Patents
Literature
32results about How to "Safety verification" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
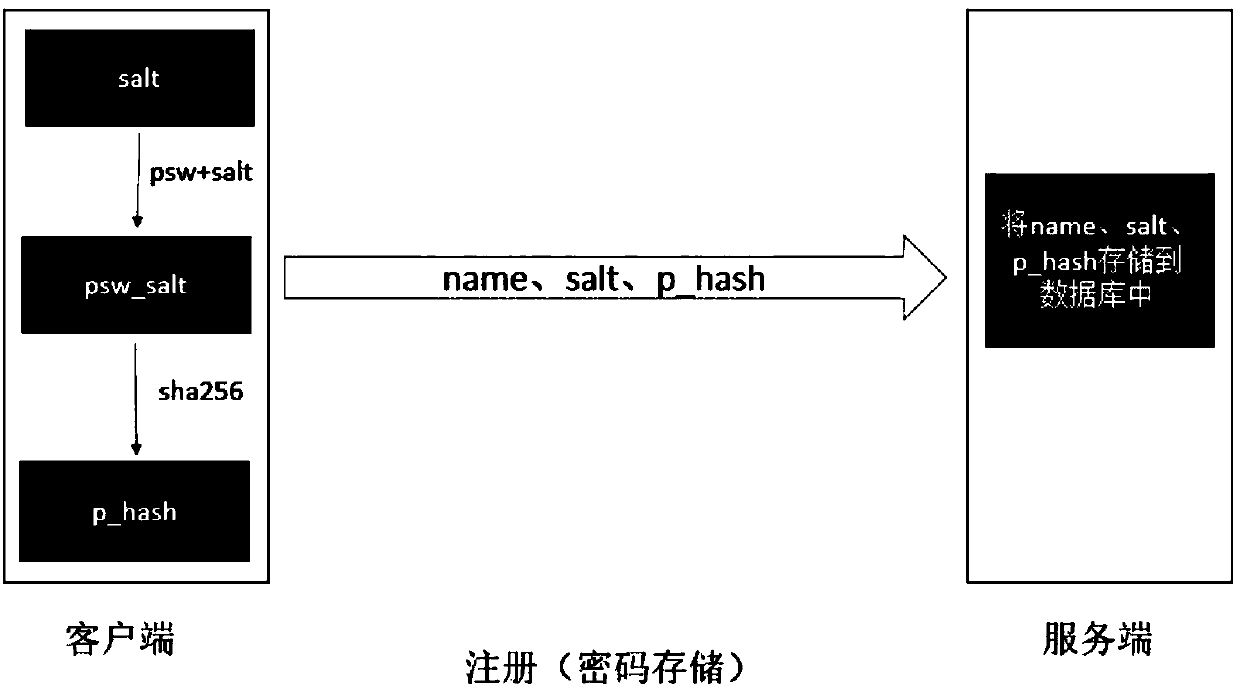
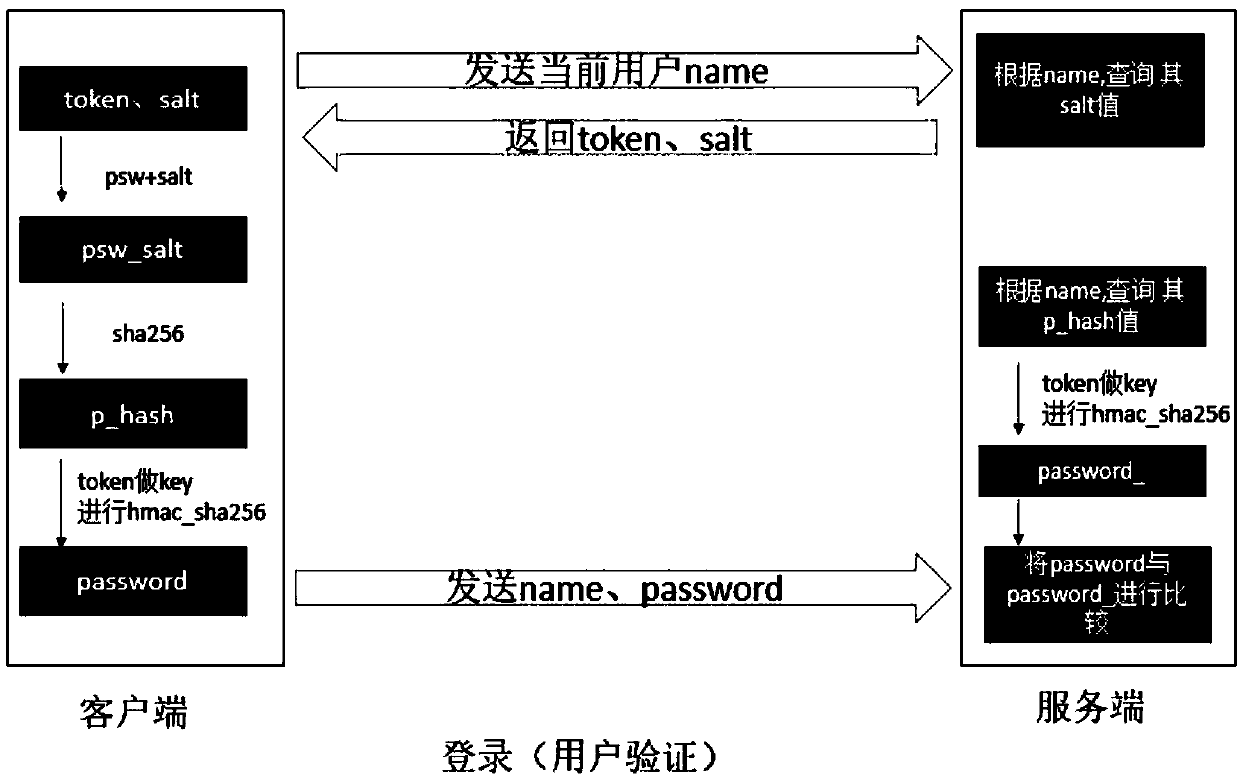
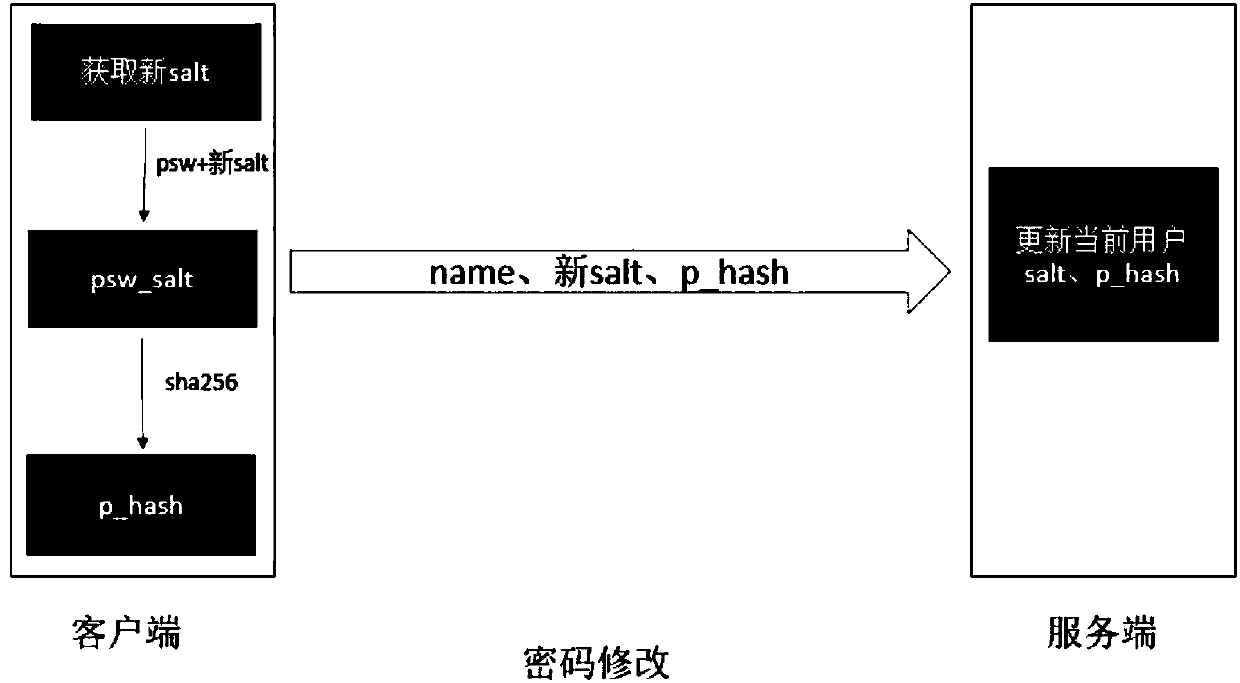
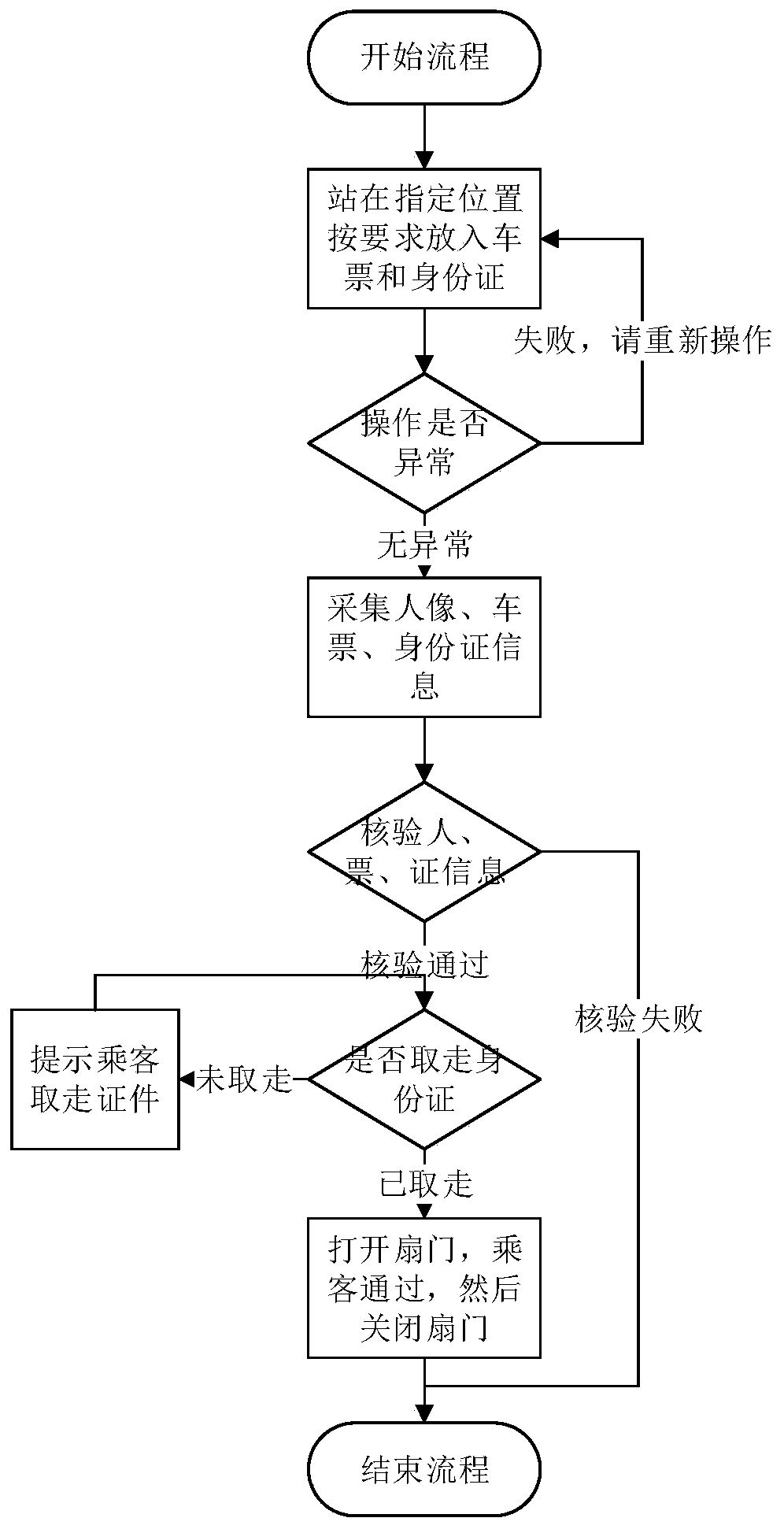
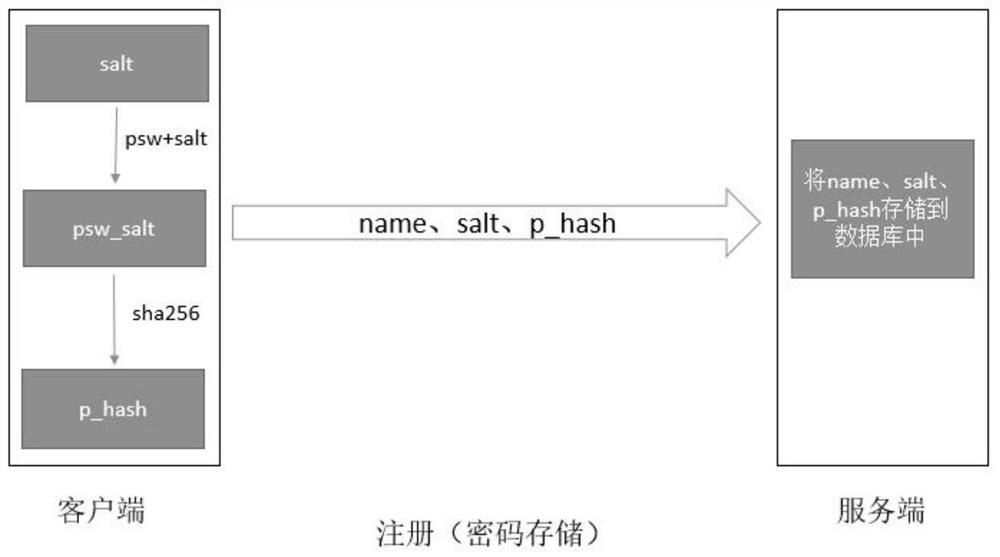
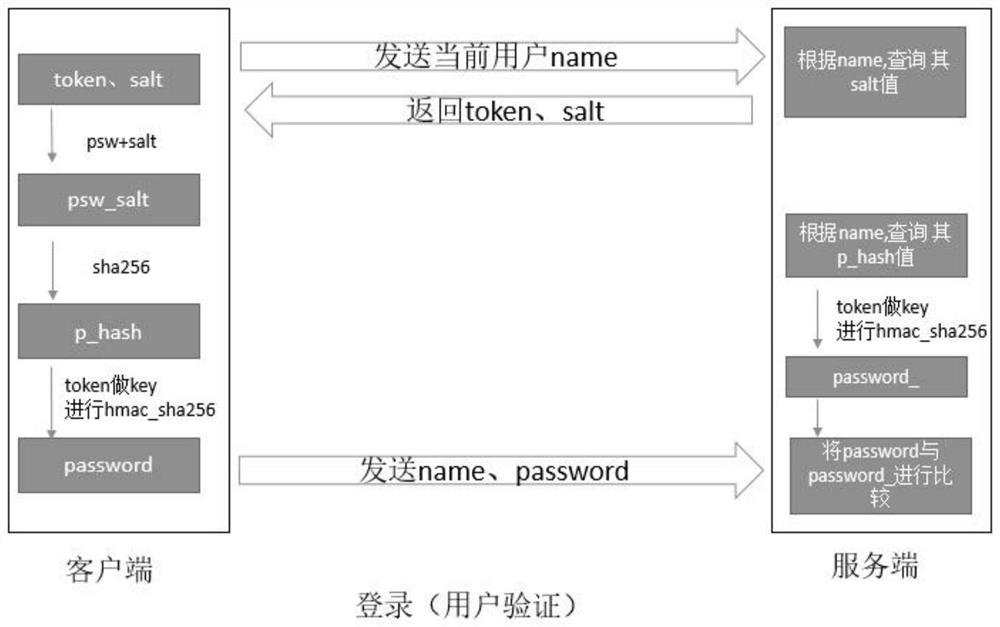
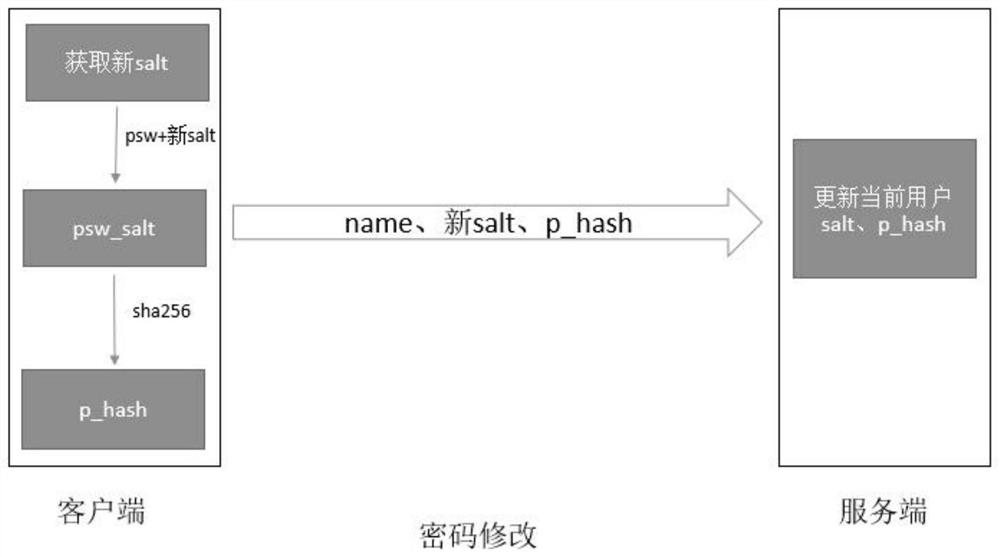
Secure password storage and verification method and device
ActiveCN107911343ASafe storageSafety verificationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesValidation methodsPassword hashing
The invention provides a secure password storage and verification method and device. When a password is stored, Salt is added into the password and the password is encrypted by a hash algorithm; a hash value of the password is stored into a server side; when a user logs in the server to carry out password verification, the server side generates token, and secondary encryption is carried out on thepassword hash value stored by the server side and a password hash value for logging in of the user by using the token as a key; and then comparison and verification are carried out. Therefore, the security of the password of the user during the storage and verification processes is improved.
Owner:SHENZHEN INFINOVA
Multi-mode biological characteristic authentication device and system
ActiveCN104978510ASafety verificationAccurate verificationDigital data authenticationMatching and classificationComputer visionHuman body
The present invention discloses a multi-mode biological characteristic authentication device which is provided with a first fingerprint sensing module, a second fingerprint sensing module, a palm print sensing module, an information receiving unit and a prompting unit. The first fingerprint sensing module is used for acquiring first fingerprint information of an index finger, a middle finger, a ring finger and / or a little finger of a user; the second fingerprint sensing module is used for acquiring fingerprint information of a thumb of the user; the palm print sensing module is used for acquiring palm print information of the user; the information receiving unit is used for receiving the first fingerprint information from the first fingerprint sensing module, the second fingerprint information from the second fingerprint sensing module and the palm print information from the palm print sensing module and determining whether the information is synchronously and correctly acquired; and if the information is synchronously and correctly acquired, correct acquisition prompt information is sent out by the prompting unit. According to the present invention, the identity can be authenticated better; reliability is high; difficulty and complexity in counterfeiting of biological characteristics of a human body are improved; and safety of the system is improved.
Owner:河南华辰智控技术有限公司
Voice identifying code system and implementation method of the same
InactiveCN106504745AUser Experience OptimizationSecurity security issuesKey distribution for secure communicationSpeech synthesisMalwareComputer hardware
The invention provides a voice identifying code system and an implementation method of the same. The voice identifying code system is characterized in that a voice identifying code mode is used to perform authentication; the voice identifying code can more clearly give a prompt about the specific business content operated by a user to the user, and preferably complement a short message identifying code verification mode; and the short message identifying code + voice identifying code authentication mode enables the verification process of the user to be more safe, easy and efficient, so that the user experience can be optimized. The voice identifying code has the advantages: 1) safety: using the voice identifying code can prevent malicious software intercepting and capturing short messages so as to avoid the safe problem; 2) efficiency: the voice identifying code is high in the delivery rate, and is not easy to be intercepted by a mobile phone; and 3) selectivity: when the short message identifying code cannot be delivered timely, the user can quickly complete business through the voice identifying code.
