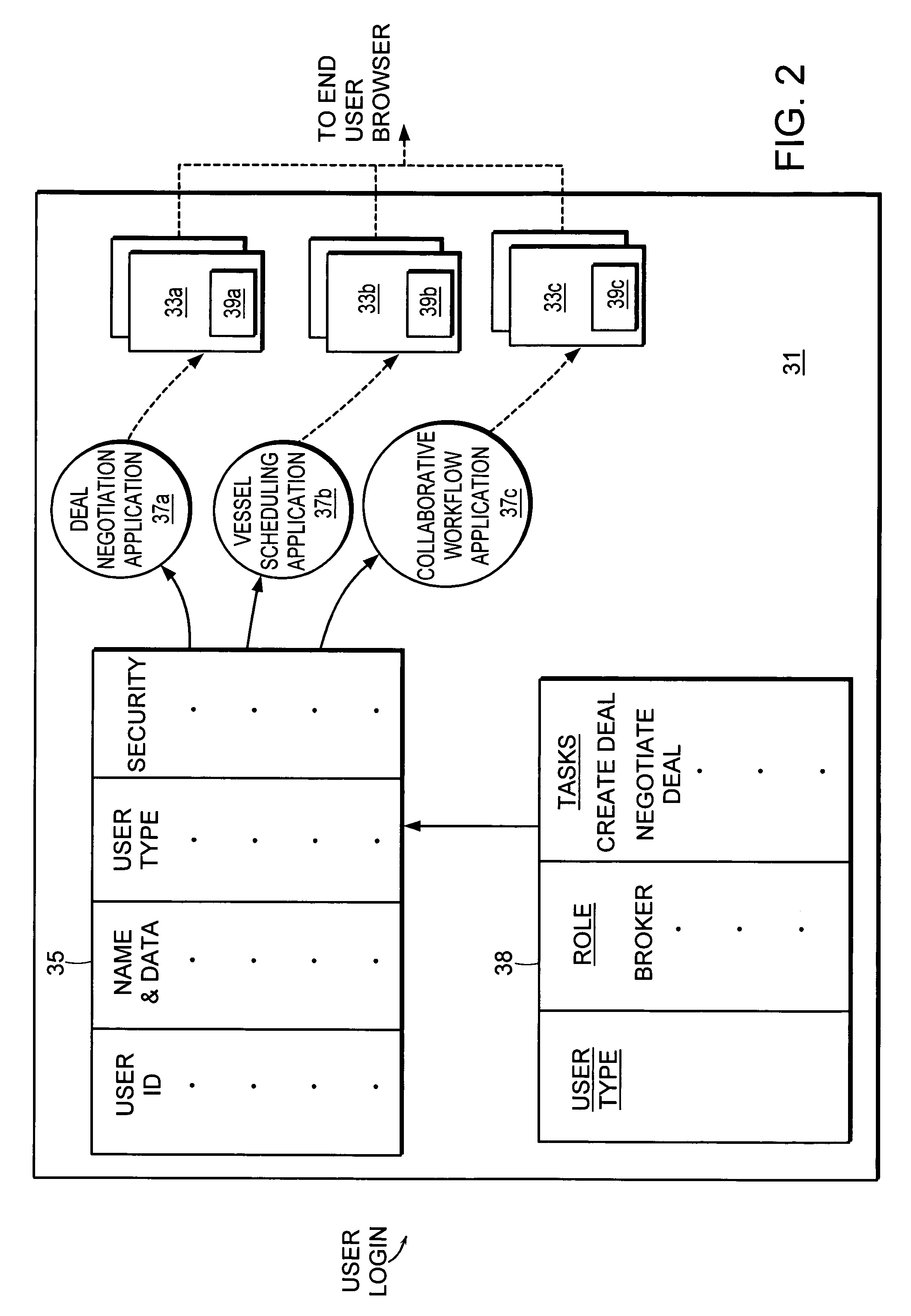
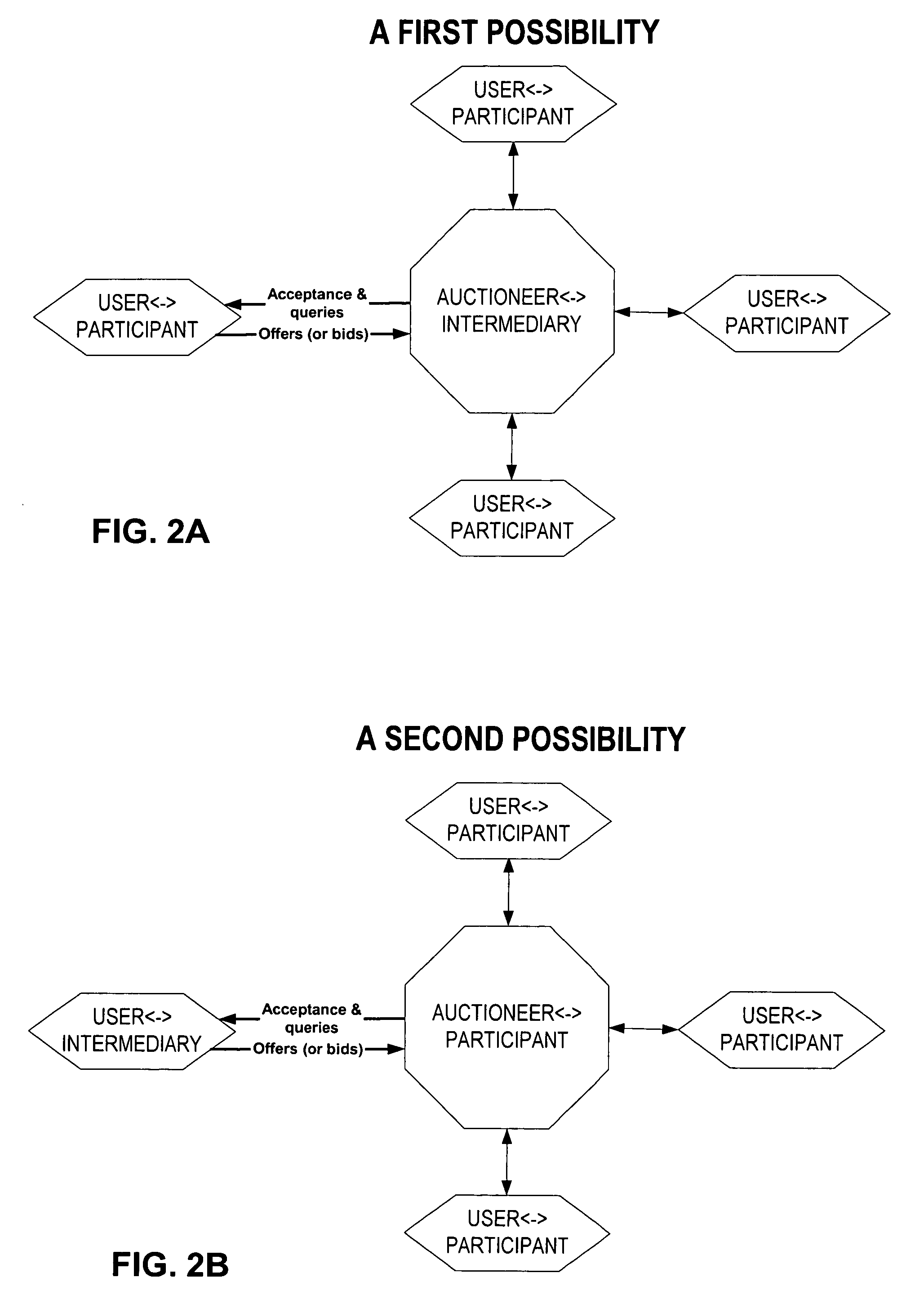
Computer method and system for intermediated exchanges
InactiveUS6968318B1Maximize tradeoffMaximizes number of unitFinanceSpecial data processing applicationsComputer methodsSoftware
In a preferred embodiment, this invention includes software processes distributed on one or more computer systems that exchange messages in order to facilitate an intermediated exchange of financial commodities between a plurality of participants. The messages are exchanged according to a preferred protocol that leads to a satisfactory exchange that meets the objectives of the participants, and that substantially maximizes in a fair manner the total amount of financial commodities exchanged. Optionally, the invention employs heuristic rules in association with the preferred protocol that adapt the protocol to the time and exchange requirements of financial commodities. In other embodiments, this invention is equally applicable to the exchange of any tangible or intangible commodities. In a general embodiment, this invention further includes a preferred message-exchange protocol for the construction of computer programs representing exchange participants and an intermediary. These constructed computer programs exchange messages such that a satisfactory intermediated exchange of commodities is substantially certain to be achieved.
