Patents
Literature
211results about How to "Avoid traffic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
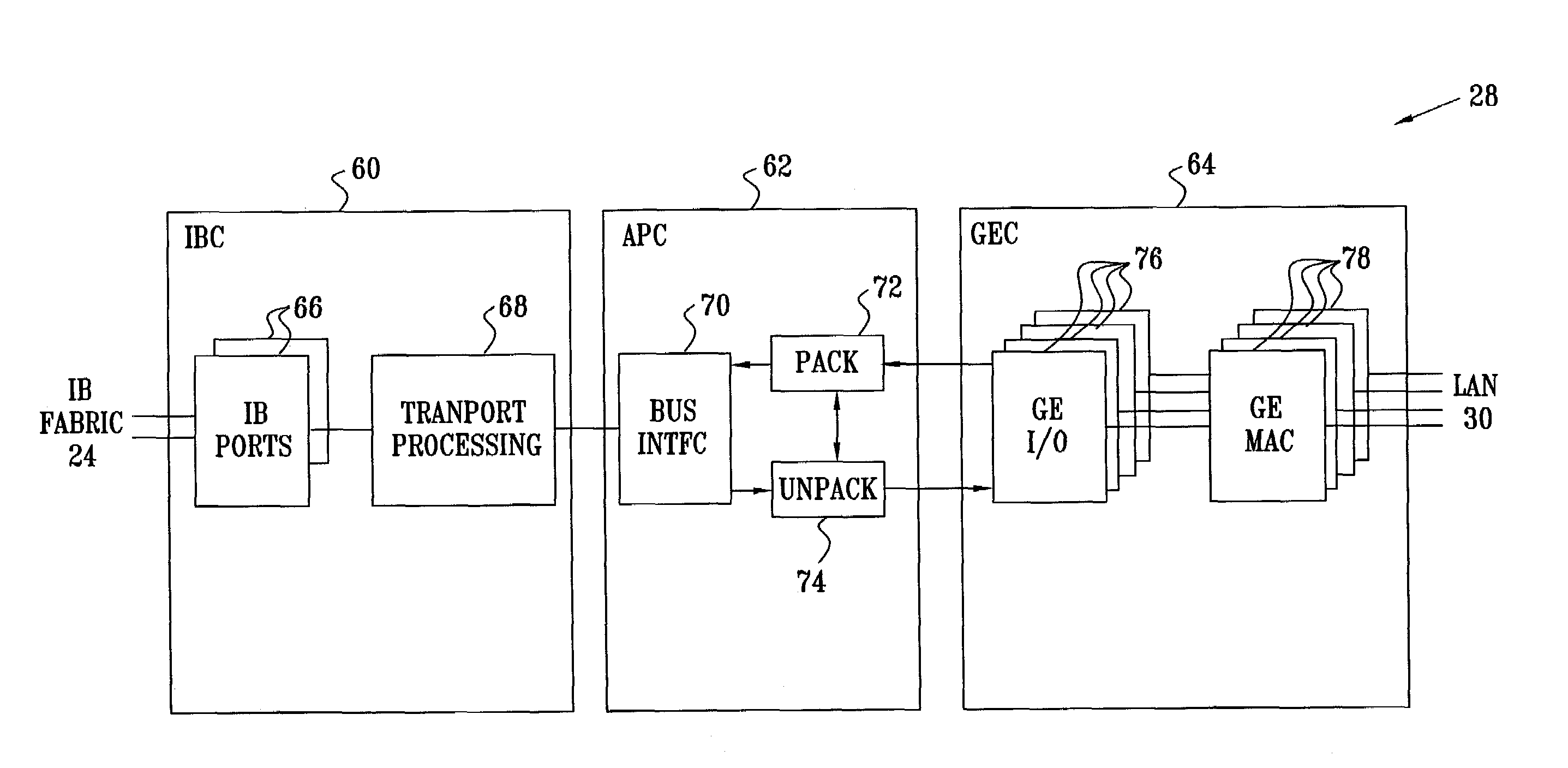
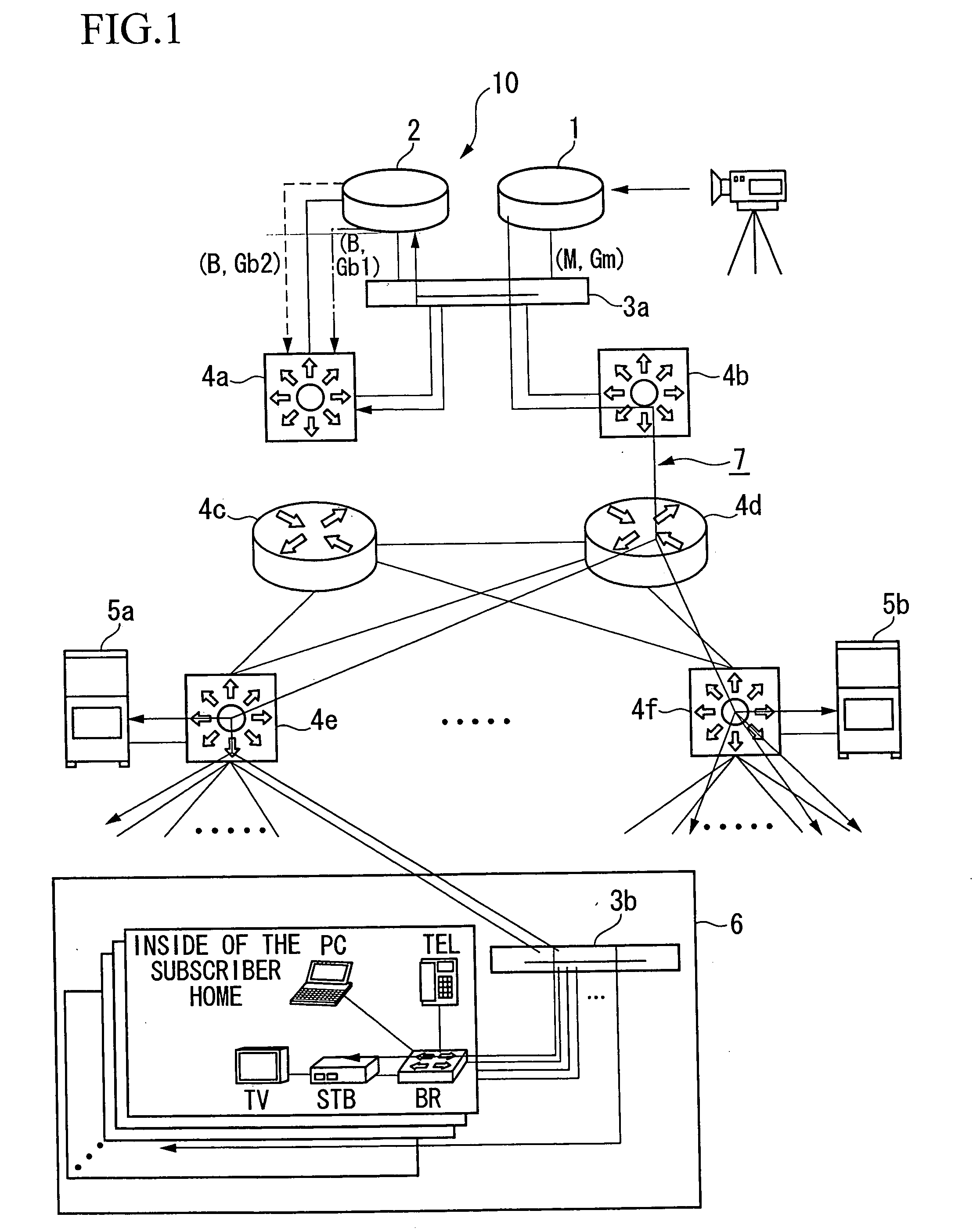
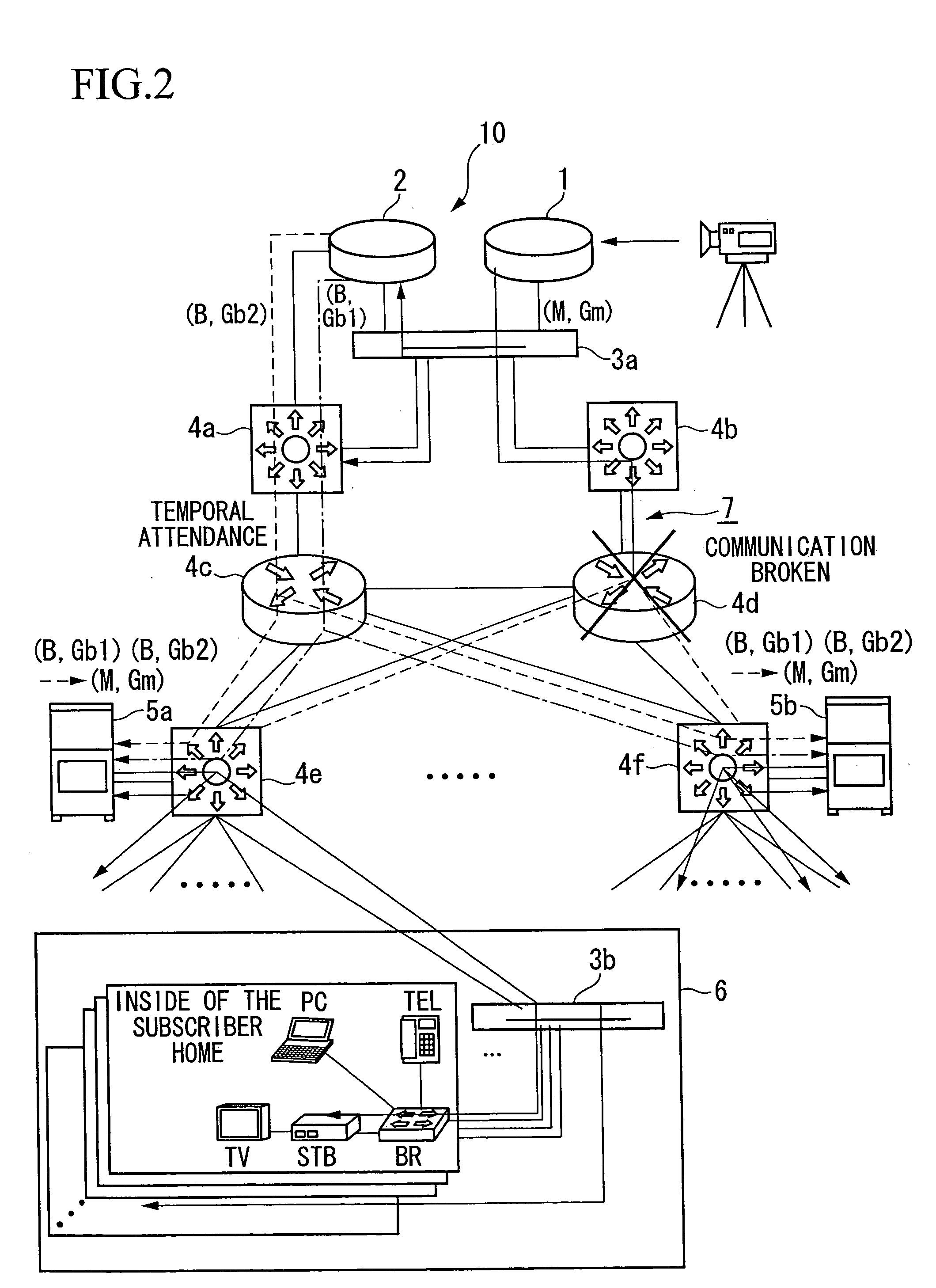
Sharing a network interface card among multiple hosts
ActiveUS7245627B2Allows costly, high-speed network processing resources to be sharedAvoid trafficData switching by path configurationMultiple digital computer combinationsSwitched fabricDistributed computing
A network interface device includes a fabric interface, adapted to exchange messages over a switch fabric with a plurality of host processors, the messages containing data, and a network interface, including one or more ports adapted to be coupled to a network external to the switch fabric. Message processing circuitry is coupled between the fabric interface and the network interface, so as to enable at least first and second host processors among the plurality of the host processors to use a single one of the ports substantially simultaneously so as to transmit and receive frames containing the data over the network.
Owner:MELLANOX TECHNOLOGIES LTD
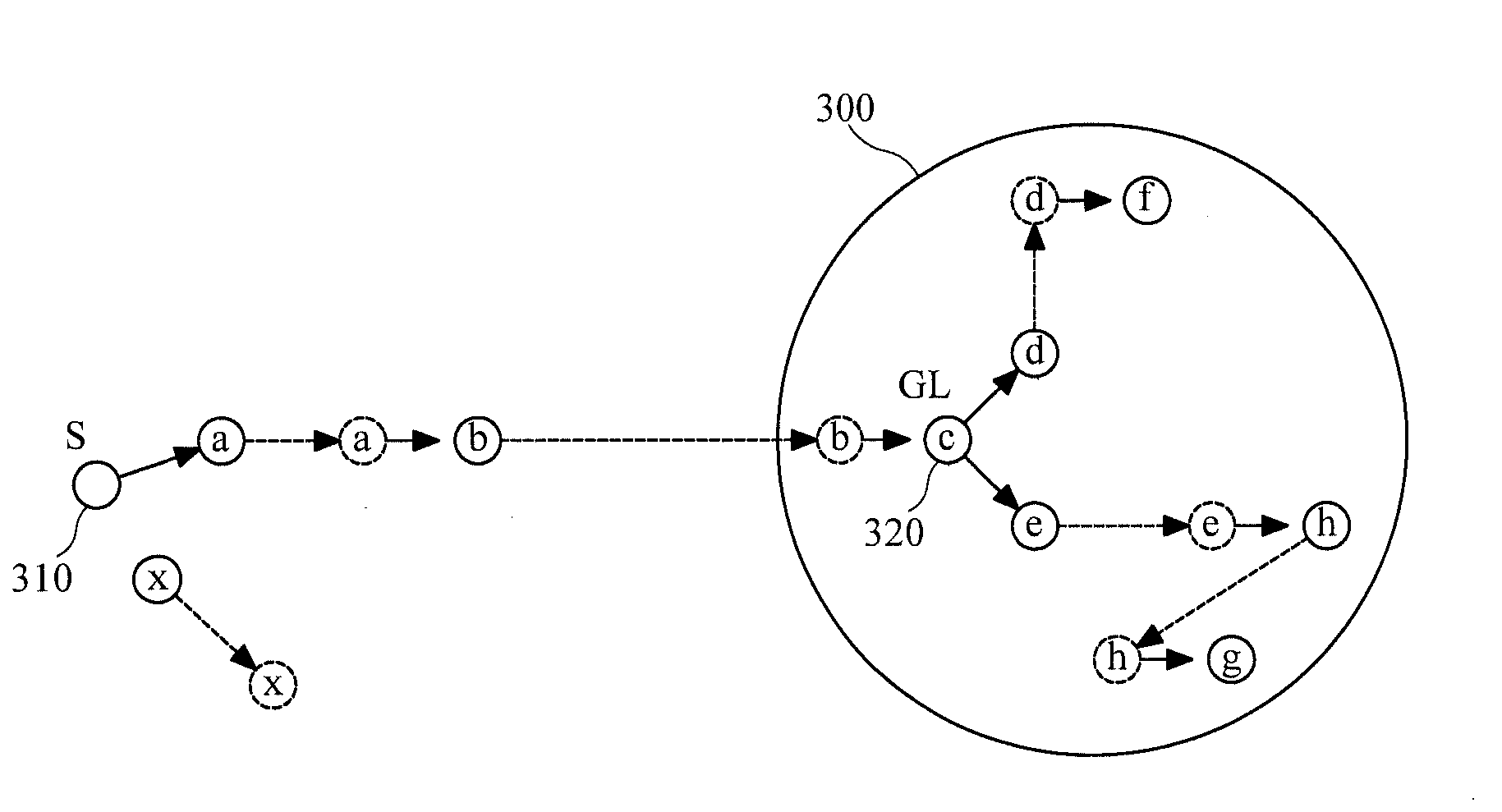
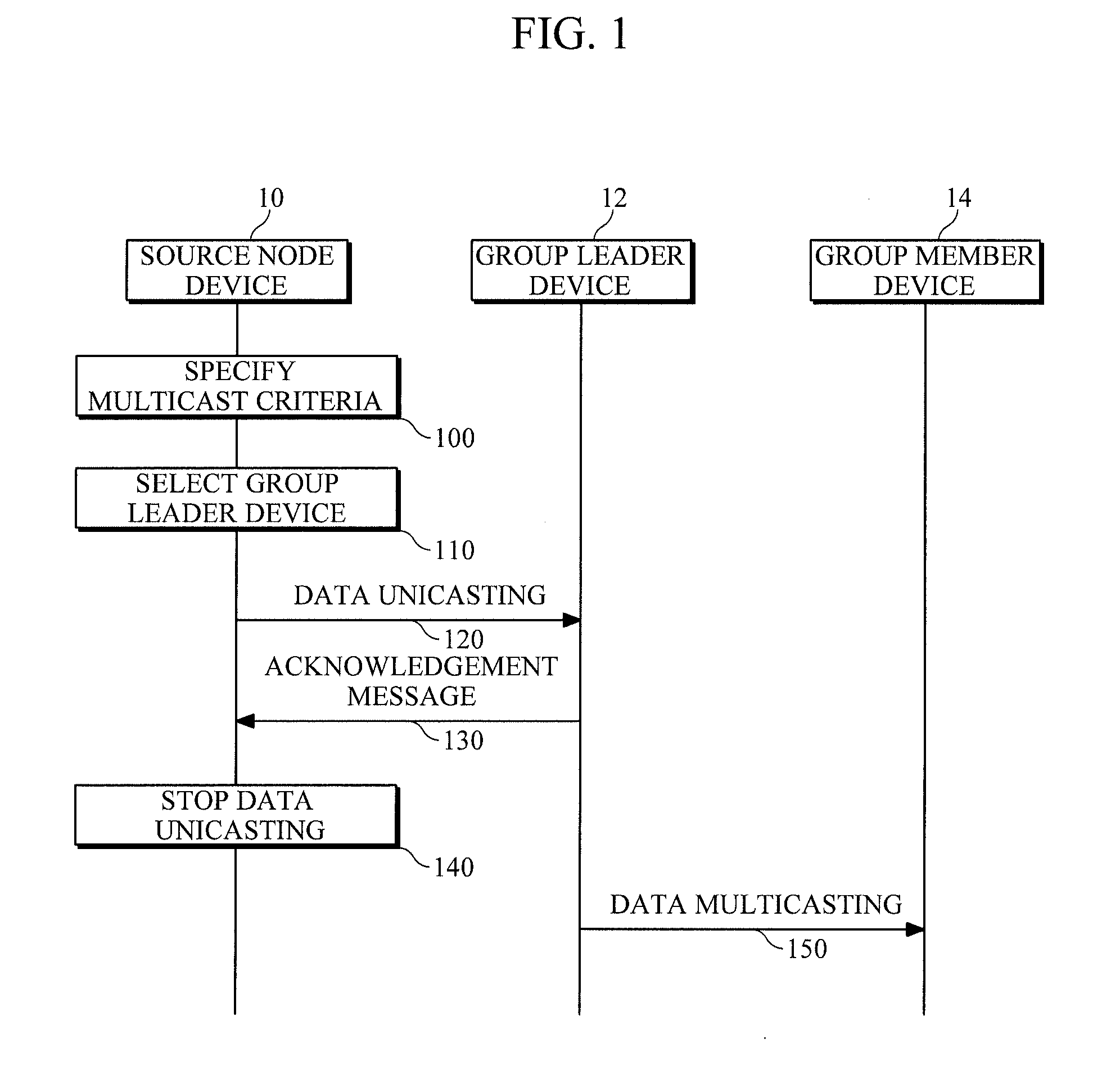
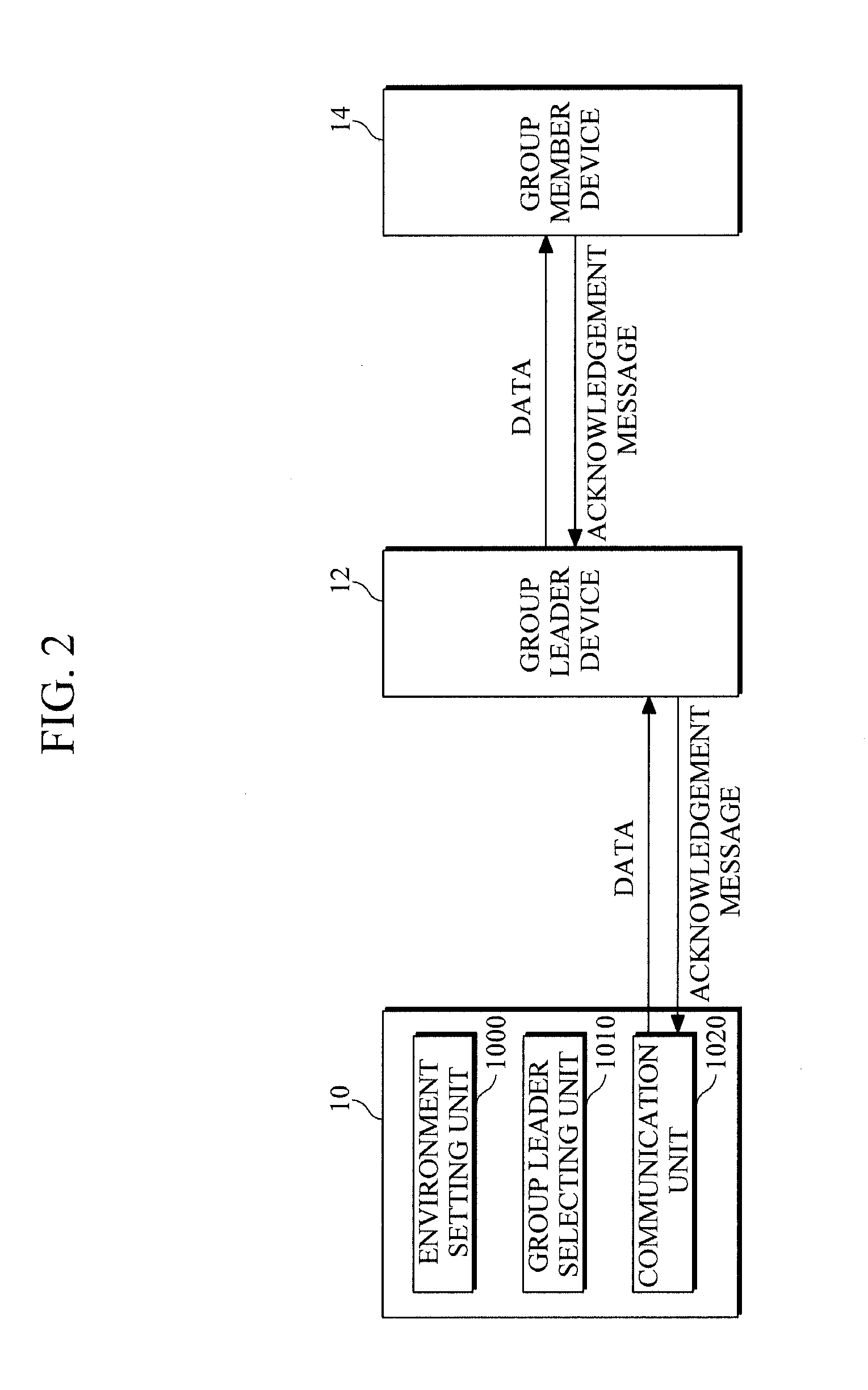
Multicast communication method, apparatus and system for intermittently connected network
InactiveUS20120127994A1Effective supportAvoid trafficSpecial service provision for substationData switching by path configurationTraffic volumeTraffic capacity
A multicast communication method, a multicast communication apparatus and a multicast communication system in a network environment lacking a continuous connectivity. The source node device selects a group leader device which is able to forward data to group member devices belonging to a multicast group, and forwards the data to the selected group leader device, thereby reducing traffic between node devices, improving network reliability and saving the communication cost.
