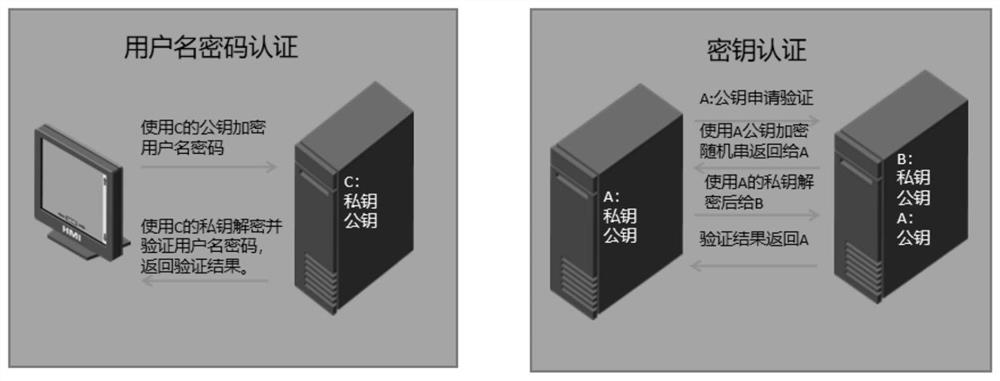
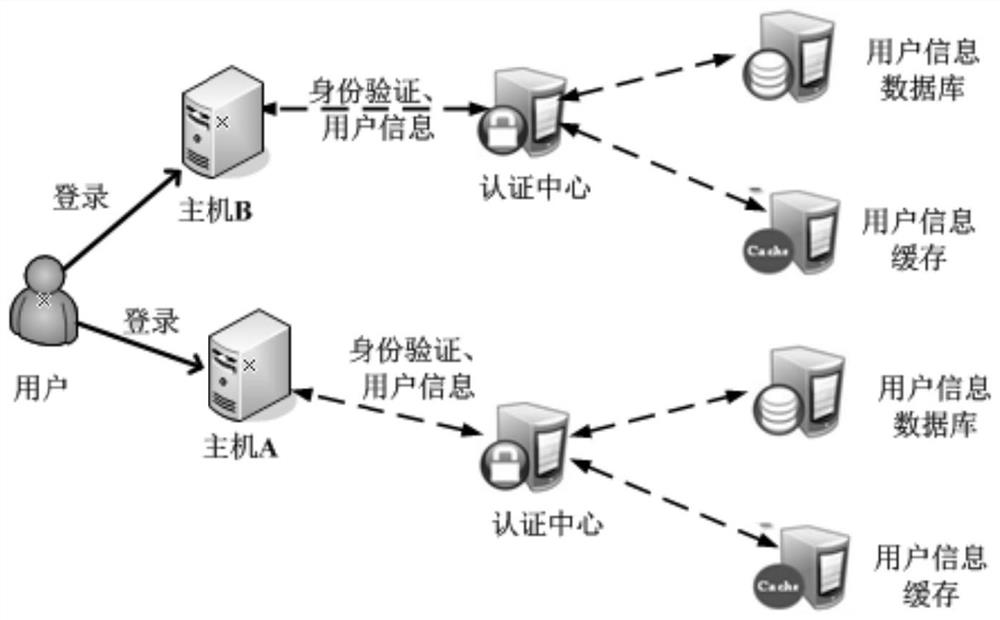
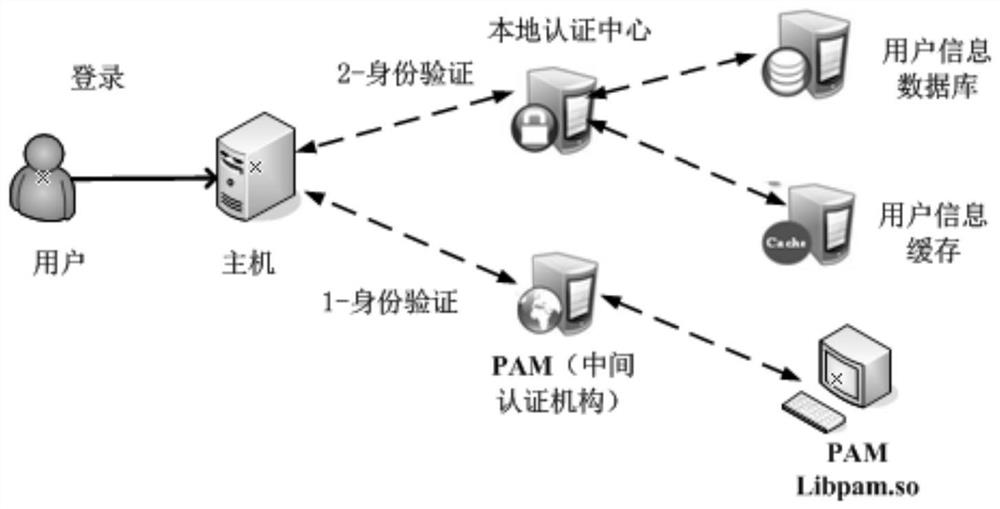
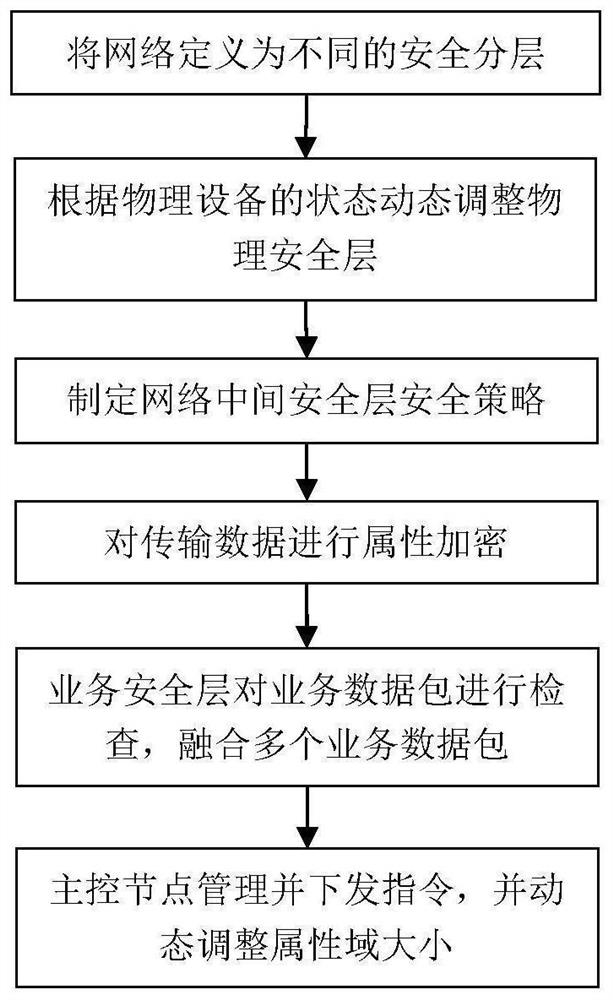
Patents
Literature
32results about How to "Reduce the probability of being attacked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
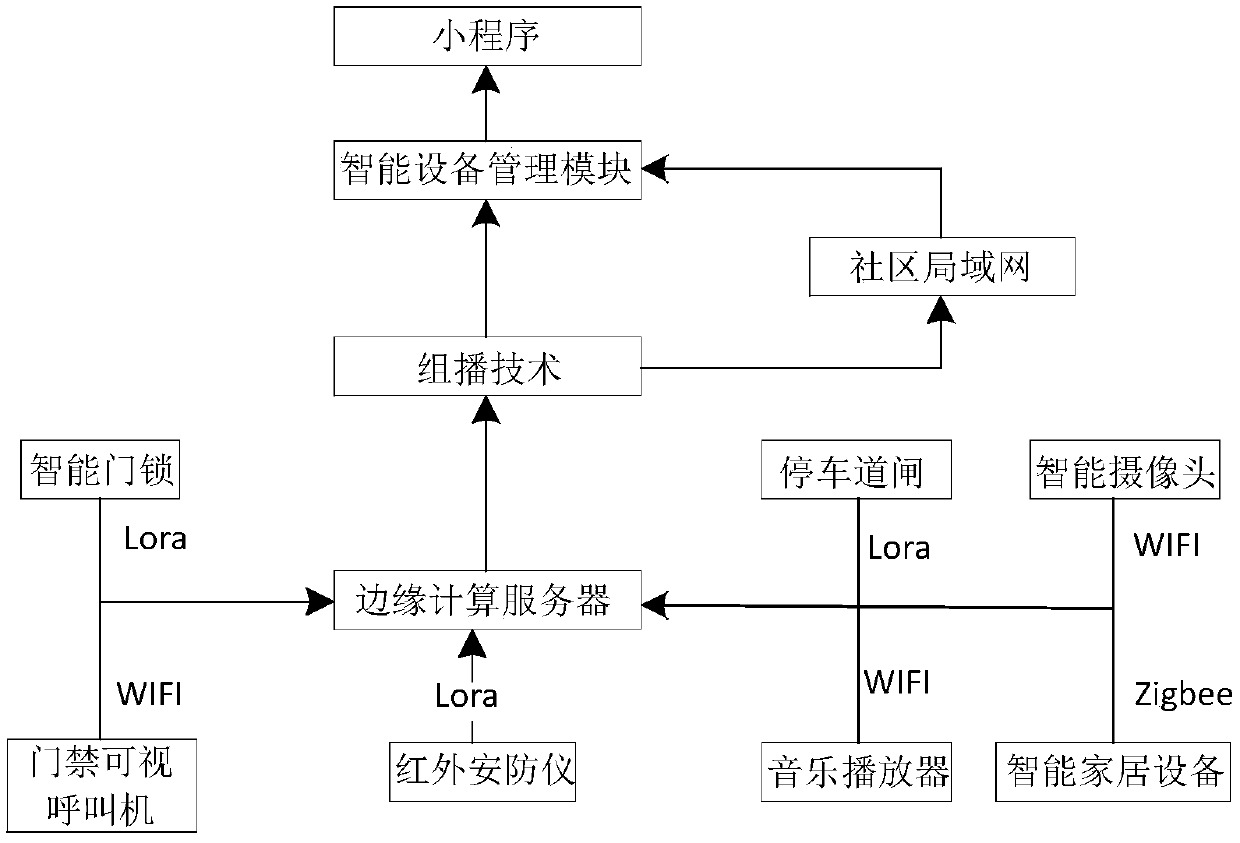
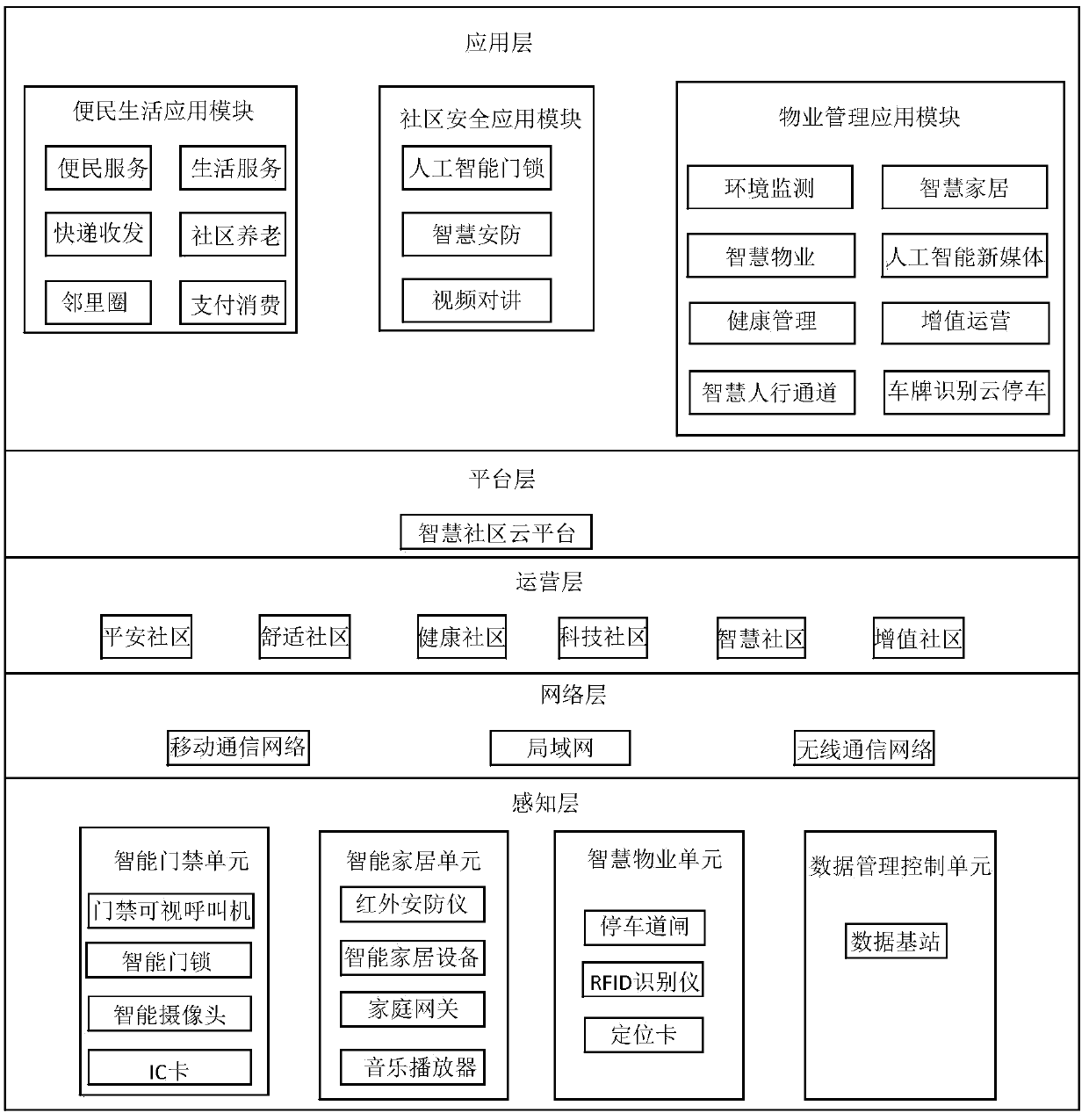
A smart community management system based on the edge computing server of the Internet of Things
InactiveCN109544052AEnsure safetyReduce the probability of being attackedResourcesThe InternetCommunity management
The embodiment of the invention discloses a smart community management system for an edge computing server on the Internet of things, The smart community management system comprises: a perceptual layer, an operations layer, a platform layer, and an application layer; the sensing layer is comprised of a plurality of intelligent hardware, the sensing layer uploads the data of the intelligent hardware to the operation layer through the network layer, The edge computing server in the operation layer processes the data, the platform layer is a smart community cloud platform, the operation layer isconnected with the platform layer through the multicast technology, the application layer is an interactive entrance of the smart community cloud platform, and the application layer comprises a plurality of application modules to realize different interactive control. The invention solves the problems of low intelligence degree and low safety coefficient of the existing community management system.