Owner:ITG SOFTWARE SOLUTIONS INC
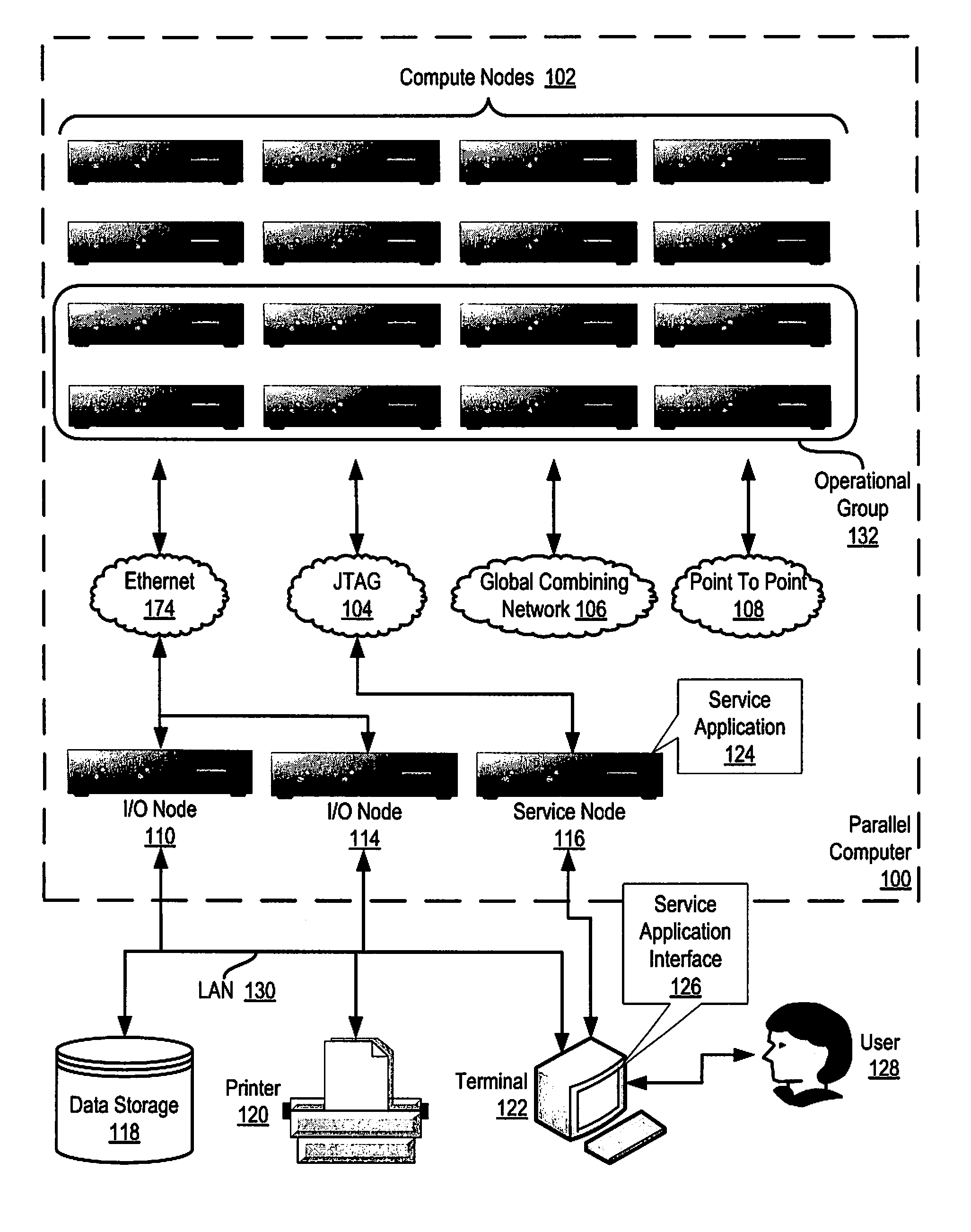
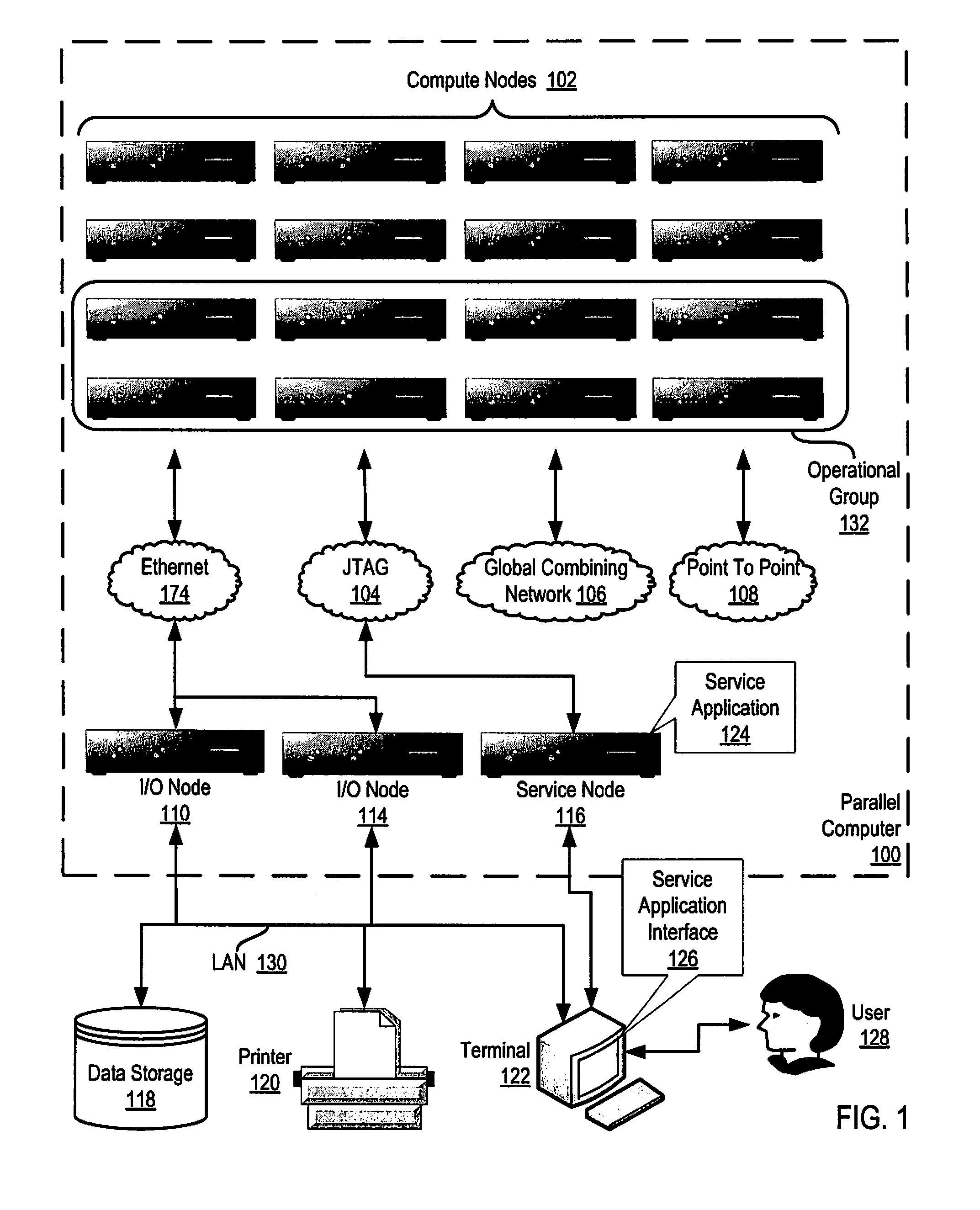
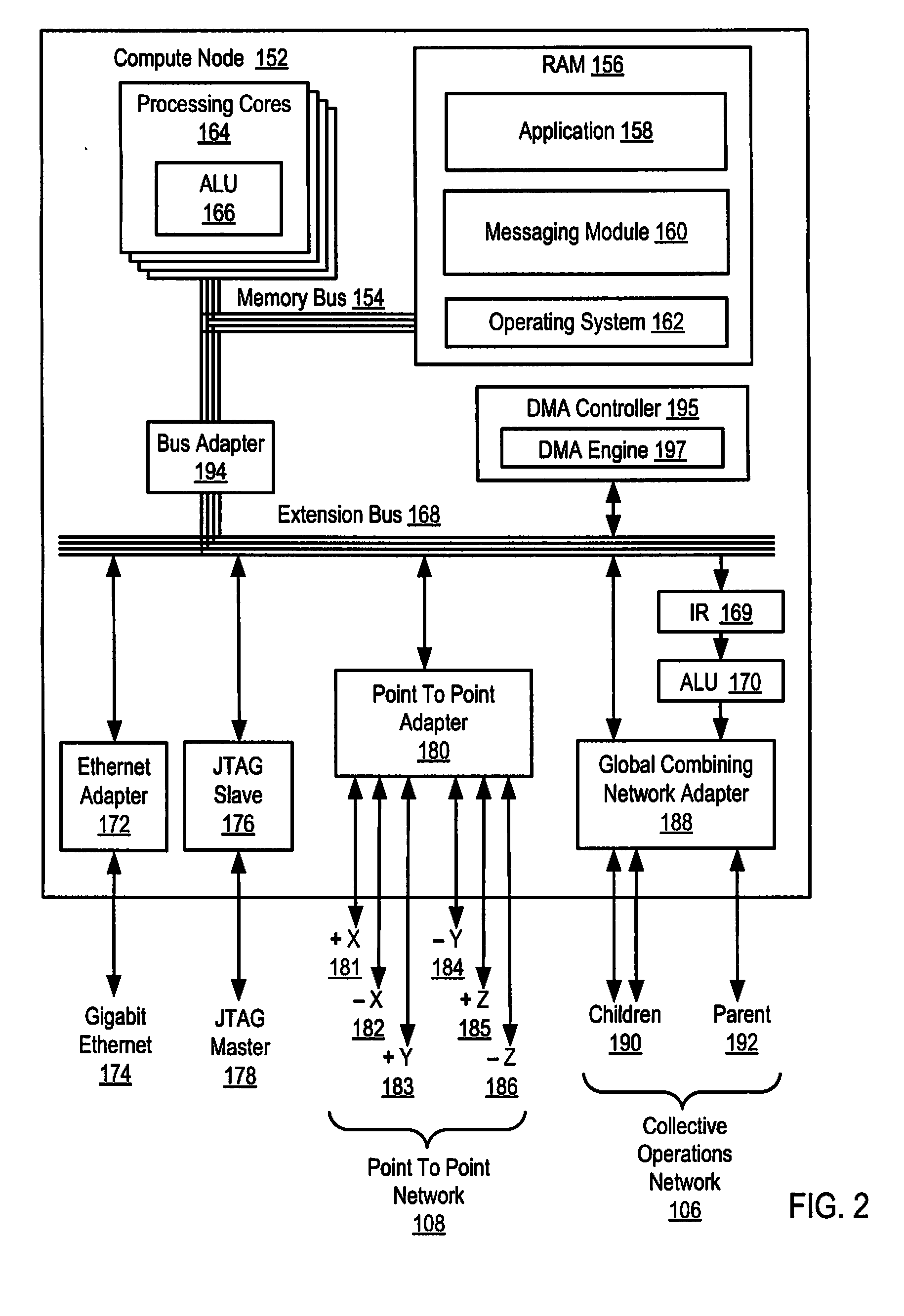
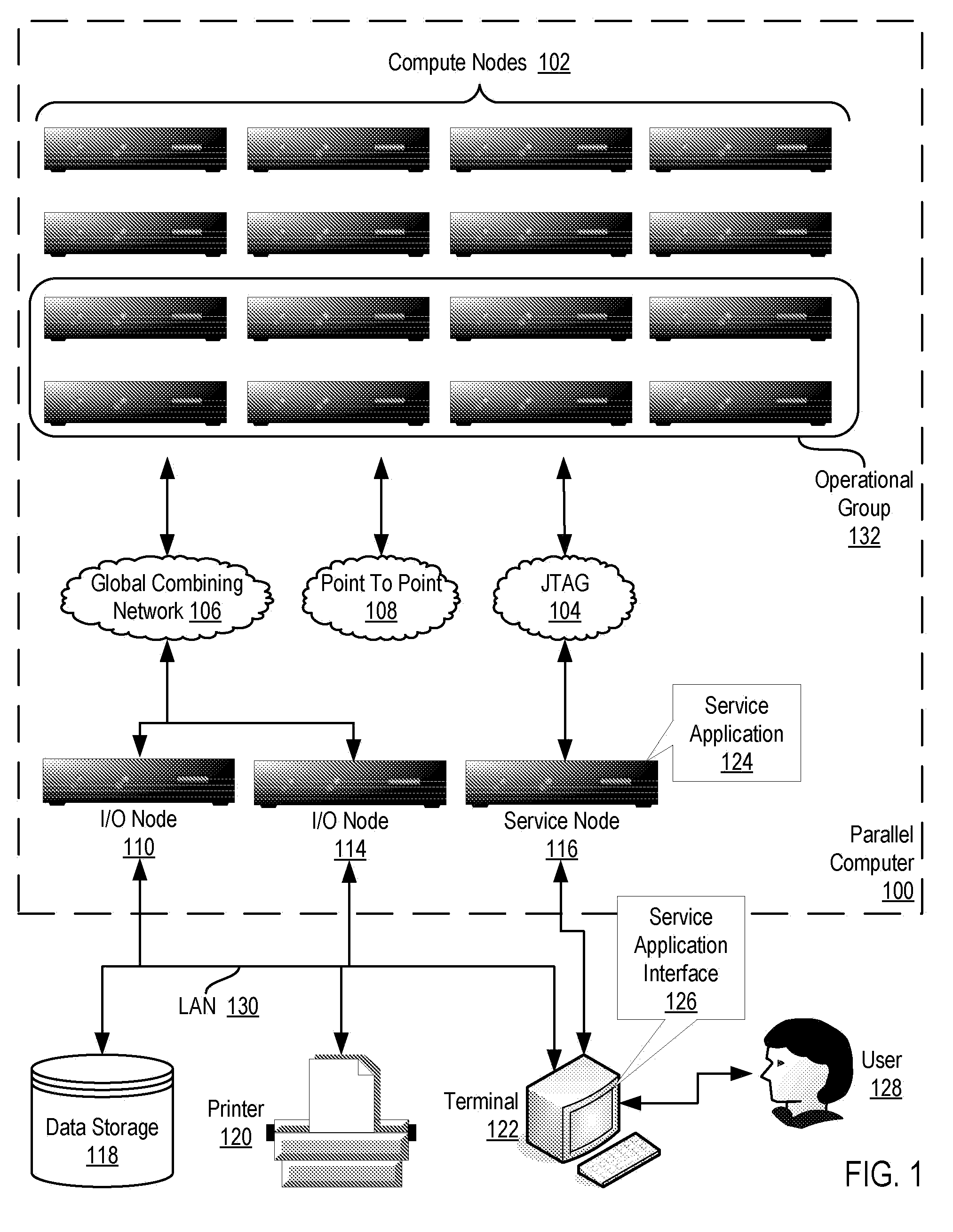
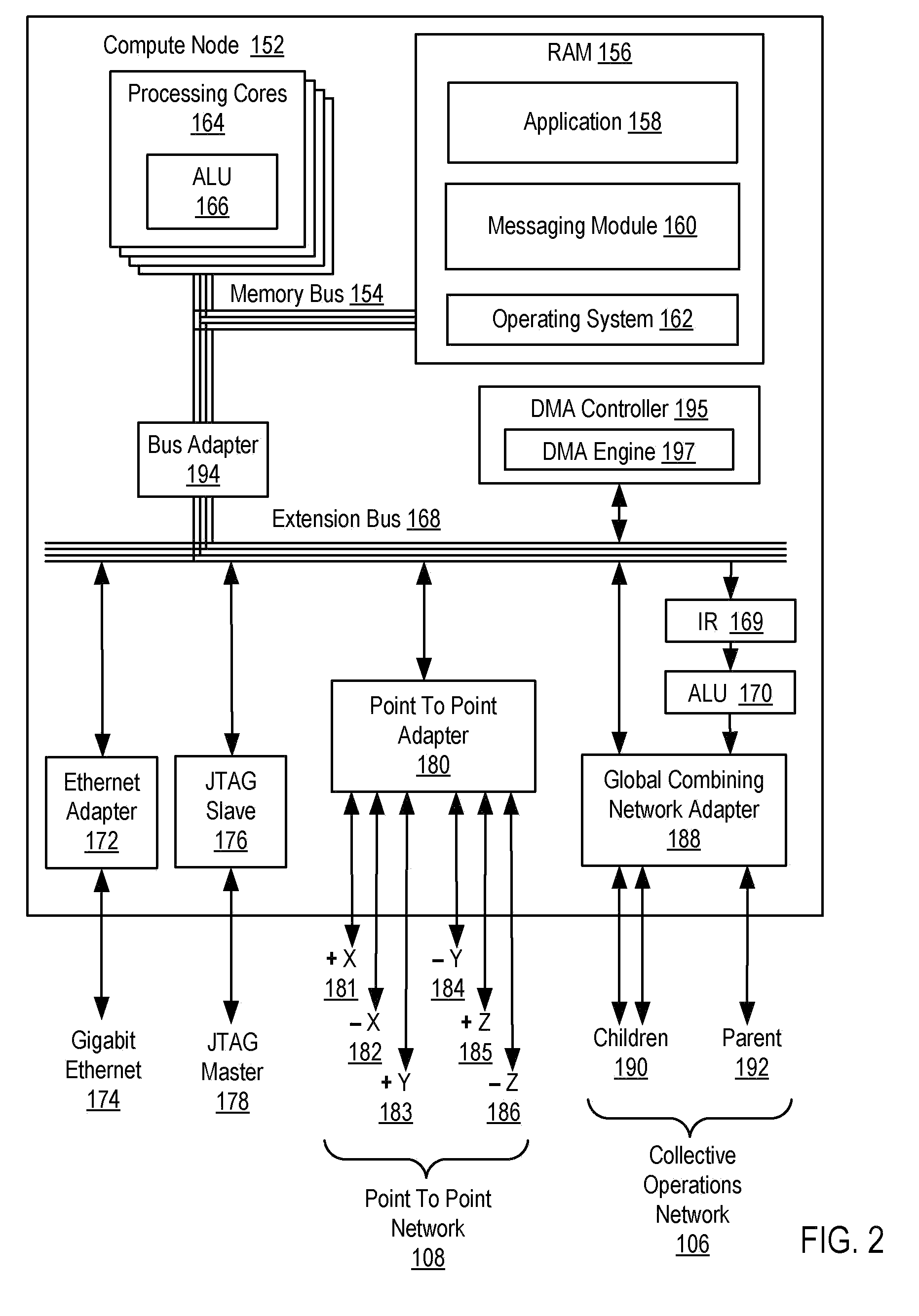
Pacing a Data Transfer Operation Between Compute Nodes on a Parallel Computer
InactiveUS20090022156A1Data switching by path configurationElectric digital data processingDirect memory accessRemote direct memory access
Methods, systems, and products are disclosed for pacing a data transfer between compute nodes on a parallel computer that include: transferring, by an origin compute node, a chunk of an application message to a target compute node; sending, by the origin compute node, a pacing request to a target direct memory access (‘DMA’) engine on the target compute node using a remote get DMA operation; determining, by the origin compute node, whether a pacing response to the pacing request has been received from the target DMA engine; and transferring, by the origin compute node, a next chunk of the application message if the pacing response to the pacing request has been received from the target DMA engine.
