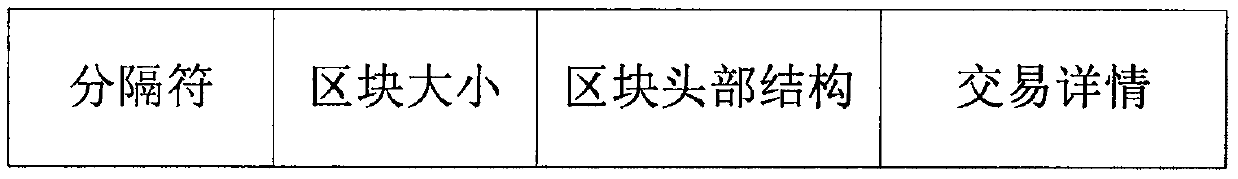
Patents
Literature
121results about How to "Not tampered with" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
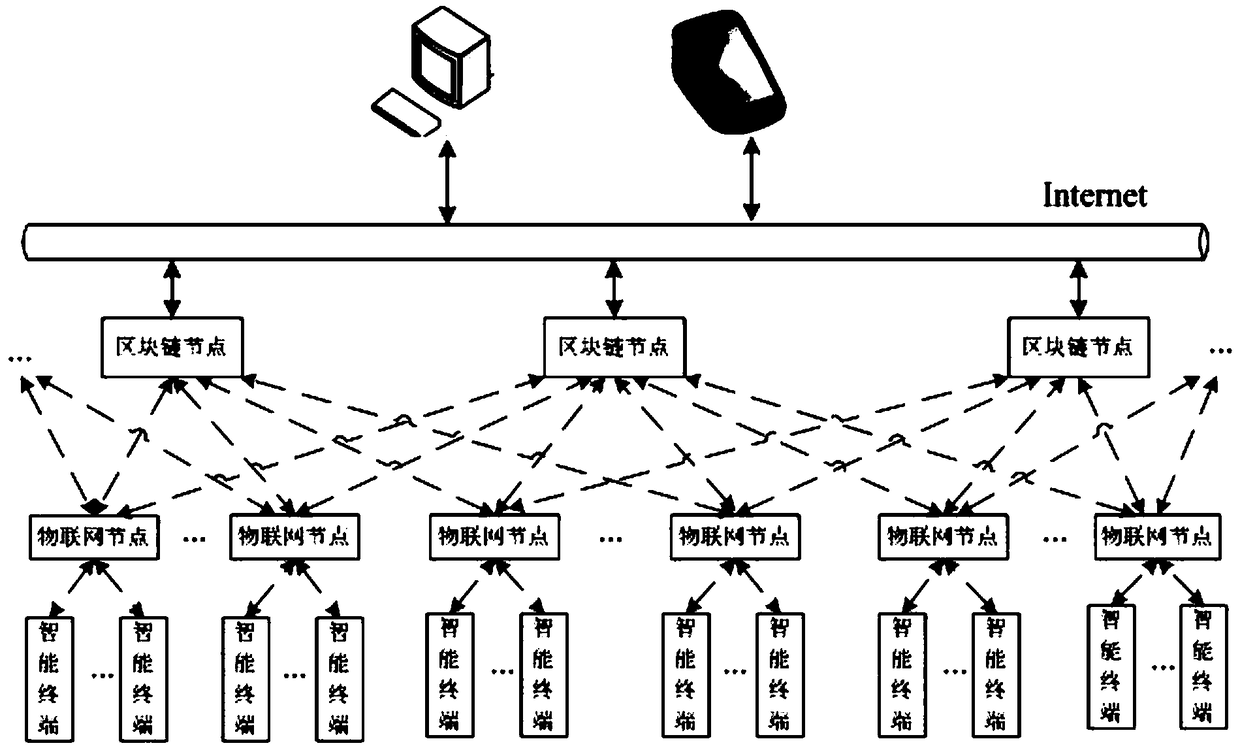
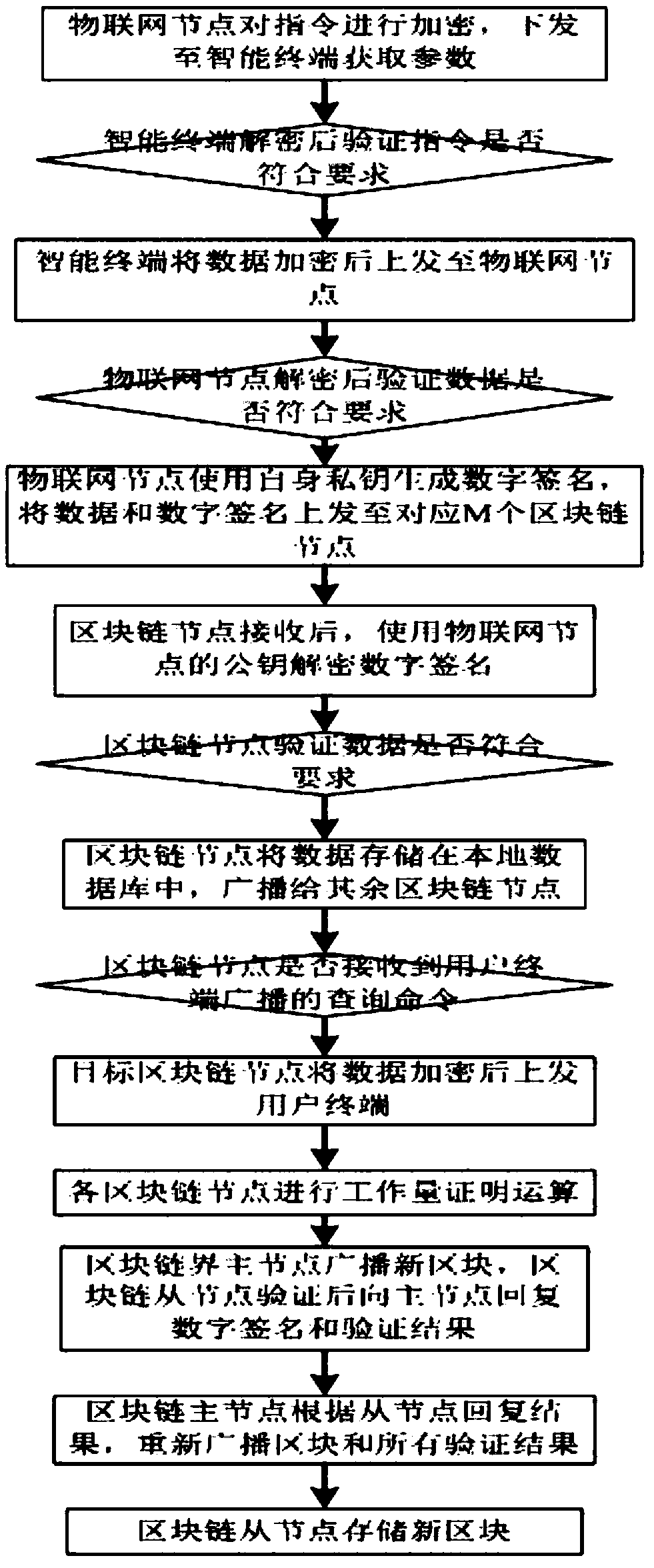
Construction equipment Internet of Things system and method based on blockchain technology
ActiveCN108632293ASolve processing problemsSaving facilityEncryption apparatus with shift registers/memoriesUser identity/authority verificationElectrical devicesThe Internet
The invention discloses a construction equipment Internet of Things system and method based on the blockchain technology. The system comprises a plurality of Internet of Things nodes, a plurality of blockchain nodes, a plurality of intelligent terminals and a plurality of user terminals, the detection of various environmental information in the building and the monitoring of electrical equipment can be achieved, data are stored in the blockchain nodes in a distributed manner, a data transmission process is encrypted by using the asymmetric encryption technology, and data sharing is performed through a smart contract. According to the construction equipment Internet of Things system and method disclosed by the invention, the blockchain technology is combined with the Internet of Things technology, the consensus mechanism, distributed storage, asymmetric encryption and smart contract of the blockchain technology are applied to the Internet of Things, and many problems faced by the current Internet of Things are solved.
Owner:SHANDONG JIANZHU UNIV
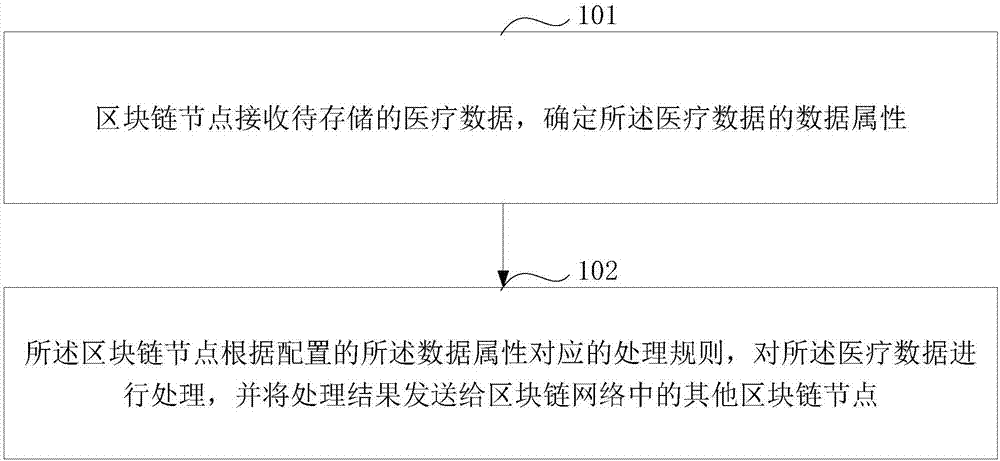
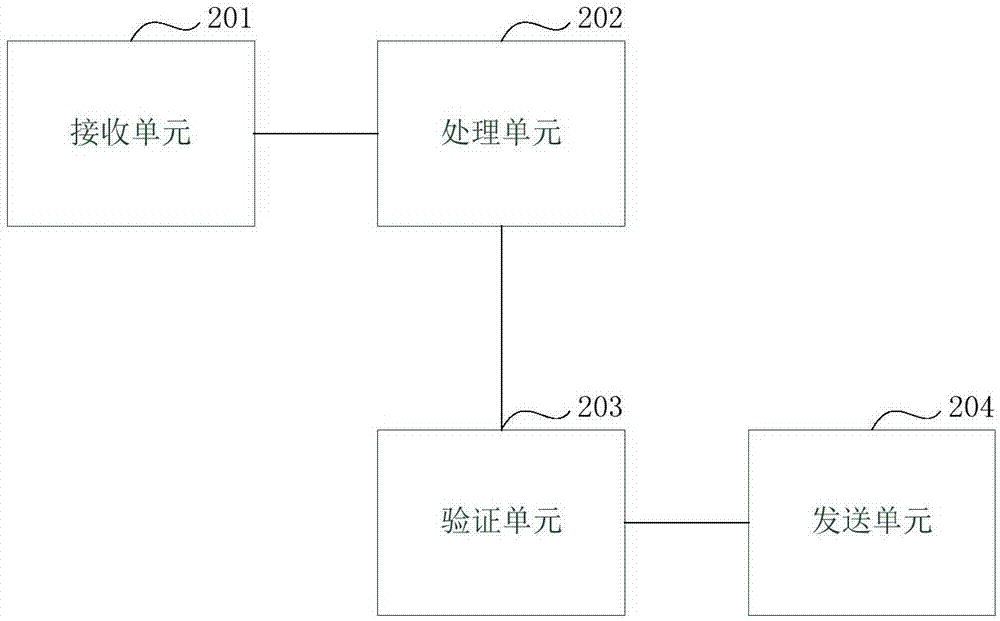
Method and device for data processing based on block chain
ActiveCN107426170AGuarantee authenticityNot tampered withComputer security arrangementsSpecial data processing applicationsTamper resistanceData authenticity
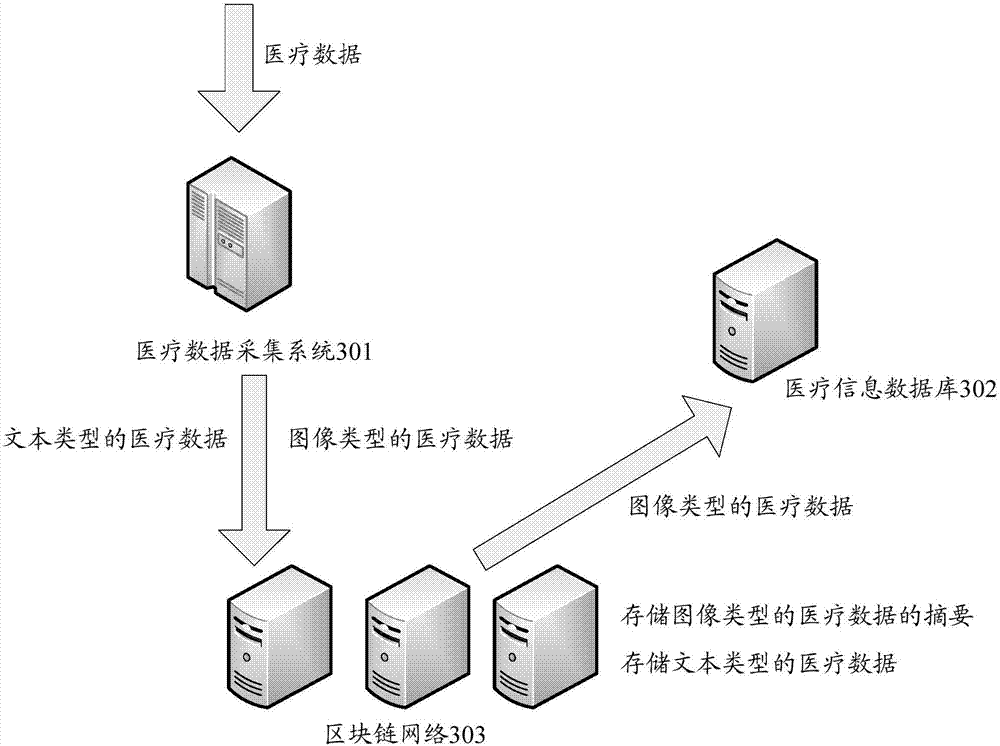
The present invention discloses a method and device for data processing based on a block chain. The method comprises: when a block chain node receives business data to be stored, determining the data attributes of the business data; if the data attributes of the business data is a text type, employing a preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the business data; and if the data attributes of the business data is an image type, determining the abstract of the business data, and employing preset private key in a public and private key pair corresponding to the user identification included in the business data to perform encryption processing of the abstract. The features of decentration, openness and transparency, tamper resistance and dependability of the block chain technology are employed to employ different processing modes according to the data attributes of the business data to store the business data into the block chain network so as to ensure the business data authenticity and ensure that the business data is not tampered.
Owner:ADVANCED NEW TECH CO LTD
Block chain based PKI (public key infrastructure) system and semi-random joint certificate signature method
ActiveCN106789090ANot tampered withNot forgedUser identity/authority verificationWeb serviceCertificate authority
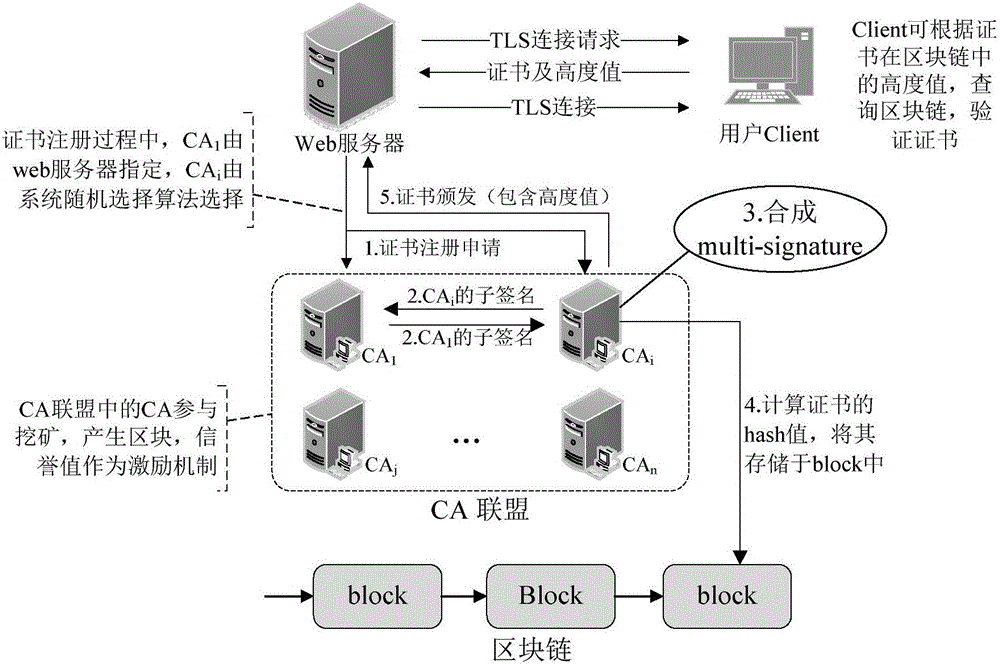
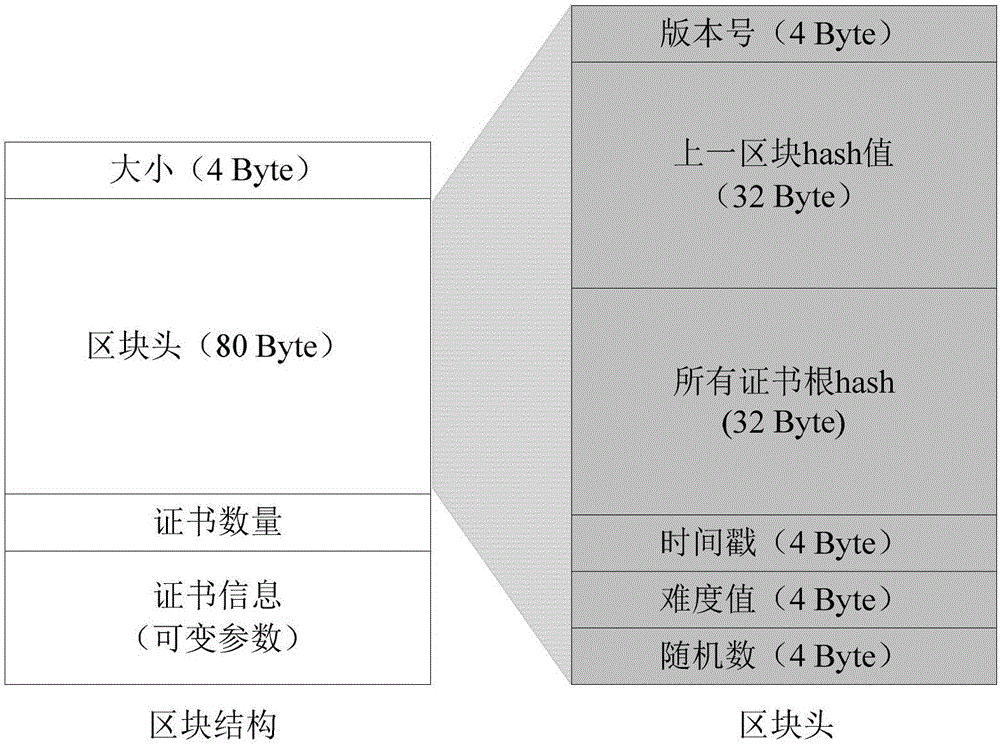
The invention discloses a block chain based PKI (public key infrastructure) system and a semi-random joint certificate signature method. The system comprises a user Client, a Web server and a plurality of CAs (certificate authorities), wherein the plurality of CAs constitute a CA coalition; the Web server applies to the plurality of CAs for a certificate, the plurality of CAs sign jointly, then the certificate is stored in a block chain, after storage, the CAs issue the certificate to the Web server, and when the user Client and the Web server are in TLS connection, the user Client needs to verify the legitimacy of the certificate of the Web server.
