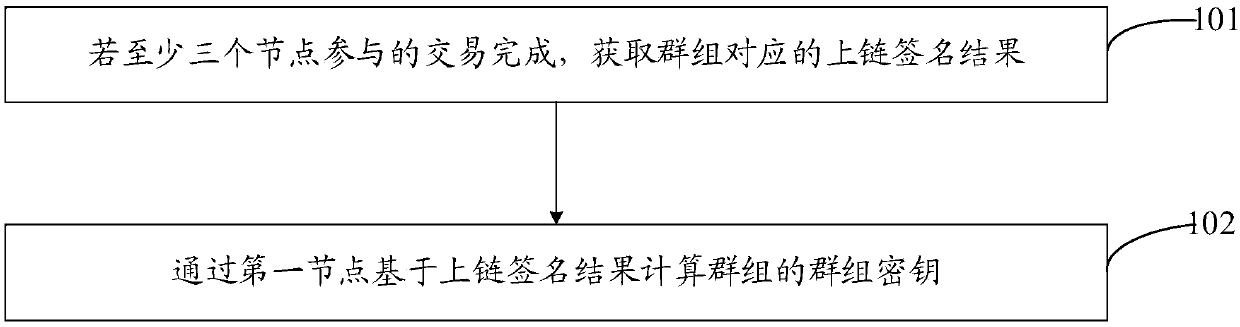
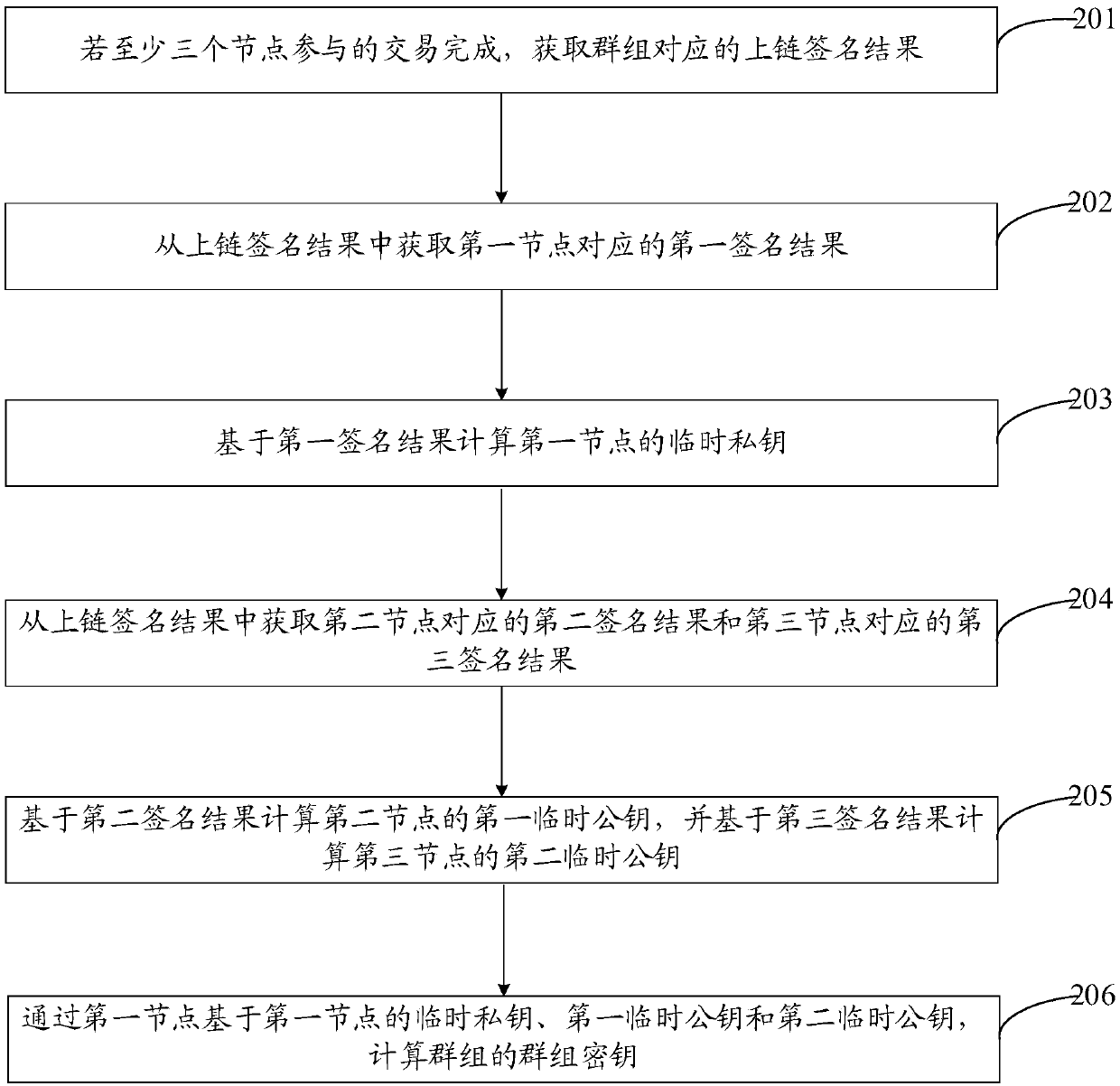
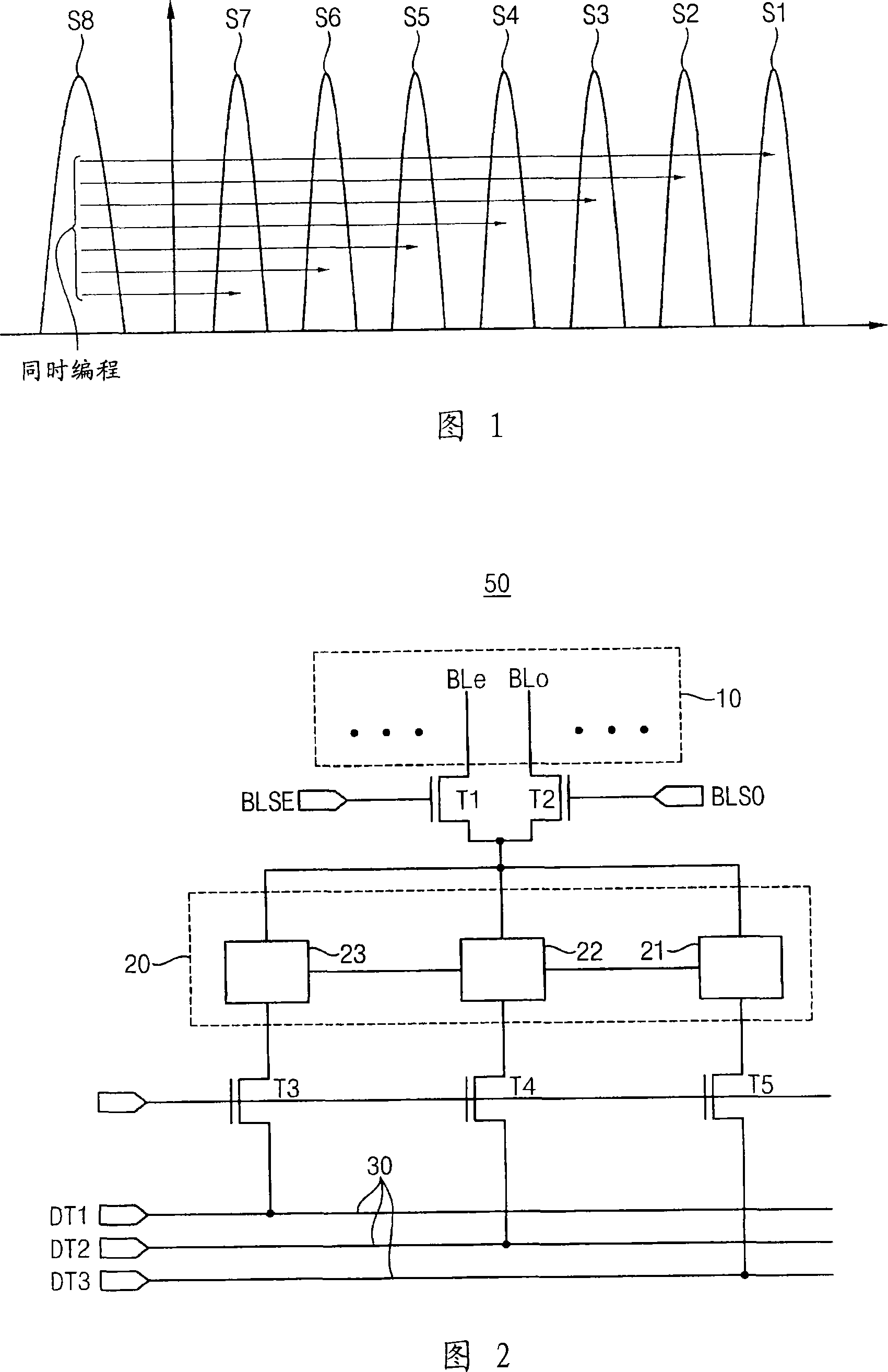
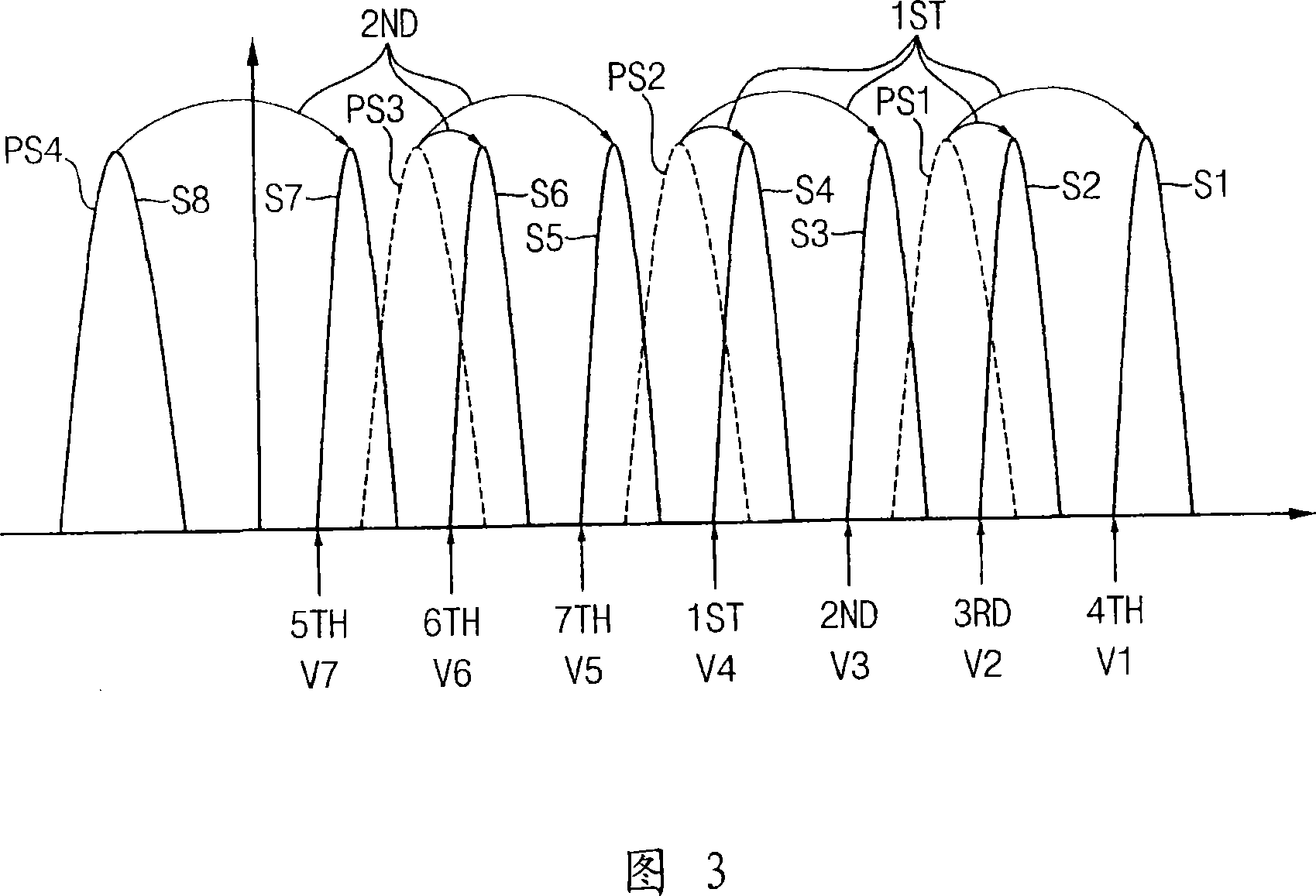
Patents
Literature
87results about How to "Avoid verification process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
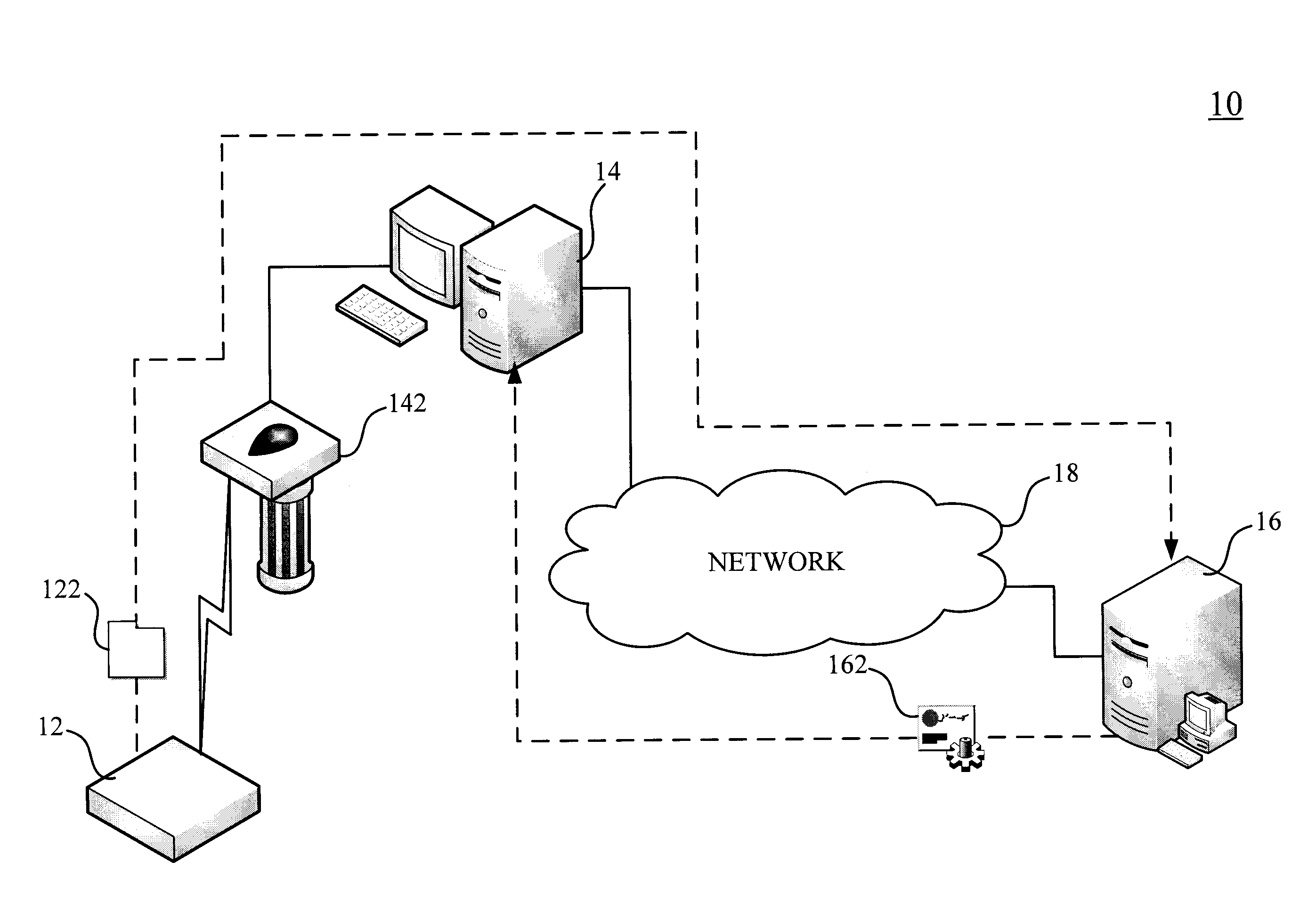
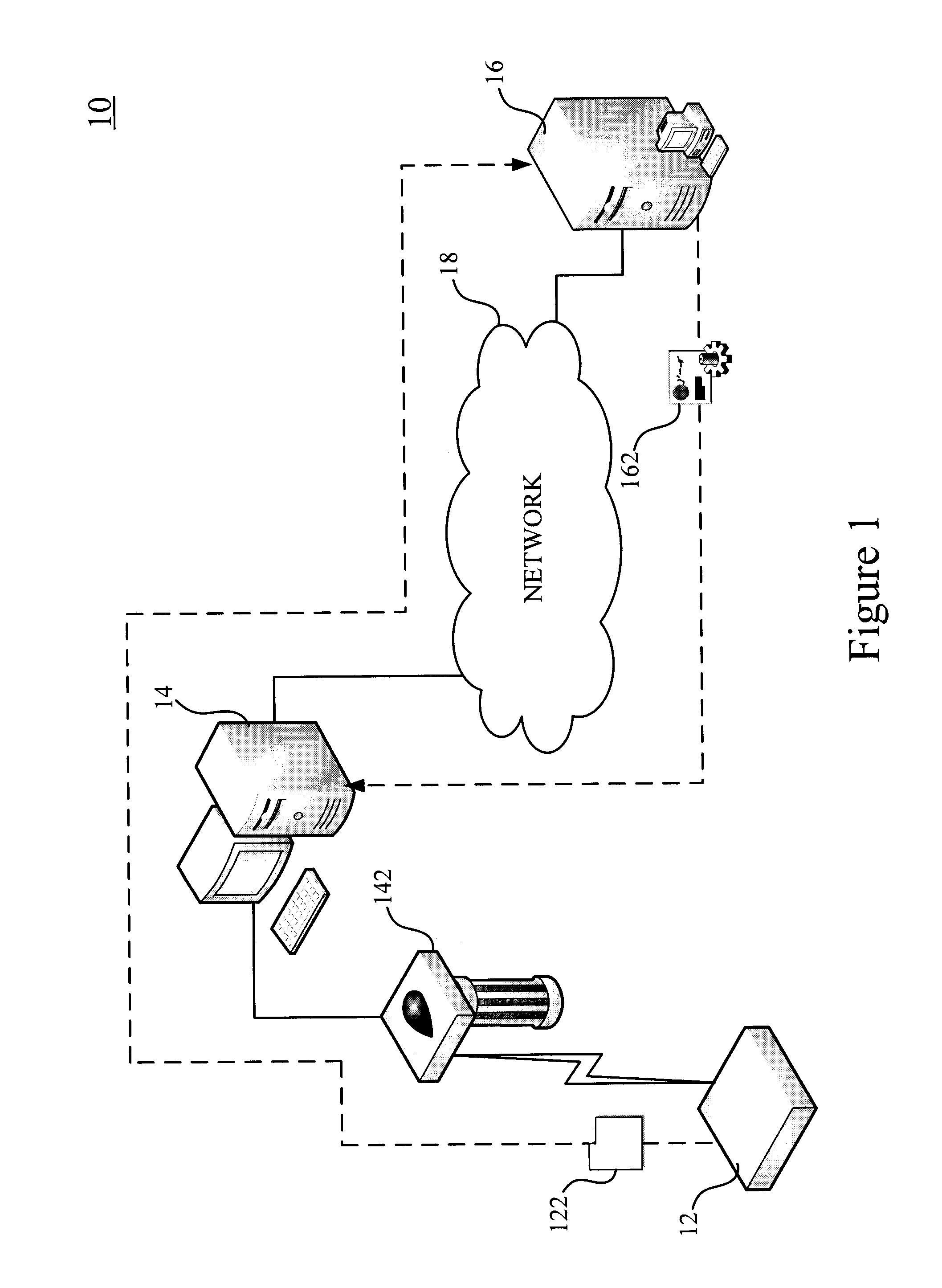
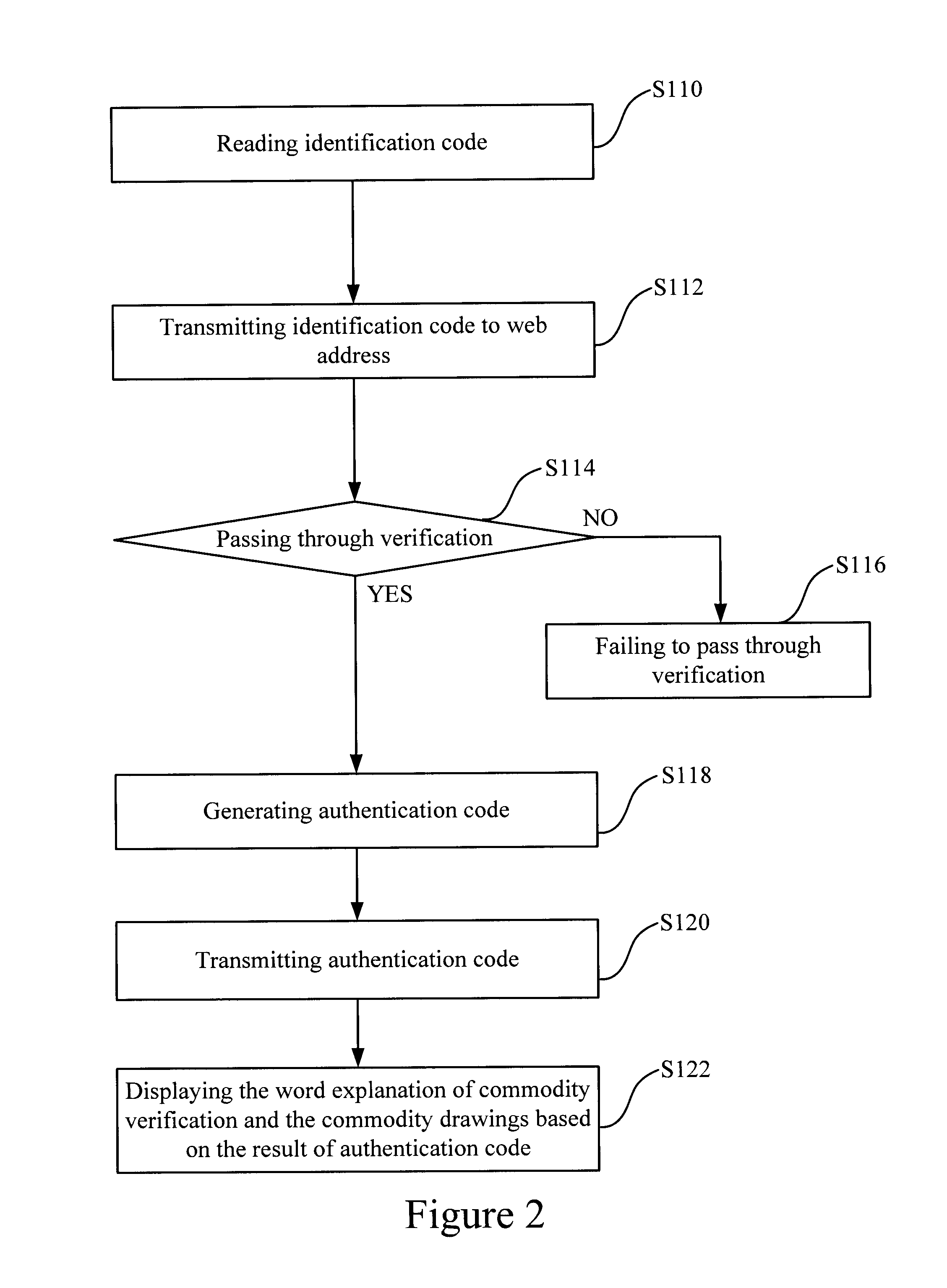
Anti-fake identification system and method capable of automatically connecting to web address
ActiveUS20090140040A1Accuracy in determineFully understandBuying/selling/leasing transactionsVerifying markings correctnessService informationAuthentication
This invention relates to an anti-fake identification system and method capable of automatically connecting to web address, in which an electronic tag of commodity is scanned by a reader device so as to read the identification code into the computer device; the identification code includes a web address of a remote maker to which the computer can automatically connect so as to transmit the identification code to the web address; a verifying device receives and verifies the identification code at the web address, and produce an authentication code according to the identification code after the identification code passes through verification so as to confirm the accuracy of the identification code. The method comprises the following steps of: reading an identification code of commodity; transmitting the identification code to the web address; verifying the identification code and generating an authentication code when the identification code is accurate. When the identification code is verified to be accurate according to the authentication code, the computer can keep consumer informed that the commodity passing through anti-fake verification is genuine, and that the user's manual and service information of the commodity can be understood.