Owner:南京我在智能科技有限公司
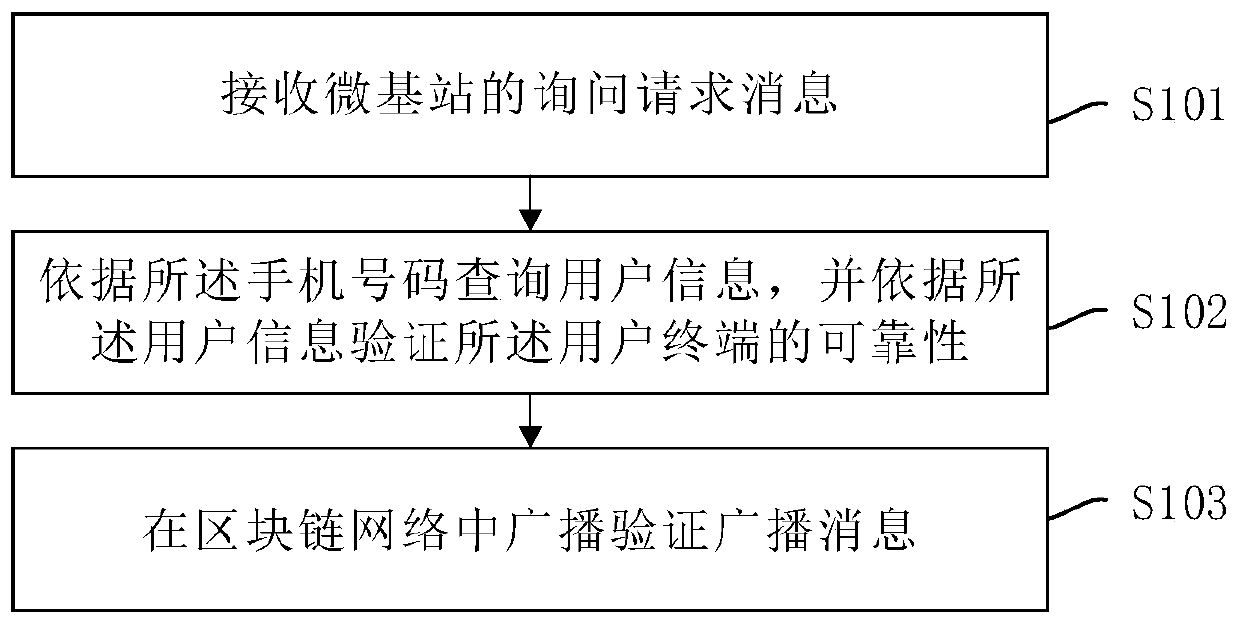
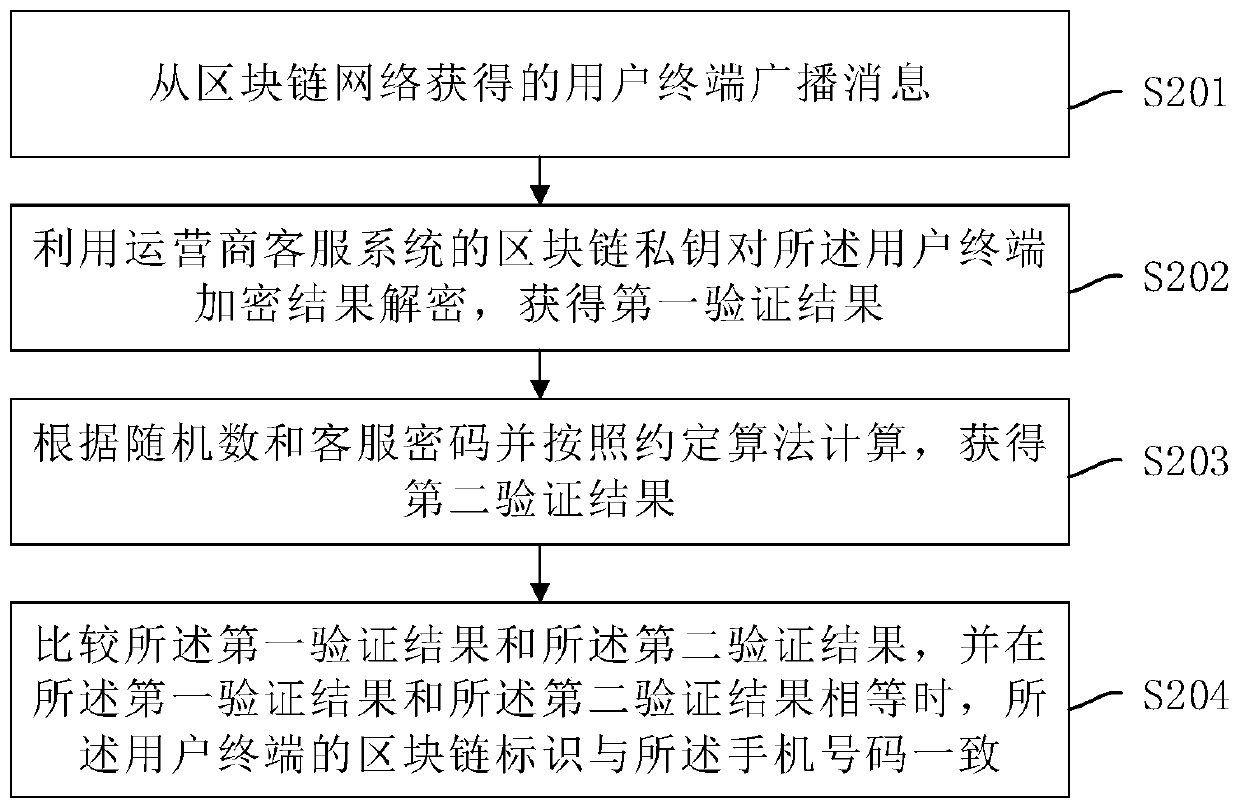
Terminal access method and device
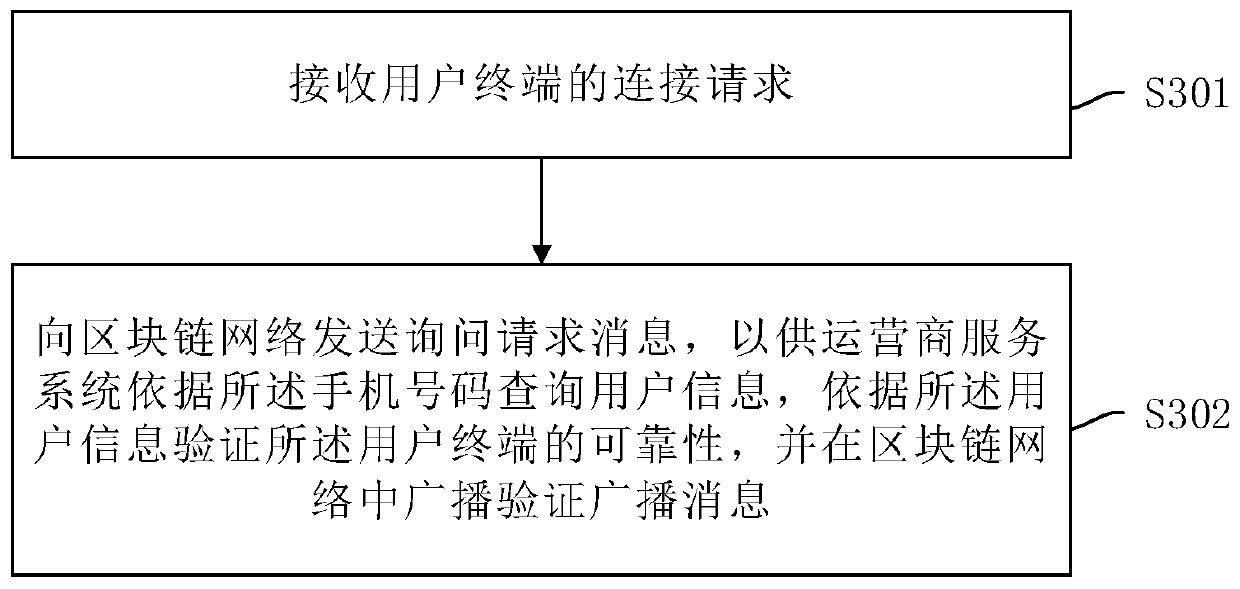
ActiveCN111246471AImprove experienceAvoid accessKey distribution for secure communicationAssess restrictionMobile Telephone NumberBlockchain
The invention belongs to the technical field of communication, and particularly discloses a terminal access method and device. The method comprises the steps: receiving an inquiry request message of amicro base station, wherein the inquiry request message carries a micro base station identifier, a blockchain identifier of a user terminal, a mobile phone number and deadline; querying user information according to the mobile phone number, and verifying the reliability of the user terminal according to the user information; broadcasting a verification broadcast message in the blockchain network,wherein the verification broadcast message carries a blockchain identifier, a mobile phone number and a reliability identifier of the user terminal. According to the terminal access method, the probability that the micro base station alliance is attacked can be reduced, the privacy information of the user terminal is protected, and the development of the micro base station alliance is promoted while the user experience is improved.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Android malicious application detection method based on dual-channelconvolutional neural network
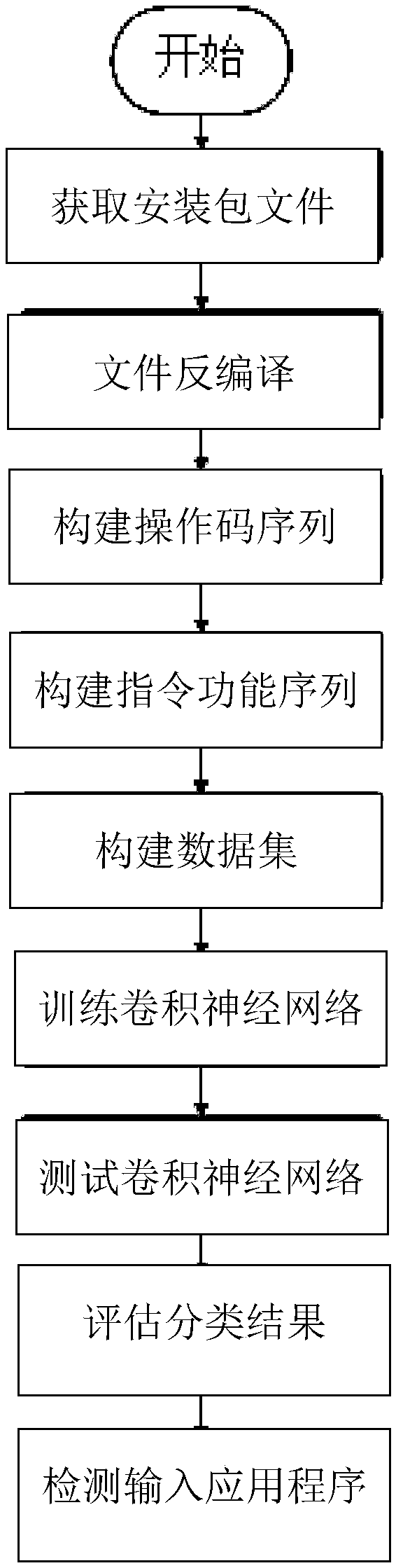
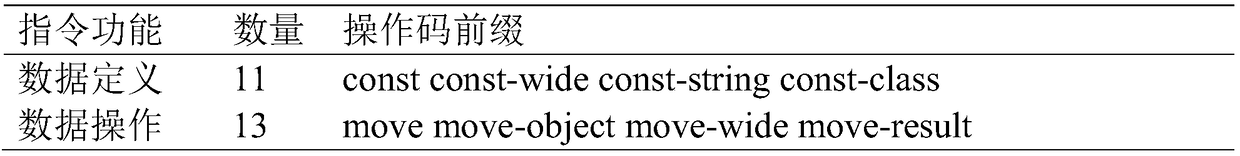
ActiveCN109165510AHigh classification precision and recallReduce the probability of being attackedPlatform integrity maintainanceApplication softwareNerve network
An Android malicious application detection method based on a dual-channel convolutional neural network is provided. The method includes obtaining an installation package file; decompiling the installation package files; constructing an opcode sequence; construct an instruction function sequence; carrying out vectorization processing on the features of the operation code sequence and the instruction function sequence; training a convolutional neural network; testing the convolutional neural network; evaluating the malicious application detection model; detecting an application to be detected, etc. Compared with the traditional detection model, the malicious application detection model generated by the method provided by the invention has higher classification accuracy and recall rate, and reduces the probability of the Android system being attacked due to missing detection.
Owner:CIVIL AVIATION UNIV OF CHINA
Image encryption method based on composite chaotic system and image processing device
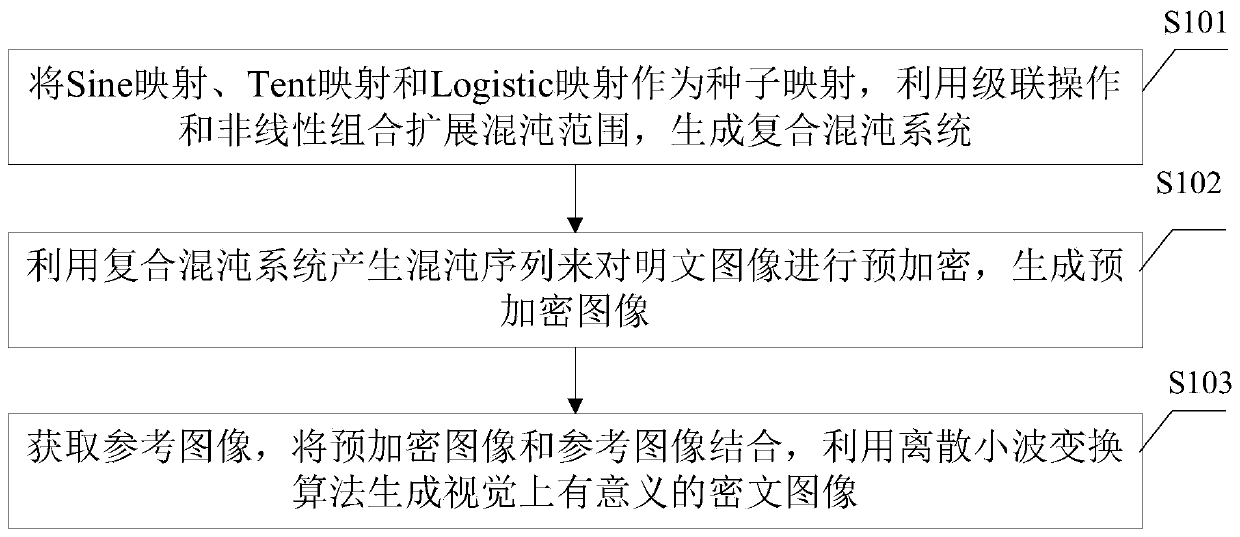
ActiveCN109977686AWide range of chaosComplex chaotic behaviorDigital data protectionImage data processing detailsChosen-plaintext attackImaging processing
The invention is applicable to the field of image encryption, and provides an image encryption method based on a composite chaotic system and an image processing device. The method comprises the following steps of taking Sine mapping, Tent mapping and Logistic mapping as seed mapping, and generating a composite chaotic system by utilizing a cascade operation and a nonlinear combination expansion chaotic range; generating a chaotic sequence by using a composite chaotic system to pre-encrypt the plaintext image, and generating a pre-encrypted image; and obtaining a reference image, combining thepre-encrypted image with the reference image, and generating a visually meaningful ciphertext image by using a discrete wavelet transform (DWT) algorithm. The method provided by the invention has a wider chaotic range and the more complex chaotic behaviors, and the encryption performance is improved. In addition, due to the fact that the visually significant ciphertext image is generated, the attack probability is reduced, the selected plaintext attack and the exhaustion attack can be resisted, and the encryption performance is better.
Owner:GUILIN UNIV OF ELECTRONIC TECH
Double-layer grouping Byzantine fault-tolerant consensus method and system
PendingCN113642019AReduce Communication ComplexityReduce the number of communicationsDigital data protectionDigital data authenticationChain networkCommunication complexity
The invention discloses a double-layer grouping Byzantine fault-tolerant consensus method and system. The method comprises the following steps: S1, determining node groups; S2, for each group of nodes, selecting a part of nodes from the nodes as committee nodes, forming committee of the group, taking the remaining nodes except the committee nodes as common nodes, and selecting a main node of each group from the committee nodes; S3, building a block chain network; S4, if a certain group of committee receives a proposal request, the main node of the group generating a block according to the proposal request and sending the block to other committee nodes of the group for a first round of consensus, and if the first round of consensus passes, generating an initial block and sending the initial block to the common node of each group; and S5, performing a second round of consensus on the initial block by the common node of each group, and if the second round of consensus is passed, chaining the initial block and storing the initial block in a local account book. According to the method, a double-layer grouping consensus structure is adopted, and the system robustness is improved on the premise that low communication complexity is guaranteed.
Owner:NAT UNIV OF DEFENSE TECH
Information distribution method for mobile terminal
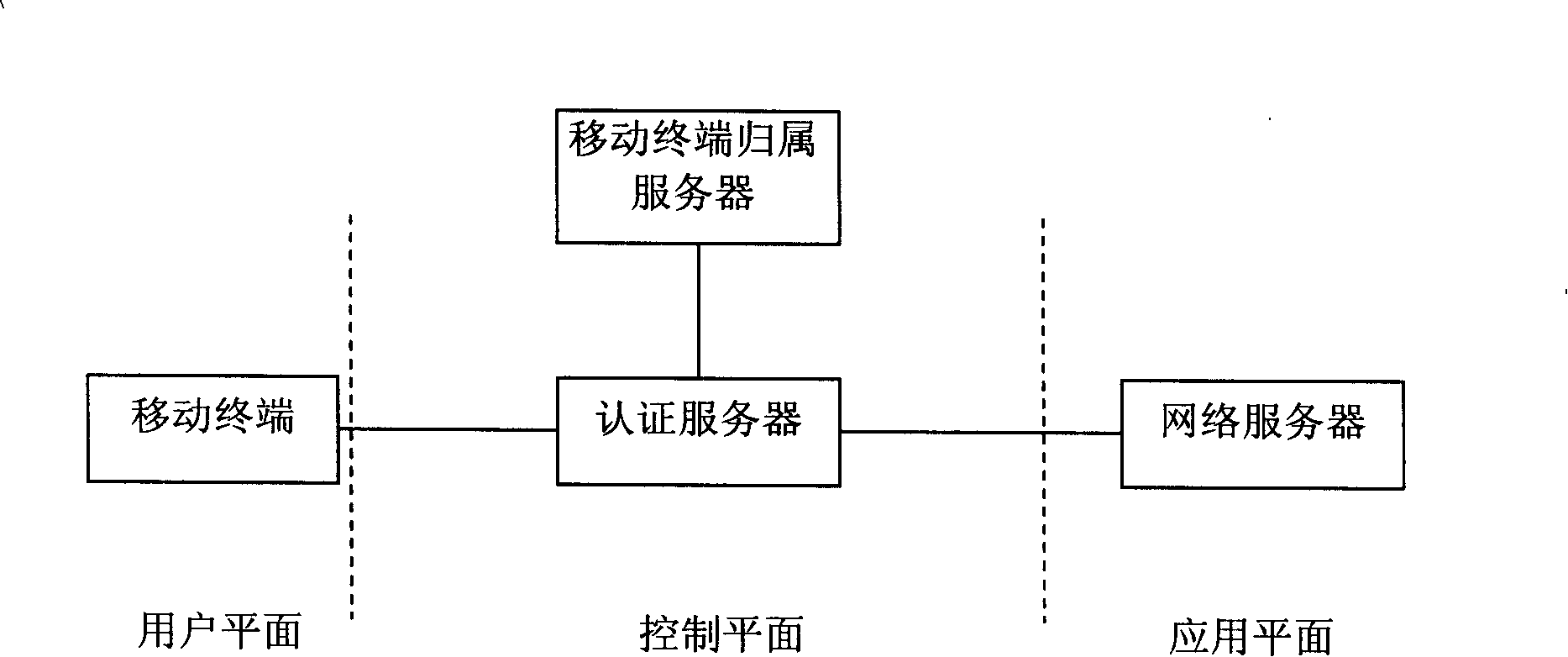
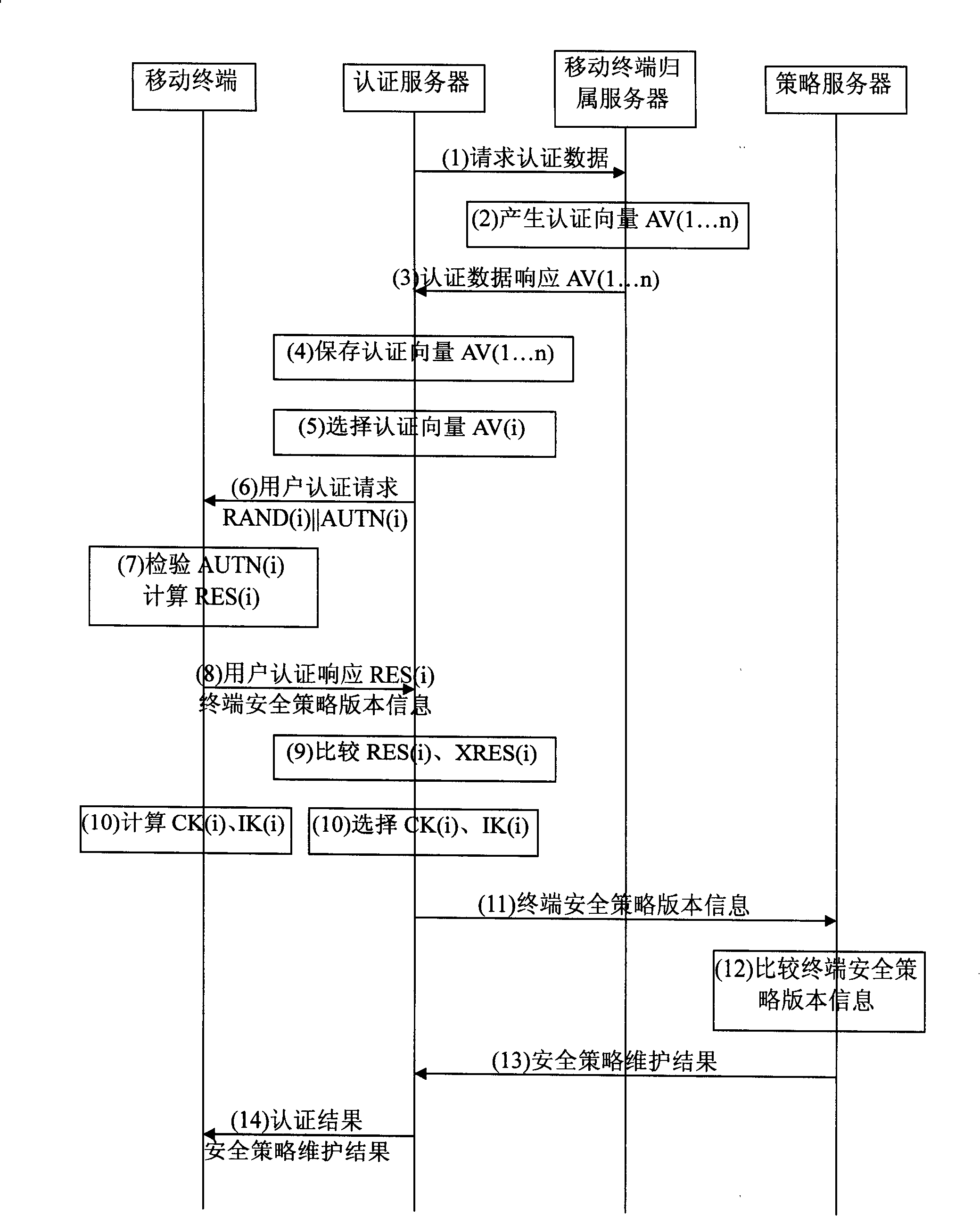