Owner:WUHAN UNIV
System and method for controlling intelligent equipment
InactiveCN105978851AImprove securityIntegrity guaranteedTransmissionWireless controlTransfer procedure
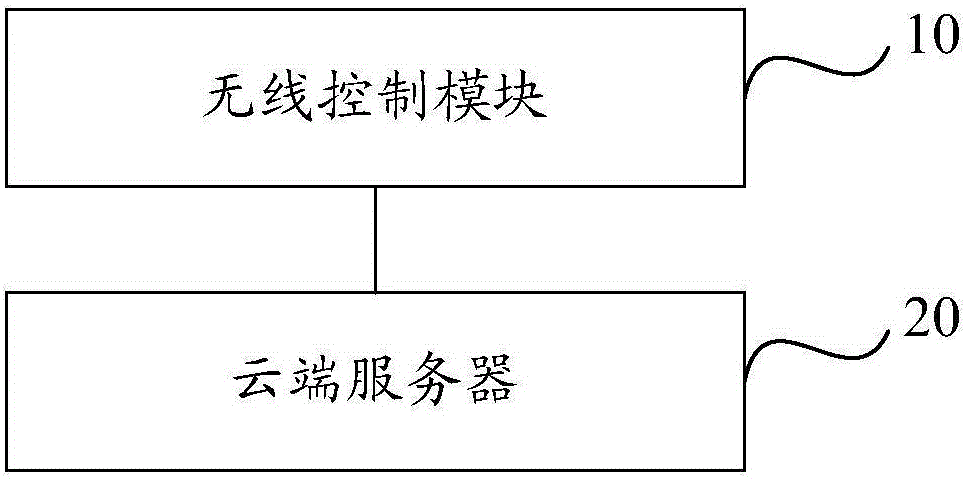
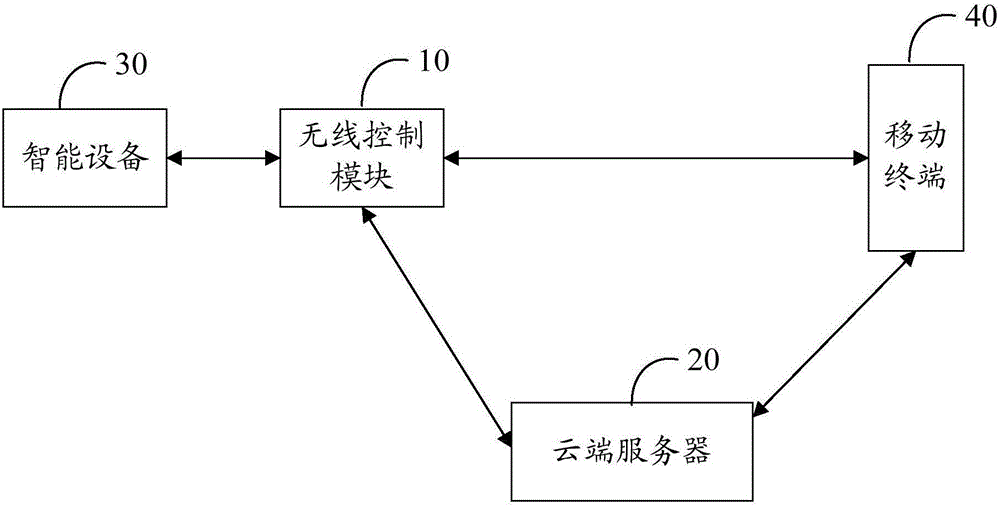
Embodiments of the present invention provide a system and method for controlling smart devices, the system at least includes: a wireless control module of the smart device, and a cloud server, wherein the message structure of the communication message transmitted between the wireless control module and the cloud server Including a message header, a message body, a message signature, and a message terminator; the communication message includes an authentication request message and a corresponding authentication response message, and the wireless control module is configured to generate an authentication request message and send the authentication request message to the cloud The server, wherein the authentication request message includes the identification of the wireless control module; the cloud server, configured to verify whether the identification of the wireless control module is legal, and generate an authentication response message according to the verification result, and return the authentication response message The wireless control module. The invention can use the message signature mechanism to ensure that the message is not tampered with in the transmission process, thereby ensuring the integrity of the communication message.
Owner:JUHAOKAN TECH CO LTD
Trusted data transmission method and system, electronic equipment and storage medium
PendingCN110535647AReduce message lossReduce message tamperingPublic key for secure communicationUser identity/authority verificationComputer securityData messages
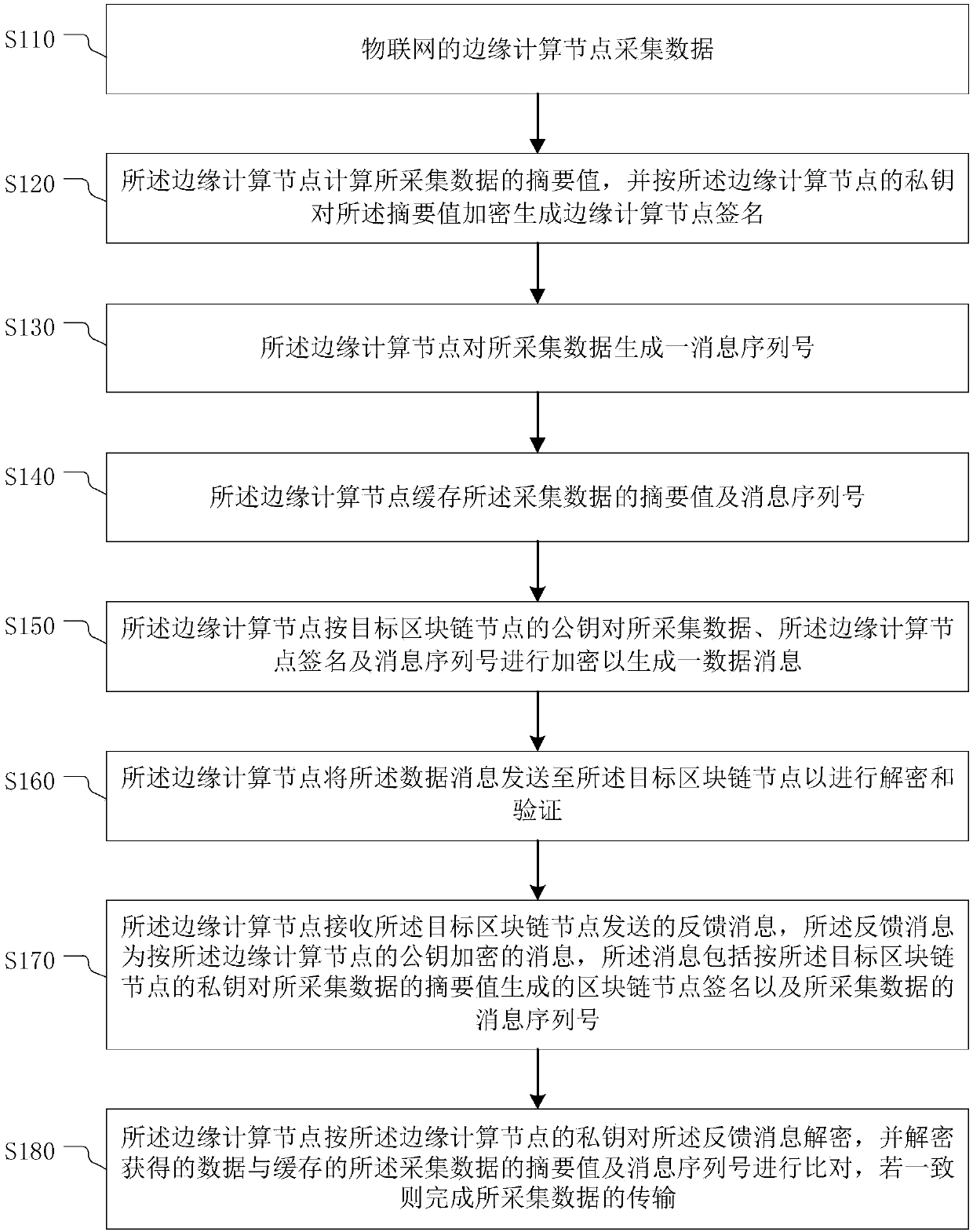
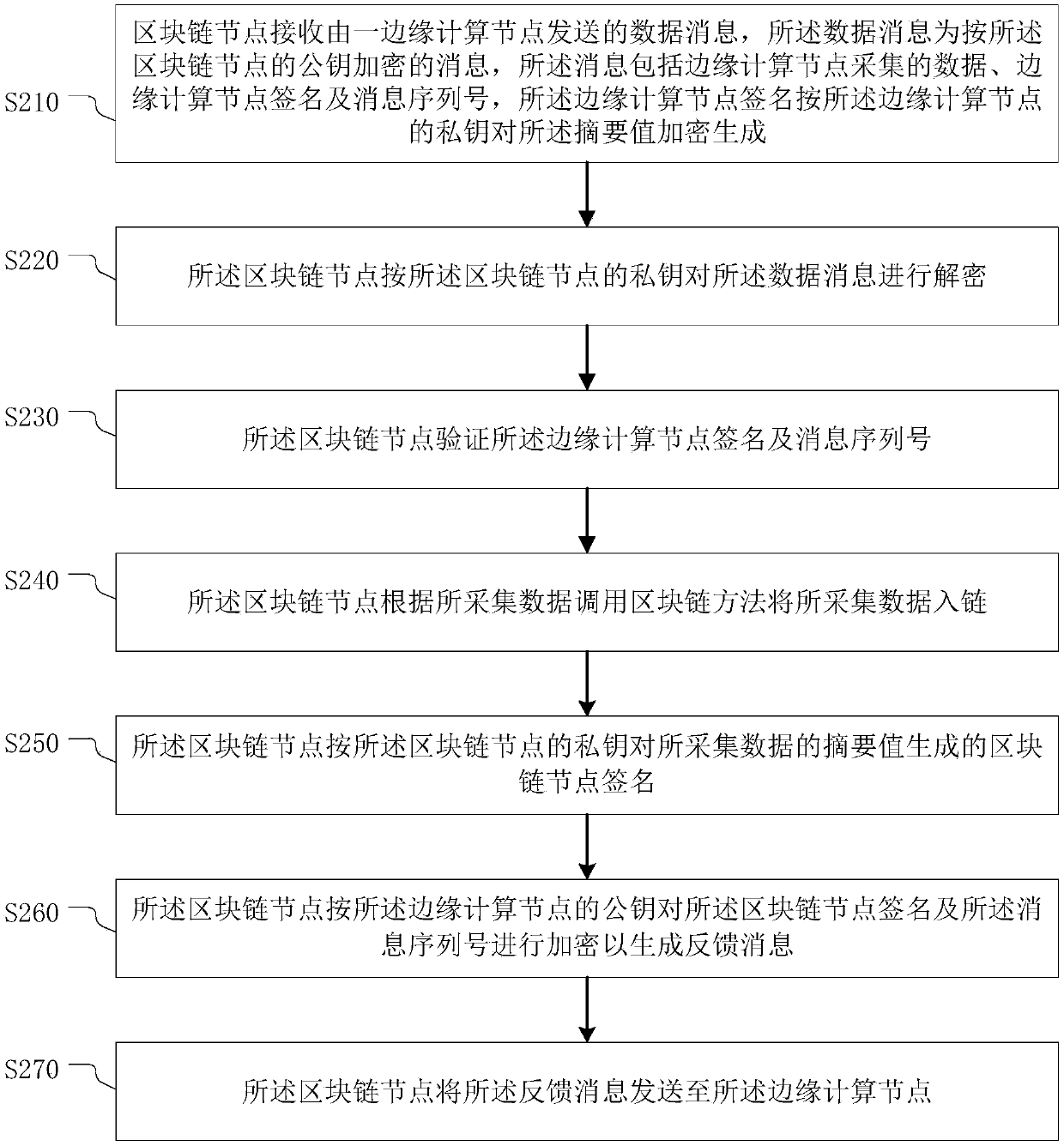
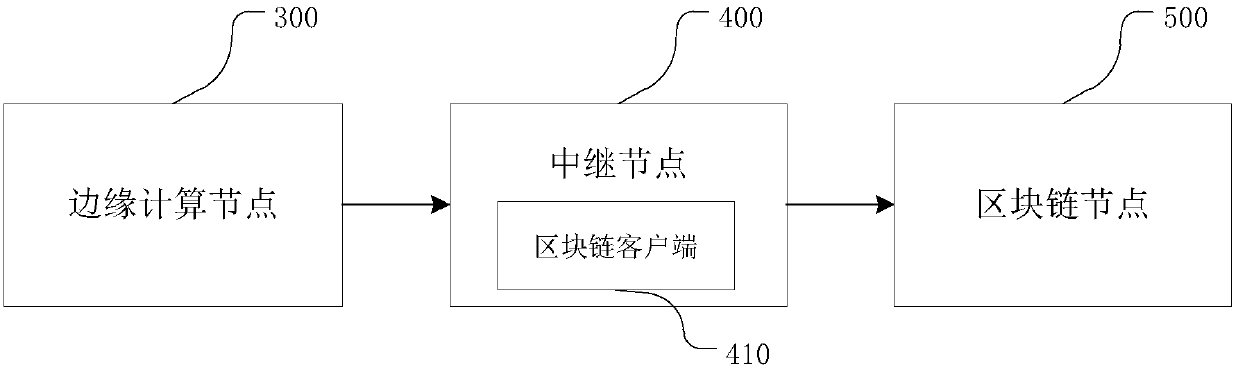
The invention provides a trusted data transmission method and a system, electronic equipment and a storage medium. The trusted data transmission method comprises the following steps: acquiring data; calculating an abstract value of the collected data, and encrypting the abstract value according to a private key of the edge computing node to generate an edge computing node signature; generating a message serial number for the acquired data; caching the abstract value and the message serial number of the acquired data; generating a data message according to the public key of the target blockchain node; sending the data message to the target blockchain node for decryption and verification; receiving a feedback message sent by the target blockchain node; and decrypting the feedback message according to the private key of the edge computing node, comparing the decrypted data with the cached abstract value and message serial number of the acquired data, and if the decrypted data is consistent with the cached abstract value and message serial number of the acquired data, finishing the transmission of the acquired data. According to the method and the device provided by the invention, thesecurity of message transmission between the Internet-of-thingsInternet-of-things and the blockchain can be realized.
Owner:上海诚频信息科技合伙企业(有限合伙)
Mobile terminal with long-range control function and its long-range control method
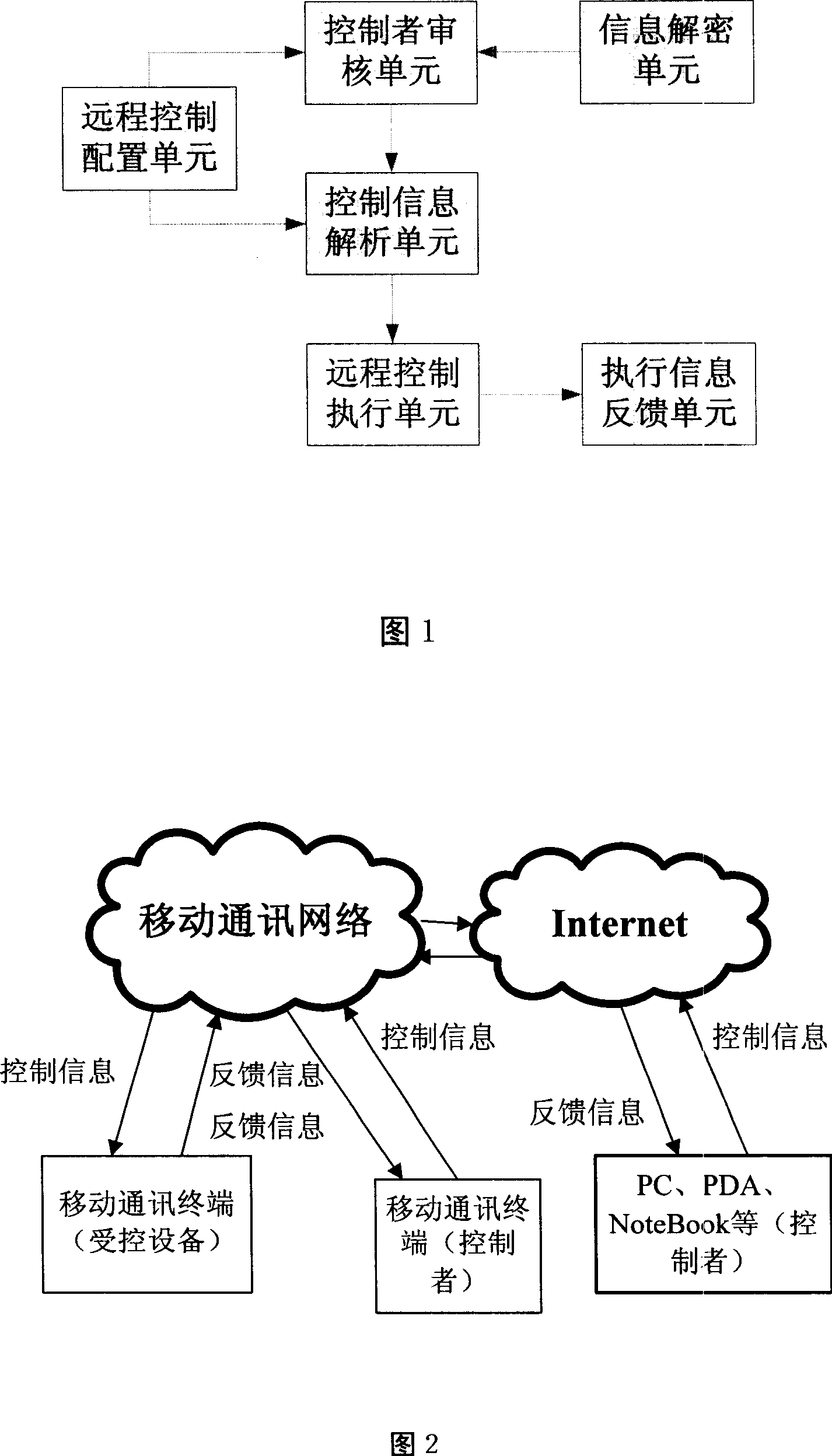
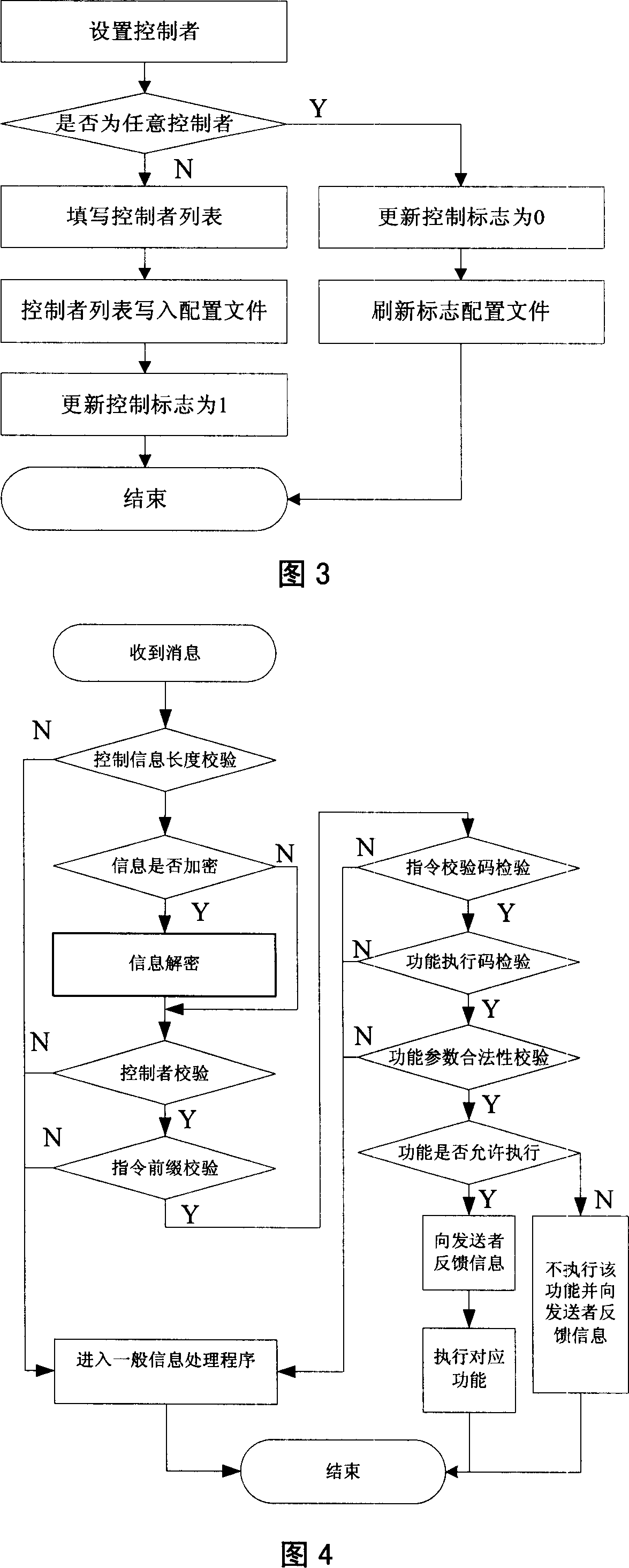
InactiveCN101005662AImprove securityVarious control methodsTelemetry/telecontrol selection arrangementsTransmission systemsControl functionControl mode
The terminal thereof comprises: a remote-control setting unit, a control-person examining unit, a control-information analyzing unit, a remote-control executing unit, an execution-information feeding back unit and a decryption unit. The invention can be used to receive the control information sent from an appointed control-person in order to ensure the remote-control can't be used by illegal users, and can be used in CDMA, GSM, and 3G mobile terminals.
