Terminal control method, terminal and computer readable storage medium
A terminal control and terminal technology, applied in computing, instruments, digital data authentication, etc., can solve problems such as difficulty in one-handed operation of users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
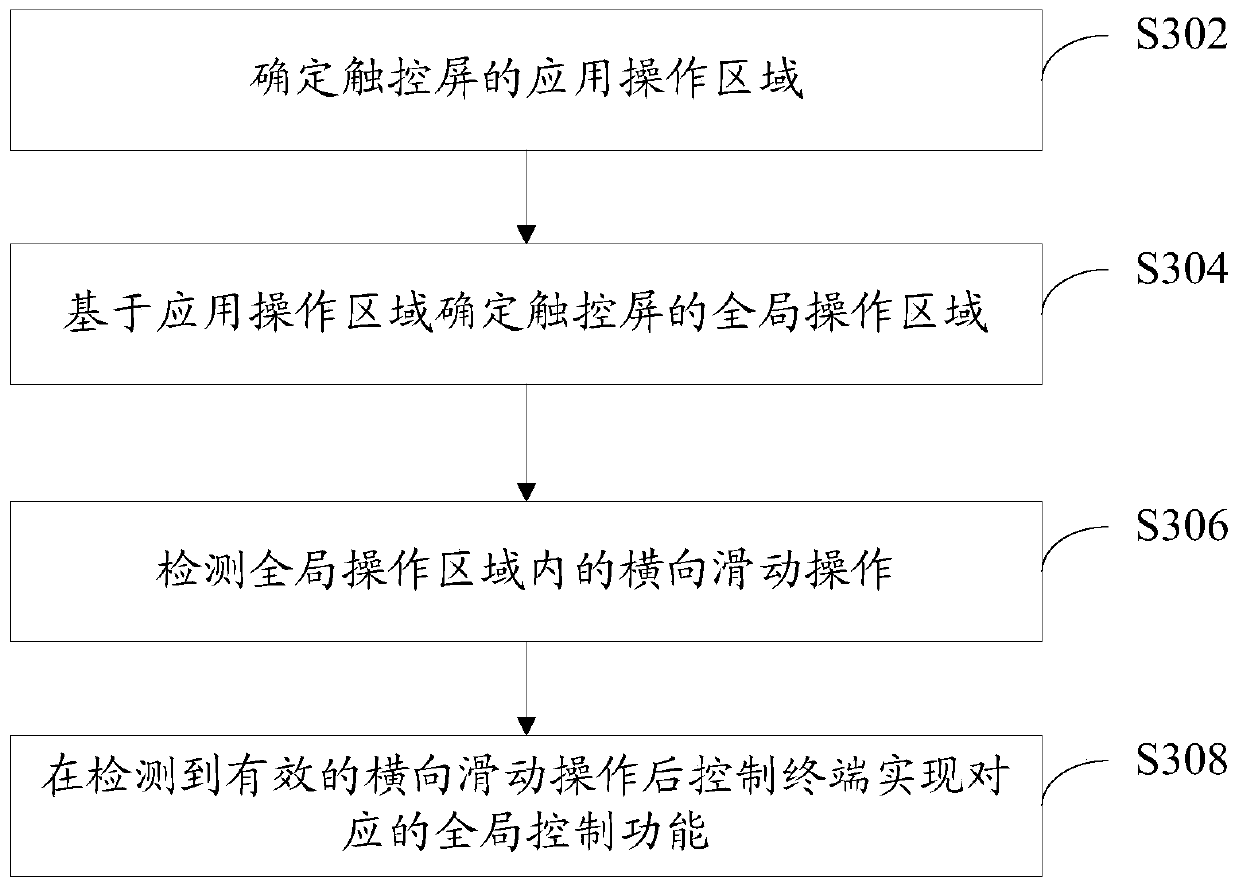
[0085] In order to solve the problem that the full-screen operation gesture control solution in the prior art requires the user to slide upwards from the bottom of the screen, which makes it difficult for the user to operate with one hand and the user experience is not high, this embodiment provides a terminal control method. image 3 It is a flow chart of the terminal control method:
[0086] S302: Determine an application operation area of the touch screen.
[0087] In this embodiment, the terminal sets an area on the touch screen that preferentially detects the touch operation according to the detection and control principle of the foreground application, that is, the application operation area. For example, in a certain application, it is stipulated that the "user profile setting interface" can be called out by sliding horizontally from left to right. Therefore, when a horizontal sliding operation from left to right is detected according to the detection and control prin...
no. 2 example
[0123] In order to make those skilled in the art more clear about the advantages and details of the terminal control method provided in the first embodiment, this embodiment will further illustrate the terminal control method with examples, please refer to Figure 9 The flowchart shown:
[0124] S902: Obtain the fingerprint feature of the current user when the terminal is unlocked.
[0125] When the terminal does not receive user operations for a long time, the terminal will actively enter the lock screen state. In addition, or the user finishes a stage of transaction processing on the terminal, the user will also control the terminal to enter Lock screen status. When the user needs to use the terminal, the terminal needs to be unlocked.
