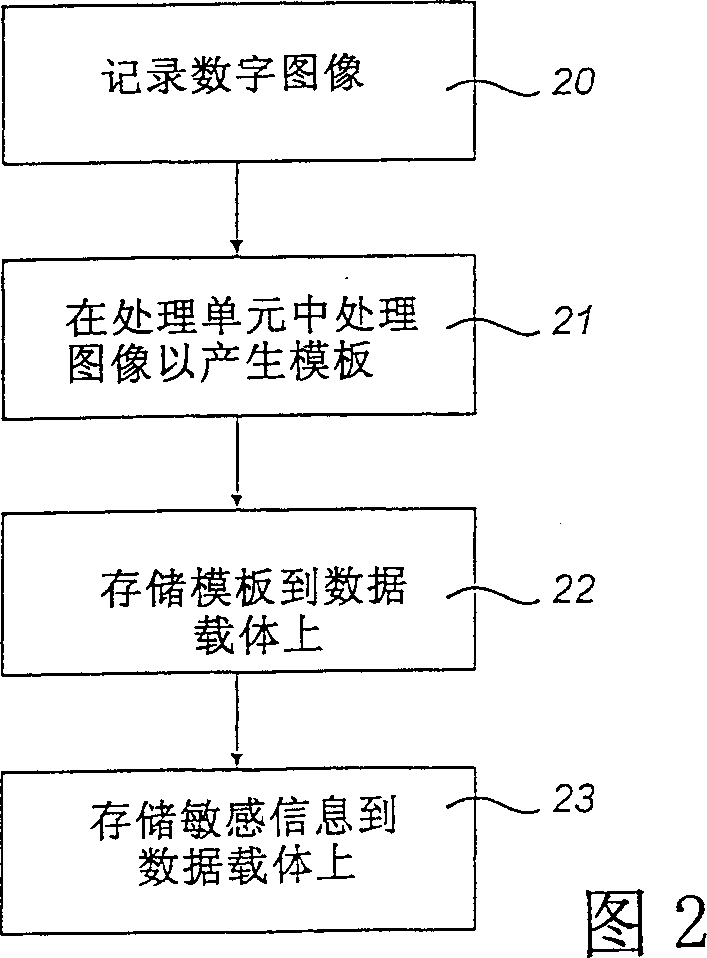
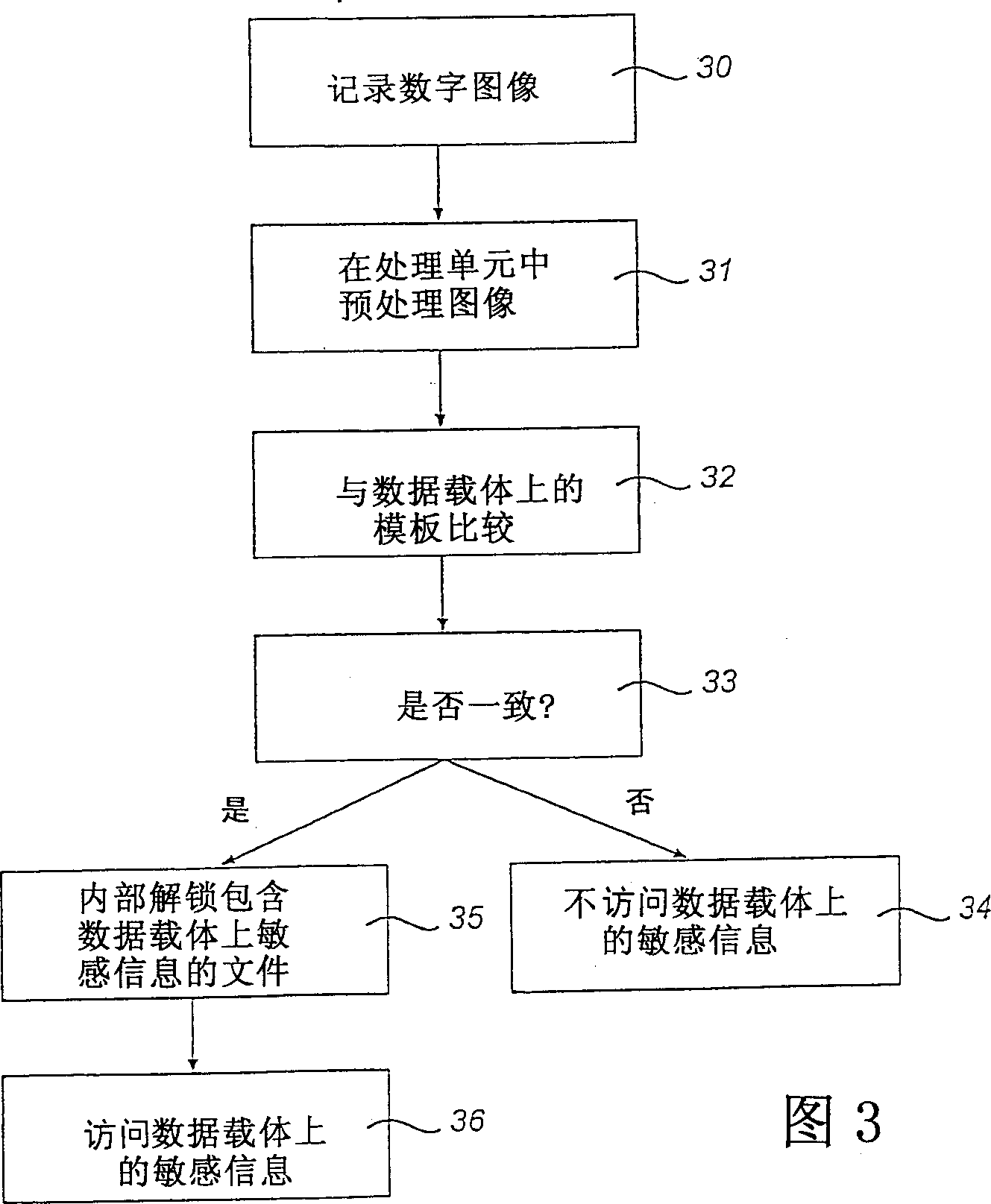
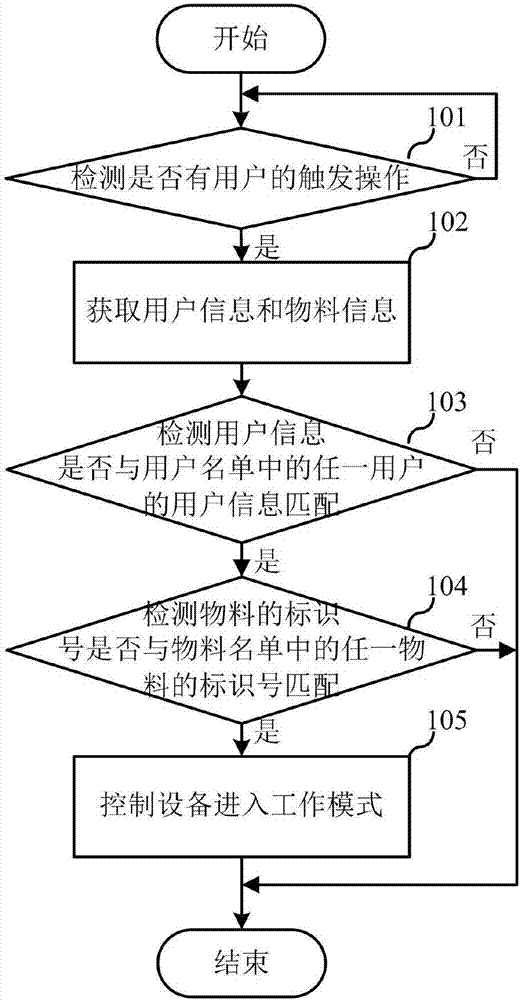
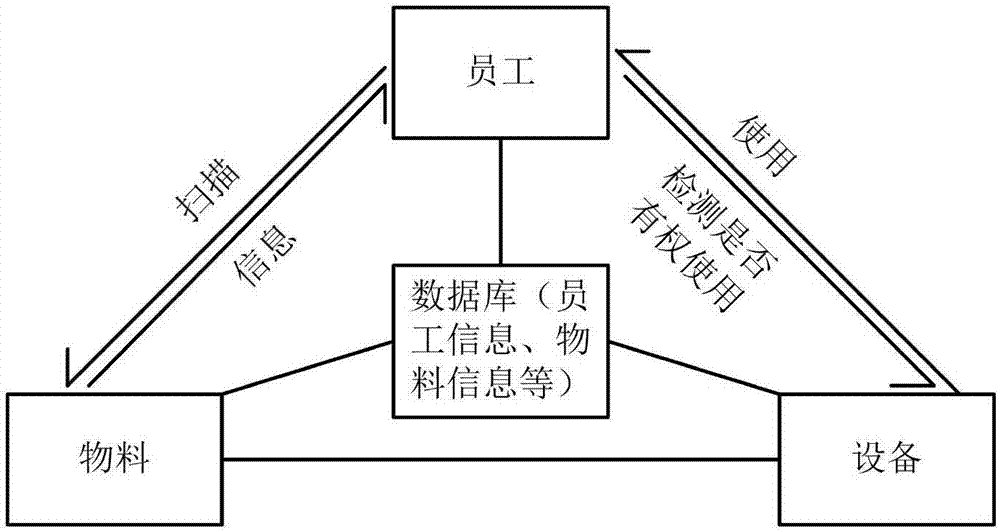
Patents
Literature
148results about How to "Improve verification speed" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
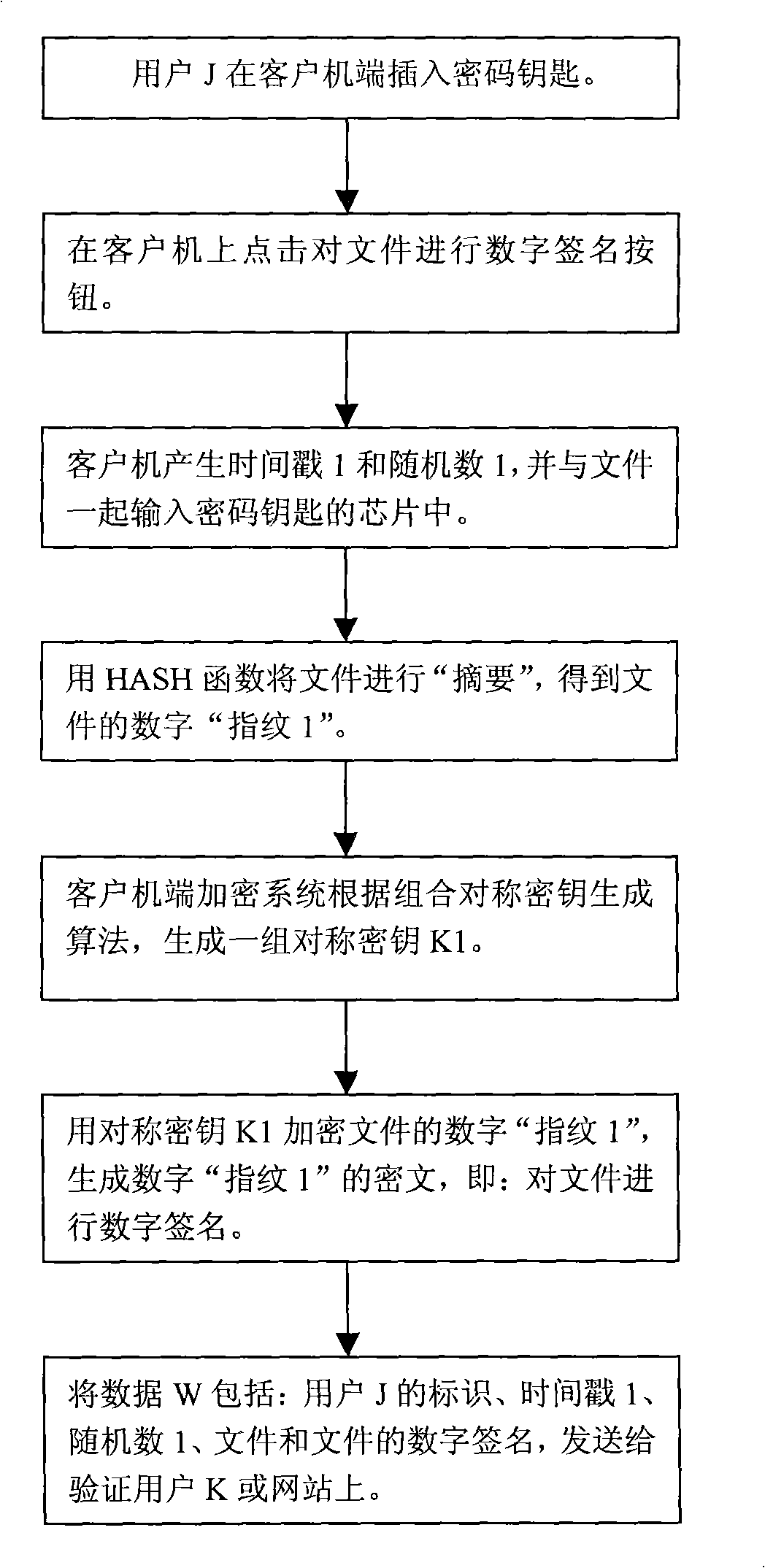
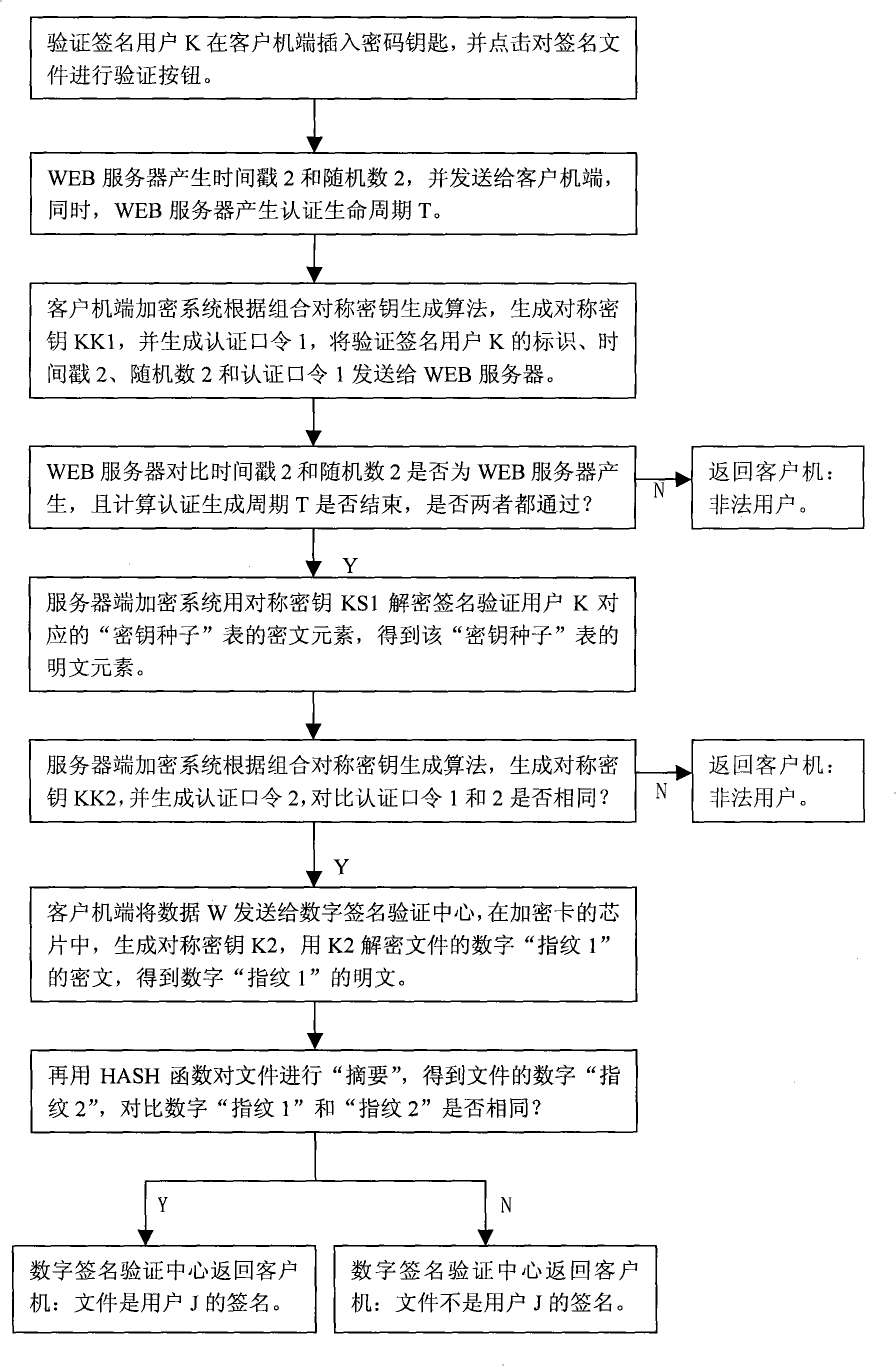
Digital signature method based on CSK
ActiveCN101282222AAvoid attackImprove security levelPublic key for secure communicationUser identity/authority verificationWeb siteSignature file
A digital signature method based on CSK establishes a digital signature checking center on the website for checking the signature file. A client computer is established with a ciphering system and a digital signature protocol. Each subscriber is distributed with a hardware device of the cipher key. A signature subscriber uses the cipher key for executing digital signature to the file. The digital signature protocol adopts a combined symmetrical cipher technique for executing digital signature to the file and realizes that the signature cipher is different each time. A signature checking subscriber also uses a cipher key for checking the signature file. The digital signature checking center firstly checks the identity of the signature checking subscriber, and subsequently executes the checking to the signature file. The identity checking protocol and the digital signature checking protocol are all completed with a combined symmetrical key technique thereby realizing the digital signature of the file and the checking to the signature file.
Owner:胡祥义
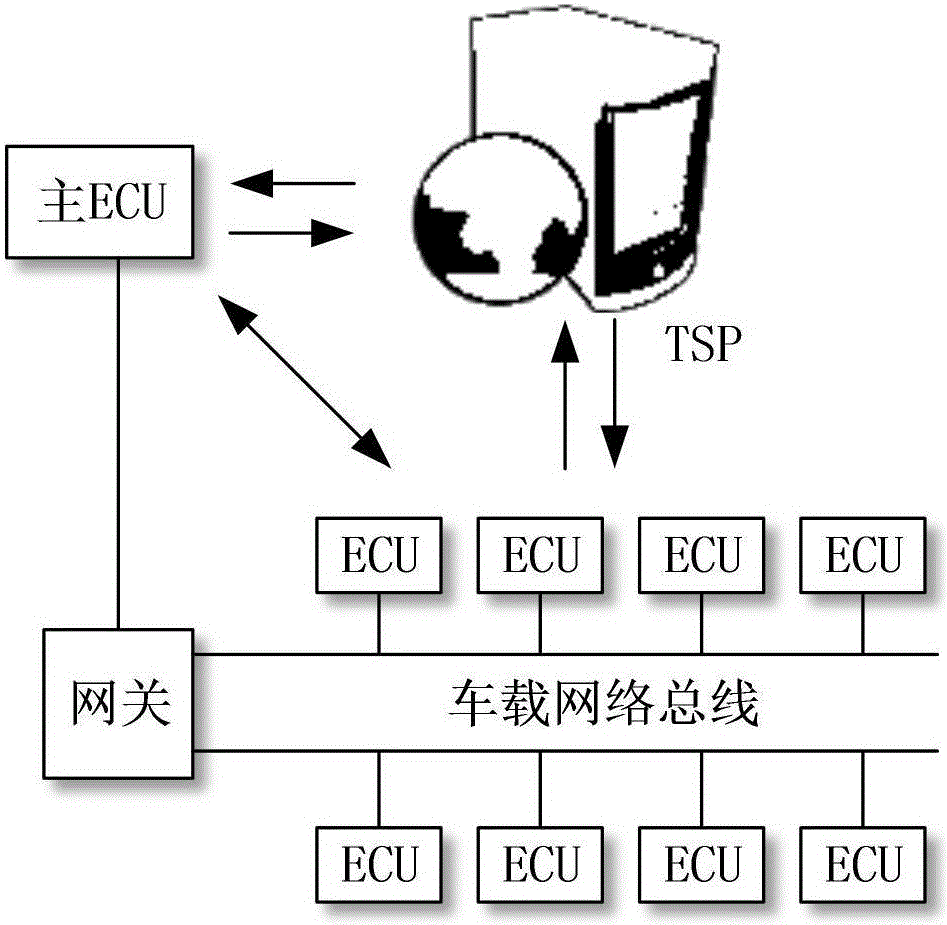
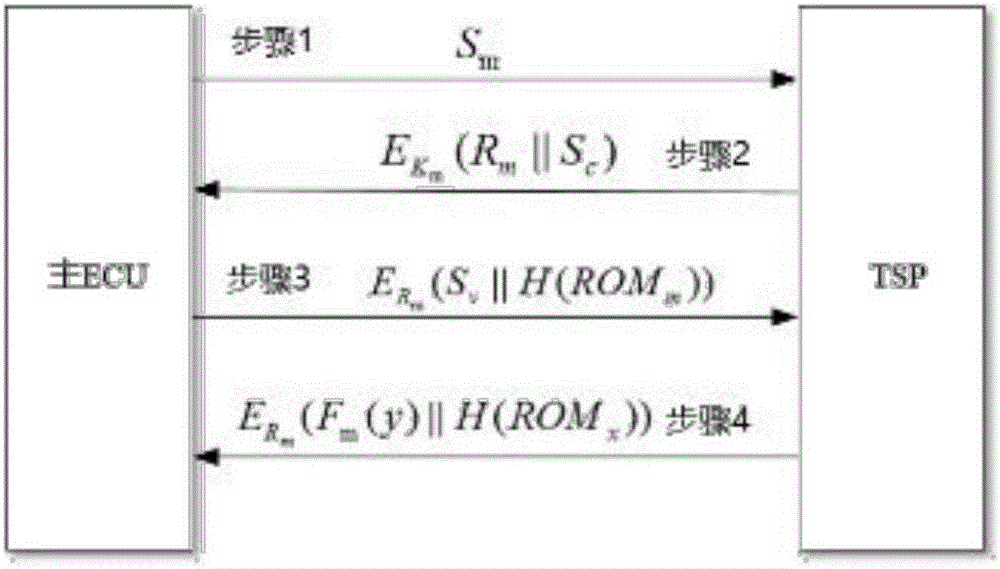
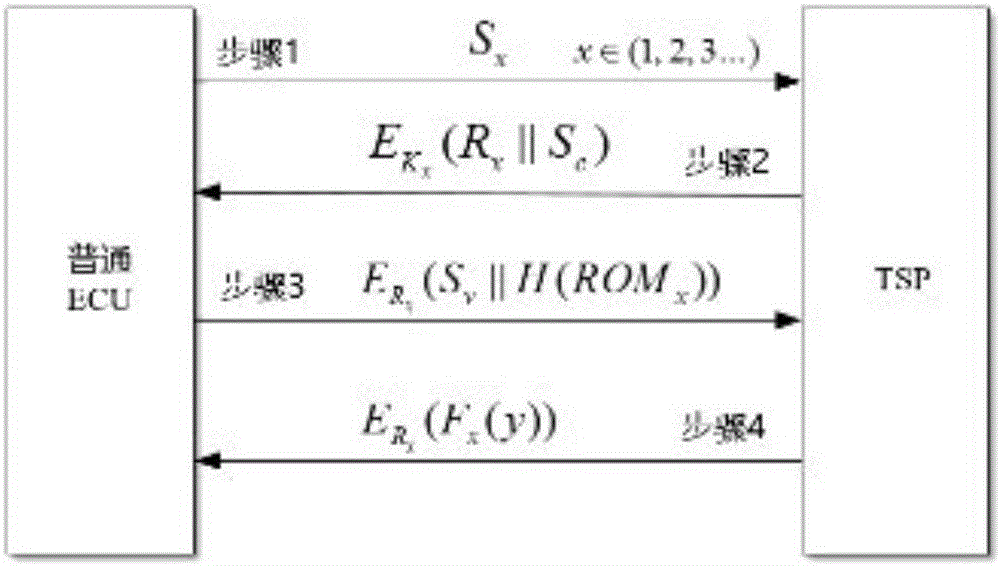
Key pre-distribution based automobile ECU integrity authentication and encrypted communication method
ActiveCN106027260AProtection securityImprove verification speedKey distribution for secure communicationUser identity/authority verificationComputer moduleTwo-step verification
The invention discloses a key pre-distribution based automobile ECU (Electronic Control Unit) integrity authentication and encrypted communication method. The key pre-distribution based automobile ECU integrity authentication and encrypted communication method comprises the steps of providing a unique session key for each ECU by using KPS; carrying out identity authentication through comparing ECU firmware Hash values; judging whether one ECU is tampered; and adopting a two-step authentication mechanism which combines local authentication with remote authentication, wherein safety authentication comprises automobile factory initialization and automobile start self-inspection. As the remote authentication and the local authentication are combined in the key pre-distribution based automobile ECU integrity authentication and encrypted communication method, a communication channel is safe, session keys among the ECU are different, and extremely high safety is obtained; as the keys rather than an encryption algorithm are pre-distributed to the ECU, the difficulty in key distribution is greatly reduced; as the integrity of each ECU is detected by comparison of the Hash values, the efficiency is high, and the cost is low; as key data are stored at a safety module of each ECU, physic attacks can be resisted; and after one original ECU is replaced and one ECU firmware is updated, authentication and encrypted communication still can be carried out by applying the safety mechanism.
