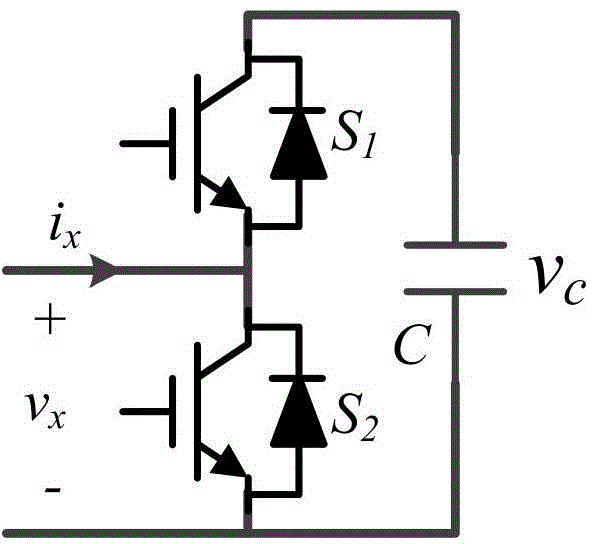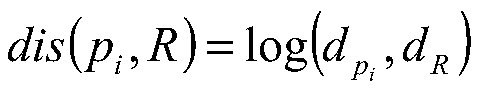Patents
Literature
124 results about "Communication complexity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
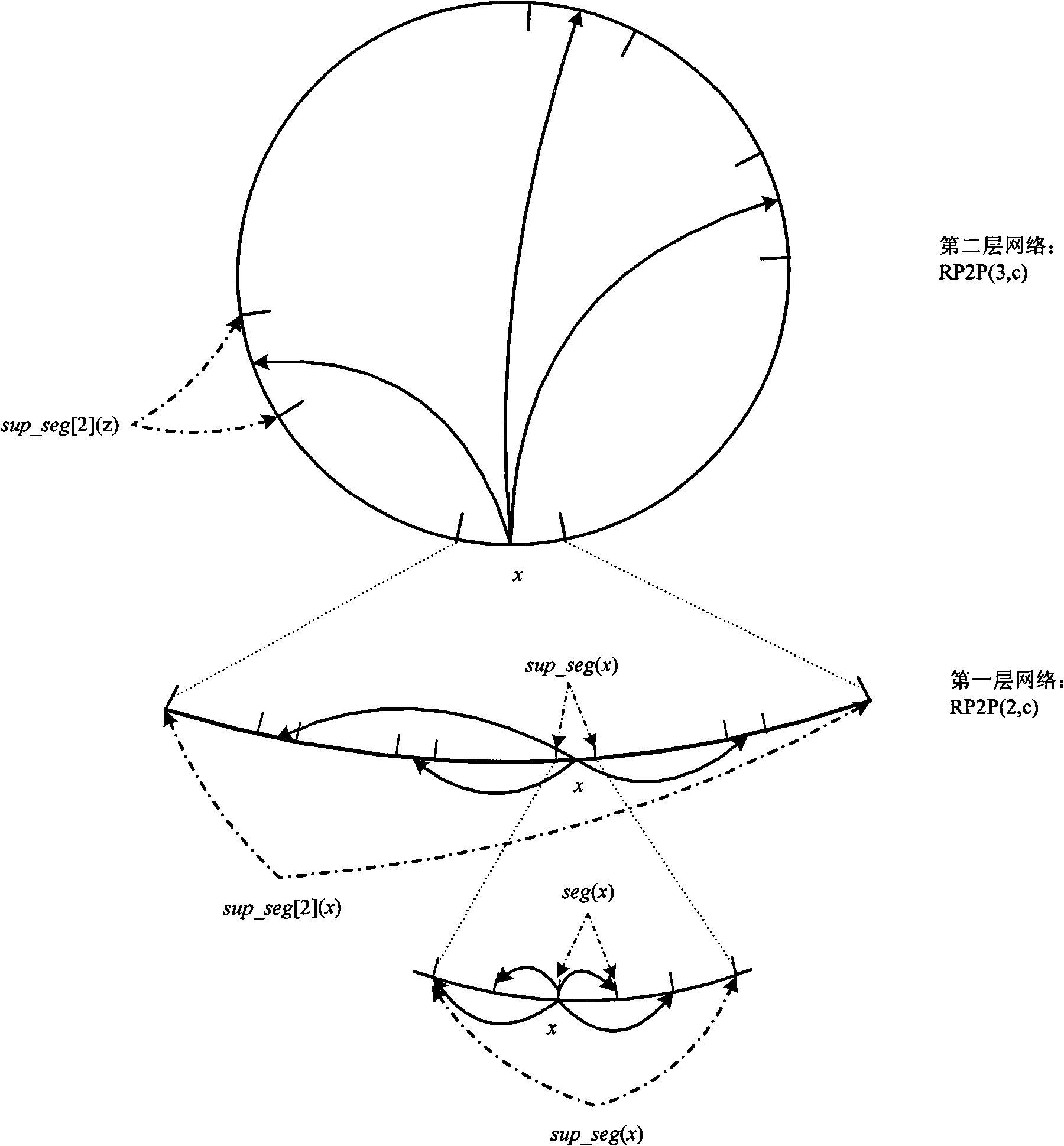
In theoretical computer science, communication complexity studies the amount of communication required to solve a problem when the input to the problem is distributed among two or more parties. The study of communication complexity was first introduced by Andrew Yao in 1979, while studying the problem of computation distributed among several machines. The problem is usually stated as follows: two parties (traditionally called Alice and Bob) each receive a (potentially different) n-bit string x and y.
Finite element methods and systems
ActiveUS20150120261A1Address limitationsComputation using non-denominational number representationDesign optimisation/simulationMulticore architectureCpu architecture
The computational efficiency of Finite Element Methods (FEM) on parallel architectures is typically severely limited by sparse iterative solvers. Standard iterative solvers are based on sequential steps of global algebraic operations, which limit their parallel efficiency, and prior art techniques exploit sophisticated programming techniques tailored to specific CPU architectures to improve performance. The inventors present a FEM Multigrid Gaussian Belief Propagation (FMGaBP) technique that eliminates global algebraic operations and sparse data-structures based upon reformulating the variational FEM into a probabilistic inference problem based upon graphical models. Further, the inventors present new formulations for FMGaBP, which further enhance its computation and communication complexities where the parallel features of FMGaBP are leveraged to multicore architectures.
Owner:MCGILL UNIV
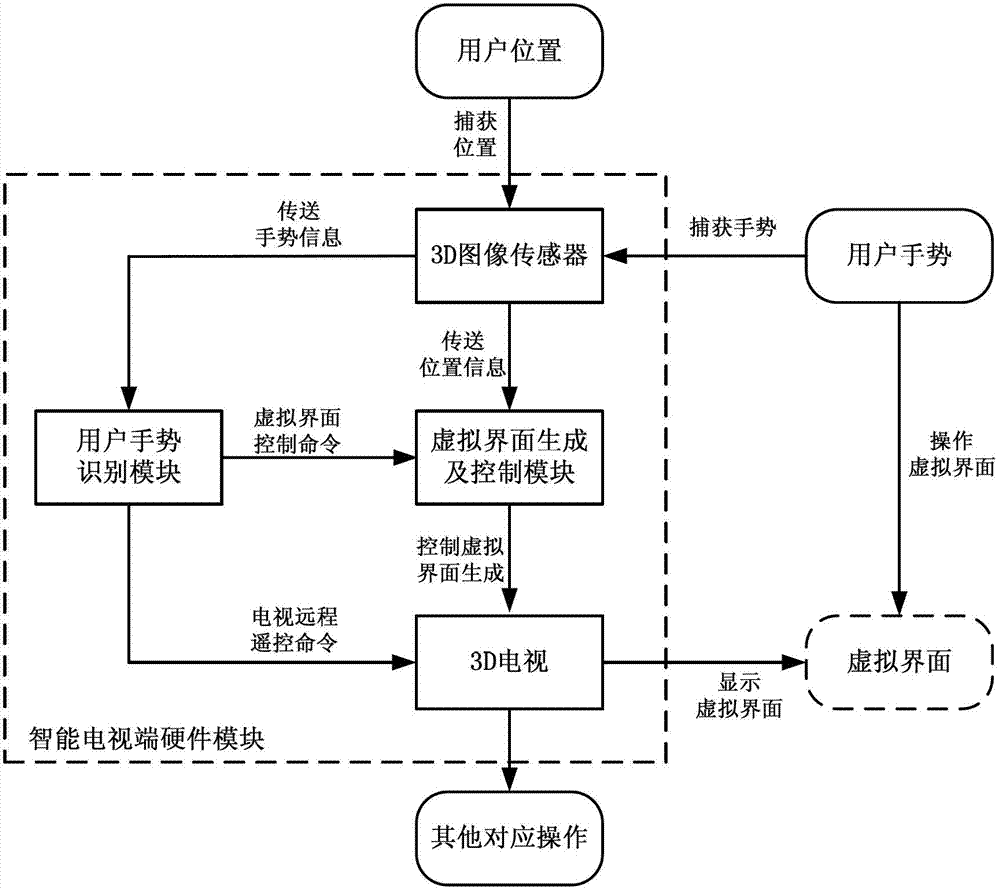
Man-machine interactive system and man-machine interactive method of smart television
InactiveCN102769802ASwitch anytimeInput/output for user-computer interactionSelective content distributionMan machineHuman–computer interaction
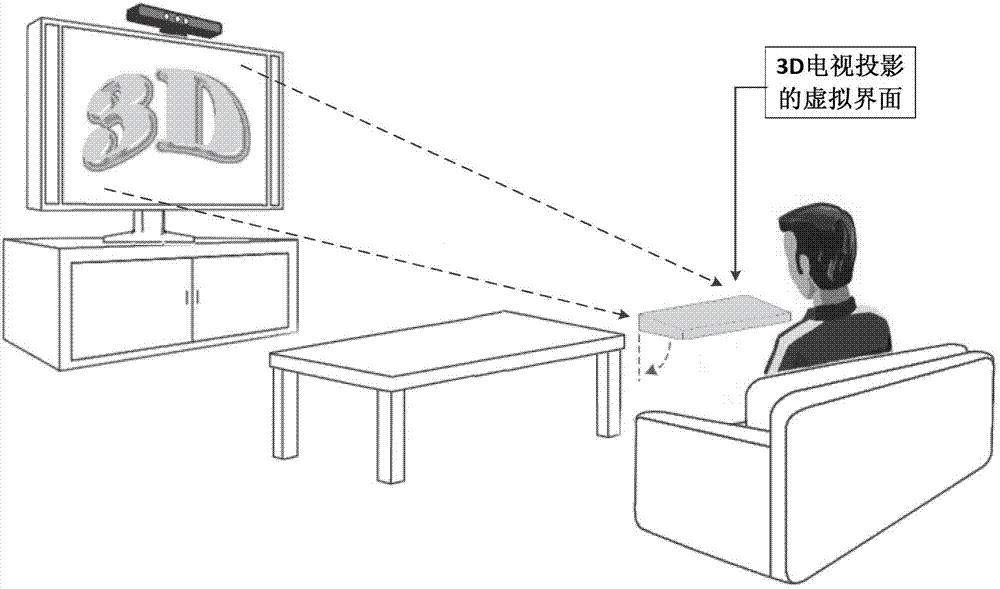
The invention discloses a man-machine interactive system and a man-machine interactive method of a smart television. The man-machine interactive system comprises a 3D (three-dimensional) television, a virtual interface generating and control module, a 3D image sensor and a user gesture recognition module, wherein the virtual interface generating and control module is used for generating and controlling optimal positions and angles of virtual interface imaging; the 3D image sensor is used for obtaining object depth or three-dimensional visual information; and the user gesture recognition module is used for analyzing user depth or three-dimensional image information to recognize postures or gestures of a user, obtaining a user operating intention and sending a corresponding control command by combining virtual interface information. The system obtains the user position and the distance by the aid of the 3D image sensor, the user performs point touch actions on a virtual interface with fingers by the aid of the virtual interface generating and control module and by controlling the projected virtual interface of the 3D television, and the system obtains the operating intention of the user by capturing gesture information of the user and combining the virtual interface to perform corresponding operations, so that man-machine interaction is achieved. Communication complexity is greatly simplified by relying on the virtual interface, and the system is high in practicality.
Owner:XI AN JIAOTONG UNIV
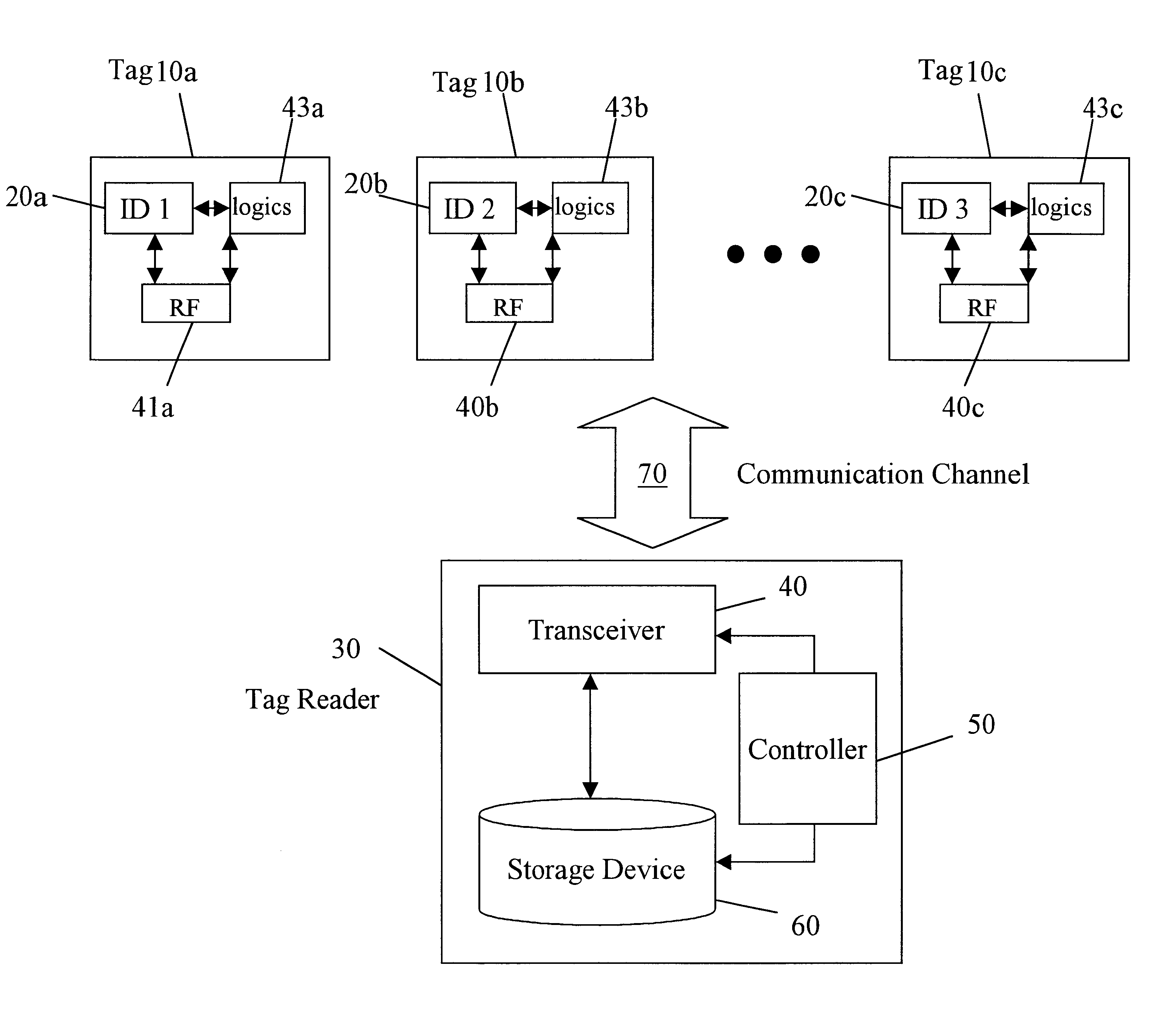
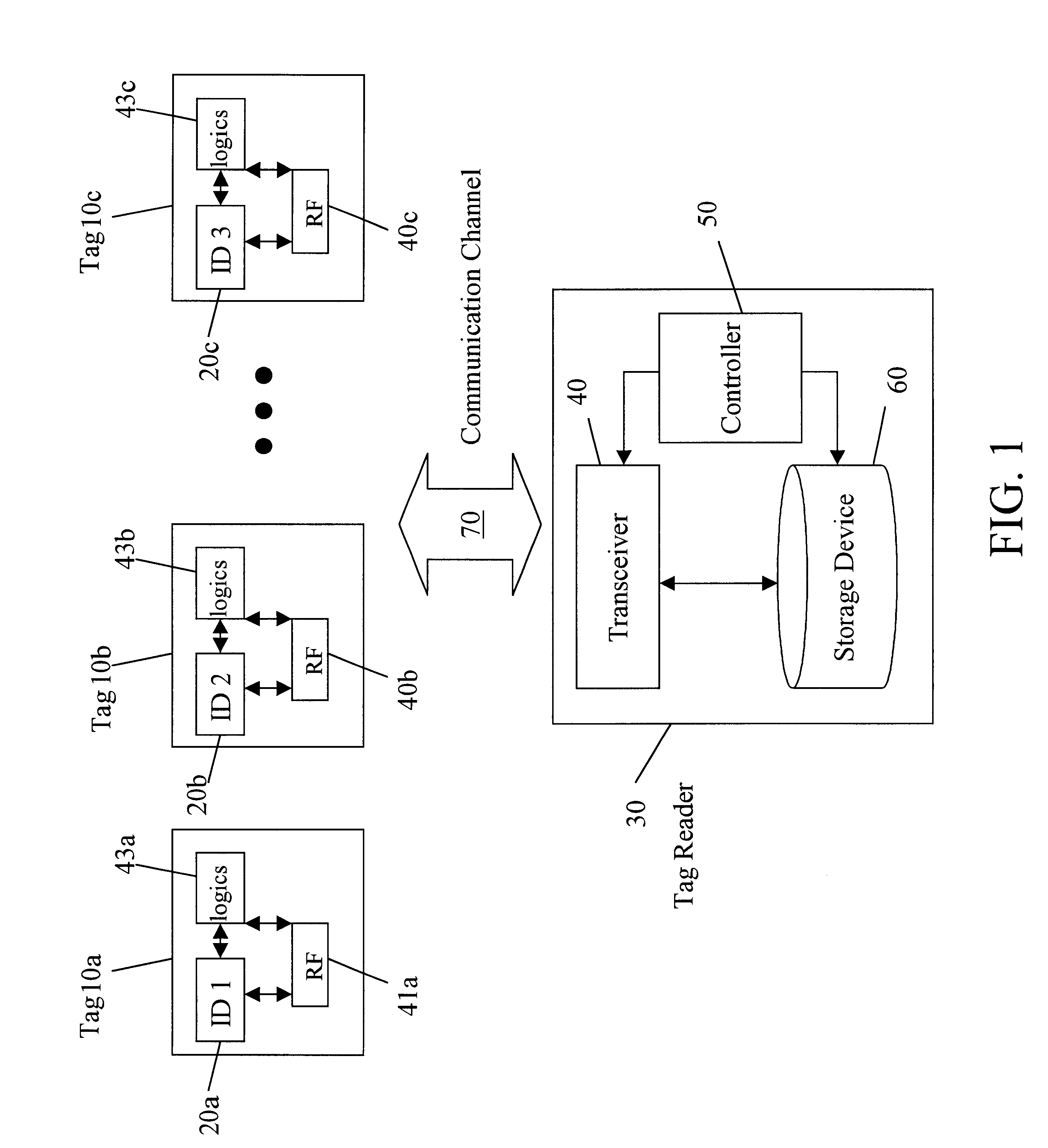
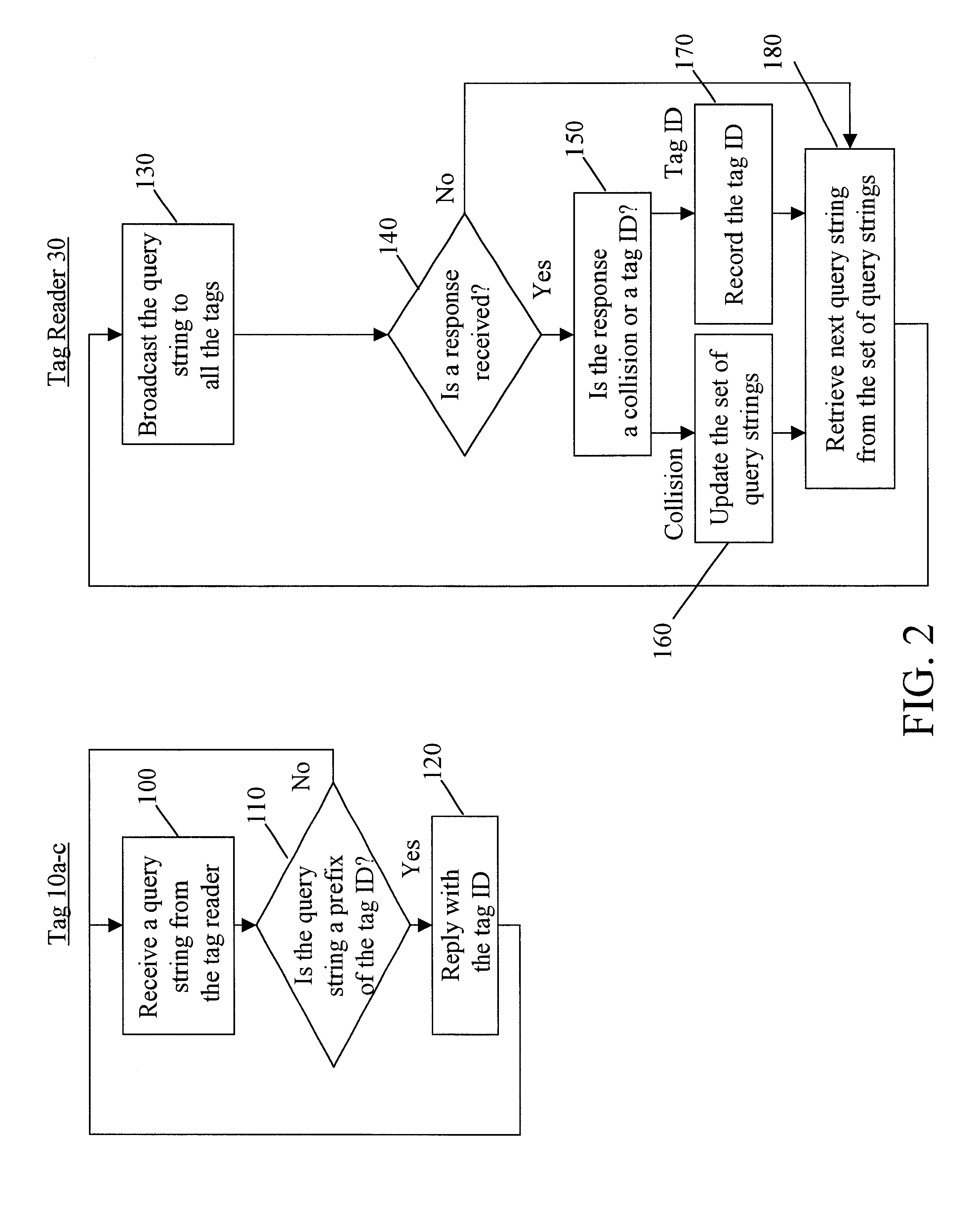
Efficient memoryless protocol for tag identification
InactiveUS6859801B1Data processing applicationsPosition fixationQuery stringCommunication complexity
The invention features a method and system for identifying a plurality of tags using an efficient memoryless protocol. The system includes a reader and a plurality of tags. The reader is adapted to maintain an ordered set of query strings; select a string from the set of query strings; broadcast a query message containing the selected string or a portion of the selected string to the tags; and receive a response from one of the tags. The tags operate without batteries and are adapted to respond to the selected string broadcast by the reader. Accordingly, the tag identification methods are efficient in terms of both time and communication complexities.