Owner:广州市讯飞樽鸿信息技术有限公司
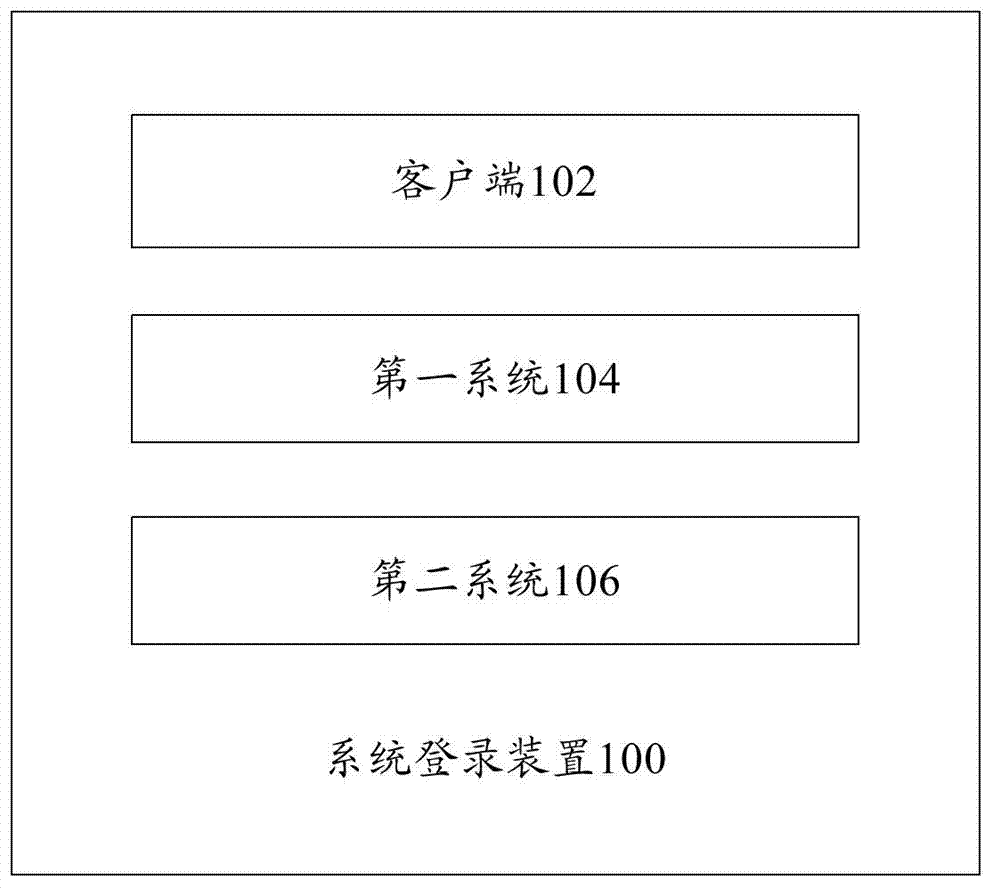
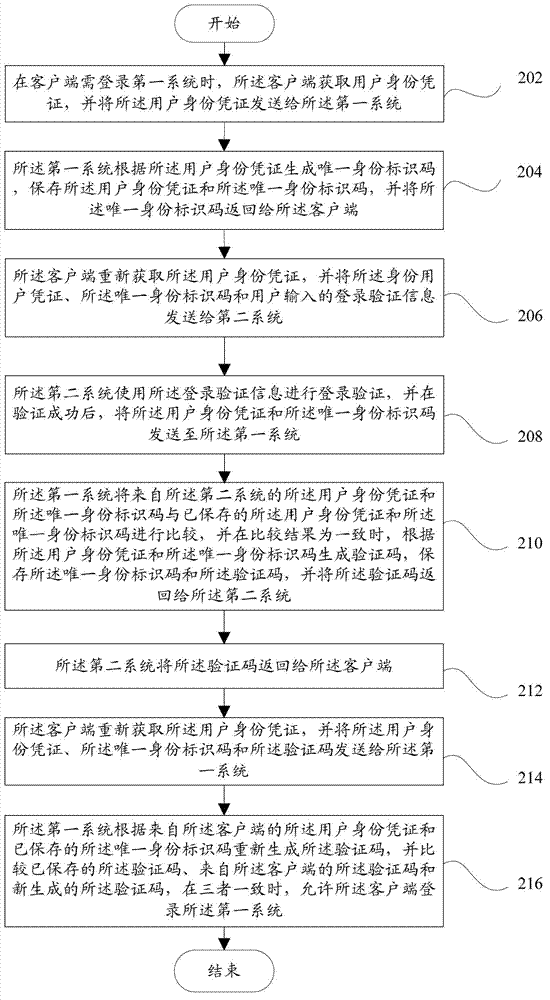
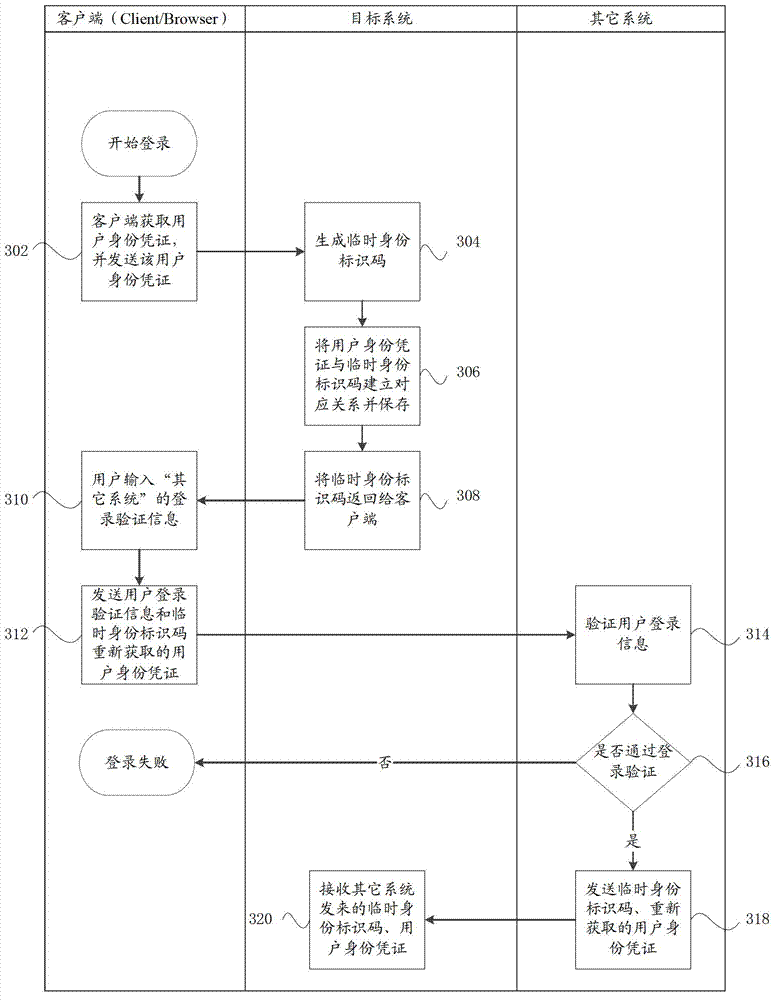
System login device and system login method
ActiveCN102868702ALightweight identity informationLightweight authenticationTransmissionUser authenticationClient-side
The invention provides a system login device and a system login method, wherein the device comprises a client-side, a first system and a second system. By means of the system login device and the method, users only need to input identity authentication information of another system during login of a target system to realize safe login of the target system. Based on safety, the target system is not provided with any user identity authentication information, and data including user identity authentication information and the like of other systems do not go through or are not stored in the target system. Users use temporary identity identification code to login the target system, and the fact of bypassing user identity authentication of other systems and using counterfeit information to directly login the target system is rejected.
Owner:YONYOU NETWORK TECH
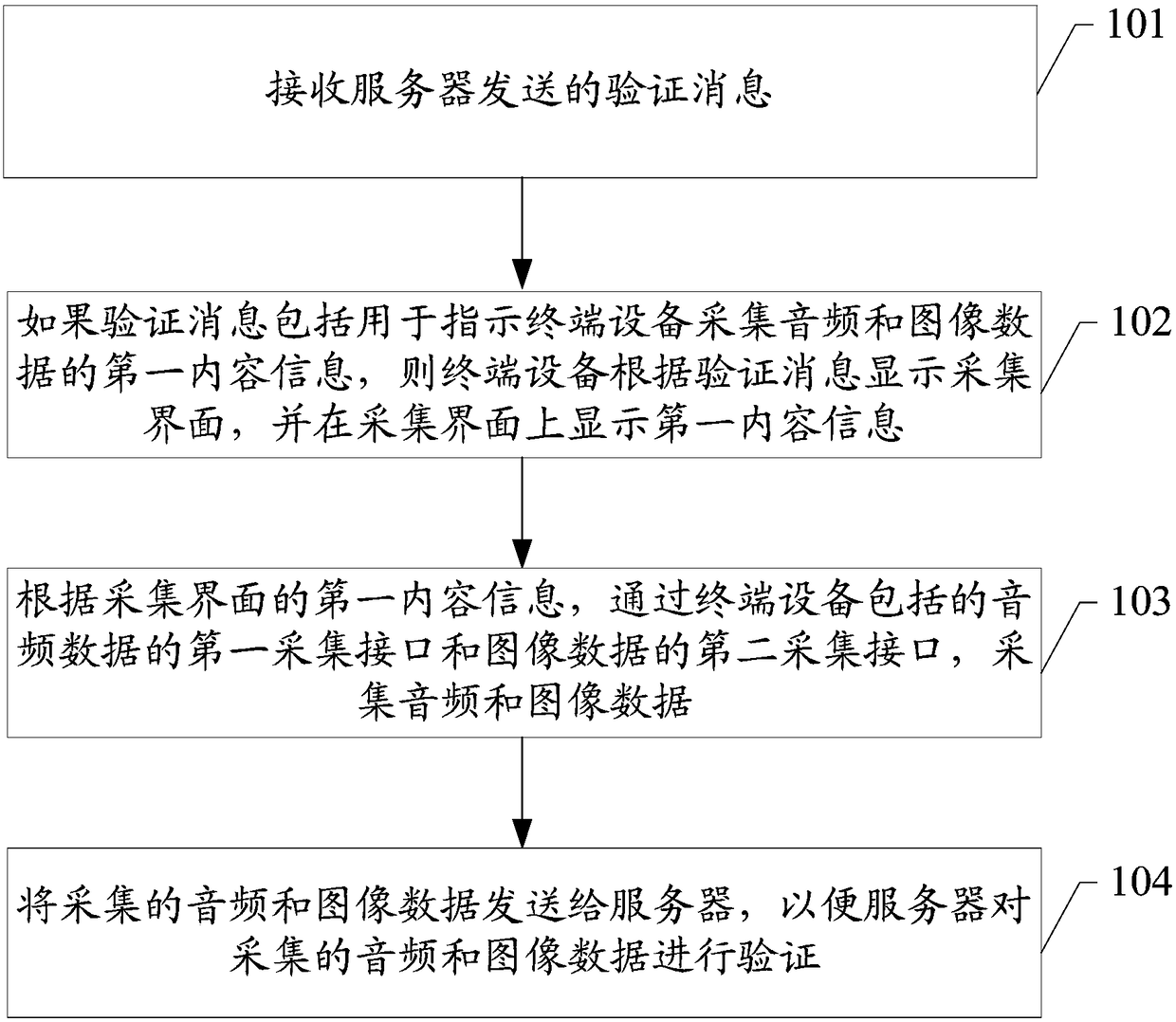
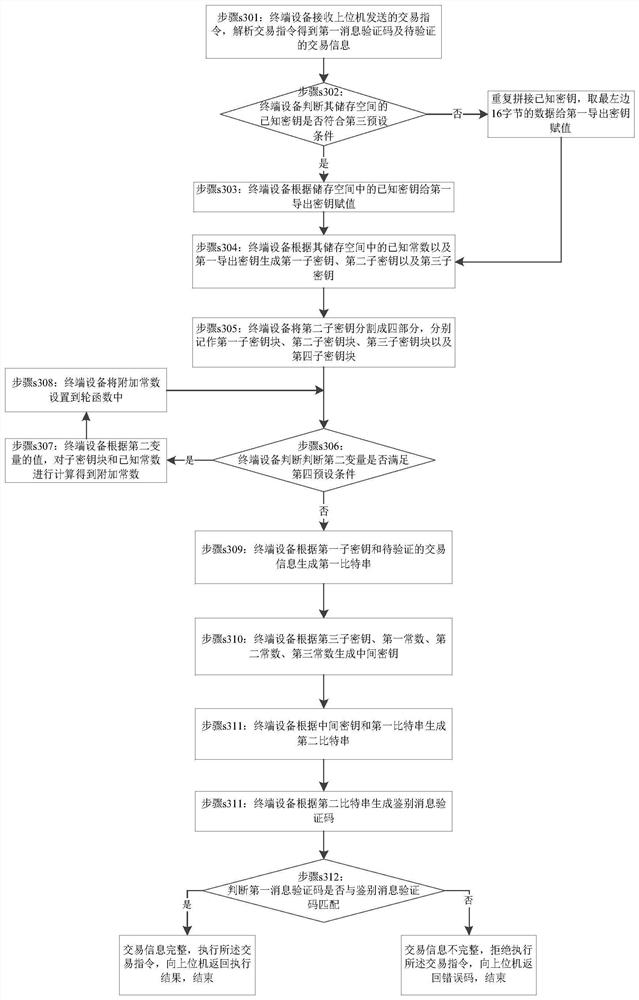
Identity verification method and device, and storage medium
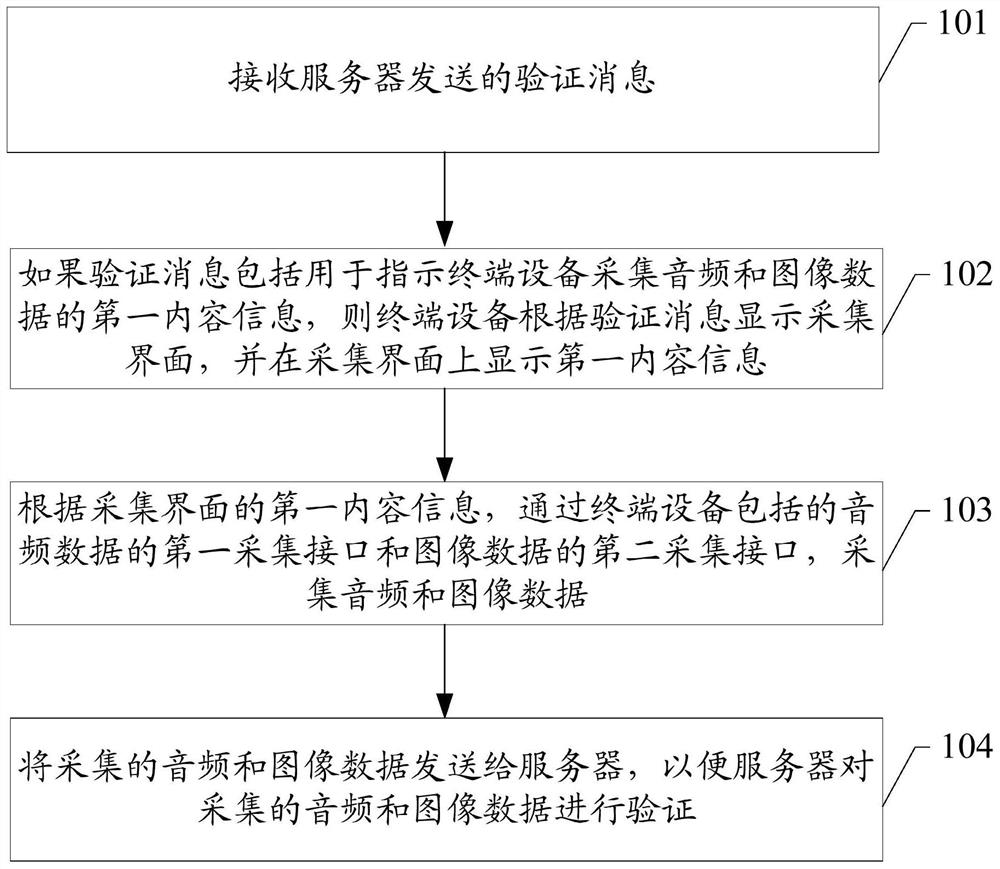
The embodiments of the invention disclose an identity verification method and a device, and a storage medium which are applied to the information processing technology field. When terminal equipment in a system based on user login initiates a certain type of request, a server sends a verification message including first content information to the terminal equipment so as to notify an operation user to collect audio and image data. The user needs to use the terminal equipment to collect the audio and image data and transmits to the server for verification. If the audio and image data passes theverification, the identity of the operation user of the terminal equipment passes the verification. Through the collected audio and image data, whether the user operating the terminal equipment is avalid user can be verified and a verification process is safe. And when the collected audio and image data corresponds to the first content information, the verification can be passed so that other users can be prevented from using pre-recorded audio and image data of the valid user to carry out verification, and safety of terminal equipment operation is increased.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Portable multi-mode biological feature identity recognition device and system
InactiveCN105138877AIdentify securitySafety verificationDigital data authenticationAcquiring/reconising fingerprints/palmprintsPattern recognitionIdentity recognition
The invention discloses a portable multi-mode biological feature identity recognition device, comprising: a first fingerprint sensing region arranged on the upper surface and used for acquiring first fingerprint information of an index finger, a middle finger, a ring finger and / or a little finger of a user; a second fingerprint sensing region arranged on the lower surface and used for acquiring fingerprint information of a thumb of the user; an iris sensing region positioned at the front end surface and used for acquiring iris information of the user; and an information receiving unit used for receiving the first fingerprint information from the first fingerprint sensing region, the second fingerprint information from the second fingerprint sensing region and the iris information from the iris sensing region, confirming whether the information is synchronously and correctly acquired, and if so, sending out prompt information of correct acquisition through a prompt unit. The device is convenient to operate and carry, can improve working efficiency and accuracy of acquiring multi-mode biological information in one time, and can conveniently protect personal safety of acquisition and inspection personnel.
Owner:DAFENG YUNRUN TECH
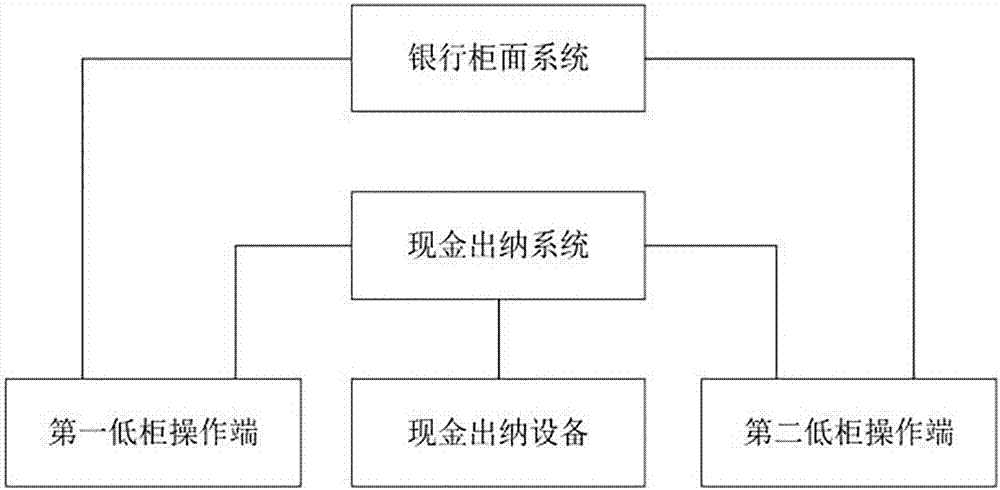
Cash business processing method and system based on accounting and cashier separation
The invention discloses a cash business processing method and a system based on accounting and cashier separation. The method includes the following steps: (1) receiving a cash business request of a user; generating account transaction information and cashier operation information according to the cash business request, wherein the cashier operation information has an associated transaction verification certificate attached; and reading the cashier operation information and verifying the transaction verification certificate, and performing a cash withdrawal operation if the transaction verification certificate passes verification; and (2) acquiring a cash depositing operation of a customer; generating cashier operation information according to the cash depositing operation, wherein the cashier operation information has an associated transaction verification certificate attached; and reading the cashier operation information and verifying the transaction verification certificate, and generating account transaction information if the transaction verification certificate passes verification. Lower counters can share one piece of cash processing equipment to handle cash business under the premise that the existing low-counter system of banks is not transformed.