Owner:IBM CORP
Methods of using crystal structure of carboxyltransferase domain of acetyl-CoA carboxylase, modulators thereof, and computer methods
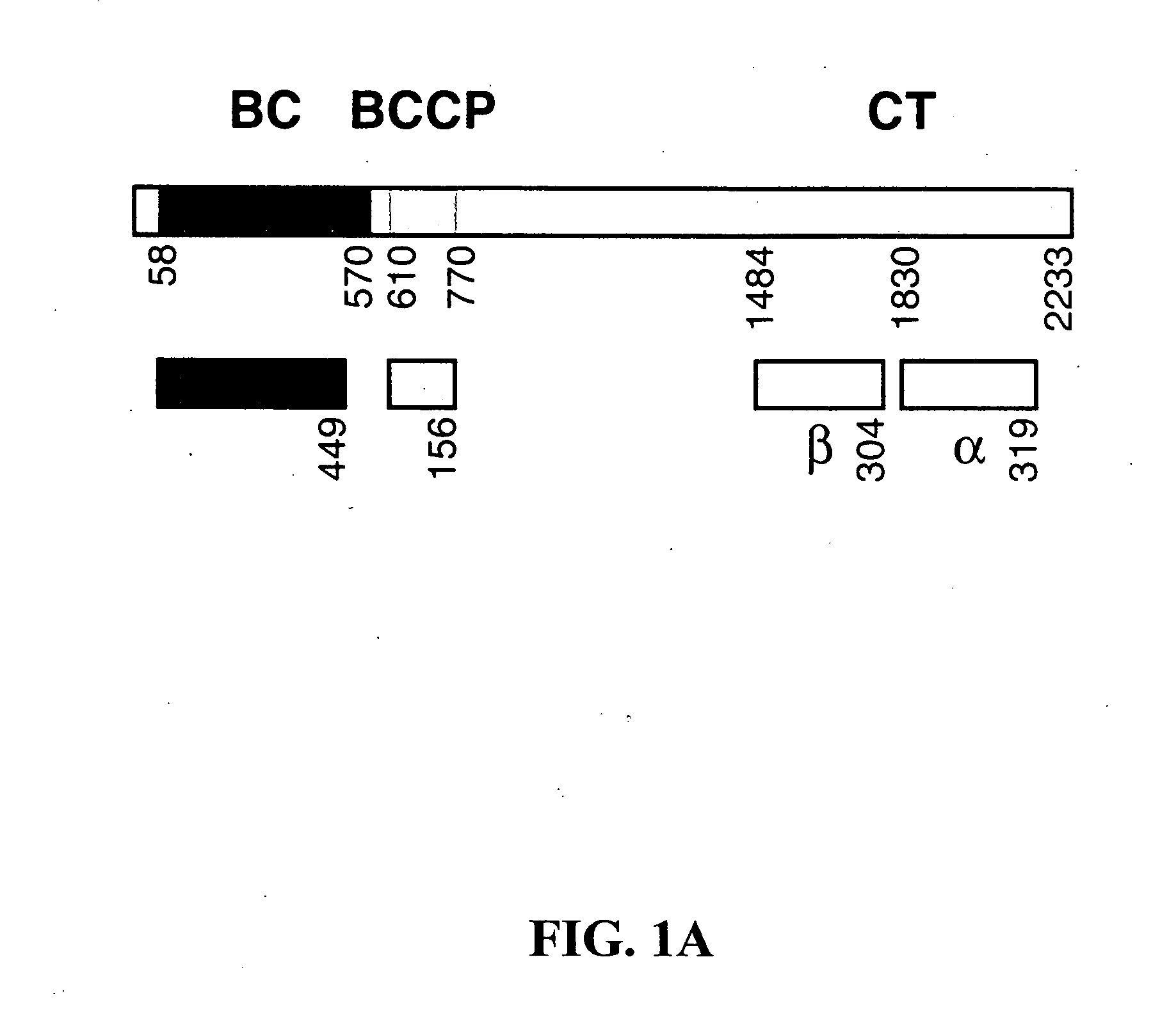
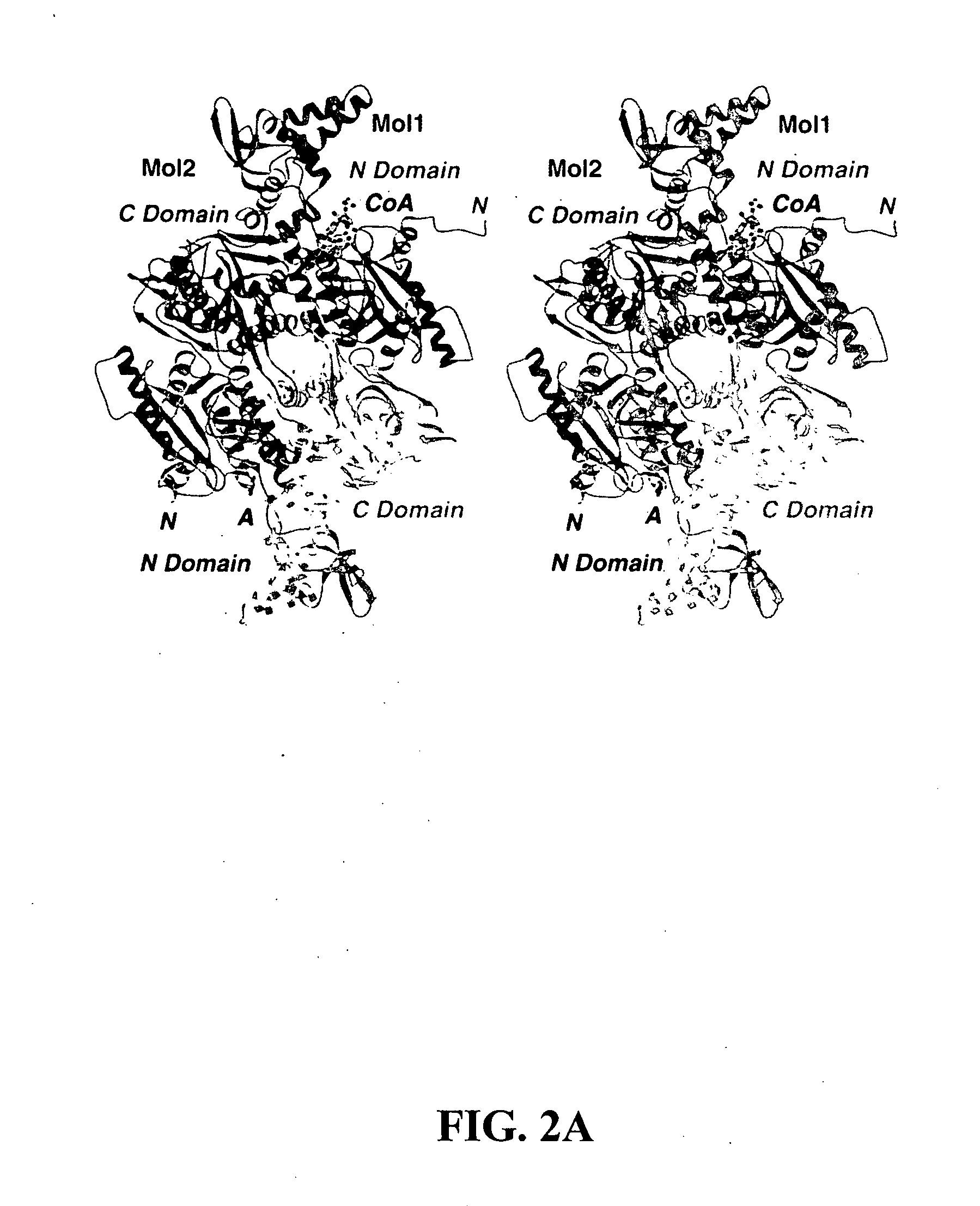
InactiveUS20050009163A1Increase and decreases acetyl-CoA carboxylase activityTransferasesPeptide preparation methodsX-rayCrystal structure
The present invention provides compositions and crystals of the carboxyltransferase (CT) domain (the C-terminal ˜90 kDa fragment) of various acetyl-CoA carboxylase (ACC) proteins, including yeast, mouse and human ACCs. Further, the present invention provides methods for identifying and designing compounds that can modulate ACC activity. These methods are based, in part, on the X-ray crystallographic structures of the CT domain of yeast ACC, either alone or bound to acetyl-CoA or a CT inhibitor, such as haloxyfop or diclofop or CP-640186. Thus, the present invention relates to the crystal structures of the carboxyltransferase (“CT”) domain of acetyl-CoA carboxylase (“ACC”), and to the use of these structures in the design of anti-obesity compounds, anti-diabetes compounds, antibiotic compounds, herbicide compounds, and in the design of herbicide resistant plants.