Owner:MASSACHUSETTS INST OF TECH
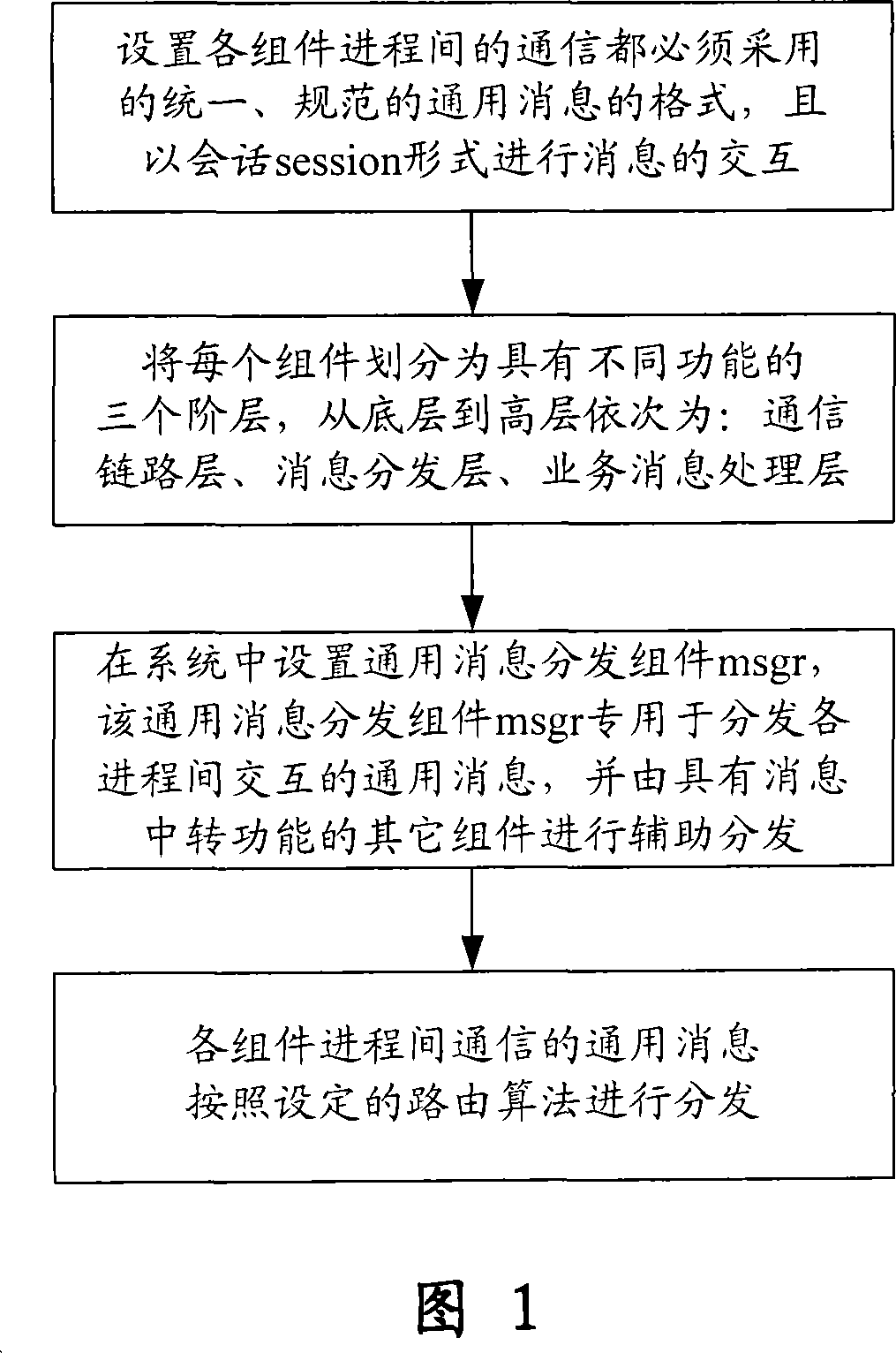
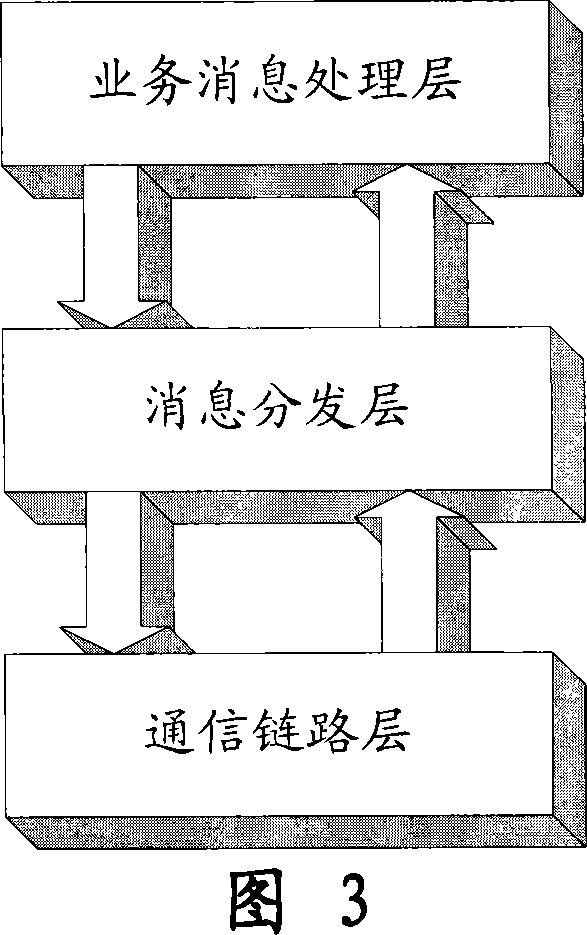
Method for realizing unified universal message bus between different assembly process
InactiveCN101075201ASimple designGuaranteed reliabilityInterprogram communicationTelecommunications linkSoftware system
A method for realizing universal message bus used integrally in communication between various component process in large-capacity software system includes setting unified communication format used between various component processes, dividing each component to be three layers, setting universal message distribution component MSGR in said system and using said component MSGR to distribute universal message to be interacted between various processes as well as distributing universal message of communication between various component processes as per set route algorithm.
Owner:BEIJING UNIV OF POSTS & TELECOMM
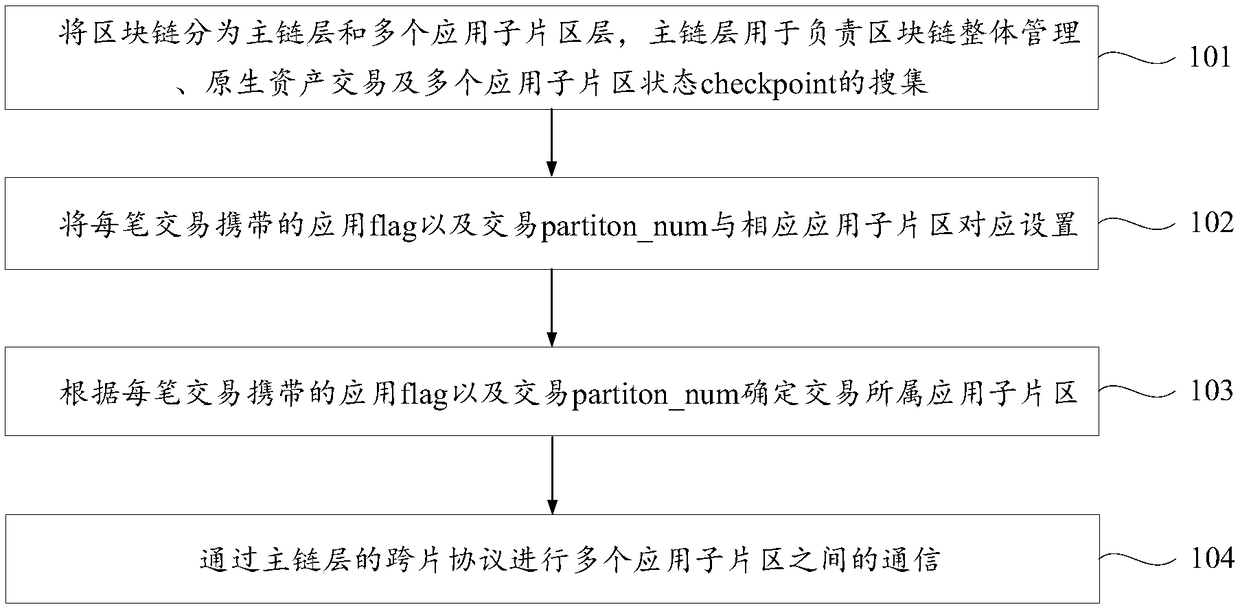
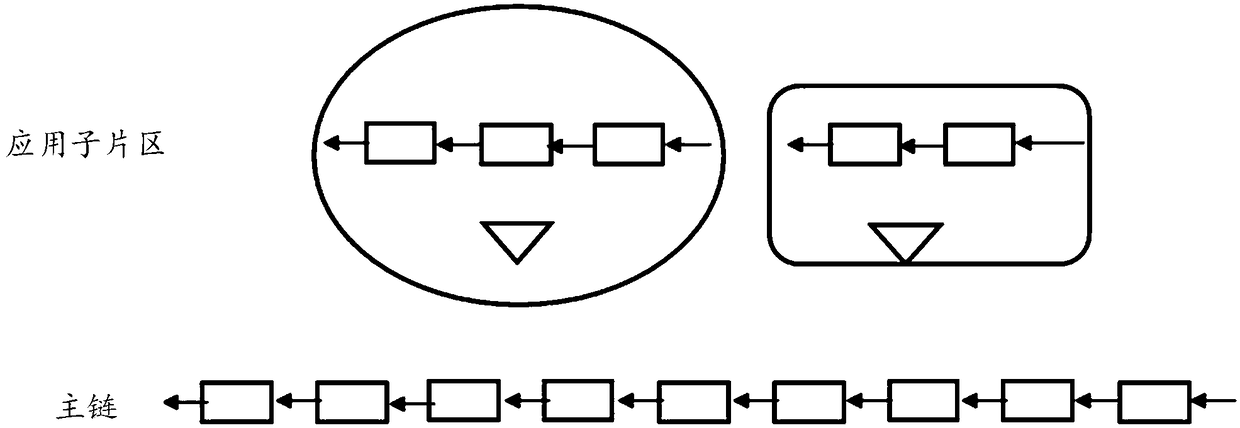
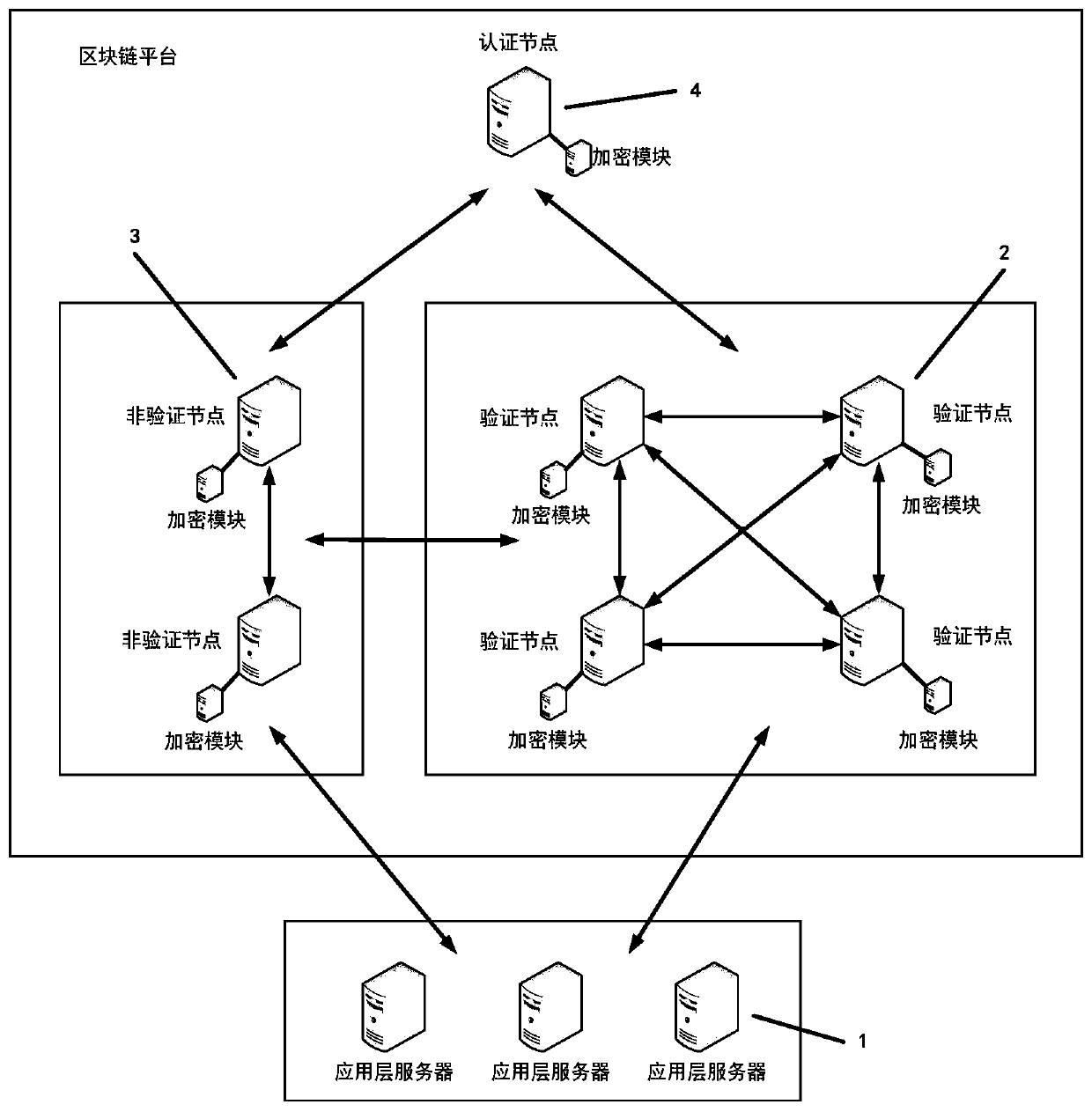
Method and device for sharding of blockchain based on application
ActiveCN108881274AImprove acceleration performanceMaintain securityFinanceTransmissionOperating systemBlockchain
The invention discloses a method and device for sharding of a blockchain based on application, and belongs to the technical field of blockchains. The method comprises the steps of: dividing the blockchain into a main chain layer and a layer consisting of a plurality of application sub-shardings, wherein the main chain layer is used for taking charging of overall management of the blockchain, primary asset transactions and collection for state checkpoint of the plurality of application sub-shardings; enabling an application flag and a transaction partiton_num carried by each transaction to be set correspondingly to the corresponding application sub-sharding; determining the application sub-sharding to which the transaction belongs according to the application flag and the transaction partiton_num carried by each transaction; and performing communication among the plurality of application sub-shardings through a cross-sharding protocol of the main chain layer. The method of the inventionhas the beneficial effects that communication complexity in a communication blockchain network is greatly reduced while security is balanced, and a consensus efficiency and network expansibility areimproved, thus the method has a good application prospect, and can be promoted in various fields related to the blockchain.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD +1
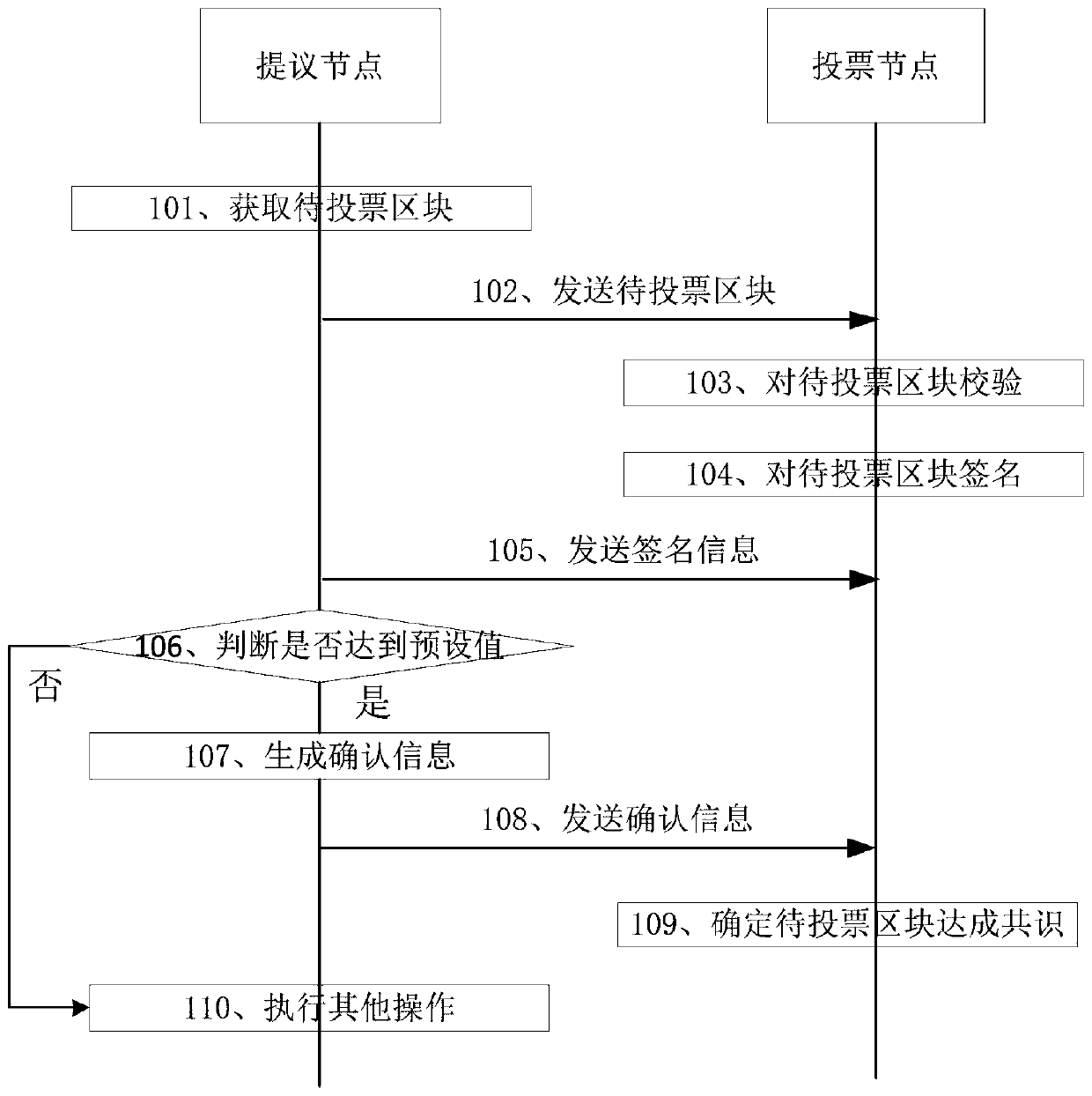
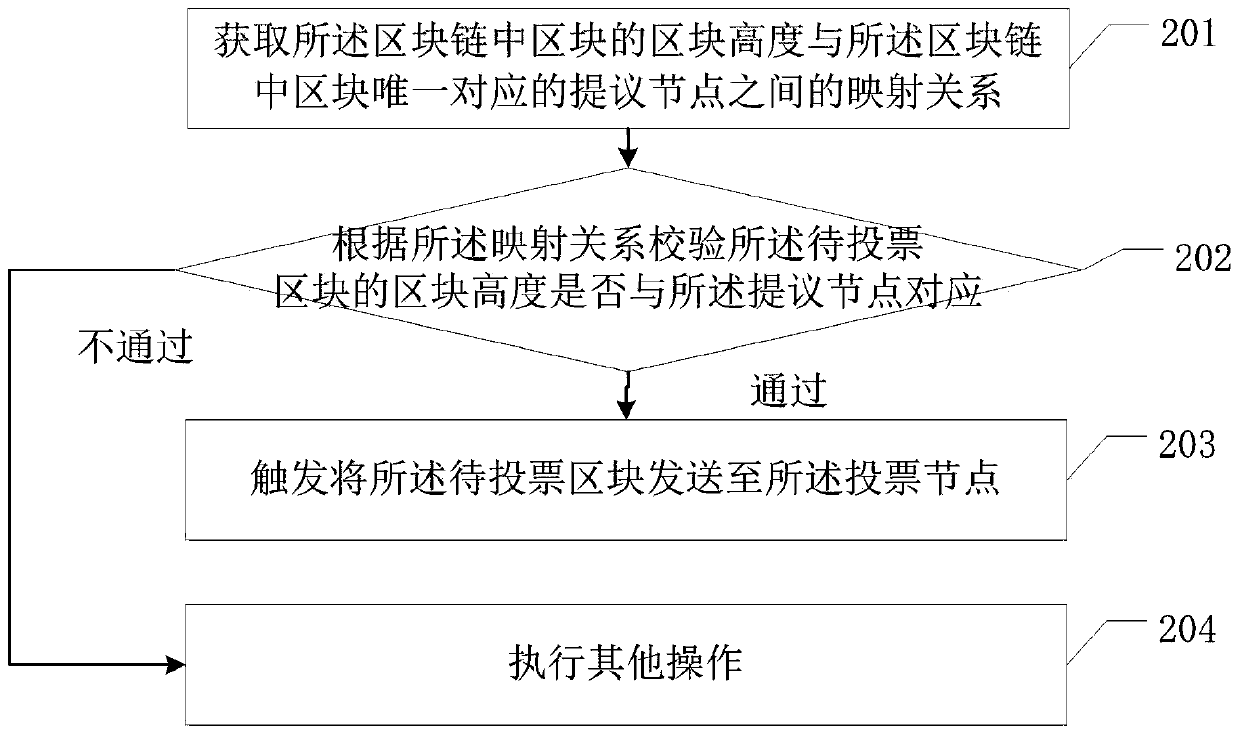
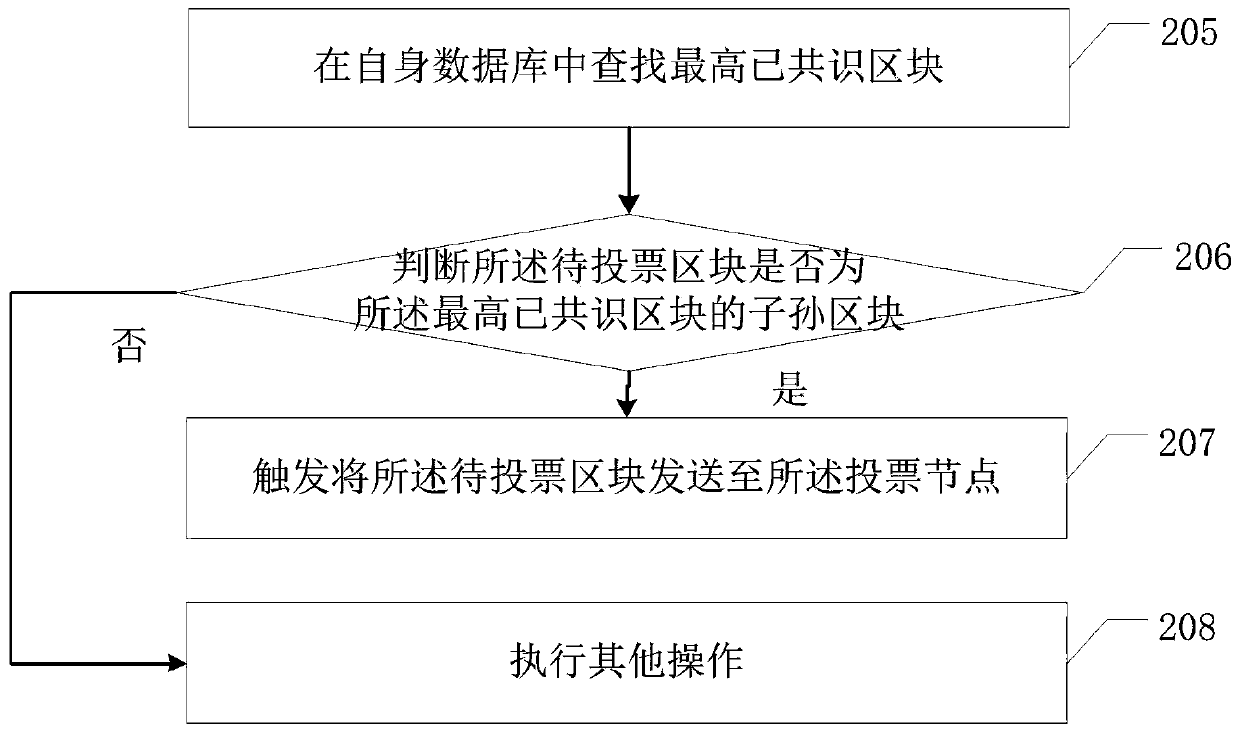
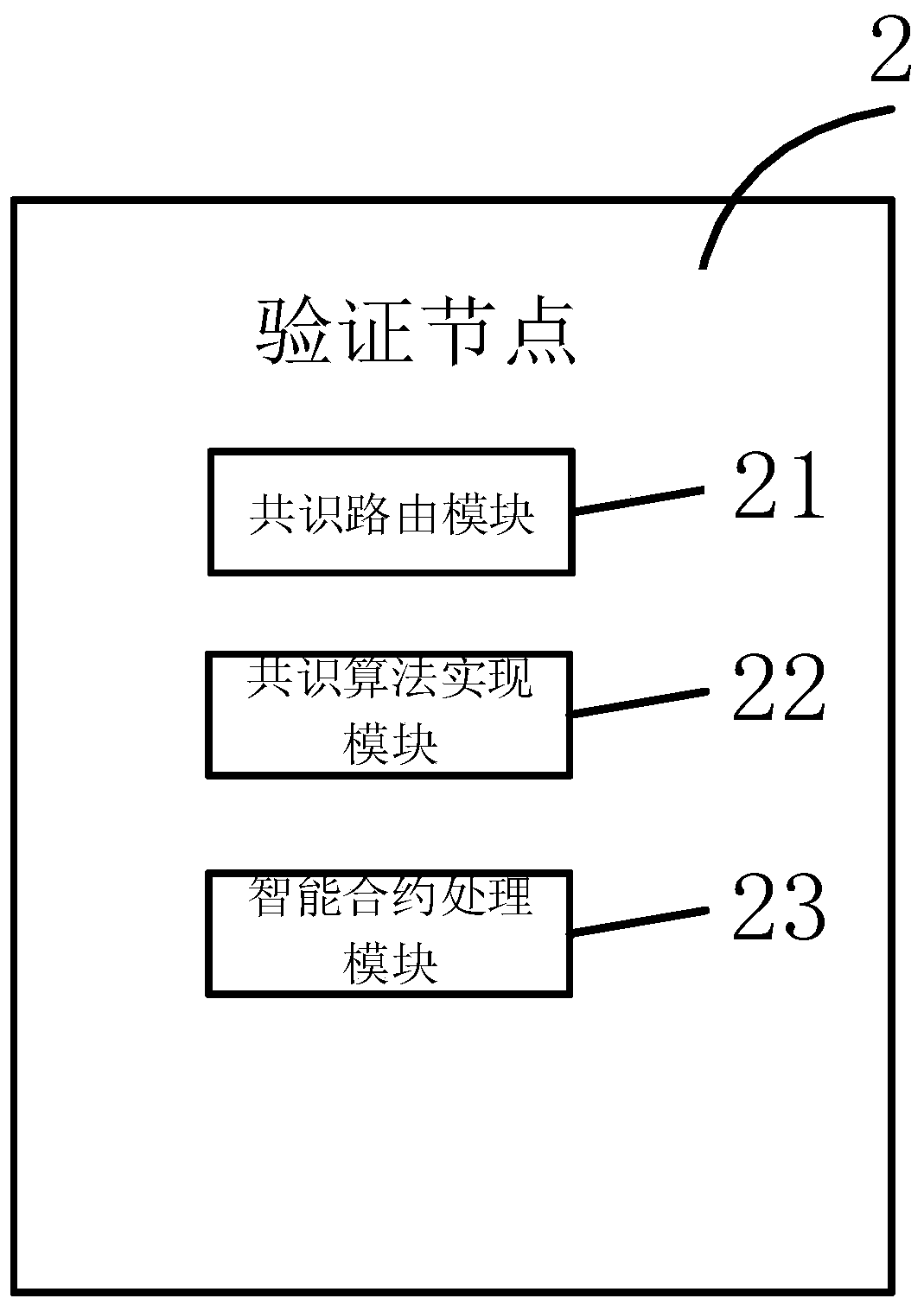
Consensus method of block chain data and related equipment
ActiveCN110288479AReduce Communication ComplexityImprove securityFinanceEnergy efficient computingBlockchainComputer security
The embodiment of the invention discloses a block chain data consensus method and related equipment thereof, which are used for reducing the communication complexity of block chain consensus. The method comprises the steps of a proposal node obtaining a to-be-voted block; sending the to-be-voted block to the voting node; receiving signature information sent by the voting node, wherein the signature information is used for indicating that the voting node successfully verifies the to-be-voted block; judging whether the number of the signature information received within preset time reaches a preset value or not; if yes, confirming information is generated according to the signature information, and the confirming information indicating that the to-be-voted block is a block achieving consensus; and sending the confirmation information to the voting node, so that the voting node determines the to-be-voted block as a block achieving consensus. The proposal node and the voting node in the block chain realize the consensus of the block to be voted through the signature information and the confirmation information, so that the communication complexity of the block chain consensus is effectively reduced.
Owner:SHENZHEN THUNDER NETWORK TECH +1
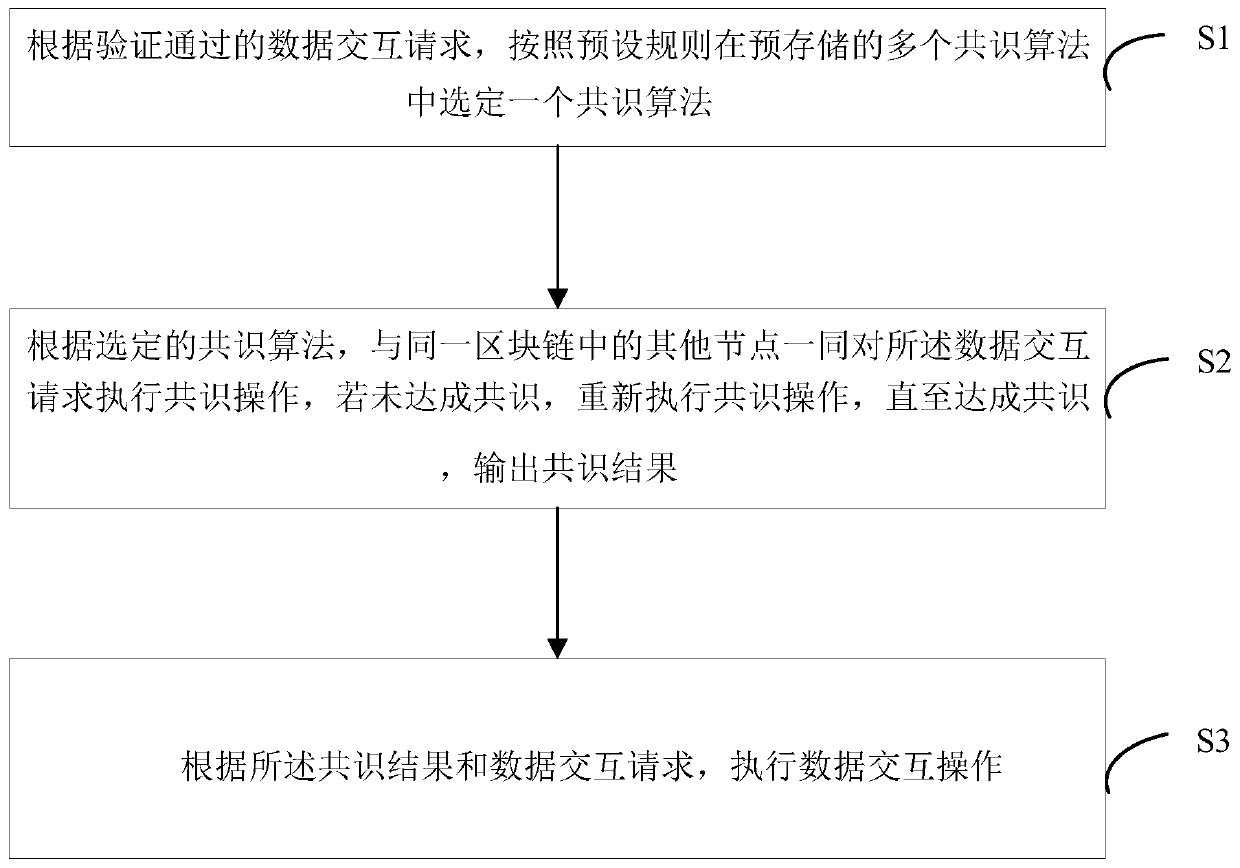
Block chain data interaction method and device capable of switching consensus algorithms
InactiveCN110365695AEasy to monitor and maintainControllable monitoring operation and maintenanceTransmissionSmart contractChain system