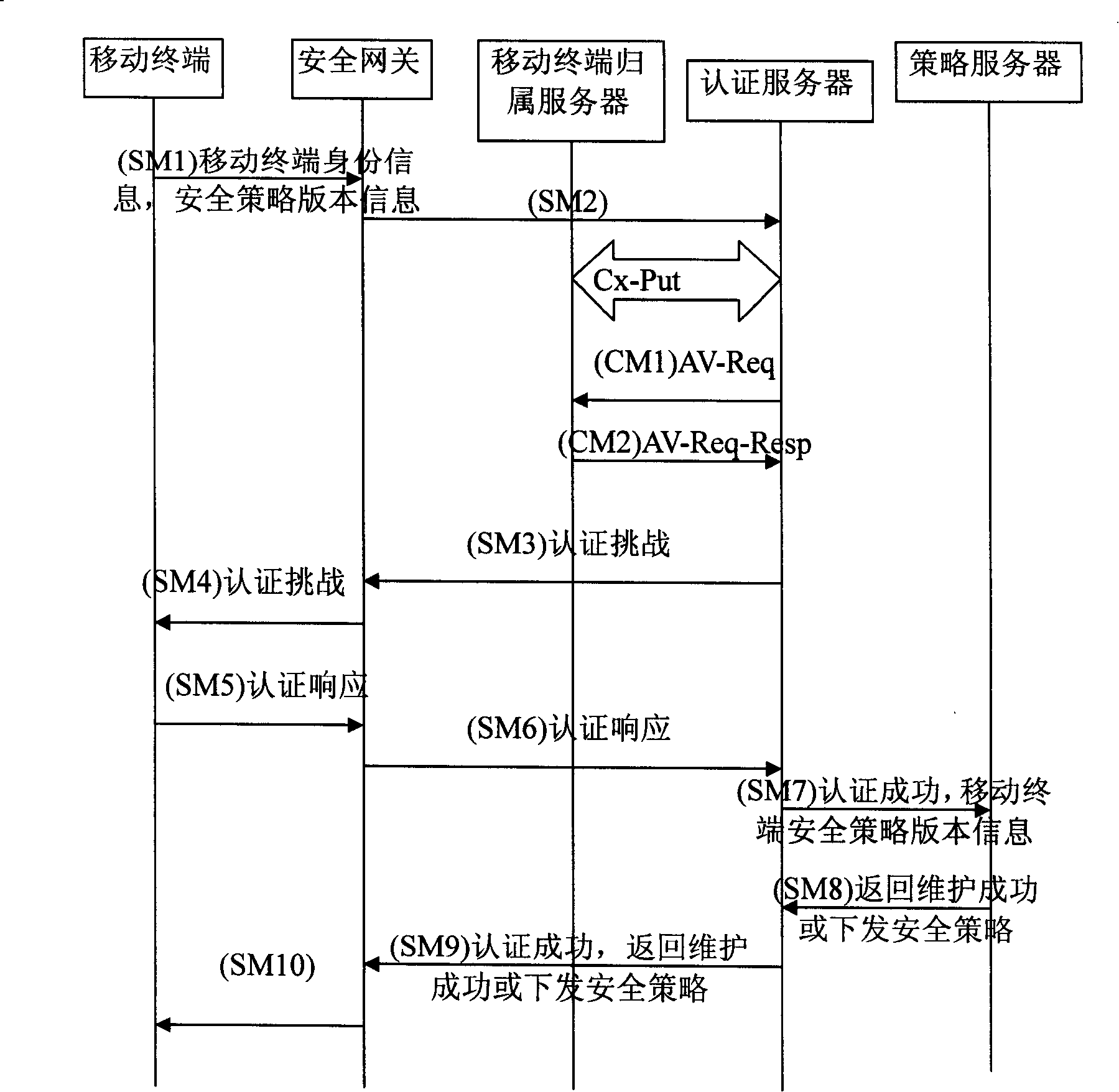
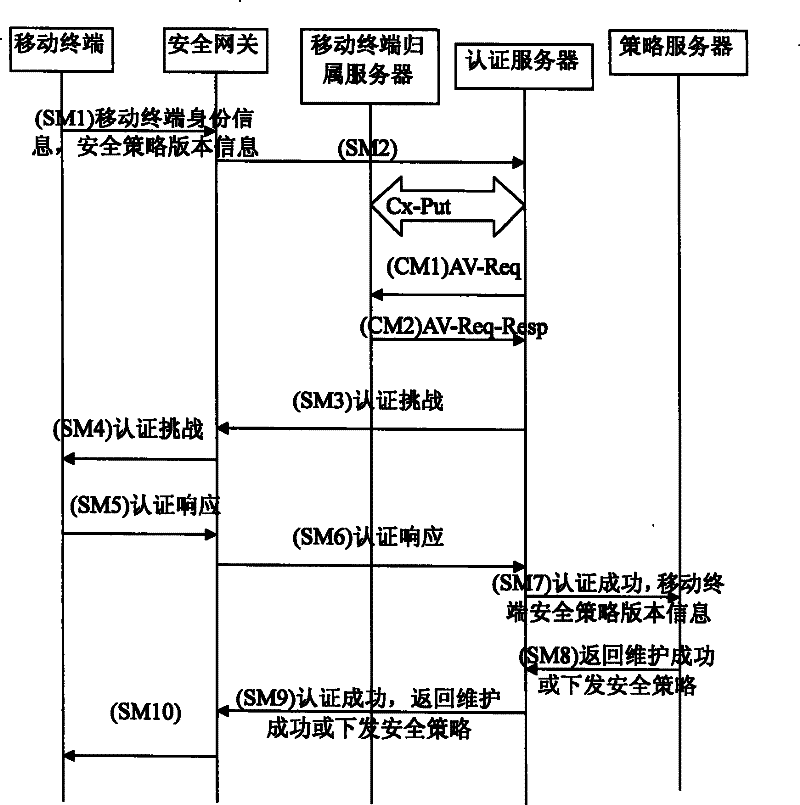
ActiveCN101198148AReduce omissionsReduce errorsSpecial service provision for substationUser identity/authority verificationRelevant informationDistribution method
The present invention relates to an information distribution method of mobile terminal; in the process of mutual authentication between a mobile terminal and a network server, the mobile terminal sends the relevant information code of the mobile terminal to an authentication server; after the authentication succeeds, a session key is established; the authentication server sends the relevant information code of the mobile terminal to the network server; according to the relevant information code of the mobile terminal, the network server completes the operation of information distribution and returns operating results to the authentication server; the authentication server informs the mobile terminal of the authentication and the information distribution results. With the method of the present invention, the information distribution is embedded to the AKA process, reduces the communication cost and can reduce omissions and errors of information distribution by the network server as possible; the present invention can use the session key consulted in the authentication process to encrypt distributed information and reduces the probability of being attacked. The key consulted in the AKA process has safe protection on data distribution and improves the safe performance.
Owner:ZTE CORP
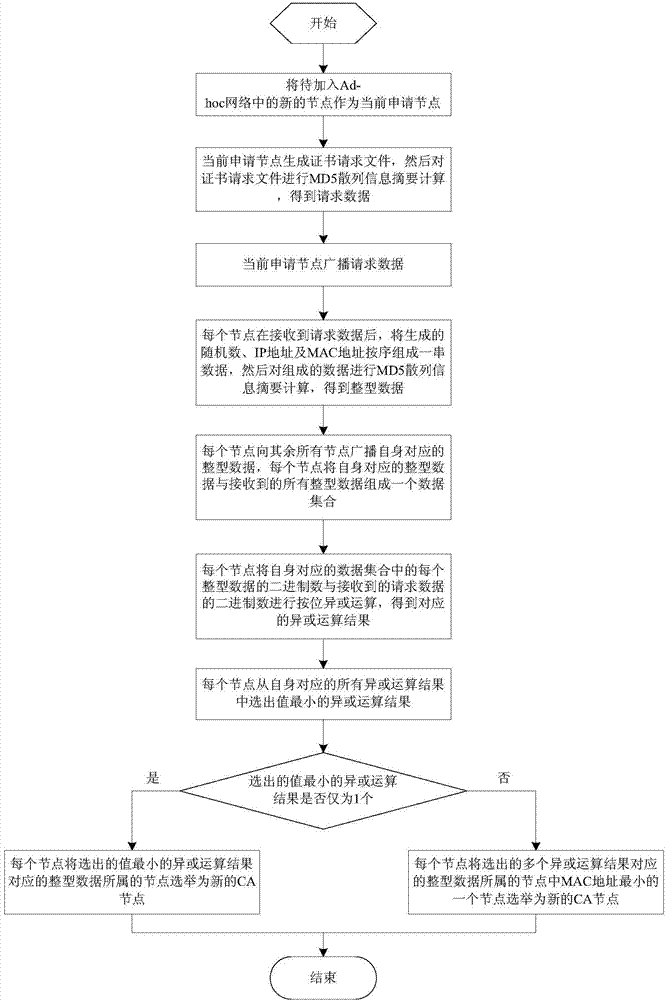
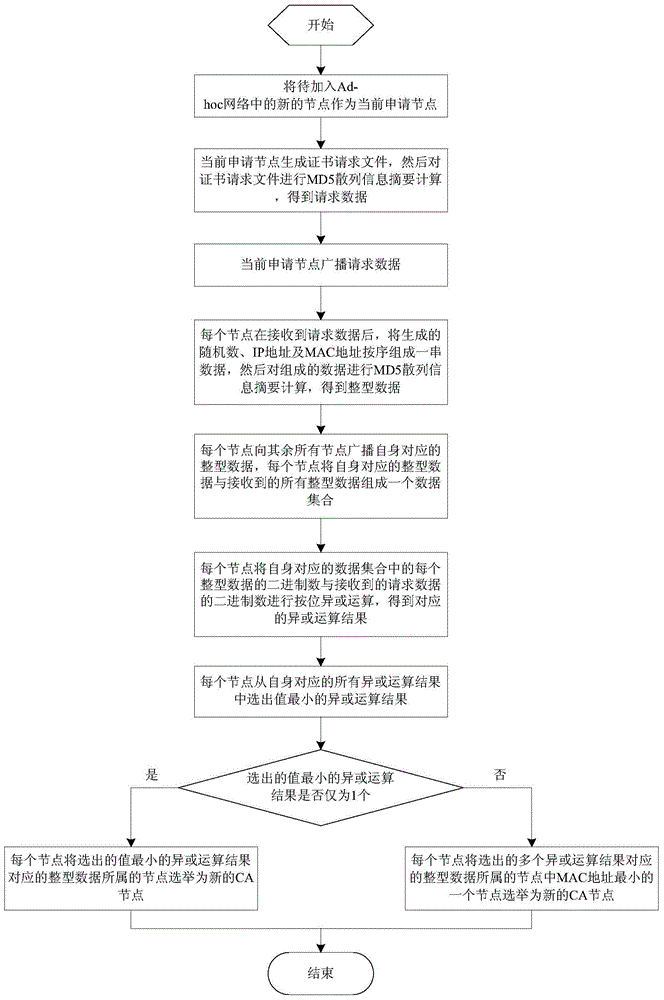
Mobile CA node electing method based on MD5 hash information abstract
ActiveCN103905198AReduce energy consumptionReduce the probability of being attackedEnergy efficient ICTPower managementIp addressKey factors
The invention discloses a mobile CA node electing method based on an MD5 hash information abstract. The method includes the steps that MD5 hash information abstract calculation is performed on certificate demand files generated by applied nodes, and demand data are obtained; each node of all the nodes is elected as a CA node according to integer data and the received demand data, wherein the integer data are obtained after data composed of the generated random number, the IP address and the MAC address are calculated through the MD5 hash information abstract; due to the fact that the key factor for determining the CA node lies in the certificate demand files generated by the applied nodes and the random number generated by the node in the Ad-hoc network, for the same applied node, a CA node electing result obtained each time differs from other results, and for the different applied nodes, the CA node electing results are different. Thus, the CA nodes are effectively prevented from providing a certificate service for a long time and the energy consumption of the CA nodes is reduced. Meanwhile, the probability of attacking the CA nodes is greatly reduced.
Owner:NINGBO UNIV
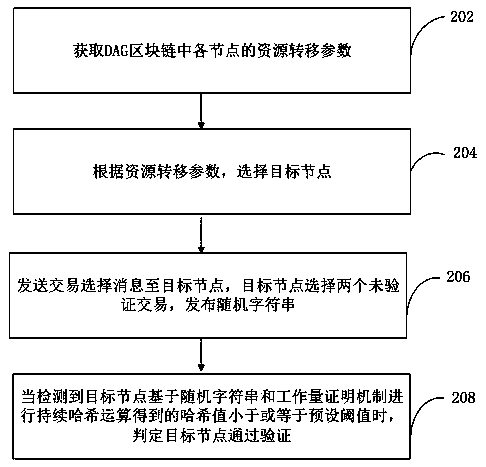
Data verification method and device based on DAG block chain and computer equipment
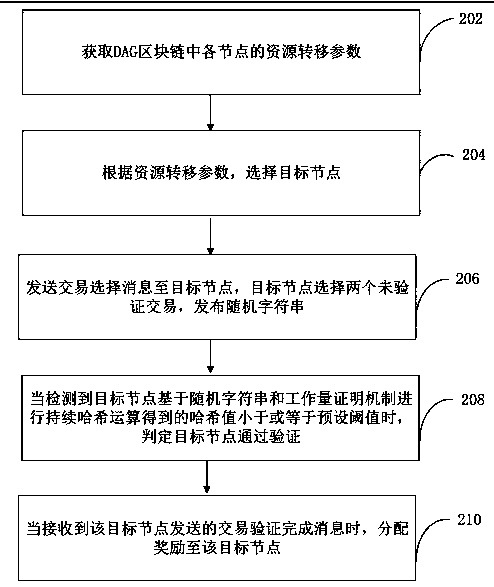
InactiveCN111429122AImprove data securityReduce the probability of being attackedFinancePayment circuitsSource Data VerificationResource transfer
The invention relates to a data verification method and device based on a DAG block chain, computer equipment and a storage medium. The method comprises the following steps of: obtaining a resource transfer parameter of each node in the DAG block chain; according to resource transfer parameters, selecting a target node, sending a transaction selection message to the target node, enabling the target node to select two unverified transactions and publish a random character string; and when it is detected that a hash value obtained by continuous hash operation of the target node based on the random character string and a workload proof mechanism is smaller than or equal to a preset threshold, judging that the target node passes verification. According to the method, a target node is used forreplacing a coordinator node in a DAG block chain to realize decentralization; through the competition mode, the verification of the transaction is no longer limited to the coordinator node, the efficiency of transaction verification is improved, the probability that the DAG network is attacked is greatly reduced, and the data security of the network is improved.
Owner:卓尔智联(武汉)研究院有限公司
Method, device and electronic equipment for protecting target application
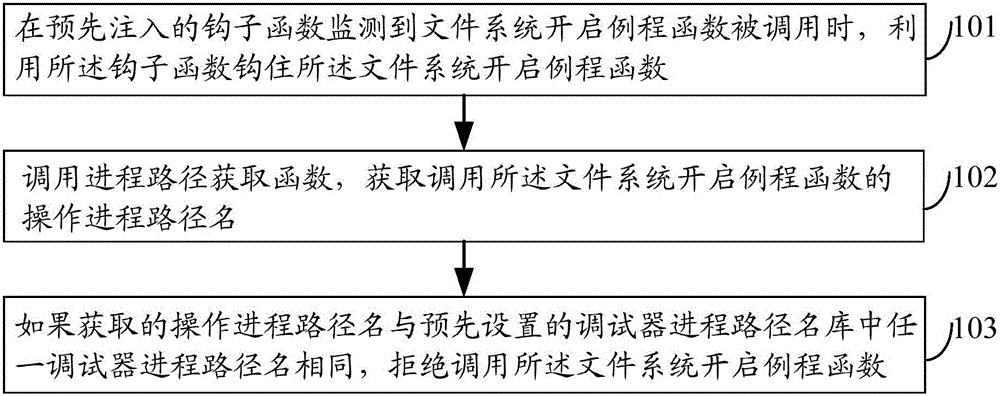
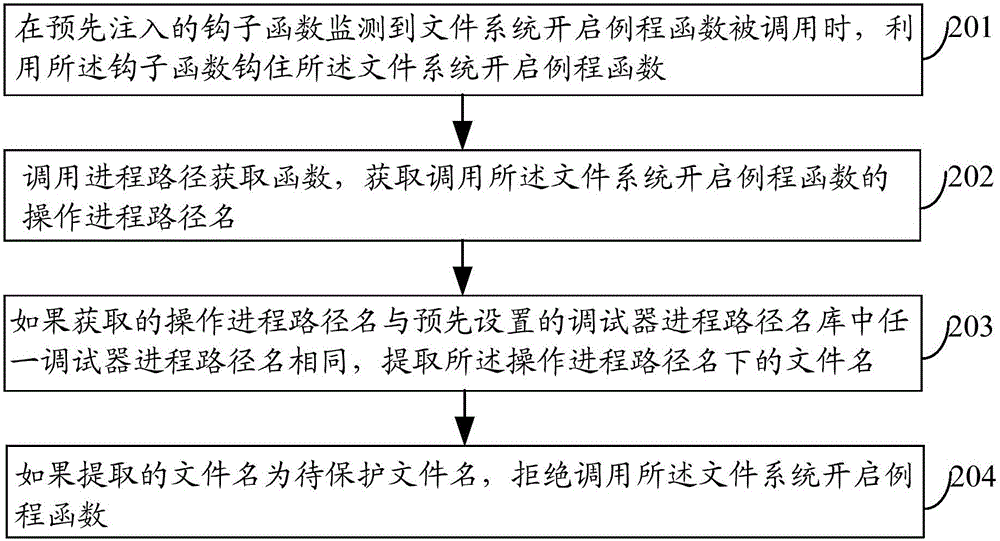
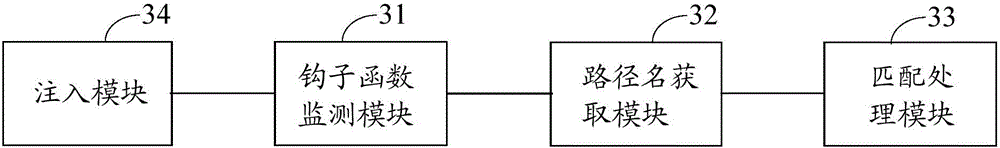
InactiveCN105893846AImprove securitySolve the problem of vulnerability to attack and low securityPlatform integrity maintainanceFile systemApplication software
The embodiment of the invention discloses a method, device and electronic equipment for protecting target application, and relates to the information security technology, wherein the probability of application attack can be reduced, and the application security is improved. The method comprises the following steps: when the pre-input hook function monitors that a file system opening routine function is called, hooking the file system opening routine function using the hook function; calling a progress path acquisition function, and acquiring the operation progress path name calling the file system opening routine function; and if the acquired operation progress path name is the same as any debugger progress path name in a preset debugger progress path name library, rejecting the calling of the file system opening routine function. The method, device and electronic equipment are applicable to the anti-debugging protection of application.