Owner:CHENGDU UNIV OF INFORMATION TECH
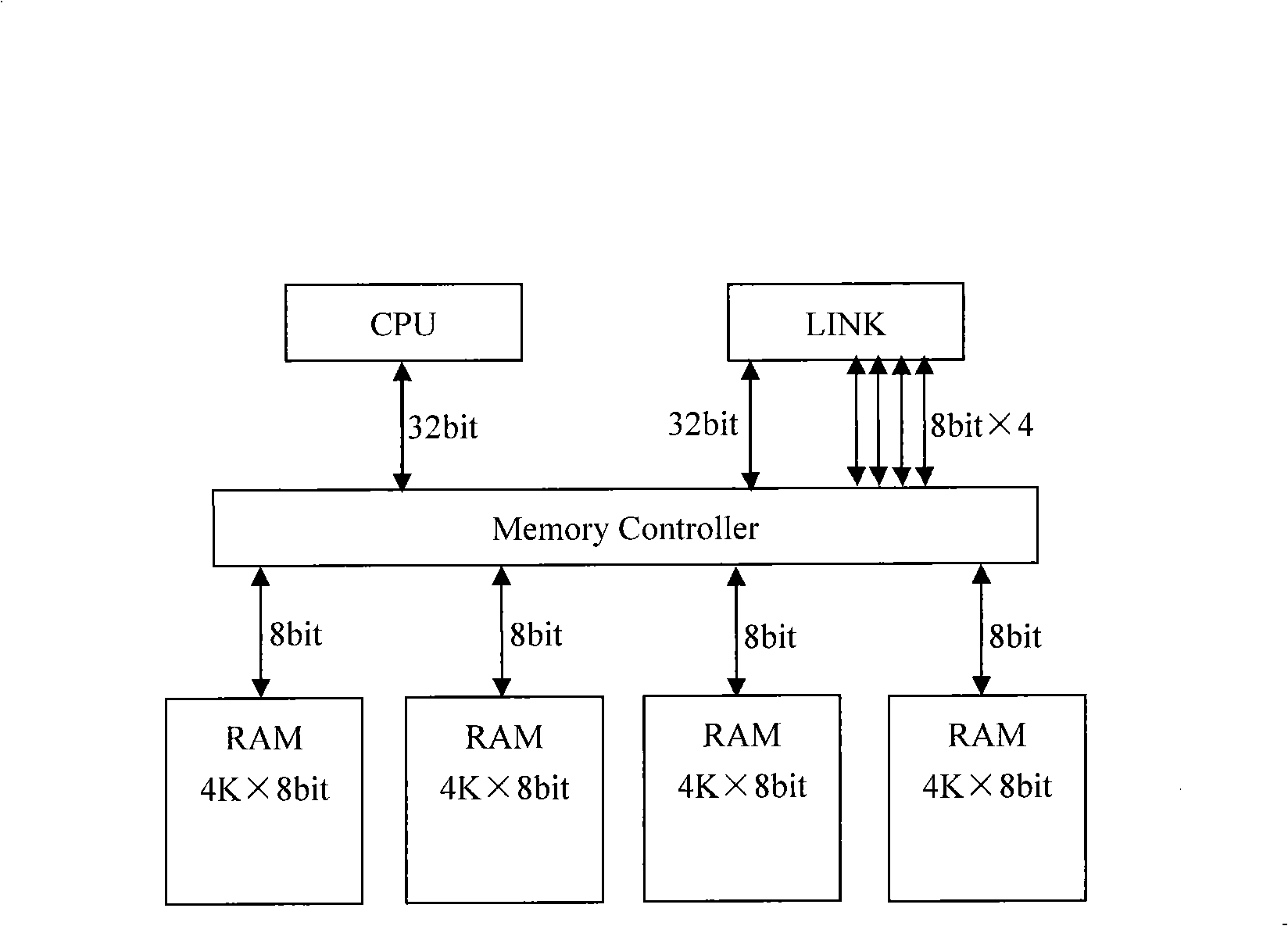
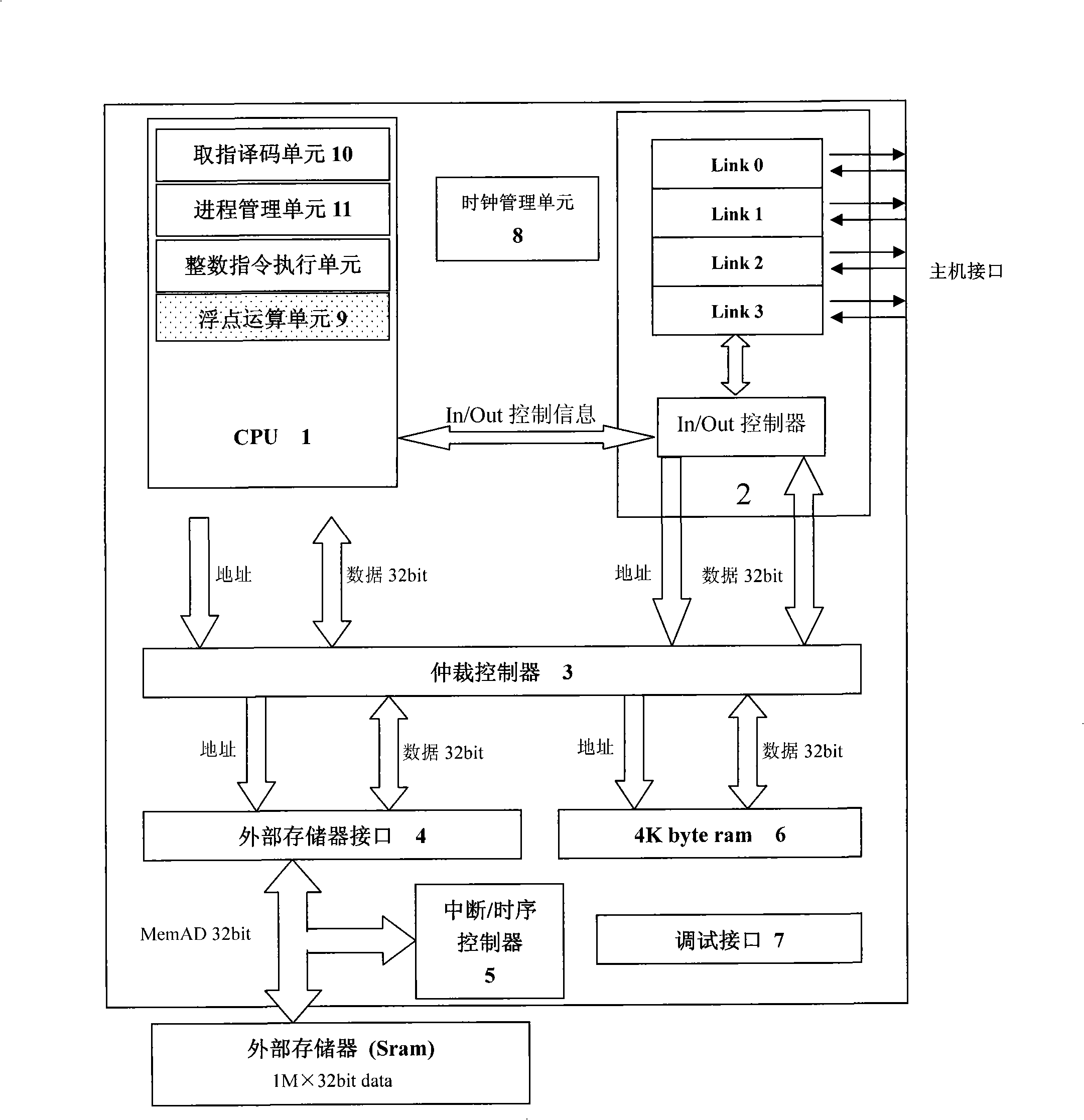
Paralleling microprocessor and its realization method
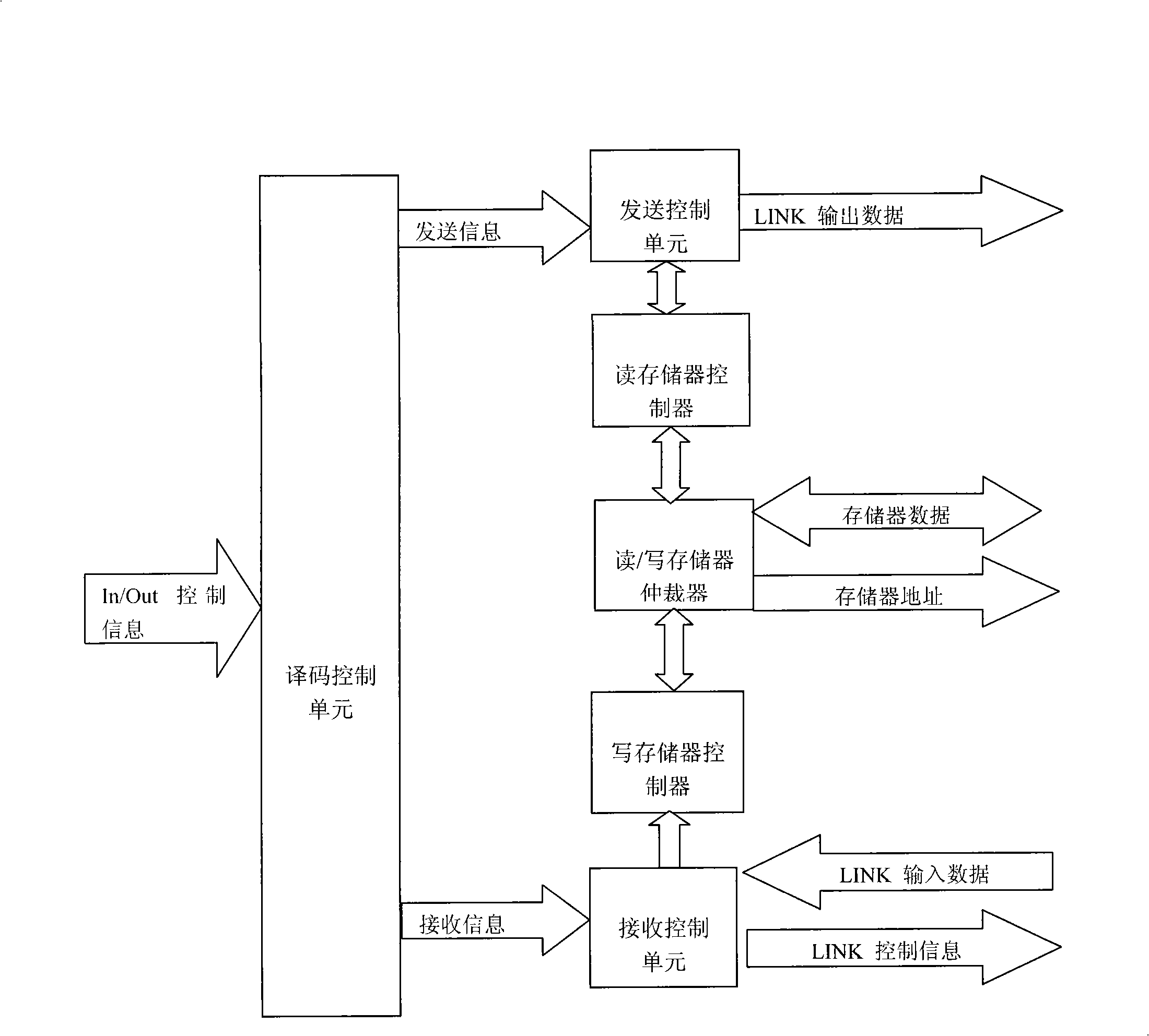
ActiveCN101334766ALow costEasy to modifyProgram initiation/switchingDigital data processing detailsInternal memoryParallel computing
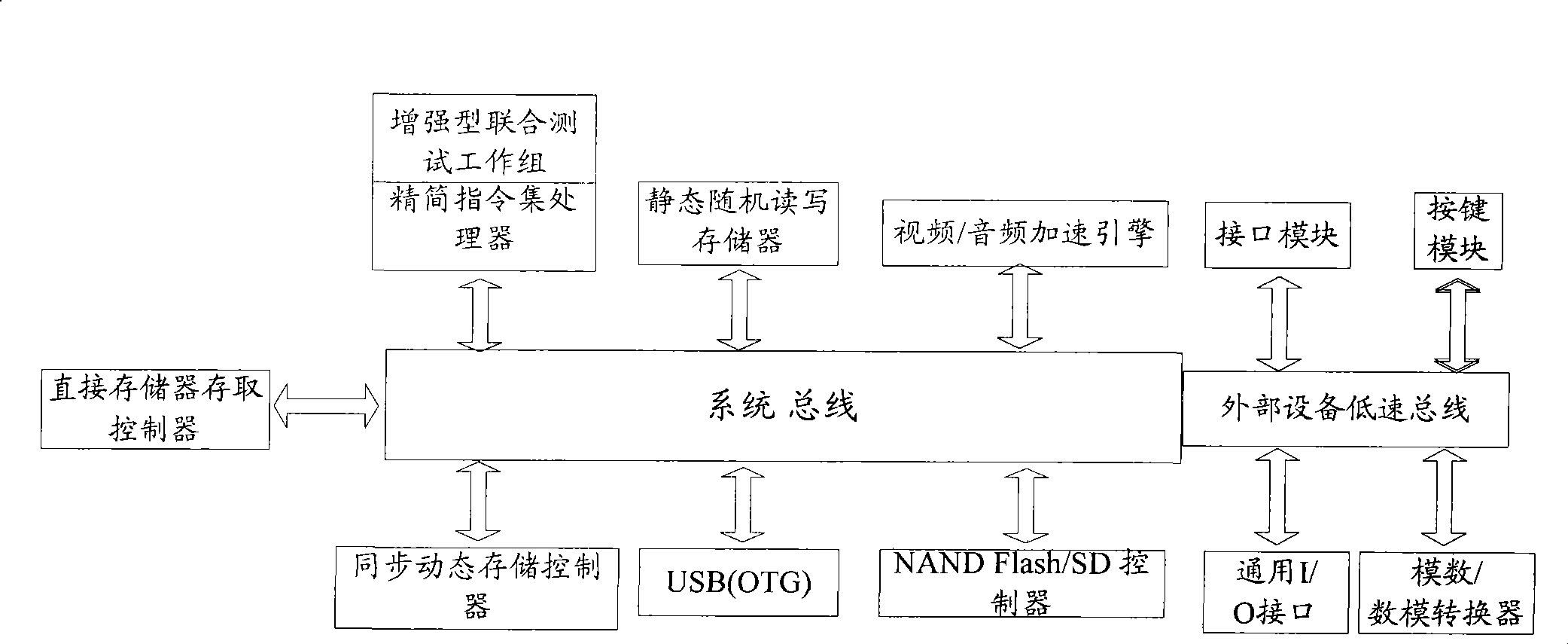
The invention relates to a parallel microprocessor and a corresponding realization method which are based on FPGA development. The parallel microprocessor comprises a CPU which is a 32-bit fixed-point CPU formed by a fetch decoding unit, a process management unit and an integer instruction execution unit; a communication module formed by a plurality of units of LINK channels and In / Out controllers; an arbitration controller used for arbitrating internal and external address buses and a data bus of the CPU; an external memory interface used for providing reading / writing time-sequence logic for an external memory; an interruption / time-sequence controller used for providing timing and interruption for the CPU; an internal memory used for providing the instructions of the CPU and quickly accessing data. The CPU is also provided with a floating point unit (FPU) combining the 32-bit fixed-point CPU to form a 64-bit floating point CPU. The 32-bit fixed-point parallel microprocessor and the 64-bit floating point parallel microprocessor provided by the invention work stably, bring convenience for system modification and debugging, accelerate verification speed and provide a low-cost operation platform for programs written in OccamII language.
Owner:NEUSOFT MEDICAL SYST CO LTD
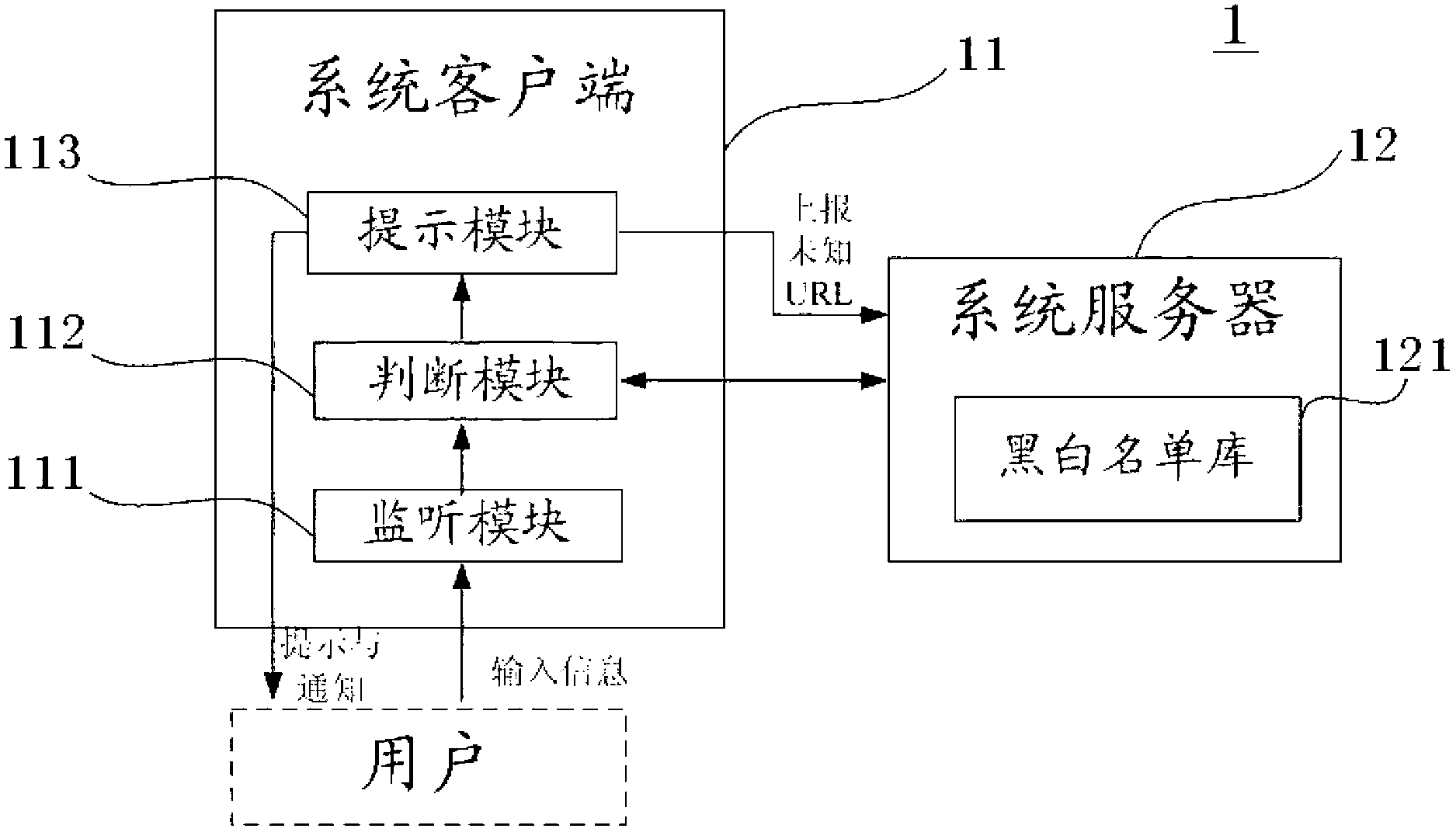
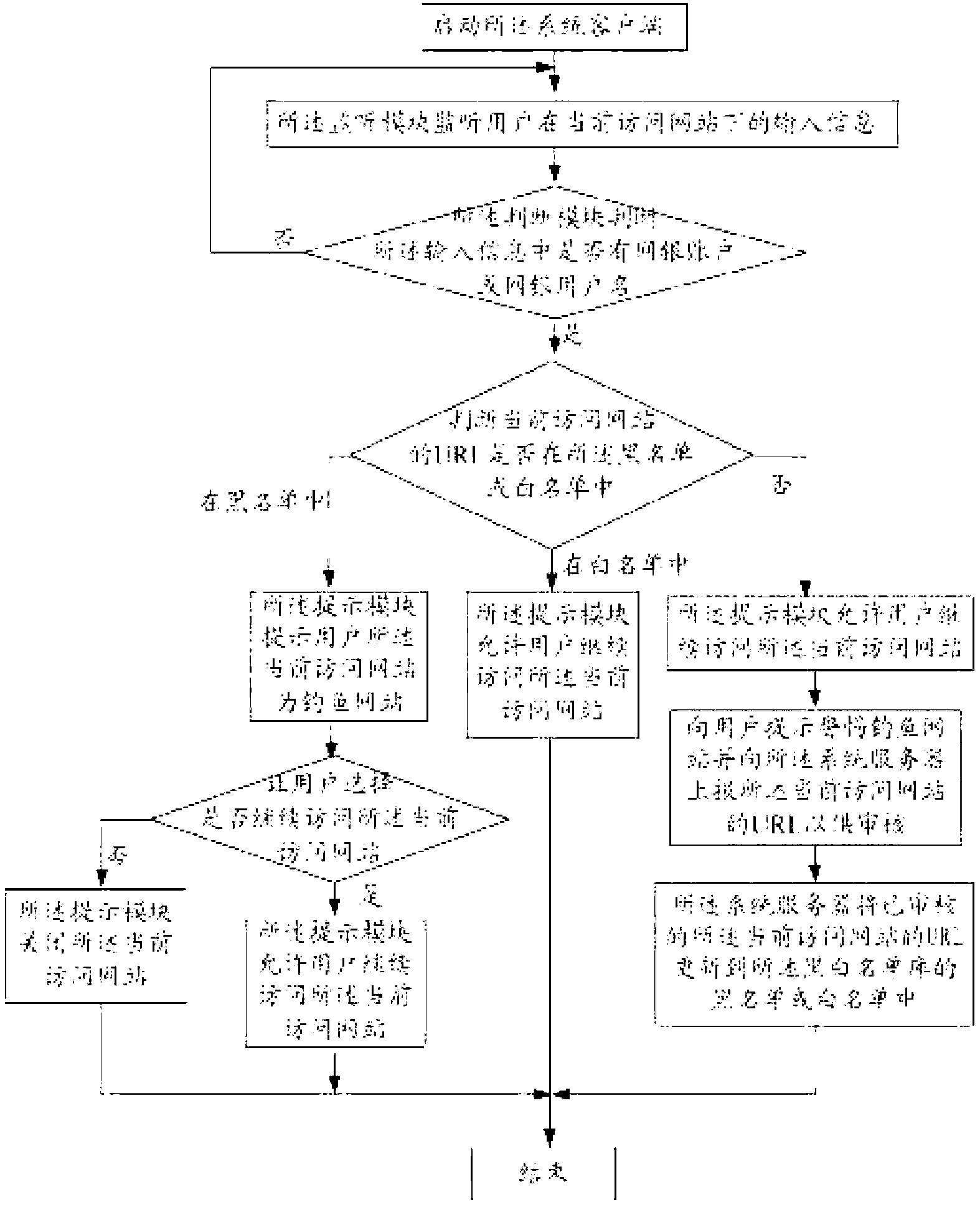
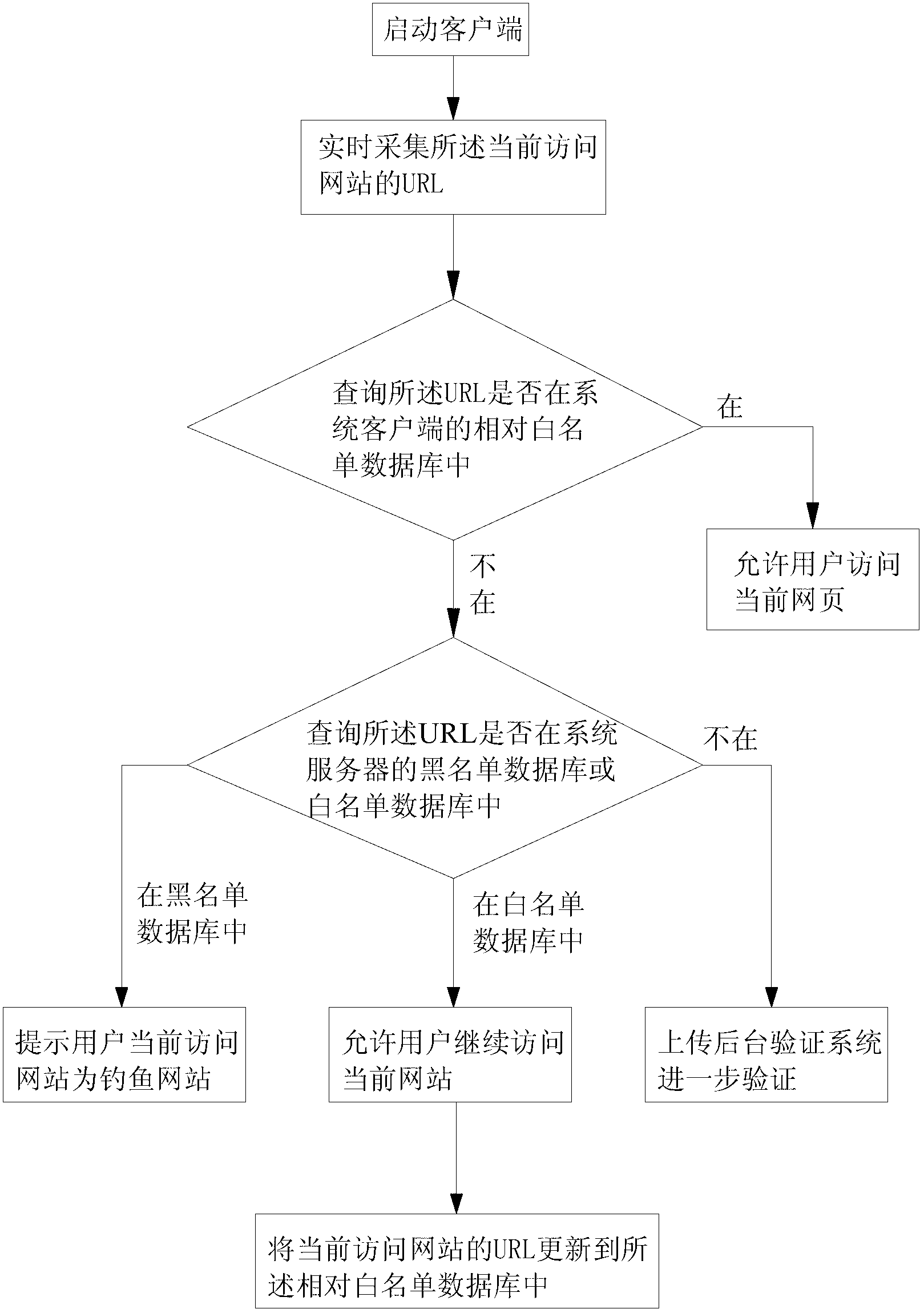
Method and system for detecting phishing website
The invention belongs to the technical field of network safety, in particular to a method and a system for detecting a phishing website. The method and the system adopt a technical scheme that the URL (Universal Resource Locator) of the current accessed website is acquired in real time; inquiring whether the URL is in a corresponding white list database of a system client, and the URL of an identified safe website in the system server in a preset time threshold value range is stored in the corresponding white list database, if in the range, the user is allowed to access the current website, and otherwise, the URL is uploaded to the system server for identification. According to the invention, repeatedly identifying the white and black lists in the system server in a period of time and in many places is avoided with the arrangement of a corresponding white list database, so that the black and white list identification speed is improved, and the operation load of the system server is lowered.