The invention provides a block chain data interaction method and device capable of switching consensus algorithms. Different consensus algorithms are accessed for different service scenes, pluggable access is realized, the consensus efficiency of the block chain system is improved, the data interaction response time is shortened, powerful support is provided for function and performance of big data services with complex block chain processing logic, convenience is provided for function development, and the research and development efficiency is improved. According to the method, high couplingof a consensus algorithm and a block chain system verification node is solved, a design idea of a pluggable consensus algorithm is provided, system consensus and intelligent contract decoupling are realized, the consensus algorithm is high in availability and easy to expand, and monitoring operation and maintenance of the consensus node are more convenient and controllable. Meanwhile, the problemthat the communication cost of the original PBFT algorithm is too high in a private chain environment is solved, and the communication complexity is reduced after the RAFT algorithm is used. The average response time of the block chain can be effectively reduced, the utilization rate of a CPU and a memory of a server is reduced, and the resource overhead is saved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
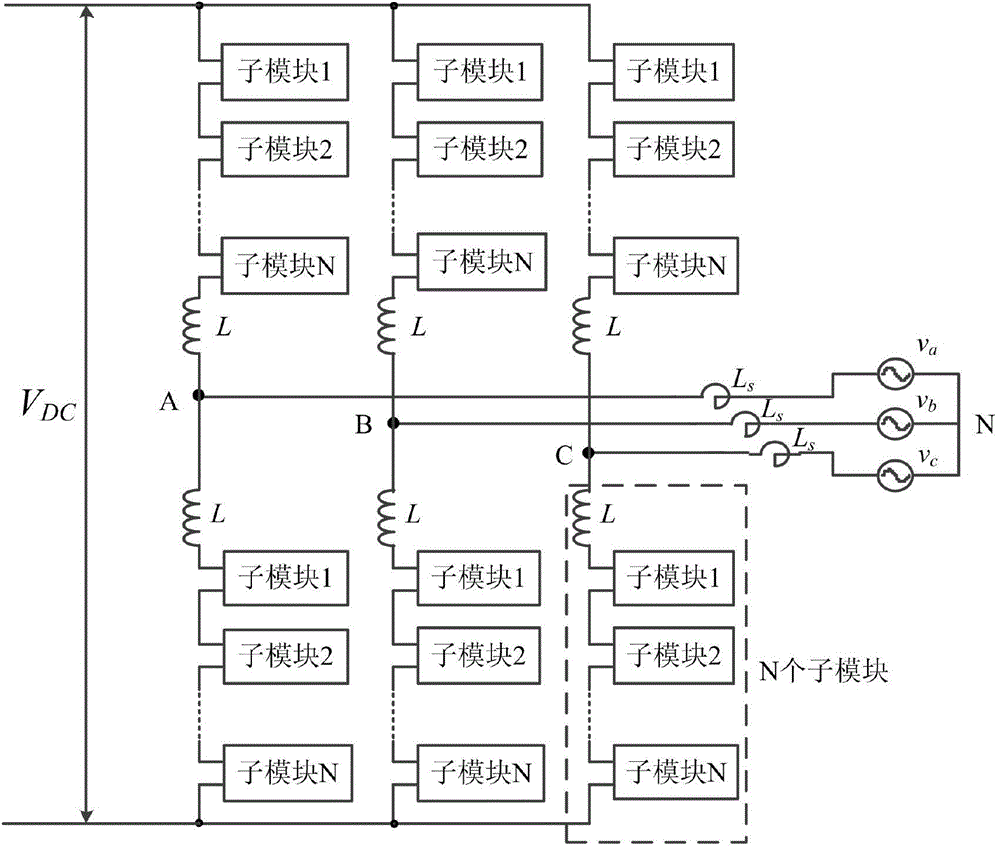
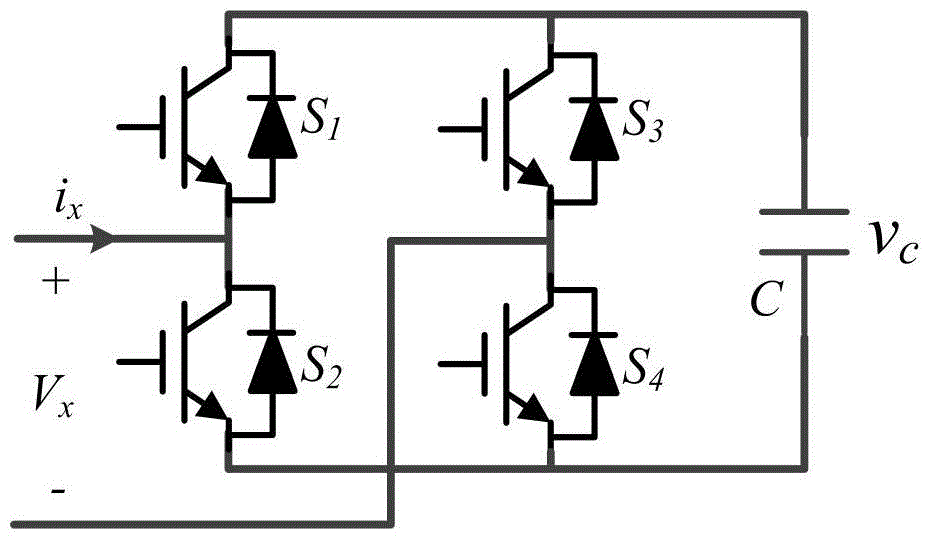
Method for balancing capacitor voltage of modularization multilevel converter
ActiveCN104158419ALow real-time requirementsSave computing resourcesAc-dc conversionCapacitor voltageCurrent sensor
The invention discloses a method for balancing capacitor voltage of a modularization multilevel converter. The method comprises the following steps: (1) the present value of submodule capacitor voltage is sampled to obtain increment of capacitor voltage in a power frequency period; (2) the increment of the capacitor voltage and the present value of submodule capacitor voltage are ranked; (3) a new corresponding relation between a drive signal and a submodule is obtained; (4) the drive signal is allocated to the submodule again according to the new corresponding relation. According to the method, the requirement for real-time performance is lower, and the computing resource of controllers is saved, so that the controllers can be used for processing a large-scale MMC system; no bridge arm current needs to be detected, so that the communication complexity among the controllers is simplified, part of the cost of a current sensor is saved, an additional hardware circuit is not needed to be added, and additional system cost is avoided; under the control of the method, all switch frequencies of the submodule are the same, the switch frequency is lower, the switch stresses are consistent and the system thermal design is facilitated and the system reliability is realized.
Owner:ZHEJIANG UNIV
ICN device and method
ActiveCN103729329AReduce communication delayImprove good performanceProgram synchronisationDigital computer detailsComputer moduleTelecommunications equipment
The invention provides an ICN device and method. The device comprises postbox modules and BA modules. The postbox modules are used for storing messages sent to message receiving cores by message sending cores and informing the message receiving cores of message reading. The BA modules are connected between the postbox modules and the message receiving cores and between the postbox modules and the message sending cores, wherein the message receiving cores and the message sending cores are in communication. The BA modules are used for providing read / write interfaces between the postbox modules and the message receiving cores and between the postbox modules and the message sending cores. According to the ICN device and method, the problems that in the prior art, an ICN device and method are high in complexity and poor in real-time performance, and expandability is poor in the process of multi-core application are solved, so that ICN complexity is remarkably lowered, communication time delays are reduced, and expandability and reducibility are excellent.
Owner:SANECHIPS TECH CO LTD
Method for pre-distributing wireless sensor network cipher key
The invention relate to a wireless sensor network key pre-distribution method, which comprises the following steps: step S001: disposition server generating R upper triangular matrixes G and R diagonal matrixes D at random on the finite field GF (q); step S002: generating R groups of real symmetric matrixes K; step S003: saving the ID of every node, row vector seed gir, column vector; step S004: starting base station, and clustering networking; step S005: discovering the shared secret key pair corresponding to secret key space between nodes by pre-distributing secret key; step S006: distributing cluster secret keys with cluster head towards inner-cluster by the constructed shared secret key pair between nodes; step S007: expanding the secret key space dimension. The invention achieves lower node capacity, communication complexity and calculation complexity while ensuring the network completely is communicated; and has higher node anti-capture capability.