Owner:NAT CHUNG SHAN INST SCI & TECH
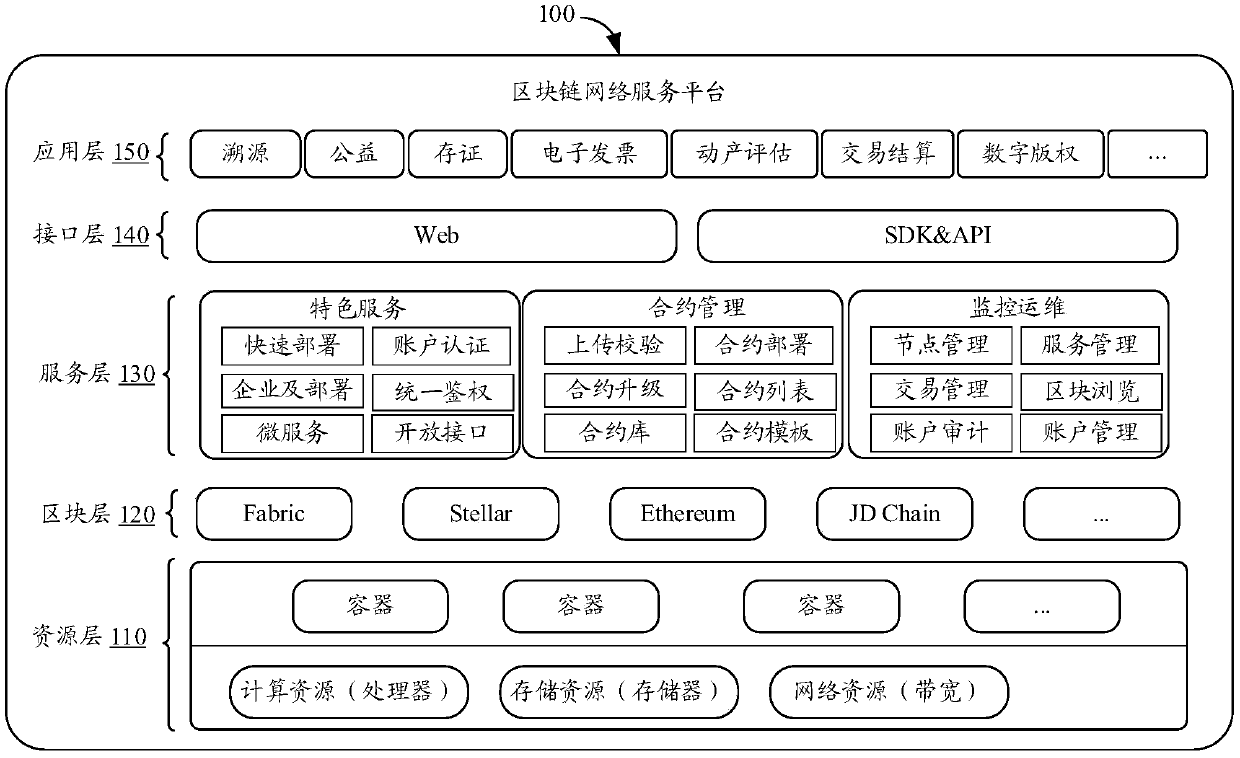
Key generation methods, block chain network service platform and memory medium
PendingCN109617699AAvoid certificate queriesAvoid queryKey distribution for secure communicationUser identity/authority verificationChain networkBlockchain
Owner:BEIJING WODONG TIANJUN INFORMATION TECH CO LTD
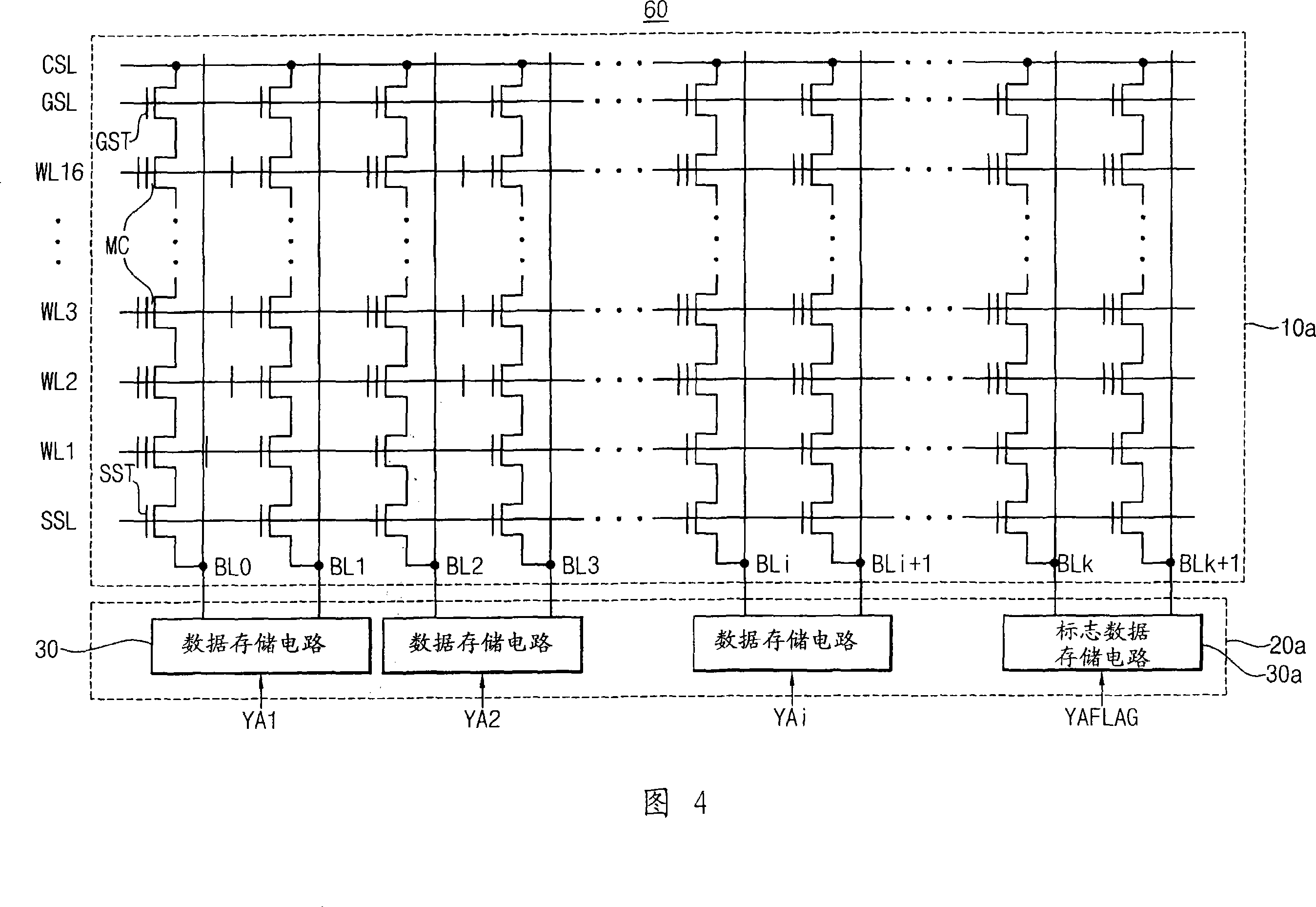
Method of programming multi-level cells and non-volatile memory device including the same
InactiveCN101206923AReduce integration rateAvoid verification processRead-only memoriesDigital storageComputer scienceMulti-level cell
Owner:SAMSUNG ELECTRONICS CO LTD
Cryptographic key distribution
InactiveUS20180270052A1Reduce or eliminate impactLower requirementKey distribution for secure communicationTelecommunications linkCryptographic nonce
Disclosed is a cryptographic key distribution method and apparatus for installing a cryptographic key in an ECU. The method comprises: establishing a first communication link between the ECU and a key source; sending, via the first link, a first cryptographic key from the key source to the ECU; establishing a second communication link between the key source and a key manager; sending, via the second link, the first key from the key source to the key manager; encrypting, by the key manager, using the first key, a second cryptographic key; sending, by the key manager, to the ECU, the encrypted second key; and decrypting, by the ECU, using the first key, the encrypted second key, thereby providing the ECU with the second key.
Owner:BAE SYSTEMS PLC
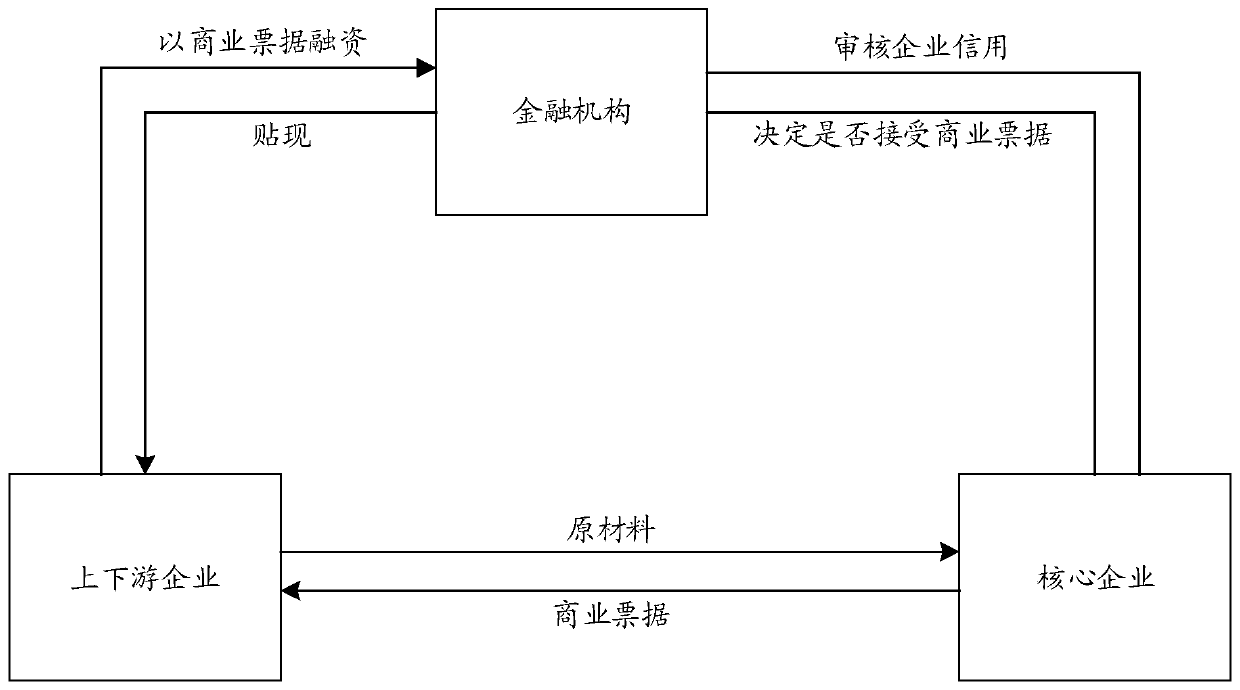
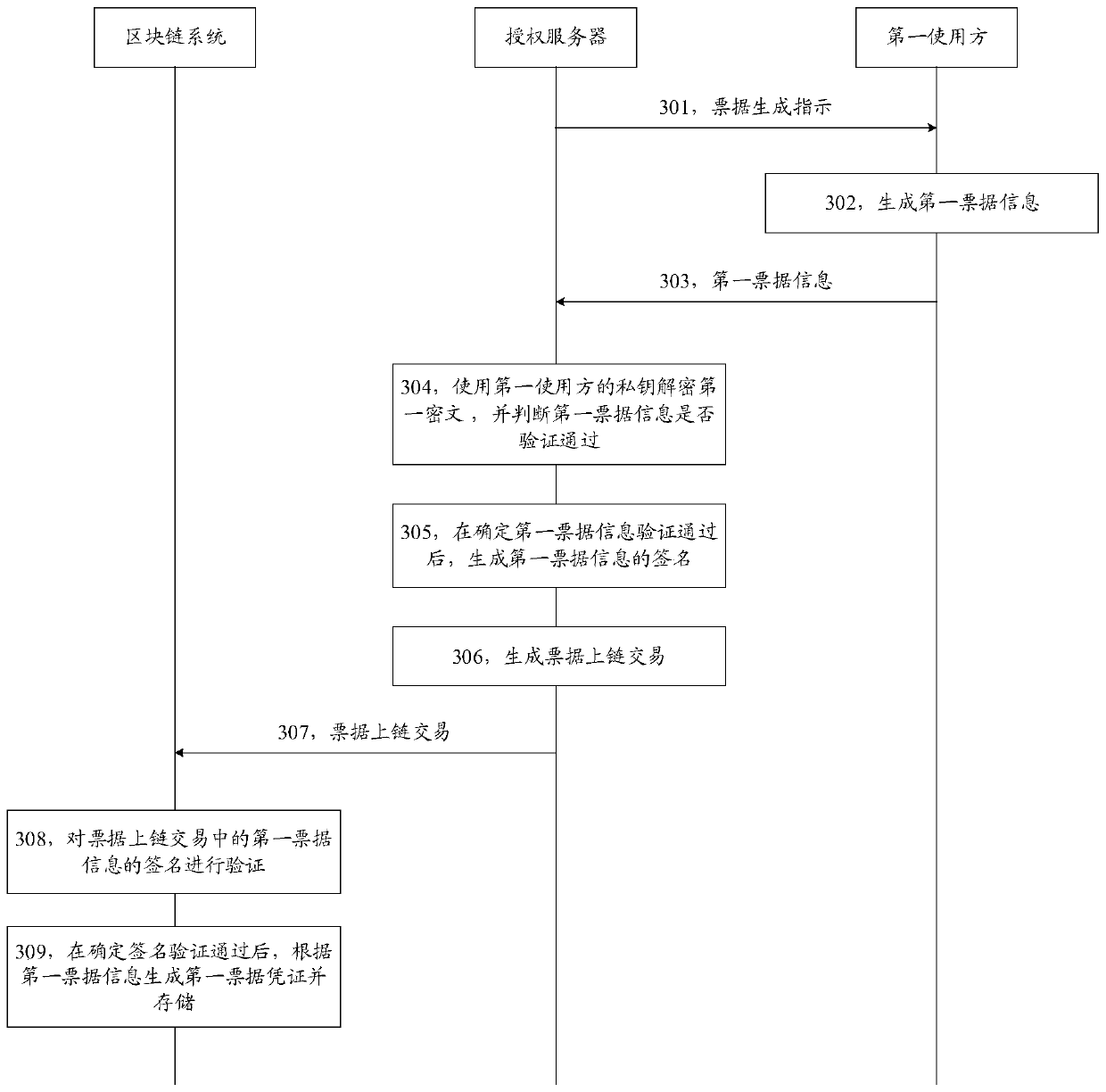
Bill processing method and device based on block chain
ActiveCN110070443AReduce verification effortRun fastFinanceDigital data protectionCiphertextChain system
The invention discloses a bill processing method and device based on a block chain. The method comprises the following steps: the authorization server sends a bill generation instruction to the firstuser, the first user generates a first ciphertext in which a first bill random number and a first bill amount are recorded; the first bill information is sent to an authorization server; and the authorization server generates a signature of the first bill information after determining that the first bill information passes the verification, and sends a bill chain transaction to the block chain system, and the block chain system generates a first bill certificate according to the first bill information after determining that the signature of the first bill information in the bill chain transaction passes the verification, and stores the first bill certificate. The technical scheme is used for guaranteeing bill transaction privacy in a block chain system.
Owner:WEBANK (CHINA)
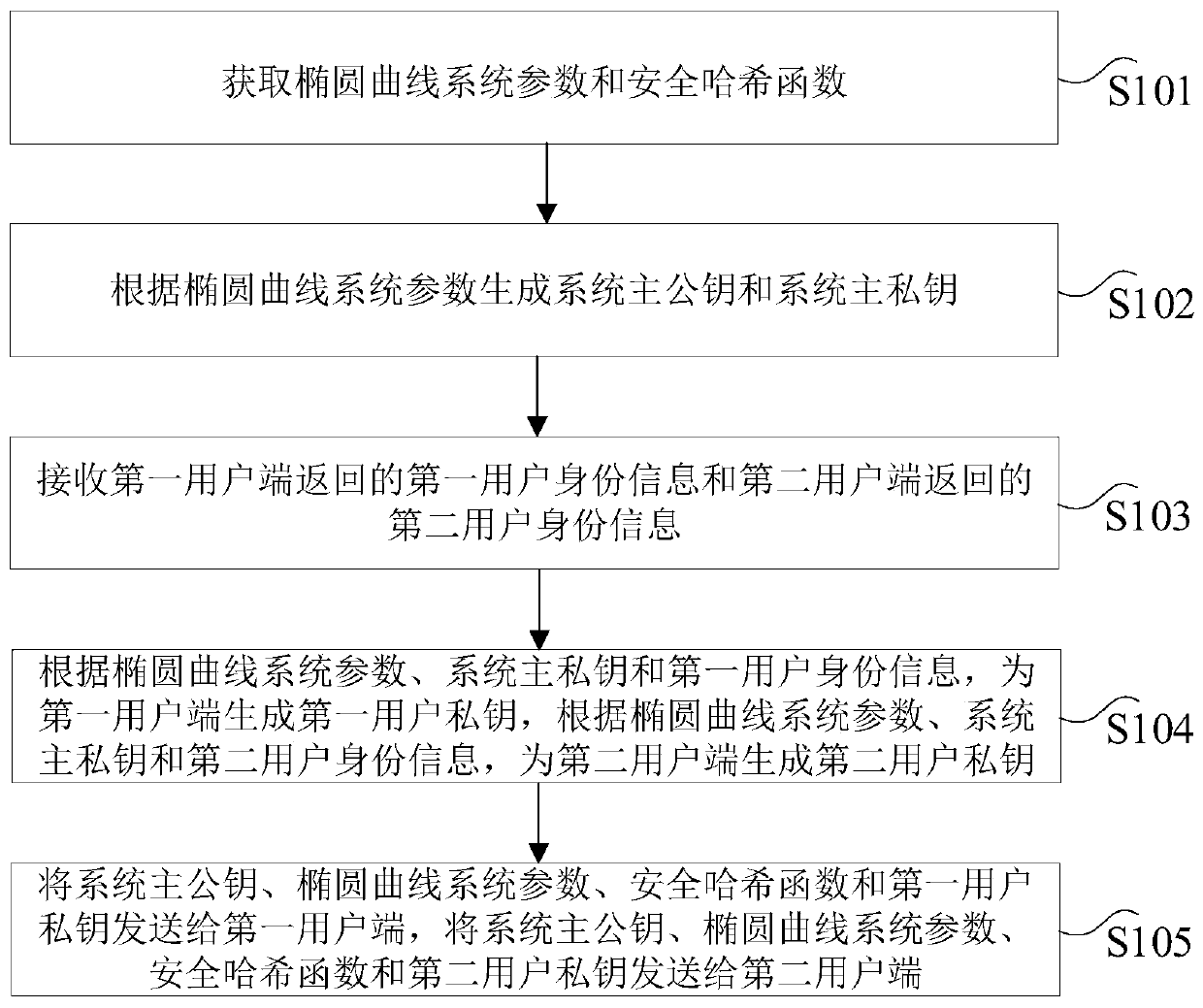
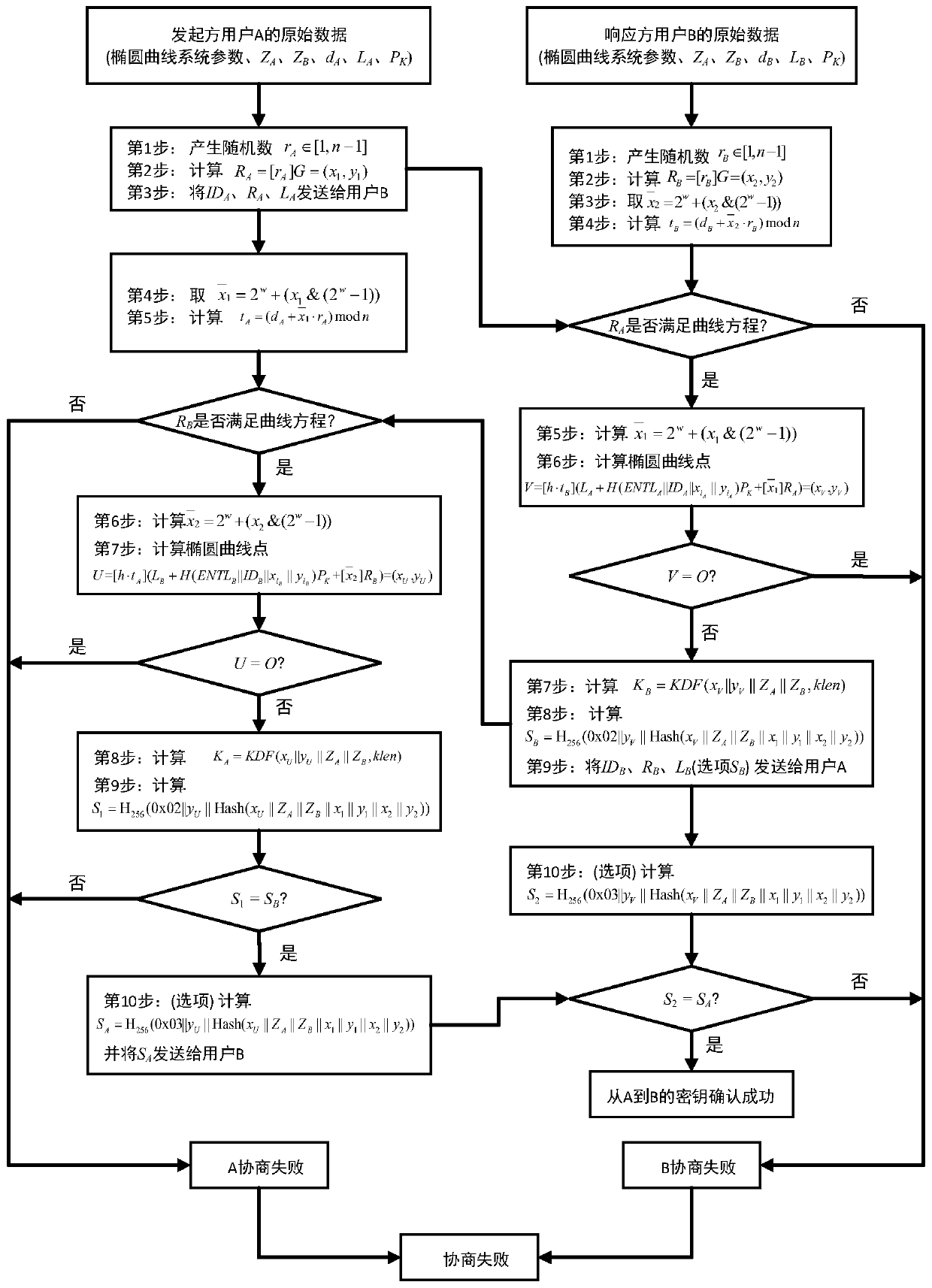
Shared secret key generation method and device, computer equipment and storage medium
ActiveCN109818744APromote generationAvoid sendingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesHash functionKey generation
The invention provides a shared secret key generation method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining an elliptic curve system parameter and asecurity hash function; generating a main public key and a main private key according to the elliptic curve system parameters; receiving first user identity information returned by the first user side and second user identity information returned by the second user side; generating a first user private key for the first user side according to the elliptic curve system parameters, the main privatekey and the first user identity information, and generating a second user private key for the second user side according to the elliptic curve system parameters, the main private key and the second user identity information; And sending the main public key, the elliptic curve system parameter, the security hash function and the first user private key to the first user side, and sending the main public key, the elliptic curve system parameter, the security hash function and the second user private key to the second user side. According to the scheme, the technical problem of high certificate management cost in the prior art is solved.