Owner:ZHUHAI BAOQU TECH CO LTD
Integrated circuit front-end verification method
InactiveCN102622471AImprove verification speedReduce the burden onSpecial data processing applicationsRegression testingTest case
The invention discloses an integrated circuit front-end verification method, which includes: establishing a verification platform for a top module to be tested, calling the top module of the verification platform through verification scripts, and establishing a simulation environment used in verification; allowing the verification platform to transmit a header file for configuring parameters of the module to be tested before compiling of the top module to be tested, and configuring the top module to be tested according to configuration of the header file when the top module to be tested is compiled; nesting open interface scripts used before and after simulation, and configuring a simulation environment; appointing parameters used by the verification platform through the interface scripts open to developers by the verification platform; passing the scripts in by regression testing according to the appointed parameters for the verification platform and calling a test case to verify the top module to be tested; and covering all covering points of the top module to be tested according to functional coverage. By the method, burden can be relieved for verification engineers, and verification speed is high.
Owner:SHANDONG SINOCHIP SEMICON
System and method for validating and testing on-chip system
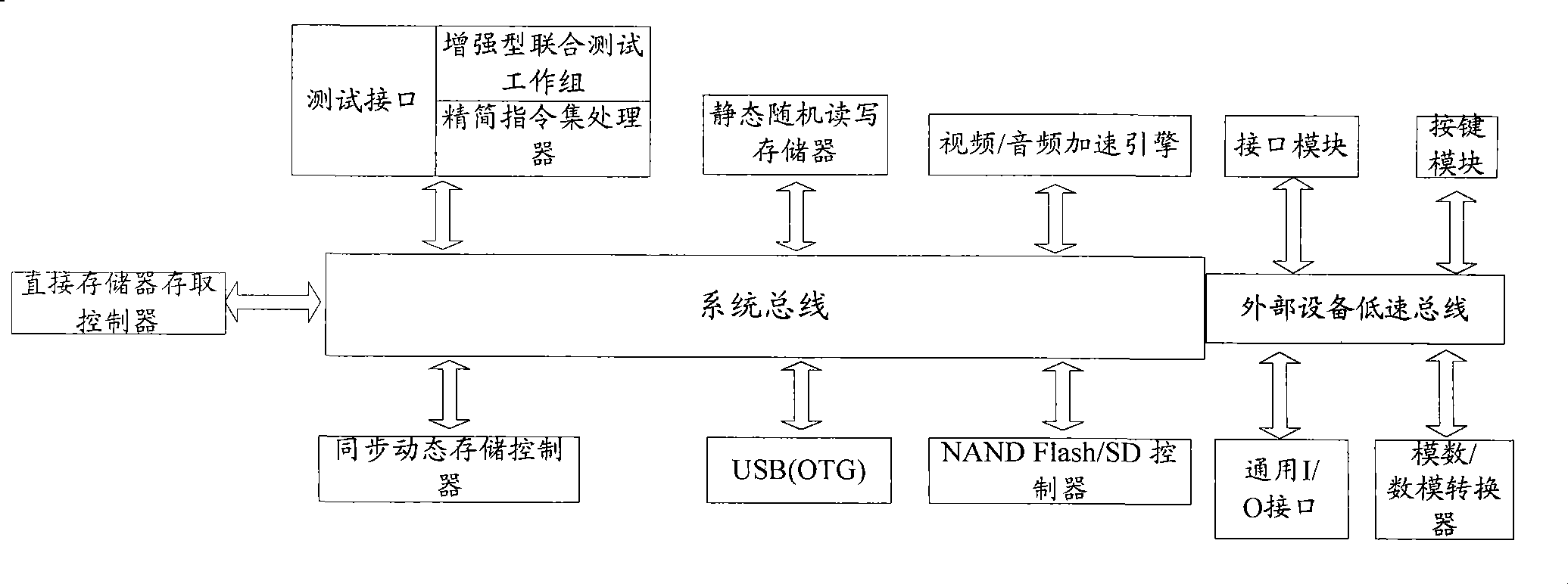
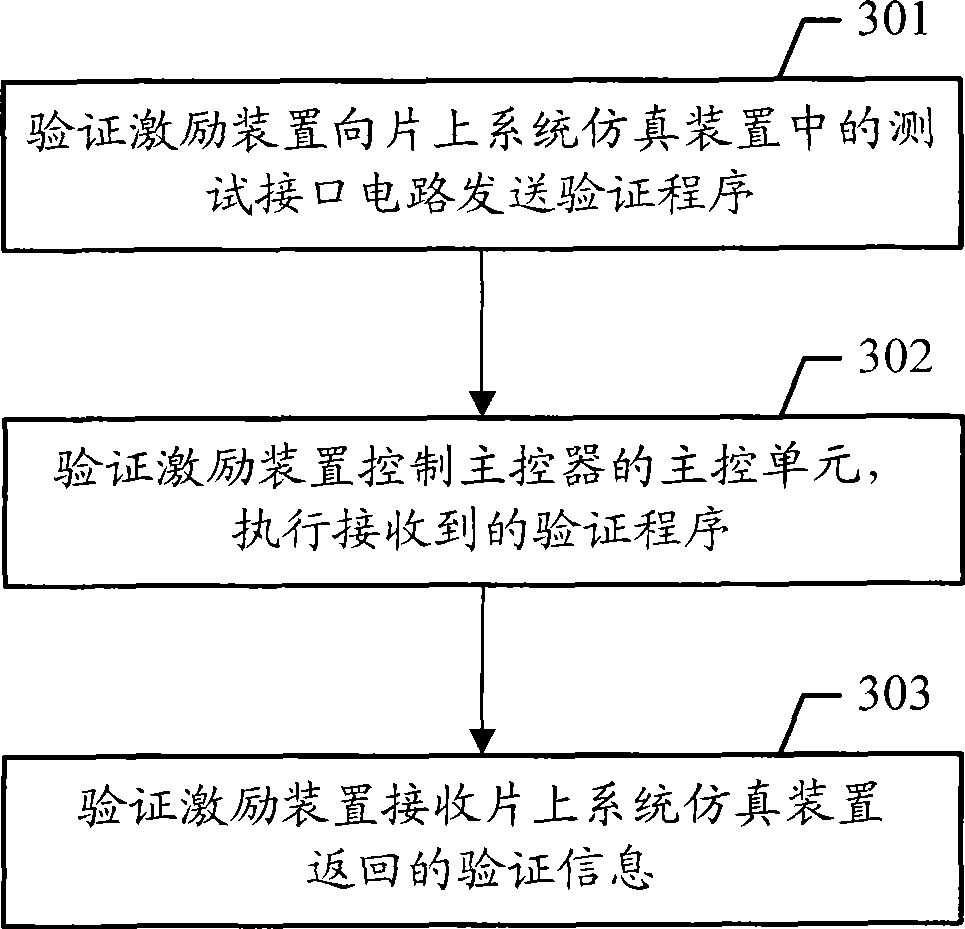
InactiveCN101504692AReduce latencyImprove verification speedSpecial data processing applicationsLow speedInterface circuits
The invention discloses a system for verifying a system on a chip (SoC), which is used for solving the problems of low speed and requirement of a large number of pins when the SoC is verified in the prior art. The system comprises a verification exciting device and an SoC simulation device, wherein the verification exciting device is connected with a test interface circuit in the SoC simulation device and used for transmitting a verification program to the test interface circuit, driving the SoC simulation device to execute the received verification program, and receiving verification information returned by the SoC simulation device; and the SoC simulation device is used for receiving the verification program, executing the received verification program under the driving of the verification exciting device, and returning the verification information to the verification exciting device. The invention also discloses a method for verifying the SoC and a system and a method for verifying the SoC.
Owner:ACTIONS ZHUHAI TECH CO
Public bicycle renting system using two-dimensional code scanning
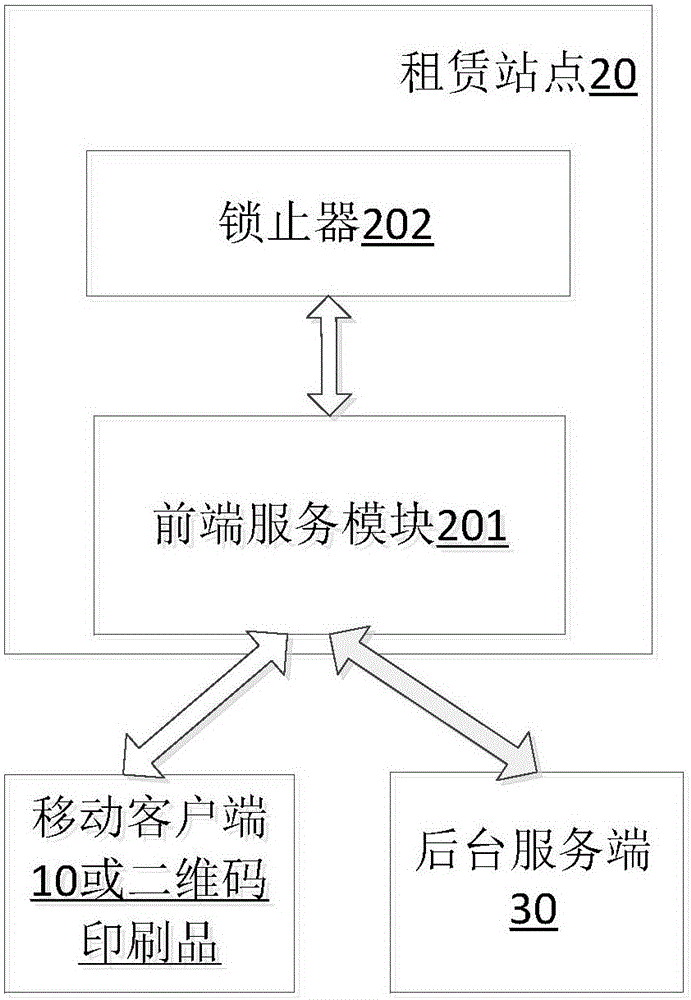
InactiveCN105894677AReduce cumbersomeImprove experienceApparatus for meter-controlled dispensingBuying/selling/leasing transactionsNetwork connectionComputer module
The invention discloses a public bicycle renting system using two-dimensional code scanning. The public bicycle renting system comprises a mobile client, a renting station and a background service end which are communicated through network connection by the aid of respectively communication modules, wherein the mobile client is used for generating a two-dimensional code according to the data of a user; the renting station comprises a front-end service module and a lock, the front-end service module is used for identifying the two-dimensional code, transmitting a matching request to the background service end, detecting the returning action of a public bicycle to obtain the information of the public bicycle, locking the public bicycle and charging a user according to the rate; the background service end responds to the matching request, judges the information legitimacy of the two-dimensional code and returns a matching result; the front-end service module controls of the lock to unlock or lock the public bicycle. The public bicycle renting system has the advantages that public bicycle renting is achieved by using the front-end service module to scan the two-dimensional code, the complexity caused by card application is alleviated, and user experience is improved.
Owner:HANGZHOU GST TECH
ECC algorithm-based identity authentication system and identity authentication method
ActiveCN101626291AImprove securityImprove verification speedKey distribution for secure communicationUser identity/authority verificationPasswordAuthentication server
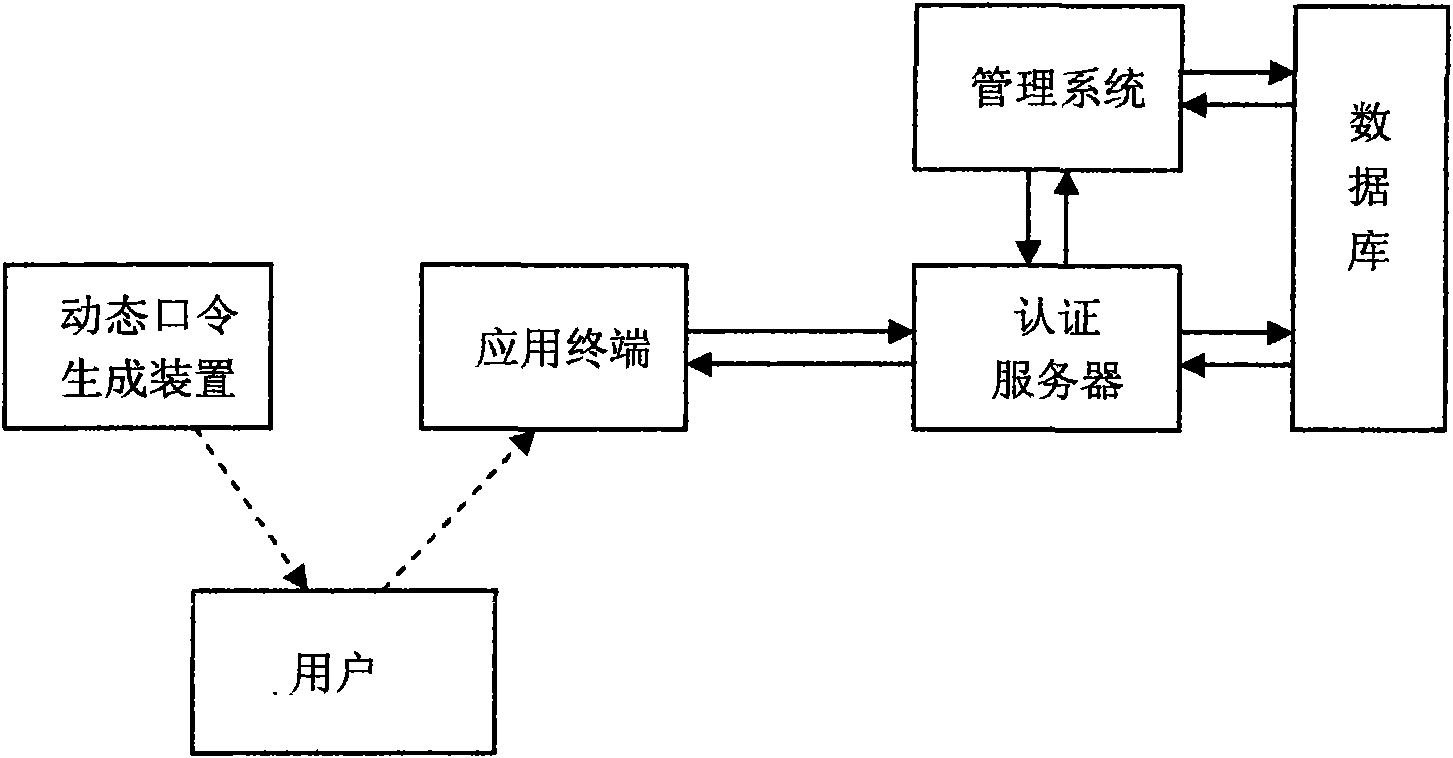
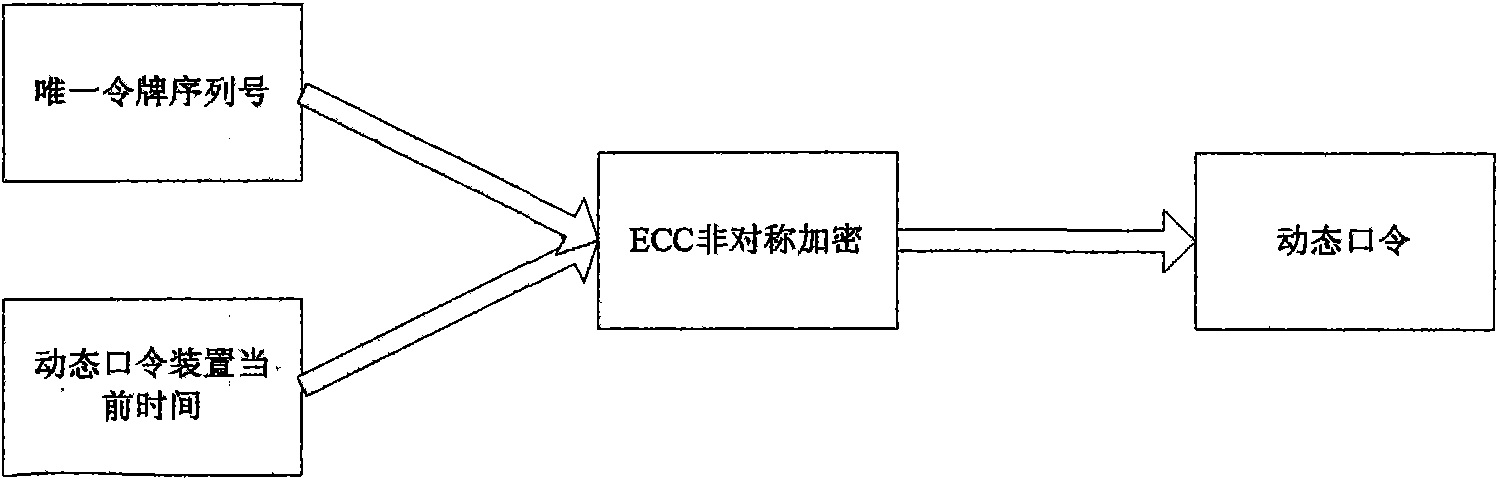
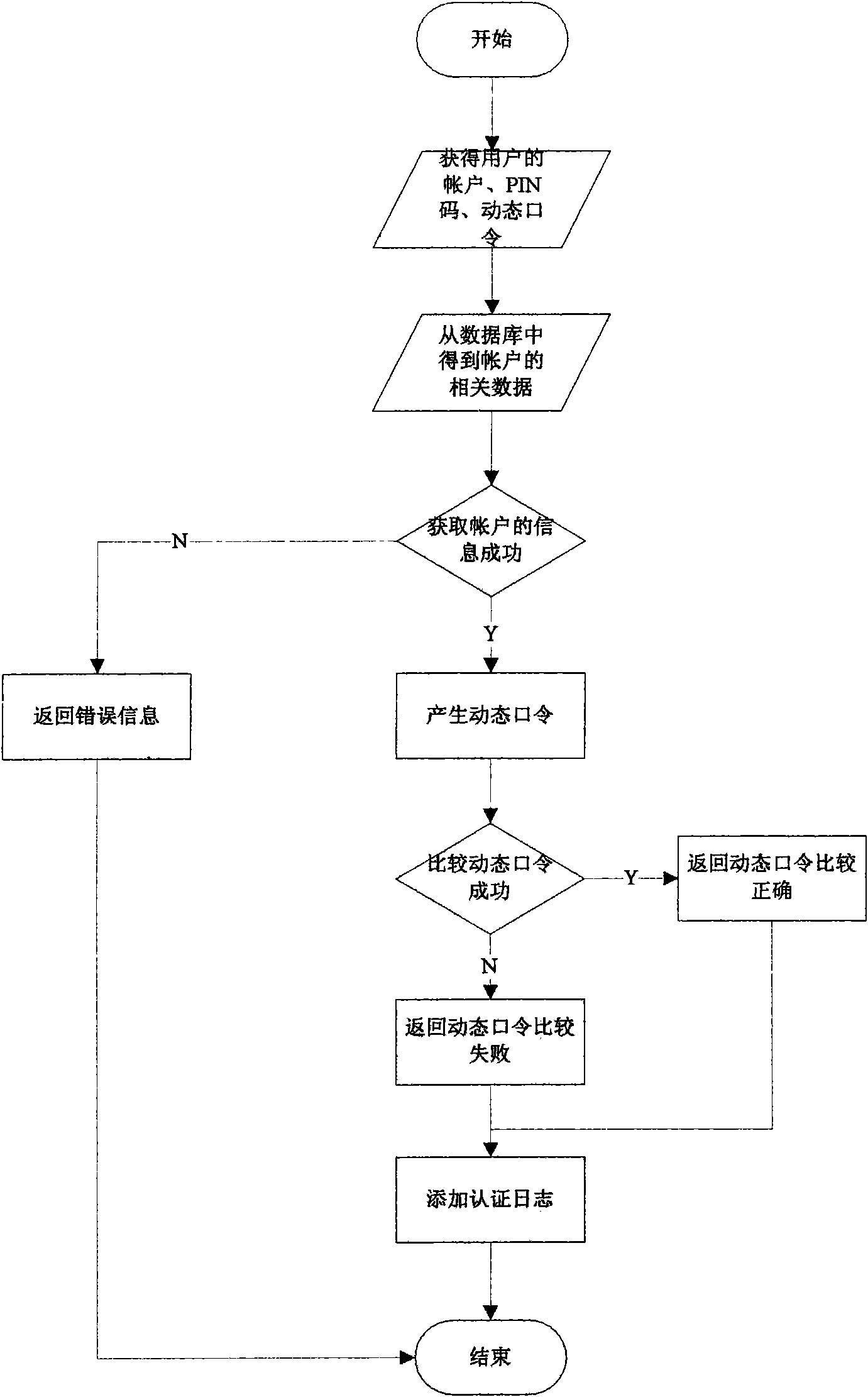
The invention relates to an ECC algorithm-based identity authentication system and an identity authentication method. The system comprises a client interface, a dynamic password generator, an application terminal, an authentication server, a management system and a database. The system and the method are characterized in that: the client interface is connected with the dynamic password generator; the client interface is connected with the application terminal; the application terminal is connected with the authentication server; the authentication server is connected with the management system; the authentication server is connected with the database; and the management system is connected with the database. The system and the method have the advantages of improving the safety performance of dynamic password identity authentication, improving the verification speed of an authentication center, reducing system space consumption and saving the network bandwidth.