Owner:THE TRUSTEES OF COLUMBIA UNIV IN THE CITY OF NEW YORK
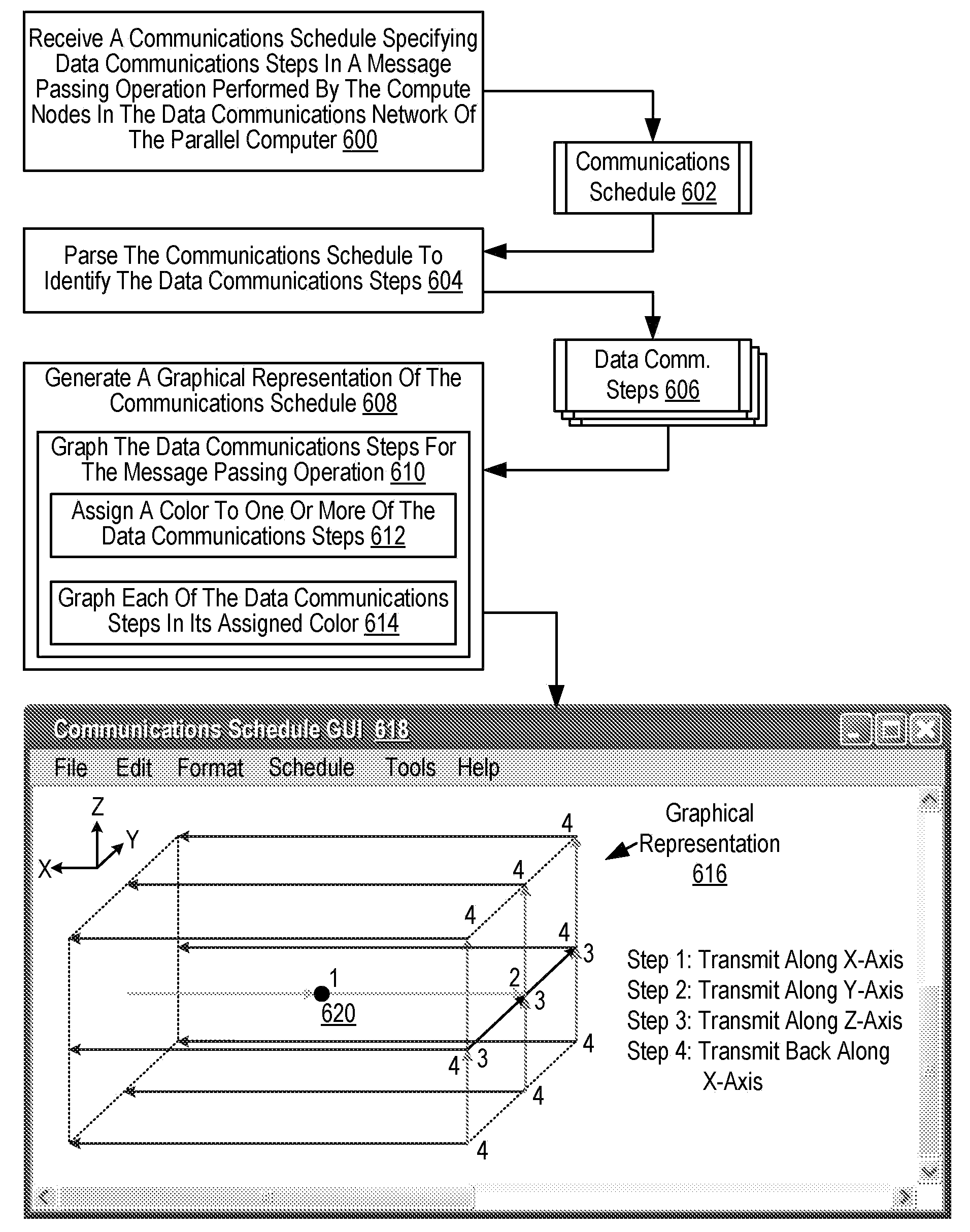
Administering Communications Schedules for Data Communications Among Compute Nodes in a Data Communications Network of a Parallel Computer
Methods, apparatus, and products are disclosed for creating and administering communications schedules for data communications among compute nodes in a data communications network of a parallel computer that include: receiving a communications schedule specifying data communications steps in a message passing operation performed by the compute nodes in the data communications network of the parallel computer; parsing the communications schedule to identify the data communications steps; and generating a graphical representation of the communications schedule, including graphing the data communications steps for the message passing operation.
Owner:IBM CORP
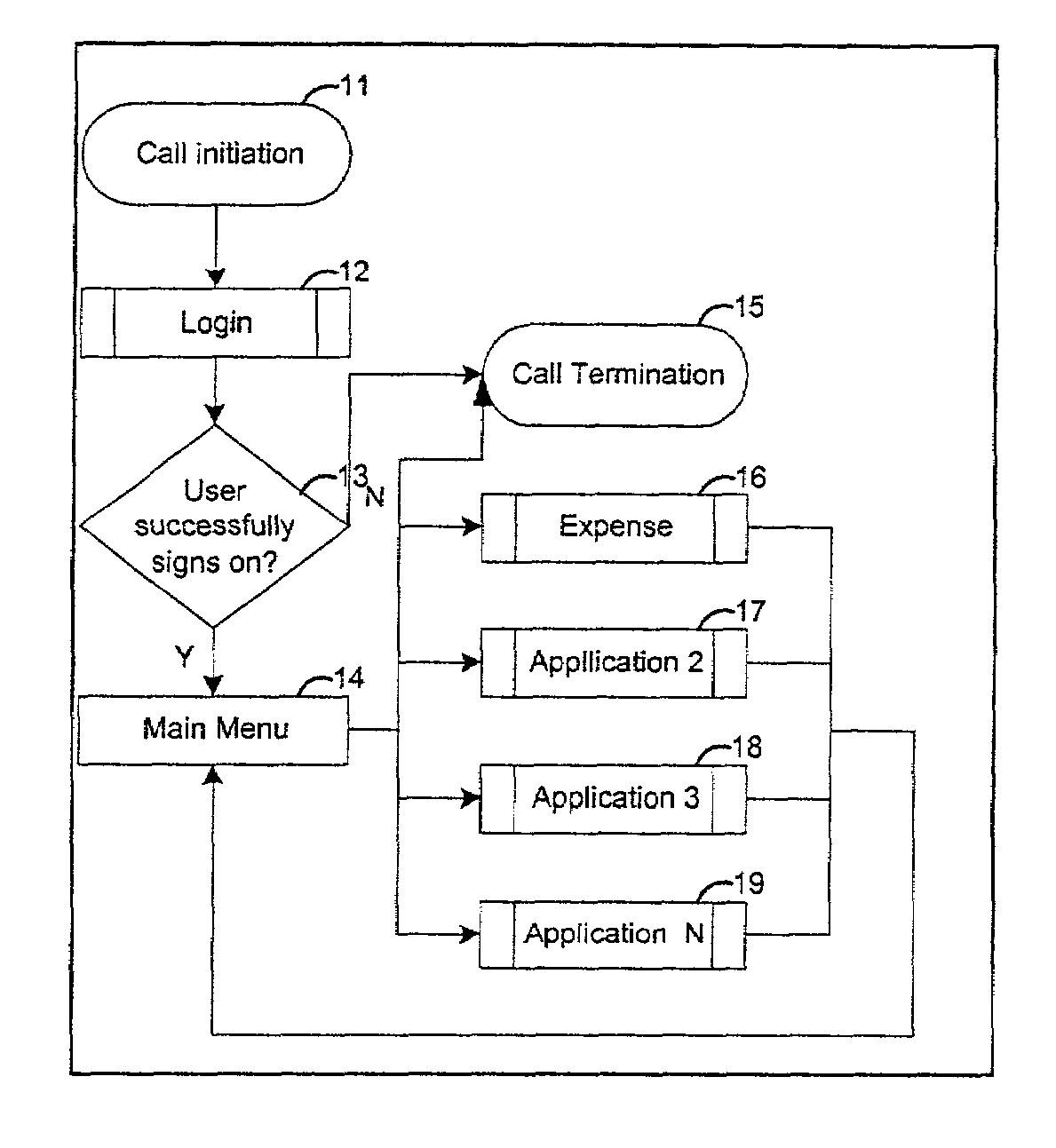
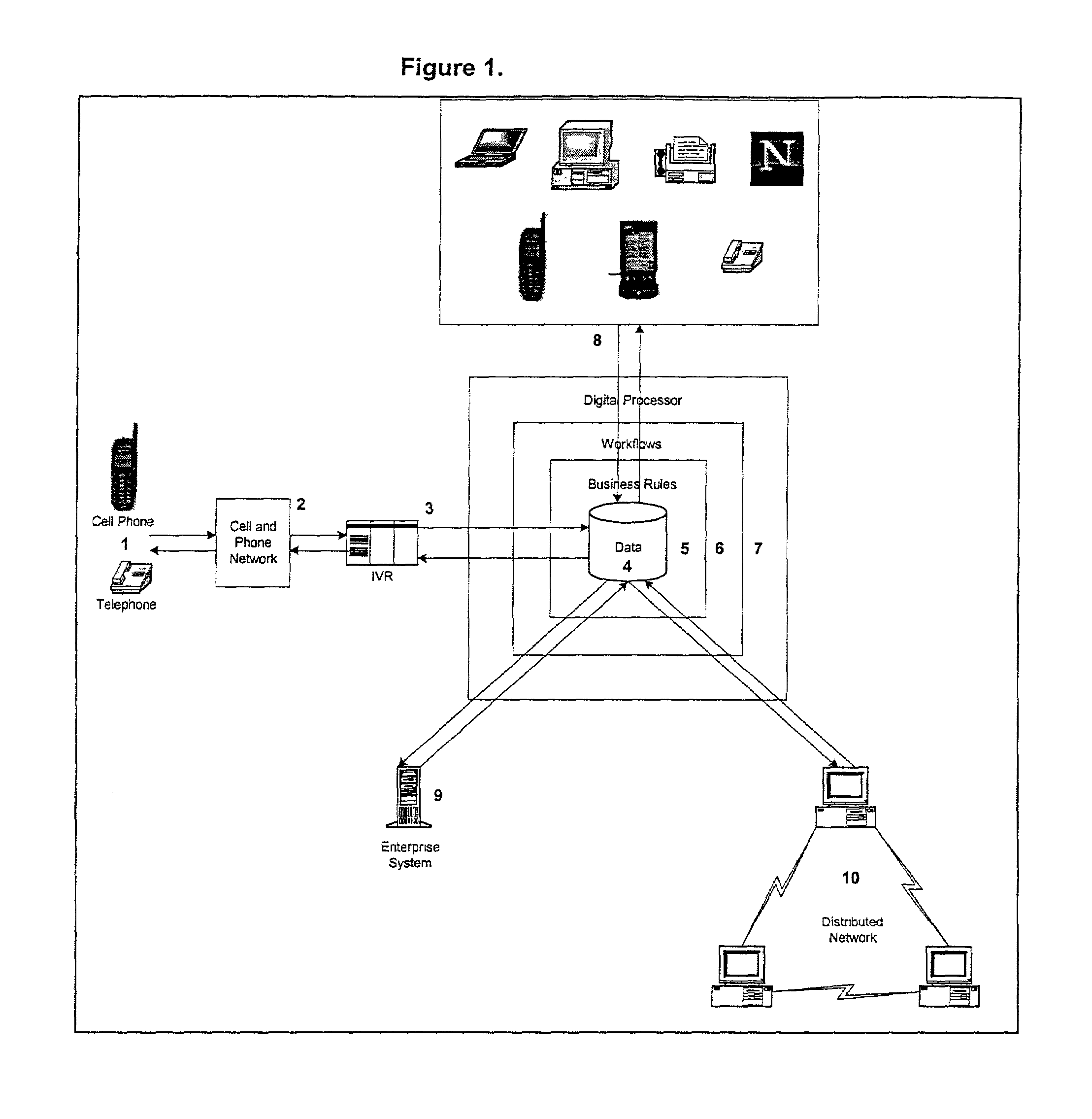
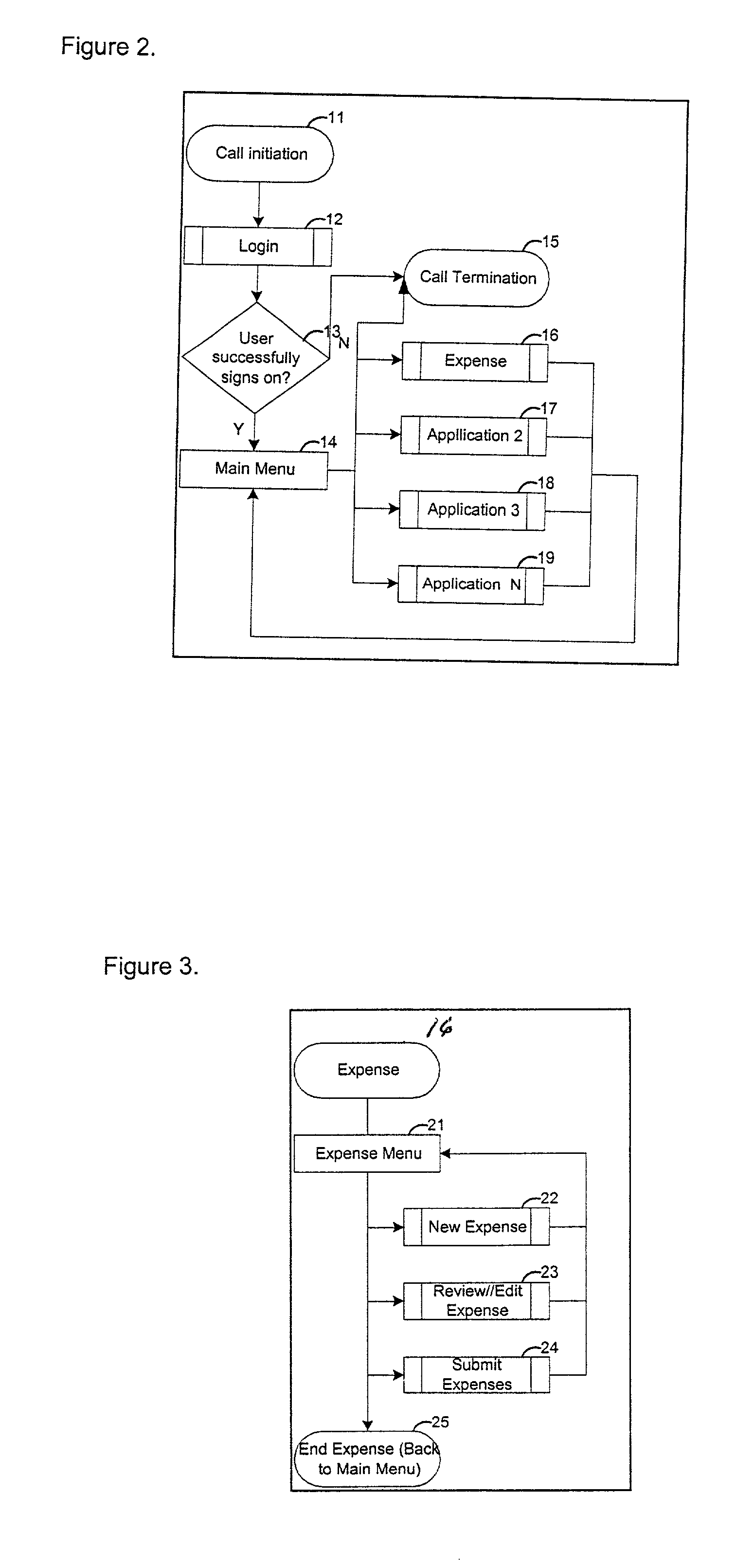
Computer accounting method using natural language speech recognition
InactiveUS7110952B2Saving of flexibilityShorten the timeComplete banking machinesFinanceElectronic mailPeer-to-peer
A computer method is disclosed for the capture, tracking, and management of accounting data using natural language speech recognition with landline or wireless telephones. Information is stored in a central or peer-to-peer database, which in addition to the speech recognition interface, may be accessed using touchtone telephone menus; Personal Digital Assistants (PDAs); WAP, RIM and other. wireless protocol phones and devices; the Web; fax; email and other messaging protocols; synchronizable off-line applications; corporate financial systems; and distributed networks. In one form, the user initiates a telephone call and the invention confirms the user's identification, prompts the user for accounting information, records the information provided by the user into the appropriate database and language if the user's native tongue is different than that used by the accounting system, and provides to the user information in response to inquiries using natural language speech recognition.
