A method for identifying the integrity of transaction information
A technology for transaction information and integrity, which is applied in the field of information security and can solve problems such as hidden dangers of user interests and security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
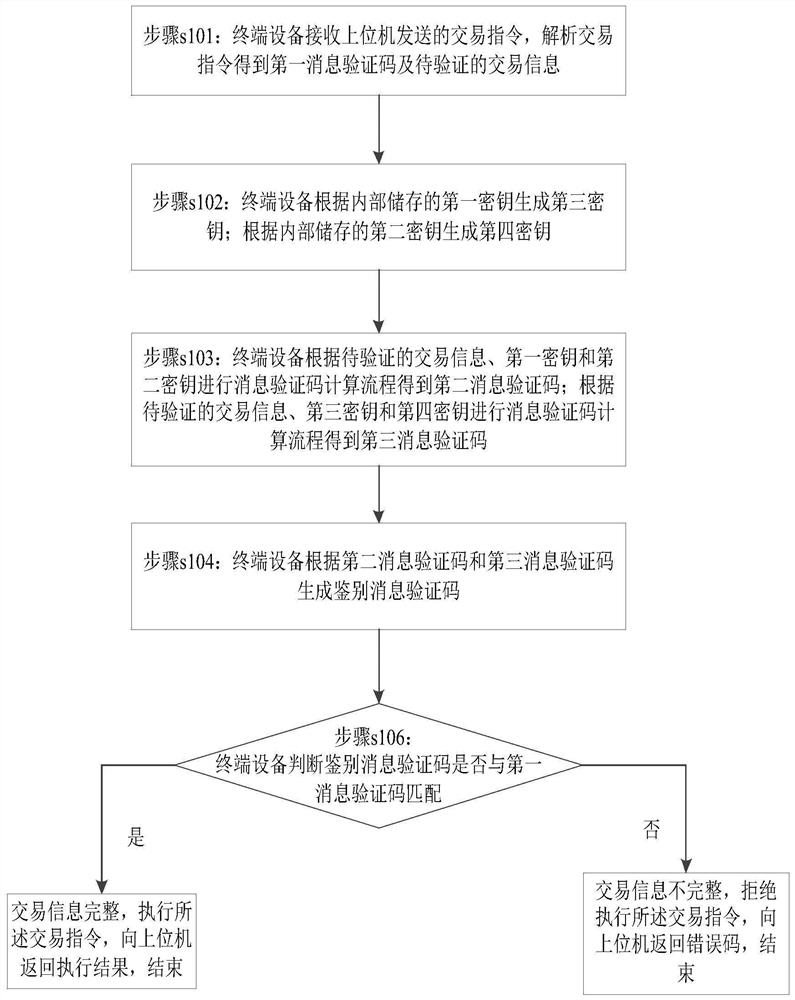
[0036] According to Embodiment 1 of the present invention, a method for identifying the integrity of transaction information is provided, such as figure 1 shown, including:
[0037] Step s101: the terminal device receives the transaction instruction sent by the host computer, analyzes the transaction instruction to obtain the first message verification code and the transaction information to be verified.
[0038] Step s102: the terminal device generates a third key according to the internally stored first key; generates a fourth key according to the internally stored second key;
[0039] Wherein, the first key and the second key are preset known keys;
[0040] Specifically, starting from the fourth bit group of the first key, every four bits are alternately complemented to obtain the third key, and starting from the fourth bit group of the second key, every four bits are alternately complemented to obtain Fourth key.
[0041] For example: the first key is 01 23 45 67 89AB C...