Owner:SHANGHAI PEOPLENET SECURITY TECH
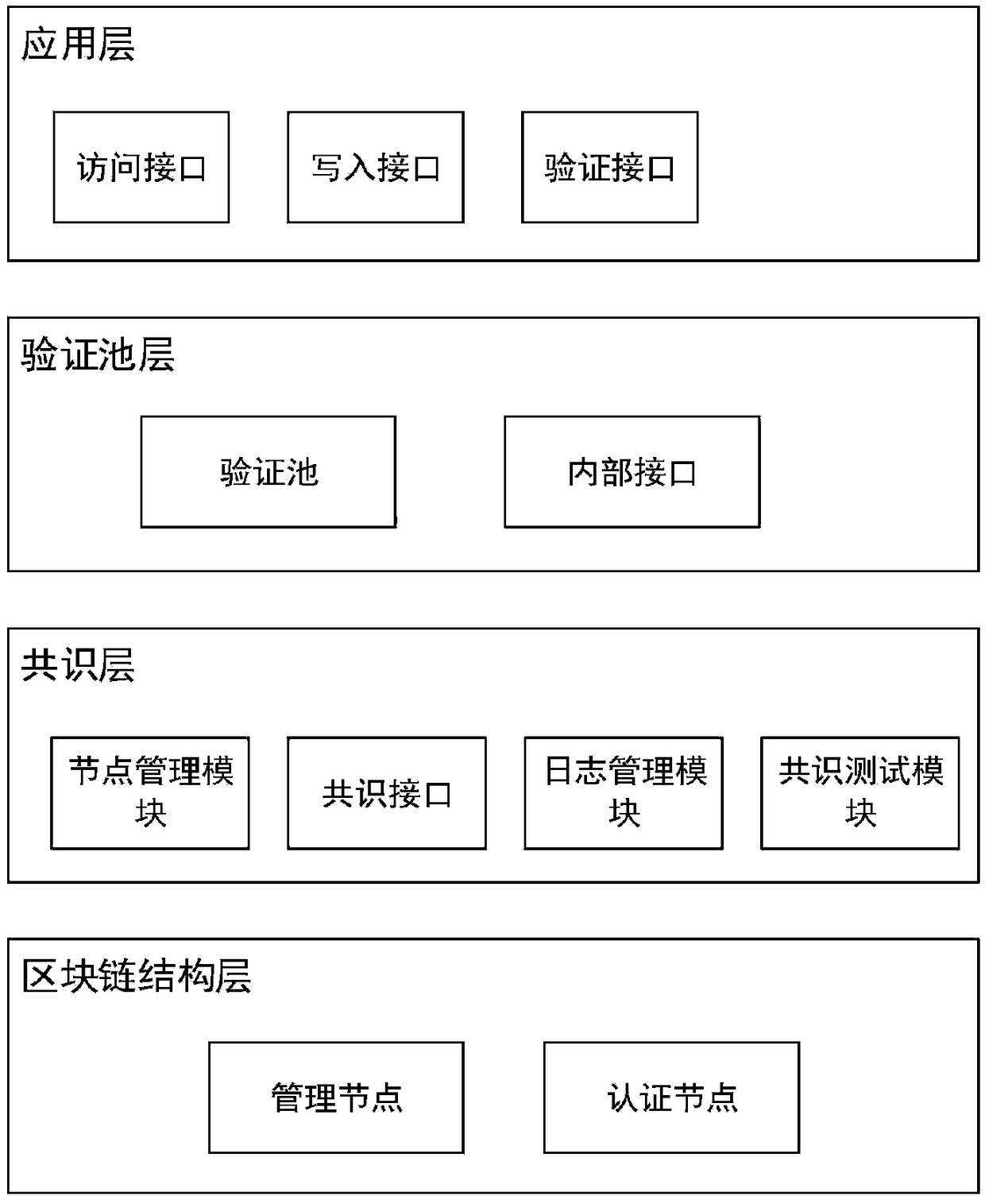
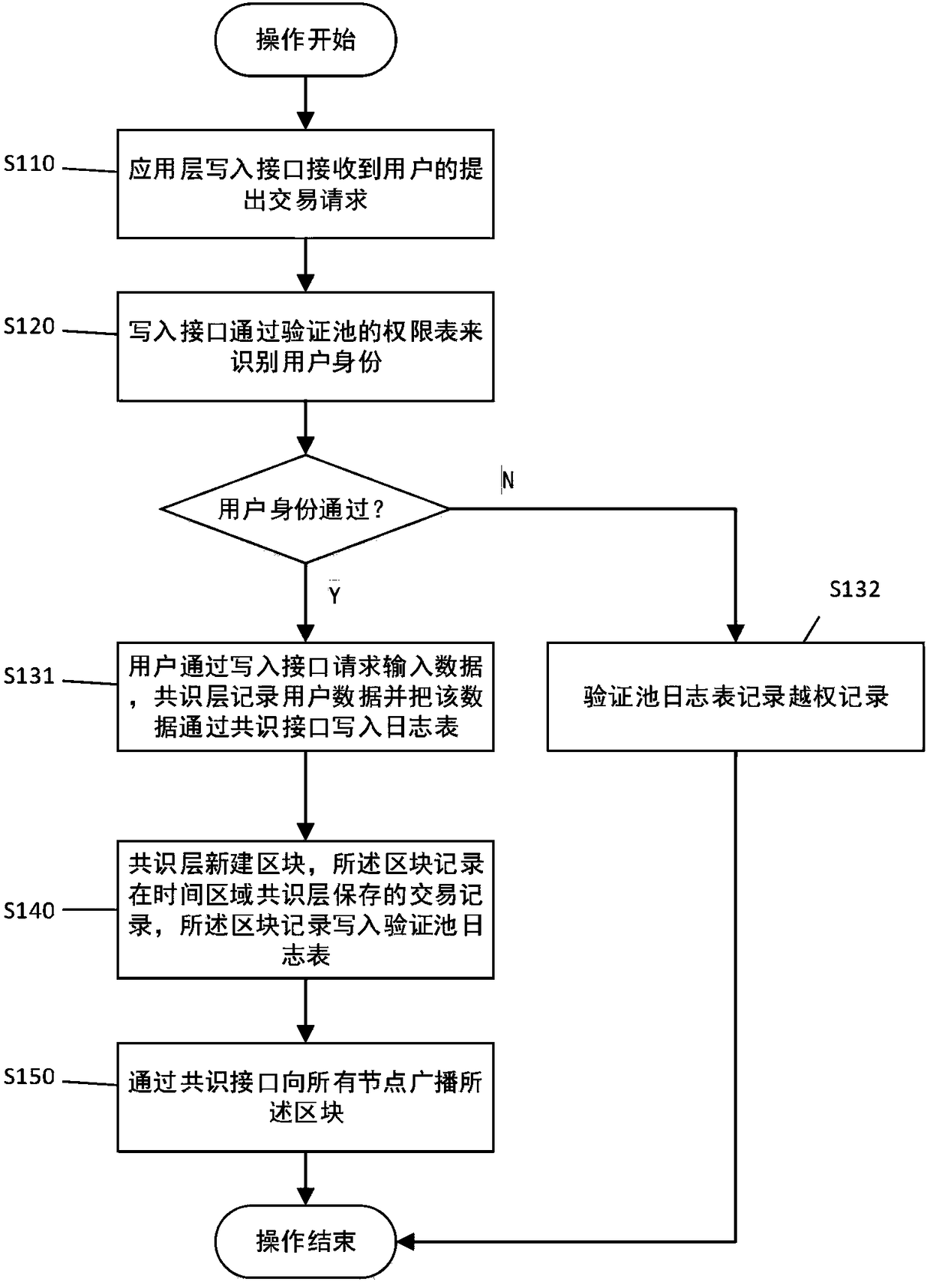
Quick verified pool, quick verified system and operating method base on blockchain
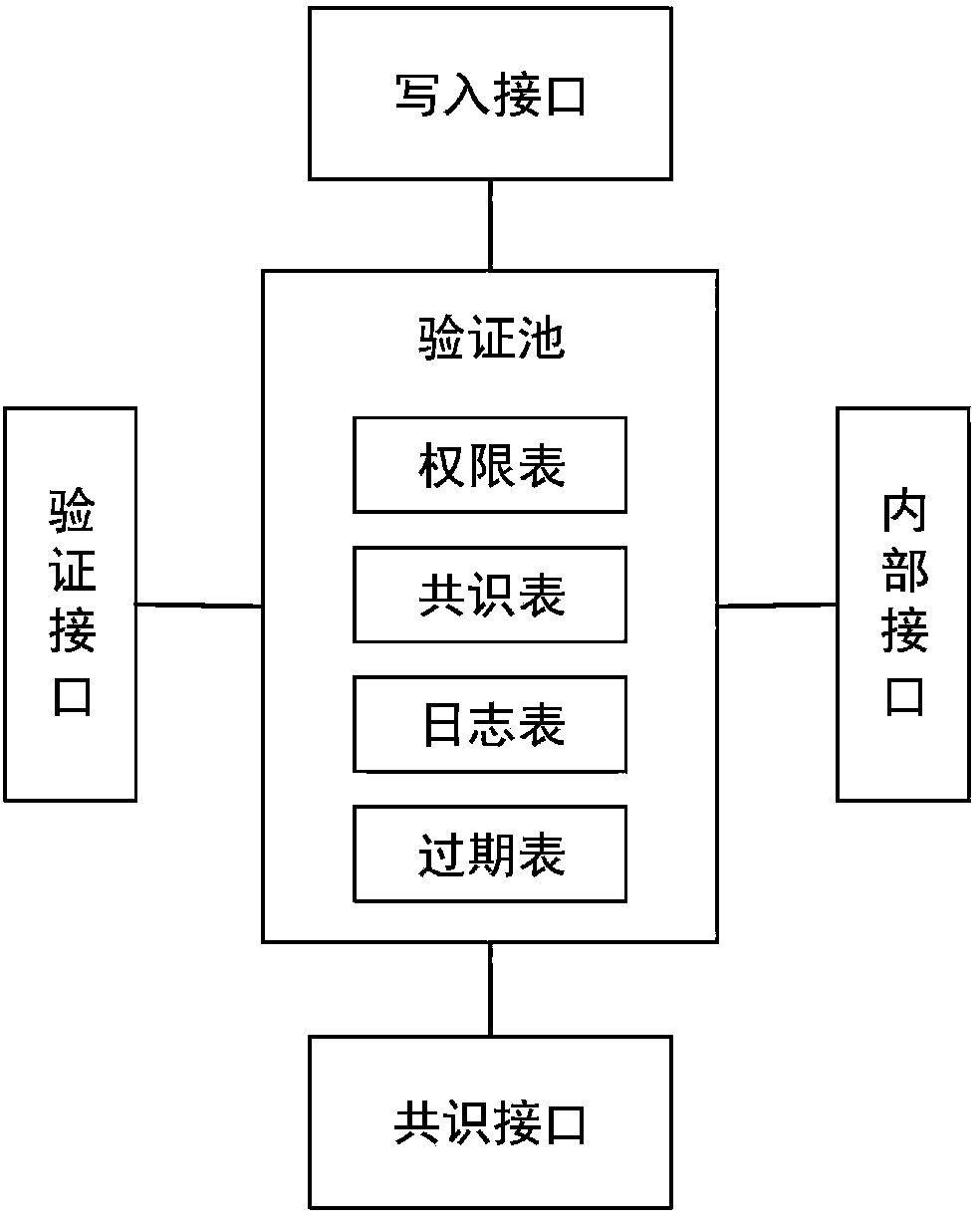
ActiveCN108197959AImprove verification speedSolve the problem that requires a lot of consensus verification timeDigital data protectionTransmissionProtocol ApplicationOperating system
The invention discloses a quick verified pool based on blockchain. The verified pool comprises an authority list, a log list, a consensus list, a past due list, a write in port, a consensus port and averified port. The invention further discloses a quick verified system and an operating method based on the blockchain. The system and method comprise an application layer, a verified pool layer, a consensus layer, and a blockchain structure layer, transaction proposition, transaction verification, transaction stop and the like are carried out. The quick verified pool, quick verified system and operating method base on the blockchain achieves that the blockchain technology can be quickly verified in a second level, the transaction information can be supervised, and the function of data auditing is achieved.
Owner:SOUTH CHINA UNIV OF TECH
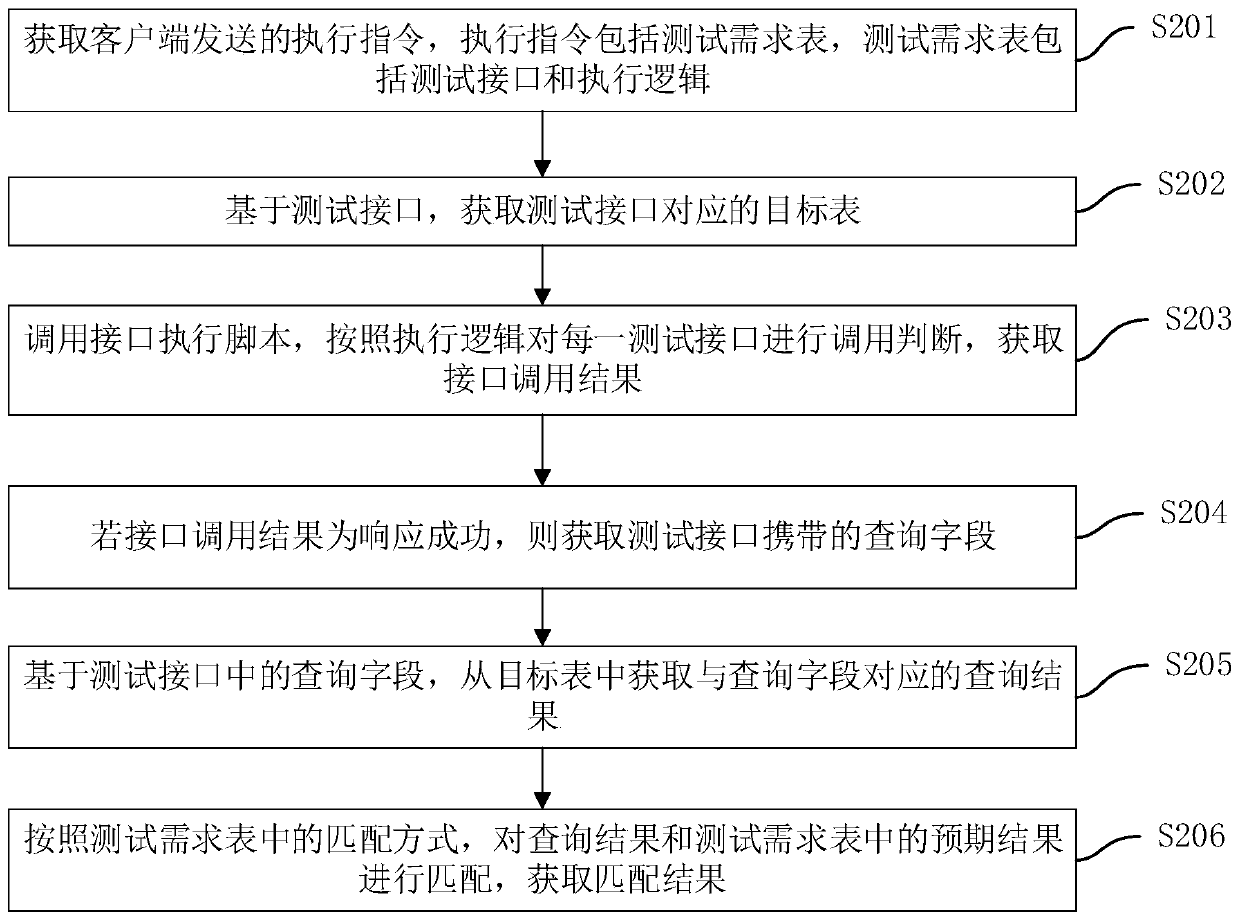
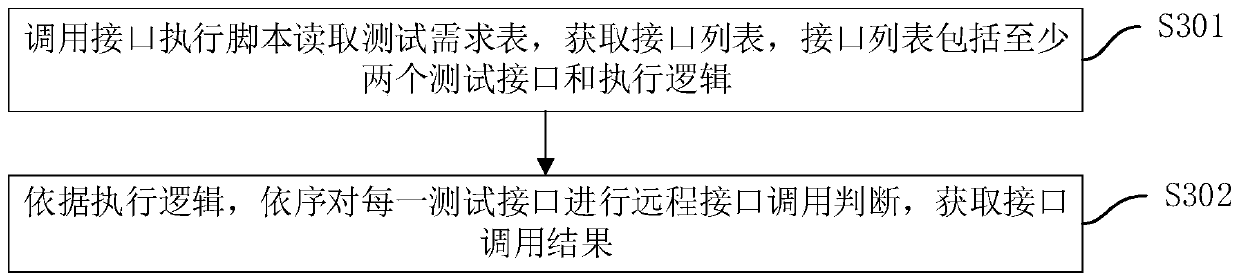
Big data test verification method and device, computer equipment and storage medium
PendingCN110781070AReduce manual query stepsHigh speedSoftware testing/debuggingValidation methodsDatabase
The invention discloses a big data test verification method, a big data test verification device, computer equipment and a storage medium. The method comprises the following steps: obtaining an execution instruction sent by a client, wherein the execution instruction comprises a test demand table, and the test demand table comprises a test interface and execution logic; obtaining a target table corresponding to the test interface based on the test interface; calling an interface execution script, and performing calling judgment on each test interface according to the execution logic to obtainan interface calling result; if the interface calling result is that the response is successful, obtaining a query field carried by the test interface; obtaining a query result corresponding to a query field from the target table based on the query field in the test interface; and matching the query result with an expected result in the test demand table according to a matching mode in the test demand table to obtain a matching result. By adopting the method, the expected result and the test result are automatically compared and verified, and the big data test and verification efficiency is improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
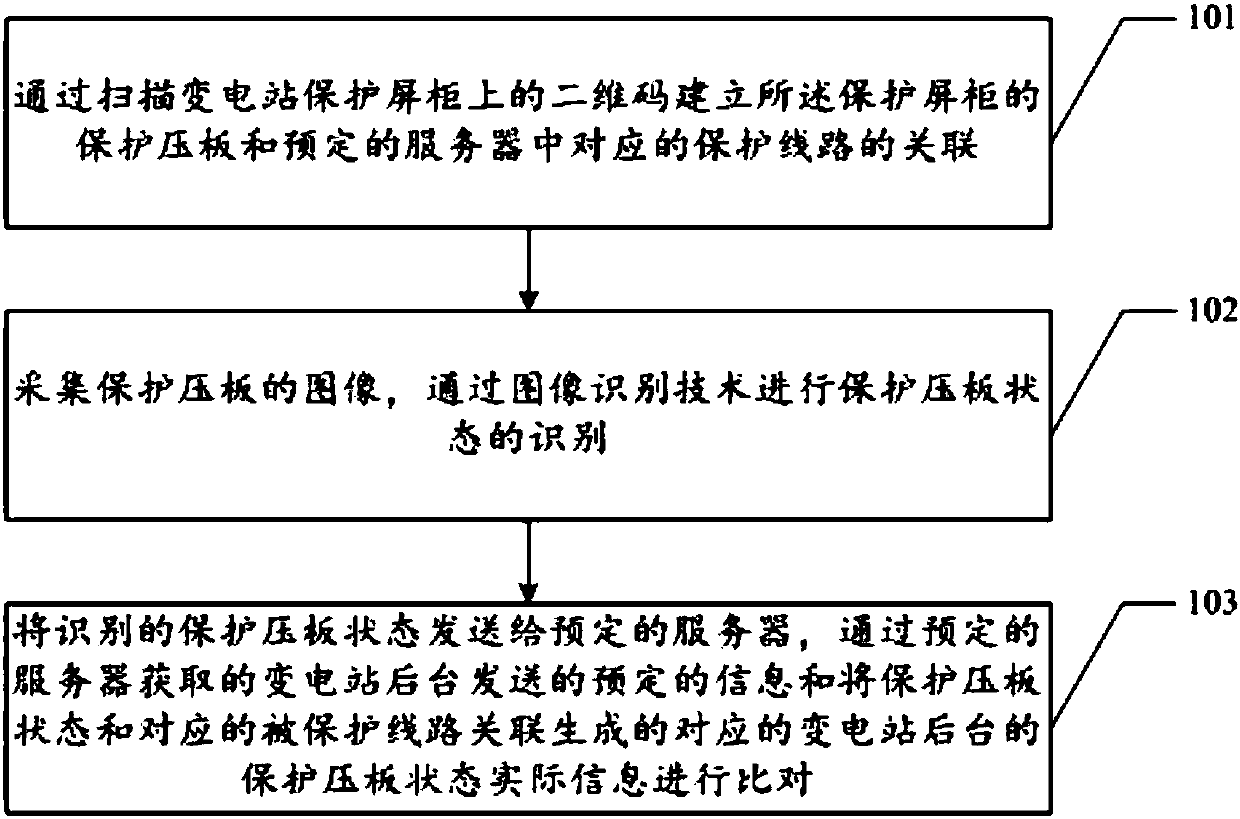
Substation protection strap state comparison method and device
PendingCN107808162AReduce participationReduce workloadCircuit arrangementsCharacter and pattern recognitionPower substationImage identification
The embodiments of the invention disclose a substation protection strap state comparison method and device. With the method and device adopted, the complexity of manual recognition can be simplified,and verification speed can be improved. The substation protection strap state comparison method of the embodiments of the present invention includes the following steps that: S1, an association between the protection strap of a protection screen cabinet and a corresponding protection circuit in a predetermined server is established through scanning a two-dimensional code on the protection screen cabinet of a substation; S2, the image of the protection strap is acquired, and a protection strap state is identified through an image recognition technology; and S3, the identified protection strap state is sent to the predetermined server, predetermined information which is sent by the background of the substation and is obtained through the predetermined server is compared with the protection strap state actual information of the corresponding background of the substation which is generated by associating the protection strap state and a corresponding protected circuit.
Owner:JIANGMEN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID
DPoS consensus method based on threshold signature and fair reward and system
ActiveCN111988137APrevent Corruption AttacksReach the right to generate blocks in the decentralized centerKey distribution for secure communicationEncryption apparatus with shift registers/memoriesThird partyAlgorithm
The invention relates to the technical field of DPoS consensus, and discloses a DPoS consensus method based on threshold signature and fair reward, which comprises the following steps: step 1, in an initial node voting stage, a plurality of self-referring nodes can be finally selected to enter a witness candidate pool; step 2, 21 witnesses are selected by using a verifiable delay function; 3, a threshold signature consensus stage is carried out by the witness; step 4; and the award issuing stage is finished by one round of consensus. According to the DPoS consensus method and system based on the threshold signature and the fair reward, a fair reward and decentralized block chain consensus system can be realized without a trusted third party, and the verification speed can be remarkably increased, so that the transaction volume per second is greatly improved.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
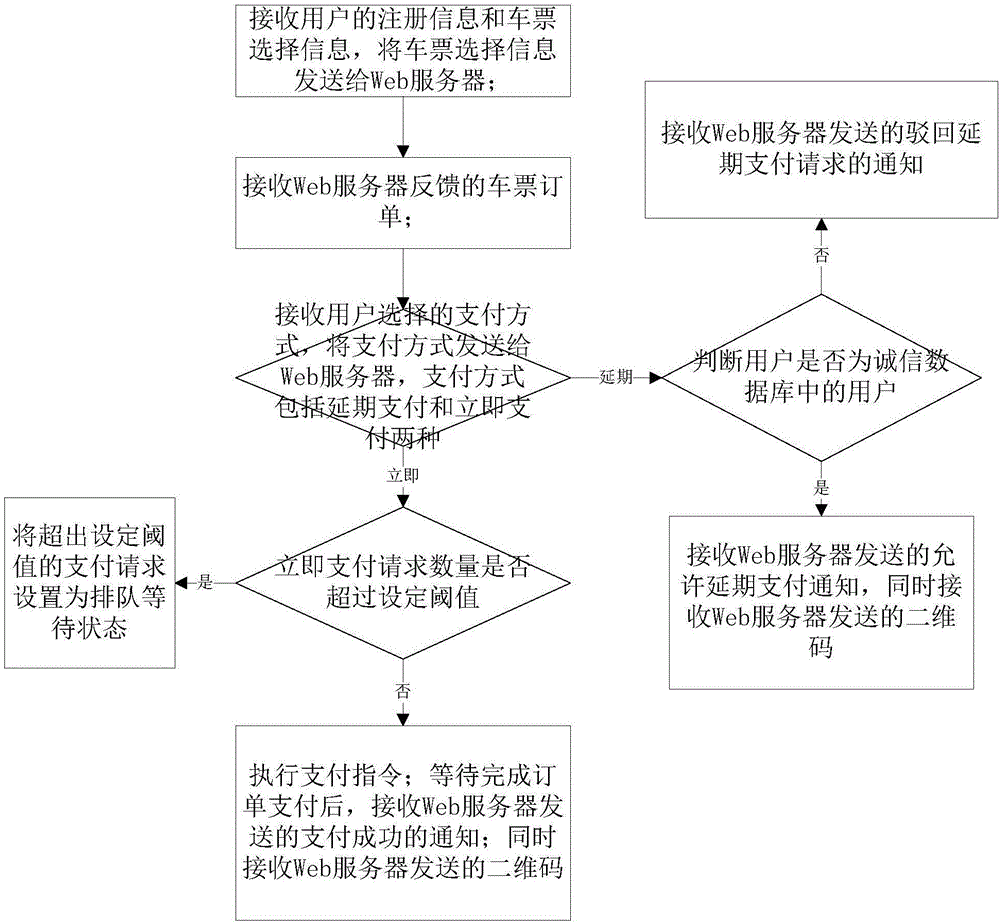
Network payment-based card-free metro ticket selling and checking methods, terminal and server
ActiveCN106779937AEliminate the risk of lossHigh speedCredit schemesDebit schemesPaymentComputer terminal
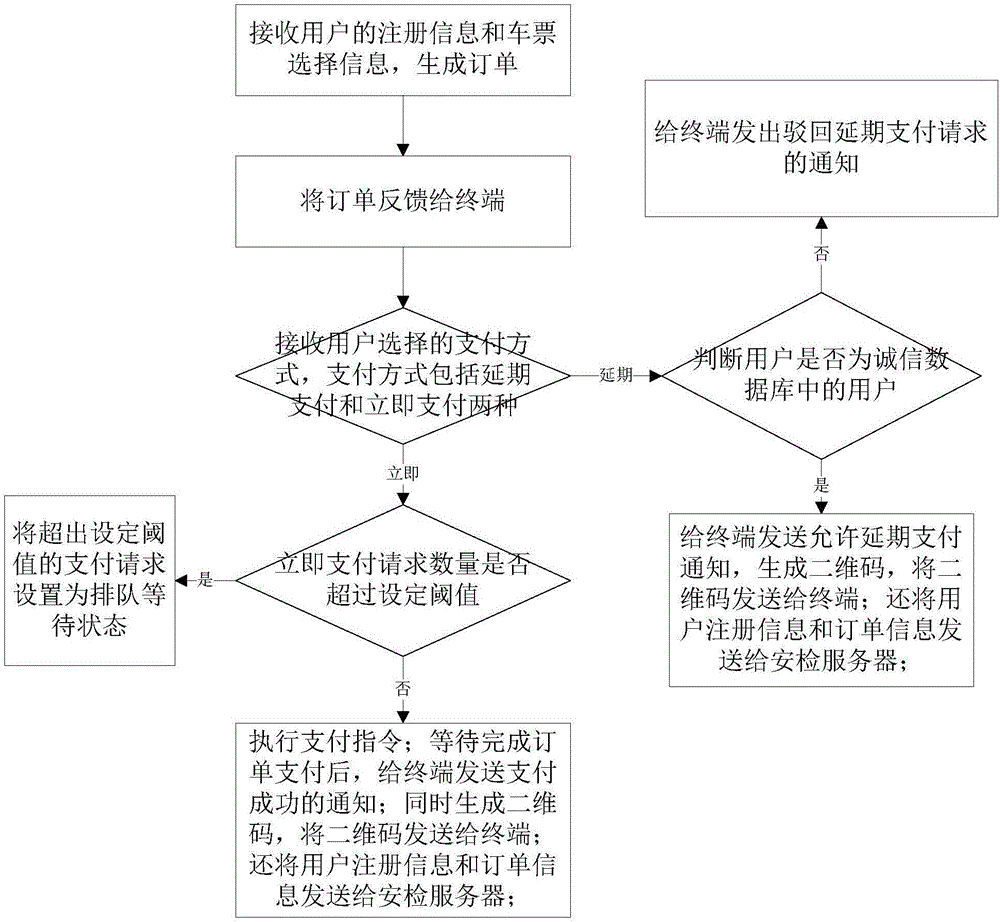
The invention discloses a network payment-based card-free metro ticket selling method, a network payment-based card-free metro ticket checking method, a terminal and a server. The ticket selling method comprises the steps of receiving registration information and ticket selection information of a user, and generating an order; feeding back the order to the terminal; receiving a payment mode selected by the user, wherein the payment mode includes deferred payment and immediate payment; if the payment mode is the immediate payment, judging whether an immediate payment request quantity exceeds a set threshold or not, and if the immediate payment request quantity exceeds the set threshold, setting payment requests with the quantity exceeding the set threshold to be in a queue waiting state, otherwise, executing a payment instruction; after the order is paid, sending a notification of payment success to the terminal; generating a two-dimensional code, and sending the two-dimensional code to the terminal; sending the registration information of the user and order information to a safety inspection server; if the payment mode is the deferred payment, judging whether the user is a user in a honesty database or not, and if yes, sending the two-dimensional code to the terminal; and if not, sending a notification of rejecting a deferred payment request to the terminal. The ticket selling and checking methods have the advantages of card-free ticket selling and checking.