Owner:JUZIX TECH SHENZHEN CO LTD +1
User passing method and system
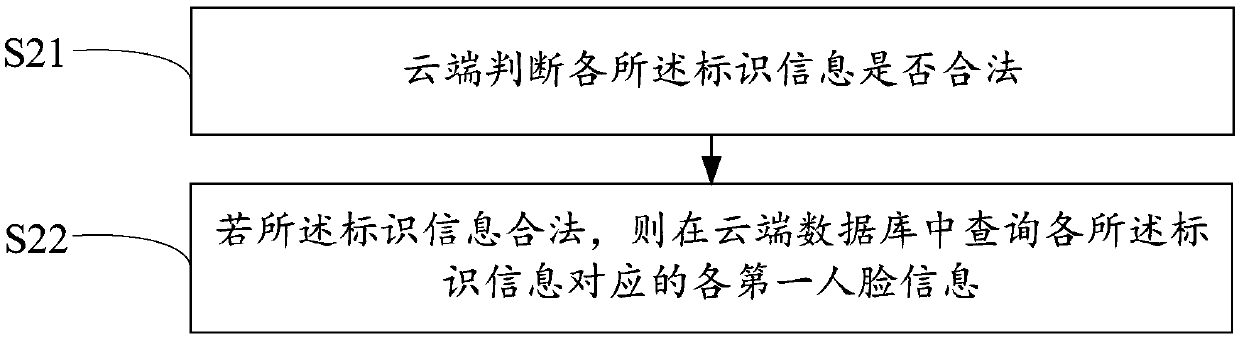
InactiveCN109544737AAvoid trafficAvoid verification processCharacter and pattern recognitionIndividual entry/exit registersTelecommunicationsComputer terminal
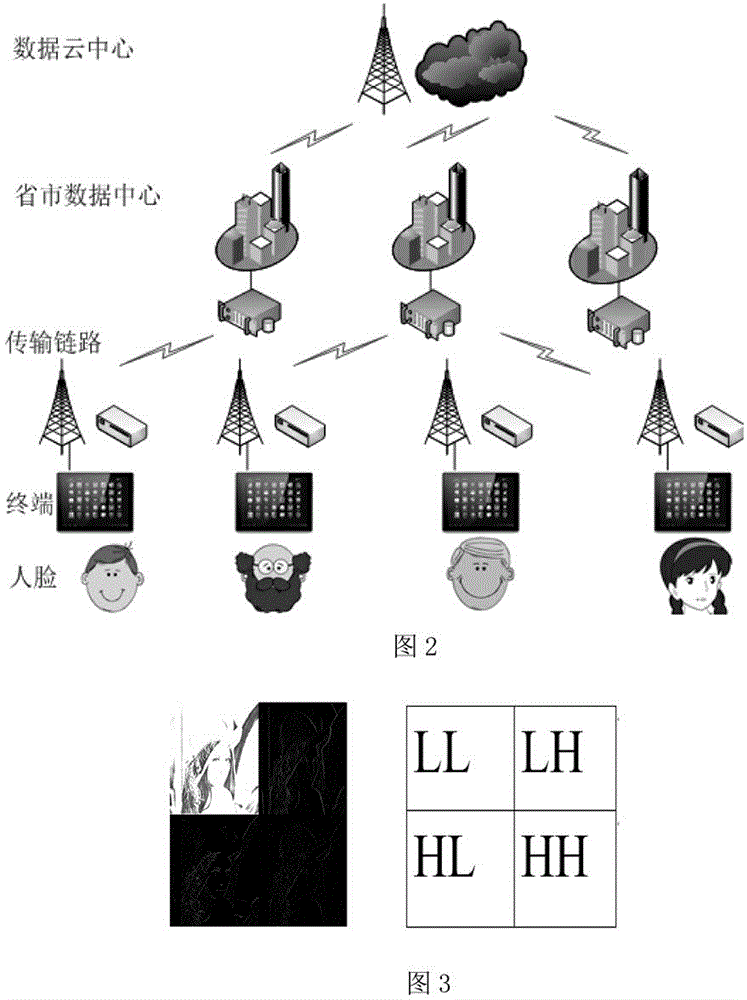
The invention provides a user passing method which comprises the following steps: detecting whether a mobile terminal exists in a preset detection range or not by a user passing device; if yes, sending an acquisition request to each mobile terminal so as to obtain the identification information sent by each mobile terminal on the basis of the acquisition request and sending the identification information to a cloud terminal; inquiring the first face information corresponding to the identification information in a cloud database by the cloud terminal, and sending the first face information to user passing equipment so as to form a comparison database, collecting the second face information of the user through a camera shooting device by means of the user passing equipment, matching the second face information with each first face information in the comparison database, and determining whether a matched target face information exists in the comparison database or not; finally, if yes, controlling a gate to be opened by the user passing equipment so as to allow the user to pass through. The invention further provides a user passing system. According to the invention, the verificationaccuracy is improved, and the passing efficiency is improved.
Owner:深圳市靓工创新应用科技有限公司
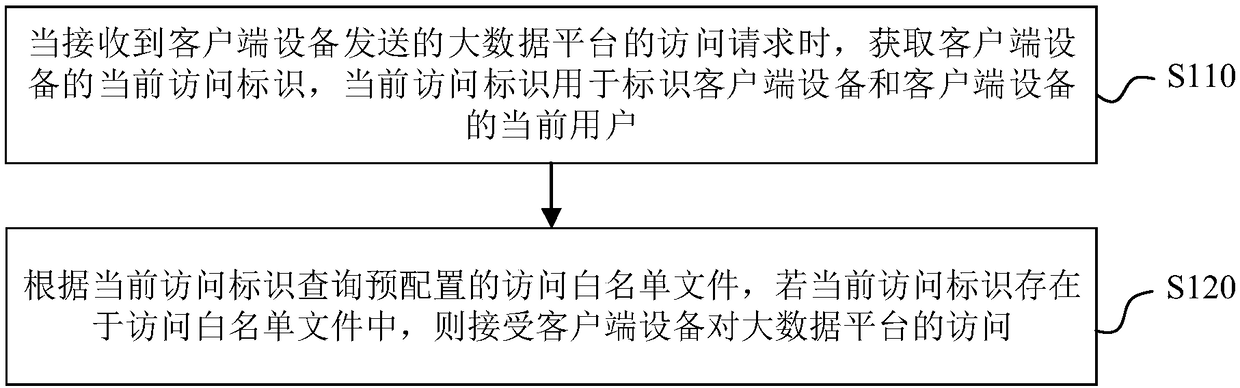
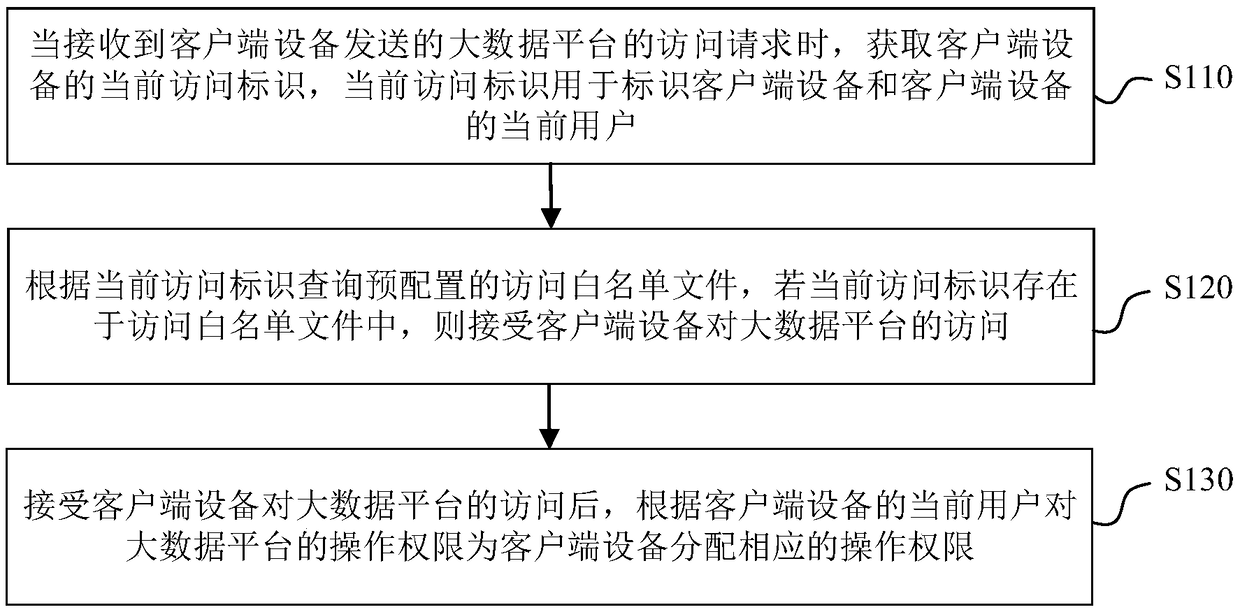
Large data platform access method, device, electronic equipment and readable storage medium
The embodiment of the invention provides a large data platform access method, device, electronic equipment and a readable storage medium. The method comprises steps: when a large data platform accessrequest sent by a client device is received, the current access identity of the client device is acquired, wherein the current access identity is used for identifying the client device and the currentuser of the client device; and according to the current access identity, a pre-configured access white list file is queried, and if the current access identity exists in the access white list file, access to the large data platform by the client device is accepted. In the scheme disclosed by the embodiment of the invention, based on whether the access identity of the client device exists in the access white list file, whether to accept the access to the large data platform by the client device is determined, and as the access identity can identify the device and the current user of the deviceat the same time, the large data platform access safety can be effectively ensured through the scheme.
Owner:BEIJING QIHOO TECH CO LTD
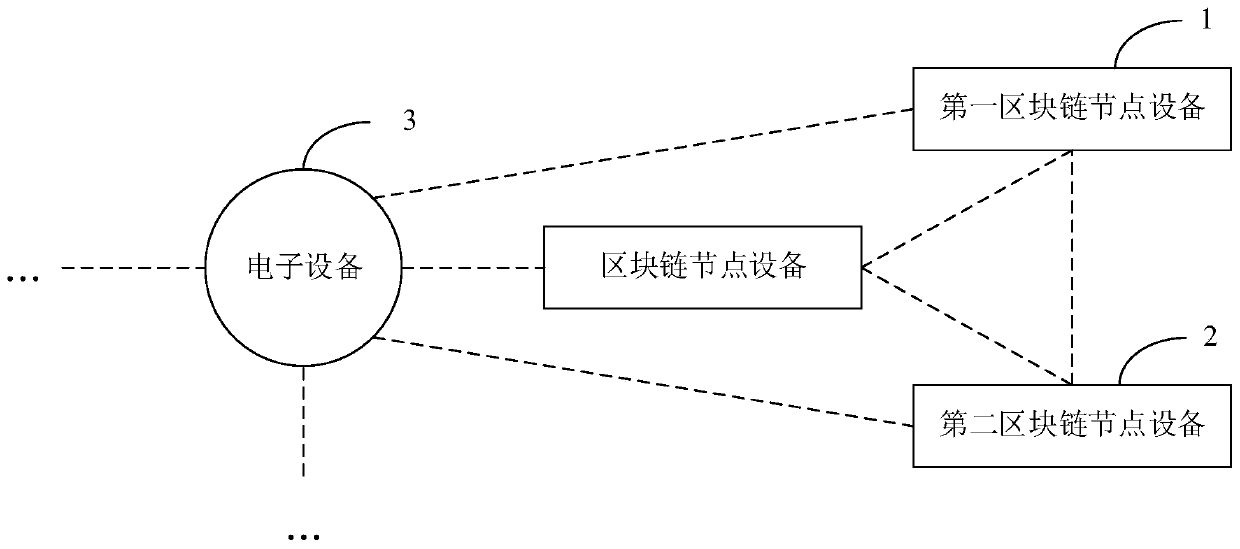
Data transmission method and device based on block chain and electronic equipment
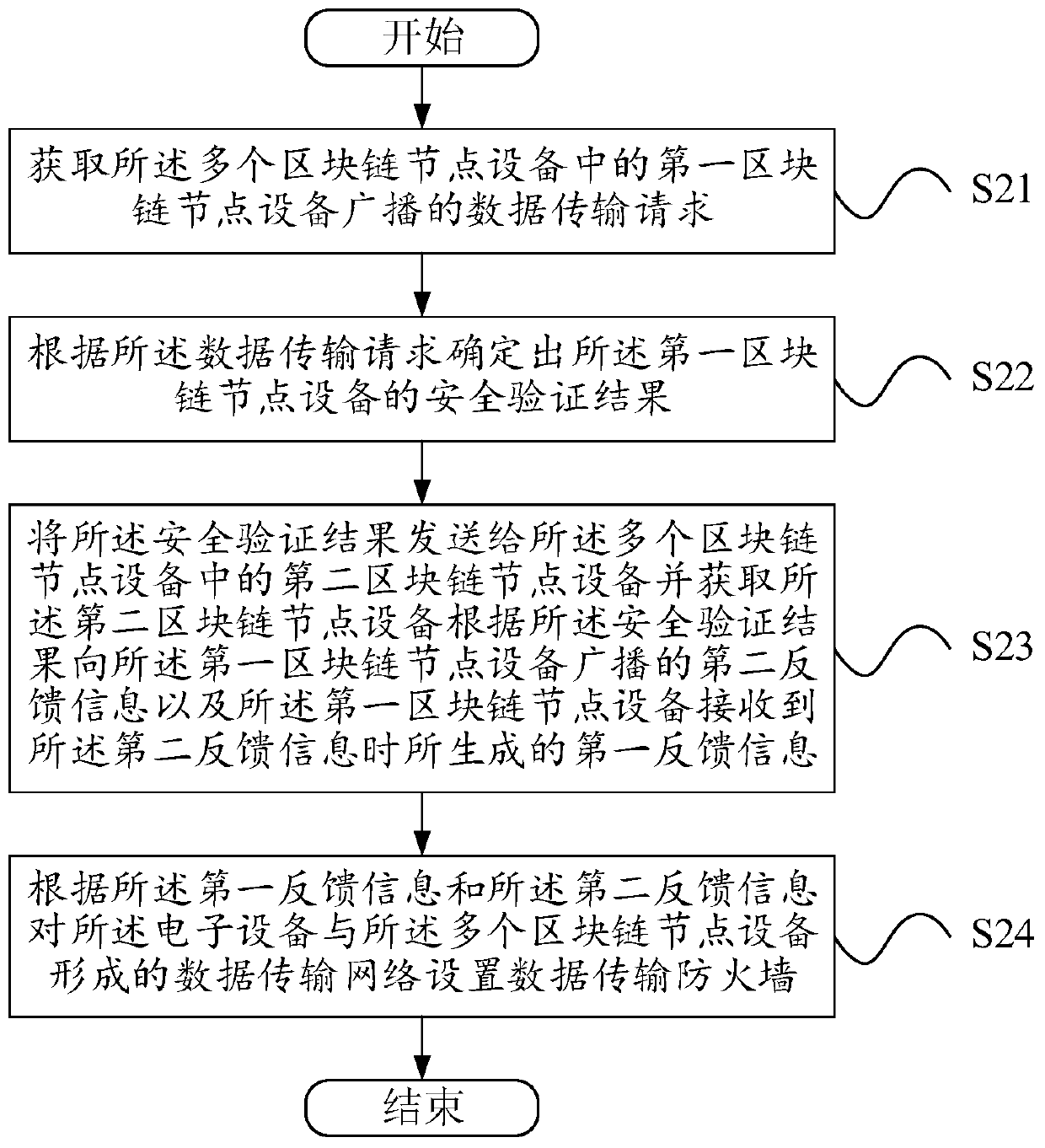
ActiveCN110933072AImprove timelinessEnsure data transmission securityDatabase distribution/replicationDigital data protectionData transmissionSecurity validation
The embodiment of the invention discloses a data transmission method based on a block chain. In this method, the second blockchain node device is prevented from carrying out security verification on the data transmission request, so that the second blockchain node device is prevented from allocating time slice resources for security verification and encryption algorithm processing; the second blockchain node device can directly respond according to the security verification result sent by the electronic device, and the timeliness of data transmission interaction between the second blockchain node device and the first blockchain node device is improved. The electronic equipment can fully and comprehensively verify the data transmission request, thereby ensuring the data transmission security between the second blockchain node device and the first blockchain node device. By setting the data transmission firewall, the data transmission potential safety hazard between the second blockchainnode device and the first blockchain node device can be eliminated, and thus the data transmission security of the whole data transmission network is ensured.
Owner:宁波平辅寅保险科技有限公司
Design method for optimum speed characteristics of trunk cab damper
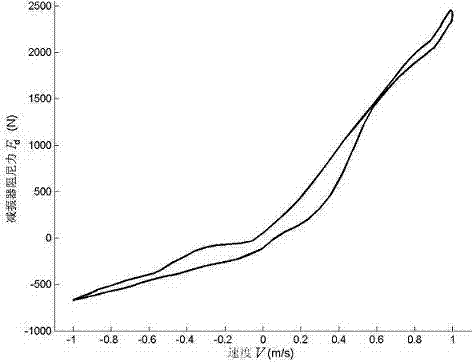
InactiveCN103112508ABest speed characteristicsReliable speed characteristicsLoading-carrying vehicle superstructuresDamperDamping ratio
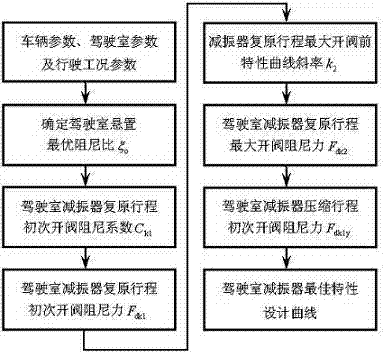
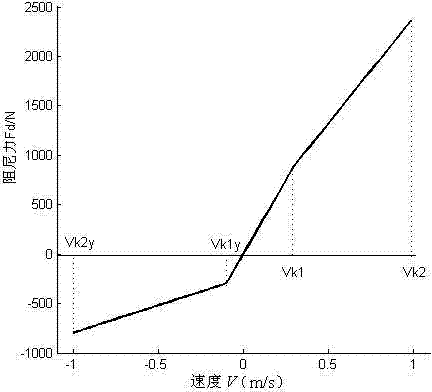
The invention relates to a design method for optimum speed characteristics of a trunk cab damper, and belongs to the technical field of cab suspension. Because analysis and calculation of a cab three quality vibration system are very complex, none reliable design method for design of the optimum speed characteristics of the trunk cab damper exists all the time at the moment. According to the method, the three quality vibration system and an optimum damping ratio determined by the three quality vibration system are composed of wheels, a trunk body and a cab, utilizes safety ratios, bi-directional characteristics, lever ratios and installment angles of the damper to design the optimum speed characteristics of the cab damper, and obtain recovery-travel and compression-travel segmented characteristic curves required by the design. By adopting the design method, the reliable speed characteristics of the cab damper are achieved. The design of the damper can ensure that the optimum damping effects of the damper are reached, and riding comfort is satisfied. Meanwhile, repeating tests, verification and modify are avoided, and test cost of the cab damper is reduced.
Owner:SHANDONG UNIV OF TECH
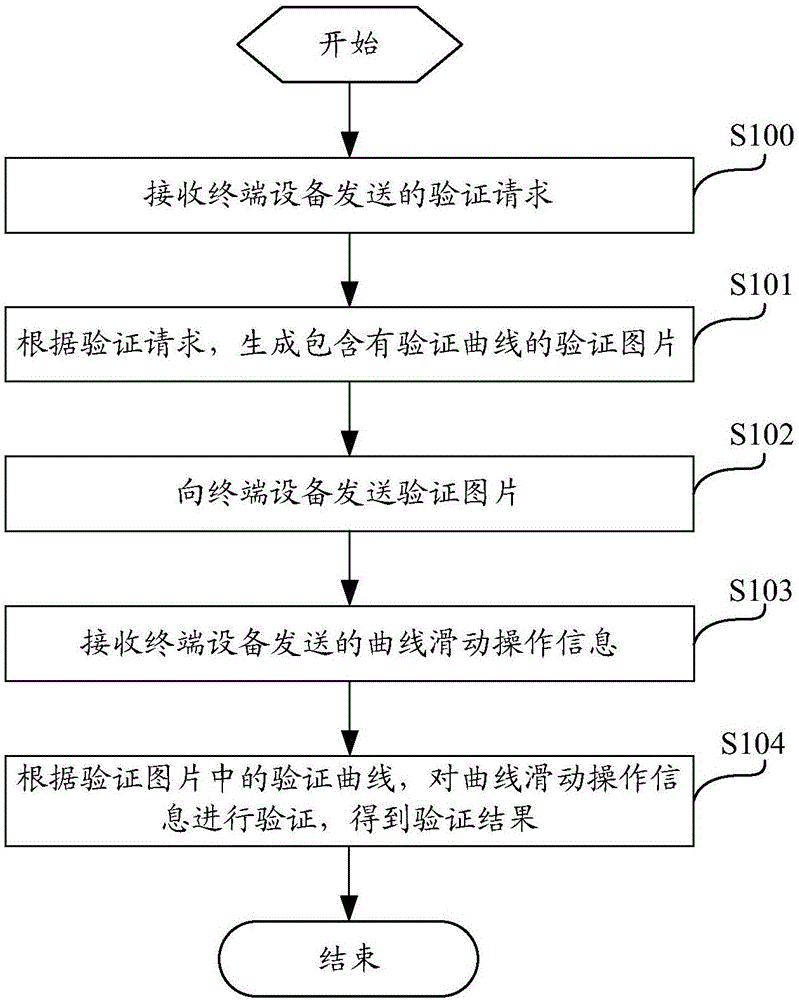
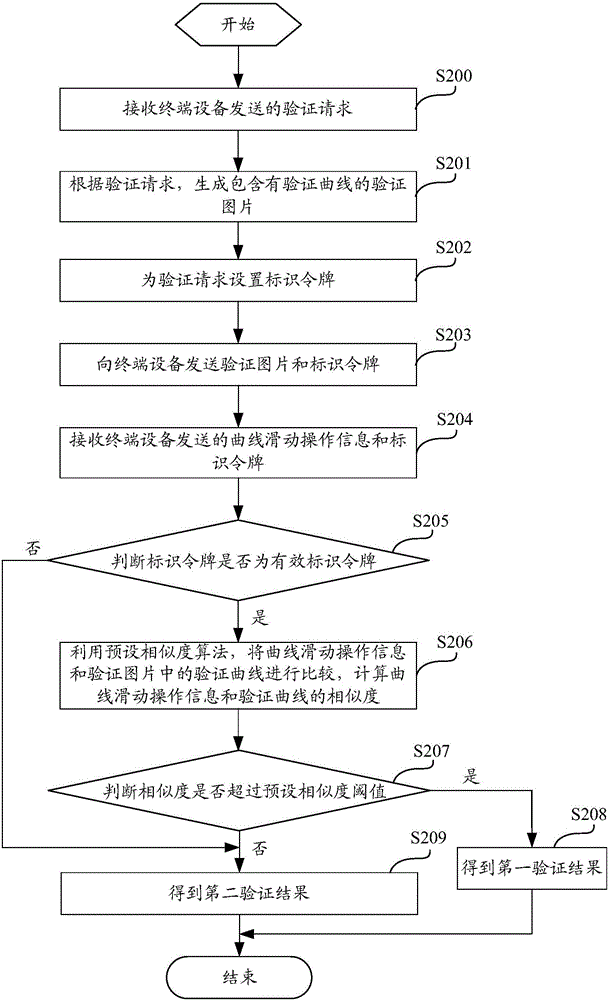
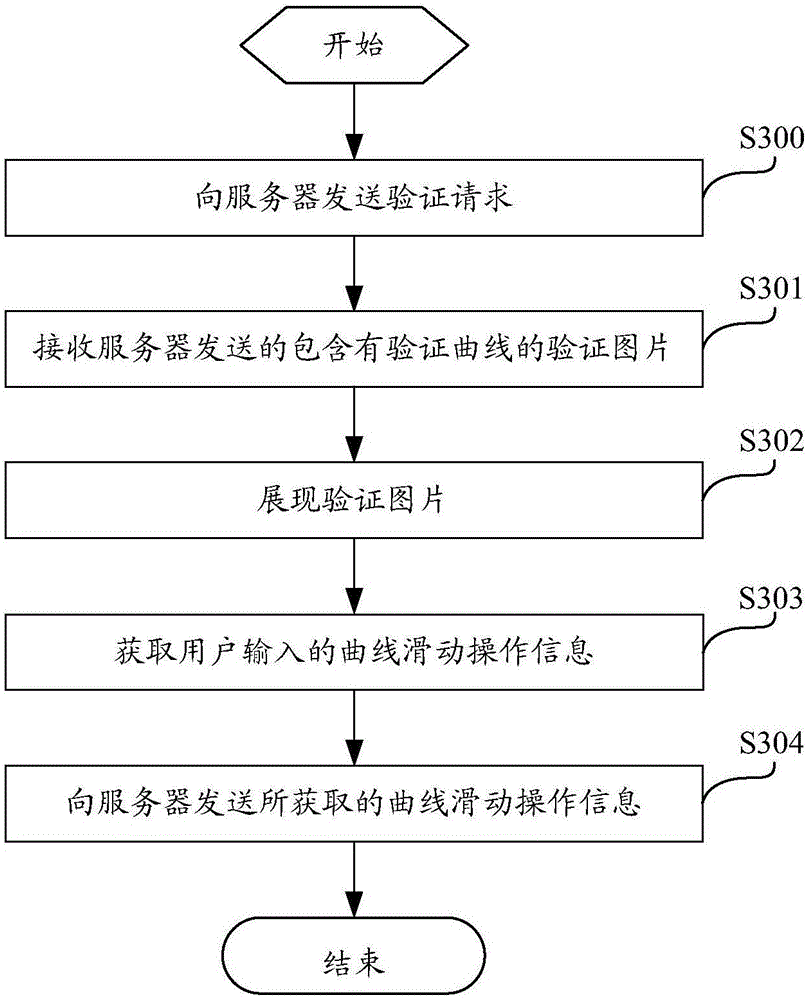
Verification method based on interaction operation, server, terminal equipment and system
InactiveCN106603545AEasy to verifyAvoid verification processTransmissionComputer architectureValidation methods
The invention discloses a verification method based on interaction operation, a server, terminal equipment and a system; the verification method based on interaction operation comprises the following steps: receiving a verification request sent by the terminal equipment; forming a verification image containing a verification curve according to the verification request; sending the verification image to the terminal equipment; receiving curve slide operation information sent by the terminal equipment; verifying the curve slide operation information according to the verification curve in the verification image, thus obtaining a verification result. The method can effectively prevent robot verification, so user can easily carry out verification, thus improving safety and verification efficiency, and optimizing the verification modes.