Owner:ELECTRONICS & TELECOMM RES INST
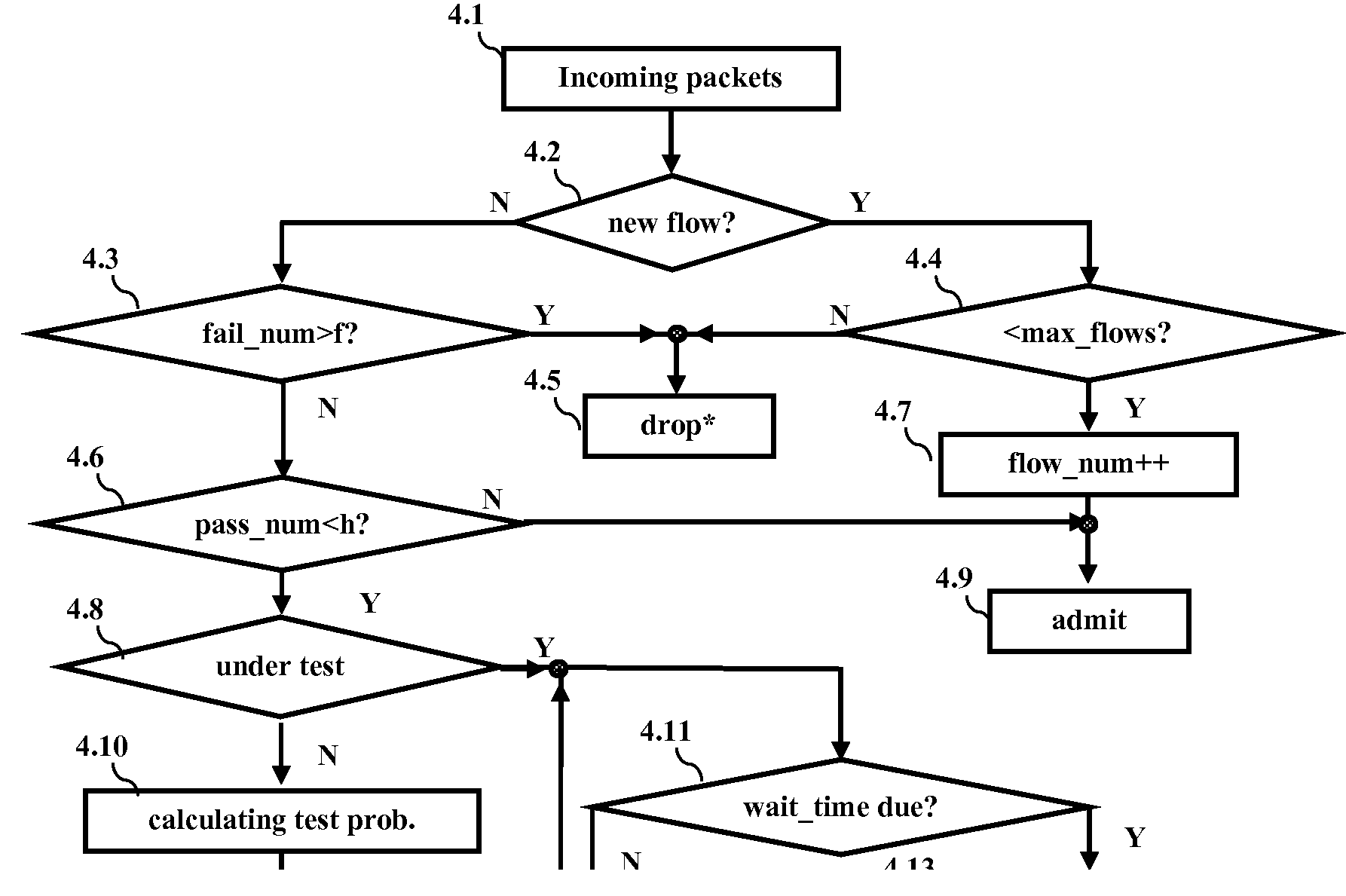
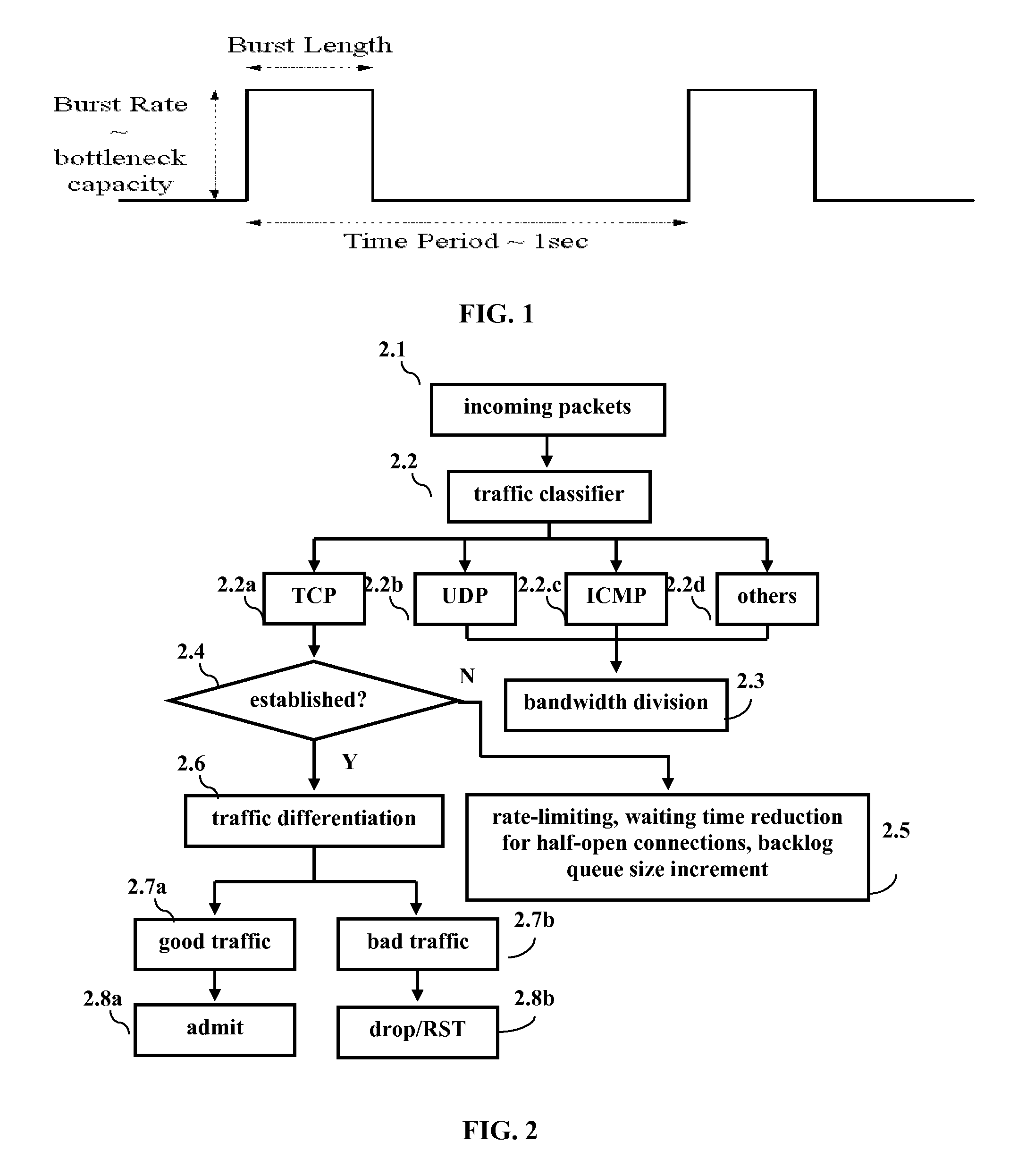
BEHAVIOR-BASED TRAFFIC DIFFERENTIATION (BTD) FOR DEFENDING AGAINST DISTRIBUTED DENIAL OF SERVICE (DDoS) ATTACKS
ActiveUS20070209068A1Improve throughputMinimal requirementMultiple digital computer combinationsTransmissionTraffic differentiationEngineering
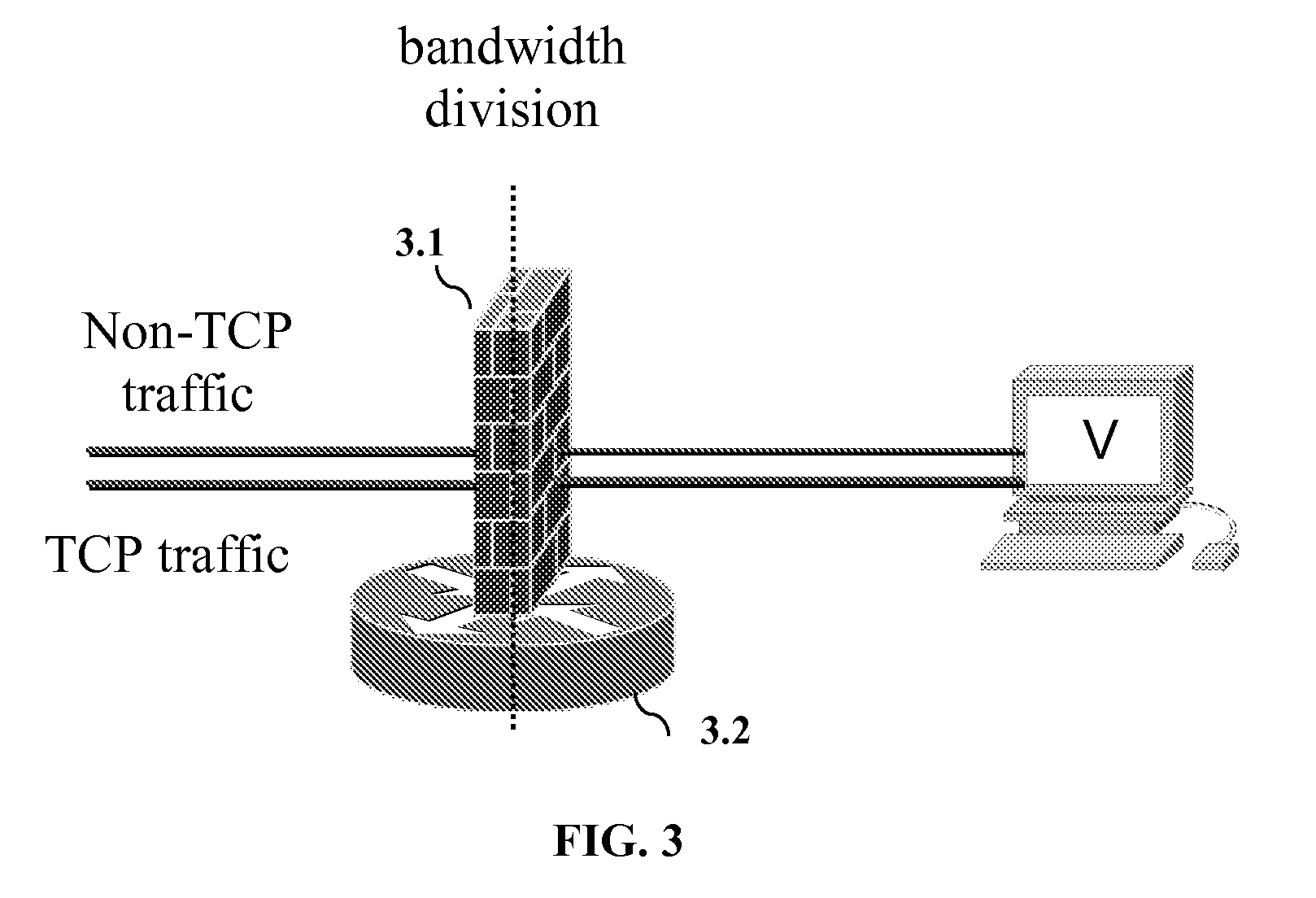
Embodiments are directed toward a method for Behavior-based Traffic Differentiation (BTD) that initially receives incoming packets and performs traffic classification to determine the protocol of the incoming packets. In addition, BTD performs bandwidth division / allocation to further support traffic classification amongst non-TCP traffic such as UDP and ICMP. For TCP traffic, the method for BTD determines whether a TCP connection has been established and performs at least one of rate limiting, waiting time reduction for half-open connections, and incrementing backlog queue size when the TCP connection has not been established. If the TCP connection has been established successfully, the method for BTD further includes proactive tests for traffic differentiation which identify normal traffic, which is admitted, and attack traffic, which is dropped.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
Communications scheduler
ActiveUS20080031149A1Sacrificing reliabilityReducing and eliminating needError preventionTransmission systemsCommunication interfaceData stream
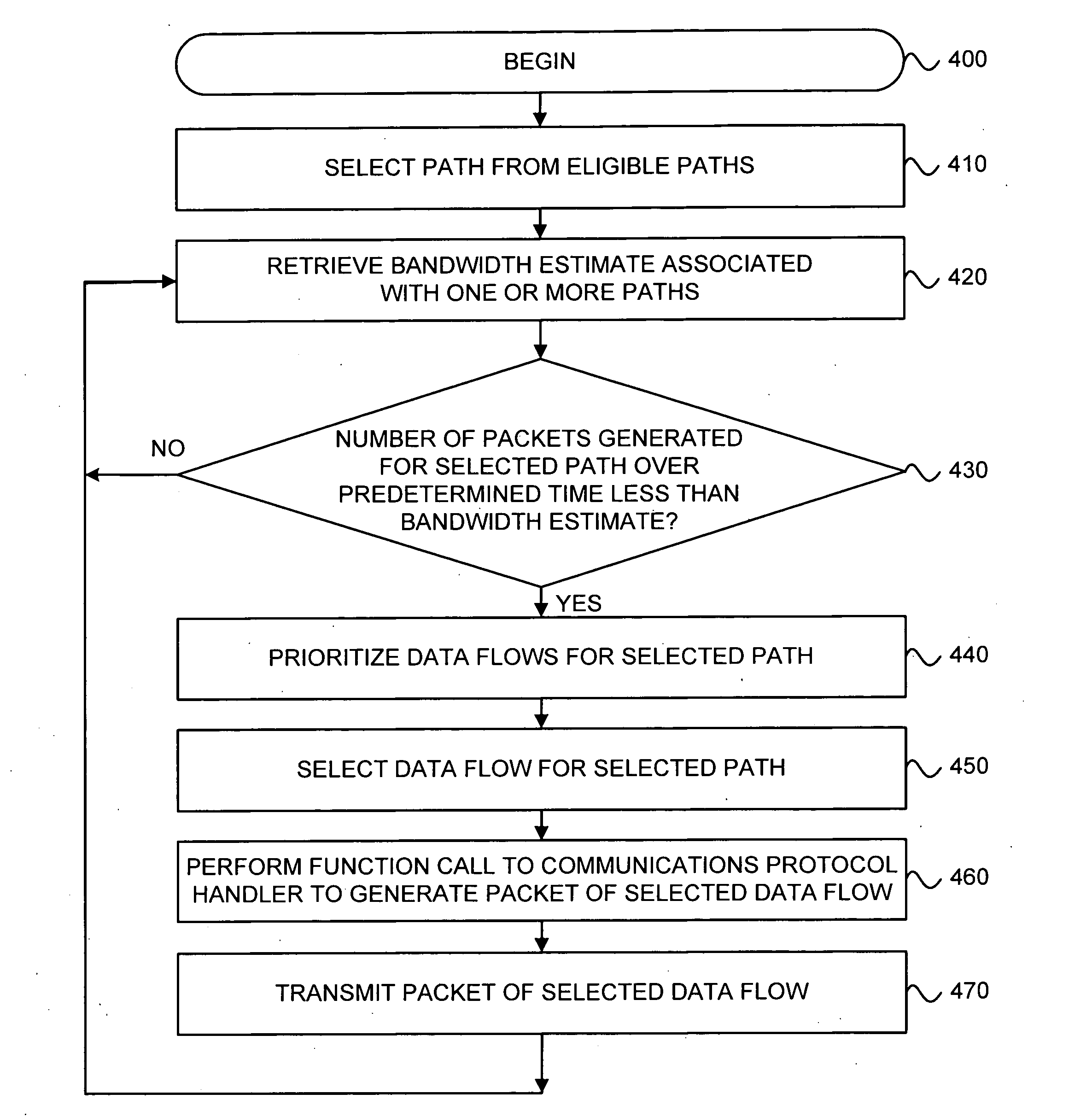
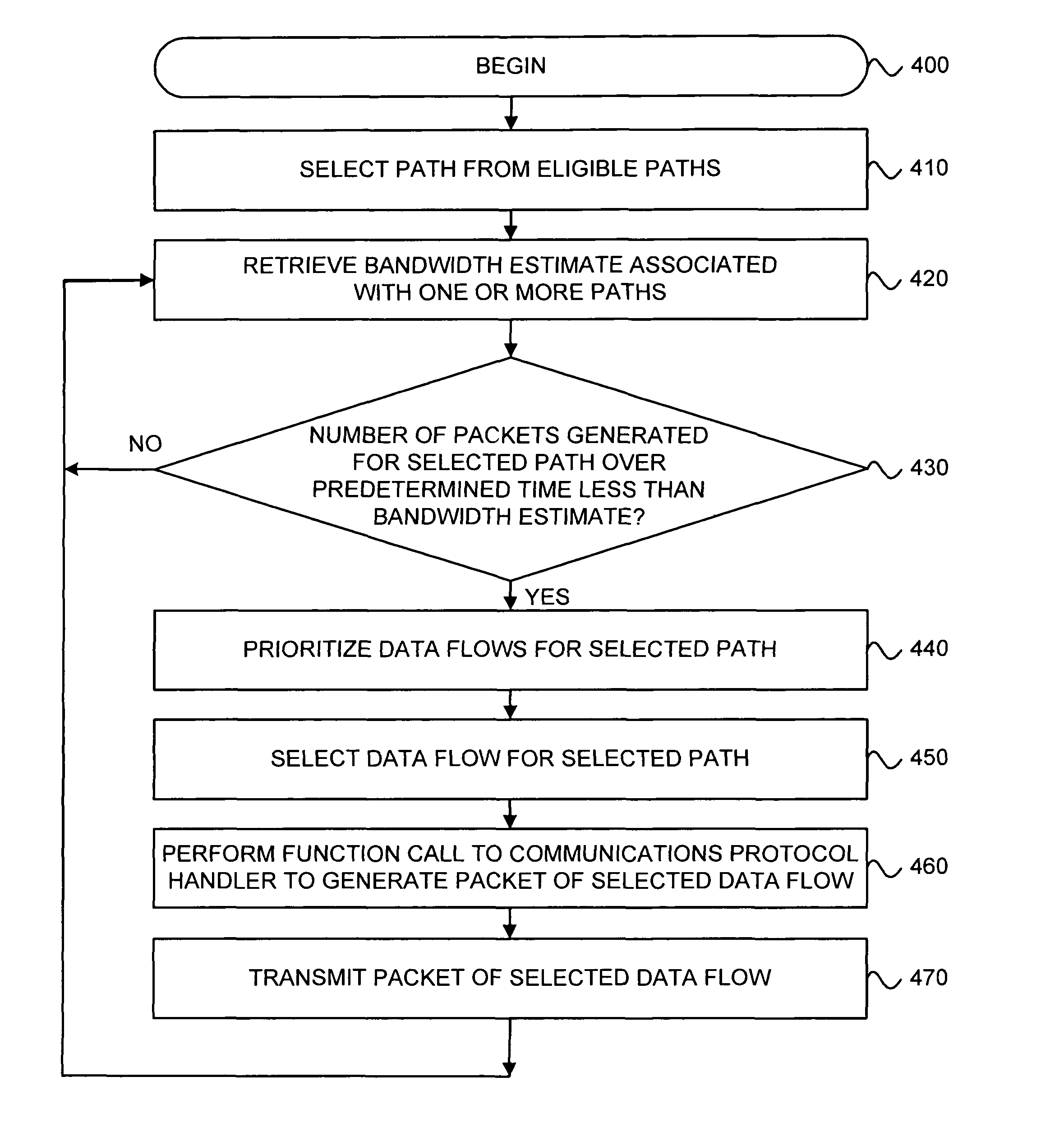
A System for providing communications over a communications network includes a communications interface and processor. The communications interface communicates over the communications network. The processor directs a communications scheduler to determine at least one metric for a path within the communications network. The processor also selects a data flow for the path and determines whether to transmit a packet in the selected data flow based on the at least one metric. The processor then directs a communications protocol handler to generate the packet for the selected data flow.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Obstacle detecting system and method
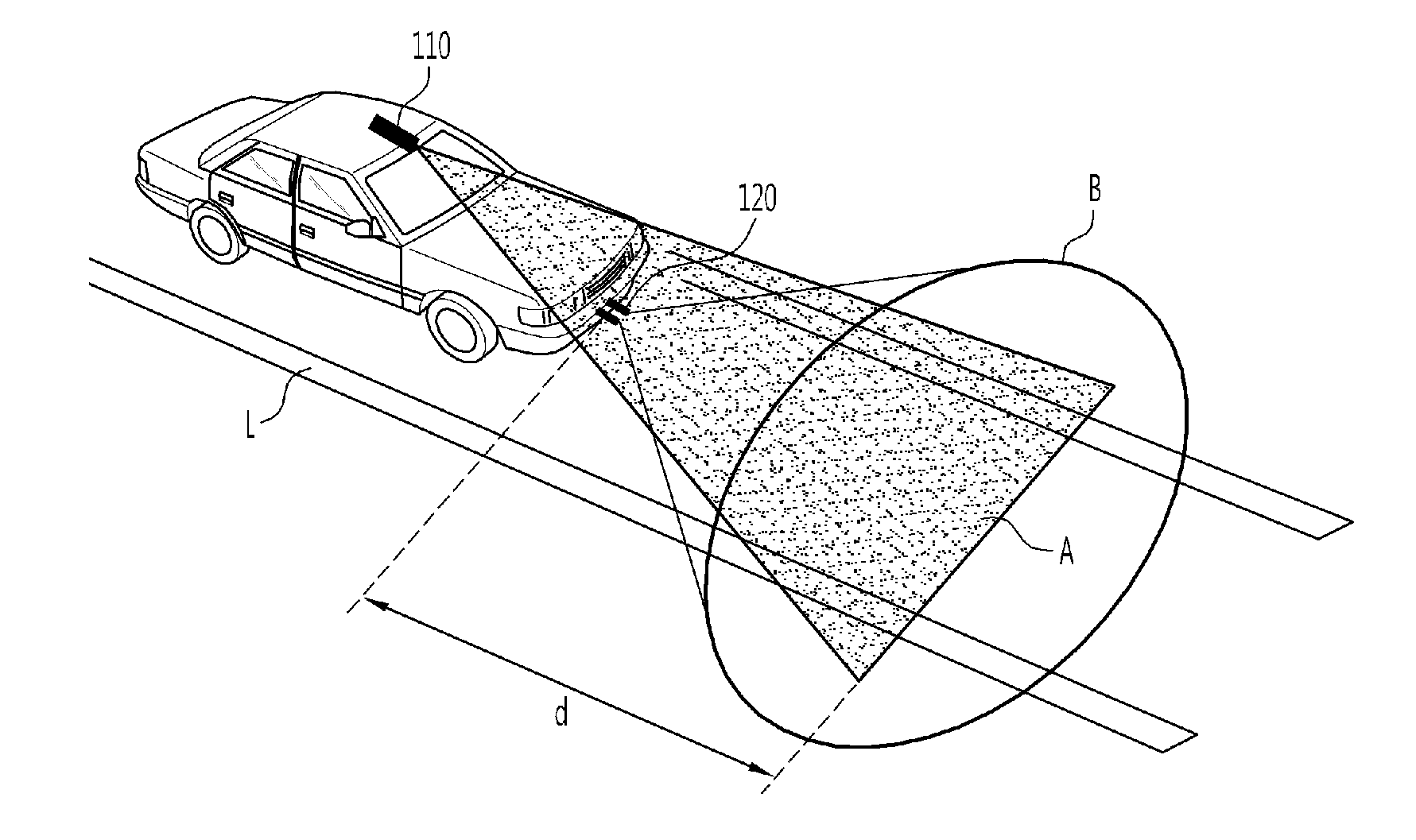
InactiveUS20120081542A1Quick fixAvoid detectionColor television detailsScene recognitionRoad surfaceComputer science
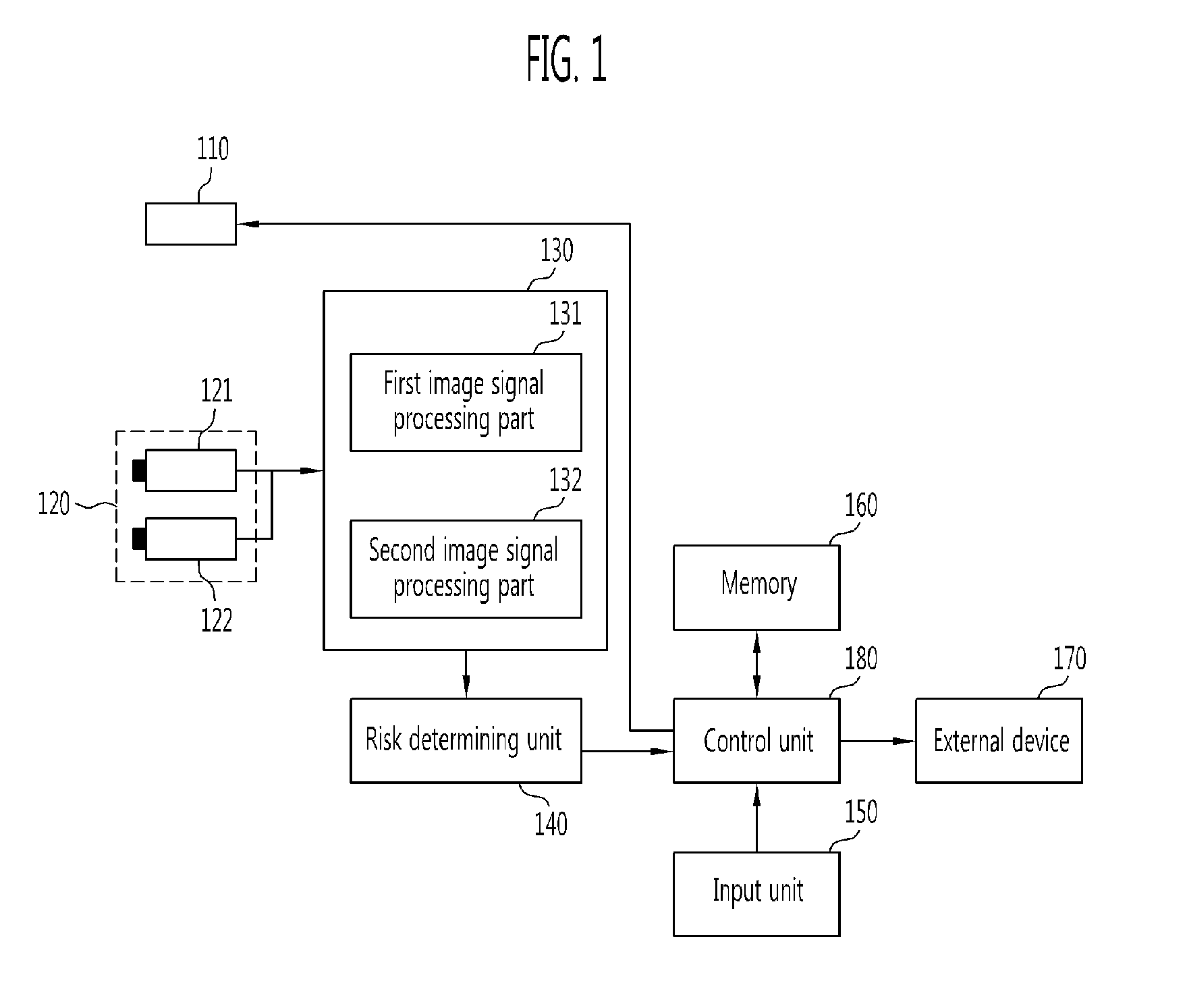
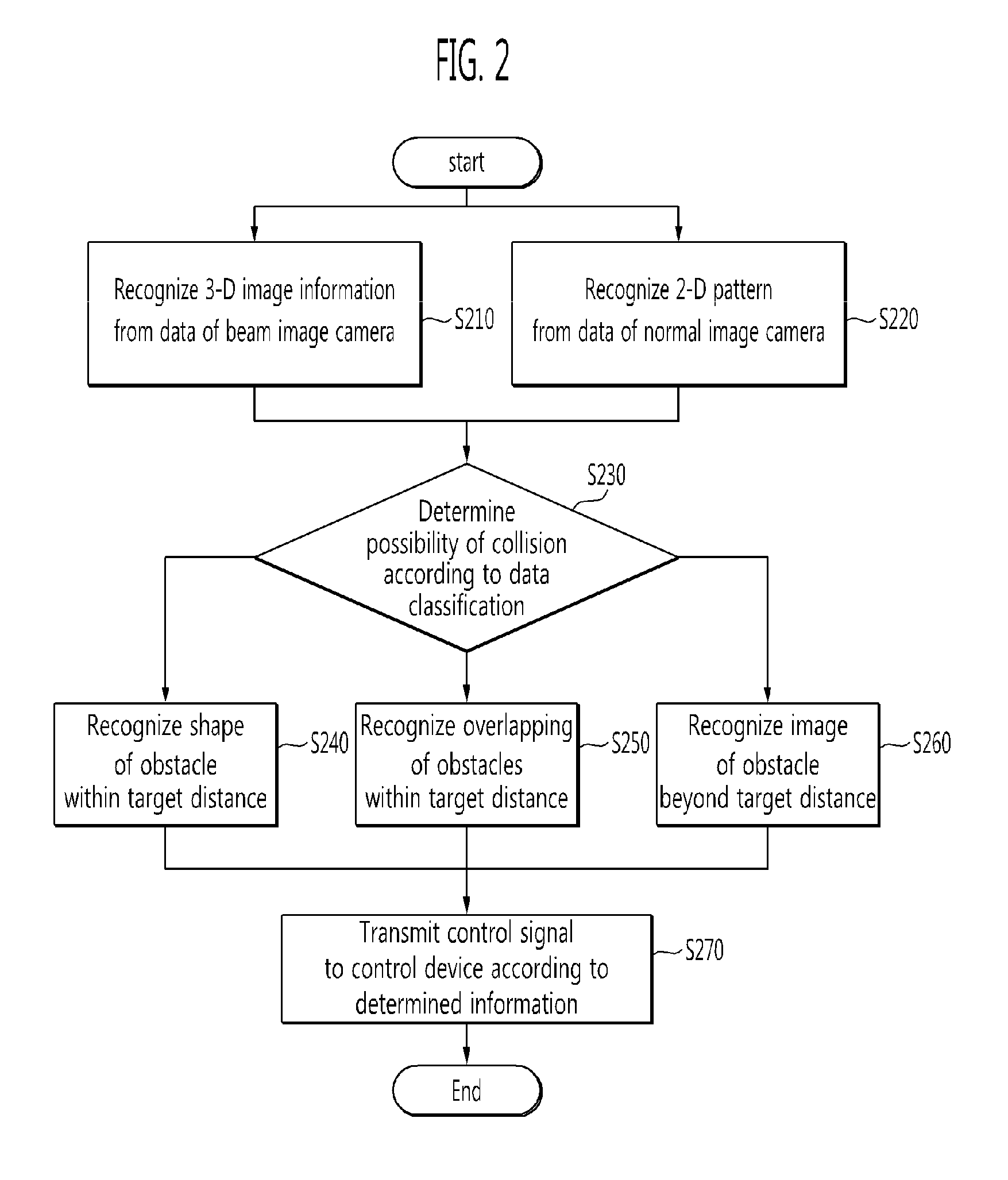
The obstacle detecting system includes a first image acquiring unit which acquires first image information by selectively receiving a laser beam emitted from at least one laser source toward a road surface at a target distance; a second image acquiring unit which acquires an image of actual surroundings as second image information; an image recognizing unit which recognizes an image of an obstacle by performing 3-D image recognition signal processing on line information of the laser beam using the first image information, and recognizes a pattern of the obstacle by performing pattern recognition signal processing on the second image information; and a risk determining unit which determines a possibility of collision due to presence of the obstacle within the target distance by classifying the recognized obstacles according to whether or not the image-recognized obstacle is matched with the pattern-recognized obstacle.