Owner:SHANDONG UNIV
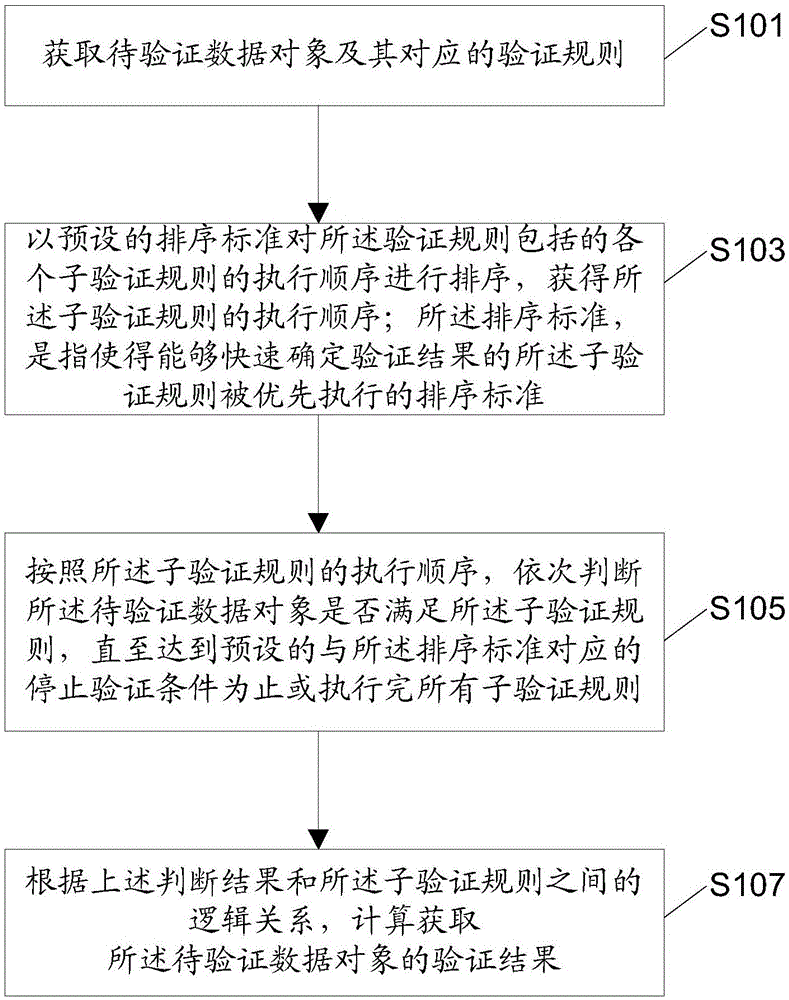
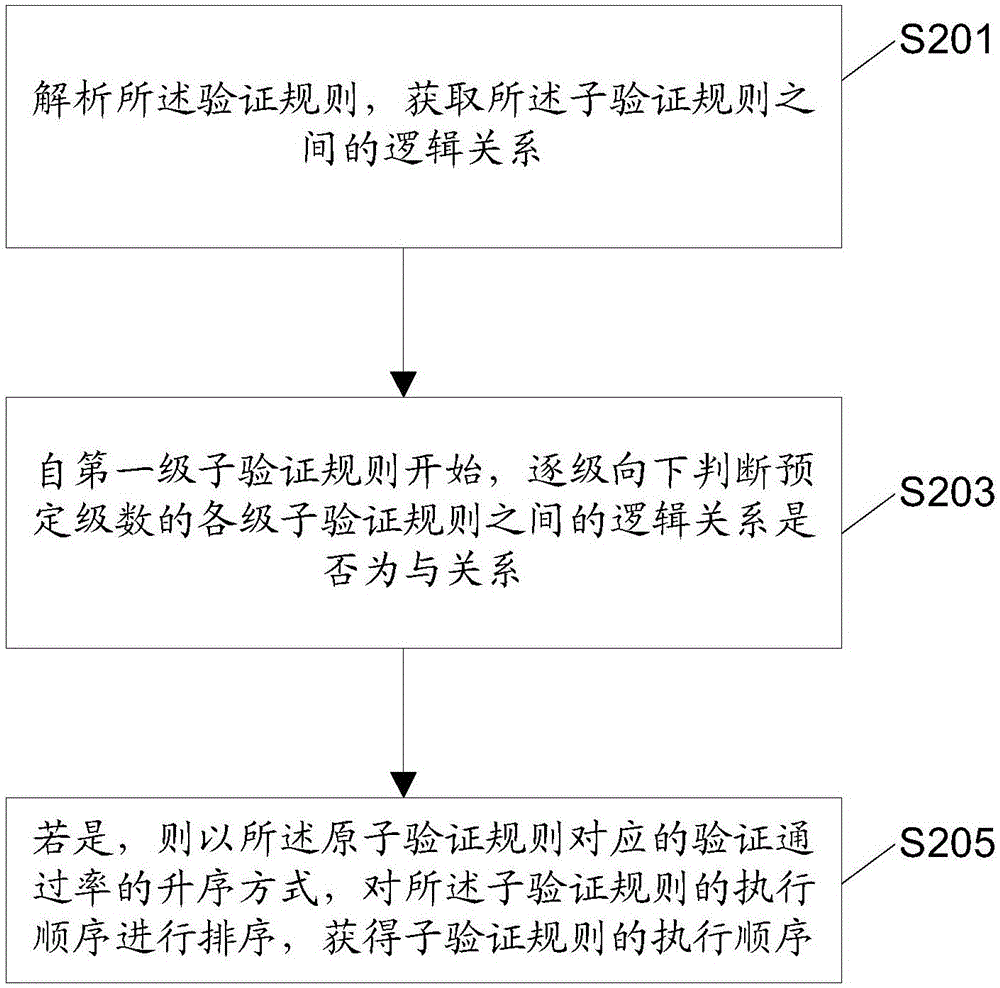
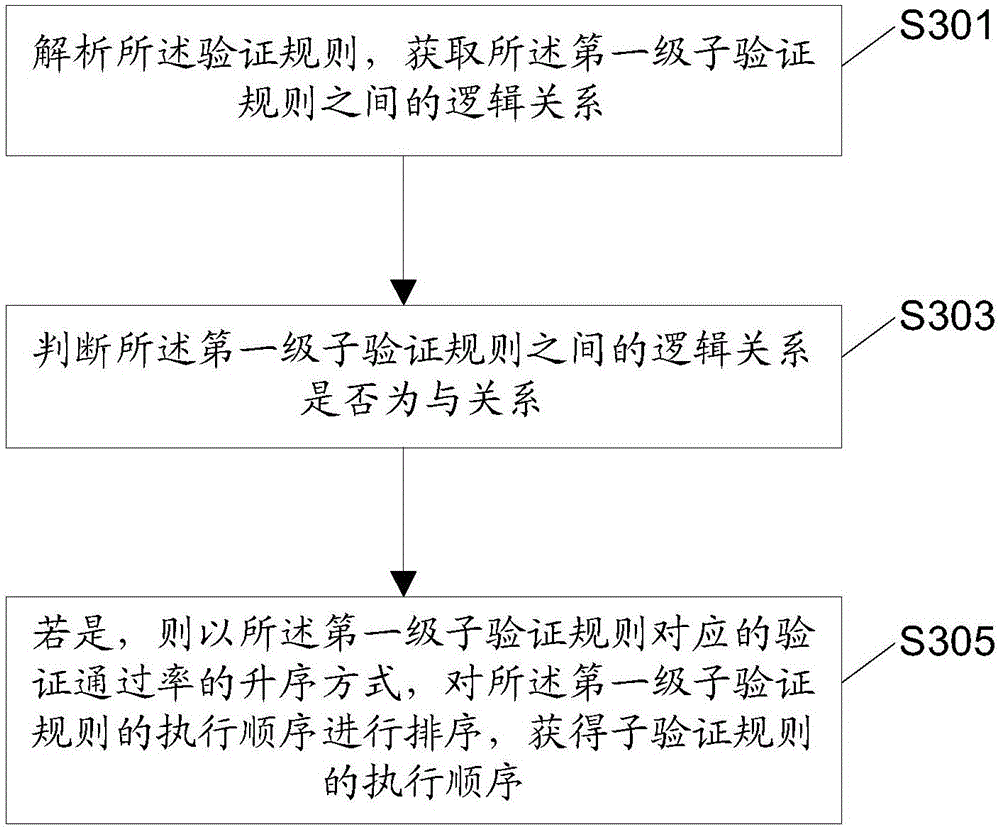
Data object verification method, device and system based on rules, and electric device
InactiveCN106326776AImprove verification speedReduce the number of executionsDigital data protectionSource Data VerificationValidation rule
The invention discloses a data object verification method, device and system based on rules, and an electric device. The data object verification method based on the rules comprises the steps of obtaining a to-be-verified data object and a corresponding verification rule; sorting a performing sequence of sub-verification rules contained in the verification rule according to a preset sorting standard, thereby obtaining the performing sequence of the sub-verification rules; judging whether the to-be-verified data object satisfies the sub-verification rules or not in sequence according to the performing sequence of the sub-verification rules, until a preset verification stopping condition corresponding to the sorting stand is realized or all the sub-verification rules are performed completely; and calculating to obtain a verification result of the to-be-verified data object according to logic relationships between judging results and the sub-verification rules. Through adoption of the method provided by the method, the device, the system and the electric device, the sub-verification rules capable of determining the verification result rapidly are performed preferentially, and the sub-verification rules are prevented from being performed completely, thereby achieving an effect of improving a data verification speed.
Owner:ALIBABA GRP HLDG LTD
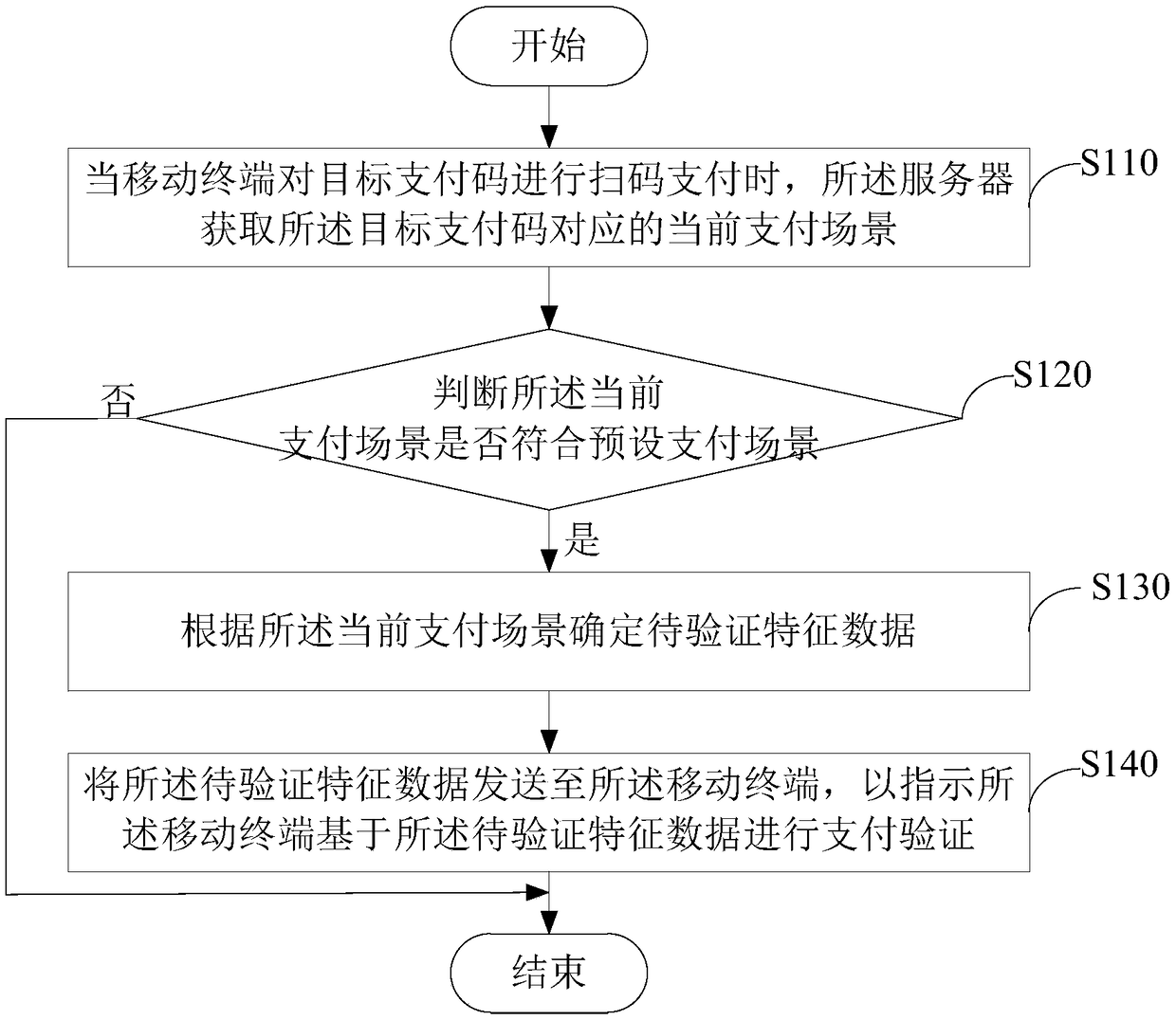
Payment method and device, server and storage medium
InactiveCN108629594AImprove experienceImprove verification speedProtocol authorisationFeature dataMobile payment
The embodiment of the invention discloses a payment method and device, a server and a storage medium, and relates to the technical field of mobile payment. The method comprises the steps that when a mobile terminal carries out code scanning payment on a target payment code, the server acquires a current payment scenario corresponding to the target payment code and determines whether the current payment scenario meets a preset payment scenario; if the current payment scenario meets the preset payment scenario, feature data to be verified are determined according to the current payment scenario;and the feature data to be verified are sent to the mobile terminal to instruct the mobile terminal to perform payment verification based on the feature data to be verified. According to the paymentmethod and device, the server and the storage medium, the payment scenario of the user is acquired and judged; different levels of verification is carried out based on the judgement result; the payment verification speed is accelerated; and the user experience is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
Chip subsystem verification method and device
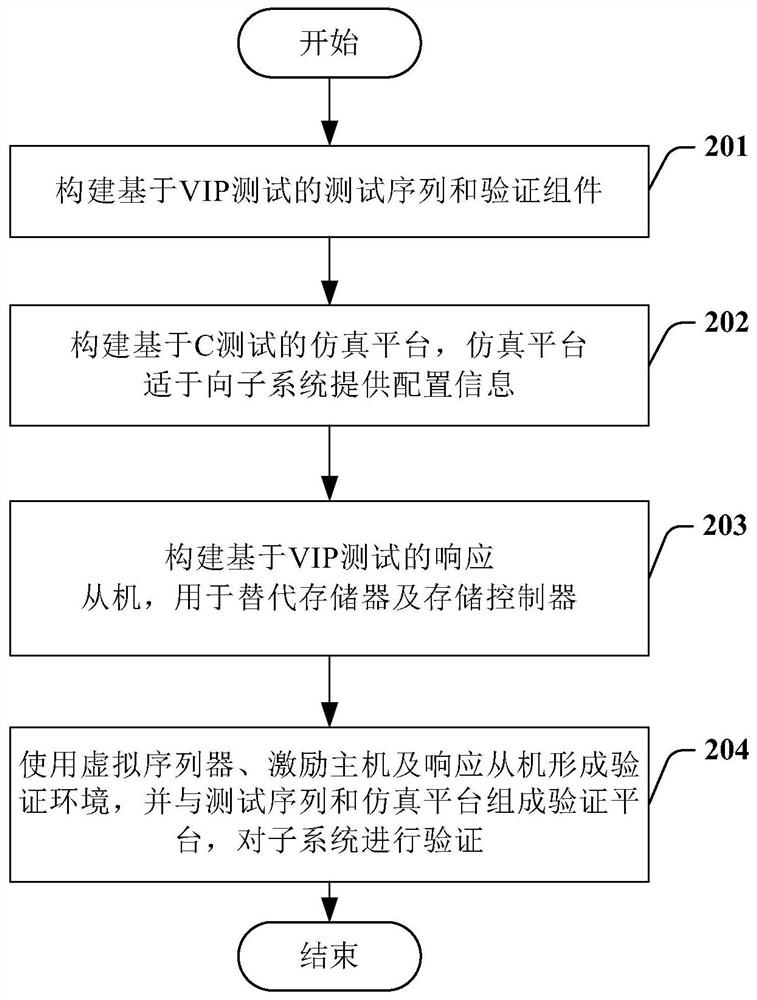
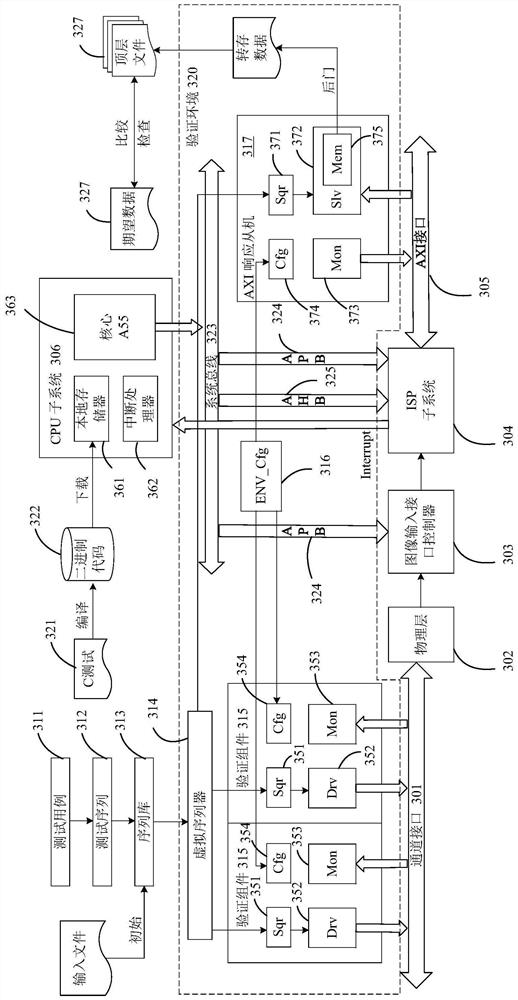
PendingCN112685240AConvenient back pressureEasy to spot errorsDetecting faulty computer hardwareCAD circuit designSystem verificationControl store
The invention provides a chip subsystem verification method and device. The method comprises the following steps: constructing a test sequence based on VIP testing, a virtual sequencer and an excitation host, wherein the virtual sequencer is used for receiving the test sequence and is coupled with the excitation host, and the excitation host is suitable for inputting excitation to a to-be-verified subsystem of a chip; constructing a simulation platform based on a C test, wherein the simulation platform is suitable for providing configuration information for the subsystems; constructing a VIP test-based response slave for replacing a memory and a storage controller; and forming a verification environment by using the virtual sequencer, the excitation host and the response slave, and forming a verification platform together with the test sequence and the simulation platform to verify the subsystem.
Owner:JLQ TECH CO LTD
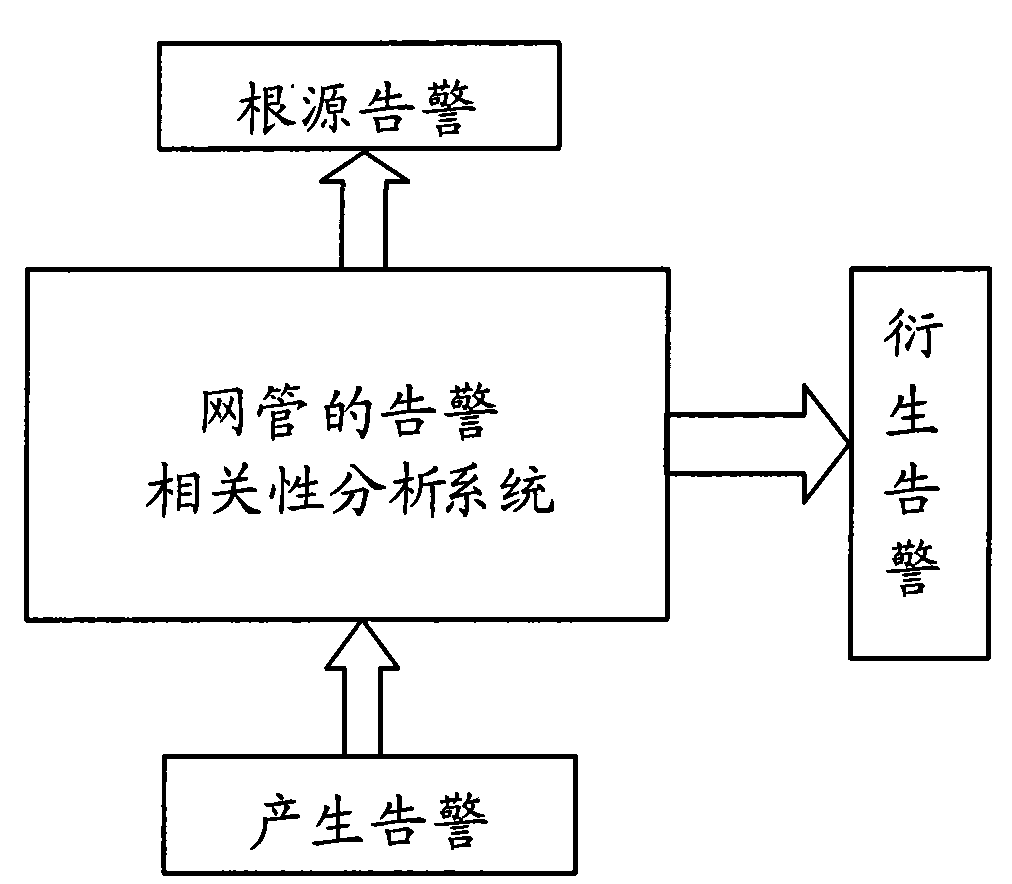
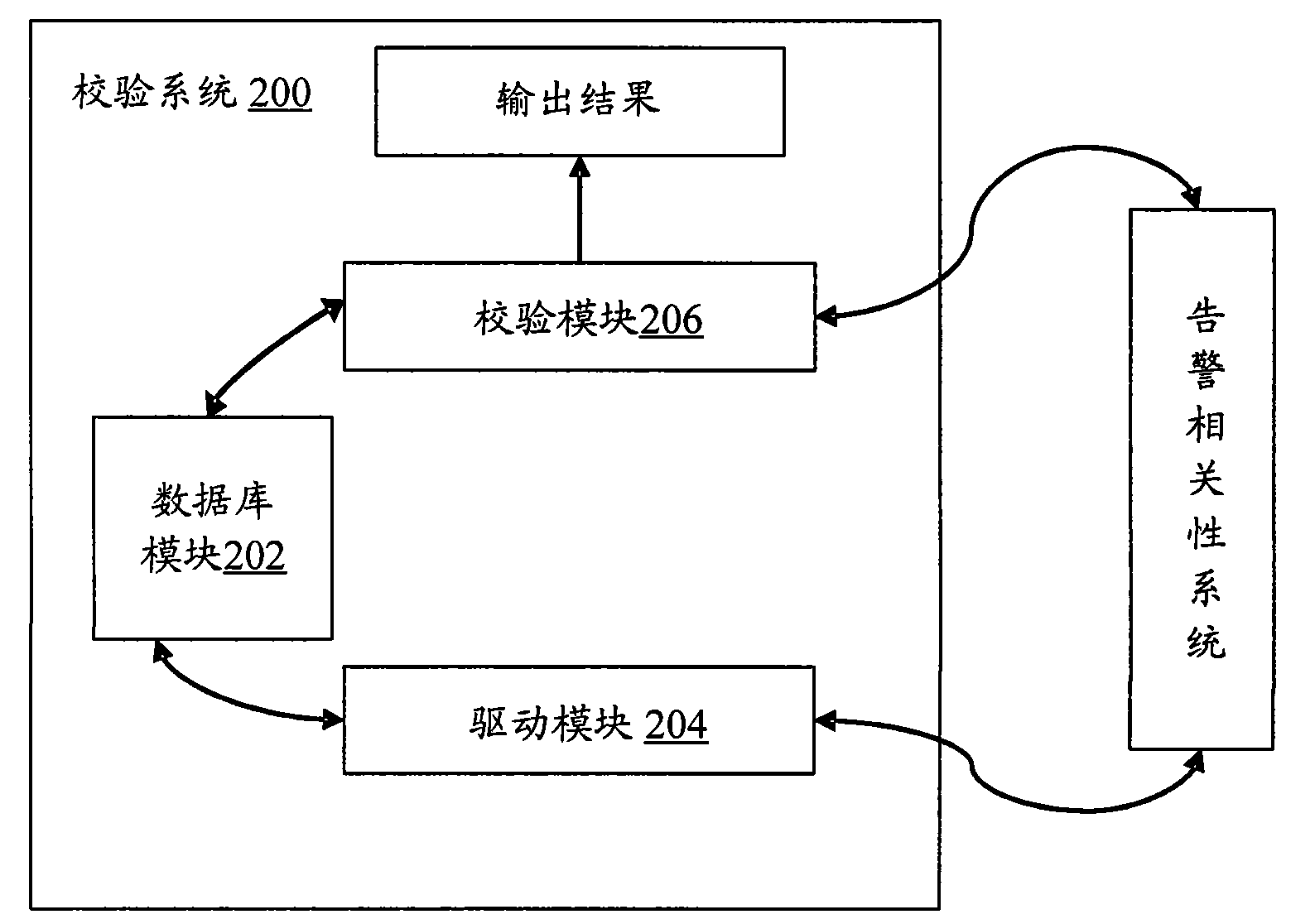
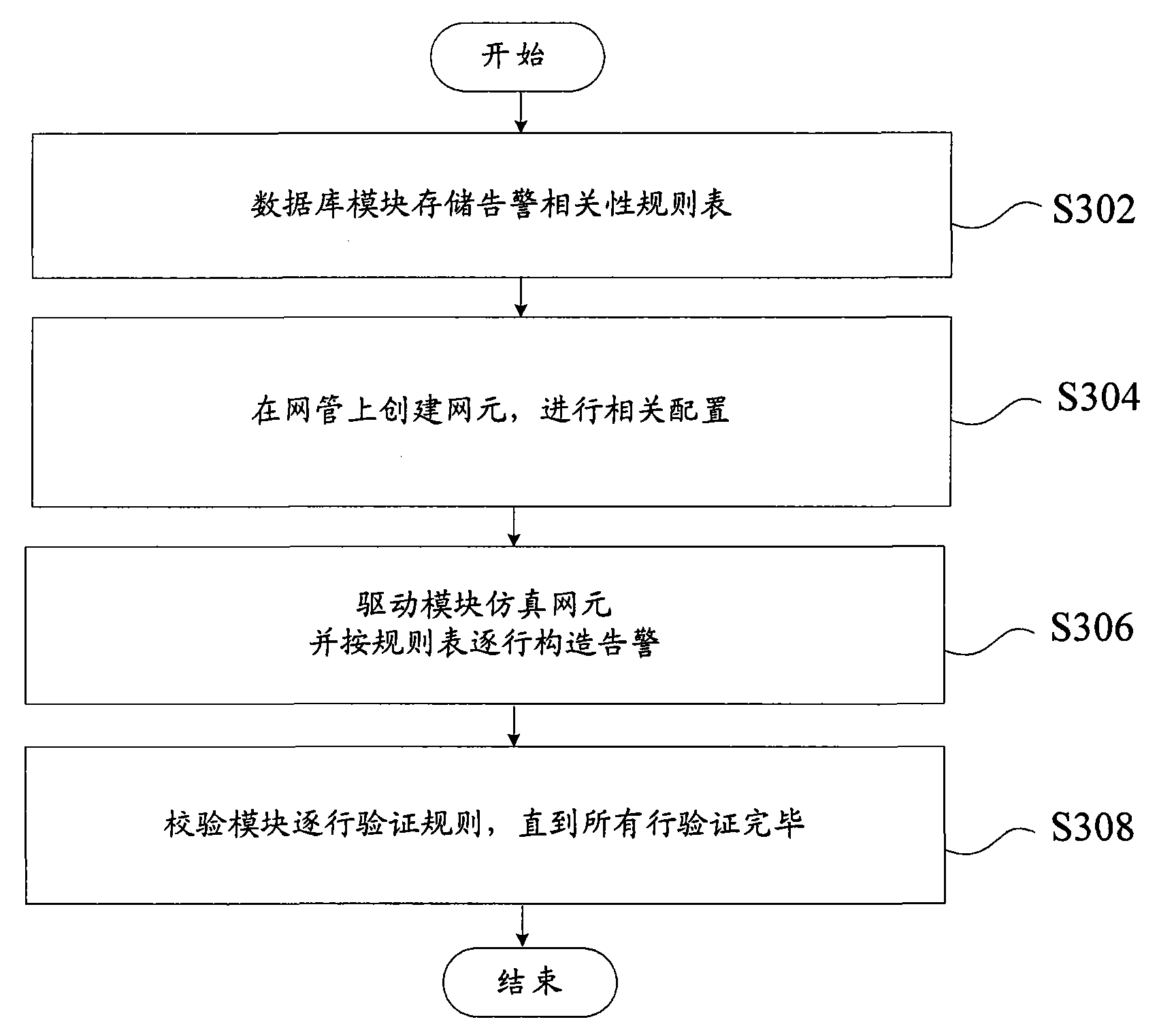
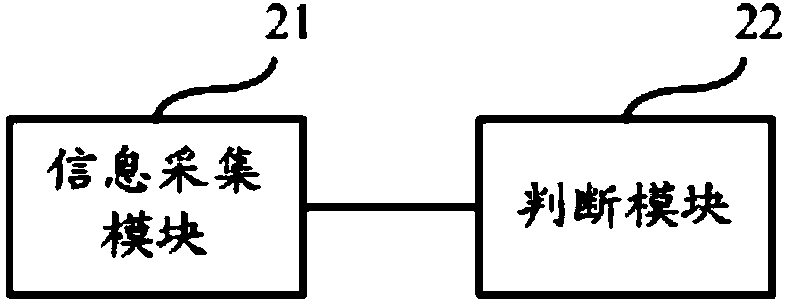
Check system and method for checking alarm correlation analysis system
ActiveCN101599874AOvercome limitationsImprove verification speedData switching networksSpecial data processing applicationsAlarm correlationRelevance analysis
The invention provides a check system for checking an alarm correlation analysis system, which comprises a driving module 204 and a check module 206, wherein the driving module 204 is used for simulating a network element, constructing an alarm in a preset alarm correlation rule table, and reporting the alarm to the alarm correlation analysis system; and the check module 206 is used for checking whether an output result of the alarm correlation analysis system aiming at the alarm meets rules in the alarm correlation rule table. The invention also provides a check method for checking the alarm correlation analysis system. The system and the method overcome actual equipment limitation brought by the conventional check method, improve check speed, and fully check the recursive relation and priority of the alarm.
