Network transaction platform account control method and device, and server
A technology for network transactions and account control, applied in the network field, can solve the problems of inability to find secure login management and authority division, account information being stolen, and unsuitable for company-level merchants' security needs and experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] This embodiment provides an account control method for an online trading platform, including:
[0099] Provide a hierarchical control function for a user account, divide the functions provided for the user account into at least two layers, each layer includes one or more functions, and each layer corresponds to a security check;
[0100] Enable or authorize the hierarchical control function for the user account;
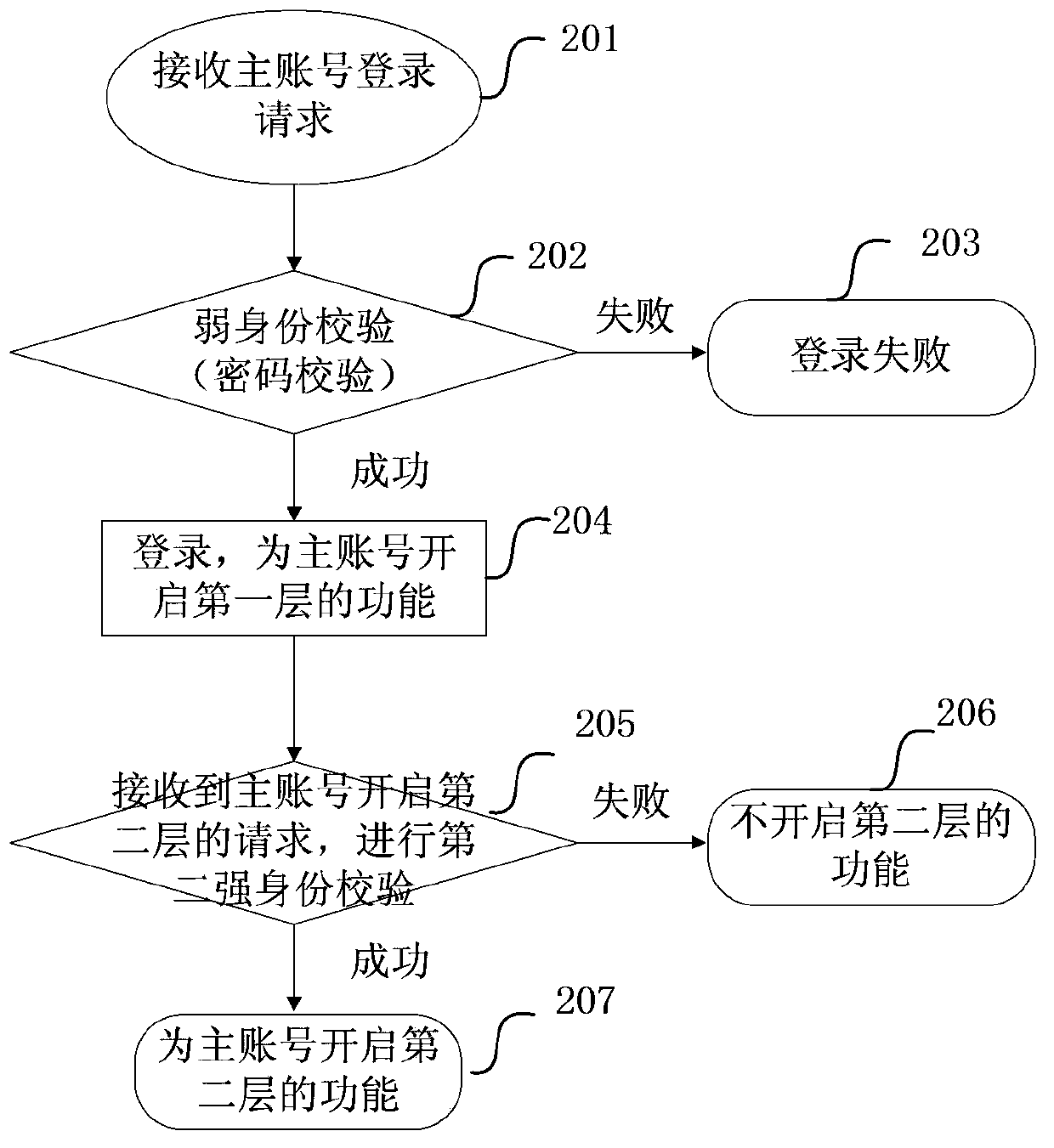
[0101] When the user account is subsequently logged in, after receiving the request to open the layer of the user account, if the user account passes the security check corresponding to the layer requested to be opened, the user account opens the requested layer. Each function of the opened layer; and maintain the opened state of the opened layer until the user account is logged out of the system or the opened layer is closed for the user account. Among them, opening a layer means opening each function of the layer.