Owner:南京合荣欣业金融软件有限公司
Real-name verification gate and application method thereof
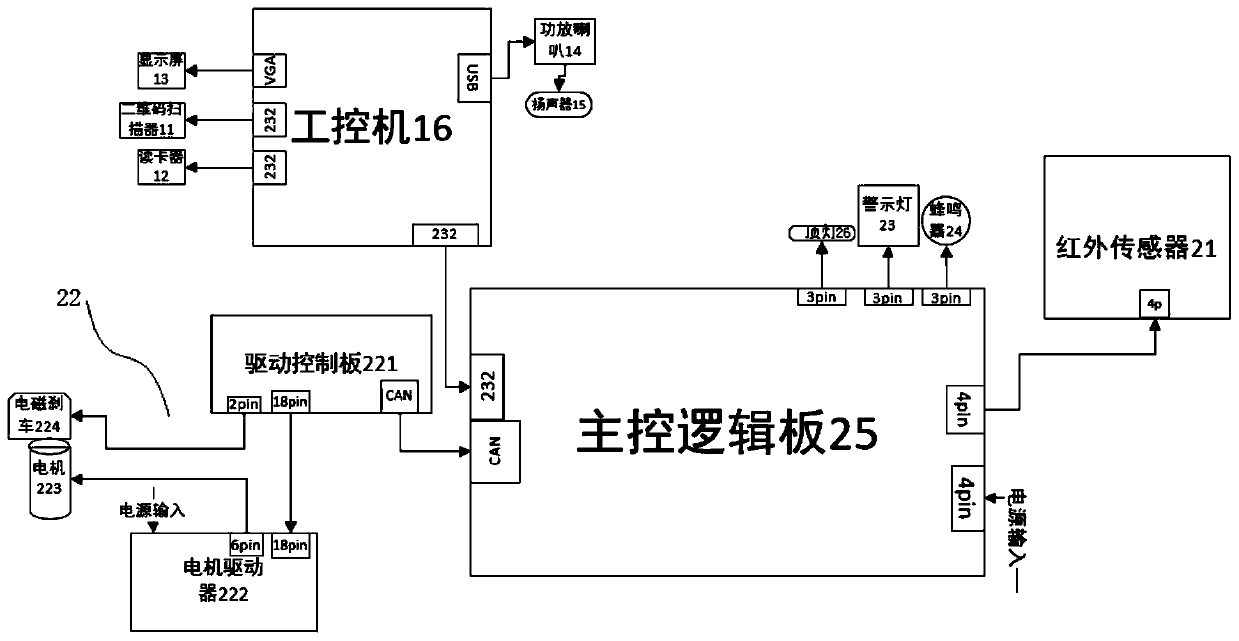
InactiveCN110648433ASecurity Verification ProcessSave human effortTemperatue controlIndividual entry/exit registersVerification systemLoudspeaker
The invention relates to a real-name verification gate and an application method thereof. The real-name verification gate is characterized by comprising a real-name verification system, a gate systemand a power supply, wherein the real-name verification system comprises a camera, a card reader, a two-dimensional code scanner, a display screen, a power amplifier horn, a loudspeaker and an industrial personal computer, the camera, the card reader, the two-dimensional code scanner, the display screen, the power amplifier horn, the loudspeaker and the industrial personal computer are arranged onthe gate system, the industrial personal computer is electrically connected with the camera, the card reader, the two-dimensional code scanner, the display screen and the power amplifier horn, the power amplifier horn is further electrically connected with the loudspeaker, the industrial personal computer is used for verifying whether information of a current user is qualified or not by a human face identification algorithm, the gate system is electrically connected with the industrial personal computer, the gate system is used for automatically opening a gate or warning according to a verification result sent from the industrial personal computer, and the power supply is used for supplying power to each electrical part of the real-name verification gate. The real-name verification gate can be widely applied to the field of security and protection.
Owner:CRSC COMM & INFORMATION GRP CO LTD
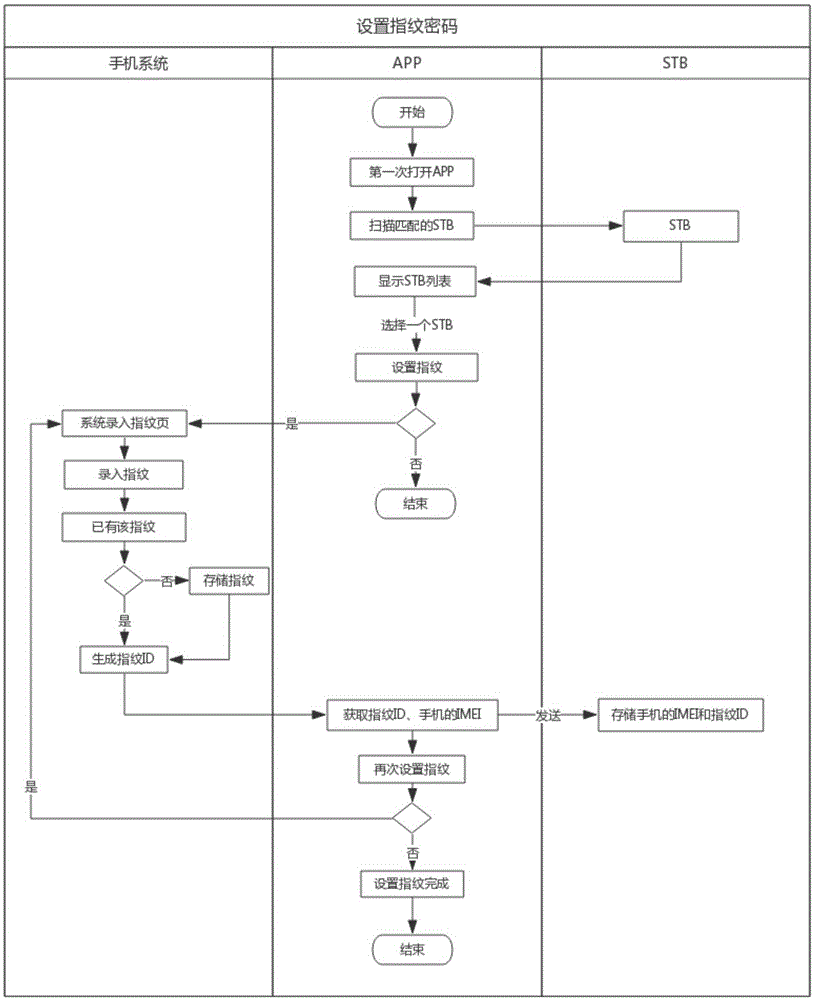
Security authentication method for intelligent set-top box
InactiveCN105307016AEasy to useUse of security authenticationSelective content distributionUser verificationUser needs
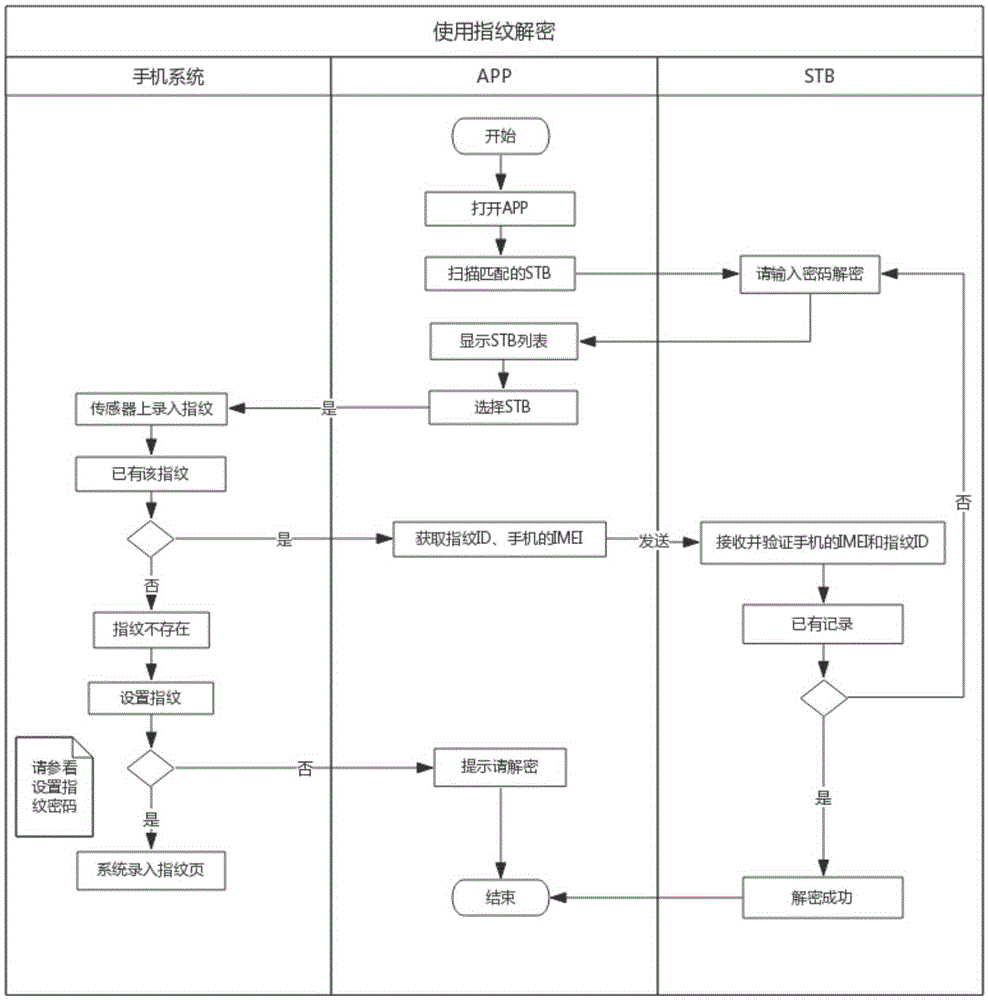
The invention discloses a security authentication method for an intelligent set-top box. The security authentication method comprises the following steps: a mobile phone interacts with the intelligent set-top box through a local area network; a user inputs fingerprint on a mobile phone fingerprint sensor, and the mobile phone combines an IMEI code of the mobile phone and the user fingerprint information into a user identifier and sends the user identifier to the set-top box through the local area network; the set-top box stores the received user identifier; the user needing to decrypt the set-top box inputs the fingerprint on the mobile phone fingerprint sensor, the mobile phone combines the IMEI code of the mobile phone and the user fingerprint information into a user verification identifier and sends the user verification identifier to the set-top box through the local area network; and after receiving the user verification identifier, the set-top box verifies whether a user identifier record matched with the user verification identifier exists in a local storage list, and if so, the decryption is successful. By adopting the security authentication method disclosed by the invention, the user does not need to input a digital password, and the user can easily and safely use his own fingerprint password on the intelligent set-top box to enjoy services.
Owner:SHENZHEN SOWELL TECH
Method for using authentication security in electronic communication
InactiveCN109617701AElectronic communication process securityAuthentication securityUser identity/authority verificationElectronic communicationVerification problem
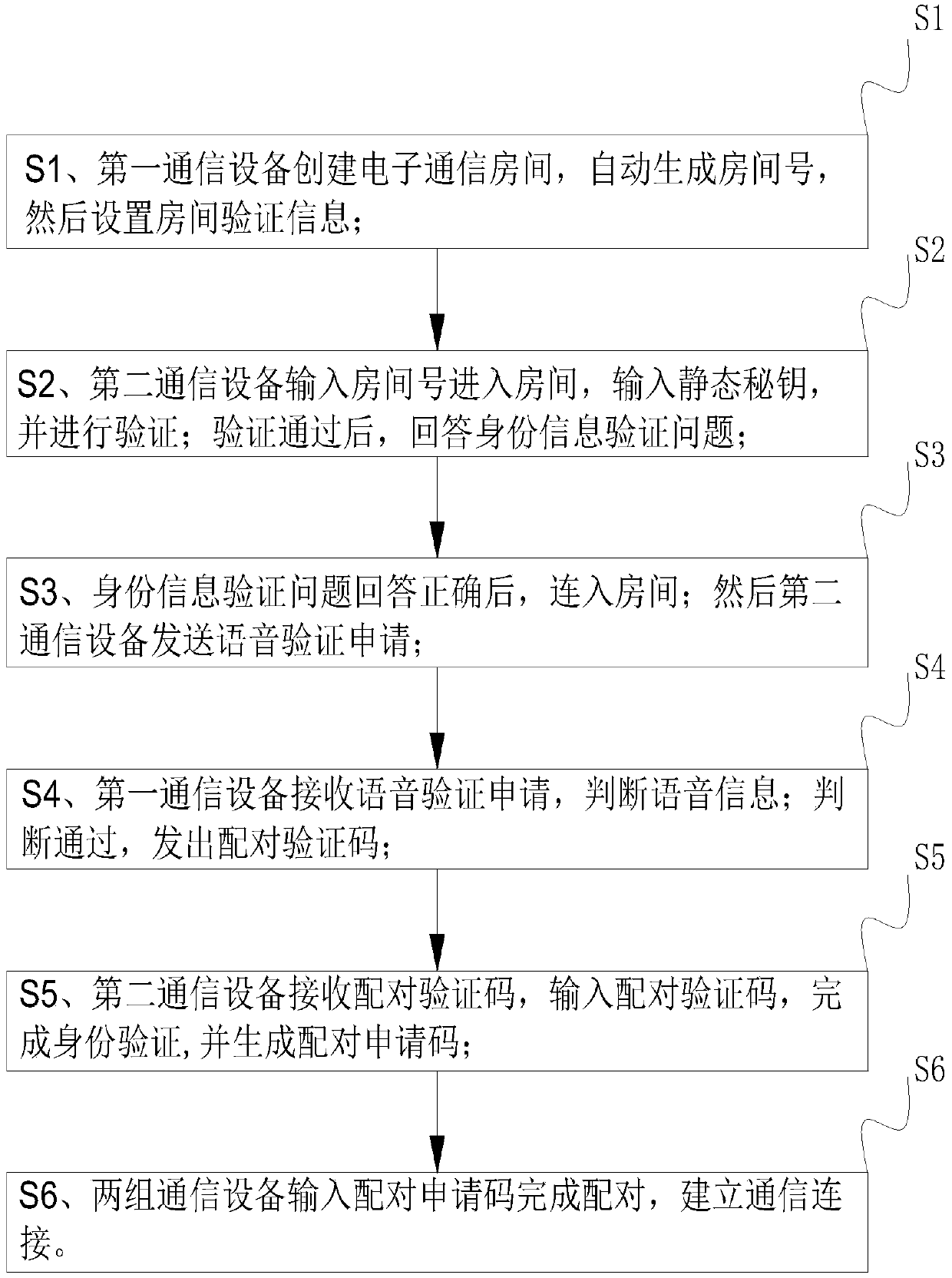
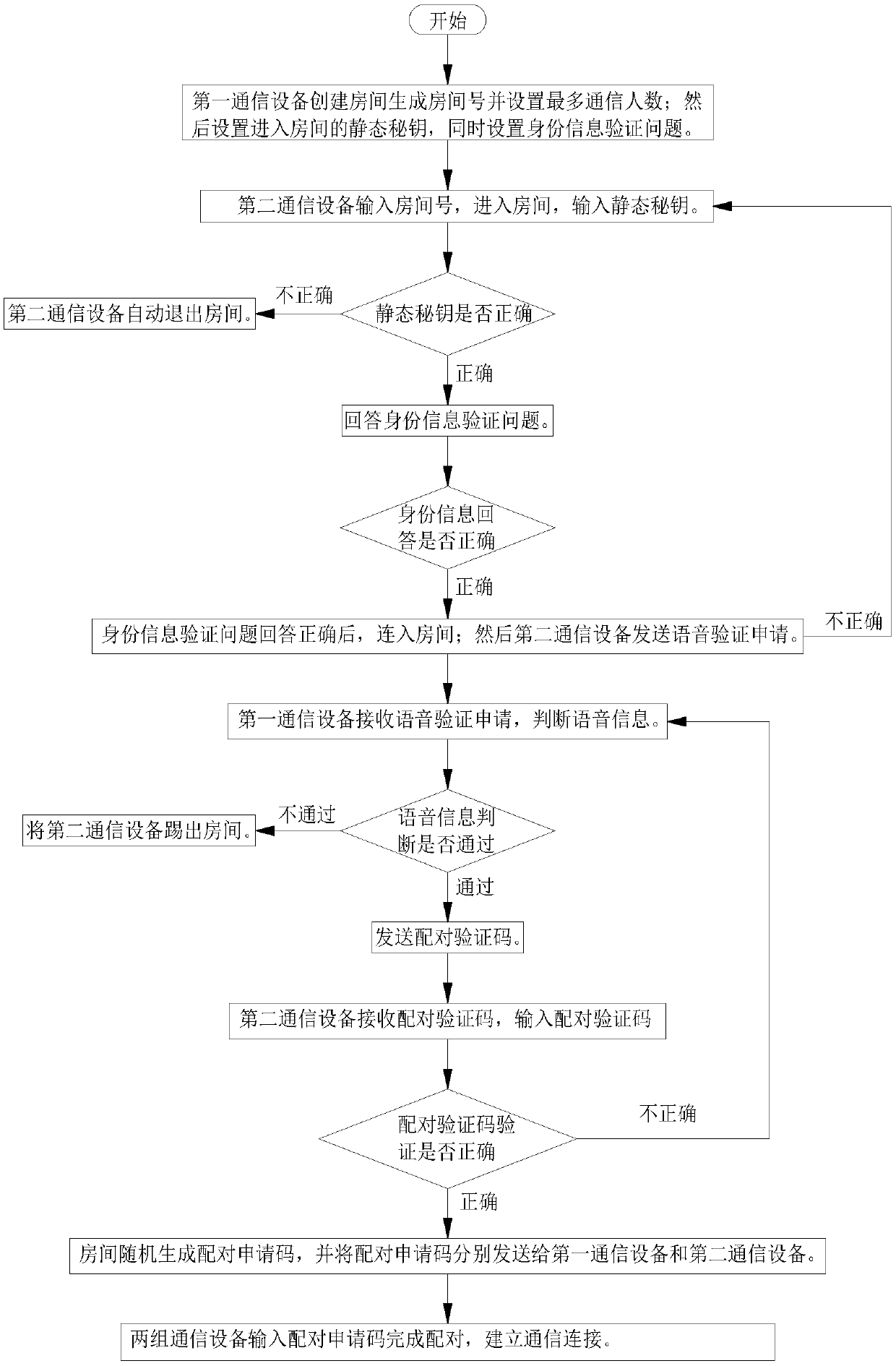
The invention relates to the technical field of electronic communication security, and specifically relates to a method for using authentication security in an electronic communication. The method comprises the following steps: creating an electronic communication room by first communication equipment, automatically generating a room number, and then setting room verification information; inputting the room number and entering a room by second communication equipment, inputting a static key, and verifying the static key; after the verification is passed, answering an identity information verification problem; after the identity information verification problem is answered correctly, connecting to the room; and sending a voice verification application by the second communication equipment;receiving the voice verification application by the first communication equipment, and judging voice information; receiving a pairing verification code by the second communication equipment and generating a pairing application code; and inputting the pairing application code by two groups of communication equipment to complete pairing, and establishing a communication connection. The method for using the authentication security in the electronic communication provided by the invention solves the problem that information is leaked since irrelevant personnel can enter the communication in the communication process due to the lack of a secure identity authentication method in the existing multi-person electronic communication process.