Owner:ZTE CORP
Payment method and device, electronic device and storage medium
InactiveCN108734472AImprove experienceImprove verification speedCharacter and pattern recognitionProtocol authorisationComputer graphics (images)Payment
The embodiment of the invention discloses a payment method and device, an electronic device and a storage medium and relates to the technical field of electronic devices. The payment method is appliedto the electronic device. The electronic device is provided with a rotatable camera. The method comprises the steps that when it is detected that a payment application in the electronic device is started, the camera is controlled to rotate to acquire a target face image, and the target face image is cached; when a payment request of the payment application is acquired, the target face image is matched with a pre-stored face image; and when the target face image is successfully matched with the pre-stored face image, payment is completed. Through the payment method and device, the electronic device and the storage medium in the embodiment, the face image is pre-collected through the camera arranged on the electronic device for storage, and after a user confirms payment, the face image is directly verified. Therefore, payment verification speed is increased, and user experience is improved.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
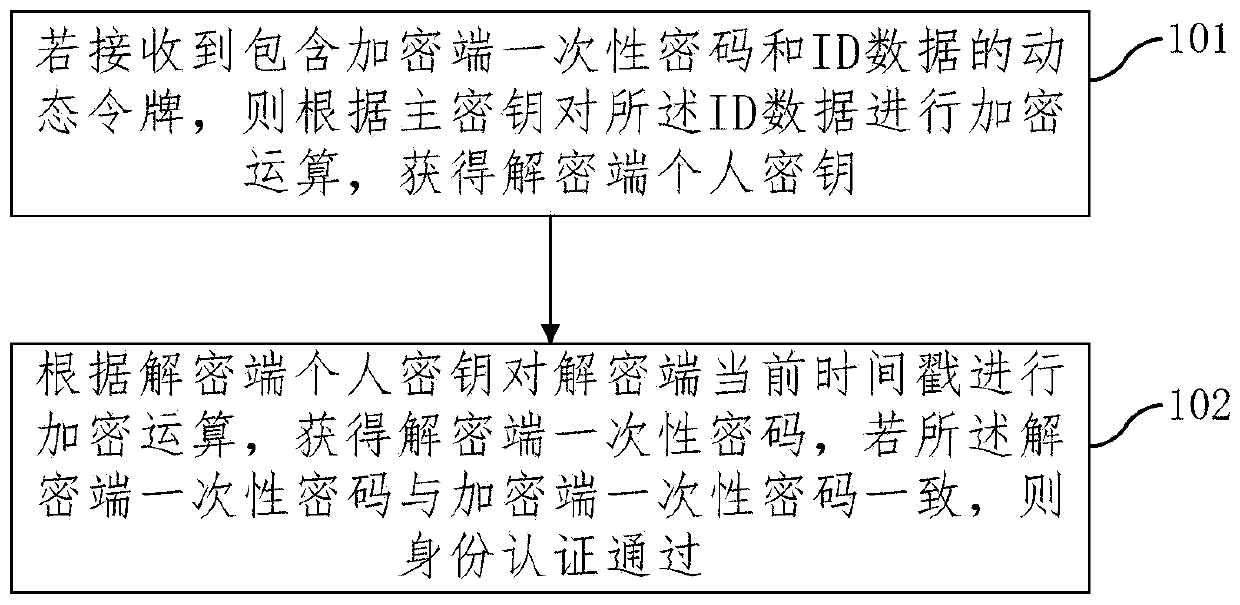
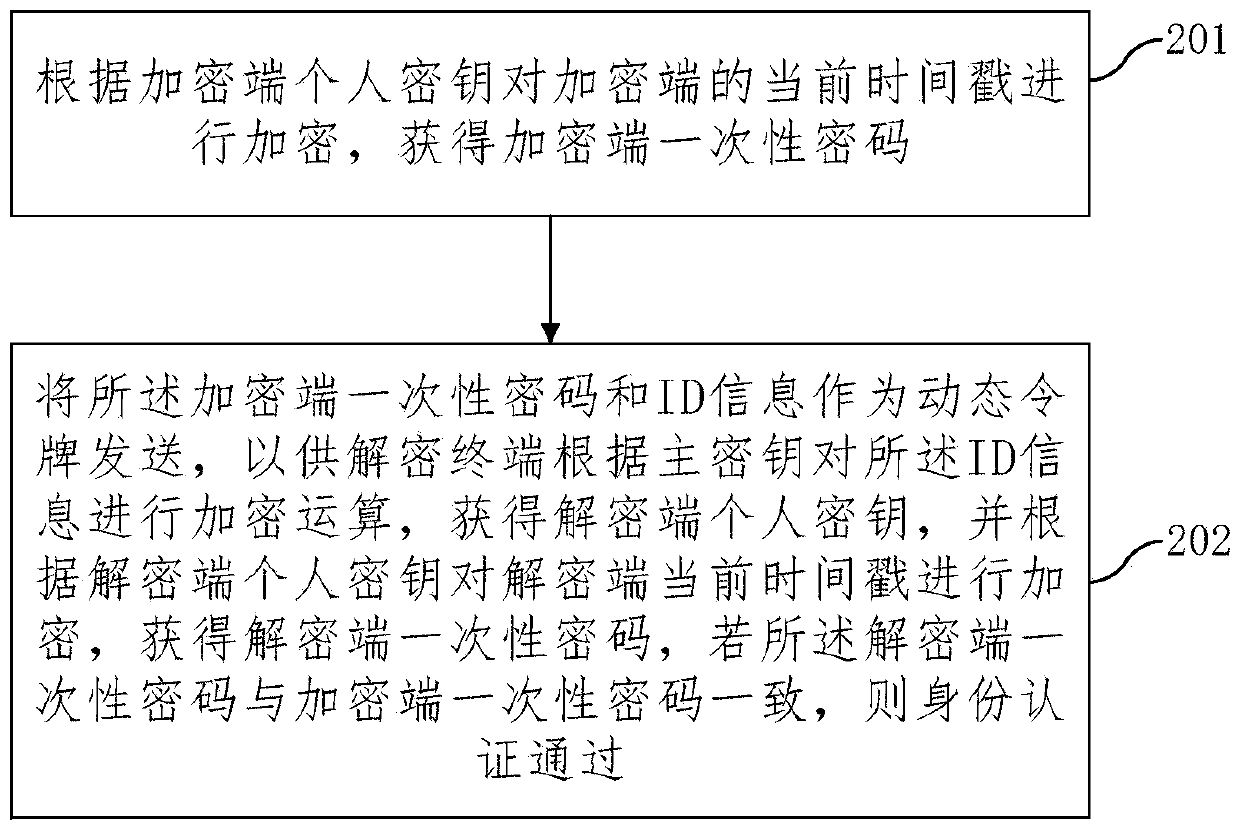
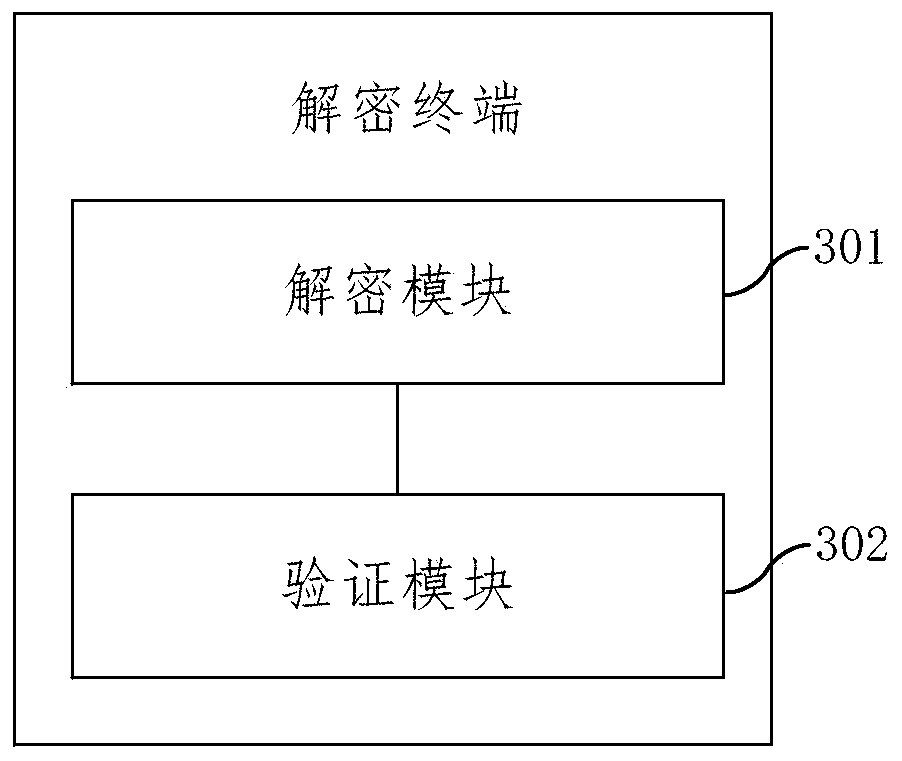
Identity authentication method based on dynamic token, and decryption and encryption terminal
InactiveCN110224834AImprove securityImprove the speed of verificationKey distribution for secure communicationUser identity/authority verificationSystem safetyDisk encryption
The embodiment of the invention provides an identity authentication method based on a dynamic token and a decryption and encryption terminal. The method comprises the steps: carrying out the encryption operation of ID data according to a main secret key if the dynamic token comprising an encryption end one-time password and the ID data is received, and obtaining a decryption end personal secret key; performing encryption operation on the current timestamp of the decryption end according to the personal secret key of the decryption end to obtain a one-time password of the decryption end, and ifthe one-time password of the decryption end is consistent with the one-time password of the encryption end, passing identity authentication; wherein the encryption end one-time password is obtained after the encryption end personal secret key carries out encryption operation on the current timestamp of the encryption end, and the encryption end personal secret key is obtained after the decryptionterminal carries out encryption on the ID information according to the main secret key. The invention has the advantages that the secret keys used by users are different, the system safety is improved under the scene that the terminal safety cannot be guaranteed, bidirectional communication is not needed, the verification speed is increased, the one-time password is obtained according to the timestamp, and the replay attack can be effectively avoided.
Owner:TSINGHUA UNIV
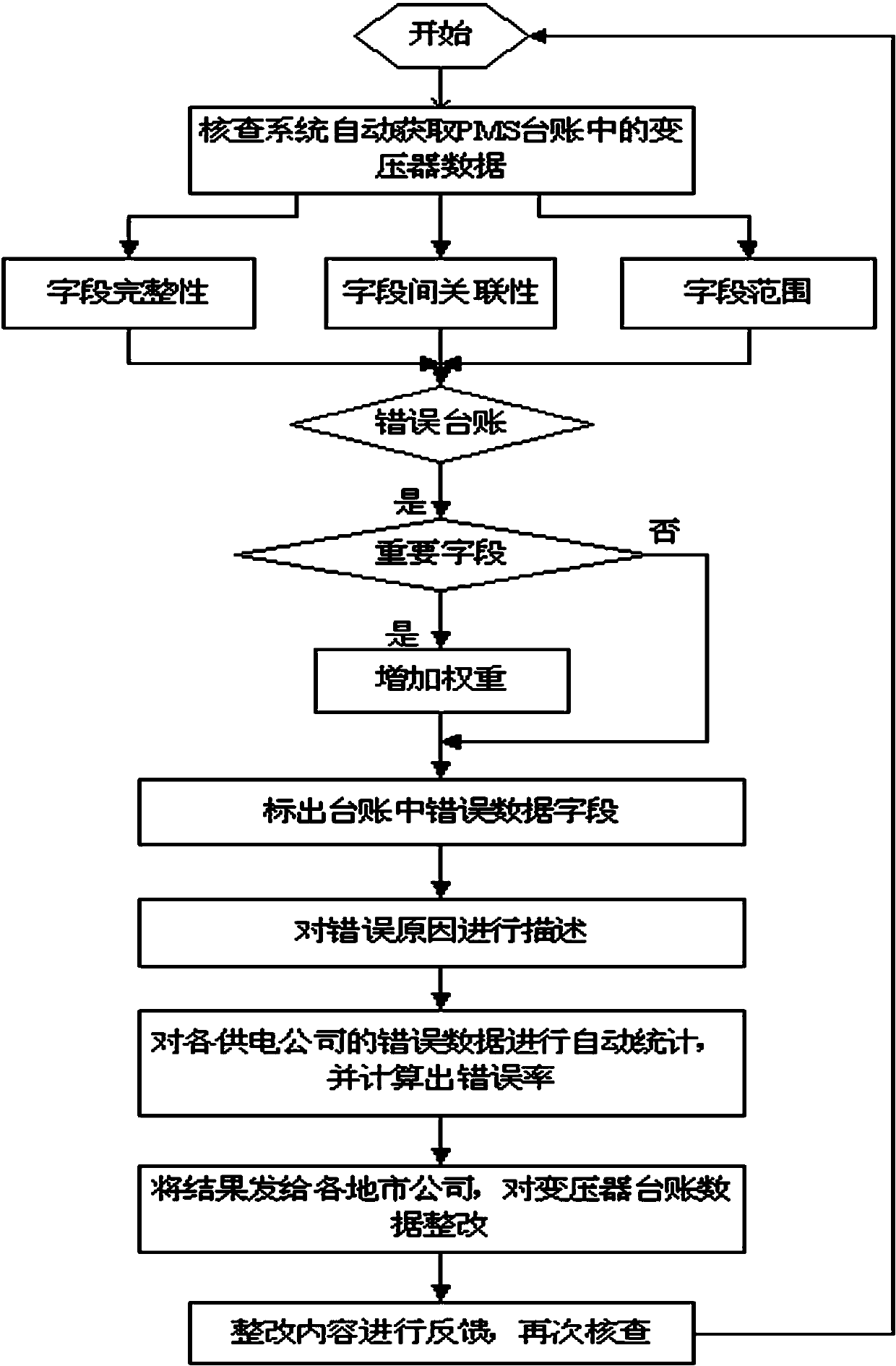
Intelligent checking system for transformer accounts for production management system (PMS)
InactiveCN103426125AIntegrity guaranteedGuaranteed accuracyData processing applicationsInformation technology support systemTransformerPower grid
The invention relates to an intelligent checking system for transformer accounts for a PMS for grid equipment, particularly to a checking method for the transformer accounts based on the relevance among technical parameters. The intelligent checking system is applicable to transformer account checking, through in-depth understanding of theoretical knowledge and various technical parameters of a transformer, correlations among the various parameters of the transformer and actual ranges of the parameters, solidification is performed by programs, errors of the accounts are looked up automatically, automatic statistics of error rates is performed, error causes are prompted automatically, and the integrity and accuracy of the transformer accounts are guaranteed. Meanwhile, a large number of labor and material resources are saved, missed checking and inaccurate checking in an artificial account checking process are avoided, the checking speed and the integrity and accuracy of the accounts are improved, a foundation is laid for launching of advanced applications of transformer-type equipment in the PMS, launching of advanced applications of the transformer-type equipment in the PMS is ensured, and stable and efficient operation of the PMS is promoted.
Owner:STATE GRID CORP OF CHINA +1
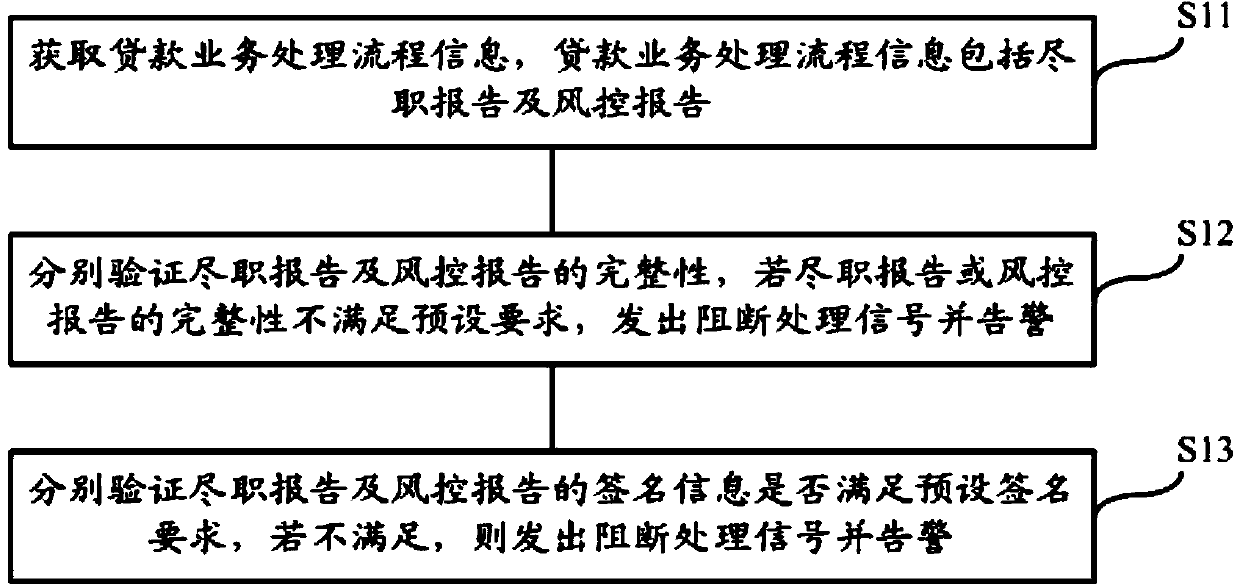
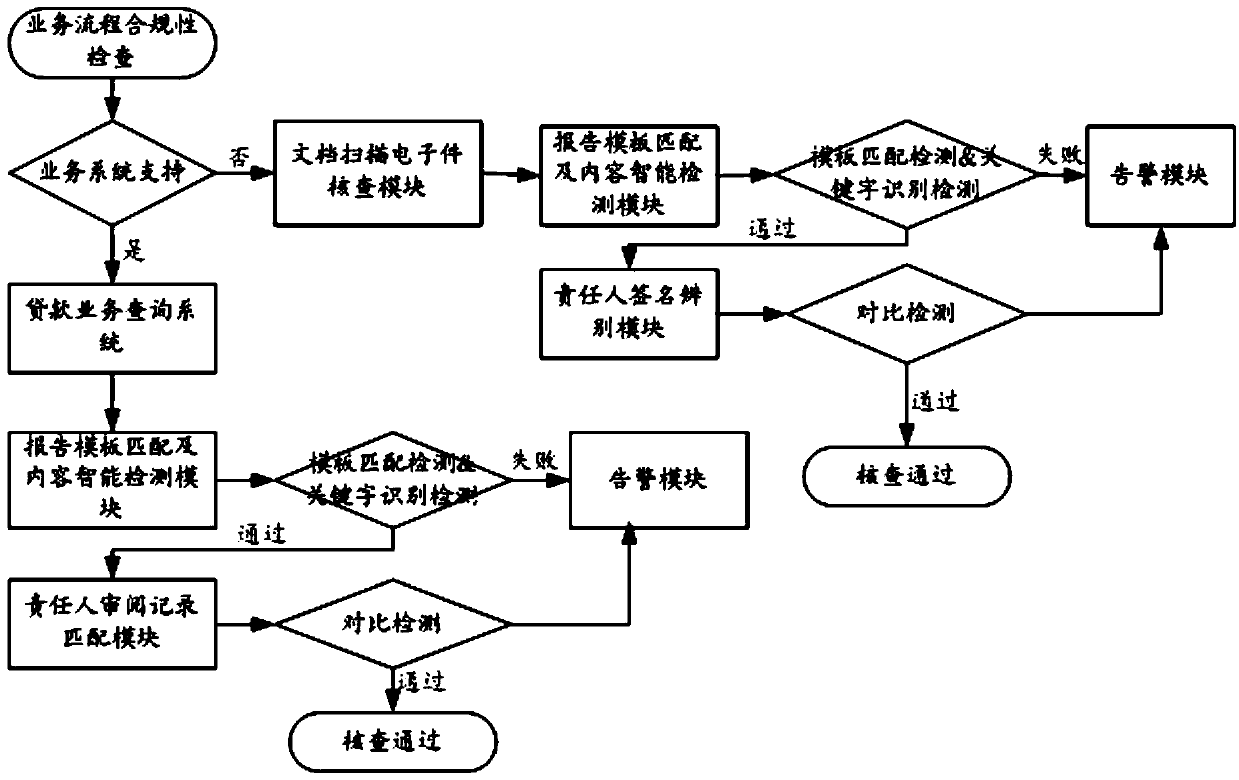
Method and device for realizing checking of loan business processing flow
The invention relates to the technical field of information, in particular to a method and a device for realizing checking of loan business processing flow. The method for realizing checking of loan business processing flow comprises the following steps: acquiring loan business processing flow information, wherein the loan business processing flow information comprises a due diligence report and a risk control report; verifying the completeness of the due diligence report and the risk control report respectively, and transmitting a blocking processing signal and alarming if the completeness of the due diligence report or the risk control report does not meet a preset requirement; verifying whether the signature information of the due diligence report and the risk control report respectively meets a preset signature requirement, and if not, transmitting a blocking processing signal and alarming. By adopting the method and the device for realizing checking of loan business processing flow, the technical problems of low efficiency and easiness in making errors due to manual checking of the loan business processing flow in relevant technologies are solved.