Owner:ELECTRONICS & TELECOMM RES INST +1
Load balancing between users of a wireless base station
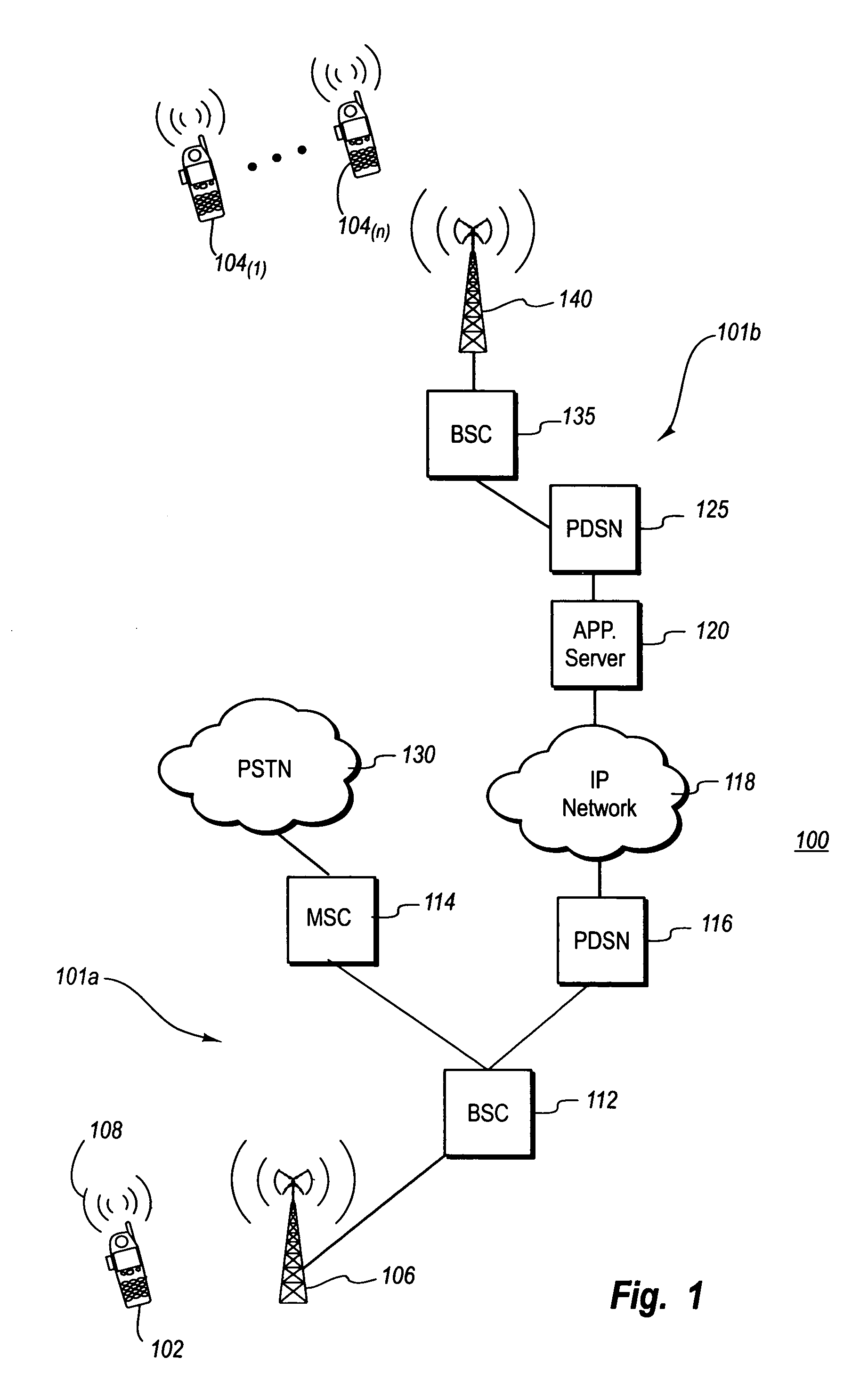
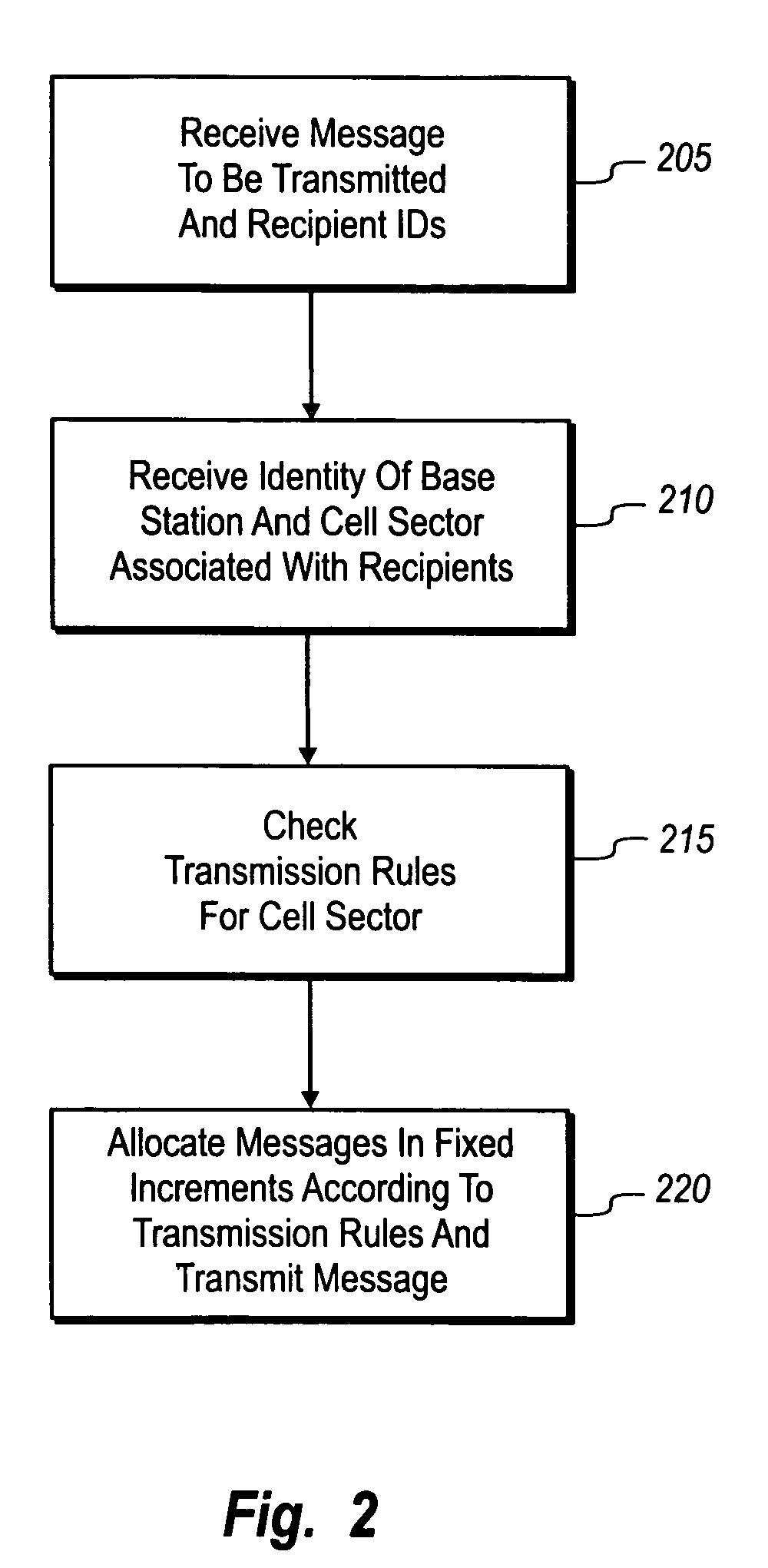
ActiveUS7272400B1Prevent overloadAvoid trafficNetwork traffic/resource managementSubstation equipmentCurrent loadLoad Shedding
The load in a cell or a cell sector is balanced in the process of sending store and forward messages to multiple recipients located in a single cell or cell sector. When one or more messages are sent over a wireless communication network to one or more recipient devices, information about the identity of the base station and cell sector serving the recipient device(s) is obtained. A current load for the cell or cell sector can also be obtained and used to control the number of simultaneous message transmissions to the cell sector to avoid overloading the sector. Message transmission may be allocated according to predetermined transmission rules for a cell sector or by dynamically allocating message transmission according to fluctuating traffic loads in the cell sector. Accordingly, a first subset of messages may be transmitted to a single recipient, or a single message may be transmitted to a subset of intended recipient devices. Thereafter, message transmission takes place incrementally without overloading the cell or cell sector.
Owner:SMITH MICRO SOFTWARE INC
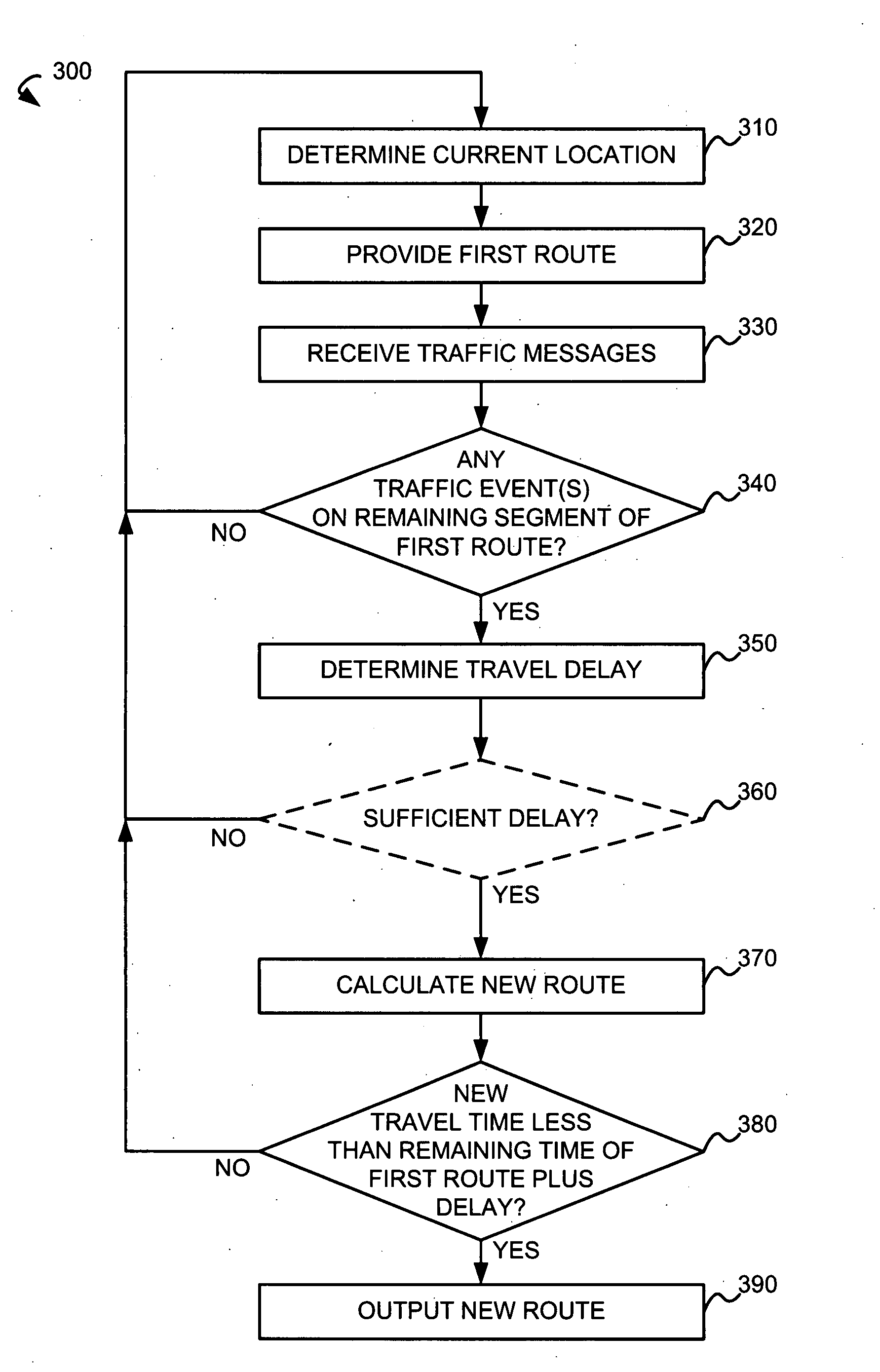
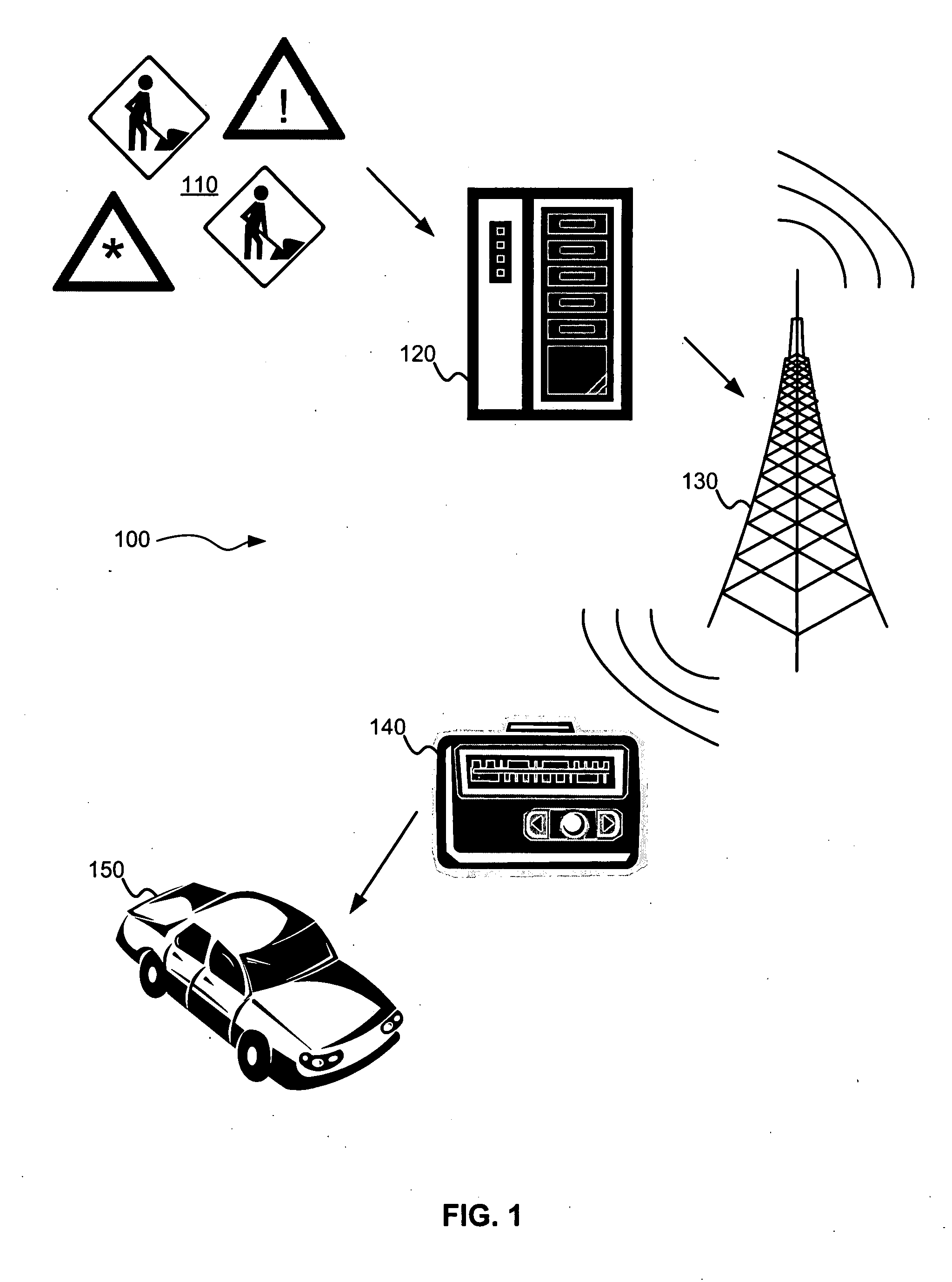
Route calculation based on traffic events
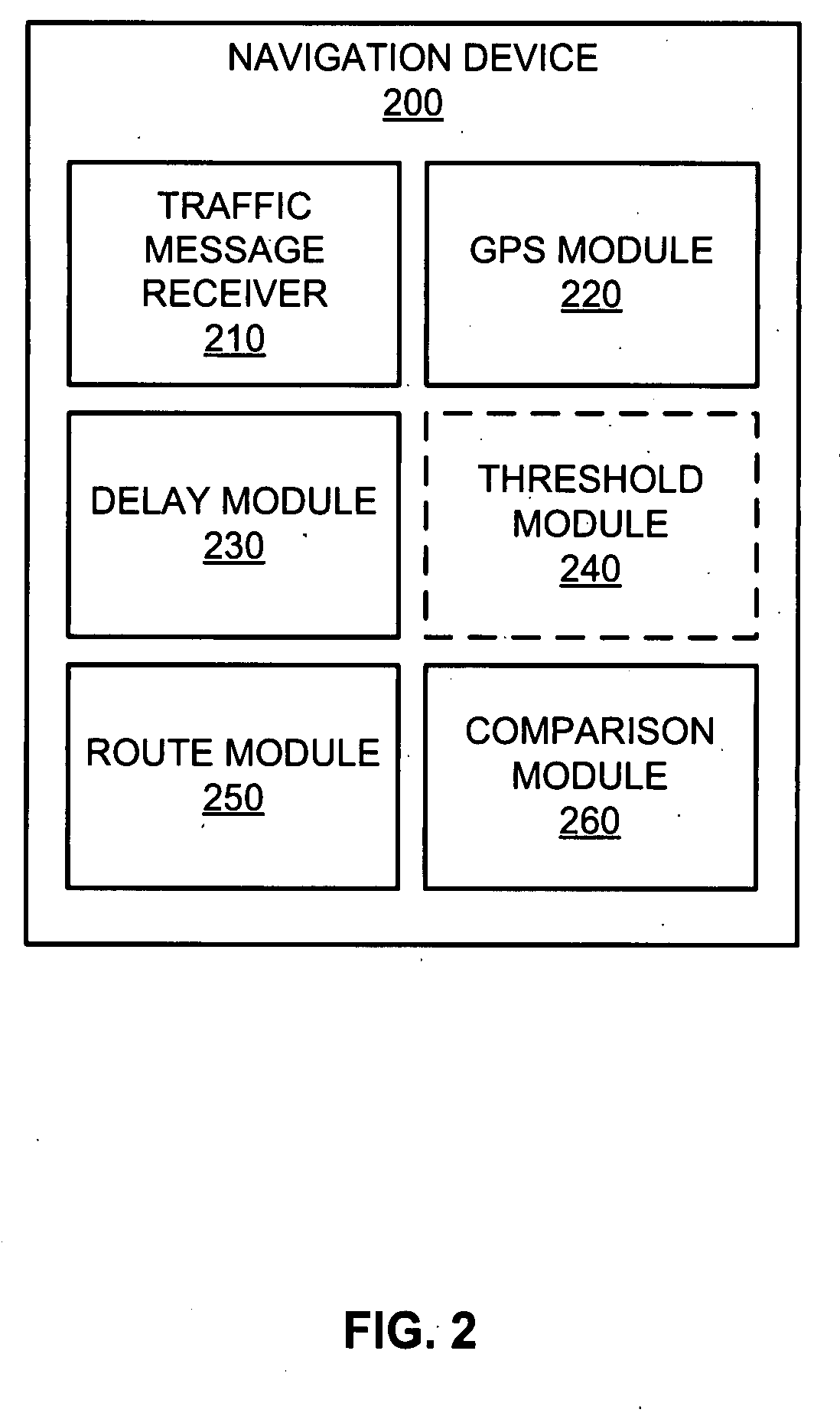
InactiveUS20090105940A1Avoid trafficInstruments for road network navigationRoad vehicles traffic controlMarine navigationReal-time computing
Based on an origin location and a destination location, a navigation device is configured to provide an initial route. Traffic messages describing traffic events are received by the navigation device. Based on a location code in each of the traffic messages, the navigation device determines a traffic event delay if the location code corresponds to any remaining segment(s) of the initial route. If at least one of the traffic messages corresponds to any remaining segment(s) of the initial route, a travel delay is calculated based on one or more traffic event delays. The navigation device calculates a new route from the current location to the destination location, and, if a new travel time of the new route is less than a remaining travel time of the initial route from the current location to the destination location plus the travel delay, the navigation device outputs the new route.
Owner:INTRINSYC SOFTWARE INT
Communications scheduler
ActiveUS8885632B2Sacrificing reliabilityReducing and eliminating needError preventionTransmission systemsCommunication interfaceData stream
A System for providing communications over a communications network includes a communications interface and processor. The communications interface communicates over the communications network. The processor directs a communications scheduler to determine at least one metric for a path within the communications network. The processor also selects a data flow for the path and determines whether to transmit a packet in the selected data flow based on the at least one metric. The processor then directs a communications protocol handler to generate the packet for the selected data flow.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
ADDRESS AUTOCONFIGURATION METHOD AND SYSTEM FOR IPv6-BASED LOW-POWER WIRELESS PERSONAL AREA NETWORK
InactiveUS20090161581A1Avoid trafficReduce network trafficPower managementAssess restrictionAuto-configurationIp address
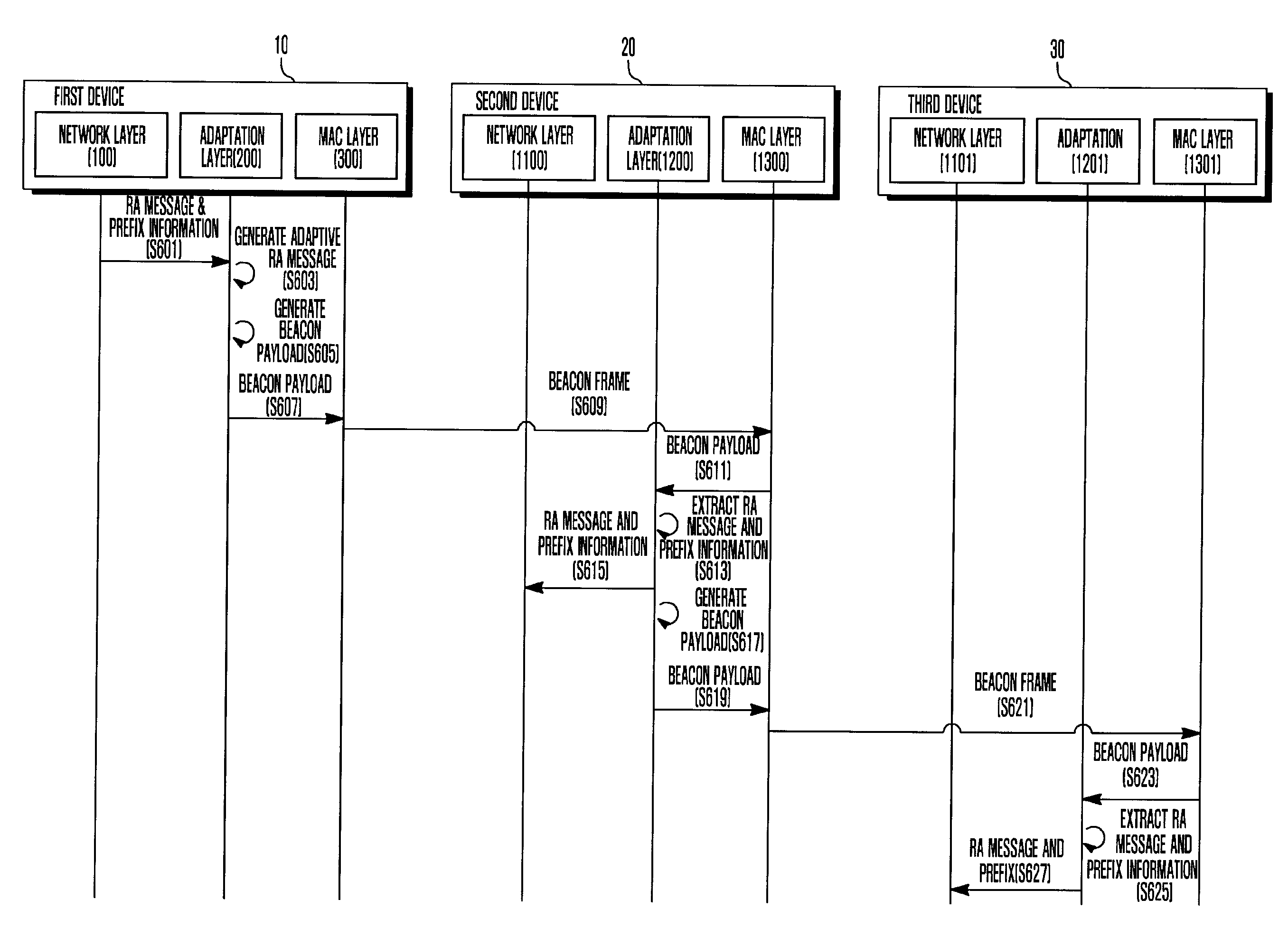
An IP address autoconfiguration method and system of an IPv6-based Low Power WPAN for reducing network traffics is applicable for an Internet Protocol (IP) based network including a plurality of devices. The address autoconfiguration method generates and broadcasts, at a first device, a beacon frame containing an adaptive router advertisement (RA) message having prefix information, and configures, at a second device received the beacon frame, an IP address using the prefix information extracted from the adaptive RA message carried by the beacon frame and a physical address of the second device. The system includes a first type device which broadcasts a beacon frame carrying a prefix; at least one second type device which relays the prefix using a beacon frame; and at least one terminal device which configures an IP address using the prefix in the beacon frame and a physical address of the terminal device.