Owner:KAIHONG MOBILE COMM
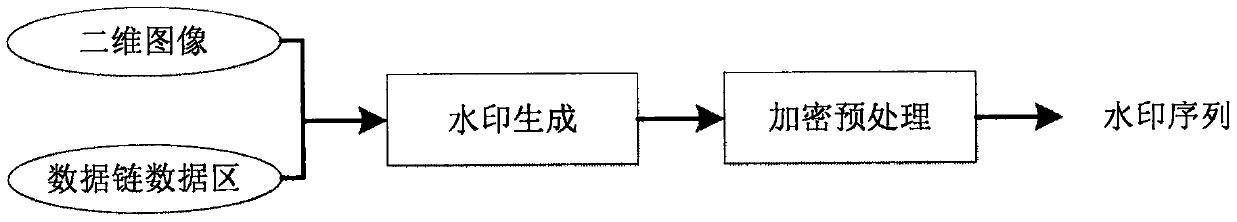
Block chain embedding method for wavelet domain watermark in image
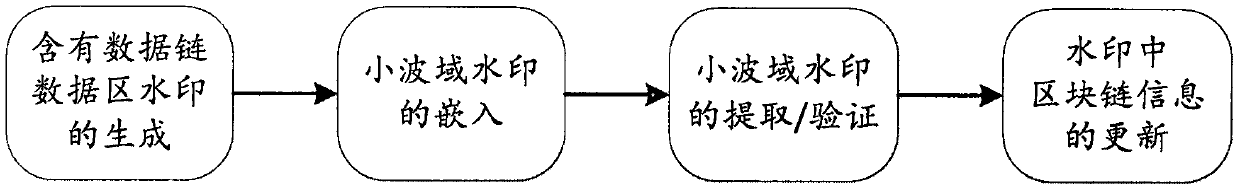
InactiveCN108053359AIntegrity guaranteedPrevent malicious tamperingImage enhancementImage analysisInformation securityDigital watermarking
The invention discloses a block chain embedding method for a wavelet domain watermark in an image. The method comprises the following steps of 1, generating a watermark containing data blocks of a block chain; 2, embedding the generated watermark containing the data blocks of the block chain into the wavelet domain watermark; 3, extracting and verifying the wavelet domain watermark; and 4, updating watermark information in the block chain. According to the block chain embedding method for the wavelet domain watermark in the image, a watermark sequence is generated by utilizing the data blocksof the block chain; a block chain technology is introduced in a digital watermark, so that the security of image information is ensured and the watermark information is prevented from being tampered by any attack means; and by updating the data blocks of the block chain in the watermark, the watermark is not modified at will in a network transmission process, attack in an invalid network is avoided, and the information security in the transmission process is ensured.
Owner:北京泛融科技有限公司
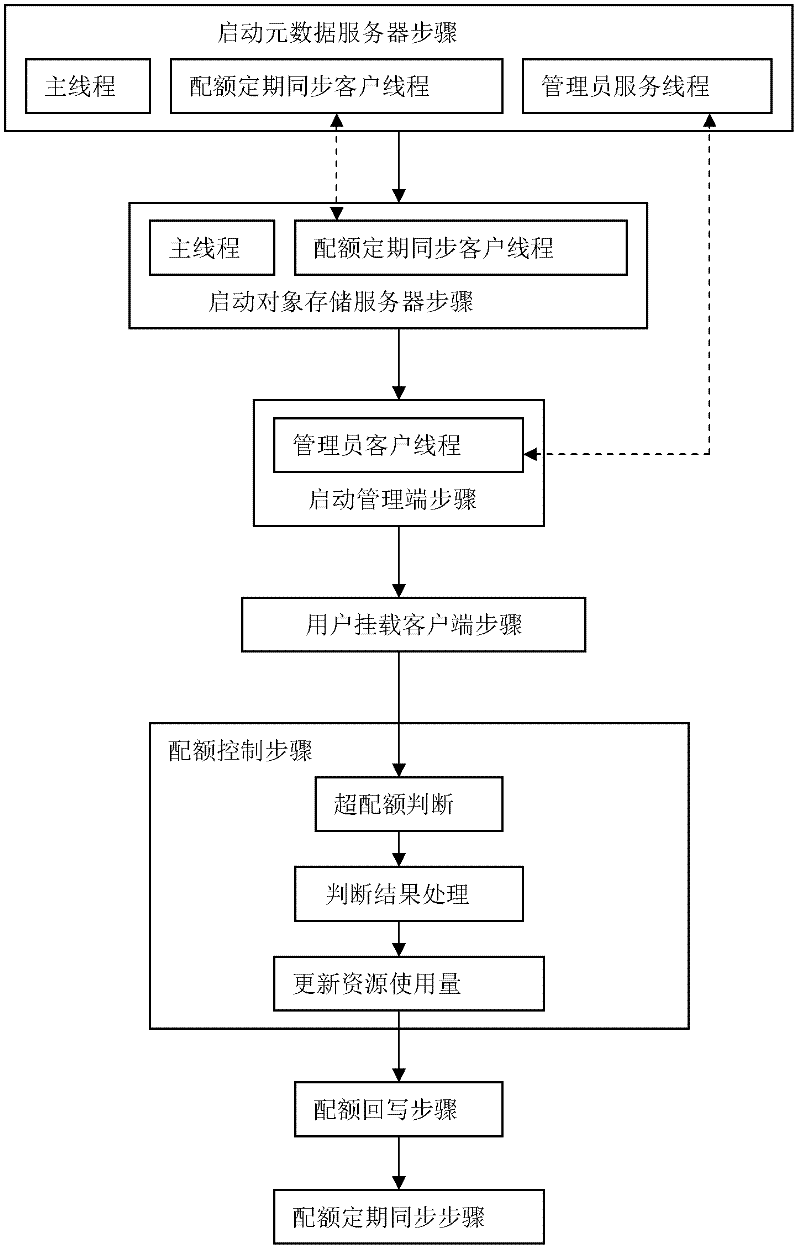
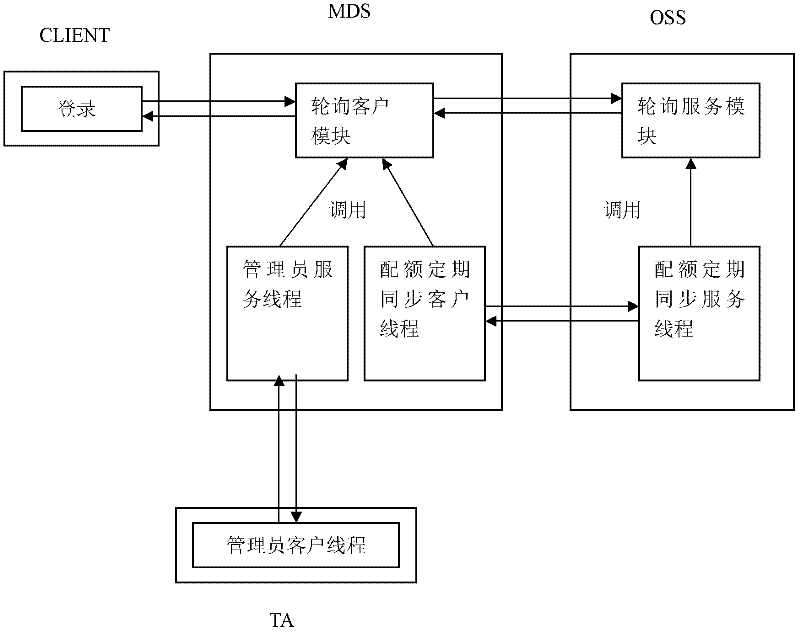
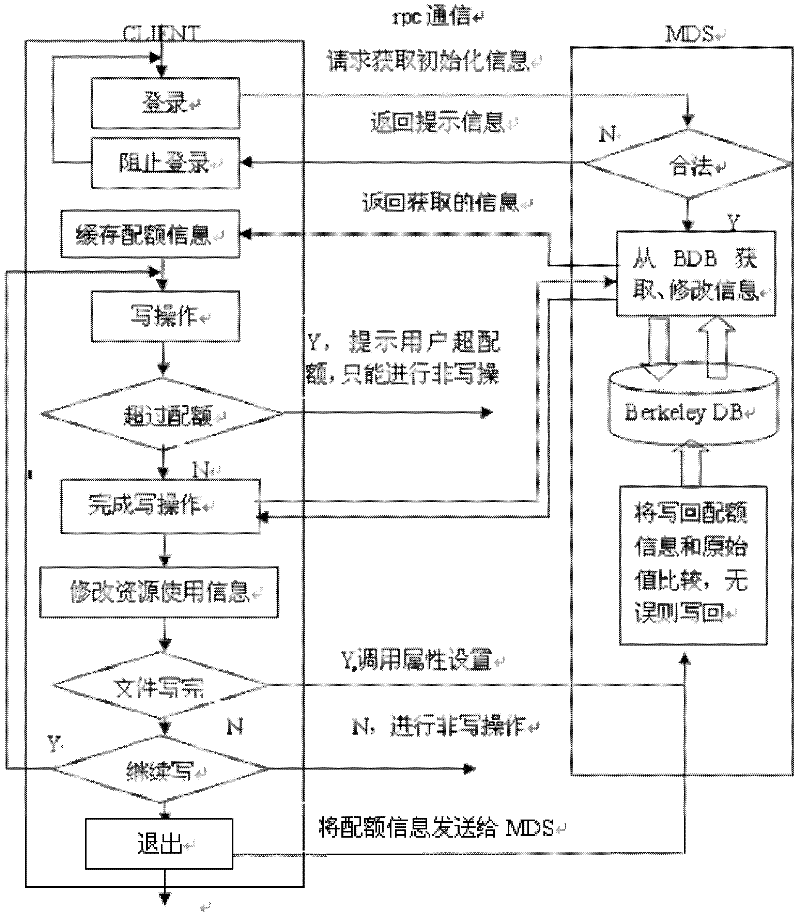
Management and control method for user quota in multi-network storage system
The invention discloses a management and control method for user quota in a multi-network storage system. The method comprises the following steps of starting a metadata server, starting an object storage server, starting a management end, carrying a client end, controlling quotas and back writing quotas. The invention further discloses a management and control system for user quotas. The system comprises a management end, a client end, a metadata server and an object storage server; the management end has an administrator client thread; the client end comprises a quota control module; the metadata server comprises a metadata service thread, a quota regularly synchronized client thread and an administrator service thread; and the object storage server has a document service thread and a quota regularly synchronized service thread. With the adoption of the method and system provided by the invention, waste of network bandwidth caused by unnecessary communication and excessive quota data among servers due to change of resource usage can be avoided, the influence of the quota control function to the system performance is reduced, and meanwhile, a quota consistency synchronizing mechanism is further provided to ensure correctness and consistency of the usage amount of user resources in the system.
Owner:HUAZHONG UNIV OF SCI & TECH
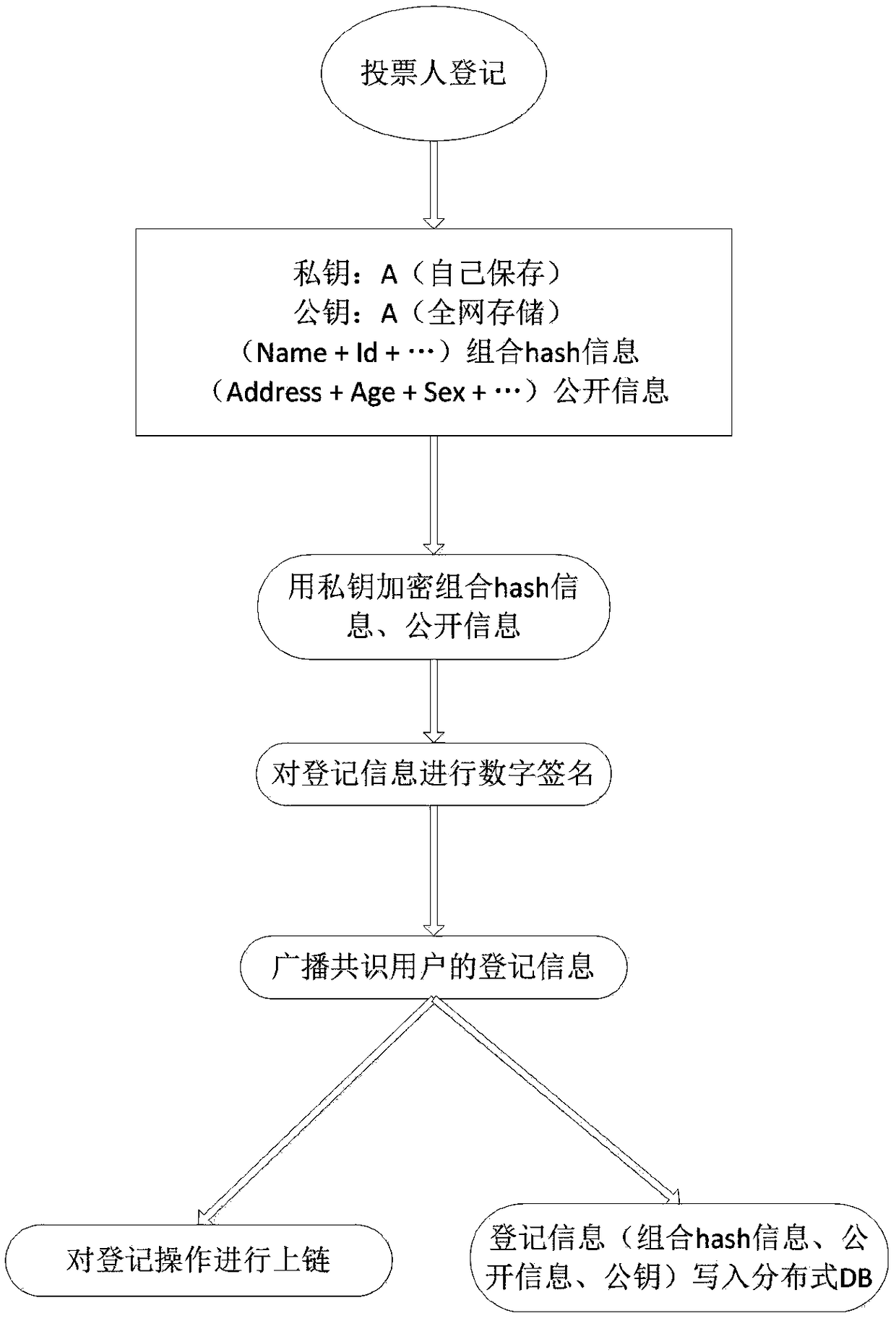
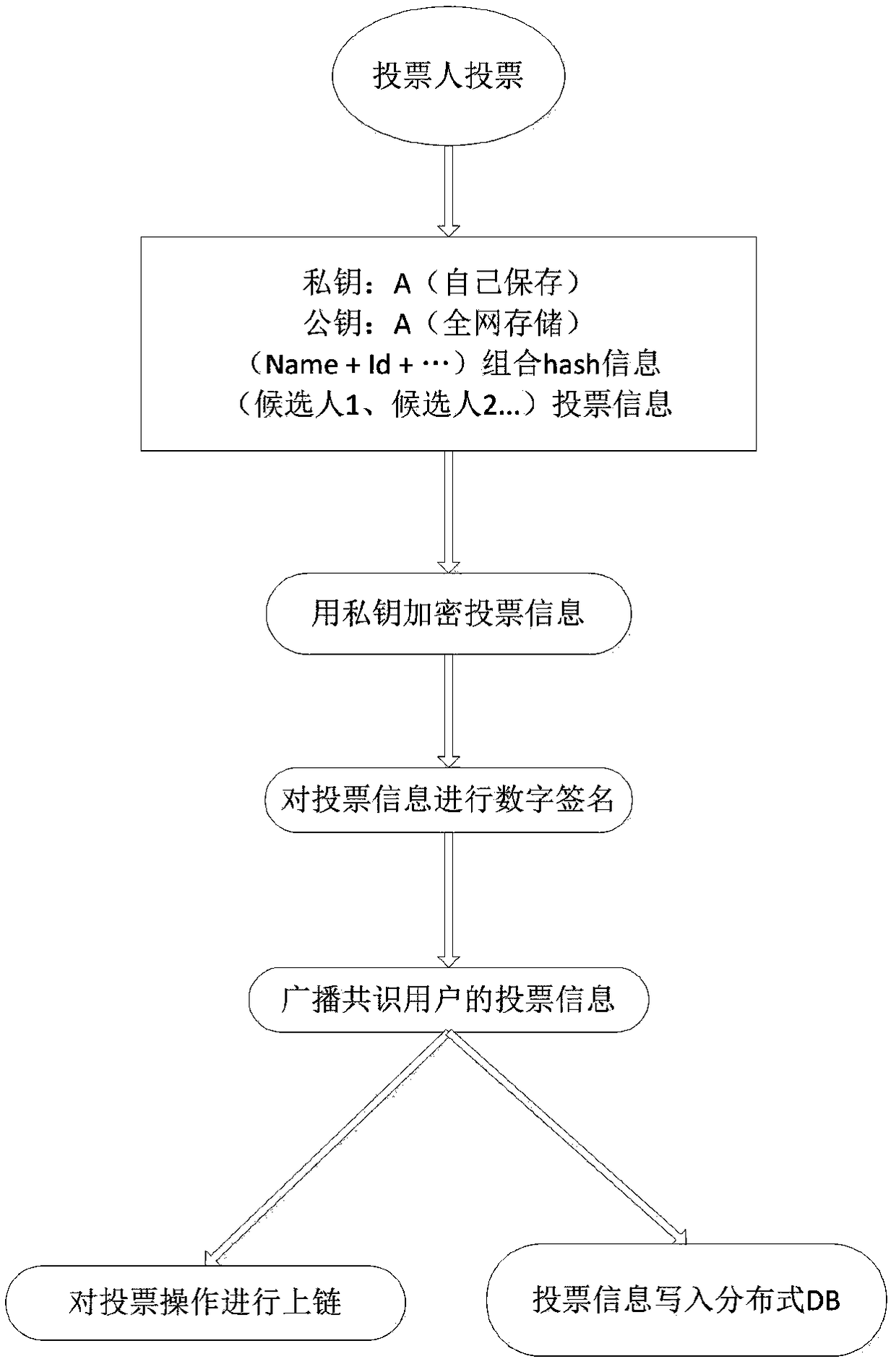
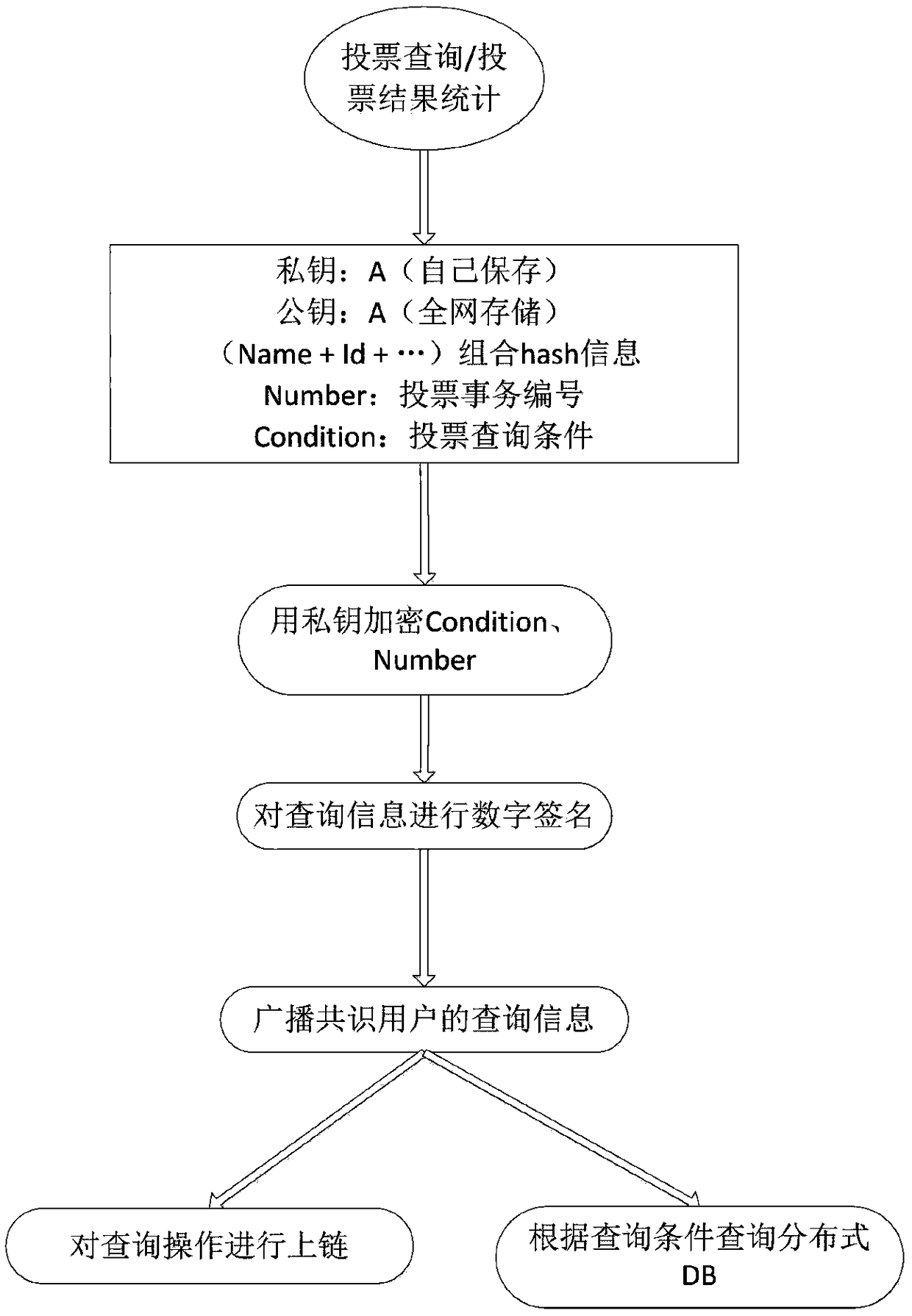
Method for anonymous voting and multi-condition vote counting based on block chain
ActiveCN109286497ANot tampered withEnsure information securityVoting apparatusEncryption apparatus with shift registers/memoriesDigital signatureThe Internet
The invention discloses a method for anonymous voting and multi-condition vote counting based on a block chain, and belongs to the technical field of Internet. The method comprises the steps of voterregistration, voting, voting query and result statistics. Public key encryption and hash are carried out on key and unique identity information of voters to generate unique secret identity informationof the voters, thereby ensuring the identity uniqueness of the voters and the information security, and preventing malicious repeated voting behaviors. The secret identity information of the voters is firstly encrypted by a voter public key and then subjected to hash, so that the information can only be checked by the voters, and anonymous voting is realized. The public information of the votersis encrypted and digitally signed, and the encrypted and signed public information is stored in the database of each network node of the block chain, thereby being capable of achieving multi-conditionvote counting through an intelligent contract in the case of ensuring the voting rights and information security of the voters.
