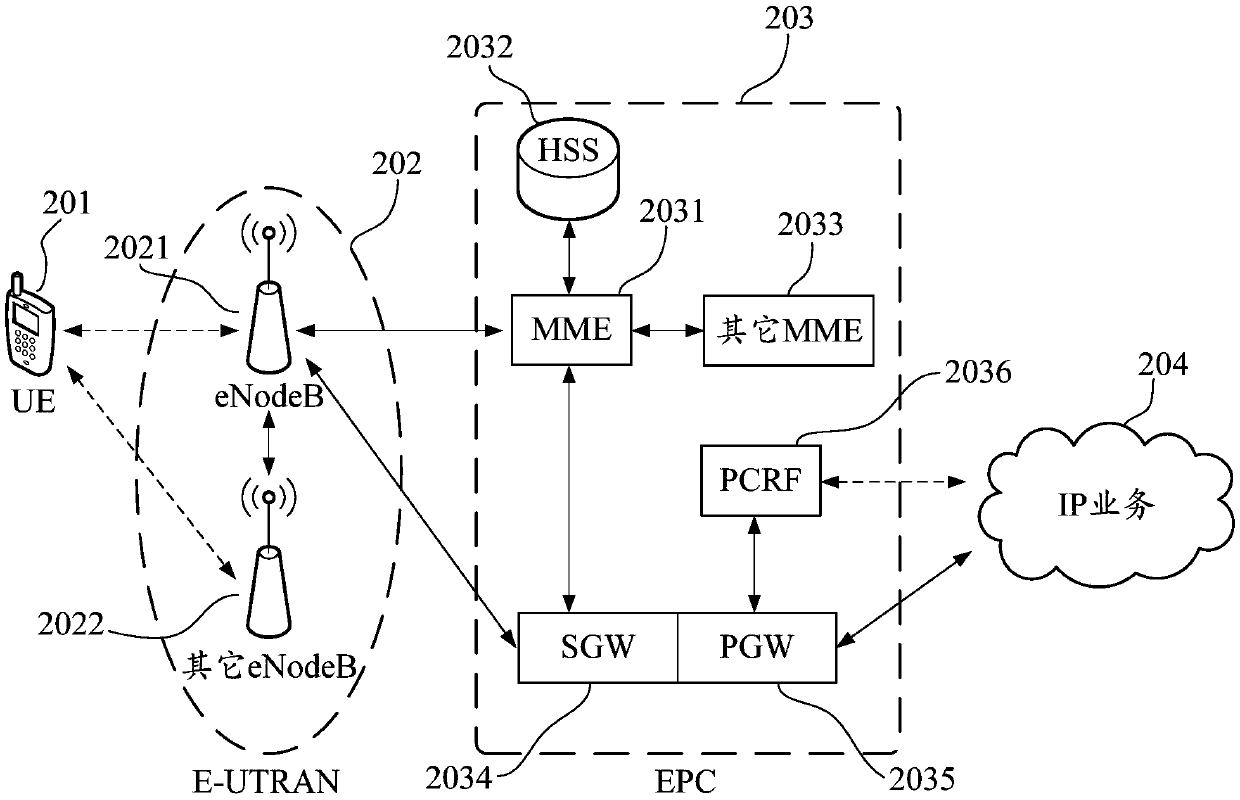
Patents
Literature
50 results about "Iris verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
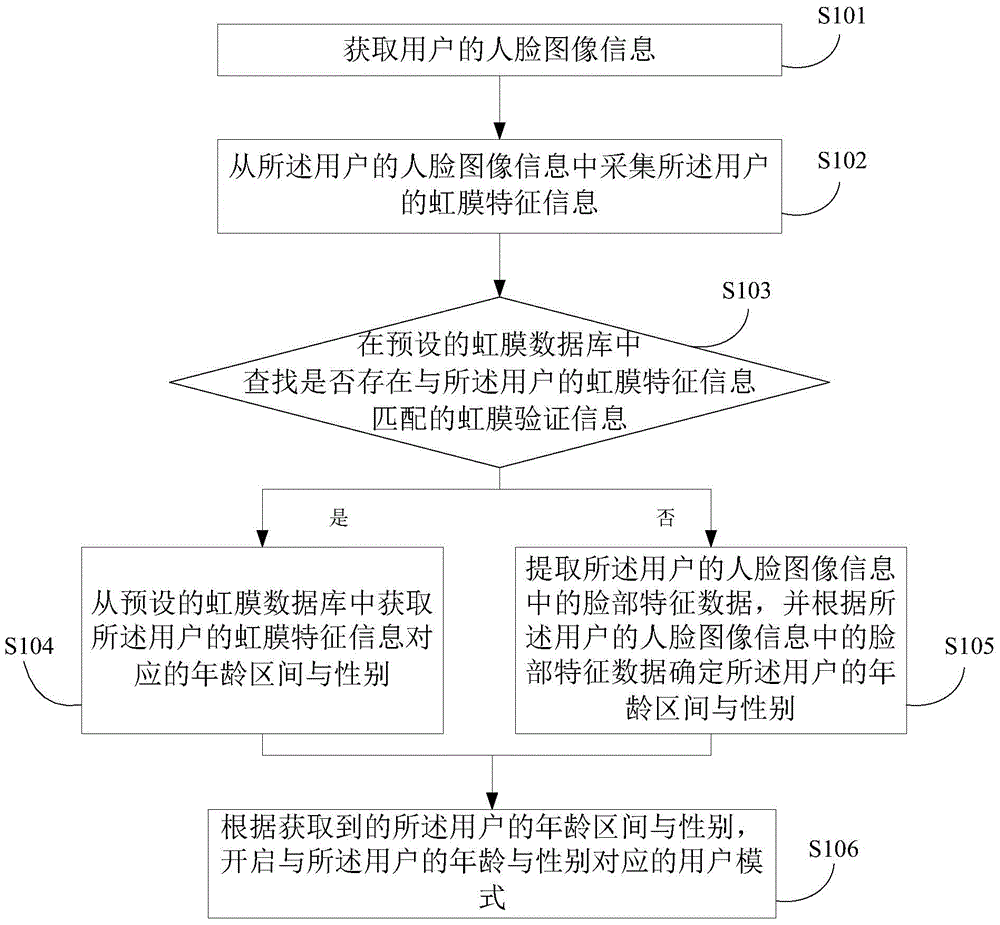
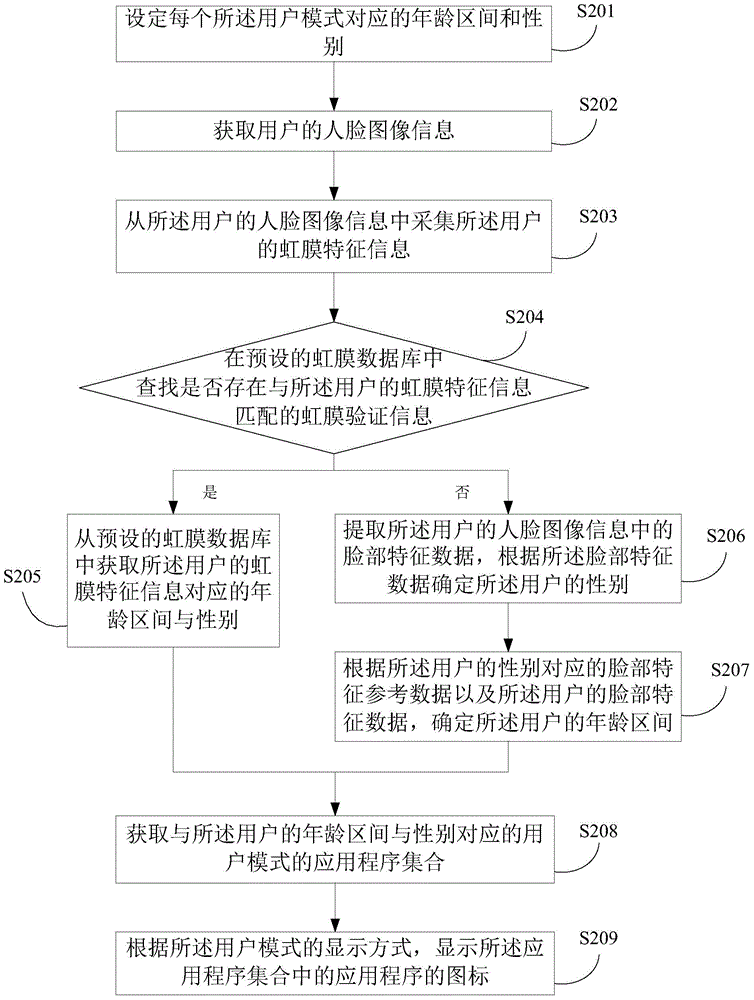
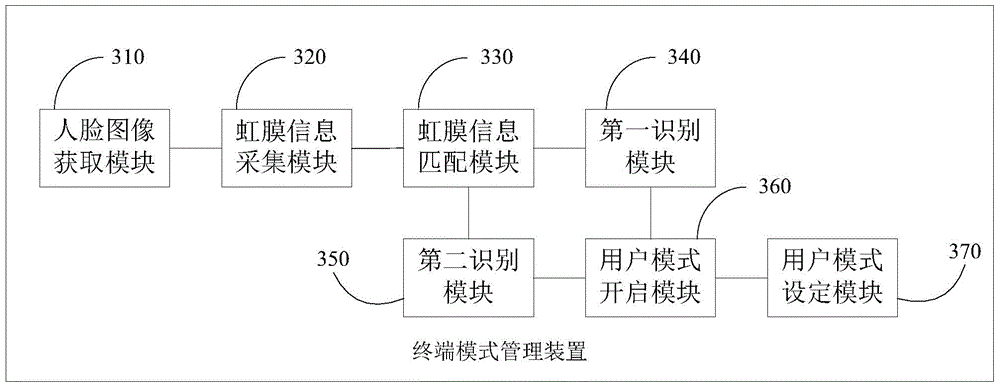
Terminal mode management method and apparatus
InactiveCN105574386AAvoid multiple mode switchesAvoid mode settingDigital data authenticationAcquiring/recognising facial featuresFeature dataComputer science
Embodiments of the invention disclose a terminal mode management method and apparatus. The terminal mode management method comprises the steps of obtaining facial image information of a user; collecting iris feature information of the user from the facial image information; checking whether iris verification information matched with the iris feature information of the user exists or not; of so, obtaining the age section and the gender corresponding to the iris feature information of the user; or otherwise, extracting facial feature data from the facial image information of the user for determining the age section and the gender of the user; and opening a corresponding user mode according to the obtained age section and the gender of the user. The invention also discloses a terminal mode management apparatus. By adoption of the terminal mode management method and apparatus, the age section and the gender of the user can be determined according to the iris feature information of the facial image information or the facial feature data so as to adaptively present the user mode suitable for the user, and to avoid multiple times of mode switching and mode setting by the user.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
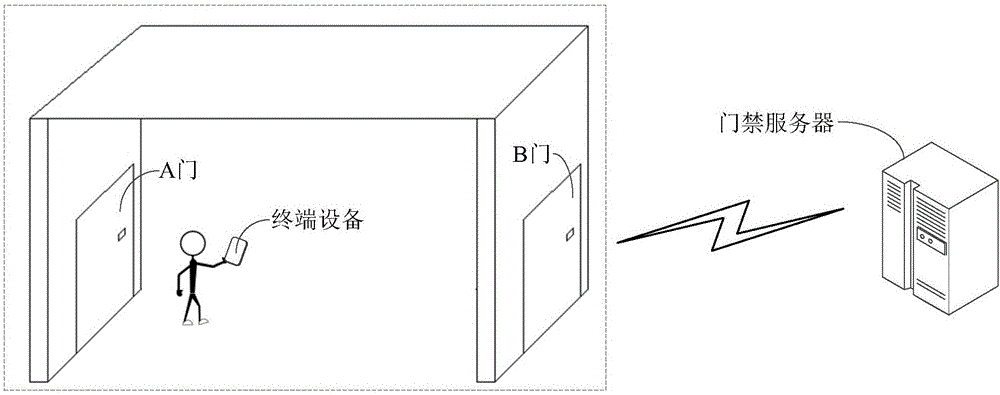
A safety verification method, device and server
InactiveCN106716503AImprove securityIndividual entry/exit registersTerminal equipmentComputer terminal
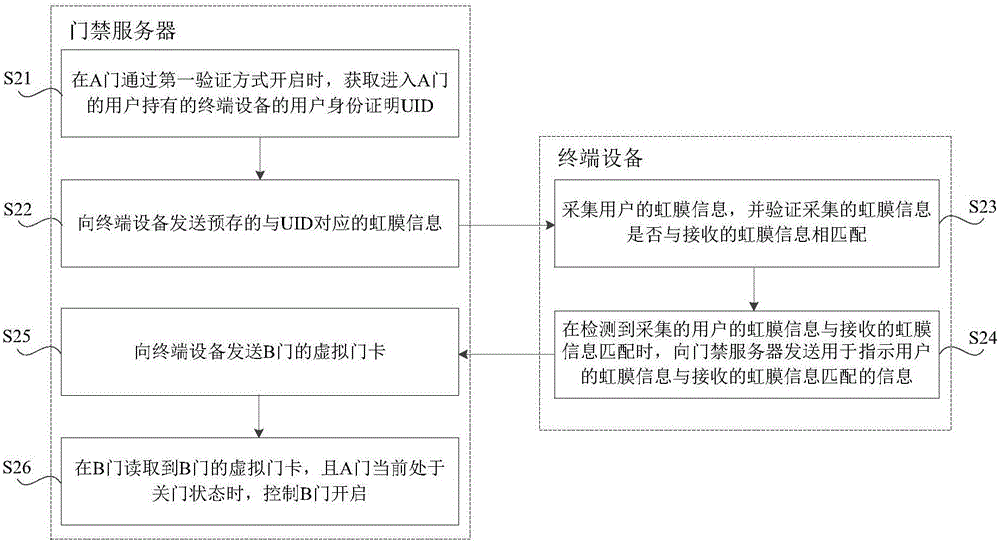
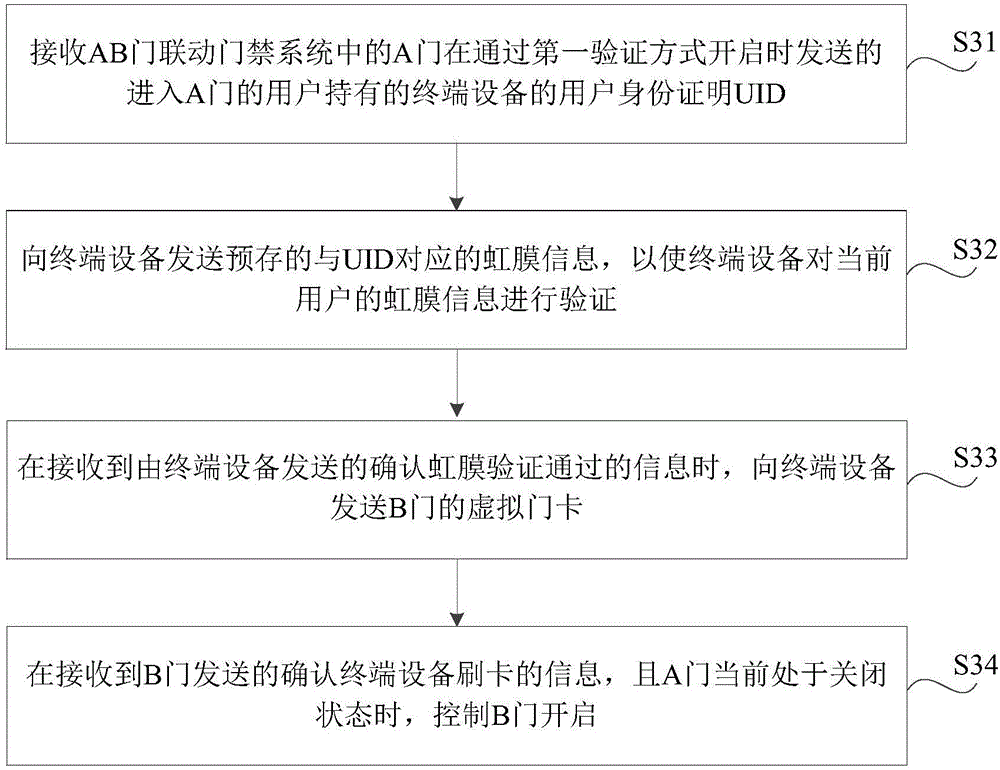
A safety verification method, device and server are disclosed and are used for improving safety of an AB door linkage access control system. The method includes: acquiring a user identity certificate UID of a terminal device held by a user entering an A door at an access control server when the A door is opened through a first verification manner, with the first verification manner being a non-iris verification manner; sending prestored iris information corresponding to the UID to the terminal device; at the terminal device, collecting iris information of the user, and verifying whether the collected iris information is matched with the received iris information or not; if the collected iris information is matched with the received iris information, sending a message indicating that the iris information of the user is matched with the received iris information to the access control server; at the access control server, sending a virtual door card of a B door to the terminal device; and reading the virtual door card of the B door at the B door, and controlling the B door to open when the A door is in a closed state.