Owner:SAMSUNG ELECTRONICS CO LTD
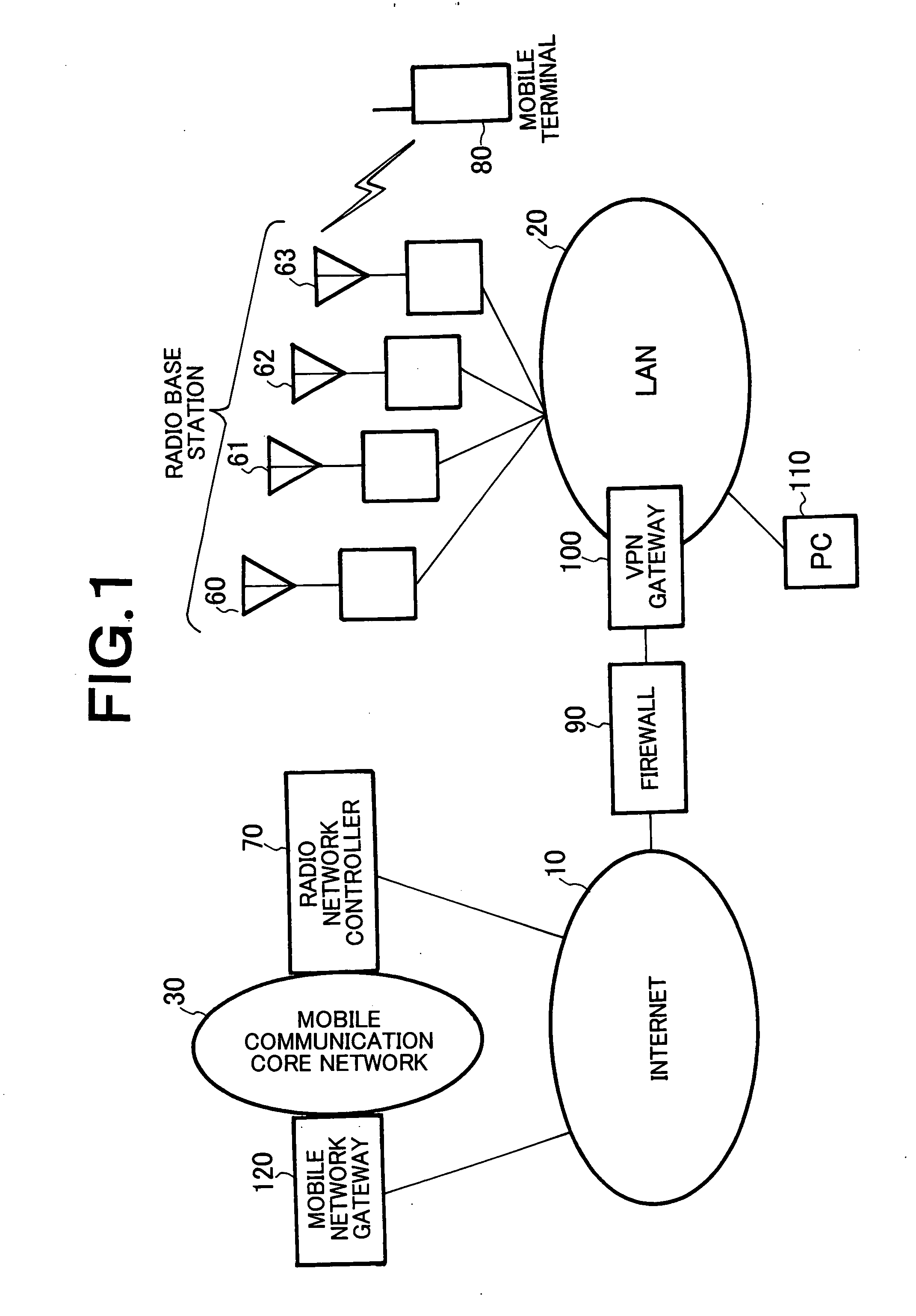
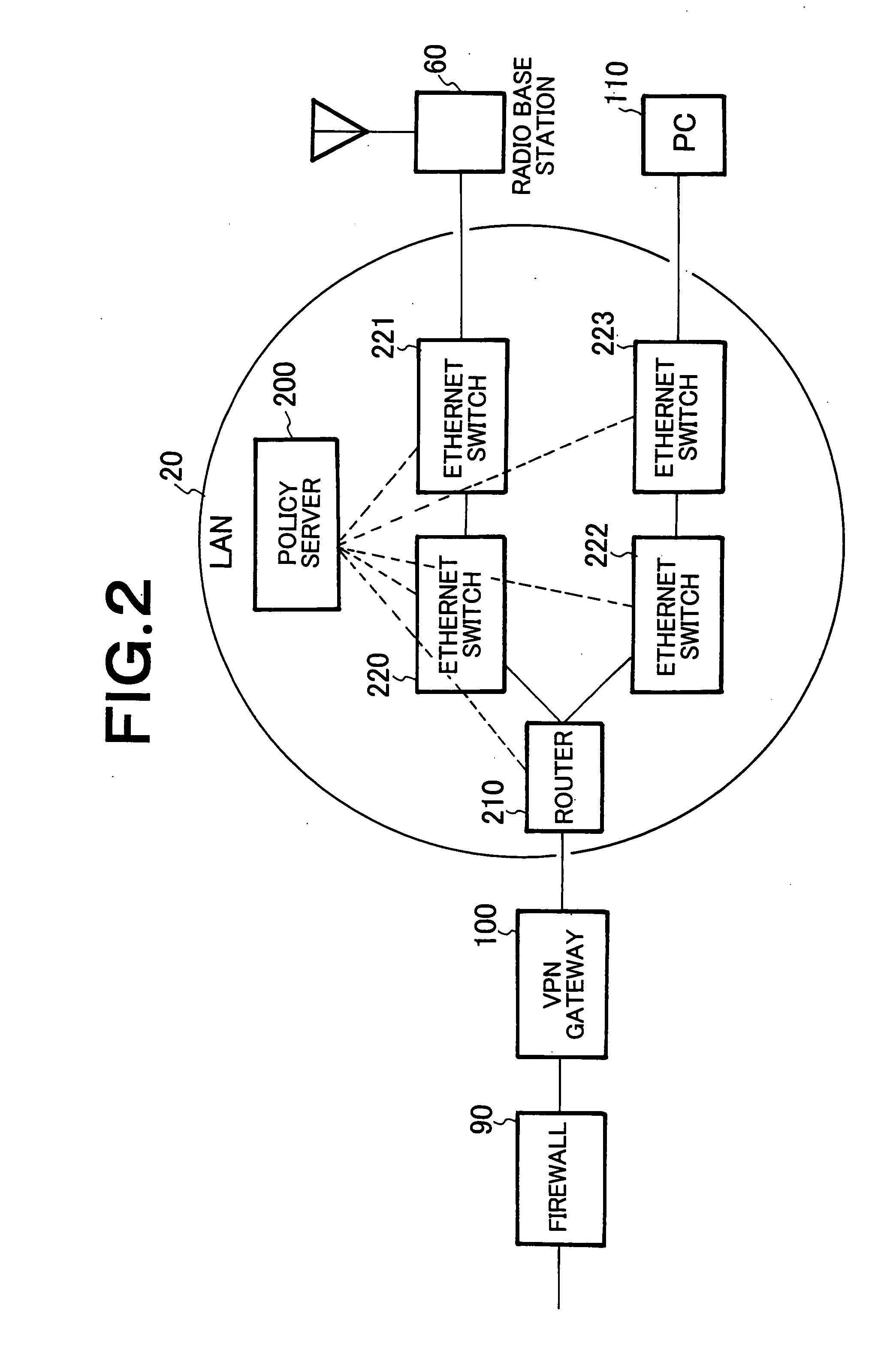
Mobile communication system using private network, relay node, and radio network controller
InactiveUS20070105549A1Avoid trafficEasy to operateNetwork traffic/resource managementNetwork topologiesRadio networksPrivate network
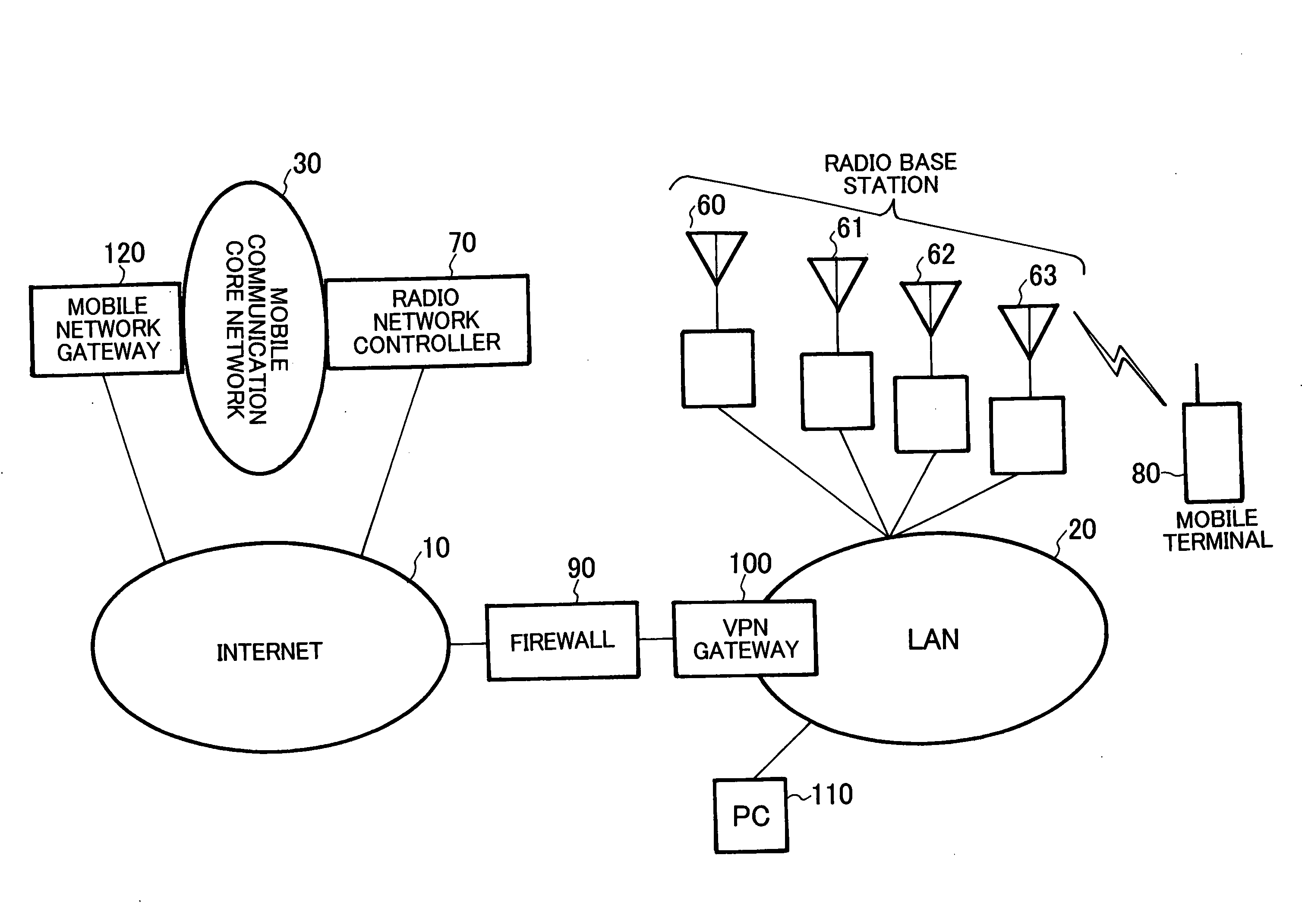
Upon receiving a mobile communication control signaling at the time when a mobile terminal 80 makes or receives a call, VPN gateway 100, which serves as a relay node, performs reception determination in cooperation with policy server 200 serving as a bandwidth control mechanism within LAN 20 which is a private network. When permitting the reception, the VPN gateway 100 provides a communication line to the mobile terminal 80 or a pre-shared key is dynamically generated between a radio base station and radio network controller 70, and the pre-shared key is notified to the VPN gateway 100 by the radio network controller 70.
Owner:NEC CORP
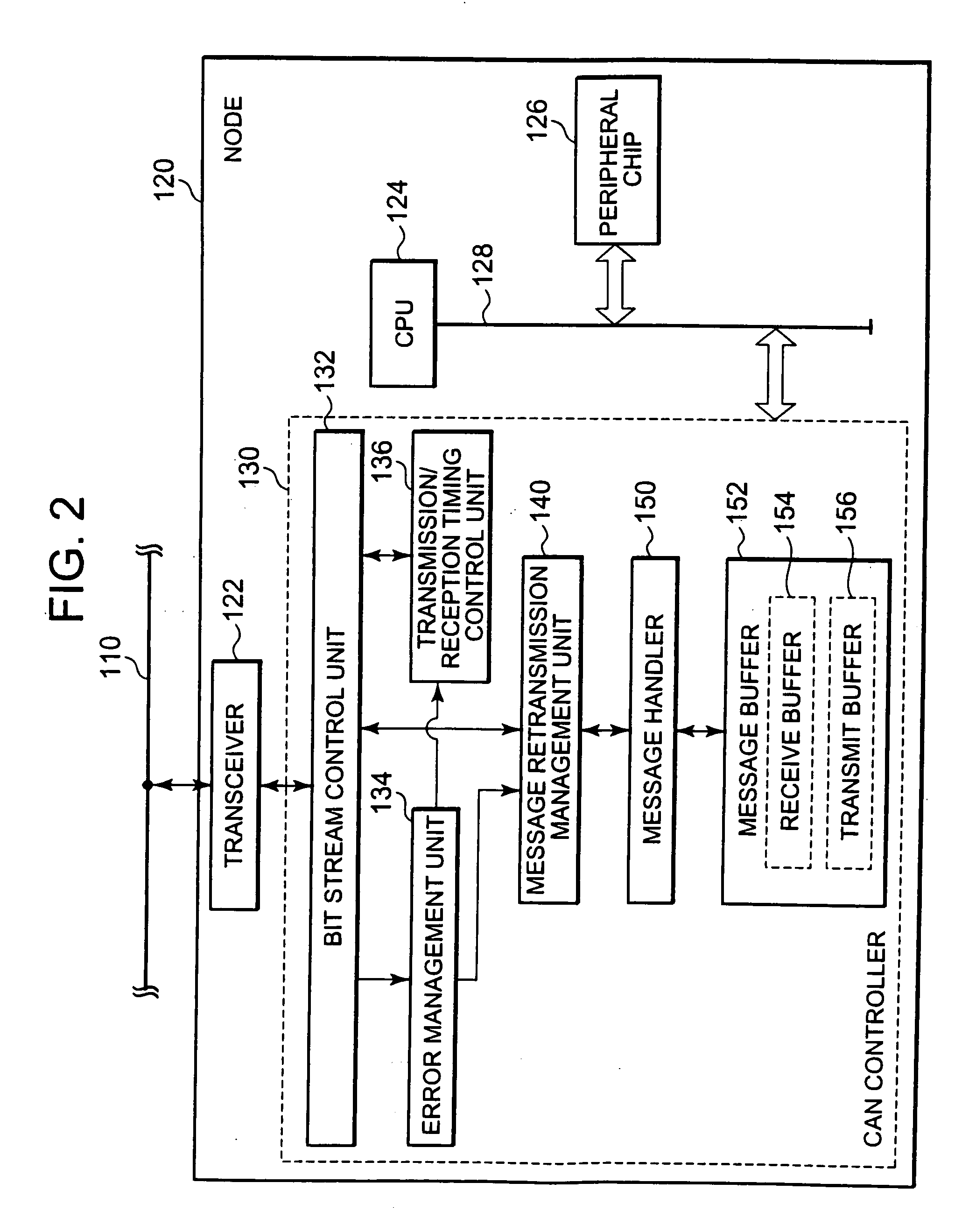
CAN node, and communication method of communication system including CAN node
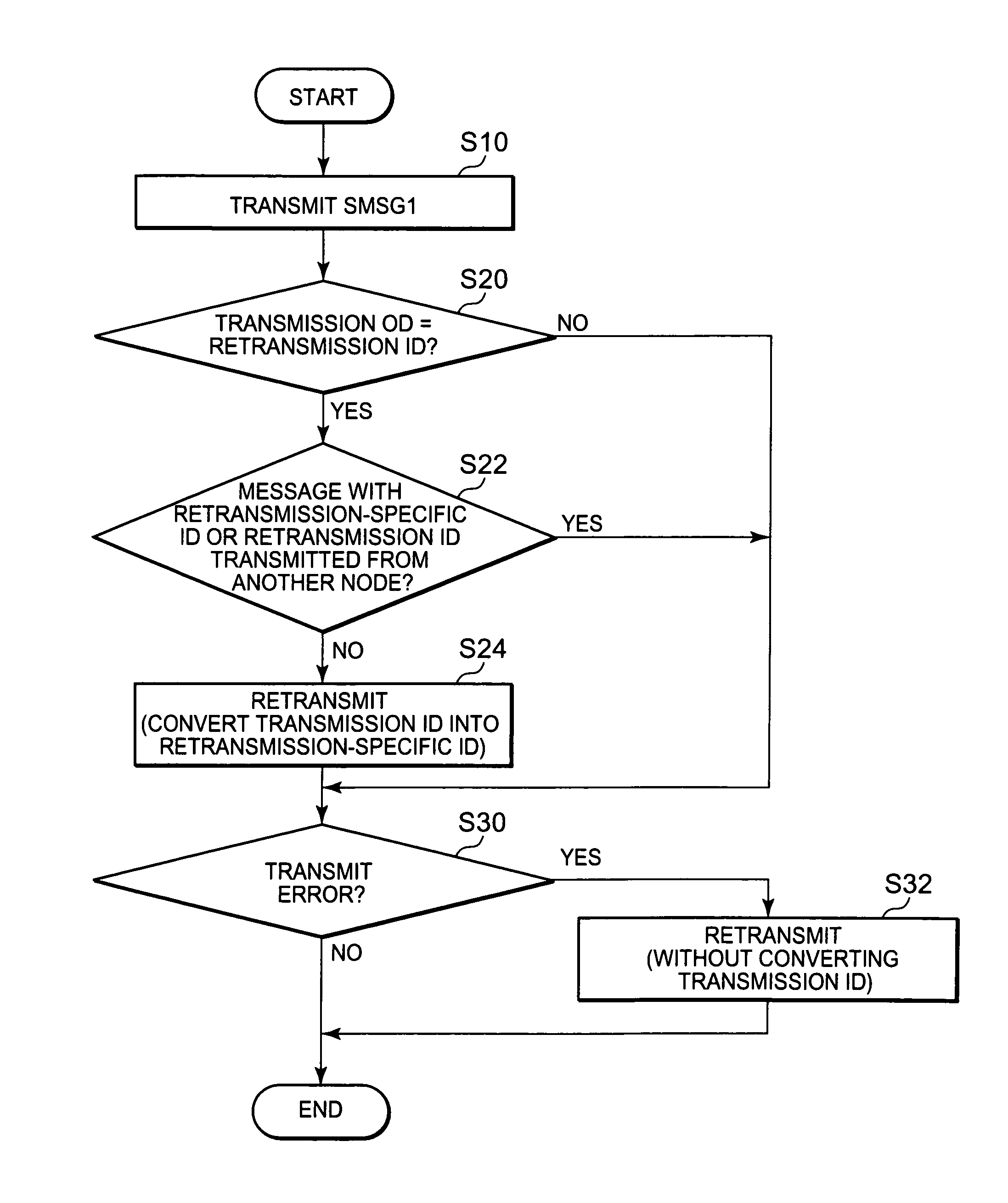
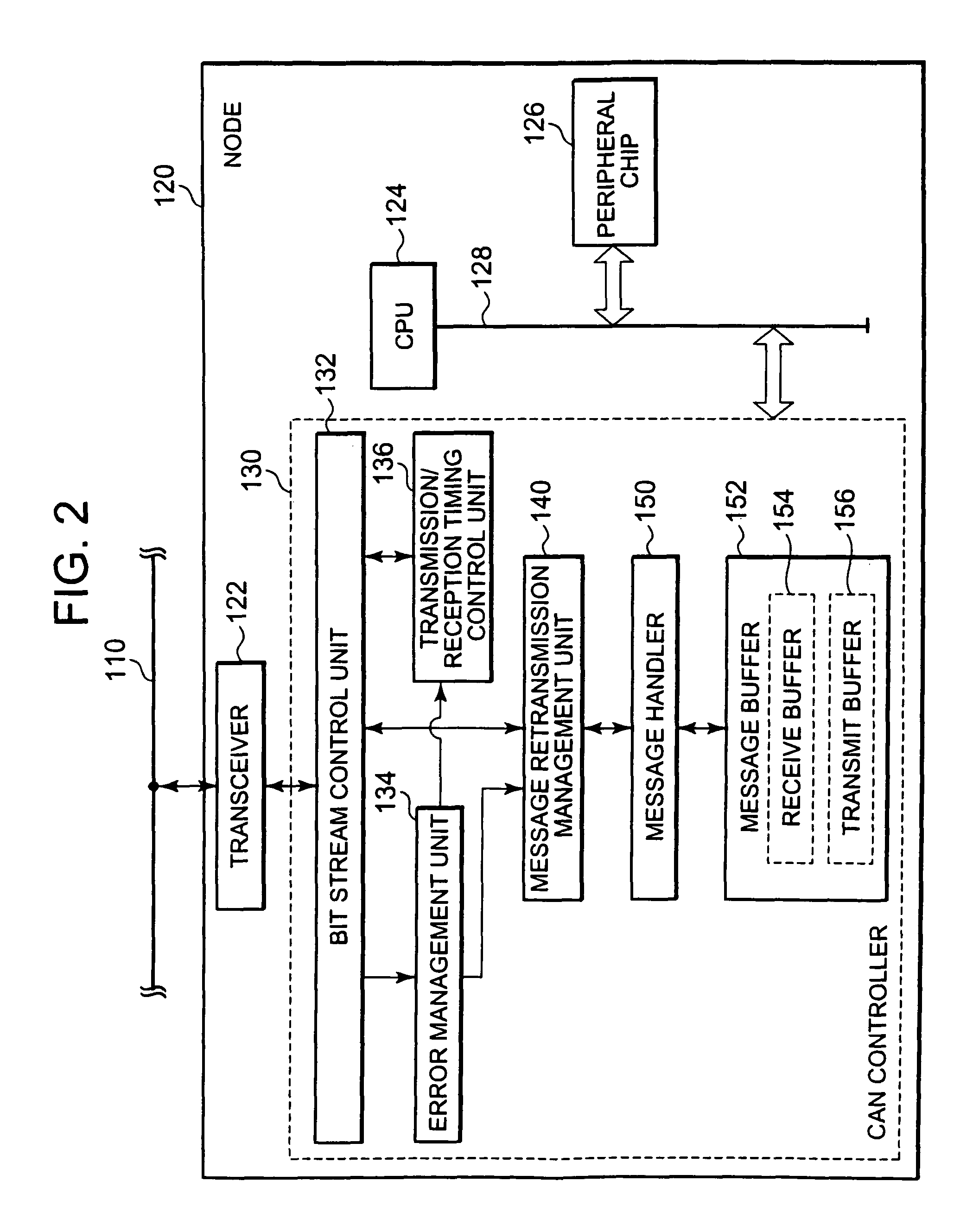
ActiveUS20100150176A1Avoid excessive traffic increaseReduce decreaseError preventionTime-division multiplexCommunications systemArea network
A Controller Area Network (CAN) node includes a conversion and retransmission unit which retransmits a transmit message if the transmit message carries a retransmission ID out of ID codes, by changing the ID code of the transmit message to a retransmission-specific ID corresponding to the retransmission ID, where the ID codes indicate priorities of transmit messages, the retransmission ID indicates that the transmit message is to be retransmitted, and the retransmission-specific ID is an ID code specifically for use in retransmission, and a conversion and reception unit which checks whether an original message corresponding to a retransmit message has been received successfully, the retransmit message being a receive message carrying the retransmission-specific ID, and discards the retransmit message if the original message corresponding to the retransmit message has been received successfully, but converts the ID code of the retransmit message into a retransmission ID corresponding to the retransmission-specific ID if the original message corresponding to the retransmit message has not been received successfully.
Owner:RENESAS ELECTRONICS CORP
Technique for providing interconnection between communication networks
InactiveUS20090274155A1Avoids drawbackAvoid trafficData switching by path configurationNetwork elementDistributed computing
Technique for interconnecting a first communication network and a second communication network, for example layer 2 Ethernet networks, which uses a fully or partially redundant dual homing configuration. The configuration includes: at least three network elements where at least two of them are peer elements belonging to the second network, and at least two traffic lines respectively associated with the peer elements and connecting the first and the second networks via the three network elements. The technique comprises establishing a bi-directional signaling between the peer elements and, based on the signaling information, deciding which traffic line should forward the traffic.
Owner:ECE TELECOM LTD
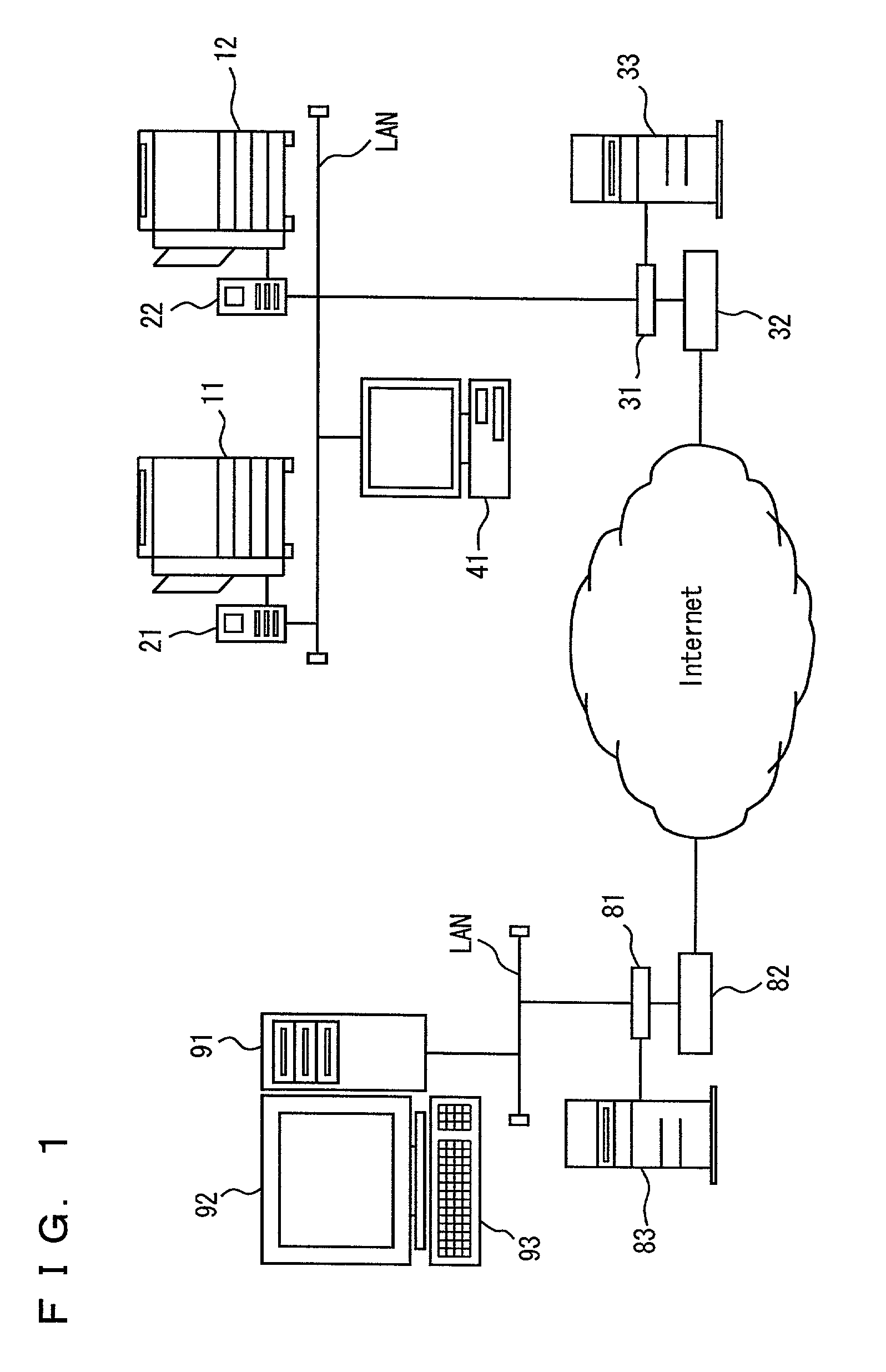
Communication system and printer therefor
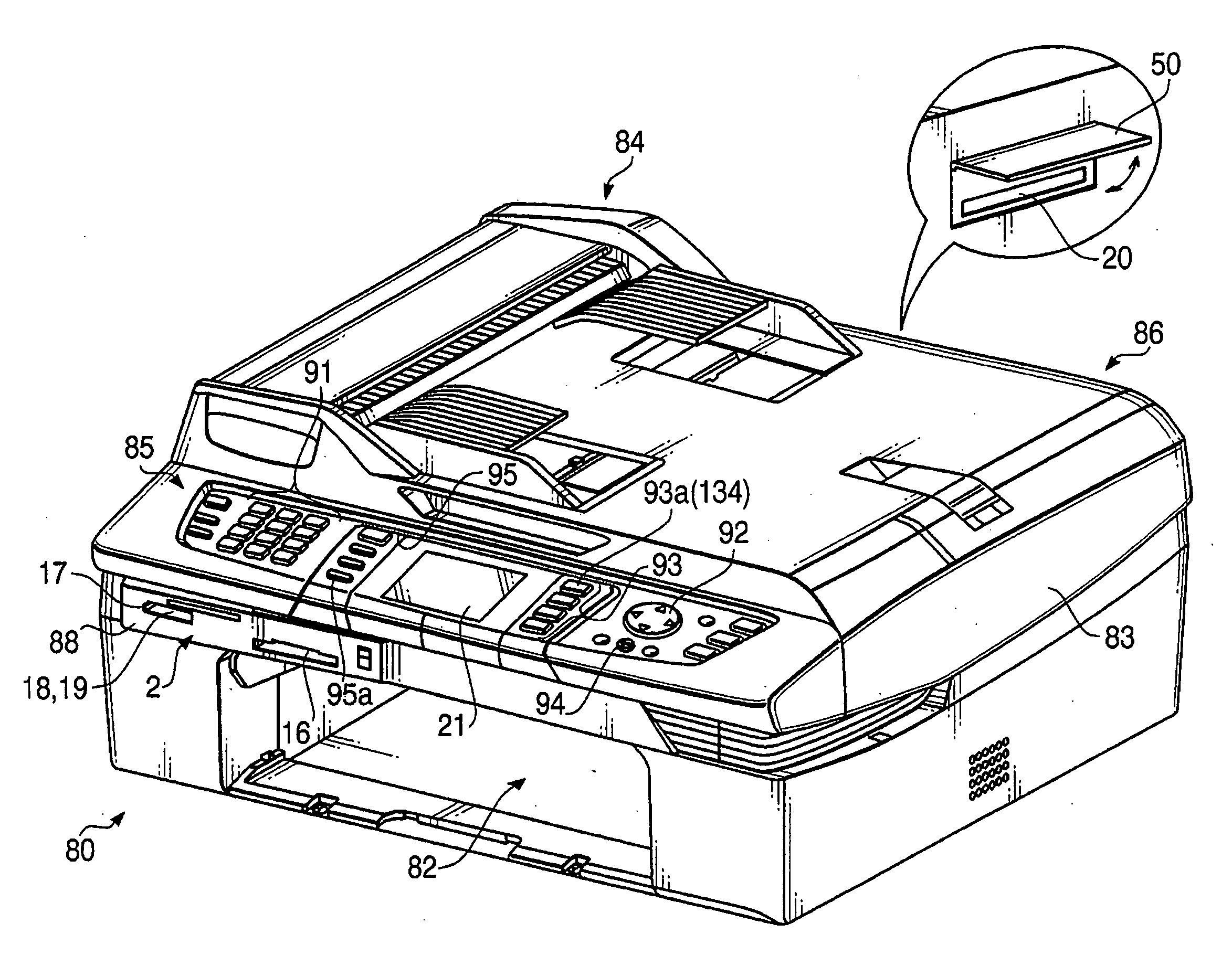
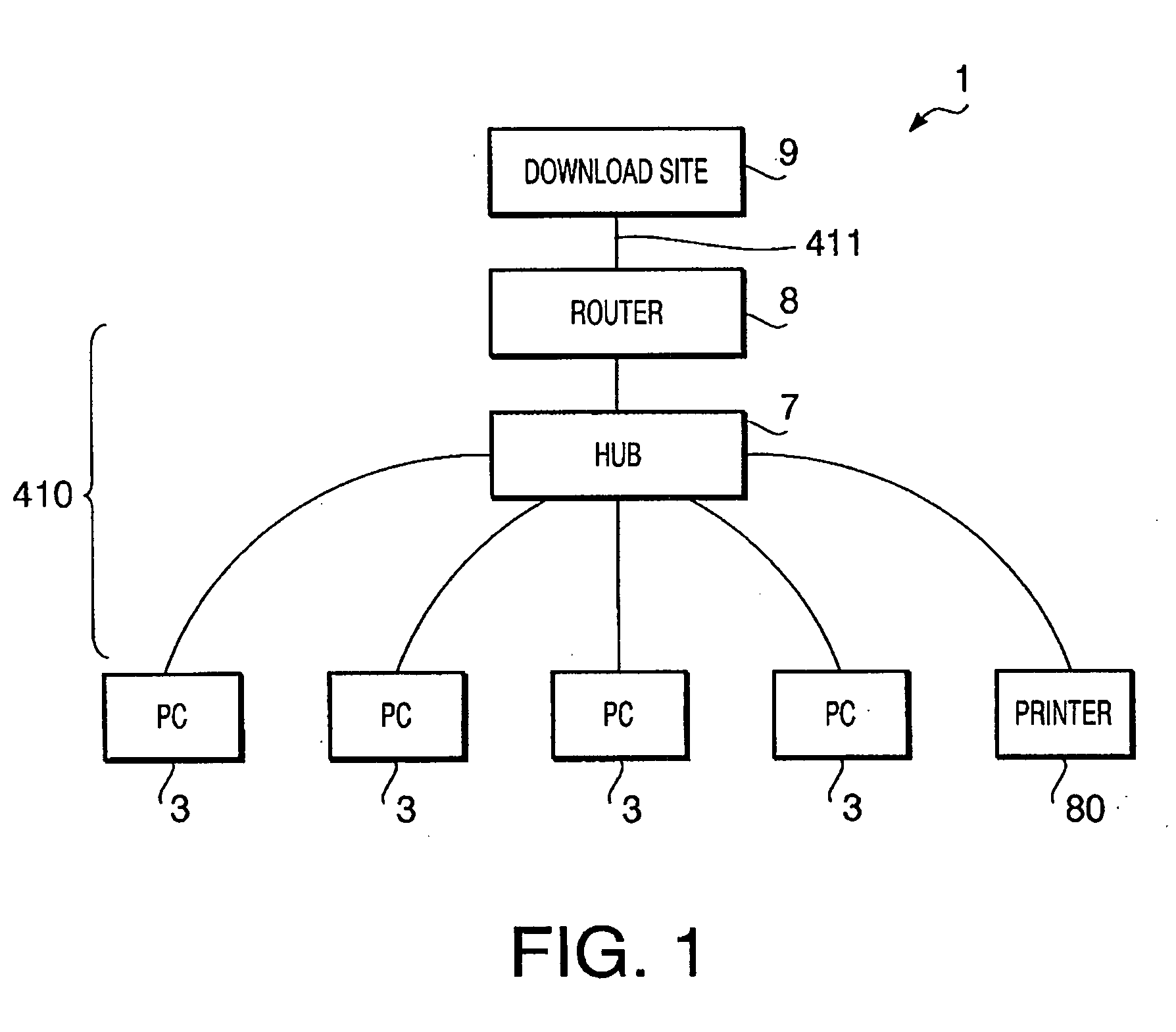
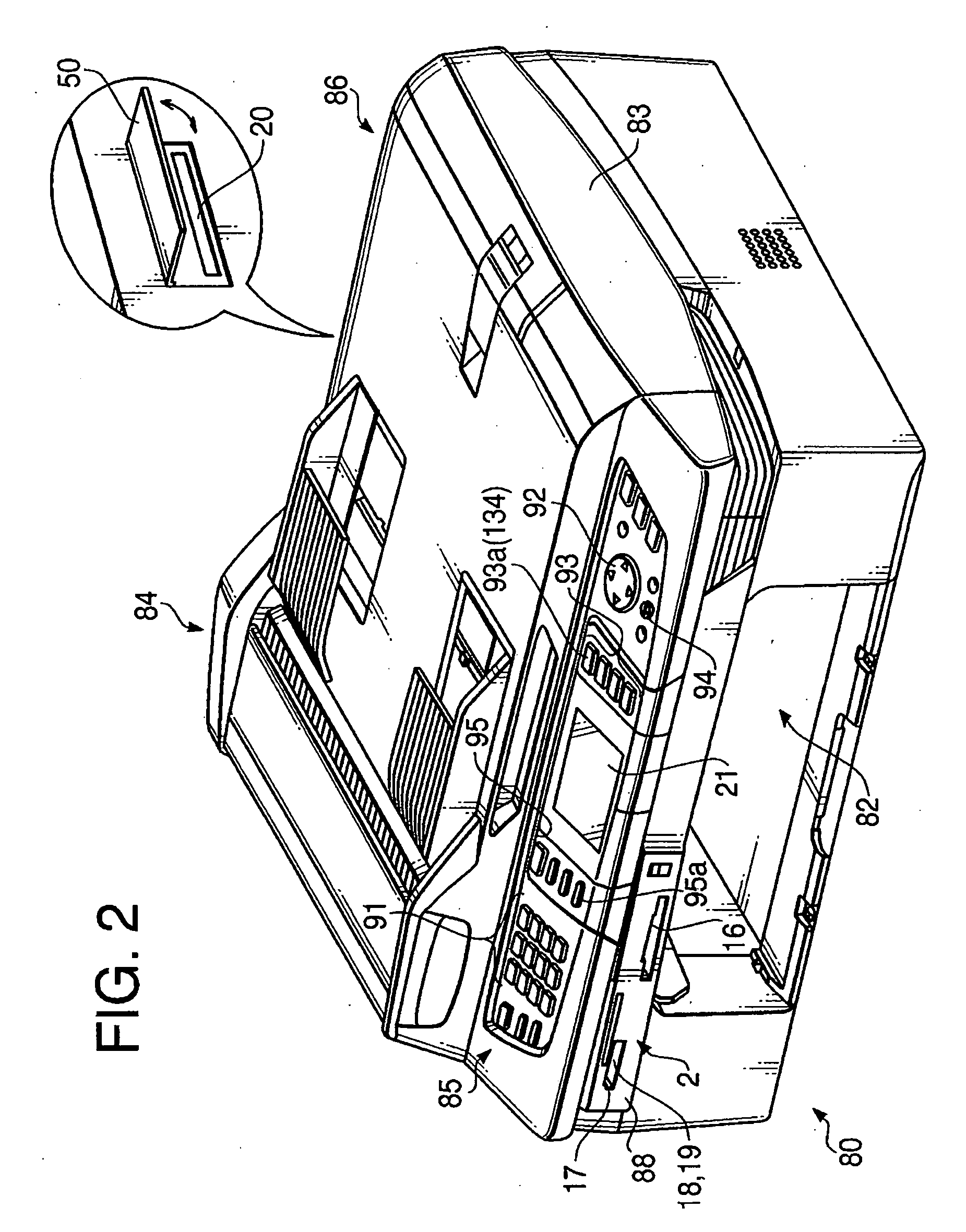
InactiveUS20080055640A1Avoid trafficEasy accessVisual presentationProgram controlCommunications systemNetwork connection
A communication system includes a first network, a printer connected with the first network, a host device, connected with the first network, which are configured to use the printer as a network printer with a printer driver being installed therein, a second network connected with the first network via a router, and an external server device, connected with the second network, which is configured as a providing source of a first printer driver. The printer includes a downloading unit that downloads the first printer driver from the external server device via the first and second networks, a storing unit that stores the downloaded first printer driver, and a sending unit that sends the stored first printer driver to the host device via the first network. The host device includes a receiving unit that receives the first printer driver from the sending unit.