Owner:GUILIN UNIV OF AEROSPACE TECH
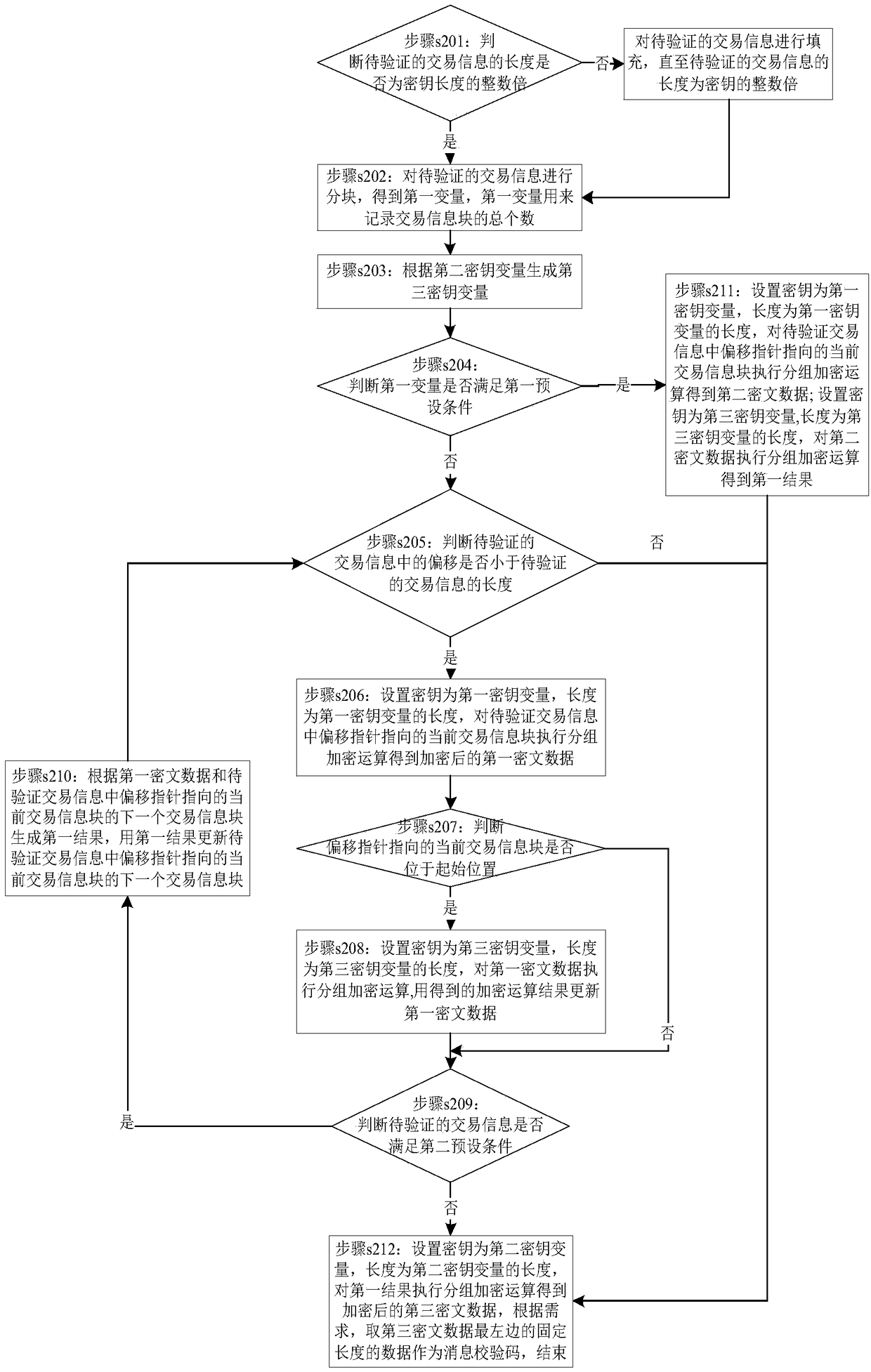
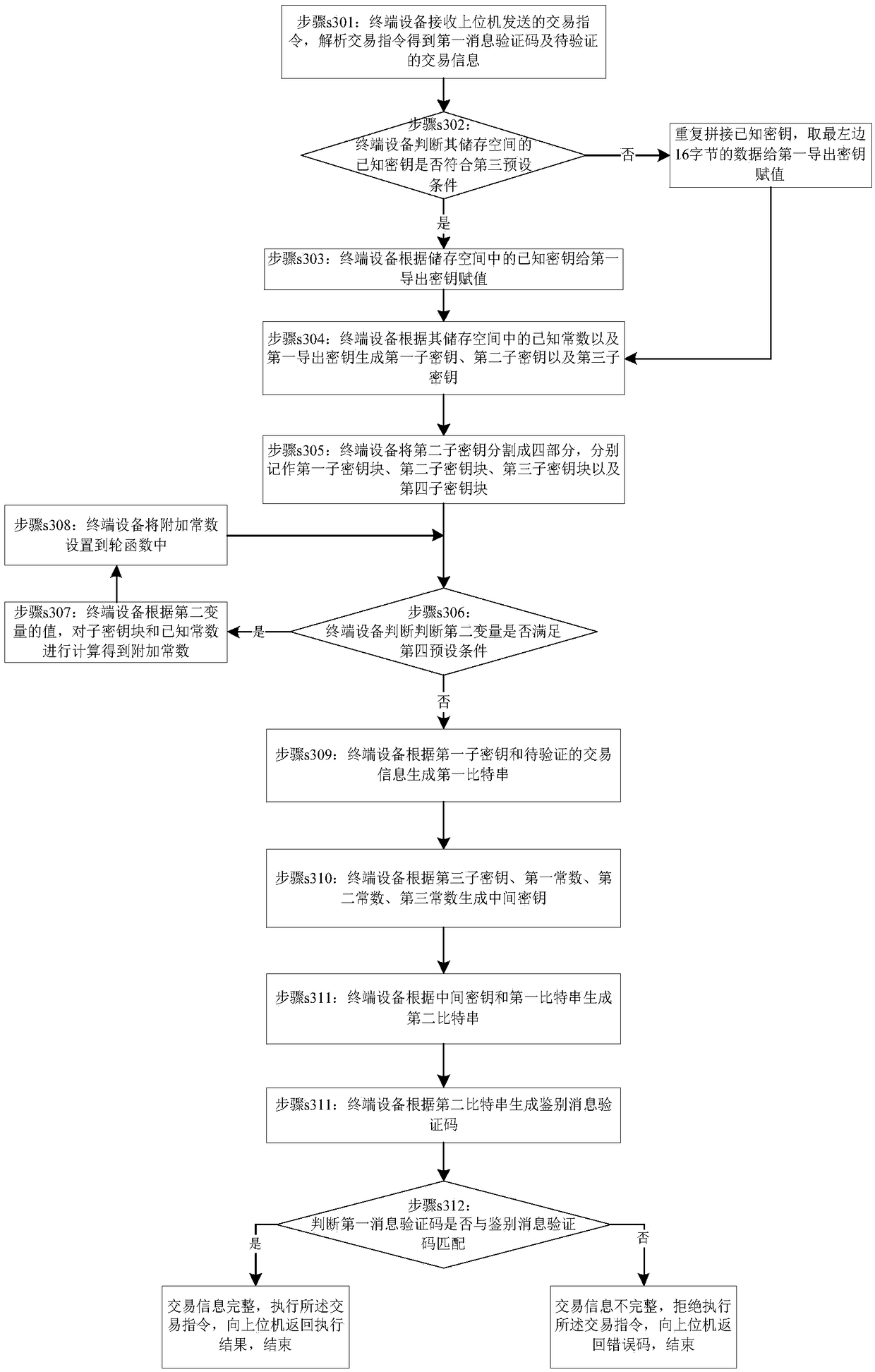
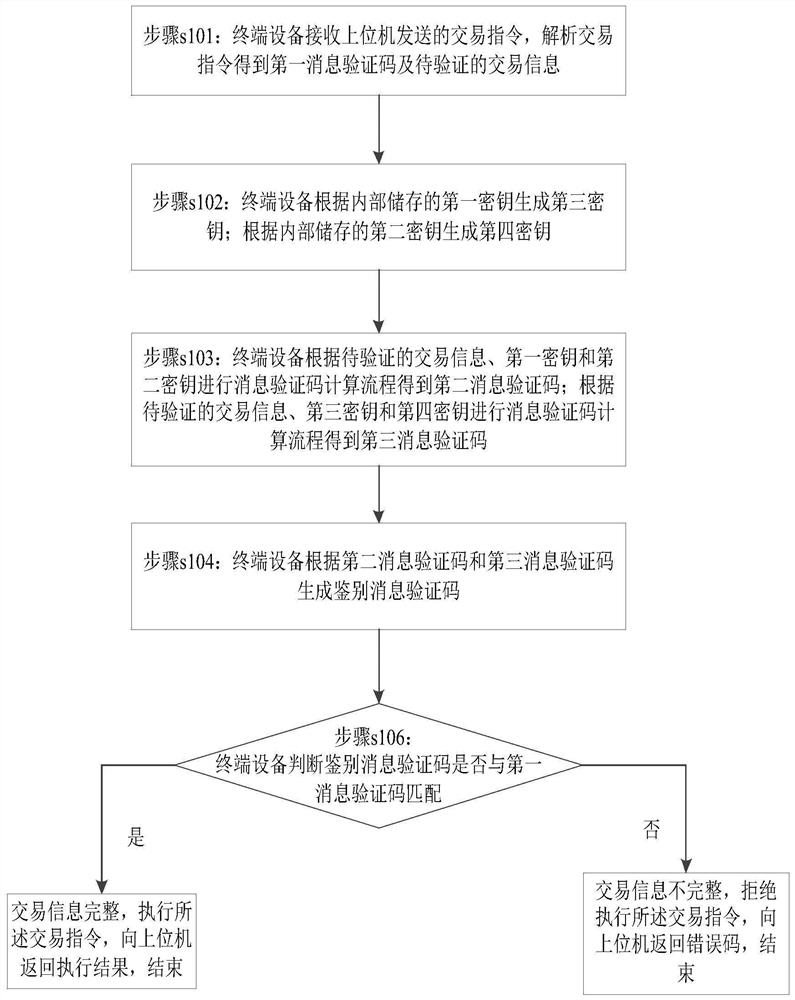
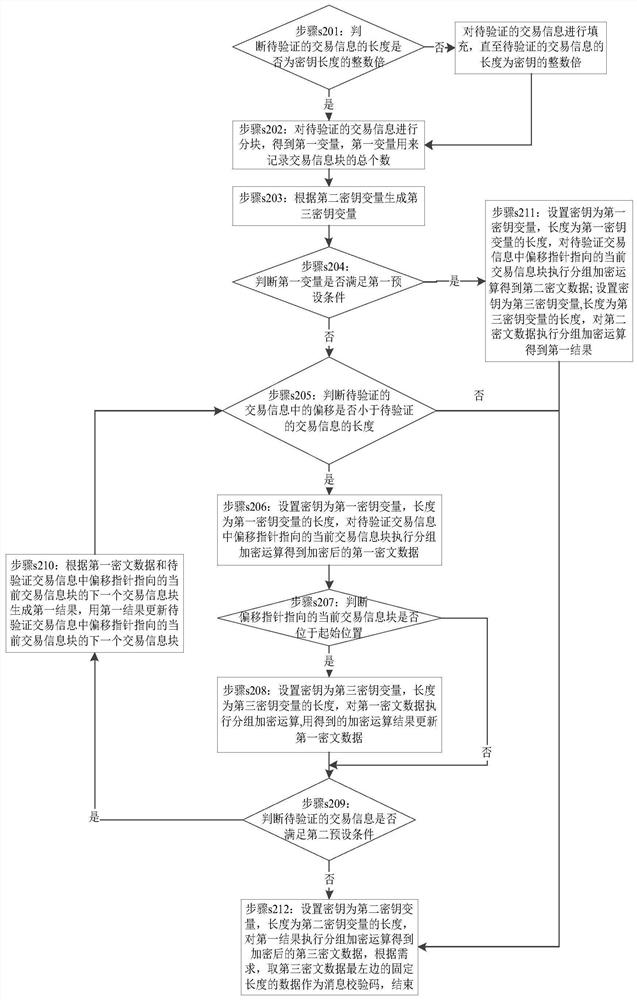
Method for identifying integrity of transaction information
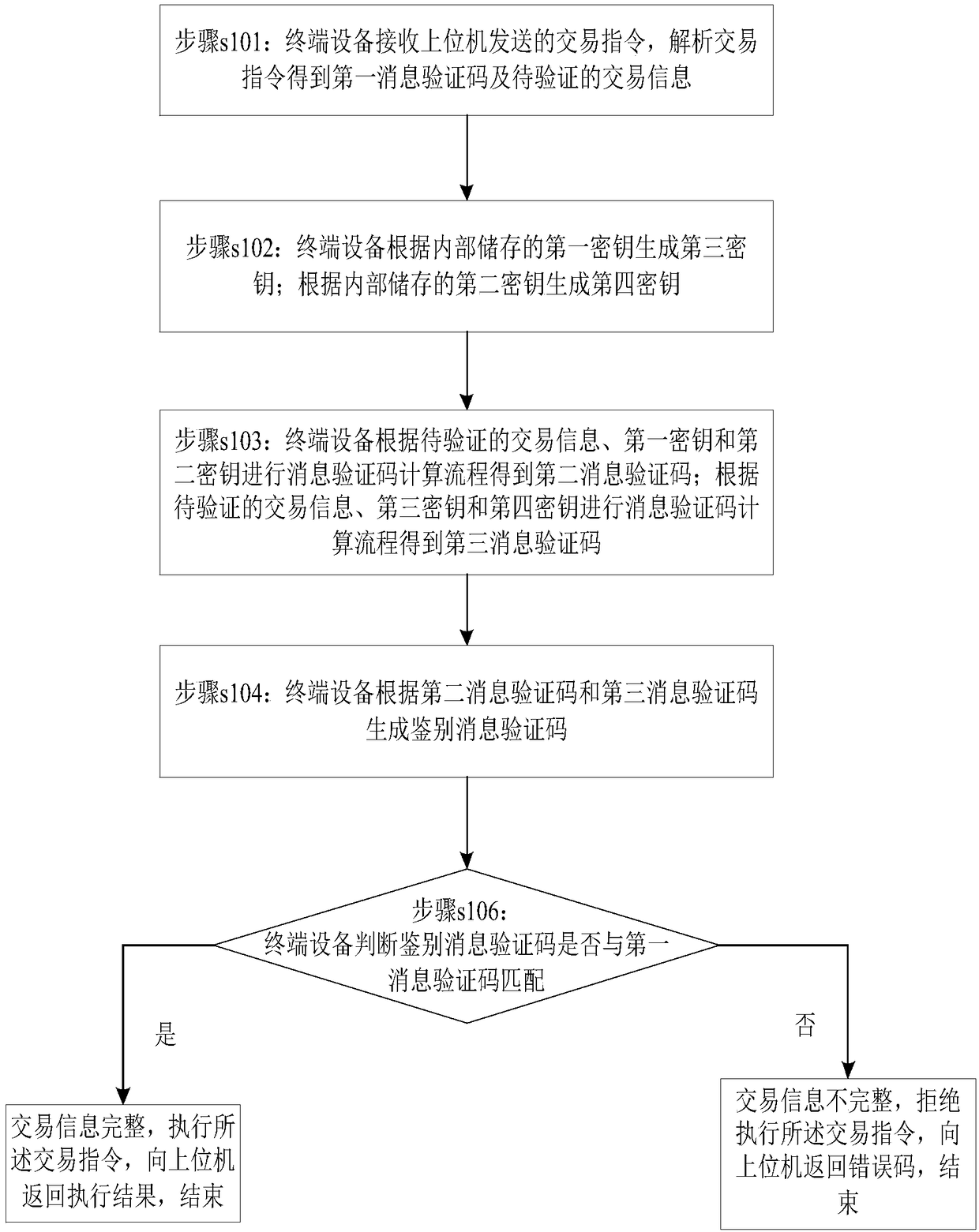
The invention provides a method and a device for identifying integrity of transaction information. The method comprises steps that a terminal device receives a transaction instruction sent by a host and analyzing the transaction instruction so as to obtain a first information verification code and to-be-verified transaction information; blocking the to-be verified transaction information so as toobtain transaction information blocks, according to the first secret key, generating a third secret key, according to a second secret key, generating a fourth secret key, and according to the transaction information blocks, the first secret key, the second secret key, the third secret key and the fourth secret key, carrying out calculation so as to generate a transaction information code; judgingwhether the transaction information code matches the first information verification code, if yes, determining that the transaction information is complete, executing the transaction instruction and returning a transaction result to the host and finishing; or else, determining that the transaction information is not complete, rejecting execution of the transaction instruction, returning an error code to the host and finishing the execution. In this way, according to the to-be-verified transaction information, to-be-verified trade information is subjected to processing for many times in a calculation process of the verification code, the important data in the transaction information is quite safe in the verification process.
Owner:FEITIAN TECHNOLOGIES
Purchase-sales-inventory management system based on micro-service architecture
The invention relates to the technical field of purchase-sales-inventory micro-service architecture management, and discloses a purchase-sales-inventory management system based on a micro-service architecture, which comprises a user client Ui and a micro-service architecture consisting of a purchase management cloud server Sa, a sales management cloud server Sb and an inventory management cloud server Sc, a discovery server Sf used for storing registration information of any cloud server Si in the micro-service architecture and receiving service access, and an API gateway used for dynamicallyrouting request access of the user client Ui to any cloud server Si in the micro-service architecture through the discovery server Sf. User authentication management system software runs on the discovery server Sf, and the user authentication management system adopts an authentication method based on zero knowledge proof to perform identity authentication on the user client Ui accessing the discovery server. The technical problem that an existing purchase-sales-inventory management system based on the micro-service architecture cannot perform security authentication on the identity of a user accessing a discovery server is solved.
Owner:汪洵
Cloud storage data access control system based on zero knowledge proof
InactiveCN111259352ASafety verificationDigital data protectionDigital data authenticationData access controlEngineering
The invention relates to the technical field of cloud storage data access control, and discloses a cloud storage data access control system based on zero knowledge proof, the system comprising: a cloud storage server Si configured with a cloud storage database Di, cloud storage access control system software running on the cloud storage server Si. The system also comprises an access client Ui, andthe access client Ui is in communication connection with the cloud storage server Si; when an access client Ui sends a data access request to a cloud storage database Di of the cloud storage server Si, the cloud storage access control system of the cloud storage server Si verifies the identity of the access client Ui by adopting an access verification method based on zero knowledge proof, and only the access client Ui passing the identity verification is allowed to access the data in the cloud storage database Di of the cloud storage server Si. According to the invention, the technical problem that the identity of an access user cannot be subjected to security verification when the user sends an access request to a cloud storage server in existing conventional cloud storage access controlsystem is solved.
Owner:熊国华
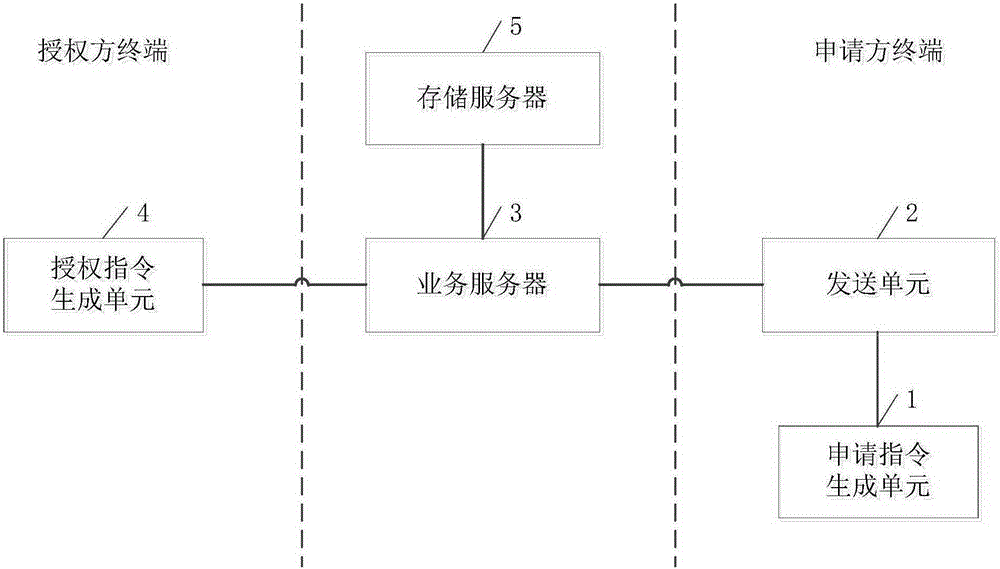
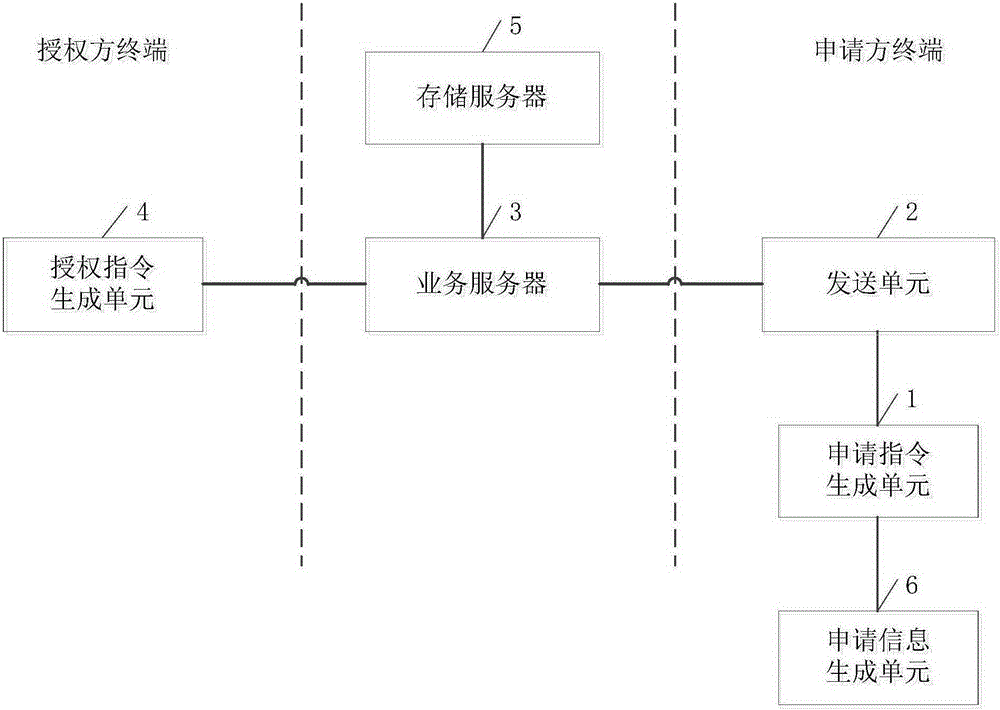
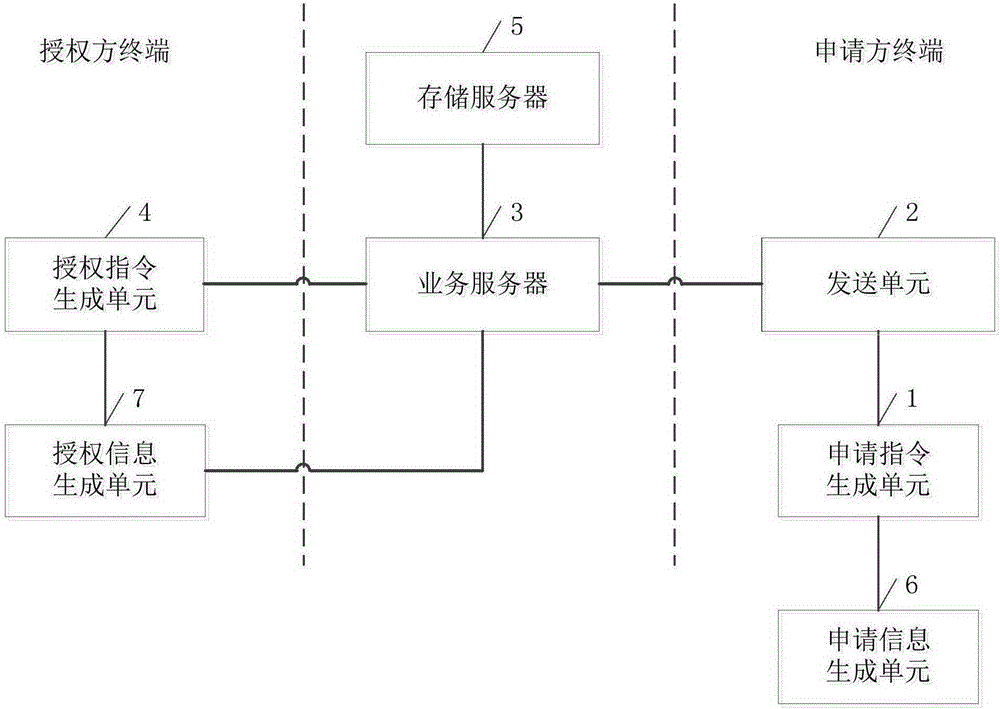
Verification device based on fingerprint application and verification method based on fingerprint application
InactiveCN105279414ASafety verificationUniqueness guaranteedDigital data authenticationValidation methodsAuthorization
The invention discloses a verification device based on fingerprint application. The verification device comprises an application instruction generating unit, an applicant terminal sending unit, a service server, an authorization instruction generating unit and a storage server. In the verification process, the fingerprint information verification is needed for both an applicant and an authorized party, so that the verification process is secure. The fingerprint information has the uniqueness, and the input is convenient and fast, so that the input error condition is avoided; the efficiency of the verification process is effectively improved; and the time is saved. The invention also discloses a verification method based on fingerprint application.