Owner:ZHUHAI BAOQU TECH CO LTD
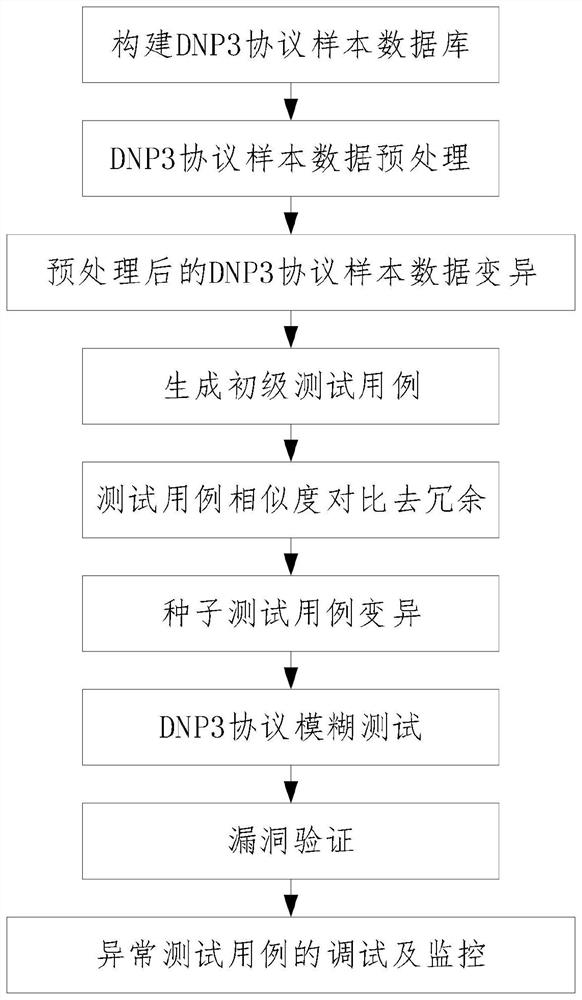
DNP3 protocol fuzzy test method based on sequence generative adversarial network
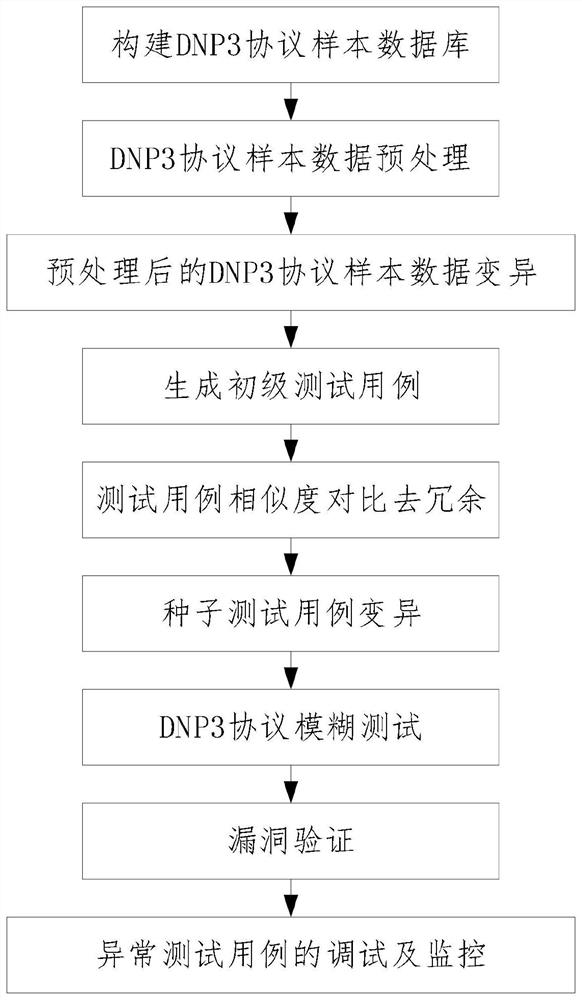
ActiveCN112104525AQuality improvementReduce redundancyNeural architecturesData switching networksAttackScreening algorithm
The invention discloses a DNP3 protocol fuzzy test method based on a sequence generative adversarial network. The DNP3 protocol fuzzy test method comprises the following steps: 1, constructing a DNP3protocol sample database; 2, preprocessing DNP3 protocol sample data; 3, carrying out data variation on the preprocessed DNP3 protocol sample; 4, generating a primary test case; 5, comparing the similarity of the test cases to remove redundancy; 6, carrying out seed test case variation; 7, performing a DNP3 protocol fuzzy test; 8, carrying out vulnerability verification; and 9, debugging and monitoring the abnormal test case. According to the method, the sequence generative adversarial network is utilized to generate the high-pass-rate test case; the redundancy of the test cases is reduced through a screening algorithm taking case similarity as an index; a random variation strategy is introduced to perform test case variation, so that the test case diversity and the vulnerability discoveryprobability are improved; by analyzing the stack frame information of the program when the vulnerability occurs, the cause of the vulnerability is found and recorded, so that the attack probability of the industrial control system is reduced, and the security of the industrial control system is improved.
Owner:XIAN UNIV OF SCI & TECH
Attack detection method and device based on attack detection model, medium and equipment
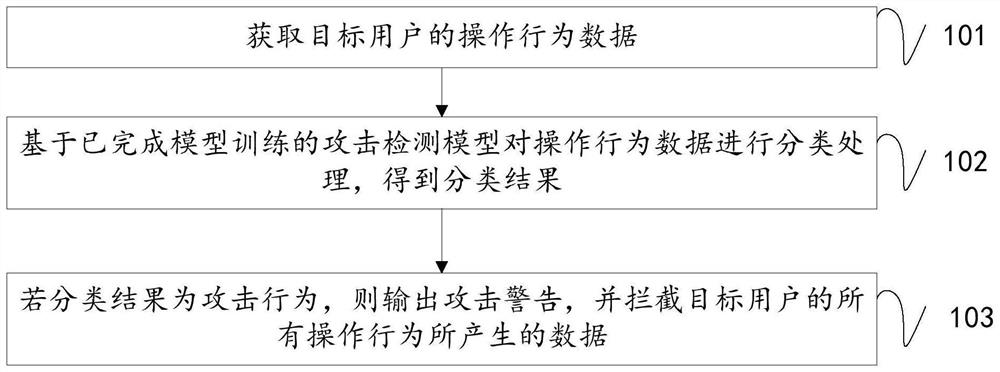
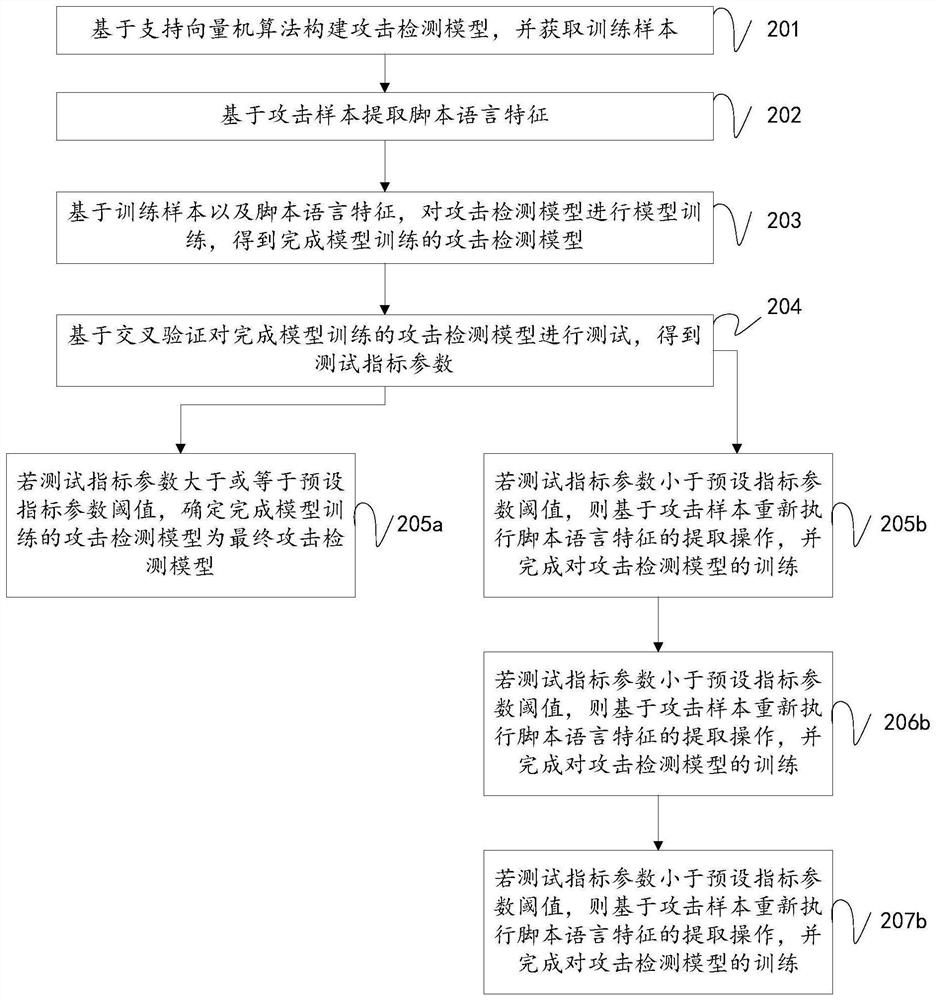
PendingCN114553523AImprove accuracyReduce false alarm rateKernel methodsCharacter and pattern recognitionScripting languageAttack
The invention discloses an attack detection method and device based on an attack detection model, a medium and equipment, relates to the field of network security, and mainly aims to solve the problems that when an existing machine learning algorithm is used for attack behavior detection, due to the fact that the number of training samples and the number of feature selection are small, the accuracy of an attack detection result is low, and the efficiency is high. And the false alarm rate is high. Comprising the steps of obtaining operation behavior data of a target user; the operation data are classified based on an attack detection model after model training is completed, a classification result is obtained, the attack detection model is constructed based on a support vector machine algorithm, model training is completed based on training samples and script language features, and the classification result is obtained. The training sample is composed of an attack sample collected based on an attack tool and a normal sample generated based on an automatic test attack, and the script language feature is extracted based on the attack sample; and if the classification result is an attack behavior, outputting an attack warning, and intercepting data generated by all operation behaviors of the target user.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
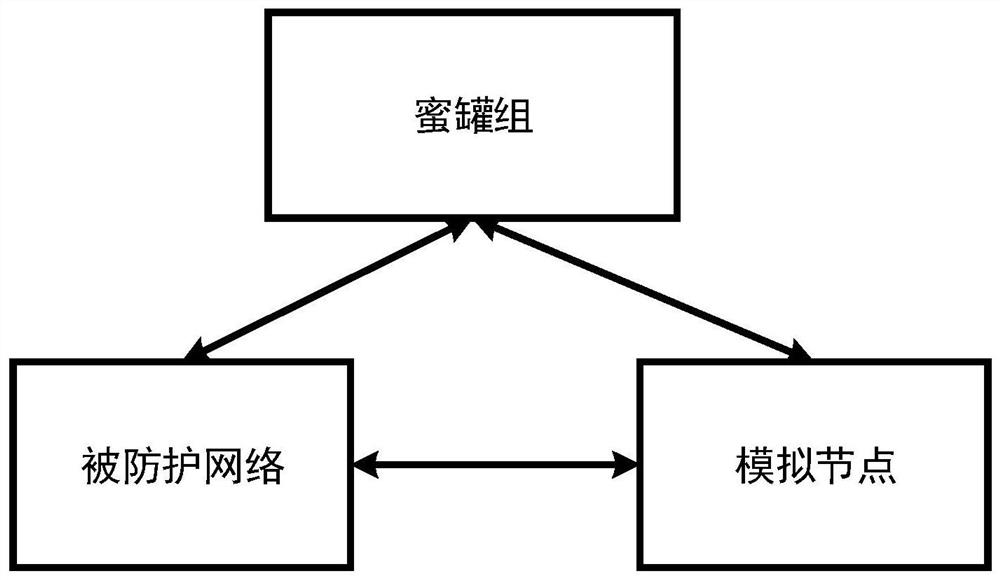
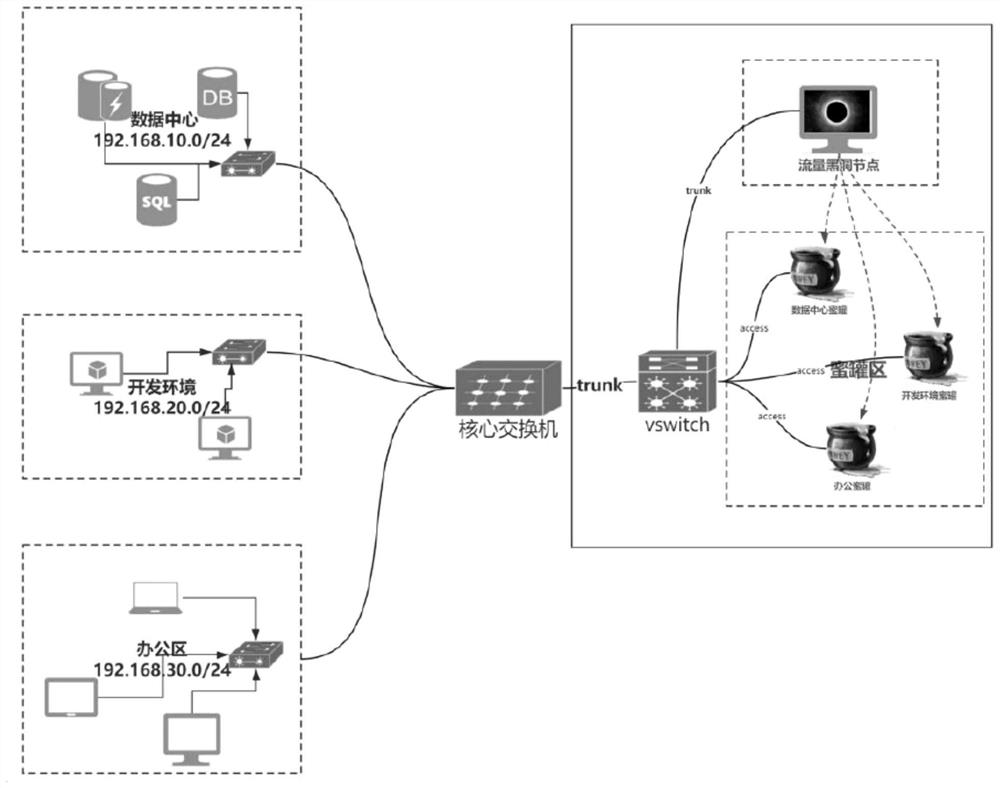
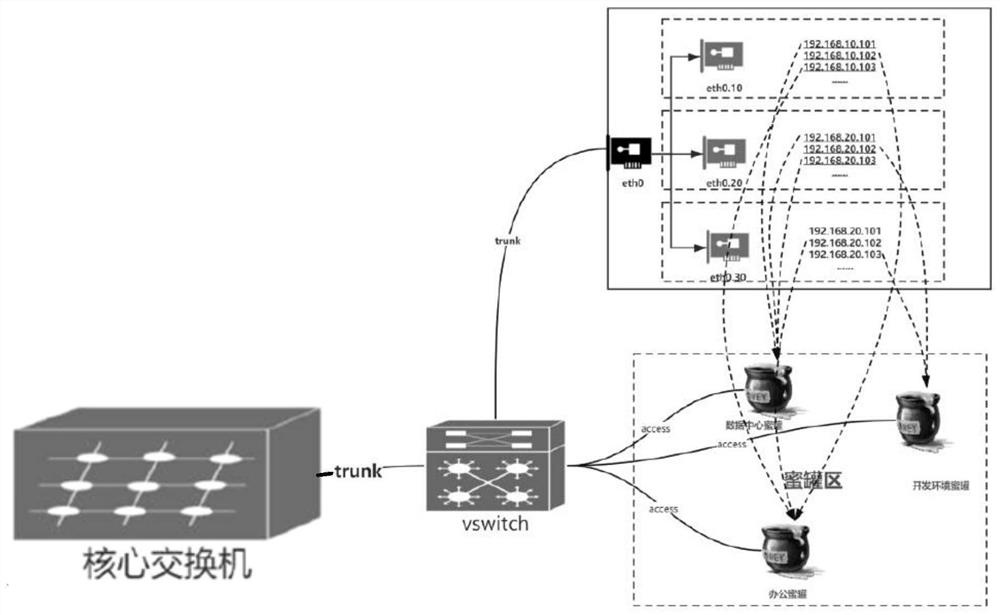
Honeypot protection system
ActiveCN113612783AImprove securityReduce the probability of being attackedTransmissionSoftware simulation/interpretation/emulationIp addressAttack
The invention discloses a honeypot protection system, which uses a simulation node to simulate a real node in a protected network, and the simulation node is configured with all idle IP addresses in the protected network, so that the simulation node can be accessed externally as the real node in the protected network. Under the condition, if an attacker accesses the protected network, the attacker does not only access the real node in the protected network but possibly accesses the simulation node, but the simulation node does not run the actual network service, so that the probability that the protected network is attacked is reduced, and the probability that the real server is attacked is also reduced. Meanwhile, the honeypot group can capture the flow data of the access simulation node and the protected network, so that the attack information can be captured by the honeypot, and the network safety is protected and improved.