Owner:BROTHER KOGYO KK
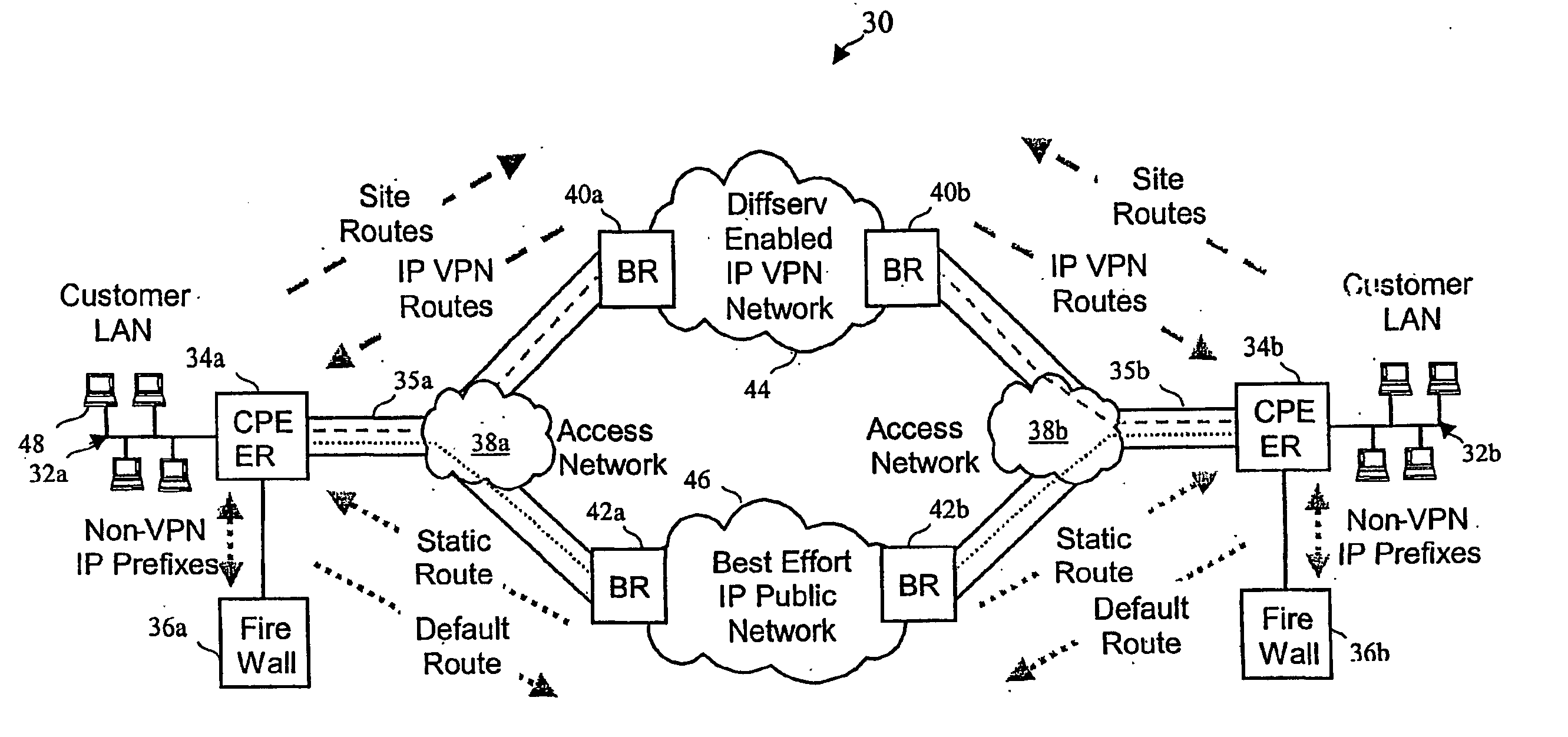
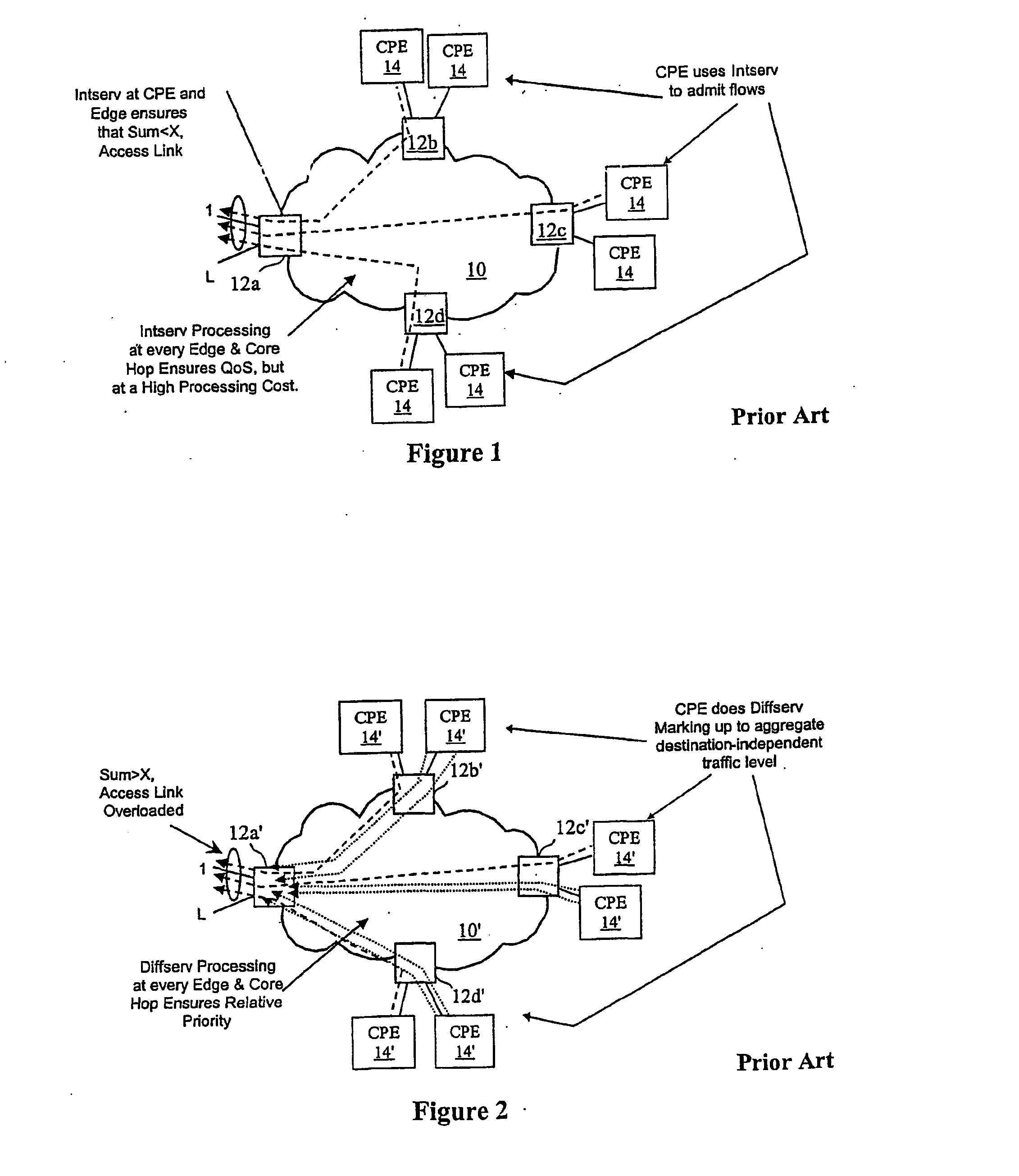
System, method and apparatus that isolate virtual private network (VPN) and best effort traffic to resist denial of service attacks
InactiveUS20050066053A1Improve scalabilityAvoid trafficMetering/charging/biilling arrangementsMultiple digital computer combinationsDenial-of-service attackNetwork element
A network architecture in accordance with the present invention includes a communication network that supports one or more network-based Virtual Private Networks (VPNs). The communication network includes a plurality of boundary routers that are connected by access links to CPE edge routers belonging to the one or more VPNs. To prevent traffic from outside a customer's VPN (e.g., traffic from other VPNs or the Internet at large) from degrading the QoS provided to traffic from within the customer's VPN, the present invention gives precedence to intra-VPN traffic over extra-VPN traffic on each customer's access link through access link prioritization or access link capacity allocation, such that extra-VPN traffic cannot interfere with inter-VPN traffic. Granting precedence to intra-VPN traffic over extra-VPN traffic in this manner entails special configuration of network elements and protocols, including partitioning between intra-VPN and extra-VPN traffic on the physical access link using layer 2 multiplexing and the configuration of routing protocols to achieve logical traffic separation between intra-VPN traffic and extra-VPN traffic at the VPN boundary routers and CPE edge routers. By configuring the access networks, the VPN boundary routers and CPE edge routers, and the routing protocols of the edge and boundary routers in this manner, the high-level service of DoS attack prevention is achieved.
Owner:VERIZON PATENT & LICENSING INC
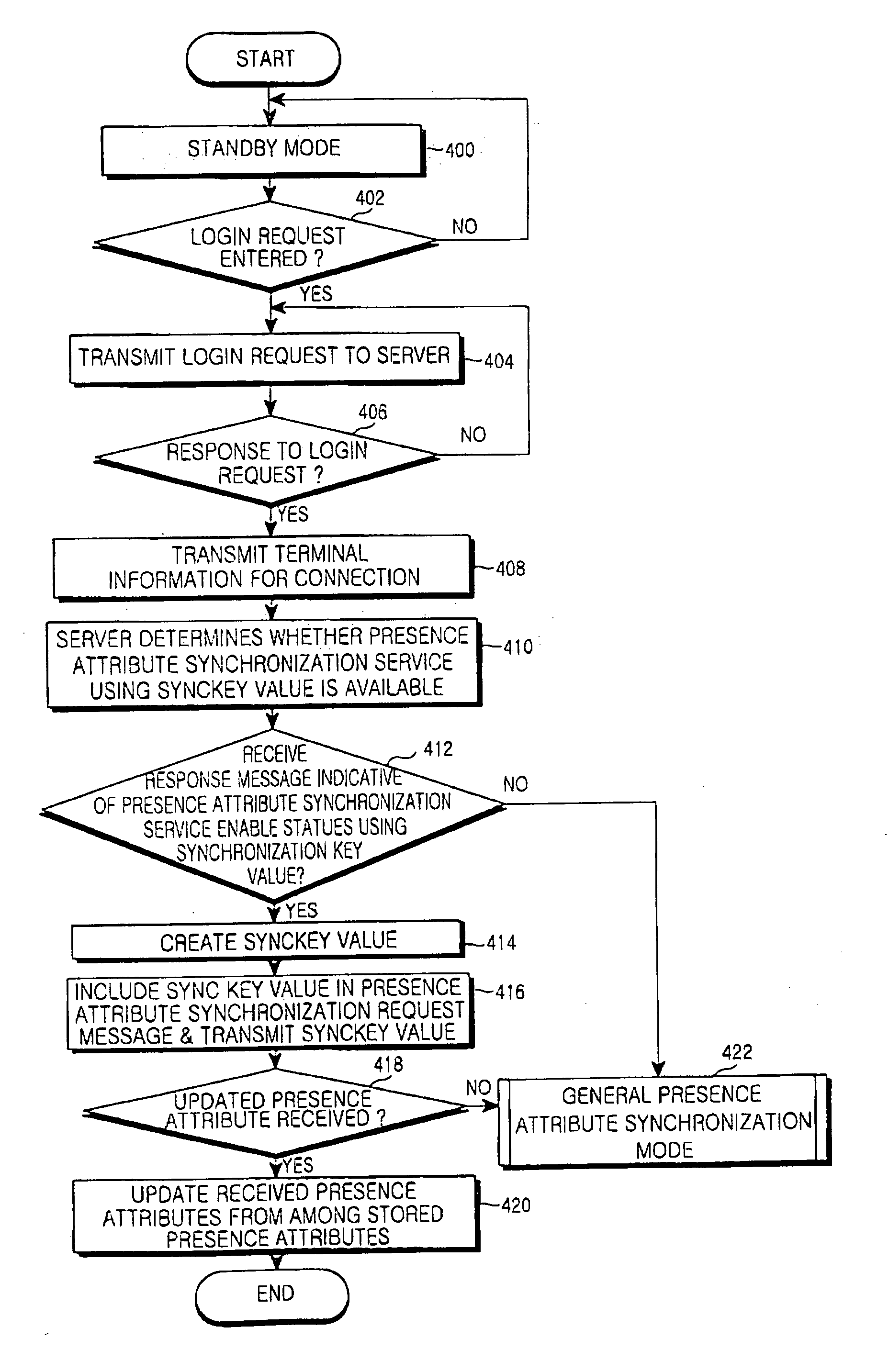
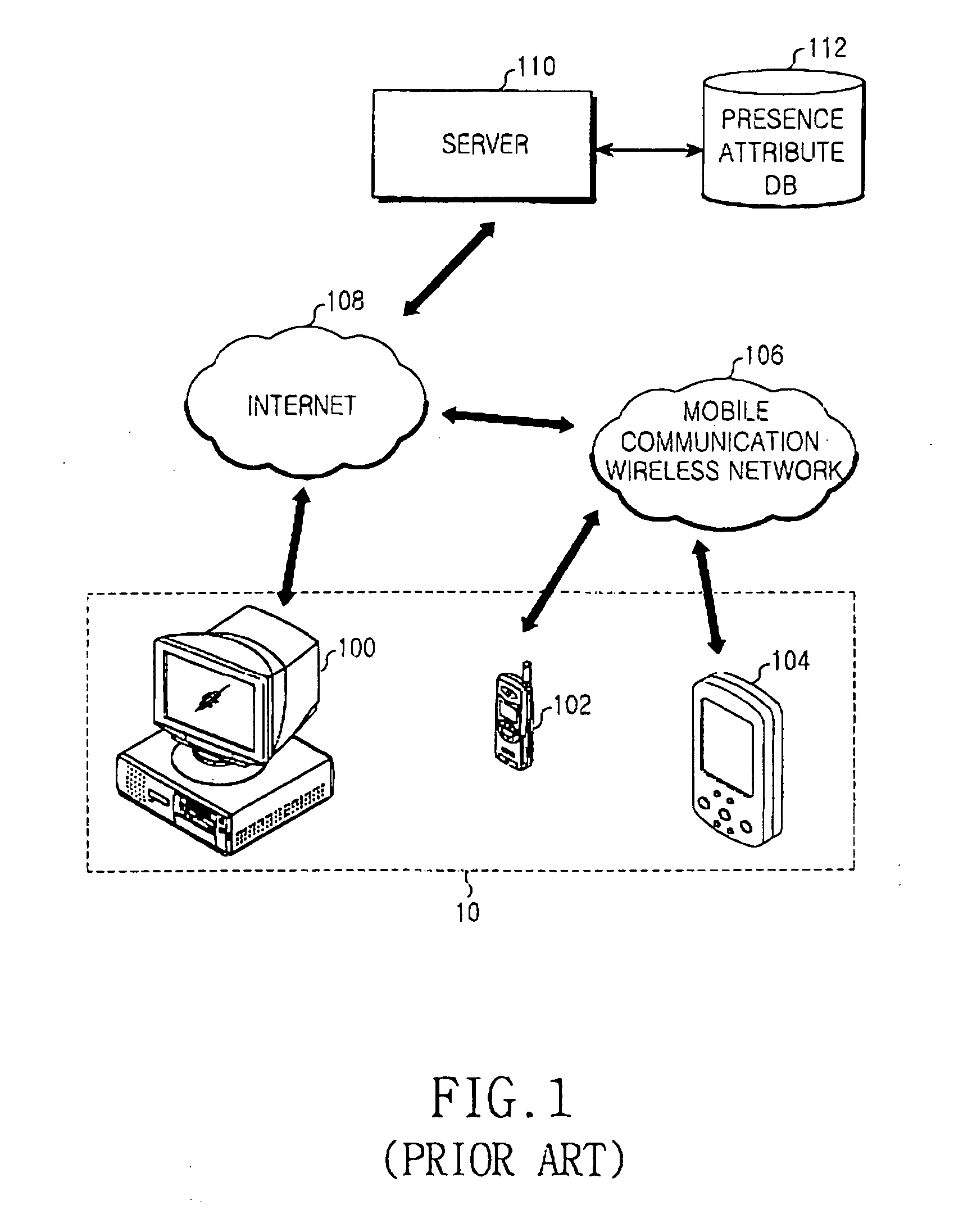
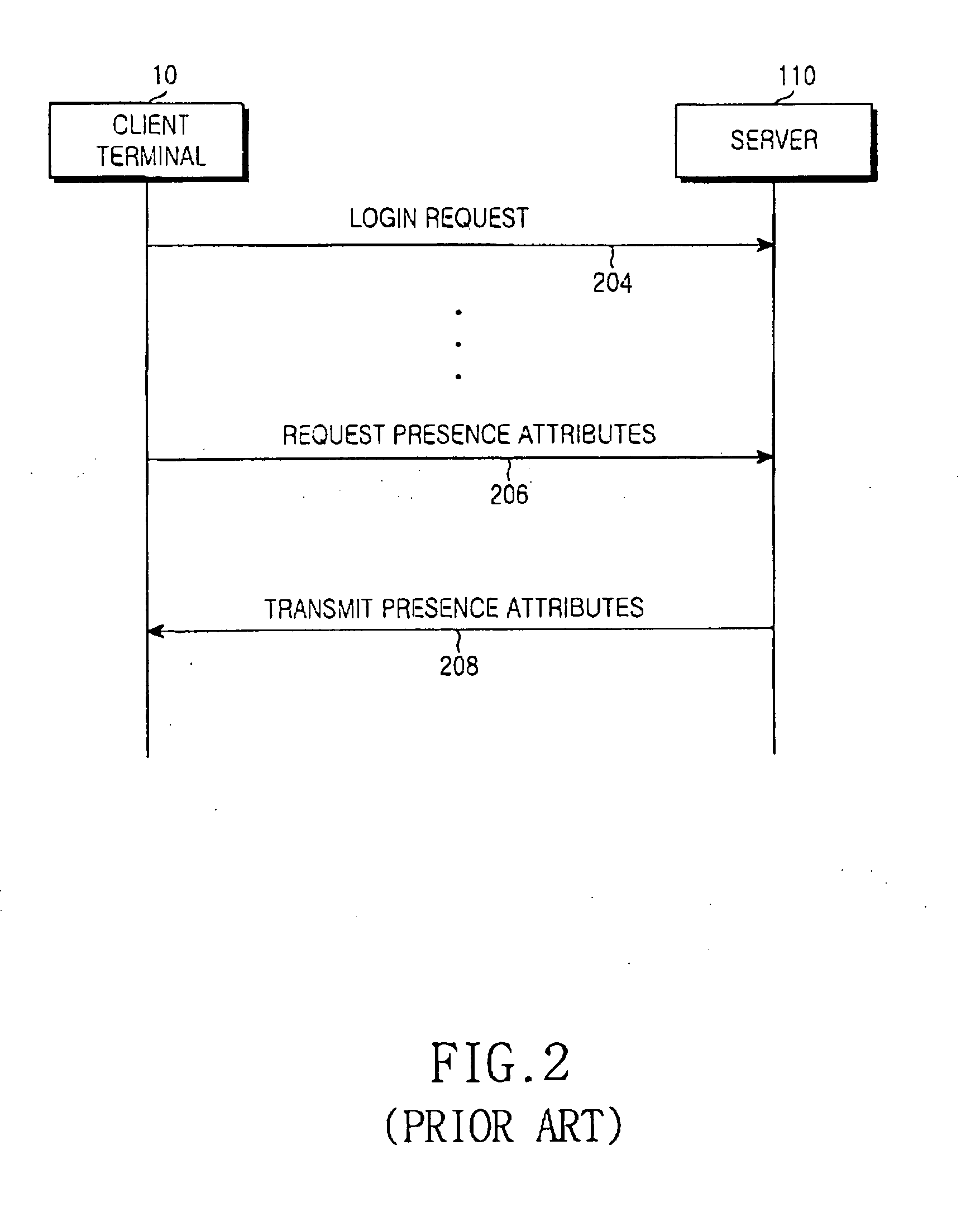
Apparatus and method for synchronizing presence attribute data between terminal and server
ActiveUS20050086376A1Efficient Data SynchronizationAvoid trafficData switching by path configurationMultiple digital computer combinationsClient-sideData storing
An apparatus and method for synchronizing data between a terminal and a server. The apparatus synchronizes presence attribute data when the terminal and the server are connected to each other to establish a messenger service between them. The client terminal requests presence attribute data to be updated from a server when it is reconnected to the server having been previously connected to the client terminal to perform the messenger service, and updates presence attribute data stored at a time of a previous connection upon receiving the presence attribute data to be updated from the server. The server receives a presence attribute data request to be updated from the client terminal, and transmits only updated presence attribute data, created after releasing the previous connection, from among current presence attribute data to the client terminal.