Owner:张迎新
Power transmission and distribution production management system based on micro-service architecture
InactiveCN111245835ASafety verificationData processing applicationsUser identity/authority verificationEngineeringUser authentication
The invention relates to the technical field of power transmission and distribution micro-service architecture management, and discloses a power transmission and distribution production management system based on the micro-service architecture. The system comprises a user client, an API gateway, a discovery server Sf, and the micro-service architecture composed of a power generation management cloud server S1, a power transmission management cloud server S2 and a power distribution management cloud server S3. The user client communicates with the discovery server Sf through the API gateway, and the discovery server Sf communicates with any cloud server Si in the micro-service architecture; user authentication management system software runs on the discovery server Sf, and the user authentication management system performs identity authentication on a user client accessing the discovery server by adopting an authentication method based on zero knowledge proof. The technical problem thatan existing power transmission and distribution production management system based on the micro-service architecture cannot perform security authentication on the identity of a user accessing a discovery server is solved.
Owner:万庆文
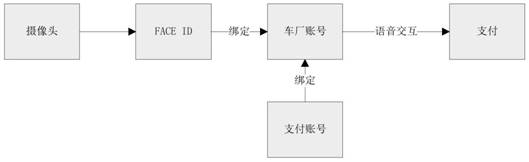
Automobile online payment system and method
PendingCN113627944ASafety verificationEnhanced authenticationProtocol authorisationComputer networkThe Internet
An automobile online payment system disclosed by the present invention comprises an Internet of Vehicles module, a personal payment system and a man-machine interaction module, the man-machine interaction module is used for inputting an Internet of Vehicles account, and the Internet of Vehicles module is connected with the personal payment system through a network and is used for binding the Internet of Vehicles account with the personal payment system, and when operation related to a payment function is carried out through the human-computer interaction interface in the vehicle, the vehicle networking module is matched with a personal payment system through a vehicle networking account to complete payment operation. The system has the advantages that the structure is simple, payment is convenient, when payment is needed, the personal payment system is rapidly connected and called through the FACE ID and the Internet of Vehicles account number to conduct payment, the Gemangeran is reliable, verification of the face ID and the Internet of Vehicles account number is safer, the payment efficiency is guaranteed, meanwhile, the payment safety is improved, the in-vehicle payment experience of a user is improved, and the improvement of the function of the Internet of Vehicles in the vehicle is promoted.
Owner:YIBIN COWIN AUTO CO LTD
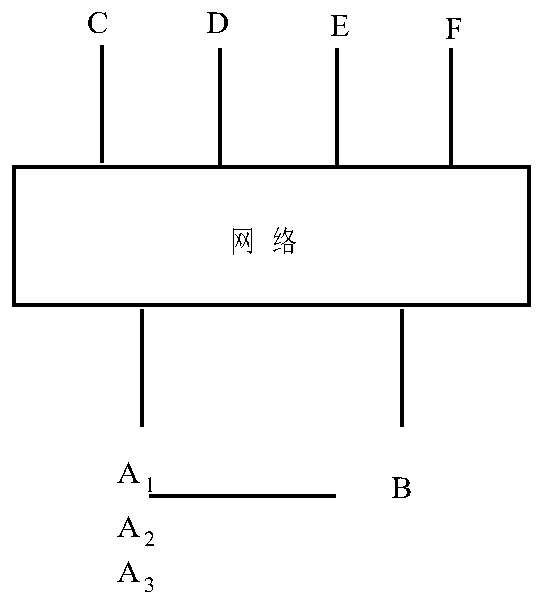
Multistage verification authorization system and method based on positioning device
InactiveCN110210202ASimple and flexible authorization operationEasy to installDigital data authenticationProtocol authorisationThird partyPayment
The invention discloses a multistage verification and authorization system and method based on a positioning device. The multistage verification and authorization system comprises a positioning identity module, a biological information acquisition module, an information verification total platform, a local information verification platform, a third-party application server and an identification terminal. According to the invention, a plurality of persons or objects can be authorized in a grading manner through one input terminal. Authorization operation is simple and flexible. Modifying operation is conducted any time. An authorized device is protable, cheap and stable and can be easily mounted on other objects. The device is convenient to promote, quickly verified, safe and reliable. Therefore, daily needs of verification and small-sum payment are achieved. Personal privacy and identity information of users do not divulge even if smartphones are lost. Specific activities of authorizedpersonnel or things are monitored at the same time.
Owner:刘德权
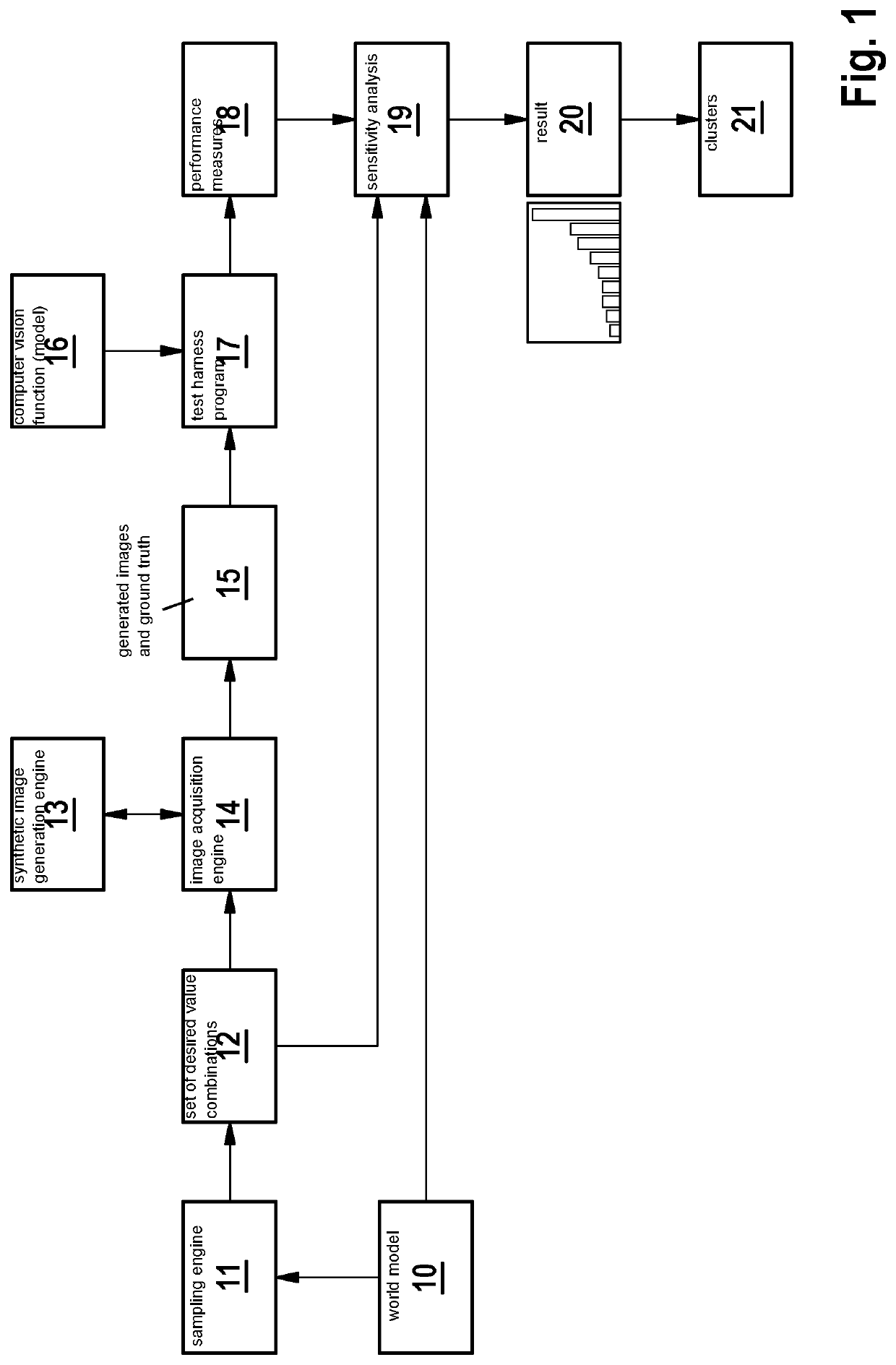
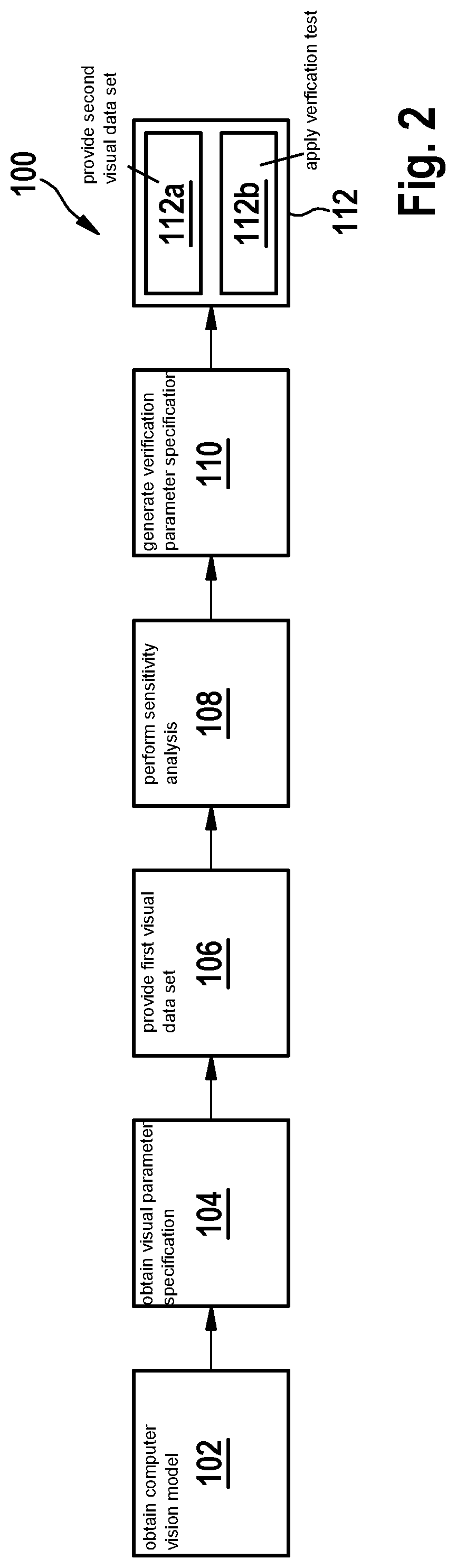
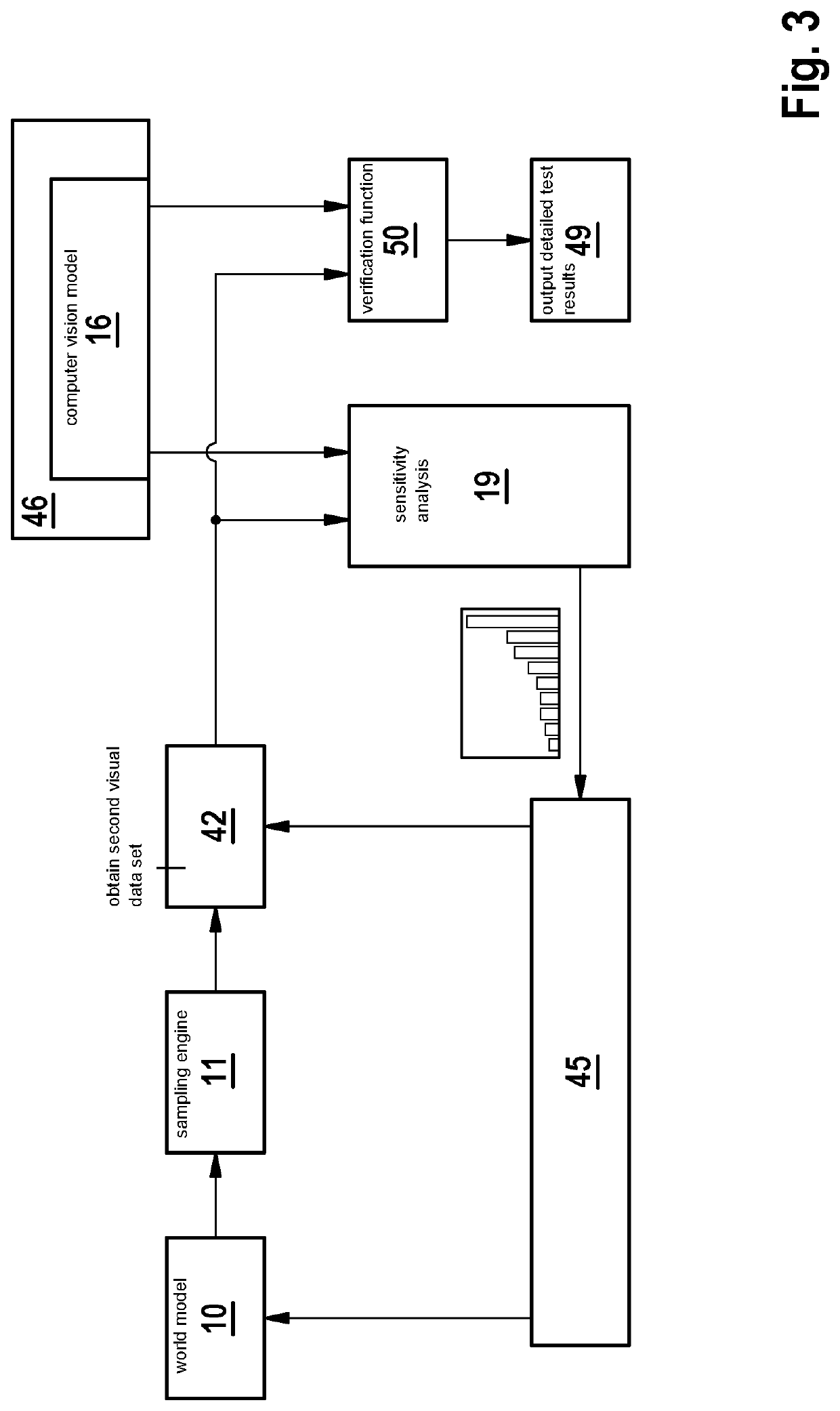
Verification of computer vision models
PendingUS20220230419A1Safety verificationReduce complexityBiological modelsScene recognitionSensitive analysisComputer graphics (images)
Reducing the number of parameters in a visual parameter set based on a sensitivity analysis of how a given visual parameter affects the performance of a computer vision model to provide a verification parameter set having a reduced size.
Owner:ROBERT BOSCH GMBH
How to verify login authority
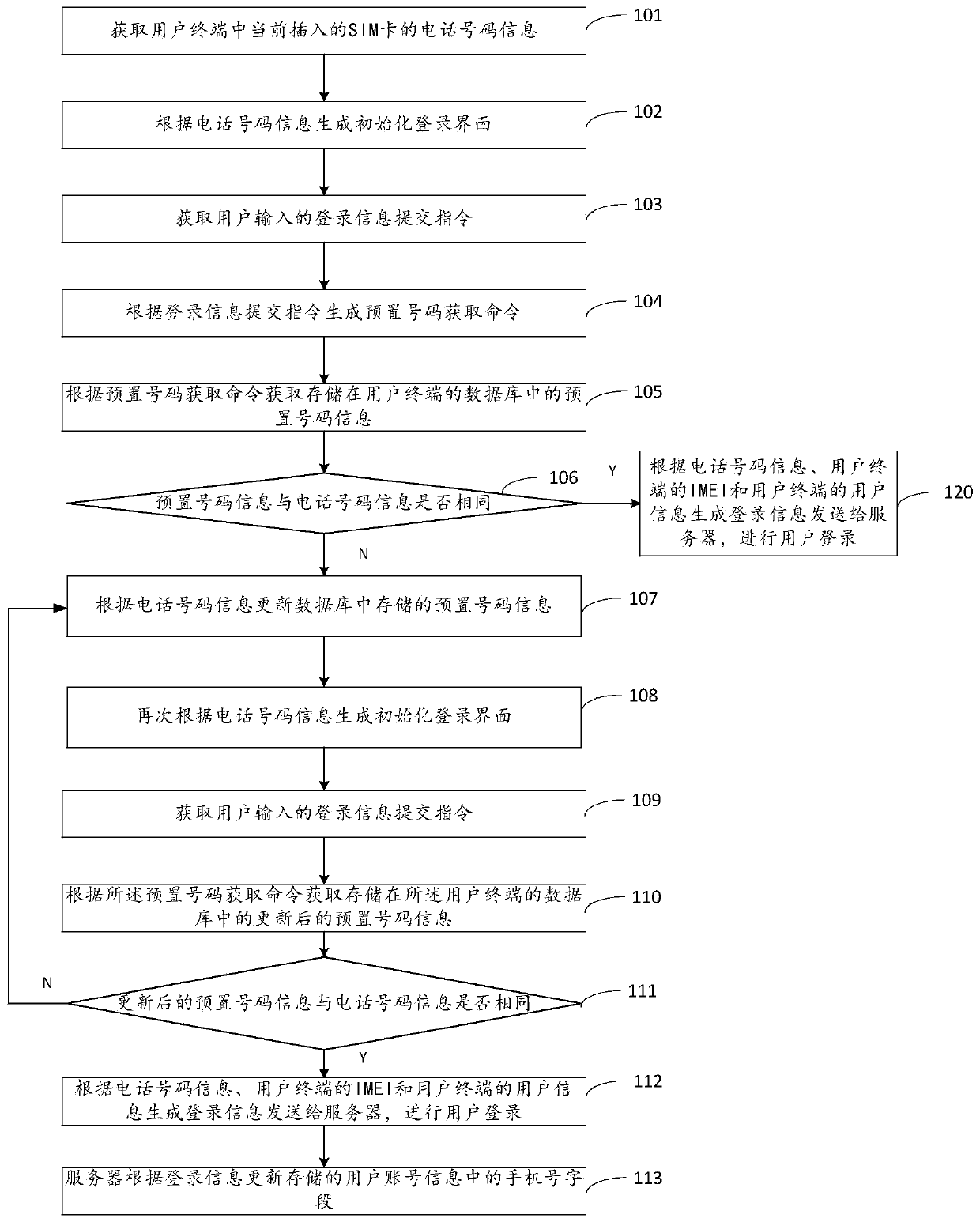
ActiveCN106572081BQuick verificationSafety verificationTransmissionNetwork data managementUser inputComputer terminal
The embodiment of the invention relates to a login authority verifying method, and the method comprises the steps: obtaining the telephone number information of a currently inserted SIM (subscriber identity module) card in a user terminal; generating an initialized login interface according to the telephone number information; obtaining a login information submitting instruction inputted by a user; generating a preset number obtaining command according to the login information submitting instruction; obtaining the preset number information stored in a database of the user terminal according to the preset number obtaining command; determining whether the preset number information is the same as the telephone number information or not; updating the preset number information stored in the database according to the telephone number information when the preset number information is not the same as the telephone number information; determining whether the updated preset number information is the same as the telephone number information or not again; generating login information according to the telephone number information, the IMEI of a user terminal and the user information of the user terminal when the updated preset number information is the same as the telephone number information, transmitting the login information to a server, and carrying out the login of a user; and enabling the server to update the cellphone number field stored in user account information according to the login information.