Owner:杭州安恒信息安全技术有限公司
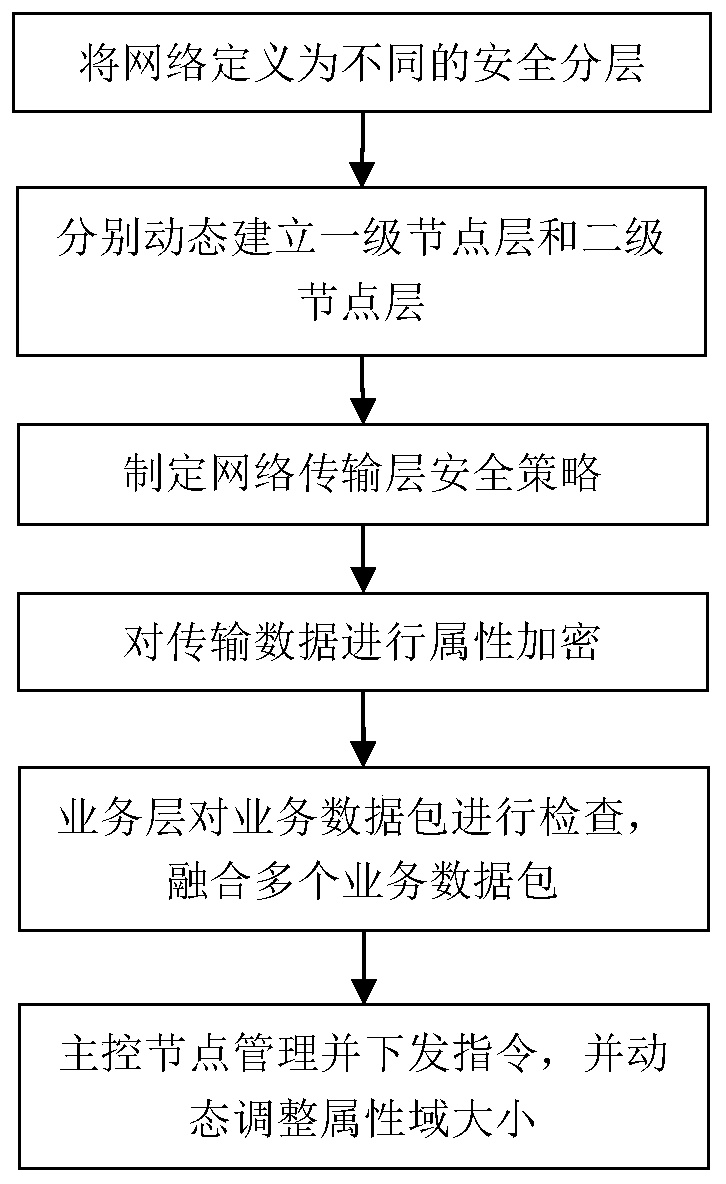
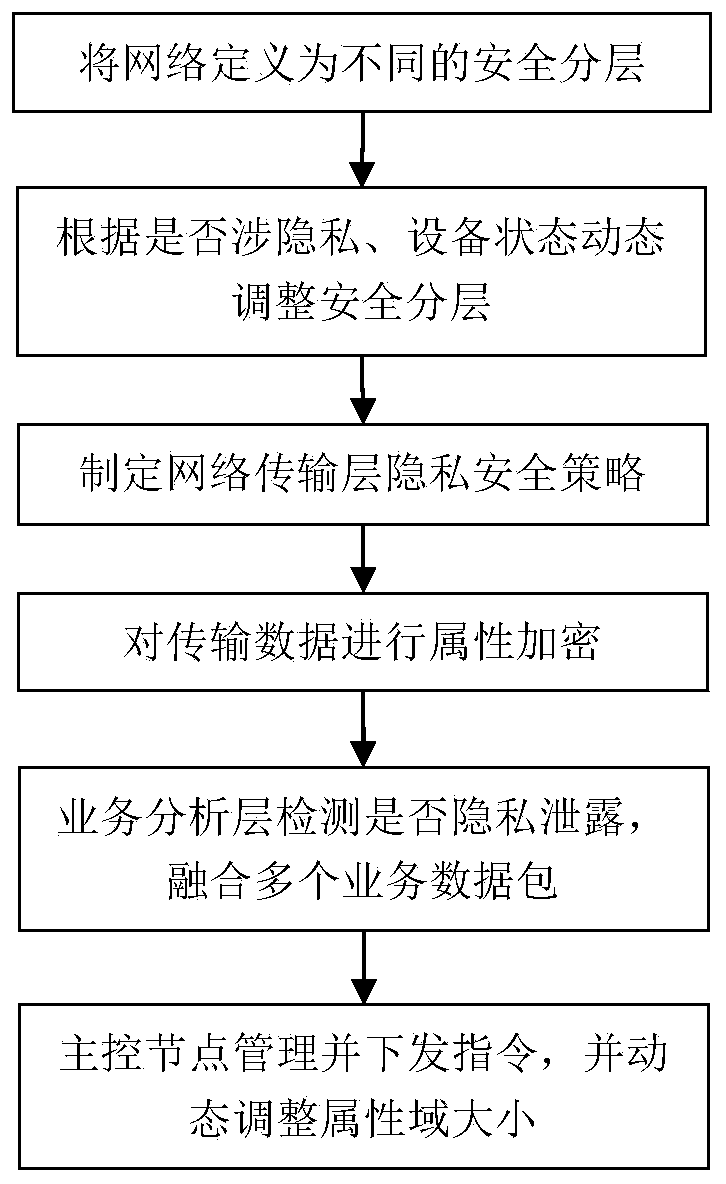
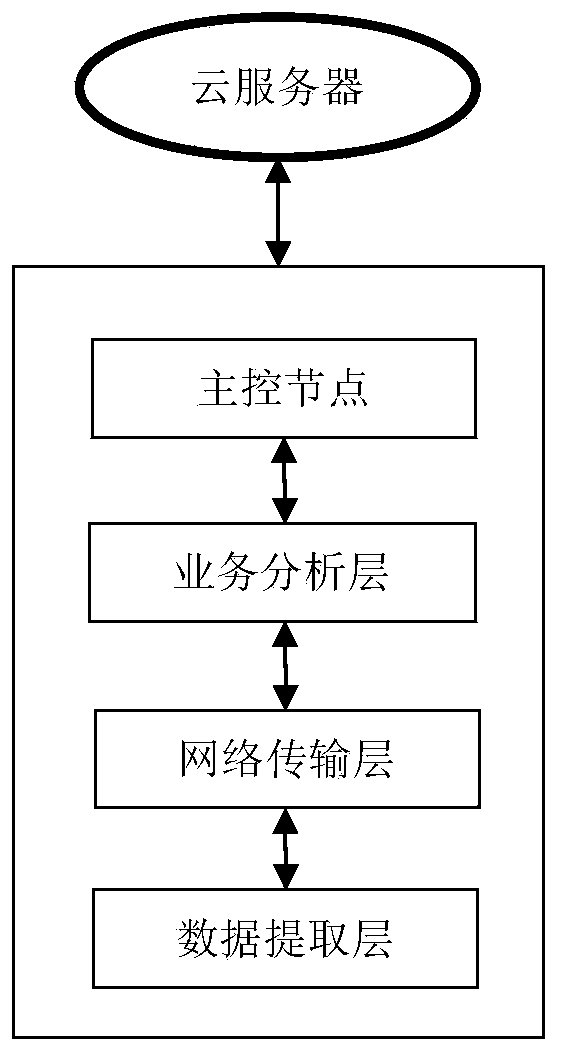
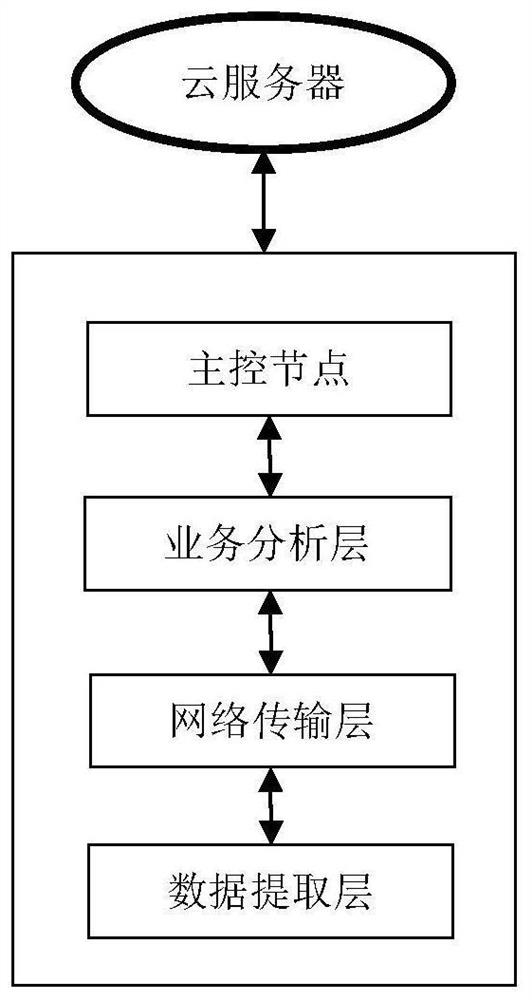
Method and system for managing network nodes in Internet of Things environment
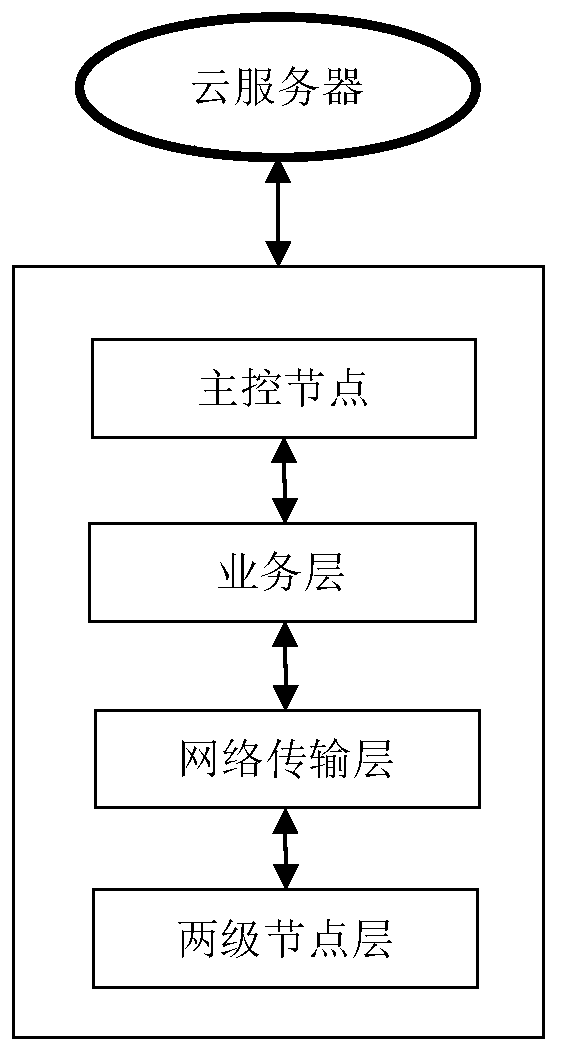
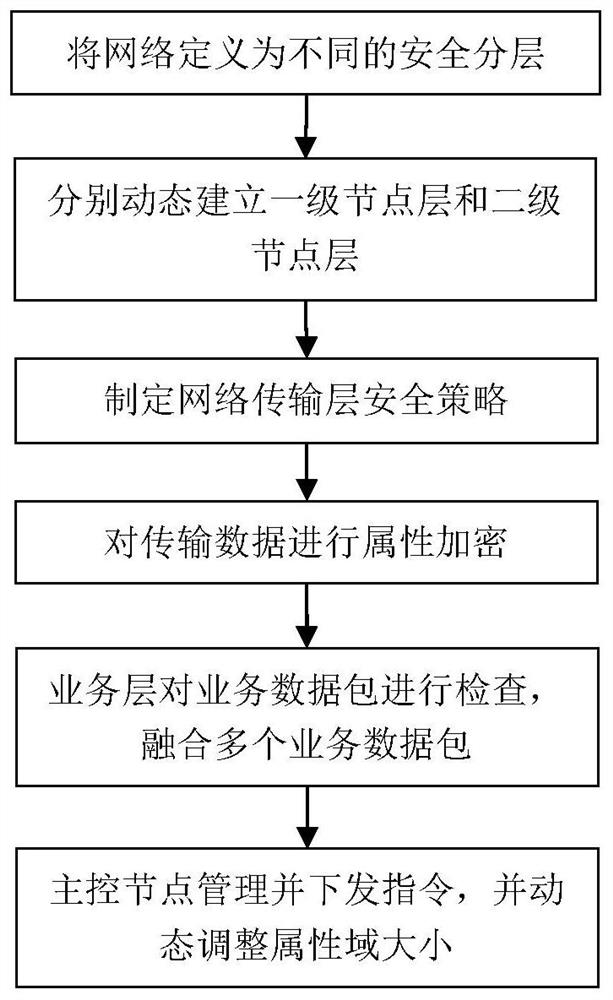
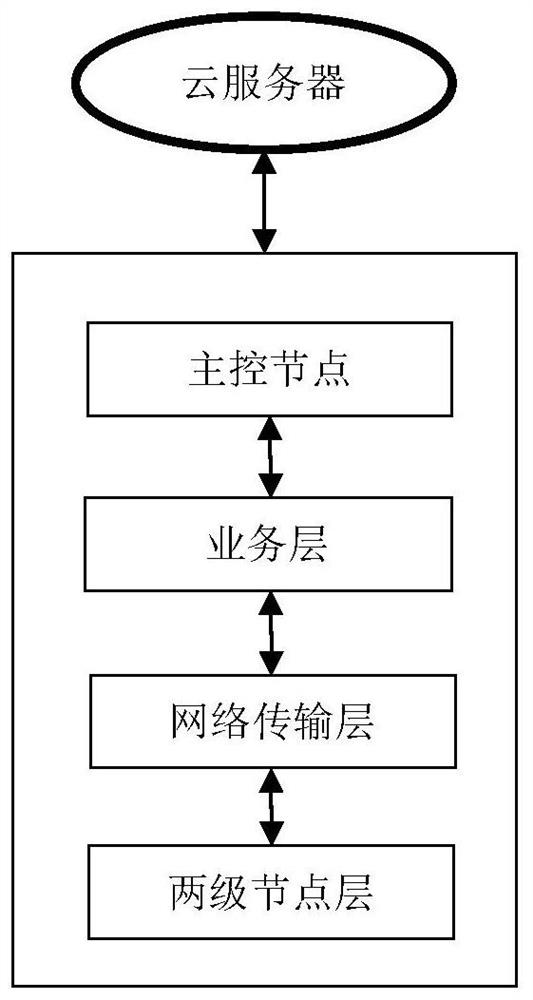
ActiveCN111585813AReduce the probability of being attackedProtect business dataData switching networksTransport layerNetwork management
According to the method and system for managing network nodes in an Internet of Things environment, specified network resources and system are defined as a first-level node layer, a second-level nodelayer, a network transmission layer, a service layer and a main control node, a two-level network management mode is adopted, multi-level management can be easily expanded, and a large number of nodeaddresses are saved. Not only can the security hierarchy be dynamically adjusted in real time according to the state of the primary node, but also the size of the attribute domain can be dynamically adjusted, the secondary node is prevented from being excessively concentrated, and the attacked probability is reduced. A technical means of attribute encryption is introduced to perform attribute encryption on the transmission data, so that the service data of different users can be better protected.
Owner:武汉思普崚技术有限公司
Attack identification method, device and apparatus and computer readable storage medium
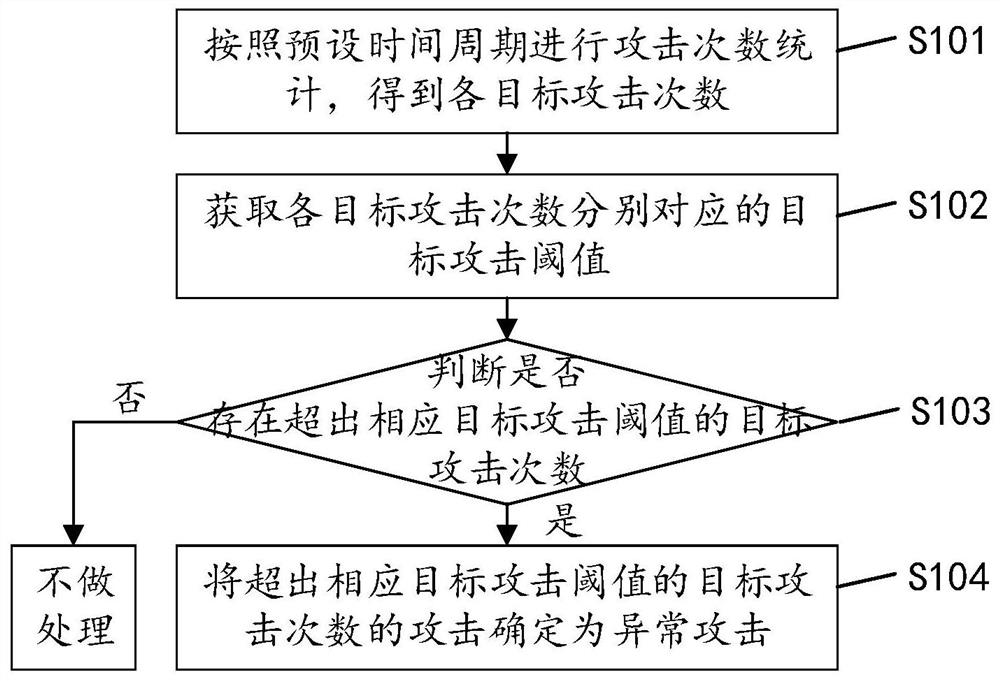
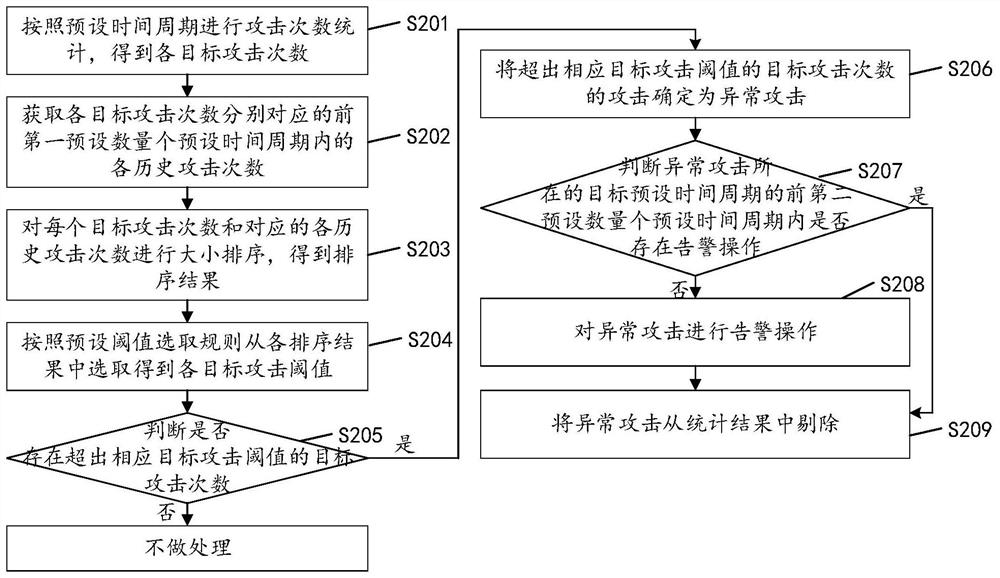
ActiveCN112333168AImprove accuracyReduce the probability of being attackedTransmissionAttackIdentification device
The invention discloses an attack identification method, which comprises the following steps of: counting attack times according to a preset time period to obtain each target attack time; obtaining atarget attack threshold corresponding to each target attack frequency; judging whether a target attack frequency exceeding a corresponding target attack threshold value exists or not; and if so, determining the attack of the target attack times exceeding the corresponding target attack threshold as an abnormal attack. By applying the attack identification method provided by the invention, the accuracy of abnormal attack identification is improved, the probability that the system is attacked is reduced, and the system security is improved. The invention also discloses an attack identification device, apparatus and a storage medium, which have corresponding technical effects.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Access security control method and system
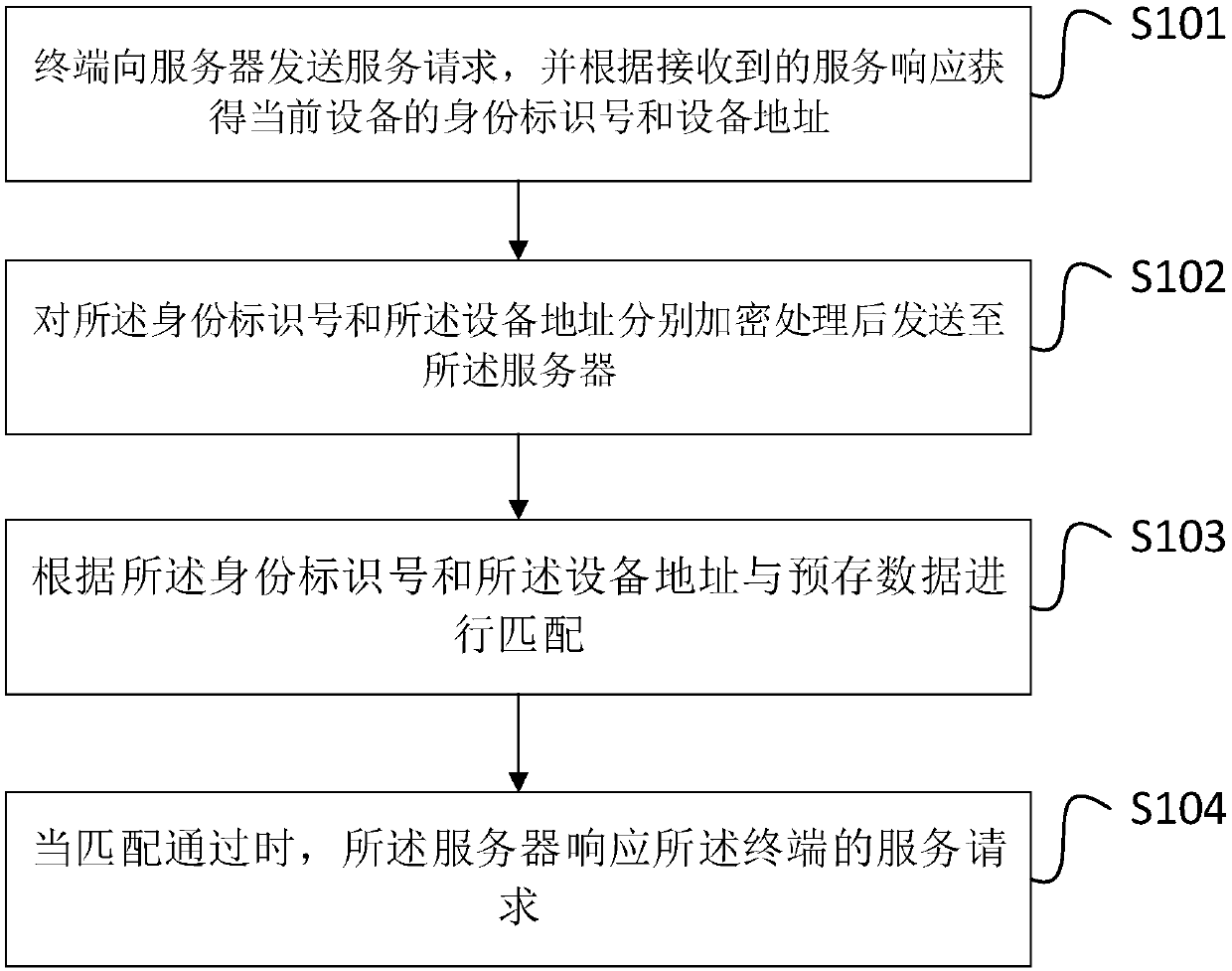
InactiveCN109617895AReduce operating costsImprove securityEncryption apparatus with shift registers/memoriesMobile identification numberSecurity controls
The invention provides an access security control method and system. The method includes: sending a service request to a server by a terminal, and obtaining an identity identification number and an equipment address of the current equipment according to received service response; respectively encrypting the identity identification number and the equipment address, and then sending the same to theserver; carrying out matching with pre-stored data according to the identity identification number and the equipment address; and responding to the service request of the terminal by the server when matching is successful. Therefore, a security factor of security access control is increased, probability of being attacked is lowered, and network operation costs are saved.