Owner:KURSH STEVEN R
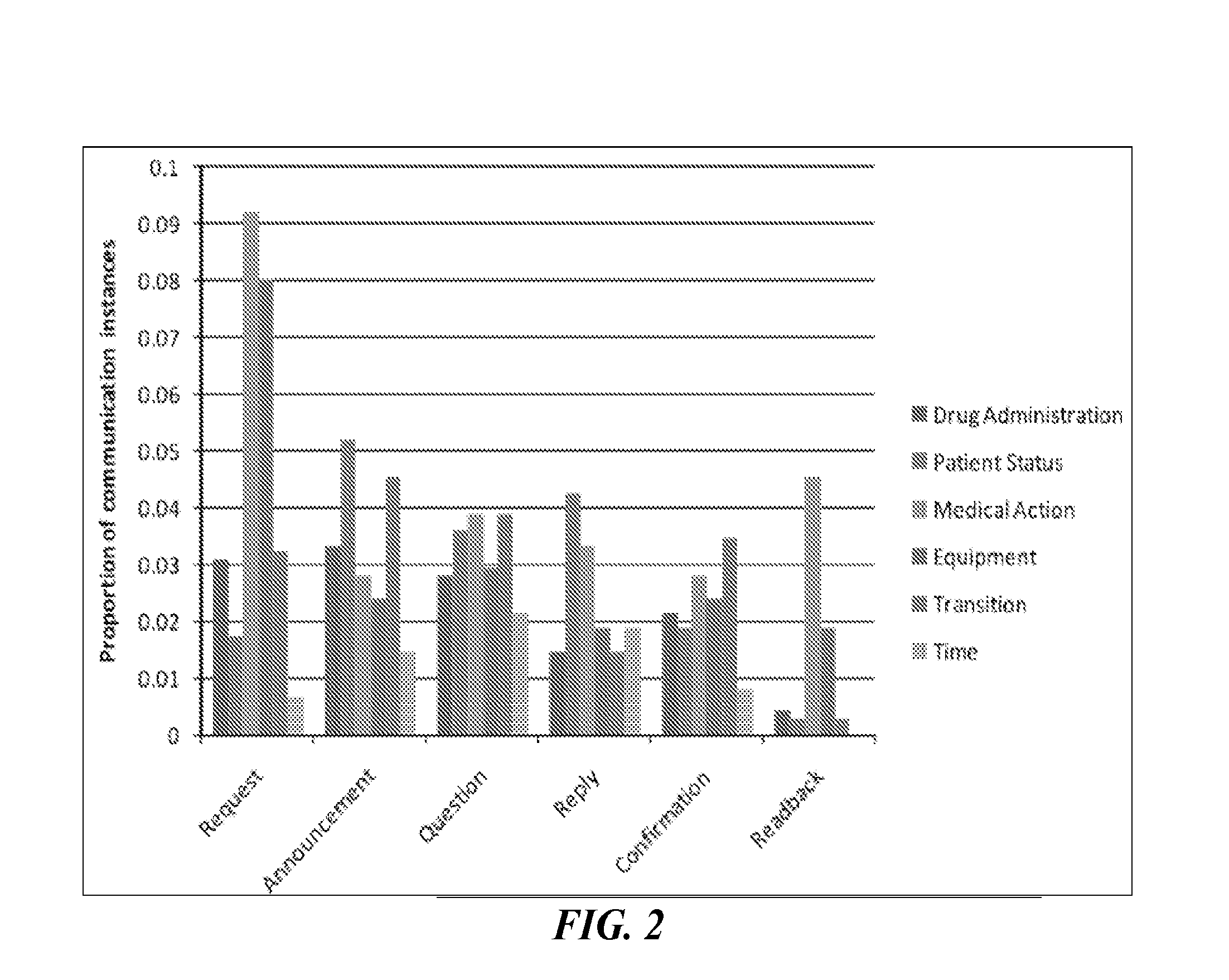
Computer implemented method, computer system and software for reducing errors associated with a situated interaction
InactiveUS20160246929A1Reduce errorsEnhanced Situational AwarenessMedical communicationTelevision system detailsComputerized systemComputer methods
A computer implemented method and computer system for reducing errors associated with a situated interaction performed by at least two agents of a sociotechnical team and for augmenting situation awareness of the at least two agents. Also, a non-transitory computer-readable storage medium used to store instructions relating to the computer method and the computer system. The situated interaction can be surgery and the at least two agents can be members of a surgical team.
Owner:U S GOVERNMENT REPRESENTED BY THE DEPT OF VETERANS AFFAIRS +1
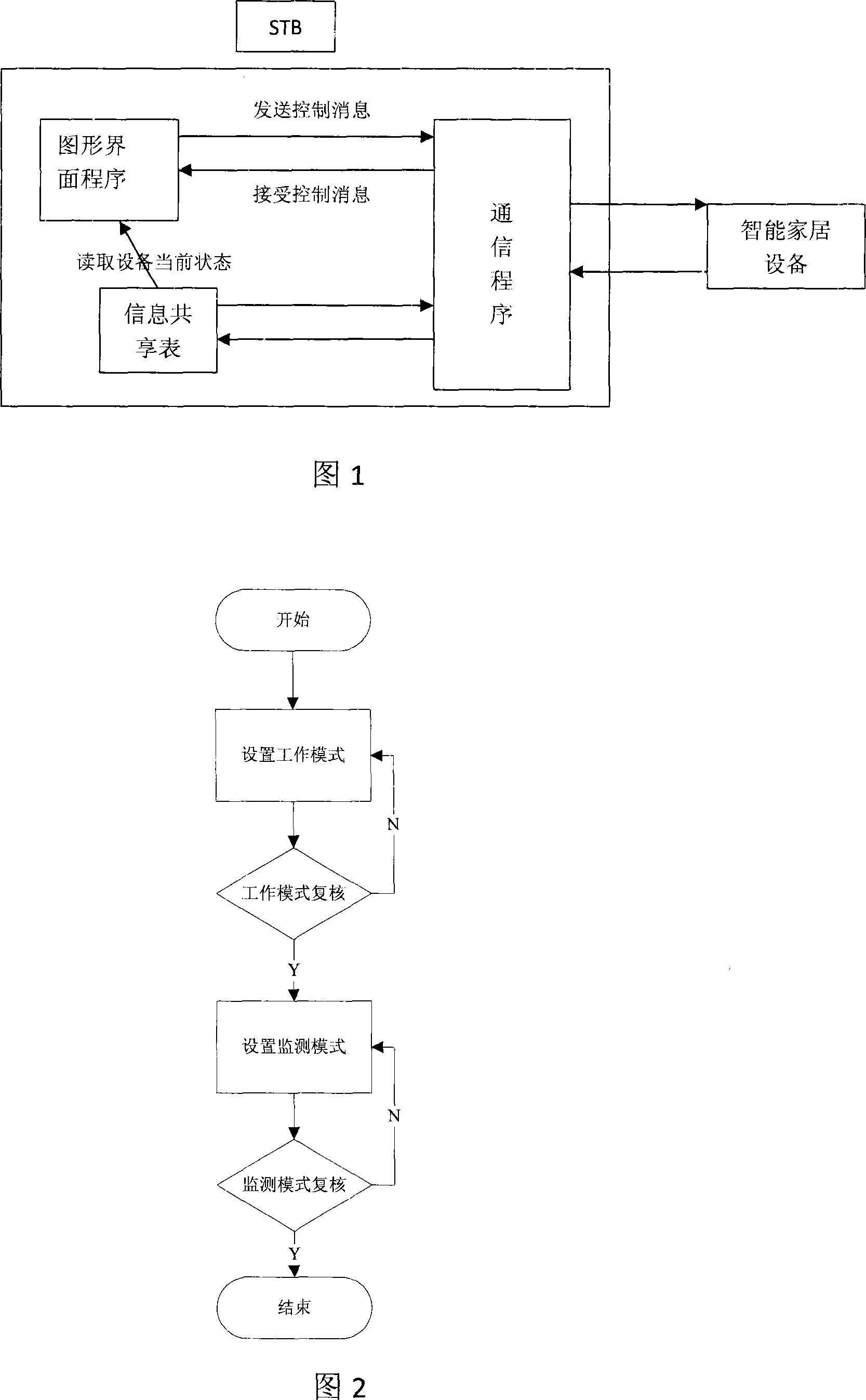
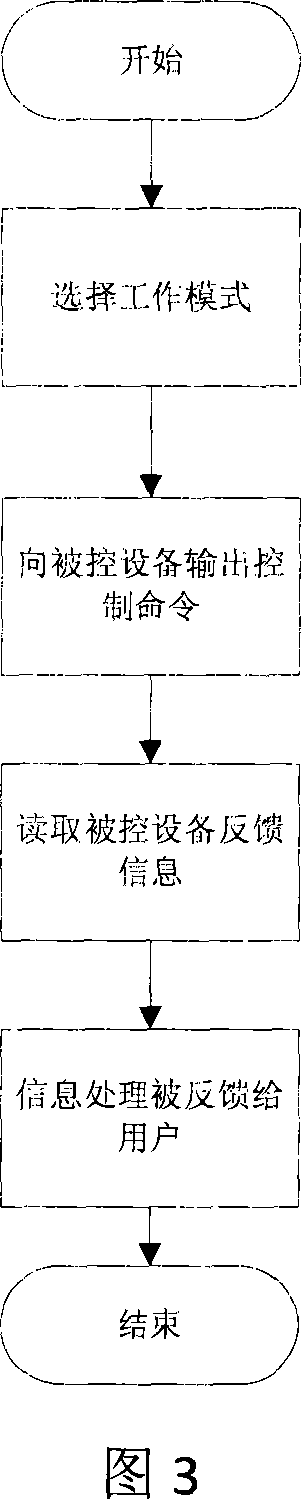
Intelligent household networking structure containing set-top box and its operation method
InactiveCN101247301ASolve the costSolve real-timeTelevision system detailsColor television detailsComputer methodsNetwork interface
The invention provides an intelligence household group network structure with set-top box and its operation method. The group network structure consists of the set-top box and intelligence household equipment through network connection. The set-top box is provided with a network joint connected with the intelligence household equipment and the memory of the set-top box divides a special storage area as intelligence household information. The invention adopts the set-top box to control the intelligence household equipment, which saves abundant funds for users and saves plentiful energy for society, finally realizing the effects of easy use, easy monitoring and convenience for users. The invention effectively resolves the problem of high cost and difficulty for realizing real-time monitoring by adopting computer method to household equipment and inconvenient operation by controlling the household equipment respectively.