Owner:JIANGSU PAYEGIS TECH CO LTD
Monitoring system and monitoring method based on campus network
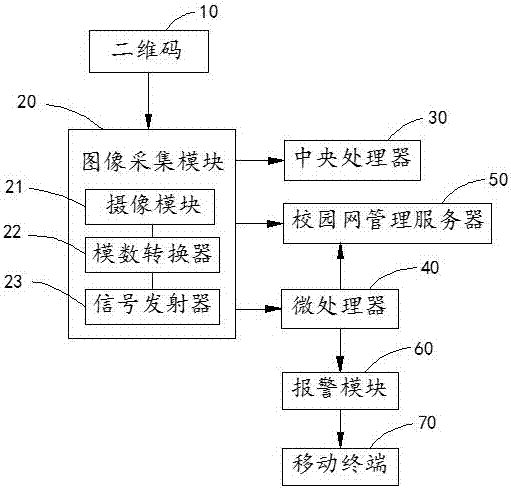
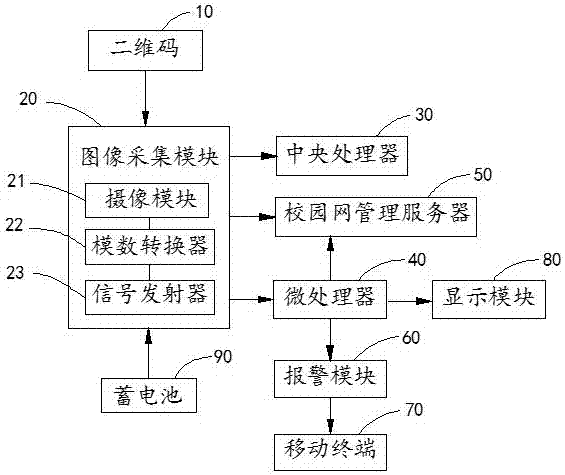
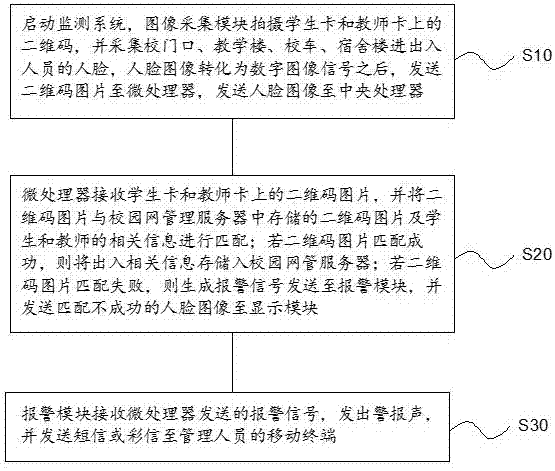
InactiveCN107277136AImprove securityEnsure school safetyClosed circuit television systemsTransmissionReal time acquisitionSchool bus
The invention discloses a monitoring system and a monitoring method based on a campus network. The monitoring system comprises a two-dimensional code, camera modules, a central processor, a campus network management server and a microprocessor, wherein the two-dimensional codes are used for storing related information of students and teachers; the camera modules are used for shooting two-dimensional codes on student cards and teacher cards, and human faces of people walking through campus doors and teaching buildings; the campus network management server is used for storing two-dimensional code pictures on the student cards and teacher cards and related information of the students and the teachers; and the microprocessor is used for receiving the two-dimensional code pictures on the student cards and teacher cards, and matching the two-dimensional code pictures with the two-dimensional code pictures stored in the campus network management server. According to the monitoring system and the monitoring method provided by the invention, the condition of the students and the teachers entering and quitting the campus doors, school buses and apartment buildings can be accurately and efficiently monitored, the safety factor is high, and safety of the students and the teachers in the campus is ensured thoroughly.
Owner:合肥博之泰电子科技有限公司
Intensity checking method of overlaying valve plates of compression valve of vehicle buffer
InactiveCN103161871AGuaranteed design lifeReduce test costsSpringsShock absorbersEngineeringStructural engineering
The invention relates to an intensity checking method of overlaying valve plates of a compression valve of a vehicle buffer, and belongs to the technical field of hydraulic buffers. At present, a reliable calculation method for checking the maximum stress and intensity of the overlaying valve plates of the compression valve is not given at home and aboard, the checking is conducted through numerical simulation by finite element software most of the time, and therefore modern design requirements of the buffers can not be satisfied. The intensity checking method is characterized in that checking of the intensity of the overlaying valve plates of the compression valve is conducted according to the thicknesses, the number of pieces, the allowable stress and the maximum stress of the overlaying valve plates of the compression valve. According to the intensity checking method, not only influences of normal open holes of a rebuilt valve, piston gaps and a circulation valve are considered, but also the stress condition of actual non uniform pressure is considered. The intensity checking method of the overlaying valve plates of the compression valve of the vehicle buffer is capable of calculating the maximum stress of the overlaying valve plates of the compression valve accurately, checking the intensity reliably, guaranteeing the design service life of the buffer, reducing maintenance cost, avoiding repeated testing and modification, reducing the cost of designing and testing, and shortening the development cycle.
Owner:SHANDONG UNIV OF TECH
Admittance identity authentication system based on image identification
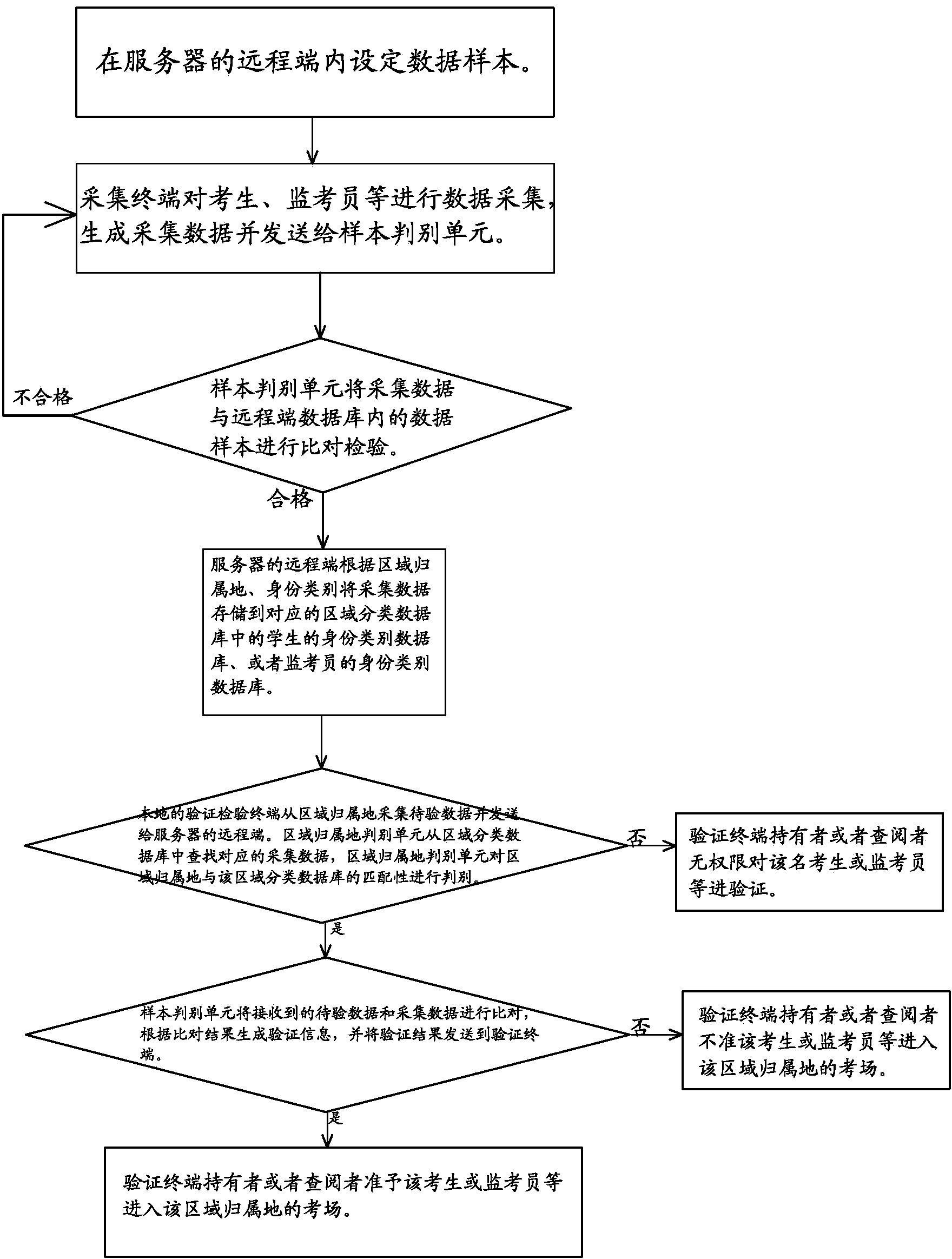
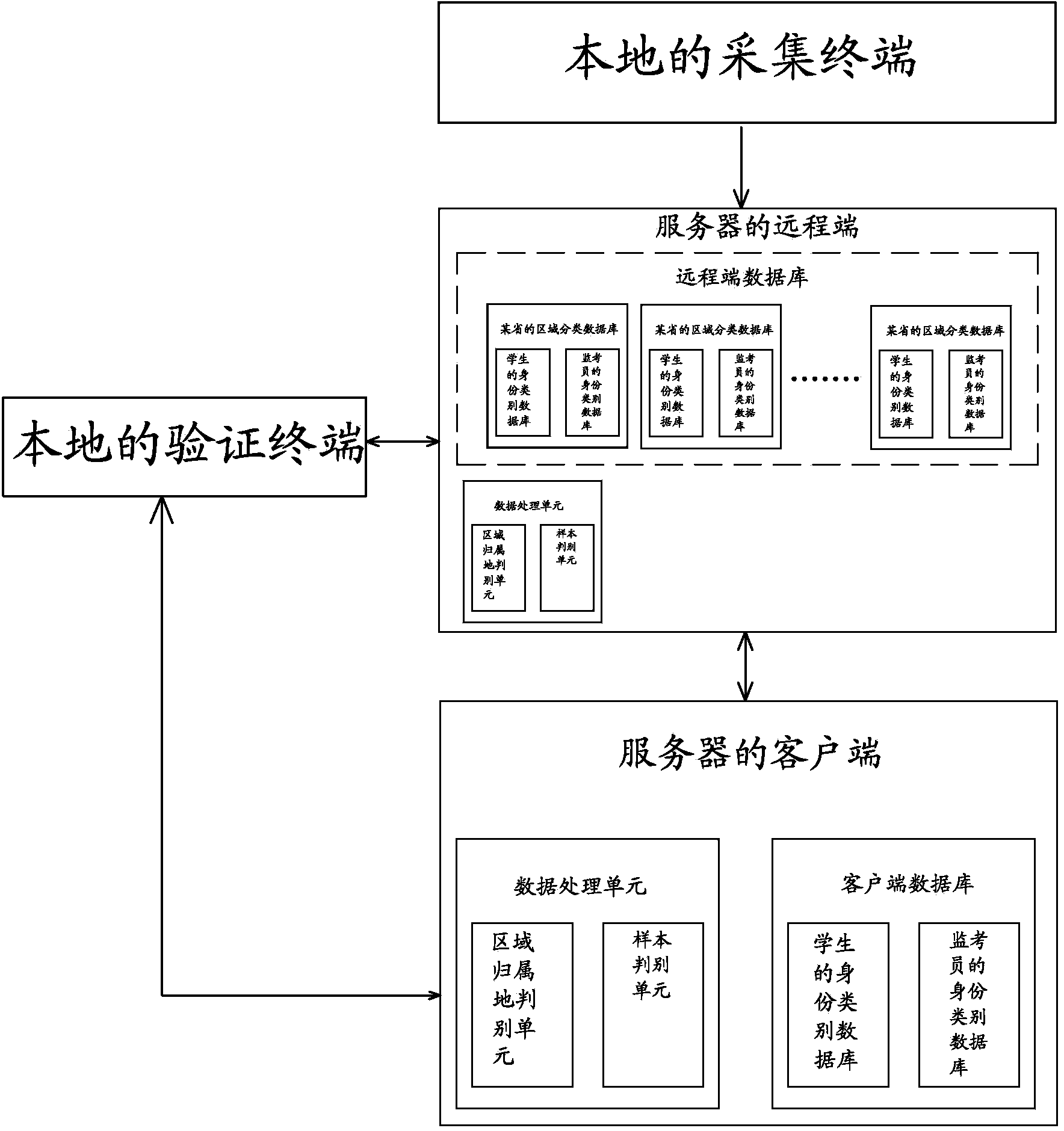
InactiveCN104240347APrevent Identity InquiryImprove recognition efficiencyIndividual entry/exit registersInternet privacyConfidentiality
The invention discloses an admittance identity authentication system based on image identification. According to the system, an acquisition terminal acquires character information and image information, so as to generate acquired data; a server stores the acquired data in corresponding region classification databases according to regional attributions of the acquired data; an authentication terminal acquires data to be authenticated from the regional attributions; the server compares the data to be authenticated with the acquired data, judges whether the regional attributions are matched with the region classification databases, where the corresponding acquired data are located, or not, generates authentication information according to matching results and sends the authentication information to the authentication terminal, the authentication terminal judges whether authentication permissions can be obtained or not, and then, whether the data to be authenticated pass through the admittance authentication of the regional attributions or not is acquired. The system has the advantages that the anti-counterfeiting performance is good, forgery and theft are difficult, convenience is brought for the arrangement of various types of field services, the admittance efficiency is increased, the staff setting is simplified, then, the effect of getting twice the result with half the effort is achieved, the identity check and authentication among different regional attributions can be prevented, and thus, the confidentiality of identity authentication is improved.
Owner:福建省智慧物联网研究院有限责任公司
Big data write-in method and device, big data read method and device and big data processing system
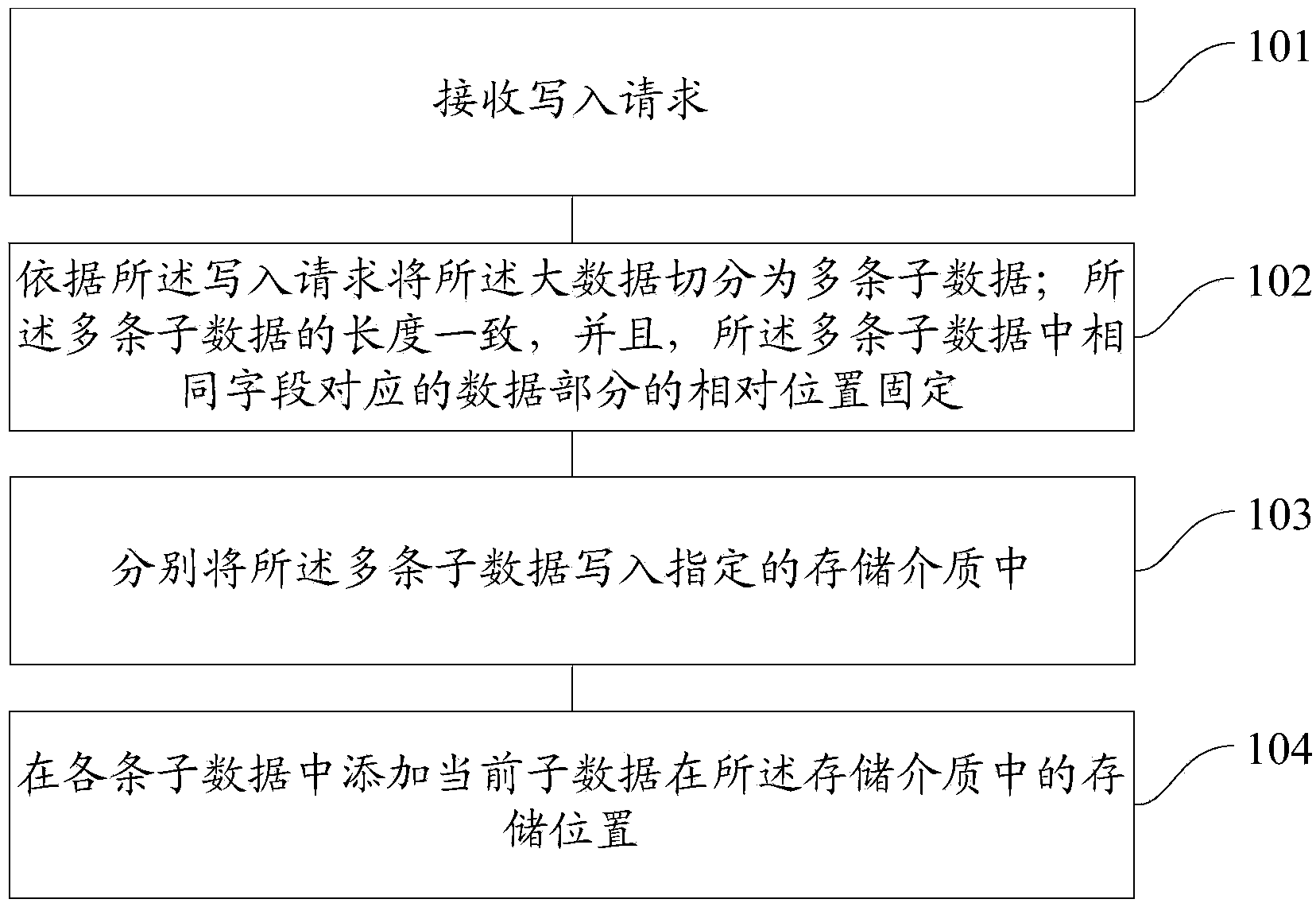
ActiveCN103970844AOrderly storageEasy to storeInput/output to record carriersSpecial data processing applicationsHandling systemData store
The embodiment of the invention provides a big data write-in method and device, a big data read method and device and a big data processing system. The write-in method includes the steps that a write-in request is received; big data are segmented into multiple pieces of subdata according to the write-in request; the subdata are uniform in length, and relative positions of data parts, corresponding to the same field, in the subdata are fixed; the subdata are written in a specified storage medium; storage positions, in the storage medium, of current subdata are added to all the subdata. The big data can be positioned easily, conveniently and rapidly, time consumption is reduced, the speed of storing and reading the big data is increased, and system performance and working efficiency are improved.
