Patents
Literature
1185 results about "Data Property" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
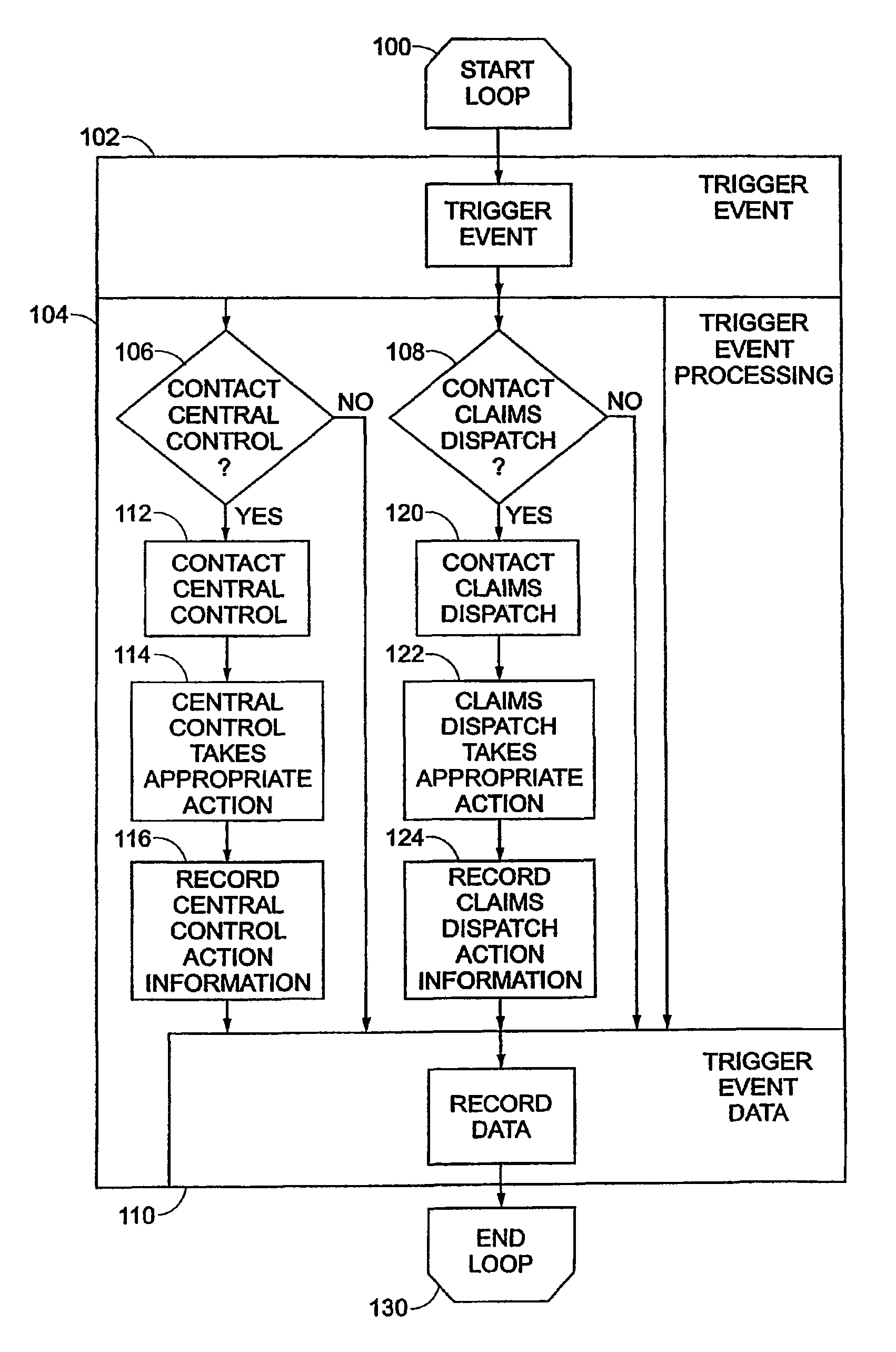
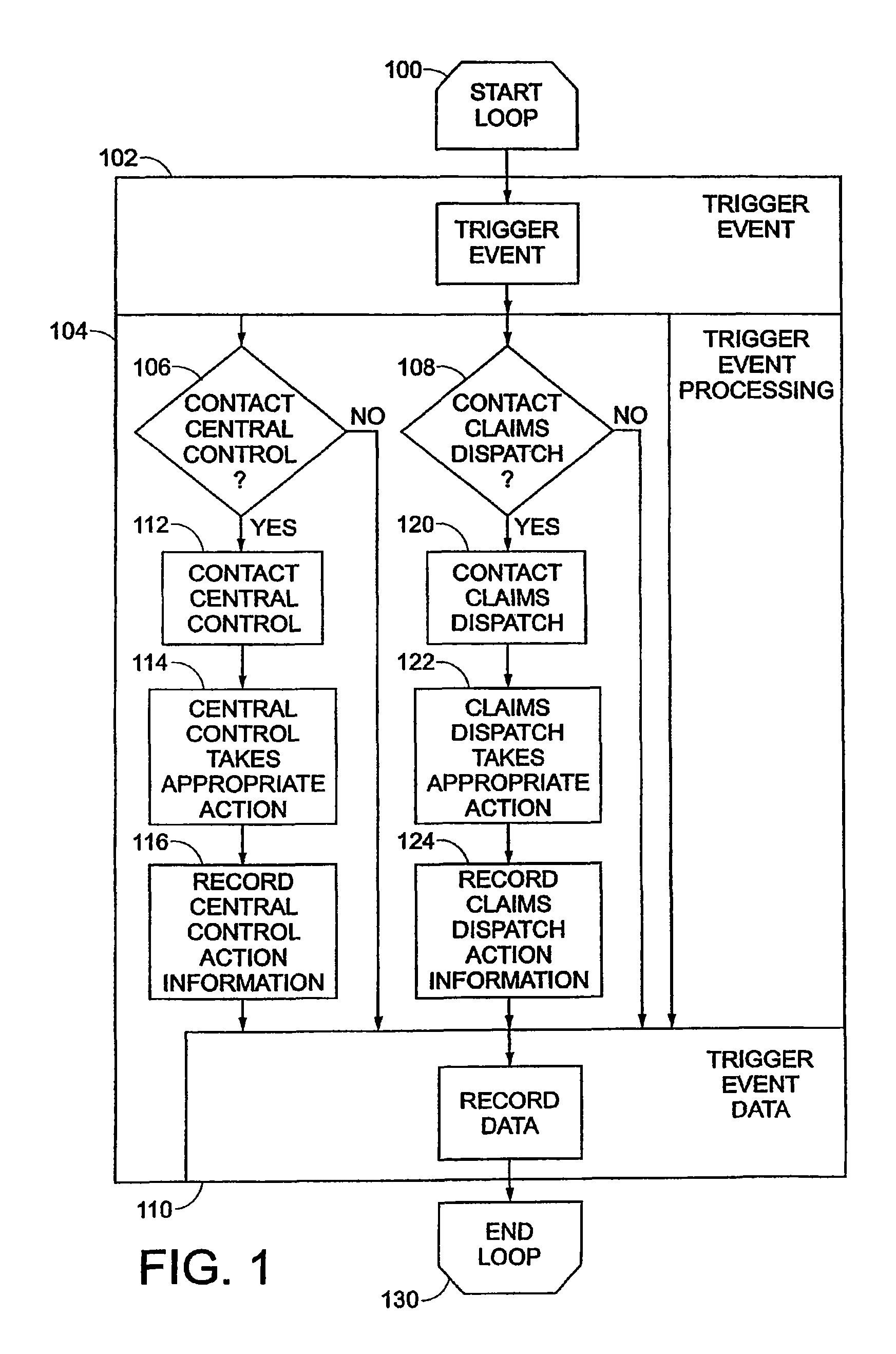
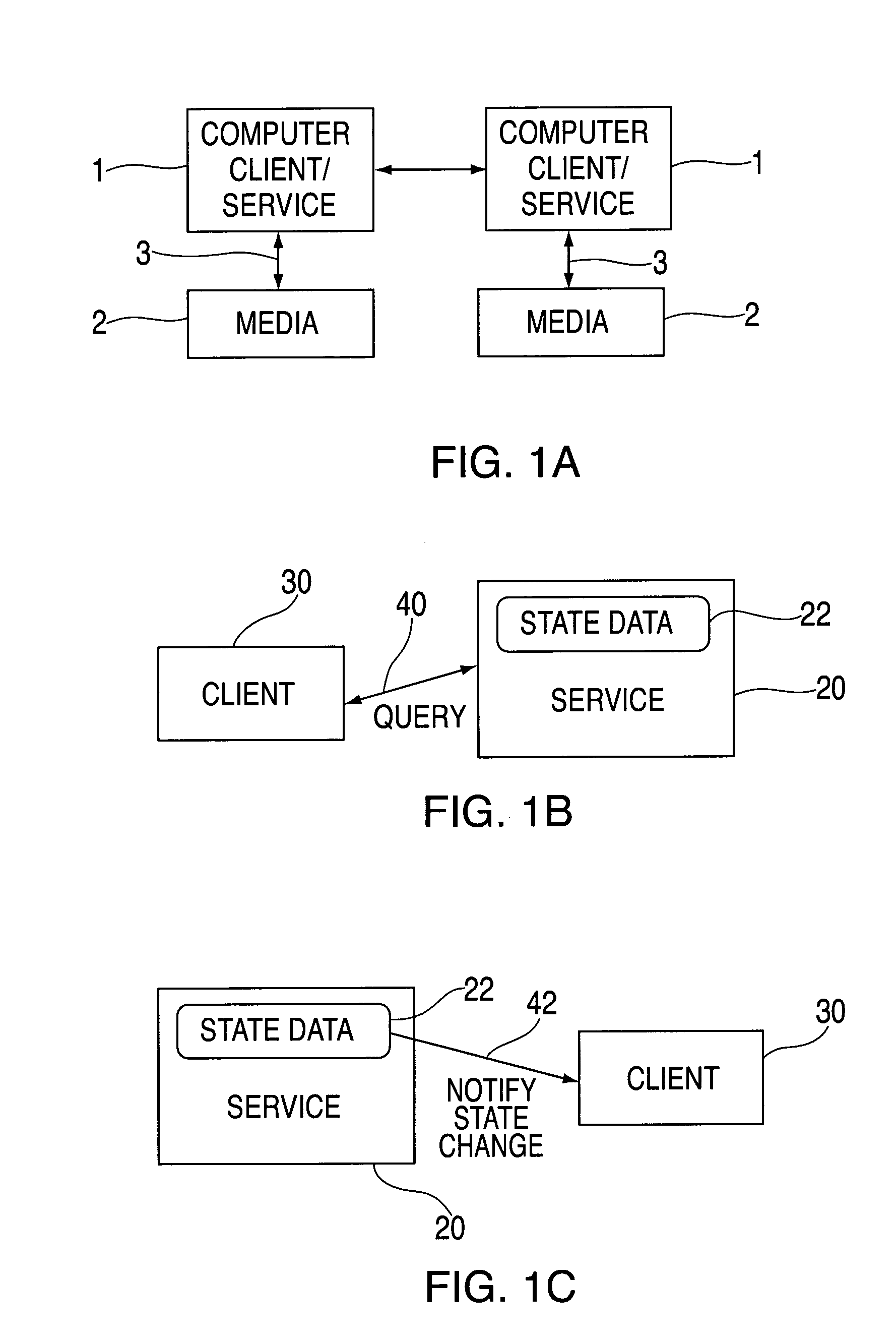
Vehicle monitoring system
InactiveUS8140358B1FinanceRegistering/indicating working of vehiclesDriver/operatorMonitoring system
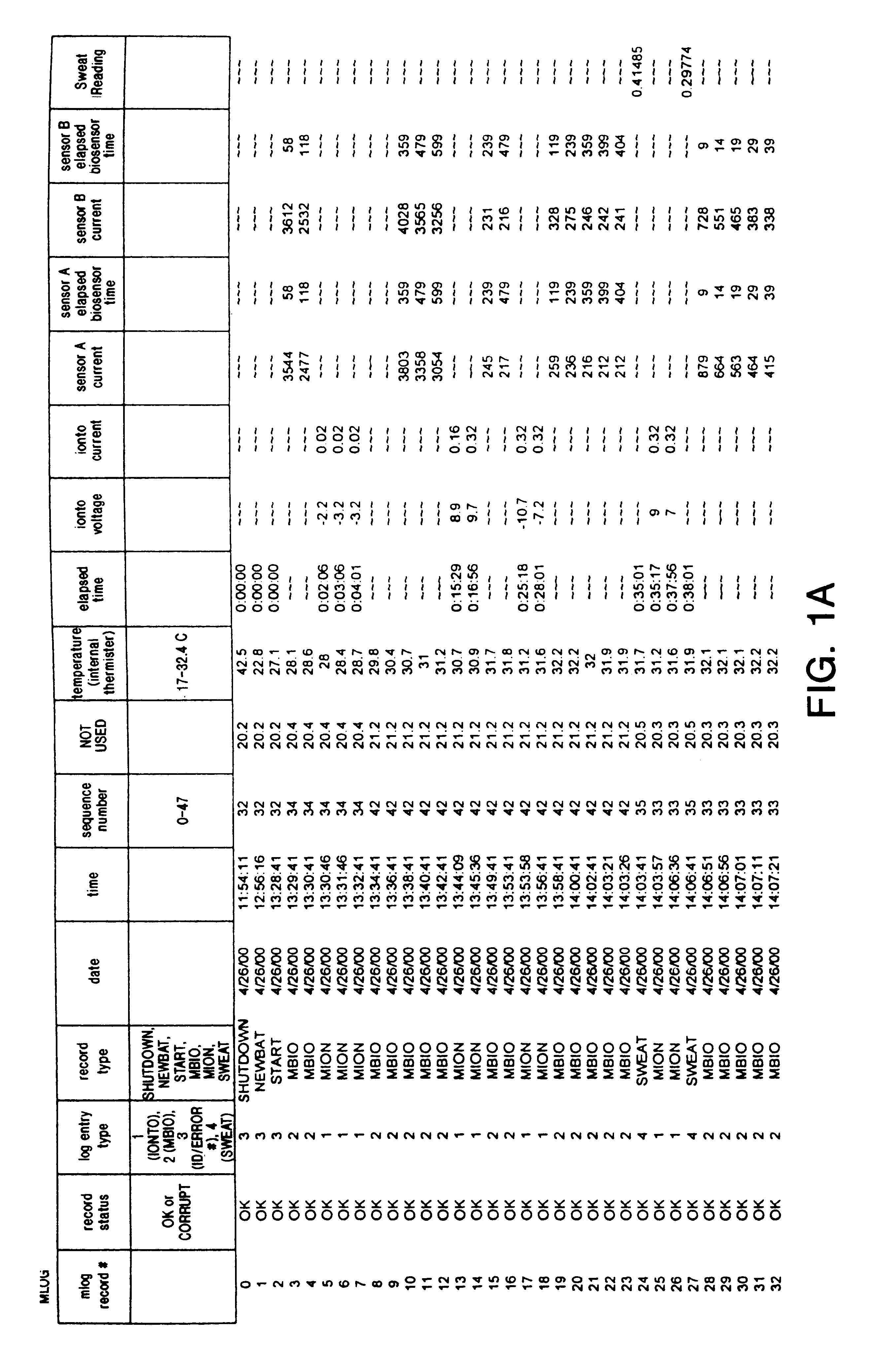
A data logging device tracks the operation of a vehicle or driver actions. The device includes a storage device, which may be removable or portable, having a first memory portion that may be read from and may be written to in a vehicle and a second memory portion that may be read from and may be written to in the vehicle. The second memory portion may retain data attributes associated with the data stored in the first removable storage device. A processor reads data from an automotive bus that transfers data from vehicle sensors to other automotive components. The processor writes data to the first memory portion and the second memory portion that reflect a level of risk or safety. A communication device links the storage device to a network of computers. The communication device may be accessible through software that allows a user to access files related to a level of risk or safety and other software that may be related to those files.
Owner:PROGRESSIVE CASUALTY INSURANCE
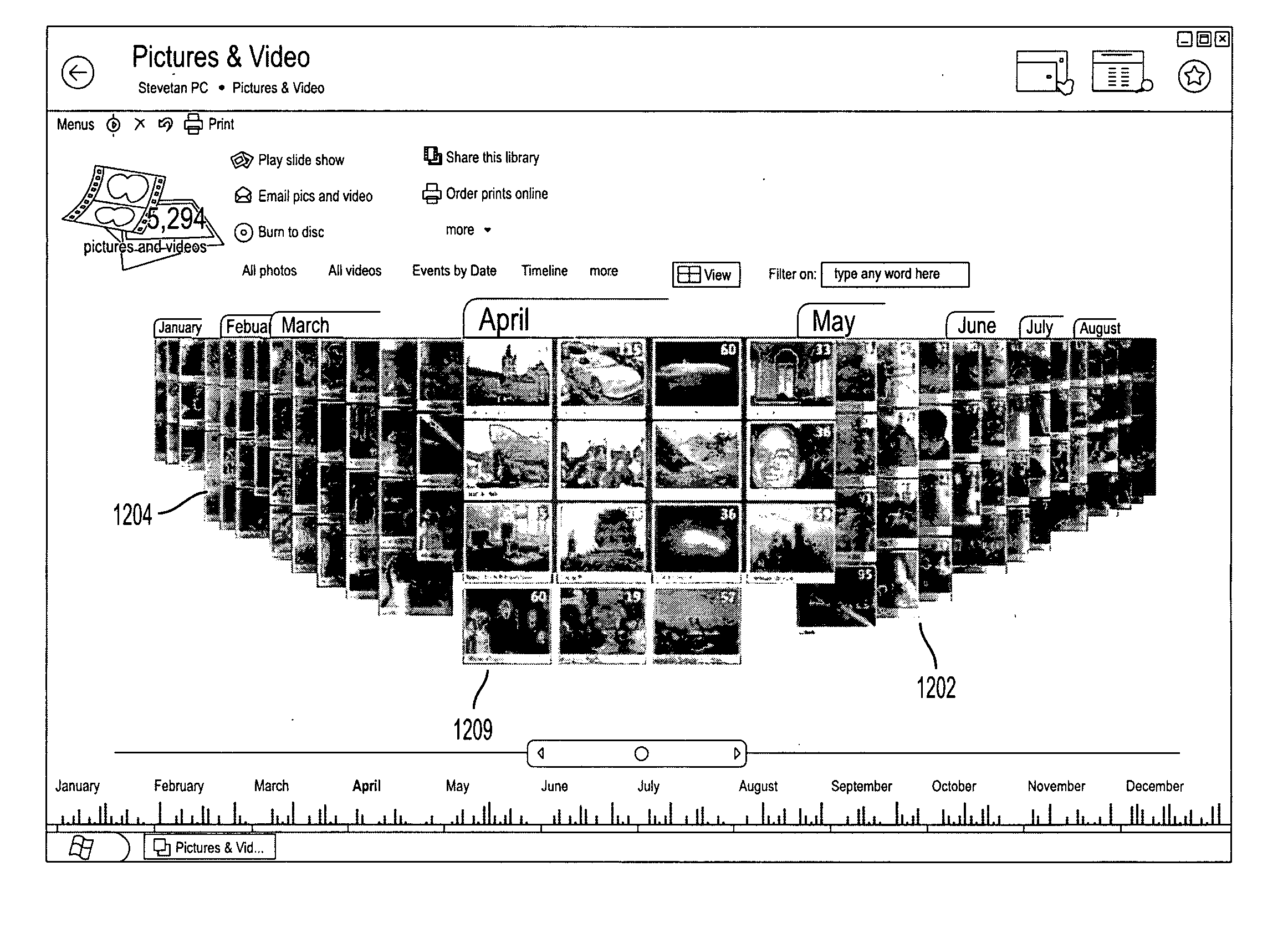
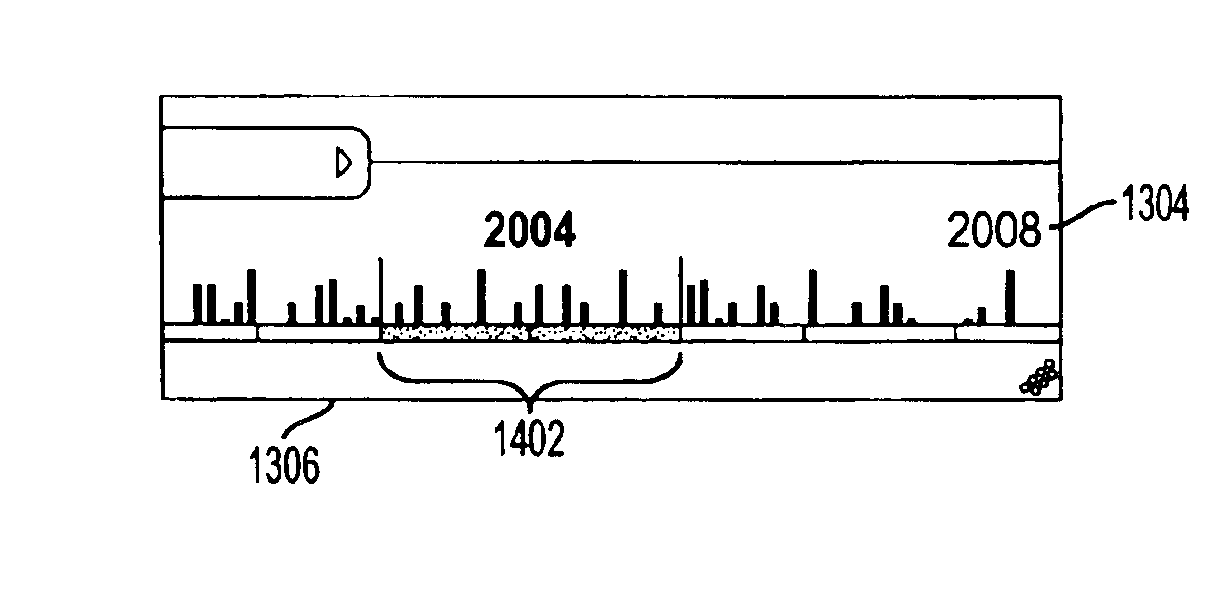
Graphical user interface for 3-dimensional view of a data collection based on an attribute of the data
A three-dimensional (3D) view of a data collection based on an attribute is disclosed. A timeline is provided for displaying files and folders. The timeline may include a focal group that displays detailed information about its contents to the user. Remaining items on the timeline are displayed in less detail and may be positioned to appear further away from the user. A histogram may be provided as part of the view to allow the user to more easily navigate the timeline to find a desired file or folder.
