Industrial internet intrusion detection and defense method and device
An industrial Internet and intrusion detection technology, which is applied in the field of industrial Internet intrusion detection and defense methods and devices, can solve problems such as cumbersome operations, and achieve the effects of ensuring normal operation, reducing the probability of network attacks, and reducing the intensity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
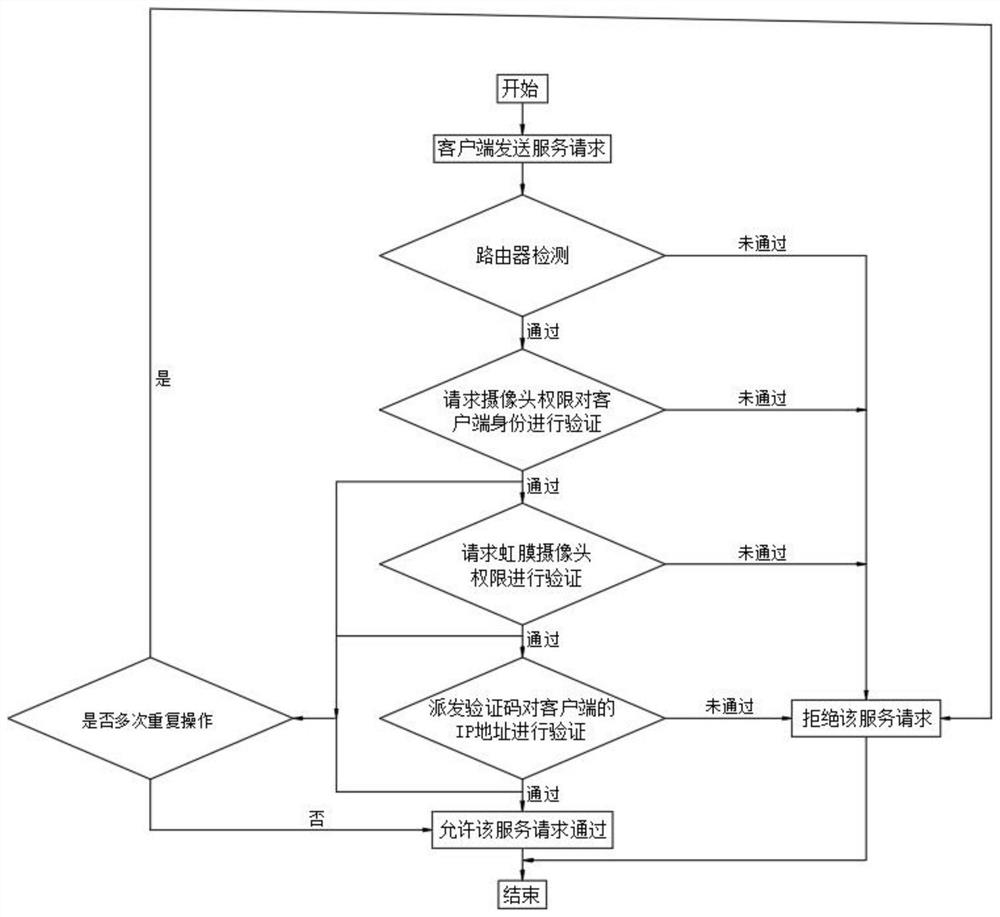
[0022] Such as figure 1 An embodiment of the present invention provides an industrial Internet intrusion detection and defense method, including the following steps:
[0023] When the client sends a service request, it first goes through the router detection. When the detection fails, the service request will be rejected directly. When the detection passes, the camera permission of the client is requested to identify and verify the identity of the operator's face on the client. When the verification fails When the verification is passed, the service request will also be rejected. When the verification passes and enters the next step of verification, it will accept the detection of the number of verification times. When too many verification times are detected, the service request will also be rejected, and the next step will be to request the iris of the client. The authority of the camera will further verify the identity of the operator. If the verification fails, the service...
Embodiment 2
[0028] The difference between this embodiment and Embodiment 1 is: when only verifying the number of operations to verify the IP address, then the number of times the operator can perform repeated operations on face authentication and iris authentication, although to a certain extent, it can be convenient The operator performs the operation, but repeating the two steps of the operator many times will also cause a certain impact on the network operation, increase the possibility of the network being attacked, and further reduce the operation security of the network.
Embodiment 3
[0030] An embodiment of the present invention provides an industrial Internet intrusion detection and defense device, including a face verification module, an iris verification module, an IP address verification module, and an operation count detection module;
[0031] The face verification module will determine whether the camera picture belongs to special processing through operations such as blinking, nodding, and shaking the head, so as to avoid whether the account is stolen;
[0032] The iris verification module is to further verify the identity information of the operator by detecting and comparing the iris information of the operator;
[0033] The verification of the number of operations is to avoid the risk of man-made multiple operations that may attack the network, and directly cut off the source of the attack.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com