Owner:SAMSUNG ELECTRONICS CO LTD
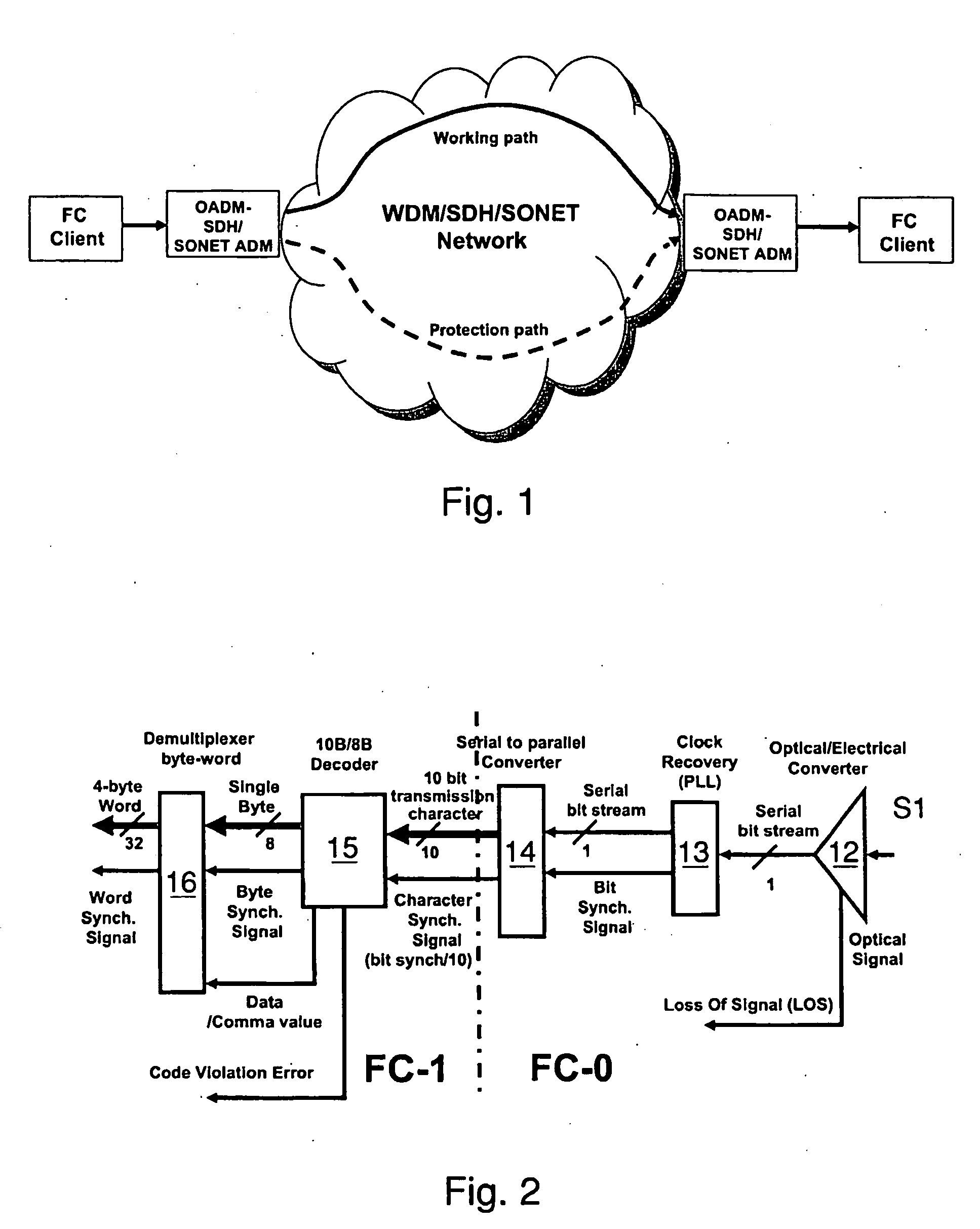
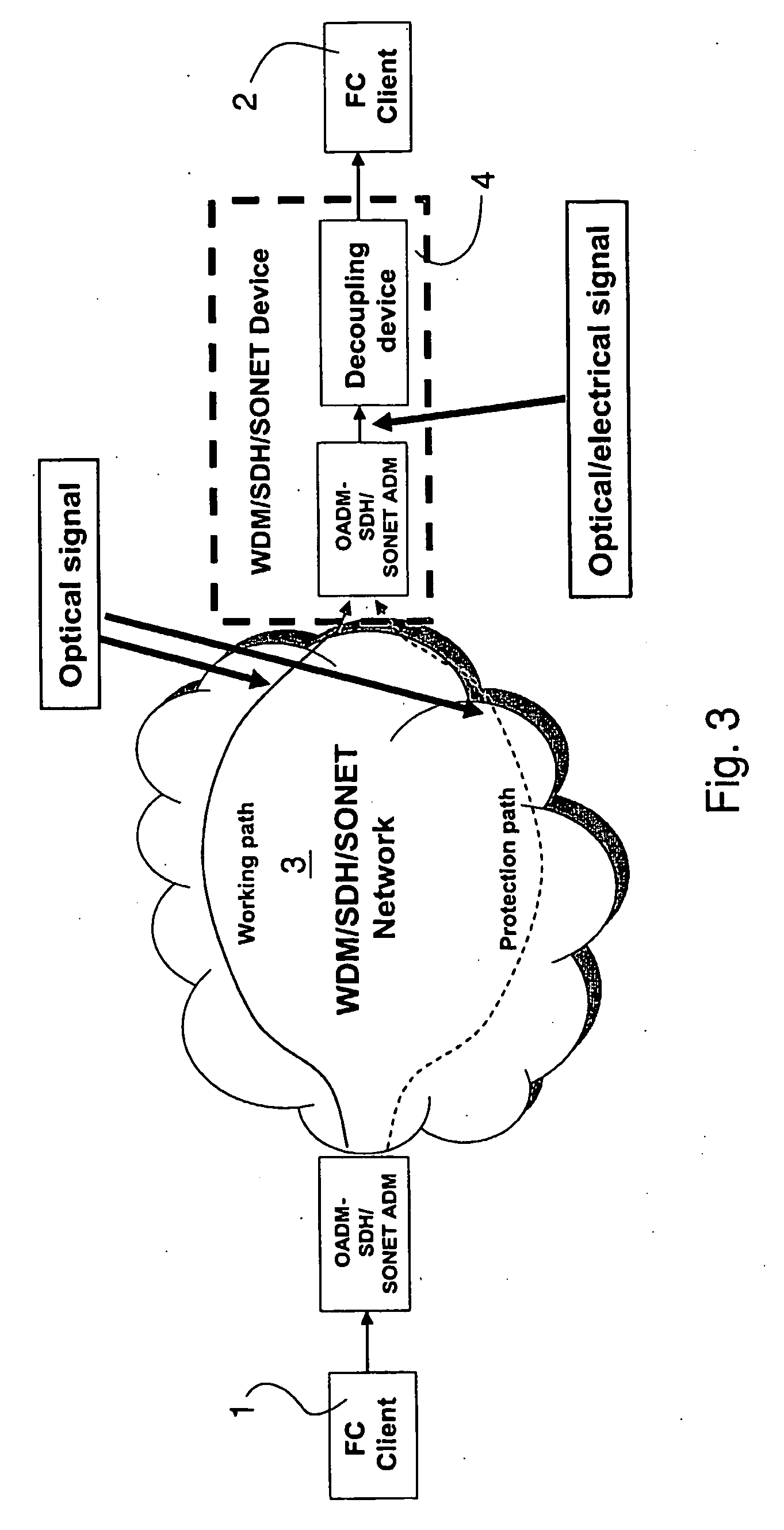
Method and an apparatus for preventing traffic interruptions between client ports exchanging information through a communication network
A method for preventing a temporary traffic interruption between two client ports and the consequent state transition of the receiving port in a communication network providing for the transmission of a data stream between two clients along at least one path when a fault condition is detected in the path. The method includes the steps of monitoring the data stream directed to the receiver and, upon detecting in the data stream an error sequence capable of starting the state transition, replacing the data stream with a filling data stream to prevent the receiver from detecting an error condition, and resuming the forwarding of the received data stream after a predetermined time interval. An apparatus able to mask to the receiver for the predetermined time interval, a storage area network and a computer program product are also disclosed.
Owner:TELECOM ITALIA SPA
Labels, containers, system and method for providing reagents
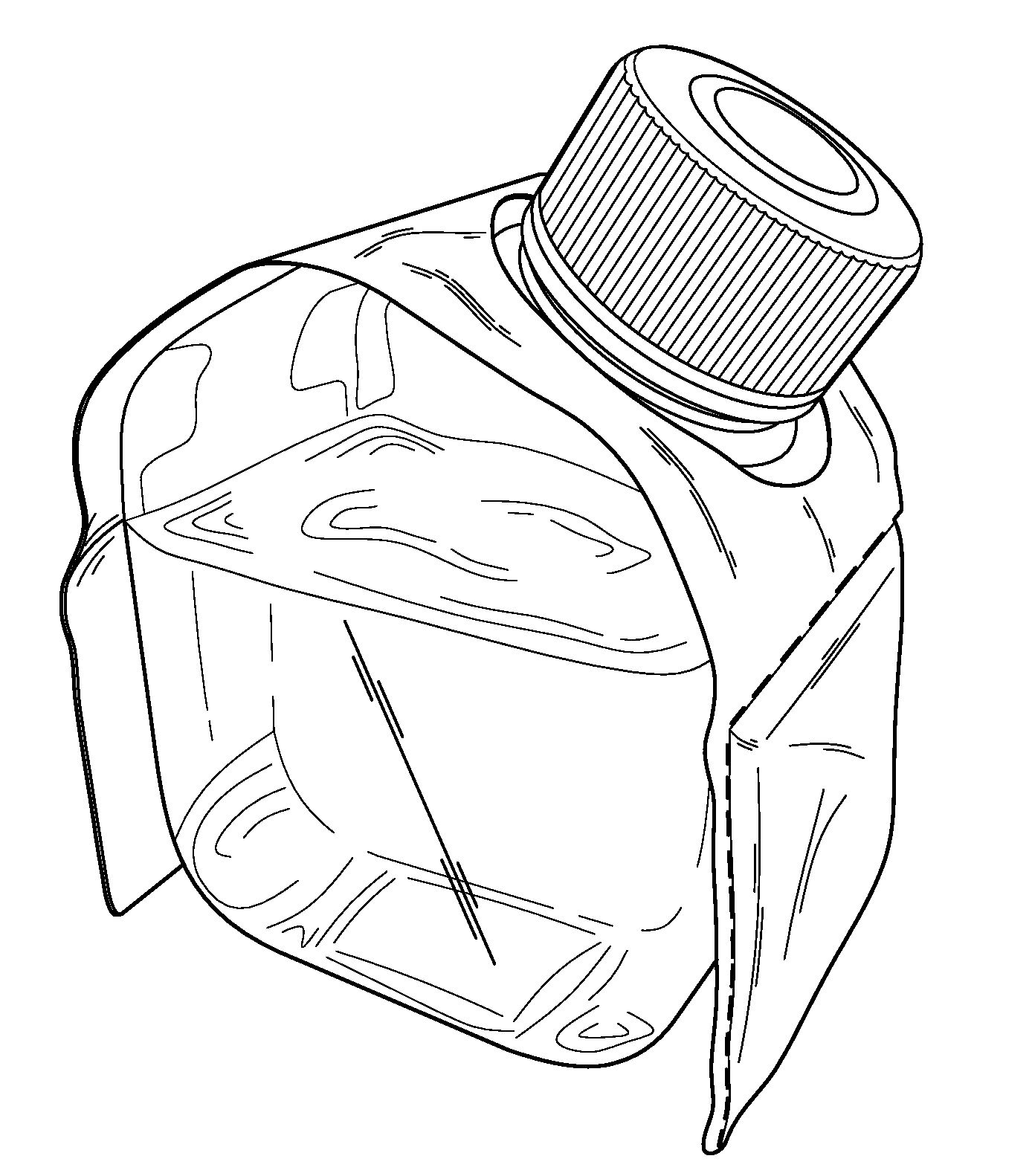
InactiveUS20100059533A1Avoid trafficStop the flowContainer decorationsLevel indicationsAlphanumericLaboratory facility
The invention relates to systems and methods for marketing and using products such as liquid materials, especially liquid reagents for use in microbiological and cellular biological laboratory settings include the use of unique color and simple numeric or alphanumeric identifiers to quickly and easily identify any product from a catalog list of products. Methods of marketing, advertising and producing such products are also disclosed. Particular embodiments include products, product packaging and product labeling. The invention also relates to collars and sleeves for containers, flexible stabilizers for containers, as well as related methods of use.
Owner:LIFE TECH CORP
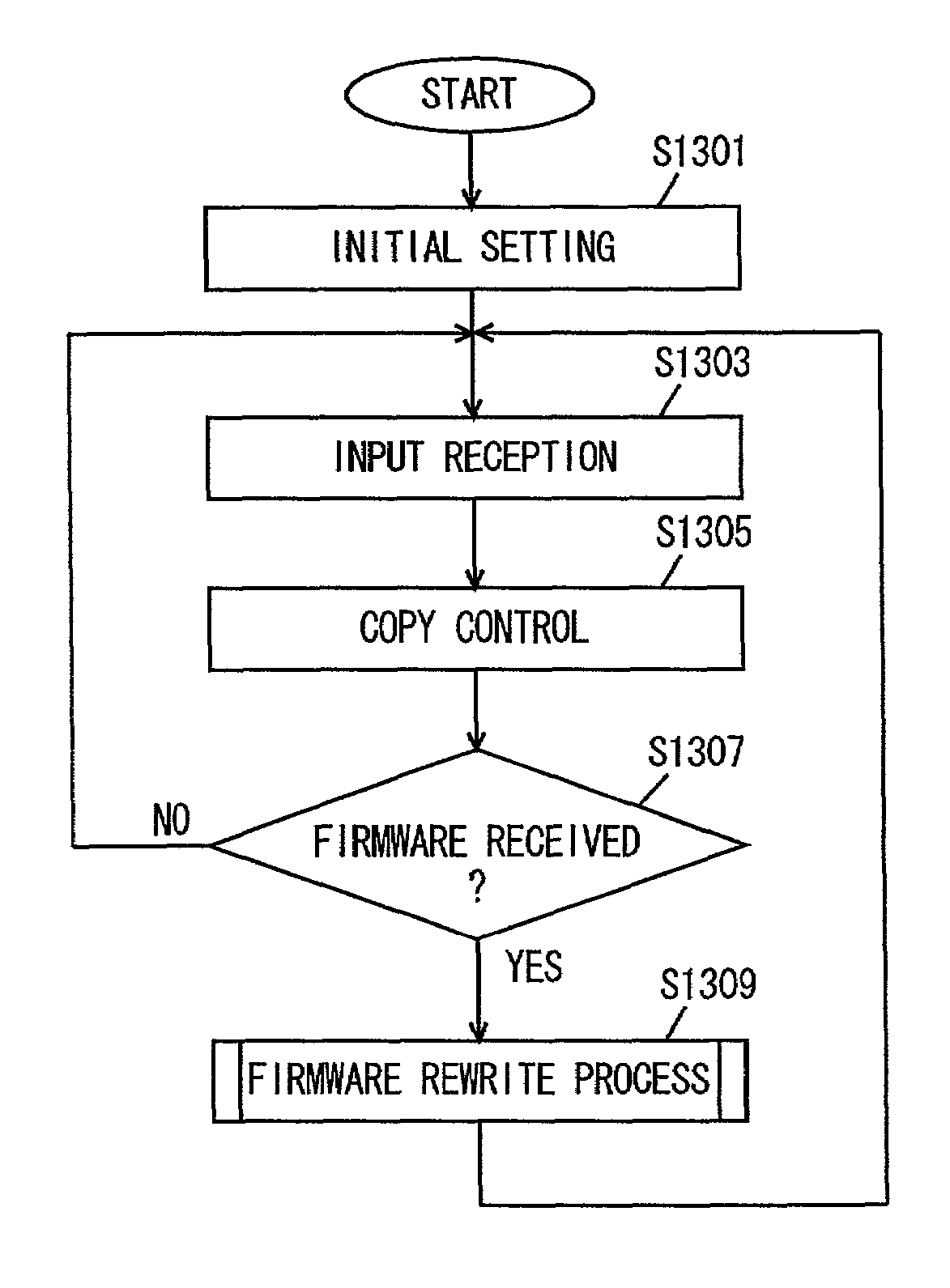
Data communication program product to rewrite simultaneously firmware of plurality of devices connected to network
ActiveUS7058088B2Reduce loadPrevent communication trafficFrequency-division multiplexProgram loading/initiatingTraffic capacityImage formation
New firmware is attached to electronic mail from a computer of the service center to be transmitted towards a monitor device at the user side. The monitor device of the user side reads out the electronic mail from a mail server and downloads the electronic mail into its own apparatus. Then, the firmware is derived from the electronic mail and transmitted to an image formation apparatus that is the subject of transmission. The image formation apparatus receiving the firmware writes the new firmware into the flash ROM that is the subject of rewriting. Accordingly, increase of the communication traffic can be prevented and the load on the mail server can be alleviated in the case where the same firmware for a plurality of devices connected on a network is to be altered using an electronic mail system.
Owner:MINOLTA CO LTD
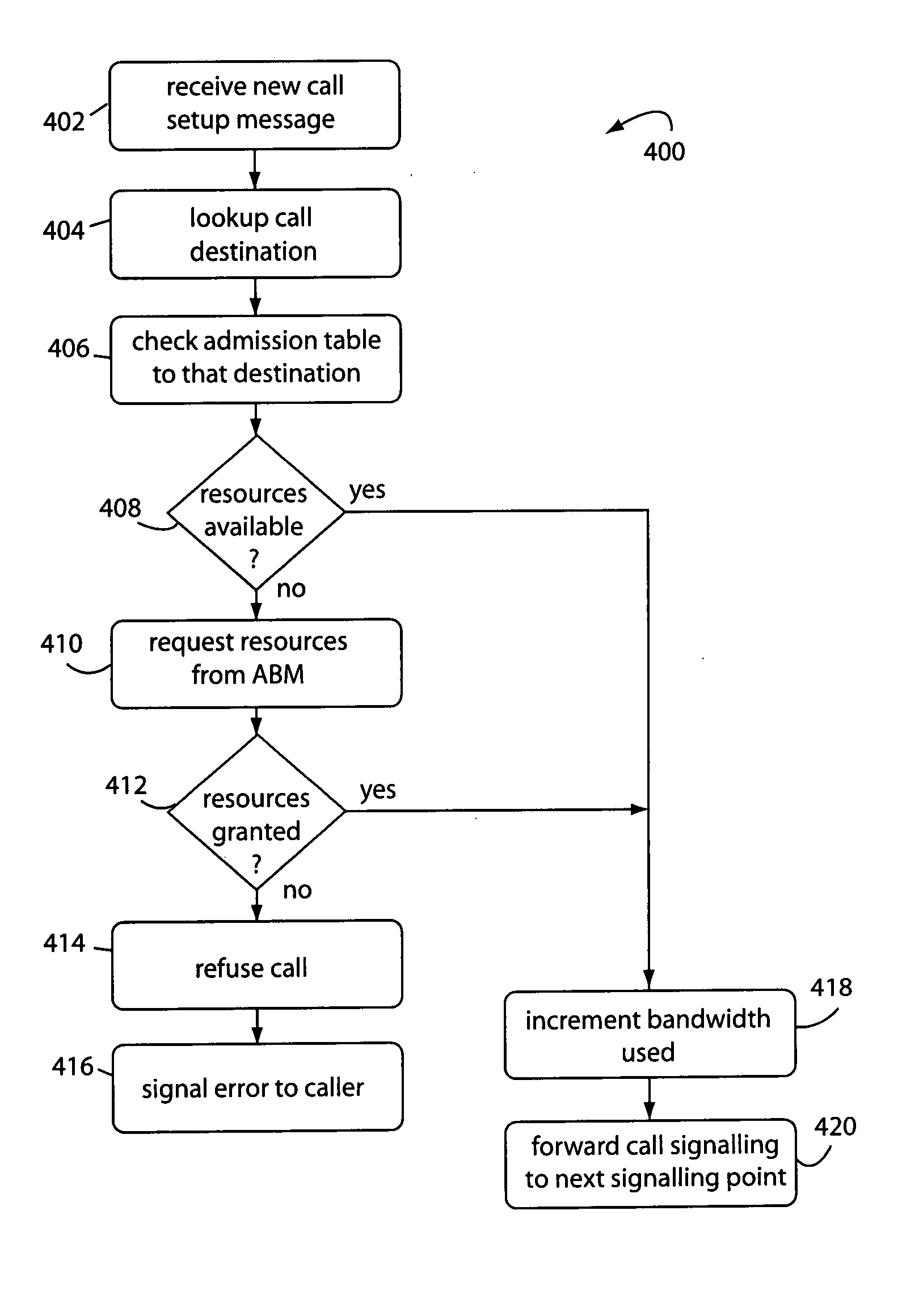
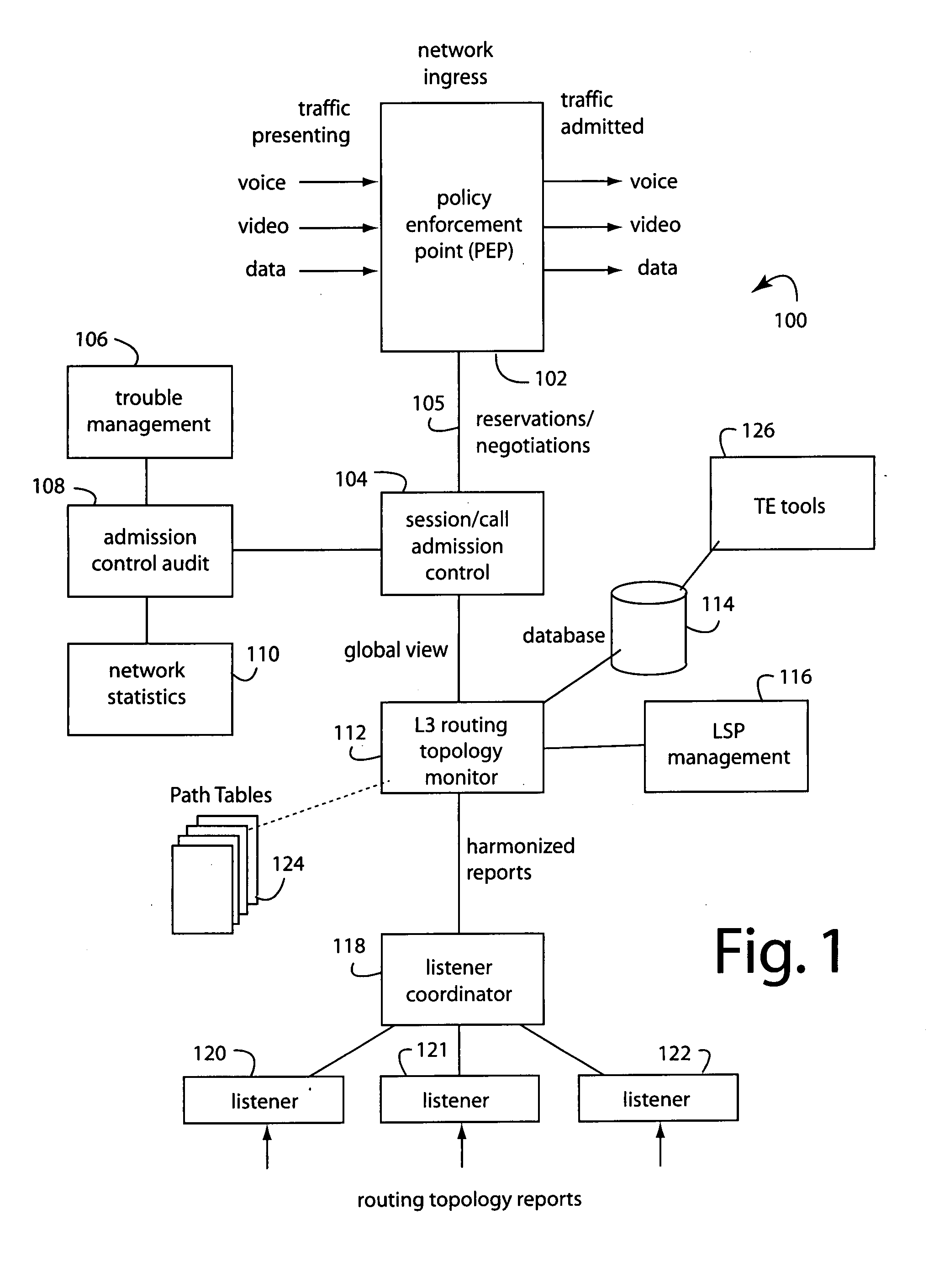
Under-assigning resources to video in triple-play virtual topologies to protect data-class traffic
ActiveUS20080225706A1Low costEasy to planError preventionTransmission systemsShort termsData traffic
A method for video-on-demand (VoD) admission control at a network edge assigns to a triple-play network virtual topology lesser resources than there exists in a corresponding underlying physical link bandwidth. This prevents video-on-demand (VoD) starvation of data-class traffic. At least one policy enforcement point (PEP) is attached to an edge of the network, providing for autonomous short-term, application-aware controls to be applied to corresponding network ingress traffic, and also providing for long-term controls on corresponding network ingress traffic. The network ingress traffic to the network comes under management when the traffic nears or exceeds network capacity. It is enabled to do so by computations of current network routing topology and bandwidth reservations. Path tables are used to calculate if a PEP may admit more, or must shed, sessions / calls to maintain service for other existing application traffic. The PEP and a session / call admission controller (S / CAC) may be independently located within the topology of the network, and together implement admission controls that differentiate between triple-play video, voice, and data traffic classes.
Owner:RPX CORP
Hybrid wired and wireless communication system and a communication method thereof
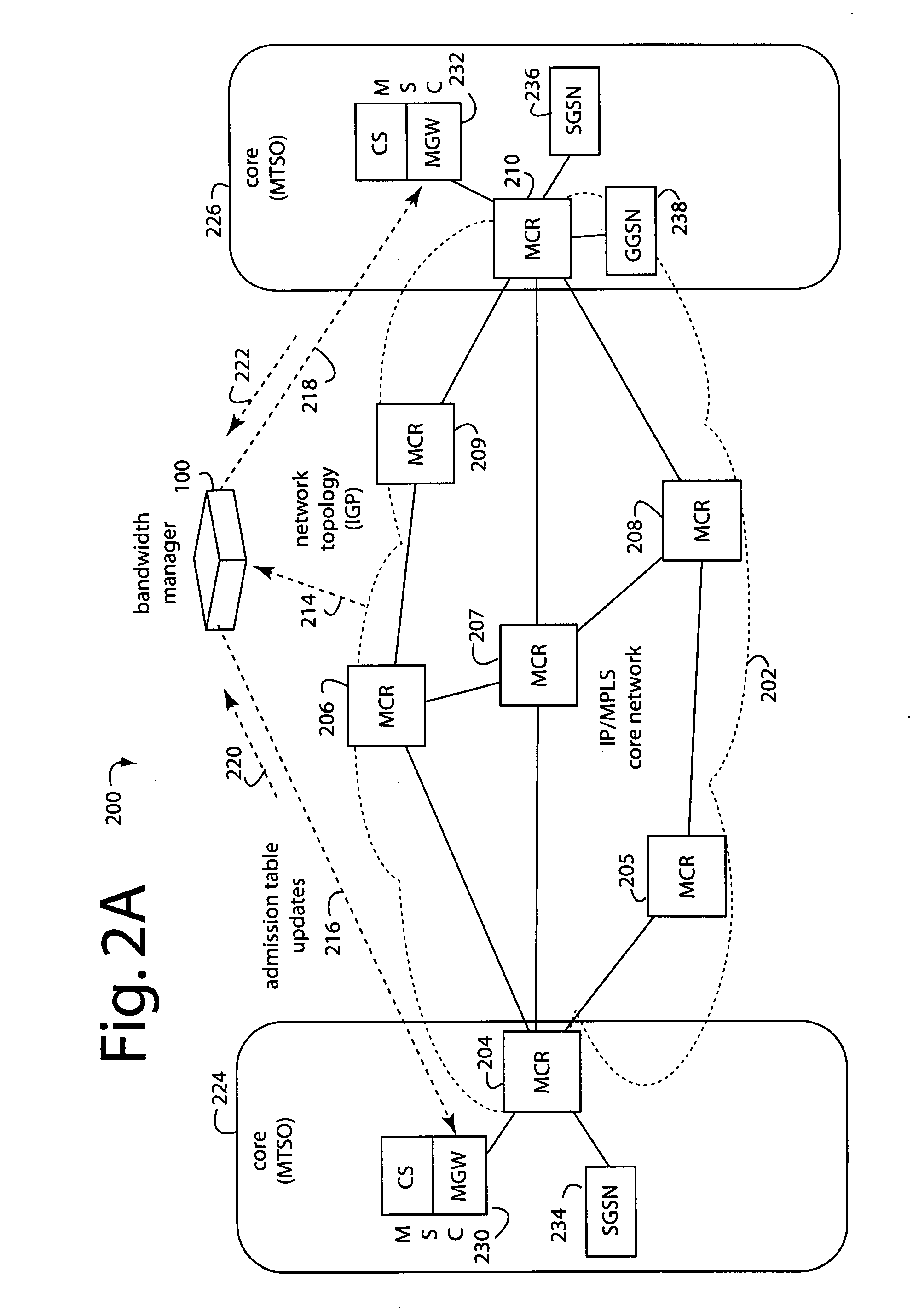
ActiveUS20040258051A1Avoid trafficAvoid it happening againNetwork topologiesHybrid transportCommunications systemPhysical address
A communication method for a hybrid wired and wireless communication system includes registering an entry comprising a physical address of a source transmitting a received packet and an identifier indicating a wired or wireless network interface linked to the physical address in a predetermined management list; receiving a transmission packet from an upper layer and determining whether a physical address identical with a destination physical address of the transmission packet is present in the management list; and when the destination physical address is present in the management list, transmitting the transmission packet through either of the wired network interface and the wireless network interface according to the identifier.