Owner:MICROSOFT TECH LICENSING LLC
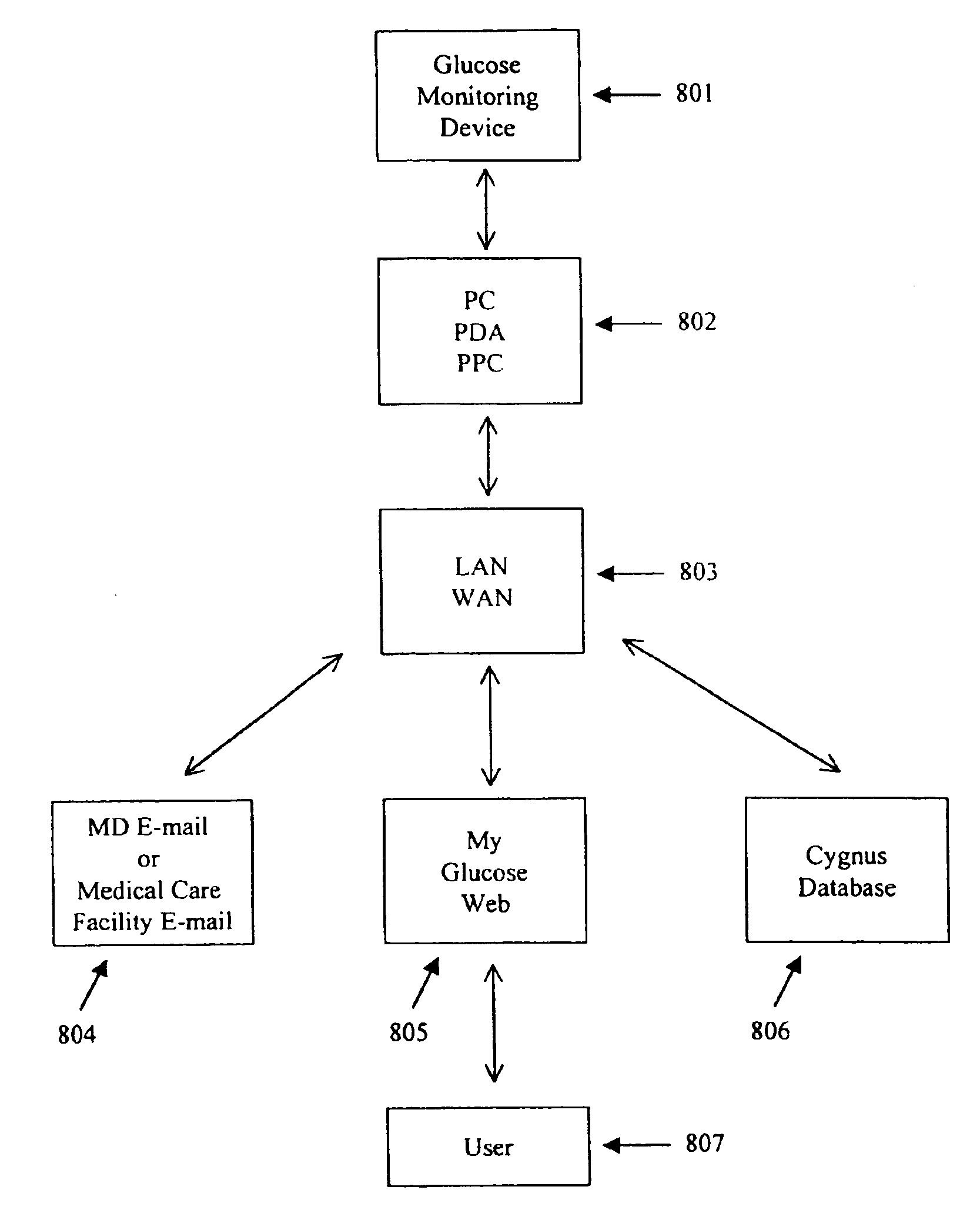
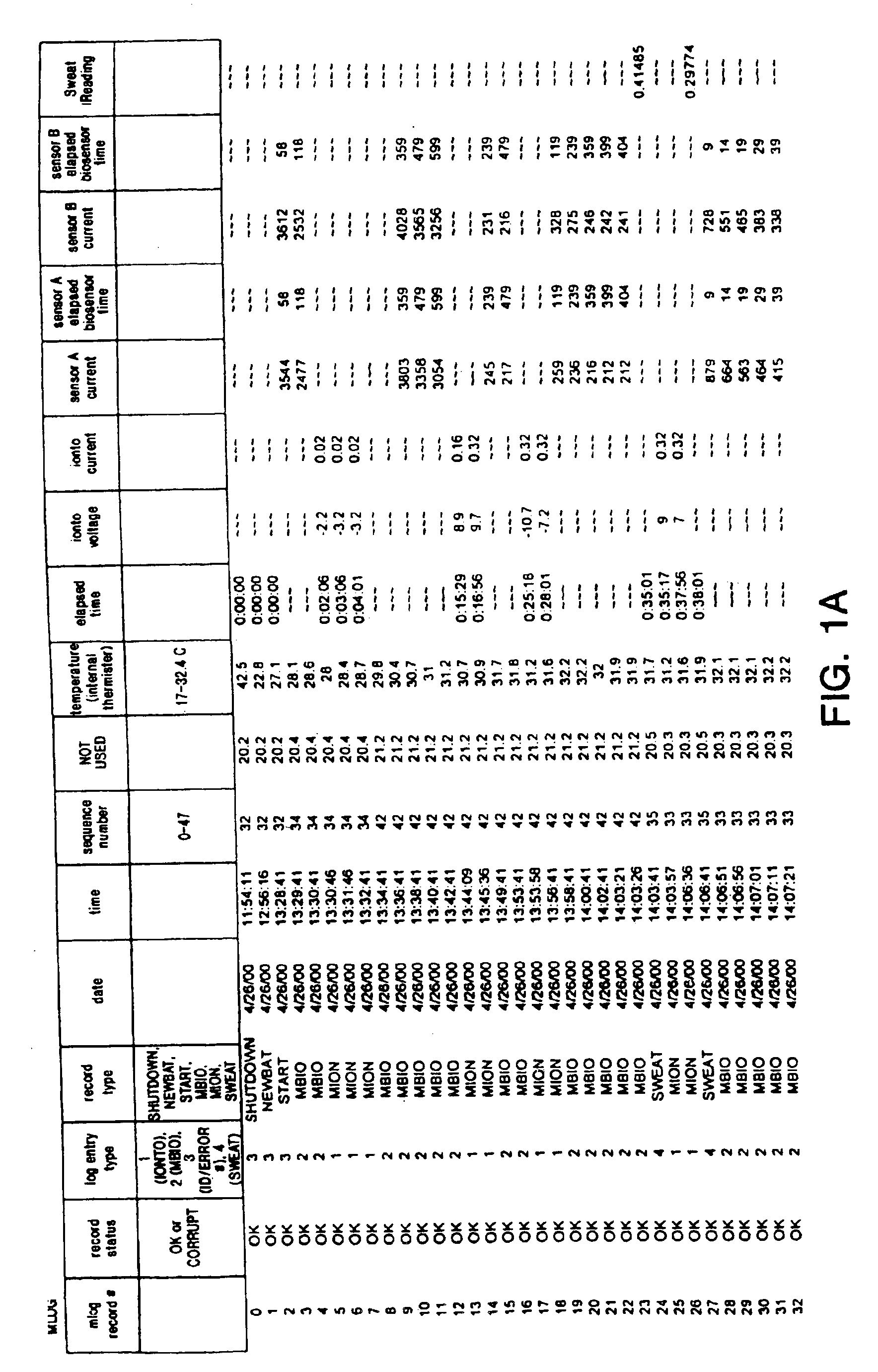
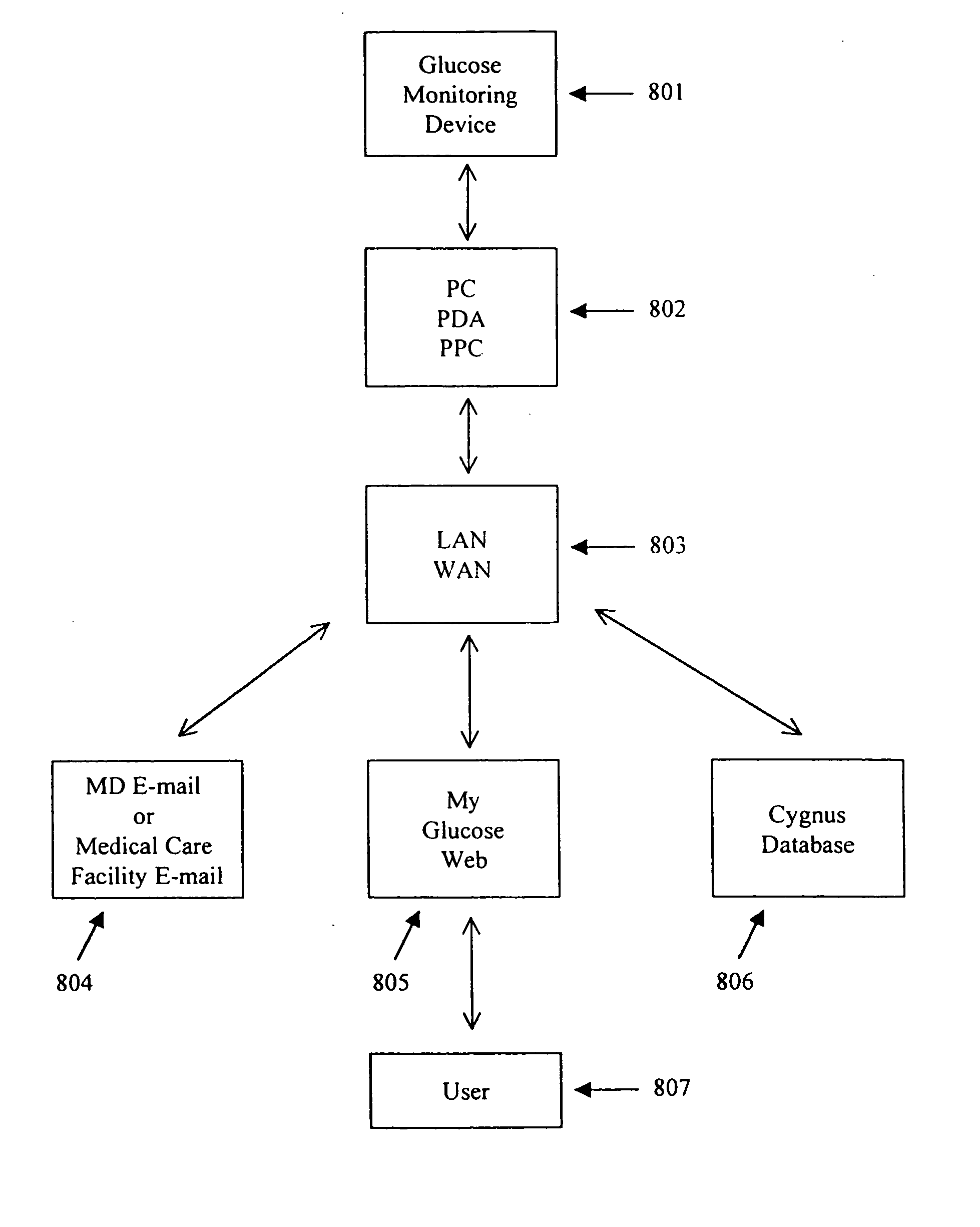
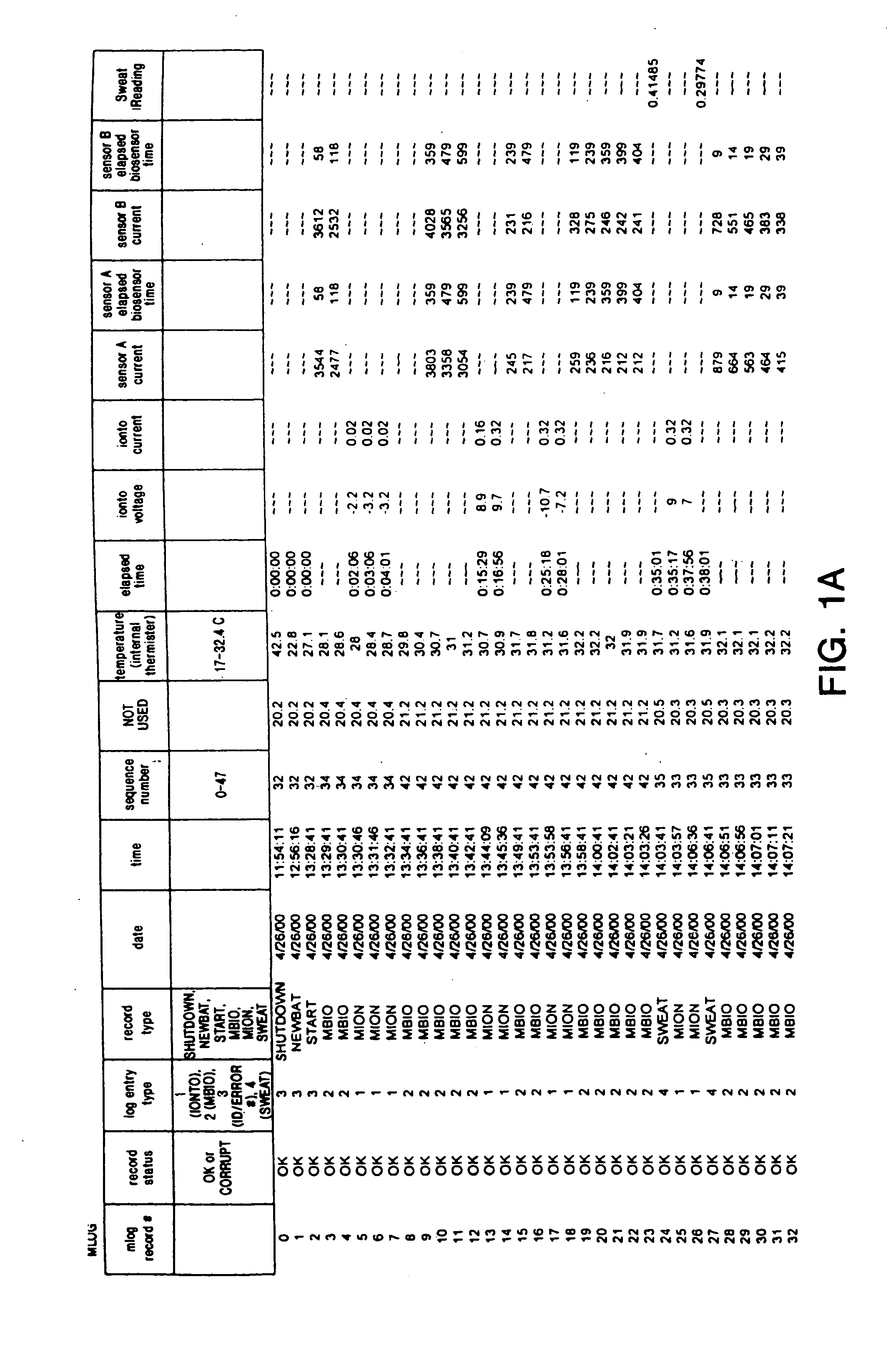
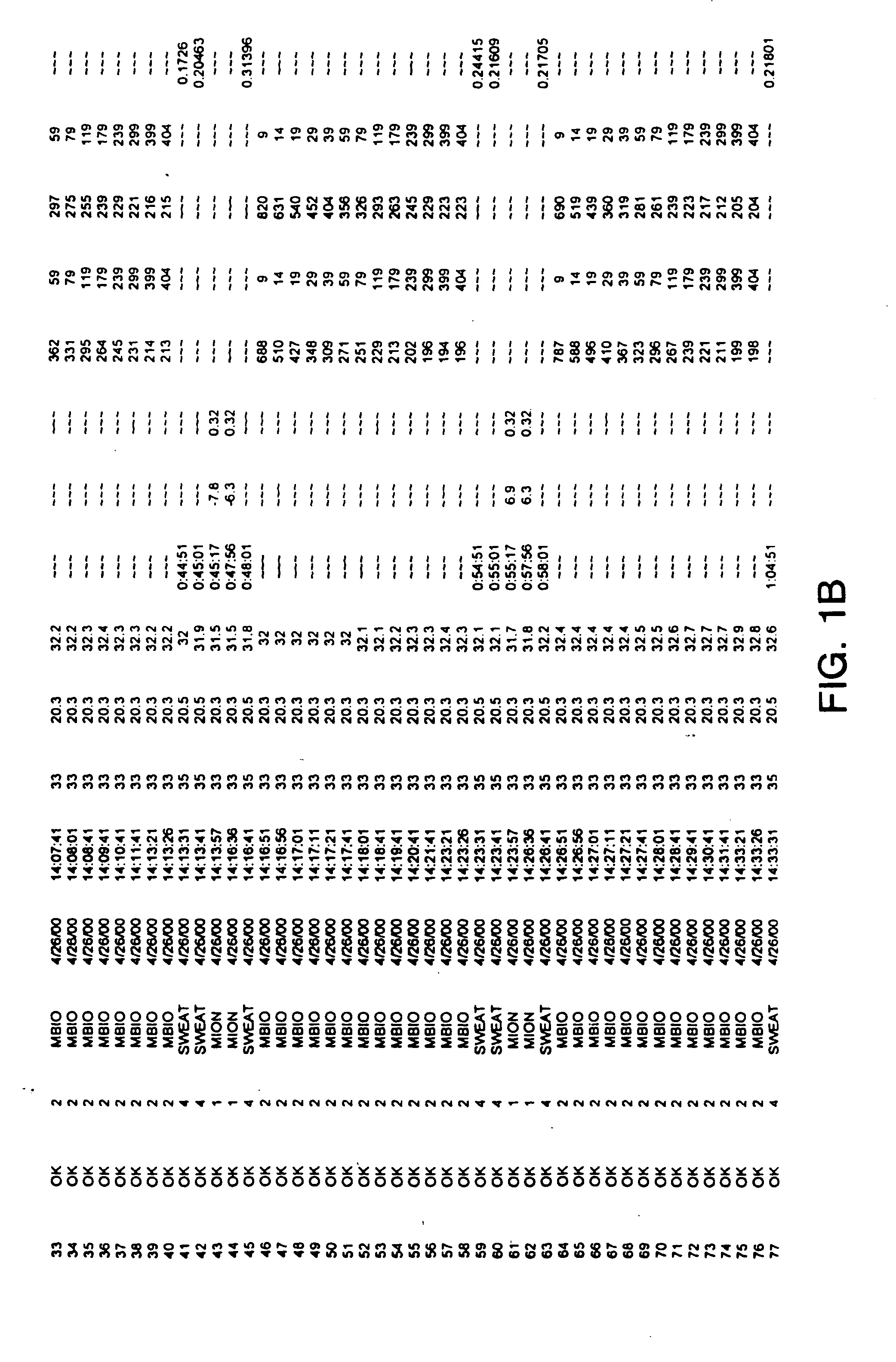
Formulation and manipulation of databases of analyte and associated values
The present invention relates to methods of formulating analyte data databases, the databases themselves, and methods of manipulating the same. In one aspect the present invention includes the formulation of analyte data points, derived data, and data attributes databases comprising data points collected using an analyte monitoring device capable of frequent monitoring of analyte concentrations or amounts. Such data points may comprise acquired data (e.g., values corresponding to analyte concentrations or amounts as measured by said analyte monitoring device). These data points are then associated with one or more relevant data attributes. The resulting databases may be manipulated to determine relationships among the components of the database.
Owner:ANIMAS TECH +1
Vehicle monitoring system
InactiveUS20120209634A1Vehicle testingUnauthorised/fraudulent call preventionMonitoring systemRemovable media
A data logging device tracks the operation of a vehicle or driver actions. The device includes a storage device, which may be removable or portable, having a first memory portion that may be read from and may be written to in a vehicle and a second memory portion that may be read from and may be written to in the vehicle. The second memory portion may retain data attributes associated with the data stored in the first removable storage device. A processor reads data from an automotive bus that transfers data from vehicle sensors to other automotive components. The processor writes data to the first memory portion and the second memory portion that reflect a level of risk or safety. A communication device links the storage device to a network of computers. The communication device may be accessible through software that allows a user to access files.
Owner:PROGRESSIVE CASUALTY INSURANCE
Formulation and manipulation of databases of analyte and associated values
The present invention relates to methods of formulating analyte data databases, the databases themselves, and methods of manipulating the same. In one aspect the present invention includes the formulation of analyte data points, derived data, and data attributes databases comprising data points collected using an analyte monitoring device capable of frequent monitoring of analyte concentrations or amounts. Such data points may comprise acquired data (e.g., values corresponding to analyte concentrations or amounts as measured by said analyte monitoring device). These data points are then associated with one or more relevant data attributes. The resulting databases may be manipulated to determine relationships among the components of the database.
Owner:ANIMAS TECH +1
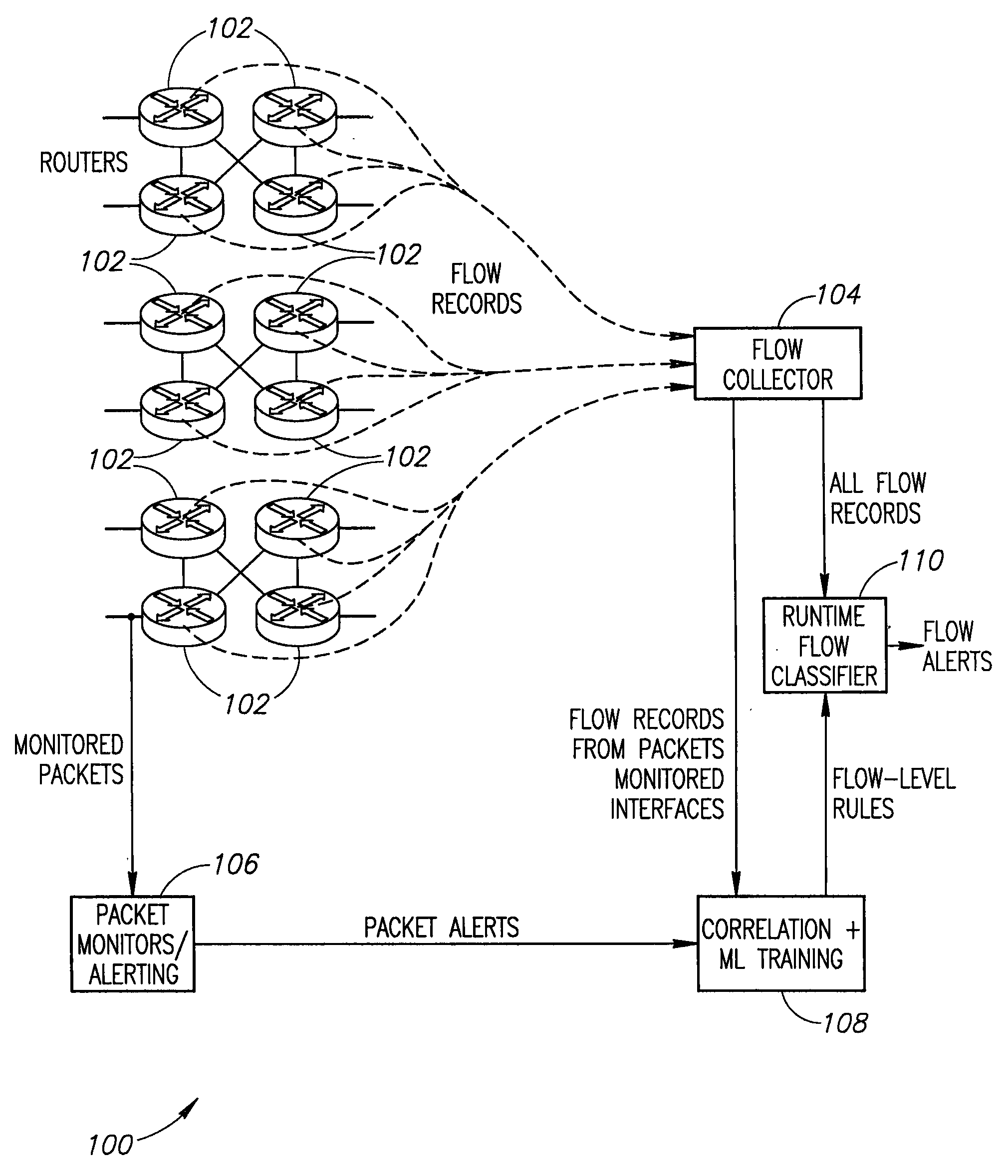
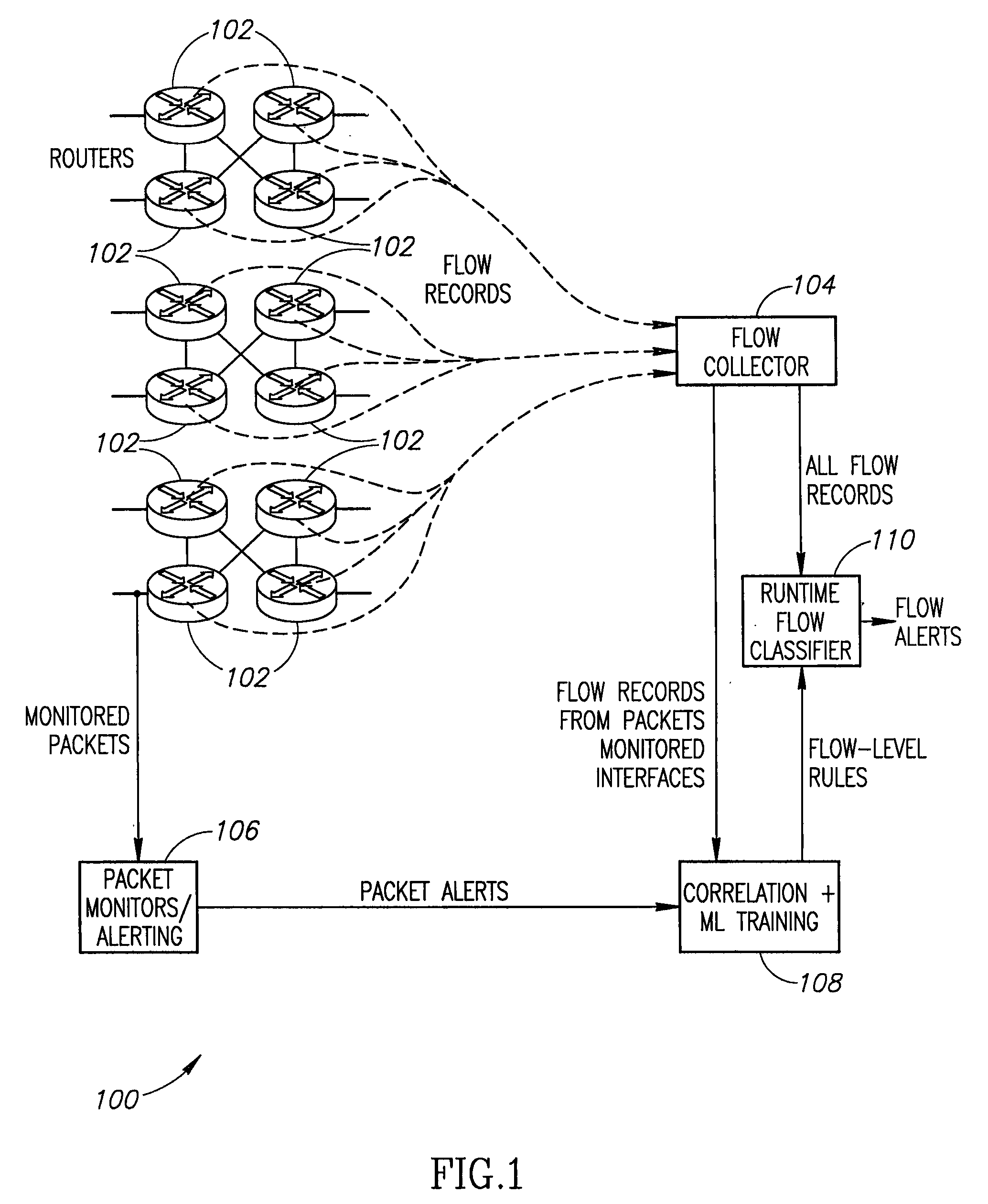
Systems and methods for rule-based anomaly detection on IP network flow
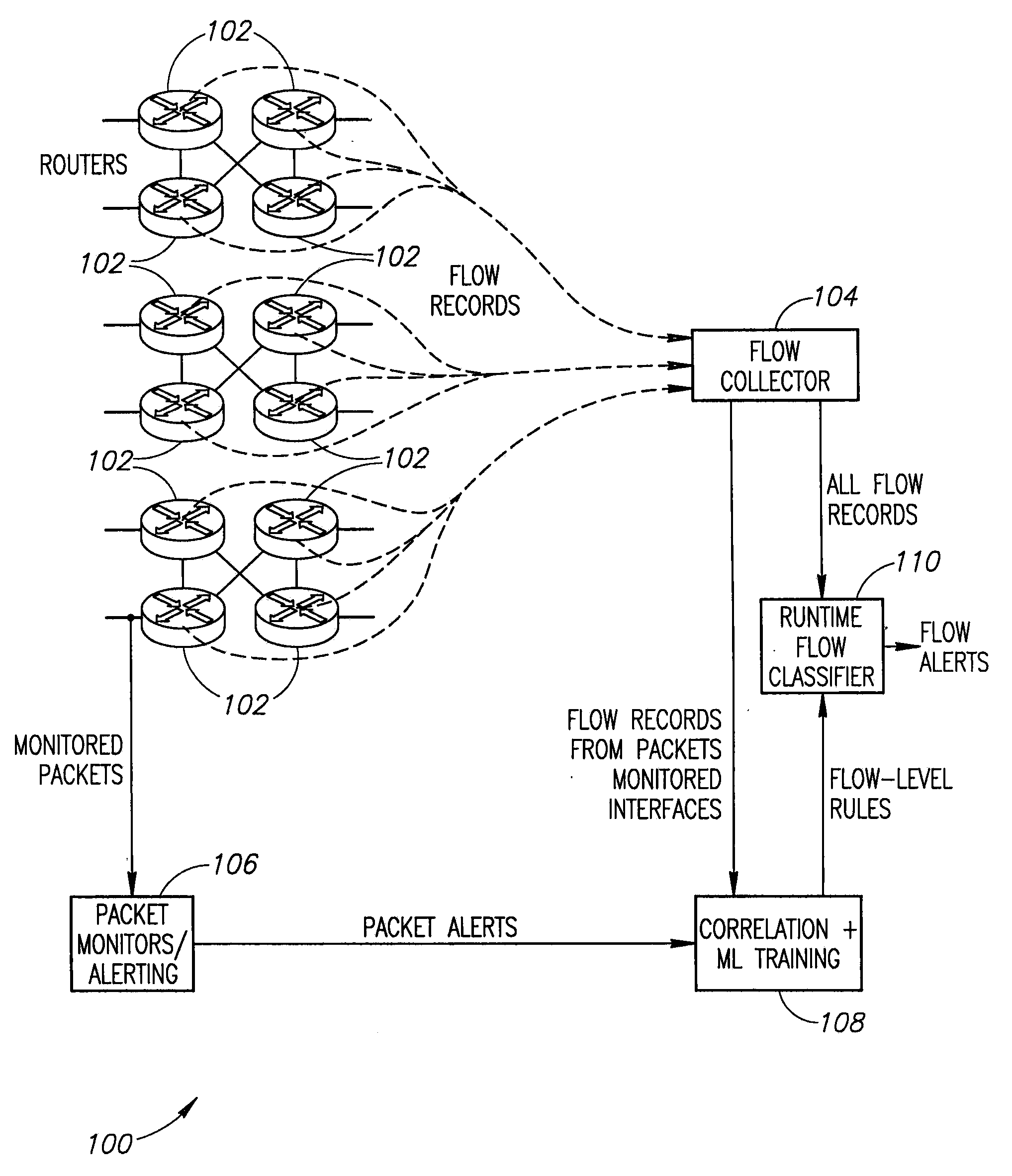
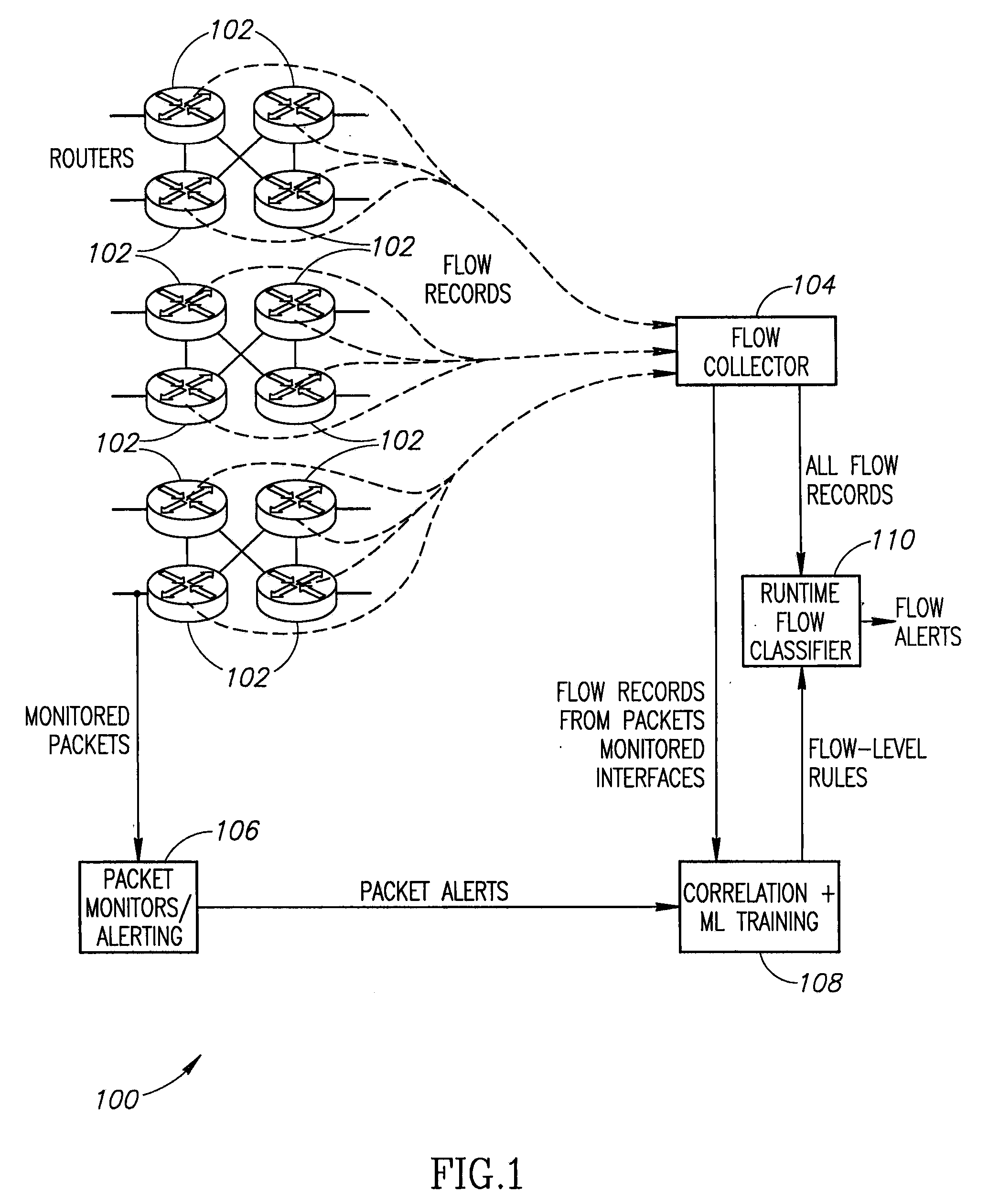
A system to detect anomalies in internet protocol (IP) flows uses a set of machine-learning (ML) rules that can be applied in real time at the IP flow level. A communication network has a large number of routers that can be equipped with flow monitoring capability. A flow collector collects flow data from the routers throughout the communication network and provides them to a flow classifier. At the same time, a limited number of locations in the network monitor data packets and generate alerts based on packet data properties. The packet alerts and the flow data are provided to a machine learning system that detects correlations between the packet-based alerts and the flow data to thereby generate a series of flow-level alerts. These rules are provided to the flow time classifier. Over time, the new packet alerts and flow data are used to provide updated rules generated by the machine learning system.
