Method for pre-distributing wireless sensor network cipher key
A wireless sensor and network key technology, applied in the field of information network, can solve the problems of huge communication overhead, decreased security of the whole network, and high security threshold
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
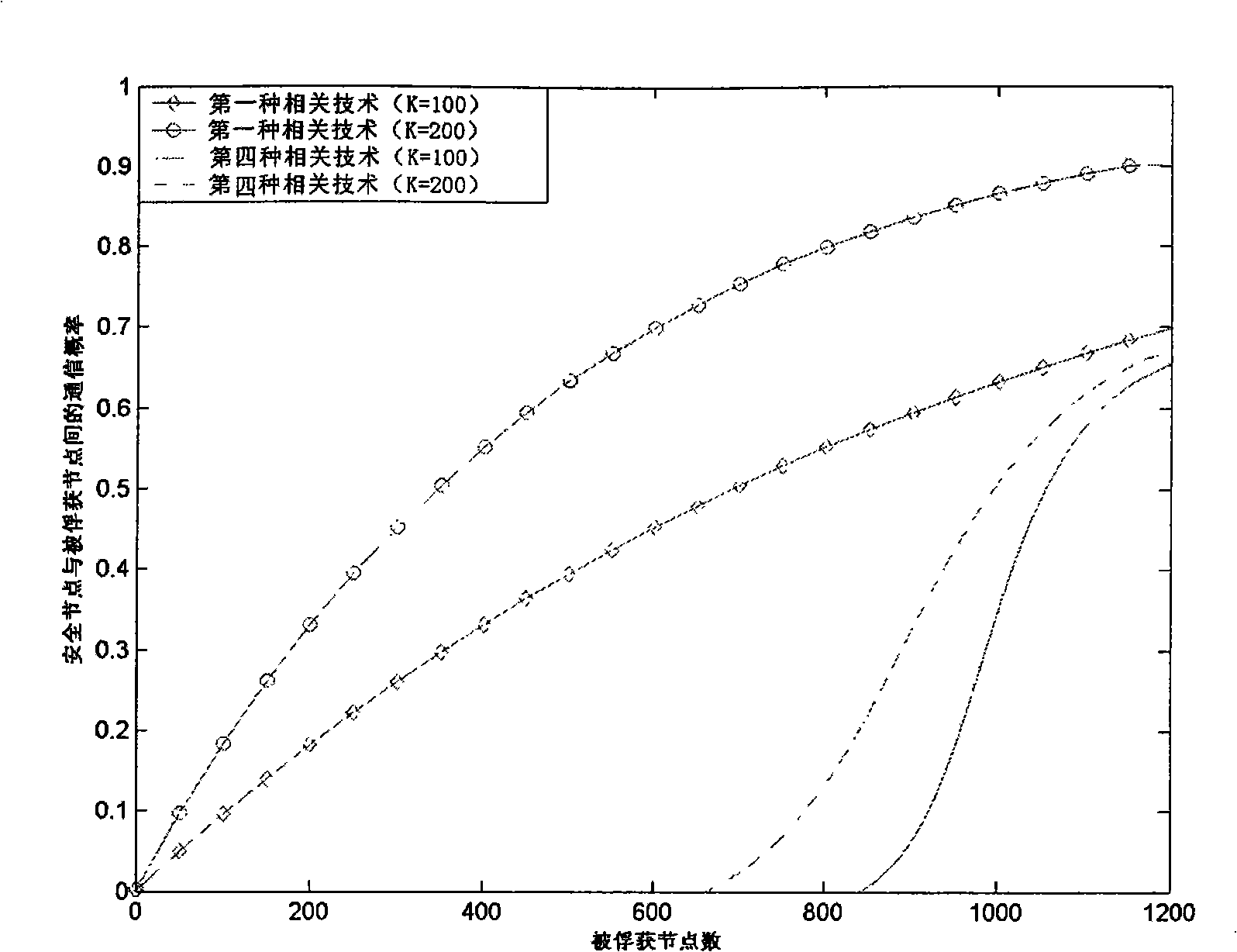