Owner:BEIJING TRUSTMEDU SCI TECH
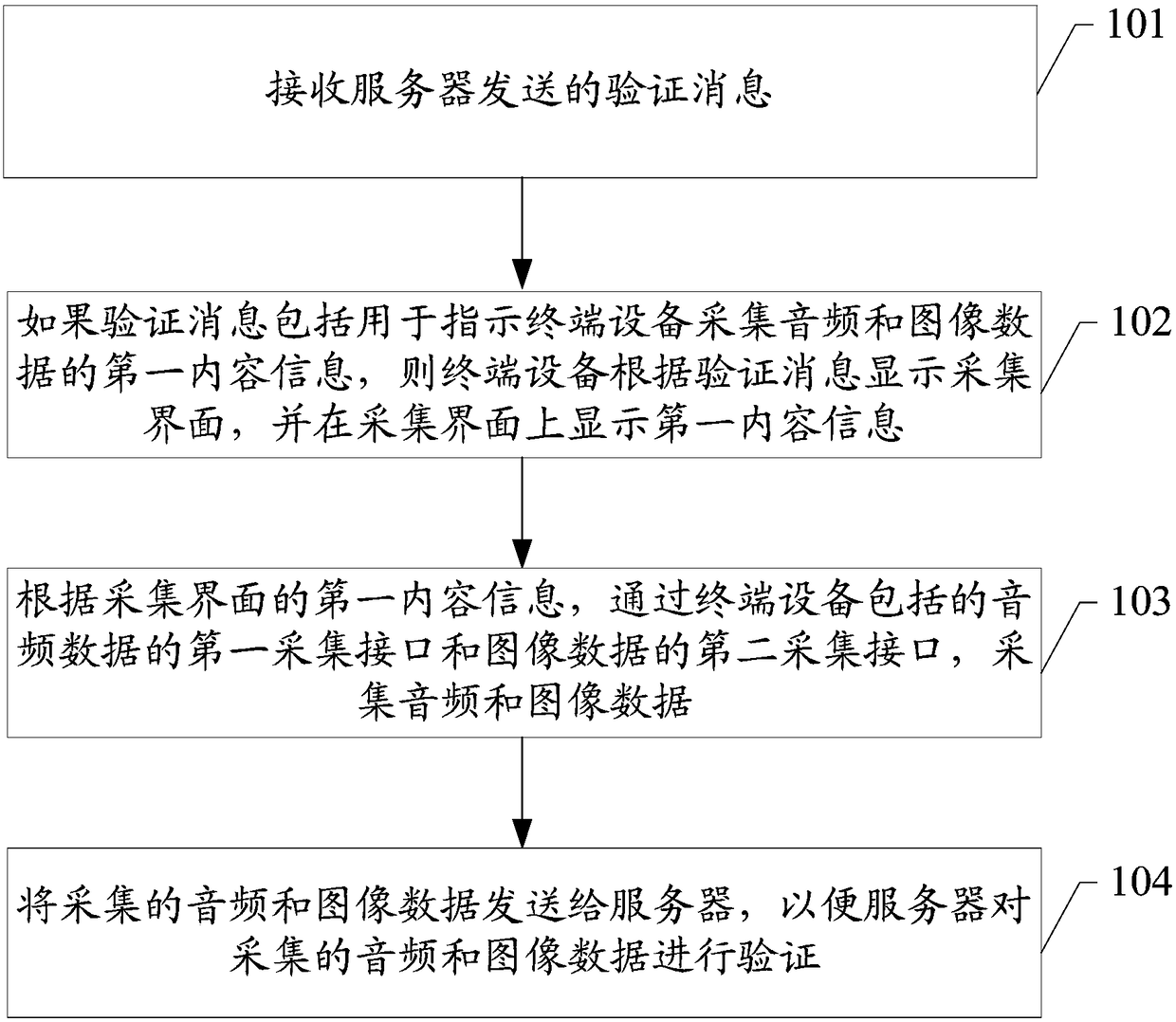
Identity verification method and device, and storage medium
The embodiments of the invention disclose an identity verification method and a device, and a storage medium which are applied to the information processing technology field. When terminal equipment in a system based on user login initiates a certain type of request, a server sends a verification message including first content information to the terminal equipment so as to notify an operation user to collect audio and image data. The user needs to use the terminal equipment to collect the audio and image data and transmits to the server for verification. If the audio and image data passes theverification, the identity of the operation user of the terminal equipment passes the verification. Through the collected audio and image data, whether the user operating the terminal equipment is avalid user can be verified and a verification process is safe. And when the collected audio and image data corresponds to the first content information, the verification can be passed so that other users can be prevented from using pre-recorded audio and image data of the valid user to carry out verification, and safety of terminal equipment operation is increased.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
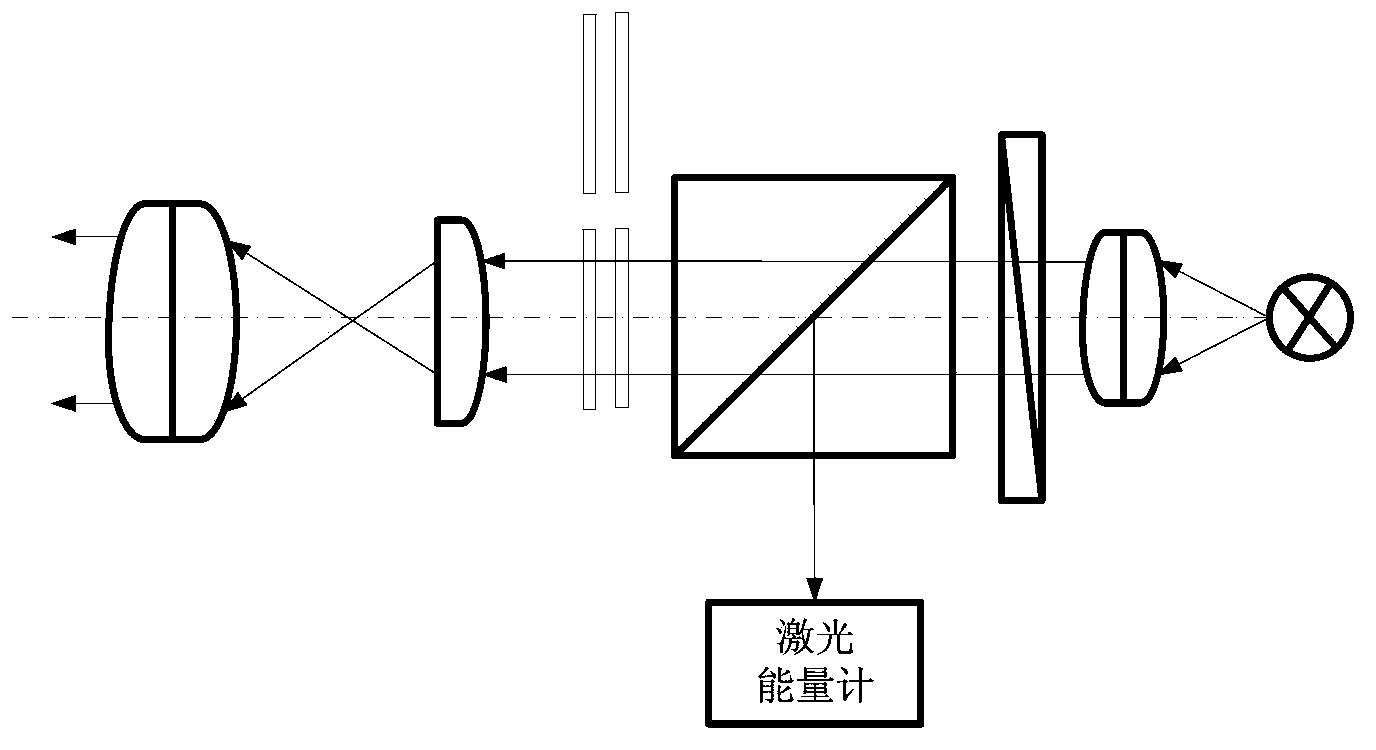
Joule-level pulse laser light source
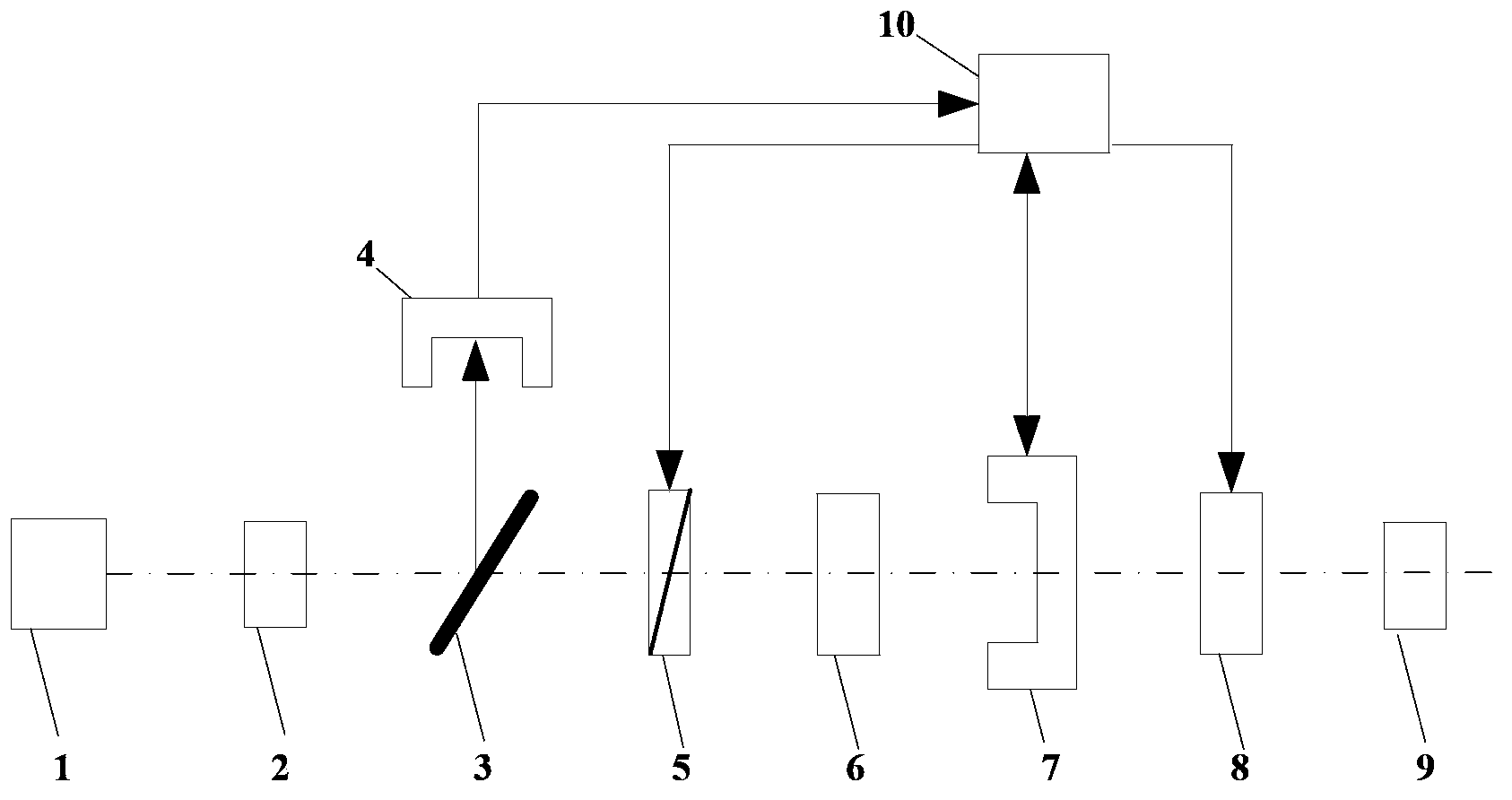
ActiveCN103441424AReduce design costAvoid beam non-uniformity problemsLaser output parameters controlActive medium shape and constructionPolarizerTransmittance
The invention discloses a joule-level pulse laser light source which comprises a laser, a collimating mirror, a beam splitter, an energy monitor meter, a polarizer component, a fixed attenuator component, a reference energy meter, a variable attenuator, a beam expander and a computer. Light emitted by the laser passes through the collimating mirror and is changed into parallel light, the parallel light is split into two beams through the beam splitter, the reflective light beam is received and detected by the energy monitor meter, the computer judges whether the laser emits light stably or not according to the detection value of the energy monitor meter, the transmission light beam passes through the polarizer component and the fixed attenuator component and is changed into attenuate linearly polarized light, and the attenuate linearly polarized light is attenuated to a required energy value through the variable attenuator with transmittance controlled by the computer and is finally output by the beam expander. The joule-level pulse laser light source solves the problem of simulating long-distance diffuse reflection echo signals in a measurement test, and the provided analog light beams have the advantages of being uniform and stable in energy.
Owner:西安应用光学研究所
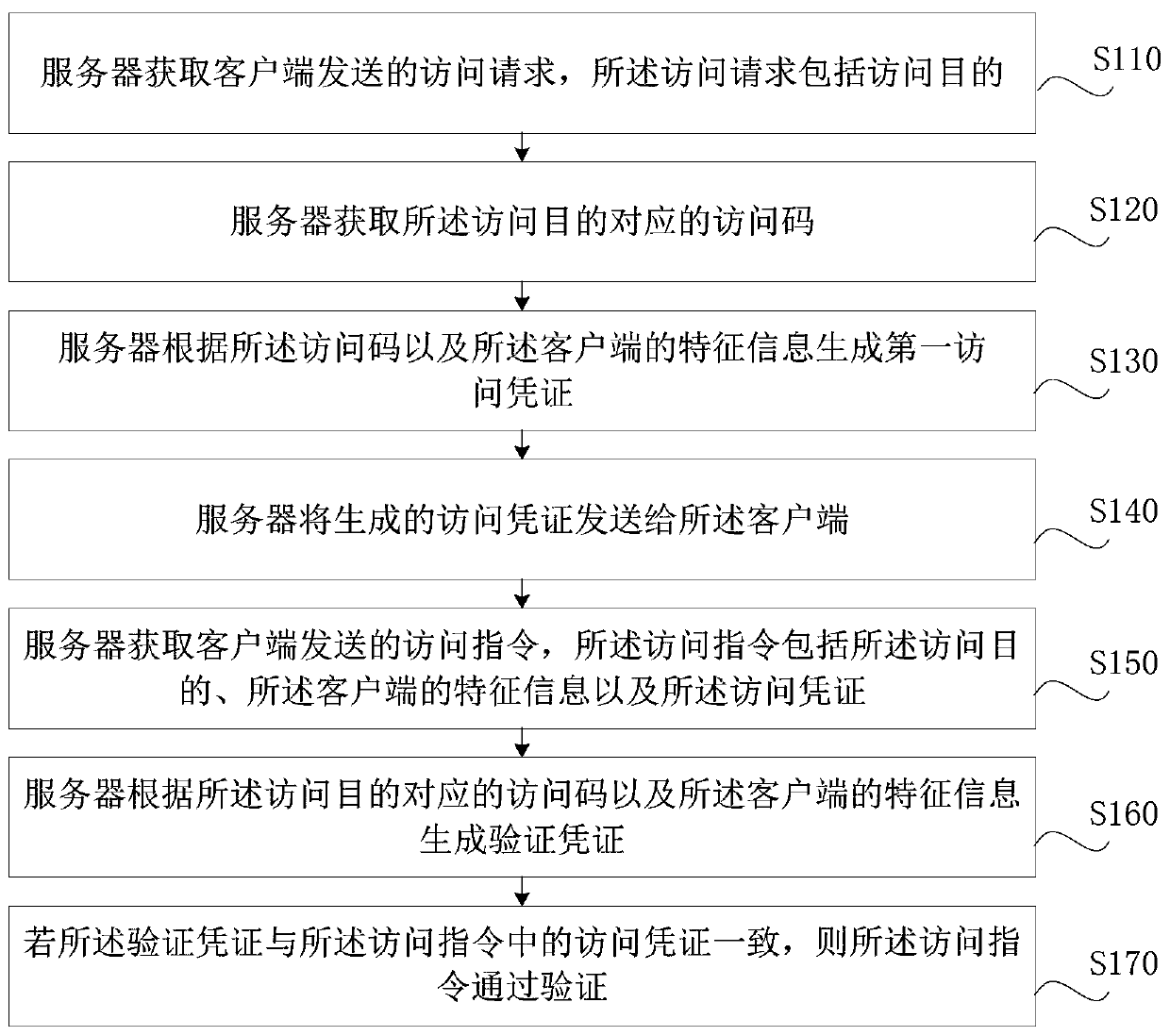
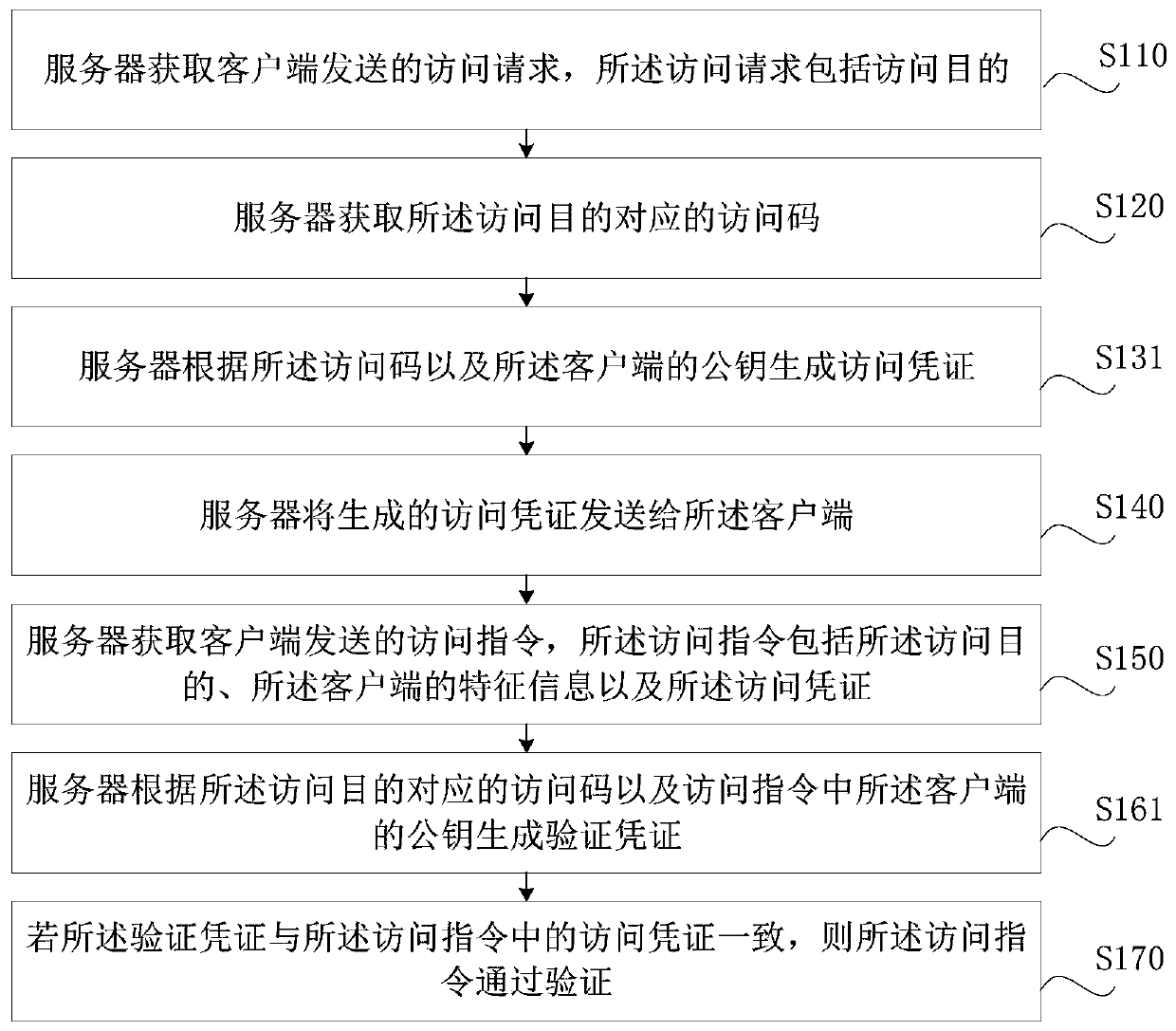
Access certificate verification method and device, computer equipment and storage medium
PendingCN109992976APrevent leakageGuaranteed privacyDigital data protectionValidation methodsVoucher
The invention relates to the field of identity authentication. An access certificate is generated and verified according to an access code corresponding to a file requested by a client and feature information of the client, and the file is prevented from being accessed through a stolen, tampered or forged access certificate. The invention concretely discloses an access certificate verification method and device, computer equipment and a storage medium. The access certificate verification method comprises the steps of acquiring an access request sent by a client side, wherein the access requestcomprises an access purpose; obtaining an access code corresponding to the access purpose; generating an access certificate according to the access code and the feature information of the client; sending the access certificate to the client; obtaining an access instruction sent by the client, wherein the access instruction comprises an access purpose, feature information of the client and an access certificate; generating a verification certificate according to the access code corresponding to the access purpose and the feature information of the client; and if the verification voucher is consistent with the access voucher in the access instruction, enabling the access instruction to pass the verification.
Owner:PING AN TECH (SHENZHEN) CO LTD
Method for Operating Automated Parking Brake
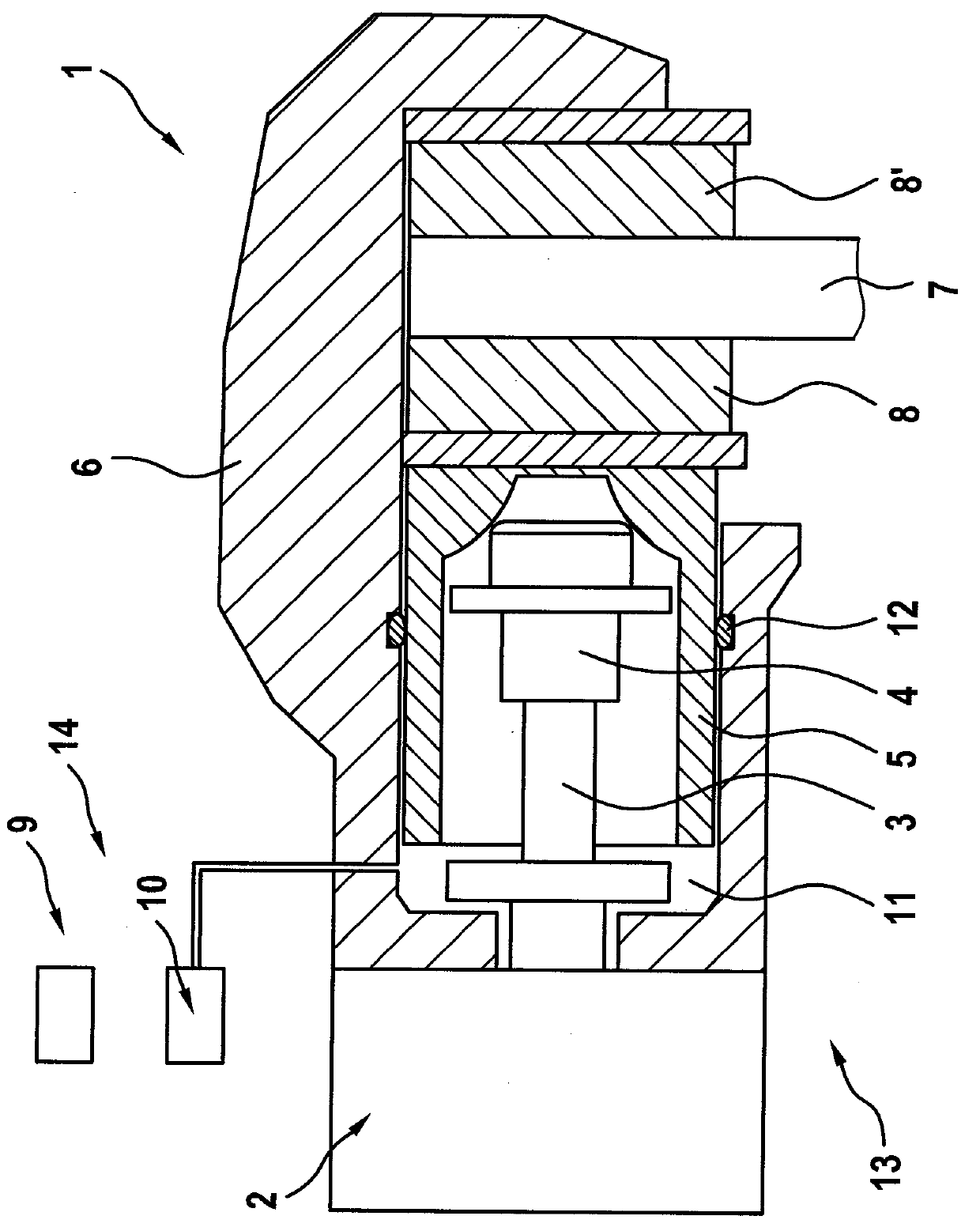
ActiveCN107650899AEasy to checkValid checkBraking action transmissionAutomatic initiationsControl theoryParking brake
A method for operating an automated parking brake in a motor vehicle with a hydraulic actuator for generating a hydraulic force component and an electromechanical actuator for generating an electromechanical force component, includes overlaying the hydraulic force component and the electromechanical force component to achieve a total clamping force for a parking brake process. The method further includes setting, on occurrence of a first condition, a first hydraulic pressure level, and setting, on occurrence of a second condition, a second hydraulic pressure level. The method also includes holding substantially constant the set first hydraulic pressure level with the hydraulic actuator until the occurrence of the second condition.
Owner:ROBERT BOSCH GMBH
Novel face authentication system for examination
InactiveCN104899493APrevent Identity InquiryImprove recognition efficiencyCharacter and pattern recognitionDigital data authenticationData acquisitionData cloud
The present invention relates to the technical field of internet-of-things information, in particular to a novel face authentication system for examination. The novel face authentication system comprises a data collection apparatus, a data processing apparatus, a cloud storage server and a plurality of entrance authentication collection apparatuses, wherein the data collection apparatus is in data communication connection with the data processing apparatus through a wired or wireless internet; the data processing apparatus is in data communication connection with the cloud storage server through a wired or wireless local area network; the data collection apparatus collects character information and image information, generates collection data and sends the collection data to the data processing apparatus in real time; the data processing apparatus, according to region attribution of the collection data, stores the collection data into a corresponding region classification database in a remote end database of the cloud storage server; the novel face authentication system is based on a data cloud center and an internet-of-things technology, so that the authentication efficiency is greatly improved and the anti-counterfeiting property is improved.