Owner:AT&T INTPROP I L P
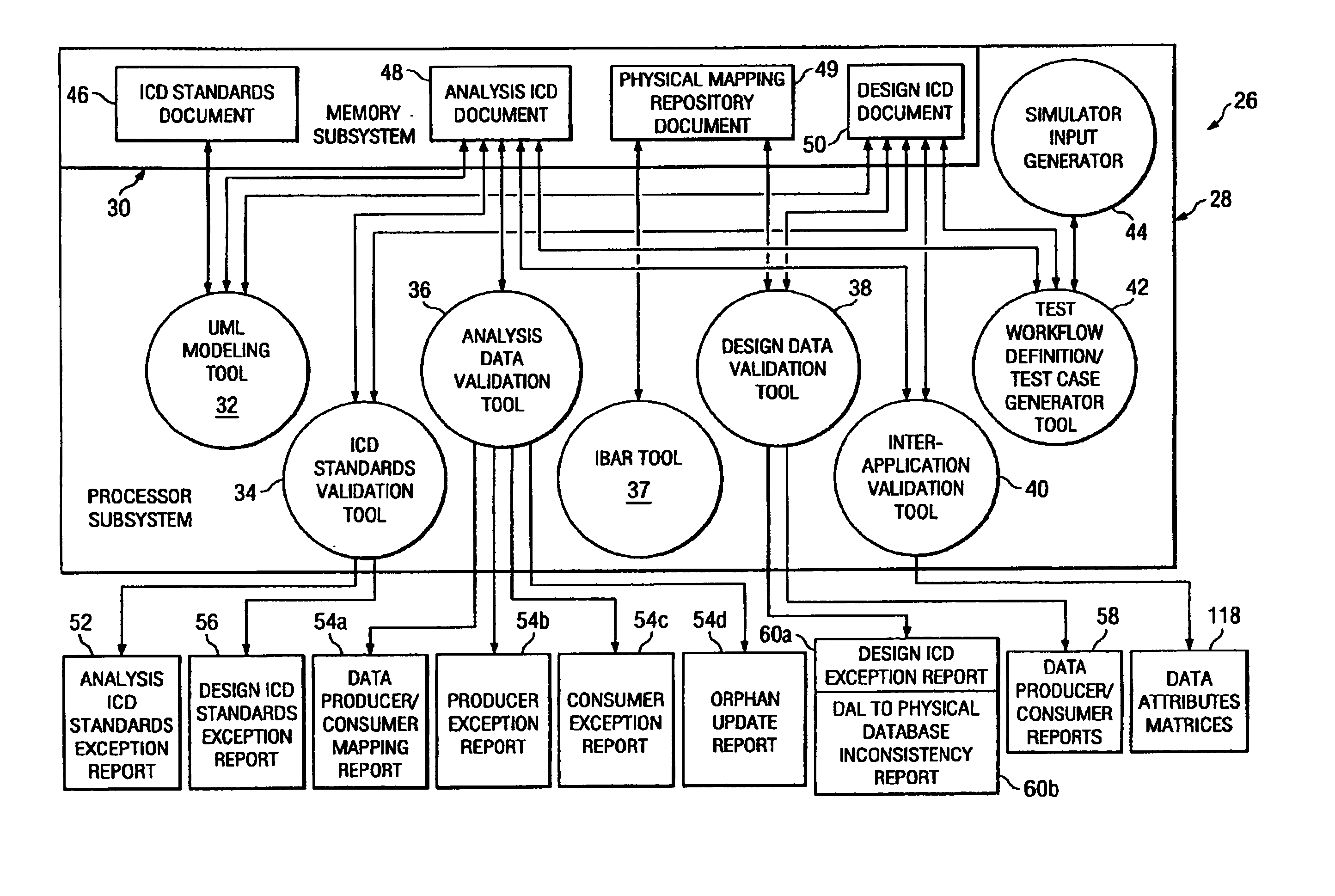
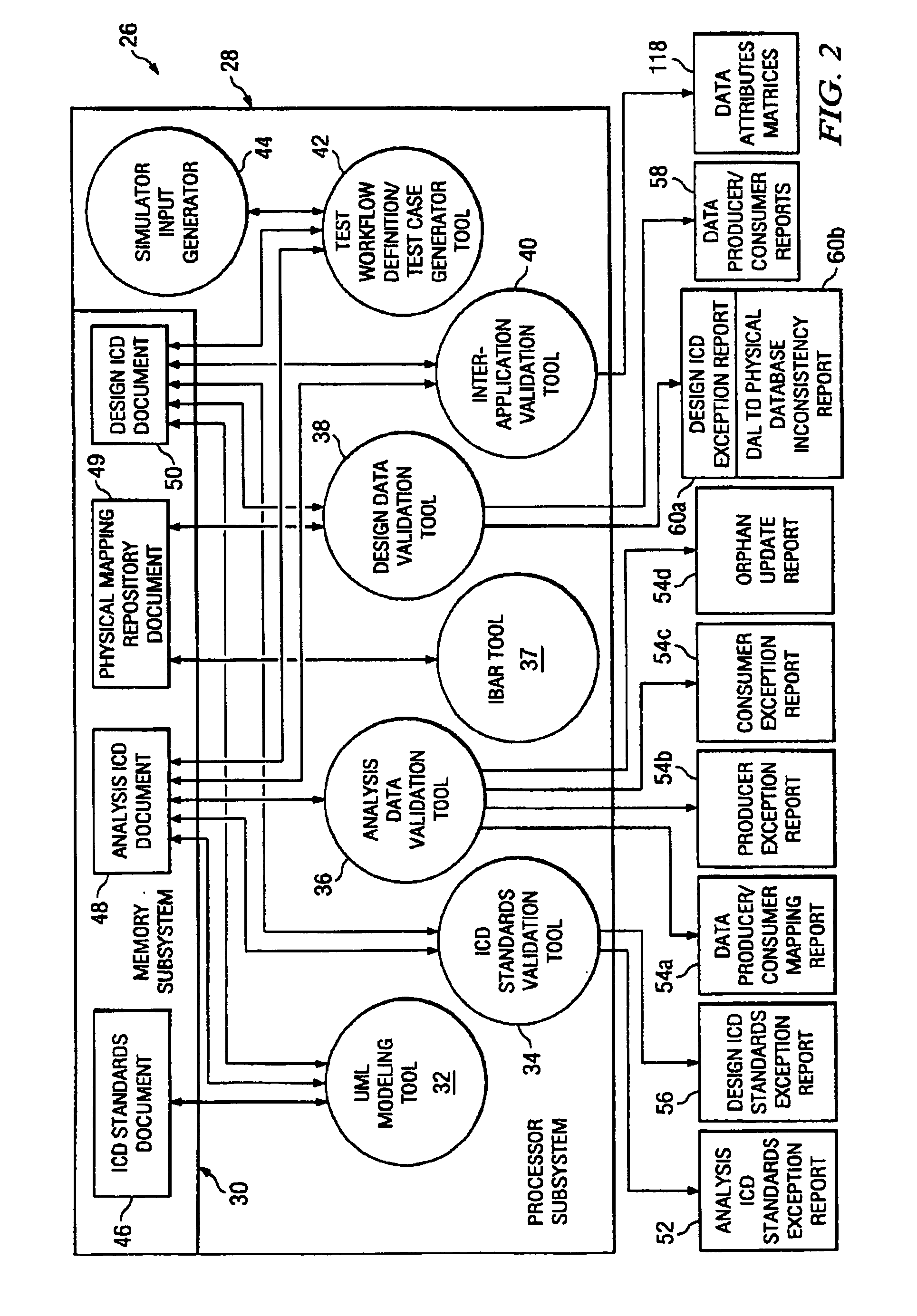
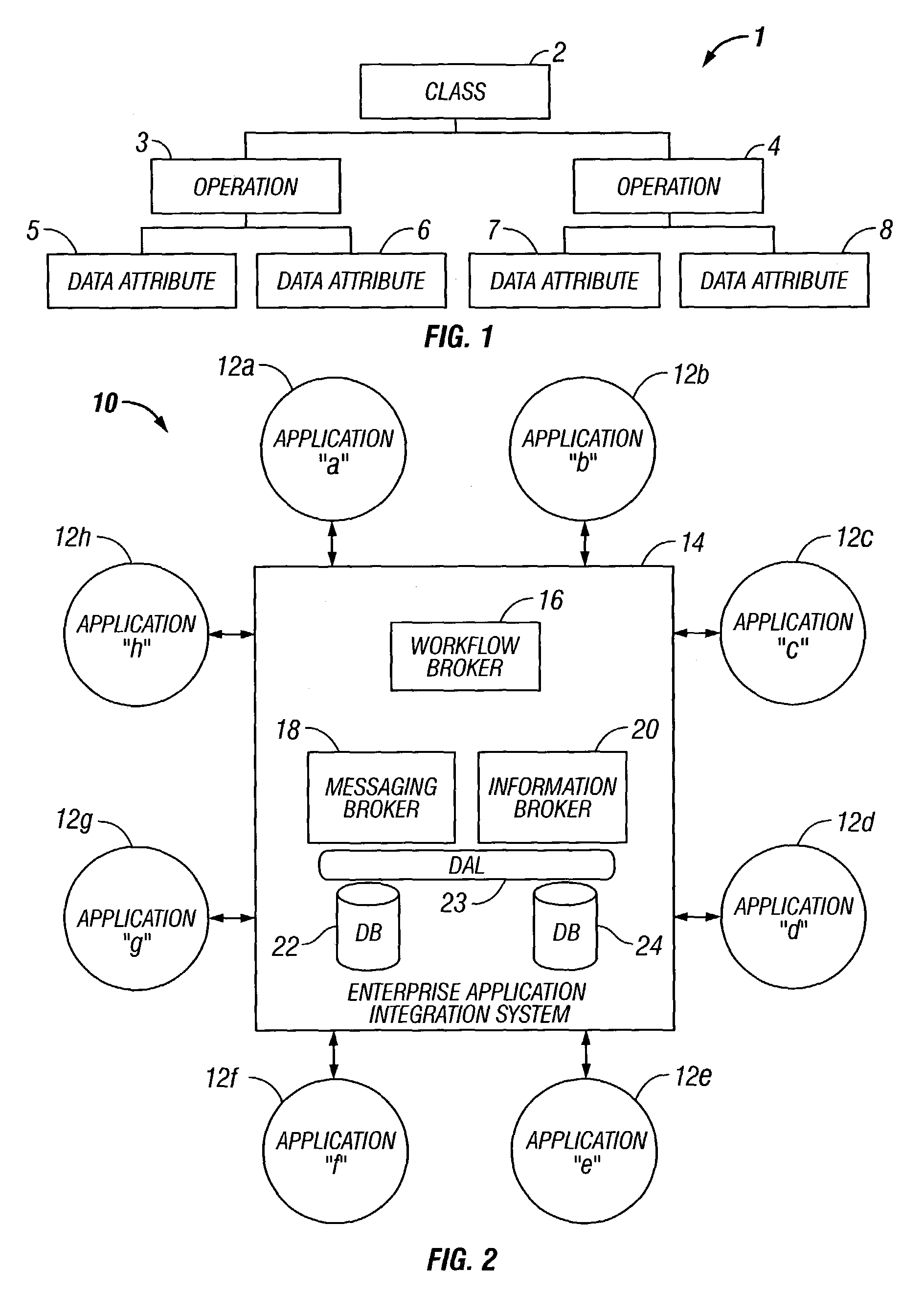
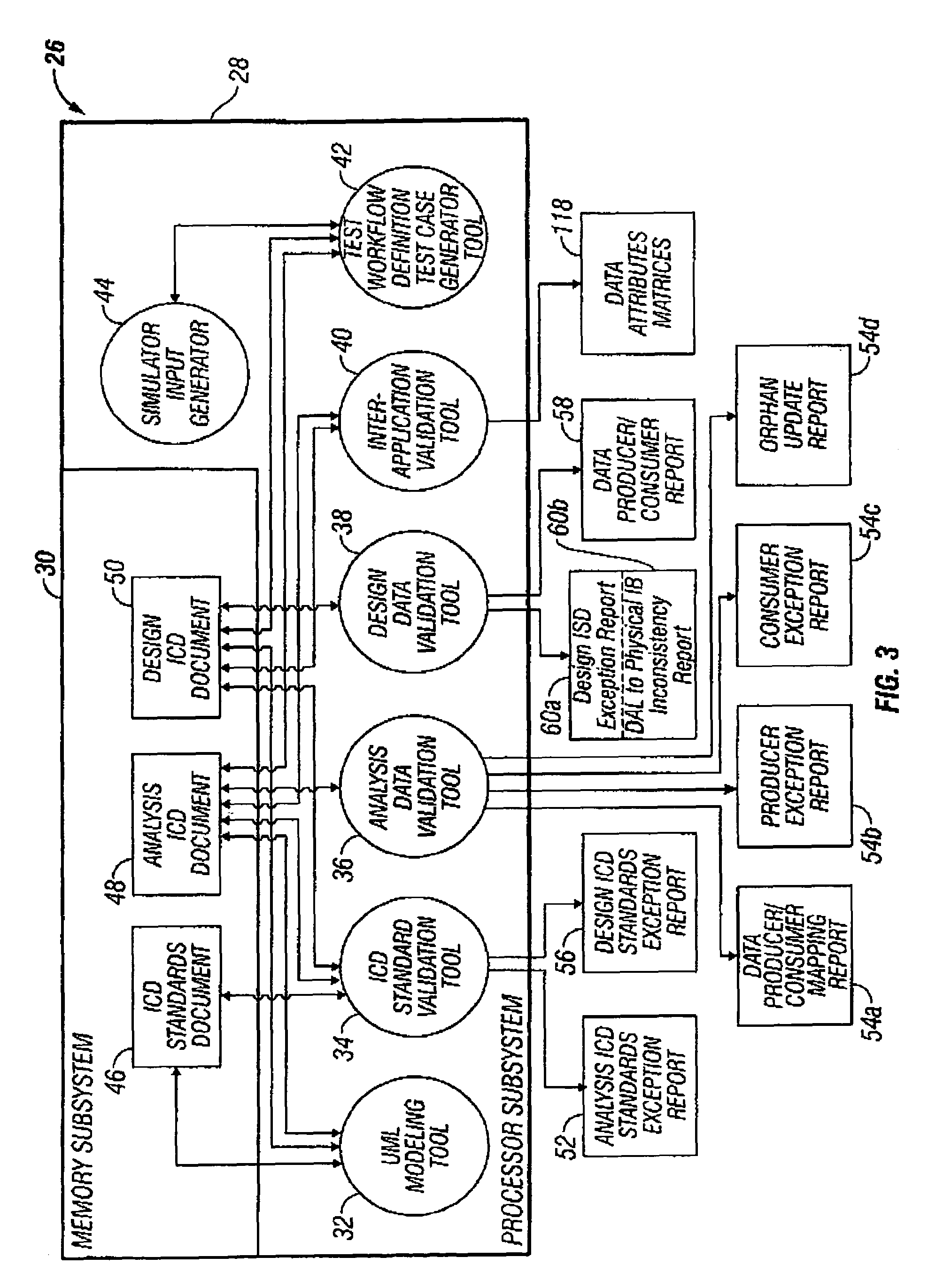
Design data validation tool for use in enterprise architecture modeling
InactiveUS7203929B1Requirement analysisSpecific program execution arrangementsData validationSequence diagram
A selected scenario of a design ICD document for an integrated enterprise is validated by examining each IDL call of each sequence diagram forming part of the selected scenario. A list of data attributes contained in one or more of the IDL calls are generated and each IDL call associated therewith is generated. A physical location to which each such IDL call is mapped is then associated with the IDL call. By analyzing the IDL calls and associated physical locations on a data attribute-by-data attribute basis, inconsistencies in the physical mapping of the data attributes to the databases forming an IIS for the integrated enterprise may be identified and subsequently corrected.
Owner:SPRINT CORPORATION
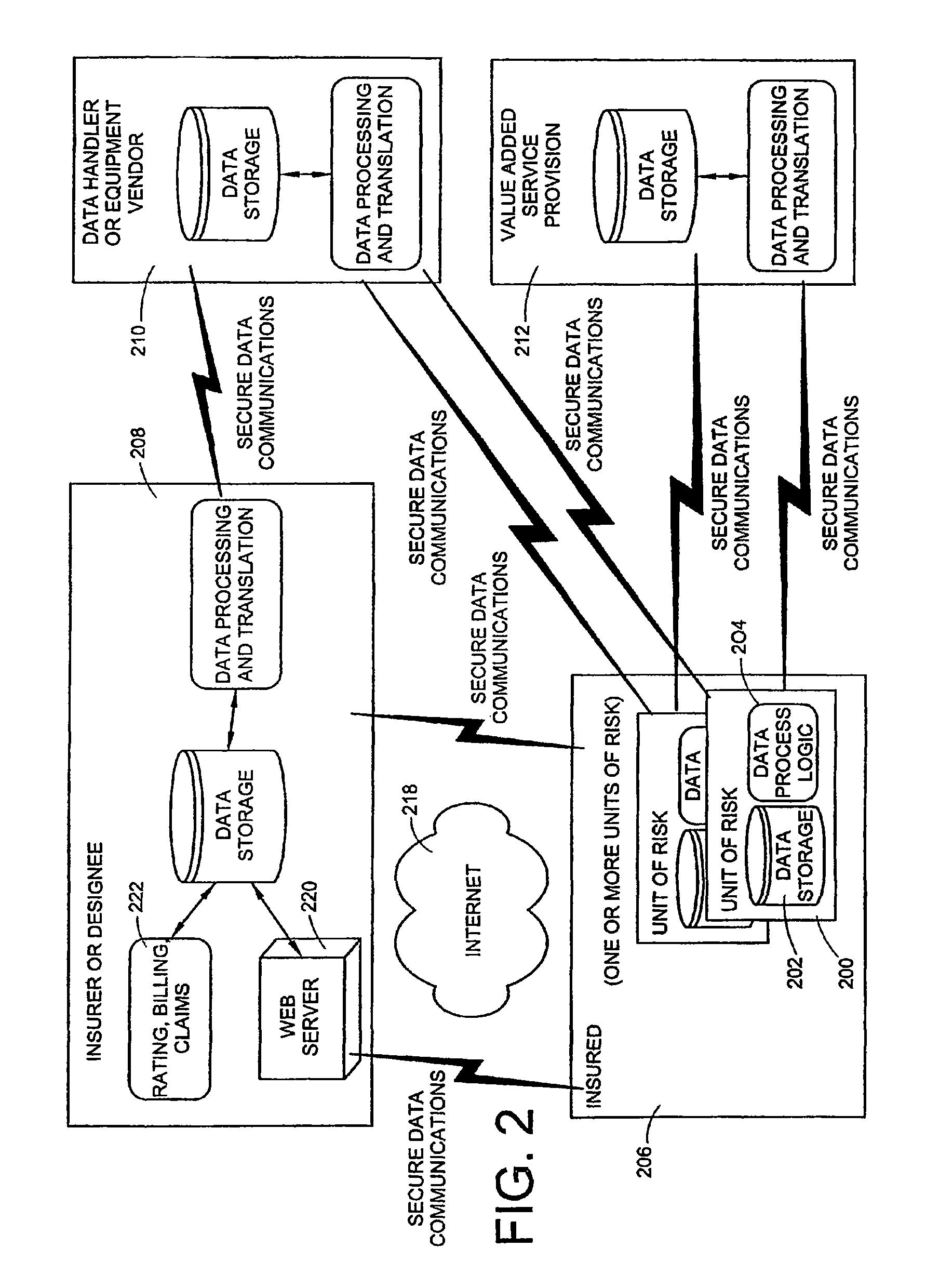
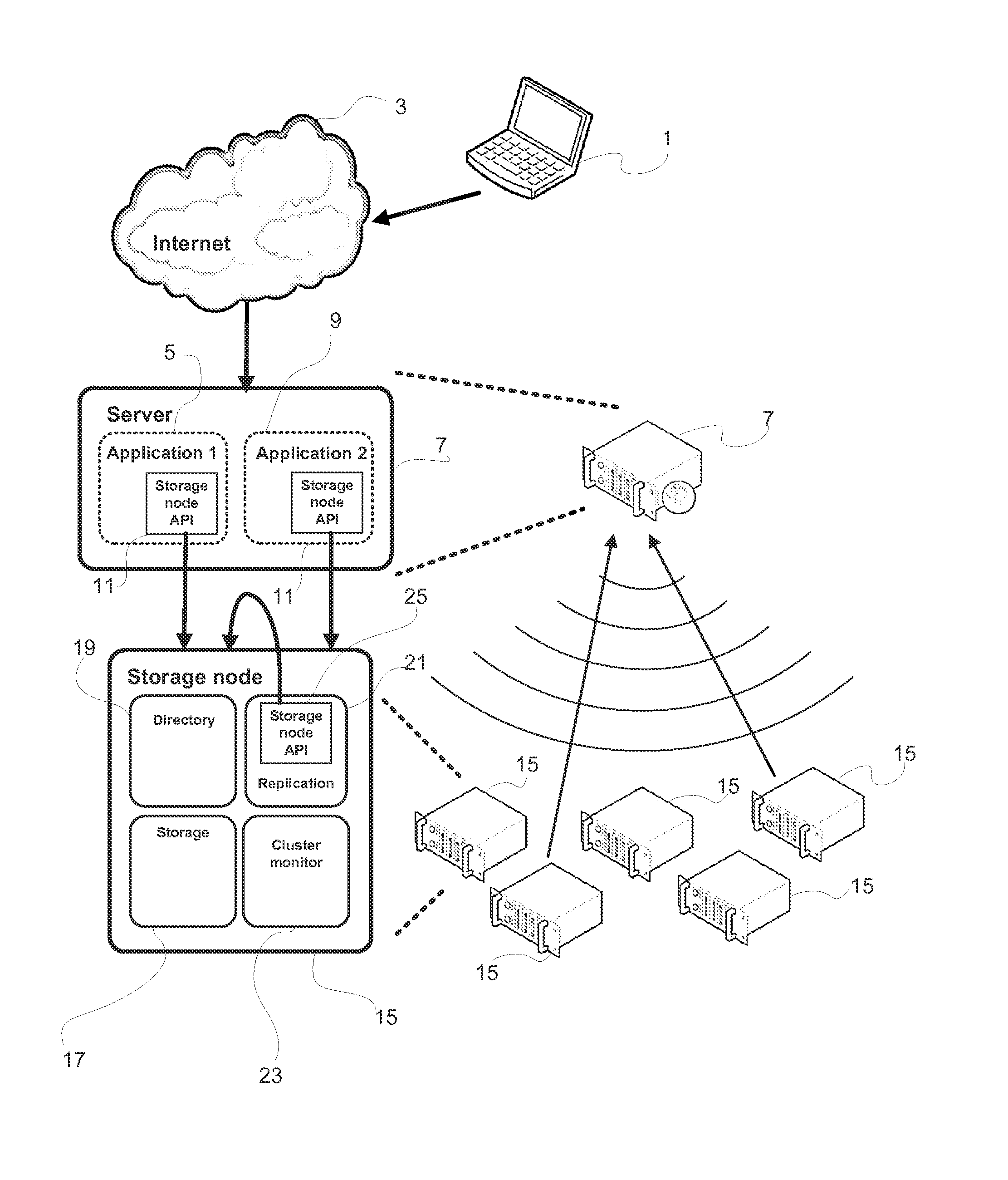
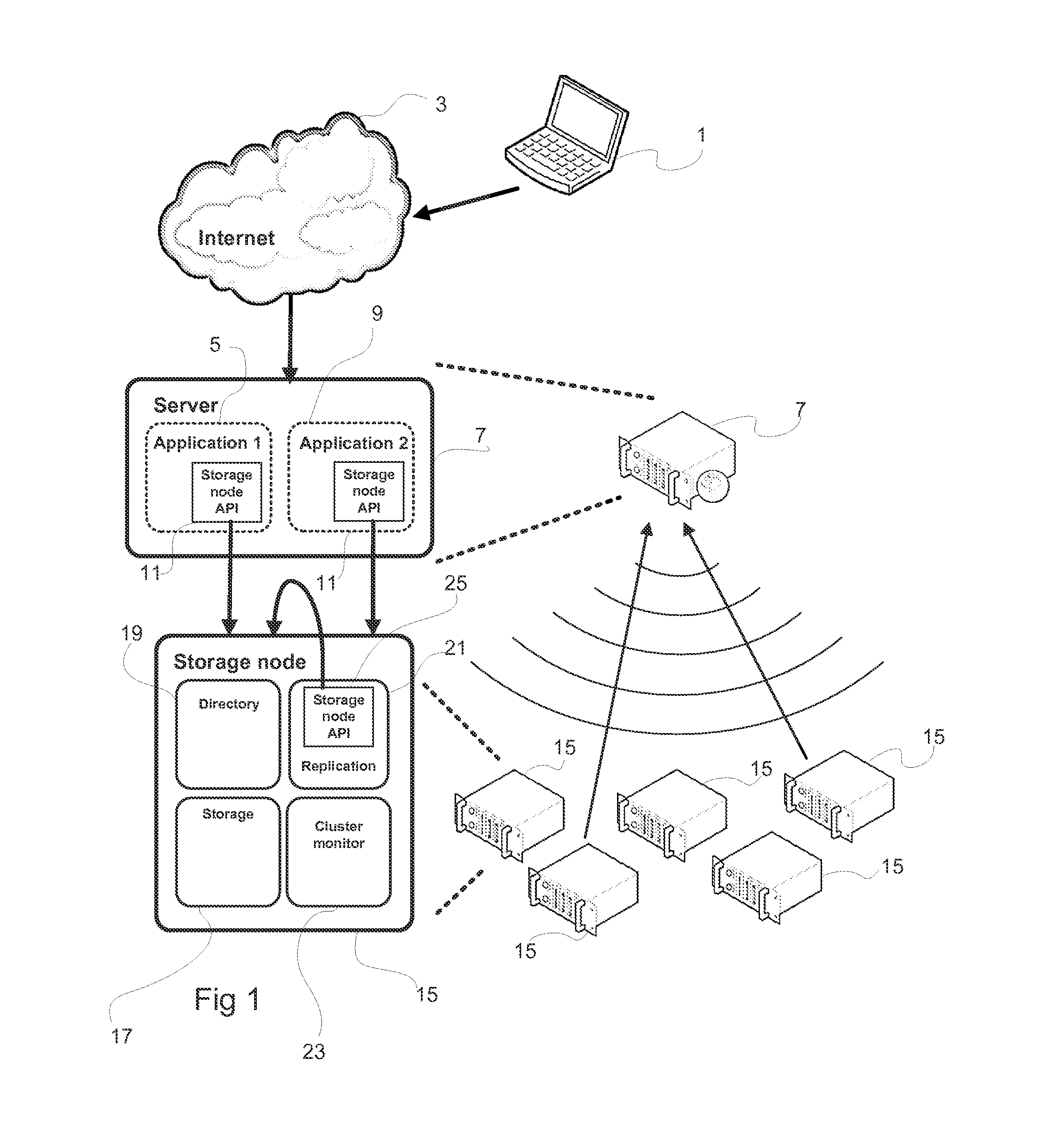
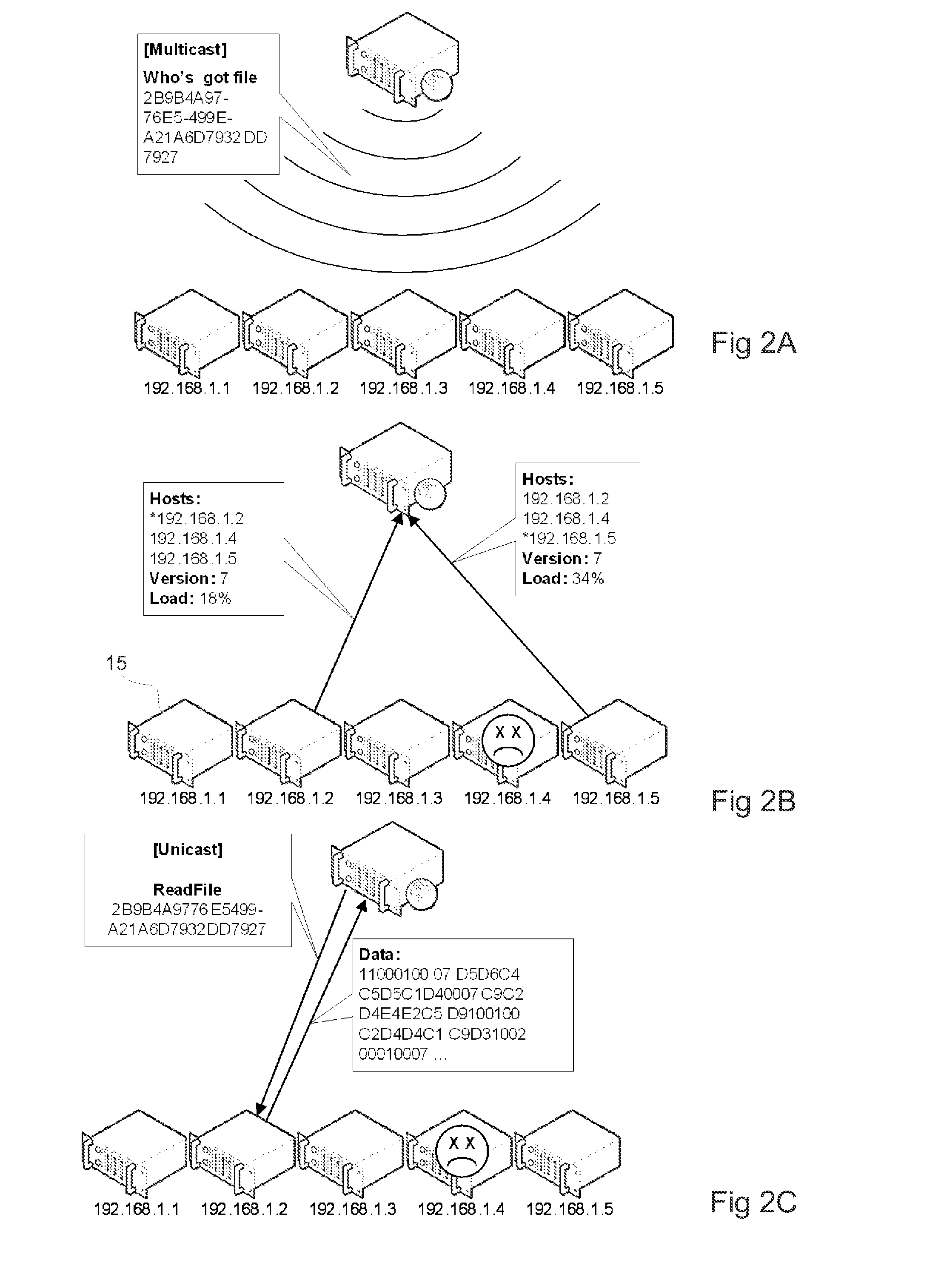
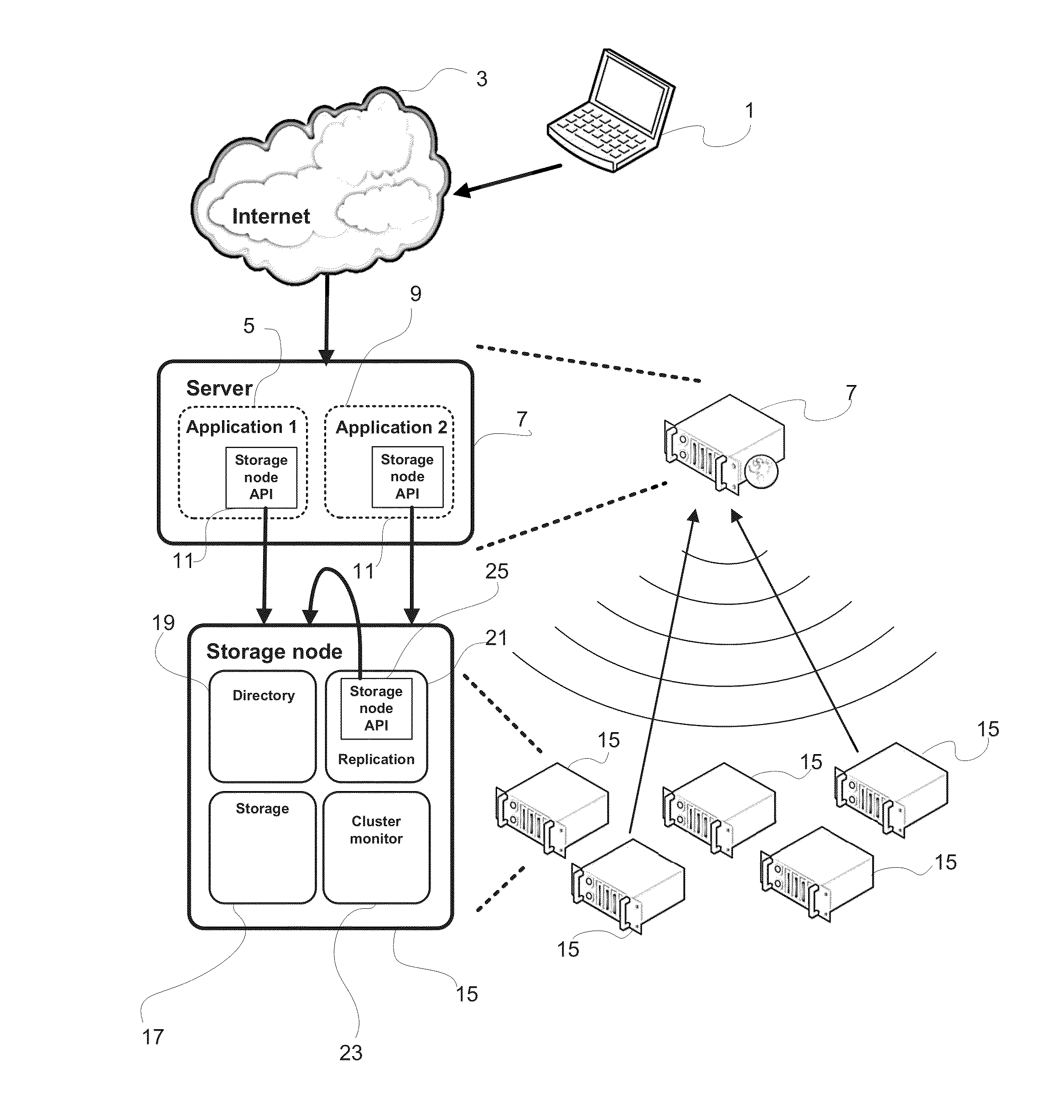
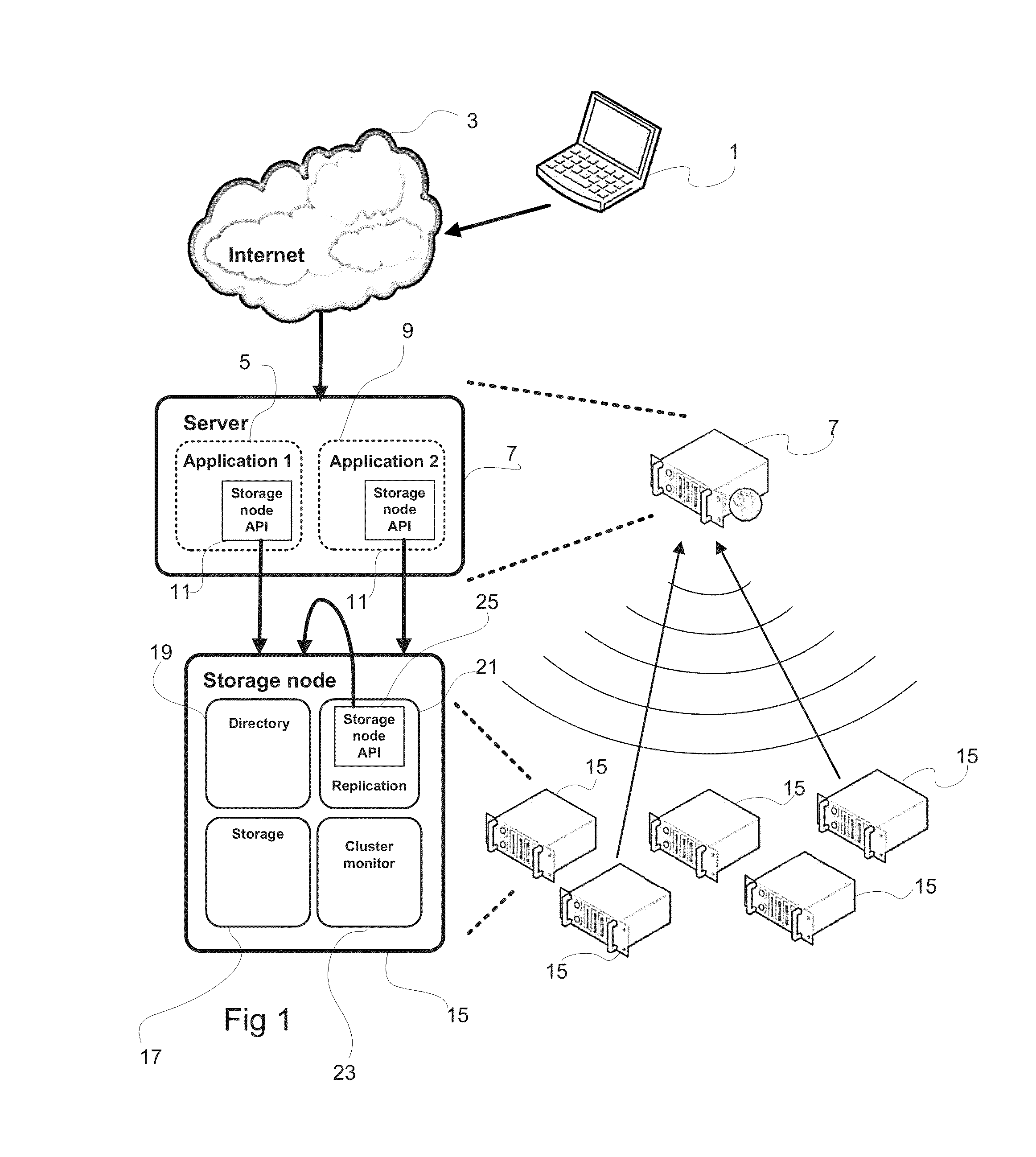
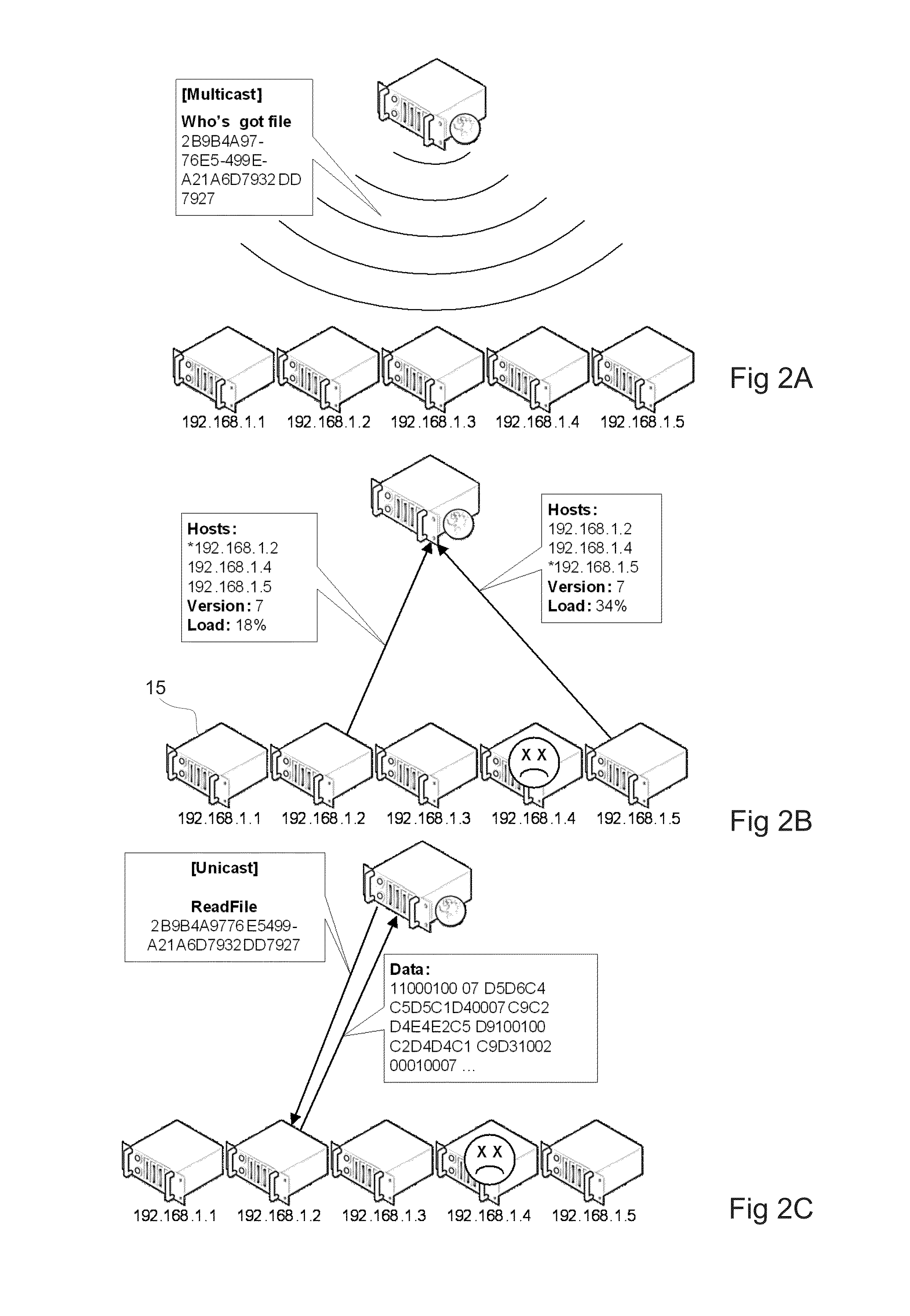
Method And Device For Writing Data To A Data Storage System Comprising A Plurality Of Data Storage Nodes
ActiveUS20130060884A1Requirement for reliabilityDigital data information retrievalDigital computer detailsApplication softwareData store
There is disclosed a method for writing data in a data storage system comprising a plurality of data storage nodes, the method being employed in a server running an application which accesses data in the data storage system, and comprising: sending a multicast storage query to a plurality of said storage nodes; receiving a plurality of responses from a subset of said storage nodes, said responses including a storage node property; selecting at least two storage nodes in the subset for storing said data, based on said responses, wherein the selecting is based on a data property of the data to be stored and a storage node property.