Owner:贵阳信息技术研究院 +1
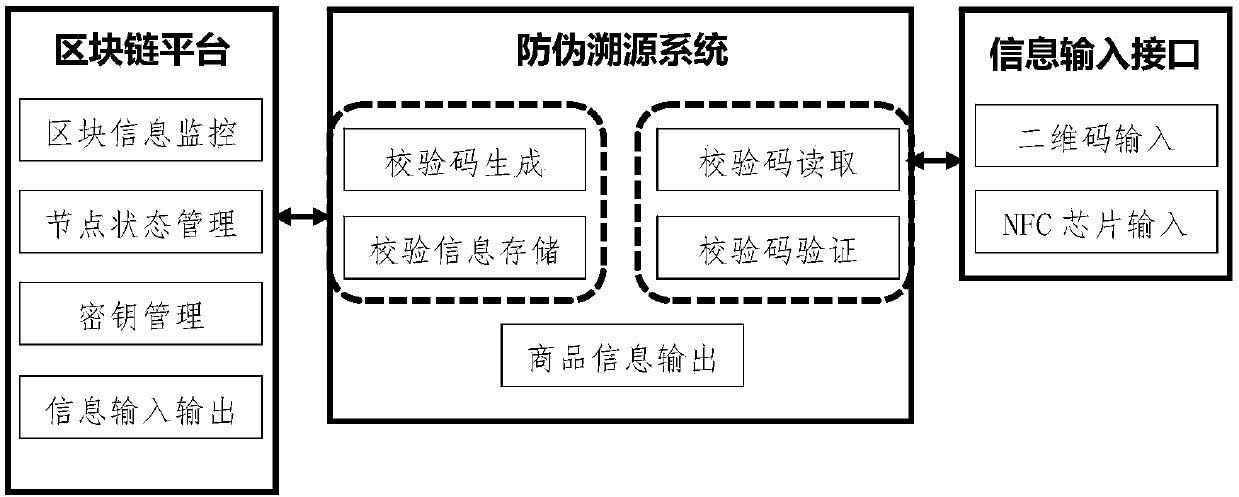
Anti-counterfeiting source tracing system based on block chain
InactiveCN107748994ANot easy to tamper withNot stolenTransmissionCommerceComputer architectureSource tracing
The invention discloses an anti-counterfeiting source tracing system based on a block chain. The system comprises the following functional modules: (1) a verification code generation module which is used for generating the unique verification code of the product; (2) a verification information storage module which stores verification information in the block chain; (3) a verification code readingmodule which reads external anti-counterfeiting information and identifies the corresponding verification code; (4) a verification code verification module which decodes and identifies the verification code; and (5) a commodity information output module which reads product information out of a database after successful matching. The unified and secure anti-counterfeiting verification mode is provided through the block chain technology and can be additive to the existing external anti-counterfeiting means so that the multistep anti-counterfeiting verification process can be simplified and the cost for anti-counterfeiting verification can be saved. New technical support is adopted so that more product information can be provided on the basis of the original anti-counterfeiting information, and the buyer of the commodity is enabled to participate in the source tracing process of the commodity and get more recognition from the commodity buying process.
Owner:HANGZHOU QULIAN TECH CO LTD
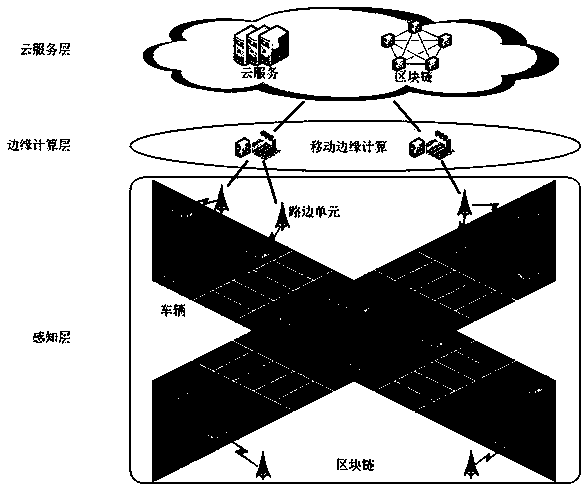
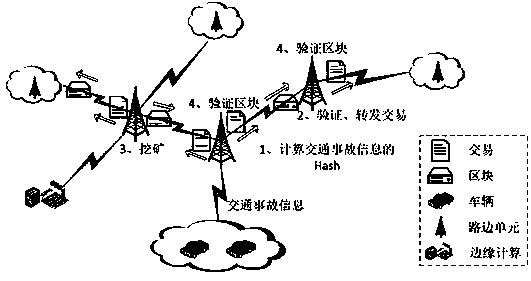
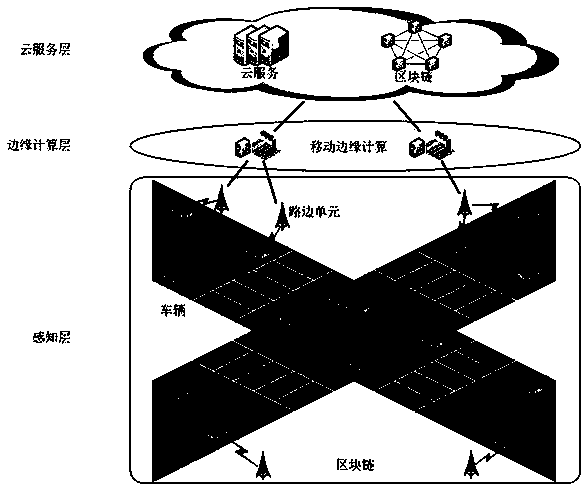
Architecture for collecting traffic accident information based on block chain, and working method
ActiveCN109993847ANot tampered withReduce the burden onRegistering/indicating working of vehiclesTraffic accidentWorking set
The patent provides architecture for collecting traffic accident information based on a block chain, and a working method. The architecture comprises three layers: a cloud service layer, an edge computation layer and a sensing layer; the sensing layer comprises a vehicle and a roadside unit, the vehicle and the roadside unit commonly form a block chain network; the edge computation layer providesa computation resource for the sensing layer so as to accomplish consensus task; the service layer comprises cloud service and the block chain; the working method based on the architecture comprises four steps: traffic accident information querying, traffic accident information returning, roadside unit consensus and traffic accident information storage. By adopting the block chain technology, thetraffic accident information cannot be tampered and is traceable, thereby providing powerful evidence for the traffic department; by adopting the edge computation technology, the task with large computation quantity is unloaded to the edge network from the roadside unit, the burden of the roadside unit is relieved, and the efficiency of collecting the traffic accident information is improved.
Owner:INNER MONGOLIA UNIVERSITY +1
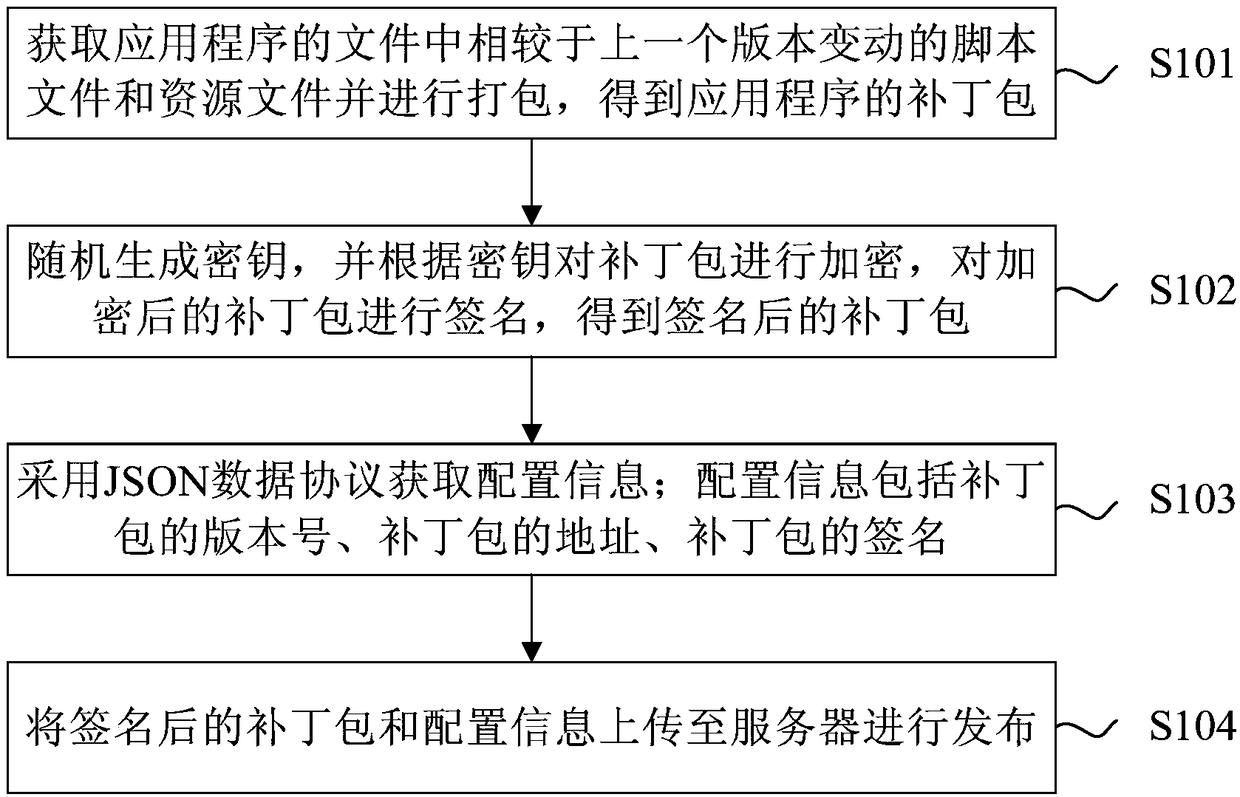
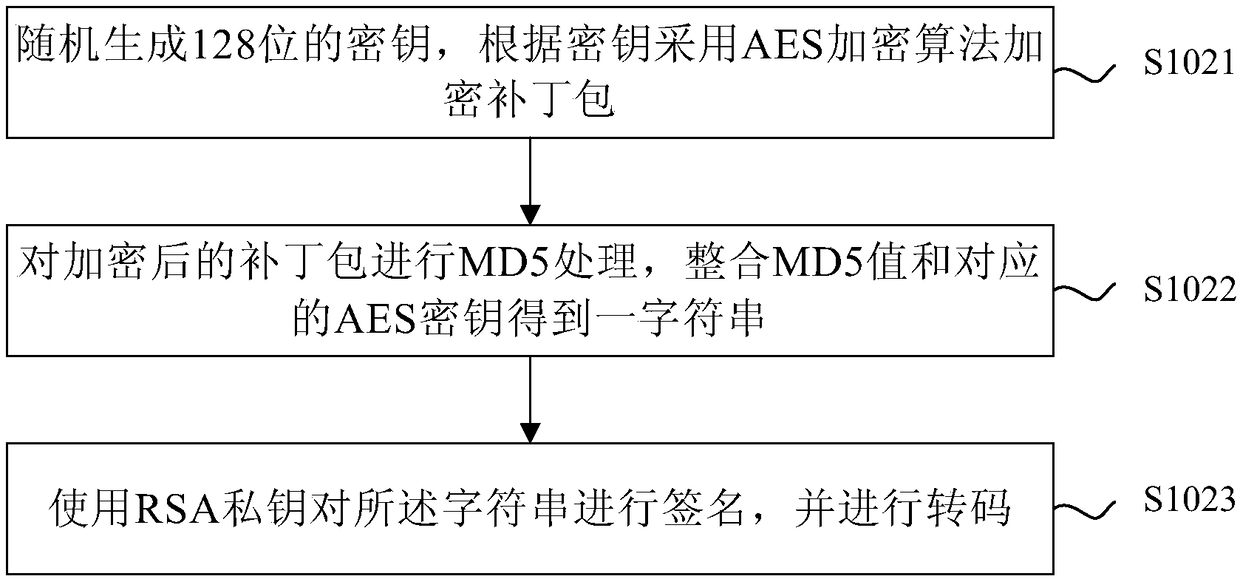
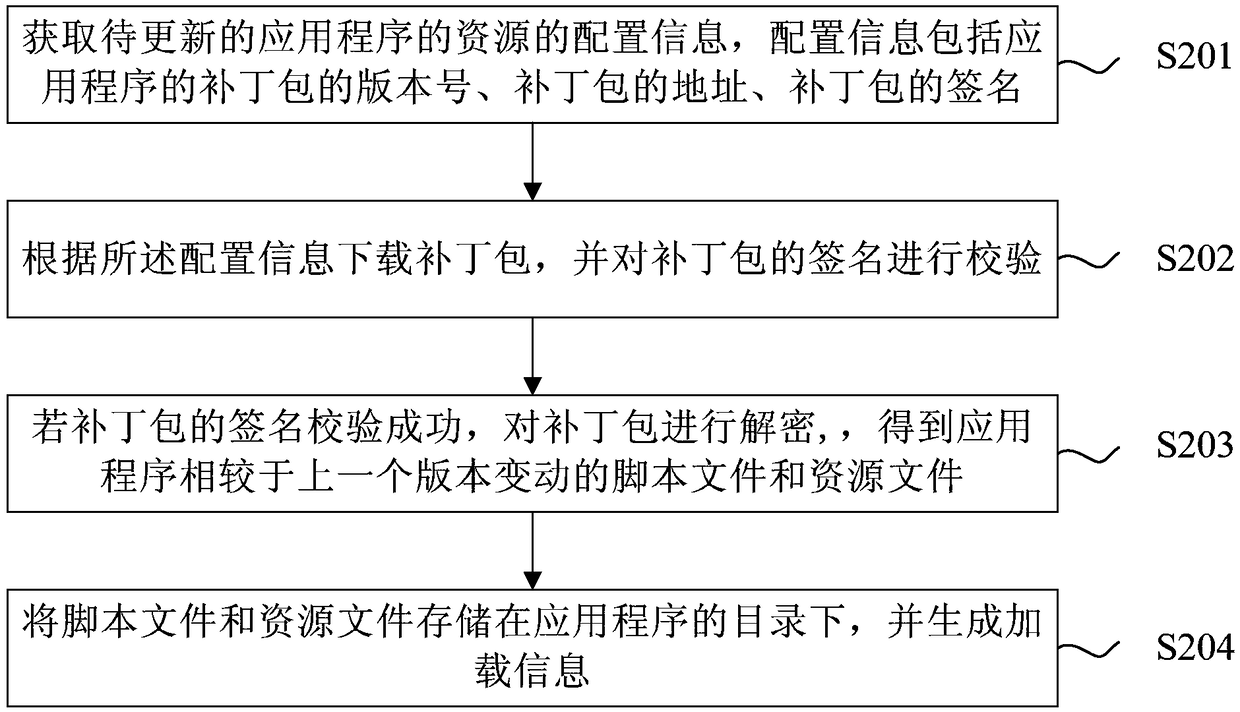
Method for publishing resources, updating method and device
InactiveCN108710500AEnsure safetyNot tampered withVersion controlDigital data protectionApplication softwareOperating system
The invention provides a method for publishing resources, an updating method and a device. The resource publishing method comprises: obtaining script files and resource files changed from the previousversion in the file of the application program and packaging to obtain the patch pack of the application program, randomly generating a key, encrypting the patch pack according to the key, and signing the encrypted patch pack. The JSON data protocol is adopted to obtain configuration information integrally, and the configuration information includes the version number of the patch package, and the signed patch package and the configuration information are uploaded to the server for publication. By encrypting the patch pack of the application program and signing the encrypted key to ensure that the key is not tampered with to ensure the security of the patch pack.
Owner:BEIJING 58 INFORMATION TTECH CO LTD
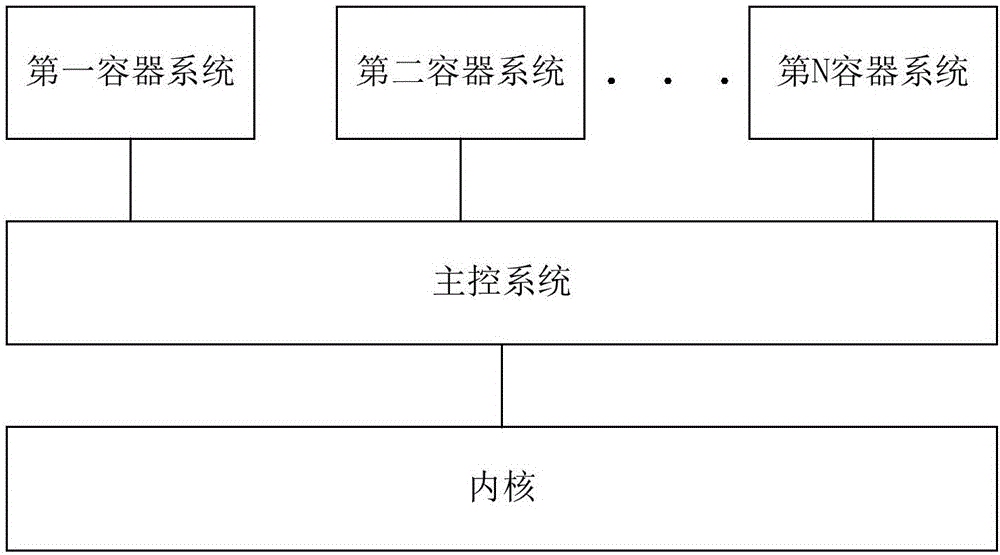
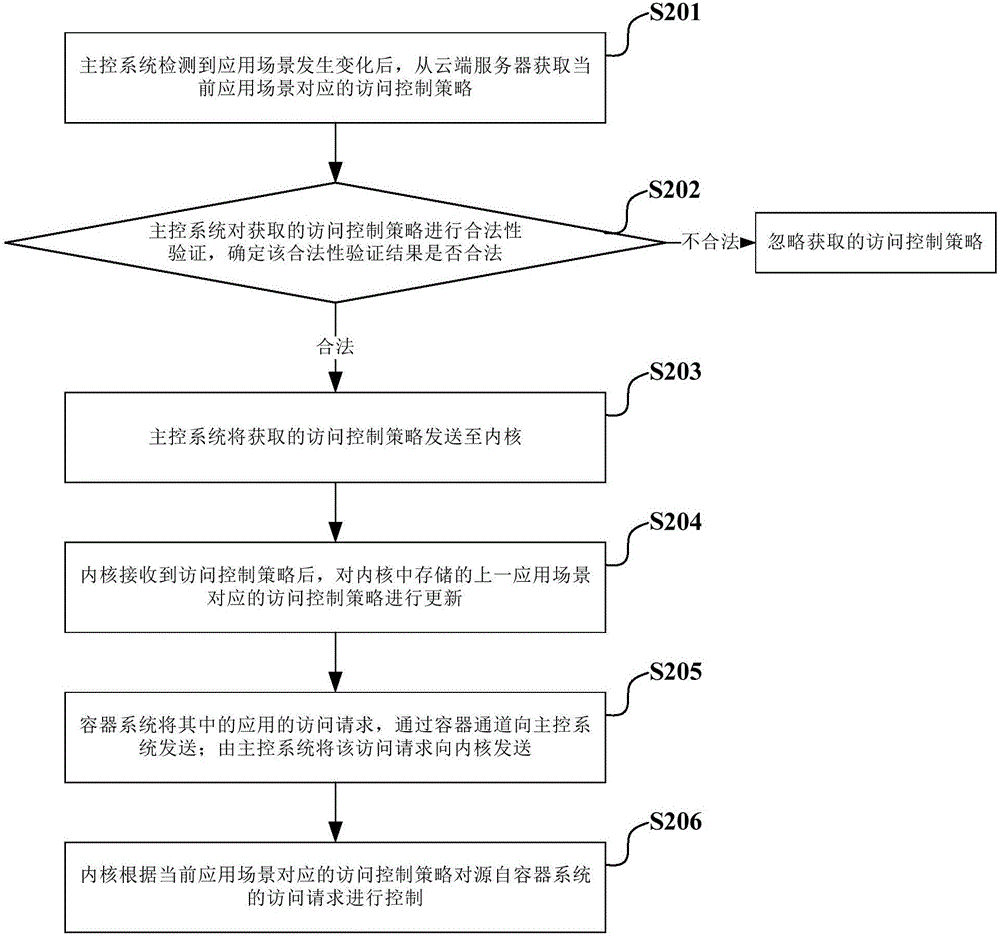
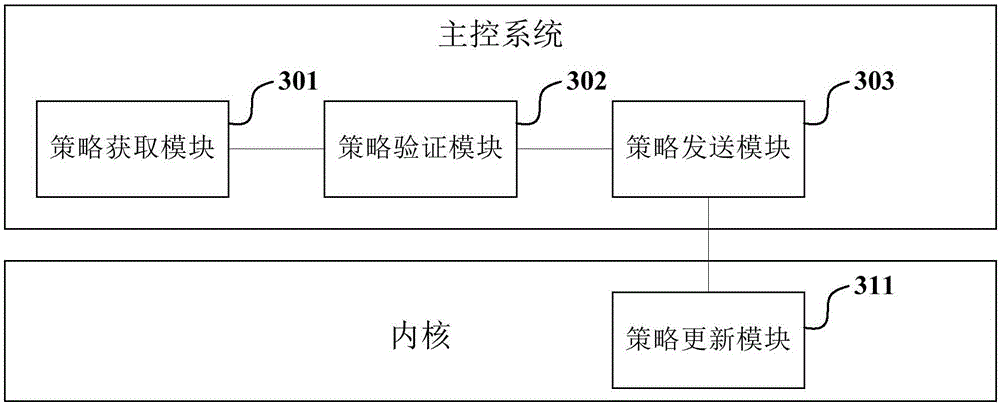
Method and device for dynamic update of access control policies
ActiveCN106330984ARealize dynamic updateEnsure safetyTransmissionClassified informationControl system
An embodiment of the invention provides a method and a device for dynamic update of access control policies. The method includes that a master control system acquires the access control policy corresponding to a current application scene from a cloud server after detecting that a previous application scene changes; the master control system subjects the acquired access control policy to legality validation; when a result of the legality validation is legal, the master control system sends the acquired access control policy to a core; after receiving the access control policy, the core updates the access control policy corresponding to the previous application scene stored in the core so as to control access to a container system according to the access control policy corresponding to the current application scene. The method is capable of dynamically updating the access control policies on the basis of guaranteeing safety of the master control system, the core and the access control policies, so that classified information in terminal equipment can be protected and the access control policies can be updated conveniently.