Owner:福建省智慧物联网研究院有限责任公司
Method for arranging display equipment software and method for writing control parameters into FLASH
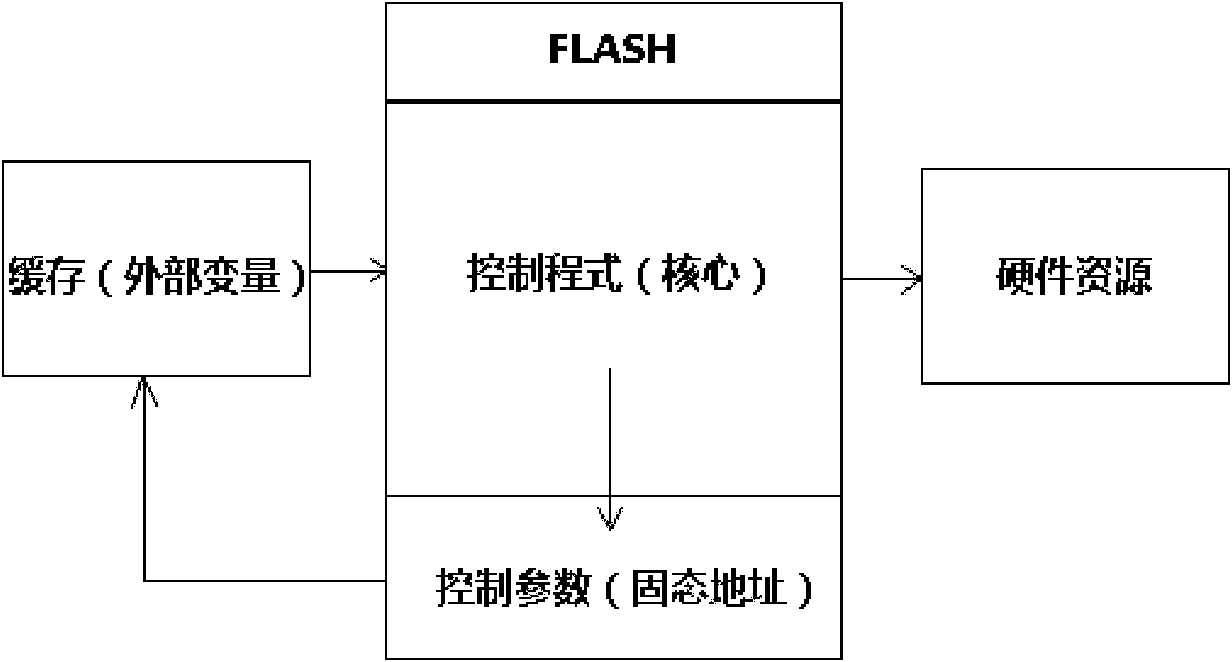
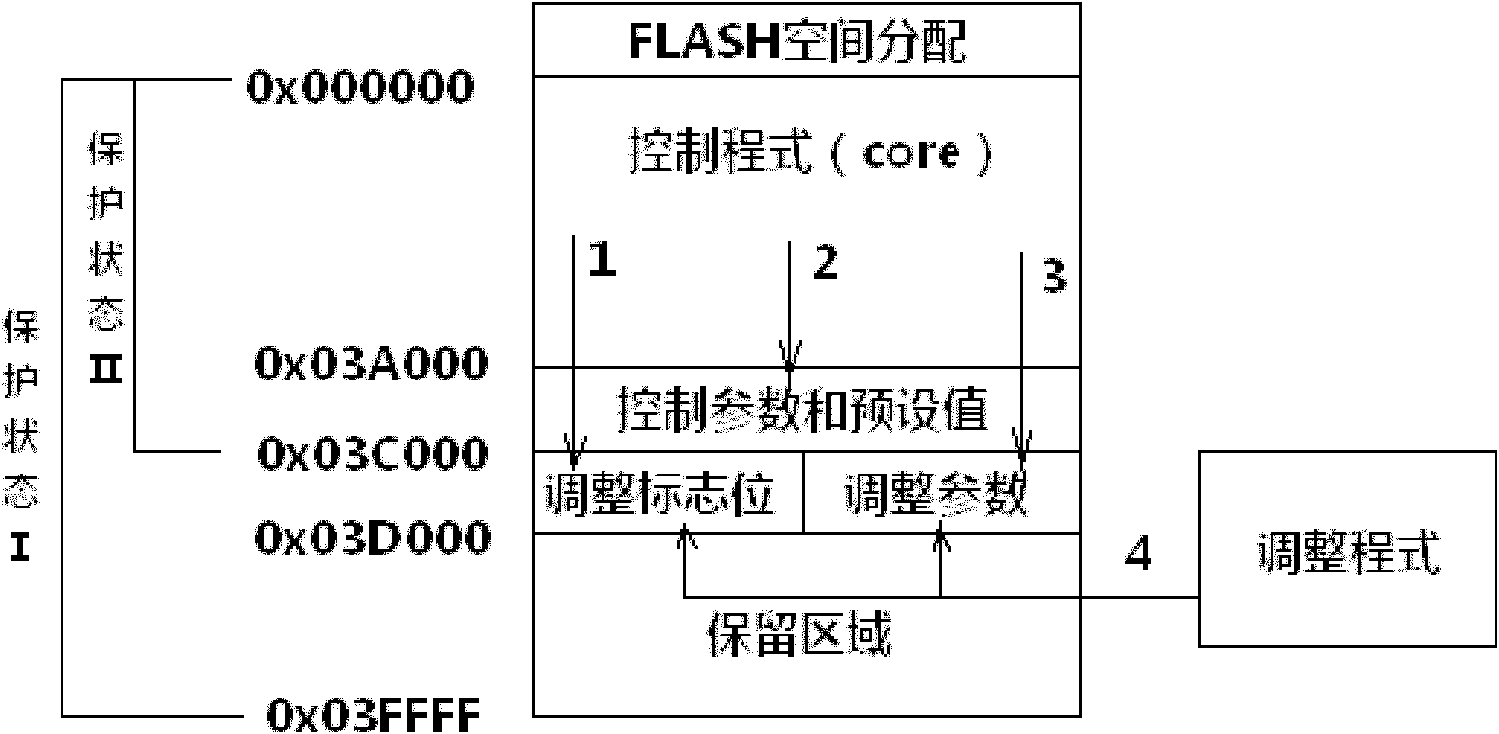
InactiveCN101976577AImprove design and development efficiencyReduce complexityRead-only memoriesElectricityPaper document
The invention discloses a method for arranging display equipment software and a method for writing control parameters into FLASH. A control program of the software is separated from the control parameters; a part of invariable control parameters and preset fixed values are stored in the FLASH (flash memory); and the FLASH is set in protected states for realizing read-only effect. The methods havethe advantages that: the control program and the control parameters are arranged separately, so that the setting complexity and risk of the control parameters can be lowered greatly, a large number of redundant verification processes are avoided and the development and design efficiencies of display equipment are improved; the writing opportunity of the control parameters is reduced, so that the risk of data loss caused by surge is lowered; simultaneously, an after-sales service department does not need to prepare for a large number of stock products; and once mechanism sizes are accordant, only the control parameters of the conventional product are set into a software document and are burnt, so that stock quantity can be reduced greatly and maintenance efficiency is improved.
Owner:TPV DISPLAY TECH WUHAN
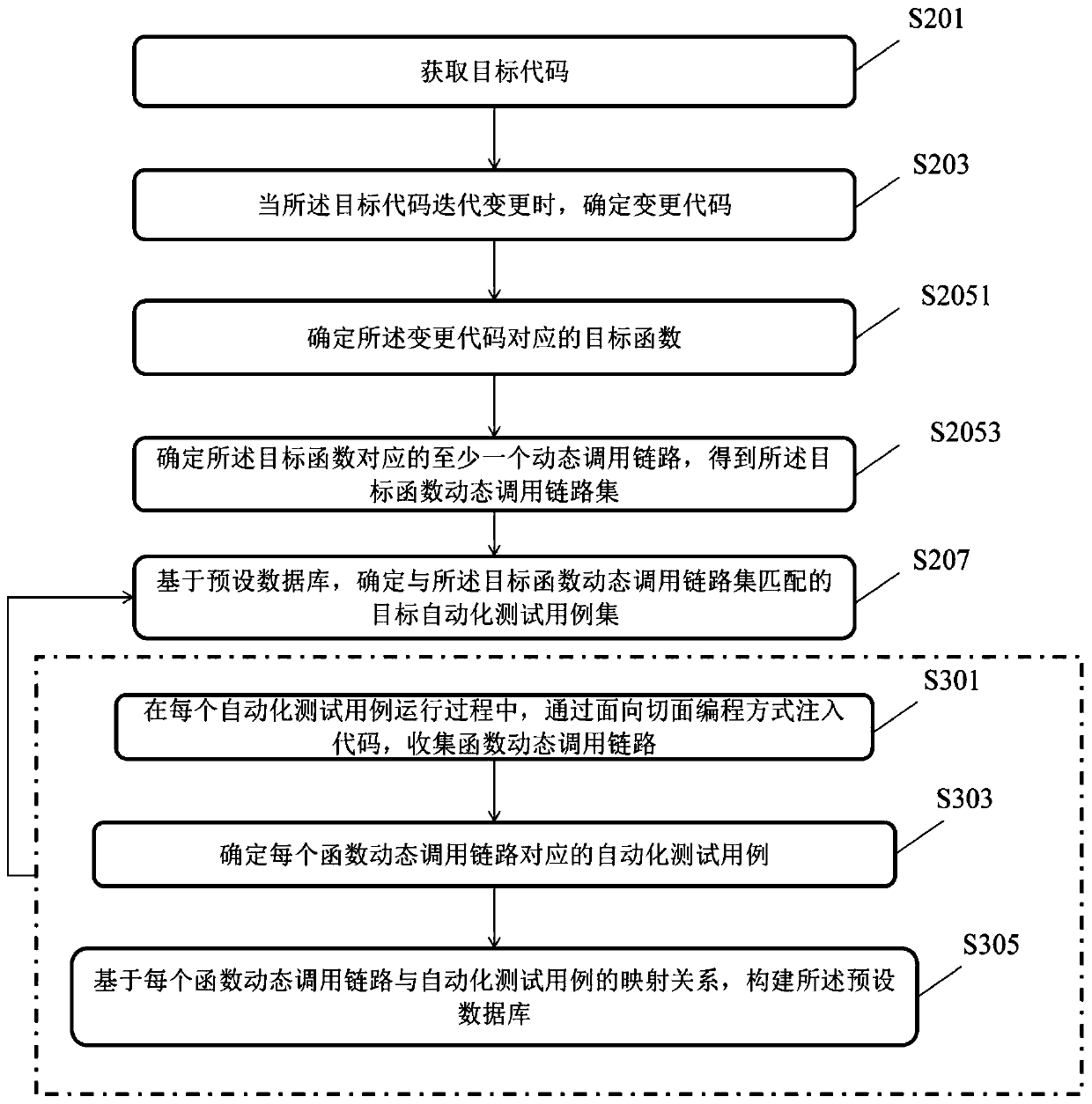
Automatic test case determination method and device, equipment and storage medium
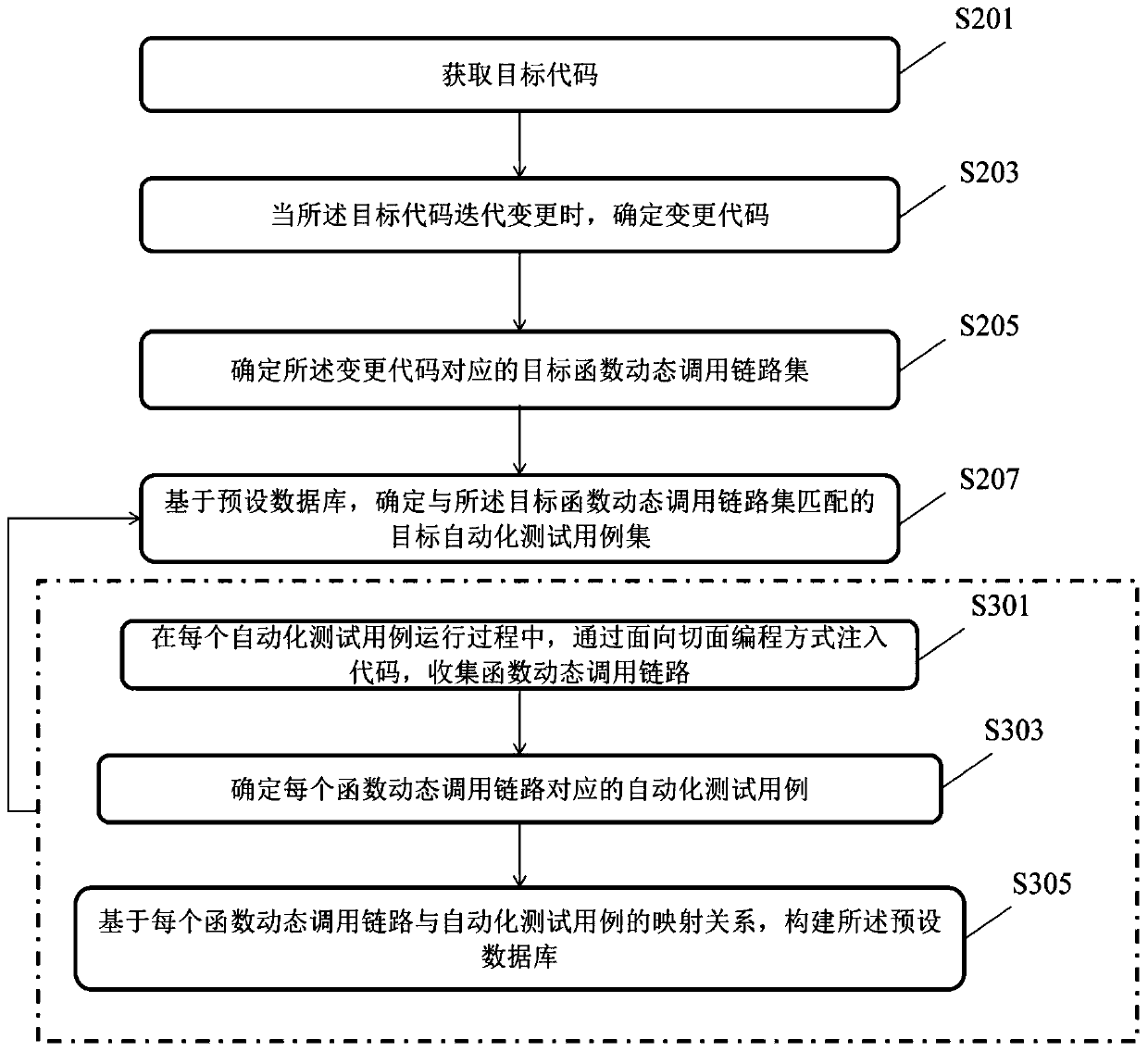
PendingCN111382073AAvoid verification processImprove verification efficiencySoftware testing/debuggingVerificationAutomatic testing
The invention discloses an automated test case determination method and device, equipment and a storage medium. The method comprises the steps of obtaining a target code; when the target code is iteratively changed, determining a change code; determining a target function dynamic call link set corresponding to the change code; determining a target automatic test case set matched with the target function dynamic call link set based on a preset database; the construction method of the preset database comprises the steps that in the running process of each automatic test case, codes are injectedin a section-oriented programming mode, and collecting a function dynamic calling link; determining an automated test case corresponding to each function dynamic call link; and constructing a preset database based on the mapping relationship between each function dynamic call link and the automatic test case. According to the method and the device, the automated test cases influenced by code change can be determined, so that all the automated test cases are prevented from being verified, and the verification efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
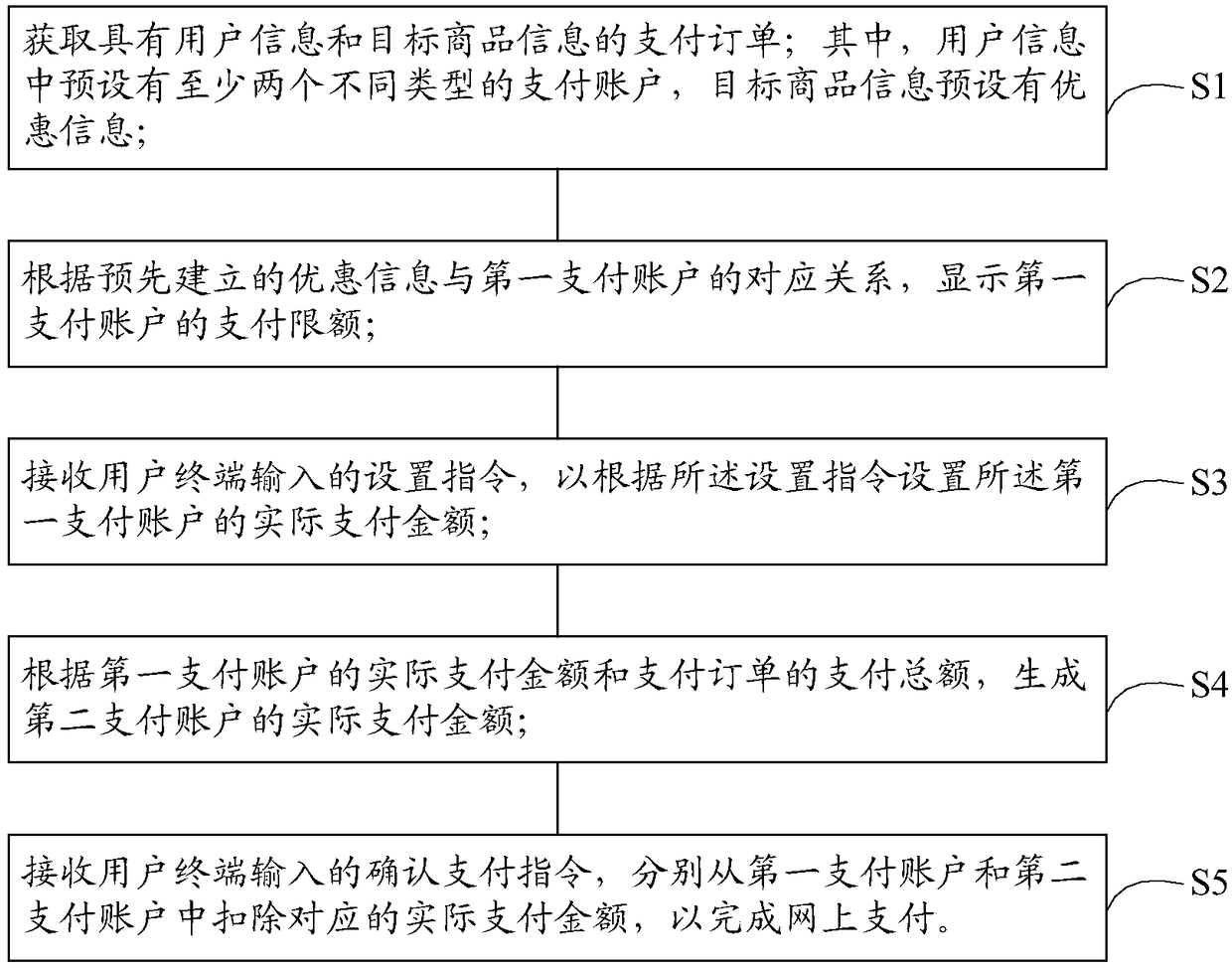
Online payment method and device
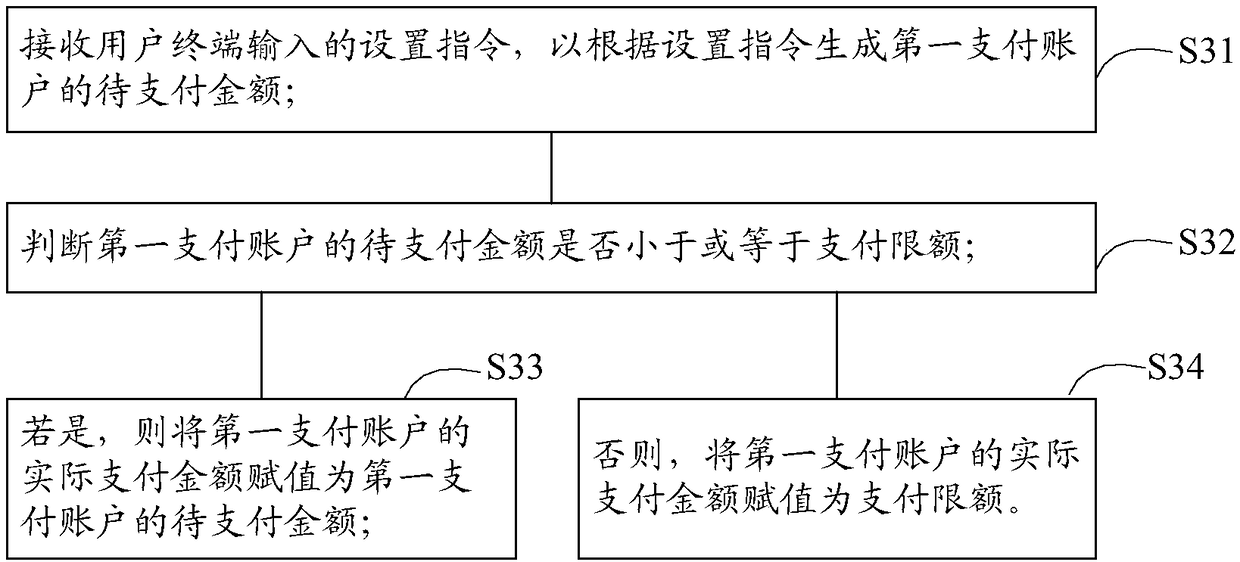
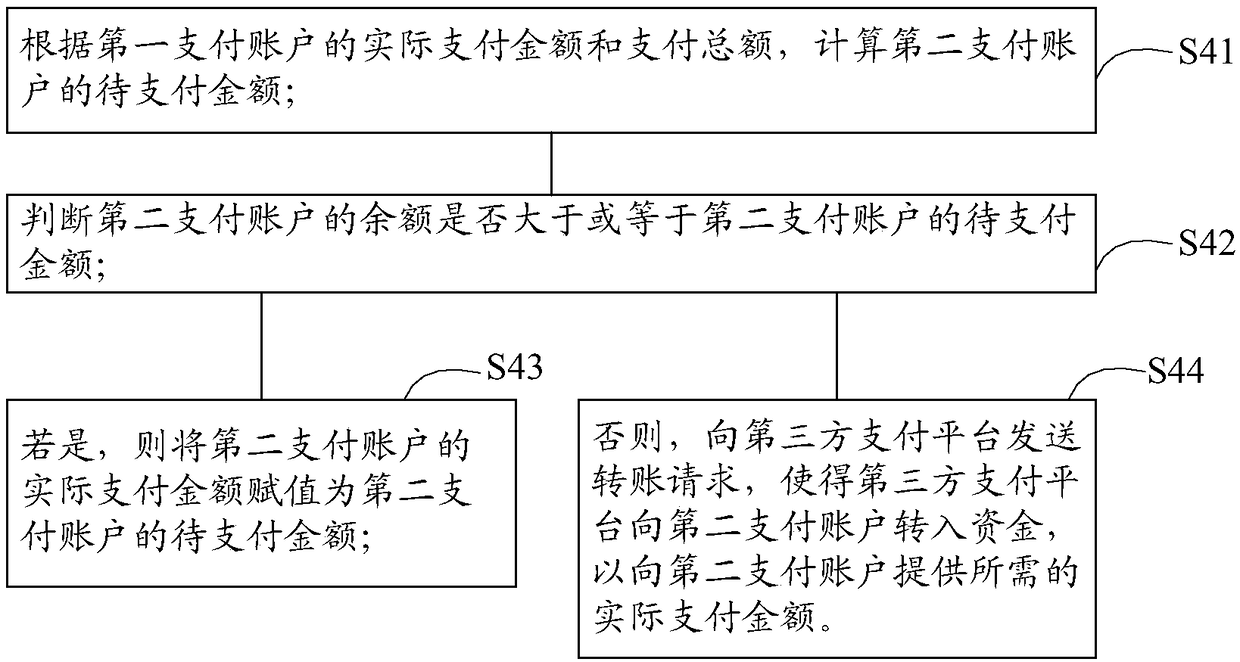
InactiveCN109426951AImprove payment efficiencyImprove user experiencePayment protocolsPayment schemes/modelsPayment orderMonetary Amount
The invention discloses an online payment method, comprising the following steps of obtaining a payment order with user information and target commodity information; displaying a payment limit of thefirst payment account according to a correspondence relationship between the preferential information and the first payment account; receiving a setting instruction inputted by the user terminal to set an actual payment amount of the first payment account according to the setting instruction; generating the actual payment amount of the second payment account according to the actual payment amountof the first payment account and the total payment amount of the payment order; and receiving a confirmation payment instruction inputted by the user terminal, and respectively subtracting the corresponding actual payment amounts from the first payment account and the second payment account to complete online payment. The invention also provides an online payment device. By adopting the online payment method and the device of the invention, the online payment efficiency can be effectively improved, and the user experience can be improved.
