Method and device for writing safety verification
A security verification and handwriting technology, applied in the fields of digital data authentication, character and pattern recognition, special data processing applications, etc., can solve the problems of complex technical solutions, low safety factor, large investment, etc., to reduce the probability of hacker attacks, The effect of improving safety and ensuring simplicity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
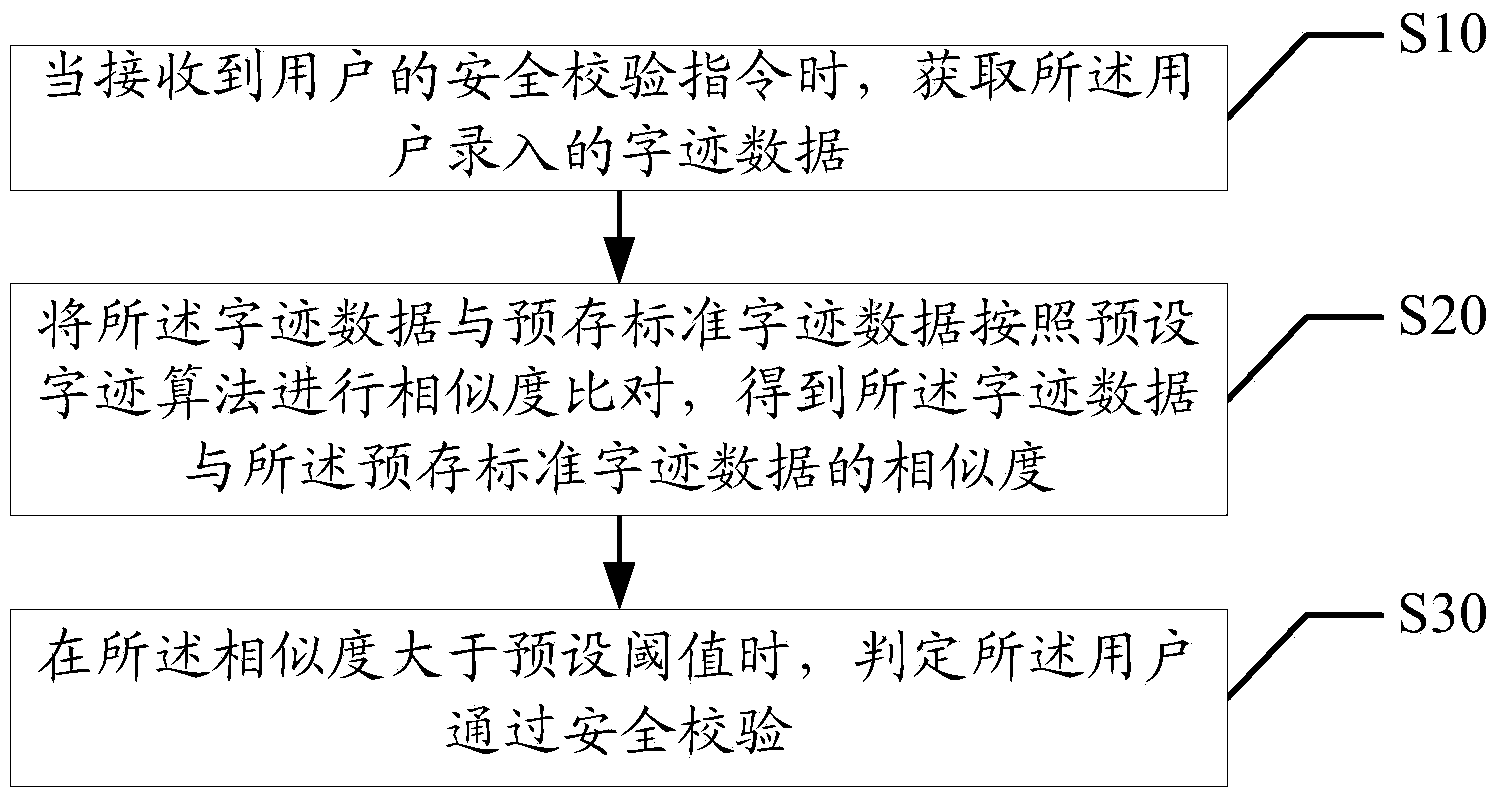
[0048] like figure 1 As shown, it is a schematic flow chart of the first embodiment of the handwriting security verification method of the present invention.