Owner:PRANUS BEIJING TECH CO LTD
Method and system for supporting multi-mode identification network addressing to gradually go to IP, and storage medium
ActiveCN111373704AAchieve securityRealize immutabilityUser identity/authority verificationData switching networksNetwork addressIp layer
The present invention provides a method and system for supporting multi-mode identification network addressing to gradually go to IP, and a storage medium. The present invention proposes a set of newnetwork multi-mode identification generation management and routing addressing system that integrates blockchains. The multi-mode identification dynamic adaptation and intercommunication technology isused to break through all existing network performance and security bottlenecks based on the IP layer, and the distributed blockchain consensus algorithm is used to achieve the original wish of Internet co-management and co-governance. All network resources on the network are locked on the blockchain to ensure that network resources are authentic and not tampered; the high-performance and low-overhead distributed storage technology is used to achieve the security of multi-mode identification addressing and tamper-proof modification, and, at the same time, the introduction of user real-name registration and network login management strategies combined with biometric identity information and signature strategies for privacy protection are introduced to reduce system management costs and improve the privacy and security of access node information.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +3
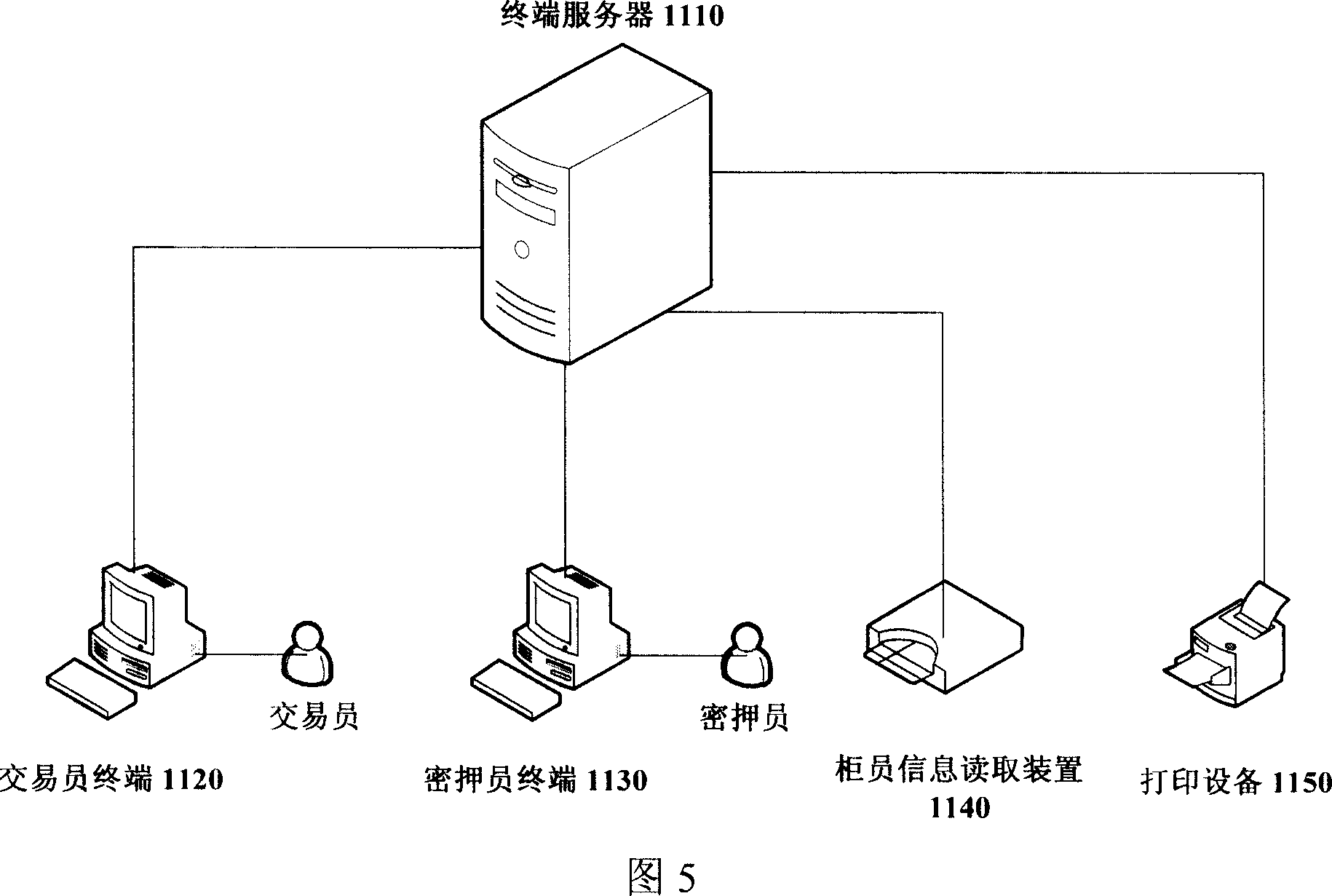
Data ciphered-mortgage transaction system, teller identification system, trans-center transaction system and method
InactiveCN101145233AHigh degree of automationImprove transfer efficiencyComplete banking machinesFinanceInformation storageSecure authentication
The invention discloses a data cipher transaction system, which comprises a counter information storage device, a going-account transaction terminal, a cipher coding unit, a coming-account transaction terminal, a prepositive computer, a safety authentication and cipher check center, and a business system host. The data cipher transaction system performs authentication on the counter identity; if the authentication is passed, the invention carries out cipher coding on the transaction data; the coded cipher of the transaction data is checked in the safety authentication and cipher check center; if the cipher check is successfully done, the transaction data is sent to the coming account for treatment. The data cipher transaction system provided by the invention can improve the safety and reliability of banking transaction.
Owner:AGRICULTURAL BANK OF CHINA
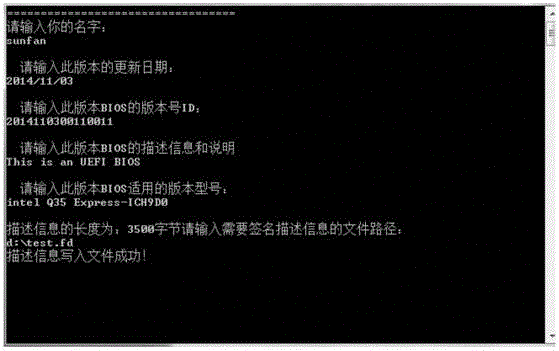
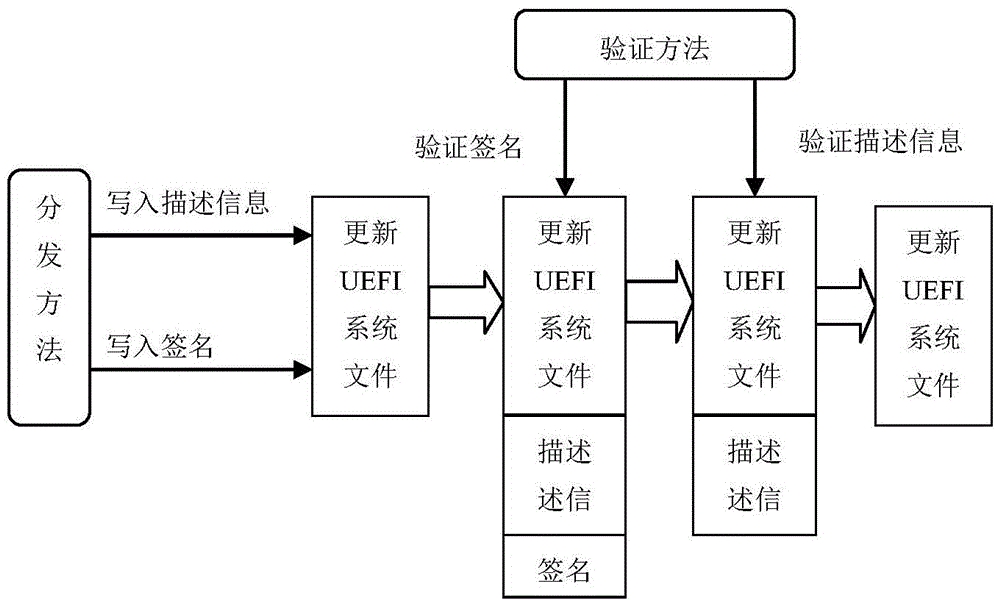
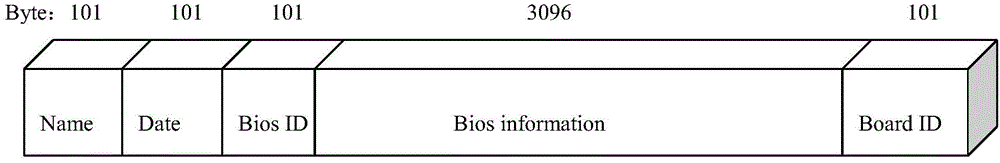
UEFI system updating method based on updating security mechanism
InactiveCN104573527AGuaranteed CompatibilityNot tampered withDigital data protectionPlatform integrity maintainanceDigital signatureValidation methods
The invention discloses a UEFI system updating method based on an updating security mechanism and belongs to the field a computer software systems. The UEFI updating mechanism includes a distribution method and a verification method and is used for guaranteeing that the updating file loaded to a system is not tampered, cannot be illegally accessed and is compatible with hardware. A layer of outer-layer data whose security can be verified is encapsulated outside the updating file through the digital signature and encryption technology, a DXE driver is built in the verification method of the updating security mechanism to detect the outer-layer data, and accordingly whether the updating file is complete or, is tampered or not, is illegally used or not and is compatible with the hardware or not can be judged.
Owner:BEIJING UNIV OF TECH
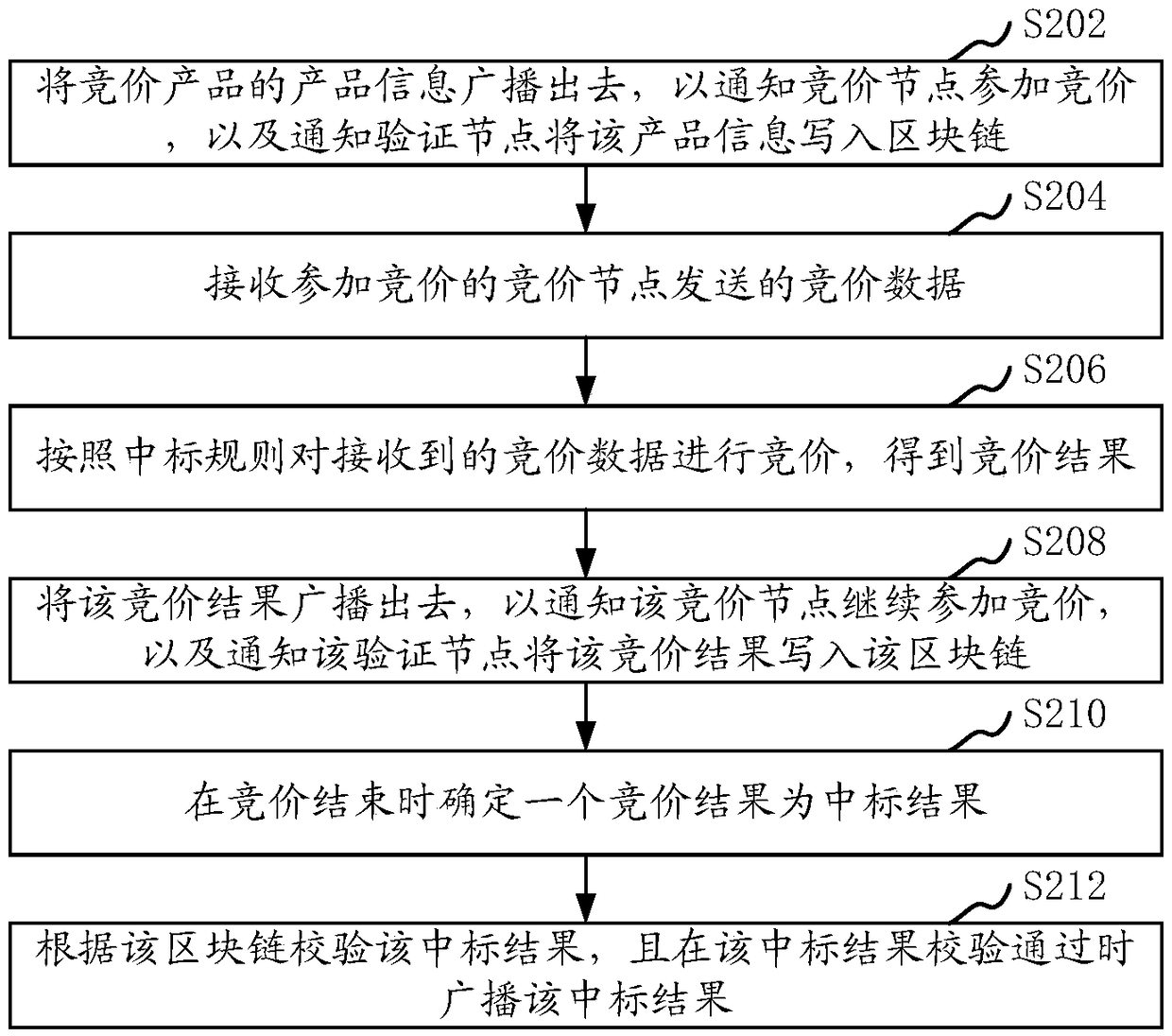
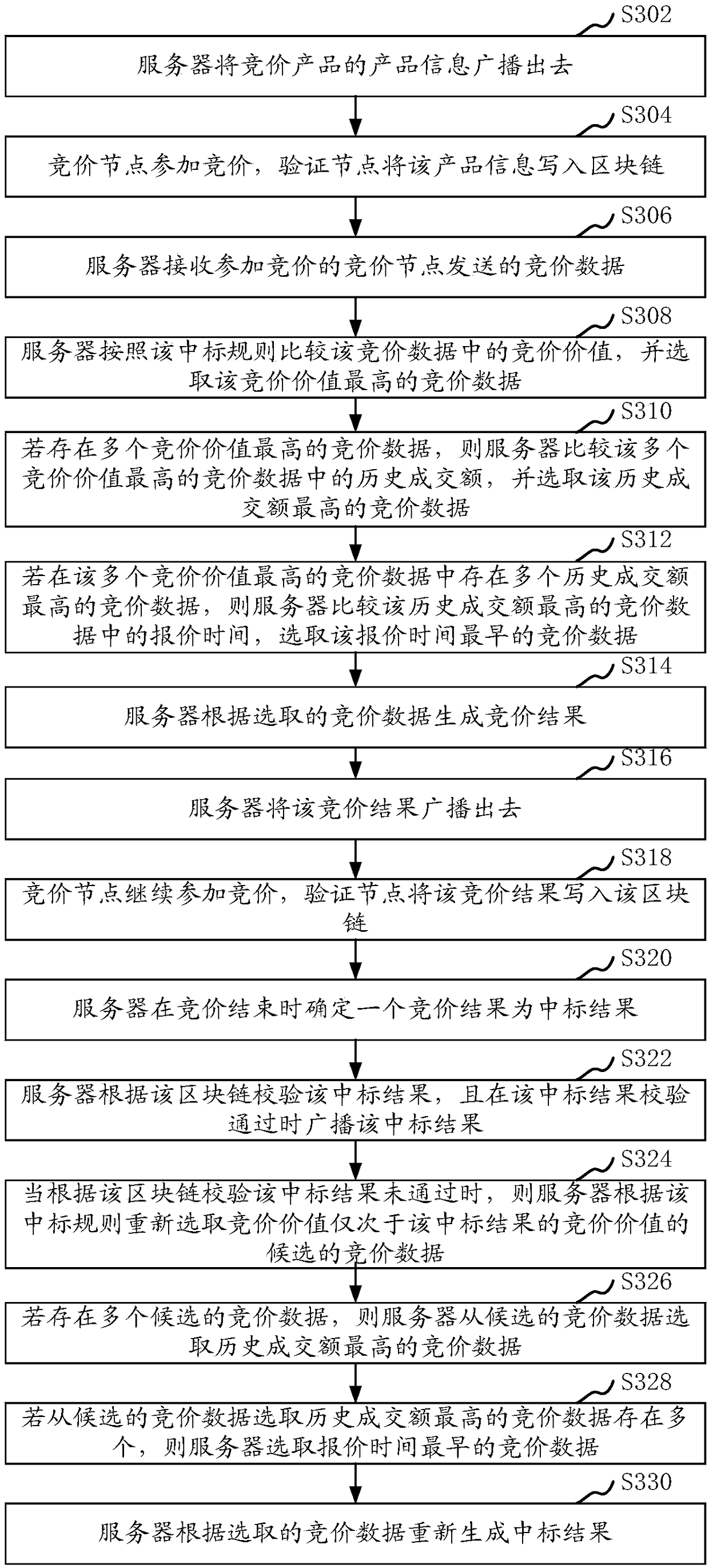
Real-time bidding method and device based on blockchain, equipment and storage medium
InactiveCN108305156AWide spreadGuarantee authenticityPayment protocolsCommerceTime line methodData mining
The invention relates to a real-time bidding method based on a blockchain, a system, computer equipment and a storage medium. The method comprises the steps that the product information of a bid product is broadcast to notify bidding nodes to participate in the bidding and notify a verification node to write the product information into the blockchain; bidding data sent by the bidding nodes participating in the bidding are received; according to a bid winning rule, the received bidding data are bid to acquire bidding results; the bidding results are broadcast to notify the bidding nodes to continue to participate in the bidding and notify the verification node to write the bidding results into the blockchain; a bidding result is determined as a bid winning result at the end of the bidding;the bid winning result is verified according to the blockchain; and the bid winning result is broadcast when the bid winning result is successfully verified. The method can ensure that the bidding data are open, transparent and safe.
Owner:重庆金融资产交易所有限责任公司
A traceability system based on a block chain
PendingCN109829724ANot easy to tamper withNot stolenCo-operative working arrangementsCommerceInformation securityTraceability
The invention discloses a traceability system based on a block chain, and relates to the technical field of blockchain and information traceability. The system comprises an alliance chain management module, a block chain browser module, a traceability code generation module, an information storage module, an information reading module, a caching module, a commodity information reading module and an SDK module, and the alliance chain management module can manage and maintain block chain nodes and newly add consensus nodes for key link manufacturers on a supply chain in the block chain. According to the traceability system based on a block chain, the information security Tamper-resistant properties of the block chain are utilized;, the information can be protected from being stolen and tampered; the product information can be kept transparent and public in front of consumers; the credibility of the traditional traceability system is improved, the anti-counterfeiting traceability system can adapt to the existing external traceability means on the market, the anti-counterfeiting traceability work of the original product is supplemented and updated, and multiple anti-counterfeiting processes adopted by manufacturers are simplified, so that the labor and financial cost of the work is reduced.