Owner:COMPUVERDE
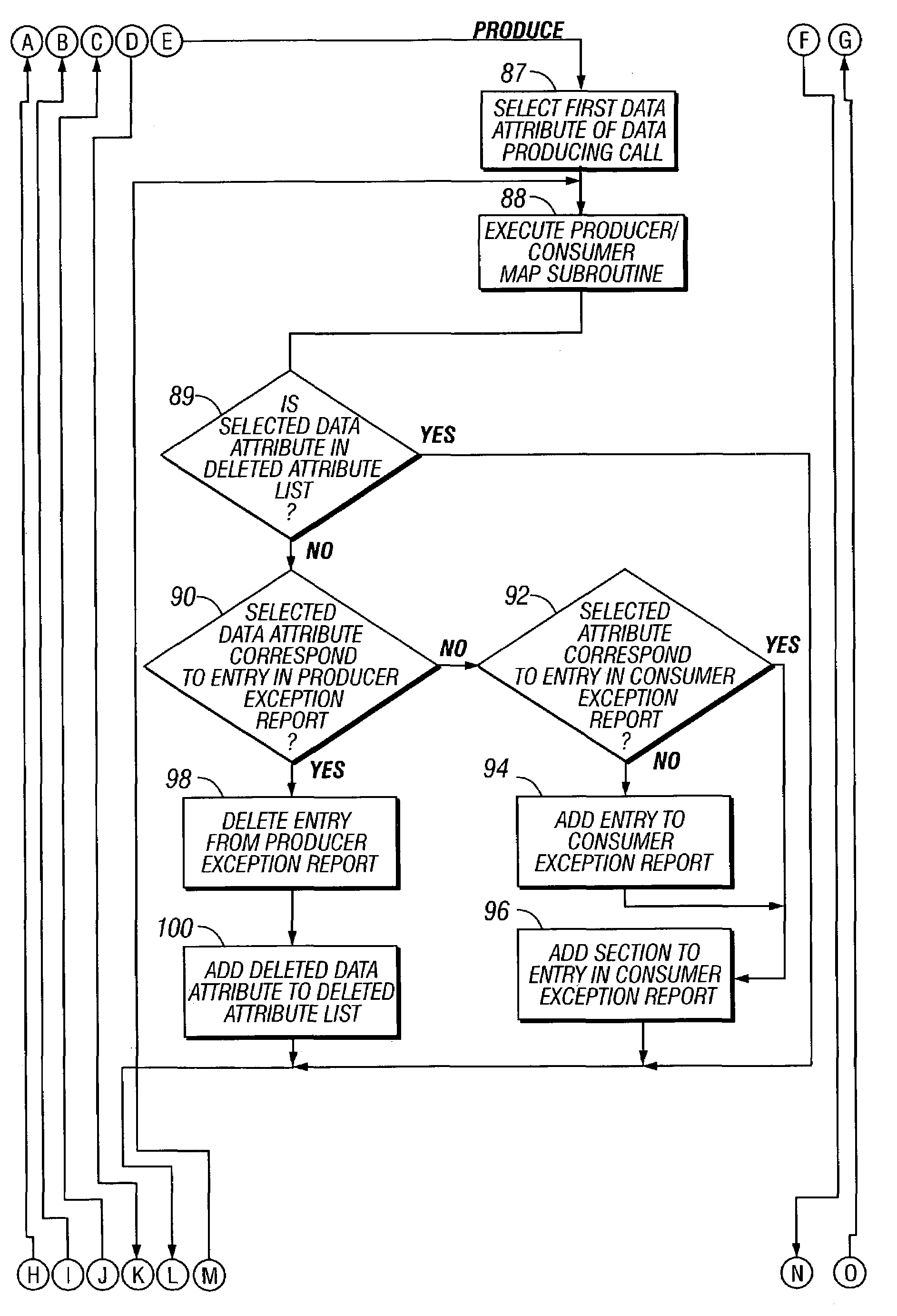
Analysis data validation tool for use in enterprise architecture modeling with result based model updating
InactiveUS7216340B1Digital data information retrievalSpecial data processing applicationsAnalysis dataEnterprise architecture
A device for modeling an integrated enterprise includes a first tool for constructing a model of the integrated enterprise and a second tool for analyzing calls, contained in the constructed model, between applications of the integrated enterprise and a database shared thereby. The call analysis tool identifies data attribute imbalances in calls between the applications of the integrated enterprise and the shared database. Data attribute imbalances result if the calls attempt to consume data which was never produced or if the calls produce data which is never consumed. The call analysis tool also generates producer / consumer maps of the data attributes used in the model, producer exception reports which identify data attributes which are consumed but never produced and consumer exception reports which identify data attributes which are produced but never consumed.
Owner:SPRINT CORPORATION
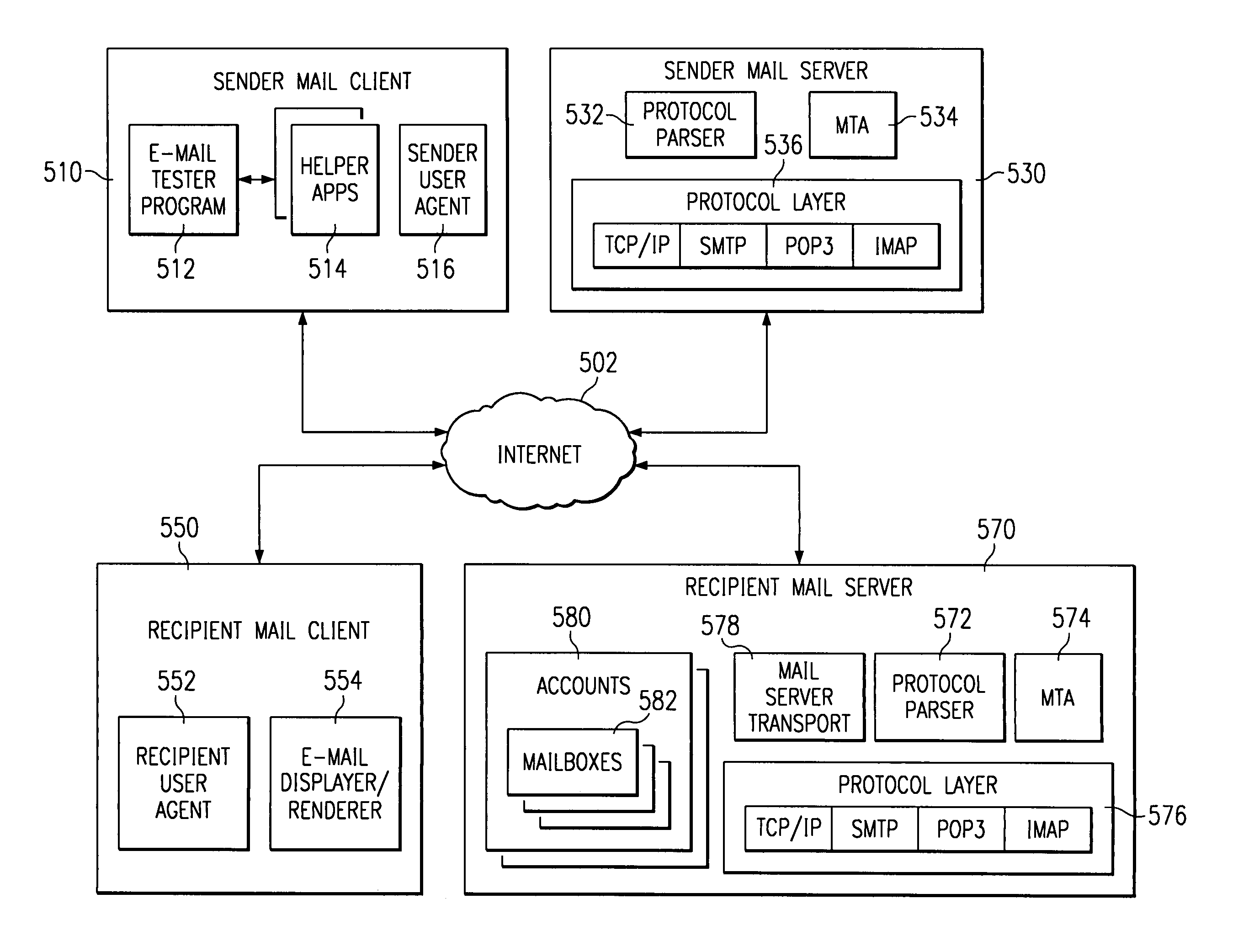
Method and apparatus for adding data attributes to e-mail messages to enhance the analysis of delivery failures
InactiveUS6959324B1Multiple digital computer combinationsData switching networksEmail addressMessage delivery
A dead e-mail identification locator discovers dead e-mail addresses without forwarding messages to valid recipients. Existing headers in the mail protocol are extended to include a test header. A mail server that supports the protocol extension of the present invention may send a reply if the address does not exist and may discard the message if the address does exist. The test header allows a sender to test an e-mail address for validity without the message being forwarded to the user, as will be described below. The sender may be a dead e-mail locator program, which tests a plurality of e-mail addresses. The sender and recipient mail servers may include attributes in the test header to enhance the analysis of delivery failures. Using these attributes, the dead e-mail address locator can pinpoint the location of e-mail message delivery failure and profile the performance of routing of messages and other details hidden from users.
Owner:SNAP INC
Graphical user interface for 3-dimensional view of a data collection based on an attribute of the data
A three-dimensional (3D) view of a data collection based on an attribute is disclosed. A timeline is provided for displaying files and folders. The timeline may include a focal group that displays detailed information about its contents to the user. Remaining items on the timeline are displayed in less detail and may be positioned to appear further away from the user. A histogram may be provided as part of the view to allow the user to more easily navigate the timeline to find a desired file or folder.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for writing data to a data storage system comprising a plurality of data storage nodes
ActiveUS9021053B2Digital data information retrievalMultiple digital computer combinationsData storeOperating system
There is disclosed a method for writing data in a data storage system comprising a plurality of data storage nodes, the method being employed in a server running an application which accesses data in the data storage system, and comprising: sending a multicast storage query to a plurality of said storage nodes; receiving a plurality of responses from a subset of said storage nodes, said responses including a storage node property; selecting at least two storage nodes in the subset for storing said data, based on said responses, wherein the selecting is based on a data property of the data to be stored and a storage node property.
Owner:COMPUVERDE
Graphical user interface for 3-dimensional view of a data collection based on an attribute of the data
A three-dimensional (3D) view of a data collection based on an attribute is disclosed. A timeline is provided for displaying files and folders. The timeline may include a focal group that displays detailed information about its contents to the user. Remaining items on the timeline are displayed in less detail and may be positioned to appear further away from the user. A histogram may be provided as part of the view to allow the user to more easily navigate the timeline to find a desired file or folder.
Owner:MICROSOFT TECH LICENSING LLC
Formulation and manipulation of databases of analyte and associated values
InactiveUS20050010093A1Easy to produceComputer-assisted medical data acquisitionDiagnostic recording/measuringAnalyteDerived Data
The present invention relates to methods of formulating analyte data databases, the databases themselves, and methods of manipulating the same. In one aspect the present invention includes the formulation of analyte data points, derived data, and data attributes databases comprising data points collected using an analyte monitoring device capable of frequent monitoring of analyte concentrations or amounts. Such data points may comprise acquired data (e.g., values corresponding to analyte concentrations or amounts as measured by said analyte monitoring device). These data points are then associated with one or more relevant data attributes. The resulting databases may be manipulated to determine relationships among the components of the database.
Owner:ANIMAS TECH +1
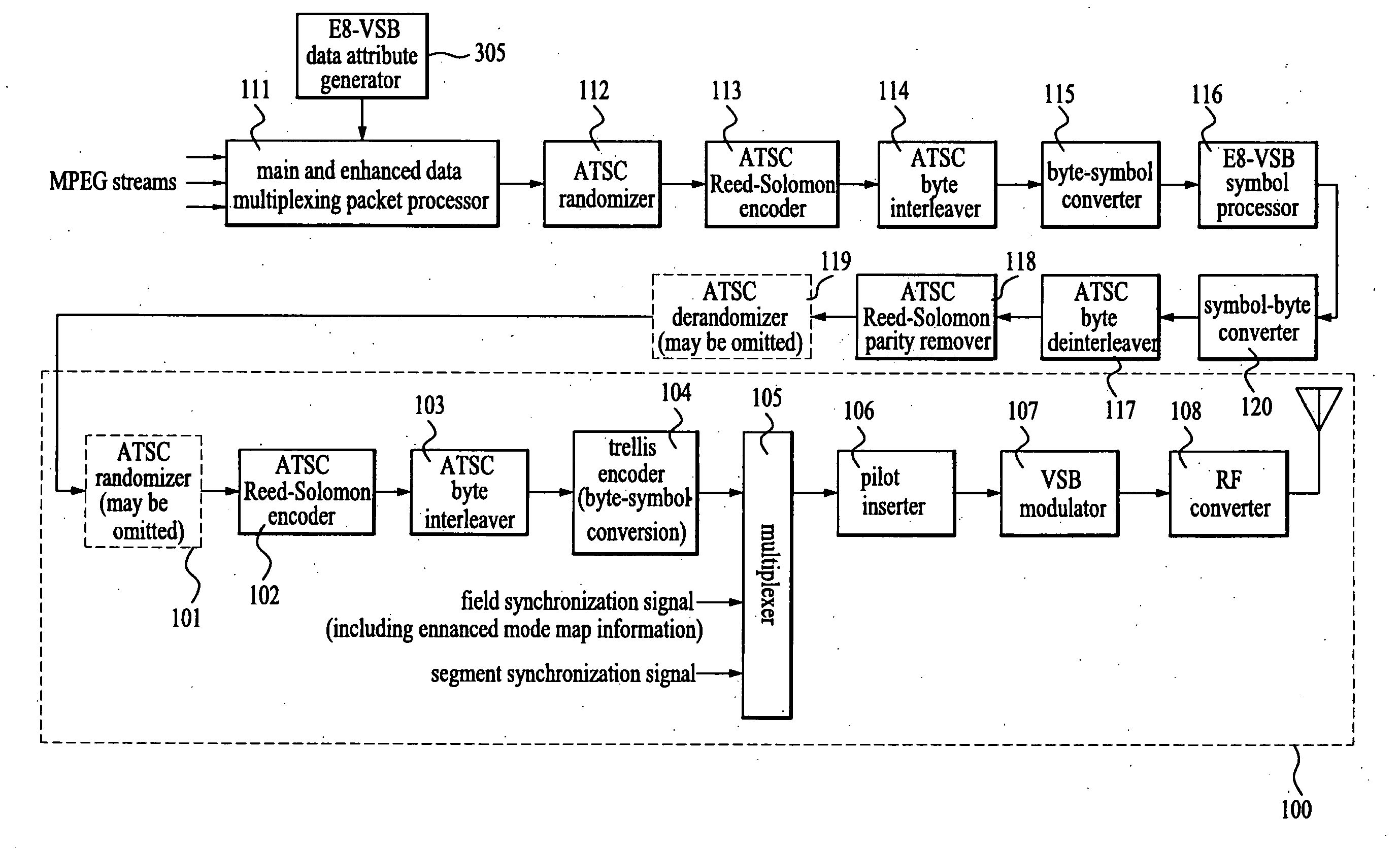
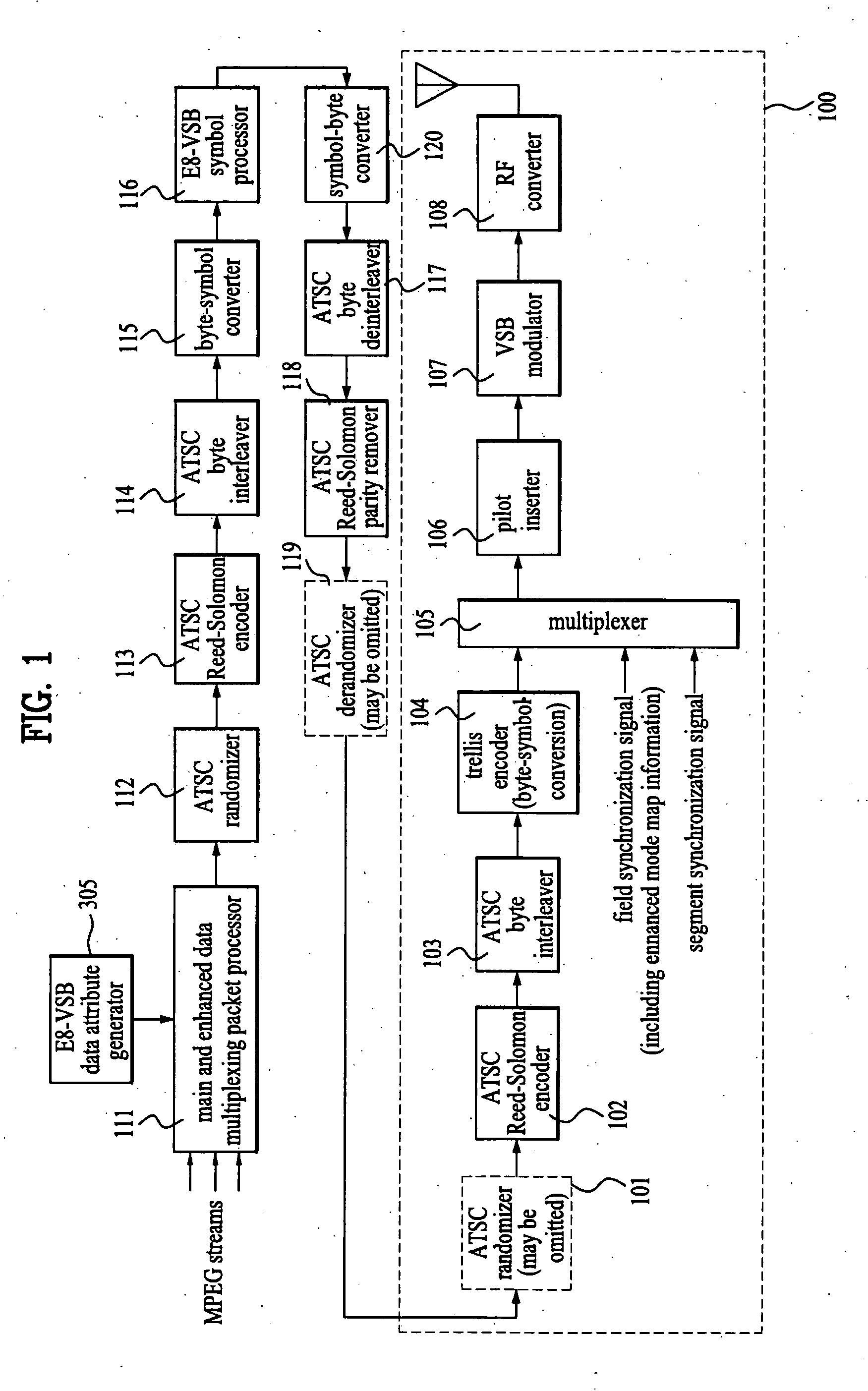
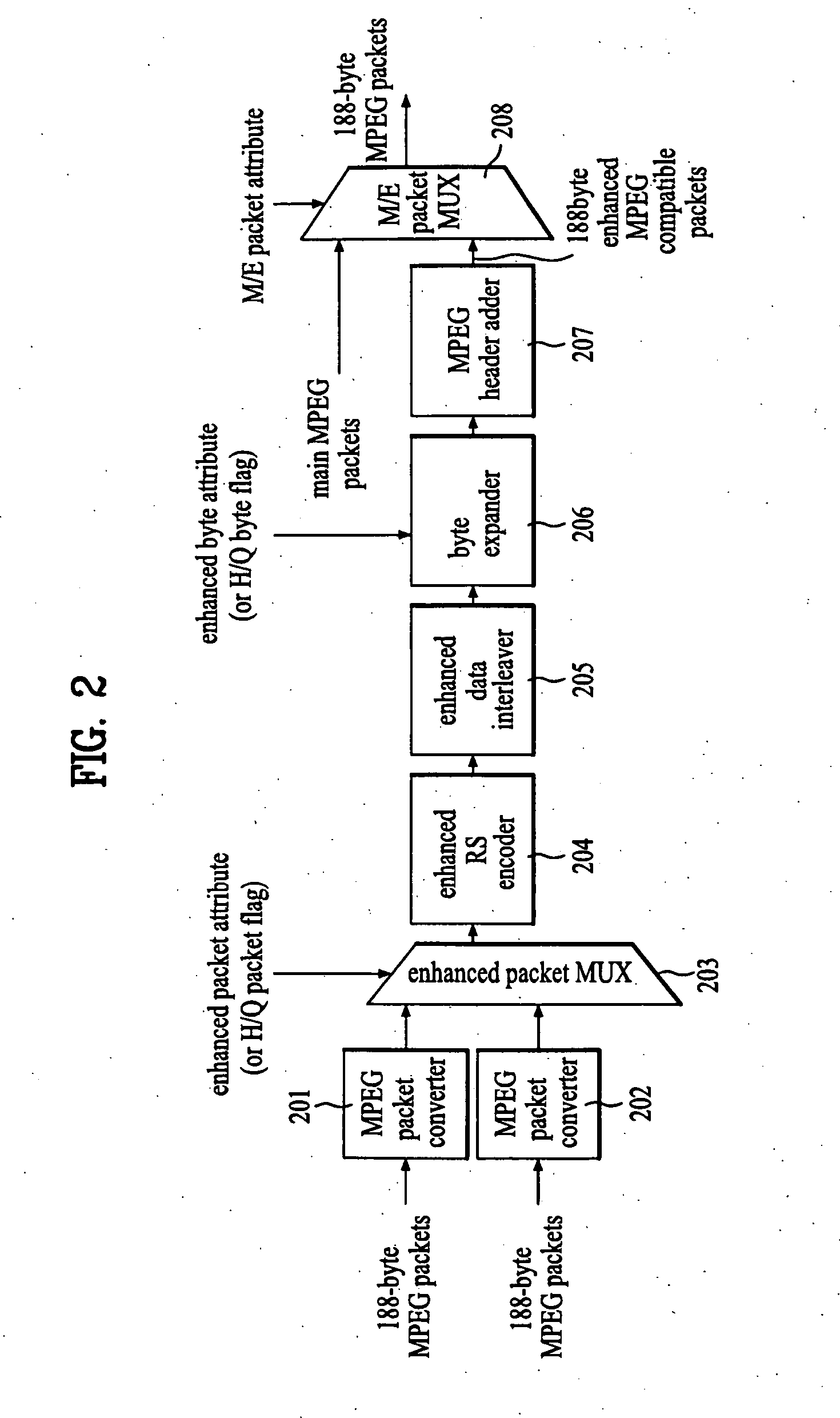
Enhanced VSB transmitter and receiver
InactiveUS20060126757A1Amplitude demodulation by homodyne/synchrodyne circuitsModulation with suppressed carrierMultiplexerPre processor
An enhanced VSB transmitter includes a data attribute generator which generates data attribute information based on a current enhanced mode map, and a VSB pre-processor which codes first and second supplemental data for error correction, interleaves the coded supplemental data, and expands the interleaved data at first and second rates, respectively, according to the data attribute information. The transmitter further includes a multiplexer which multiplexes main data with the expanded supplemental data according to the data attribute information, and a VSB processor which codes the data multiplexed by the multiplexer for error correction.