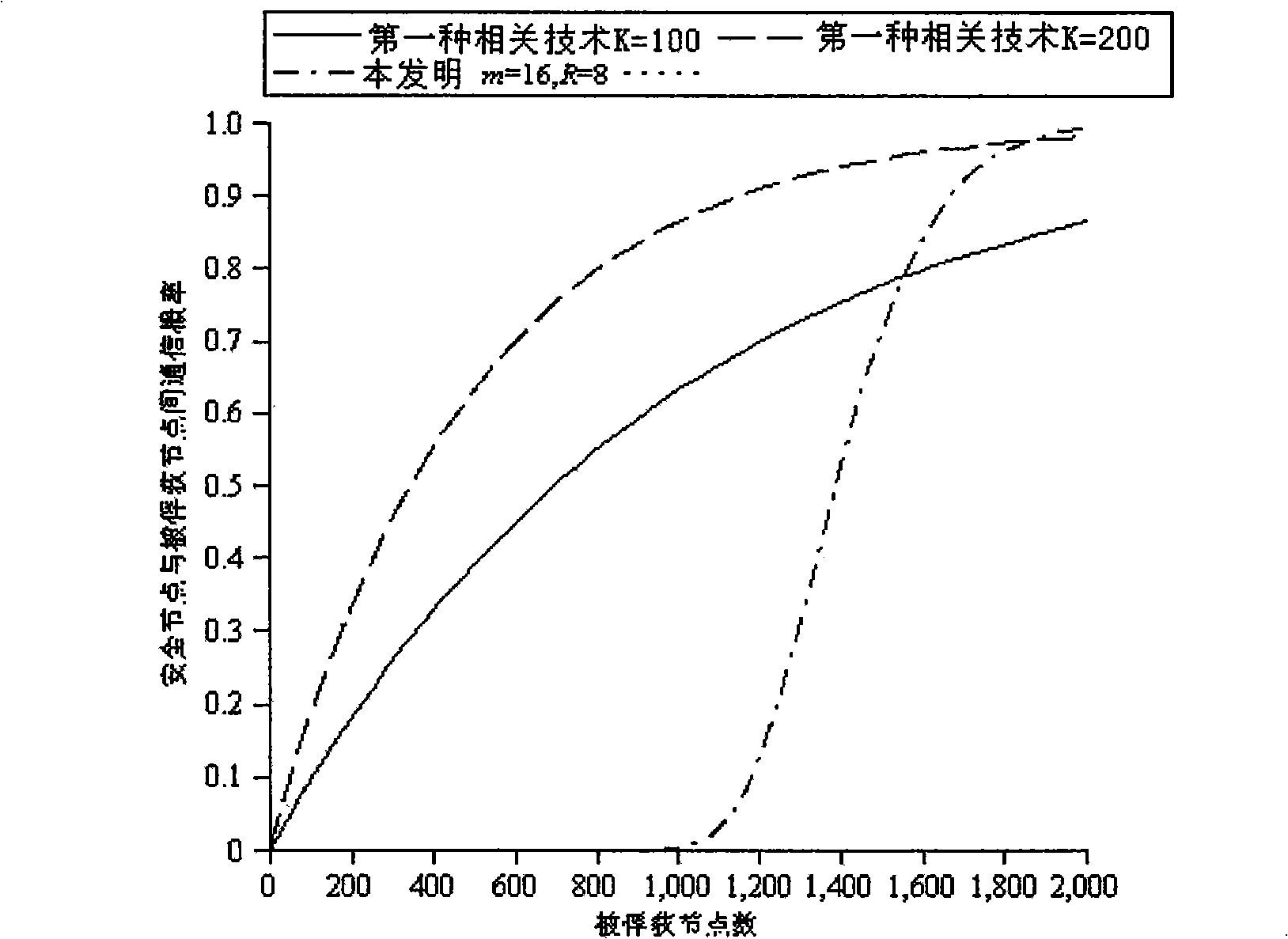
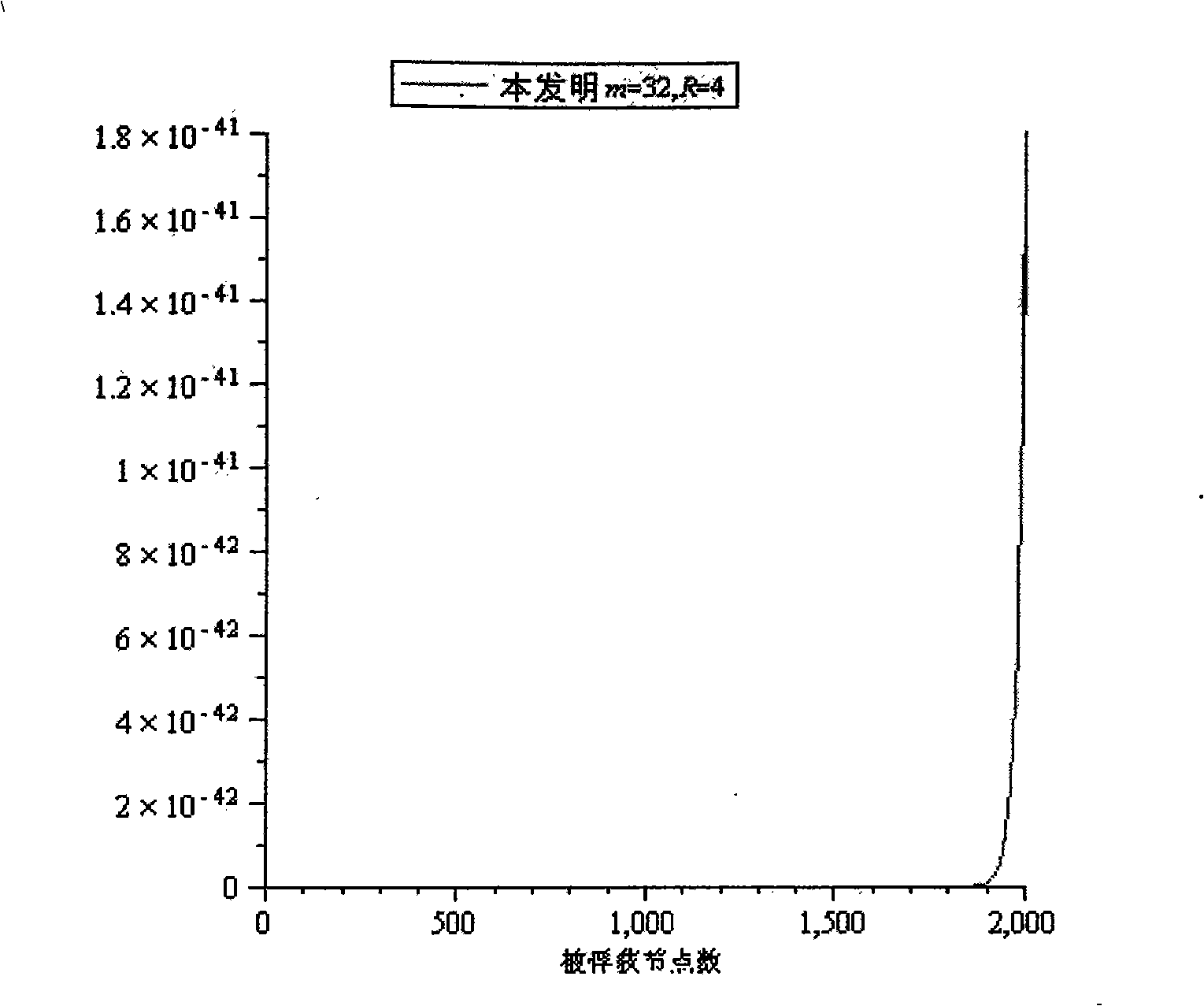
[0103] The main content of the present invention includes the inverse algorithm of LU matrix decomposition, multi-dimensional key space and 2-element R-1 degree polynomial, which is divided into three stages as follows: key pre-distribution stage, clustering networking stage, and normal operation stage.
[0104] 1. Key pre-distribution stage
[0105] (1): The deployment server randomly generates R upper triangular matrices G and R diagonal matrices D (allocated as R groups, R is the key space dimension). Among them, gi≠0 (i=2,...,m) and gi are not equal to each other, d i ≠0 (i=1,...,m) and d i are not equal to each other.
[0106] G = 1 1 1 . . . 1 g ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com