[0102] In an alternative solution of this embodim...
example 1
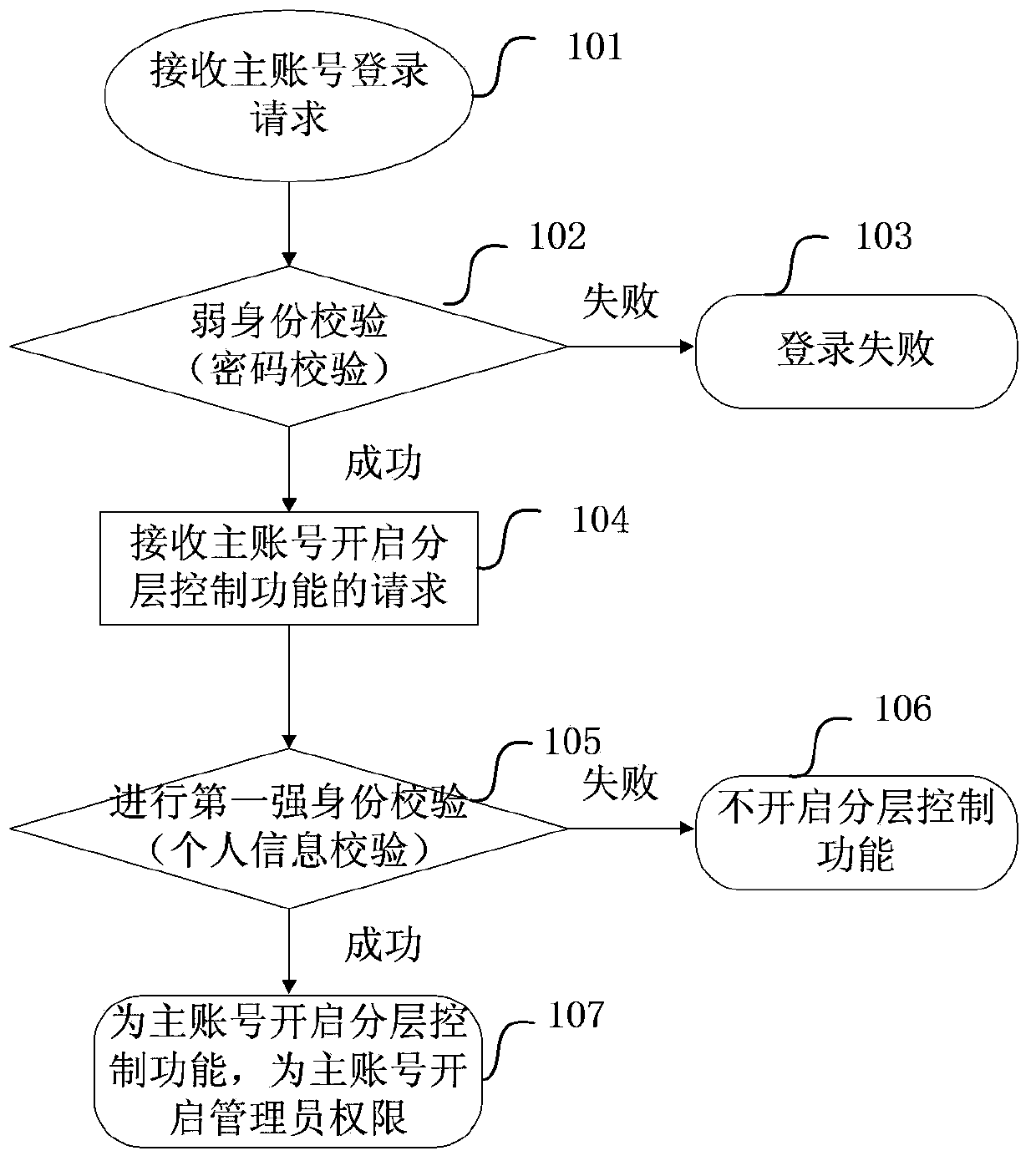
[0143] Such as figure 1 As shown, the hierarchical control function is enabled for the main account, including:
[0144] Step 101: The server receives the login request of the master account;
[0145] Step 102, the server performs identity verification, which is called weak identity verification here, for example, verifying whether the password carried in the login request is correct; if the verification is successful, go to step 104; otherwise, go to step 103;
[0146] Step 103, notify the master account that the login failed, and end;
[0147] Step 104, notify the master account that the login is successful, and receive the request of the master account to enable the hierarchical control function;
[0148] Step 105: After the server receives the request to enable the hierarchical control function of the master account, it performs a security check corresponding to the hierarchical control function, which is referred to herein as the first strong identity check, which includes personal...