Owner:SOUTHEAST UNIV
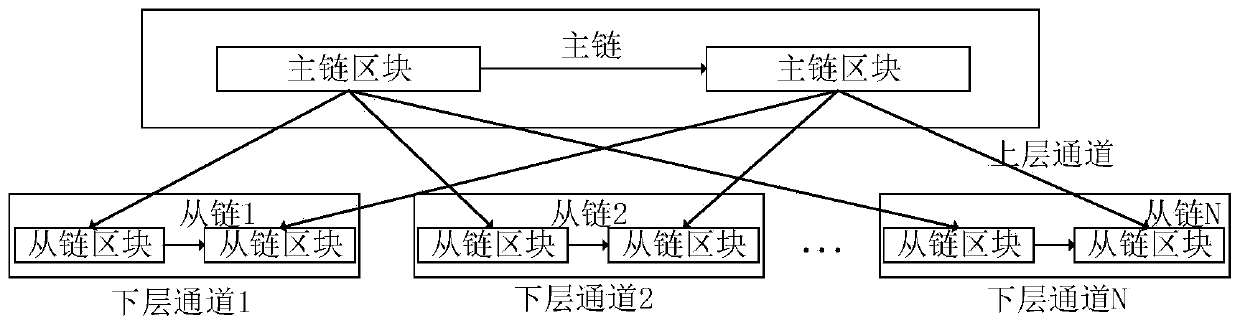
Alliance chain master-slave multi-chain consensus method based on tree structure
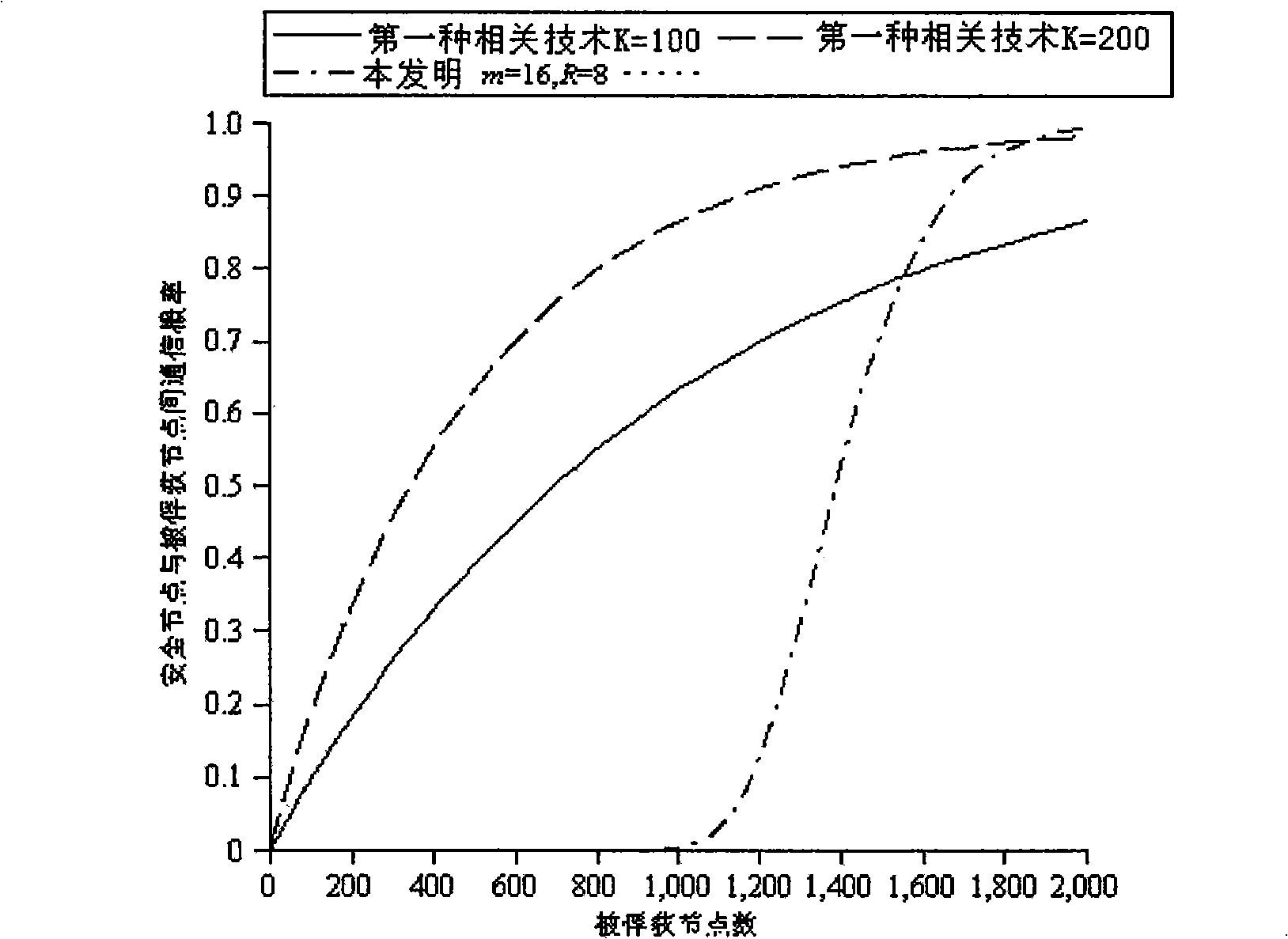
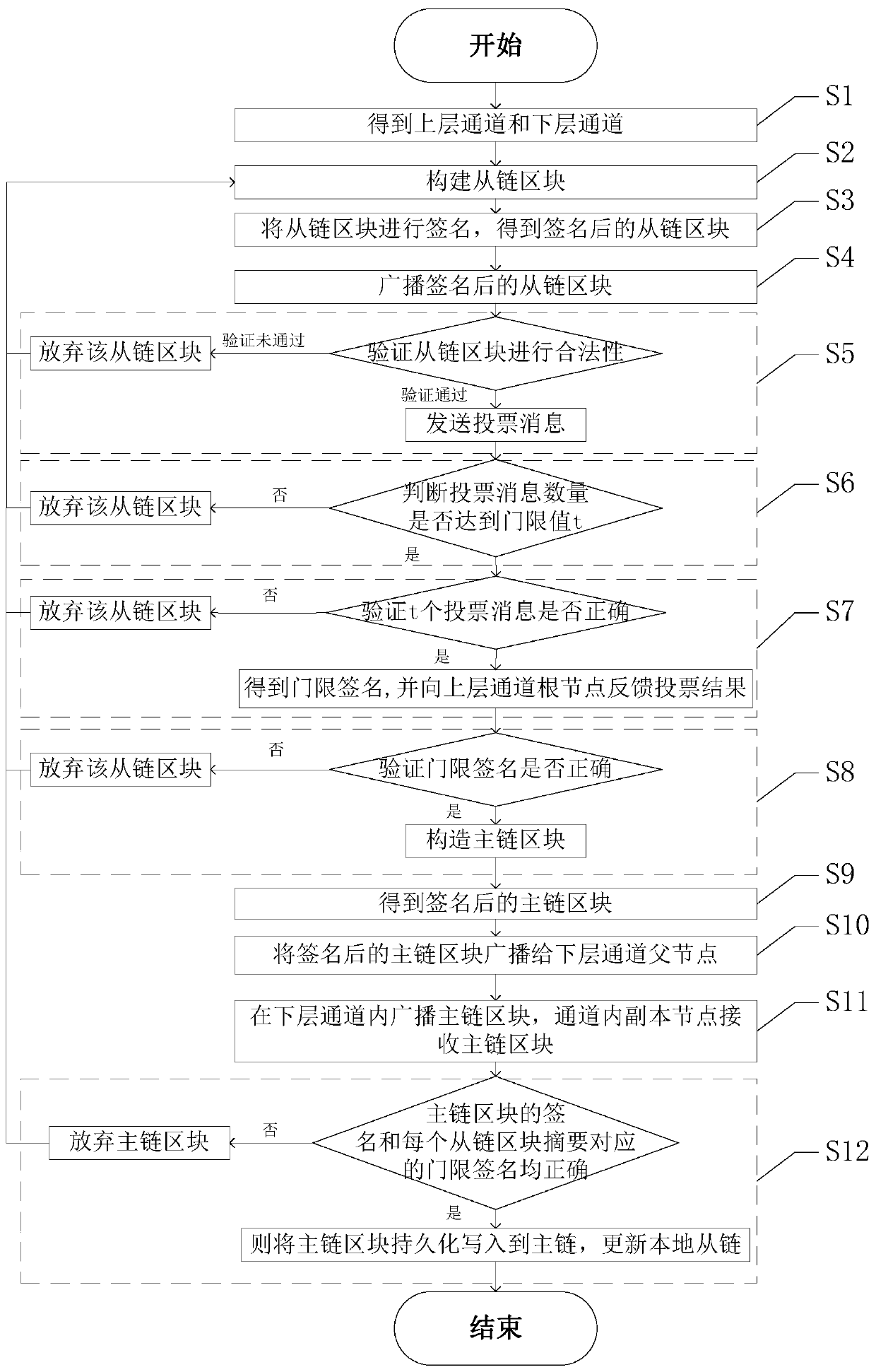
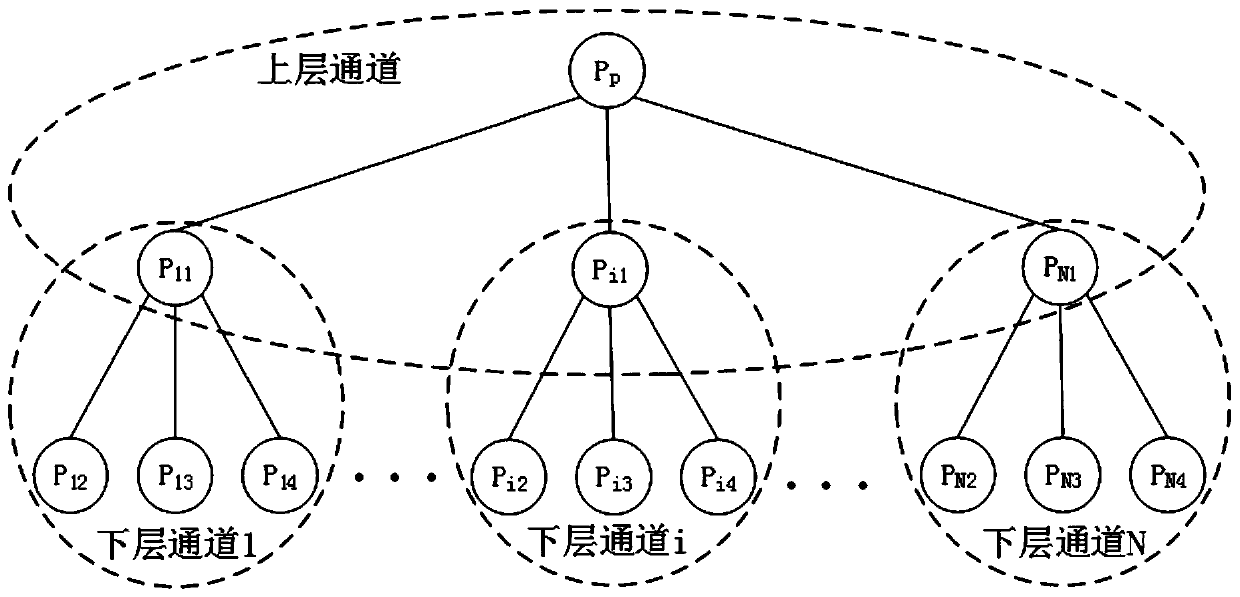
ActiveCN110245951AImplement classificationAchieve data isolationDigital data protectionPayment protocolsByzantine fault toleranceConsistency problem
The invention discloses an alliance chain master-slave multi-chain consensus method based on a tree structure. An alliance chain consensus group is divided; an upper-layer channel and a lower-layer channel are obtained; channels are mutually isolated, classification and data isolation of different digital assets are realized; privacy requirements of data isolation are met; concurrent processing ofmultiple channels is carried out, the transaction performance is improved, the problems that an existing block chain is low in throughput and too high in transaction delay are solved. The invention provides a master-slave multi-chain architecture of a tree structure and the occupancy fault-tolerant consensus algorithm based on the threshold signature under the master-slave multi-chain architecture to solve the problem of consistency caused by diversified digital asset classification concurrent processing; the method has the advantages of low communication complexity and signature verification complexity, the master-slave multi-chain structure breaks through the function and performance constraint of a single chain and has good high-concurrency transaction performance, meanwhile, isolation protection of privacy data is considered, and diversified business requirements of enterprises are met.
Owner:芽米科技(广州)有限公司
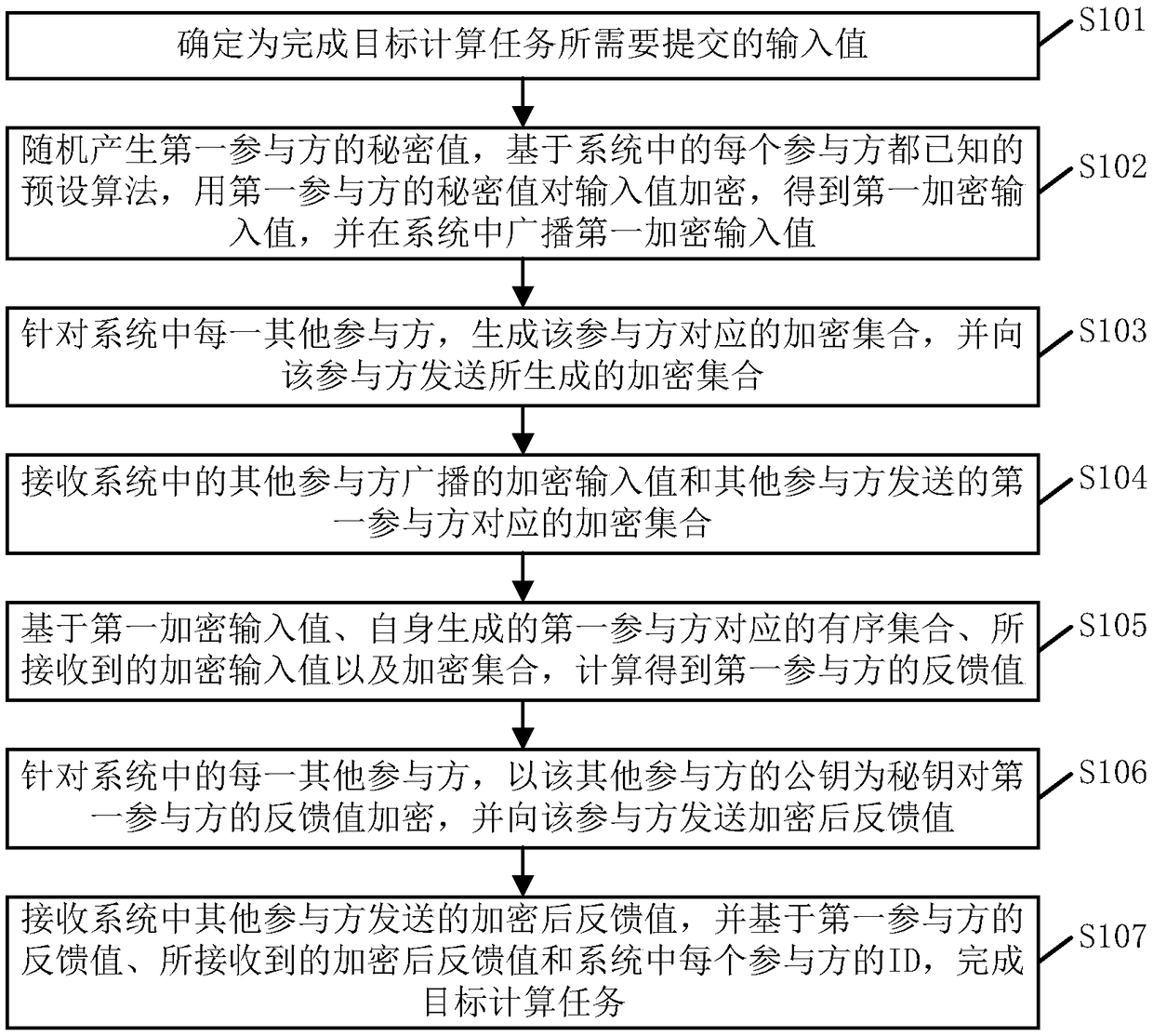
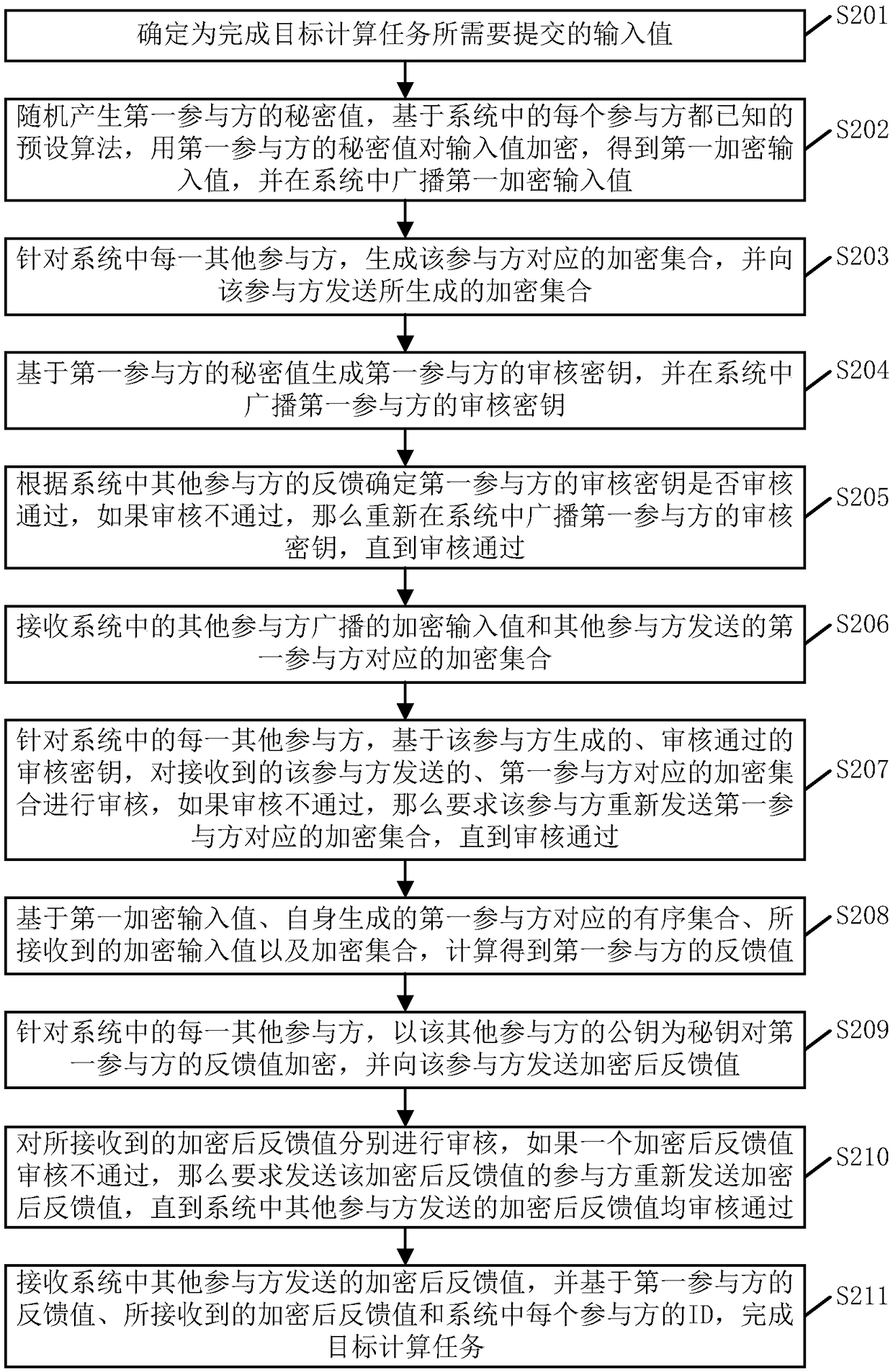
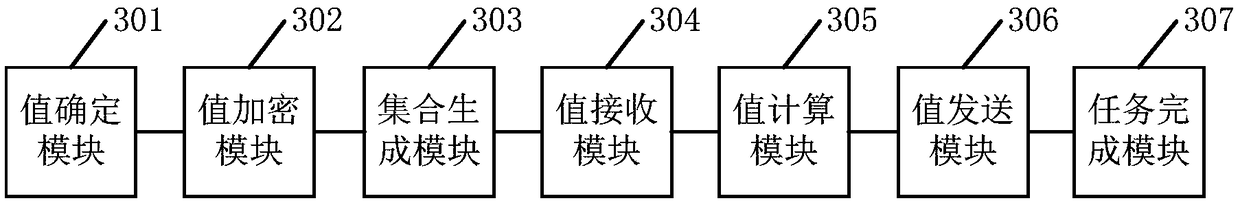
A secure multi-party computing method and device
ActiveCN109446828AReduce the number of interactionsReduce Communication ComplexityDigital data protectionInformation securitySecure multi-party computation
The embodiment of the invention provides a secure multi-party computing method and device, and relates to the technical field of information security, and the method is applied to any participant in asecure multi-party computing system, and comprises the following steps of determining an input value required to be submitted for completing a target computing task; randomly generating a secret value, encrypting the input value by using the secret value, and broadcasting the encrypted input value in the system; generating an encryption set corresponding to other participants, and sending the encryption set to the other participants; receiving an encryption input value and an encryption set broadcasted by other participants; based on the encryption input value and the encryption set, calculating to obtain a feedback value; encrypting the feedback value by using public keys of other participants, and sending the encrypted feedback value to the participants; and receiving the encrypted feedback value sent by other participants, and completing the target calculation task based on the encrypted feedback value and the ID of each participant in the system. By applying the scheme provided bythe embodiment of the invention, the communication complexity of secure multi-party calculation can be reduced, and the communication resources are saved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Application level any-source multi-cast method satisfying capacity constraint and QoS constraint
InactiveCN101577628AHigh multicast coverageSatisfy node capability constraint performanceSpecial service provision for substationData sourceThe Internet
The invention relates to an application level any-source multi-cast method satisfying capacity constraint and QoS constraint, which is established on the basis of a random overlay network and a non-DHT (distributed hash table) ring, meets distributed application requirement such as capacity constraint, dynamic membership and the like, has the characteristic of complete distribution, and can be extended within the range of Internet. The method does not need extra maintenance, so that the method is suitable for multi-cast application with a plurality of potential data sources; the method has better hop complexity and communication complexity, and high multi-cast coverage rate of nodes; the method has node capacity constraint performance, and has the performance of satisfying dynamic QoS constraint; and the method has a simple structure and easy realization.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
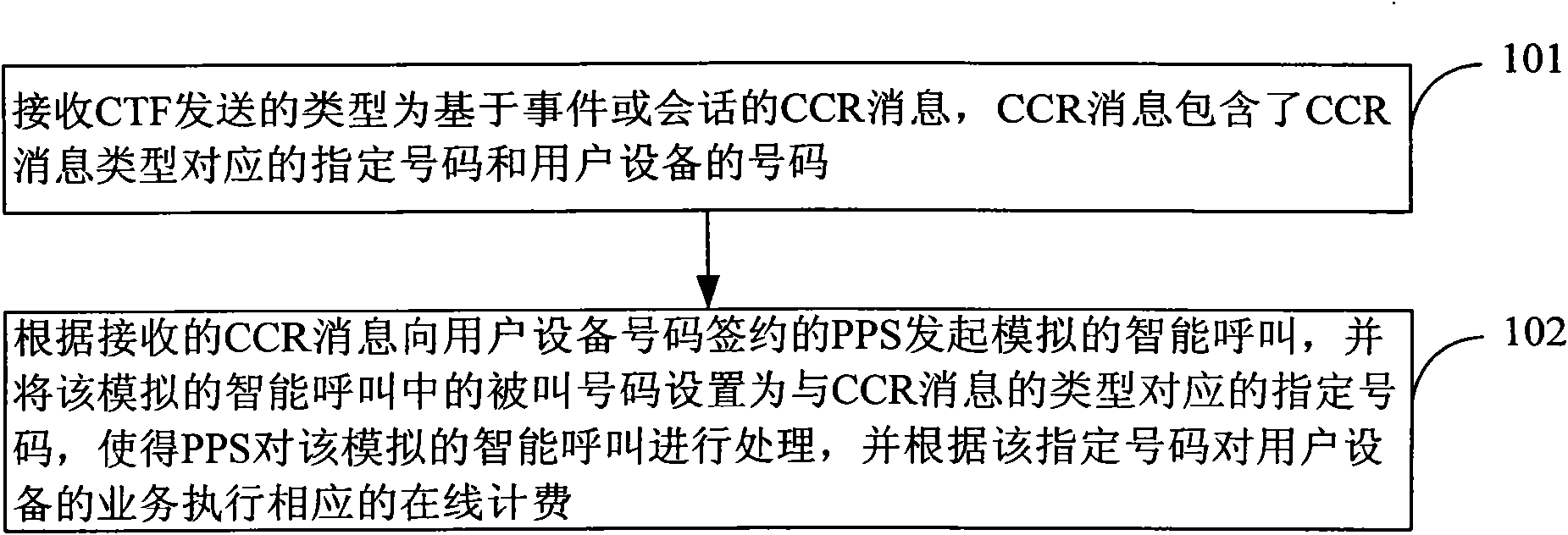
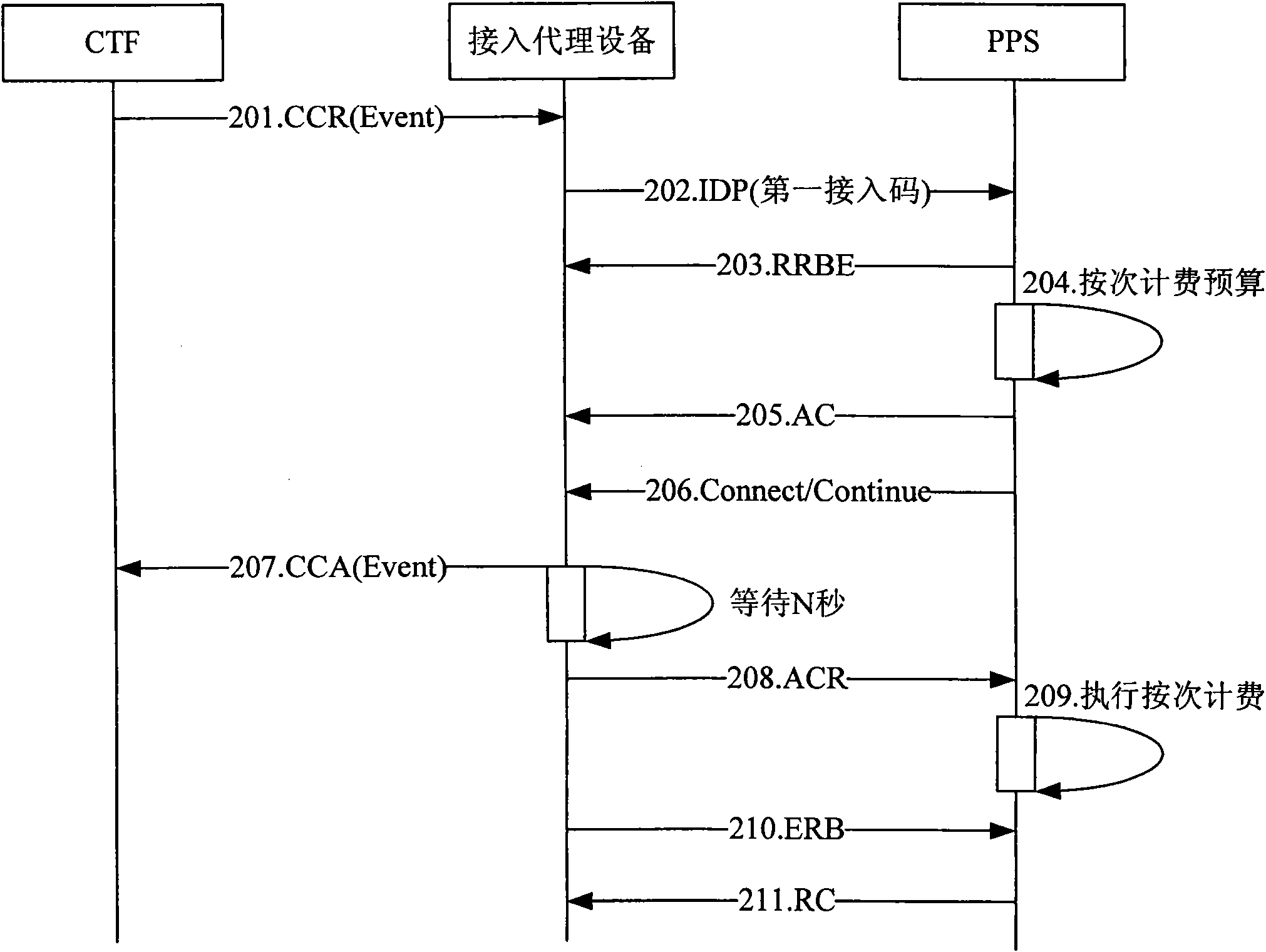
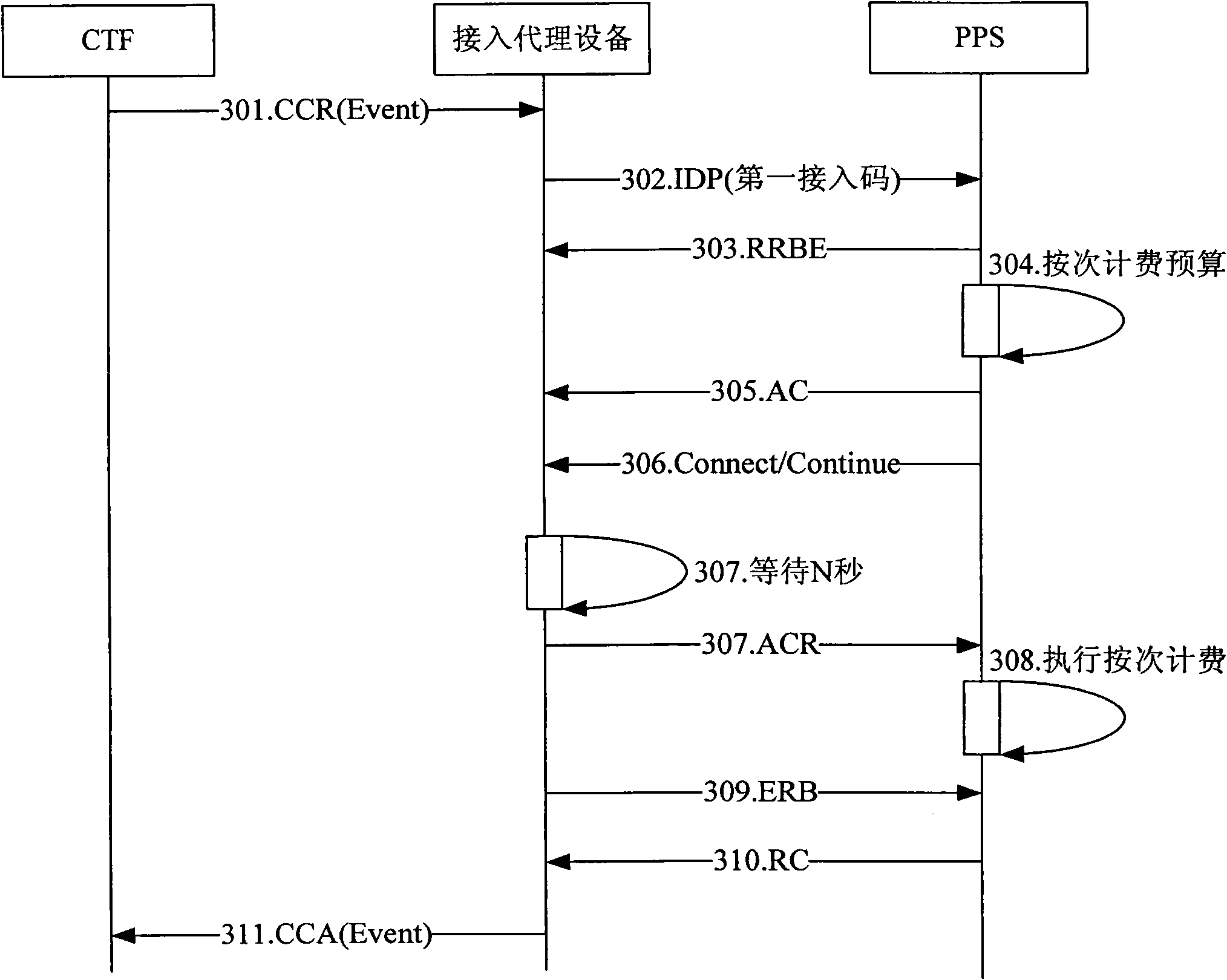
On-line charging method, access proxy equipment and system
InactiveCN102143466AReduce complexityLow costAccounting/billing servicesComputer networkUser equipment