Owner:罗笑南
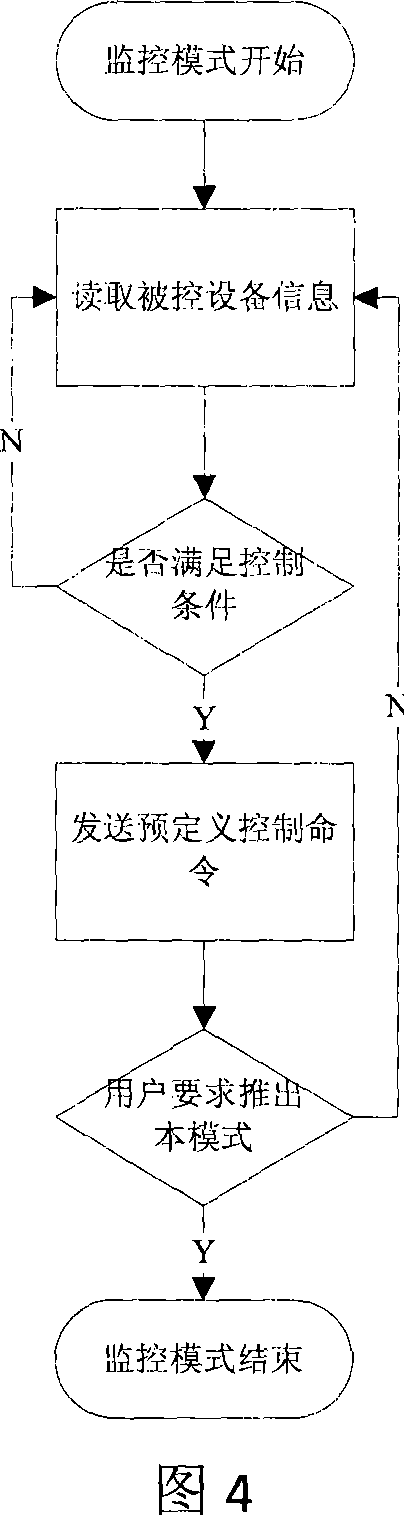
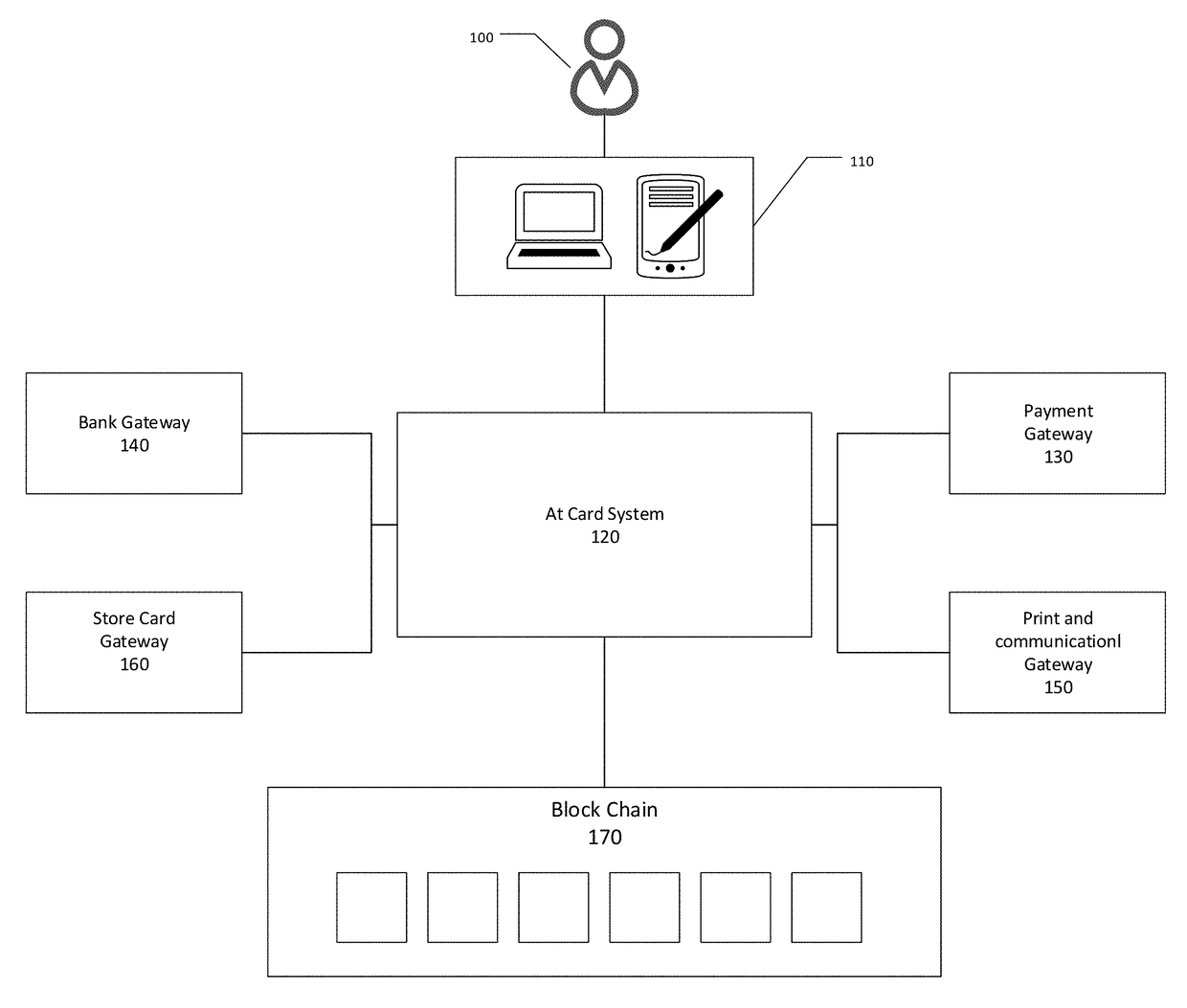
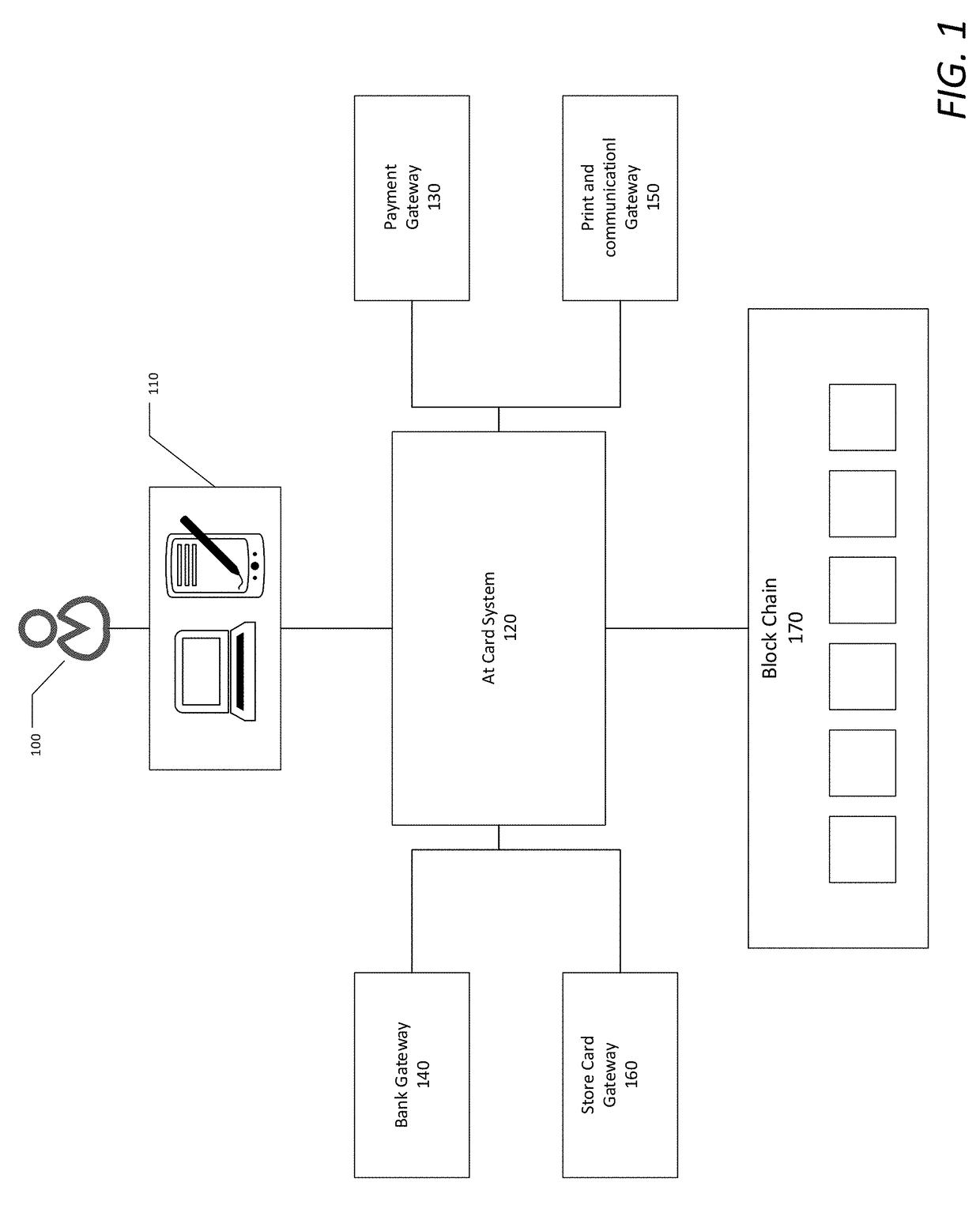
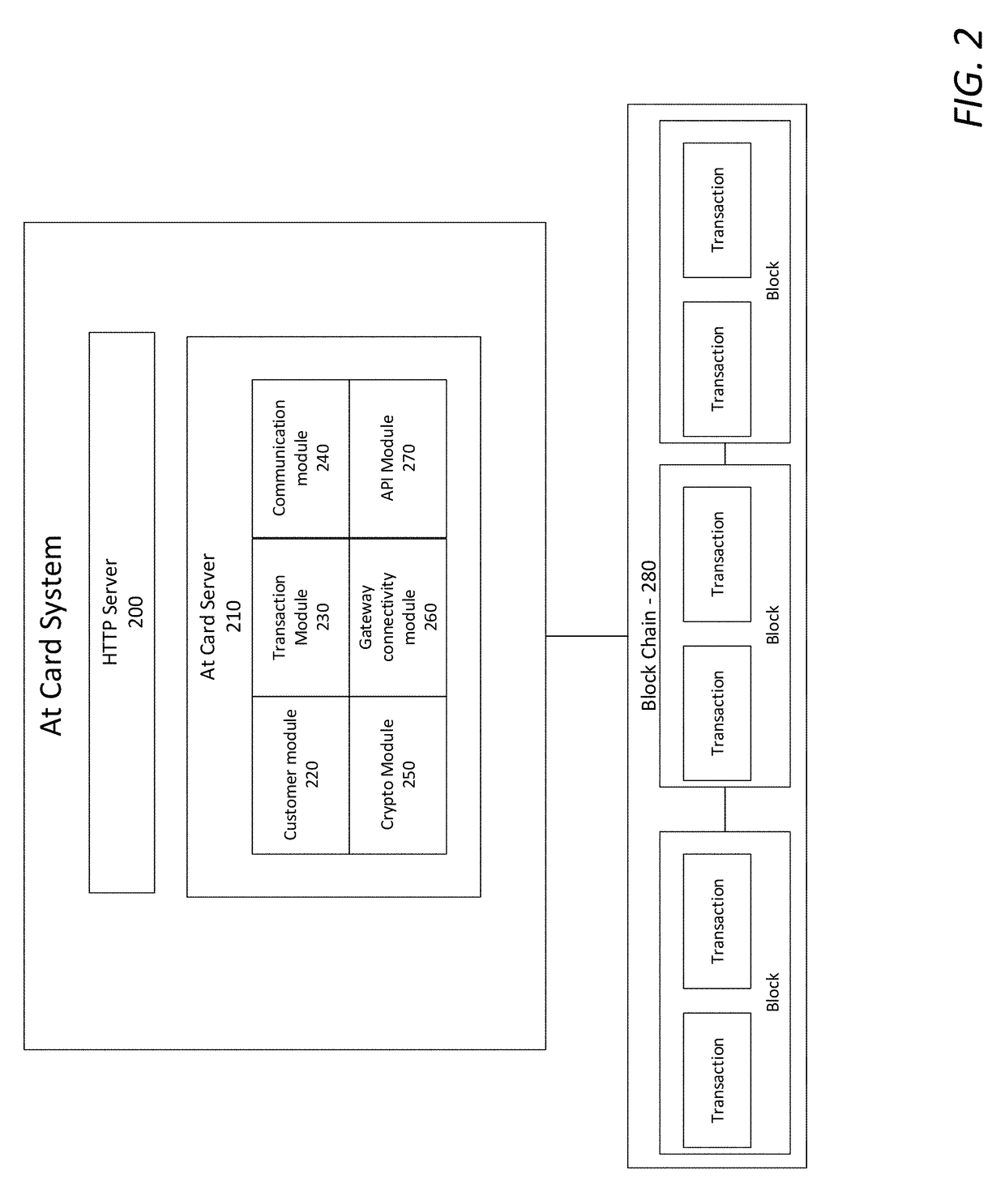
System and the computer methods of issuing, transferring and manipulating value or gift cards using blockchain technology
The described invention consists of system and the computer methods of generating and manipulating value or gift cards which are cryptographically assigned to a person's identity and stored on double entry ledger called block chain. A functional module of the system allows the transfer of such value or gift cards to other persons. The functional module in the system further allows a person owning a card to split it into multiple value or gift cards, merge more than one value or gift cards to a single card, exchange a value or gift card with a specific merchant card, redeem a value or gift card at a store front in exchange for physical or digital good or cash it out in the currency it was issued. Each transaction associated with a customer is cryptographically signed and stored on the block chain.
Owner:ANSARI AKBAR ALI
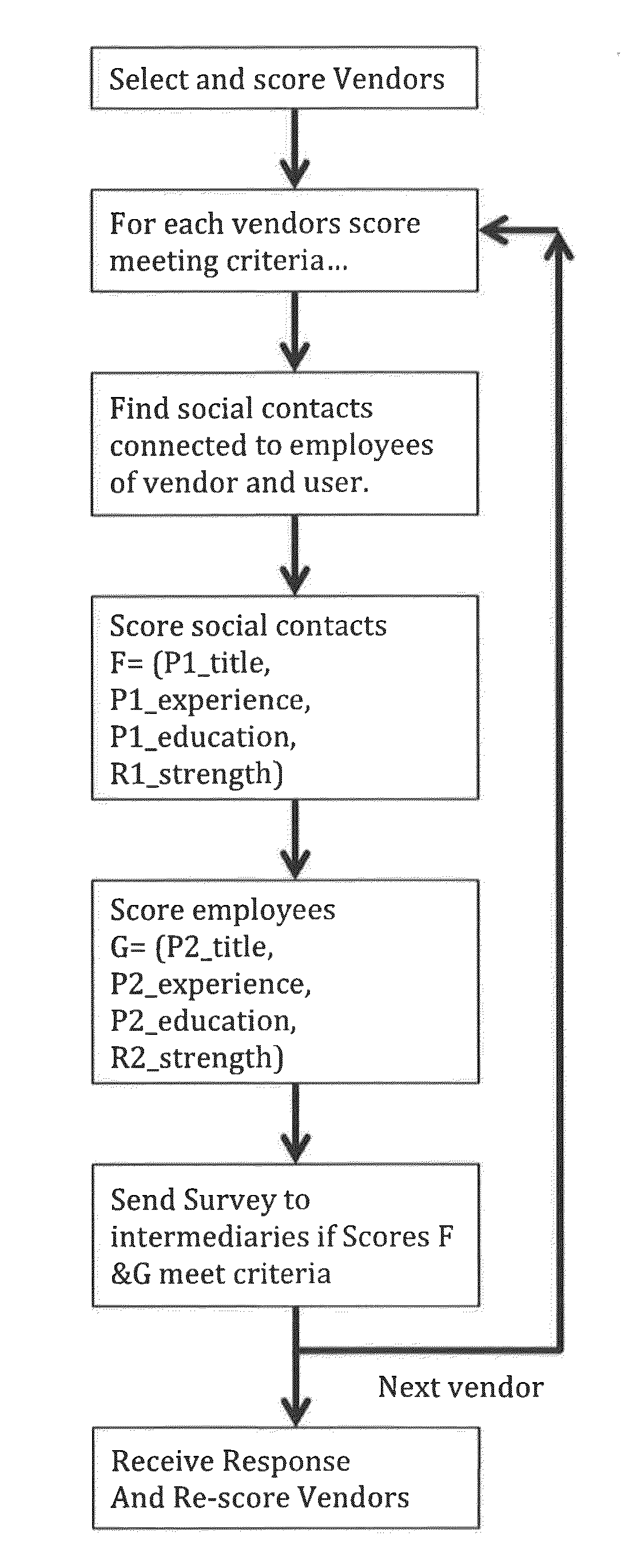
Social Proof of Organizations
InactiveUS20160148222A1Special data processing applicationsMarket data gatheringComputer methodsSocial web
A computer method and system provide means for inputting and outputting business relationship data to a user. The system comprises a database of business relationships between organizations, which is connectable to a social network. A user may search for an organization according to search criteria and the system will select a set of organizations that match the criteria along with a set of social contacts of the user. The relevancy of the social contacts to the organization is calculated and web content is displayed showing the organizations and social contacts.