Owner:CLOUDMINDS (SHENZHEN) ROBOTICS SYST CO LTD
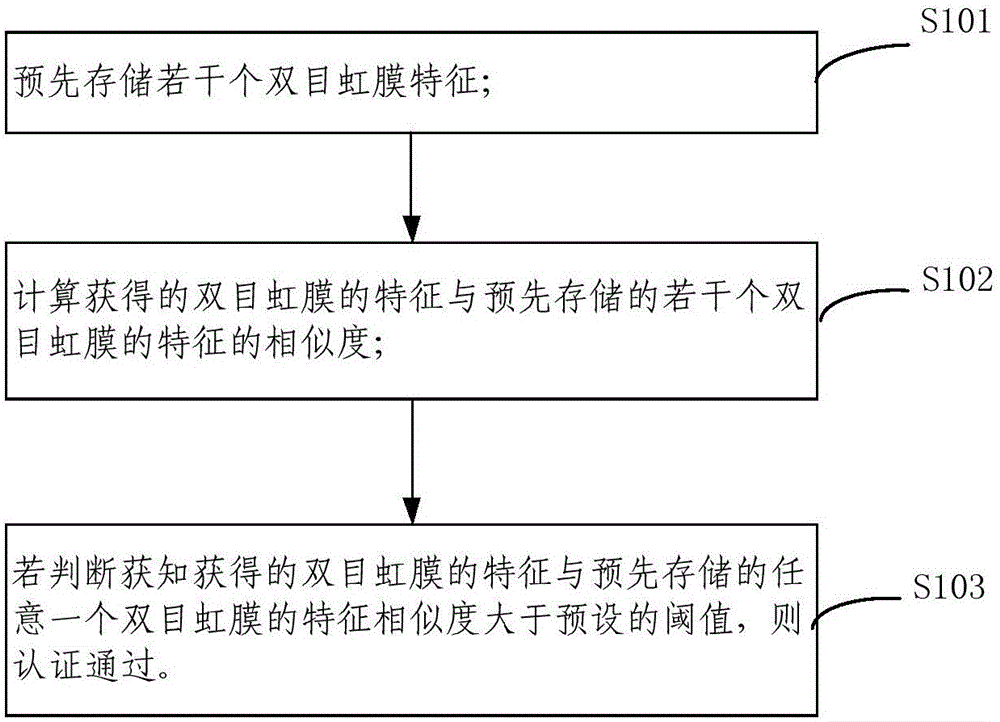
Binocular iris characteristic obtaining method, binocular iris characteristic obtaining device, identity identification method and identity identification system
InactiveCN105868731AIncrease the difficultyImprove securityAcquiring/recognising eyesPattern recognitionIdentity recognition
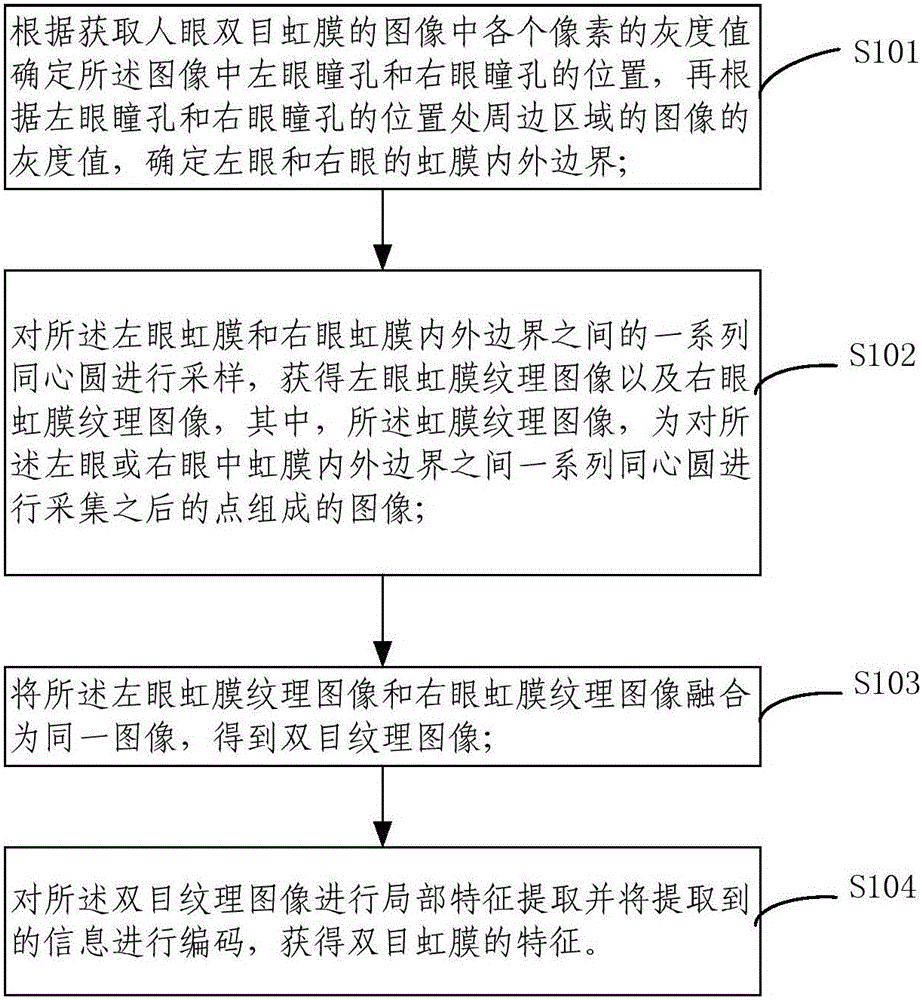
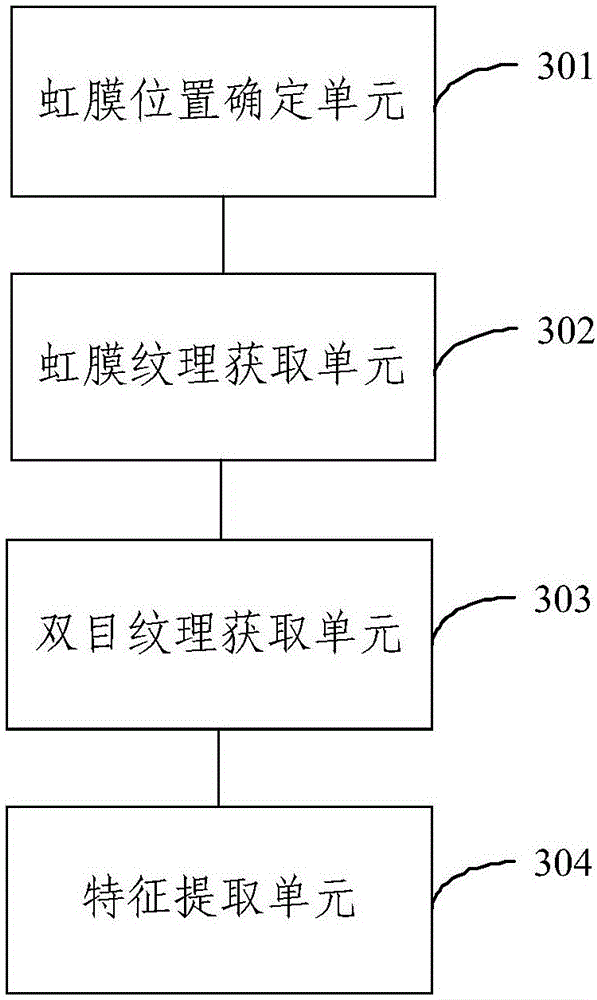
The invention provides a binocular iris characteristic obtaining method, a binocular iris characteristic obtaining device, an identity identification method and an identity identification system. The binocular iris characteristic obtaining method comprises the steps of respectively determining boundaries of a left-eye iris and a right-eye iris in an image; sampling a series of concentric circles between the left-eye iris boundary and the right-eye iris boundary, and acquiring a left-eye iris pattern image and a right-eye iris pattern image; fusing the left-eye iris pattern image and the right-eye iris pattern image for obtaining one image, thereby obtaining a binocular pattern image; performing partial characteristic extraction on the binocular pattern image and coding the extracted information, thereby obtaining a binocular iris characteristic. The amount of information contained in the binocular iris characteristic is two times of that of information contained in a single-eye iris characteristic, thereby effectively improving identification safety and improving difficulty in breaking iris verification when the binocular iris characteristic is applied in identity identification.
Owner:SHANXI WORLD TECH CO LTD
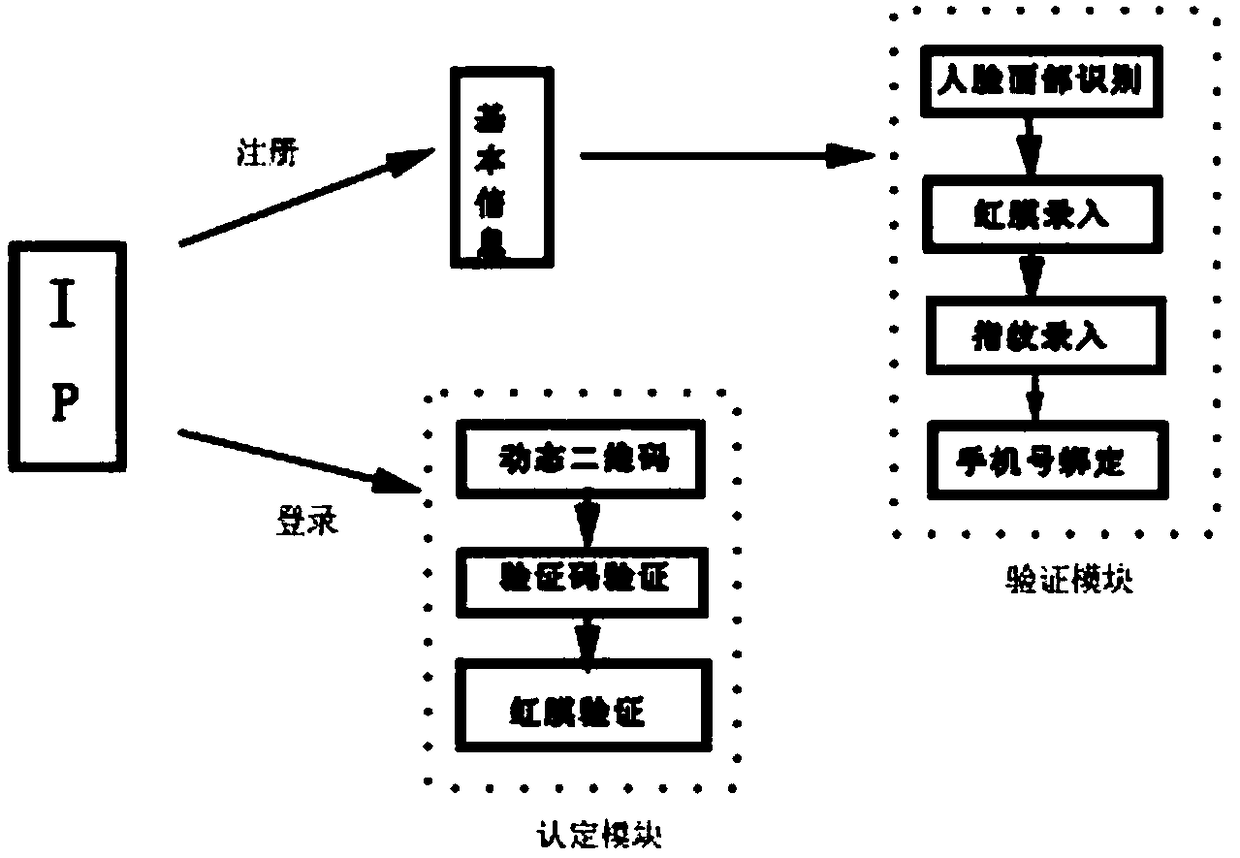
Computer network authentication system and method, computer program
InactiveCN109214160AHigh precisionPrevent leakageCharacter and pattern recognitionDigital data authenticationComputer terminalAuthentication system
The invention belongs to the field of information technology, the invention relates to a computer network authentication system and a computer program. The IP terminal of the computer network authentication system comprises a login unit and a registration unit. The registration unit comprises a basic information interface and an authentication module. The authentication module comprises a face recognition interface, an iris upload interface and a fingerprint input interface. The login unit comprises an identification module, wherein the identification module comprises a dynamic two-dimensionalcode interface, an authentication code verification interface and an iris verification interface; the dynamic two-dimensional code interface information is scanned to enter the verification code interface, and the verification code interface information enters the iris verification interface. The invention integrates real name authentication, face recognition authentication, eye iris authentication and fingerprint authentication to avoid leakage of personal identity and privacy information. Scanning two-dimensional code to improve the convenience of system login.
