Improved forest algorithm-based Android malicious software detection method
A malware and forest algorithm technology, applied in the field of software security, can solve problems such as insufficient detection accuracy, high algorithm complexity, and complex technical implementation, and achieve the effect of reducing the probability of being attacked, high classification accuracy, and improving the accuracy rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but the following embodiments in no way limit the present invention.
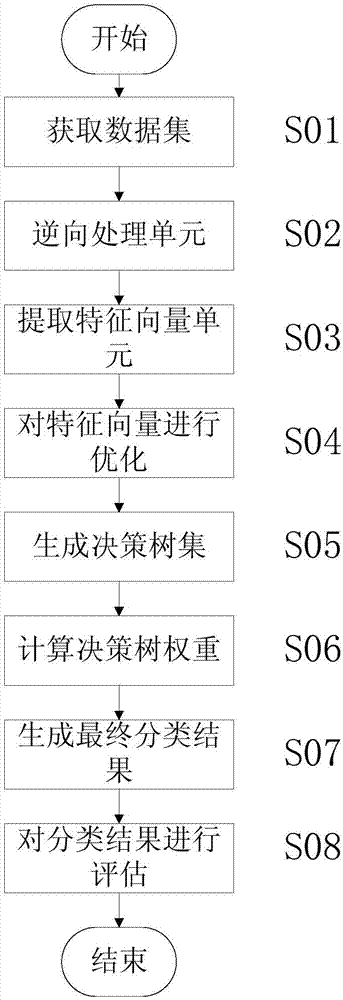
[0027] Such as figure 1 As shown, the Android malware detection method based on the improved forest algorithm includes the following steps in order:
[0028] 1) The S01 stage of obtaining the data set: obtain the installation package files of benign software and malicious software from the application store, other network forums or research institutions, and then enter the S02 stage;
[0029] 2) S02 stage of reverse processing: decompile each installation package file obtained in step 1) respectively to obtain a decompiled folder containing AndroidManifest.xml file, and use the xml.dom module and IO module in Python language to pair The AndroidManifest.xml file is parsed to obtain the attributes of the Permission tag and the Intent tag, and then enter the S03 stage;
[0030]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com