Owner:0934781 B C
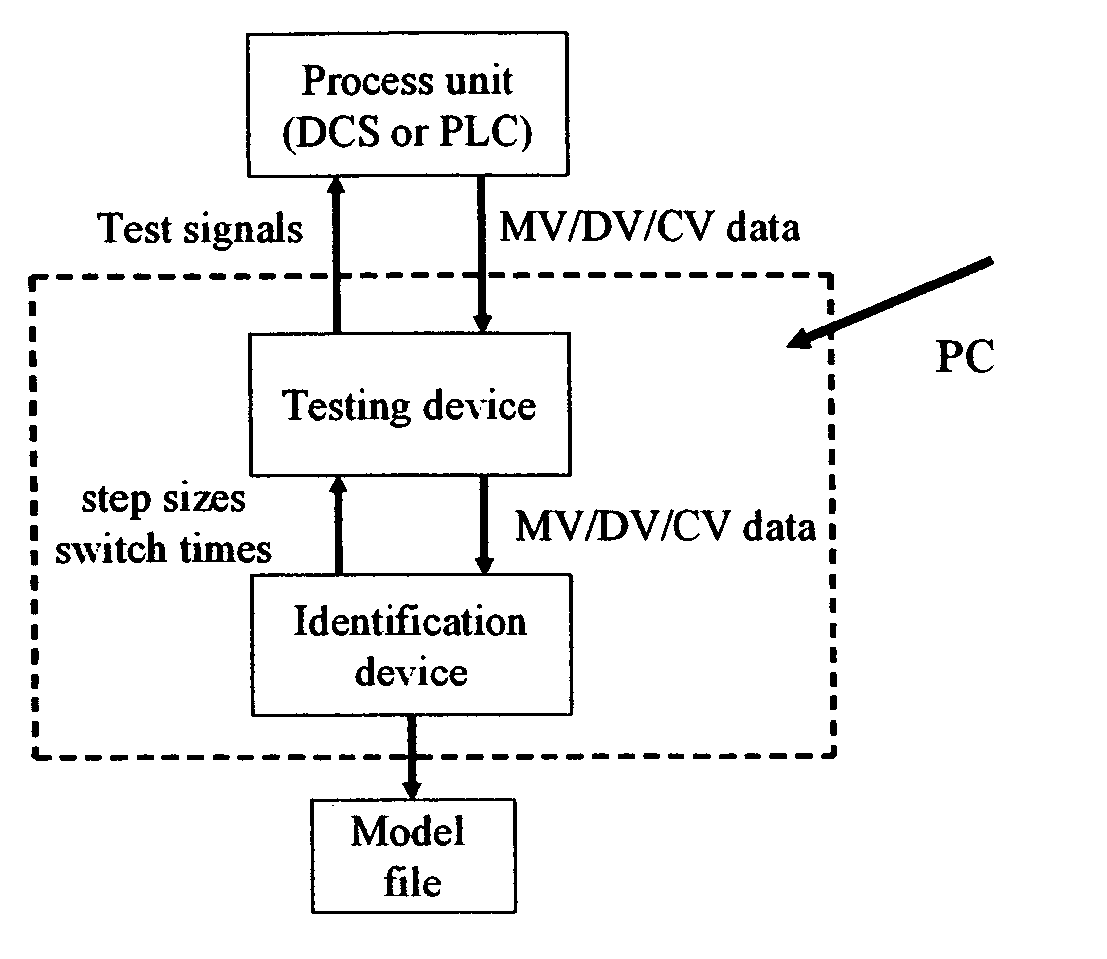
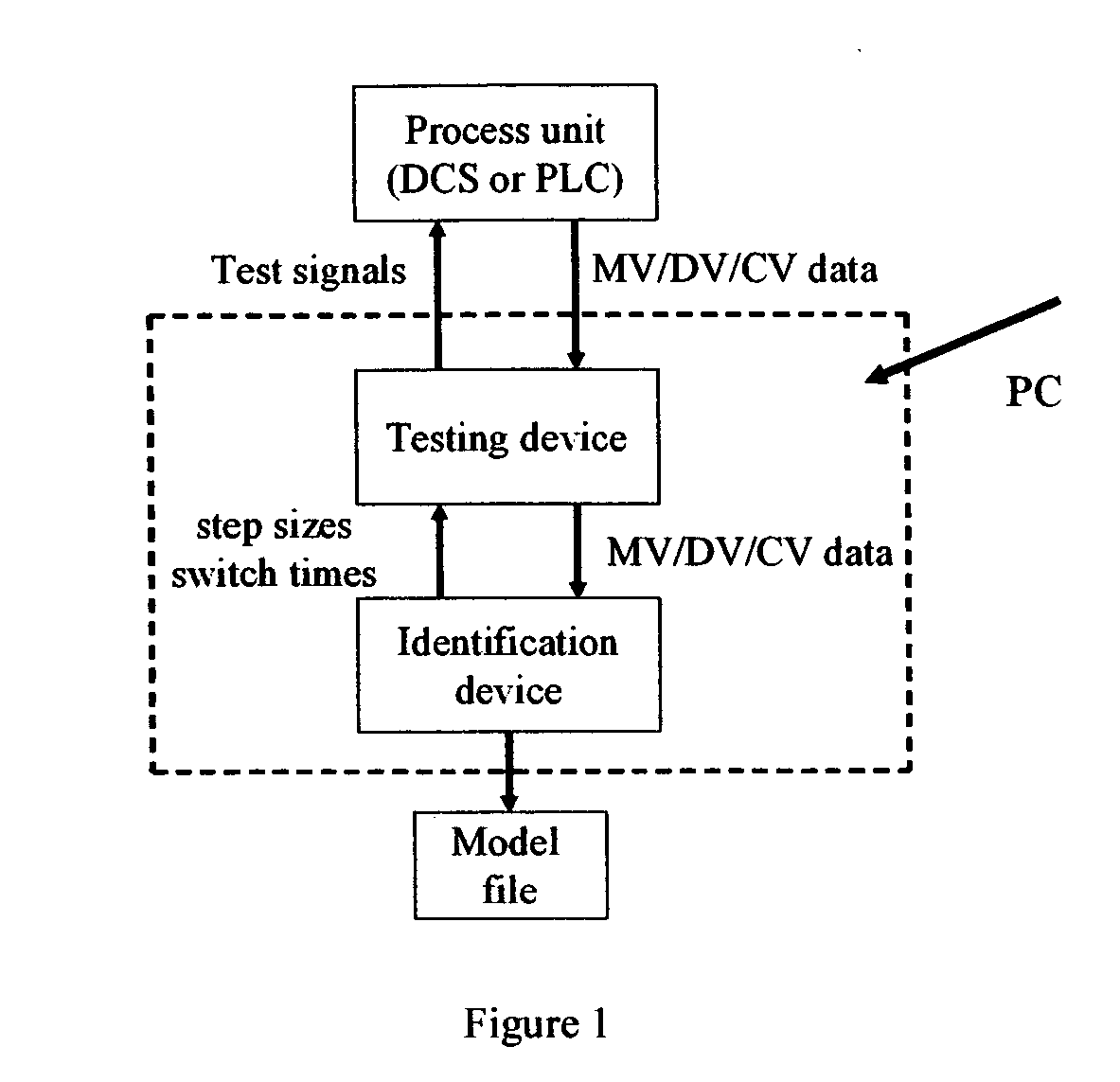
Computer method and apparatus for online process identification
InactiveUS20060111858A1Small sizeReduce stepsSimulator controlElectrical measurementsClosed loopPredictive controller
A computer method and apparatus of online automated model identification of multivariable processes is disclosed. The method and apparatus carries out automatically all the four basic steps of industrial process identification: 1) identification test signal design and generation, 2) identification plant test, 3) model identification and 4) model validation. During the automated plant test, process models will be automatically generated at a given time interval, for example, every hour, or on demand; the ongoing test can be automatically adjusted to meet the process constraints and to improve the data quality. Plant test can be in open loop operation, closed-loop operations or partly open loop and partly closed-loop. In a (partial) closed-loop plant test, any type of controller can be used which include proportional-integral-derivative (PID) controllers and any industrial model predictive controller (MPC). The obtained process models can be used as the model in advanced process controllers such as model predictive control (MPC) and linear robust control; they can also be used as inferential models or soft sensors in prediction product qualities. The apparatus can be used in new MPC controller commissioning as well as in MPC controller maintenance.