Owner:WENZHOU VOCATIONAL COLLEGE OF SCI & TECH
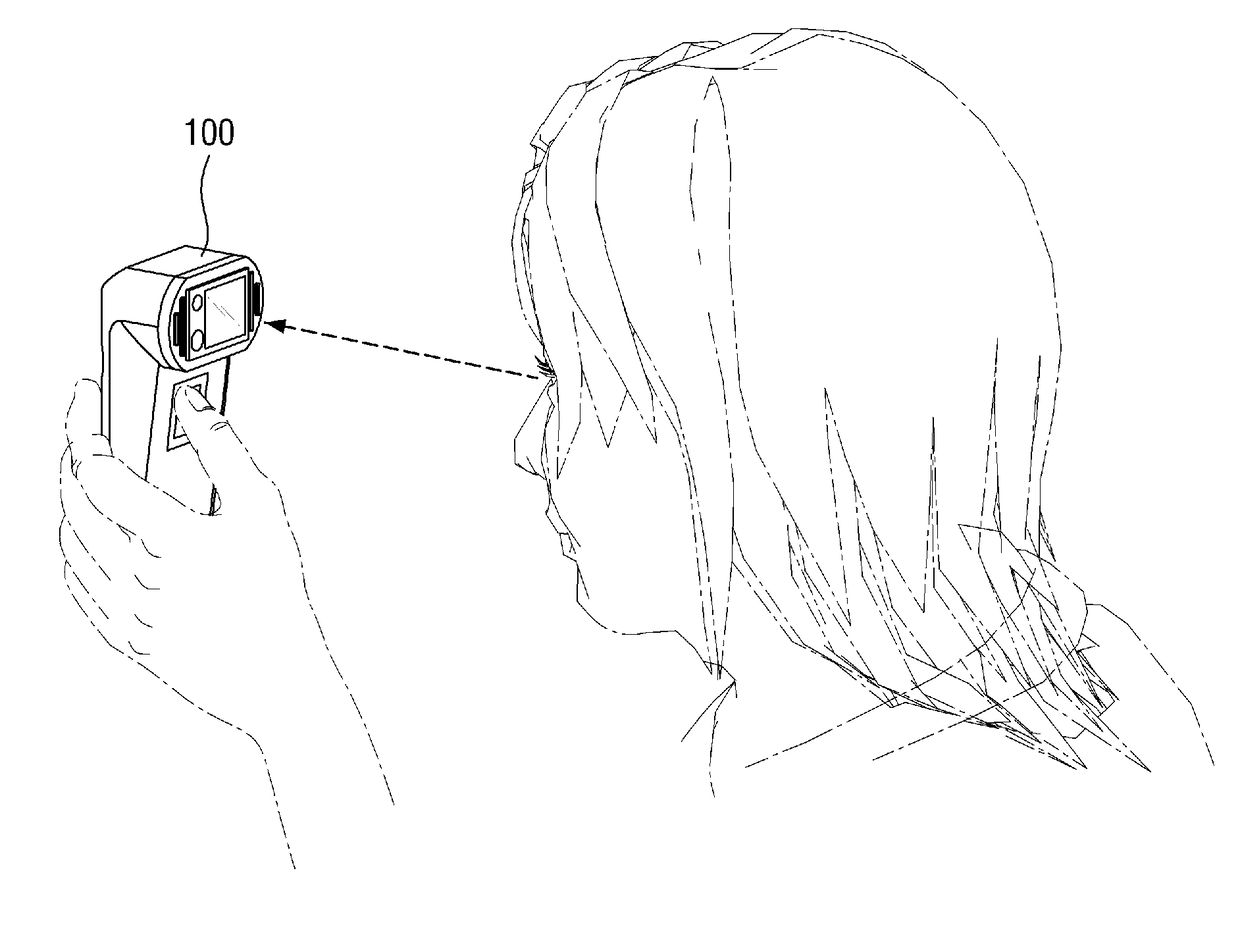
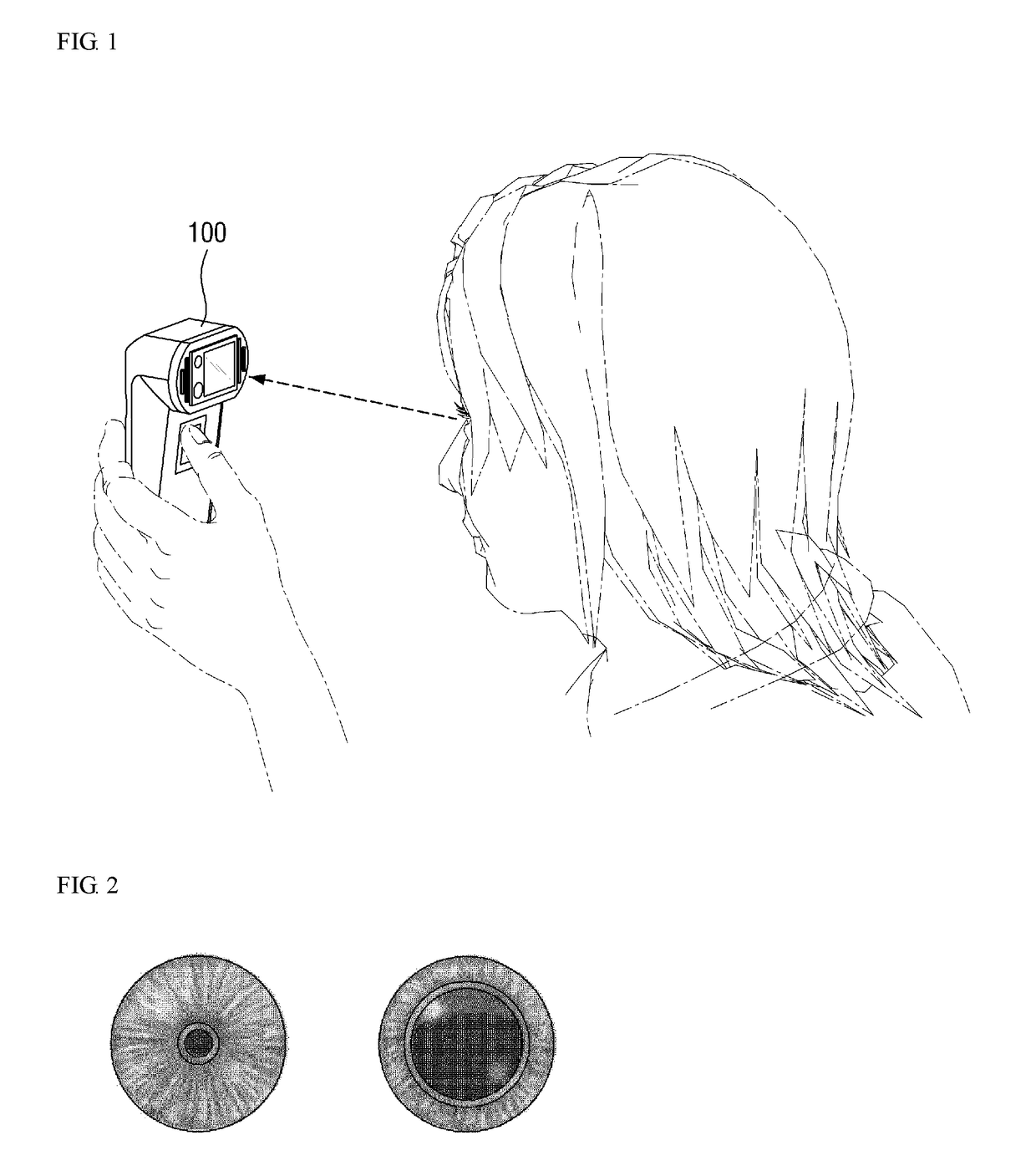
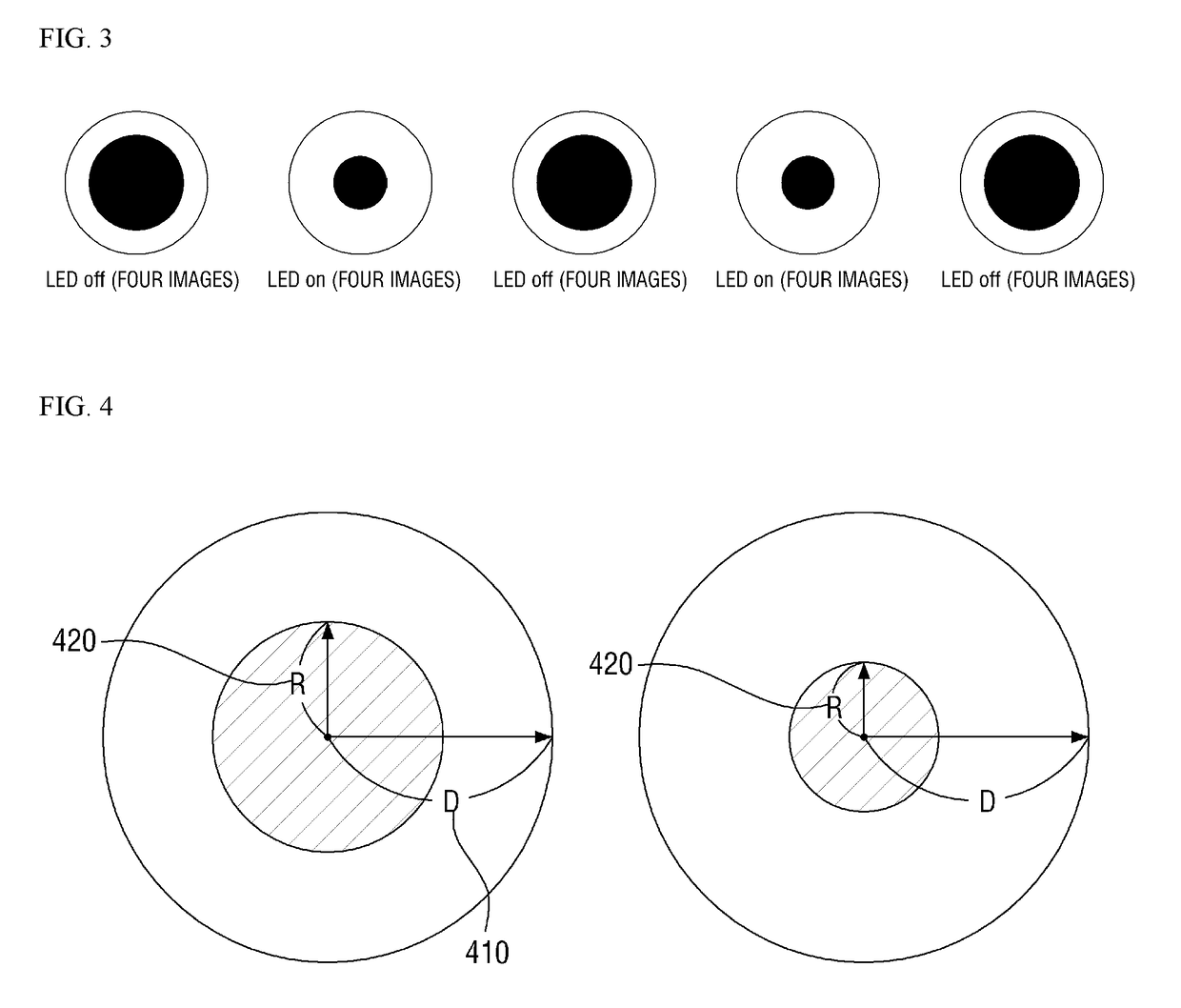
Iris Authentication Device
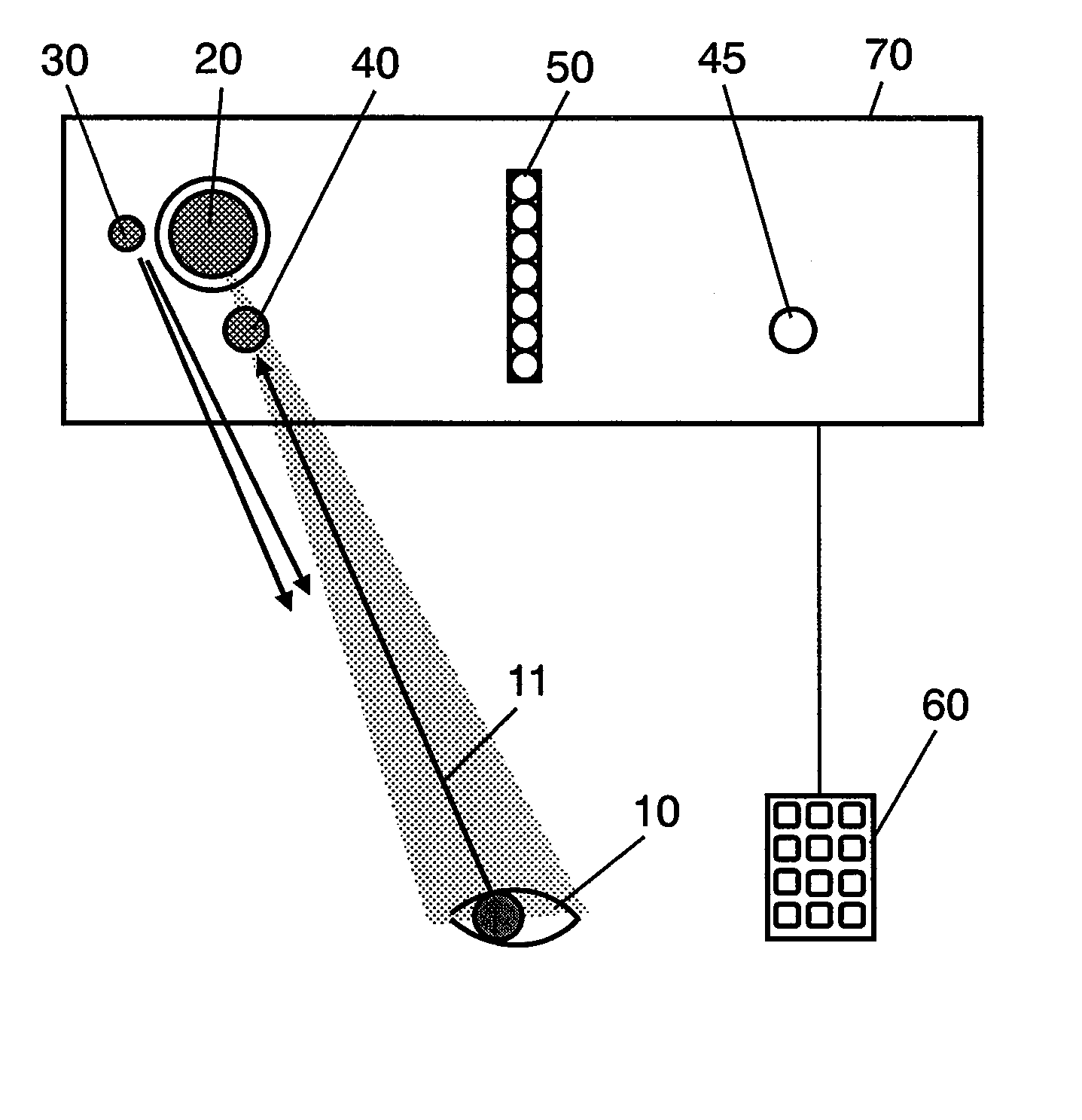
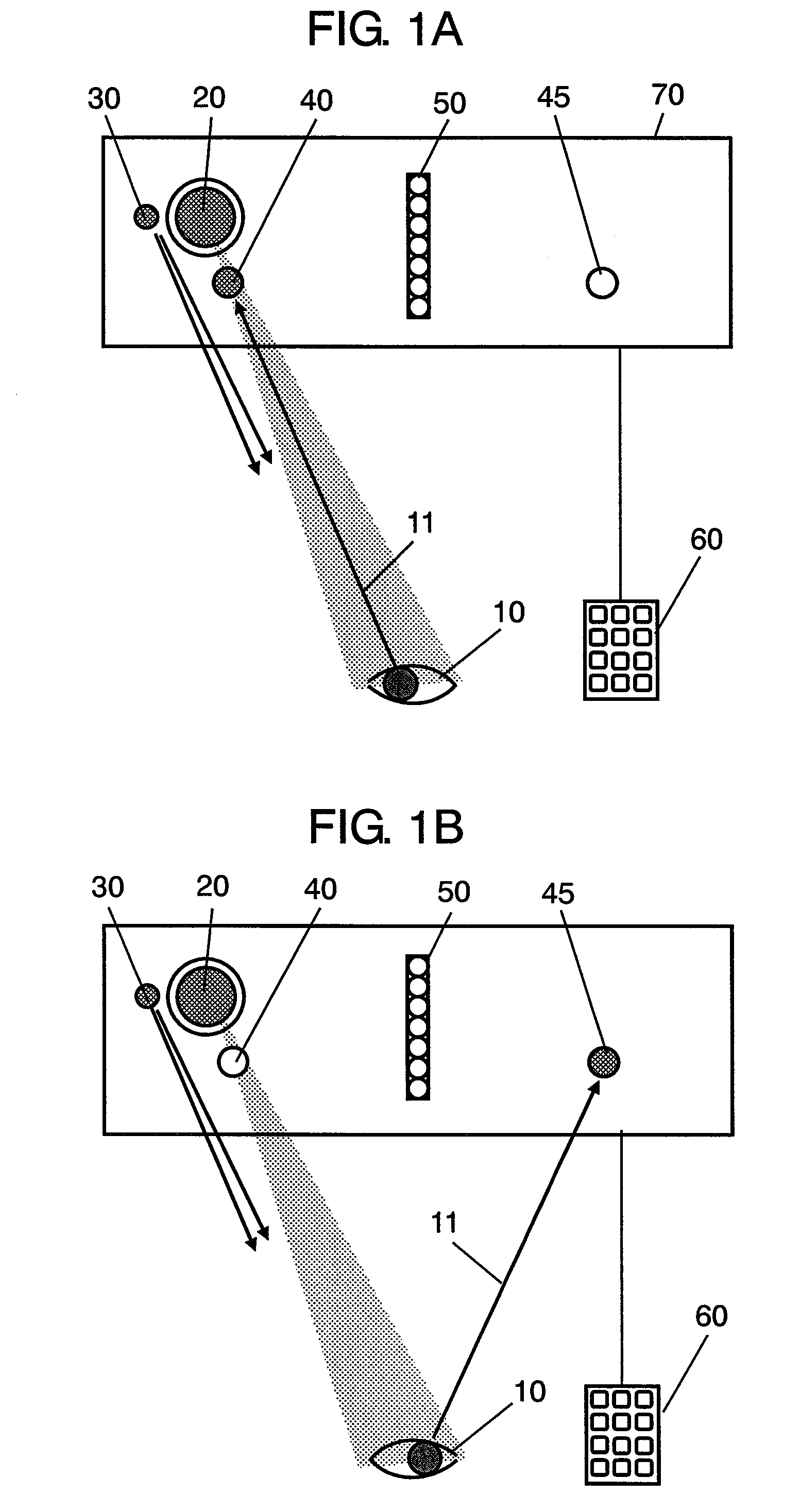
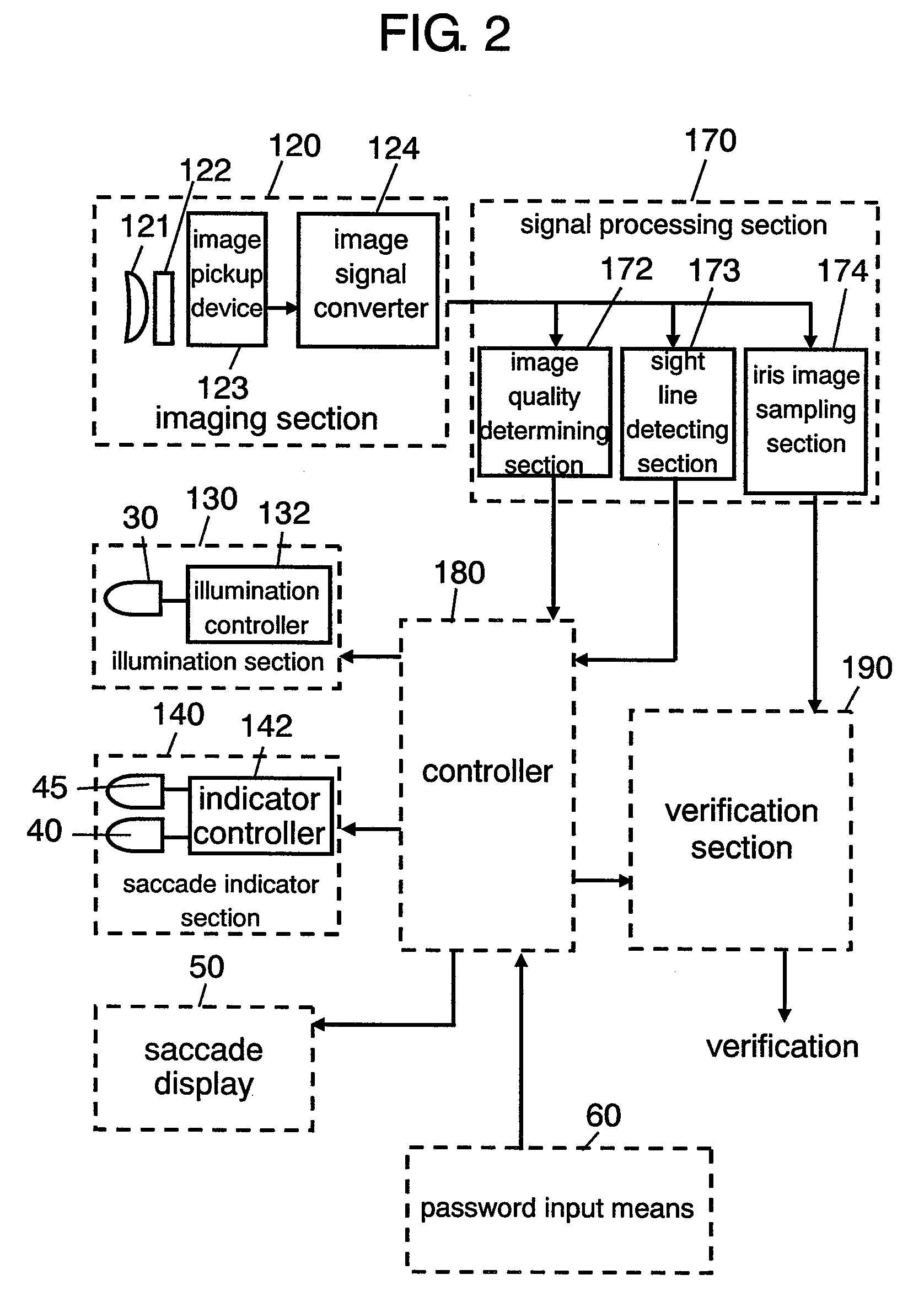
InactiveUS20070263908A1Avoid verification processMovement can be detectedPerson identificationAcquiring/recognising eyesSaccadeEffect light
An iris verification device includes: an imaging section for taking an image of an eye of a user; a first saccade indicator for pointing a sight line of the user; a second saccade indicator, which is placed apart from the first saccade indicator, for pointing the sight line of the user; a sight line detecting section for detecting the sight line of the user from the image taken at the imaging section; an iris image sampling section for sampling an iris image from the image taken at the imaging section; a verification section for performing an iris verification act based on the iris image sampled at the iris image sampling section. Variation of the sight line of the user accompanied by the lighting-up of the first saccade indicator or the second saccade indicator is detected as biological reaction by using the sight line detecting section.