The embodiment of the invention discloses an on-line charging method, access proxy equipment and a system, and belongs to the technical field of communication. The method comprises the following steps of: receiving a credit control request (CCR) message in a type based on an event or a session, which is transmitted by a charging trigger function (CTF), wherein the CCR message comprises a specified number corresponding to the type of the CCR message and a number of user equipment; and initiating an analog intelligent call to a prepaid service (PPS) subscribed by the user equipment number according to the received CCR message, and setting a called number in the analog intelligent call as the specified number corresponding to the type of the CCR message, so the PPS processes the analog intelligent call, and implements corresponding on-line charging on the service of the user equipment according to the specified number. The access proxy equipment comprises a reception module and a processing module. The system comprises the access proxy equipment and the PPS subscribed by the user equipment. By the technical scheme provided by the embodiment of the invention, the diameter credit control (DCC) charging complexity and cost, and the communication complexity are greatly reduced.
Owner:深圳市前海滕翔科技信息有限公司
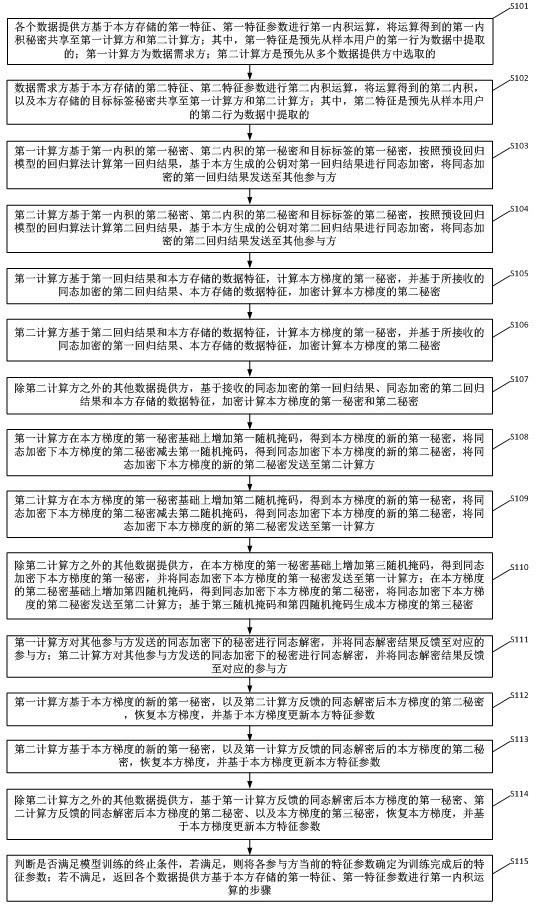
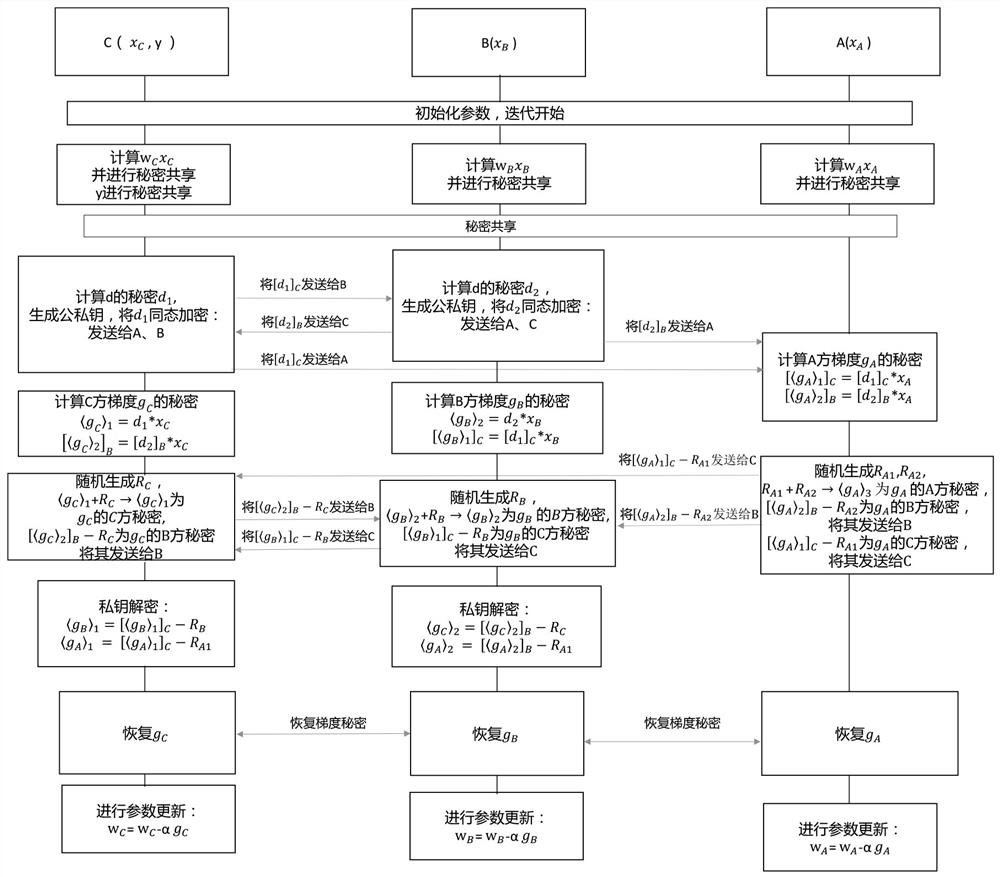
Non-third-party federal learning method and system based on secret sharing and homomorphic encryption
ActiveCN113516256AAchieve trainingReduce consumptionEnsemble learningDigital data protectionThird partySecret share
The embodiment of the invention provides a third-party-free federated learning method and system based on secret sharing and homomorphic encryption, and the method comprises the steps: enabling each participant to share an intermediate result of model training through a secret, enabling the secret obtained by the participant to be interacted with other participants in a homomorphic encryption mode, and carrying out the model training, and finally, enabling an appointed result party to obtain a final result of model training, so that model training in federated learning without a trusted third-party mechanism is realized. Moreover, since only an intermediate result of model training is shared secretly, compared with a mode that original sample data and model parameters are split and secretly shared in an MPC-based untrusted third-party federated learning scheme, the consumption of system resources and the communication complexity are greatly reduced.
Owner:深圳市洞见智慧科技有限公司
Data transmission method, equipment and system
InactiveCN107306171AUnified designSimple designError preventionSignal allocationCommunications systemTerminal equipment
The embodiment of the invention provides a data transmission method. The method comprises the following steps that: terminal equipment acquires configuration information, wherein the configuration information indicates that a sub-frame n is used for transmitting at least one of a downlink data channel, an uplink data channel, a downlink control channel, an uplink control channel, a downlink reference signal and an uplink reference signal; and the terminal equipment performs data transmission with network equipment on the sub-frame n according to the configuration information. Through the method, the design of a communication system can be unified on different flat bands; the communication complexity is lowered effectively; and the communication efficiency is increased.
Owner:HUAWEI TECH CO LTD
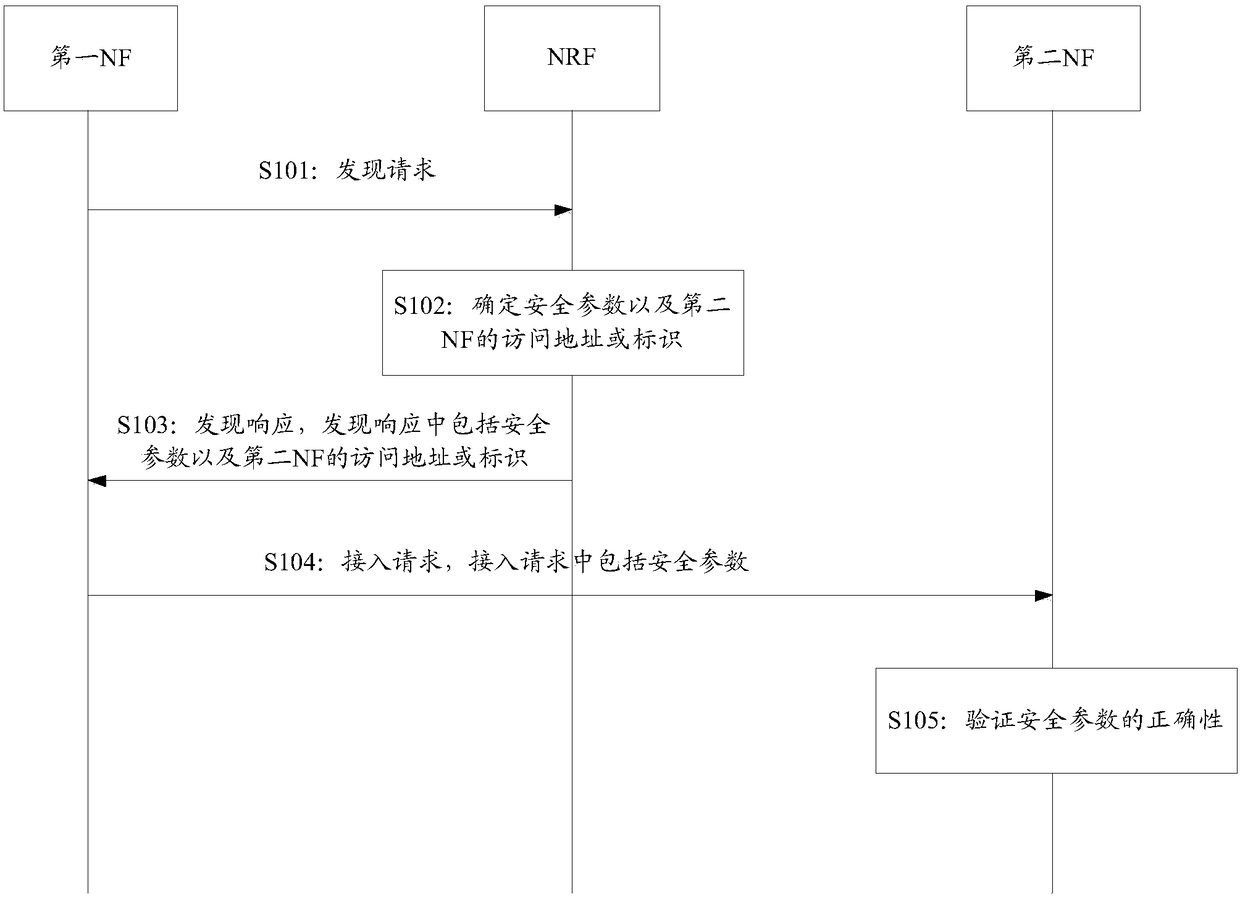
Discovery method and device based on servitization architecture
PendingCN109428875AReduce the number of communicationsReduce Communication ComplexityUser identity/authority verificationSecurity arrangementCommunication complexityFunctional networks
The application provides a discovery method and device based on a servitization architecture. In the method, a control network element sends a discovery response to a first functional network element,and the discovery response comprises a determined safety parameter and an access address or an identifier of a second functional network element; the first functional network element receives the discovery response sent by the control network element and sends an access request to the second functional network element according to the address or the identifier of the second functional network element, which is included in the discovery response, and the access request comprises the received safety parameter; and the second functional network element receives the access request sent by the first functional network element, verifies correctness of the safety parameter and determines whether the access request is authorized by the first functional network element on the basis of correctnessof the safety parameter. By the discovery method and device provided by the application, communication times can be reduced to a certain degree, and communication complexity is reduced.