Owner:DONGGUAN JIANDA INFORMATION TECH CO LTD
Industrial internet intrusion detection and defense method and device
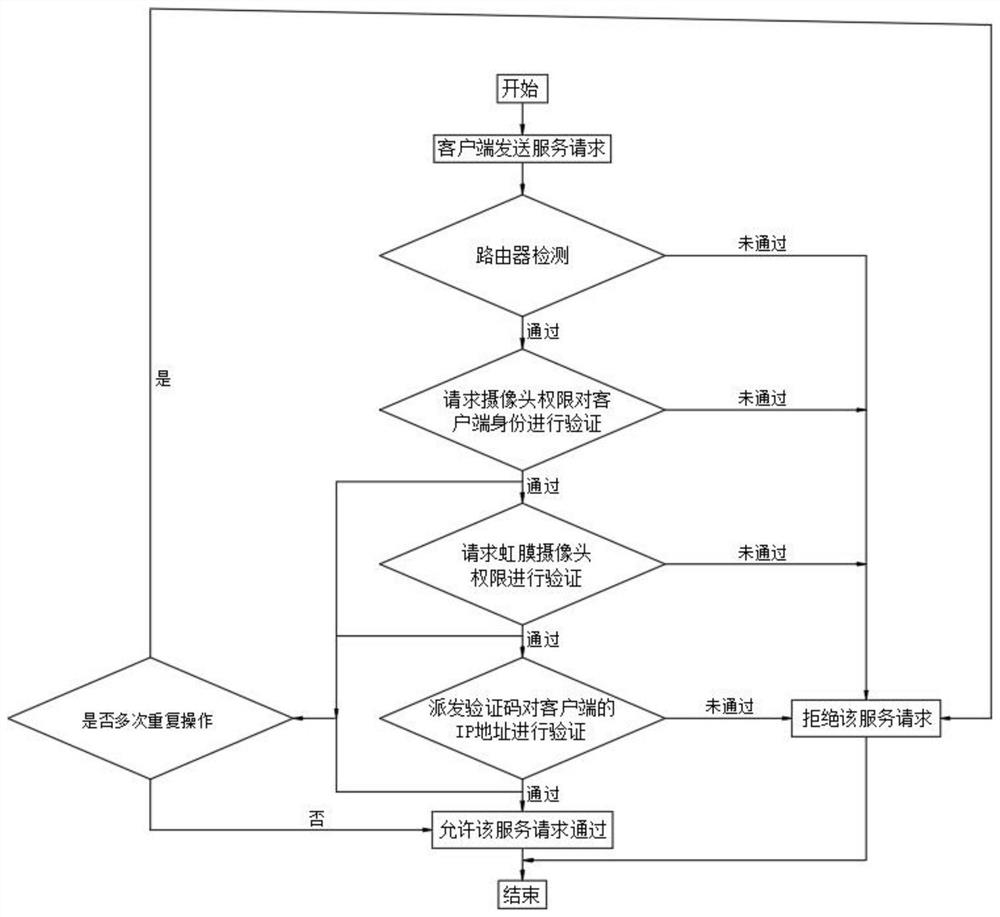
PendingCN113343197AReduce the number of operationsOperation limitDigital data authenticationIp addressThe Internet
The invention provides an industrial internet intrusion detection and defense method and device, and relates to the technical field of network security detection and defense. The industrial internet intrusion detection and defense method comprises the following steps: after a client sends a service request, the service request is detected through a router, the service request is directly rejected when the detection is not passed, and when the detection is passed, a camera authority of the client is requested to identify the face of an operator of the client to verify the identity; and when the verification is not passed, the service request is rejected. By increasing operation frequency verification, the frequency of face verification, iris authentication and IP address can be effectively reduced, the operation frequency of an operator can be well limited, the operator is prevented from carrying out operation without limitation, impact on a network can be relieved to a certain degree, the probability that the network is attacked can be reduced, the intensity that the network is attacked can be relieved, normal operation of the network is further ensured, and meanwhile the defects in the prior art can be overcome.
Owner:泉州和西利科技有限公司
A Mobile CA Node Election Method Based on MD5 Hash Information Digest
ActiveCN103905198BReduce energy consumptionReduce the probability of being attackedPower managementEncryption apparatus with shift registers/memoriesIp addressMD5
The invention discloses a mobile CA node electing method based on an MD5 hash information abstract. The method includes the steps that MD5 hash information abstract calculation is performed on certificate demand files generated by applied nodes, and demand data are obtained; each node of all the nodes is elected as a CA node according to integer data and the received demand data, wherein the integer data are obtained after data composed of the generated random number, the IP address and the MAC address are calculated through the MD5 hash information abstract; due to the fact that the key factor for determining the CA node lies in the certificate demand files generated by the applied nodes and the random number generated by the node in the Ad-hoc network, for the same applied node, a CA node electing result obtained each time differs from other results, and for the different applied nodes, the CA node electing results are different. Thus, the CA nodes are effectively prevented from providing a certificate service for a long time and the energy consumption of the CA nodes is reduced. Meanwhile, the probability of attacking the CA nodes is greatly reduced.
Owner:NINGBO UNIV
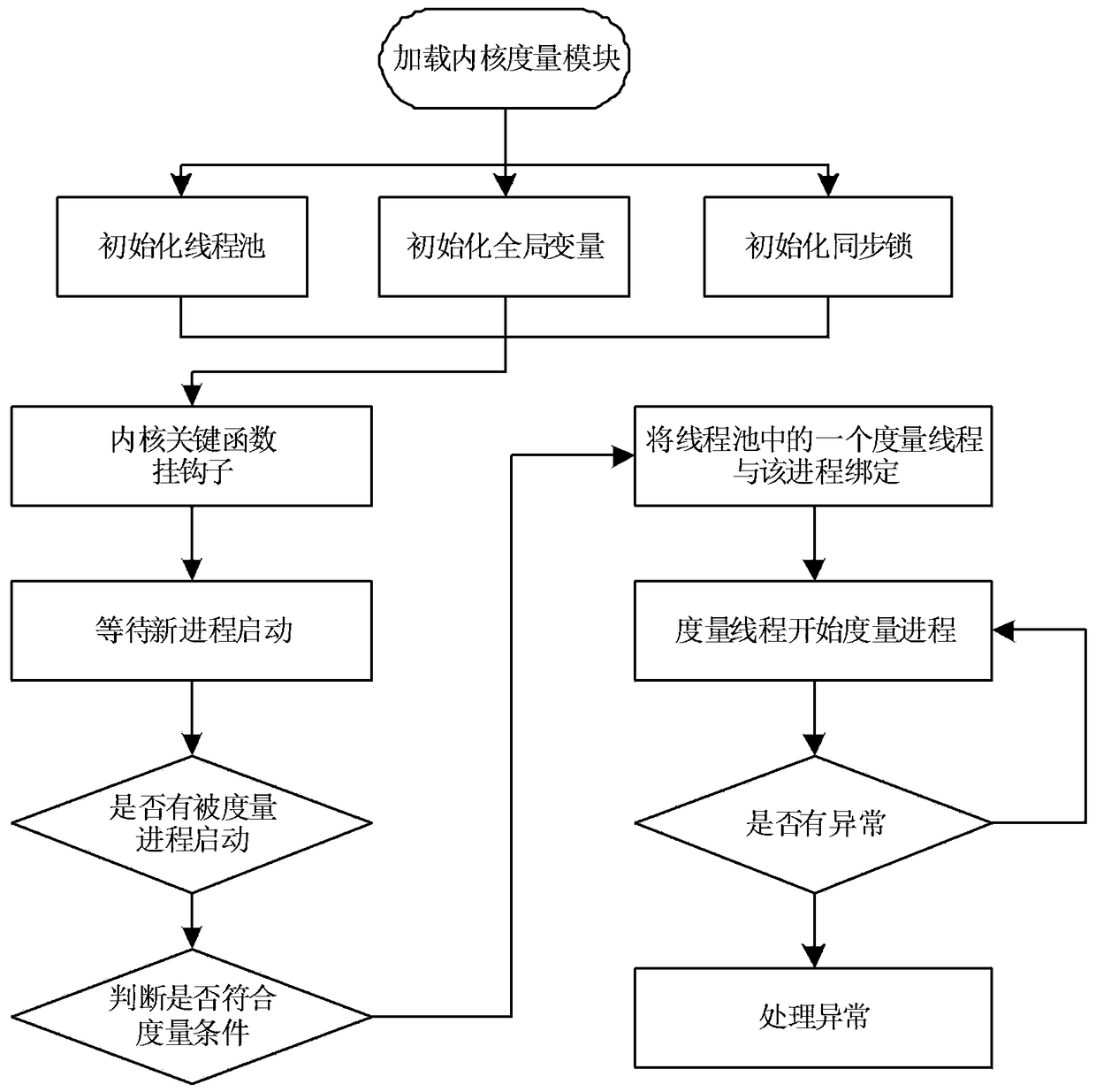
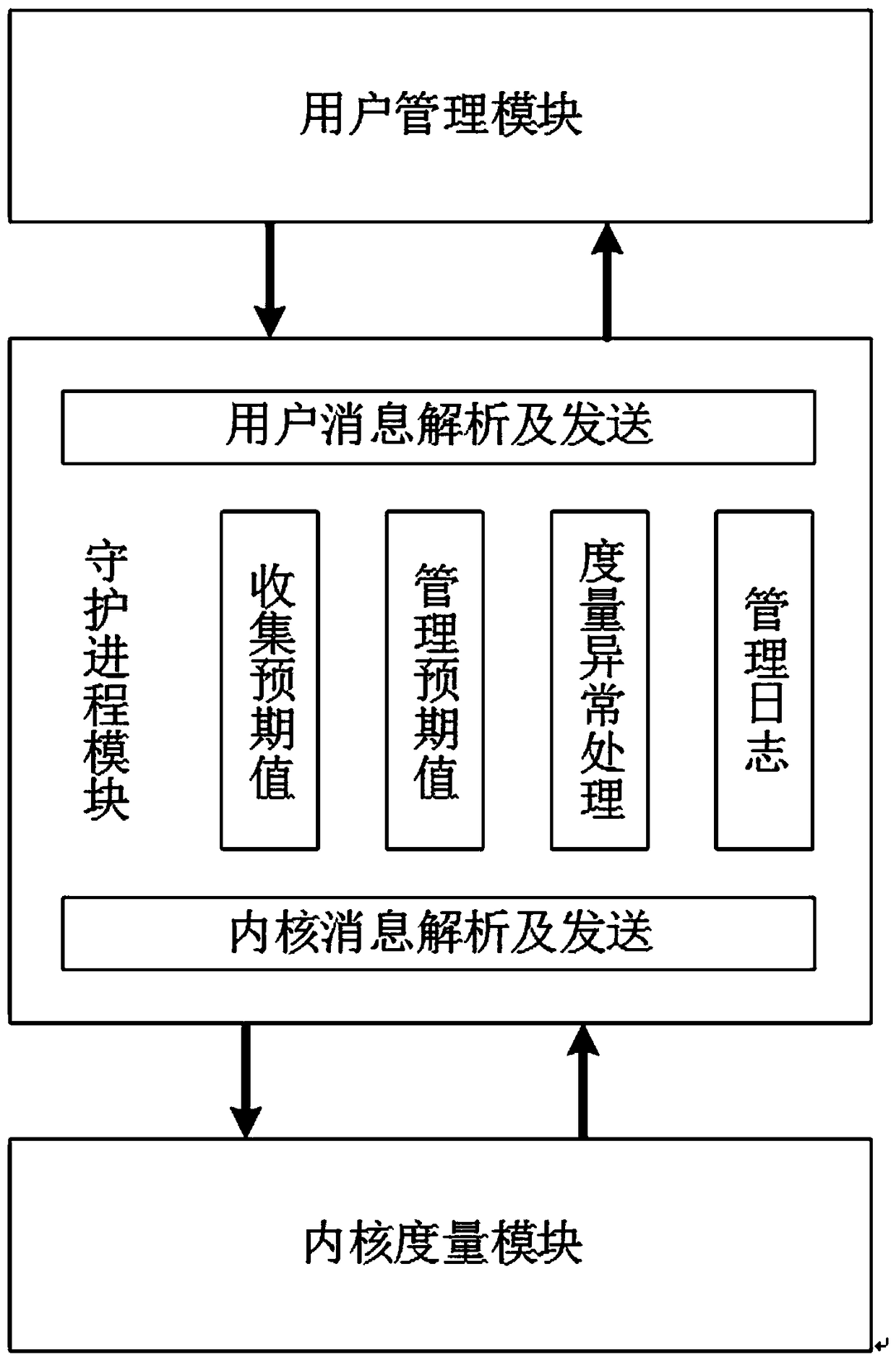
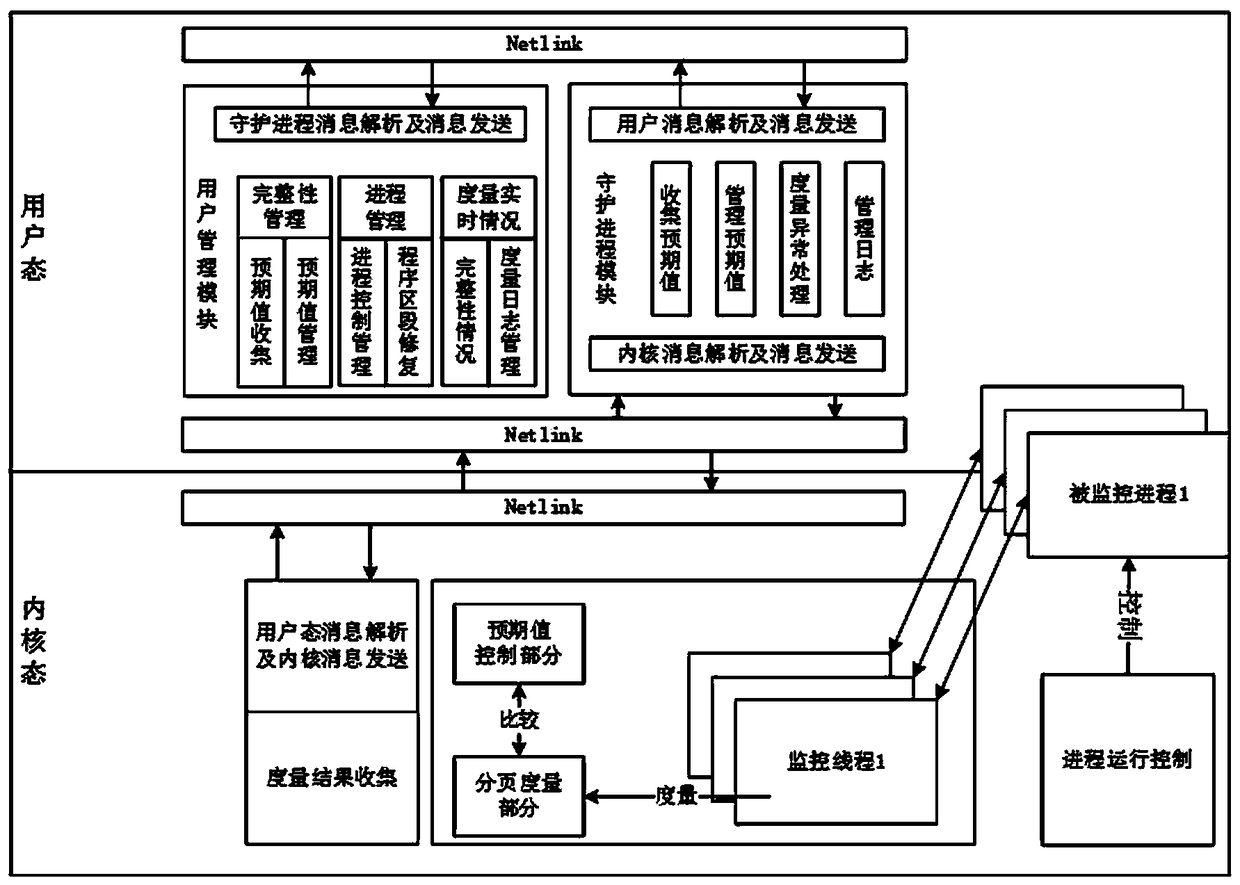
A Dynamic Measuring Method Based on Domestic TCM
ActiveCN105912929BImprove securityReduce the probability of being attackedPlatform integrity maintainanceState of artComputer science
The invention discloses a domestic TCM based dynamic measurement method. Paging measurement is performed on a program sector of a process through a TCM safe module; a kernel module instantly warns a user and pauses program execution when measurement is abnormal; the user makes a his own selection if program execution is resorted or stopped according to warning information. Compared with the prior art, the domestic TCM based dynamic measurement method can effectively improve the safe performance of a file, decrease the probability that the file is attacked, monitors a personal terminal in real time, decrease safety risk, is high in practicability, and is easy to promote.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
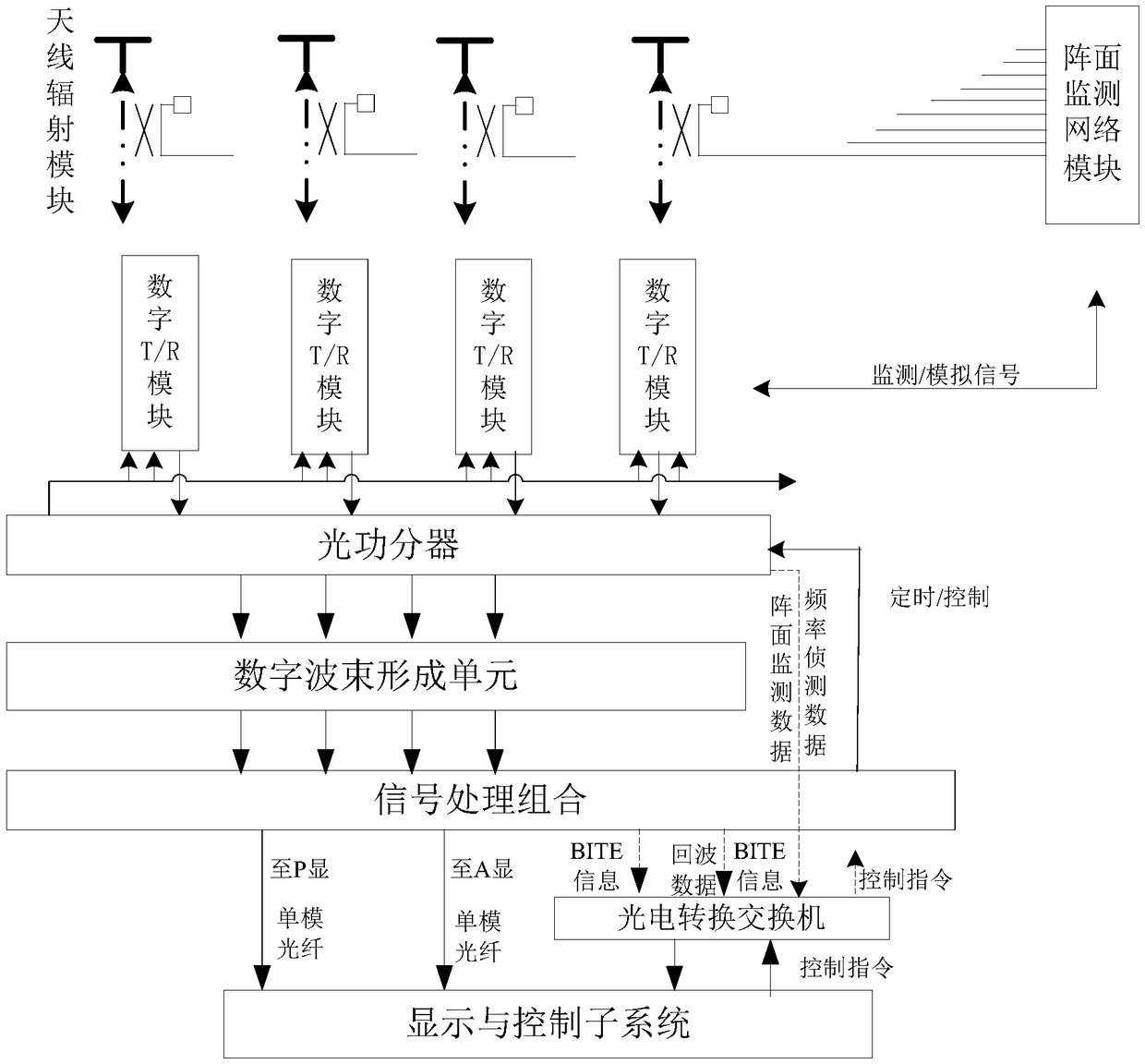
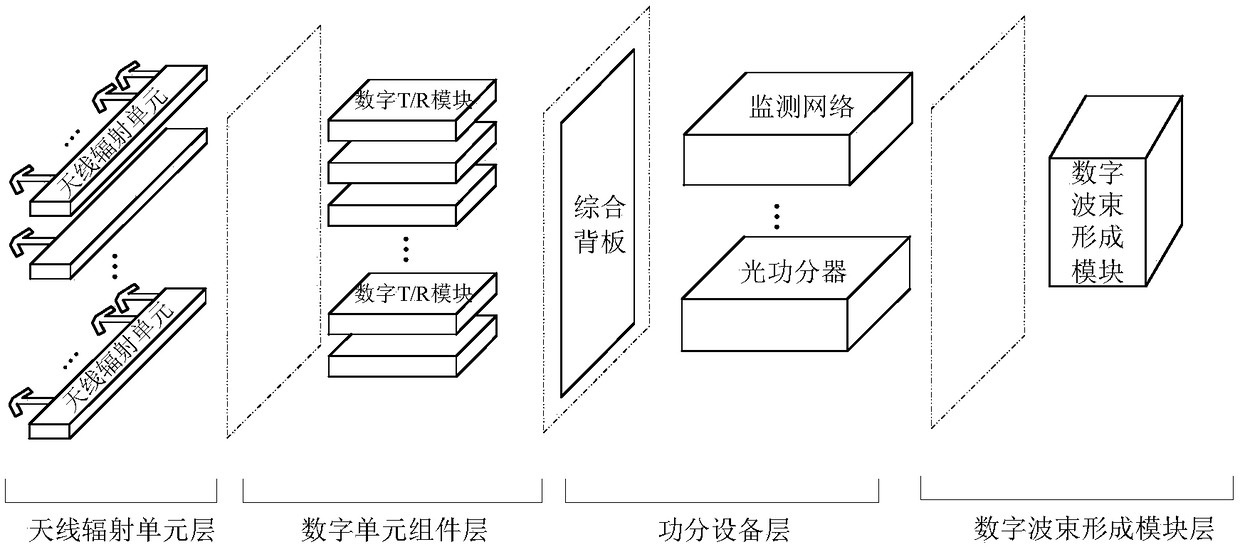
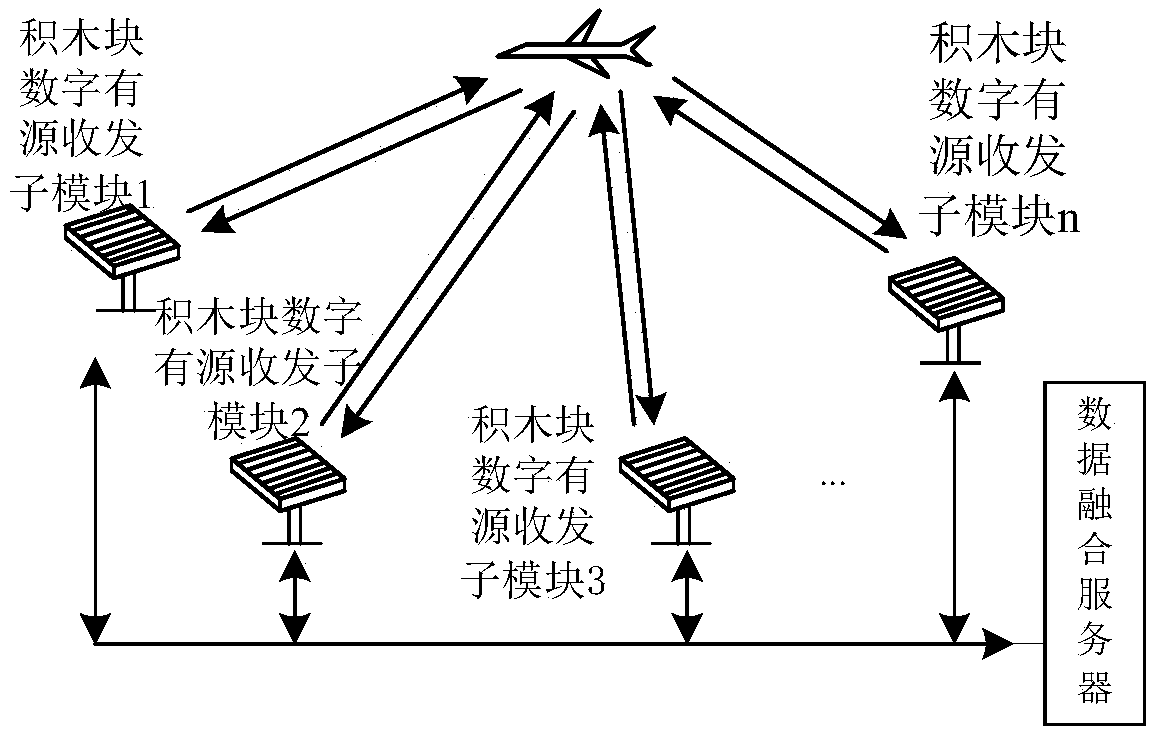
A modular and building block digital array radar system
ActiveCN106646393BIncrease flexibilityStrong remodelingWave based measurement systemsRadar systemsTransceiver
The present invention provides a modular and building block type digital array radar system. The system comprises a plurality of building block type digital active transceiver sub-modules and a data fusion server. The building block type digital active transceiver sub-modules are respectively mounted on a preset antenna array-plane framework and are respectively connected with the data fusion server. Each building block type digital active transceiver sub-module is composed of an antenna radiation module in card-inserting type connection with a comprehensive backboard, a digital T / R module, a digital beam forming unit, an optical power divider and an array-plane monitoring network module, wherein the antenna radiation module, the digital T / R module, the digital beam forming unit and the optical power splitter are sequentially in communication connection. The optical power splitter is connected with the data fusion server. The array-plane monitoring network module is respectively connected with the digital T / R module and the data fusion server. The modular and building block type digital array radar system has the advantage of multi-angle viewing angle and can effectively resist the main-lobe interference. A distributed arrangement receiving station is passive and can effectively reduce the radar intercepted probability and the radar attacked probability.
Owner:SHANGHAI SPACEFLIGHT INST OF TT&C & TELECOMM
Network data protection method for privacy leakage and corresponding firewall
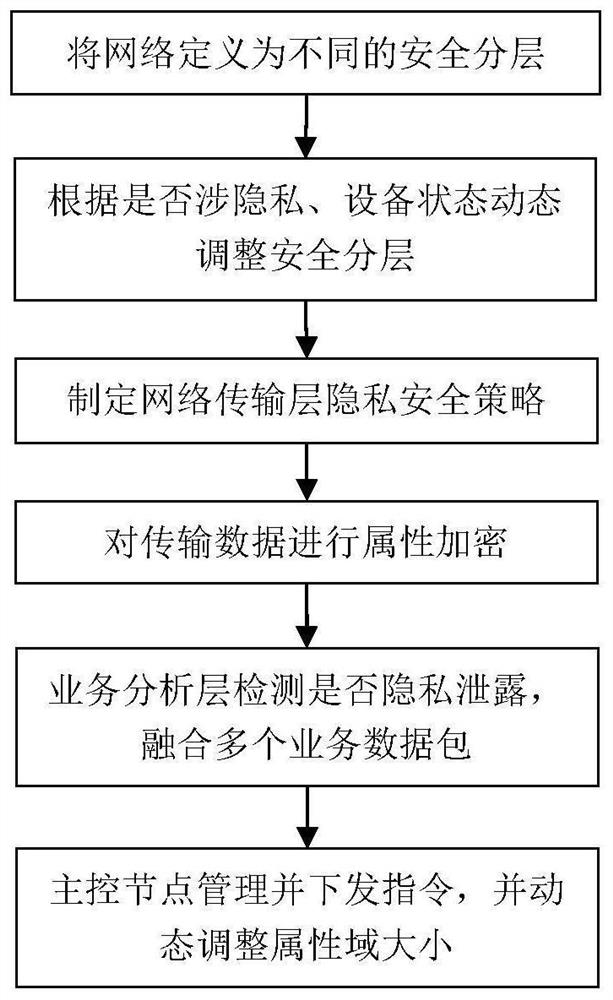
ActiveCN111586044AProtect business dataReduce the probability of being attackedTransmissionNetwork dataReliability engineering