example 2
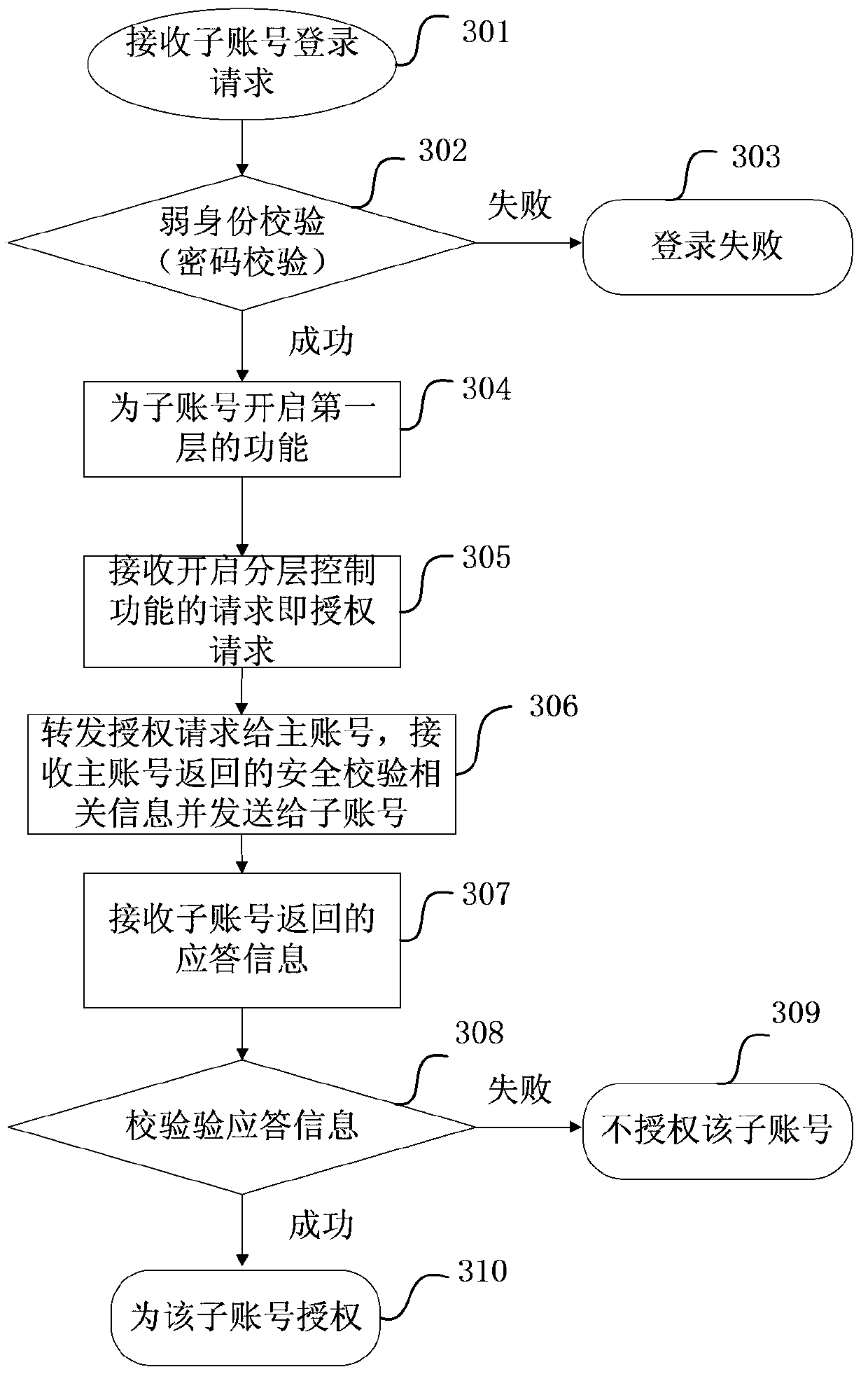
[0167] In this application, the main account and the sub-account are provided, and the sub-account needs to be authorized by the main account to obtain the second-level functions. The authorization of the sub-account is as image 3 Shown, including:
[0168] Step 301: The server receives the login request of the sub-account;
[0169] Step 302, the server performs identity verification, here is weak identity verification (verify whether the password carried in the login request is correct); if the verification is successful, go to step 304, otherwise, go to step 303;
[0170] Step 303, notify the sub-account that the login failed, and end;
[0171] Step 304, notify the sub-account that the login is successful, and enable the first-level function for the sub-account;
[0172] Step 305: Receive a request for enabling the hierarchical control function of the sub-account, which is equivalent to an authorization request;
[0173] Step 306: Forward the request to enable the hierarchical contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com