Owner:HUAWEI TECH CO LTD
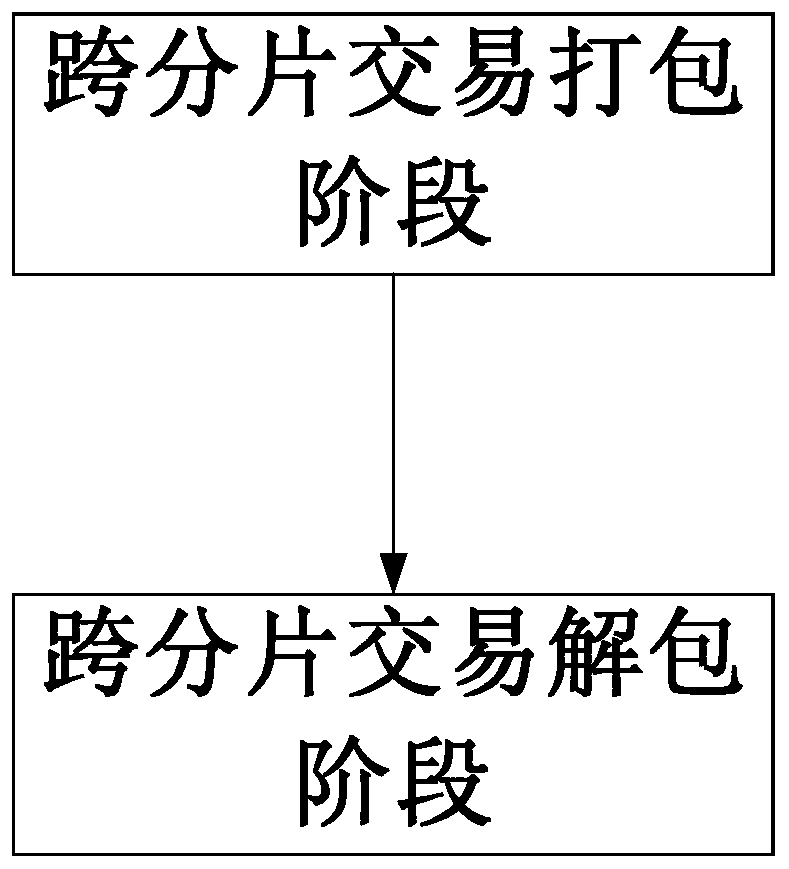
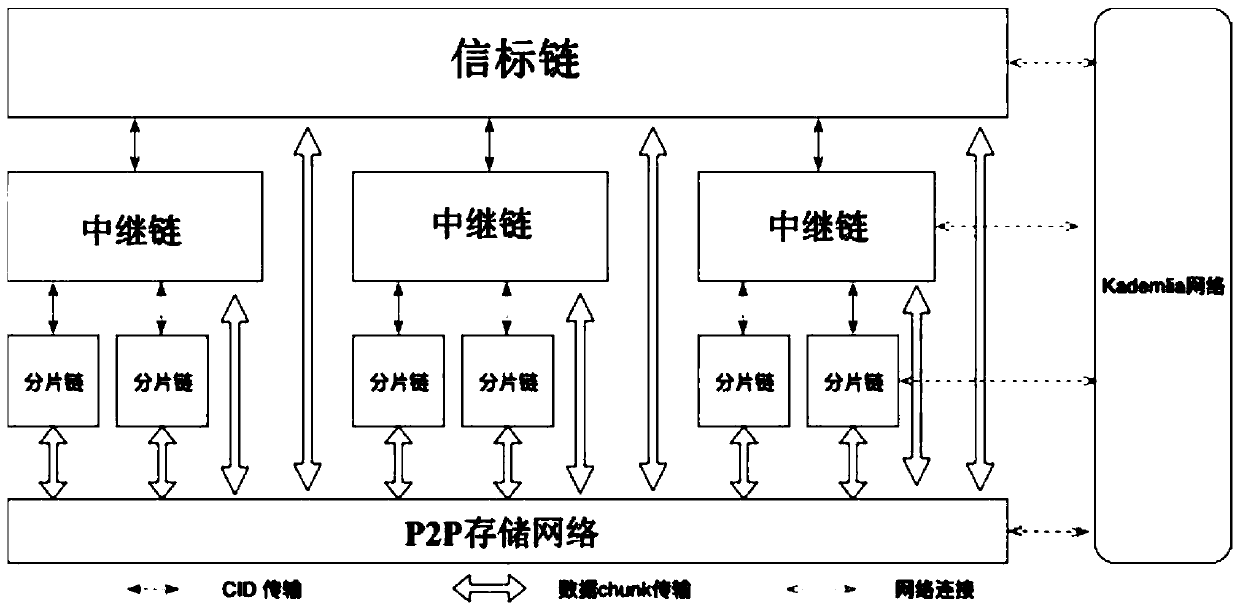
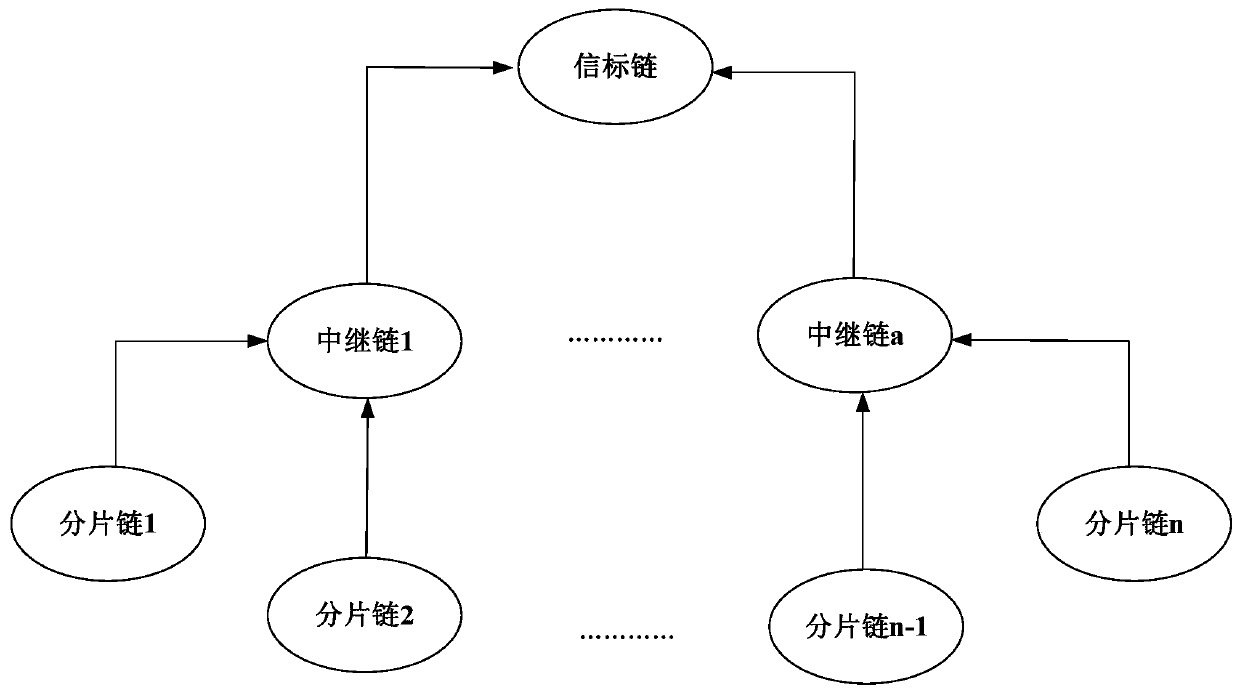
Block chain full fragmentation method and device based on P2P storage network and multi-layer architecture
ActiveCN111127017AImprove scalabilityReduce complexityDatabase distribution/replicationPayment protocolsTrunkingEngineering
The invention discloses a block chain full fragmentation method and device based on a P2P storage network and a multi-layer architecture. On one hand, network fragmentation is utilized to divide wholenetwork block chain nodes into a fragmentation chain, a relay chain and a beacon chain; namely, a beacon-relay-fragmentation three-layer architecture is adopted to realize cross-chain communication of fragments; the network requirements of the nodes and the total TPS number of the network form a linear relationship; on the other hand, the transaction is divided into W primitives and D primitives,the D primitives are grouped, the hash values corresponding to the D primitives are calculated, and the essence is that the W primitives are executed on fragments of an initiator, the D primitives are stored in a P2P storage network, and the hash values corresponding to the D primitives can perform cross-chain communication and are finally executed on fragments of a receiver. By means of the design, through the P2P storage network, a large amount of data only need to be subjected to cross-chain communication through hash values of the data, the communication complexity and bandwidth requirements are reduced, and the expansibility of the block chain fragmentation technology is greatly improved.
Owner:SICHUAN INTERSTELLAR ROEWE TECH CO LTD
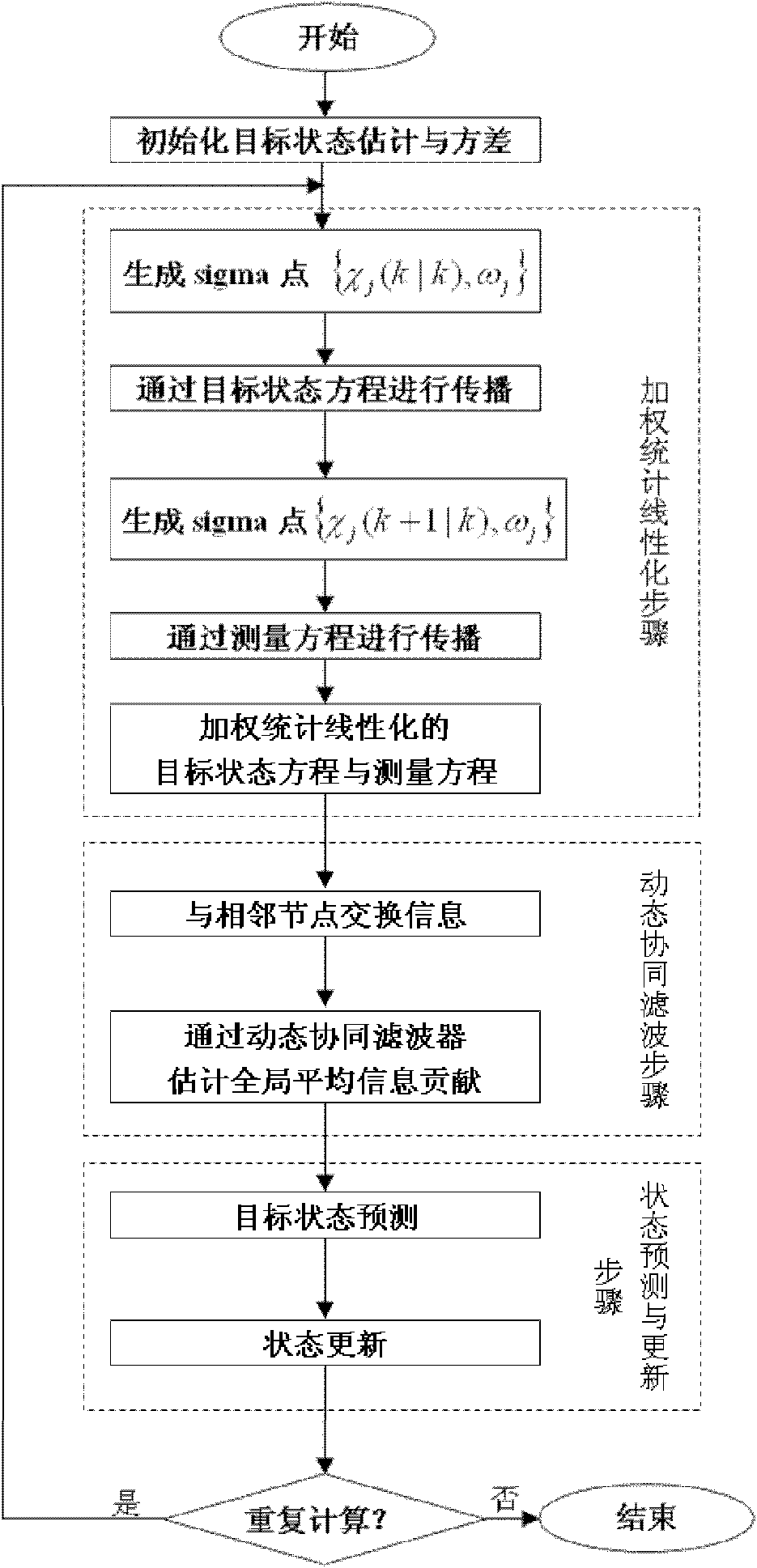
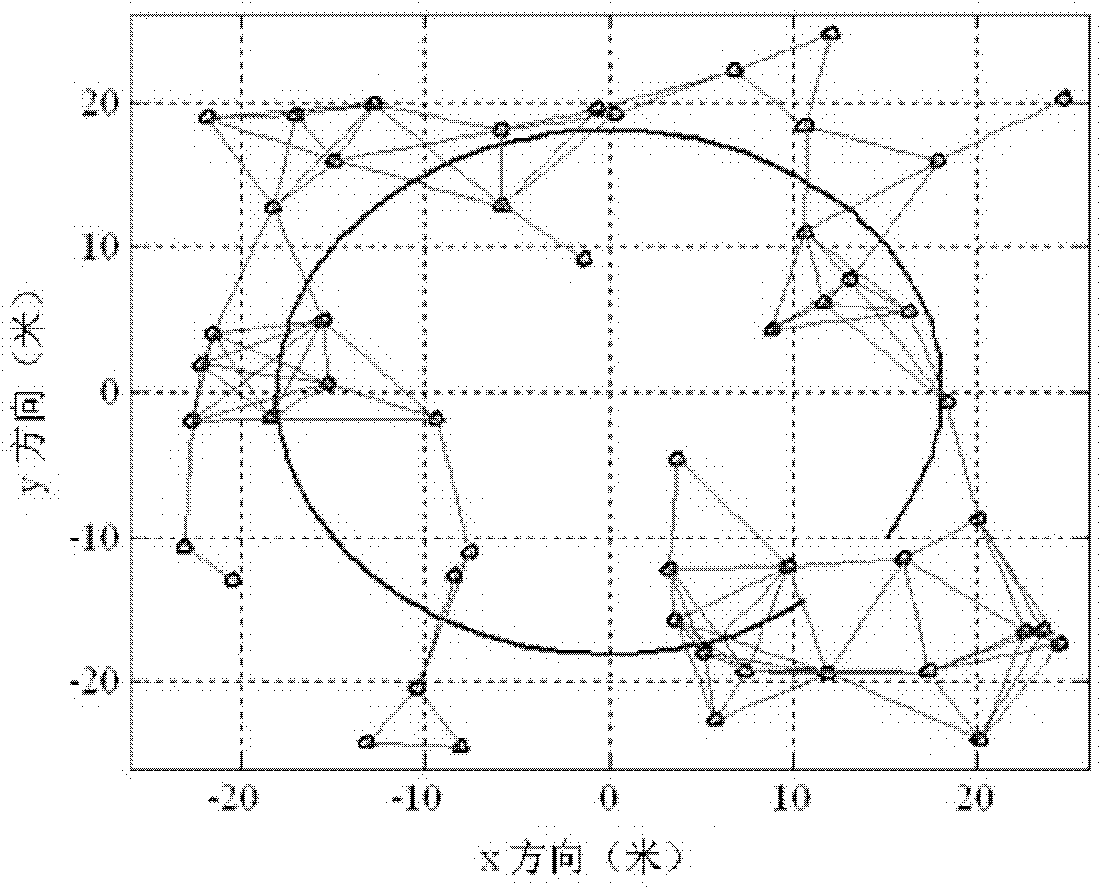
Distribution type non-linear filtering method
InactiveCN101795123AReduce Communication ComplexityReduce trafficAdaptive networkSubsonic/sonic/ultrasonic wave measurementKaiman filterStatistical linearization
The invention relates to a distribution type non-linear filtering method which belongs to the technical field of signal processing. Each sensor node in a network carries out weighing statistical linearization on a target state equation and a measuring equation to obtain a weighing statistical linearized system matrix, a measuring matrix, and linearized system noise and measuring noise; the sensor node carries out communication with the adjacent node to exchange local information contribution and obtains the overall information contribution according to a dynamic cooperation filter; the sensor node predicts the current state of the target according to the weighing statistical linearized target state equation and calculates the corresponding variance matrix; then, the target state is refreshed according to the overall information contribution obtained by the cooperation filter in the step 2, and thus, the current state evaluating valve of the target is obtained. The invention reduces the communication complexity of the filtering processing. When the traffic volume for dispersing an unscented Kalman filter is O (2450), the traffic volume required by the method is reduced to O (230).
Owner:SHANGHAI JIAO TONG UNIV
Binary weighted Byzantine fault-tolerant consensus method applied to permission blockchain
ActiveCN111682942AImprove throughputEnsure safetyUser identity/authority verificationByzantine fault toleranceComputer network
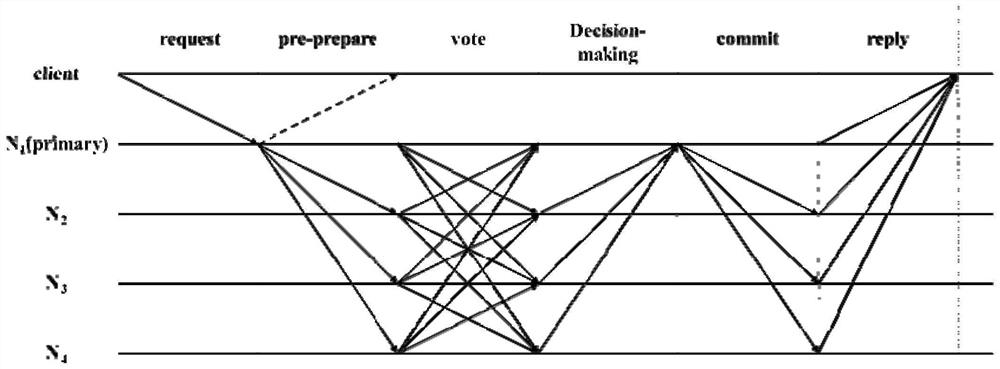
The invention discloses a binary weighted Byzantine fault-tolerant consensus method applied to a permission blockchain, and belongs to the technical field of blockchains. The method is provided for realizing weighted Byzantine fault tolerance consensus in O (n2) communication complexity in a weak synchronization network environment. The technical key points are that: the network comprises a plurality of nodes participating in consensus, and continuously monitors messages from a client or other nodes; before consensus begins, the system needs to configure global parameters including node addresses, transaction types, main node information and decision thresholds, and weight distribution is completed by each node; in an initial stage, when a main node monitors a request from the client, themain node initiates consensus; the binary weighted Byzantine fault-tolerant consensus is composed of four stages including a pre-preparation stage, a voting stage, a decision stage and a submitting stage, and after the node finishes updating a ledger, an execution result needs to be returned to the client, so that the client masters the consensus completion condition. The method is suitable for solving a consensus problem in a non-open network and a non-uniform trust permission blockchain.
Owner:HARBIN INST OF TECH +1
Safe multi-party calculation control method for realizing approximate maximum value calculation based on computer software and corresponding system
The invention relates to a safe multi-party calculation control method for realizing approximate maximum value calculation based on computer software. The method comprises the following steps: a public information negotiation module negotiates to determine an effective value range and divides intervals; the secret data preprocessing module determines the serial number of the value interval where the secret information is located and carries out calculation; the secure multi-party addition calculation and communication module performs secure multi-party summation calculation with other entities; the maximum value interval calculation module calculates an interval serial number where the maximum value is located. The invention further relates to a safe multi-party calculation control systemfor achieving approximate maximum value calculation based on computer software. By adopting the safe multi-party calculation control method for realizing approximate maximum value calculation based oncomputer software and the corresponding system, the interval where the maximum value of all secret information is located can be safely calculated under the condition that the communication complexity does not exceed O (n2), i.e., the secret information of the user is not leaked to other participating entities.