Owner:北京博瑞彤芸科技股份有限公司
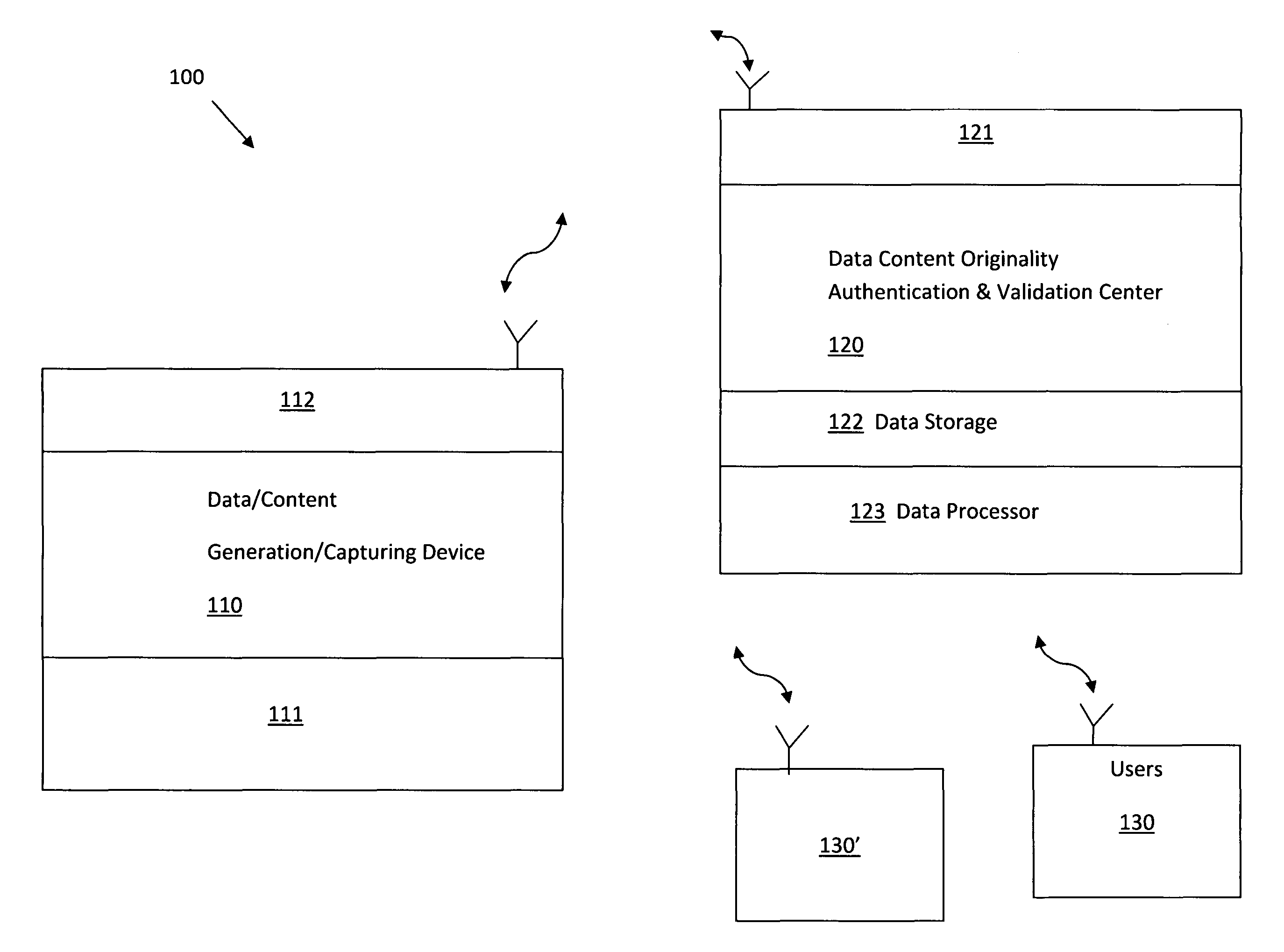
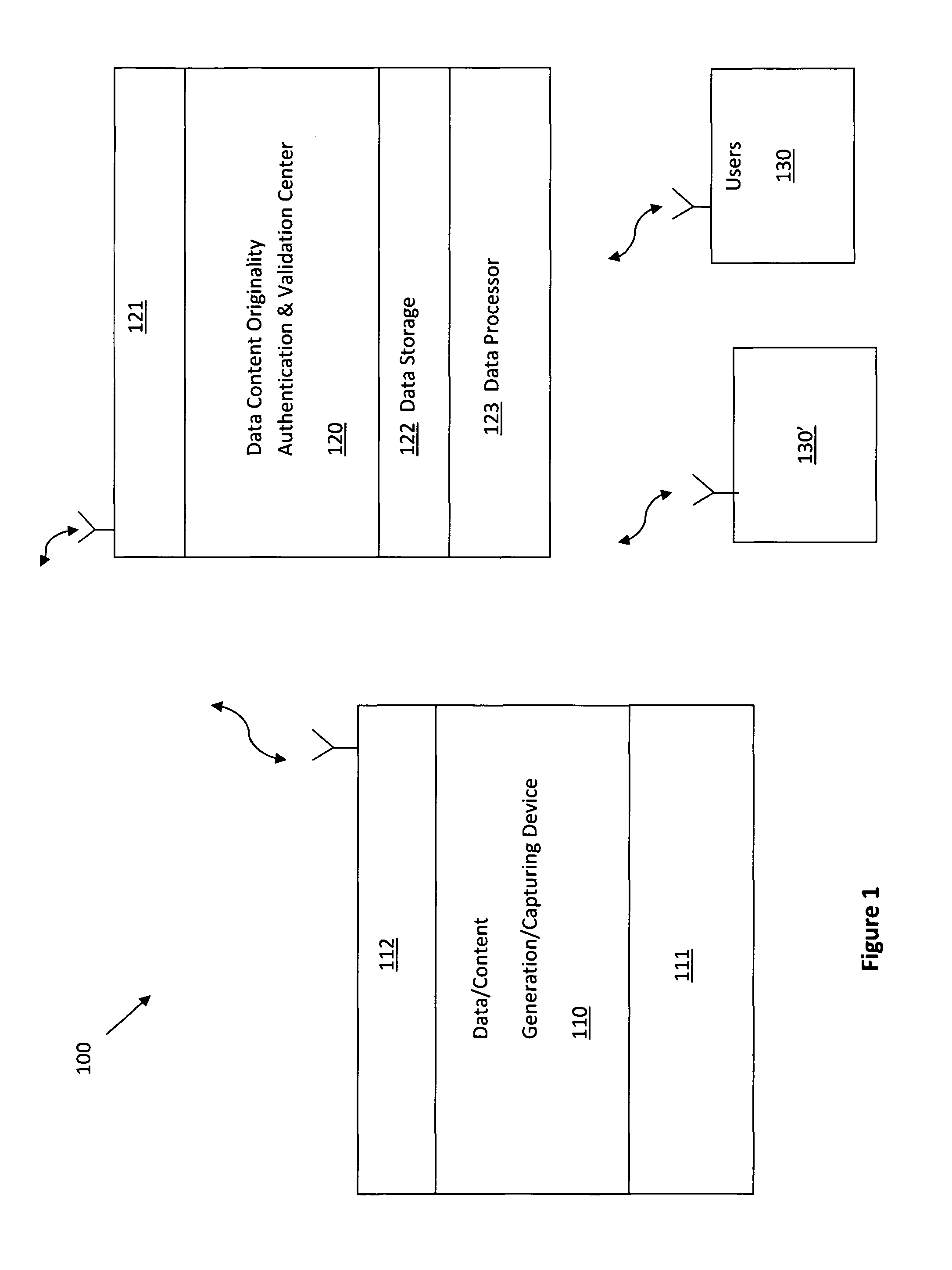
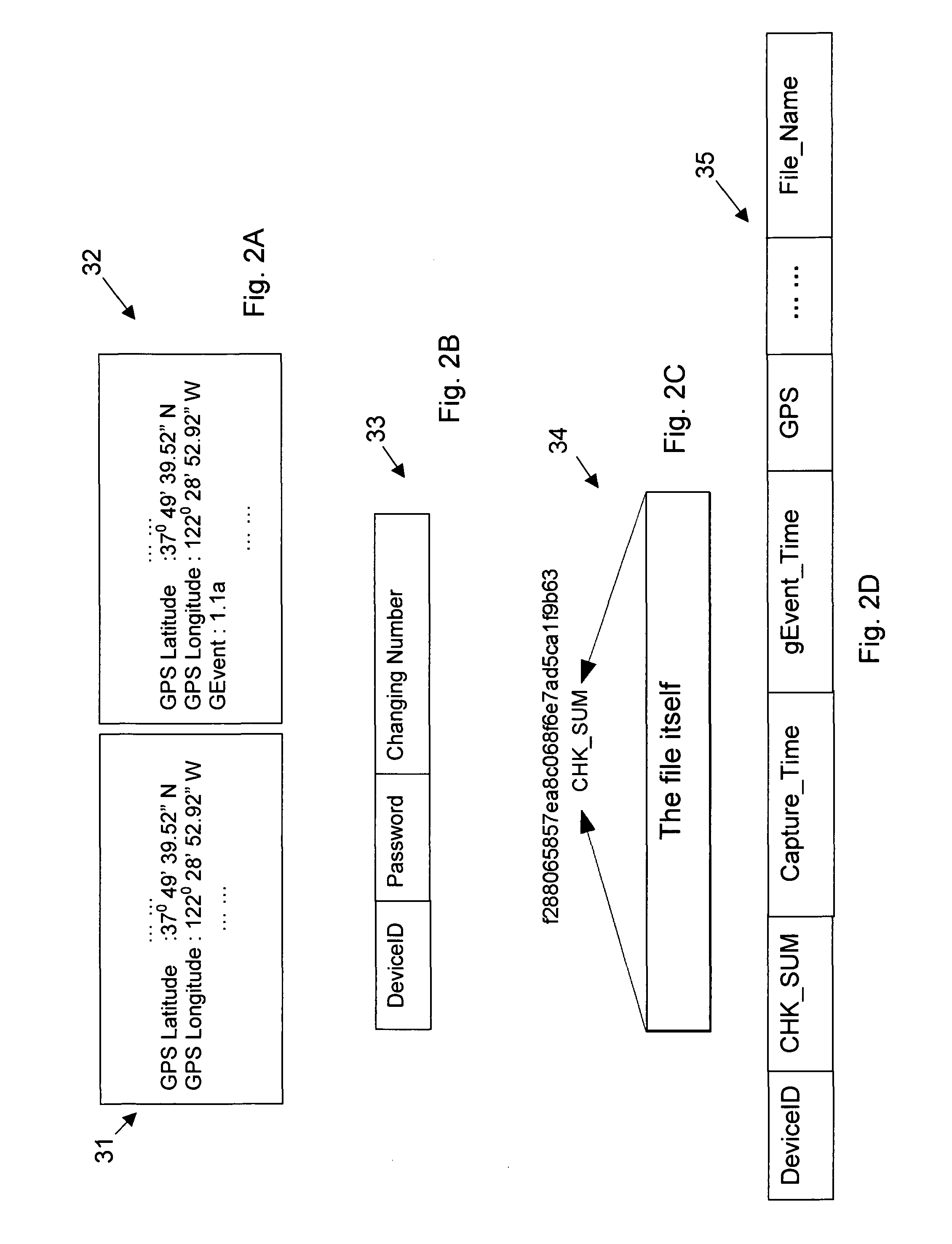
Systems and methods to generate, preserve, collect, search, and certify authentic original documents
InactiveUS9264439B2Safety verificationDigital data processing detailsUser identity/authority verificationTransceiverData content
The data-content authentication center includes a data-content receiver comprises a transceiver for receiving data / content directly from a data / content generation / capturing device by first checking and confirming a registered device identification (ID) of the data / content generation / capturing device before receiving the data / content transmitted from the data / content generation / capturing device into the data-content receiver.
Owner:LI DE XIONG
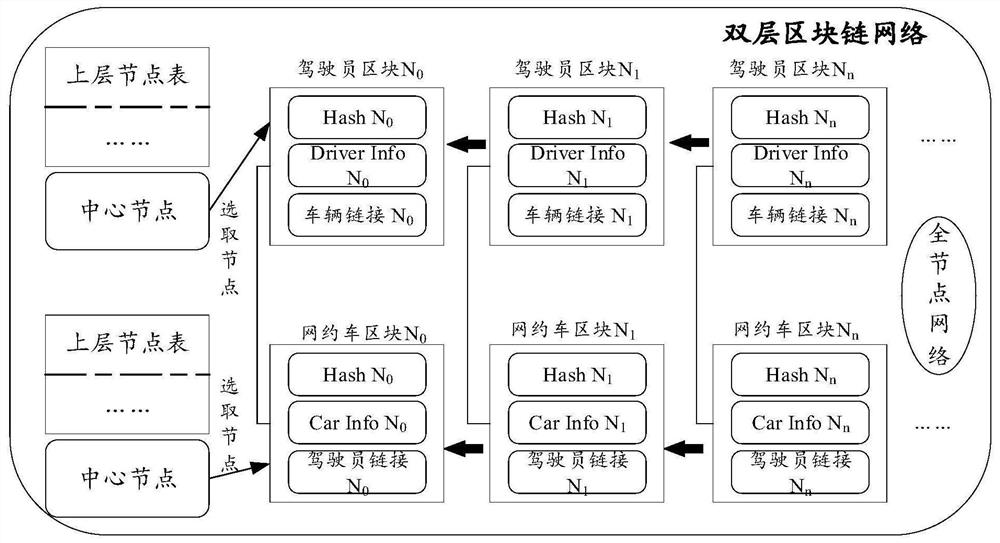
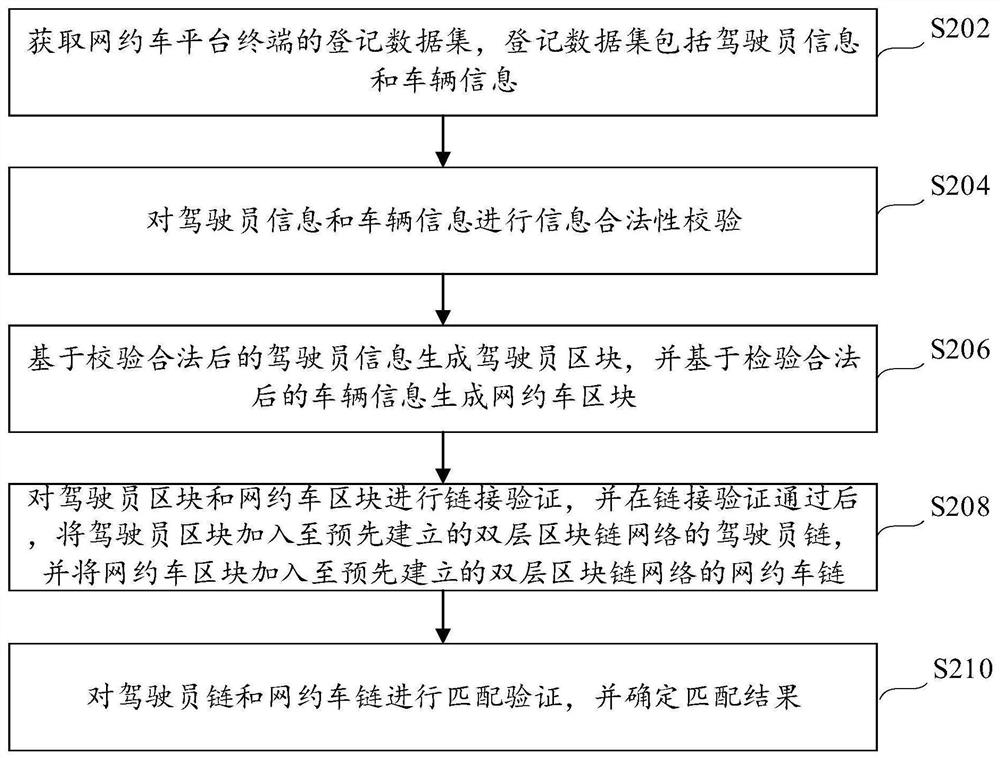
Online car-hailing information security verification method and system and server
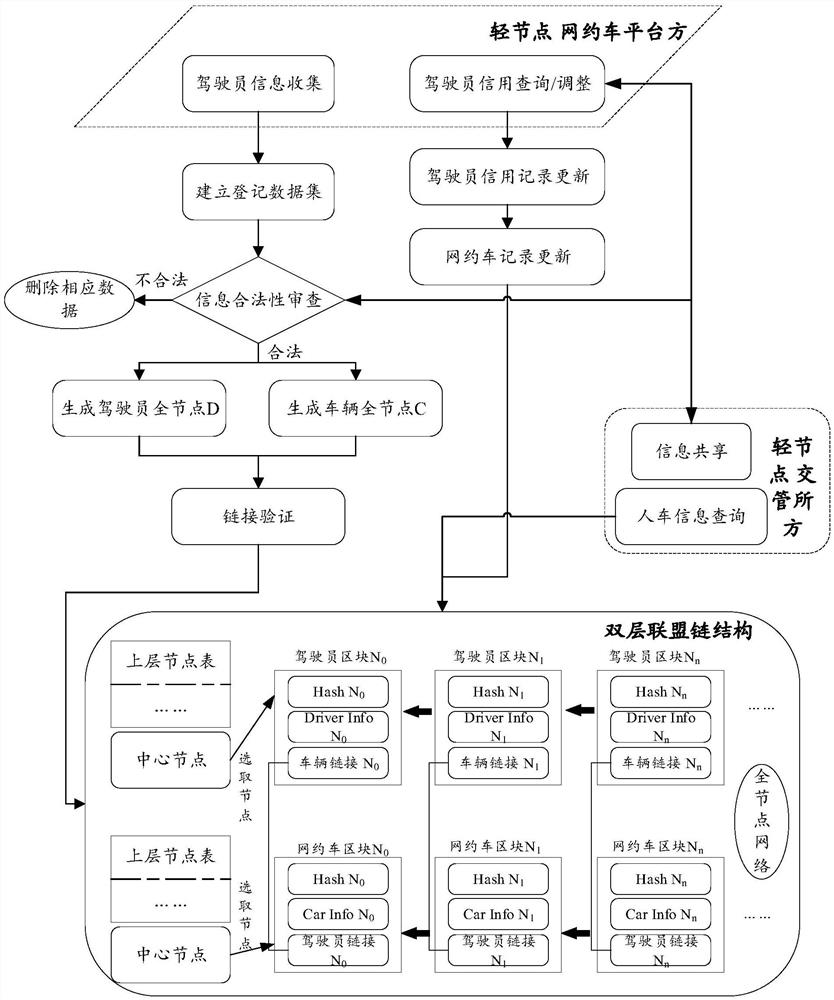
PendingCN112651754ASafety verificationImprove verification capabilitiesBuying/selling/leasing transactionsDriver/operatorBlockchain
The invention provides an online car-hailing information security verification method and system, and a server, and relates to the technical field of block chains, the method is applied to a sub-server, and the method comprises the steps: obtaining the driver information and vehicle information of an online car-hailing platform terminal; performing information legality verification on the driver information and the vehicle information; after the verification is legal, generating a driver block based on the driver information, and generating an online car-hailing block based on the vehicle information; performing link verification on the driver block and the online car-hailing block, adding the driver block to the driver chain after the link verification is passed, and adding the online car-hailing block to the online car-hailing chain; and performing matching verification on the driver chain and the online car-hailing chain to determine a matching result, so that online car-hailing information security verification can be performed according to the matching result. According to the invention, the qualification of online car-hailing drivers can be effectively managed in a decentralized manner, the cost of manual verification is greatly reduced, and the verification effect of online car-hailing information security is improved.