Owner:链极智能科技(上海)有限公司
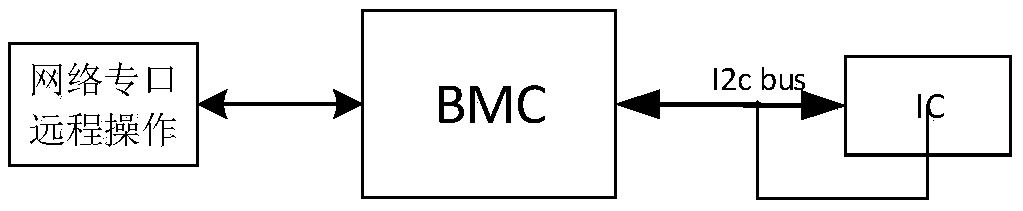
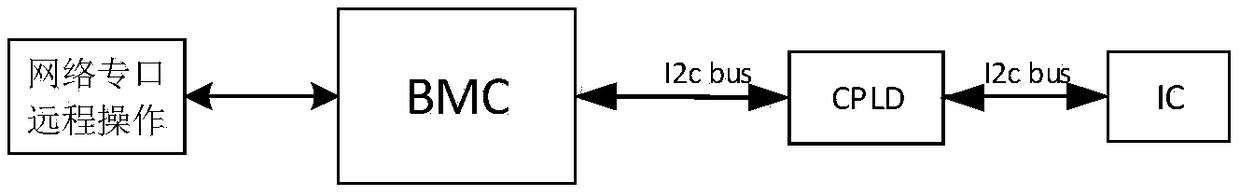
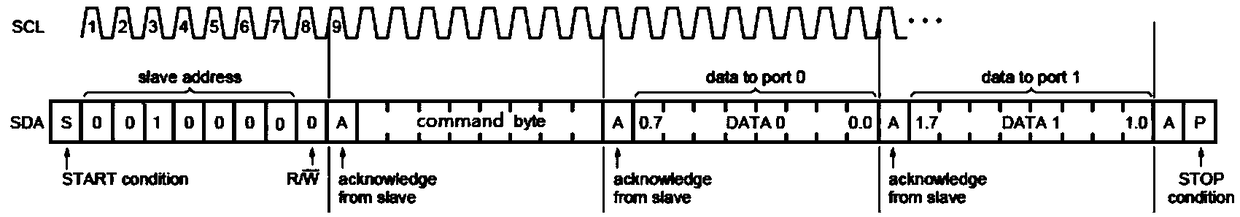
Design method for achieving i2c bus data monitoring and protection
InactiveCN108777639AEffective monitoringEffective protectionBus networksComputer moduleDesign methods
The present invention provides a design method for achieving i2c bus data monitoring and protection. CPLD is added in the hardware design to achieve monitoring and protection of data on an I2C bus, the CPLD is taken as a monitoring module to analyze the data on the I2C bus in real time, it is allowed that a controller BMC performs read-write operation of an IC by only employing a preset allowed command, and when there is an illegal command, the CPLD can immediately forbid the transmission of the I2C bus data so as to have the protection of the IC and improve the safety and the stability of thewhole system.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
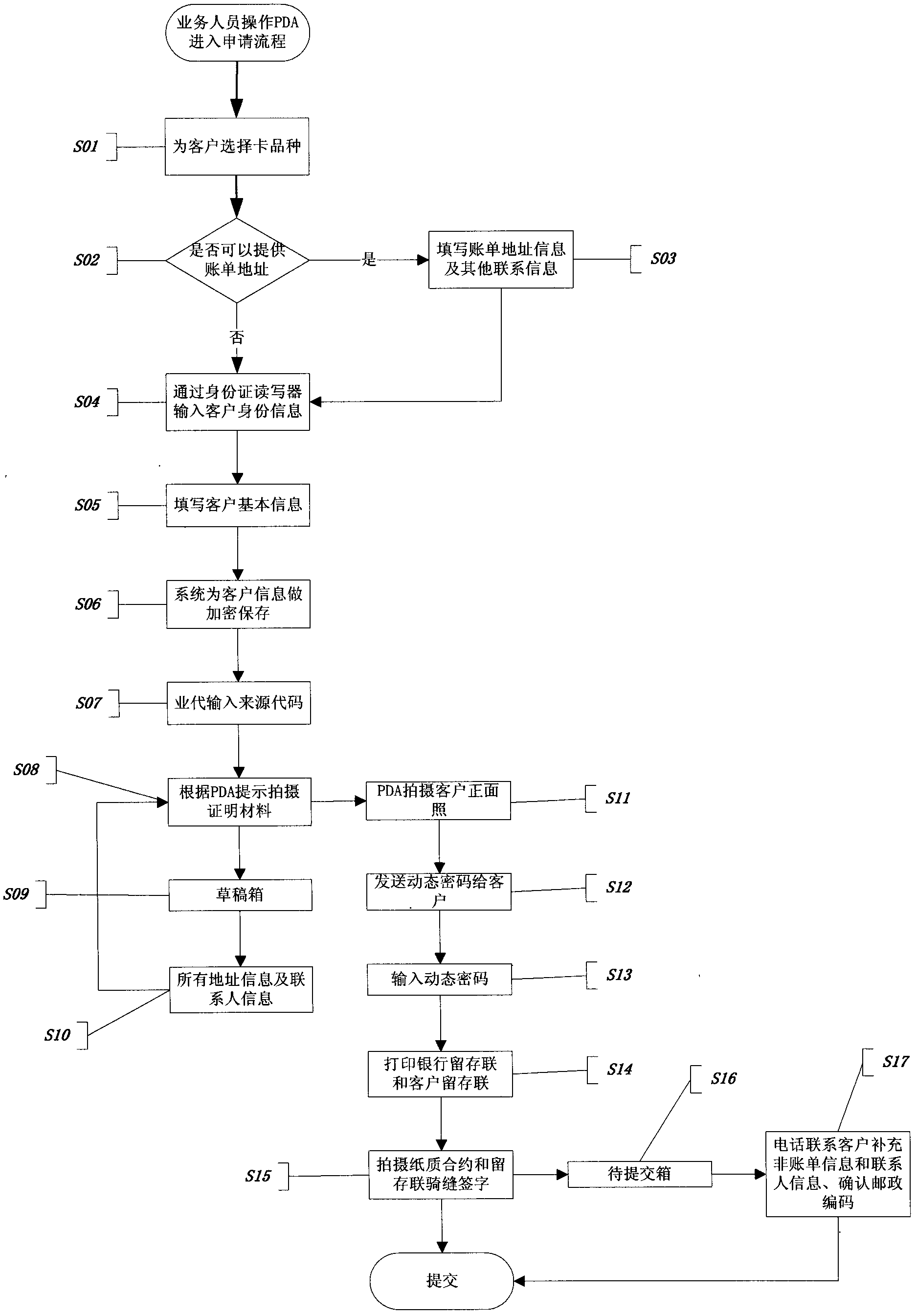
Method for transacting bankcard application through mobile intelligent terminal
InactiveCN102231200ANot tampered withAdd verification functionFinanceReal-time computingBusiness Personnel
The invention provides a method for transacting bankcard application through a mobile intelligent terminal. The method is characterized by comprising the following steps that: firstly, the mobile intelligent terminal is distributed to each salesman who is in charge of transacting the bankcard application and all the mobile intelligent terminals communicate with a server at the rear end through a wireless network; secondly, the salesman at the front end records basic client information required by the bankcard application through the mobile intelligent terminal; then the information is transmitted to the server at the rear end; after the information is processed, a business processing module calls client bankcard application information stored in a database; and a bank auditor audits the information and judges whether to approve to transact a bankcard. The invention has the advantage that: a low-carbon and environment-friendly method for transacting the bankcard application is provided; and by the method, management of the bankcard application information is facilitated and the bankcard application efficiency is improved.
Owner:BANK OF COMMUNICATIONS
Cloud computing access method based on cross domain identity authentication
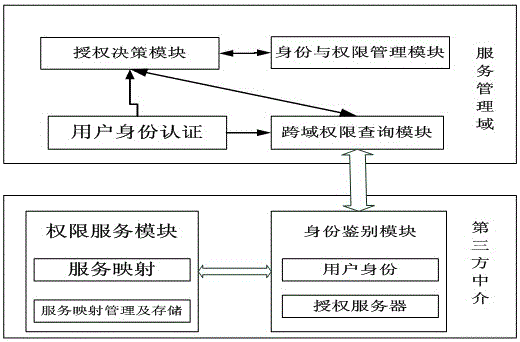
InactiveCN106657156AGuaranteed confidentialityIntegrity guaranteedUser identity/authority verificationThird partyAccess method
The invention discloses a cloud computing access method based on cross domain identity authentication. The method is realized by a local identity authentication module, a local authorization decision module, a local identity and authority management module, a cross domain authority inquiring module, a third-party identity authentication module and a third-party authority service module. The cloud computing access method based on cross domain identity authentication has the following characteristics: (1) subject identity, attribute and authority information are described in a standard manner, and certification authority of a subject, authentication validity, the attribute of the subject and the authority of the subject in a targeted organization can be clear by the standard description; (2) request query related to identity authentication and response messages in cross domain identity authentication are abstracted, a standard format for different types of messages is defined, and identity information which is transmitted among different domains can be understood; and (3) confidentiality, integrity, reliability and identifiability of transmitted messages are guaranteed by a high-reliability encryption transmission mechanism, and information of authentication of users cannot be wiretapped or tampered.
Owner:JINAN INSPUR HIGH TECH TECH DEV CO LTD
Security management system and method of dependable computing platform
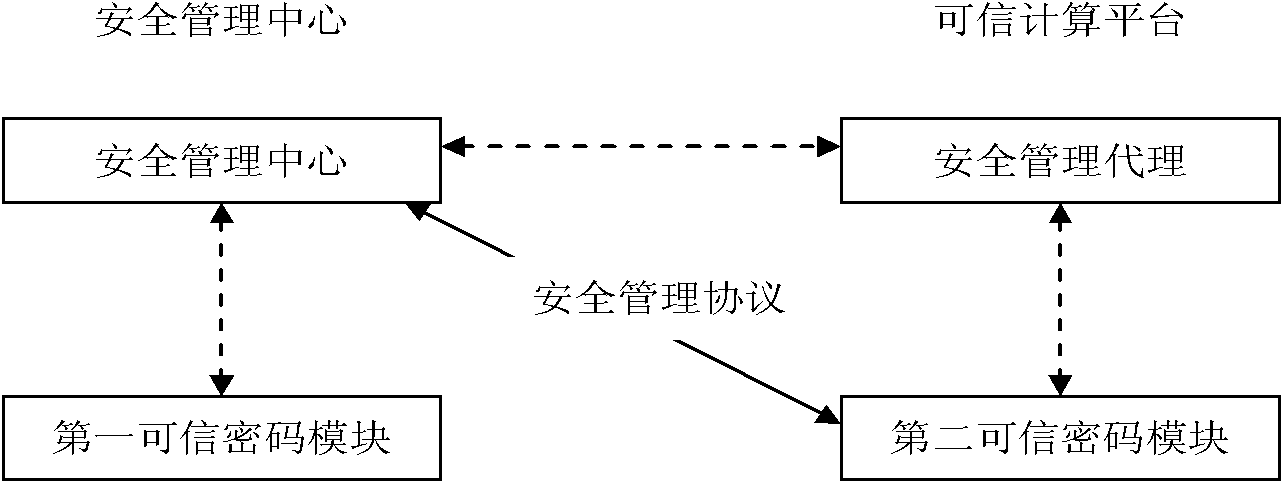
InactiveCN102340500AGuarantee authenticityIntegrity guaranteedUser identity/authority verificationCode moduleSafety management systems
The invention discloses a security management system and method of a dependable computing platform. The security management system comprises a dependable code module, a security management center module, a security management agent module and a security strategy management protocol module; the security strategy management protocol module between the security management center module and the dependable code module is realized on basis of the dependable code module so that the security of the transmission of a security management strategy is ensured; the security protection of a security strategy at a security management center is realized on basis of the dependable code module; and a security strategy at the dependable computing platform is stored in the dependable code module, and the security of the security strategy is protected by the dependable code module so that the security of the storage of the security management strategy is ensured. The security management method based on the dependable computing platform comprises a step of generating a security strategy management protocol and steps of producing, extracting and deleting a new security strategy by the security management center and has the advantages of fulfilling the protection of encryption and integrity verification of security strategy data and preventing data leakage and unauthorized tampering of the security strategy data from an attacker.
Owner:中国人民解放军海军计算技术研究所
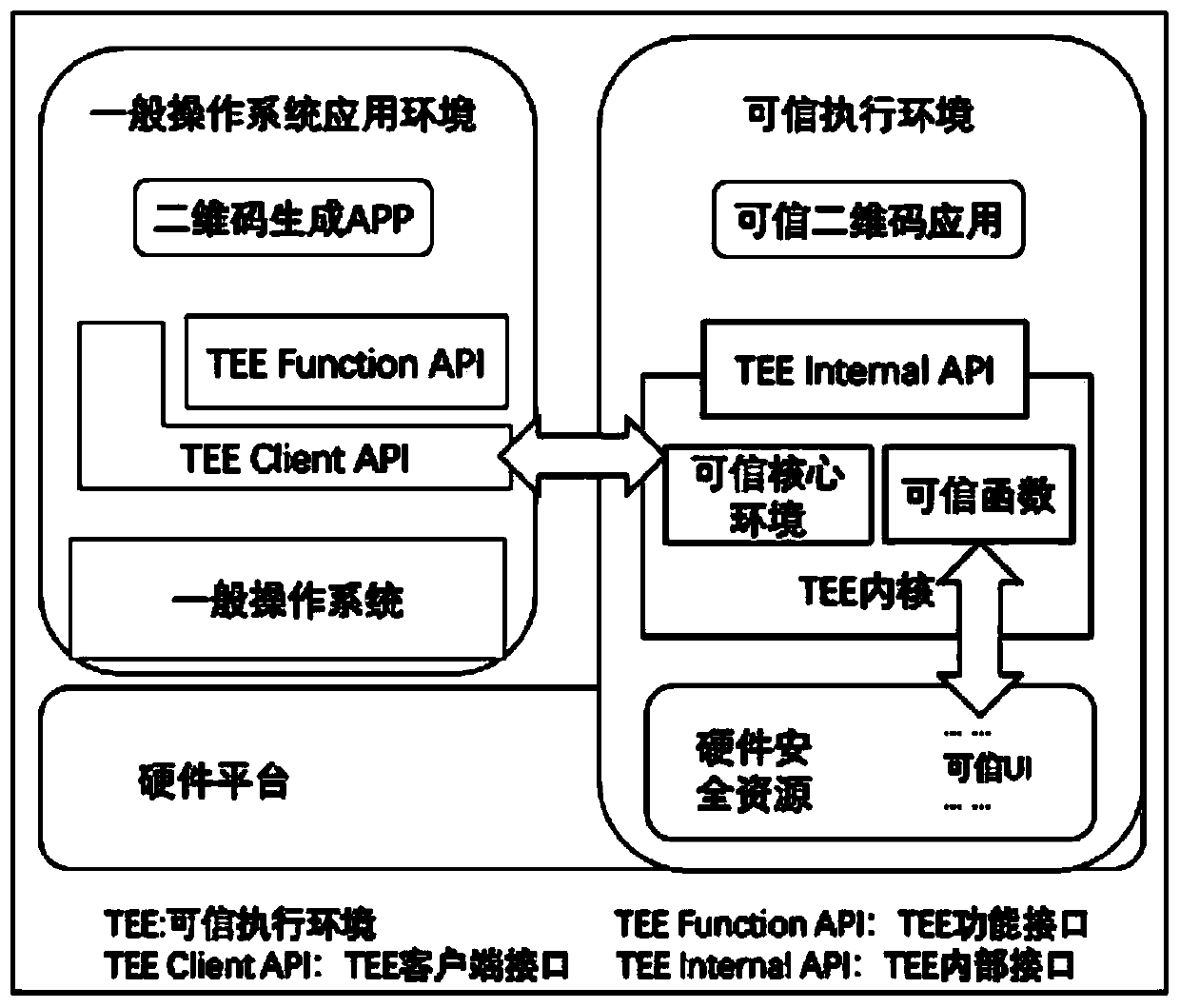
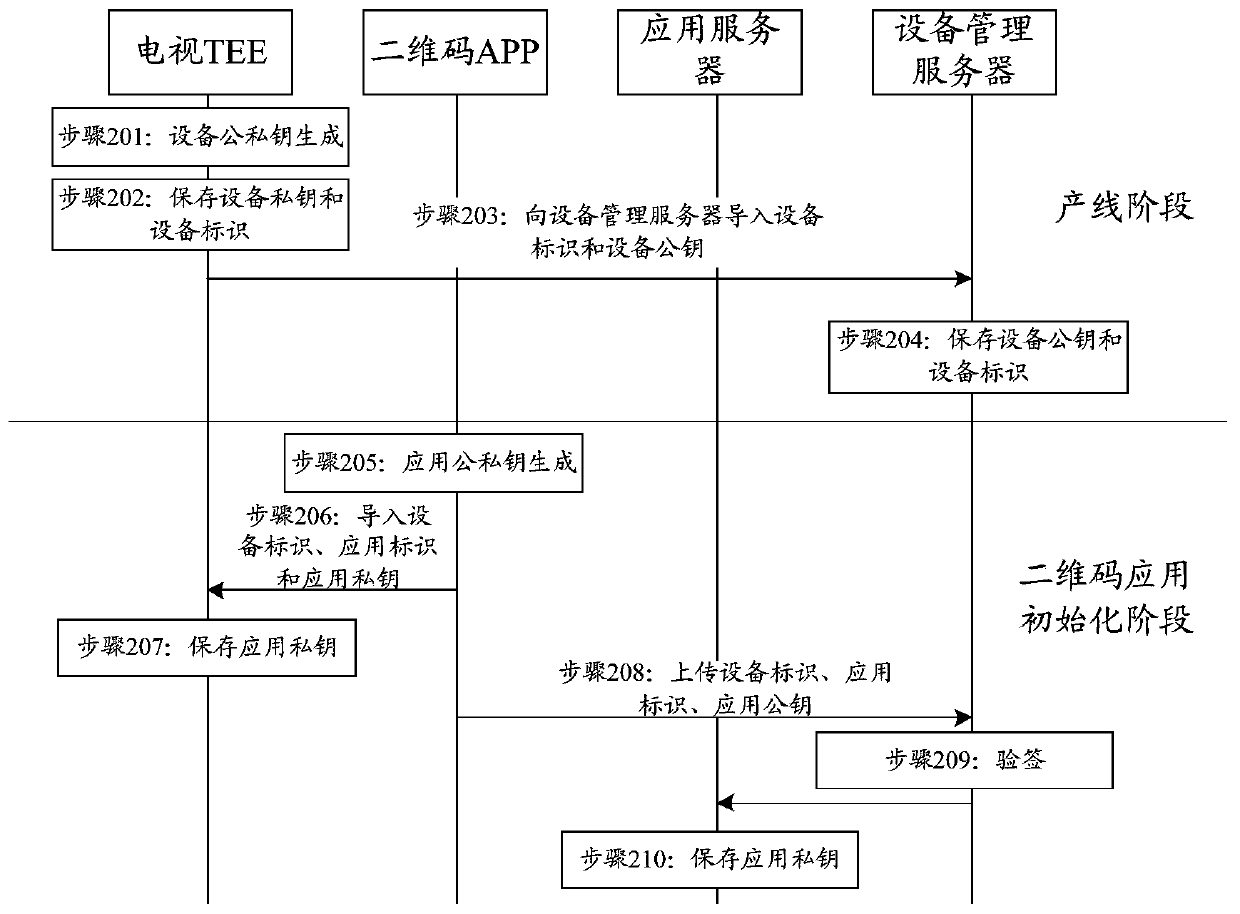
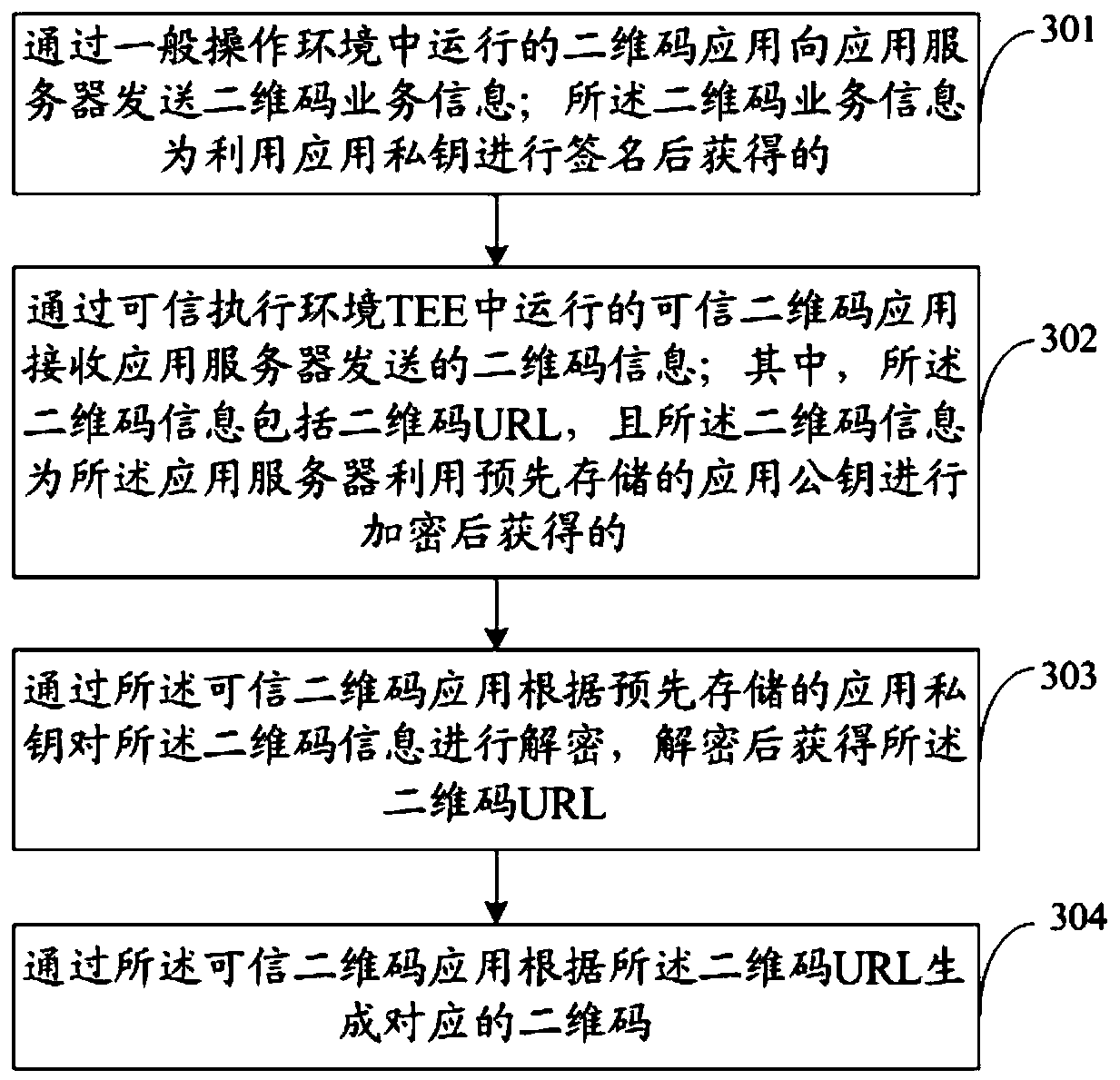
Trusted two-dimensional code generation method and device, electronic equipment and storage medium
ActiveCN110677261ANot tampered withImprove securityUser identity/authority verificationPlatform integrity maintainanceCode generationApplication server
The invention provides a trusted two-dimensional code generation method and device, electronic equipment and a storage medium. The method comprises the following steps: sending two-dimensional code service information to an application server through a two-dimensional code application, wherein the two-dimensional code service information is obtained after signature by using an application privatekey; receiving two-dimensional code information sent by the application server through the trusted two-dimensional code application, wherein the two-dimensional code information comprises a two-dimensional code URL, and the two-dimensional code information is obtained after the application server encrypts the two-dimensional code URL by using an application public key; decrypting the two-dimensional code information through a trusted two-dimensional code application according to an application private key to obtain the two-dimensional code URL; and generating a corresponding two-dimensional code according to the two-dimensional code URL through the trusted two-dimensional code application. According to the embodiment of the invention, the trusted two-dimensional code application running inthe TEE communicates with the application server, so that the generation of the two-dimensional code is realized, and the TEE provides a secure execution environment for authorizing security software, so that the security of the generation of the two-dimensional code is improved.