The invention provides a network data protection method for privacy leakage and a corresponding firewall. The method comprises the following steps: detecting identified privacy data, determining whether privacy-related equipment borne by the data supports the category of the privacy data or not, analyzing the transmission intention of a user, and if the related privacy-related equipment does not support the category of the transmitted privacy data, determining that the privacy is leaked; introducing the technical means of resource security dynamic layering, removing the privacy-related equipment with privacy leakage from the corresponding security layer. The security layers can be dynamically adjusted in real time according to the state of physical equipment. A technical means of dynamically adjusting the attribute domain is introduced, so that the attacked probability is reduced, and the service data of different users can be better protected.
Owner:武汉思普崚技术有限公司
Dnp3 Protocol Fuzzing Method Based on Sequence Generative Adversarial Network
ActiveCN112104525BQuality improvementReduce redundancyNeural architecturesData switching networksScreening algorithmGenerative adversarial network
The invention discloses a DNP3 protocol fuzzy testing method based on a sequence generation confrontation network, comprising the steps of: 1. constructing a DNP3 protocol sample database; 2. preprocessing the DNP3 protocol sample data; 3. mutating the preprocessed DNP3 protocol sample data; 4. Generate primary test cases; 5. Test case similarity comparison to remove redundancy; 6. Seed test case variation; 7. DNP3 protocol fuzz testing; 8. Vulnerability verification; 9. Abnormal test case debugging and monitoring. The invention utilizes the sequence generation confrontation network to generate test cases with a high pass rate; reduces the redundancy of test cases through a screening algorithm using the similarity of use cases as an index; introduces a random mutation strategy to mutate test cases, and improves the diversity of test cases and the probability of loophole discovery ; By analyzing the stack frame information of the program when the vulnerability occurs, find and record the cause of the vulnerability, thereby reducing the probability of the industrial control system being attacked and improving the security of the industrial control system.
Owner:XIAN UNIV OF SCI & TECH
Unified security management system and identity authentication method
ActiveCN113114464AReduce the probability of being attackedReduce leakageUser identity/authority verificationInternet privacySafety management systems
The invention discloses a unified security management system and an identity authentication method. The system comprises a security management portal and a security management center, the security management center further comprises a centralized authentication service, a remote user dialing authentication service, a program account interface and a one-time password service; the remote user dialing authentication service is used for forwarding an authentication request of a host to the centralized authentication service for centralized authentication; and the program account interface and the one-time password service are used for distributing one-time access passwords for the application programs when the application programs log in the host, and the one-time password service is further used for providing the one-time access passwords for the centralized authentication service for identity authentication. Therefore, according to the scheme of the invention, based on the transformed 4A system, the security of the host can be improved, the software complexity is reduced, the user information leakage is effectively prevented, and the possibility that a password is cracked is avoided.
Owner:中国移动通信集团重庆有限公司 +1
A security management method and system for centralized network data
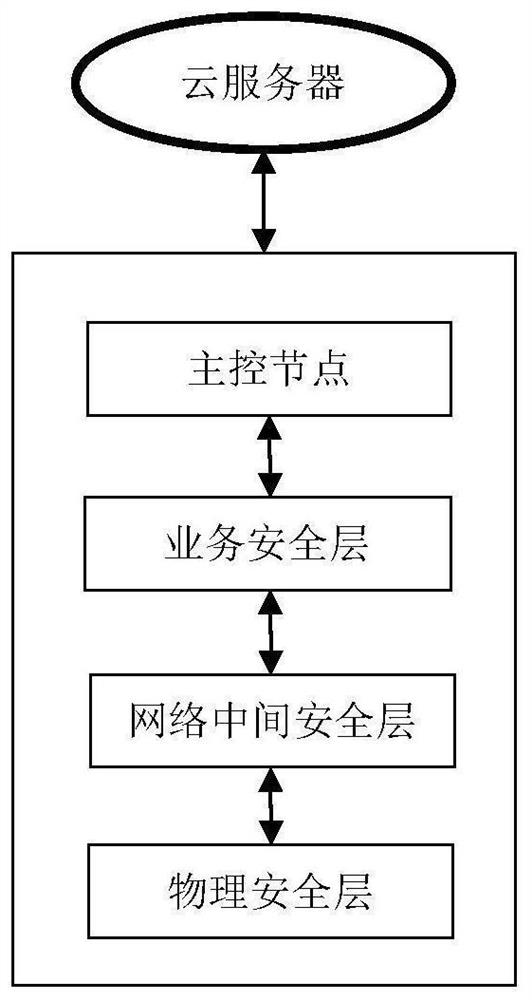
ActiveCN111586047BReduce the probability of being attackedProtect business dataSecuring communicationPhysical securityEngineering
The present invention provides a security management method and system for centralized network data, which defines designated network resources as physical security layer, network intermediate security layer, service security layer and main control node, and defines the protection system as physical security layer, network The four parts of the middle security layer, the business security layer and the main control node realize the one-to-one correspondence between the composition of the protection system and the specified network layer. Not only can the security layer be dynamically adjusted in real time according to the state of the physical device, but also the size of the attribute domain can be dynamically adjusted to avoid excessive concentration of physical devices and reduce the probability of being attacked. The technical means of attribute encryption is introduced to encrypt the transmitted data to better protect the business data of different users.
Owner:武汉思普崚技术有限公司
Connection control method, device, electronic device and readable storage medium
ActiveCN111107134BImprove network securityReduce the probability of being attackedTransmissionEngineeringProxy server
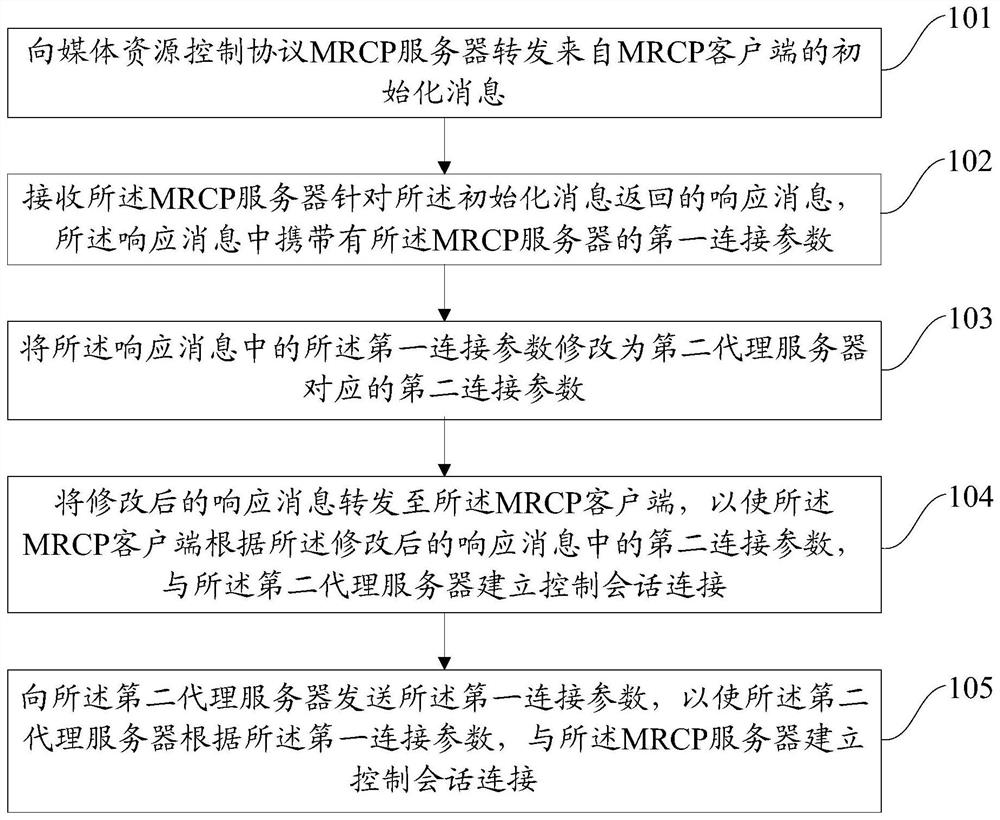
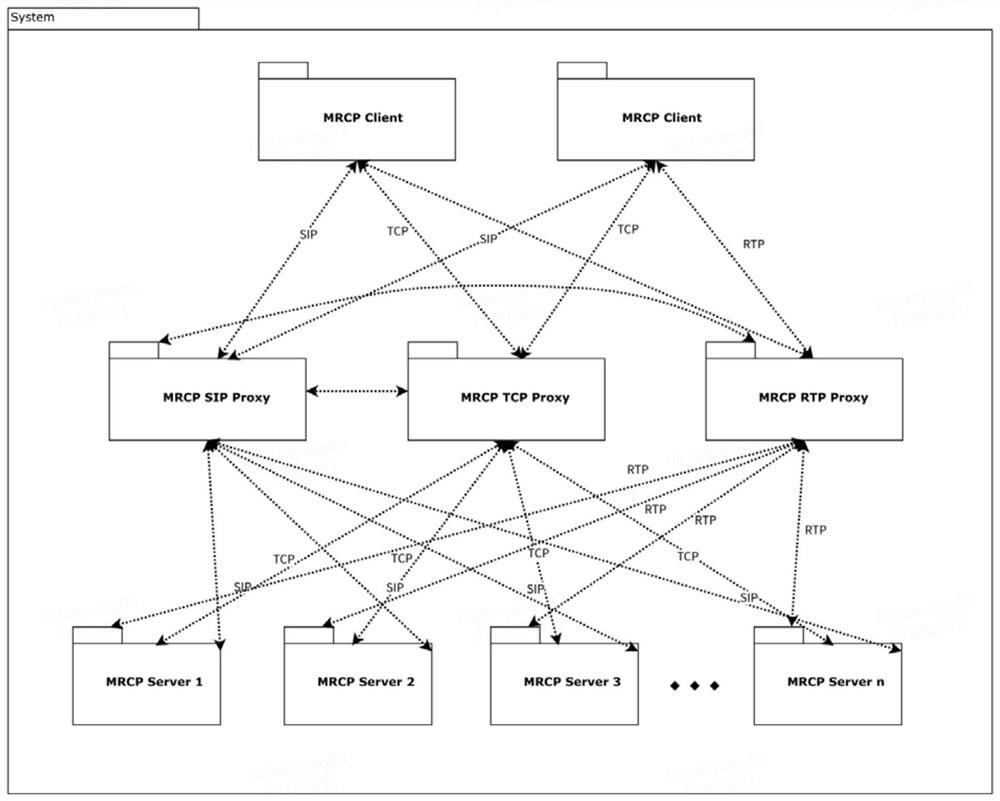
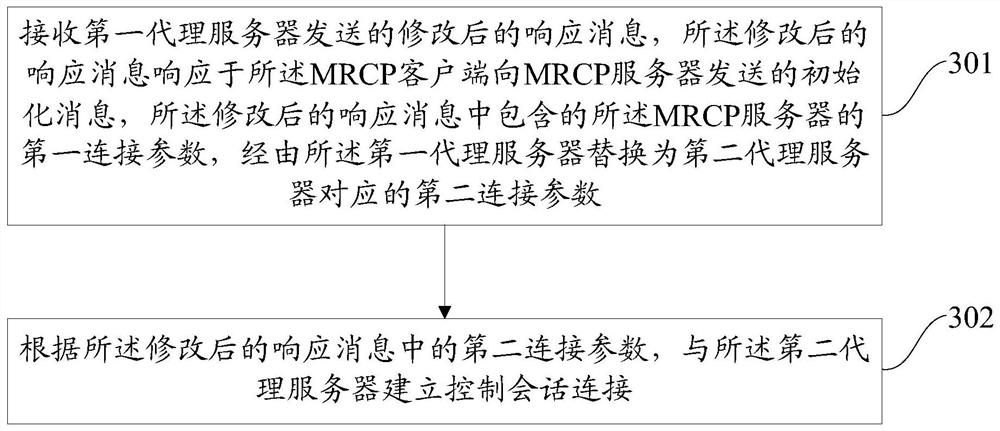
Embodiments of the present disclosure provide a connection control method, device, electronic device, and readable storage medium. The method includes: forwarding an initialization message from the MRCP client to the MRCP server; receiving a response message returned by the MRCP server for the initialization message, The first connection parameter of the MRCP server is carried in the response message; the first connection parameter in the response message is modified to the second connection parameter corresponding to the second proxy server; the modified response message is forwarded to the MRCP client, so that the MRCP The client establishes a control session connection with the second proxy server according to the second connection parameter in the modified response message; sends the first connection parameter to the second proxy server, so that the second proxy server, according to the first connection parameter, Establish a control session connection with the MRCP server. The embodiments of the present disclosure can improve the network security of the MRCP server.