Owner:LG ELECTRONICS INC
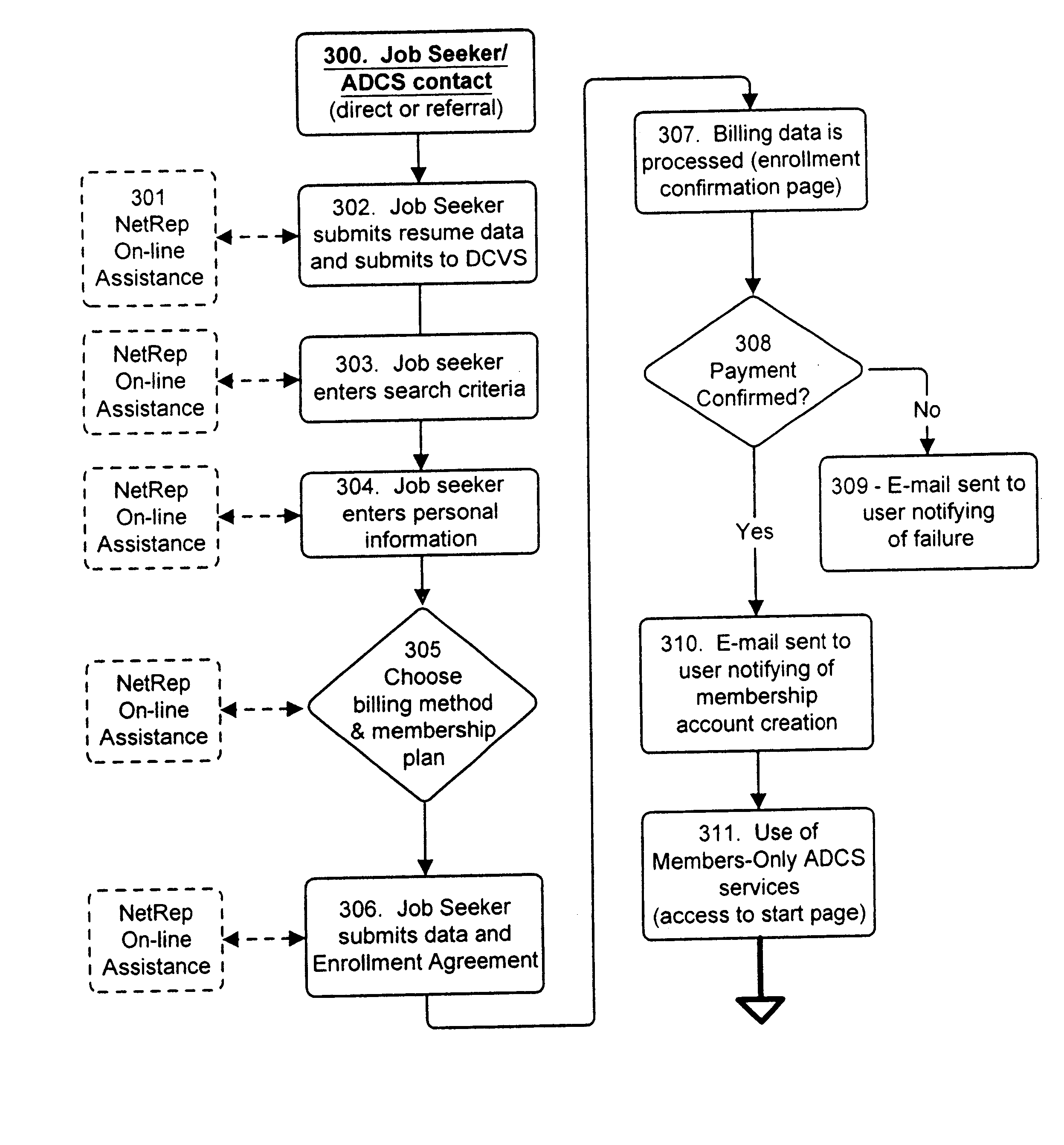
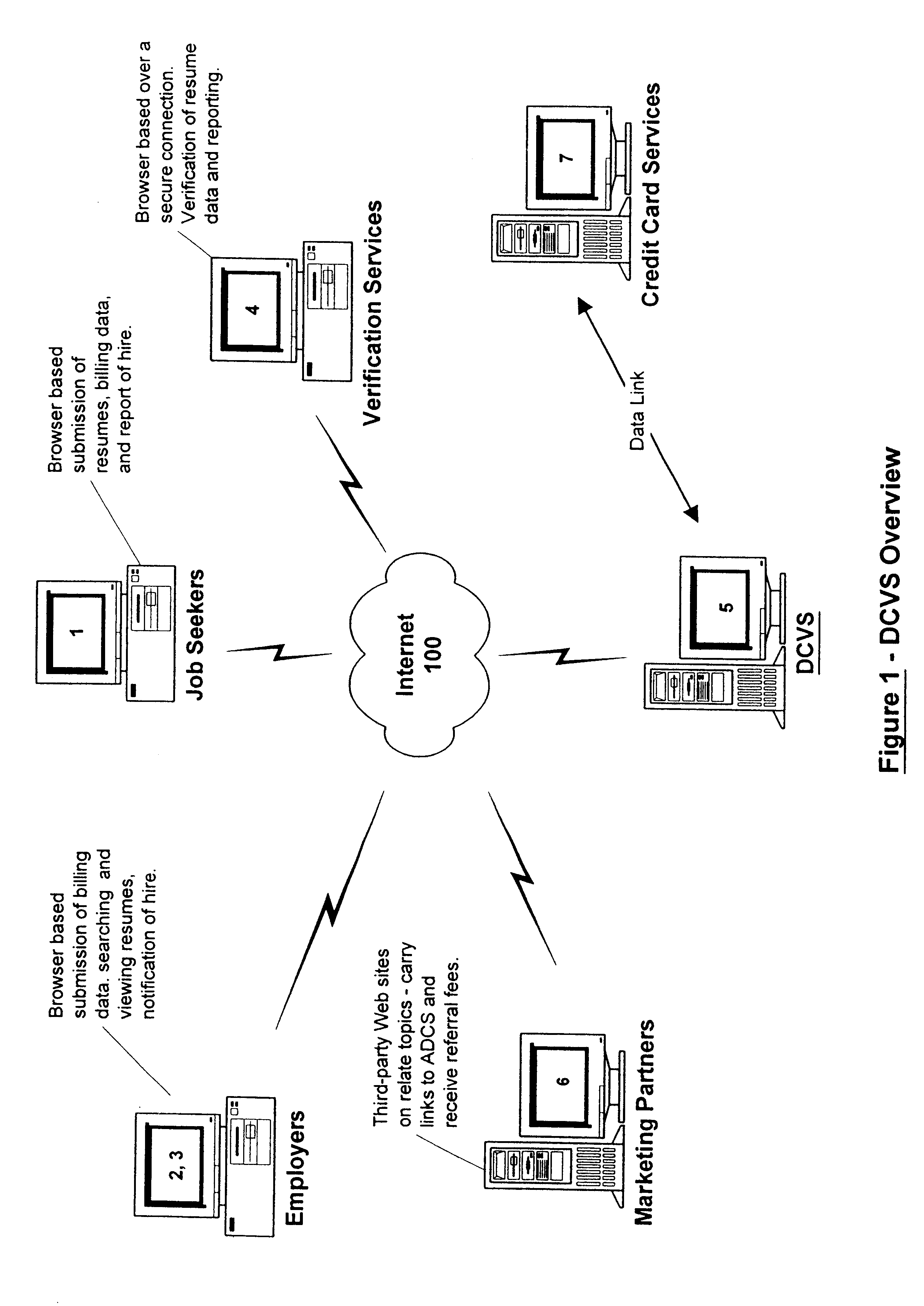
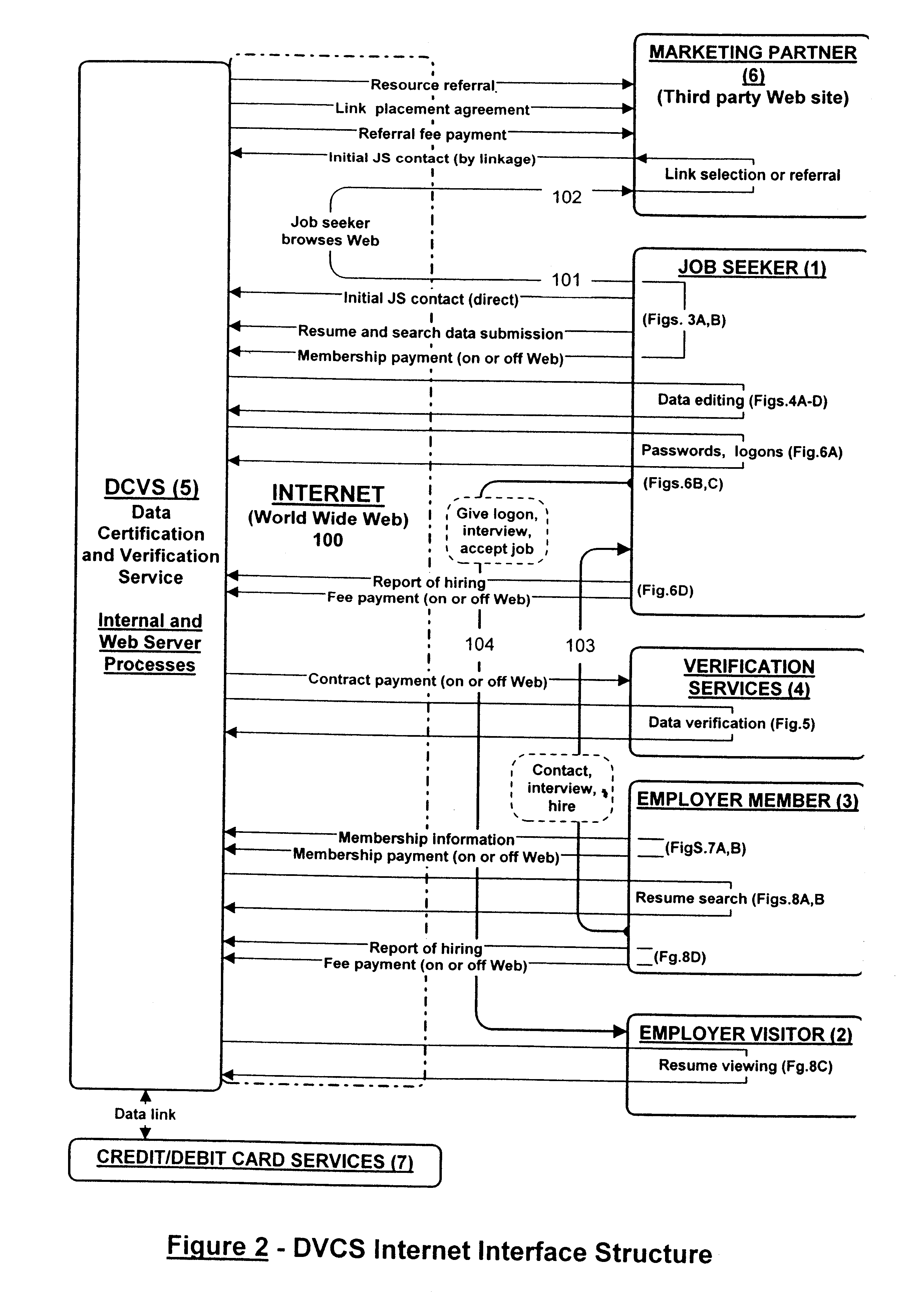
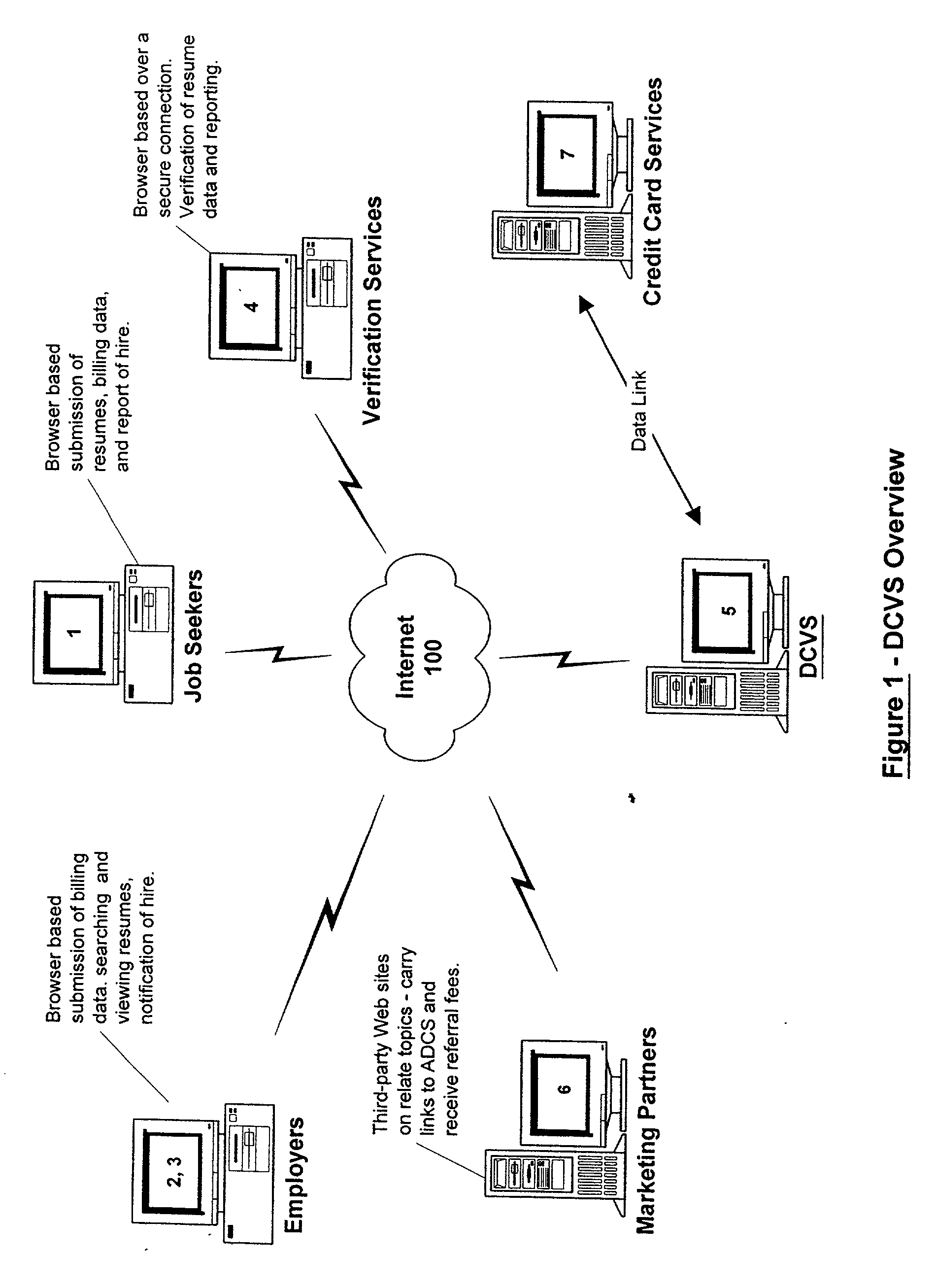
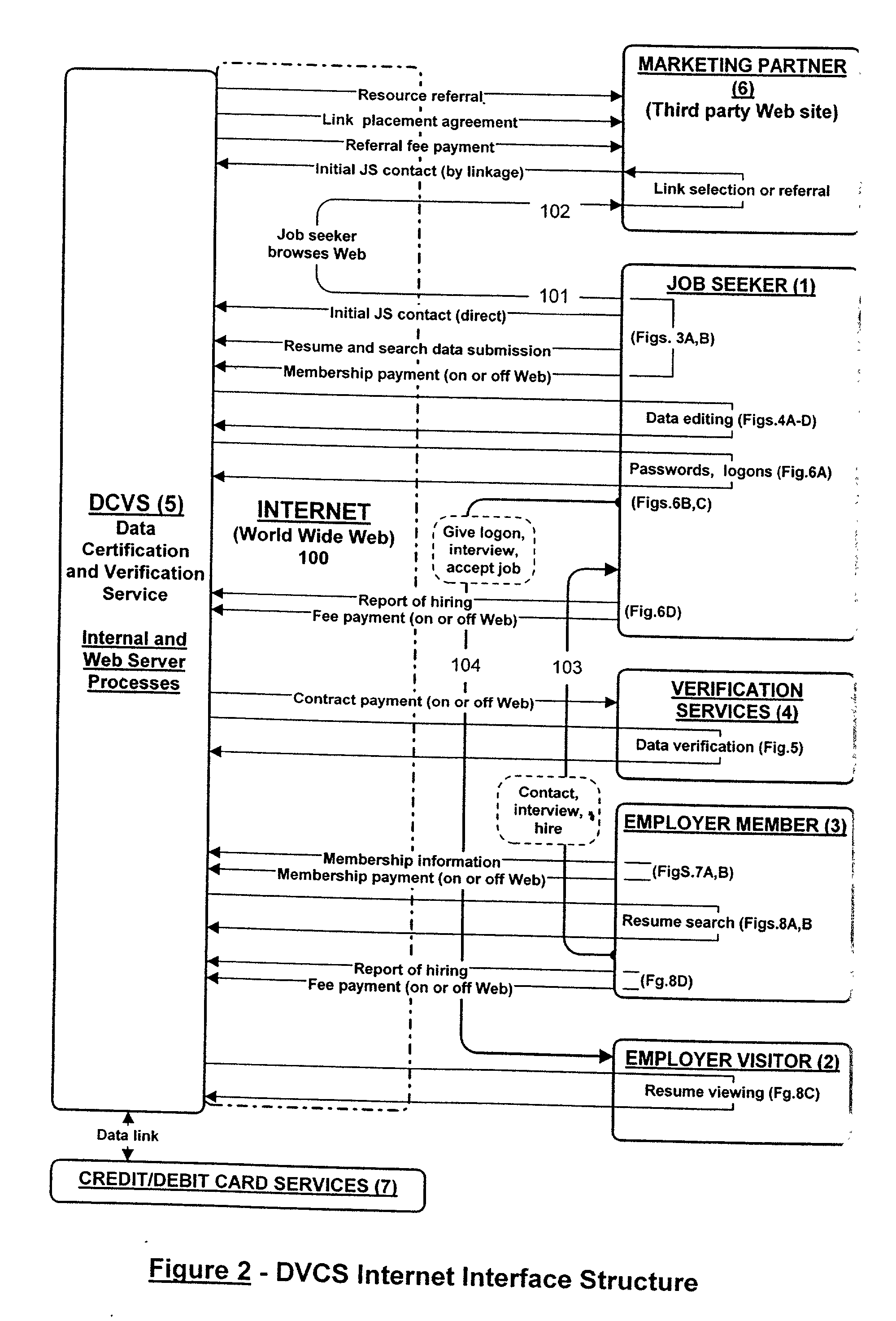
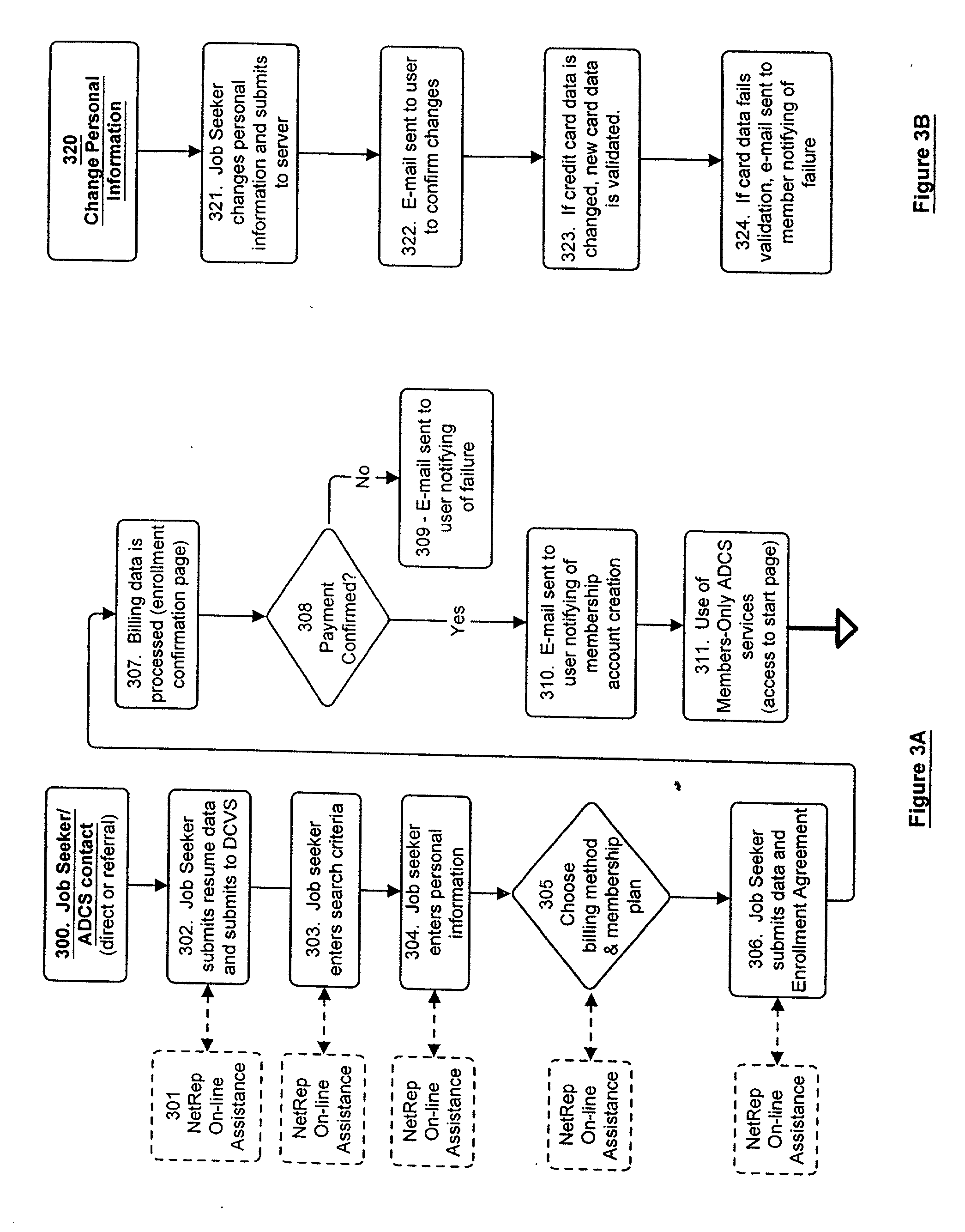
Data certification and verification system having a multiple-user-controlled data interface
InactiveUS6658400B2Preserve valueFast and cost-effective operationComputer security arrangementsOffice automationData validationSource Data Verification
A method and apparatus is described for multiple-party data attribute management system and interface structure which permits different categories of users to contribute and control different types of source data, while adding informational value to data contributed by other users. The system provides a secure repository for verified and authenticated data, and provides a system of controlled access to the repository. The preferred embodiment of the invention comprises a data verification and certification system which in a principal embodiment is useful to create a data bank to match job seekers with potential employers based on verified resume data and employer specified search criteria. The interface structure The system of the invention preferably includes computer databases and interactive Internet based server systems.
Owner:VERIFIED HIRING
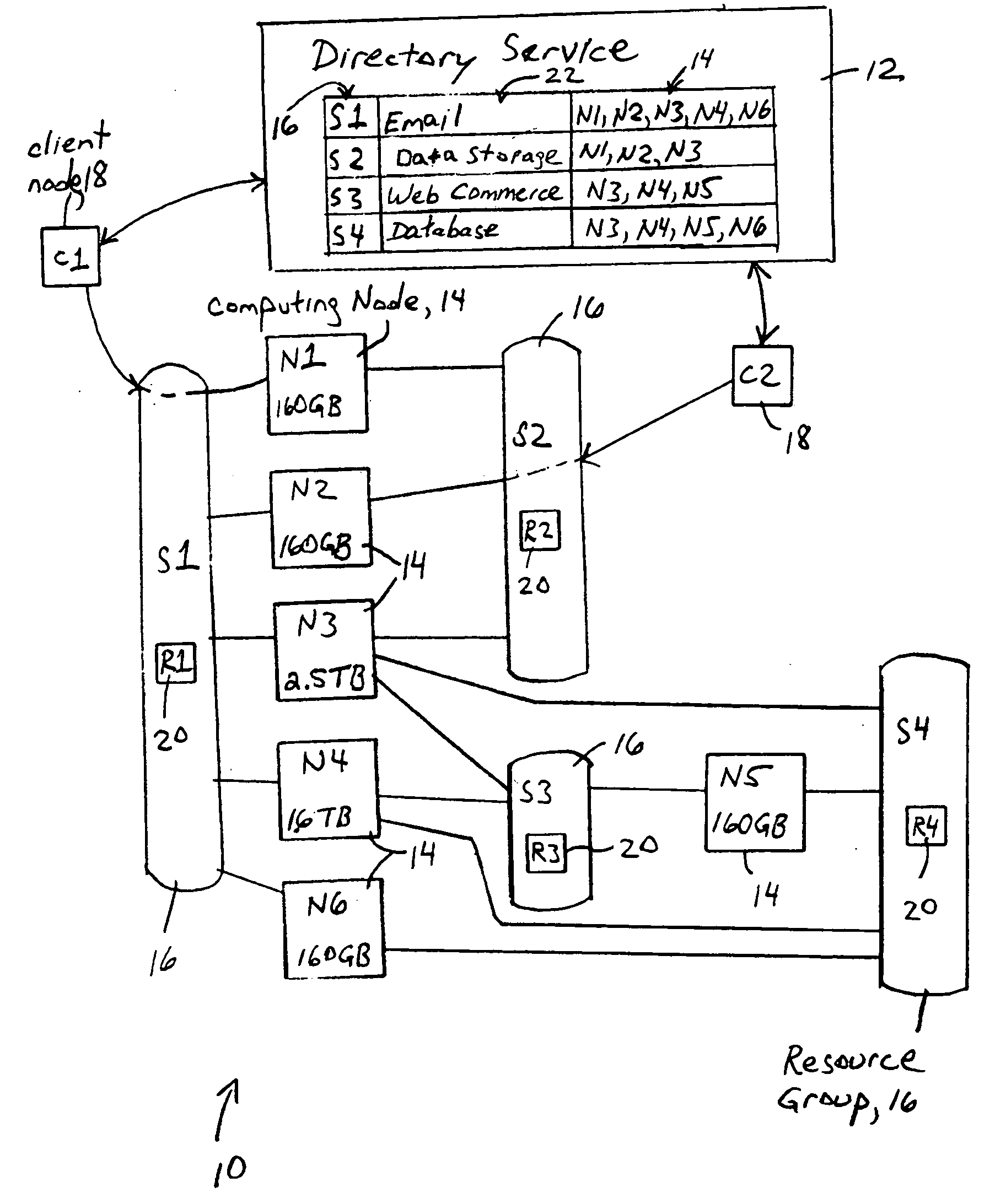
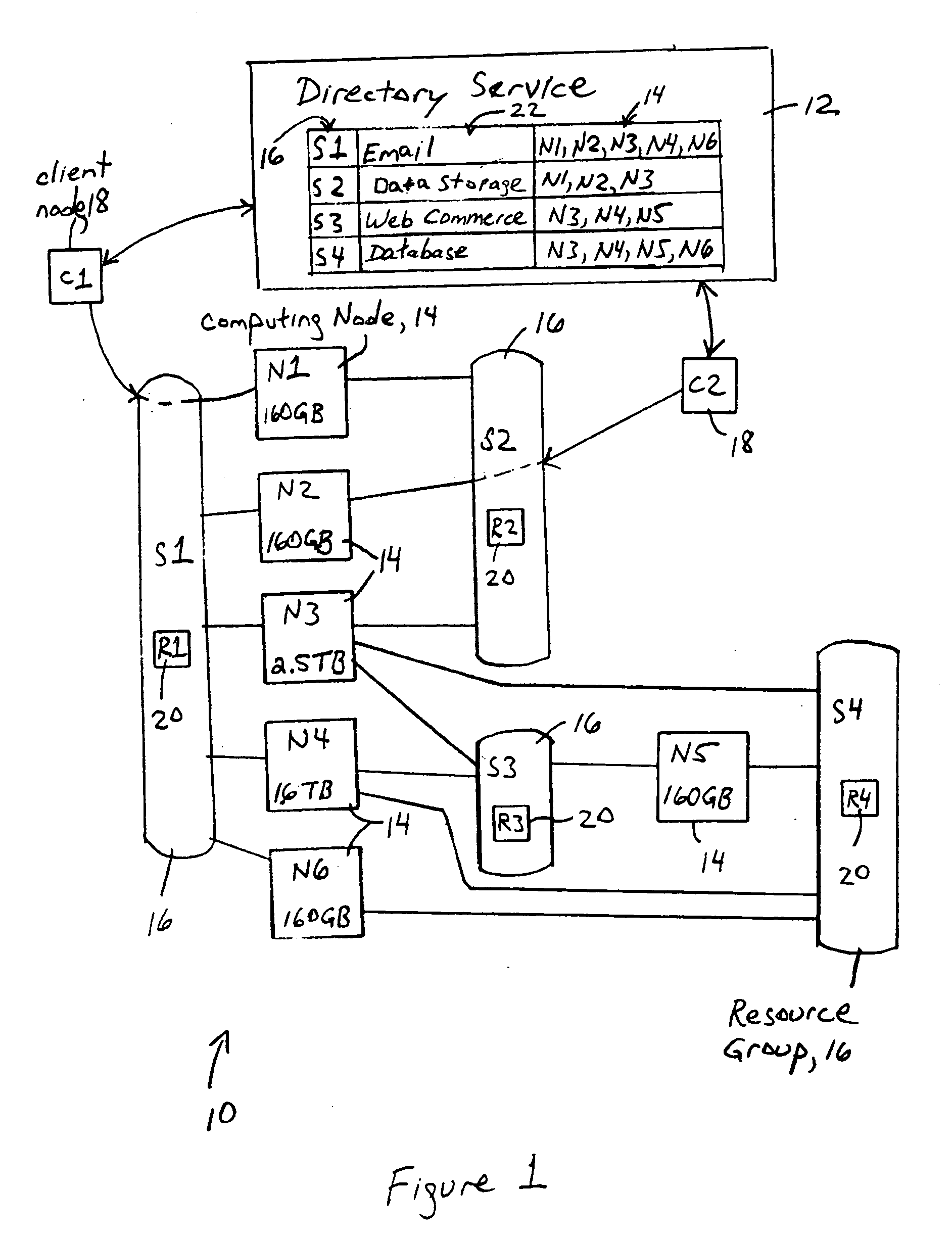
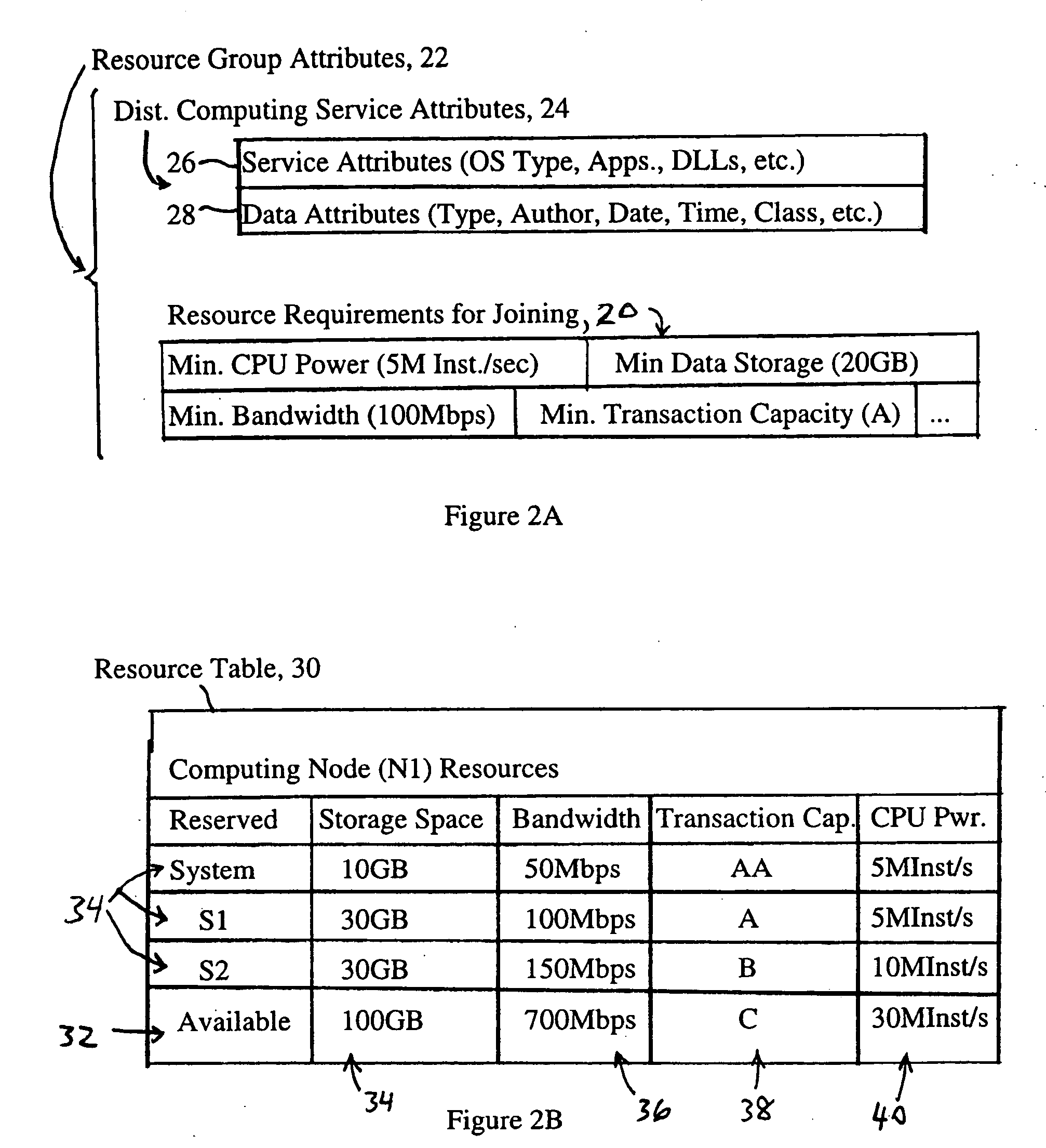
Distributed client services based on execution of service attributes and data attributes by multiple nodes in resource groups
InactiveUS20060179143A1Reduce necessityMultiprogramming arrangementsMultiple digital computer combinationsResource basedClient-side
A network provides distributed client services based on participation in respective resource groups by computing nodes, each resource group including a corresponding resource requirement for any computing node that joins the corresponding resource group for execution of the corresponding distributed client service. Each computing node, in response to determining its corresponding available node capacity, is configured for selectively creating and joining at least one new resource group for execution of a corresponding distributed client service having a corresponding resource requirement, and / or selectively joining at least one of the available resource groups, based on the corresponding available node capacity satisfying the corresponding resource requirement. Each distributed client service also includes service attributes that define parameters for execution of the distributed client service, and data attributes that define the attributes required for data to be used in the distributed client service.