Owner:PANASONIC CORP
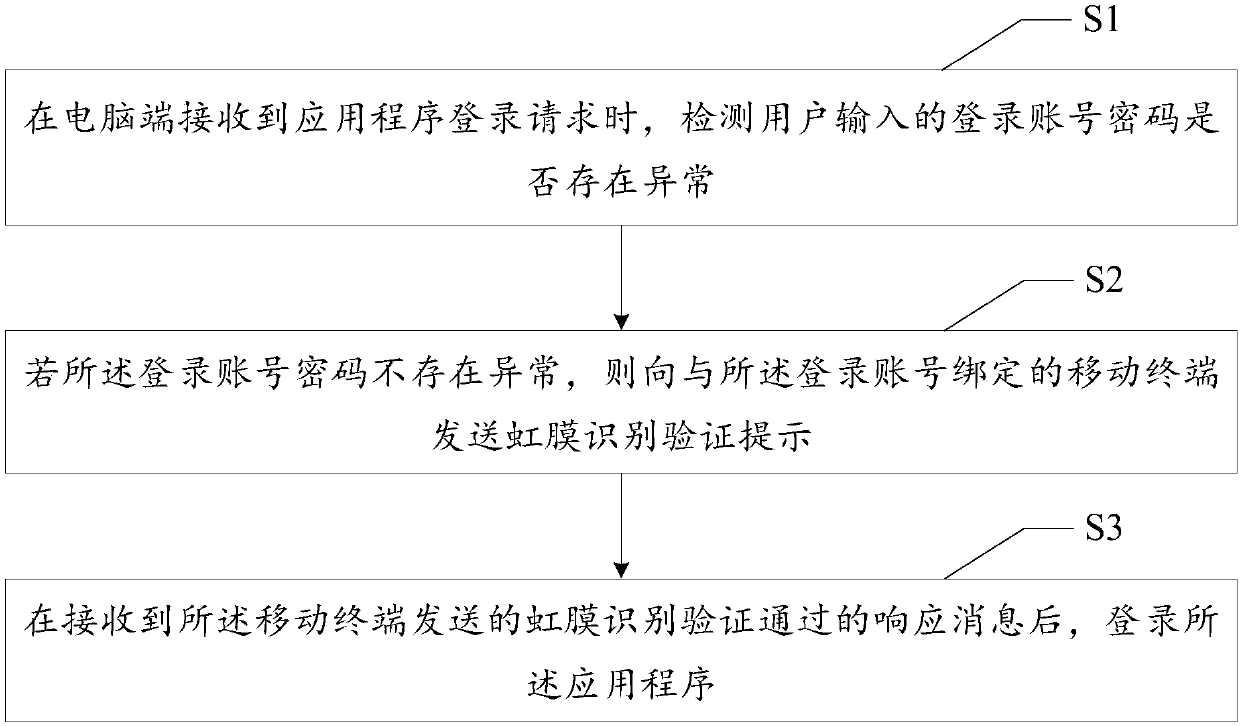
Application program login method, computer side, mobile terminal, system and storage medium
PendingCN109522695AEnsure information securityImprove login securityDigital data authenticationPasswordComputer terminal
The invention discloses an application program login method, a computer end, a mobile terminal, a system and a readable storage medium, and the method comprises the steps: detecting whether a login account password input by a user is abnormal or not when the computer end receives an application program login request; If the login account password is not abnormal, sending an iris recognition verification prompt to a mobile terminal bound with the login account; And after a response message which is sent by the mobile terminal and passes iris recognition verification is received, logging in theapplication program. The identity and login safety of the user are authenticated through double verification of password verification and iris verification, so that the login safety coefficient is improved, and the information safety of the user is ensured.
Owner:NUBIA TECHNOLOGY CO LTD
Intelligent antitheft door having fingerprint and iris identification function and needing verification of mobile phone software
InactiveCN107575137AEnsure safetyImprove securityBurglary protectionNon-mechanical controlsEngineeringElectric control
An intelligent antitheft door having a fingerprint and iris identification function and needing verification of mobile phone software comprises a door plate, an electric control door lock, a door handle, an infrared human body induction device, an emergency power source interface, a biometric fingerprint identification device, a loudspeaker, an intelligent control center, a network and extended data line, a power source line, a high-capacity accumulator, an iris identification device, a camera and a touch screen. According to the intelligent antitheft door having the fingerprint and iris identification function and needing verification of the mobile phone software, the identity of a door opener is determined through three modes of fingerprint verification, iris verification and verification of the mobile phone software, and only if verification of the three modes pass, can the door lock be opened. Compared with an antitheft door with a single unlocking mode on the market, the intelligent antitheft door has the advantages that safety is strengthened; meanwhile, information of the lock opener can be recorded through pictures for subsequent inspection, and behavior of a lawbreaker infront of the intelligent antitheft door can be also recorded through videos and the pictures; and the lawbreaker can be driven away through high-decibel voice, so that the safety is further improved.
Owner:SHANDONG JIANZHU UNIV
Iris recognition-based ticket purchase method and device
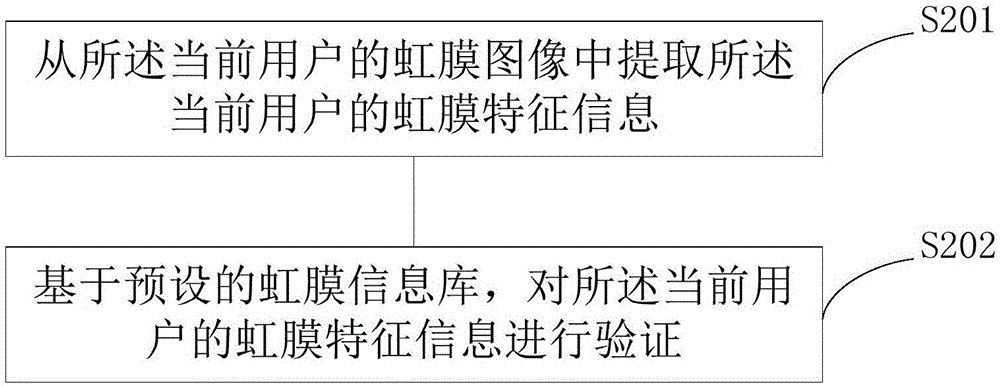
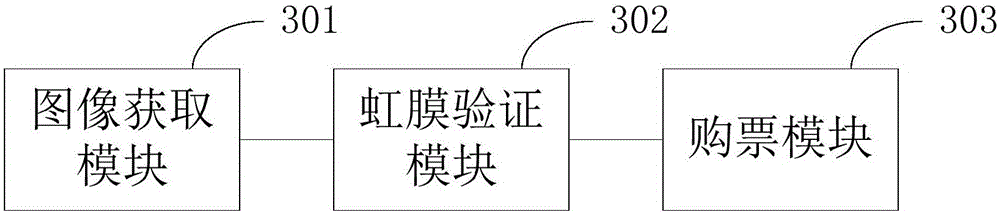
InactiveCN106339698AFix stability issuesFix security issuesCharacter and pattern recognitionMachines for printing and issuing ticketsIris imageIris verification
The invention belongs to the information technical field and relates to an iris recognition-based ticket purchase method and device. The method is applied to an electronic device. The method includes the following steps that: after the ticket purchase request of a current user is obtained, the iris image of the current user is obtained; the iris image of the current user is verified based on a preset iris information library; and after iris verification passes, ticket purchase operation is carried out. The device comprises an image acquisition module, an iris verification module and a ticket purchase module. With the iris recognition-based ticket purchase method and device provided by the embodiments of the invention adopted, the identity of a ticket purchaser is verified through iris recognition before ticket purchase, and the security of ticket purchase can be improved, and illegal ticket purchase can be prevented.
Owner:LETV HLDG BEIJING CO LTD +1
Wearable intelligent visual sense strengthening equipment
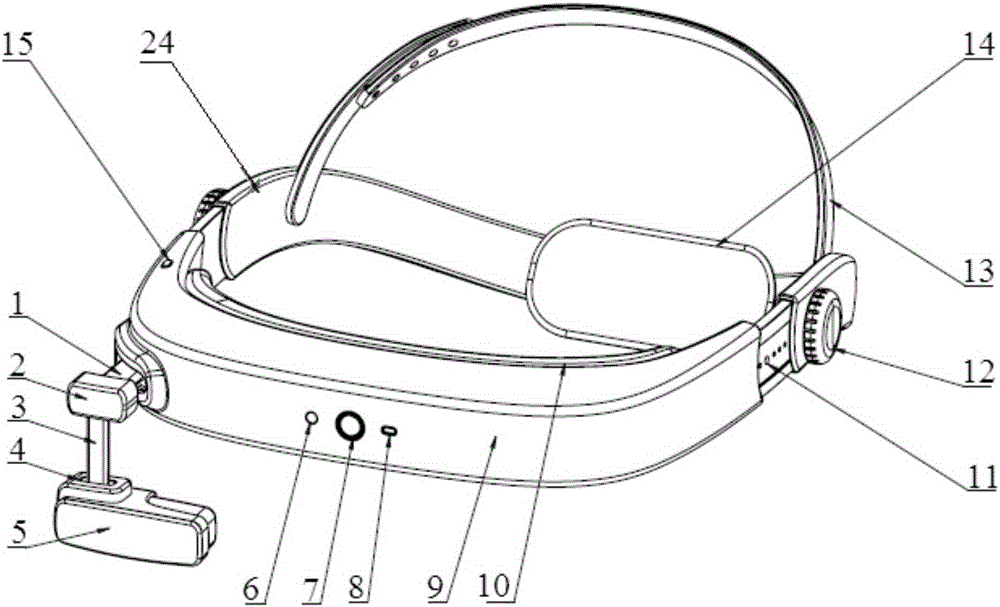
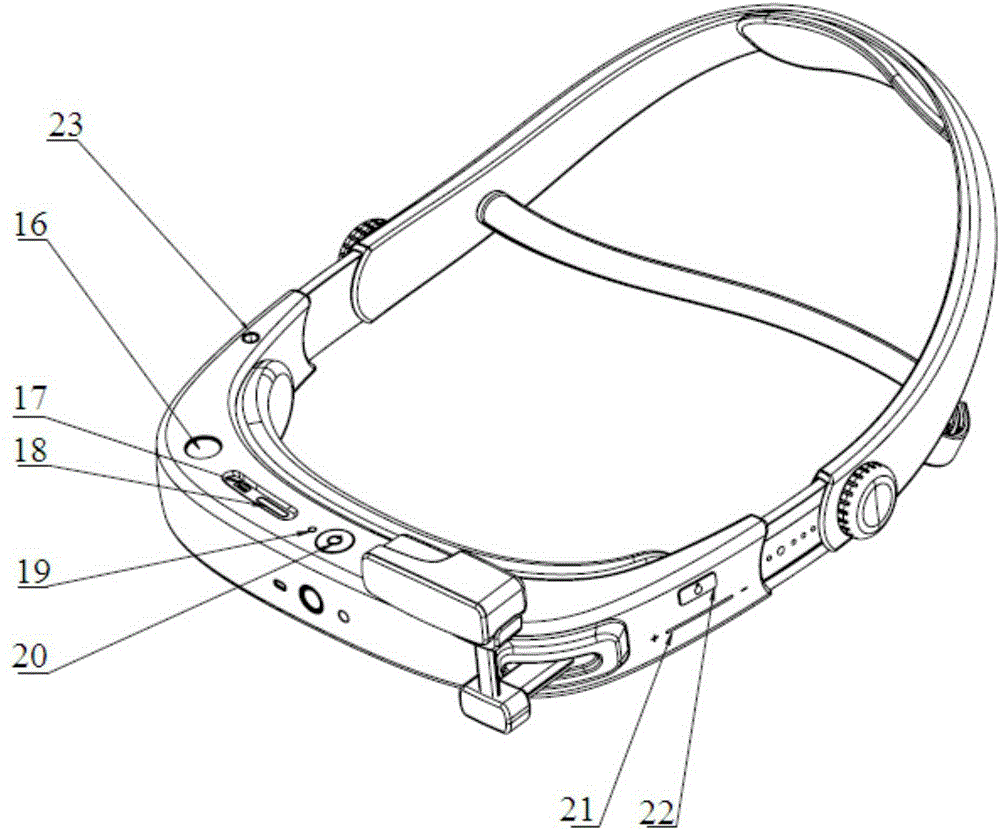
InactiveCN106842566ARealize human-computer interactive experienceEnhance virtual-real interactionInput/output for user-computer interactionCharacter and pattern recognitionVisual perceptionEmbedded system
The invention relates to wearable intelligent visual sense strengthening equipment, comprising a head adornment fixing device, a processor and a myopic display system. The head adornment fixing device comprises an arc-shaped main engine cabin and an arc-shaped rear baffle, and the main engine cabin and the rear baffle are assembled into a circular fixing device capable of being sleeved on the head; the processor is arranged in the main engine cabin and connected with the myopic display system, and the front end of the main engine cabin is provided with a camera connected with the processor; the myopic display system stretches out of one end of the front side of the main engine cabin through a stretchable revolving device, and the position and angle of the myopic display system are adjusted by the stretchable revolving device. Compared with the prior art, the intelligent visual sense strengthening equipment disclosed by the invention is simple in setup, the processor is integrated in the head adornment fixing device, and the device is adjustable in size and comfortable to wear, thereby improving the experience sense of a user. Meanwhile, the intelligent visual sense strengthening equipment disclosed by the invention has strong functions, can realize multiple functions, selectively adopts a fingerprint verification or iris verification manner, and improves safety.
Owner:上海翊视皓瞳信息科技有限公司
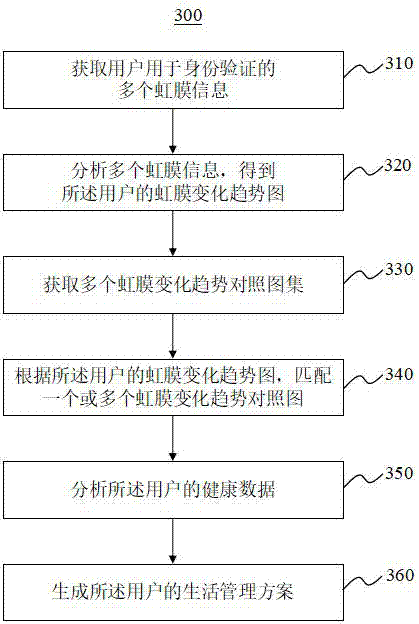
Life management system, medium and method based on iris verification
InactiveCN107358179AImprove living conditionsCharacter and pattern recognitionSpecial data processing applicationsData profilingComputer science
The embodiments of the application disclose a life management system, medium and method based on iris verification, and relates to the technical field of big data analysis. The method herein includes the following steps: acquiring a user's a plurality of iris information for identify verification; analyzing the plurality of iris information, obtaining an iris changing trend chart of the user; acquiring a plurality of iris changing trend comparison diagram atlases; based on the iris changing trend chart, matching one or a plurality of iris changing trend comparison diagrams; analyzing the user's health data; and generating the user's life management plan. According to the application, the life management system, the medium and the method use big data technologies, draw and analyze iris changing trend charts so as to make a life management plan and guarantees better life state.