Owner:HANGZHOU QULIAN TECH CO LTD
An identity verification method, device and storage medium
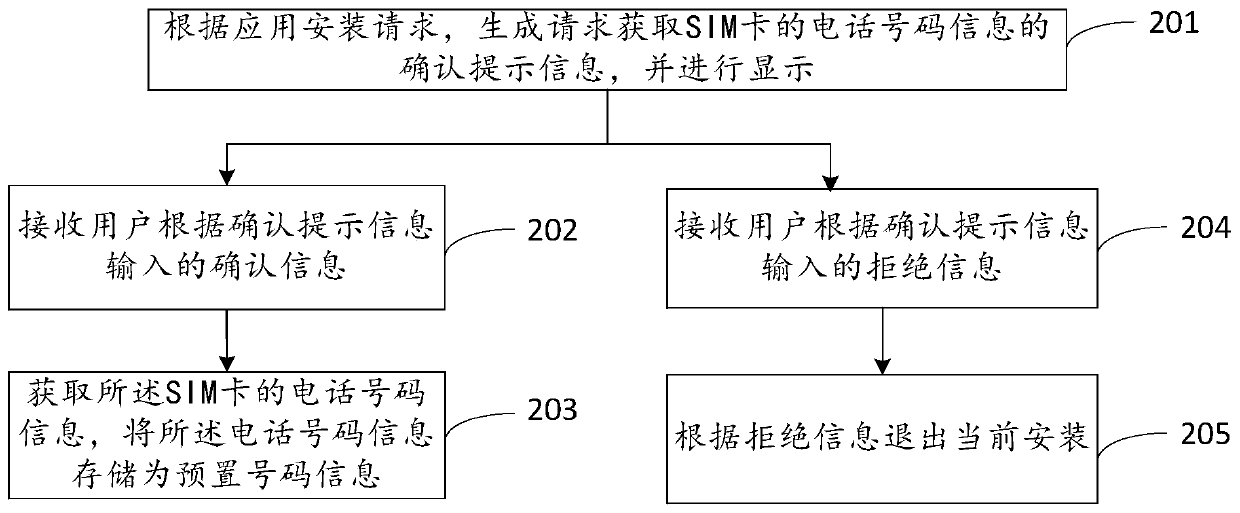
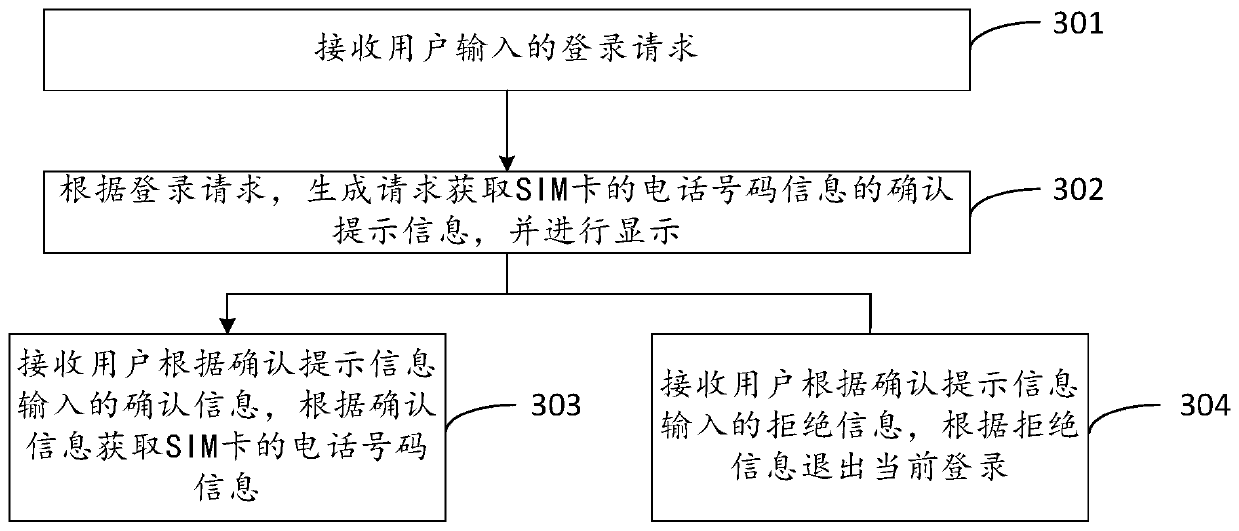
ActiveCN108306886BImprove securitySafety verificationTransmissionUser verificationInformation processing
The embodiment of the invention discloses an identity verification method, device and storage device, which are applied in the technical field of information processing. When a terminal device in the system based on user login initiates a certain type of request, the server will send a verification message including the first content information to the terminal device to inform the operating user that audio and image data need to be collected, which requires the user to pass through the terminal device Collect audio and image data and send them to the server for verification; if the verification of audio and image data is passed, the identity verification of the operating user of the terminal device is passed. In this way, through the collected audio and image data, it can be verified whether the user operating the terminal device is a legitimate user, and the verification process is relatively safe; and because the collected audio and image data can only pass the verification when it corresponds to the first content information, it can prevent other users from Using pre-recorded audio and image data of legal users for verification, improves the security of terminal equipment operations.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
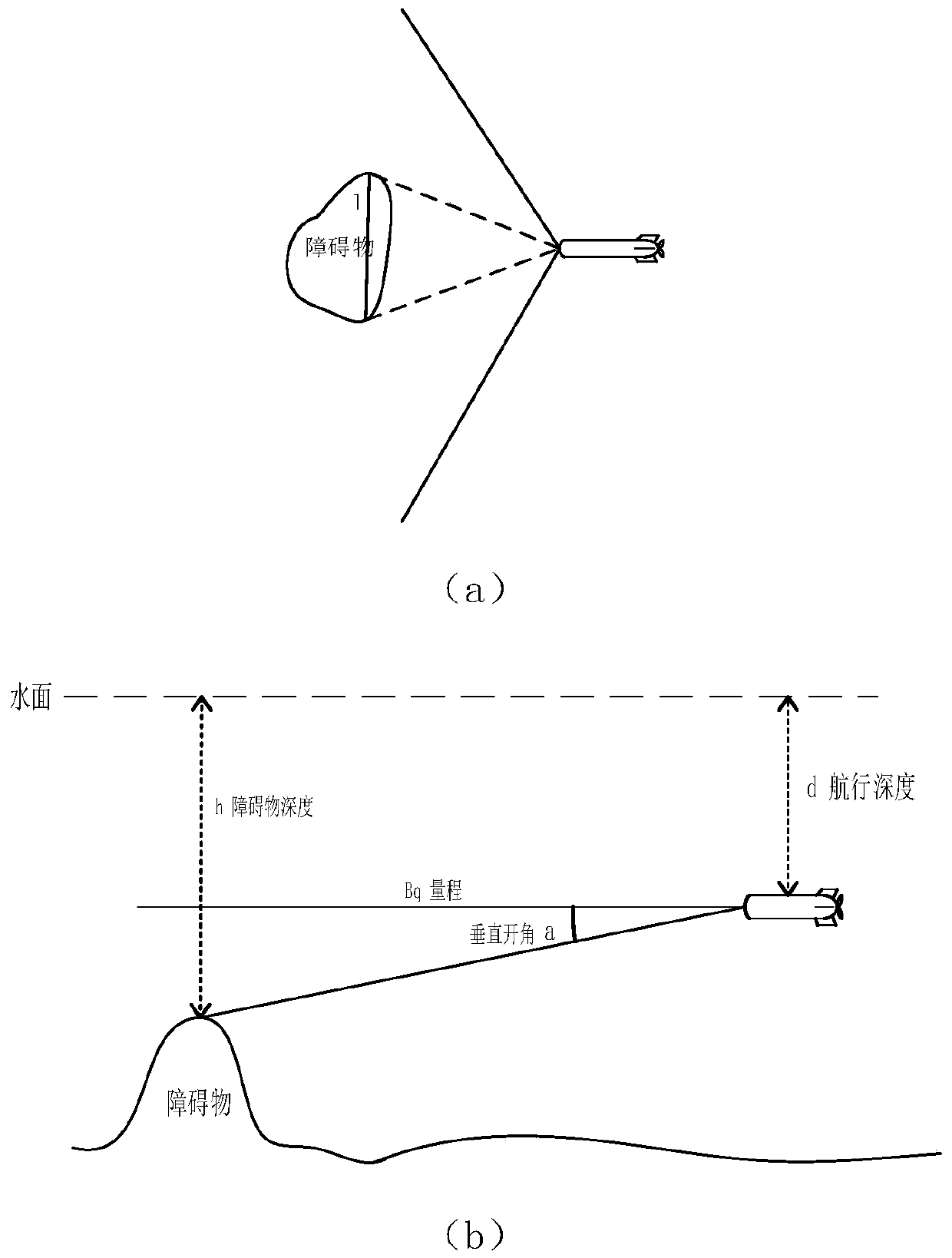
AUV collision avoidance function verification method
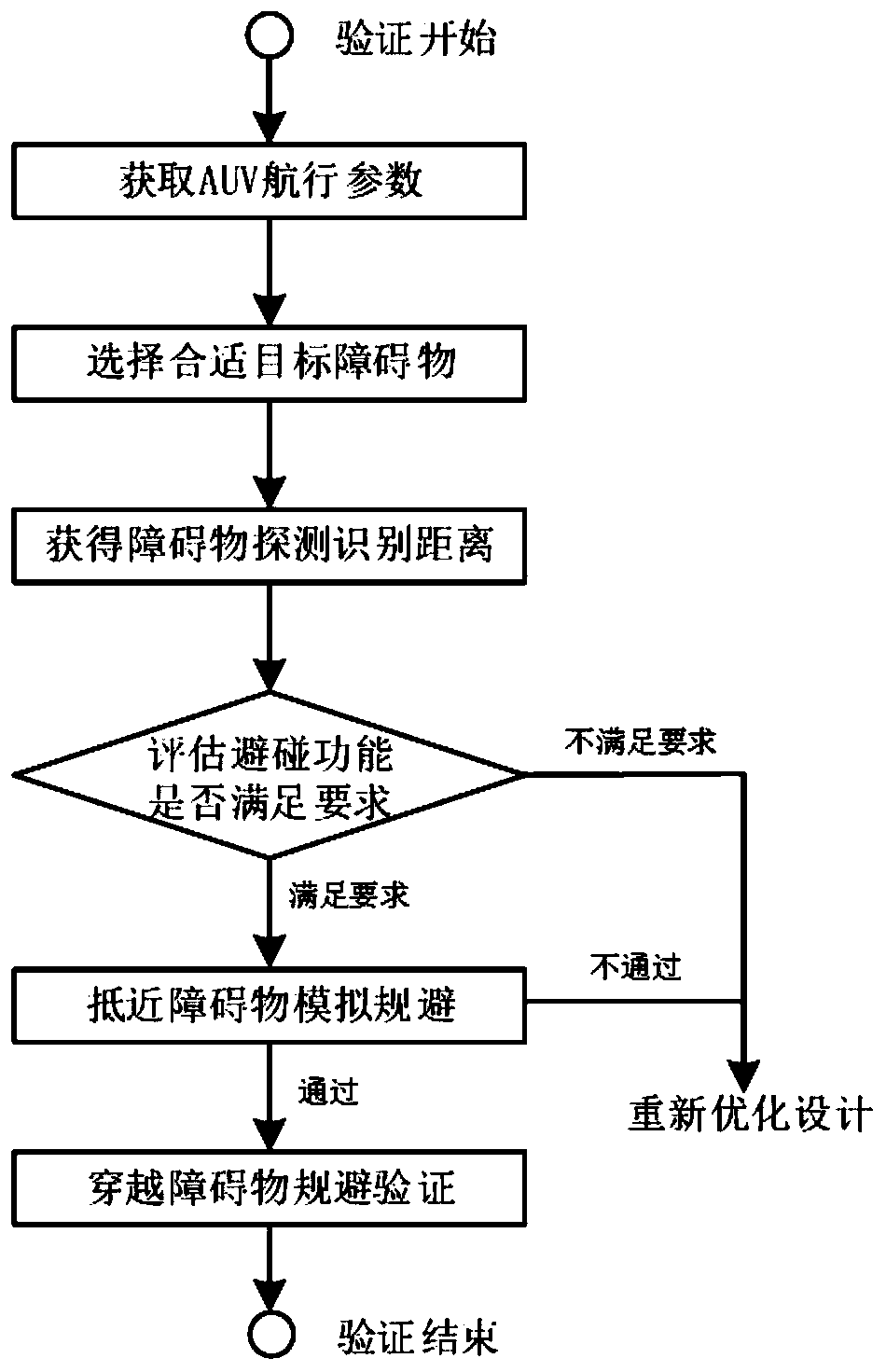
ActiveCN111176275AReduce trial riskReduce the difficulty of implementationPosition/course control in two dimensionsVehiclesTest efficiencyAlgorithm
The invention discloses an AUV collision avoidance function verification method which comprises the following steps: acquiring AUV related navigation parameters, acquiring an AUV obstacle detection and recognition distance, and performing operations such as approaching obstacle simulation avoidance, obstacle crossing collision avoidance and the like, thereby completing collision avoidance functionverification. The method can reduce the test risk and improve the test efficiency and is simple and efficient, clear and feasible, lower in implementation difficulty and safe in verification process.
Owner:中国船舶重工集团有限公司第七一0研究所
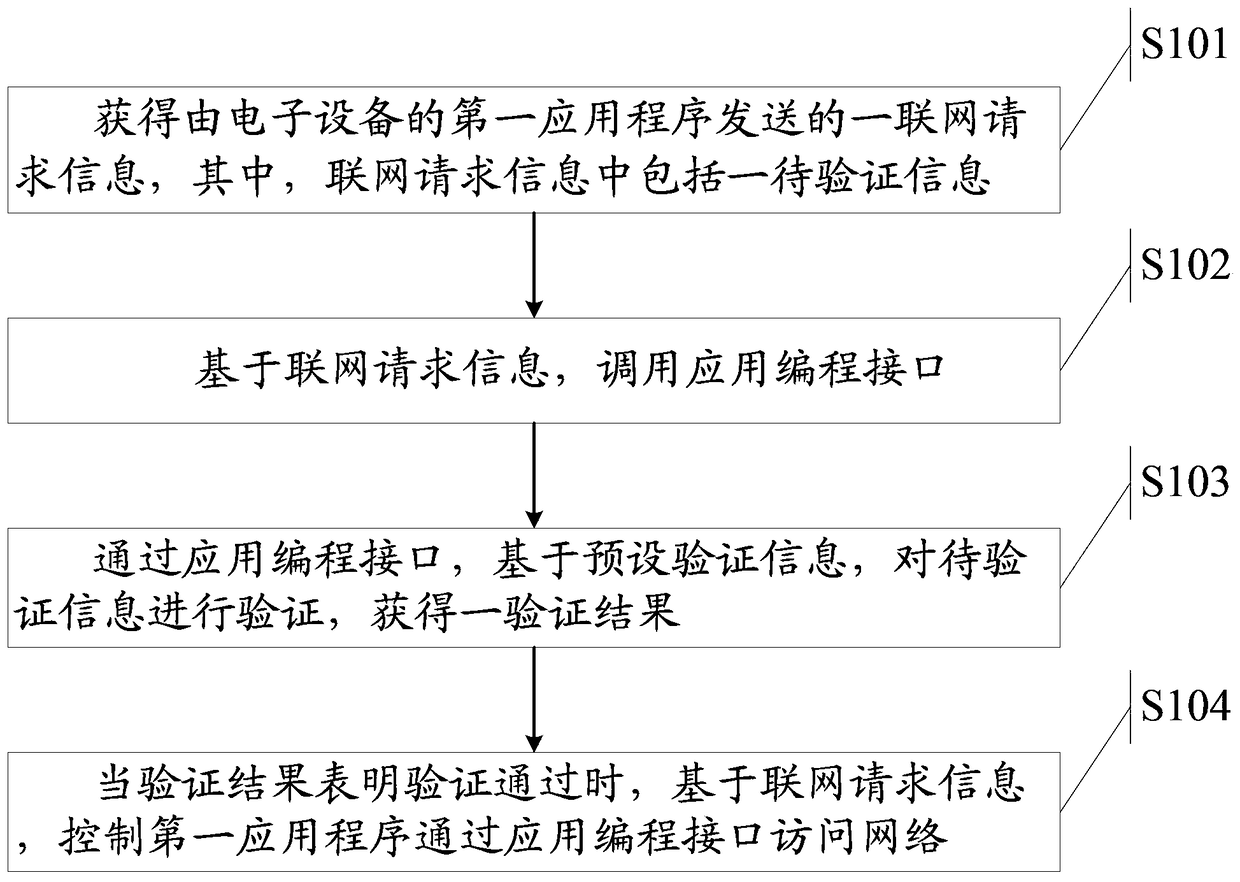
A method for networking and electronic equipment
ActiveCN103873439BEasy accessSolve the technical problem of unreliable access to the networkTransmissionApplication programming interfaceApplication software
The invention discloses a networking method and electronic equipment. The method is applied to an electronic device, and the electronic device includes an application programming interface including preset verification information, wherein the application programming interface is used to connect to a network, and the method includes: obtaining the first authentication information from the electronic device A networking request information sent by an application, wherein the networking request information includes information to be verified; based on the networking request information, calling the application programming interface; through the application programming interface, based on the preset The verification information is used to verify the information to be verified to obtain a verification result; when the verification result indicates that the verification is passed, based on the networking request information, control the first application program to access the network through the application programming interface.
Owner:LENOVO (BEIJING) LTD
A method for identifying the integrity of transaction information
A method and device for authenticating the integrity of transaction information, the method comprising: a terminal device receives a transaction instruction sent by a host computer, parses the transaction instruction to obtain a first message verification code and transaction information to be verified; the transaction information to be verified is divided into blocks to obtain Transaction information block, generate a third key based on the first key, generate a fourth key based on the second key, generate a fourth key based on the transaction information block, the first key, the second key, the third key and the fourth key Perform calculations to generate authentication message verification codes; judge whether the authentication message verification code matches the first message verification code, if yes, the transaction information is complete, execute the transaction instruction, return the transaction result to the upper computer, and end; otherwise, the transaction information is incomplete, Refuse to execute the transaction order, return an error code to the host computer, and end. Therefore, in the process of calculating the verification code according to the transaction information to be verified, the transaction information to be verified is processed multiple times, and the important data in the transaction information is more secure during the verification process.