Owner:CISCO TECH INC
Data certification and verification system having a multiple- user-controlled data interface
InactiveUS20010047347A1Fast and cost-effective operationAvoid effortComputer security arrangementsMultiple digital computer combinationsData validationSource Data Verification
Owner:VERIFIED HIRING
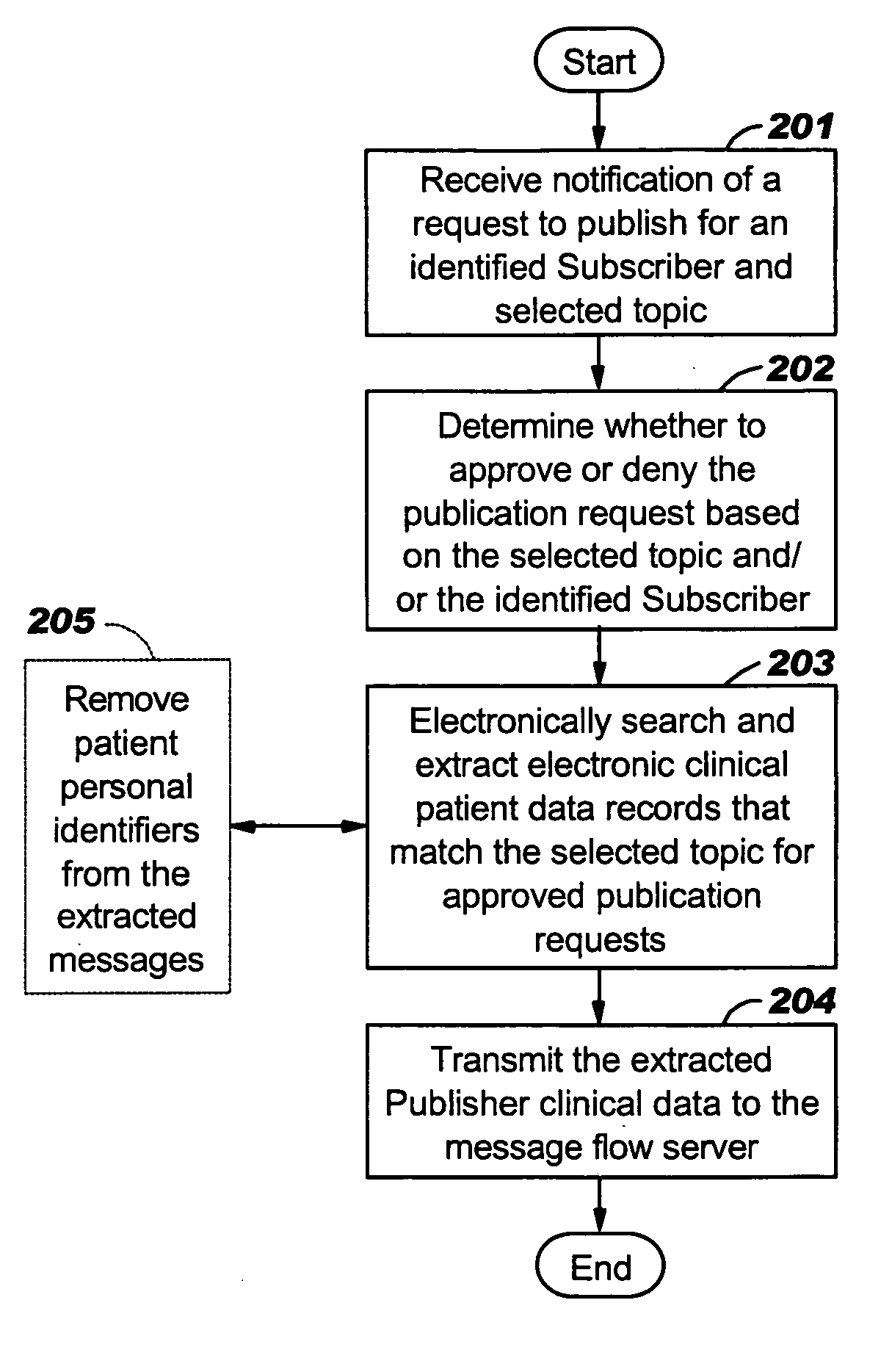
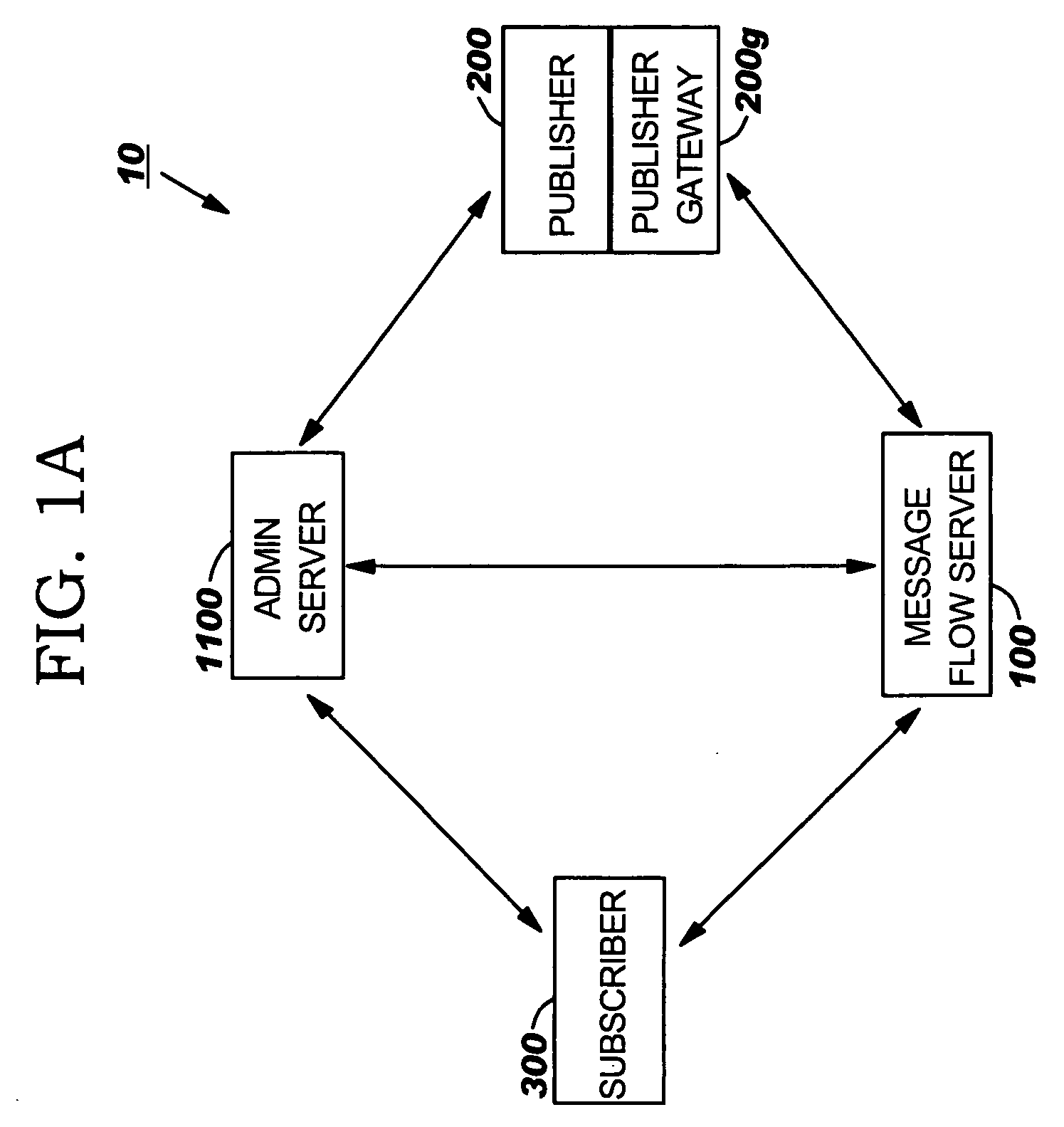
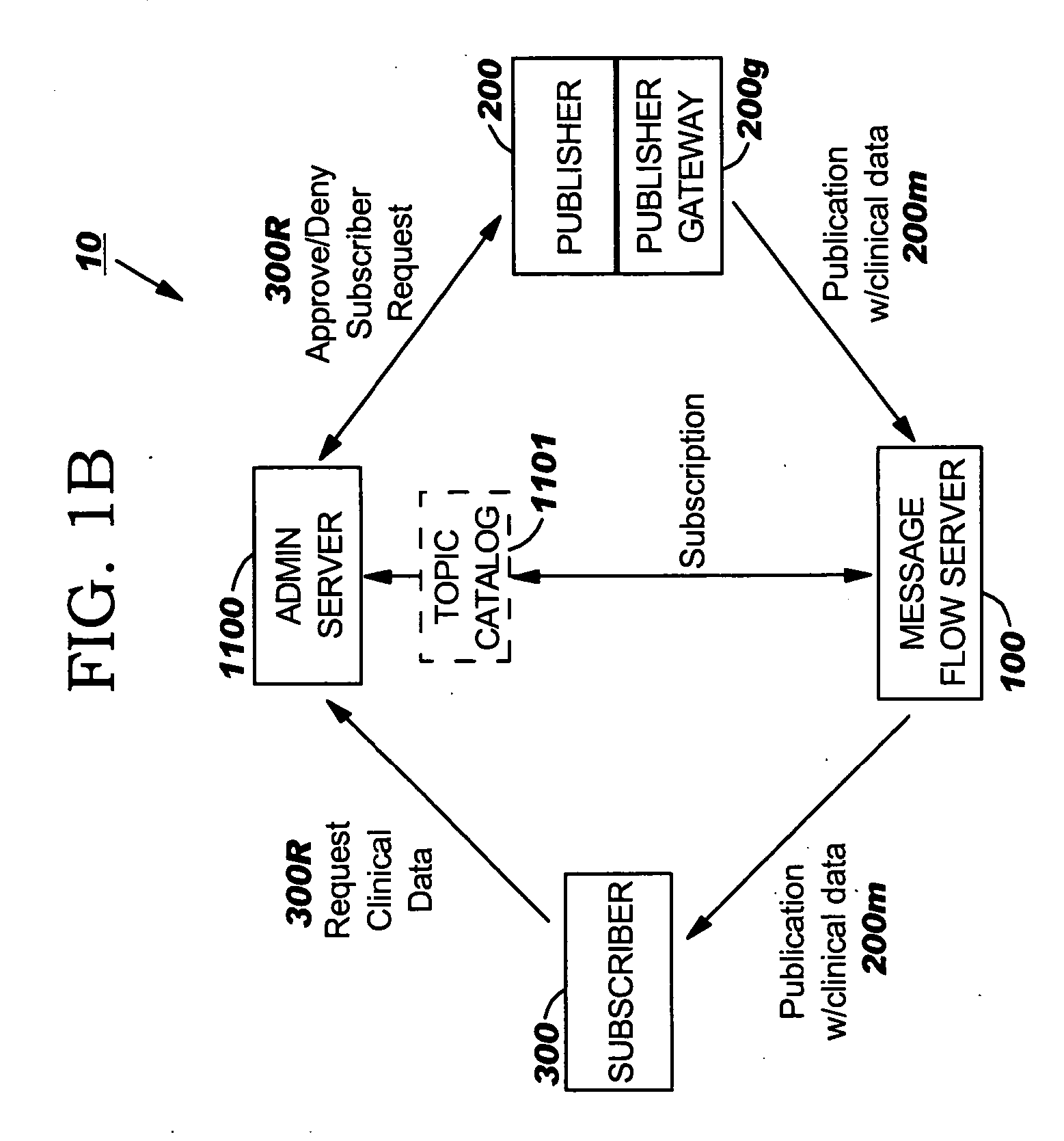
Systems with user selectable data attributes for automated electronic search, identification and publication of relevant data from electronic data records at multiple data sources
Systems, methods and computer program products that allow Subscribers to electronically obtain data of interest from participating Publishers using a computer network which employ an Administrative Server configured to allow Subscribers to electronically define, select and / or request an electronic topic data request with data elements of interest from a plurality of Publishers having non-public respective electronic repositories of source data using a web portal and a computer network.
Owner:IBM CORP
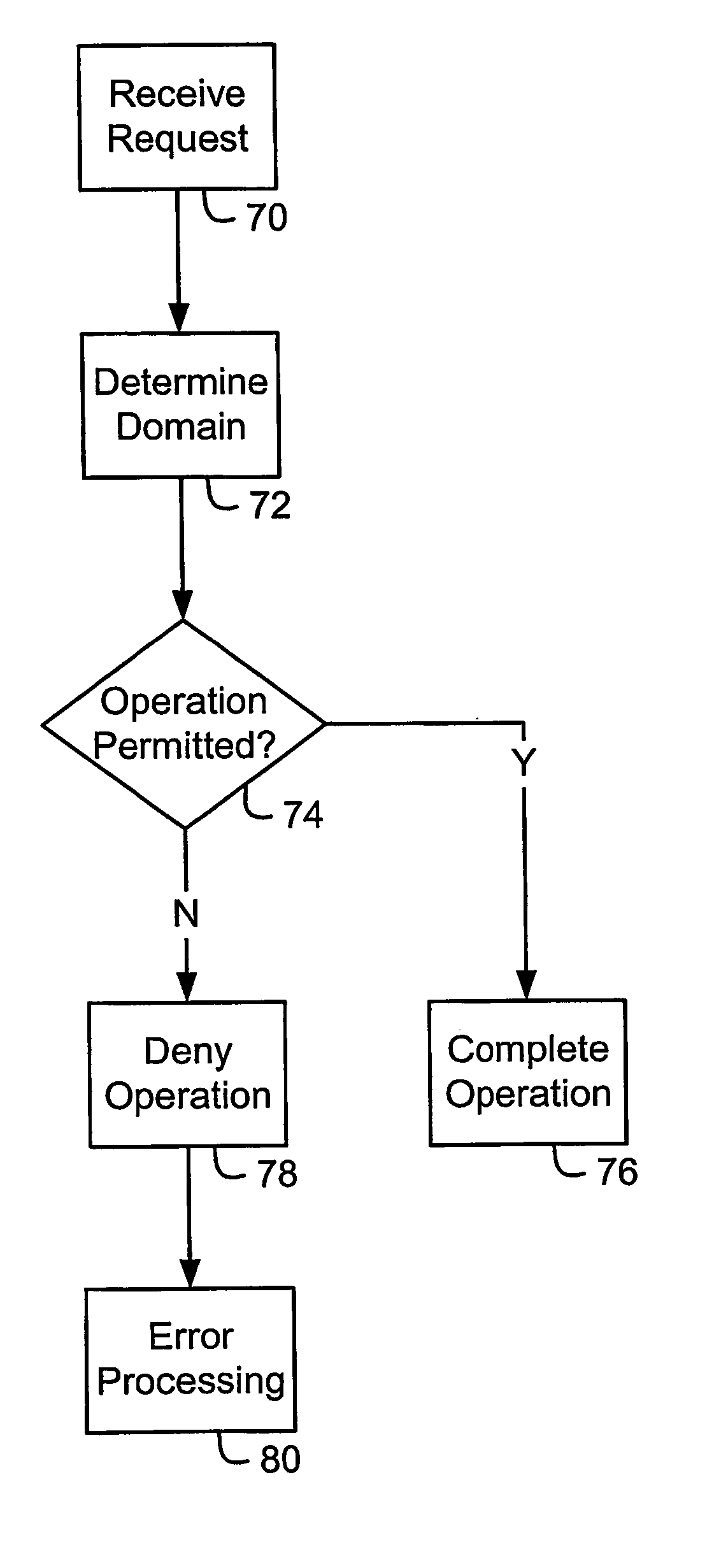
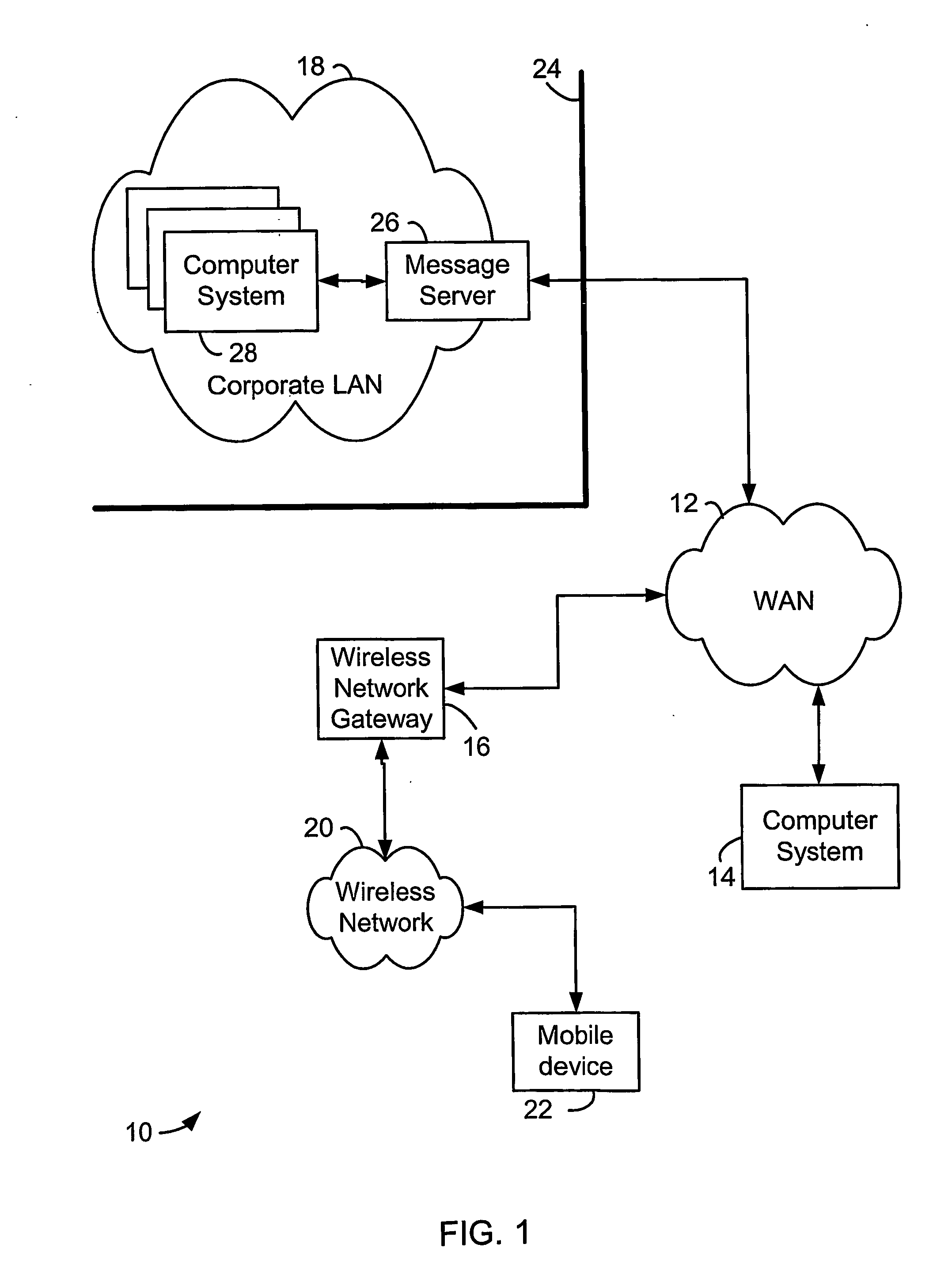
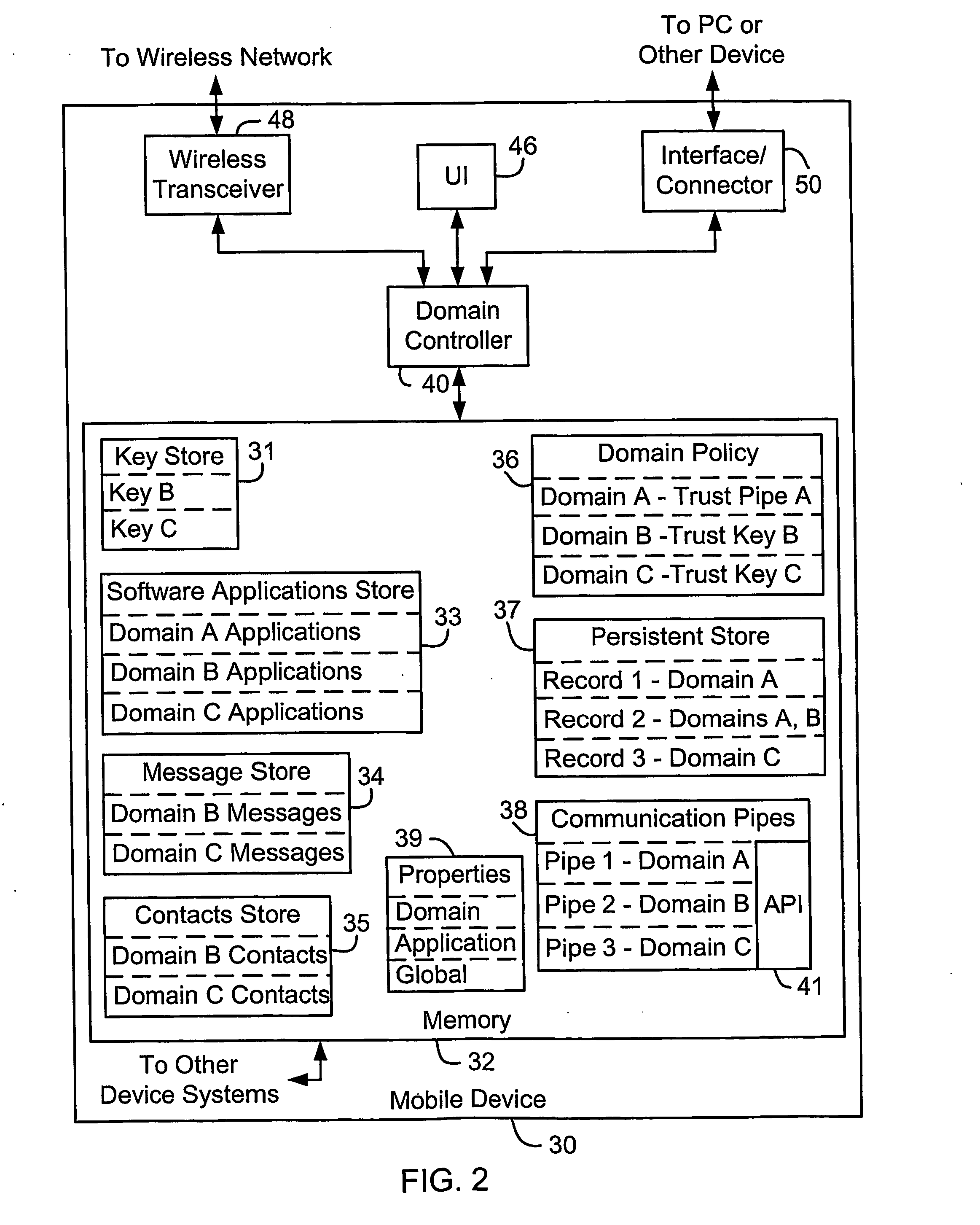
System and method for secure control of resources of wireless mobile communication devices
ActiveUS20050213763A1Digital data processing detailsUser identity/authority verificationTrust relationshipCommunication device
Systems and methods for secure control of a wireless mobile communication device are disclosed. Each of a plurality of domains includes at least one wireless mobile communication device asset. When a request to perform an operation affecting at least one of the assets is received, it is determined whether the request is permitted by the domain that includes the at least one affected asset, by determining whether the entity with which the request originated has a trust relationship with the domain, for example. The operation is completed where it is permitted by the domain. Wireless mobile communication device assets include software applications, persistent data, communication pipes, and configuration data, properties or user or subscriber profiles.