Owner:SHANGHAI IUV SOFTWARE DEV CO LTD
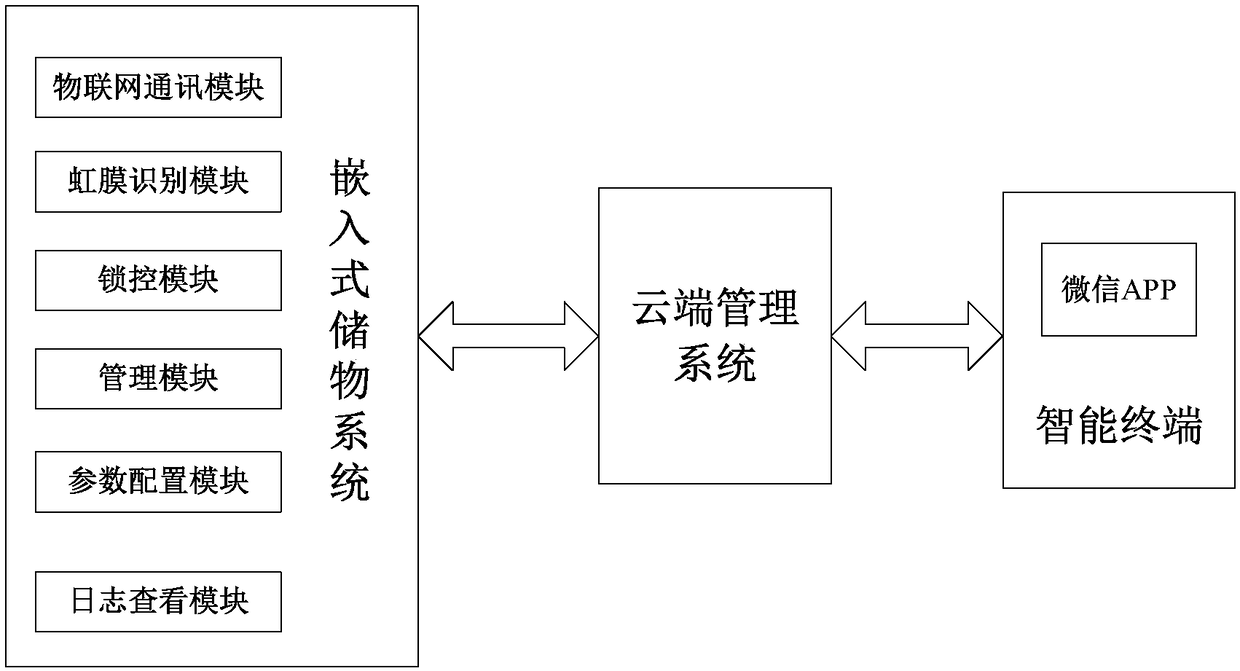
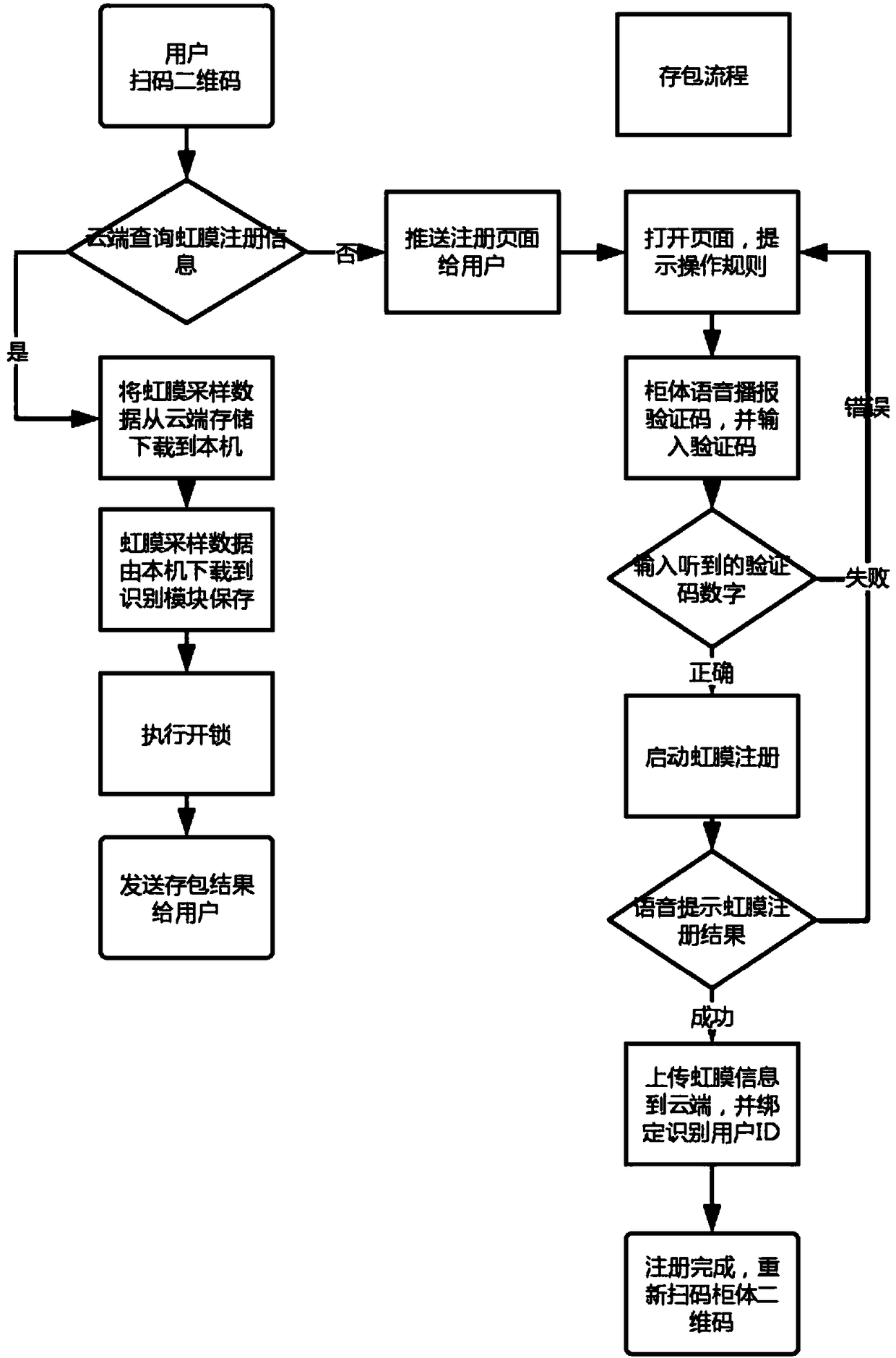
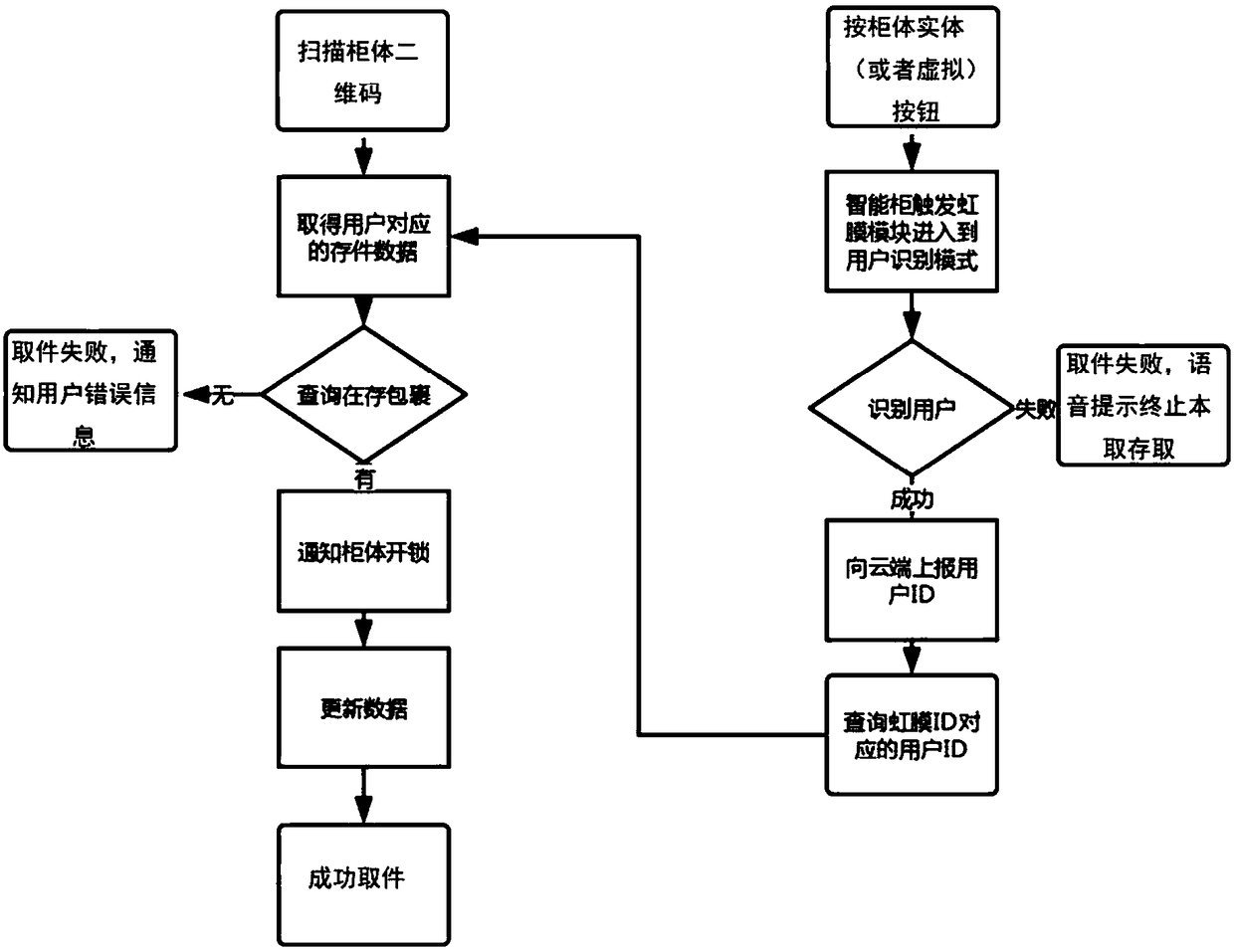
WeChat intelligent cabinet control system based on cloud technology and iris recognition and saving and pickup method
InactiveCN108492478AEasy accessEasy to operateCharacter and pattern recognitionApparatus for meter-controlled dispensingCloud baseData information
The invention discloses a WeChat intelligent cabinet control system based on cloud technology and iris recognition and saving and picking up method. The system comprises an embedded saving system integrated with iris and lock control function, a cloud management system and a WeChat APP. The two-dimensional code on the embedded saving system is scanned by using the WeChat APP, and the information is uploaded to the cloud management system for iris verification, the flow of the saving and picking up is finished. The system mainly relies on internet of things and mobile internet technologies to realize a set of cloud-based intelligent cabinet saving and picking up scheme based on iris recognition, After a user registers the iris information via WeChat on a cabinet, the iris data information of the user is uploaded to the cloud storage platform, all the cabinets under the merchant can use the iris recognition unit on the cabinet to identify the user so as to realize the function of iris saving and picking up.
Owner:广州市孚海软件技术有限公司 +1
Data storage system employing iris encryption
InactiveCN105095796AKeep safeDigital data protectionInternal/peripheral component protectionData segmentDecomposition
The invention discloses a data storage system employing iris encryption. The data storage system comprises a data acquisition unit, a data analysis unit, a data screening server, a data segment classification database, a central processing unit, a shared data storage server, a personalized data storage server, a coded mark storage server and a power management device. The data acquisition unit is used for data acquisition. The data analysis unit is used for analysis of data and decomposition of data into multiple data segments. The data screening server is used for screening data segments. The data segment classification database is used for storage of data classification regulations and automatic renewal of classification regulations. The central processing unit is used for storage of data segments to corresponding data storage servers, sequential encoding of data segments decomposed by the data acquisition unit and storage of marked codes into a marked code storage server. The shared data storage server is used for saving data classified to be shared data segments. The personalized data storage server is used for saving data classified to be personalized data segments. The power management device is used for management of server states. A front end interface of an encrypted data storage server is provided with an iris verification module. Therefore, the purpose of saving data in a real-time mode is fulfilled.
Owner:LIUZHOU SHOUGUANG TECH
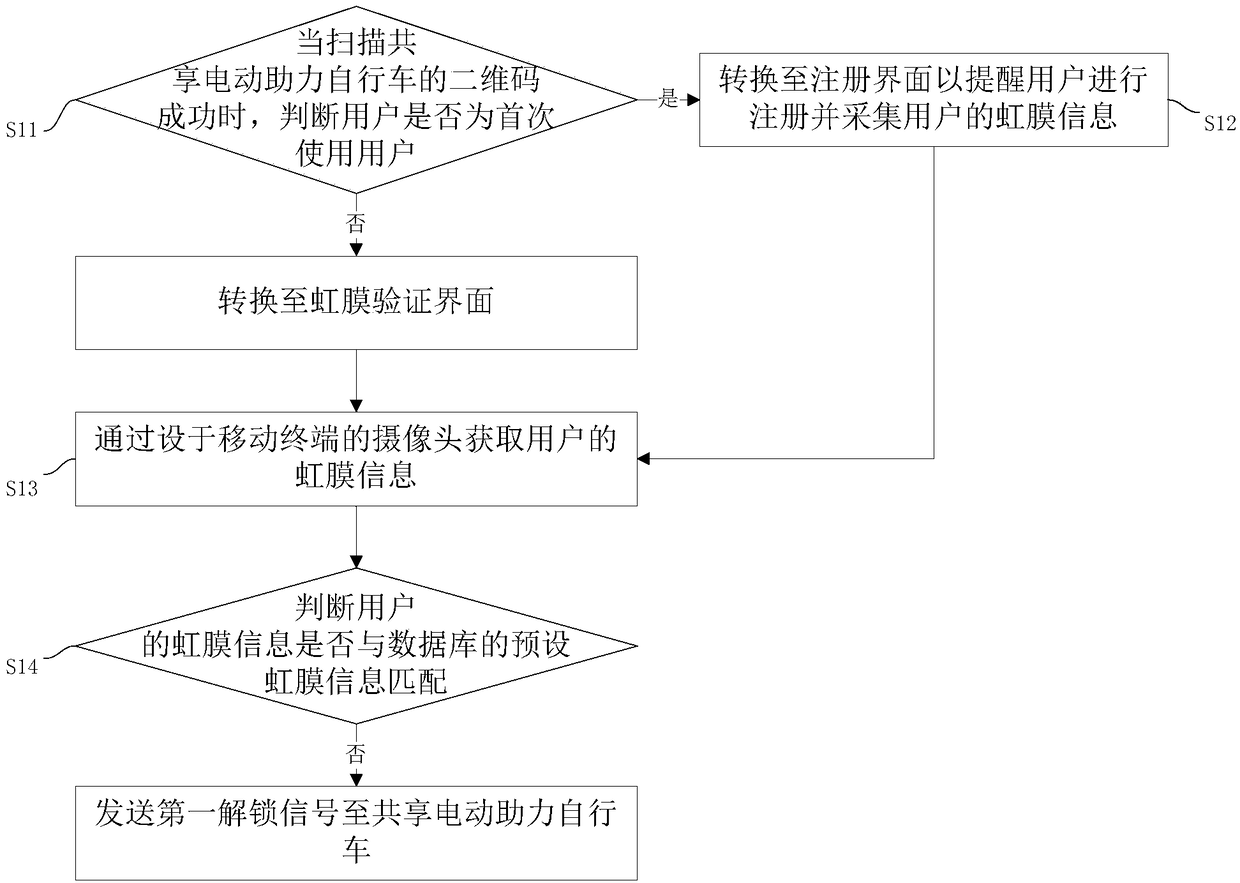
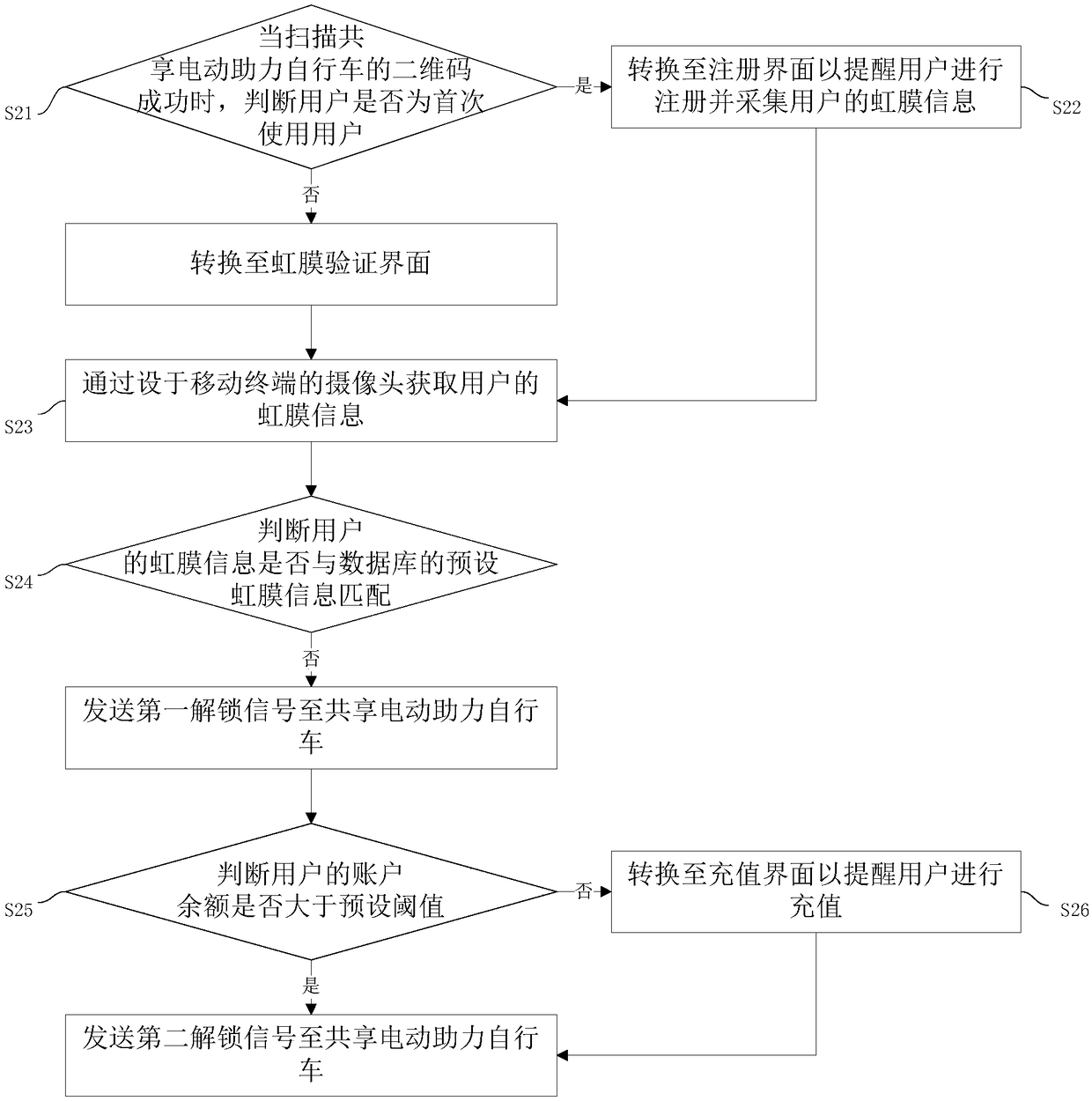
Method and system for unlocking shared electric power-assisted bicycle
InactiveCN108447151AImprove securityAvoid security issuesApparatus for meter-controlled dispensingIndividual entry/exit registersElectric power systemPassword
The invention discloses a method and system for unlocking a shared electric power-assisted bicycle to solve the problem of insecurity caused by easy access of existing passwords. The method includes the following steps: judging that whether a user uses the bicycle for the first time or not when the two-dimensional code of the shared electric power-assisted bicycle successfully scanned, and switching to an iris verification interface if not; acquiring the iris information of the user through a camera arranged on a mobile terminal; judging that whether the iris information of the user matches with preset iris information in a database or not, and sending a first unlocking signal to the shared electric power-assisted bicycle if so. The security of the iris verification is greatly better thanthat of password unlocking, so the security problem caused by the password access is avoided.