[0049] It should be emphasized that: figure 1 The flow chart shown is only a preferred embodiment, and those skilled in the art should know that any embodiment constructed around the idea of the present invention should not deviate from the scope covered by the following technical solutions:
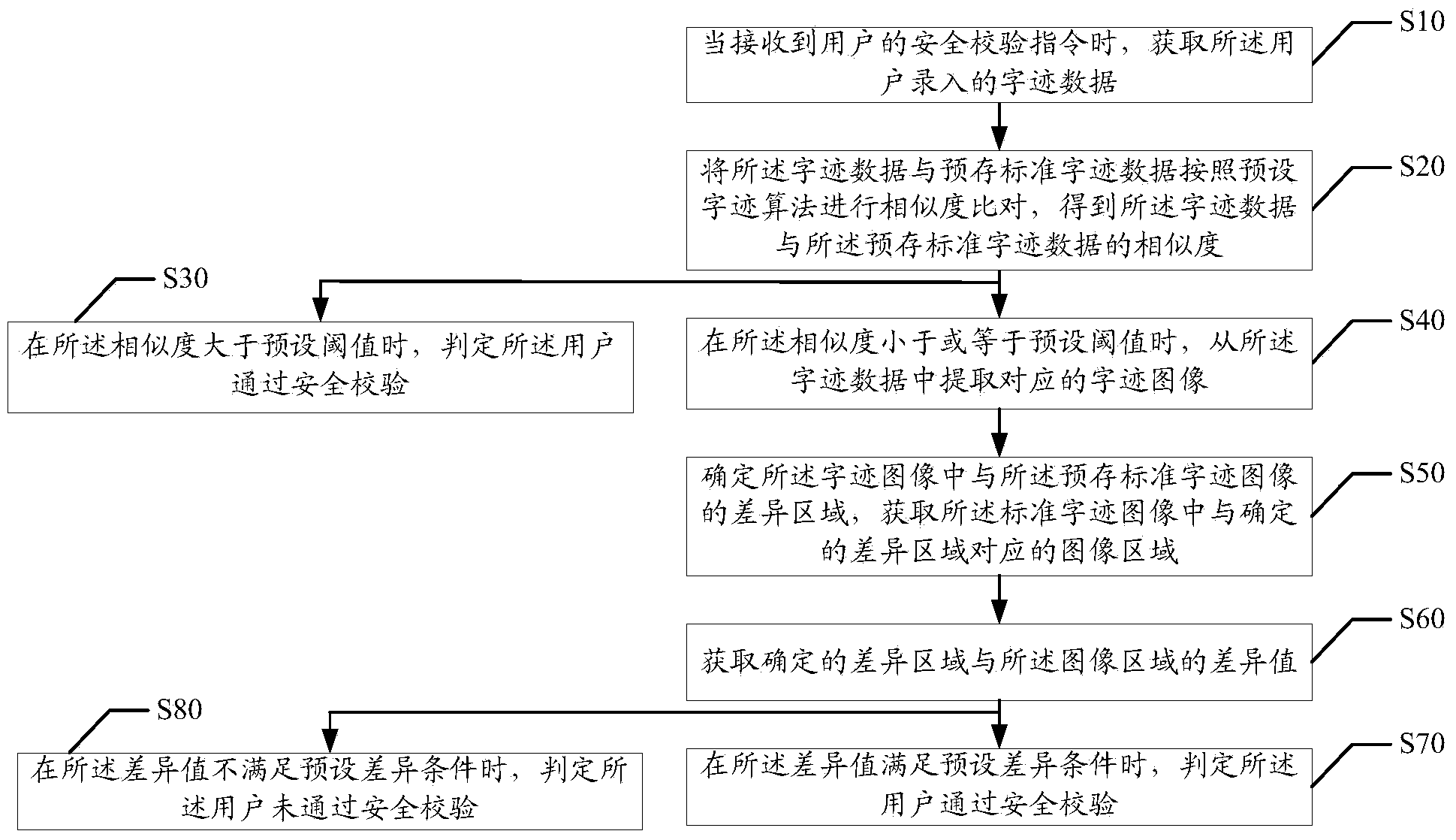
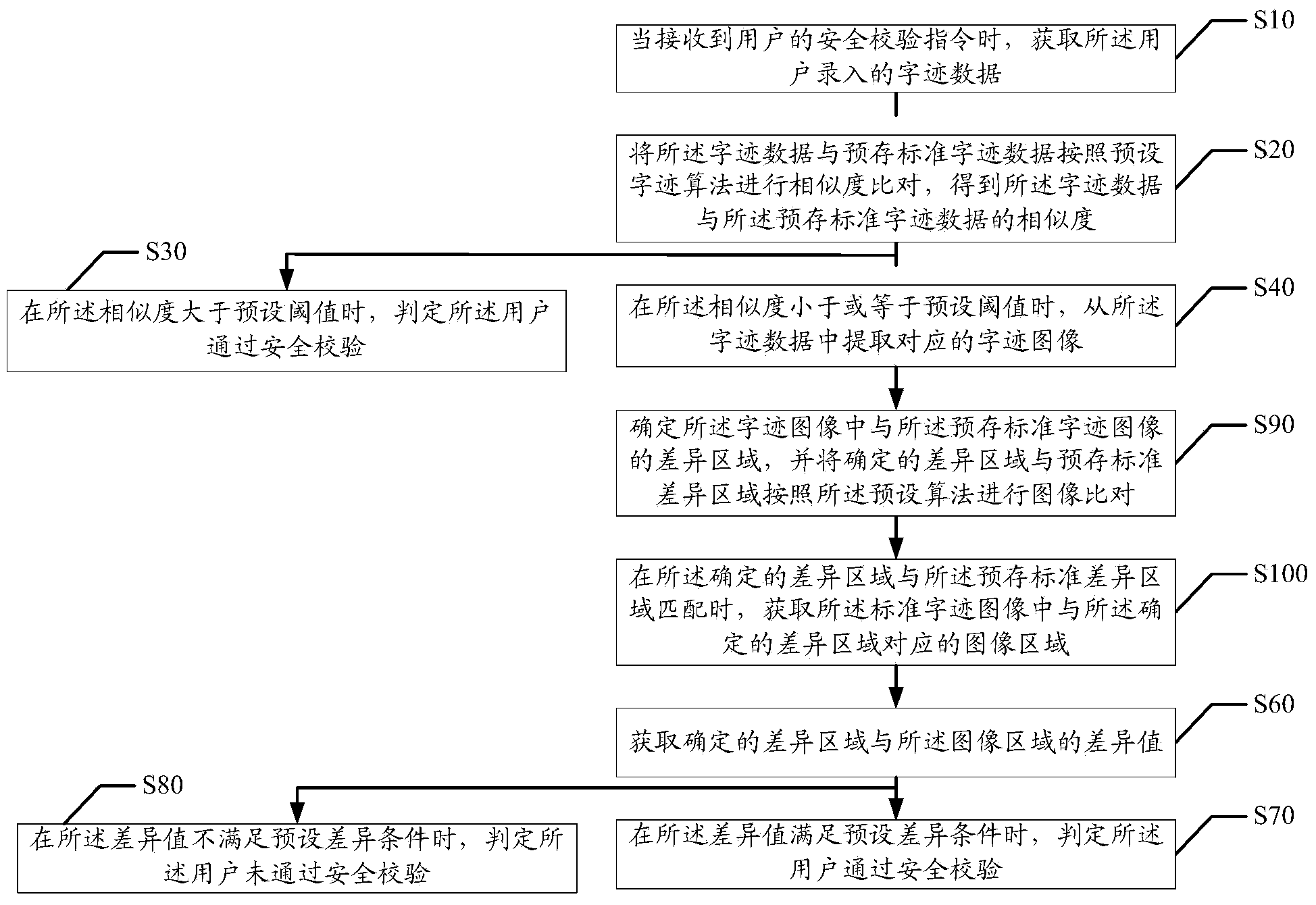
[0050] When receiving the user's security verification instruction, obtain the handwriting data entered by the user; compare the similarity between the handwriting data and the pre-stored standard handwriting data according to the preset handwriting algorithm, and obtain the handwriting data and the pre-stored The similarity of standard handwriting data; when the simi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com