Owner:SHANGHAI GUANYUAN INFORMATION TECH +1
P2P network information resource location method having constant hop routing characteristic
InactiveCN101360055ACutting costsGood time complexityData switching networksNetwork sizeRound complexity
Disclosed is a method of positioning P2P network information resource with constant hop routing feature, relating to the computer network technology field, aiming at solving the technical problem of positioning P2P network information resource of the computer network. The resource positioning method is characterized in that: 1) the method is the first information resource positioning algorithm which completes the information request inside d routing hops with the probability 1-c ( c is a constant and can be set ), and the routing delay is a constant and is not enlarged with the network scale enlarged; 2) the method combines random neighbor strategies and DHT rings, the neighbor number space complexity of each node is referred to the illustration, and as the random neighbor selecting strategy is used, the maintenance work of the node neighbor is simpler. The resource positioning method has good time, space and communication complexity and is easy to be realized with simple structure.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
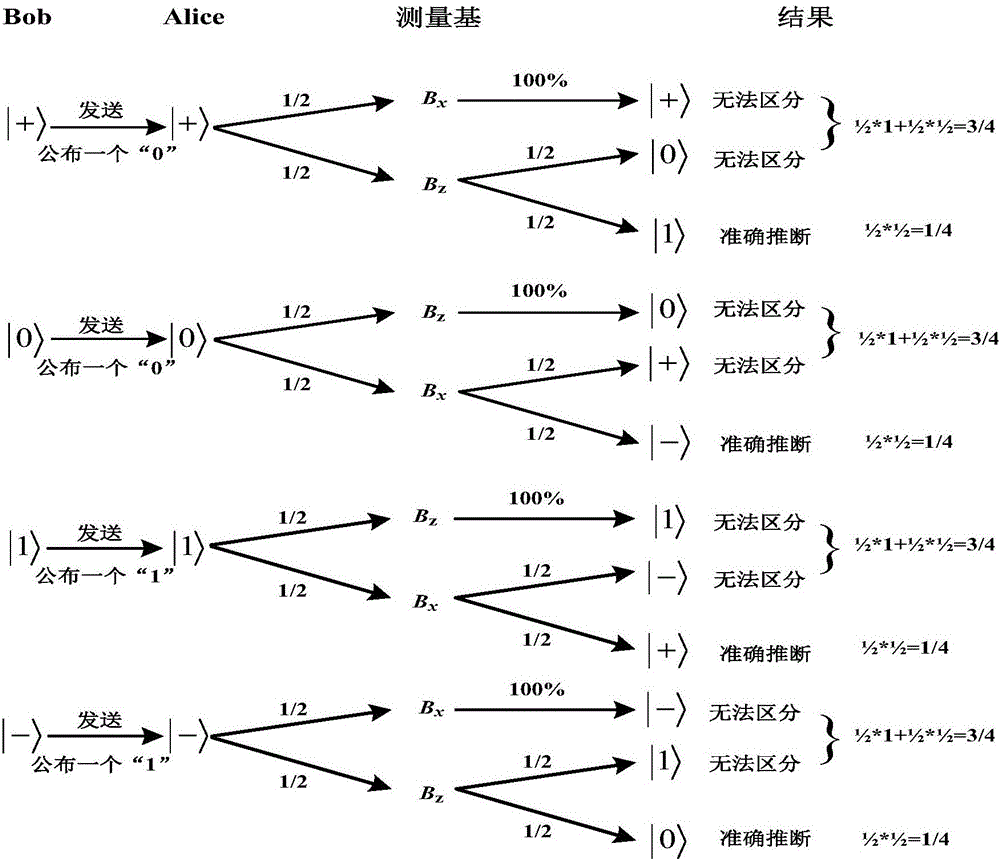
Recent privacy query method based on random quantum key distribution
InactiveCN106603232AReduce computational complexityApplicable inquiriesKey distribution for secure communicationCryptographic attack countermeasuresComputation complexityRound complexity
The invention discloses a recent privacy query method based on random quantum key distribution. The method is characterized in that two participants of a data owner Bob and a user Alice are included; the data owner Bob owns one privacy data set B; the user Alice owns one piece of privacy data x; and under the condition of protecting respective privacy, after quantum method query, the Alice acquires an element xi which is closest to the x in the Bob privacy data set. In the invention, a calculating complexity of a database server during privacy query and a communication complexity between the two parties can be reduced, and according to a physical principle of quantum mechanics, safety is increased so that the method is practical and can be suitable for recent privacy query of a large-scale database.
Owner:ANHUI UNIVERSITY
Multi-dimensional cloud resource interval finding method based on hierarchical cloud peer-to-peer network
InactiveCN105357247AGood time complexityGood space complexityTransmissionComputation complexityNetwork size
The invention relates to a multi-dimensional cloud resource interval finding method based on a hierarchical cloud peer-to-peer (P2P) network. The method comprises the following steps: establishing a multi-dimensional index by using a resource type and a resource attribute value of cloud resources respectively based on the hierarchical cloud P2P network, aggregating relevant data, and storing the aggregated relevant data in one resource bundle; and partitioning a value domain of the attribute value into a plurality of sections in order to satisfy more complex inquiries. Meanwhile, mechanisms such as resource bundle fusion and section neighbor maintenance are established, so that retrieval can be finished through an algorithm on the basis of logarithmic-degree computation complexity. The advantages of an existing structured P2P network are utilized fully. The cloud resources are stored in bundles through a hierarchical structure. The resource bundles are rapidly located at relatively low cost through a resource bundle locating technology. Meanwhile, HChord rings are established in the resource bundles, so that data relevance is kept. The structure is simple, and easy to implement. Very high time, space and communication complexity is achieved; the inquiries are finished within a logarithmic-degree hop count; and an algorithm routing hop count does not increase rapidly along with the increase of a network scale.
Owner:UNIV OF SHANGHAI FOR SCI & TECH
Consensus output block generation method based on blockchain node network
ActiveCN111130790AReduce complexityLower requirementSpecial service provision for substationUser identity/authority verificationDigital signatureEngineering
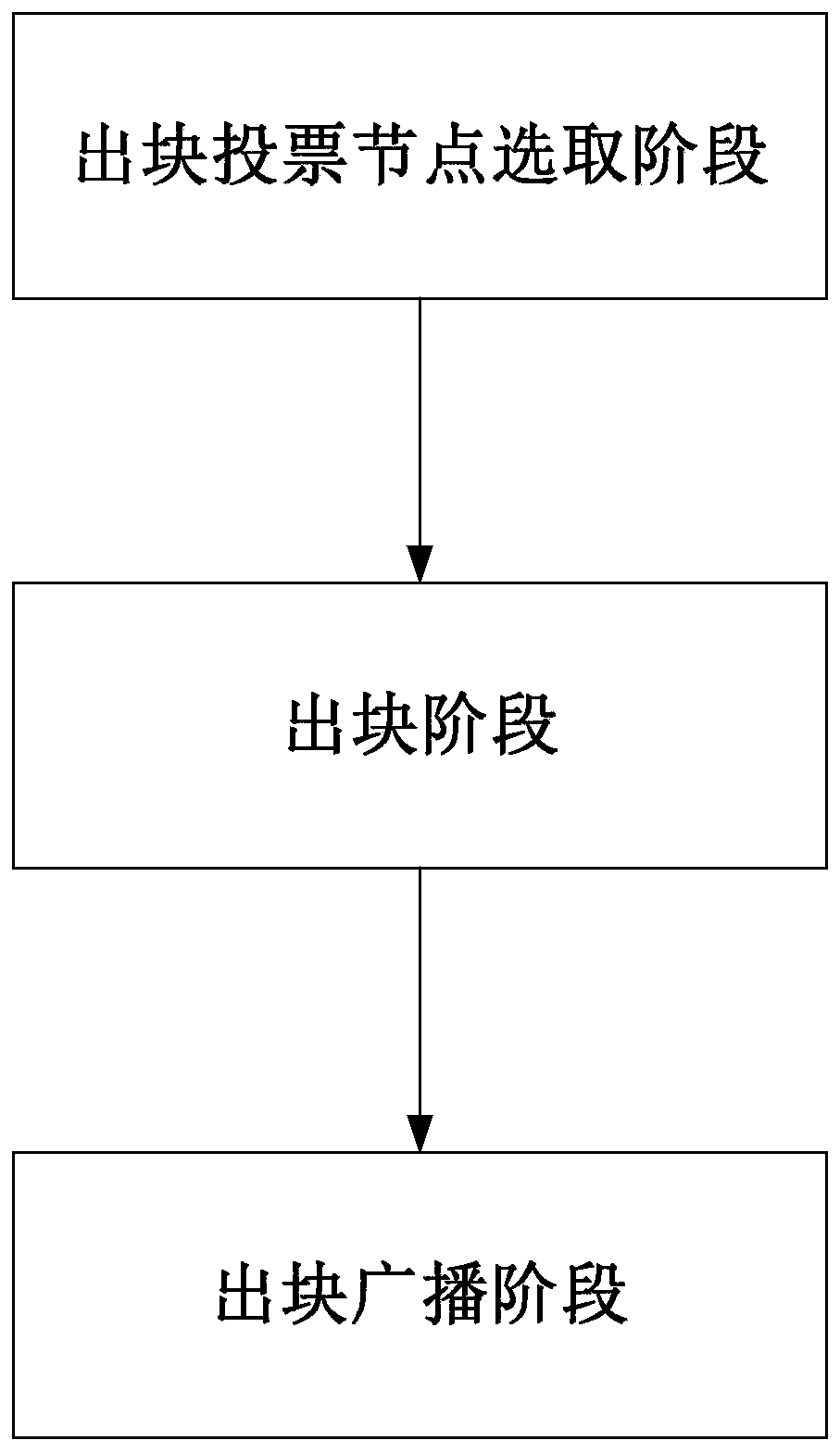
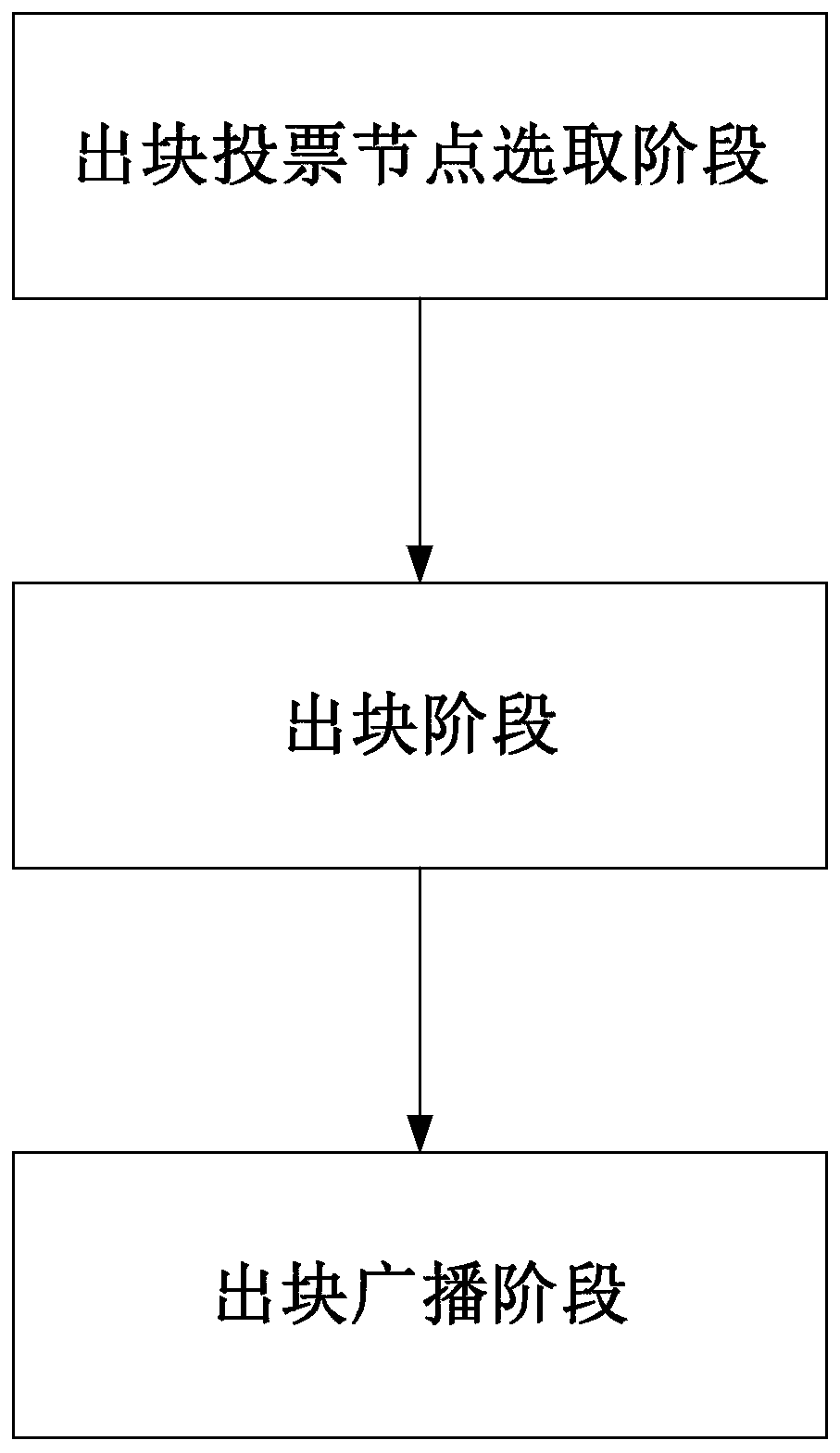
The invention discloses a consensus output block generation method based on a blockchain node network. The method comprises the following steps: firstly, output block voting nodes are selected; a voting node of a next output block is obtained; then, all the block chain nodes send the corresponding block output opportunity values OP to the voting nodes respectively; the received block output opportunity values OP is subjected to priority division and digital signature via the voting node, a digital signature voting request is generated and sent to the corresponding sending node, and the sending node obtains a voting result according to the digital signature voting request and outputs a block according to the voting result. According to the method disclosed in the invention, priority division is carried out by selecting voting nodes according to the OP; according to the method, voting is carried out substantially according to the block output opportunity values OP, so that communicationfrequency and the number of the voting nodes form a linear relationship, communication complexity can be reduced, all block chain nodes can be used to send the block output opportunity values OP, a decentration degree is guaranteed, and high safety performance is realized.
Owner:SICHUAN INTERSTELLAR ROEWE TECH CO LTD
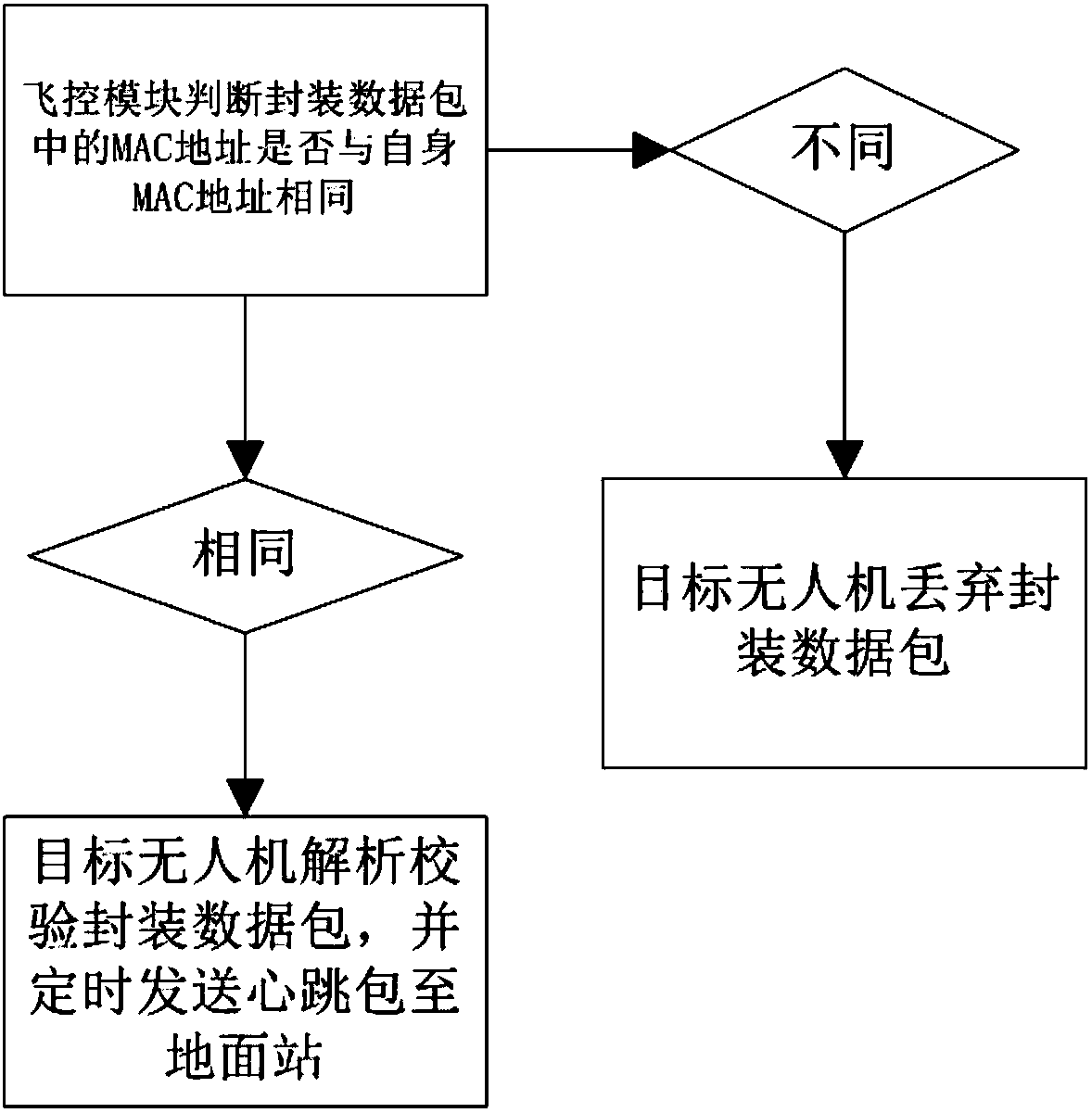
Unmanned aerial vehicle control method
InactiveCN108319294AEasy to controlImprove efficiencyPosition/course control in three dimensionsTelecommunications linkFlight control modes
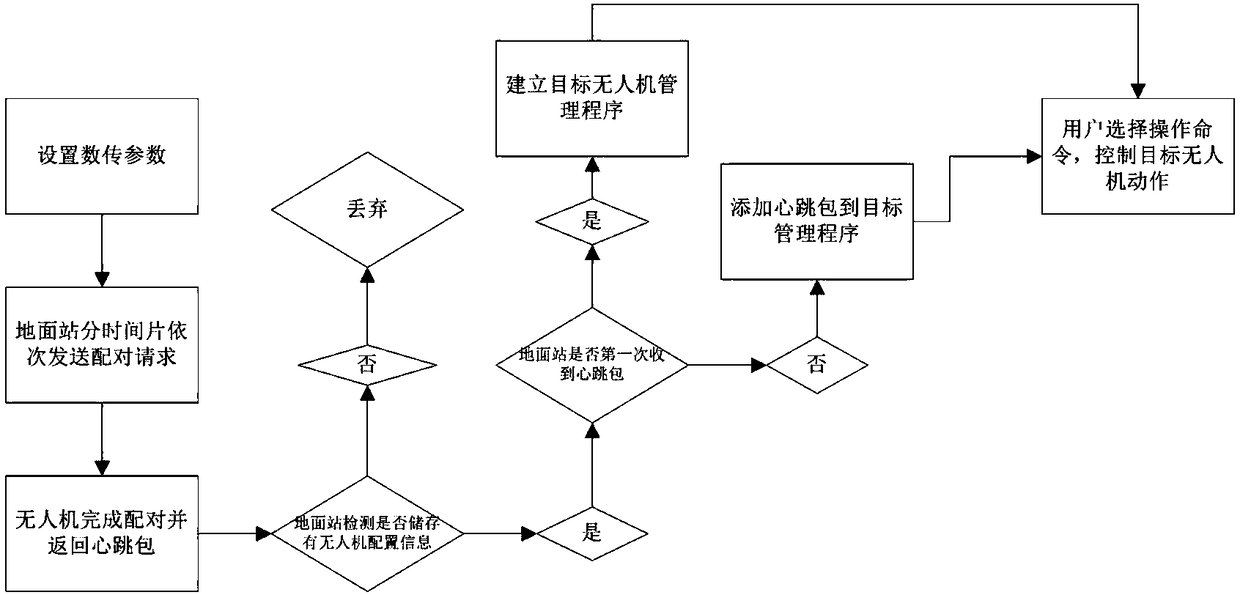
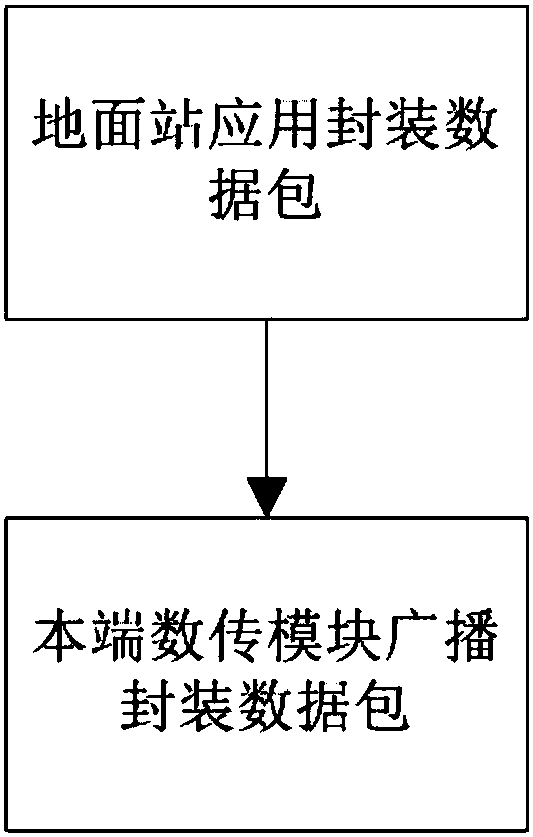
The invention discloses an unmanned aerial vehicle control method. A ground station and a number of unmanned aerial vehicles are comprised. The ground station comprises a local end data transmission module. Each unmanned aerial vehicle is provided with an independent flight control module, and the flight control module is connected with an opposite end data transmission module. The method comprises the steps that the data transmission parameters of the local end data transmission module and the opposite end data transmission modules are set in the same frequency band, so that the local end data transmission module and the opposite end data transmission modules can be connected for communication; and the local end data transmission module and each opposite end data transmission module all have independent MAC addresses. According to the unmanned aerial vehicle control method provided by the invention, the use efficiency of the ground station is improved; the communication complexity isreduced; and a communication link between a ground station application and multiple unmanned aerial vehicles is realized.
Owner:CHENGDU SKYLIN TECH CO LTD
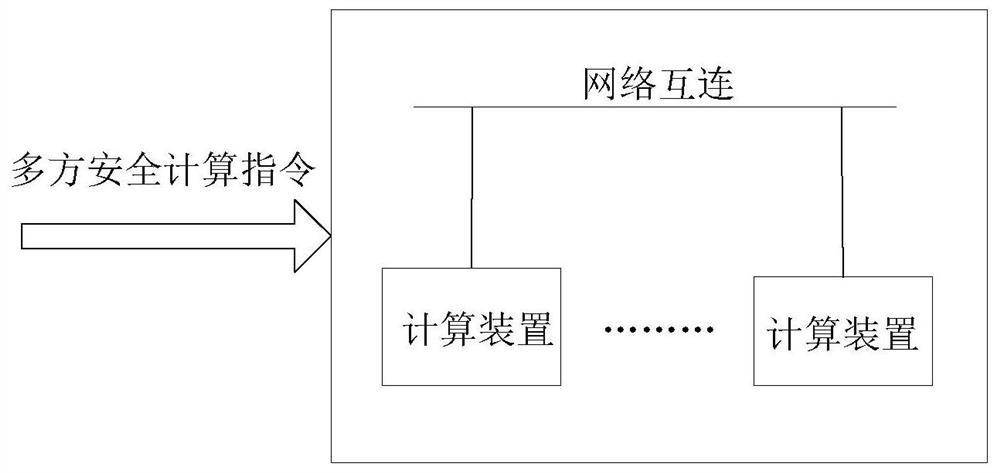
Multi-party security computing all-in-one machine
PendingCN111931250AReduce Communication ComplexityDigital data protectionInternal/peripheral component protectionCiphertextComputing systems
The invention provides a multi-party secure computing all-in-one machine. The all-in-one machine comprises a plurality of computing devices, wherein each computing device is configured in an untrustedcomputing system architecture, a multi-party security computing protocol is preset in each computing device, and when a multi-party security computing instruction is received, the multi-party security computing protocol and at least another computing device execute multi-party security computing based on the multi-party security computing protocol and the obtained scattered ciphertext. Accordingto the all-in-one machine, an integrated multi-party security computing platform is provided for users, and a problem of high computing communication complexity of multi-party security computing in the prior art is solved.