Owner:GUANGZHOU YONGZHI INFORMATION TECH CO LTD
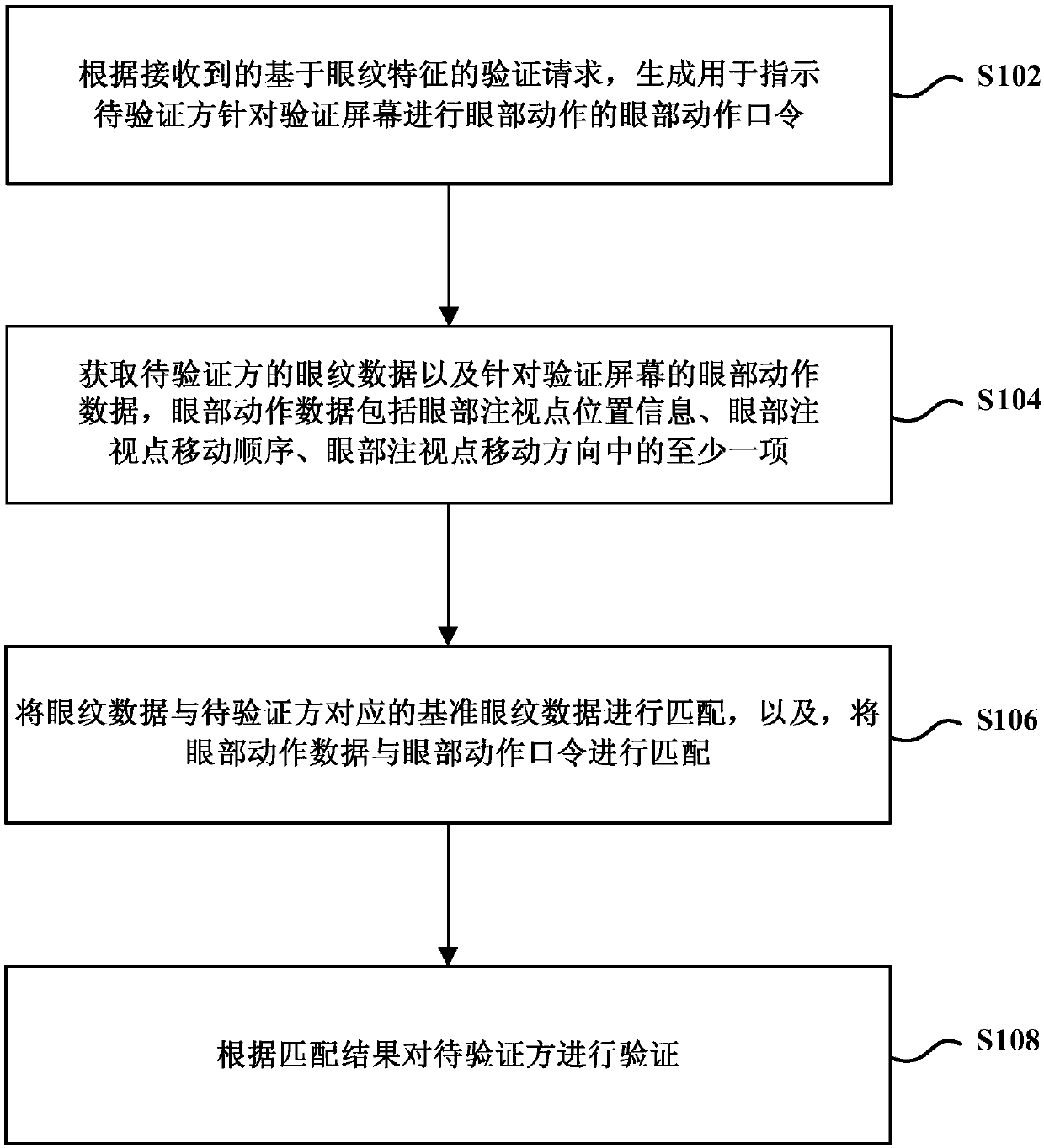
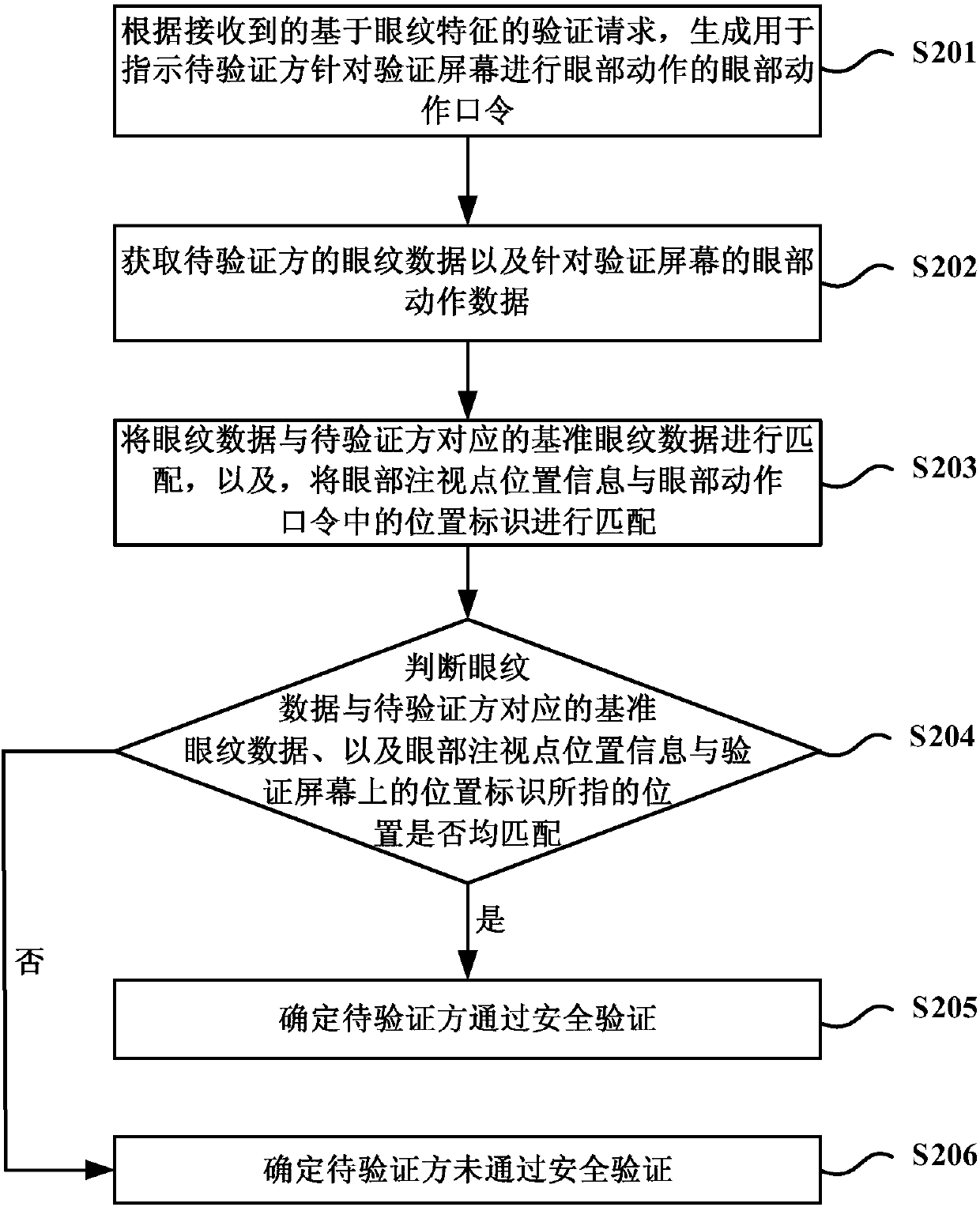
Verifying method and device based on eyeprint features
InactiveCN107590429AImprove accuracyAvoid verification processCharacter and pattern recognitionHigh-definition videoLiving body
The embodiment of the invention discloses a verifying method and a device based on eyeprint features, so as to verifying an eyeprint living body. The method comprises steps: based on a received verifying request based on the eyeprint features, an eye movement command for indicating a to-be-verified side to make an eye movement towards a verifying screen is generated; the eyeprint data of the to-be-verified side and the eye movement data towards the verifying screen are acquired; the eyeprint data and reference eyeprint data corresponding to the to-be-verified side are matched, and the eye movement data and the eye movement command are matched; and according to a match result, the to-be-verified side is verified. According to the technical scheme of the invention, while the eyeprint featureverifying accuracy is improved, the phenomenon that certain users adopt a high-definition video containing a human eye for verifying is also avoided, and verifying on the eyeprint living body is realized.
Owner:ADVANCED NEW TECH CO LTD
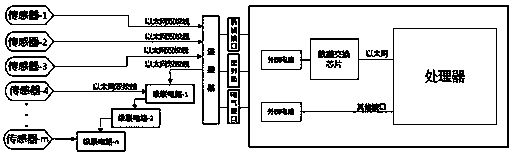
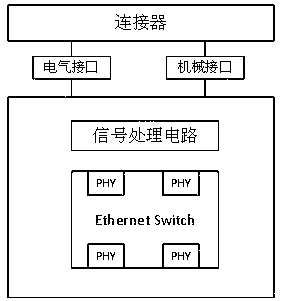
Extensible intelligent driving assistance system
PendingCN108556767AFull scalabilityExpandable and flexibleElectric/fluid circuitHardware structureTime to market
The invention discloses an extensible intelligent driving assistance system. The extensible intelligent driving assistance system comprises an extensible hardware structure and an extensible softwarestructure which is matched with the extensible hardware structure; the extensible hardware structure comprises a processor, a connector, a cascade circuit and at least one sensor; the connector is directly connected with the sensor by using an Ethernet twisted pair and is in transit connection with the sensor by using the cascade circuit; the extensible software structure is embedded in the processor; and the extensible software structure comprises a time synchronization sensor access module, an interface adapting module, a perception algorithm module and a functional logic module. Through adoption of the mode, the extensible intelligent driving assistance system has the advantages that the hardware and the software of the intelligent driving system realize sufficient extendibility, the extensible intelligent driving assistance system can be flexibly applicable to vehicle models with high, medium and low configurations, the system development efficiency is enhanced, the system development quality is improved, the development cost is reduced, and the time-to-market is reduced.
Owner:李洪运
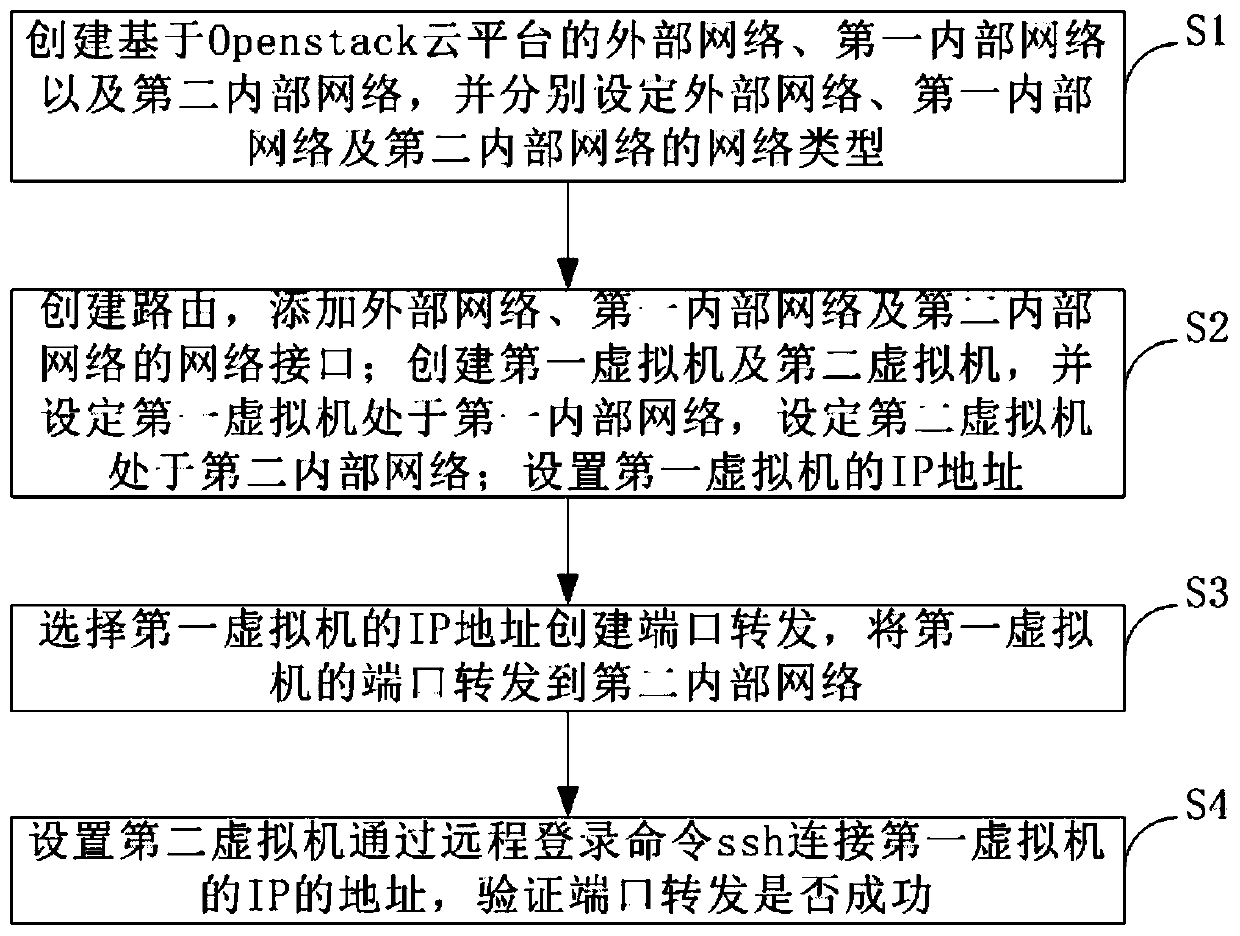
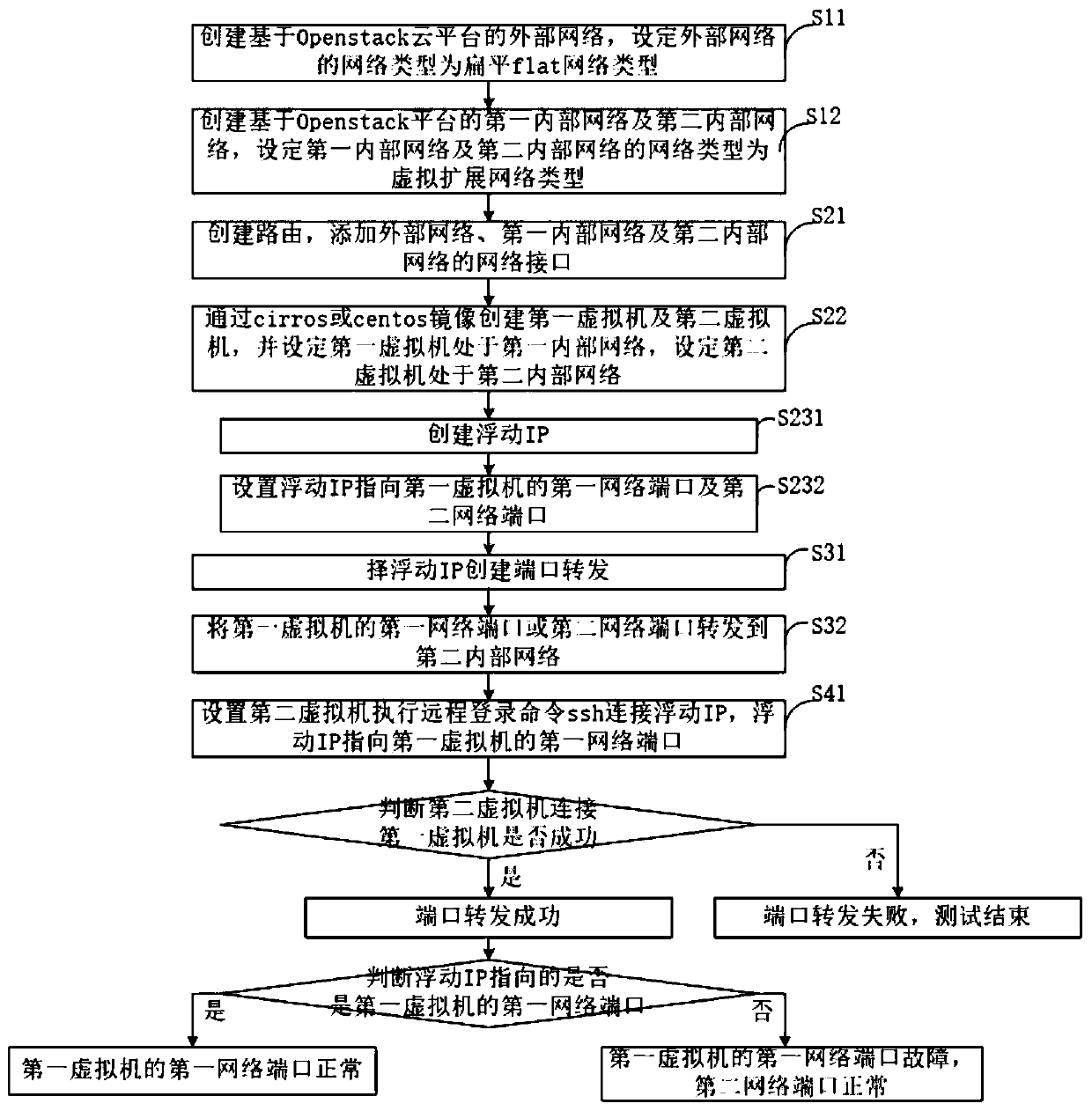
Port forwarding function test method and system based on cloud platform
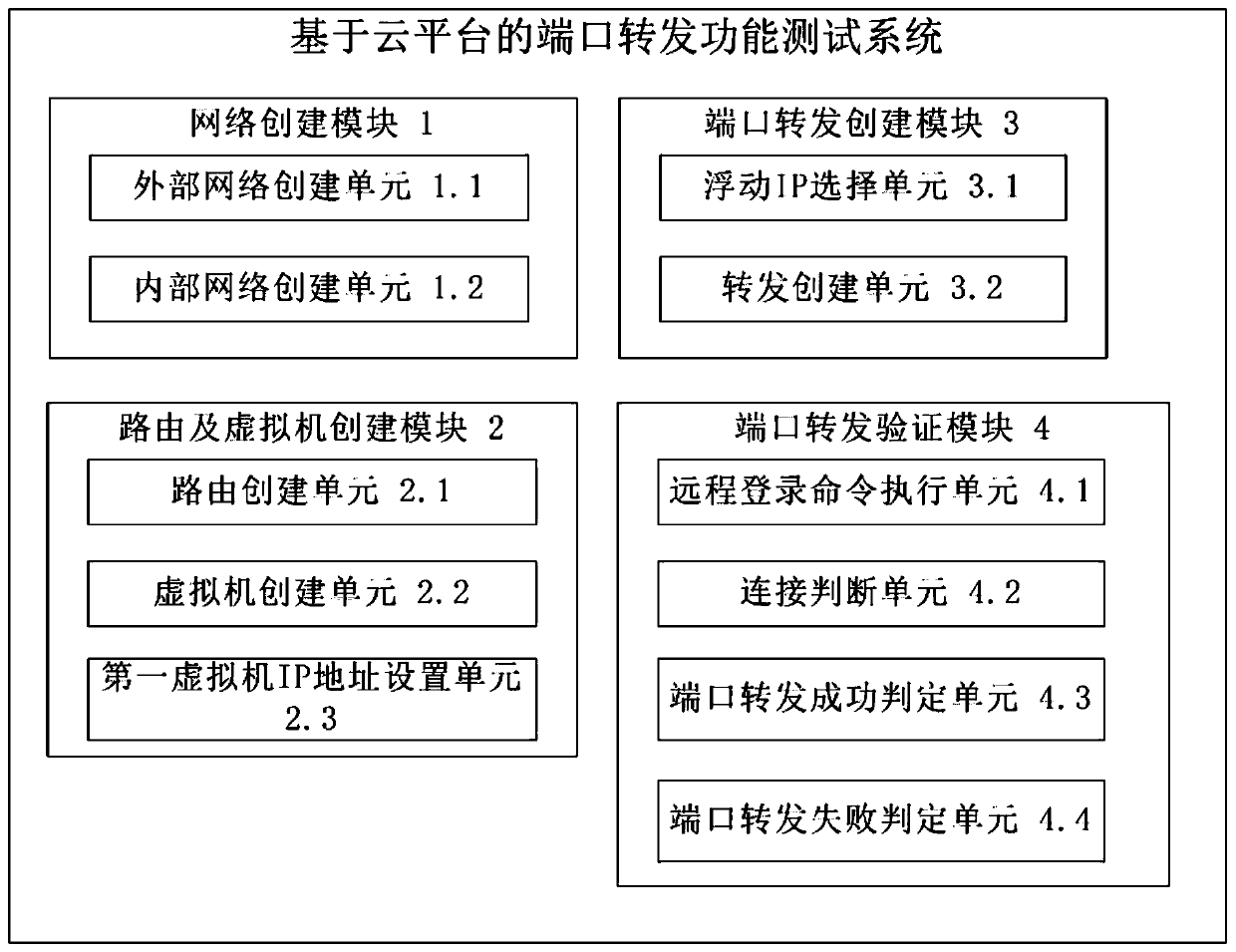
ActiveCN111371636ARealize verificationAvoid verification processData switching networksIp addressEngineering
The invention provides a port forwarding function test method and system based on a cloud platform. The method comprises the following steps: S1, creating an external network, a first internal networkand a second internal network based on an Openstack cloud platform, and respectively setting network types of the external network, the first internal network and the second internal network; S2, creating a route, and adding network interfaces of an external network, a first internal network and a second internal network; creating a first virtual machine and a second virtual machine, setting thefirst virtual machine to be in a first internal network, and setting the second virtual machine to be in a second internal network; setting an IP address of the first virtual machine; S3, selecting the IP address of the first virtual machine to create port forwarding, and forwarding the port of the first virtual machine to a second internal network; S4, setting the second virtual machine to execute the remote login command ssh to connect the address of the IP of the first virtual machine, and verifying whether port forwarding is successful or not.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Network transaction platform account control method and device, and server
ActiveCN103873435AFlexible controlFlexible managementDigital data authenticationBuying/selling/leasing transactionsComputer scienceDatabase
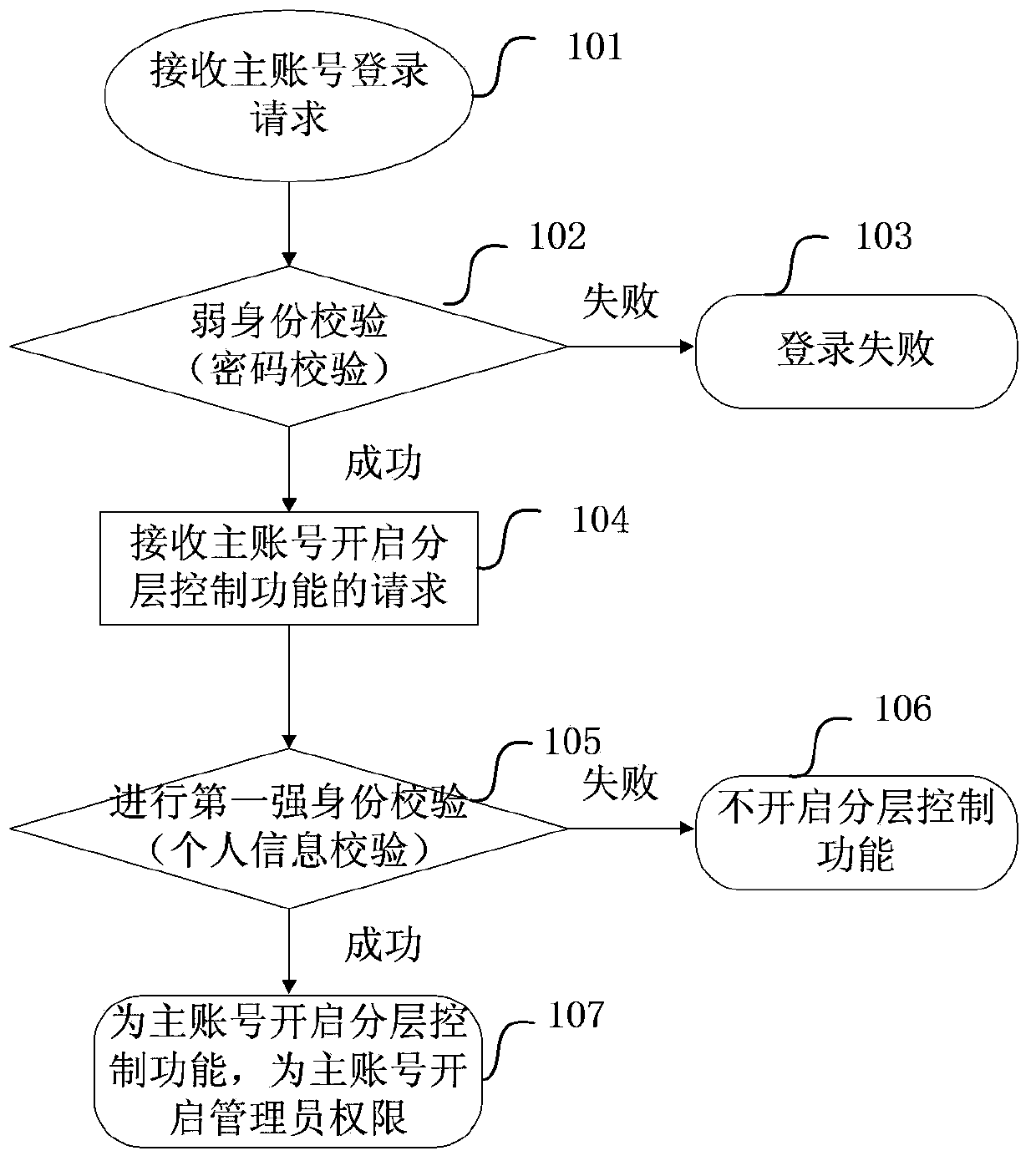
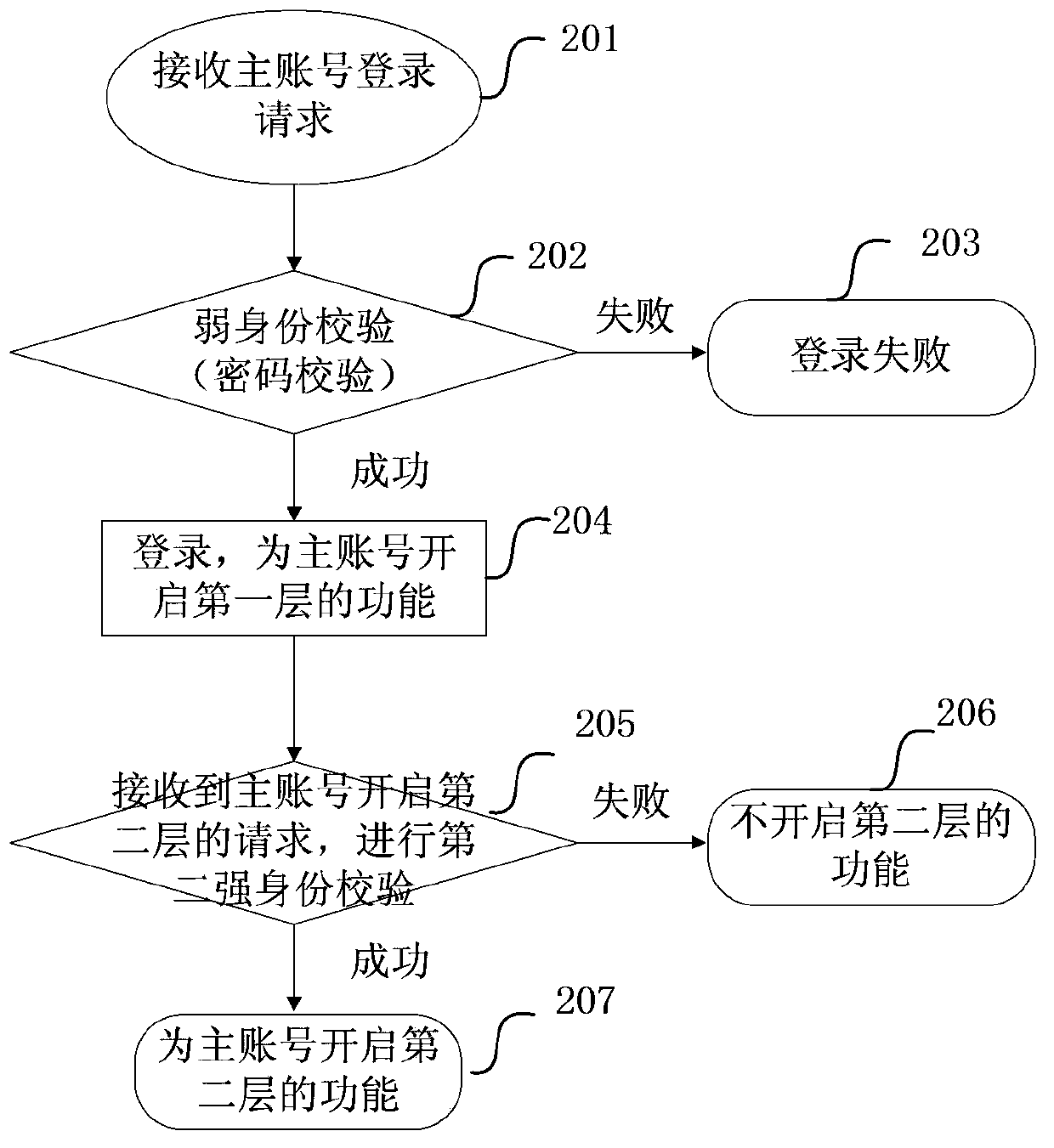
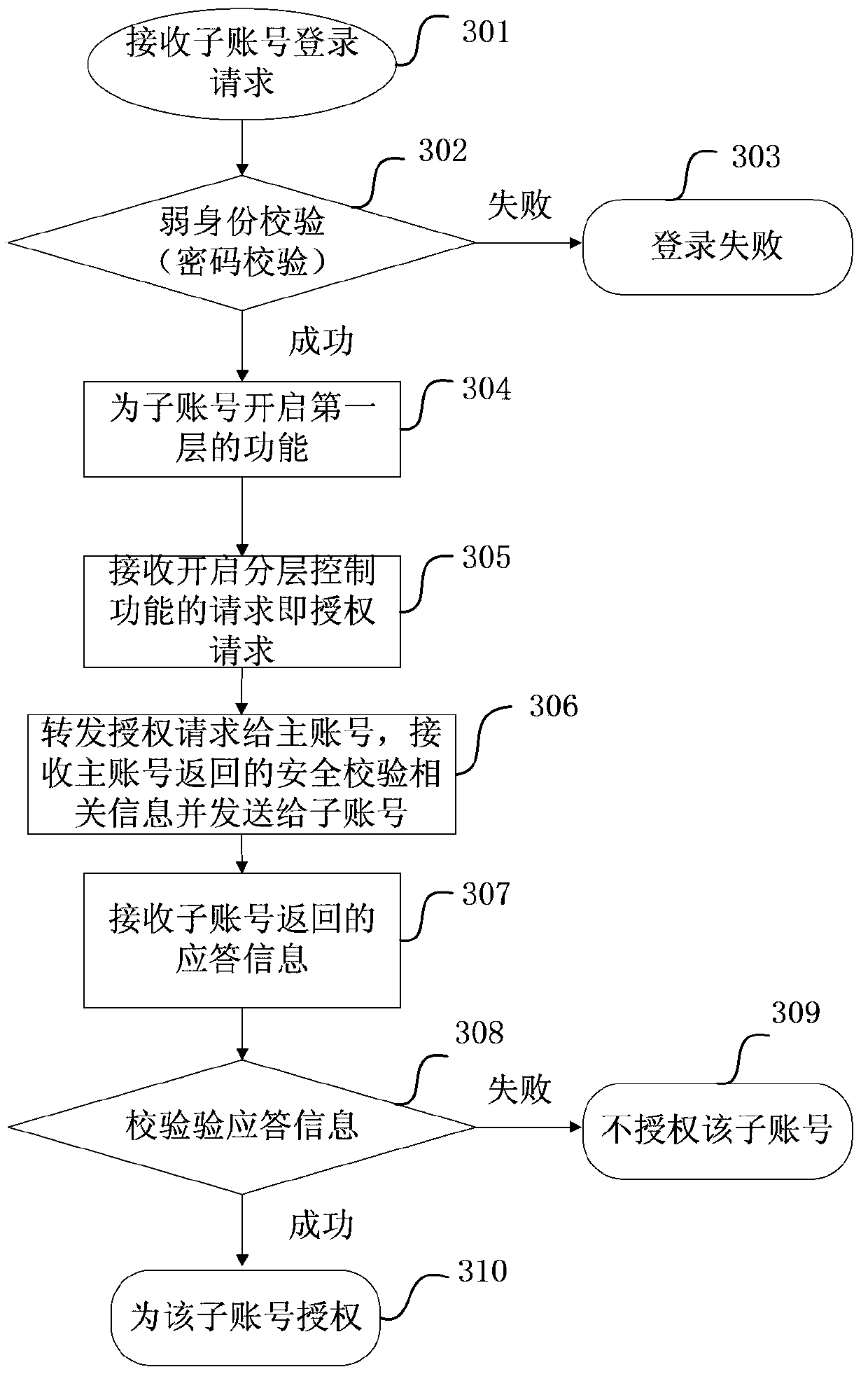