Owner:ZHEJIANG LITHELI TECH CO LTD
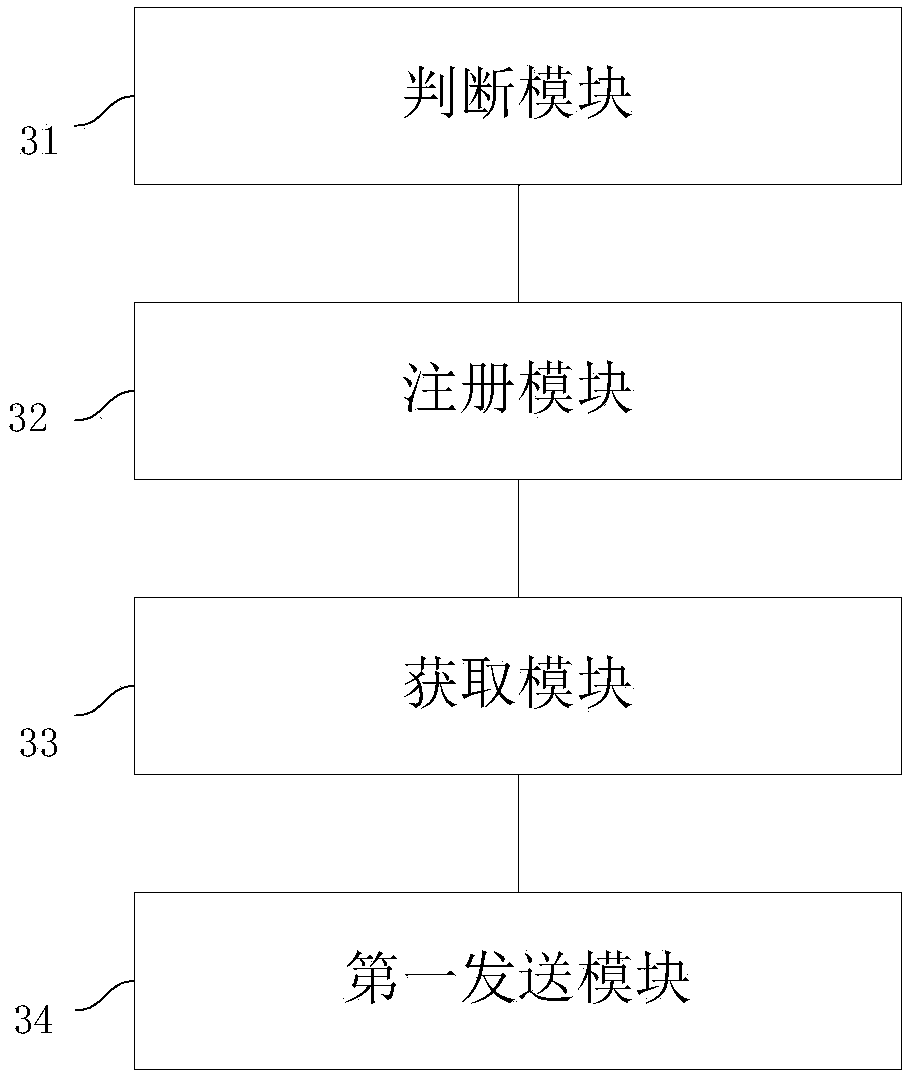
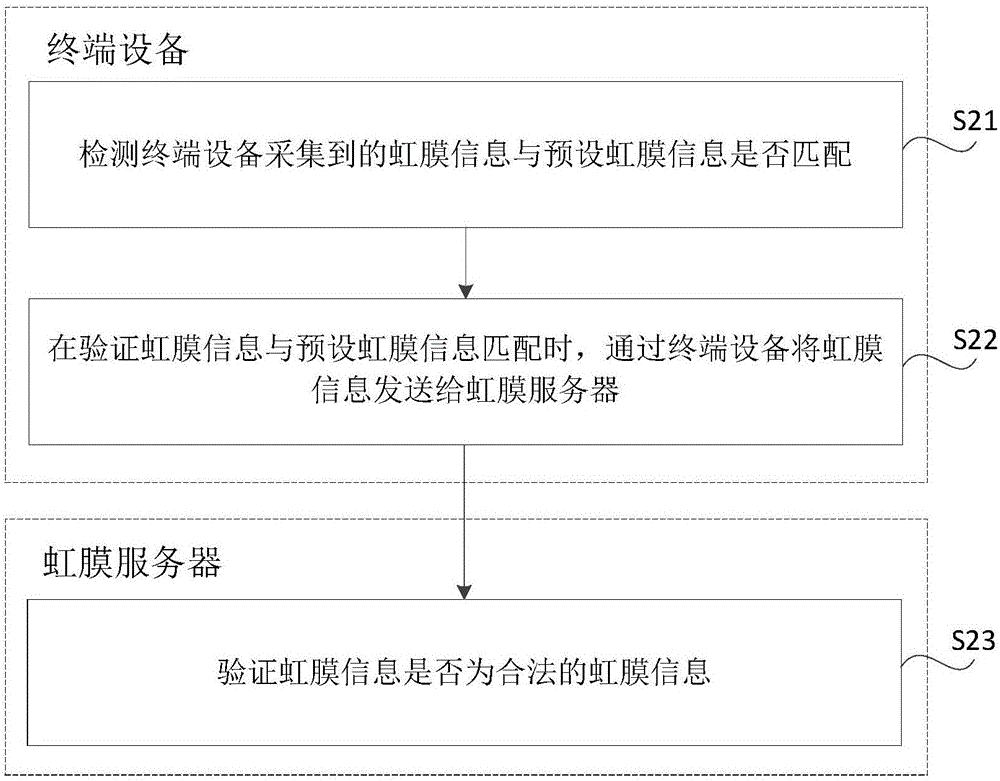
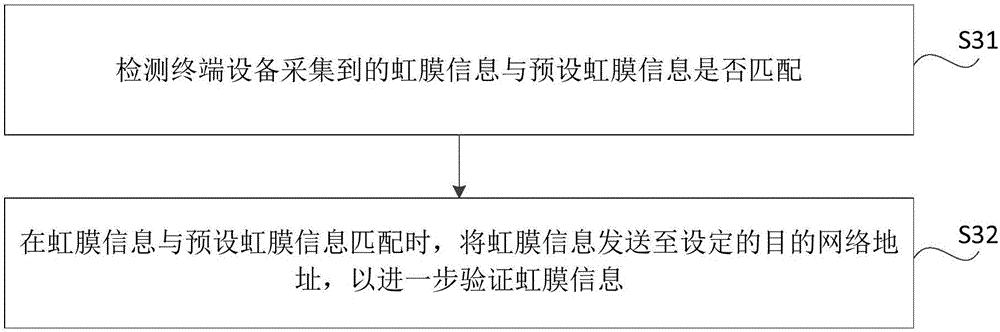
Security verification method, apparatus, terminal and server
ActiveCN106797386AAuthentication method is safeThe verification method is reliableTransmissionTerminal equipmentComputer terminal
The invention discloses a security verification method, apparatus, terminal and server to improve iris verification security. The method comprises the steps of detecting if an iris information collected by the terminal matches a preset iris information at the terminal; and if the iris information matches the preset iris information, sending the iris information to a preset website address to further verify the iris information.
Owner:深圳达闼科技机器人有限公司
Iris verification method
ActiveUS20180173977A1Accurately determineAcquiring/recognising eyesDigital data authenticationIris imageIris verification
An iris verification method is provided. According to the iris verification method, it is possible to determine whether the iris to be authenticated is a real human iris during an iris authentication process. Also, according to the iris verification method, it is possible to determine, with precision, whether iris images to be authenticated are real human iris images.
Owner:3E CO LTD
Information storage method adopting iris authentication
InactiveCN105069338AKeep safeDigital data protectionDigital data authenticationData segmentData decomposition
The invention discloses an information storage method adopting iris authentication. A data collecting unit is used for collecting data; a data analyzing unit is used for analyzing data and decomposing the data into a plurality of data segments; a data screening sever is used for screening the data segments; a data segment classification database is used for storing a data classification rule and automatically updating the classification rule; a central processor is used for storing the data segments to corresponding data storage servers; the central processor is used for performing sequential marking to the data segments decomposed by the data analyzing unit and storing the marker to a marker storage server; a sharing data storage server is used for storing the data which is classified as sharing data segments; an individual data storage server is used for storing the data which is classified as individual data segments; a power management device is used for managing the states of the servers, and an iris verification module is arranged at the front end interface of an enciphered data storage server, and a data integrating server is used for integrating scattered data. The method of the invention achieves the goal of safely storing the data in real time.
Owner:LIUZHOU SHOUGUANG TECH
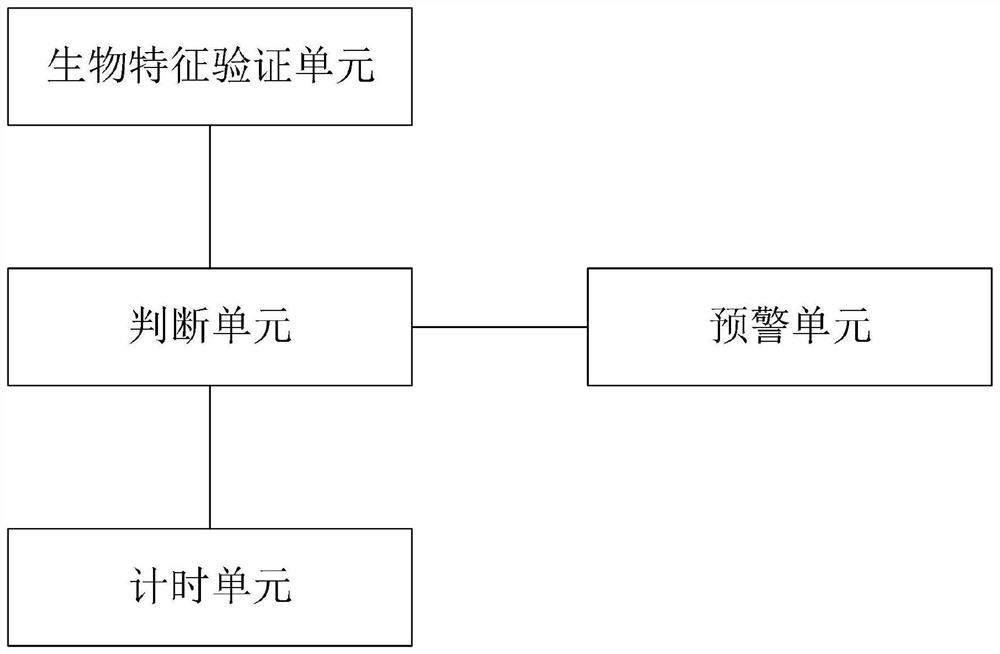
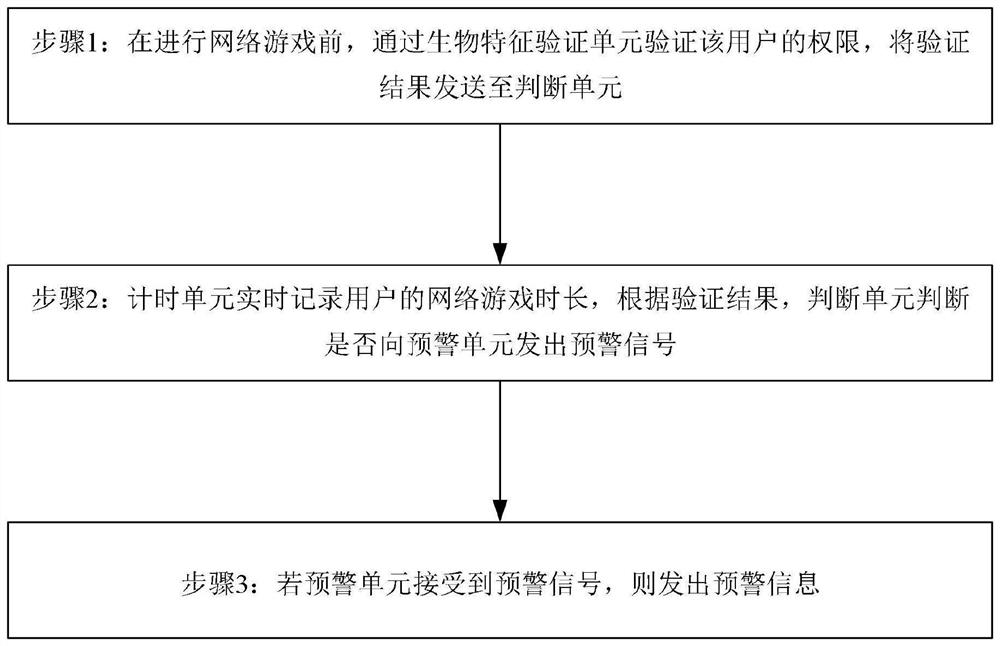
Online game anti-addiction system and method
PendingCN112494950AHigh degree of intelligenceRealize anti-addictionAcquiring/recognising eyesDigital data authenticationSimulationOperations research
The invention discloses an online game anti-addiction system and method, and relates to the technical field of online games. The system comprises a biological characteristic verification unit, a timing unit, a judgment unit and an early warning unit, the biological characteristic verification unit comprises an iris verification unit, a sound verification unit and a fingerprint verification unit; the iris verification unit, the sound verification unit and the fingerprint verification unit are in signal connection with the judgment unit; the timing unit is in signal connection with the judgmentunit; the early warning unit is in signal connection with the judgment unit; and the judgment unit judges whether to trigger the early warning unit to perform anti-addiction early warning or not in real time according to the verification result of the biological characteristic unit and the timing information of the timing unit. The system has the advantages of being high in intelligent degree andaccurate in addiction prevention.
Owner:上海海姆网络科技有限公司
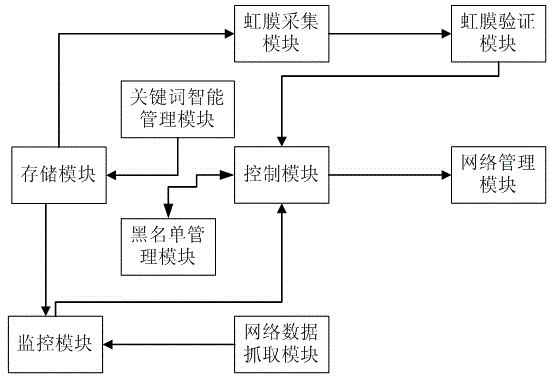
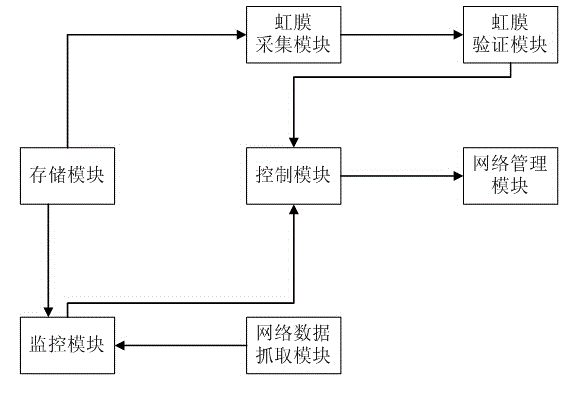
Internet data management system based on iris verification
InactiveCN104462917ATo achieve the purpose of gradingControlling access to the networkDigital data authenticationTransmissionComputer modulePhysical address
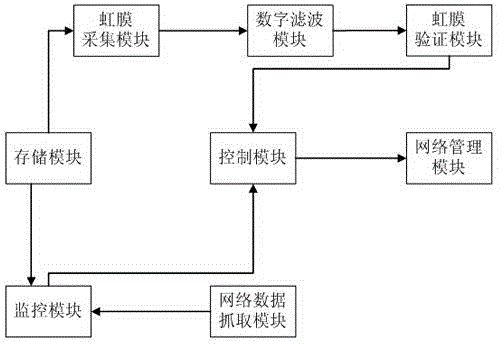
The invention discloses an Internet data management system based on iris verification. The Internet data management system comprises a network data capturing module, a storage module, a monitoring module, a network management module, an iris collecting module, an iris verifying module, a control module, an intelligent keyword management module and a blacklist management module. The network data capturing module is in charge of capturing the content of the internal storage of a computer. The storage module is used for storing set keywords and storing user information. The monitoring module receives the data transmitted by the network data capturing module. The network management module is used for controlling the authority of network access according to an instruction of the control module. The iris collecting module is used for collecting the iris information of a user through a camera. The iris verifying module is used for calling the user information in the storage module to be compared with the iris information collected by the iris collecting module, and a comparison result is transmitted to the control module. The control module is used for managing whether the network data capturing module is started or not according to the comparison result of the iris verifying module. The intelligent keyword managing module is used for updating the keywords in the storage module. The blacklist management module is used for storing the physical addresses of websites which are repeatedly shielded. The Internet data management system based on iris verification has the advantage of being capable of classifying the network data.
