A method for preventing duplicate address detection attacks based on identity authentication
A duplicate address detection and identity authentication technology, applied in the field of IPv6 security in the Internet, can solve problems such as serious consequences, achieve the effects of maintaining security, preventing attacks from duplicate address detection, and improving verification speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
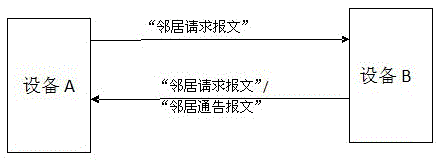
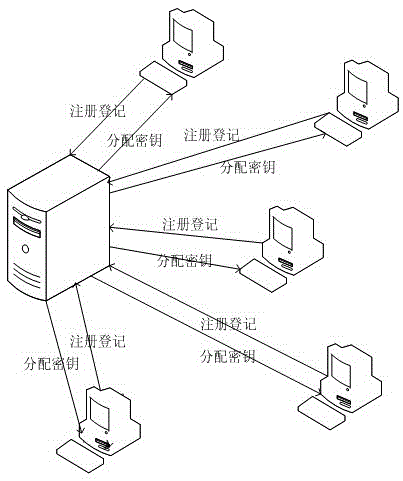
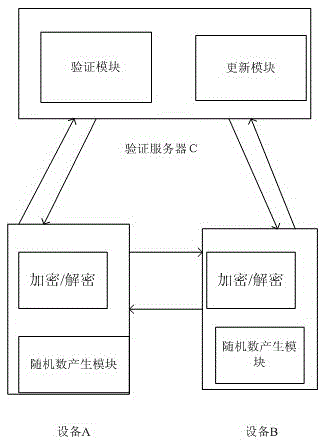
[0040] Here, we constructed a small wireless local area network in the laboratory to build an example of an overall solution to prevent DAD detection attacks. First, transform the devices in the network and add encryption / decryption modules to all network-connected devices. In addition to hardware encryption and decryption, this module can also generate random numbers to verify other devices. Each of these devices is assigned a serial number. Add the laboratory server as the authentication server (maybe set it to C) to the network.
[0041] Secondly, the small wireless LAN intranet devices in the laboratory are initialized, and all devices are registered on the server first, and a mapping table corresponding to the registration information is generated. Assuming that an unregistered device joins the network, it may be numbered B. Then, the same IPv6 address is manually assigned to the registered device and the unregistered device, so that their addresses are repeated.
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com