Owner:ZHU YUCAI
Computer method and system providing design of an assembly modeled by a graph
The invention provides a computer-implemented method and system intended for designing an assembly of a plurality of objects. The assembly is modeled by a directed acyclic modeling graph having nodes and arcs. Each node represents an object of the assembly. Each arc represents the use of an end node by an origin node. At least one arc is uniquely identified by an identifier. The assembly is further modeled by at least one relation having at least one tuple containing a first chain of at least one identifier. The method comprises the step of determining at least one mapping between the first chain and a second chain of at least one identifier as well as the step of substituting at least one occurrence of the first chain in the tuple of the relation with the second chain. The invention provides this way a means to repair broken tuples automatically and thus to facilitate design.
Owner:DASSAULT SYSTEMES
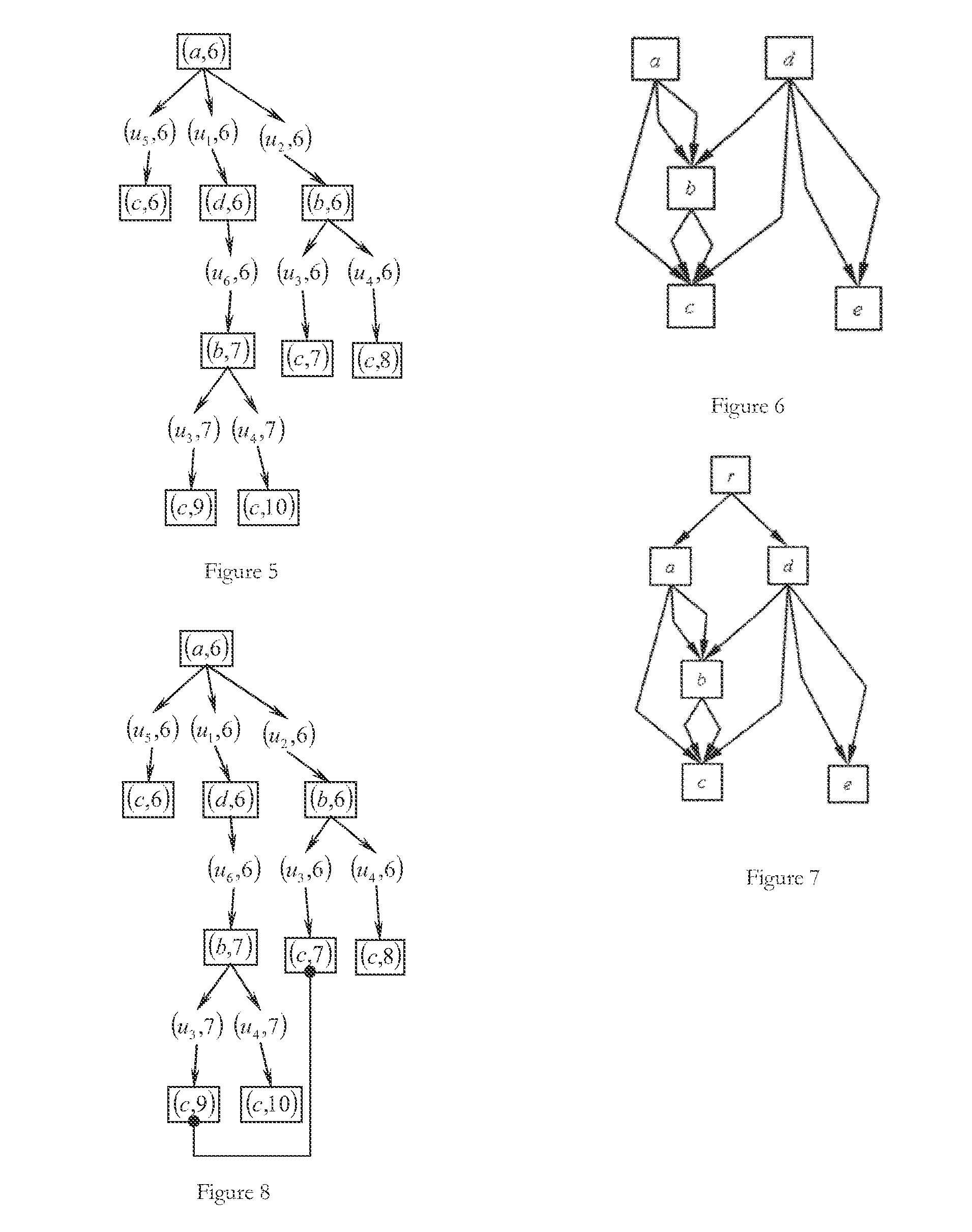
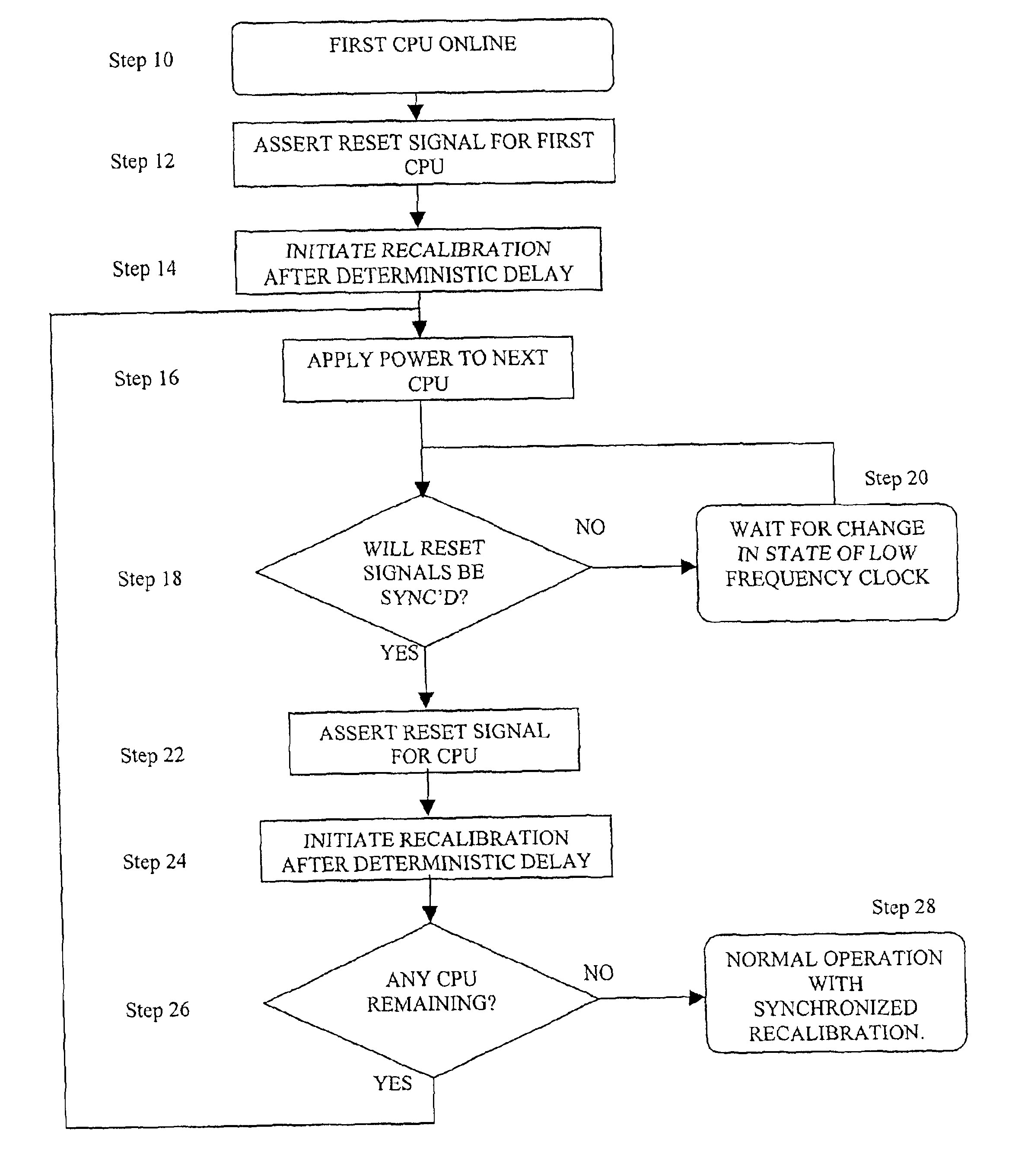
Coordinated recalibration of high bandwidth memories in a multiprocessor computer
Methods and apparatus for implementing high-bandwidth memory subsystems in a multiprocessor computing environment. Each component in the memory subsystem has a recalibration procedure. The computer provides a low-frequency clock signal with a period substantially equal to the duration between recalibration cycles of the components of the memory subsystem. Transitions in the low-frequency clock signal initiate a deterministically-determined delay. Lapse of the delay in turn triggers the recalibration of the components of the memory subsystem, ensuring synchronous recalibration. Synchronizing the recalibration procedures minimizes the unavailability of the memory subsystems, consequently reducing voting errors between CPUs.
Owner:STRATUS TECH IRELAND LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com