Embodiment 2
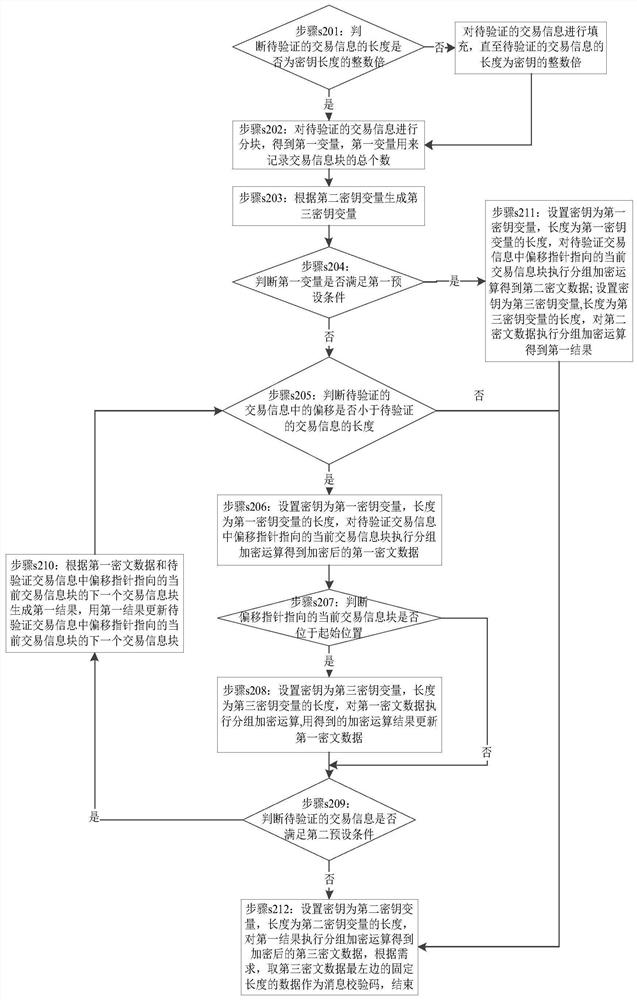
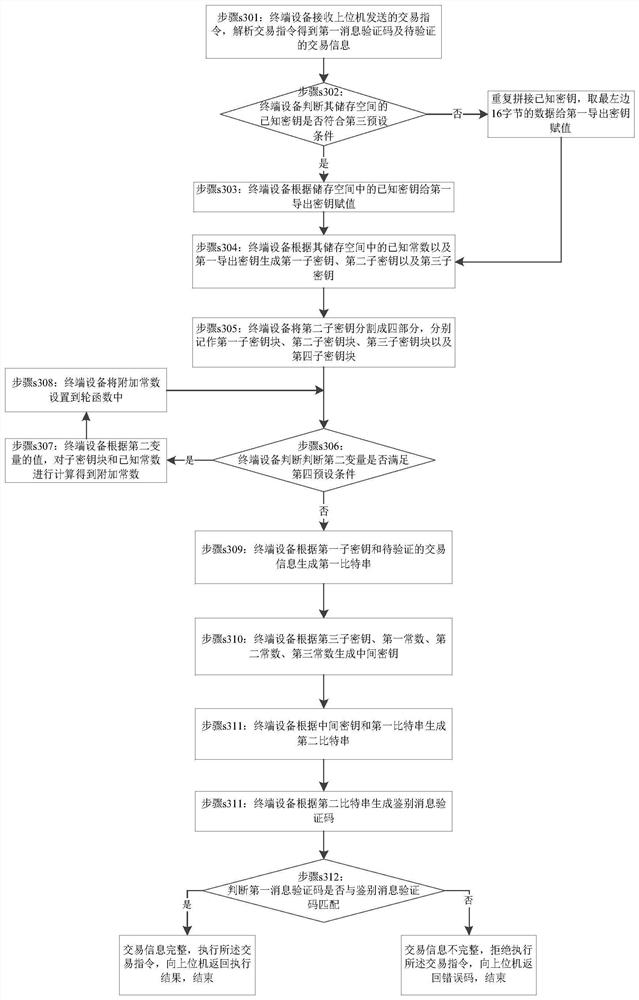
[0077] Embodiment 2 of the present invention provides a method for identifying the integrity of transaction information, such as image 3 shown, including:
[0078] Step s301: the terminal device receives the transaction instruction sent by the host computer, analyzes the transaction instruction to obtain the first message verification code and the transaction information to be verified.
[0079] Step s302: The terminal device judges whether the known key in its storage space meets the third preset condition, if yes, execute step s303; if not, repeat the splicing of the known key, and take the leftmost 16 bytes of data to the first Export key assignment, execute step s304;
[0080] Specifically, the terminal device judges whether the key in its storage space meets the third preset condition: judge whether the length of the known key is 16 bytes, if yes, perform step s303; if not, repeat the splicing of the known key , take the leftmost 16-byte data to assign a value to the f...
Embodiment 3
[0108] Embodiment 3 of the present invention provides a device for authenticating the integrity of transaction information, such as Figure 4 shown, including:
[0109] The receiving module 10 is used to receive the transaction instruction sent by the host computer;
[0110] The parsing module 11 is configured to parse the transaction instruction received by the receiving module to obtain the first message verification code and the transaction information to be verified.
[0111] The segmentation module 12 is used to divide the transaction information to be verified obtained by the parsing module into blocks to obtain transaction information blocks;
[0112] The segmentation module is also used to obtain the first variable when segmenting the transaction information to be verified, and the first variable is used to record the number of transaction information blocks.
[0113] A storage module 13, configured to store the first key and the second key;
[0114] The first gener...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com