Owner:柳州市网中网络策划中心(普通合伙)
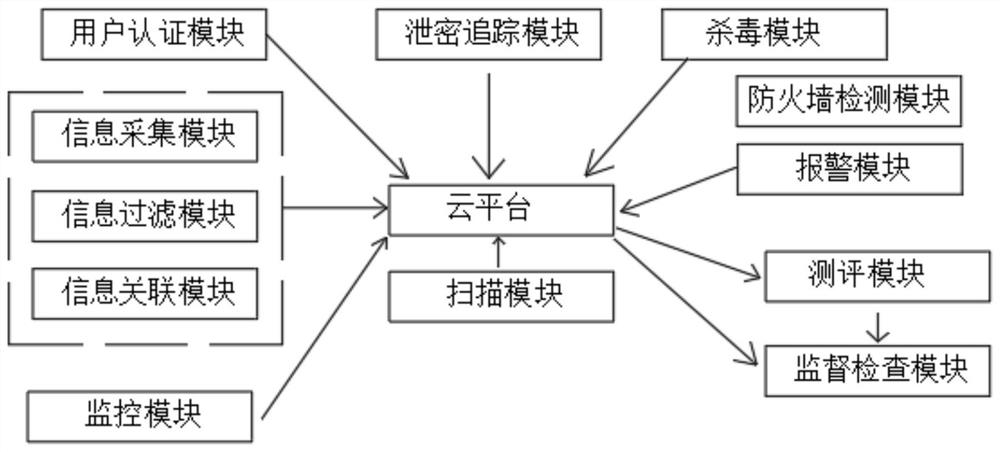
Network security management system
InactiveCN111756710APrevent leakageImprove data securityTransmissionData streamSafety management systems
The invention discloses a network security management system, which comprises a cloud platform, a user authentication module, an information acquisition module, a leakage tracking module, a monitoringmodule and a firewall detection module, and is characterized in that the cloud platform is used for maintaining the operation of the whole system; the user authentication module is used for confirming the identity of a user; and the information acquisition module is used for receiving a network data flow and uploading the acquired data to the cloud platform. The network security management systemhas the beneficial effects that the system facilitates the improvement of data safety, outgoing safety and offline safety through the designed leakage tracking module, and prevents the leakage of confidential data; one or at least two of password verification, fingerprint verification and iris verification are adopted, so that the identity of the user is favorably confirmed, the responsibility tothe network behavior of the user is realized, and the tracing to the source is facilitated; and through the designed alarm module, violation operation is alarmed, the security of confidential data isfurther improved, and leakage of the confidential data is avoided.
Owner:银鹏科技有限公司
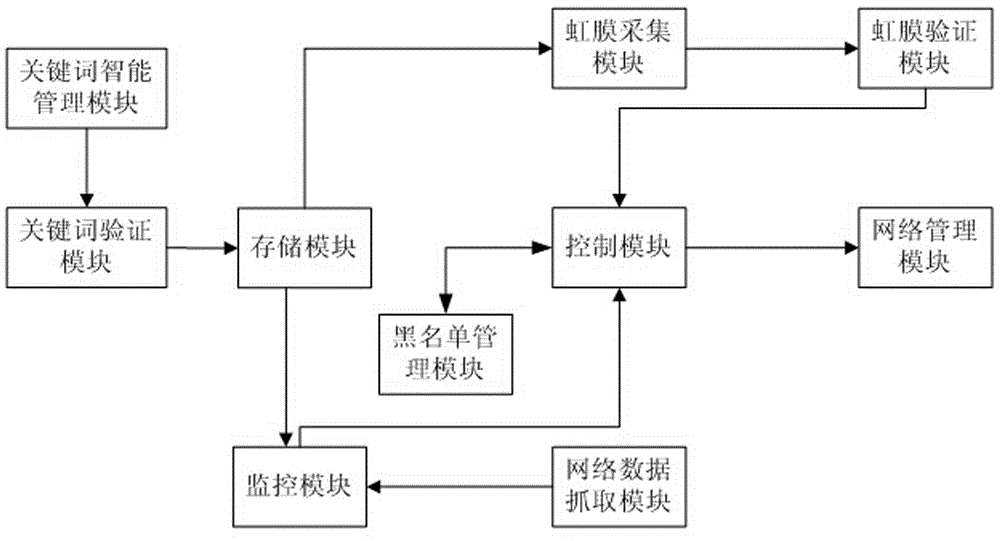
Internet data management system based on iris verification
InactiveCN104408346ATo achieve the purpose of gradingControlling access to the networkDigital data authenticationSpecial data processing applicationsThe InternetNetwork management
The invention discloses an Internet data management system based on iris verification. The Internet data management system comprises a network data acquiring module used for acquiring a computer memory, a storage module used for saving set keywords and user information, a monitoring module used for receiving data transmitted by the network data acquiring module, a network management module used for controlling network access permission according to a command of a control module, an iris acquisition module used for acquiring iris information of a user by using a camera, an iris verification module used for comparing the user information in the storage module and the iris information acquired by the iris acquisition module, a control module used for controlling whether to open the network data acquiring module based on the comparison result of the iris verification module, a keyword intelligent management module used for searching the keywords, a keyword verification module used for verifying the keywords, and a blacklist management module used for storing physical websites shielded by many times. The Internet data management system has the advantages that the network data can be graded.
Owner:柳州市网中网络策划中心(普通合伙)
Multi-modal biological feature fusion identity recognition method
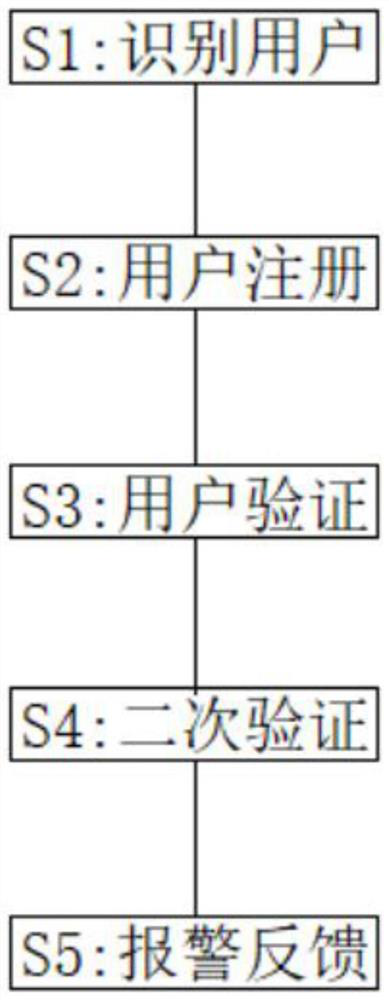
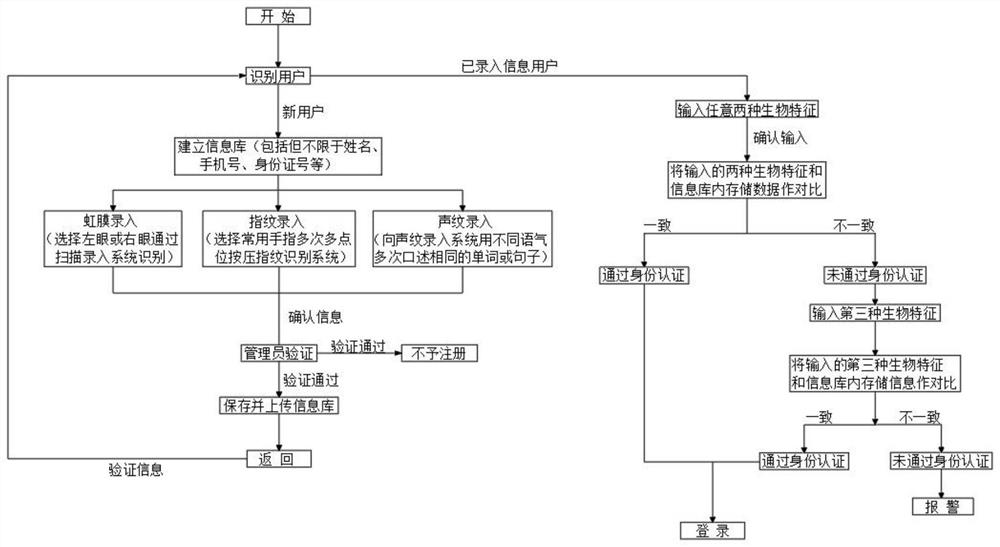
PendingCN114511933AReduce the risk of being stolenGuaranteed accuracyDigital data authenticationMultiple biometrics usePattern recognitionUser verification
The invention relates to the technical field of identity recognition methods, and discloses a multi-modal biological feature fusion identity recognition method. The multi-modal biological feature fusion identity recognition method comprises the following steps: S1, recognizing a user; s2, user registration; s3, user verification; s4, carrying out secondary verification; s5, alarm feedback; according to the invention, a dual-biological feature verification mode is adopted, any two of iris verification, fingerprint verification and voiceprint verification are selected, after identity information is input, any two verification modes of iris verification, fingerprint verification and voiceprint verification are verified, so that the risk of being stolen by people can be reduced, and when verification fails, secondary verification can be carried out, and a third verification mode is used for verification, so that the verification efficiency is improved. A user and an administrator at the receiving end judge the identity information of a user recognized at the input end, if the user is an untrusted user, positioning is started remotely, the control right of the input end is captured remotely, then the identity information is sorted, and an alarm is given.
Owner:深圳市优品智慧科技有限公司
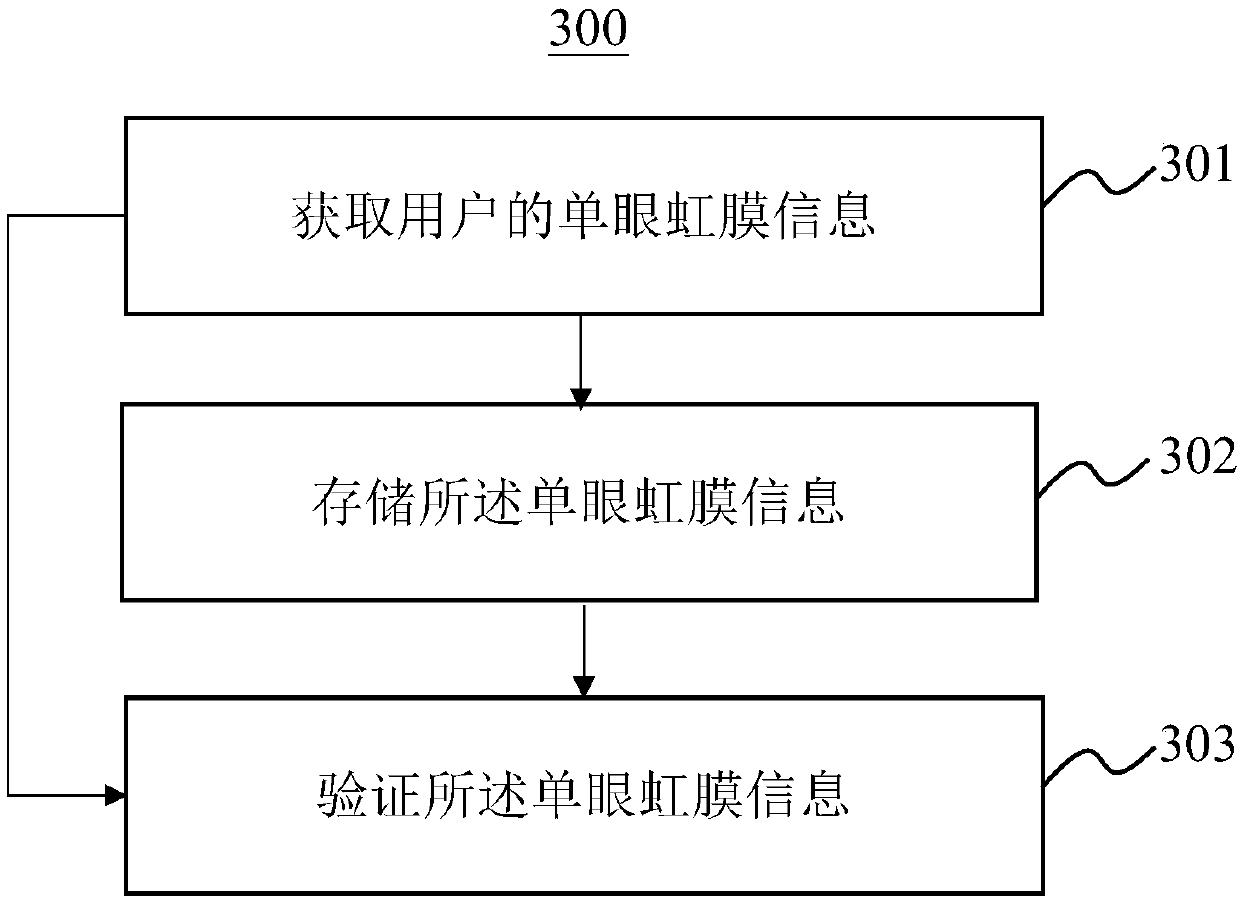
Monocular iris verification method and system
InactiveCN107704843AImprove convenienceImprove experienceCharacter and pattern recognitionValidation methodsSoftware engineering
The embodiment of the invention discloses a monocular iris verification method and system and relates to the field of intelligent terminal technology. The method comprises the steps that monocular iris information of a user is acquired; the monocular iris information is stored; and the monocular iris information is verified. Through the monocular iris verification method and system, the monoculariris information of the user is acquired and stored, then the monocular iris information of the user is verified, therefore, the convenience of using an intelligent terminal by the user is improved, and user experience is improved.
Owner:SHANGHAI IUV SOFTWARE DEV CO LTD
Multi-verification combined type intelligent door lock system
InactiveCN107945338AImprove securityImprove reliabilityIndividual entry/exit registersAlarm locksComputer architecturePassword
The invention provides a multi-verification combined type intelligent door lock system. The system is characterized in that password verification, two-dimensional code verification and iris verification are provided and can effectively improve the safety and the reliability of the intelligent lock. A verification code encrypting and decrypting process for creating a two-dimensional code is added in the two-dimensional code verification process, so that the circumstance that other two-dimensional encoders create the two-dimensional codes can be effectively avoided, and the probability of unlocking by thefts can be reduced, and as a result, the system safety and reliability can be greatly improved; and meanwhile, a verification code can be randomly sent through a lock terminal, and a clientterminal can create the two-dimensional code based on the verification code; the created two-dimensional code can be subjected to short scanning through the door lock and then translated into codes; whether the two codes are the same is compared; if the two codes are the same, the verification is finished. According to the system, the code is randomly sent through the two-dimensional code verification mode, and one client terminal can create a plurality of two-dimensional codes, so that the problem that one two-dimensional code is verified, resulting in the influence on the safety, can be avoided; and as a result, the verification reliability and validity are improved.