[0126] Now, most terminals are equipped with fingerprint identification modules. The terminal can detect fingerprint feature data through the fingerprint identification module, and then determine whether the currently unlocked device is ba...
no. 3 example
[0150] This embodiment will provide a computer-readable storage medium and a terminal. First, the computer-readable storage medium will be introduced:
[0151] The computer-readable storage medium stores one or more computer programs that can be read by the memory, compiled or executed, including a terminal control program, and the display control program can be executed by a processor so as to realize the first or second embodiment The terminal control method provided in .
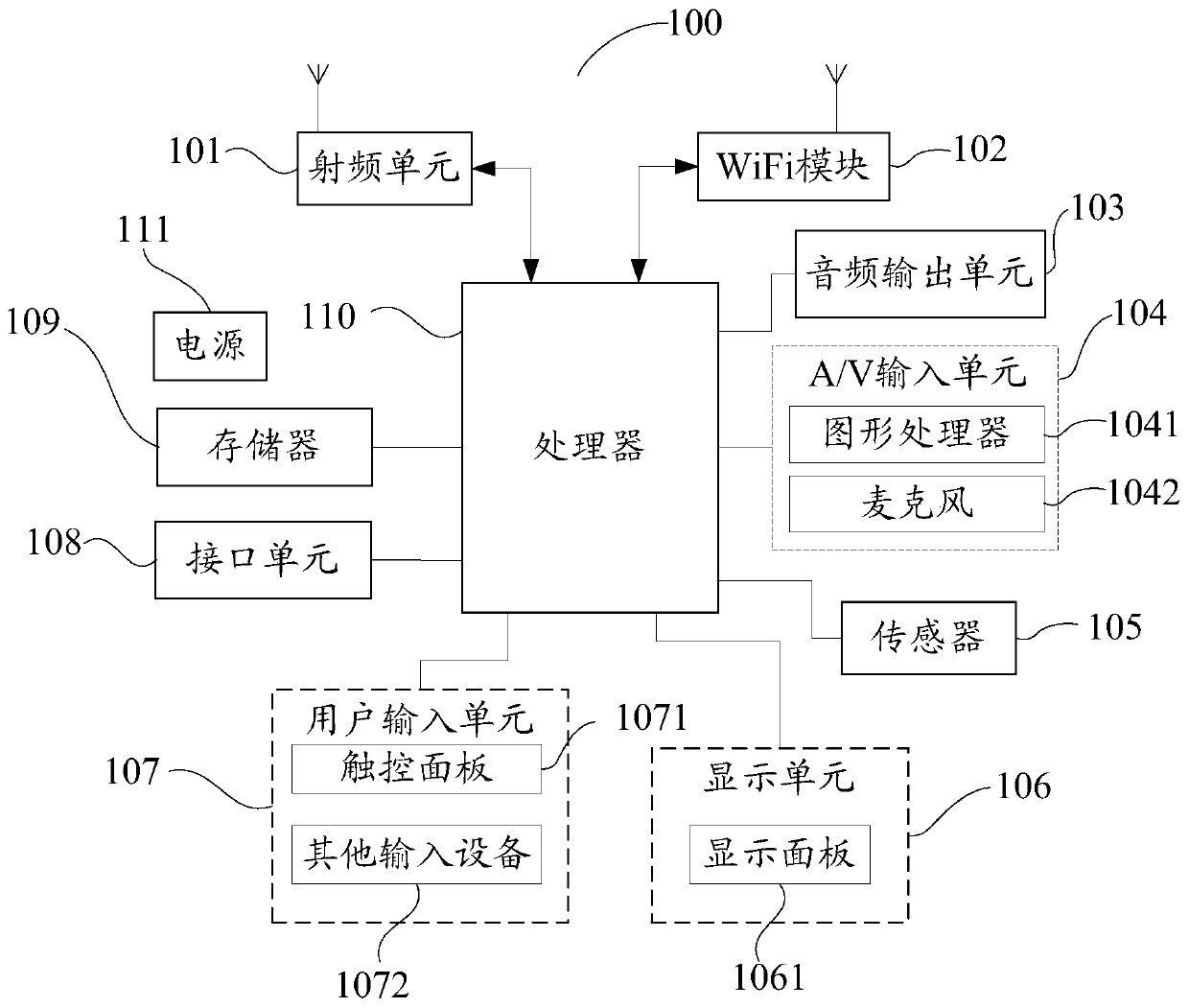
[0152] See Figure 11 Provided schematic diagram of the hardware structure of the terminal: the terminal 11 includes a processor 111, a memory 112, and a communication bus 113 for connecting the processor 111 and the memory 112, wherein the memory 112 may be the aforementioned computer-readable storage medium storing the terminal control program. The processor 111 of the terminal 11 can execute the terminal control program stored in the memory 112 to implement the terminal control method in the foregoing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com