Owner:BEIJING SANKUAI ONLINE TECH CO LTD
A method and system for managing network nodes in an Internet of Things environment
ActiveCN111585813BReduce the probability of being attackedProtect business dataSecuring communicationTransport layerThe Internet
The present invention provides a method and system for managing network nodes in an Internet of Things environment, defining designated network resources and systems as five parts: a first-level node layer, a second-level node layer, a network transmission layer, a business layer, and a master control node, and Using two-level network management, it is easy to expand to multi-level management, saving a lot of node addresses. Not only can the security layer be dynamically adjusted in real time according to the status of the first-level nodes, but also the size of the attribute domain can be dynamically adjusted to avoid excessive concentration of the second-level nodes and reduce the probability of being attacked. The technical means of attribute encryption is introduced to encrypt the transmitted data to better protect the business data of different users.
Owner:武汉思普崚技术有限公司
Voting method based on P2P network
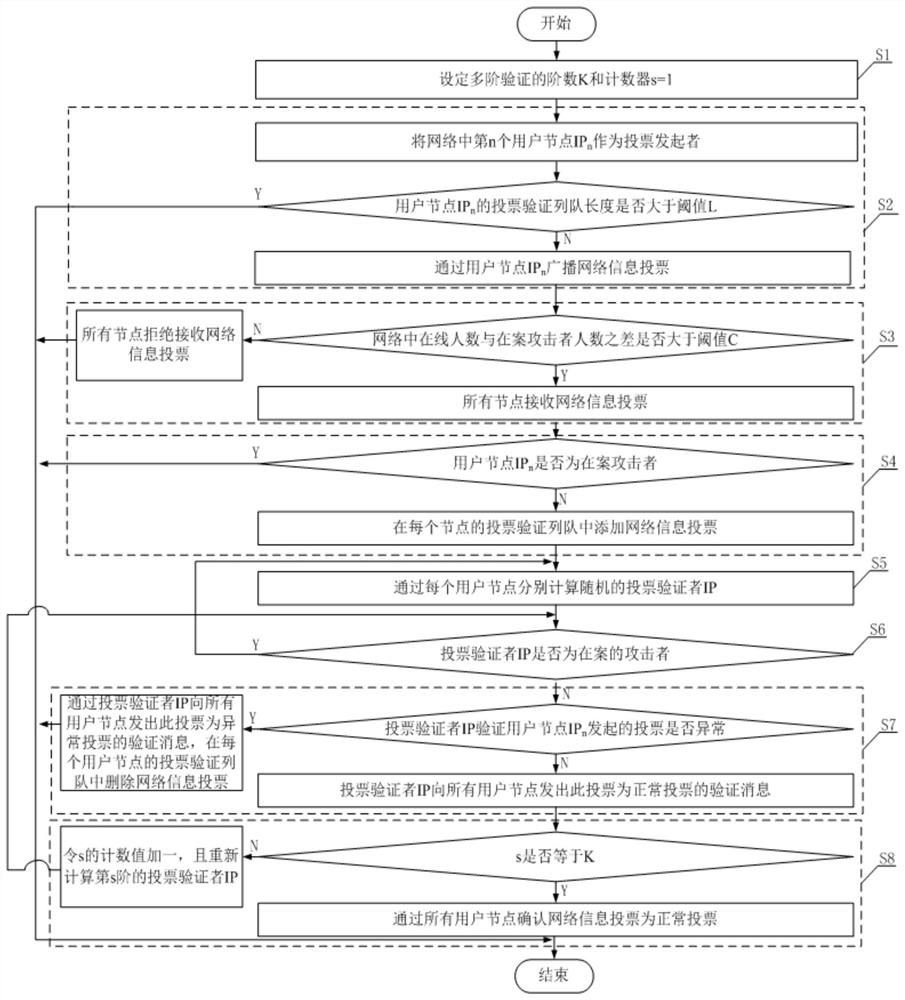
ActiveCN111696245ASave bandwidthControl voting concurrencyVoting apparatusTransmissionAttackEngineering
The invention discloses a voting method based on a P2P network. The voting method comprises the following core characteristics: a broadcasting method for saving network bandwidth; controlling the network voting concurrency; a multi-order verification / confirmation method which can reduce the attacked probability to be close to zero; and performing quantitative immunization against attacks. According to the method, several technical difficulties, such as network bandwidth occupation, network voting concurrency control and quantitative immunity of attack defense, which hinder the P2P network voting system from being put into use are solved.
Owner:郭平波
A network data protection method for privacy leakage and corresponding firewall
ActiveCN111586044BProtect business dataReduce the probability of being attackedTransmissionEngineeringNetwork data
The invention provides a network data protection method for privacy leakage and a corresponding firewall. The method comprises the following steps: detecting identified privacy data, determining whether privacy-related equipment borne by the data supports the category of the privacy data or not, analyzing the transmission intention of a user, and if the related privacy-related equipment does not support the category of the transmitted privacy data, determining that the privacy is leaked; introducing the technical means of resource security dynamic layering, removing the privacy-related equipment with privacy leakage from the corresponding security layer. The security layers can be dynamically adjusted in real time according to the state of physical equipment. A technical means of dynamically adjusting the attribute domain is introduced, so that the attacked probability is reduced, and the service data of different users can be better protected.
Owner:武汉思普崚技术有限公司
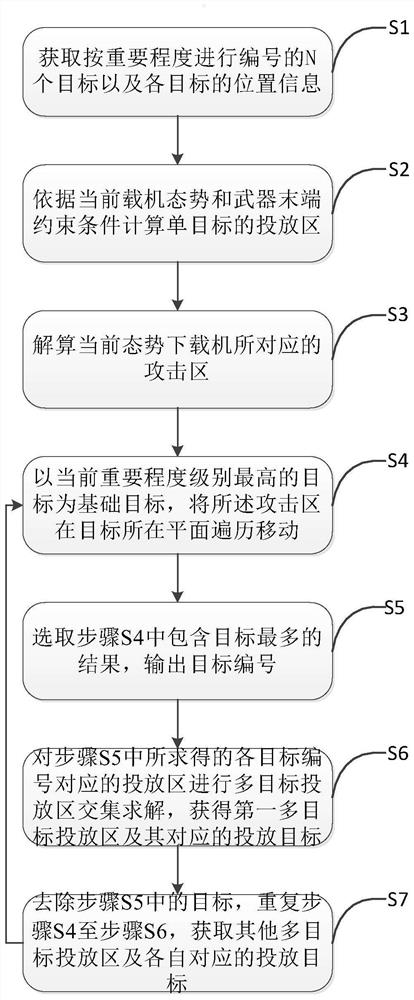
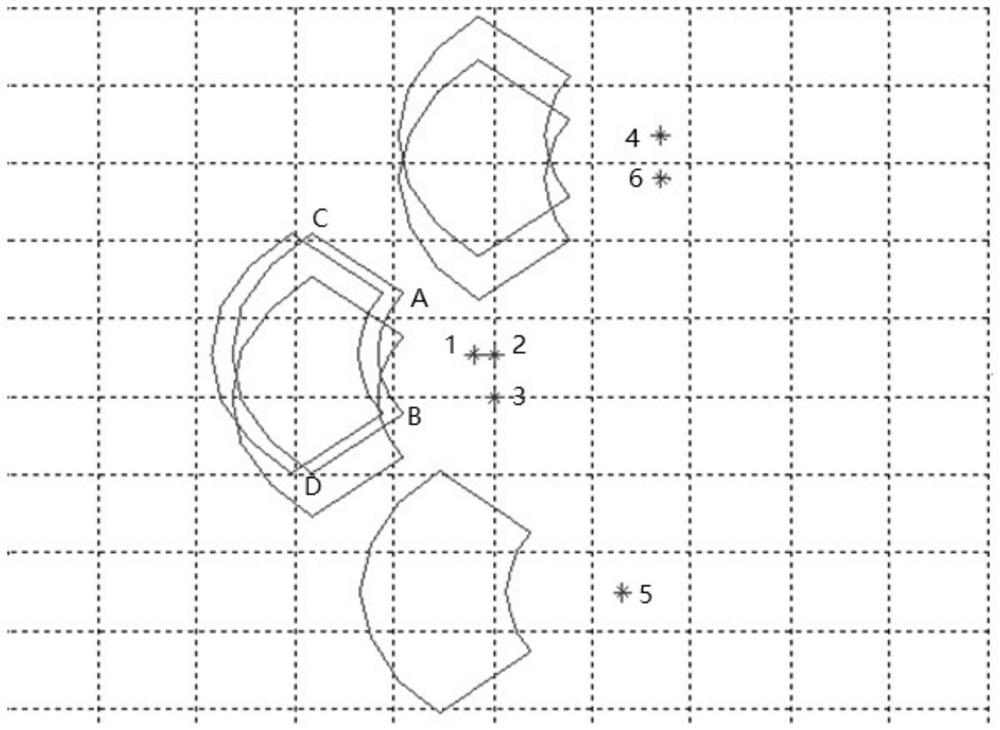
Attack batch division method in complex environment
ActiveCN112650305AShorten reflection area increase timeReduce the number of opening doorsTarget-seeking controlSimulationUncrewed vehicle
The invention belongs to the technical field of unmanned aerial vehicle control, and particularly relates to an attack batch division method in a complex environment. The method comprises the following steps: S1, acquiring each target position numbered according to importance degree; S2, according to the current aerial carrier situation and weapon tail end constraint conditions, calculating a single-target launching area; S3, calculating an attack area corresponding to the current situation downloader; S4, taking the target with the highest current importance level as a basic target, and traversing and moving the attack area in a plane where the target is located; S5, selecting a result containing the most targets, and outputting a target number; S6, performing multi-target release area intersection solution on the release areas corresponding to the solved target numbers to obtain a first multi-target release area; and S7, removing the targets in the step S5, repeating the steps S4 to S6, and obtaining other multi-target delivery areas. According to the invention, the cabin door opening time is shortened, and the radar reflection area increasing time is shortened, so that the attacked probability is reduced.
Owner:SHENYANG AIRCRAFT DESIGN INST AVIATION IND CORP OF CHINA
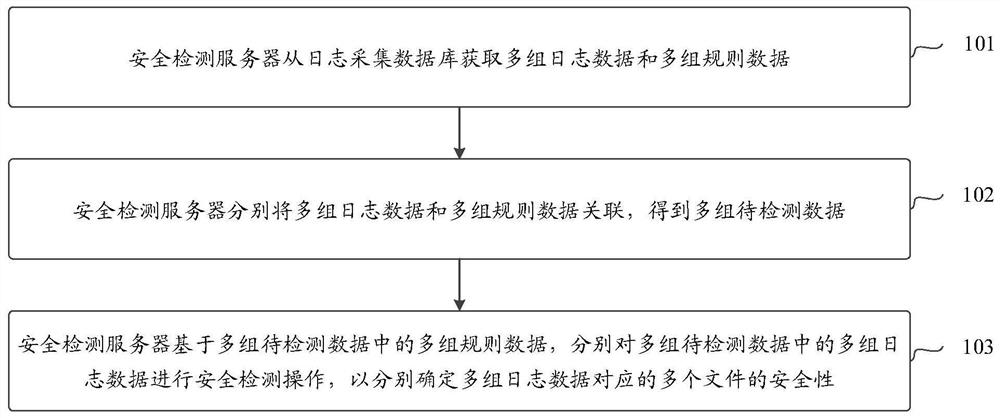
File security detection method and device and electronic equipment
PendingCN111914252ADetect securityImprove security detection efficiencyPlatform integrity maintainanceData packData library
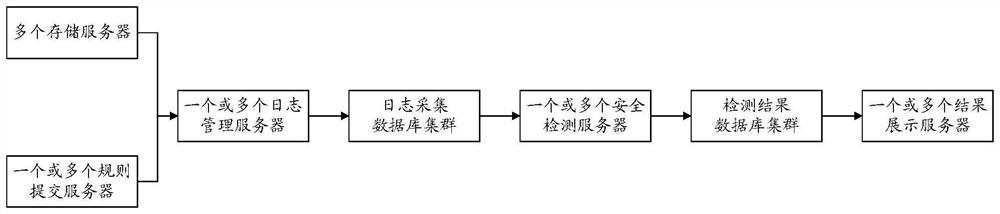
The invention discloses a file security detection method and device and electronic equipment, and is used for solving the problem that the security of files cannot be rapidly detected in batches in the prior art. The method comprises the steps that a security detection server acquires multiple groups of log data and multiple groups of rule data from a log acquisition database; the security detection server associates the multiple groups of log data with the multiple groups of rule data to obtain multiple groups of to-be-detected data, and one group of to-be-detected data comprises one group oflog data and one group of rule data; and the security detection server performs security detection operation on multiple groups of log data in the multiple groups of to-be-detected data based on multiple groups of rule data in the multiple groups of to-be-detected data, so as to determine the security of multiple files corresponding to the multiple groups of log data.
Owner:新浪技术(中国)有限公司
Information distribution method for mobile terminal
ActiveCN101198148BReduce omissionsReduce errorsSecurity arrangementRelevant informationDistribution method
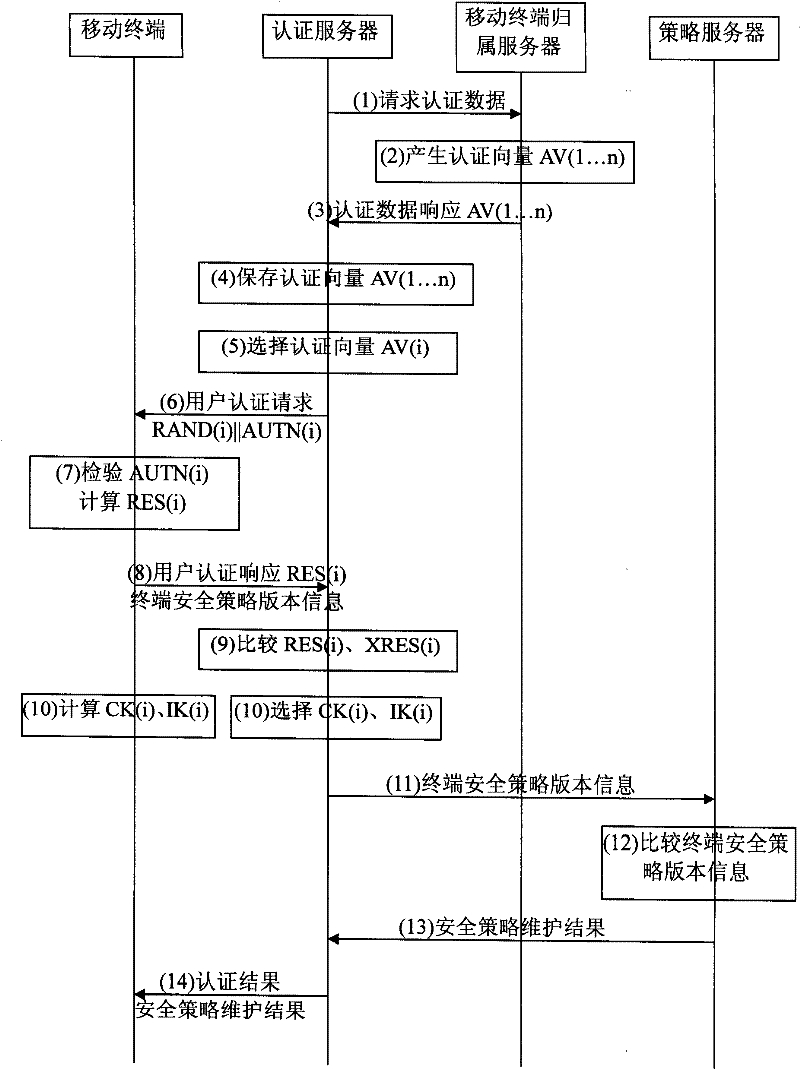
The present invention relates to an information distribution method of mobile terminal; in the process of mutual authentication between a mobile terminal and a network server, the mobile terminal sends the relevant information code of the mobile terminal to an authentication server; after the authentication succeeds, a session key is established; the authentication server sends the relevant information code of the mobile terminal to the network server; according to the relevant information code of the mobile terminal, the network server completes the operation of information distribution and returns operating results to the authentication server; the authentication server informs the mobile terminal of the authentication and the information distribution results. With the method of the present invention, the information distribution is embedded to the AKA process, reduces the communication cost and can reduce omissions and errors of information distribution by the network server as possible; the present invention can use the session key consulted in the authentication process to encrypt distributed information and reduces the probability of being attacked. The key consulted in theAKA process has safe protection on data distribution and improves the safe performance.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com