Owner:BLACKBERRY LTD
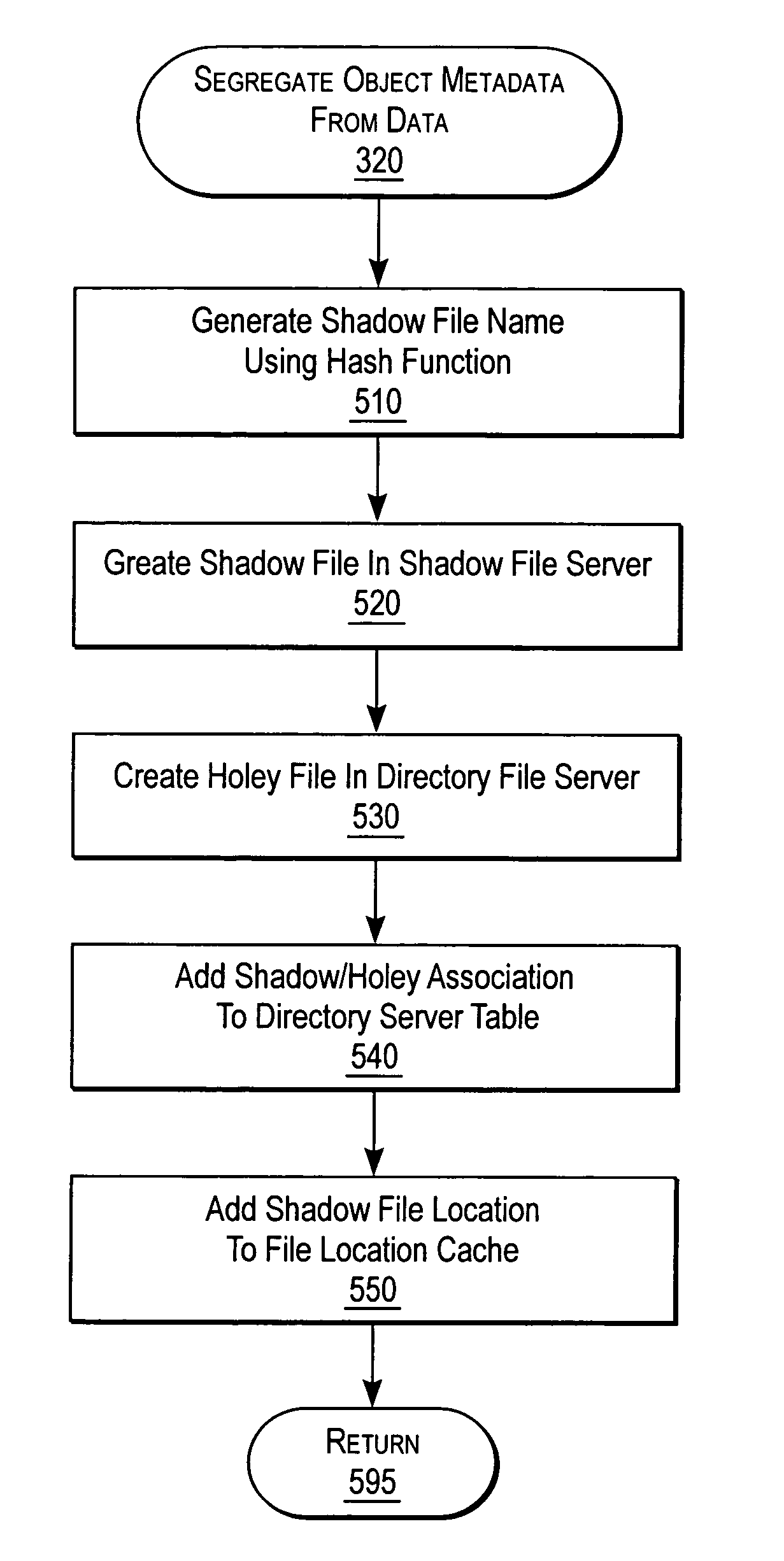
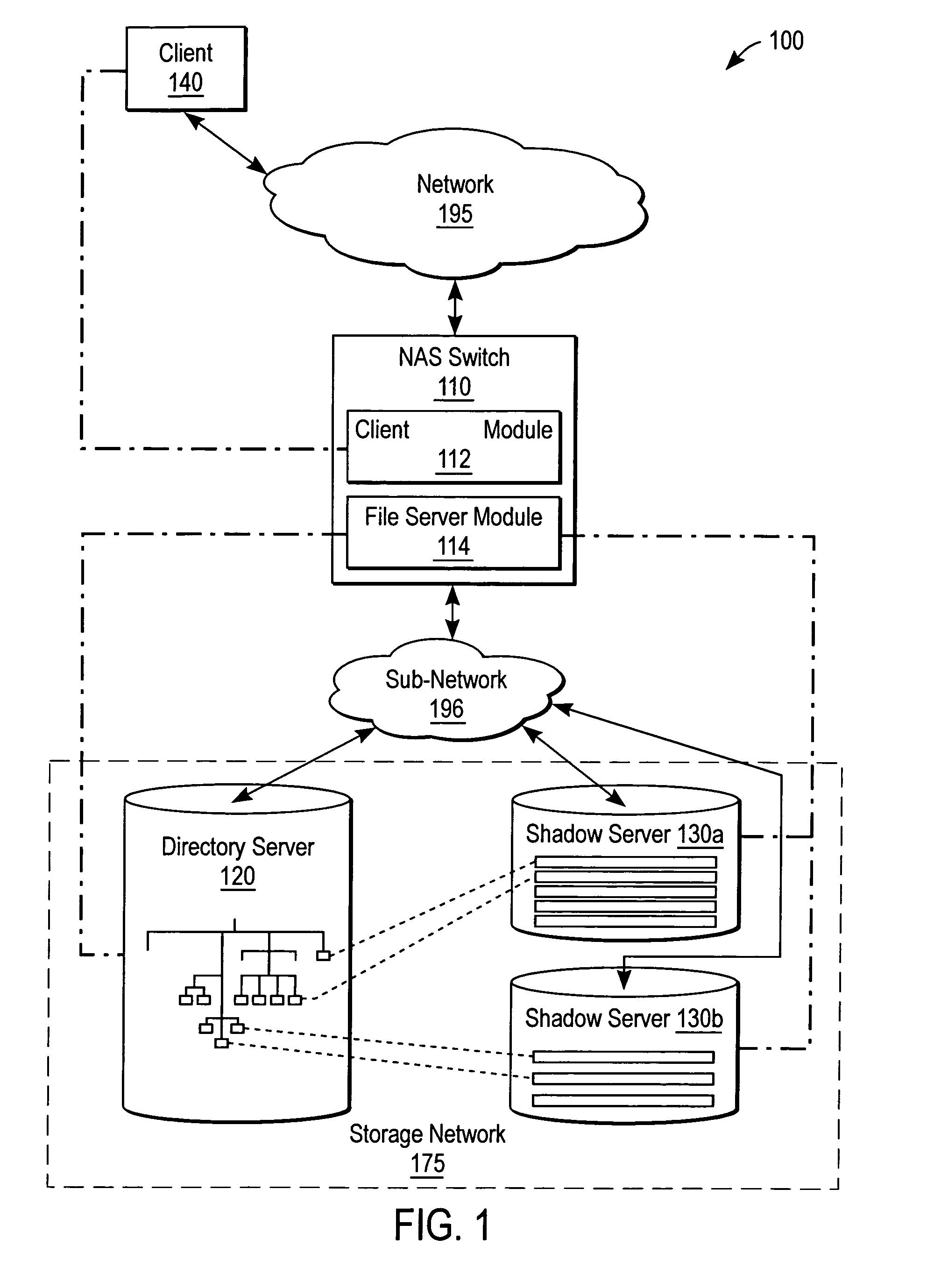
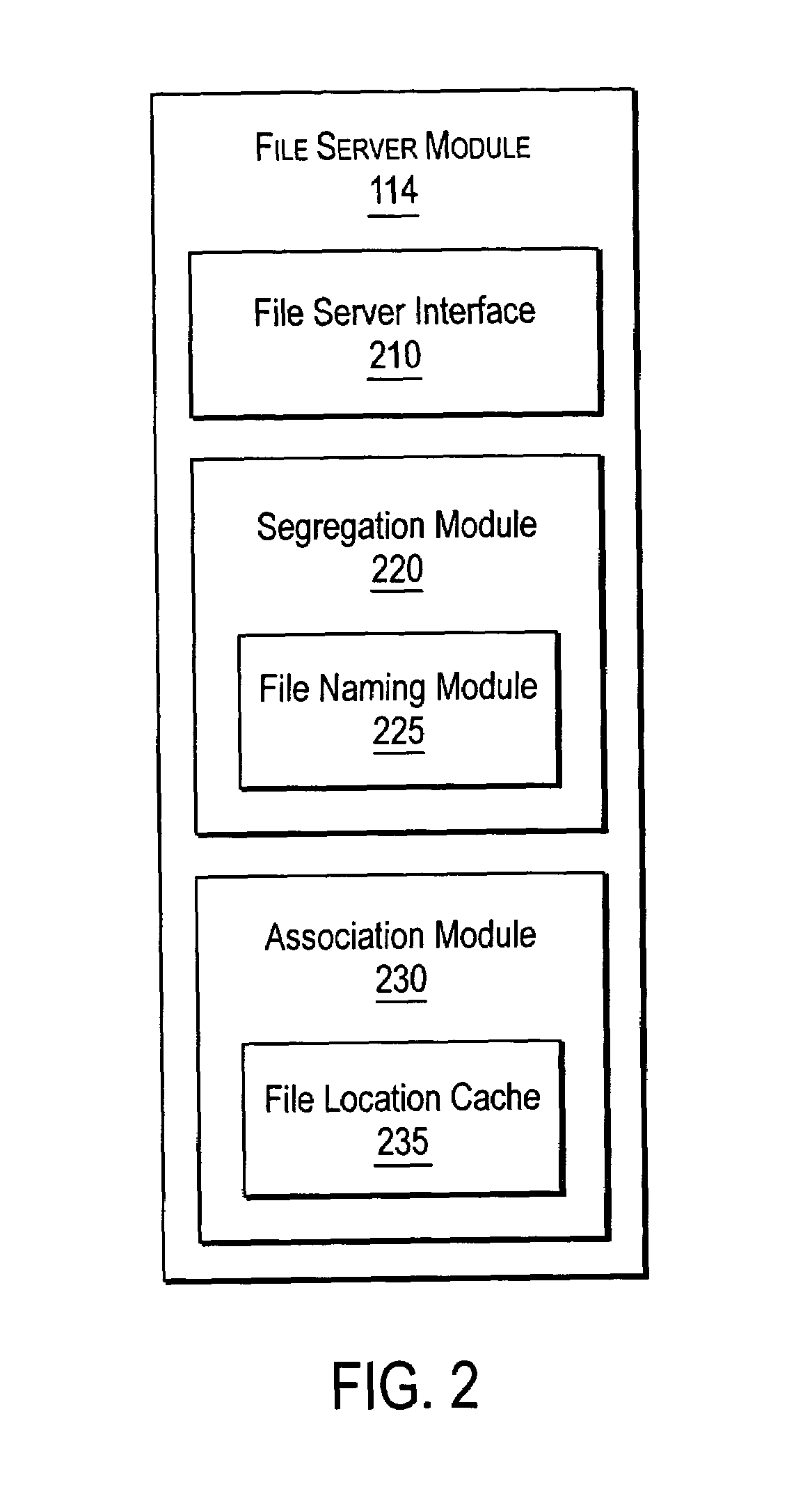
Extended storage capacity for a network file server
ActiveUS7072917B2Data processing applicationsDigital data processing detailsServer replicationData operations
A NAS switch provides extended storage capacity to a file server in a decentralized storage network such as a NAS (Network Attached Storage) storage network. The NAS switch sits in the data path of a client on the front end and a directory file server and shadow file servers on the back end. A segregation module in the NAS switch replicates data from the directory file server to a shadow file server, and then replaces the data in the directory file server with holey files. Holey files, which store a range of consecutive values such as zero with negligible storage space, retain the attributes of the data without retaining its storage consumption. Thus, the directory file server can server as a single directory hierarchy for several shadow file servers containing data beyond a capacity of the directory file server. When the NAS switch receives operations from the client, an association module forwards directory operations to the directory file server and data operations to the shadow file server. The NAS switch also provides services to several shadow file servers from a single directory file server.
Owner:CISCO TECH INC
Interpolation between relational tables for purposes of animating a data visualization
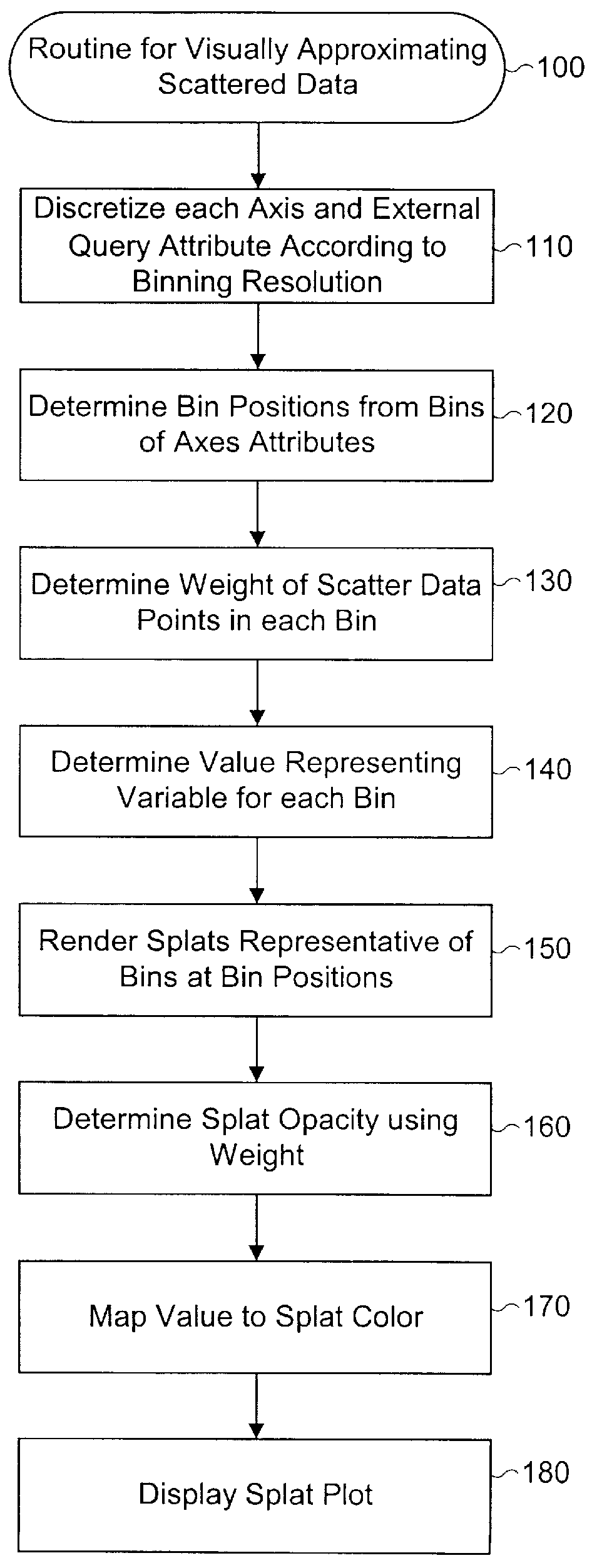
InactiveUS6034697ASmooth animationDrawing from basic elementsDigital computer detailsGraphicsAnimation
A method, system, and computer program product are provided for a new data visualization tool that visually approximates a scatter plot and provides smooth animation of graphics by using interpolated data. An interpolation process is performed over pre-processed bins of scattered data points. A user can smoothly animate a plot along several dimensions by using an external query device to vary a selected data attribute. If the external query device (or slider) control is positioned in between discrete positions of the slider, the displayed plot corresponds to interpolated data. Adjacent data structures are determined corresponding to the position of the external query device. The adjacent data structures are merged together, then aggregated the using the spatial columns of the data structure as a unique key. An interpolated bin is generated, where the weight of the bin is interpolated and the dependent attribute is also interpolated and weighted. The interpolated dependent attribute is mapped to color in the visualized scatter plot. The plot appears as rendered splats corresponding to bin positions of the interpolated bins, where each splat has an opacity that is a function of the interpolated weight of data points in the corresponding bin.
Owner:MORGAN STANLEY +1
Systems and methods for rule-based anomaly detection on IP network flow
ActiveUS9258217B2Platform integrity maintainanceKnowledge representationTraffic capacityNetwork packet
A system to detect anomalies in internet protocol (IP) flows uses a set of machine-learning (ML) rules that can be applied in real time at the IP flow level. A communication network has a large number of routers that can be equipped with flow monitoring capability. A flow collector collects flow data from the routers throughout the communication network and provides them to a flow classifier. At the same time, a limited number of locations in the network monitor data packets and generate alerts based on packet data properties. The packet alerts and the flow data are provided to a machine learning system that detects correlations between the packet-based alerts and the flow data to thereby generate a series of flow-level alerts. These rules are provided to the flow time classifier. Over time, the new packet alerts and flow data are used to provide updated rules generated by the machine learning system.
Owner:AT&T INTPROP I LP
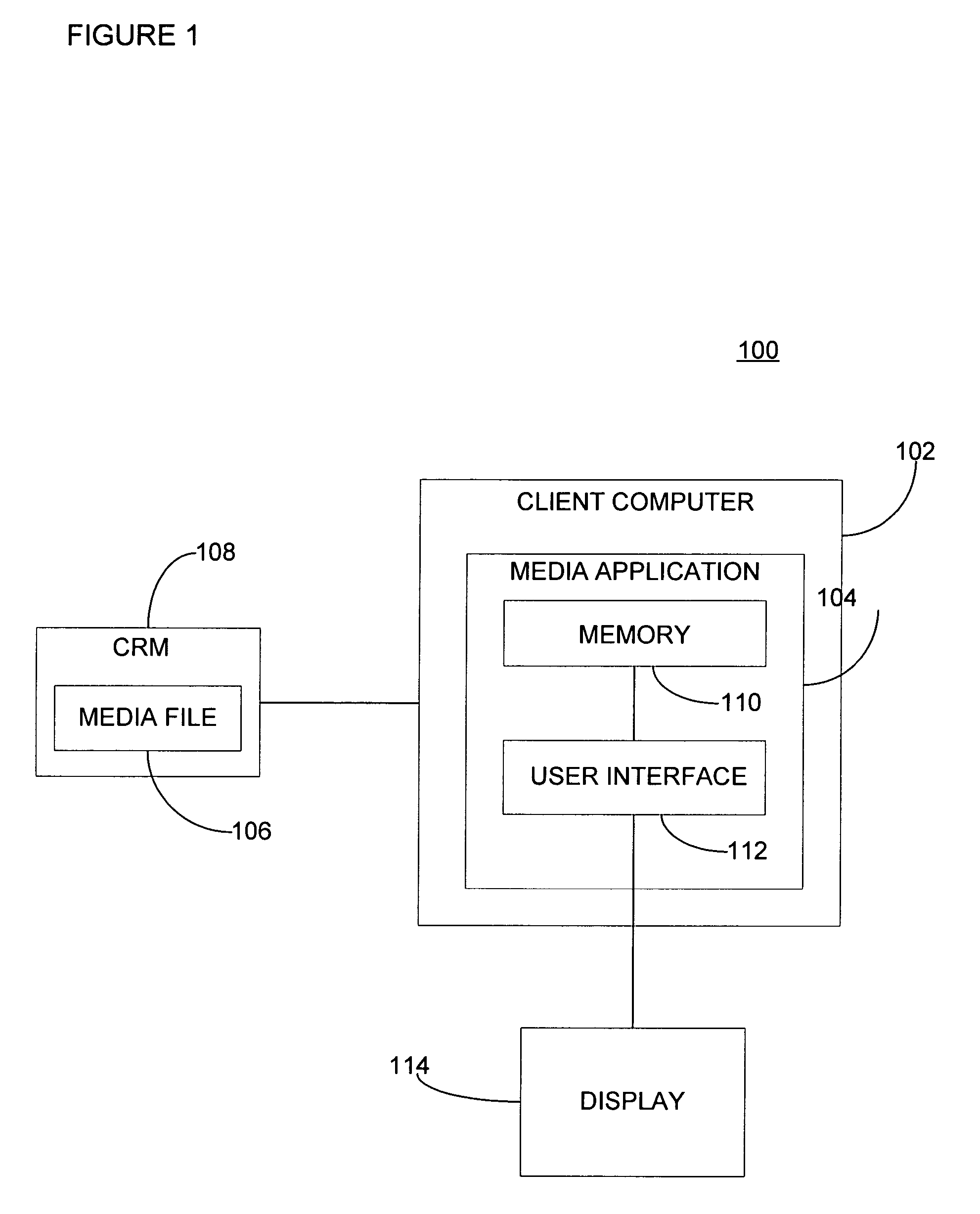
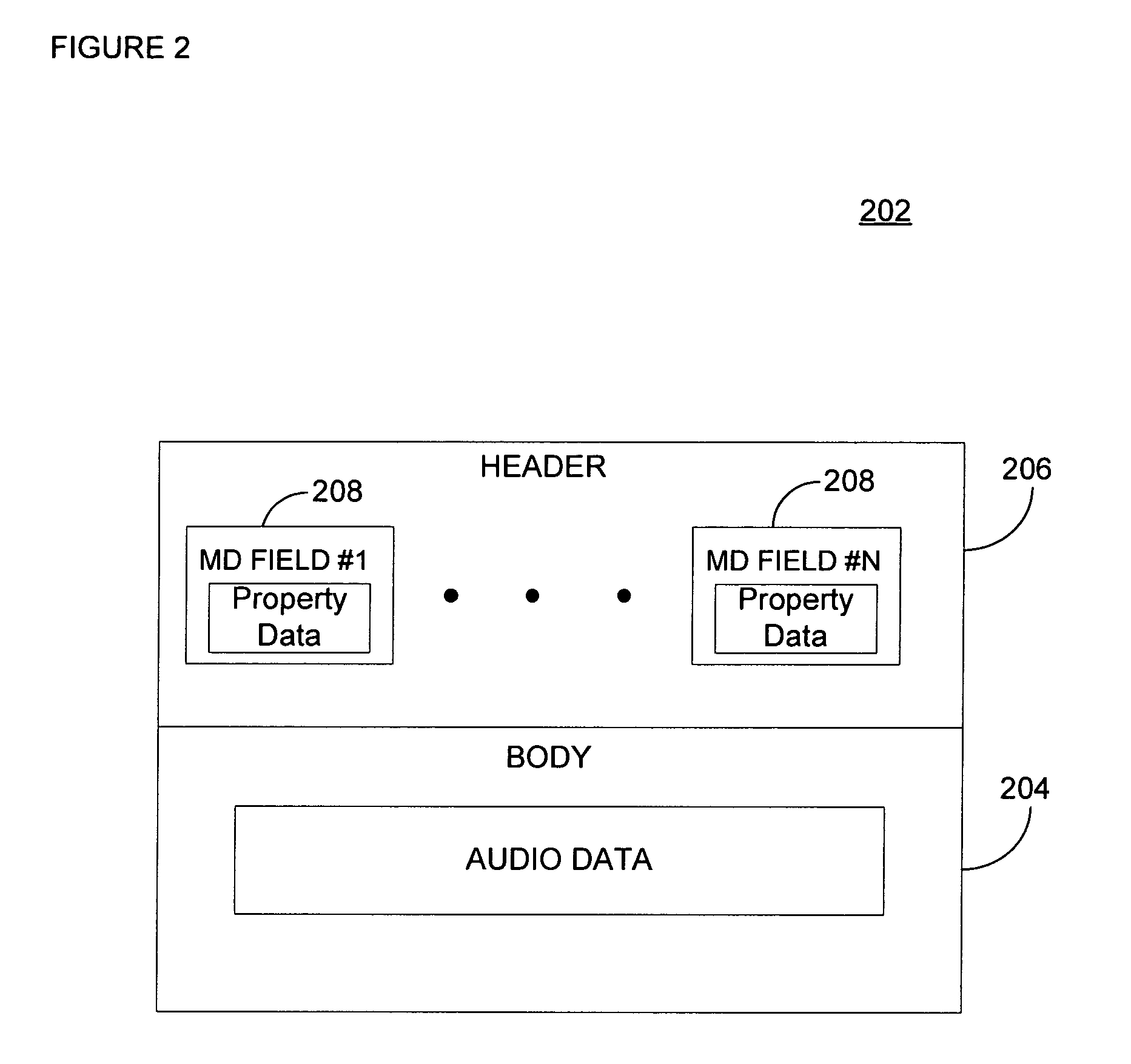
Network-based data collection, including local data attributes, enabling media management without requiring a network connection
InactiveUS20060085383A1Easy to createFlat record carrier combinationsDigital data information retrievalGeographic regionsNetwork connection
Consistent user experience of playlist capabilities, despite differences in available resources and on-line connectivity, is provided. Data embedded in a playback device compensates for lack of connectivity. For compactness, embedded data can be targeted to geographic region(s) by selecting metadata for recordings containing audio using statistics on playback of the recordings in many geographic regions. The statistics and corresponding metadata are segregated by the geographic regions. Then a portion of the corresponding metadata is selected for at least one of the geographic regions based on the statistics. By using statistics that indicate popularity of recordings within geographic regions based on frequency of playback or requests for information about a recording when it is played, the portion of the corresponding metadata that is selected can be tailored for individual geographic regions. To ensure that subregions and genres are not totally excluded, the portion selected may not be solely based on popularity.
Owner:GRACENOTE
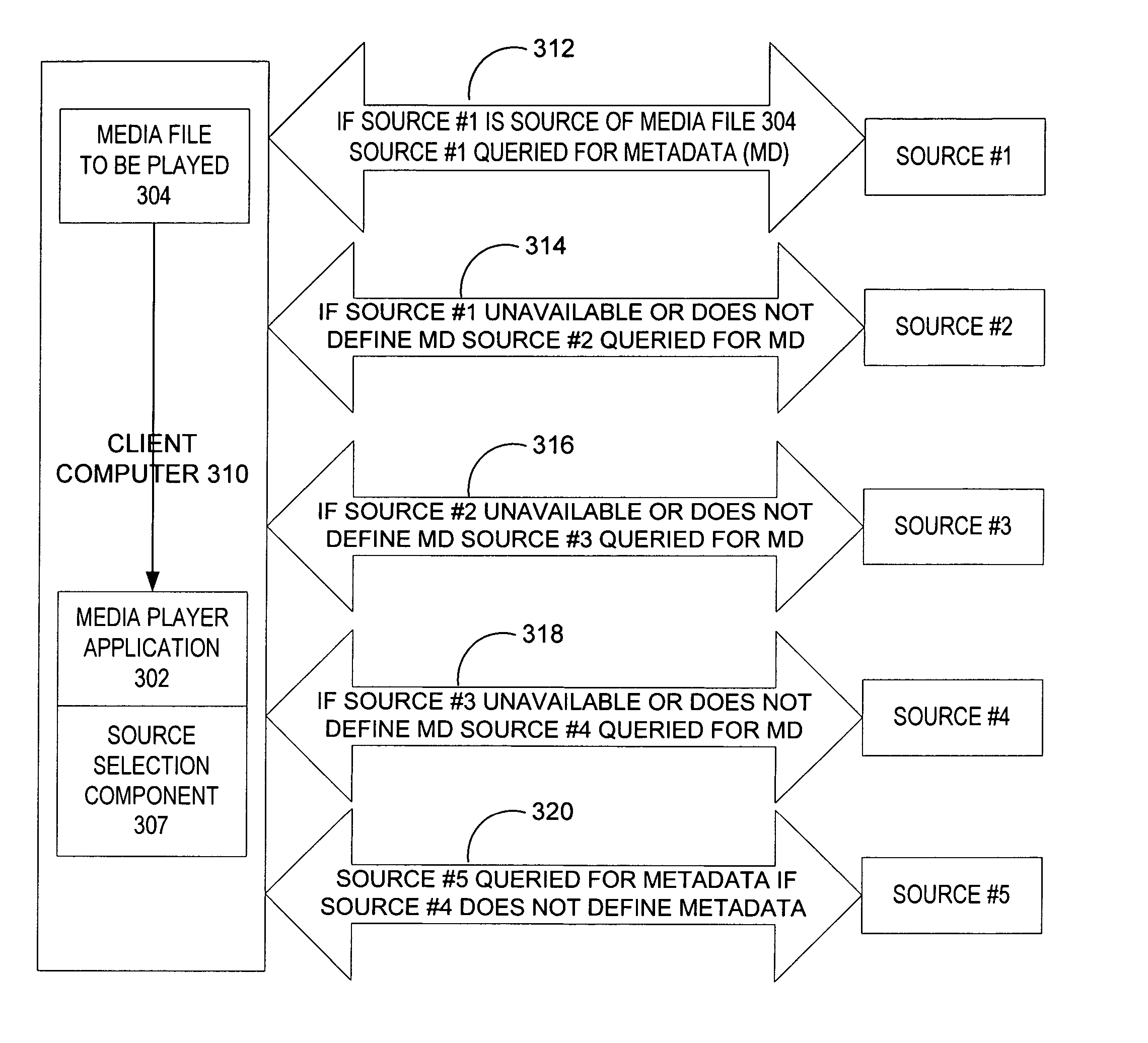
Intelligent metadata attribute resolution
InactiveUS20050015389A1Improve user experienceReduce retrieval timeMetadata multimedia retrievalSpecial data processing applicationsGraphicsGraphical user interface
A method and system for retrieving metadata for a media file. A source selection component includes instructions for querying a plurality of metadata sources in a predetermined order to retrieve metadata for the media file. The source selection component also includes instructions for retrieving metadata from metadata sources according business rules as required for specific metadata. A graphical user interface displays metadata from the first source identified as having available metadata, or displays metadata from the source designated by business rules.