Owner:罗世兰
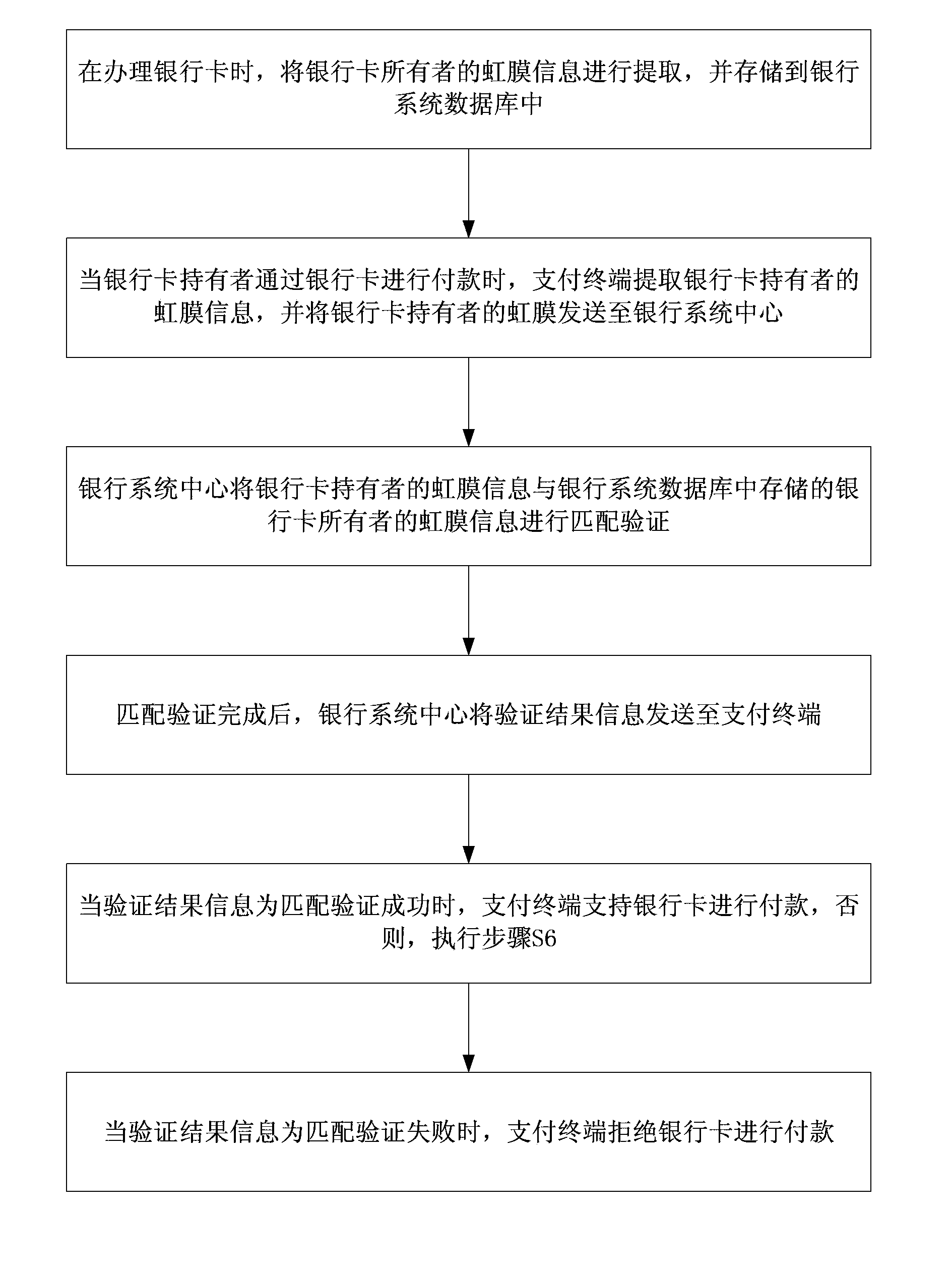
Iris-verification-based verifying method for authenticating of bank card owner
InactiveCN103854362AAvoid crackingNo forgotten passwordCoded identity card or credit card actuationComputer hardwareValidation methods
The invention discloses an iris-verification-based verifying method for the authenticating of a bank card owner. The method includes extracting the iris information of the bank card owner, and storing into a bank system database; when the bank card owner pays by a bank card, allowing a payment terminal to extract the iris information of the bank card owner and send to a bank system center; allowing the bank system center to match and verify the iris information of the bank card owner with iris information of the bank card owner in the bank system database; after matching and verification are completed, allowing the bank system center to send verifying result information to the payment terminal; when the verifying result information shows the matching and verification are succeed, allowing the payment terminal to support the bank card to pay. According to the technical scheme, the method has the advantages that the iris serves as verifying information of bank card payment, the bank card is not easy to compromise, and password forgetting is eliminated.
Owner:DALIAN HONGYU TECH
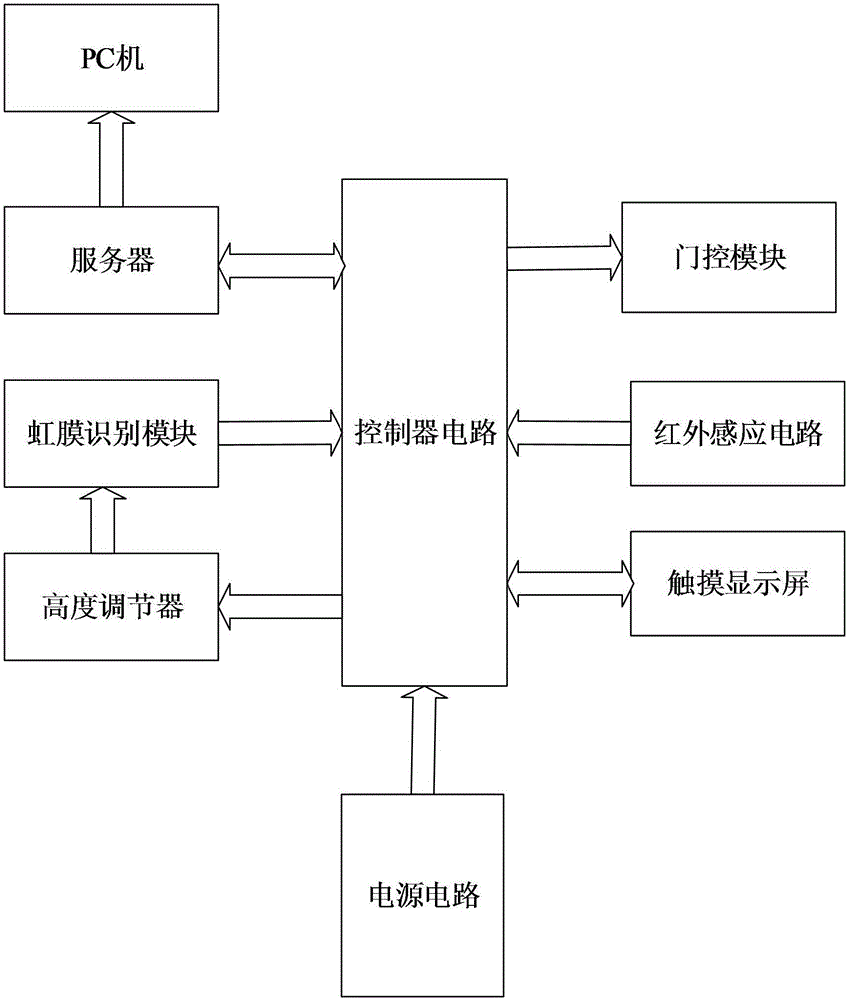
Iris technology-based student apartment access control system
InactiveCN106600764ASolve the problem of enteringIndividual entry/exit registersPower circuitsEmbedded system
The invention provides an iris technology-based student apartment access control system and belongs to the field of access control. The iris technology-based student apartment access control system comprises a controller circuit, a server, an iris identification module, a height regulator, a power supply circuit, a door control module, an infrared induction circuit and a touch display screen, wherein the output ends of the iris identification module and the infrared induction circuit are connected with the input end of the controller circuit; the server is connected with the controller circuit; the input end of the door control module is connected with the output end of the controller circuit; the touch display screen is connected with the controller circuit; the output end of the power supply circuit is connected with the controller circuit to supply power; the infrared induction circuit is used for inducing whether a person exists or not and inducing the height of the person and transmitting the induction data to the controller circuit; the controller circuit adjusts the iris identification module to the most appropriate position to perform iris verification identification; the system further comprises an alarm module which is used for sending out alarm sound to inform a manager to process when an outside person enters without being subjected to iris identification; the problem that outside persons enter a student apartment is solved.
Owner:韦玉姣
Network-based data recovery system adopting iris encryption
InactiveCN104993965ATo achieve the purpose of safe data recoveryData switching networksSecuring communicationData segmentData recovery
Owner:LIUZHOU LIUPIN TECH
Network management system based on iris verification
InactiveCN104410629ATo achieve the purpose of gradingControlling access to the networkTransmissionSpecial data processing applicationsData scrapingNetwork management
The invention discloses a network management system based on iris verification. The network management system comprises a network data capturing module, a memory module, a monitoring module, a network management module, an iris collecting module, an iris verifying module and a control module. The network data capturing module is used for capturing computer memory content and transmitting the captured data to the monitoring module. The memory module is used for saving keywords set and user information. The monitoring module is used for receiving data transmitted from the network data capturing module and comparing the same with the keywords of the memory module. The network management module is used for controlling network access permission according to commands of the control module. Iris information is collected by the collecting module collect through a camera. The iris verifying module is used for taking the user information in the memory module and comparing the user information with the iris information which is collected by the iris collecting module. According to the comparison result of the iris verifying module, whether or not to start the network data capturing module depends on the control module. In this way, the network data are classified.
Owner:柳州市网中网络策划中心(普通合伙)
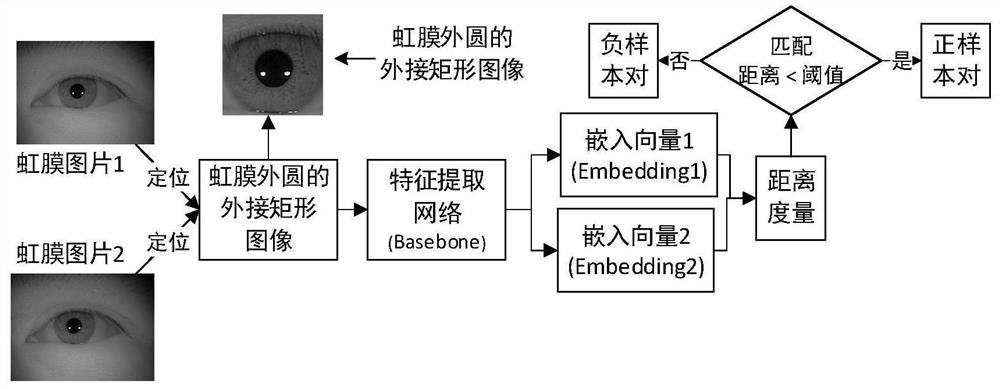
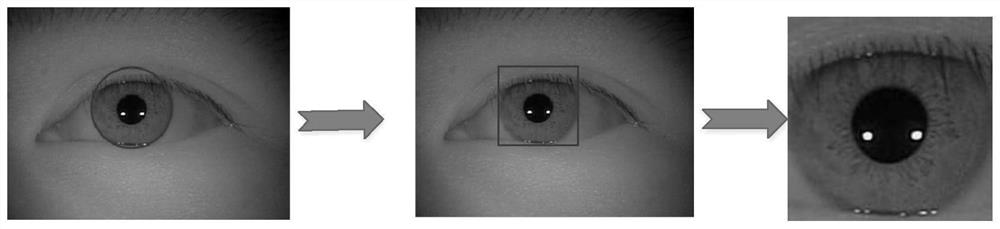
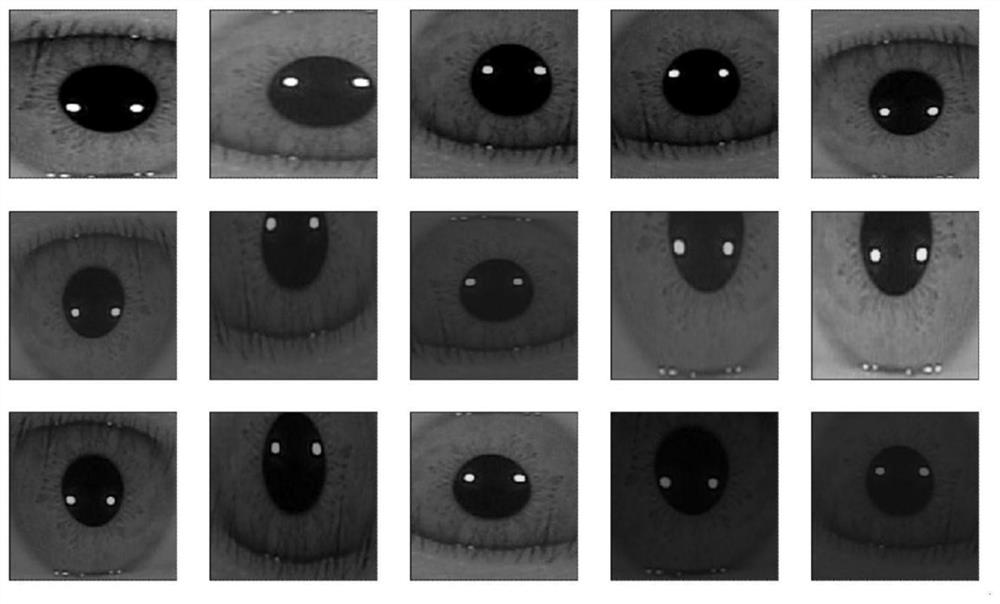
Iris verification method and system based on iris circumscribed rectangular graph
ActiveCN113191260AReduce complexityHigh precisionAcquiring/recognising eyesNeural architecturesFeature extractionIris image
The invention discloses an iris verification method and system based on an iris circumscribed rectangular graph, and belongs to the field of iris verification. The method comprises the following steps: a training stage: training an iris feature extraction network by adopting a training sample set formed by iris circumscribed rectangular diagrams of different individuals; an iris verification stage: acquiring an identity label and an iris image of a user to be verified, positioning the iris image to obtain an iris external rectangular graph, and inputting the iris external rectangular graph into the trained iris feature extraction network to obtain an iris embedding vector to be verified; determining an input iris embedding vector of the user according to the identity identifier of the user to be verified; and comparing the to-be-verified iris embedding vector with the input iris embedding vector, and judging whether the to-be-verified iris embedding vector and the input iris embedding vector belong to the same individual or not. The iris segmentation robustness problem is converted into the neural network feature extraction problem, and the neural network feature extraction robustness problem is solved through neural network training, so that the iris preprocessing complexity is reduced and the iris verification precision is improved by adopting the circumscribed rectangle positioning of the iris excircle.
Owner:HUAZHONG UNIV OF SCI & TECH
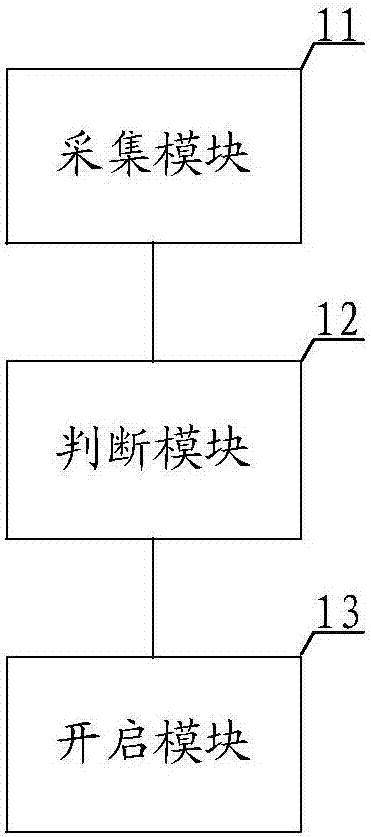
Automobile access control system and method
InactiveCN107154095AImprove securityAnti-theft devicesIndividual entry/exit registersComputer moduleIris verification
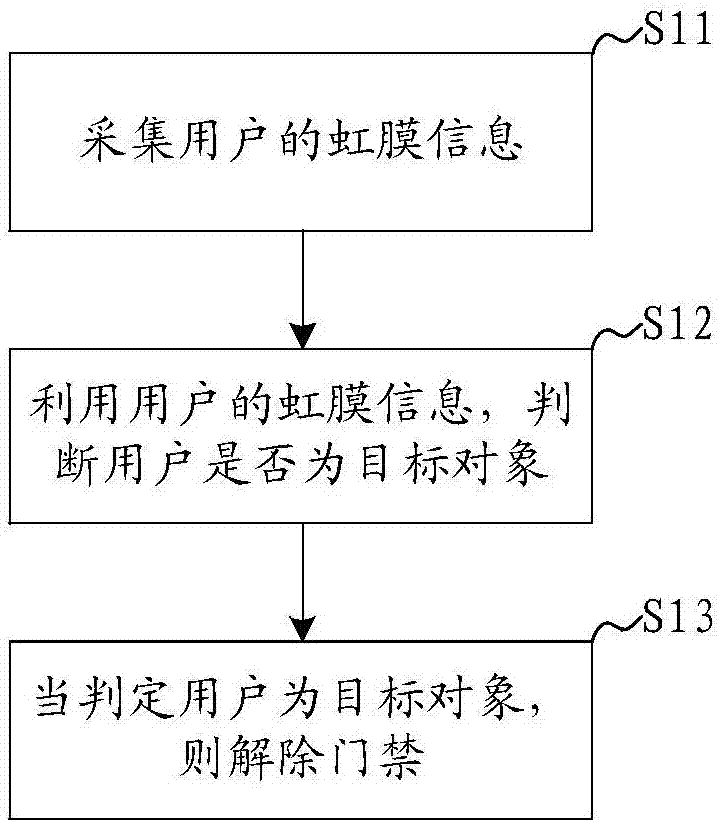
The application discloses an automobile access control system. The system comprises an acquisition module, a judgment module and an opening module, wherein the acquisition module is used for acquiring iris information of a user; the judgment module is used for judging whether the user is a target object or not by utilizing the iris information of the user; the opening module is used for releasing access control when the user is judged as the target object. In summary, according to the application, the iris information of the user is acquired by utilizing the acquisition module, and then whether the user is the target object or not is judged by the judgment module, and an automobile door is opened by the opening module for the user when the user is judged as the target object, the loss is avoided, and iris verification is difficult to crack, thereby improving the security of the automobile access control. In addition, the application also discloses an automobile access control method.
Owner:TRULY OPTO ELECTRONICS
Network management system with filter function based on iris verification
InactiveCN104363124ATo achieve the purpose of gradingControlling access to the networkData switching networksNetwork managementDigital filter
The invention discloses a network management system with a filter function based on iris verification. The network management system comprises a network data grabbing module which is responsible for grabbing content of the memory of a computer and is used for transmitting the grabbed data to a monitoring module, a storage module used for storing set key words and storing user information, the monitoring module used for receiving the data transmitted by the network data grabbing module and comparing the data transmitted by the network data grabbing module with the set key words in the storage module, a network management module used for controlling visiting permission of a network according to a command of a control module, an iris collecting module used for collecting iris information of a user through a camera, an iris verifying module used for calling the user information in the storage module for comparison, and the control module used for managing whether the network data grabbing module is started or not according to a comparison result of the iris verifying module, wherein a digital filter module is connected between the iris collecting module and the iris verifying module. The network management system has the advantage that network data are graded.
Owner:张芳
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com