Owner:南京聪诺科技有限公司
Mutual trust cluster cooperative verification method for Internet of vehicles anonymous authentication
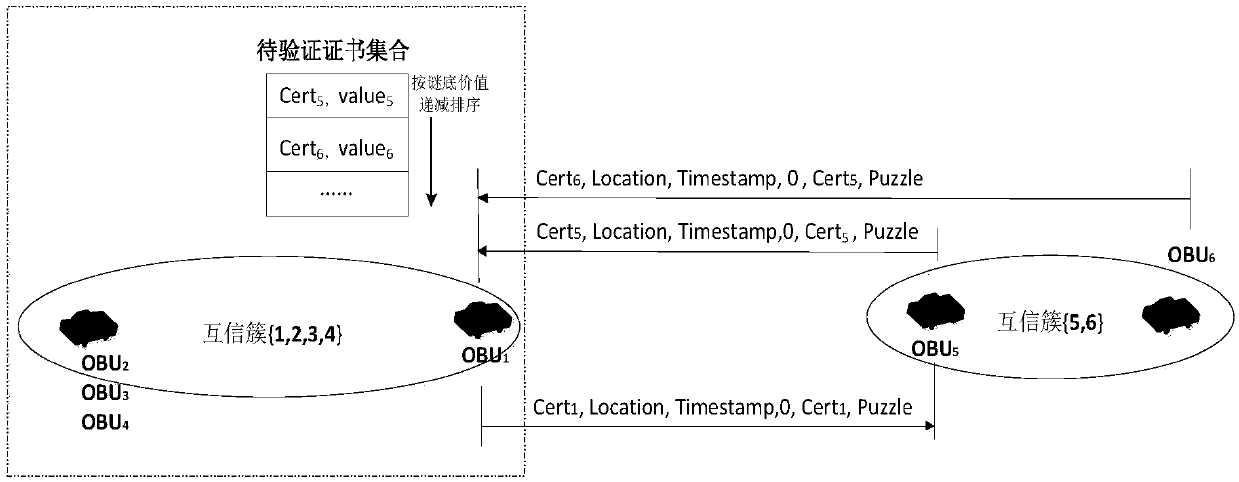
ActiveCN107835077ALimit pre-constructed hash puzzlesImprove verification speedUser identity/authority verificationThe InternetAnonymous authentication
The invention discloses a mutual trust cluster cooperative verification method for Internet of vehicles anonymous authentication, including the following steps: designing hash puzzles to limit attackers from pre-constructing a computing problem, and integrating computing resources between legal vehicles by using a cooperative verification mode. Thereby, the verification speed can be improved, andstrong practical values and good application prospects can be achieved.
Owner:NAT UNIV OF DEFENSE TECH
Checking of right to access
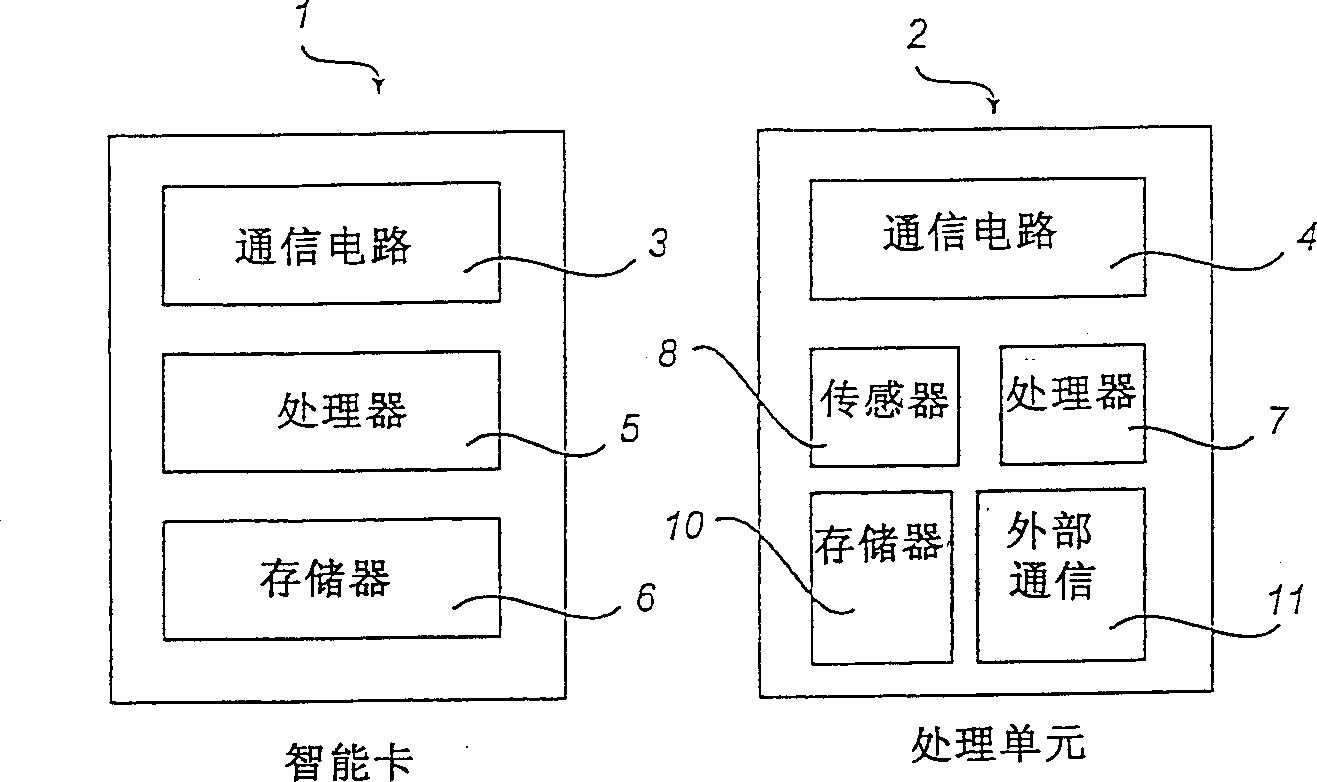
InactiveCN1369085AImprove verification speedDigital data processing detailsUnauthorized memory use protectionData shippingInternet privacy
A system for checking the right to access to sensitive information is described, said checking being based on current biometric data of a person whose right to access to the sensitive information is to be checked. The system comprises a data carrier (1) and a processing unit (2). The data carrier (1) comprises a memory (6) containing sensitive information, a signal processing means (5) and a communication means (3). The processing unit (2) is adapted to receive the current biometric data from the person and comprises a memory (10), a signal processing means (7) and a communication means (4). The processor (7) of the processing unit (2) preprocesses the current biometric data and transfers the same to the processor (5) of the data carrier (1) via the communication means (3, 4). The procesor (5) of the data carrier (1) compares the received preprocessed biometric data with biometric reference data stored in advance in the memory (6) of the data carrier (1) to determine whether the right to access to the sensitive information exists. A data carrier (1), a processing unit (2) and a method of checking, based on current biometric data of a person, the right to access to sensitive information stored on a data carrier (1) are also described.
Owner:联智科技有限公司
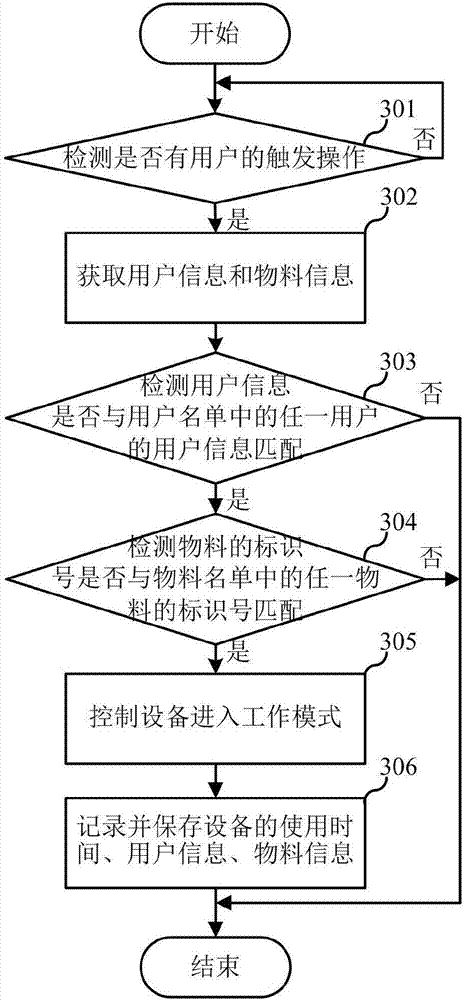
Equipment utilization method and equipment
ActiveCN107065806AImprove securityAvoid lossTotal factory controlProgramme total factory controlInformatizationComputer science
The invention relates to the informatization management system field, and discloses an equipment utilization method and equipment. The equipment utilization method is used for industrial production, and comprises steps that the equipment is in a standby state, and when a trigger operation of a user is detected, the user information of the user and material information of a material selected by the user are acquired; whether the material is matched with an identification number of any material in a material list is detected according to the identification number, and whether the user information is matched with user information of any user of a user list is detected; when the identification number of the material is matched with the identification number of any material in the material list and the user information is matched with the user information of any user in the user list, the equipment enters a working mode. The equipment utilization method and the equipment are advantageous in that the user using the equipment is guaranteed to be an authorized user, and the selected material is the material, which can be used in the equipment, and therefore unreasonable operation of an unauthorized user is prevented.
Owner:上海森永工程设备股份有限公司
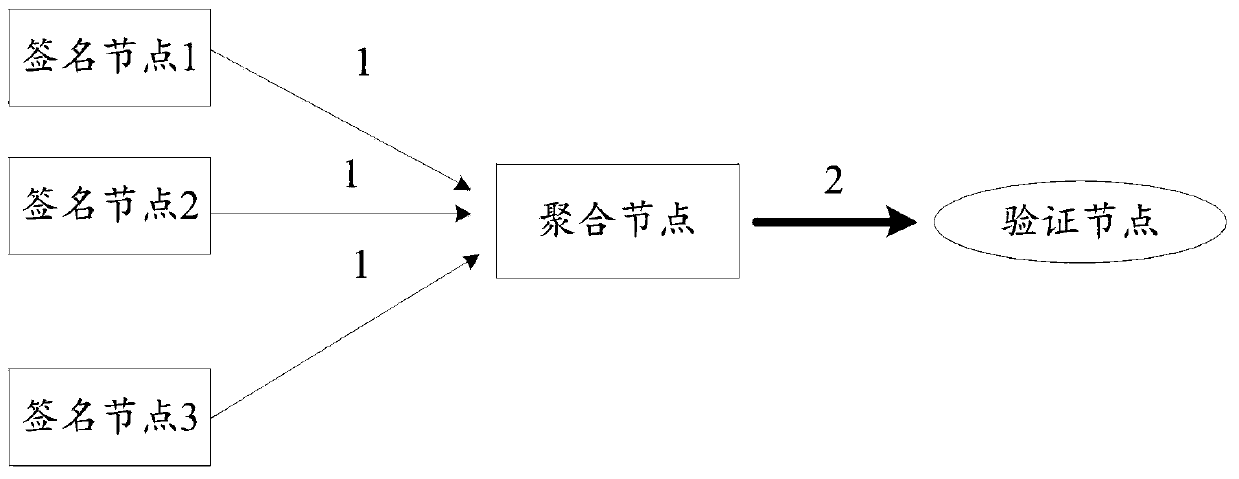
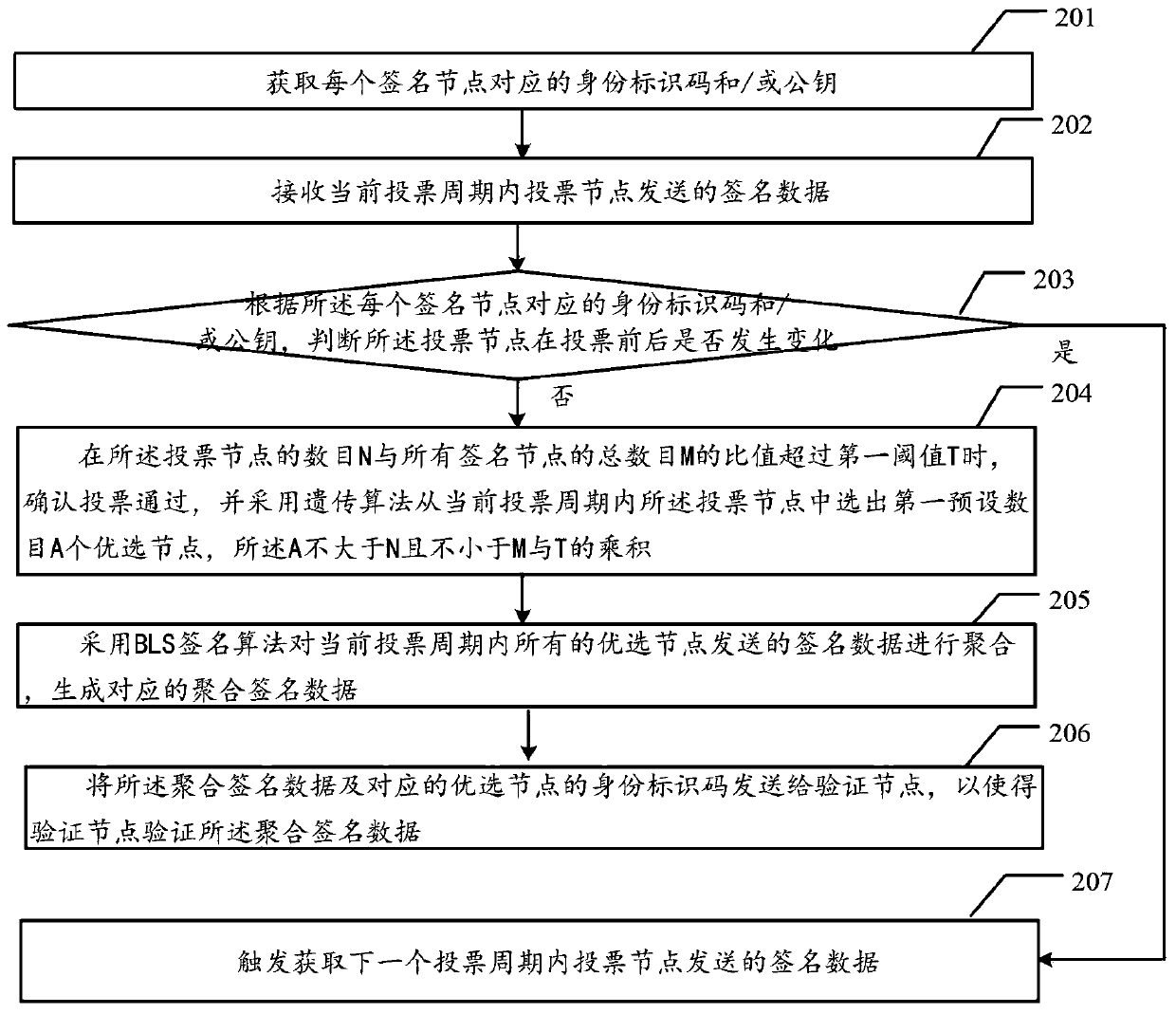
Threshold voting method based on blockchain consensus and related device
InactiveCN110399739ASmall amount of calculationSave bandwidthDigital data protectionGenetic algorithmsGenetic algorithmBlockchain
The embodiment of the invention provides a threshold voting method based on blockchain consensus and a related device. The threshold voting method and the related device are used for improving the aggregation speed and verification speed of aggregation nodes and verification nodes. The method provided by the embodiment of the invention comprises the following steps: acquiring an identity identification code and / or a public key of each signature node; receiving signature data sent by the voting node in the current voting period; judging whether the voting node changes before and after voting according to the identity identification code and / or the public key corresponding to each signature node; if not, when the ratio of the number N of the voting nodes to the total number M of all the signature nodes exceeds a first threshold T, adopting a genetic algorithm to select a first preset number A of preferred nodes from the voting nodes in the current voting period, wherein A is not larger than N and not smaller than the product of M and T; aggregating the signature data sent by the optimal node in the current voting period by adopting a BLS signature to obtain aggregated signature data;and sending the aggregated signature data and the identity identification code corresponding to the preferred node to a verification node.
Owner:SHENZHEN THUNDER NETWORK TECH +1
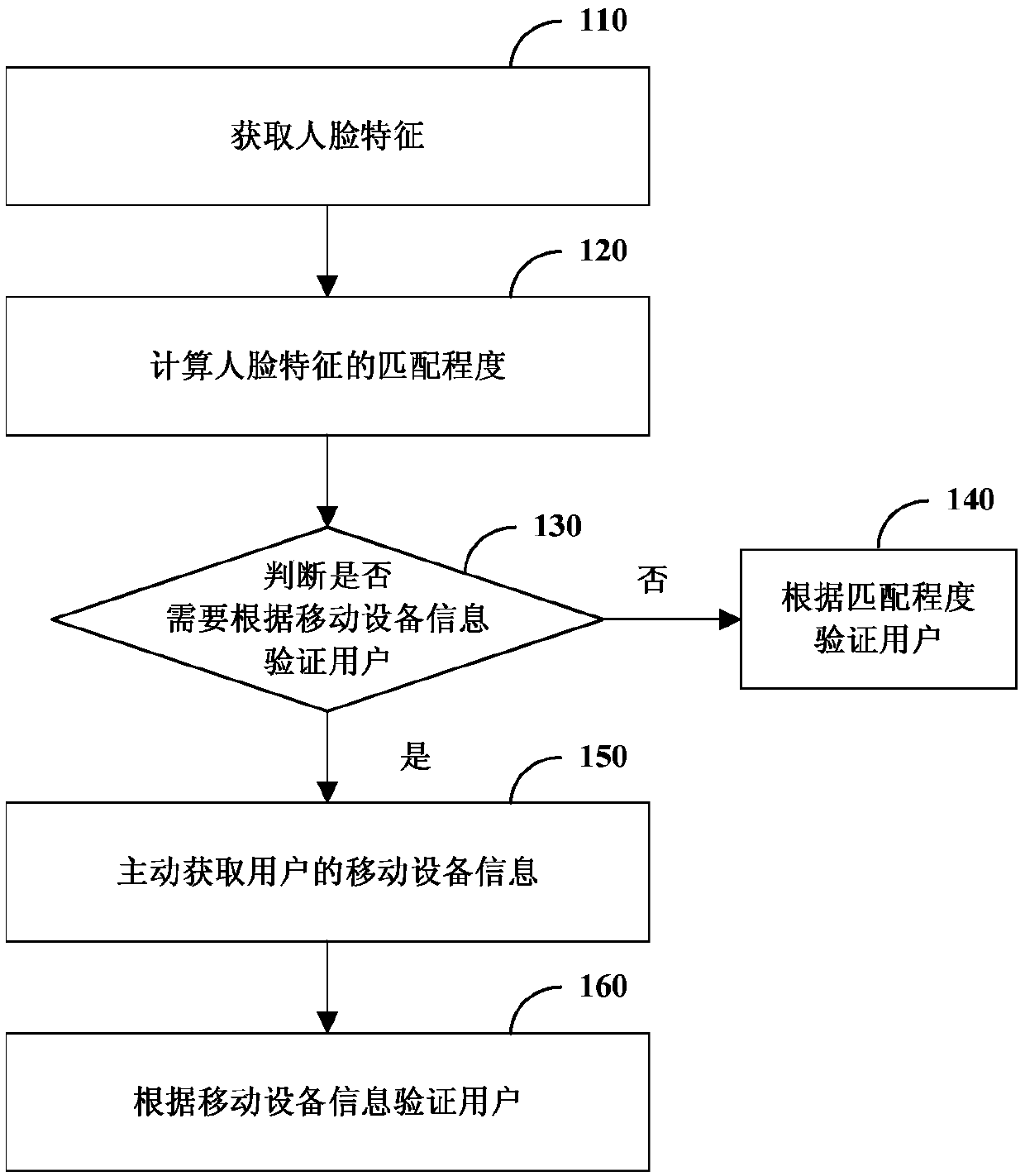
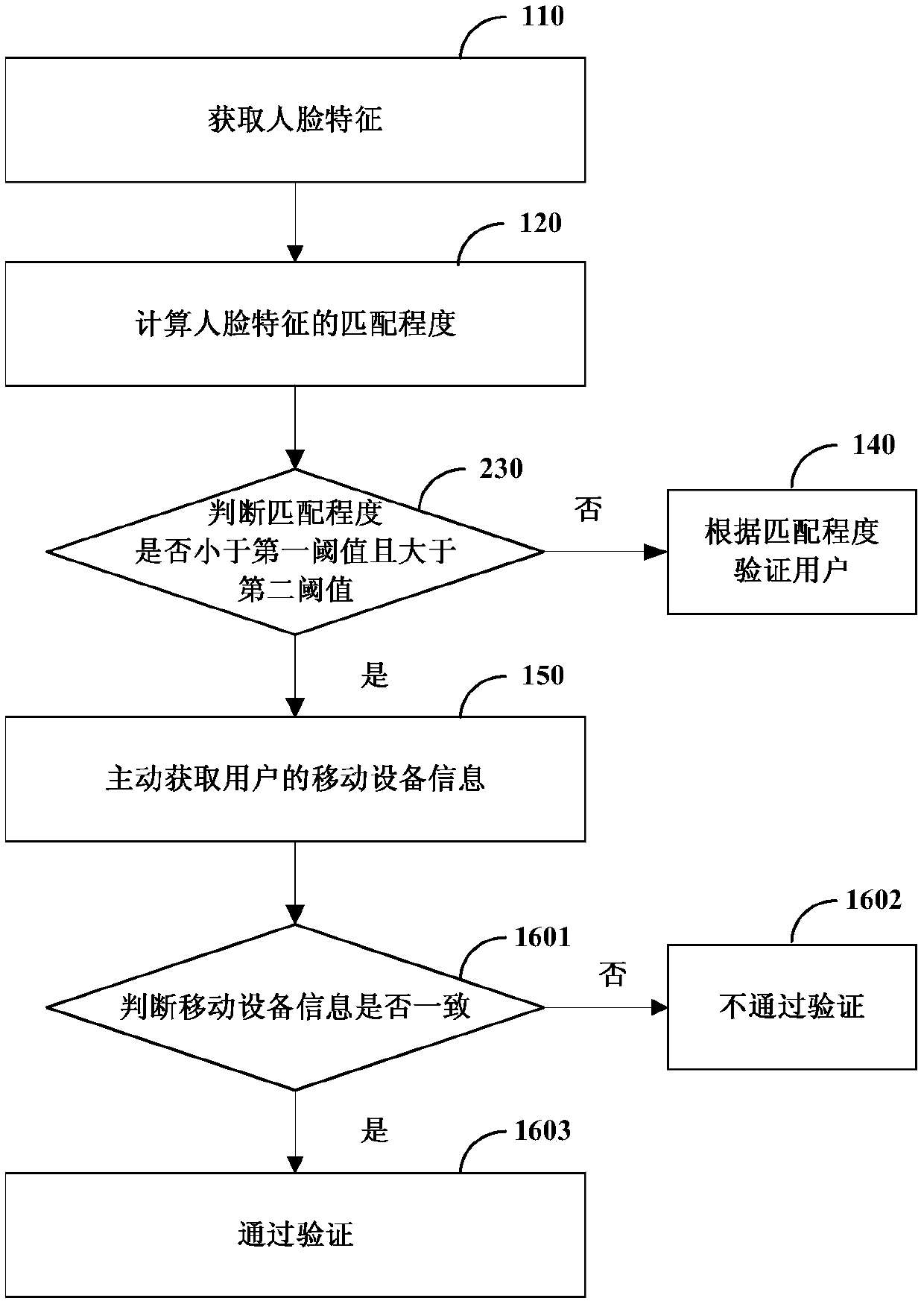
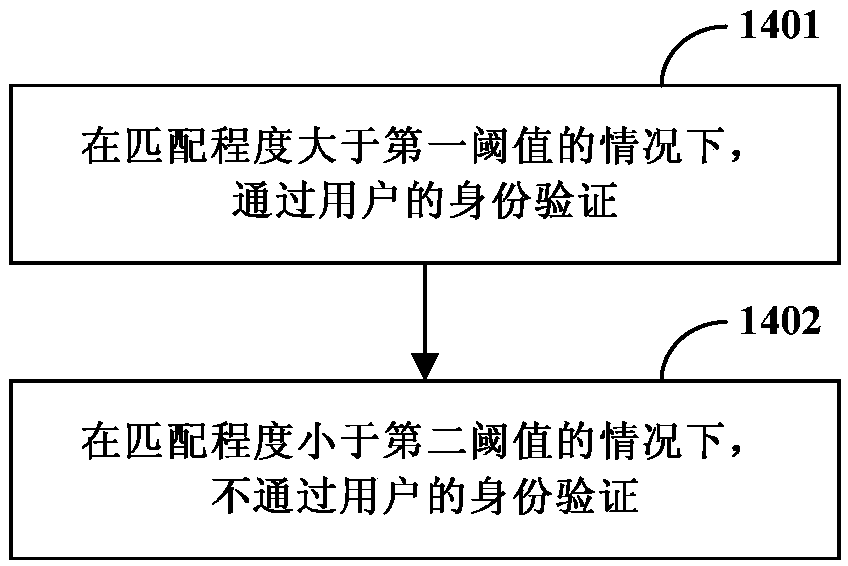
Identity verification system, method and device and computer readable storage medium
PendingCN110443098AImprove experienceImprove accuracyCharacter and pattern recognitionProtocol authorisationAuthentication systemComputer vision
The invention relates to an identity verification system, method and device and a computer readable storage medium, and relates to the technical field of information processing. The system comprises an image sensor configured to acquire a face image of a user; an equipment information acquisition device configured to acquire mobile equipment information of a user; and a processor configured to: performing face recognition on the face image to obtain face features of the user; calculating the matching degree of the acquired face features and the face features reserved by the user; judging whether the mobile equipment information of the user needs to be acquired to verify the user or not according to the matching degree; if not, determining whether the identity verification of the user is passed or not according to the matching degree; and determining whether the identity verification of the user is passed or not according to whether the acquired mobile equipment information is consistent with the mobile equipment information reserved by the user or not if necessary. According to the technical scheme, the identity verification accuracy and the user experience can be improved.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