Owner:MICROSOFT TECH LICENSING LLC
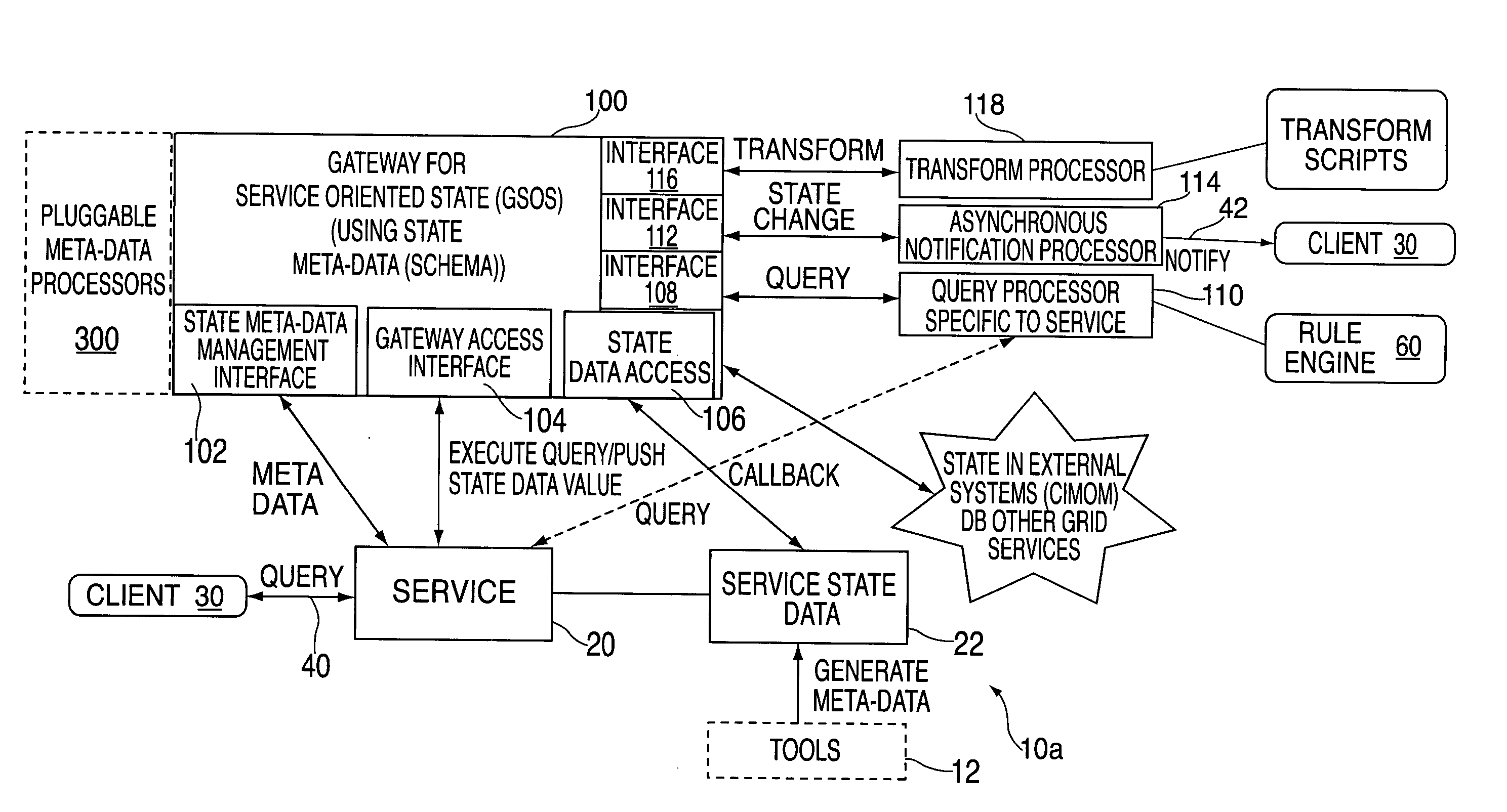
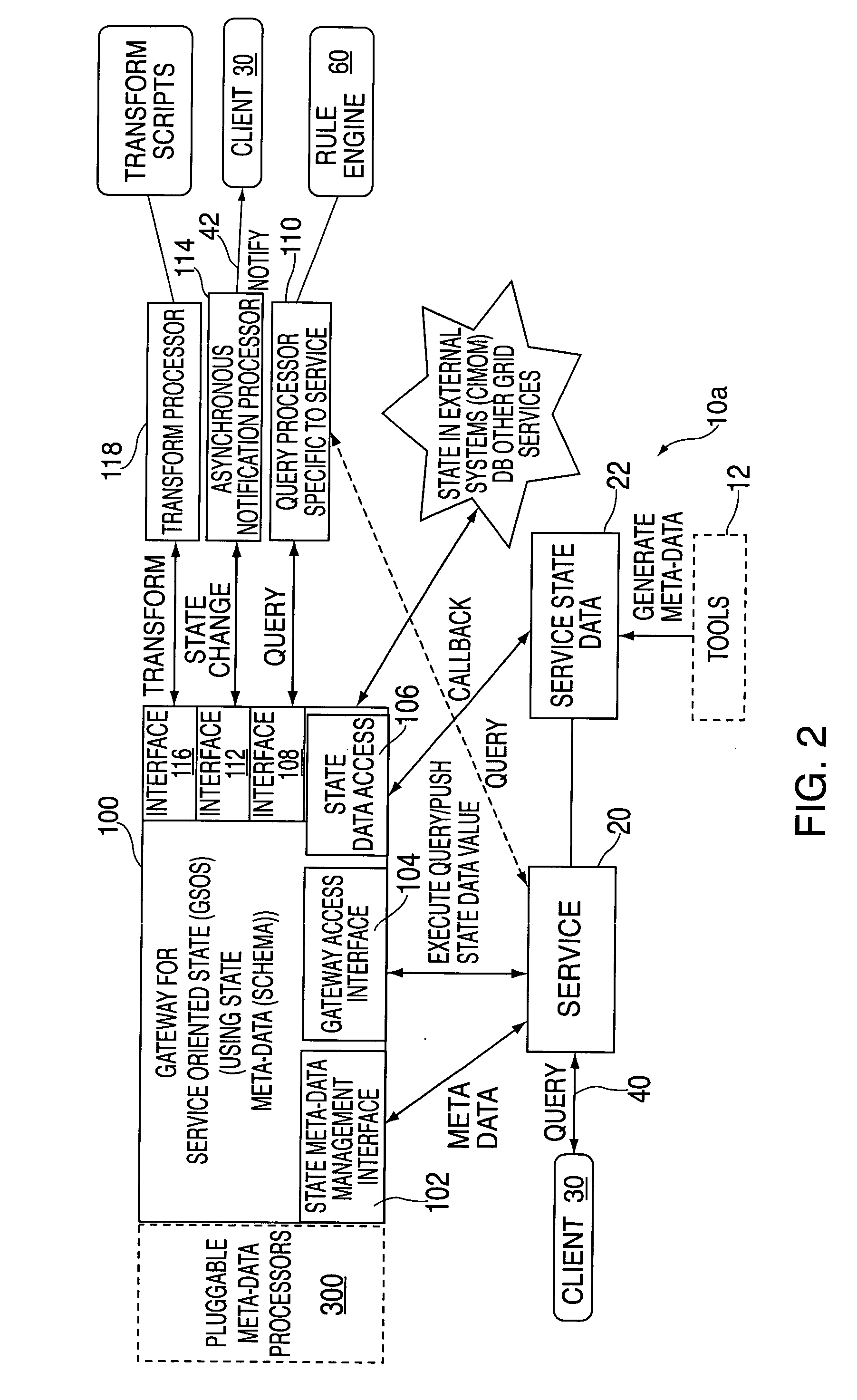
Pluggable state meta-data processors based on meta information modeling in a service oriented architecture
ActiveUS20050050311A1Multimedia data retrievalDigital computer detailsData informationService-oriented architecture
A method and system for managing service state data of a service in a service-oriented architecture by establishing a pluggable meta-data processor comprising: establishing a platform independent, extensible meta-data information model to define meta-data about service state data; establishing an extensible meta-data definition comprising an extensible set of service state data attributes; configuring one or more extensible semantic processors; configuring a controller meta-data processor; and defining contracts among the semantic processors.
Owner:IBM CORP
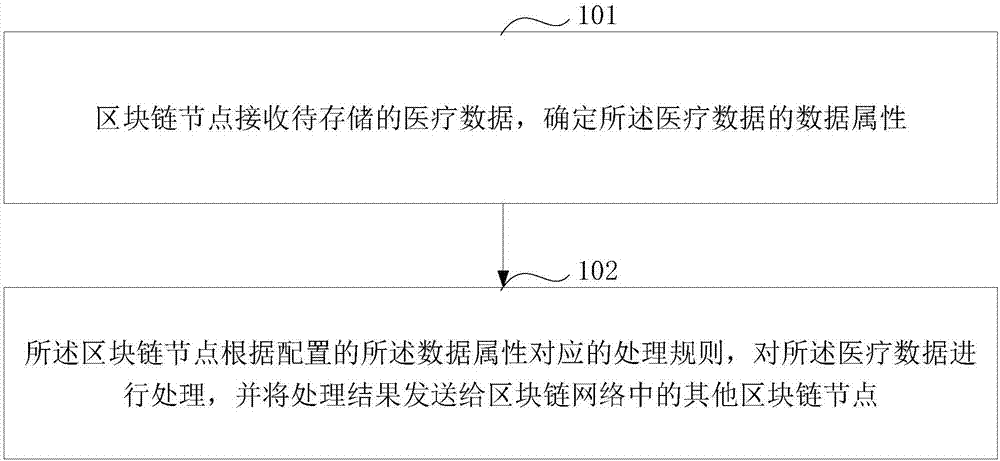
Method and device for data processing based on block chain
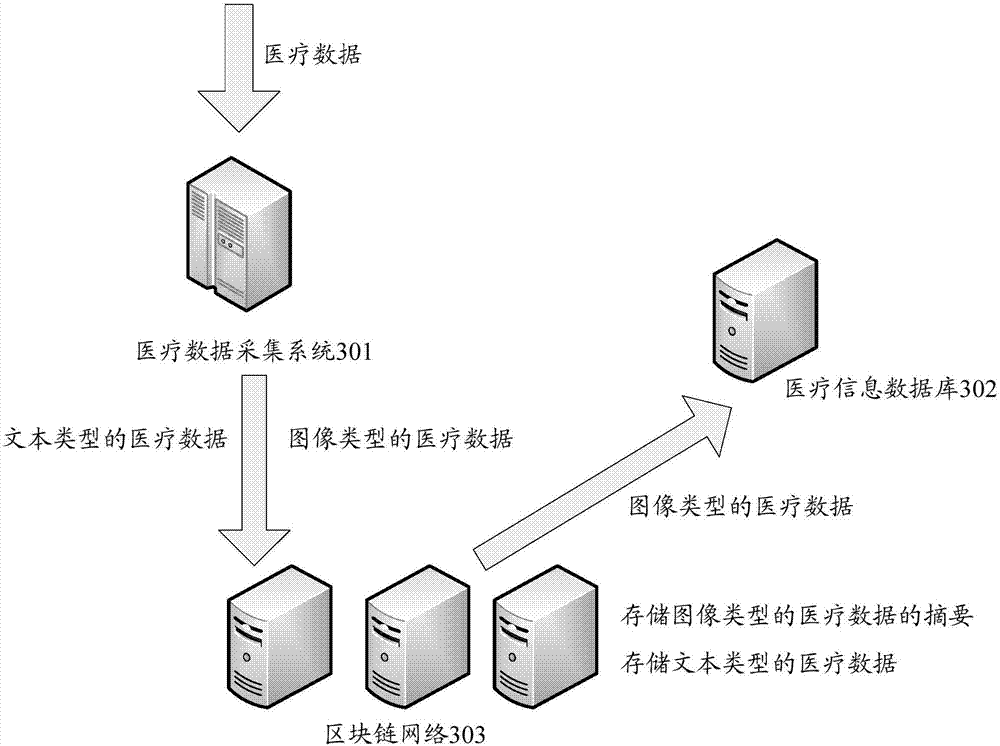
ActiveCN107426170AGuarantee authenticityNot tampered withComputer security arrangementsSpecial data processing applicationsTamper resistanceData authenticity
The present invention discloses a method and device for data processing based on a block chain. The method comprises: when a block chain node receives business data to be stored, determining the data attributes of the business data; if the data attributes of the business data is a text type, employing a preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the business data; and if the data attributes of the business data is an image type, determining the abstract of the business data, and employing preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the abstract. The features of decentration, openness and transparency, tamper resistance and dependability of the block chain technology are employed to employ different processing modes according to the data attributes of the business data to store the business data into the block chain network so as to ensure the business data authenticity and ensure that the business data is not tampered.
Owner:ADVANCED NEW TECH CO LTD
Ranking graphical visualizations of a data set according to data attributes
A computer-implemented system, method and computer readable medium to generate graphical visualizations corresponding to a data set populated in a web-based document, such as a spreadsheet. The spreadsheet is accessible in an interne or cloud-based system, and enables users to automatically create graphical visualizations or representations based on recommendations by a spreadsheet application. The graphical visualizations may be automatically ranked such that the system provides the recommendations to the user for display. Automatic ranking is accomplished, for example, by determining data types from identifying column type, differentiating column types, and extracting data sets having attributes corresponding to various graphical visualizations.
Owner:GOOGLE LLC
Extensible data model for use in an integrated platform for creating a distribution multiapplication online presence
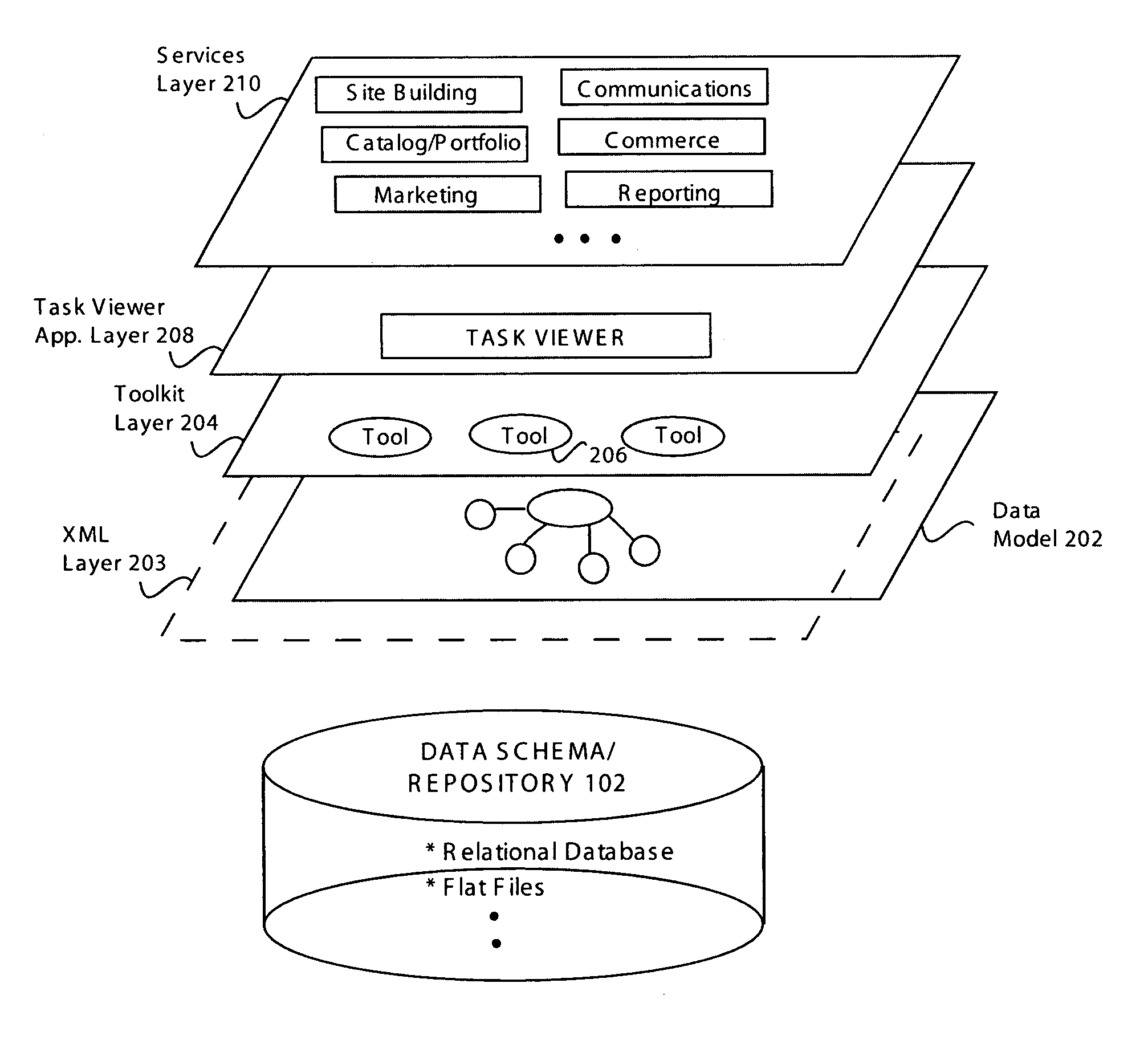
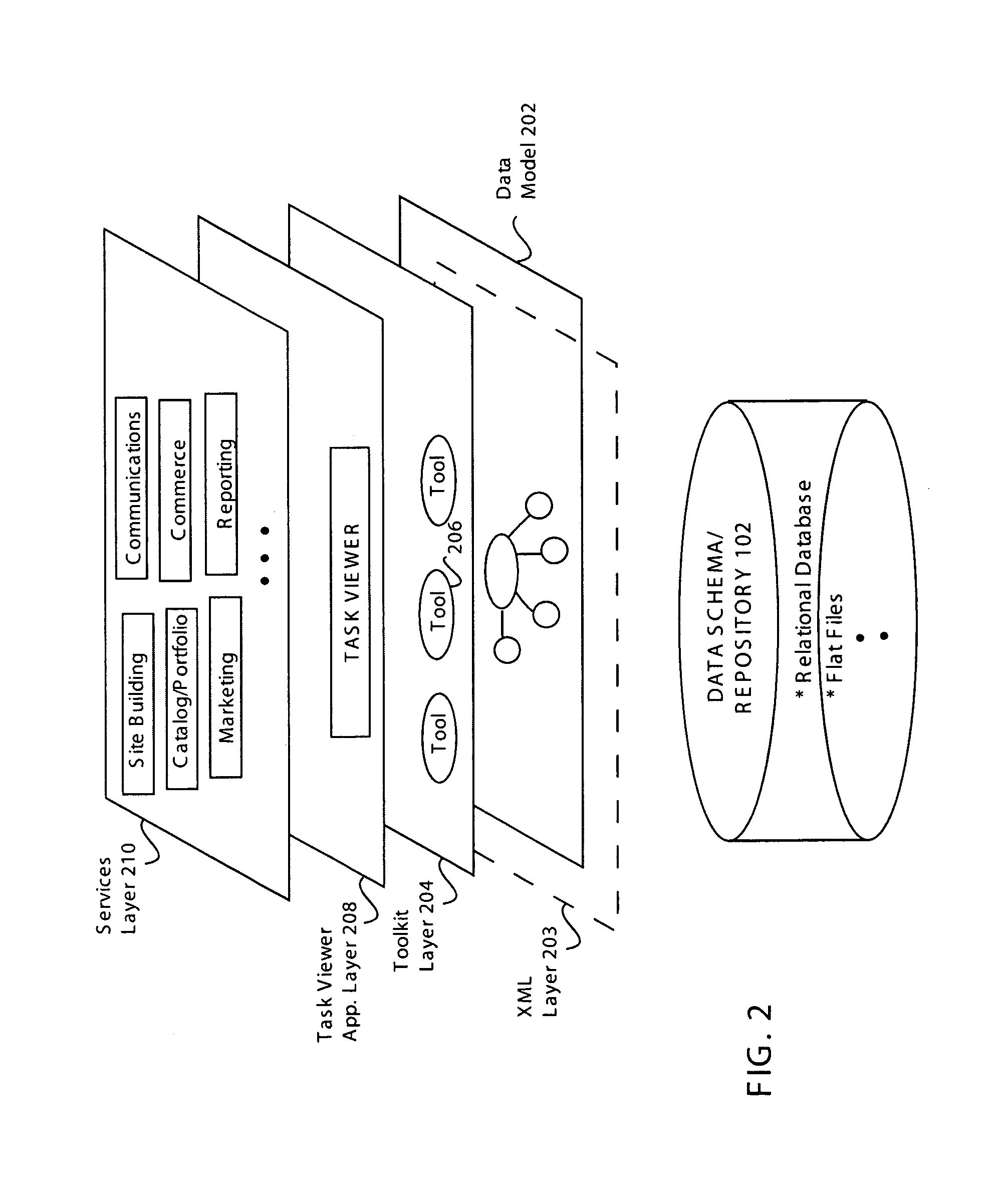
InactiveUS7219327B1Software maintainance/managementRequirement analysisApplication softwareIntegration platform
Data constructs and architectures are disclosed for providing a foundation for an application-building system for enabling a non-technical user to perform discrete tasks to build a complete network-based application and maintain the same user experience throughout the application development. A data model having an extensible underlying structure that can be used in a user-oriented application development system having a task-based architecture is defined. The data model is capable of allowing for extensible attributes such that the addition of a new data attribute can be made without changing the underlying structure of the data model. Multiple applications making up the user-oriented application development system can access data from the data model. Data stored in a database having the data model as an underlying structure can be reused by the task-based architecture for various applications.
Owner:HOSTWAY SERVICES INC
Method of representing road lanes
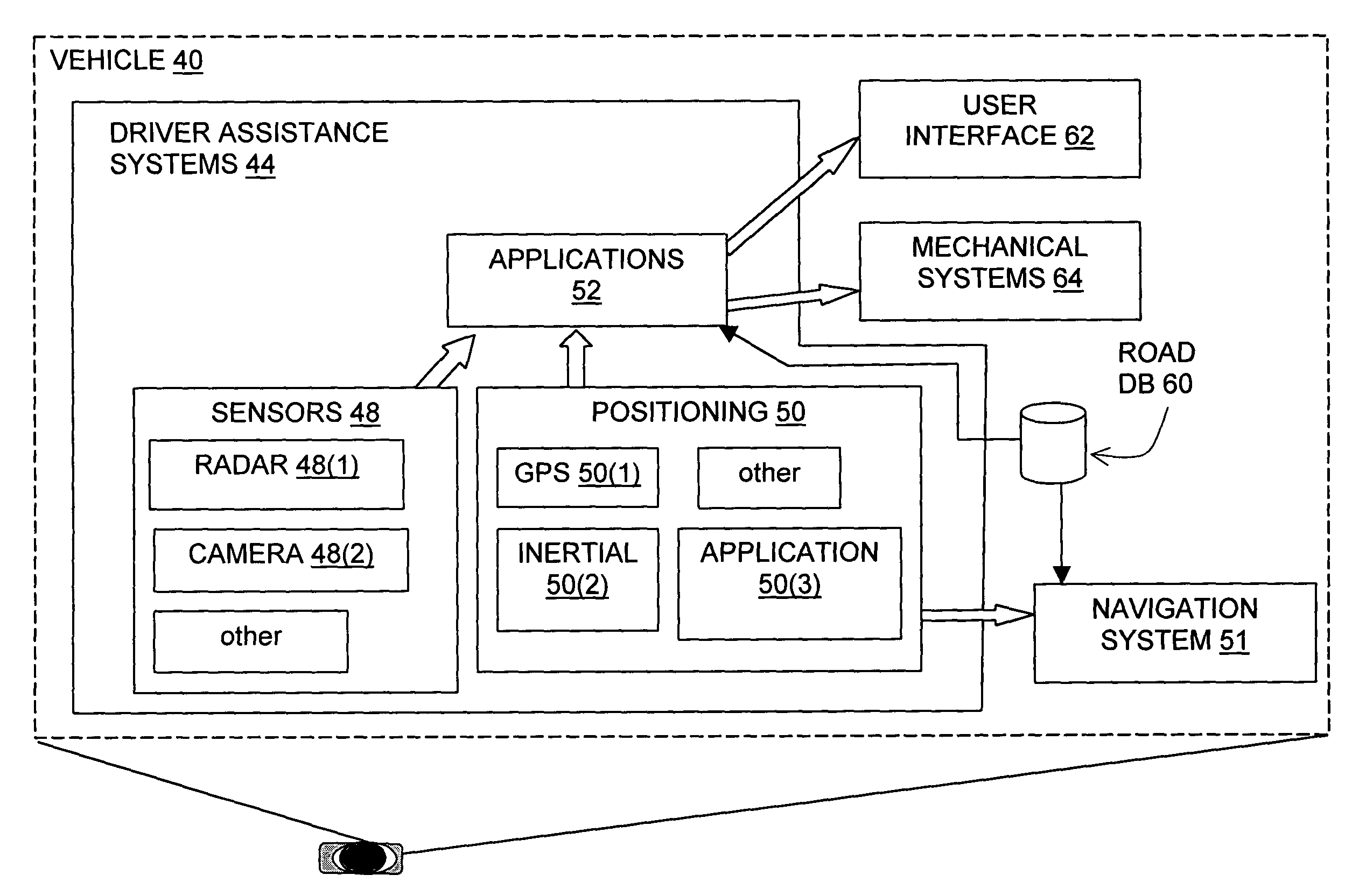
InactiveUS20050004753A1Instruments for road network navigationRoad vehicles traffic controlSystem usageComputer science
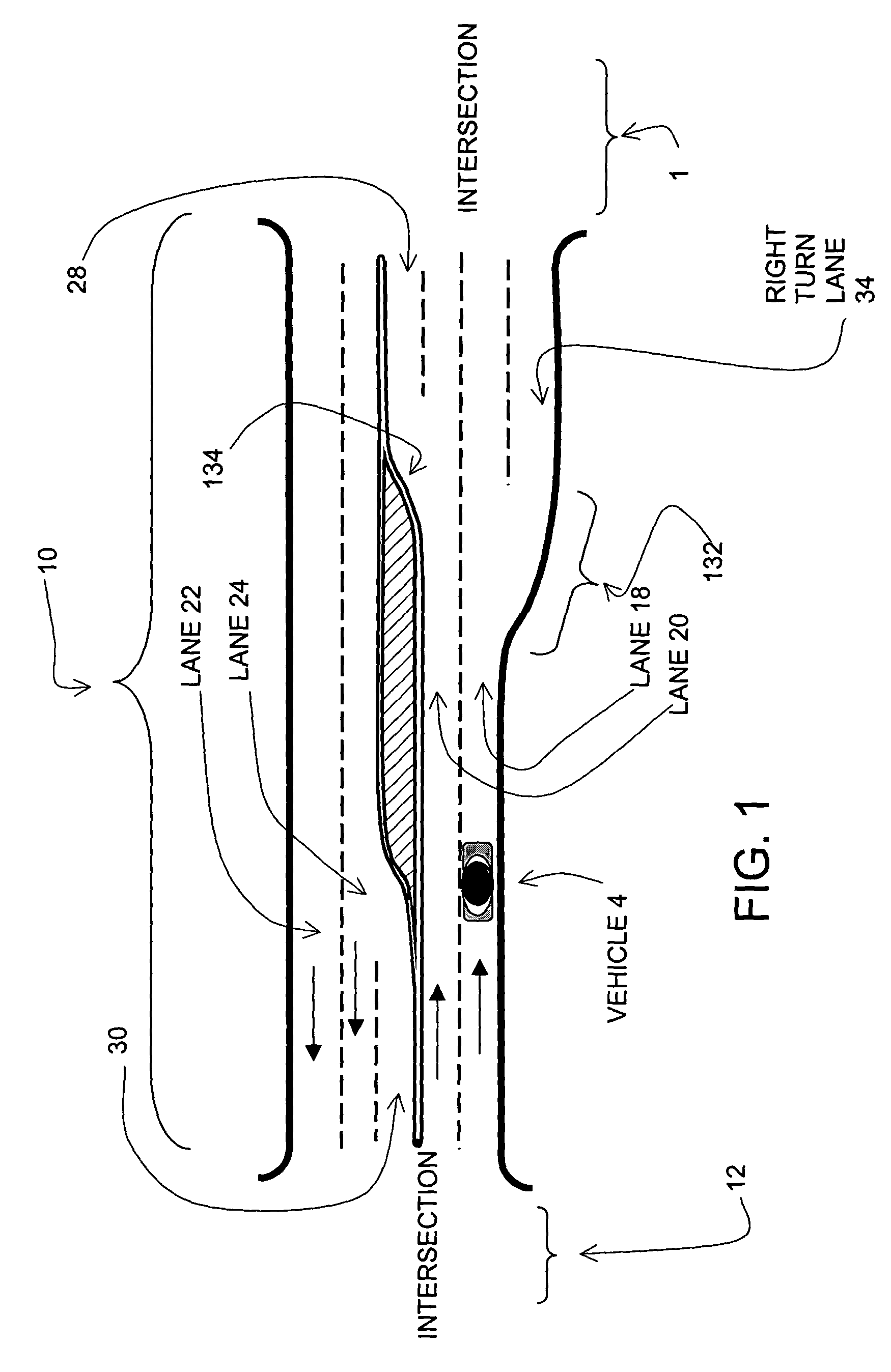
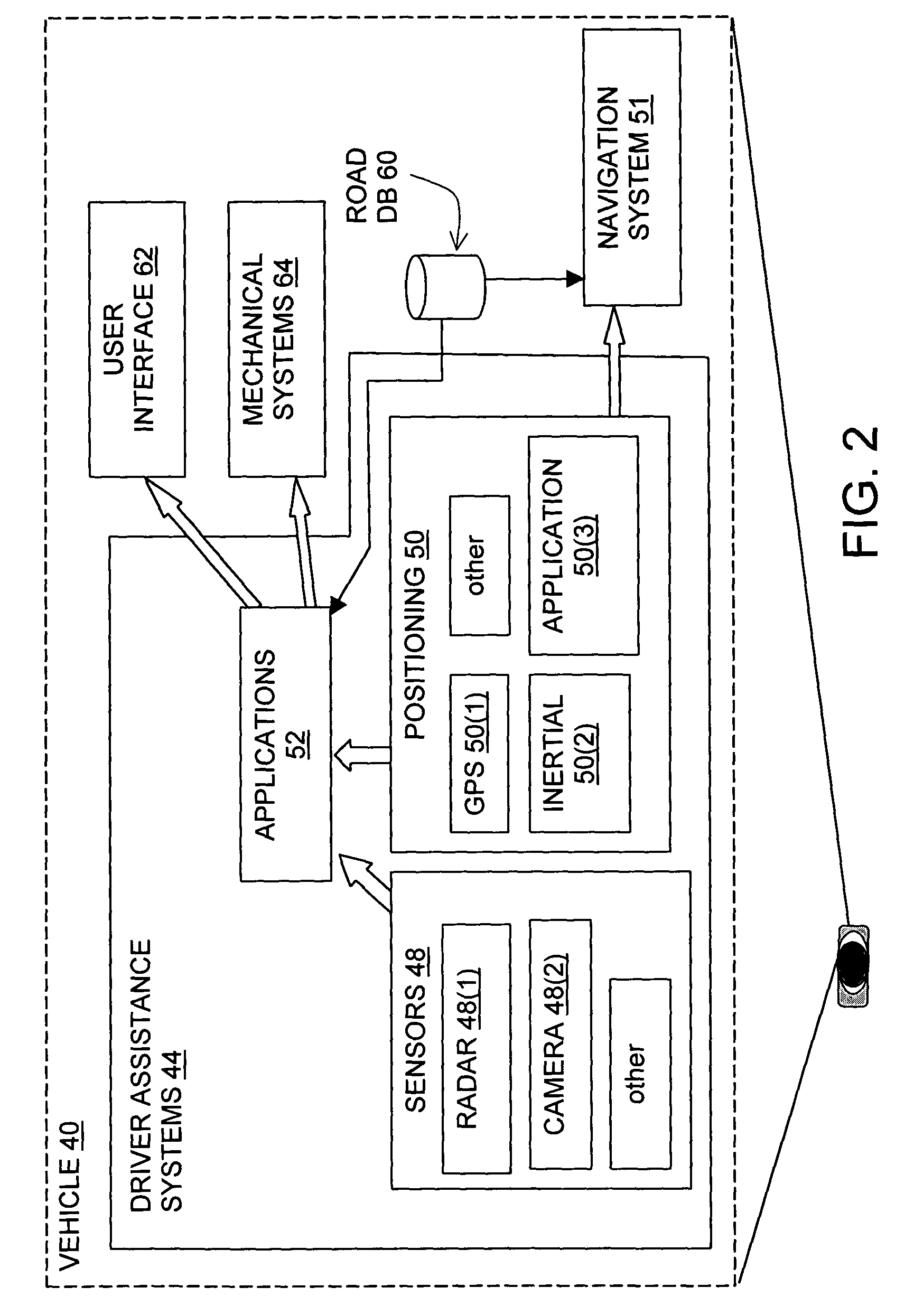
A method is disclosed for representing road lanes as data in a database that can be used by a system in a vehicle to provide a safety-related function. Each data representation of a physical road lane includes data indicating start and end points of the represented lane and other data attributes pertaining to the represented lane, including data indicating what physical features are adjacent to the represented lane on right and left sides thereof and data indicating a geometry of the represented lane. Further, at least some of the data representations of lanes are associated with data representations of sublanes. Each data representation of a sublane includes data indicating start and end points thereof, defined relative to the lane of which the sublane is a part. A data representation of a sublane includes at least one data attribute associated therewith that pertains to the represented sublane and that is different than the same attribute of the lane of which the sublane is a part. The database is compatible with navigation-related applications that use a different data model to provide navigation-related functions.
Owner:HERE GLOBAL BV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com