Control method for processing teleoperation system under DOS attack
An operating system and control method technology, applied in the field of teleoperation, can solve the problems of uncertainty of model parameters, time-varying delay, and complex bilateral control problems of teleoperating systems, so as to meet the requirements of transient performance and reduce the risk of being attacked. effect of probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
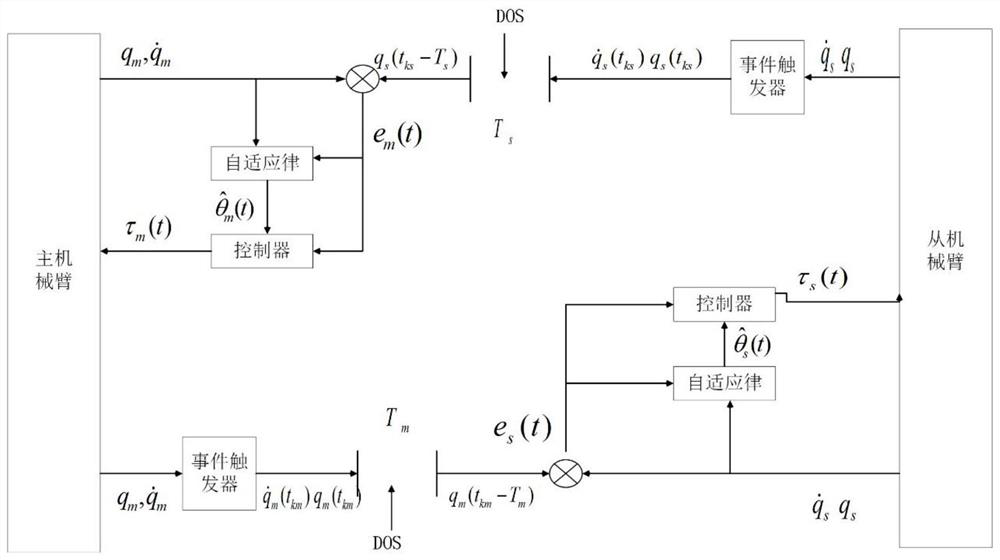
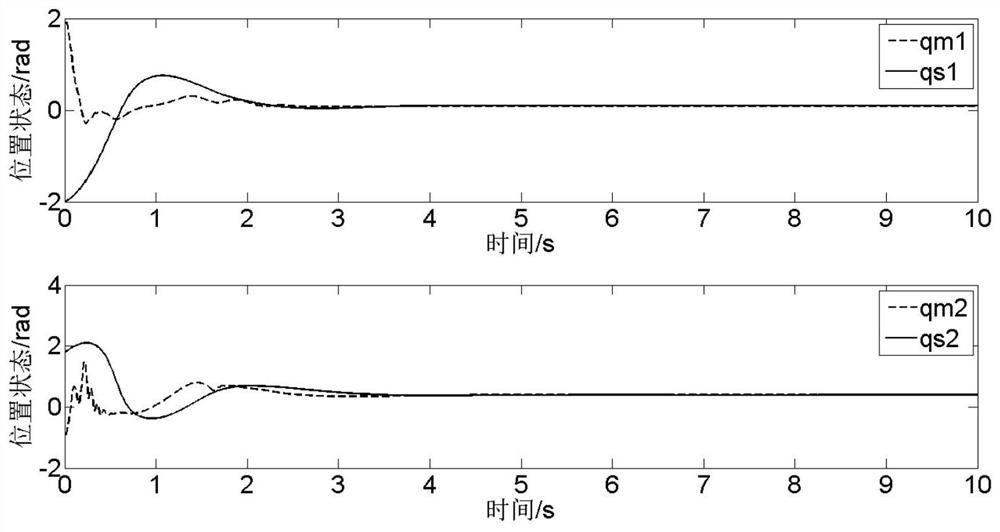
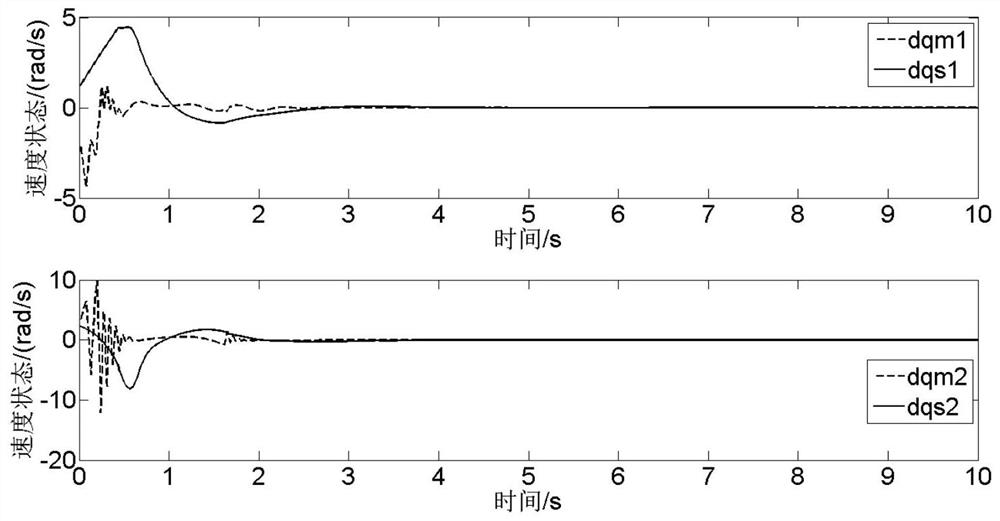
[0066] This embodiment is a simulation research on the stable tracking of the remote operating system with uncertain model parameters and time-varying time delay under DOS attack. Such as figure 1 As shown, the specific steps are as follows:
[0067] Step 1. Establish a teleoperation system dynamics model
[0068] In this embodiment, two two-degree-of-freedom and two-link manipulators are used as the simulation objects of the teleoperation system, and the commonly used Euler-Lagrange equation is used to describe the dynamics of the manipulators:
[0069] master end:
[0070] From the end:
[0071] The expressions of each matrix in the robotic arm are as follows:
[0072]
[0073]
[0074]
[0075]
[0076]
[0077]
[0078]
[0079]
[0080]
[0081] C i22 =0
[0082] g i1 =-(m 1 +m 2 )gl 1 sin(q i1 )+m 2 gl 2 sin(q i1 +q i2 )
[0083] g i2 = m 2 gl 2 sin(q i1 +q i2 )
[0084] Among them, m 1 Indicates the mass of connectin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com