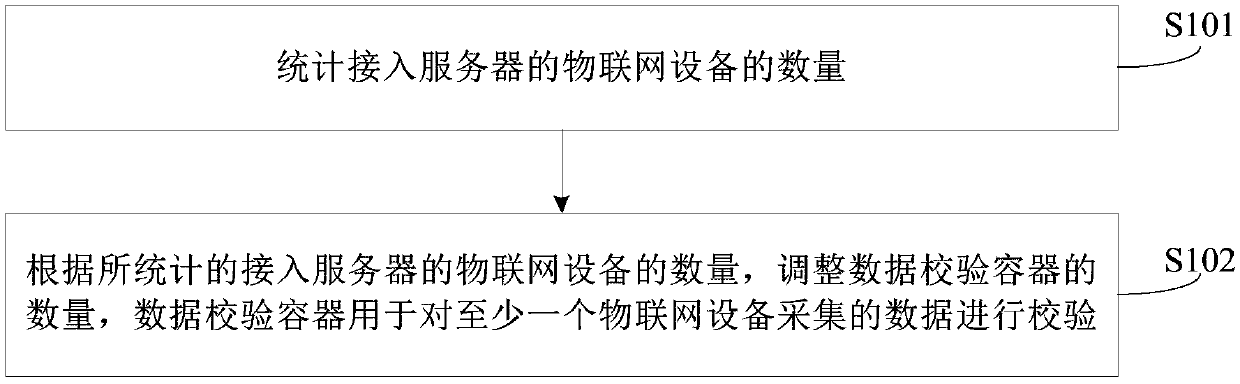
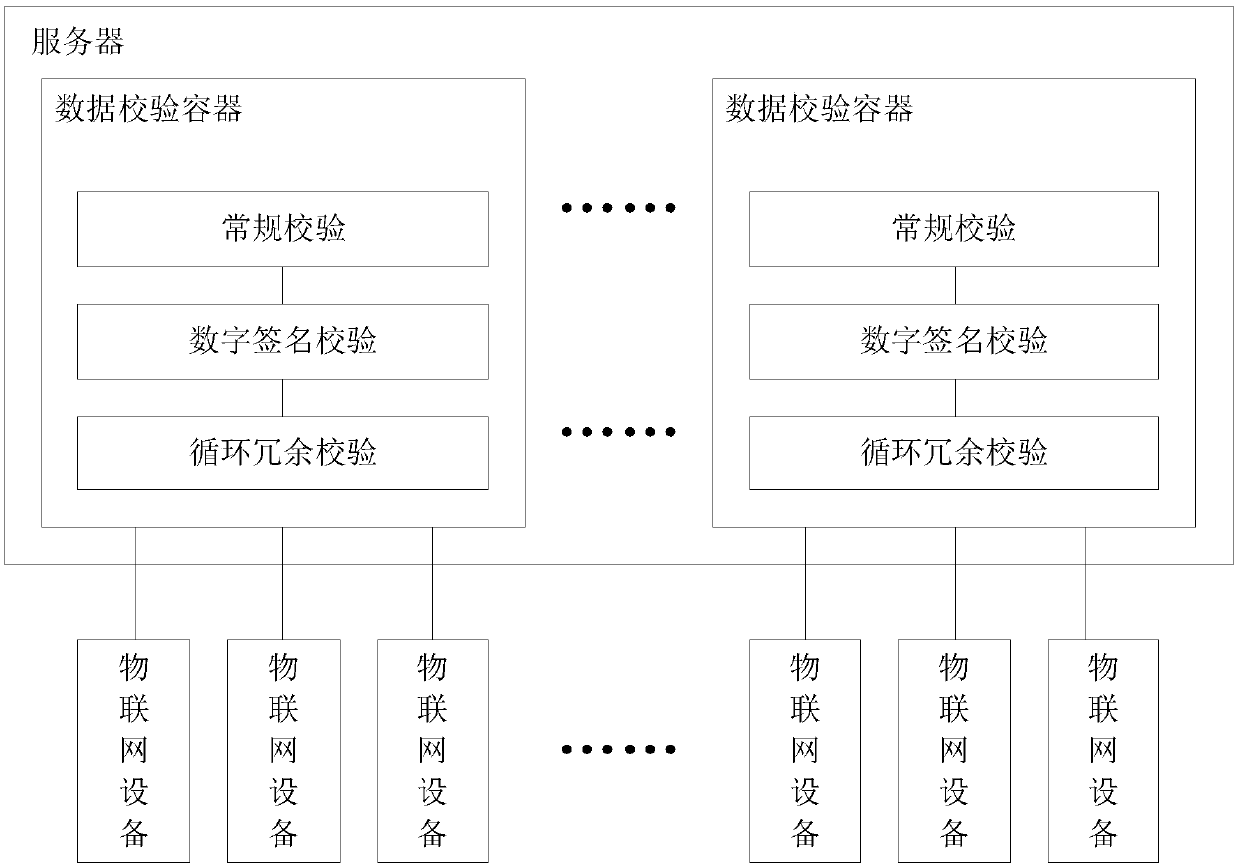
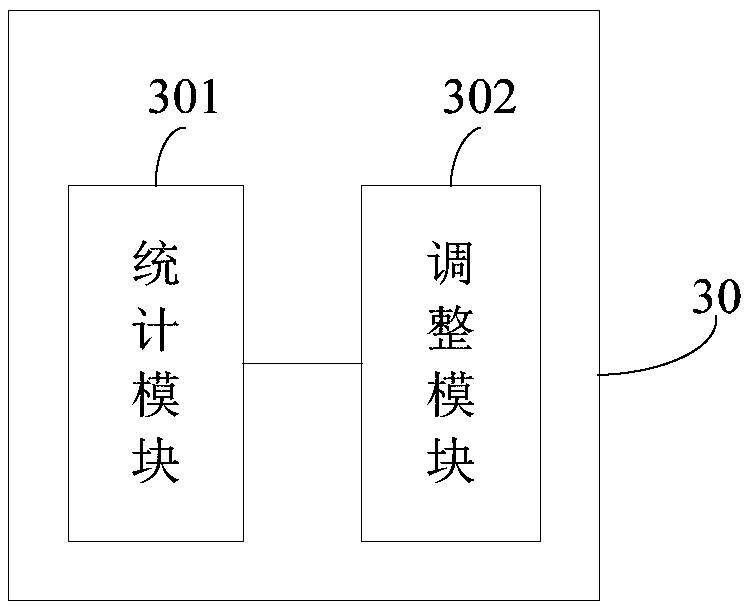
Data verification method and device, and server
An embodiment of the invention provides a data verification method, a data verification device and a server. The data verification method comprises the steps of: counting a number of IoT devices accessed to the server; and adjusting the number of data verification containers according to the number of IoT devices accessed to the server, wherein the data verification containers are configured to verify data acquired by means of at least one IoT device. The method provided by the embodiment of the invention realizes that the number of the data verification containers can be adaptively adjusted according to the number of the accessed IoT devices, and meets the massive data verification requirement when massive IoT devices are accessed to the network at the same time.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Mobile phone number verification method and system
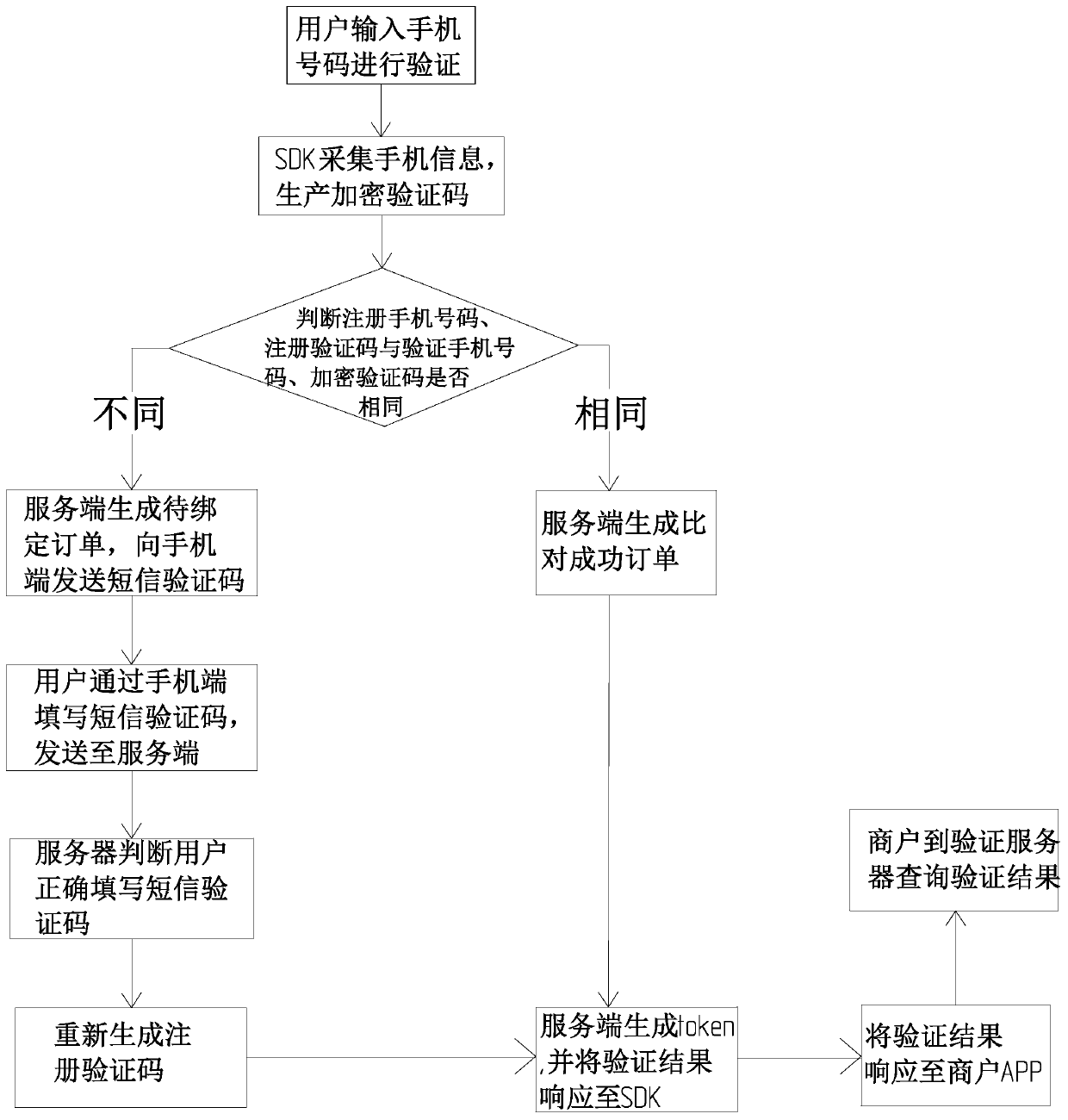
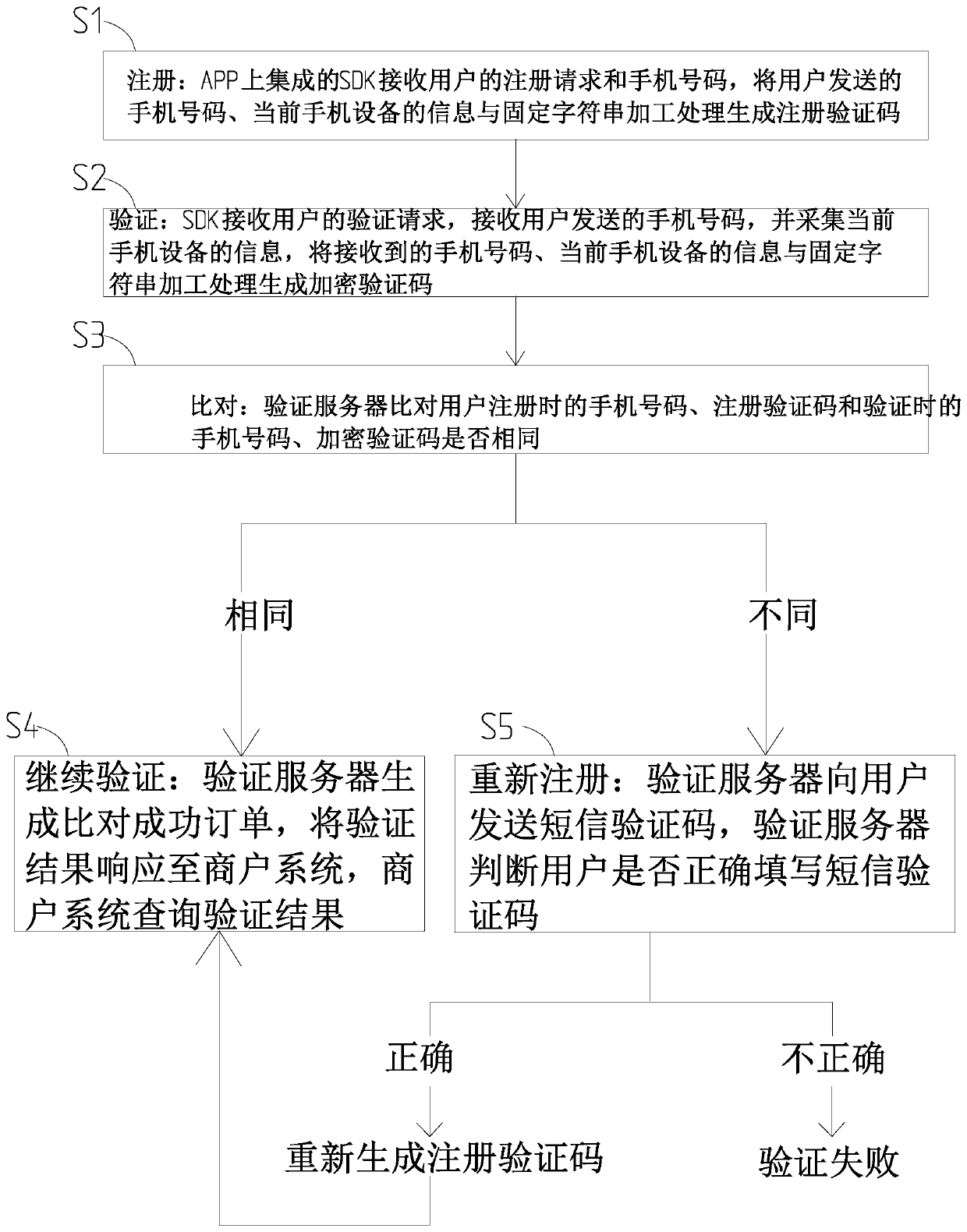
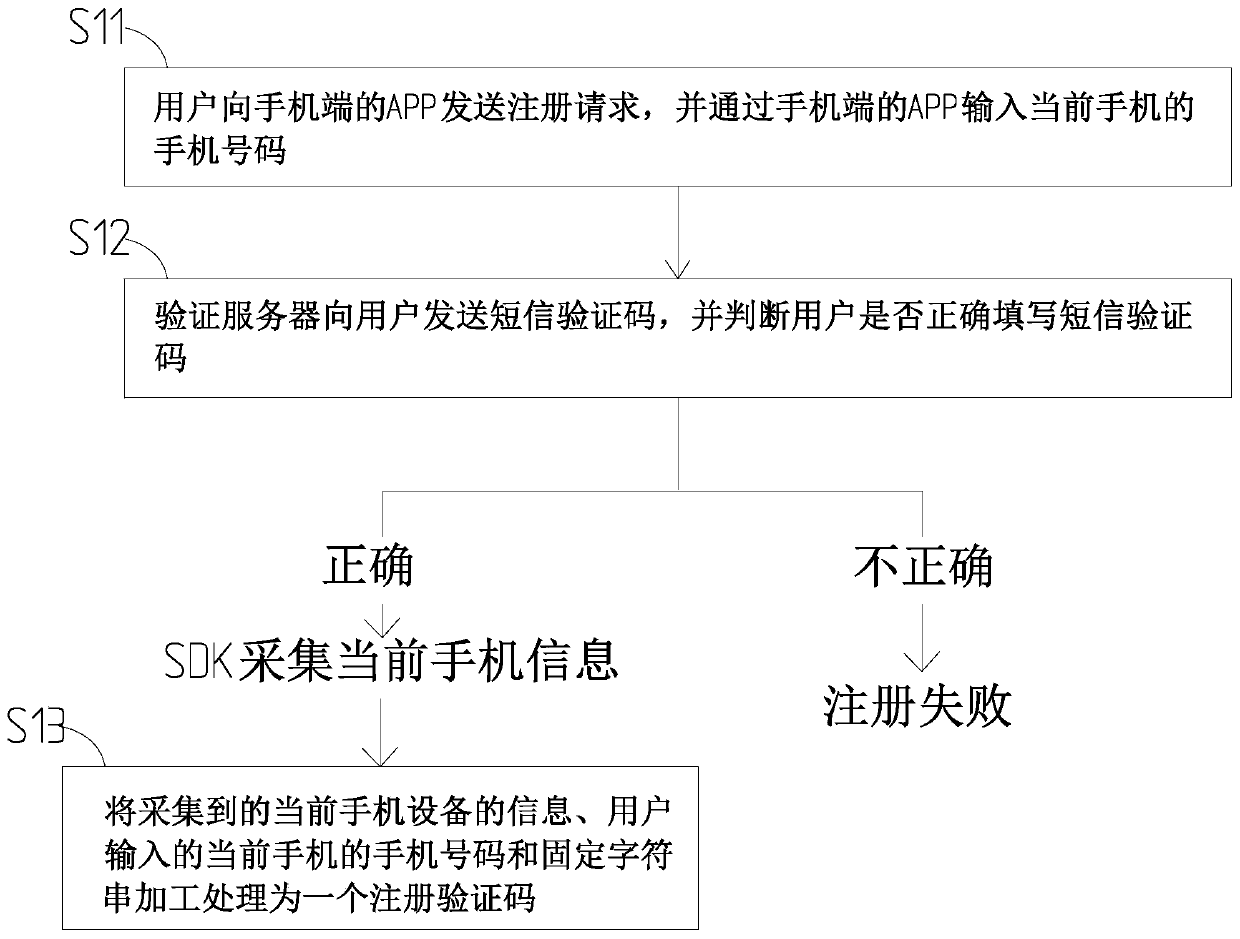
InactiveCN110149625AImprove securityImprove verification speedSecurity arrangementNetwork data managementMobile Telephone NumberComputer hardware
The invention provides a mobile phone number verification method and system, and the method comprises the following steps: S1, carrying out the processing of a mobile phone number input by a user, theinformation of a current mobile phone device, and a fixed character string, and generating a registration verification code; S2, receiving a mobile phone number input by a user, and processing the received mobile phone number, the information of the current mobile phone equipment and the fixed character string into an encrypted verification code; S3, the verification server comparing whether theregistered mobile phone number, the registration verification code, the verification mobile phone number and the encryption verification code are the same or not, if yes, performing the step S4, and if not, performing the step S5; S4, the verification server generating a comparison success order, and a verification result being corresponding to the merchant system; S5, performing short message verification, if the short message verification is correct, performing the step S4, and if the short message verification is not correct, verification failing. The method and the system have the advantages that the safety is improved, the verification speed is increased, and the operation is simple.
Owner:北京么登科技有限公司
Heterogeneous parallel block chain and technical implementation thereof
ActiveCN108881177AEnsure safetyImprove verification speedFinanceTransmissionProof-of-stakeChain structure
The invention relates to a heterogeneous parallel block chain and technical implementation thereof, and relates to the technical field of block chain bases. The heterogeneous parallel block chain is between a chain structure and a DAG, and comprises a service receiving block and a service result block; the service receiving block and the service result block are formed from existing blocks in a splitting manner; and furthermore, DPOS (Delegated Proof Of Stake) is used as a consistency protocol. The technical implementation of the heterogeneous parallel block chain comprises the steps that: a,an appointed block producer determined by the DPOS receives a service, and packs the service in the service receiving block; b, after packing, the producer runs a smart contract; and c, the producer packs a result in the service result block; and result nodes simultaneously verify two blocks: the corresponding service receiving block and the previous service result block. Parallel running of the smart contracts of different blocks can be realized; simultaneously, the security is ensured; the block verification speed is increased; the fast transaction and the verification speed can be improved;the speed is higher than that of chain structures, such as the EOS; the fast transaction can be supported; and simultaneously, the security cannot be reduced.
Owner:夸克链科技(深圳)有限公司
Fast distributed-storage multi-replica consistency checking method and storage architecture
InactiveCN107632781AAvoid readingReduce consumptionInput/output to record carriersRedundant data error correctionData segmentComputer science
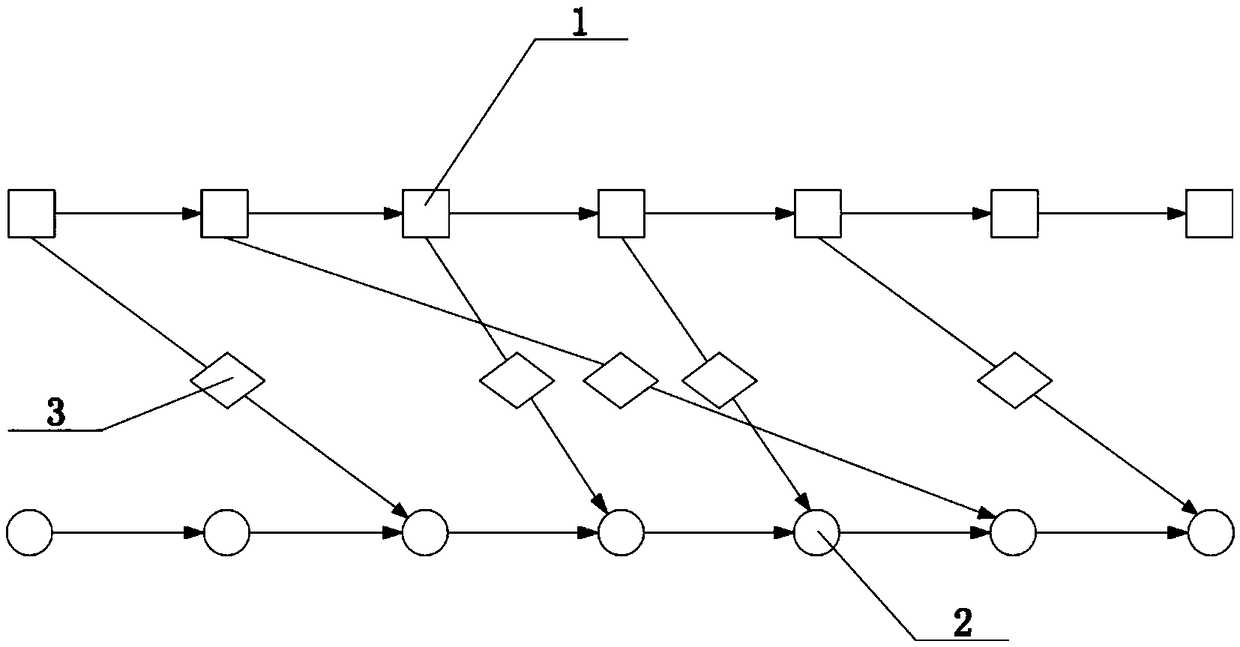
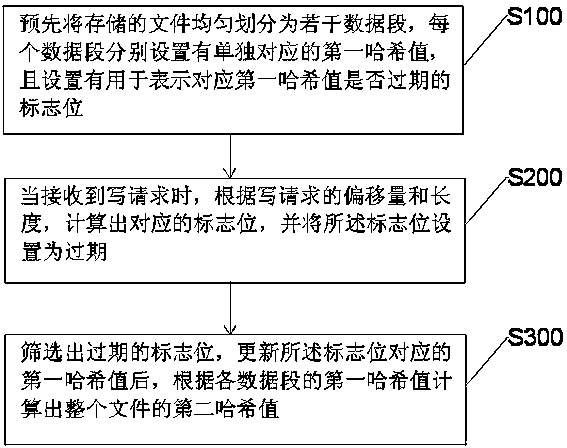
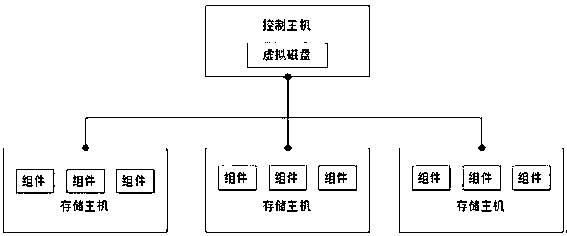
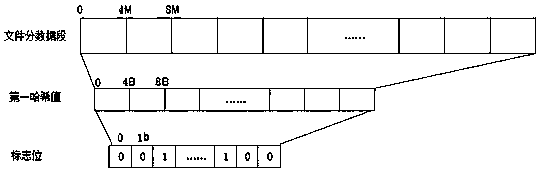
The invention discloses a fast distributed-storage multi-replica consistency checking method and a storage architecture. The method adopts a control host-storage host processing architecture, and includes: evenly dividing a stored file into a plurality of data segments in advance, and respectively setting an individually-corresponding first hash value and a mark bit, which is used for indicating whether the corresponding first hash value expires, for each data segment; when a writing request is received, calculating the corresponding mark bit according to offset and length of the writing request, and setting the mark bit to expiry; and screening out the expiry mark bit, updating the first hash value corresponding to the mark bit, and then calculating a second hash value of the entire fileaccording to the first hash value of each data segment. According to the method, the large file is divided into the plurality of data segments, the hash values of the file are calculated in a segmented manner, then the hash value of the entire file is calculated through the hash value of each segment, reading data of the entire file is avoided, thus a consistency detection speed is increased, andbandwidth consumption of storage hosts is reduced.
Owner:深圳市联云港科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com