Owner:SICHUAN PANOVASIC TECH +1
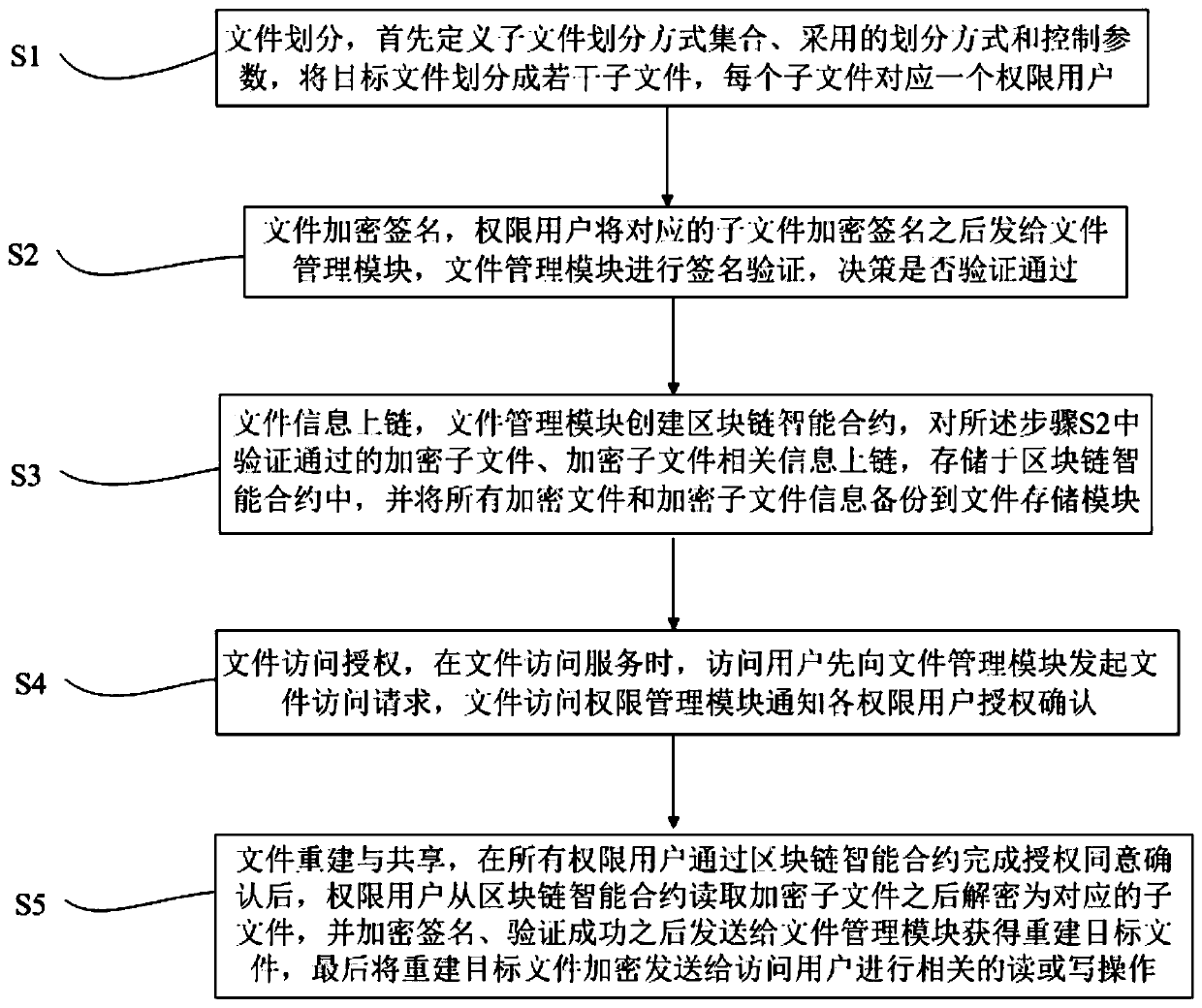
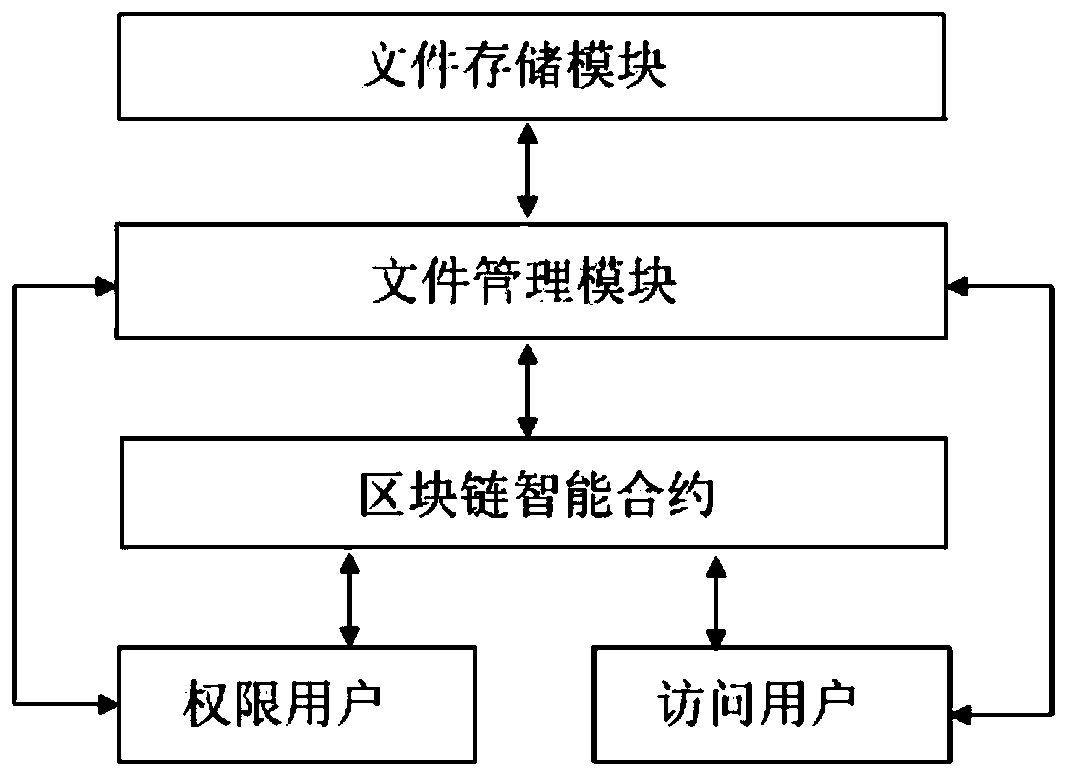
File storage and access method and system based on block chain
ActiveCN110784463AControl operation authorityNot tampered withEncryption apparatus with shift registers/memoriesPublic key for secure communicationTamper resistanceSignature file
The invention discloses a file storage and access method and system based on a block chain, and the method comprises the steps: carrying out file partitioning, carrying out file encryption signature,carrying out file information chaining, carrying out file access authorization, carrying out file reconstruction and sharing, and finally transmitting a reconstruction target file to an access user inan encrypted manner for related reading or writing operation. Separated file storage and a file management mechanism based on a blockchain smart contract are adopted, the file access permission management module utilizes the main characteristics of openness, transparency, tamper resistance and the like of a blockchain, and the security and traceability of file access are effectively enhanced. Bydividing the file into a plurality of sub-files and encrypting the sub-files with different private keys, the file can be prevented from being operated unidirectionally. Meanwhile, the sub-file related information is encrypted and stored in the block chain and cannot be tampered, so that the security of the file information is greatly enhanced.
Owner:深圳市乾数科技有限公司
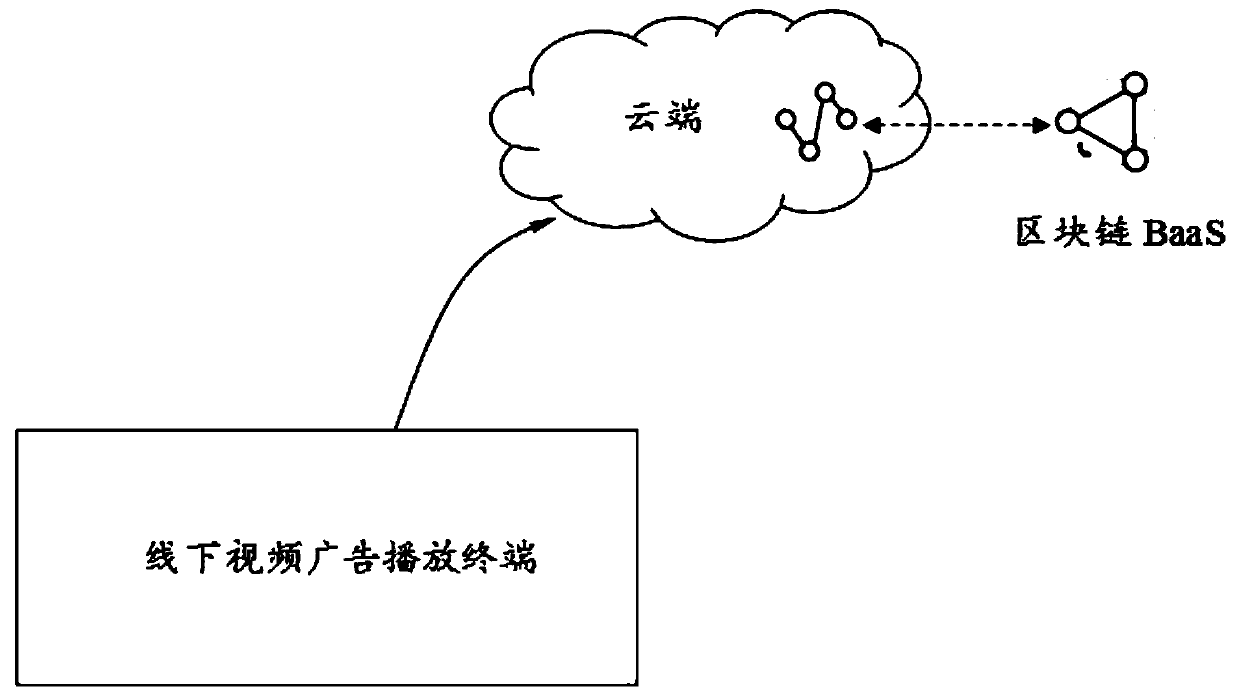
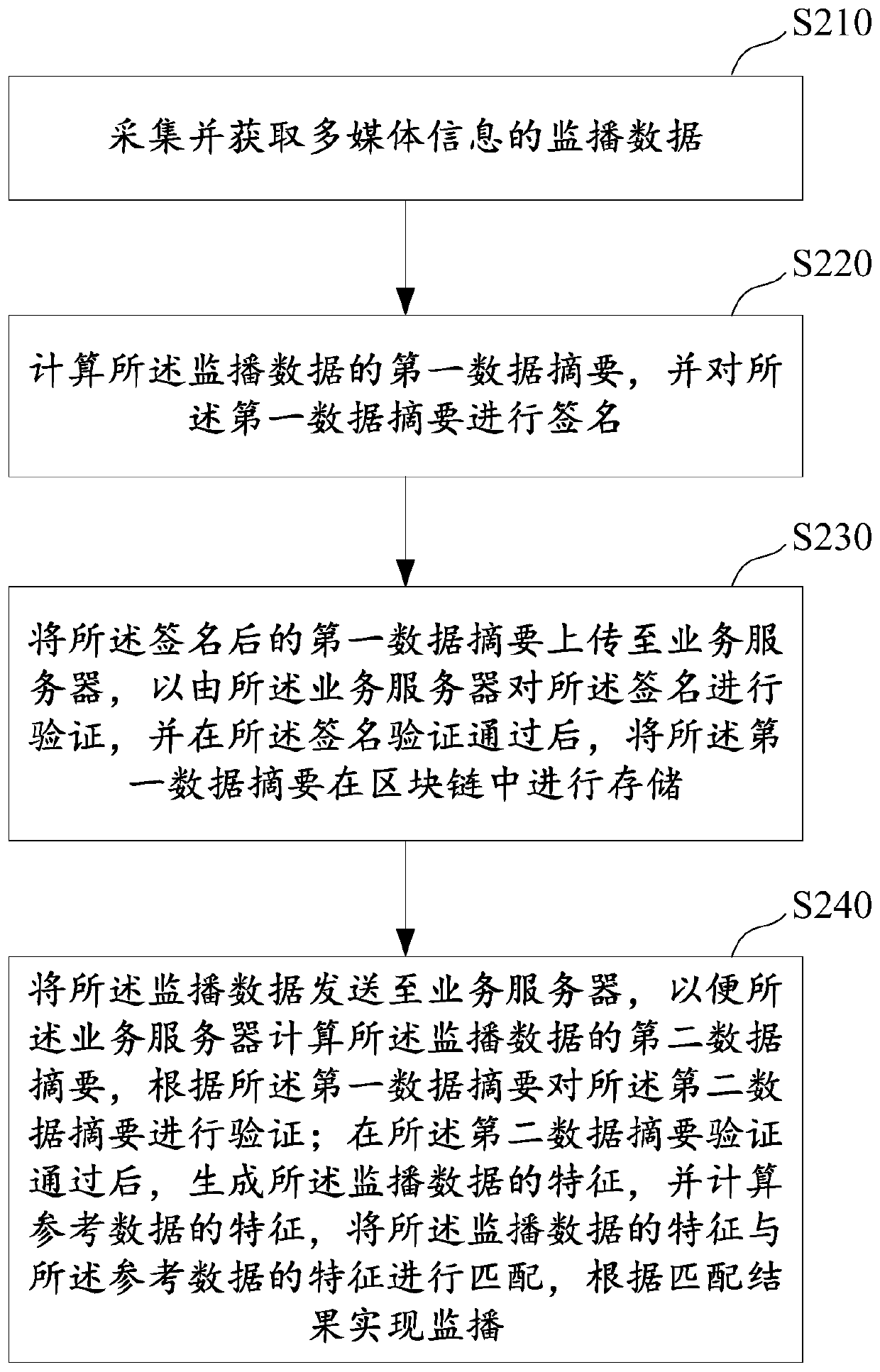
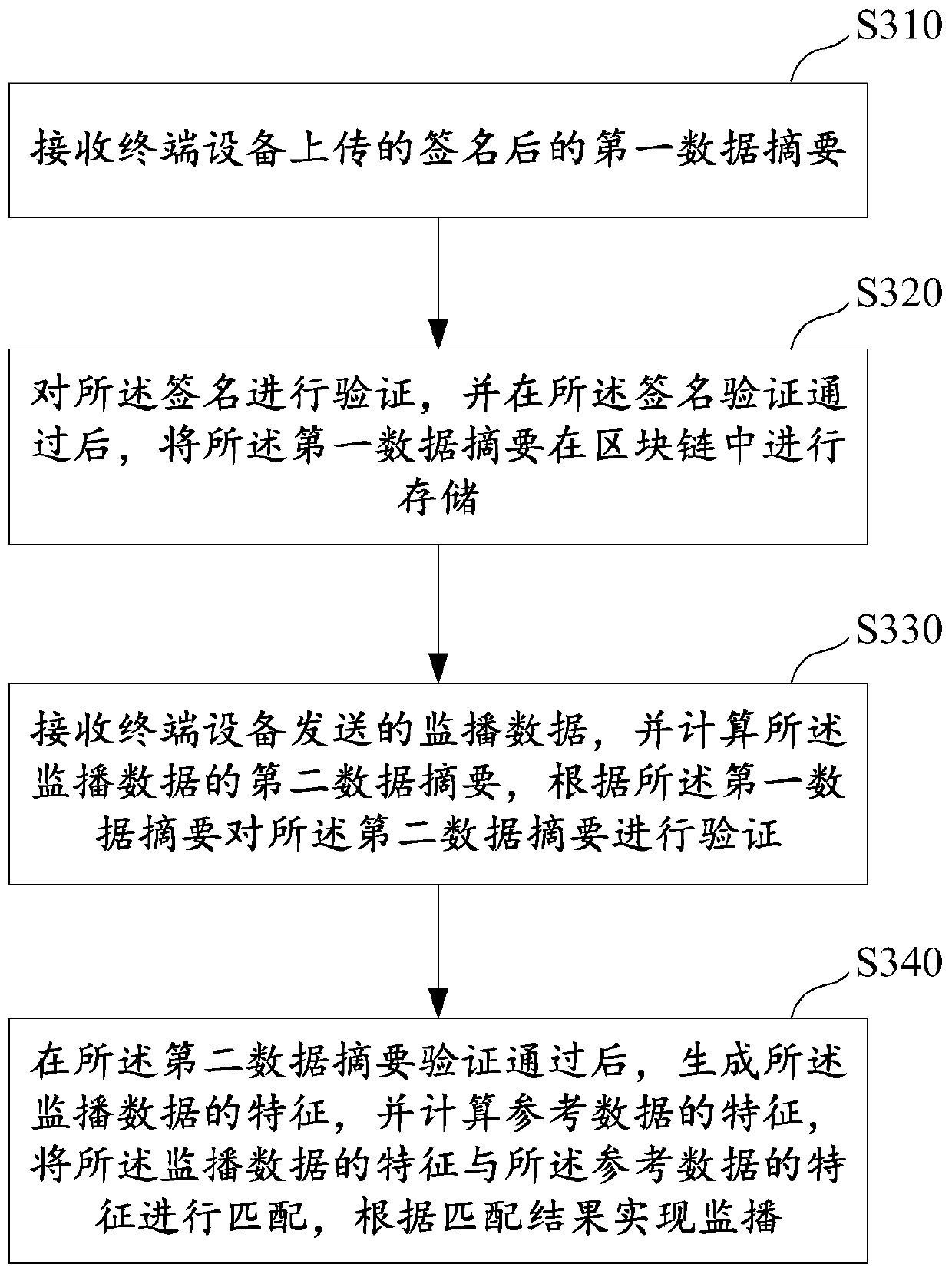
Block chain-based multimedia information monitoring broadcast method, device and system
PendingCN110046649ARealize automatic broadcast monitoringNot tampered withDigital data information retrievalCharacter and pattern recognitionBroadcast dataServer
The embodiment of the invention provides a block chain-based multimedia information monitoring broadcast method, device and system. The method comprises the steps of collecting and obtaining monitoring broadcast data of multimedia information, calculating a first data abstract of the monitoring broadcast data, signing the first data abstract, and publishing the signed first data abstract into a block chain; sending the monitoring broadcast data to a service server; enabling the service server to calculate a second data abstract of the monitoring broadcast data; and verifying the first data abstract and the second data abstract, generating the characteristics of the monitoring broadcast data after the verification is passed, calculating the characteristics of the reference data, and matching the characteristics of the monitoring broadcast data with the characteristics of the reference data, thereby realizing the monitoring broadcast of the multimedia information according to a matchingresult.