Owner:FEITIAN TECHNOLOGIES
Intelligent oscillograph safety protection method and system and computer readable storage medium
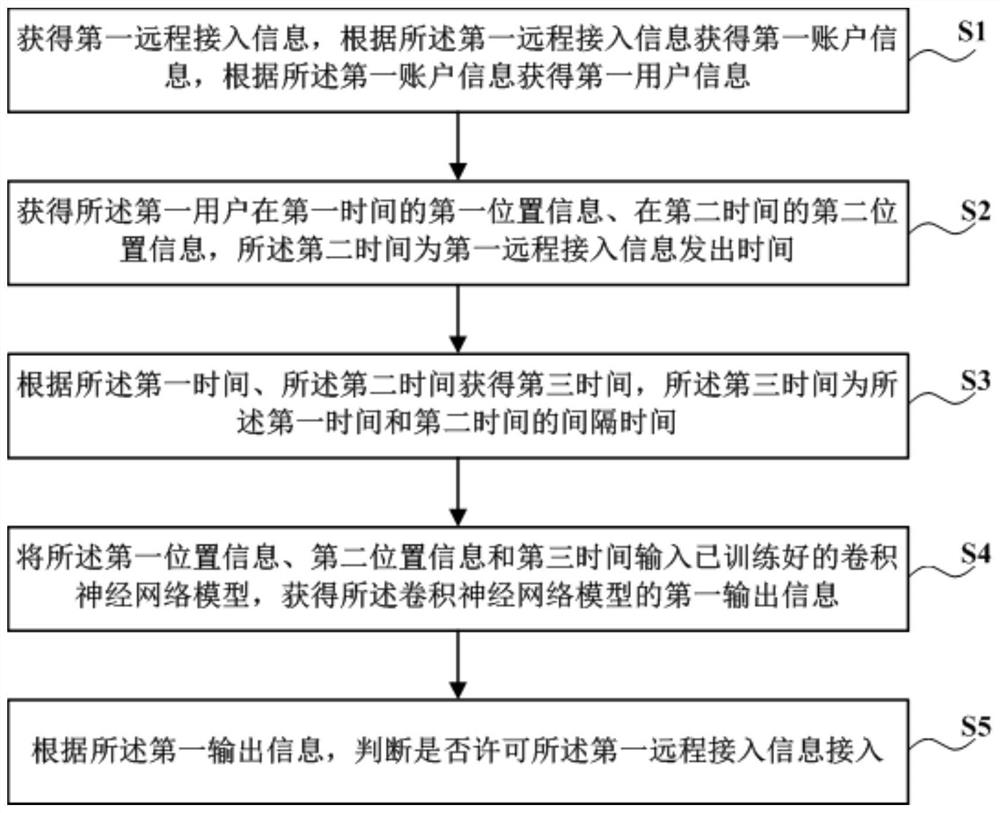
ActiveCN112788041AAccurate verificationSafety verificationNeural architecturesTransmissionEngineeringData mining
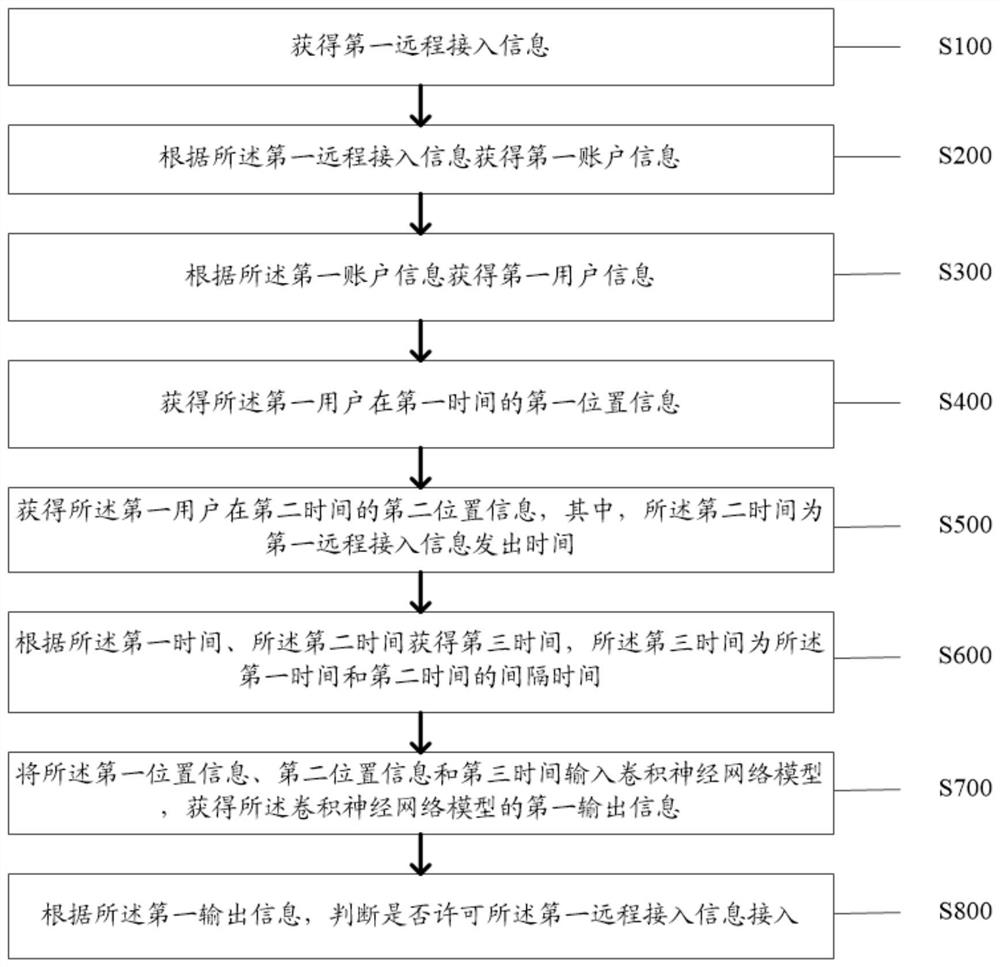
The invention discloses an intelligent oscillograph safety protection method and system and a computer readable storage medium, and the method comprises the steps: obtaining first remote access information; obtaining first account information according to the first remote access information; obtaining first user information according to the first account information; obtaining first position information of the first user at the first time; obtaining second position information of the first user at second time; obtaining third time according to the first time and the second time, wherein the third time is interval time between the first time and the second time; inputting the first position information, the second position information and the third time into a convolutional neural network model to obtain first output information of the convolutional neural network model; and judging whether the first remote access information is permitted to access according to the first output information. According to the invention, the technical problem that the verification of the information of the remote access oscillograph is not safe and accurate enough in the prior art is solved.
Owner:SHENZHEN POWER SUPPLY BUREAU
Service life management method of active medical instrument
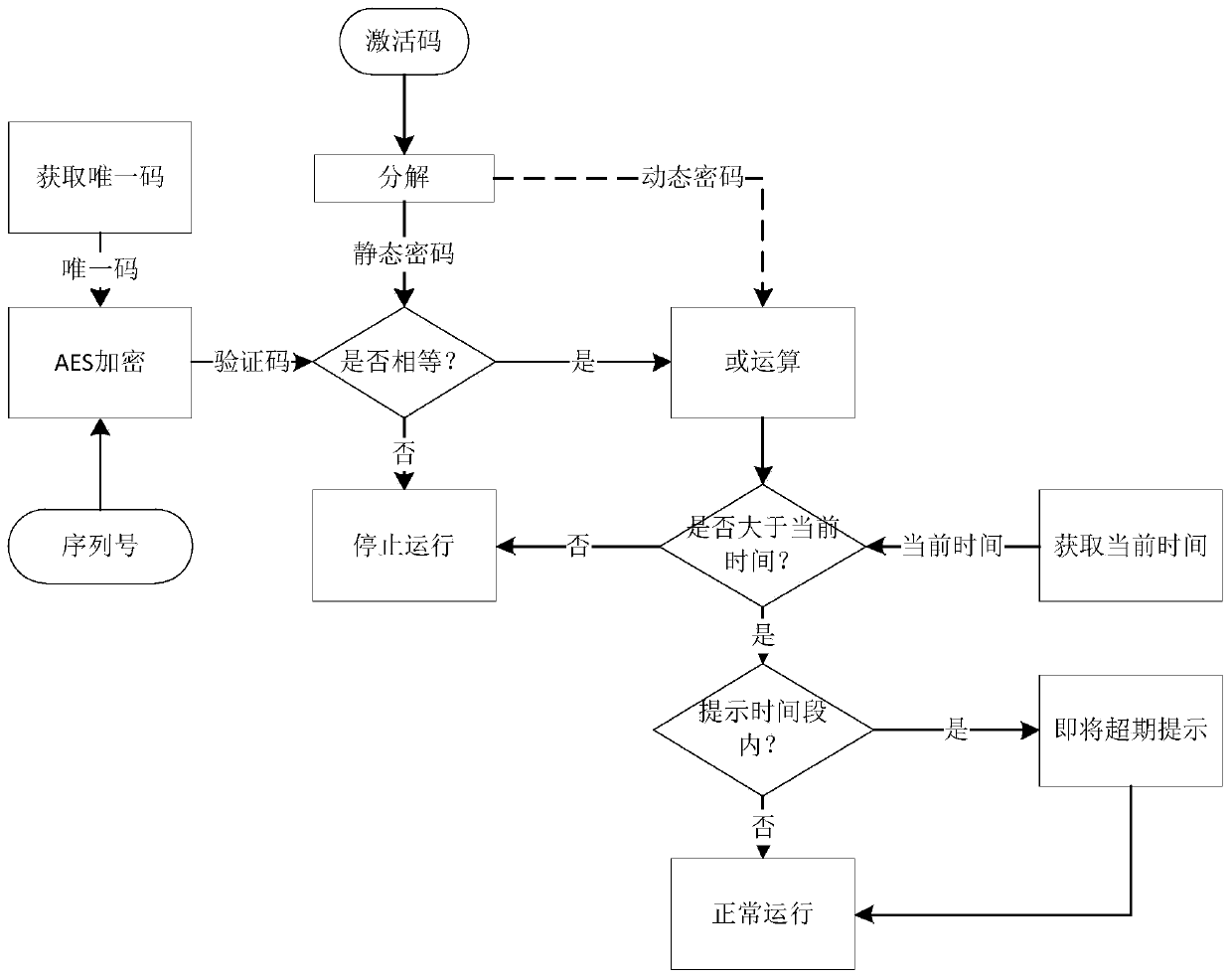
PendingCN111415734AVerify process safetyNo human intervention requiredMedical equipmentLocal machineLife management
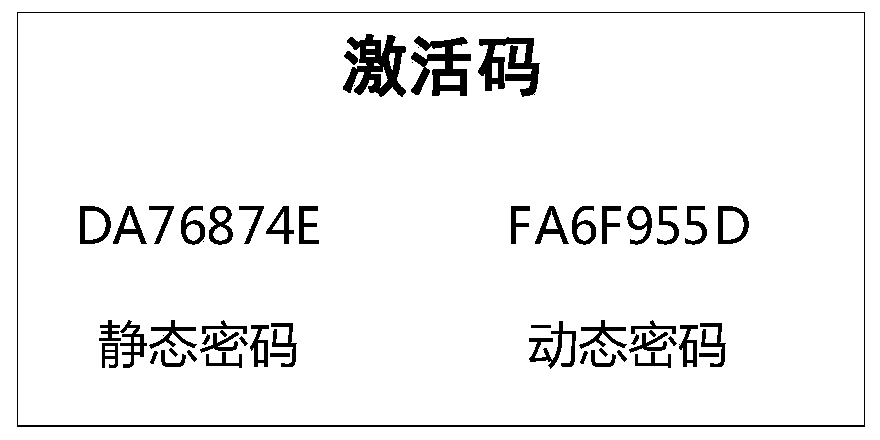
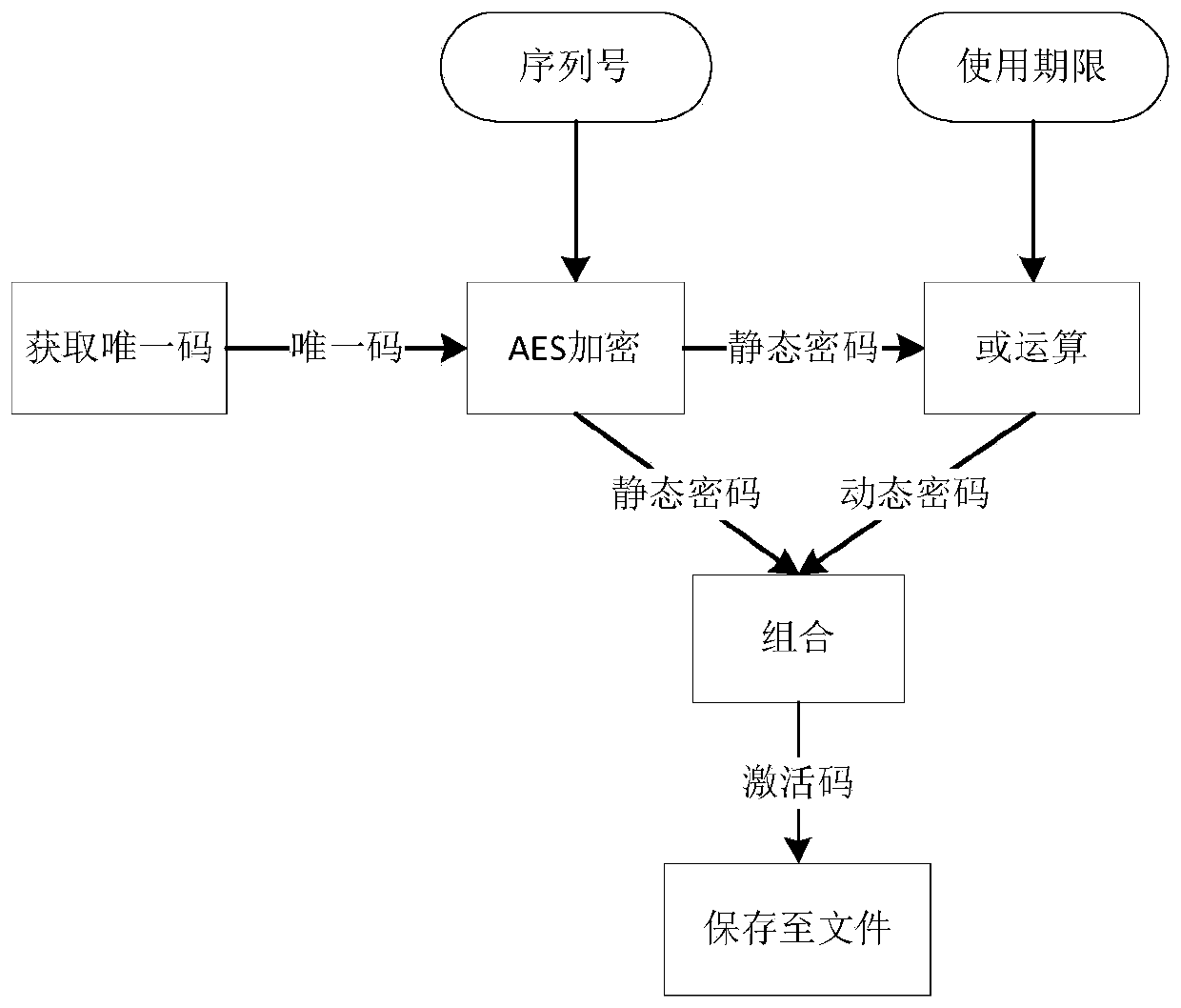
The invention provides a service life management method of an active medical instrument, and belongs to the field of medical equipment management. The service life of the active medical instrument ismanaged through the registration unit and the verification unit; the registration unit forms an activation code based on a registration code and a unique code, and the verification unit receives a file with the activation code, analyzes the activation code, judges whether the activation code is an activation code of a local machine or not, analyzes and judges the service life if the activation code is the activation code of the local machine, and shuts down if the activation code is not the activation code of the local machine. And after analyzing and judging the service life, the service lifeof the local machine is managed. The verification process is safe and reliable, off-line verification is supported, and manual intervention is not needed; when the equipment is about to reach the service life, a medical equipment using unit is prompted in advance, and after the equipment date expires, the equipment stops running except for the condition specified by Medical Instrument Supervisionand Management Regulations, so risks caused by overdue use are prevented.
Owner:四川天府南格尔生物医学有限公司
A mobile phone headset based on puf authentication and information encryption
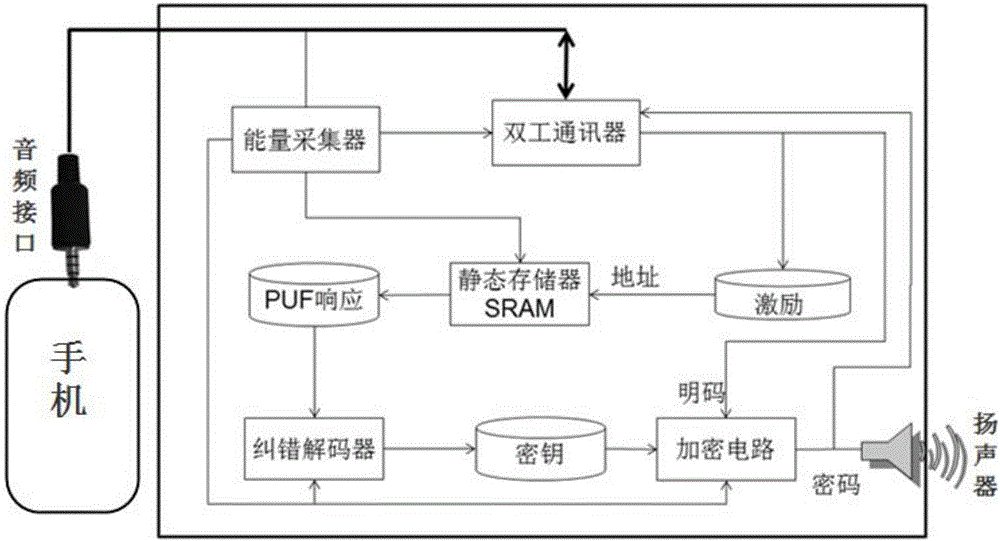
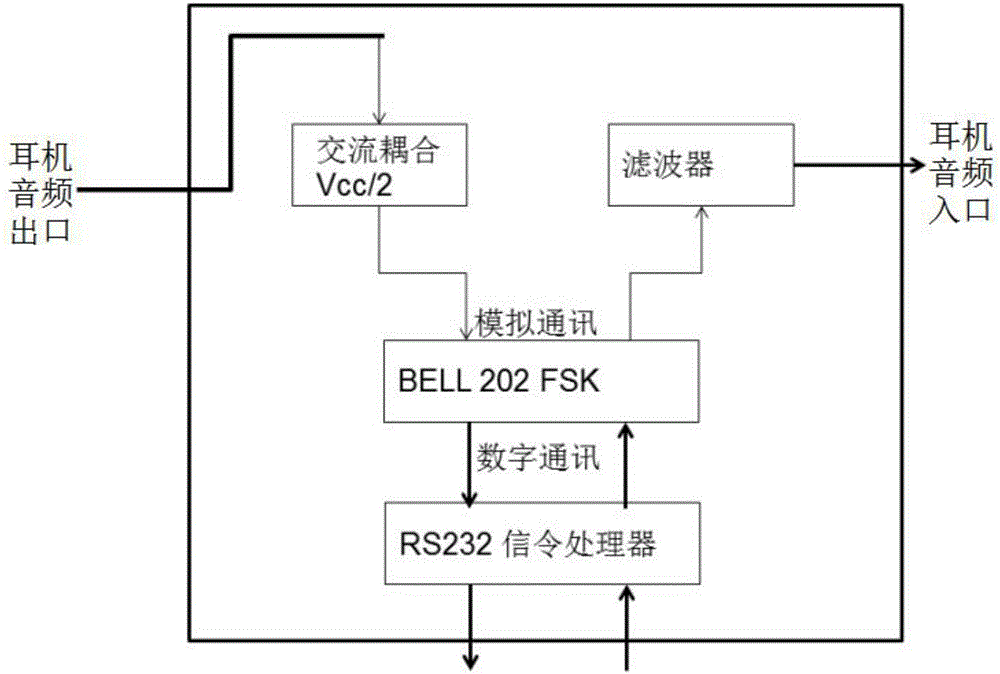
ActiveCN103888268BImprove securityQuick Security PolicyUser identity/authority verificationEarpiece/earphone attachmentsComputer hardwarePower flow
The invention relates to a mobile phone earphone based on PUF identity authentication and information encryption. The mobile phone earphone based on PUF identity authentication and information encryption is characterized in that a PUF module is arranged between an earphone audio interface and an earphone loudspeaker and is inlaid in the mobile phone earphone; the PUF module comprises an energy collector, a duplex communicator, a static storage, an error correction decoder and an encrypted circuit; the energy collector, the duplex communicator and the earphone audio interface are connected; the energy collector obtains voltage and current through the audio interface and supplies power to other modules after processing the voltage and the current; the duplex communicator is in intercommunication with a mobile phone through the earphone audio interface, and is further connected with the static storage and the encrypted circuit; the static storage is connected with the error correction decoder; the error correction decoder is connected with the encrypted circuit; the encrypted circuit is connected with the earphone loudspeaker. By the adoption of the PUF technology, the safety problem of an existing encryption algorithm is solved through hardware encryption, and the mobile phone earphone becomes a special device for identity authentication, information encryption and payment security enhancement.
Owner:TIANJIN LIANXIN TECH
A method for preventing duplicate address detection attacks based on identity authentication
ActiveCN103297563BLegal and orderly useConvenient queryUser identity/authority verificationProtocol for Carrying Authentication for Network AccessSimple computation
A method for preventing duplicated address detection attack on the basis of identity authentication is a scheme for preventing the duplicated address detection attack in an Internet Protocol version 6 (IPv6) network and is used for solving the problem of service denial attack against duplicated address detection (DAD) in the IPv6 network. The IPv6 network is not extremely high in service denial attack resistance. A system for the method is composed of a verification server, an encryption / decryption module, an update module and a mapping storage module and the like. The identity authentication on a network access device corresponding to DAD is achieved through the modules by simple calculation, operations regulated in an original IPv6 protocol can be performed only when identity authentication is performed, and no response is made to the device corresponding to DAD once the identity authentication fails. Information in the verification server is updated timely after the authentication is finished once. Attack on the DAD in the IPv6 network through illegal network access devices is effectively eliminated.
Owner:NANJING UNIV OF POSTS & TELECOMM
Safe password storage verification method and device
ActiveCN107911343BSafe storageSafety verificationKey distribution for secure communicationEncryption apparatus with shift registers/memoriesEngineeringPassword hashing
The invention provides a secure password storage and verification method and device. When a password is stored, Salt is added into the password and the password is encrypted by a hash algorithm; a hash value of the password is stored into a server side; when a user logs in the server to carry out password verification, the server side generates token, and secondary encryption is carried out on thepassword hash value stored by the server side and a password hash value for logging in of the user by using the token as a key; and then comparison and verification are carried out. Therefore, the security of the password of the user during the storage and verification processes is improved.
Owner:SHENZHEN INFINOVA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com