Owner:HEWLETT PACKARD DEV CO LP
Method and apparatus for composing virtual links in a label switched network
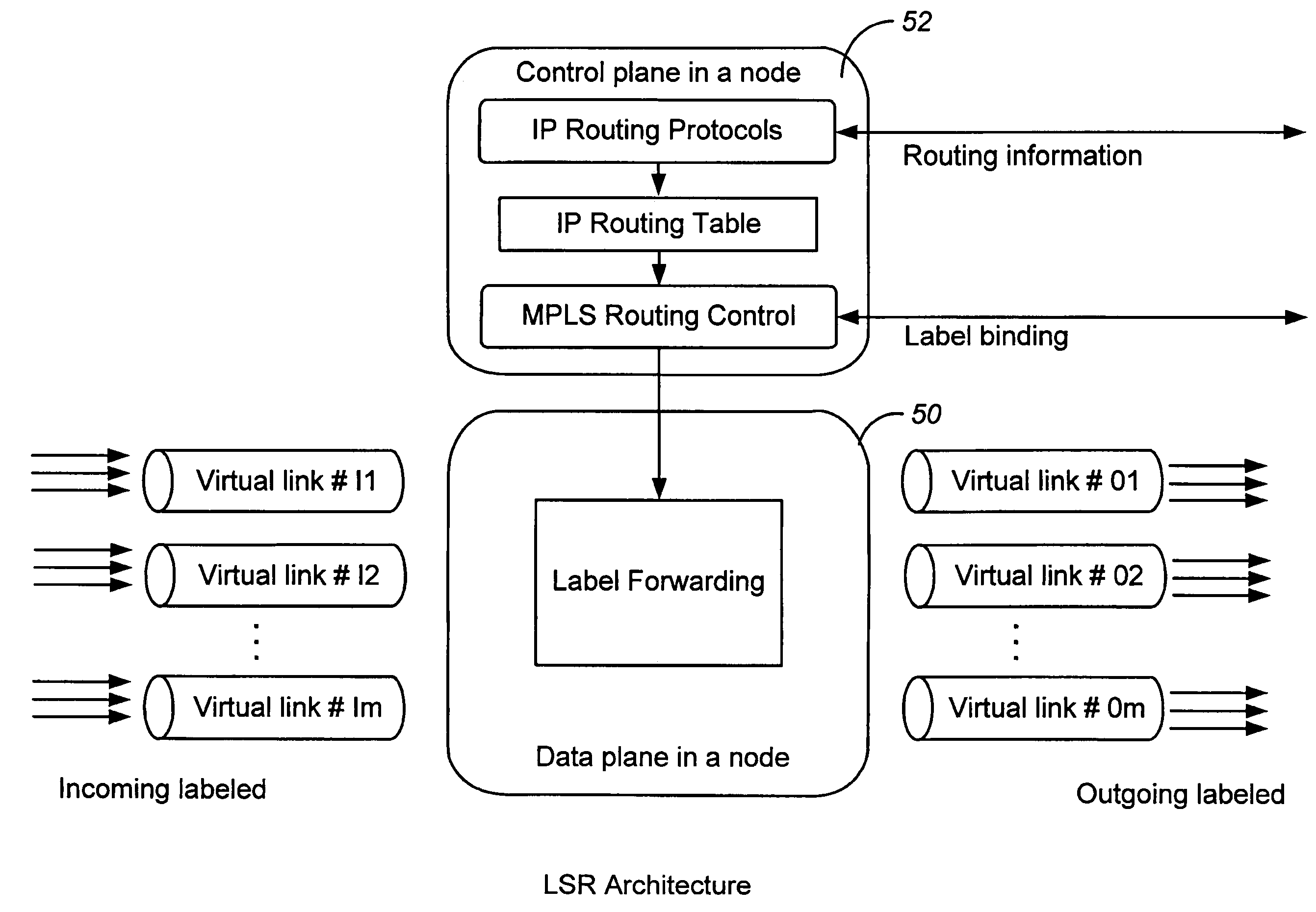
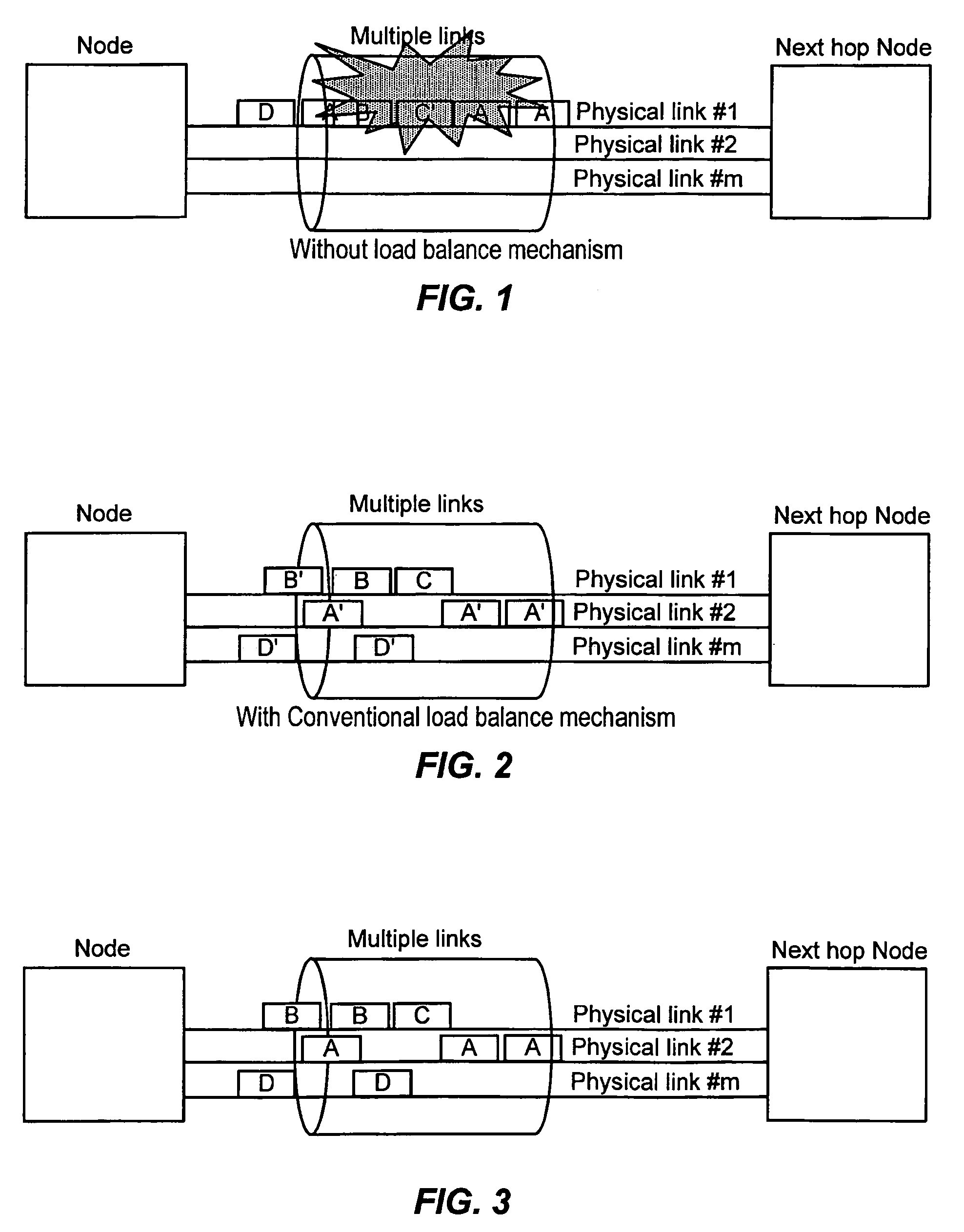
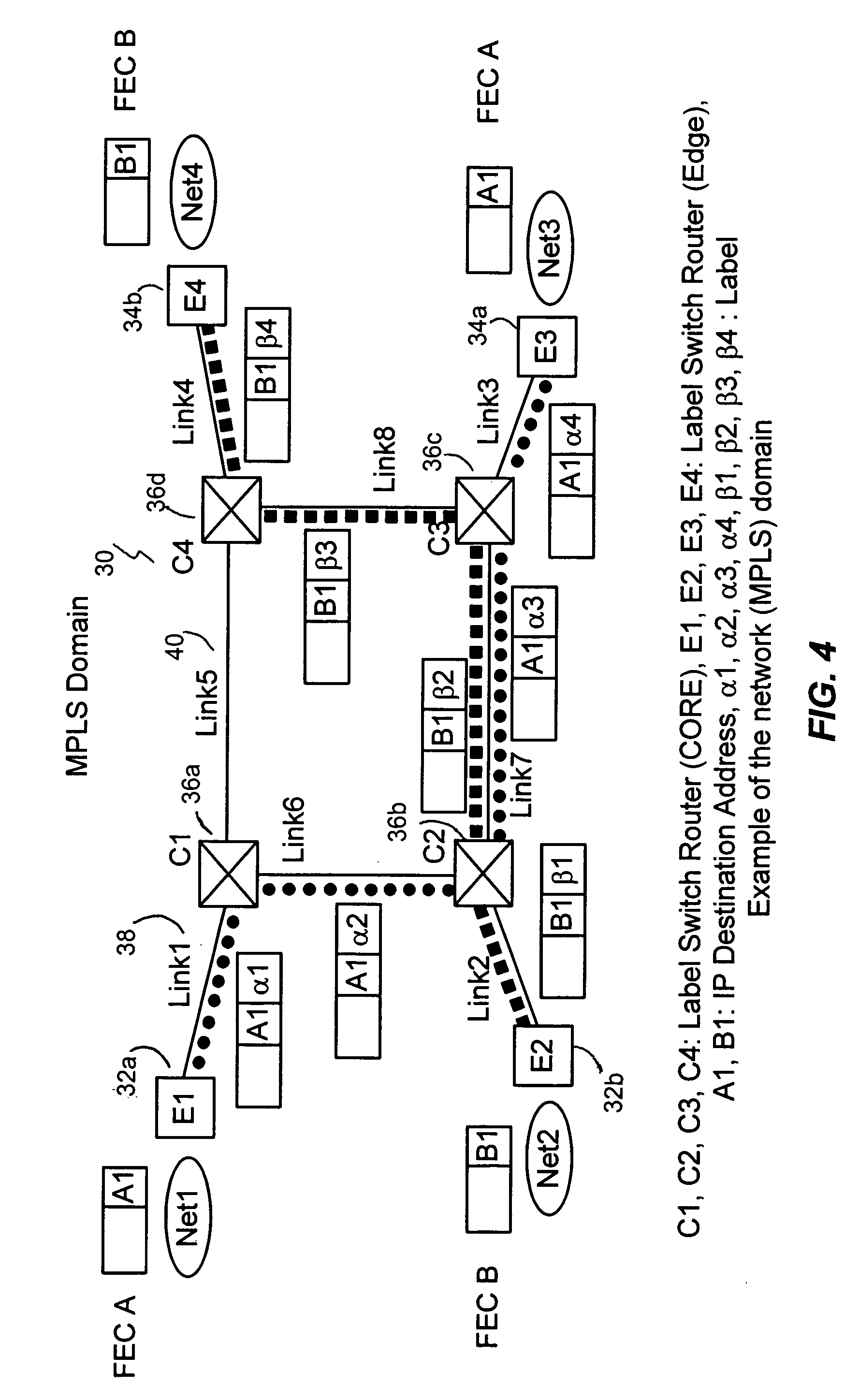
InactiveUS7212526B2Add supportReduce the amount requiredMultiplex system selection arrangementsCircuit switching systemsHash functionForwarding equivalence class
A method for managing virtual links within a multiple protocol label switched network is provided. A virtual link which includes a set of links between two devices is regarded as a single entity by a control component of a label switching router. Each packet to be transported on the virtual link is labeled based on its assigned forwarding equivalence class. A specific label is bound to a corresponding forwarding equivalence class. Such packets can be forwarded onto any one of the links within the virtual link. To load balance the various links within the virtual link, different selected hash functions are used at selected times to apportion the packets. depending on the load conditions.
Owner:HITACHI LTD
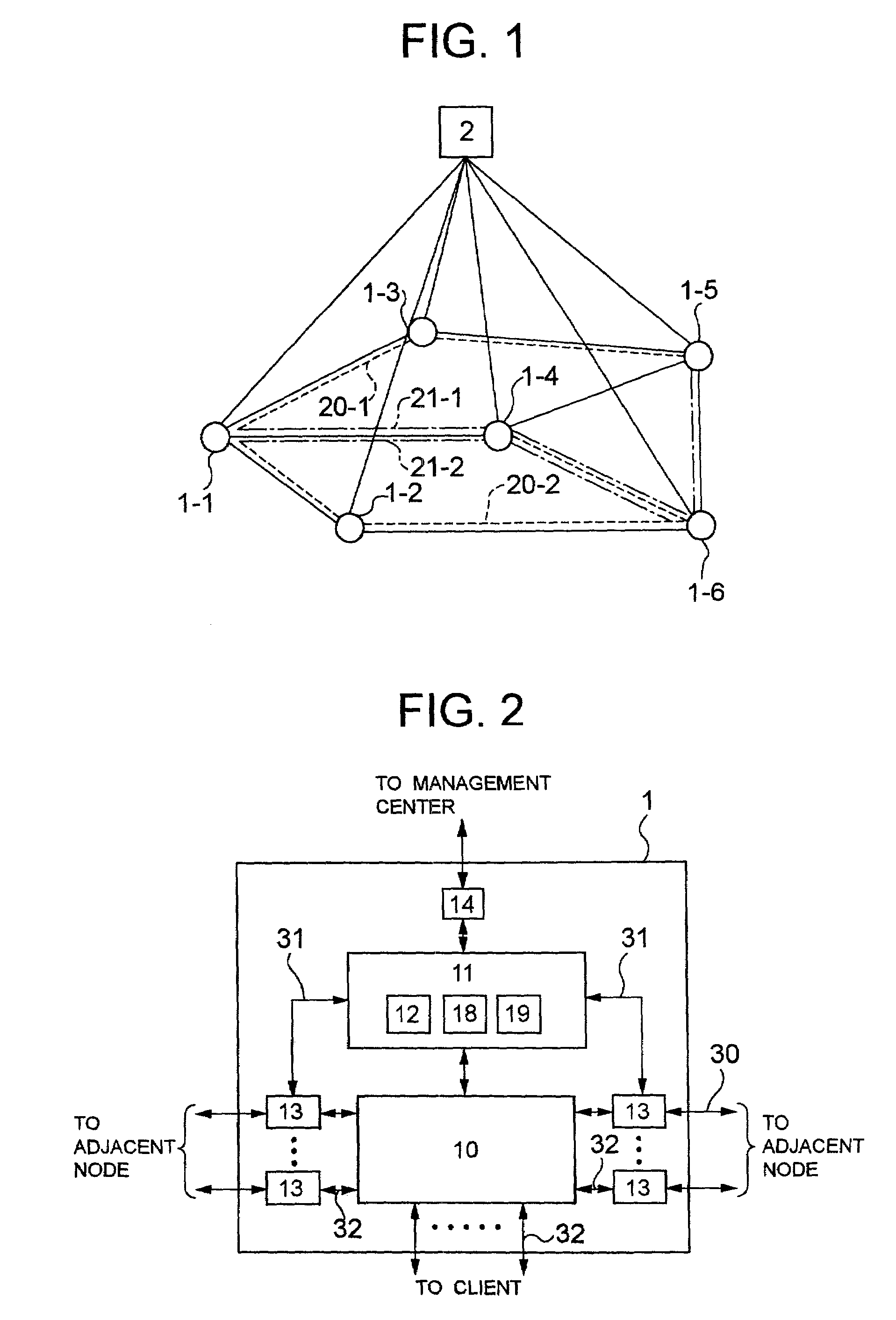
Communication network, path setting method and recording medium having path setting program recorded thereon
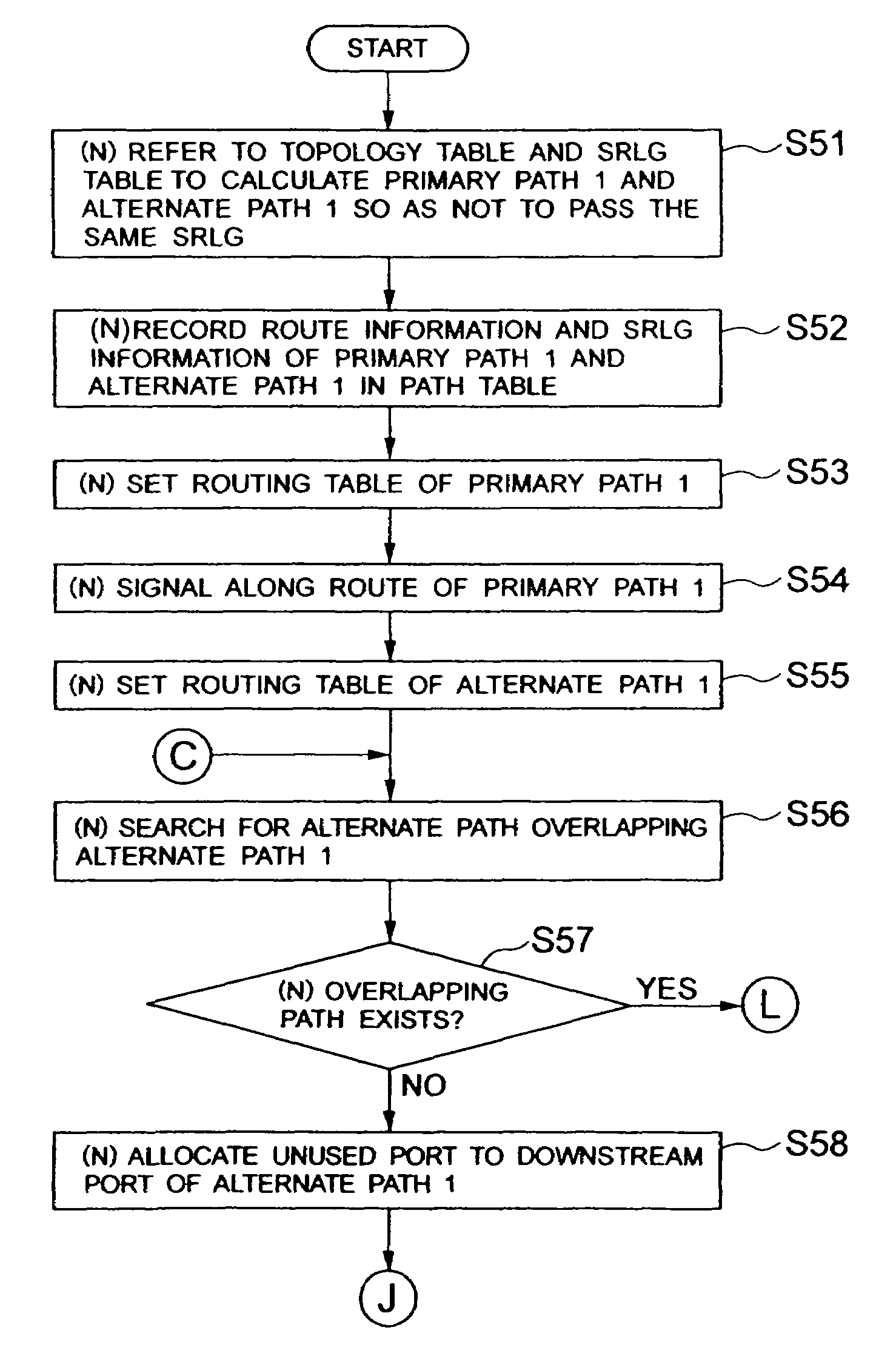
InactiveUS7411964B2Avoid loadAvoid trafficDigital computer detailsData switching by path configurationDistributed computingBroadcast communication network
To prevent load of route calculation from being centralized in part of units. A node calculates routes of a primary path and an alternate path and sends them to a management center. The management center checks whether SRLGs of the two routes overlap, and instructs the node to perform calculation again if the routes overlap. The management center searches for an alternate path having a route overlapping the route of the above described alternate path. When an overlapping alternate path exists, and SRLGs of a primary path corresponding to the alternate path and the above described primary path do not overlap, a link is shared in an overlapping portion of the routes of the two alternate paths.
Owner:NEC CORP
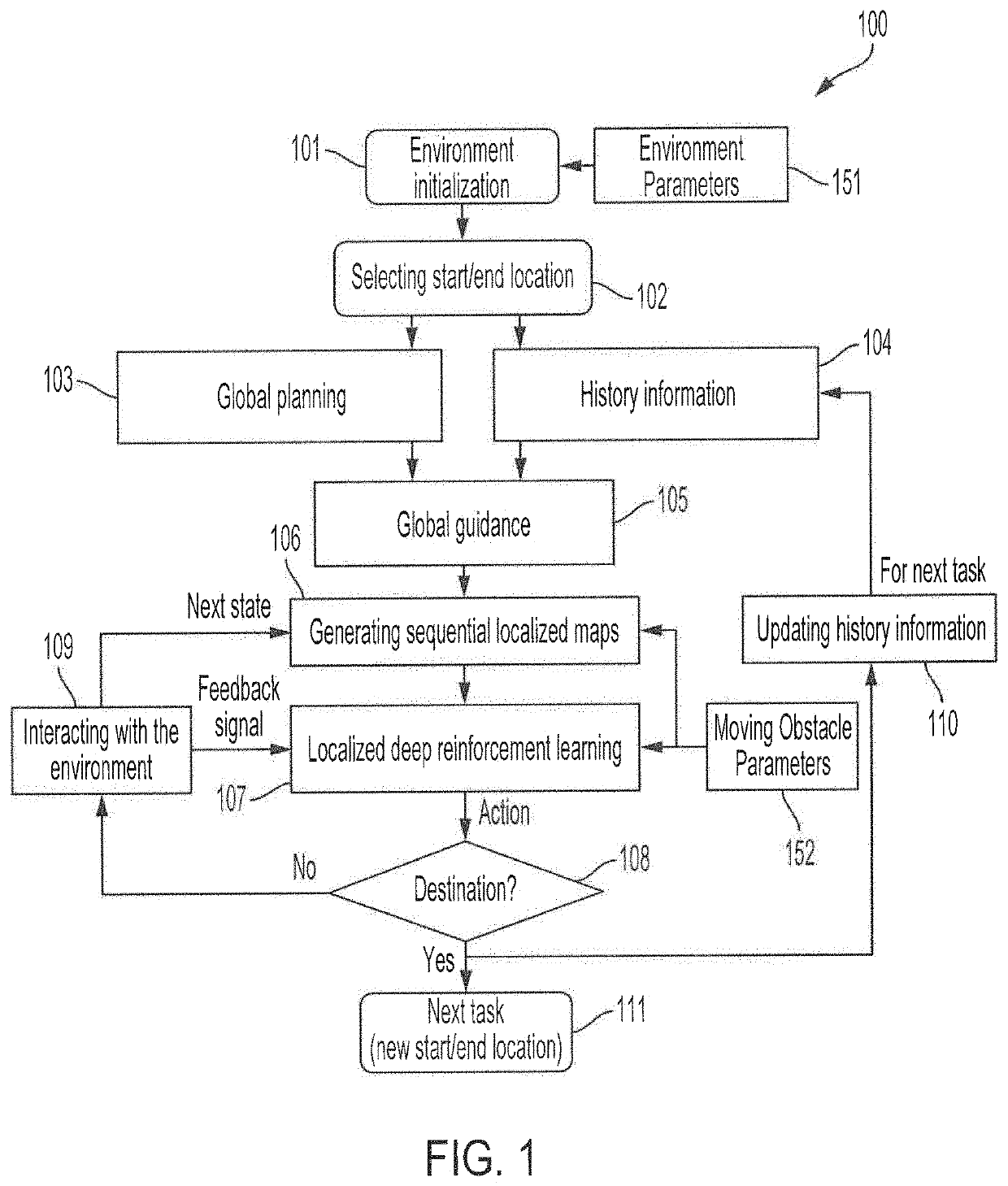
Systems and methods for adaptive path planning
InactiveUS20210103286A1Avoiding pointReduce computing costAutonomous decision making processPosition/course control in two dimensionsGlobal planningLocal planning
Systems and methods providing adaptive path planning techniques utilizing localized learning with global planning are described. The adaptive path planning of embodiments provides global guidance and performs local planning based on localized learning, wherein the global guidance provides a planned path through the dynamic environment from a start location to a selected destination while the local planning provides for dynamic interaction within the environment in reaching the destination, such as in response to obstacles entering the planned path. Global guidance may combine an initial global path with history information for providing a global path configured to avoid points of frequent traffic conflicts. Local planning may utilize localized deep reinforcement learning to direct interactions of an automated vehicle traversing the global path in a dynamic environment, such as in response to obstacles entering the global path. Sequential localized maps may be generated for deep learning models utilized by localized training techniques.
Owner:HONG KONG APPLIED SCI & TECH RES INST
Efficient fluid finishing method and device based on structure cavitation effect
ActiveCN106392863ACollapse drive effect is obviousSimple structureEdge grinding machinesPolishing machinesBubble cavitationWear particle
The invention discloses an efficient fluid finishing method based on the structure cavitation effect. According to the efficient fluid finishing method, the Venturi tube cavitation effect is introduced to fluid finishing, strong bubble cavitation action is formed in the effective polishing area formed between a processing tool and a workpiece to be processed by arranging a Venturi tube structure on the processing tool, and the bubble cavitation action is utilized to drive a liquid-solid abrasive flow in the formed effective polishing area to move in a high-speed turbulent vortex mode to achieve processing on the surface of the workpiece to be processed through abrasive particles. According to the efficient fluid finishing method based on the structure cavitation effect, the Venturi tube structure is utilized to achieve growth and collapse of bubbles in the microspur gap between the processing tool and the workpiece to be processed so as to achieve unordered and high-speed turbulent flow of the abrasive particles; compared with processing equipment adopting ultrasonic waves, the structure is simpler and the cost is lower; and compared with normal bubble-free-collapse processing equipment, the controllability is better, and the bubble collapse driving effect is more obvious.
Owner:ZHEJIANG UNIV OF TECH
CAN node, and communication method of communication system including CAN node
ActiveUS8509257B2Reduce loadHigh trafficError preventionTime-division multiplexArea networkCommunications system
A Controller Area Network (CAN) node includes a conversion and retransmission unit which retransmits a transmit message if the transmit message carries a retransmission ID out of ID codes, by changing the ID code of the transmit message to a retransmission-specific ID corresponding to the retransmission ID, where the ID codes indicate priorities of transmit messages, the retransmission ID indicates that the transmit message is to be retransmitted, and the retransmission-specific ID is an ID code specifically for use in retransmission, and a conversion and reception unit which checks whether an original message corresponding to a retransmit message has been received successfully, the retransmit message being a receive message carrying the retransmission-specific ID, and discards the retransmit message if the original message corresponding to the retransmit message has been received successfully, but converts the ID code of the retransmit message into a retransmission ID corresponding to the retransmission-specific ID if the original message corresponding to the retransmit message has not been received successfully.
Owner:RENESAS ELECTRONICS CORP
System and method for controlling, obfuscating and anonymizing data and services when using provider services
InactiveUS20140115715A1Retain privacyPreventing the source from being identifiedDigital data processing detailsAnalogue secracy/subscription systemsService providerService provision
A system, method, and computer readable medium for preventing data leakage from a transmission unit to a service provider (SP), utilizing a network system including a computer, a processor, memory, and a computer readable medium storing thereon computer code which when executed by the at least one computer causes the at least one computer to at least: identify identification information of a user included in data communication between the transmission unit and the SP; identify a SP application via an application signature; determine whether the identified SP application meets at least one data leakage prevention policy for a user; and perform at least one of a plurality of data leakage prevention processes on the transmission unit.