The invention provides a network transaction platform account control method which includes: providing a layered control function for a user account and dividing the function which is provided to the user account into at least two layers, wherein each layer includes one or more functions and each layer is corresponding to a safety verification; starting the layered control function or performing authentication for the user account; when at follow-up login of the user account, after a layer starting request of the user account is received, if the user account passes the safety verification corresponding to a layer which is requested to be opened, starting different functions of the layer which is requested by the user account to be opened; and maintaining the start state of the layer which is already started until the user account exists a system or closing the layer which is already started for the user account. The invention also provides a network transaction platform control device and a server.
Owner:ALIBABA GRP HLDG LTD
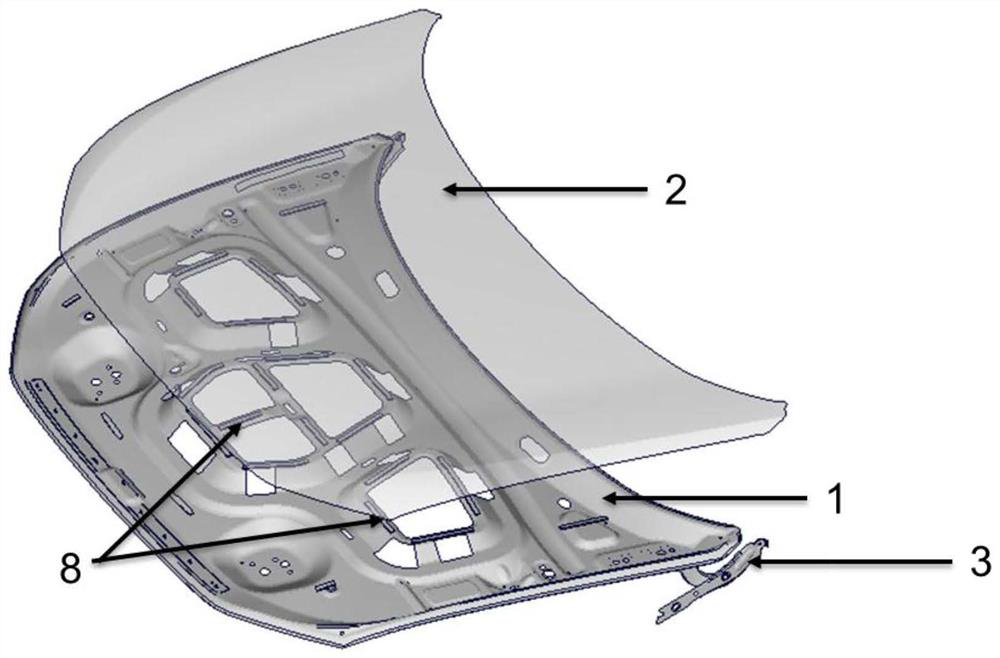
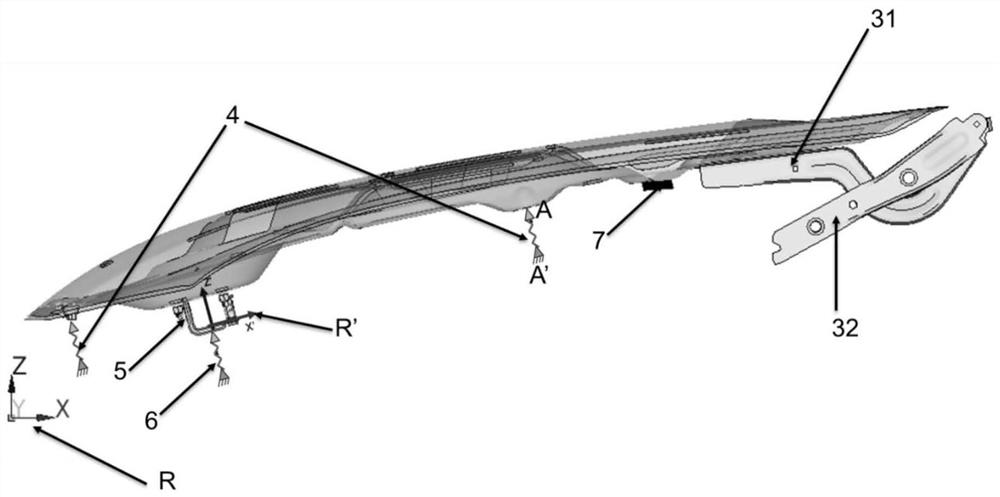
Engine hood jitter simulation analysis method based on air pressure load
ActiveCN111695236AImprove accuracyAvoid subjective evaluationGeometric CADSustainable transportationSimulationAutomotive engine
The invention discloses an engine hood jitter simulation analysis method based on an air pressure load. A model is built based on finite element calculation software; an accurate finite element modelof the automobile engine hood is established; air pressure distribution of the inner side and the outer side of an engine hood outer plate is extracted; the unit pressure is projected on all units ofthe engine hood outer plate in a unit pressure mapping manner; the air pressure load is used as the air pressure load of the engine hood jitter simulation analysis, the operation accuracy of the modelis greatly improved, the experiment result can be accurately predicted, whether the engine hood meets the jitter performance design requirement or not is judged, the cost of a sample vehicle is saved, and the research and development efficiency of the vehicle is greatly improved. By the adoption of the engine hood jitter simulation analysis method based on the air pressure load, various engine hood design schemes can be verified efficiently with low cost through a finite element simulation method, and therefore various virtual schemes can be optimized.
Owner:SAIC VOLKSWAGEN AUTOMOTIVE CO LTD
Anti-internal-crawling access control method oriented to data property right protection
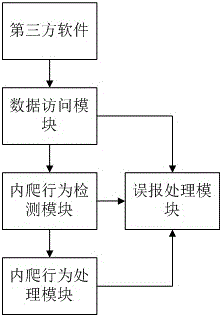
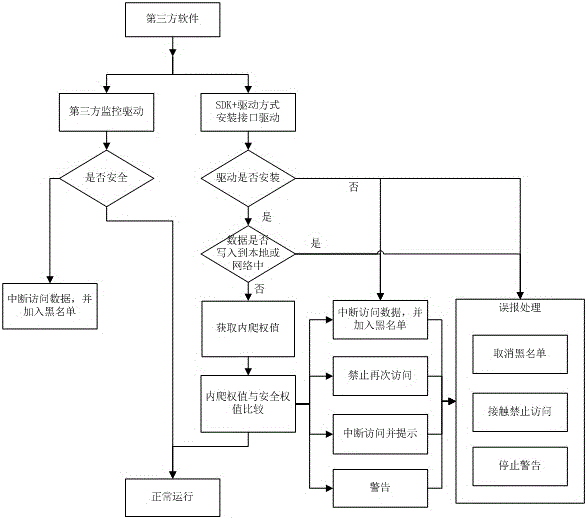
ActiveCN105912934AAvoid verification processImprove efficiencyPlatform integrity maintainanceThird partyInternet privacy
The present invention discloses an anti-internal-crawling access control method oriented to data property right protection. The method comprises: by loading an access interface for third-party software and tracking back used data of third-party software, determining an internal crawling behavior of the third-party software; detecting a data volume, access duration, an access frequency when the third-party software uses data; by means of a Naive Bayes algorithm, obtaining an internal crawling data weight, an internal crawling time weight, and an internal crawling frequency weight of the third-party software, so as to further obtain an internal crawling weight of the third-party software; comparing the internal crawling weight with a security weight; and performing targeted processing according to a risk magnitude of the internal crawling behavior of the third-party software, and providing third-party monitoring and error reporting processing. The method ensures security of data, improves the monitoring efficiency of the third-party software, and has relatively high classification accuracy and operation efficiency.
Owner:MR RAY CHENGDU TECH CO LTD
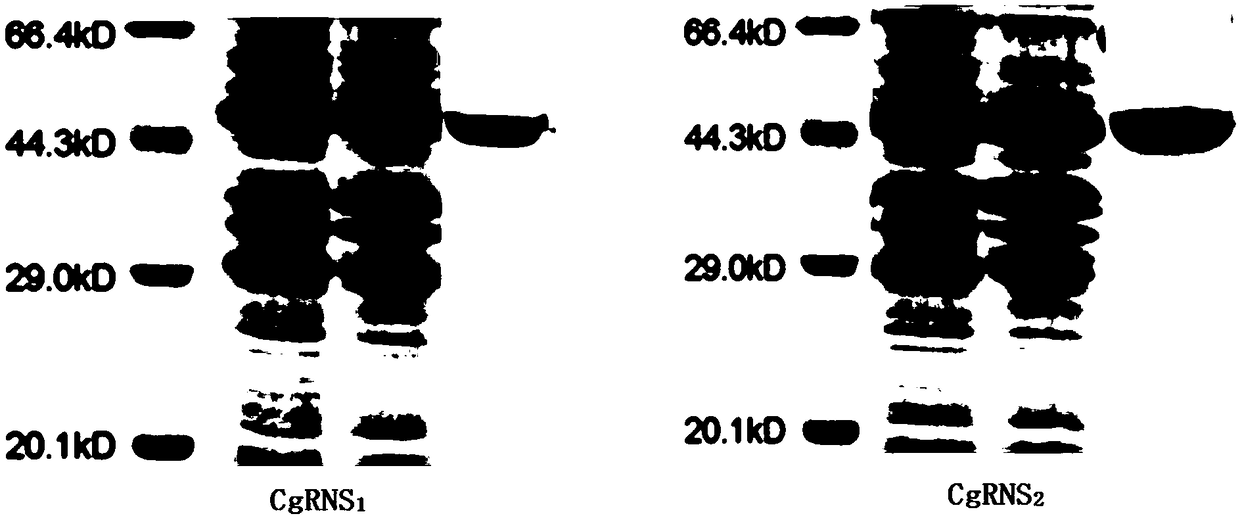
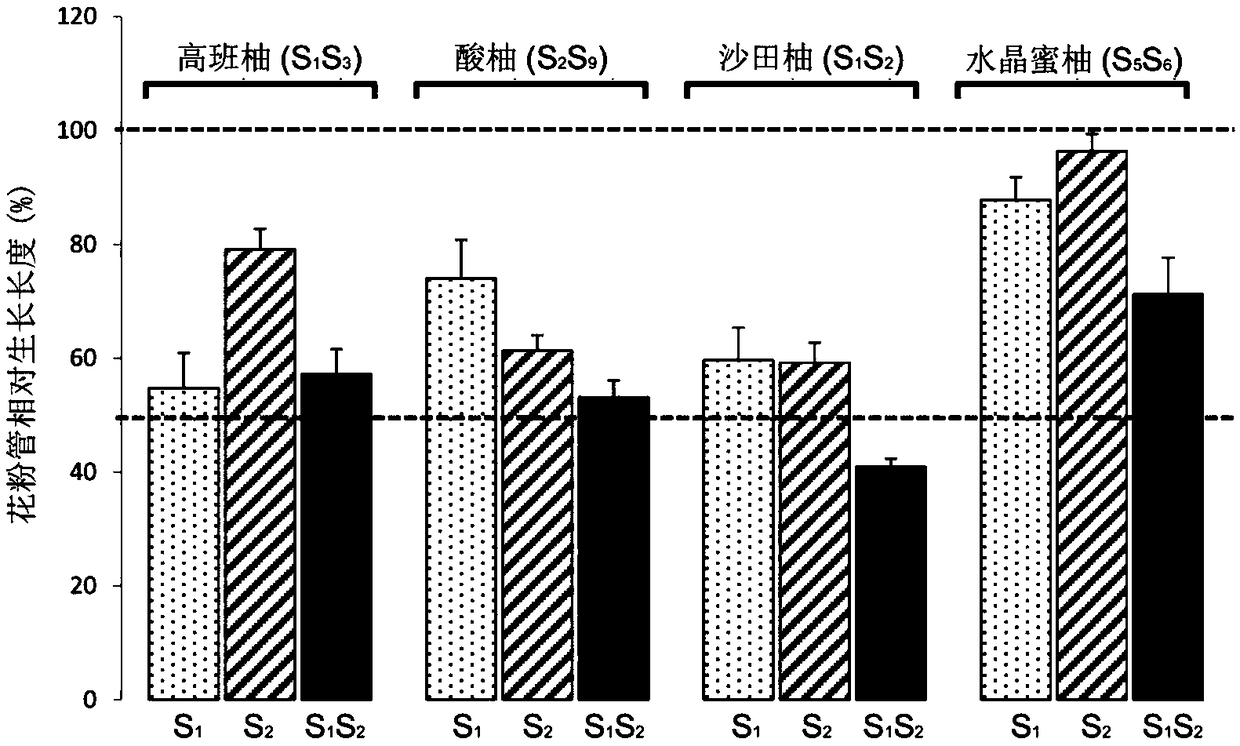
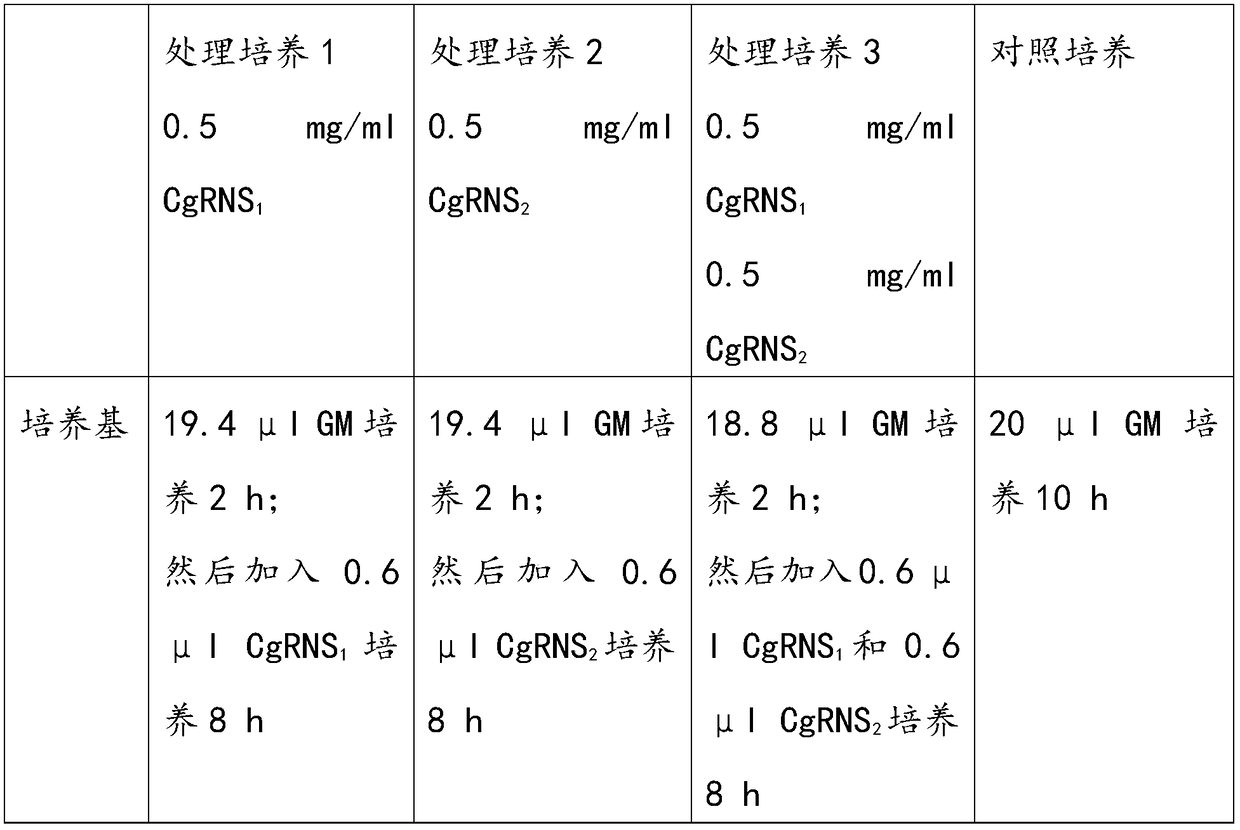
Method for in-vitro verification of self-incompatibility function of S-RNase in citrus and pomelo
The invention relates to a method for in-vitro verification of self-incompatibility function of S-RNase in citrus and pomelo. The method comprises that follow steps: step 1, obtaining an S-RNase protein; 2, collecting pollen from that donor plant; step 3: treating pollen obtained in the step 2 with S-RNase protein obtained in the step 1, and measuring the effect of the treatment of S-RNase proteinon the pollen germination pollen tube. By adopting the method of the invention, the self-incompatibility style gene of citrus can be rapidly verified in an in vitro culture mode, and the proper pollen can be treated with a recombinant protein with an appropriate concentration, which can cause a self-compatibility or incompatibility reaction, thereby avoiding the problem of transgenic verificationof the citrus S gene.
Owner:HUAZHONG AGRI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com