Owner:HUAKONG TSINGJIAO INFORMATION SCI BEIJING LTD
Personal file permission chain management system and method based on improved multi-layer PBFT
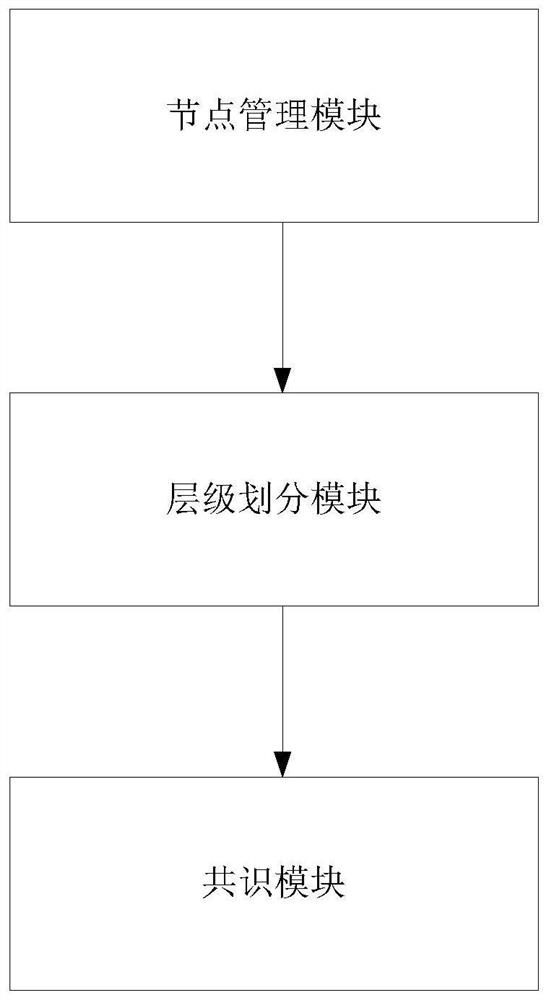
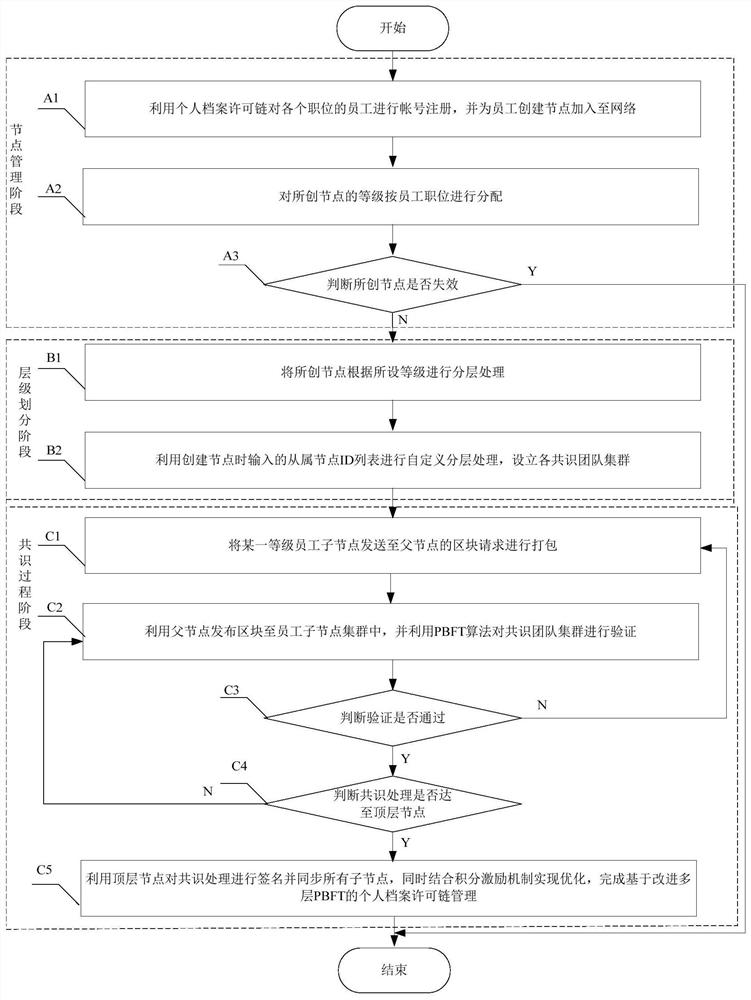
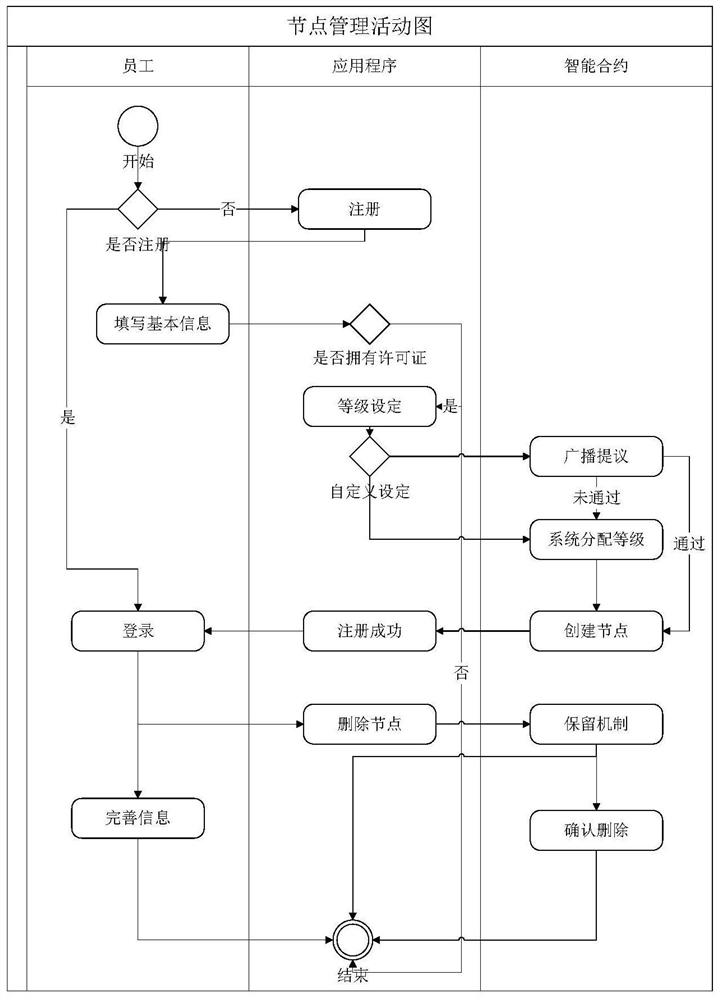
ActiveCN111858105AClear hierarchySolve scalabilityInterprogram communicationDatabase distribution/replicationDistributed computingManagement system
The invention provides a personal file permission chain management system and method based on improved multi-layer PBFT, belongs to the technical field of block chains, and comprises a node managementmodule, a hierarchical division module and a consensus module which are connected in sequence. The node management module is used for performing node creation, grade allocation and node deletion management on participated nodes by utilizing a personal file permission chain; the hierarchical division module is used for carrying out hierarchical division on all the nodes according to the levels ofthe nodes and carrying out user-defined hierarchical processing through the node levels and the slave node ID list; and the consensus module is used for realizing optimization in combination with a PBFT consensus algorithm, the multi-layer nodes and an excitation mechanism. Through the design, the problems that a license chain system is poor in node expansibility, high in inter-node communicationcomplexity, low in system efficiency after the number of nodes is increased and the like are solved, the total single consensus communication duration of the license chain management system is effectively shortened, and the single consensus communication frequency is greatly reduced.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA +1
Efficient and safe two-party computing system and computing method based on cooperation
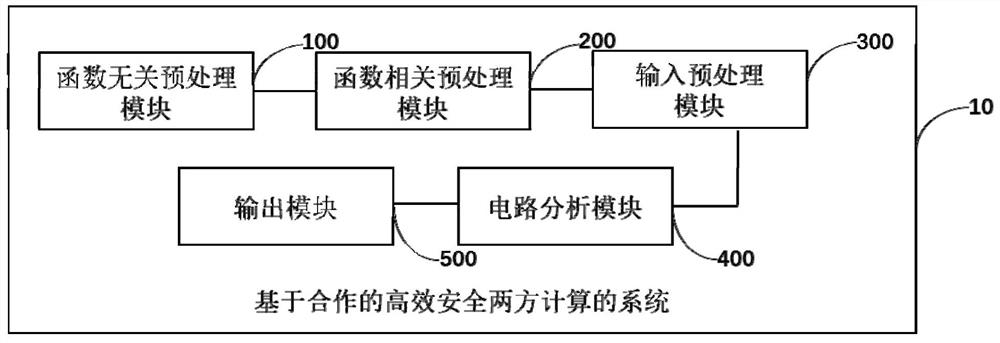
PendingCN113591146AReduce complexityReduce communication delayDigital data protectionSecuring communicationCorrectnessComputing systems
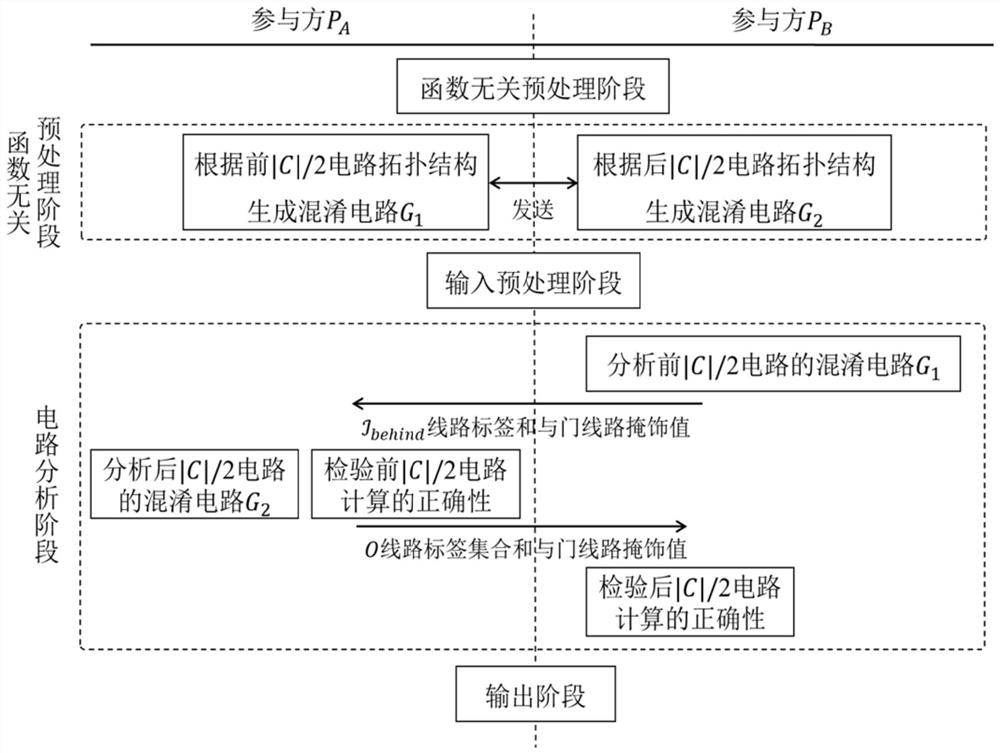
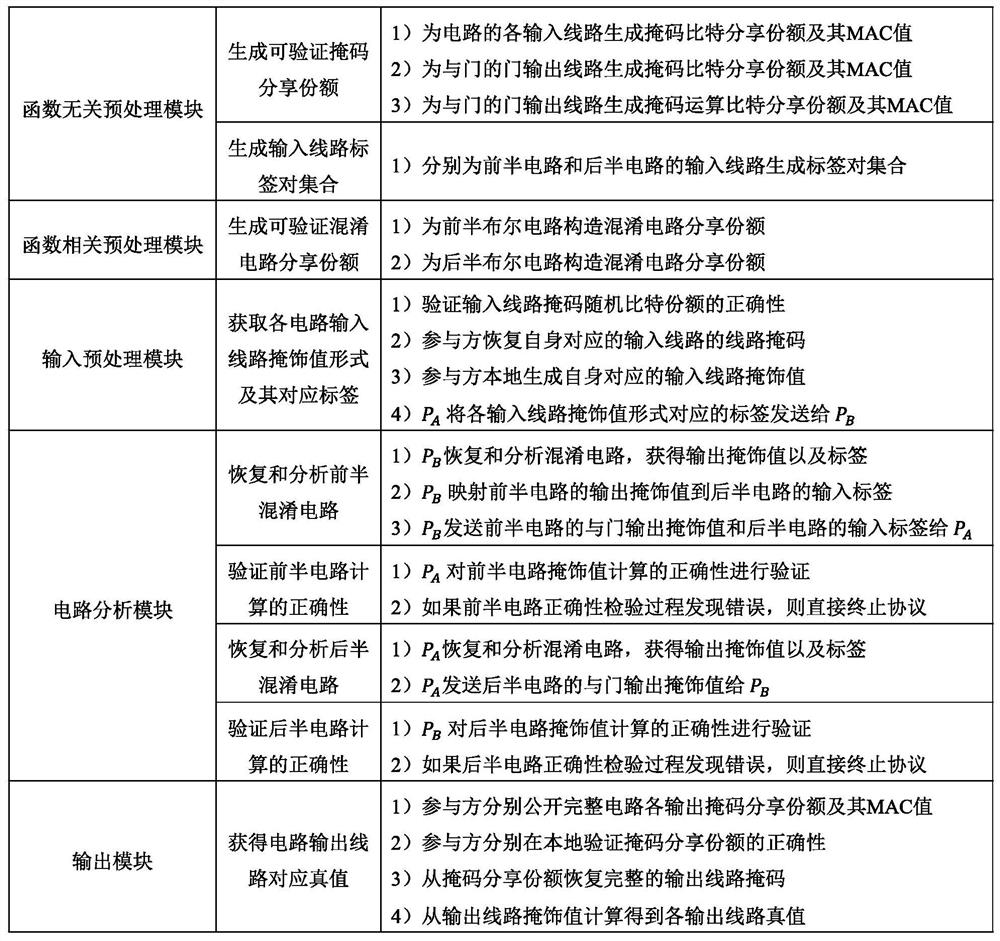
The invention discloses an efficient and safe two-party computing system and method based on cooperation, and the system comprises: a function-independent preprocessing module which is used for pre-generating verifiable random bit sharing shares and a label pair set of an input line, which are needed by safe computing, for two communication parties; a function correlation preprocessing module, wherein participants serve as confusion parties respectively, and verifiable confusion circuit sharing shares are generated for the first half circuit and the second half circuit respectively; an input preprocessing module, wherein a calculation side obtains a label set corresponding to a true value masking value form of each input line of the circuit; a circuit analysis module, wherein participants serve as calculation parties in sequence, confusion circuits of a front half circuit and a rear half circuit are recovered and analyzed respectively, and the correctness of circuit calculation is verified; and an output module, wherein the two communication parties obtain the corresponding masking values from the output line labels and recover the output true values. According to the system, circuit calculation correctness and input privacy can be ensured, communication complexity is low, both parties share calculation pressure, safety calculation efficiency is high, and malicious opponents can be resisted.
Owner:BEIHANG UNIV
Uninterruptible power supply (UPS) method and equipment having active voltage adjustment
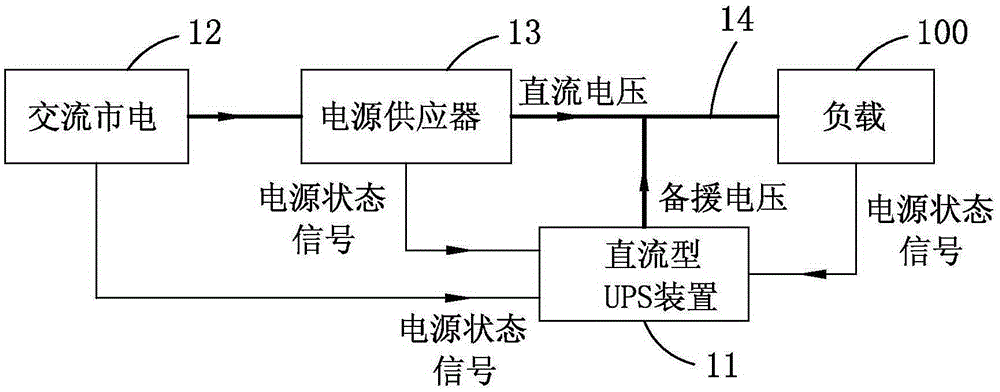
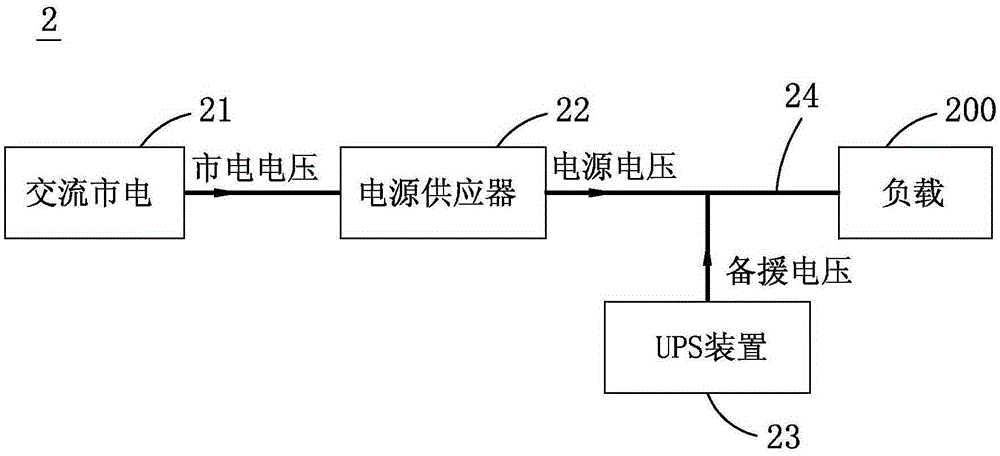
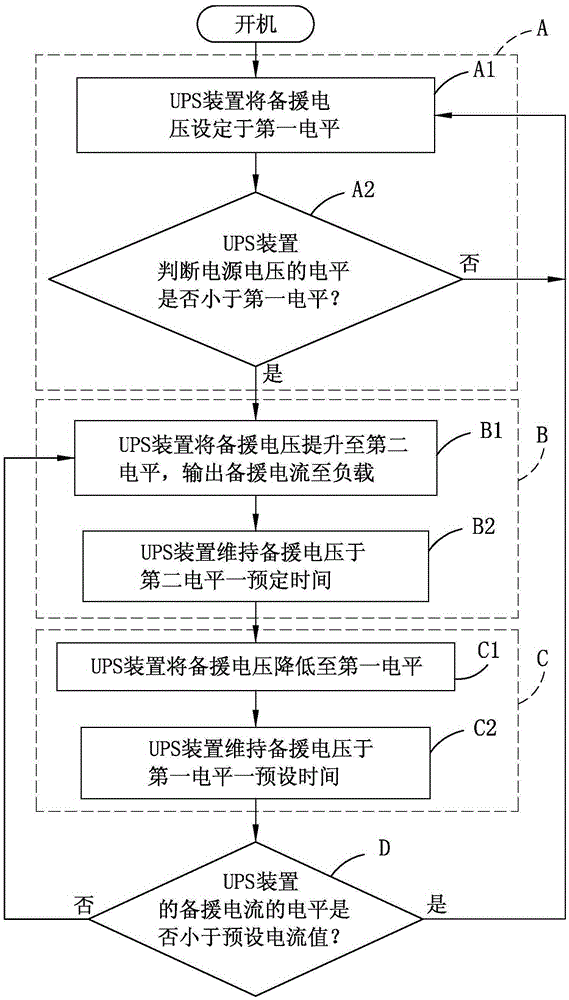
ActiveCN106611995AReduce complexityEmergency power supply arrangementsCommunication complexityMains electricity
The invention relates to UPS equipment. The UPS equipment comprises at least one power supply, at least one UPS device and a bus; the power supply receives commercial power voltage, and performs voltage conversion of the commercial power voltage so as to generate power supply voltage; the UPS device generates backup voltage; the bus outputs one of the power supply voltage and the backup voltage to a load, wherein the UPS device judges whether the power supply voltage is abnormal or not according to the level of the power supply voltage; if the power supply voltage is abnormal, the UPS device increases the level of the backup voltage to the power supply voltage, which is greater than the power supply voltage when the power supply voltage is abnormal, and outputs backup current to the load through the bus; furthermore, the UPS device gradually decreases the level of the backup voltage, and detects whether the level of the backup current is less than a pre-set current value or not, so that whether the power supply voltage is still abnormal or not is judged; the UPS device determines whether the backup current is supplied or not directly and actively; the fact that the power supply condition is known according to an external state signal from the power supply or the load is unnecessary; and the wiring and communication complexity can be lightened.
Owner:LITE ON ELECTRONICS (GUANGZHOU) LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com