Owner:PASDAR BABAK
Mobile network content based charging and access control system
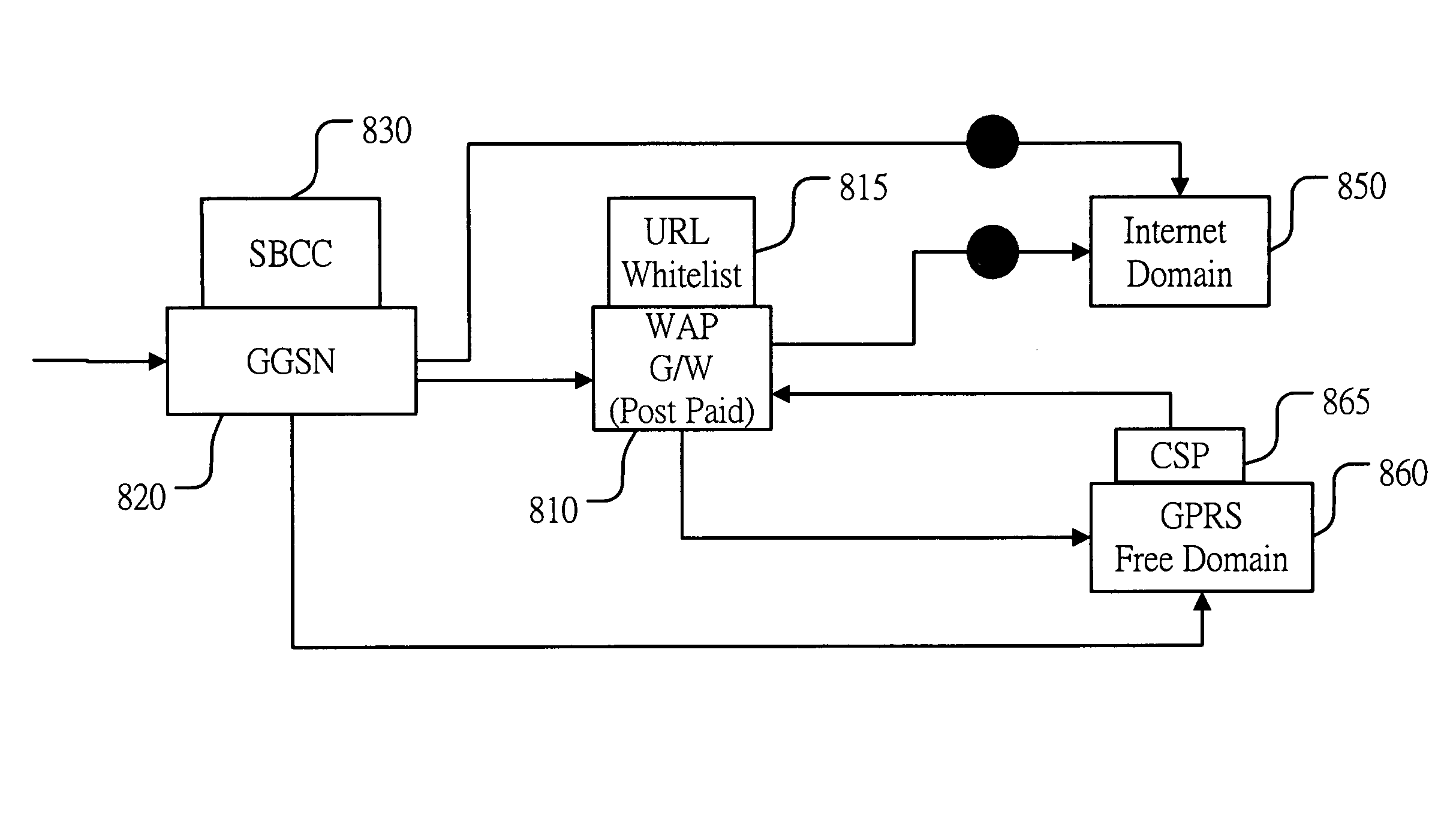
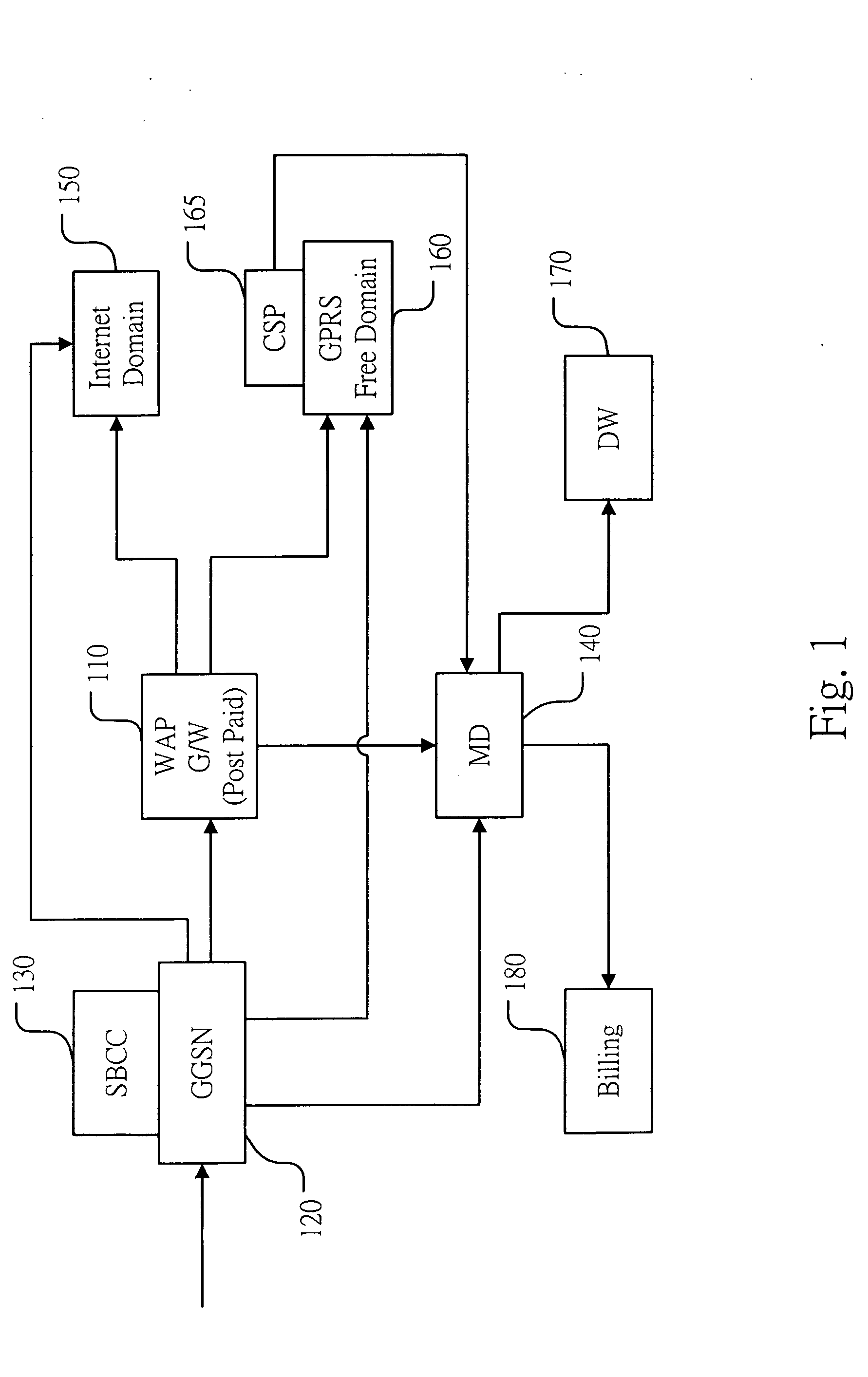
ActiveUS20050090230A1Accurate and effective and efficientAccurate and effective and efficient systemMetering/charging/biilling arrangementsAccounting/billing servicesGeneral Packet Radio ServiceDomain name
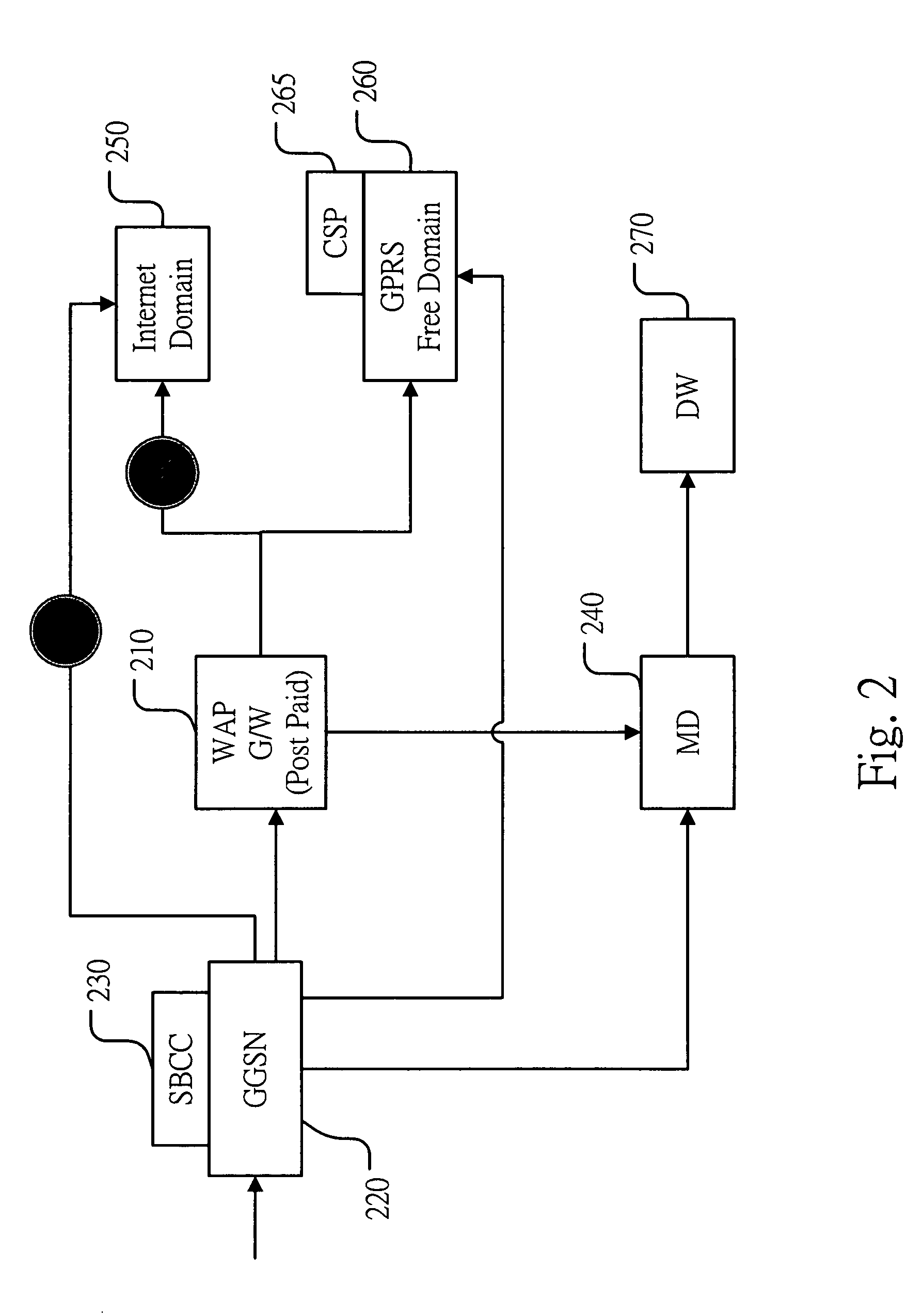
The invention provides an accurate, effective, and efficient system for content based charging, access barring, and network browsing, for pre-paid and post-paid subscribers of a wireless mobile communication network system comprising a gateway general packet radio service support node with service based content charge module; a separate WAP gateway for post-paid and pre-paid subscribers; IP, domain name and URL white list filtering; call detail records; a mediation gateway; data warehouse; and billing system. Access to the internet or free domain networks are efficiently controlled and content charges are accurately billed for both pre-paid and post-paid subscribers.
Owner:FAR EASTONE TELECOMM
Radio network controller, mobile station, and mobile communication method
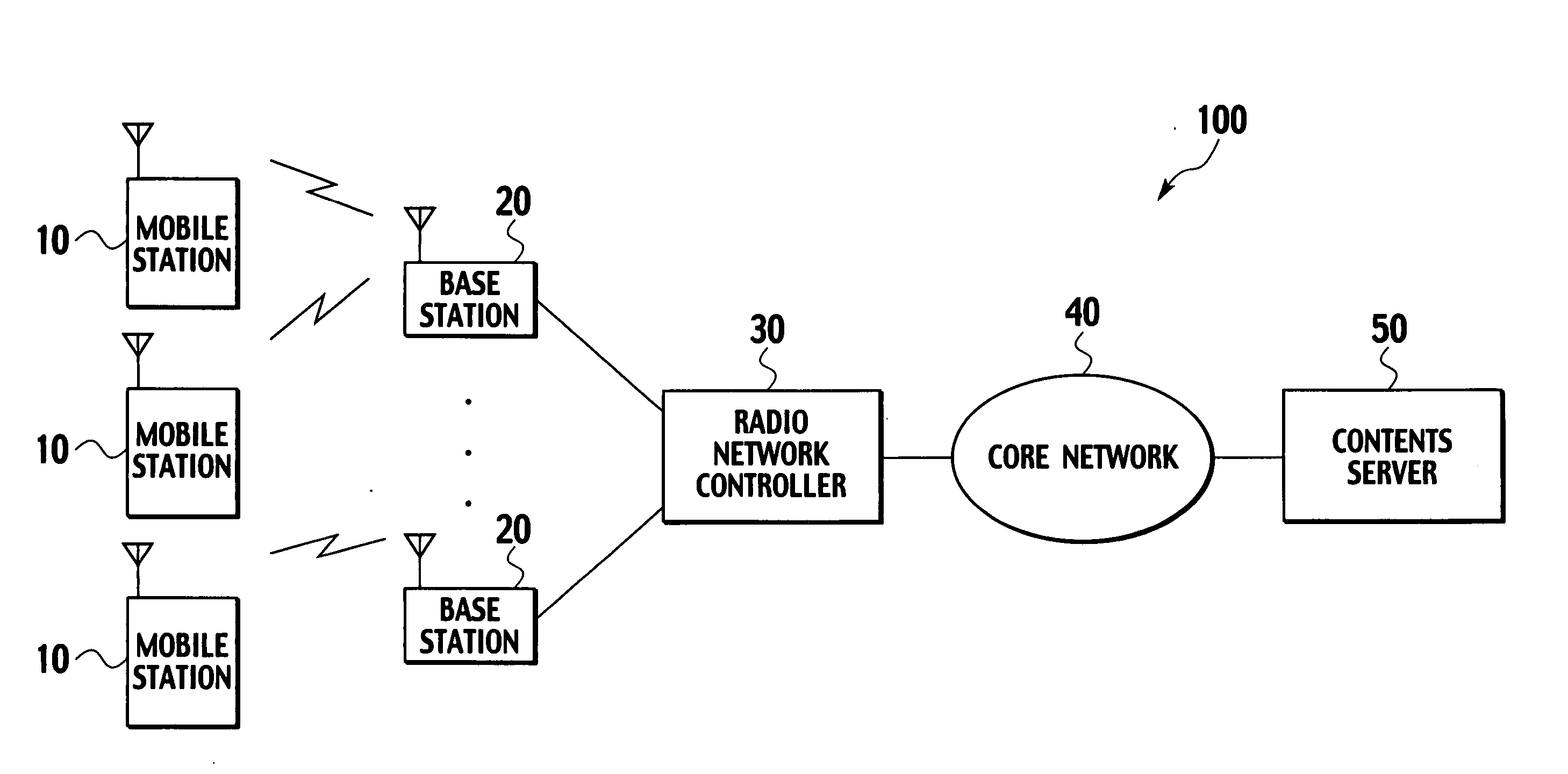
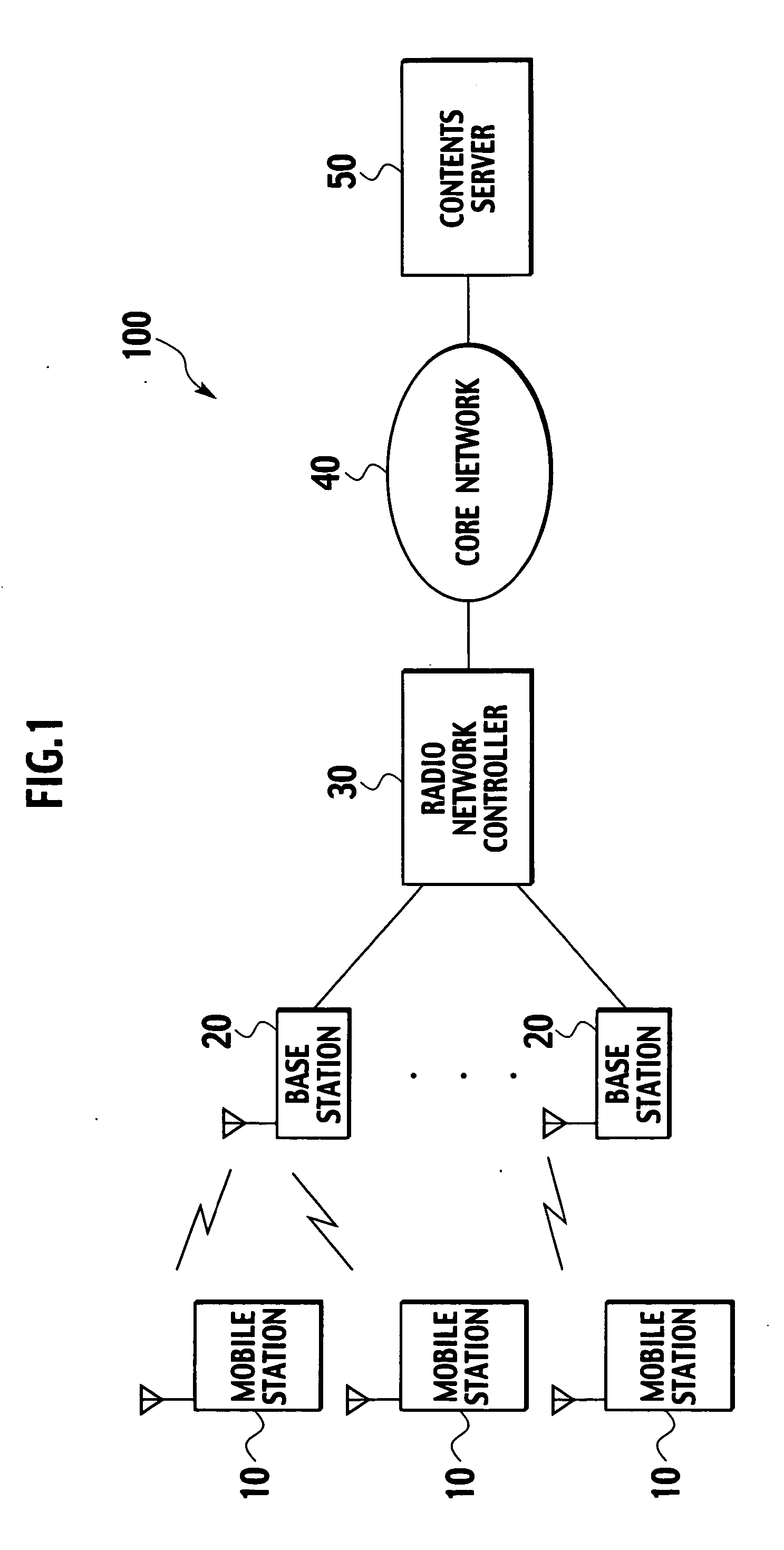
InactiveUS20060035641A1Efficient use ofAvoid trafficAssess restrictionRadio/inductive link selection arrangementsTelecommunicationsRadio Network Controller
A radio network controller comprises a cell selector configured to select a cell to use by a mobile station after data reception, and a mobile station controller configured to control the mobile station to communicate by radio using the cell selected by the cell selector after the data reception.
Owner:NTT DOCOMO INC
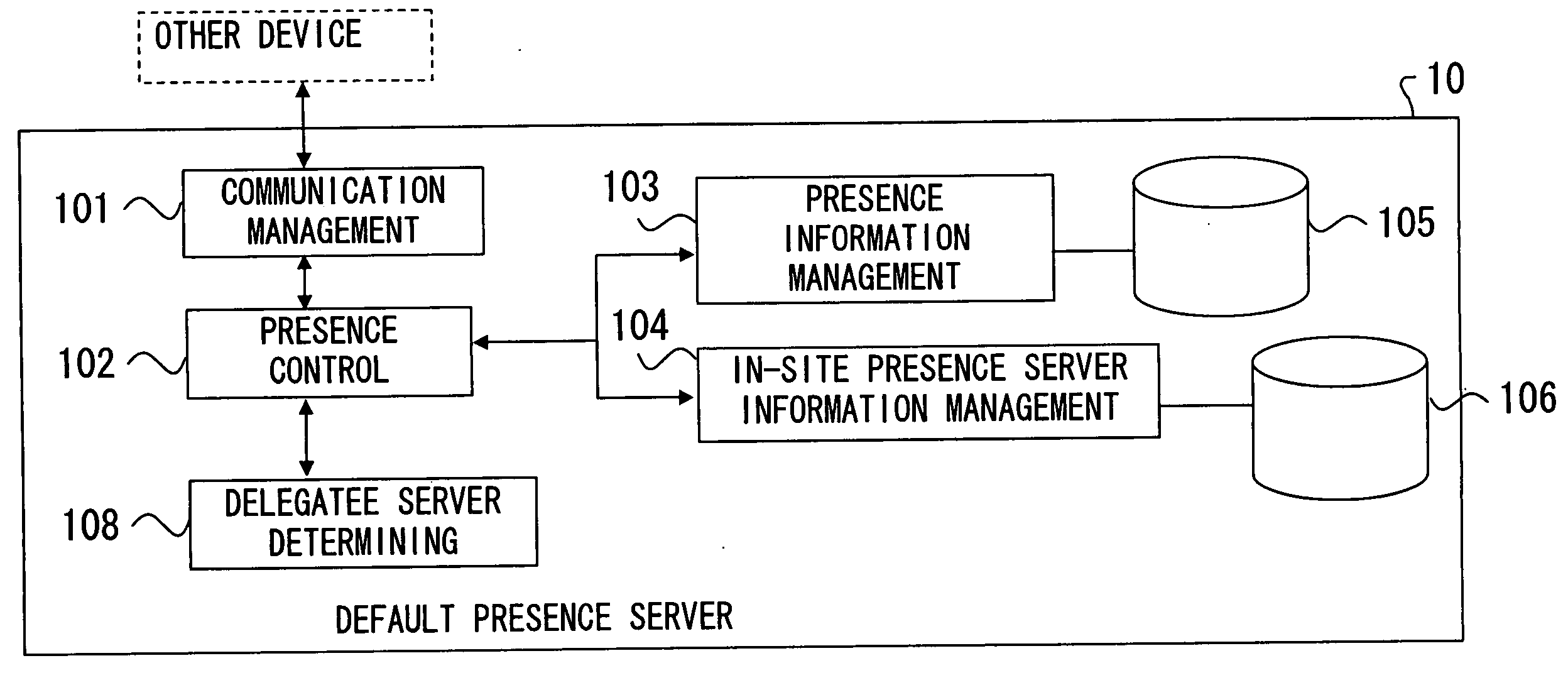
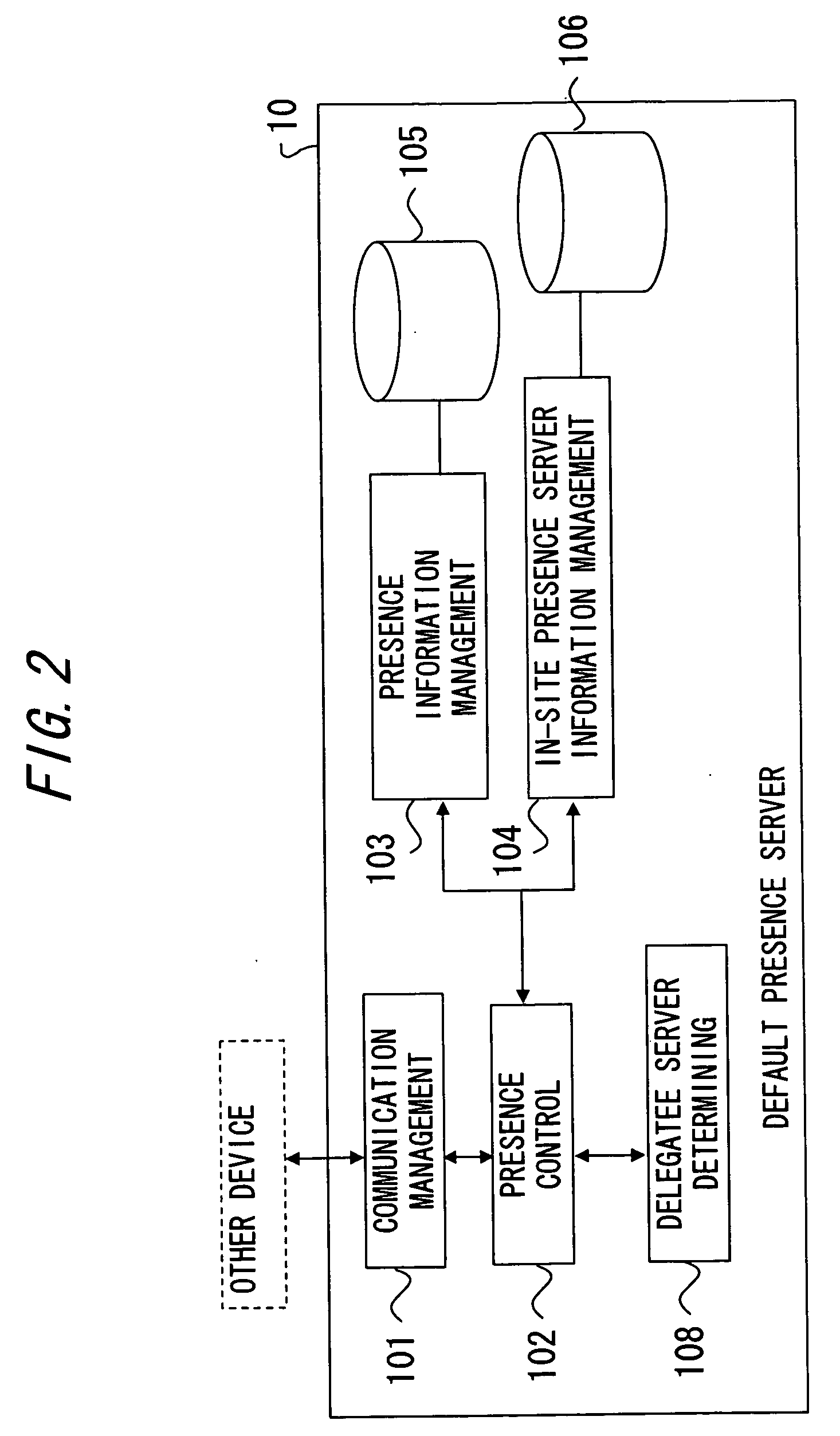
Presence information management system, presence server device, gateway device and client device
InactiveUS20080034078A1Restrain communication trafficAvoid trafficDigital computer detailsTransmissionClient-sideTraffic volume
The present invention provides a presence information management system, a presence server device, a gateway device and a client device, which notify of presence information in realtime while restraining communications traffic. The presence server device managing presence information of a plurality of presentities, comprises a delegating unit sending delegating notification of presence information management function related to at least one of the plurality of presentities, to another device becoming a delegatee of the presence information management function. The gateway device comprises a managing unit managing presence information of a presentity, and a control unit performing control so that, when receiving the delegating notification of the presence information management function about at least one of the plurality of presentities from a presence server, the managing unit is executed with respect to the function-delegated presentity.
Owner:FUJITSU LTD
Data communication system, backup server, and communication control apparatus
InactiveUS20050195818A1Prevent unnecessaryAvoid trafficData switching by path configurationClient-sideReal-time computing
In order to distribute multicast packets, using different multicast addresses and avoiding fault points, a backup server is installed close to a master and converts backup multicast packets and sends them as master multicast packets to the client. At this time, backup multicast packets are delayed and sent while the delay is determined from an allowable retransmission time, a one-direction delay to the client, a time required to detect linkage problems, and a time required to establish backup paths and so on.
Owner:KDDI CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com