Owner:ADVANCED NEW TECH CO LTD
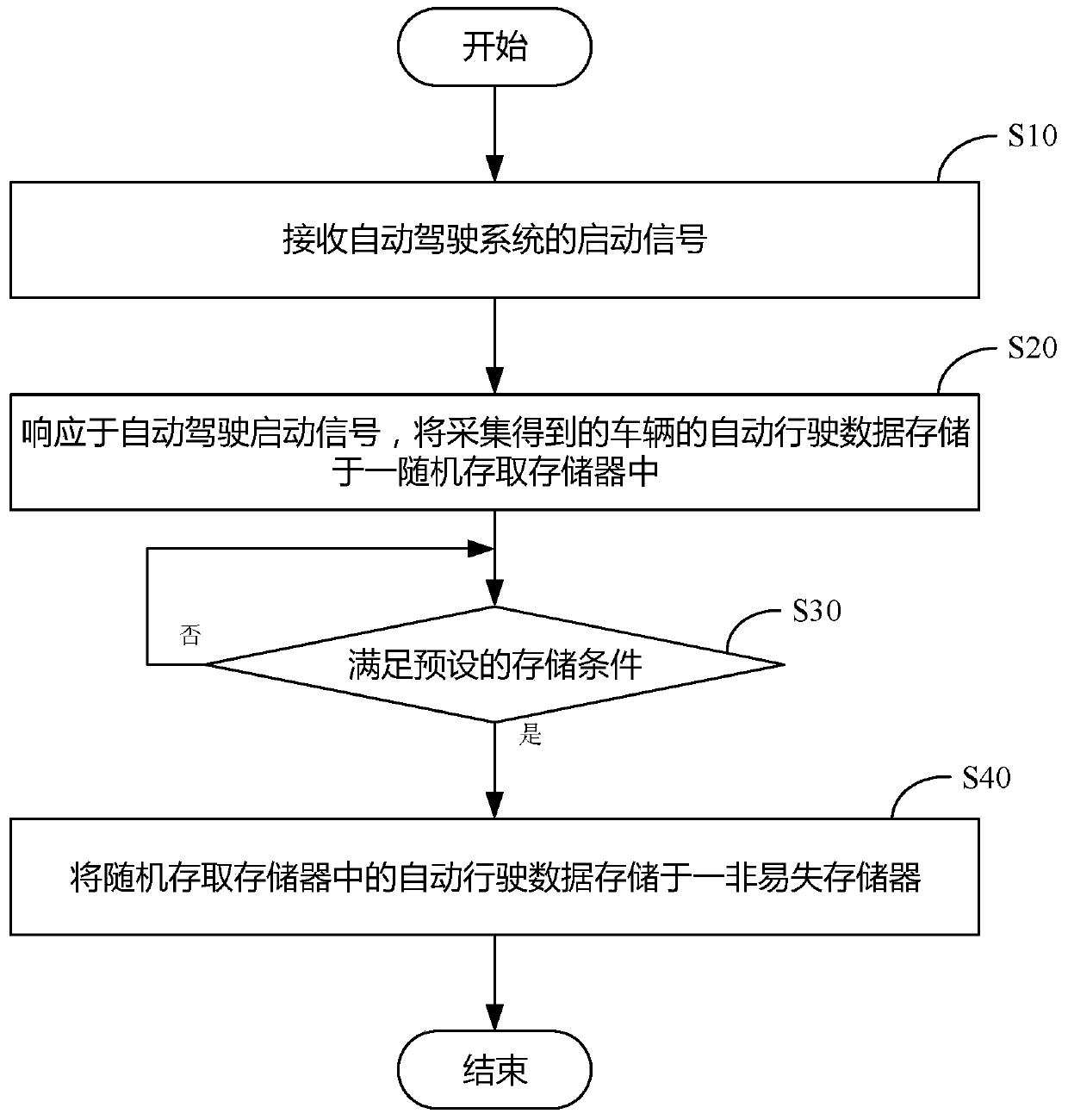
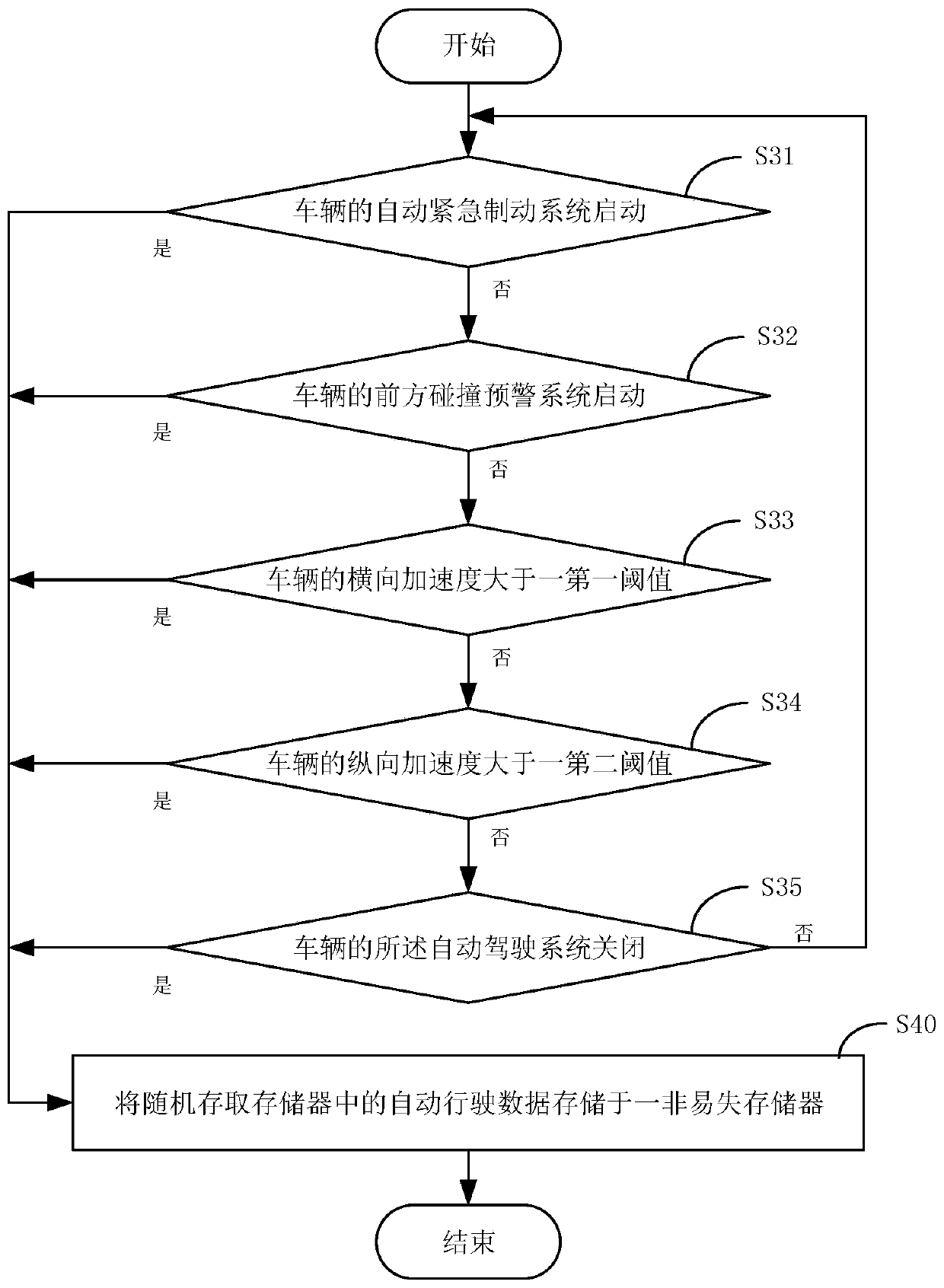
Automatic driving data processing method, system and device of vehicle black box and medium
InactiveCN110263564ANot tampered withImprove securityRegistering/indicating working of vehiclesDigital data protectionRandom access memoryComputer science
The invention discloses an automatic driving data processing method, system and device for a vehicle black box and a medium. The automatic driving data processing method comprises the steps of S10, receiving a starting signal of an automatic driving system; S20, in response to the automatic driving starting signal, storing the acquired automatic driving data of the vehicle in a random access memory; S30, when a preset storage condition is met, executing the step S40; S40, storing the automatic driving data in the random access memory in a nonvolatile memory, wherein the nonvolatile memory comprises a plurality of storage partitions, and storing the automatic driving data circularly in the storage partitions, so that the automatic driving data of the vehicle can be collected immediately when the automatic driving system is started, and the automatic driving data is stored in the nonvolatile memory. By dividing and respectively encrypting the automatic driving data, it is ensured that the stored automatic driving data is not tampered, and the safety of the data is improved.
Owner:AIWAYS AUTOMOBILE CO LTD
Multi-channel safety authenticating system and authenticating method based on U-Key
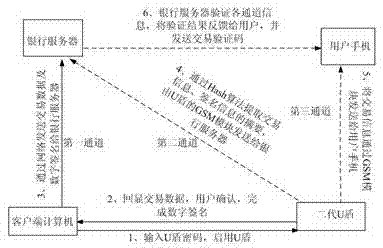
InactiveCN102819799ANot tampered withEnsure safetyPayment architectureTransmissionEngineeringFinancial transaction
The invention relates to a multi-channel safety authenticating system and an authenticating method based on a U-Key, aiming at ensuring safety of a network transaction; the authenticating system comprises the U-Key; a global system for mobile communications (GSM) module is added on the U-Key; one side of the GSM module is connected with a U-Key main control chip and the other is connected with a user mobile telephone and a bank network server through a wireless network; the U-Key comprises a display screen which is used for echoing a transaction account and amount transaction information, as well as a button for finishing an operation of confirming or canceling; data is transmitted to the user mobile telephone and the bank network server by the GSM module as authenticating a signature of the U-Key; with multi-channel transmission and multi-side authentication, risks that a user identity is falsely used and transmission data is interpolated are prevented; user transaction data is output by a USB (Universal Serial Bus) interface after authenticating a signature of the U-Key, and is then transmitted to a bank server by a user computer through a network and cached in the bank server; by checking and verifying the user identity and the transaction information through multiple channels, therefore, validity of the user identity and transmission security of the transaction data are effectively guaranteed.
Owner:ZHENGZHOU XINDA JIEAN INFORMATION TECH
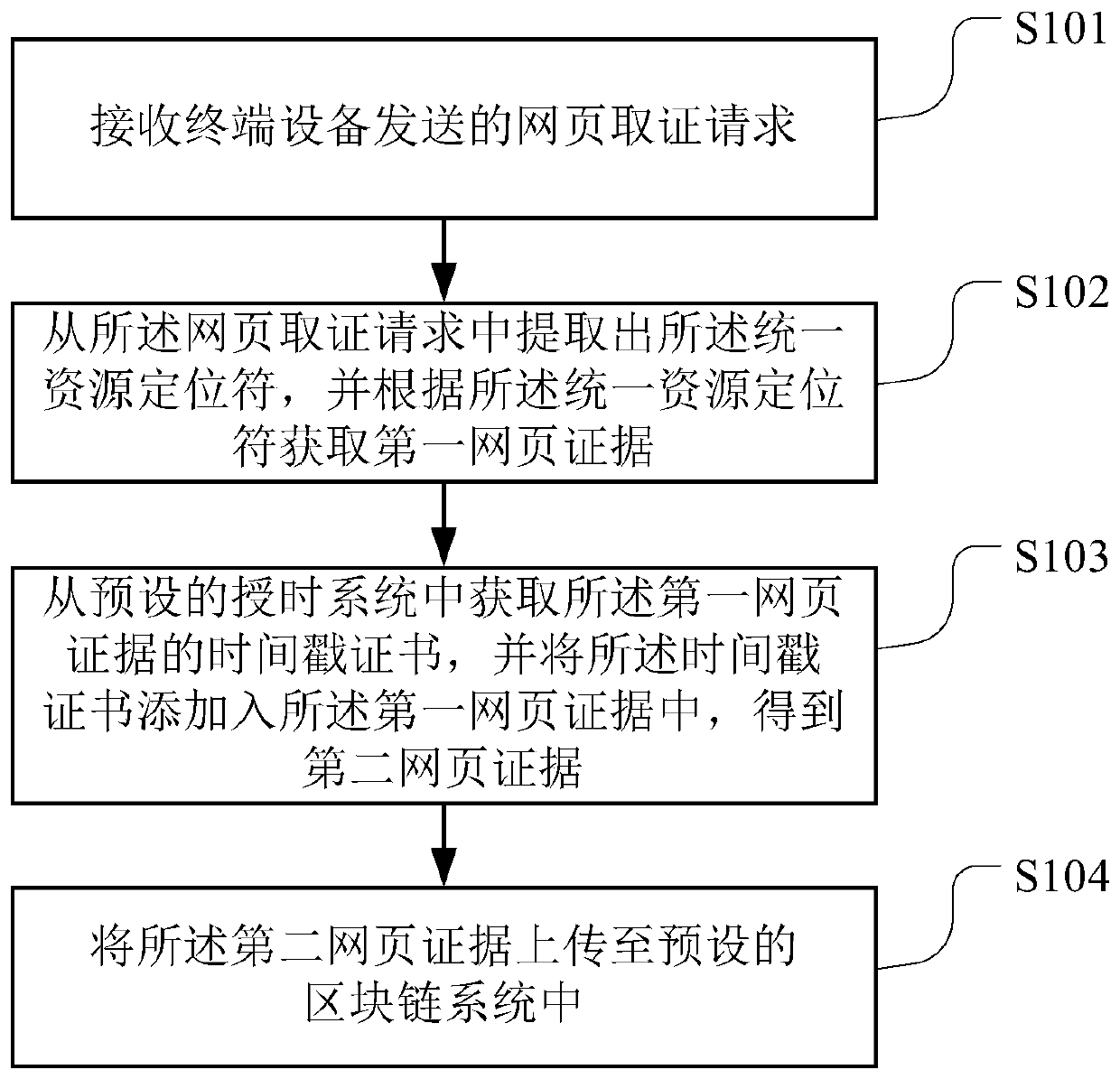
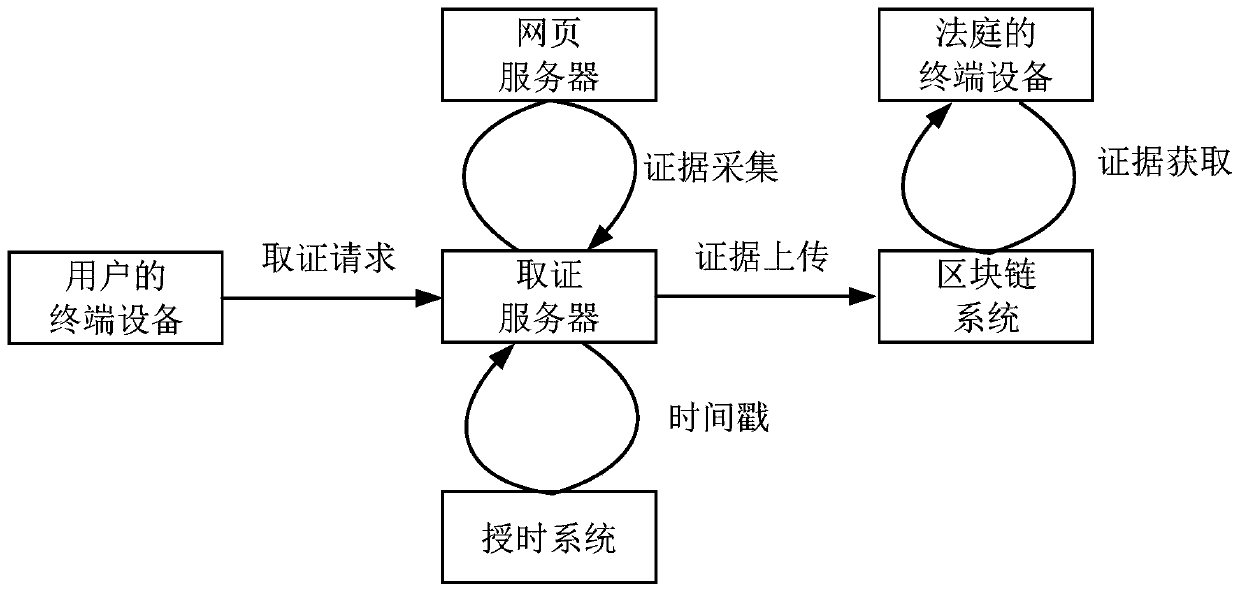
Block chain-based webpage evidence obtaining method, device, storage medium and server
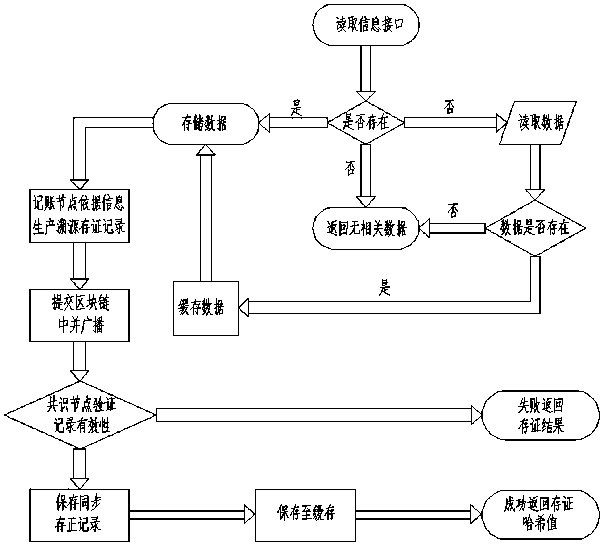
PendingCN110489676AImprove convincing powerRealize acquisitionDigital data protectionSpecial data processing applicationsChain systemService system
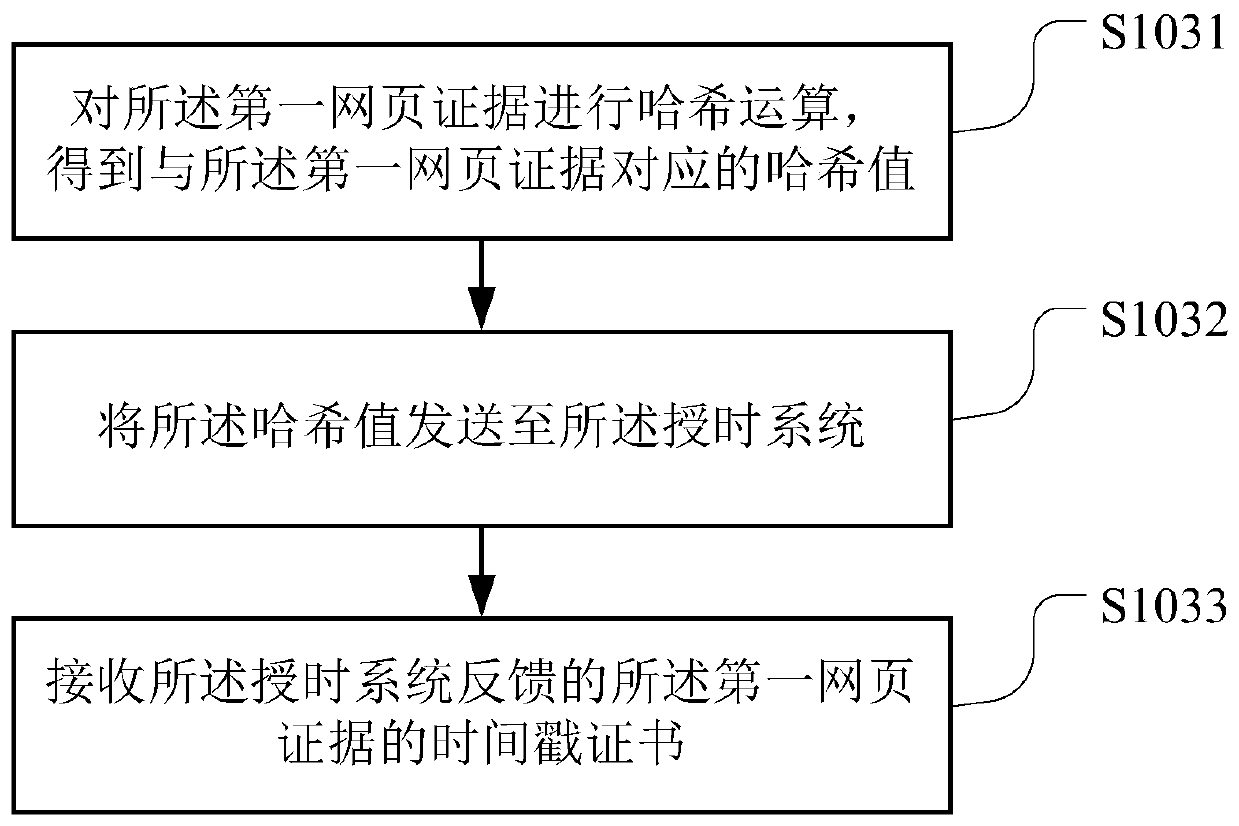
The invention belongs to the technical field of computers, and particularly relates to a block chain-based webpage evidence obtaining method, a device, a computer readable storage medium and a server.The method comprises the following steps: receiving a webpage evidence obtaining request sent by terminal equipment, wherein the webpage evidence obtaining request comprises a uniform resource locator of a target webpage; extracting the uniform resource locator from the webpage evidence obtaining request, and obtaining a first webpage evidence according to the uniform resource locator, wherein the first webpage evidence comprises an image of the target webpage; obtaining a timestamp certificate of the first webpage evidence from a preset time service system, and adding the timestamp certificate into the first webpage evidence to obtain a second webpage evidence; and uploading the second webpage evidence to a preset block chain system. As the evidence obtaining time is proved through the time service system, it is ensured that the evidence cannot be tampered through the block chain system. The credibility of the evidence is greatly improved, and the evidence can be accepted by courts.
Owner:PING AN TECH (SHENZHEN) CO LTD
Android application program strengthening method
ActiveCN107092816ANot tampered withDigital data protectionTransmissionComputer securityApplication software
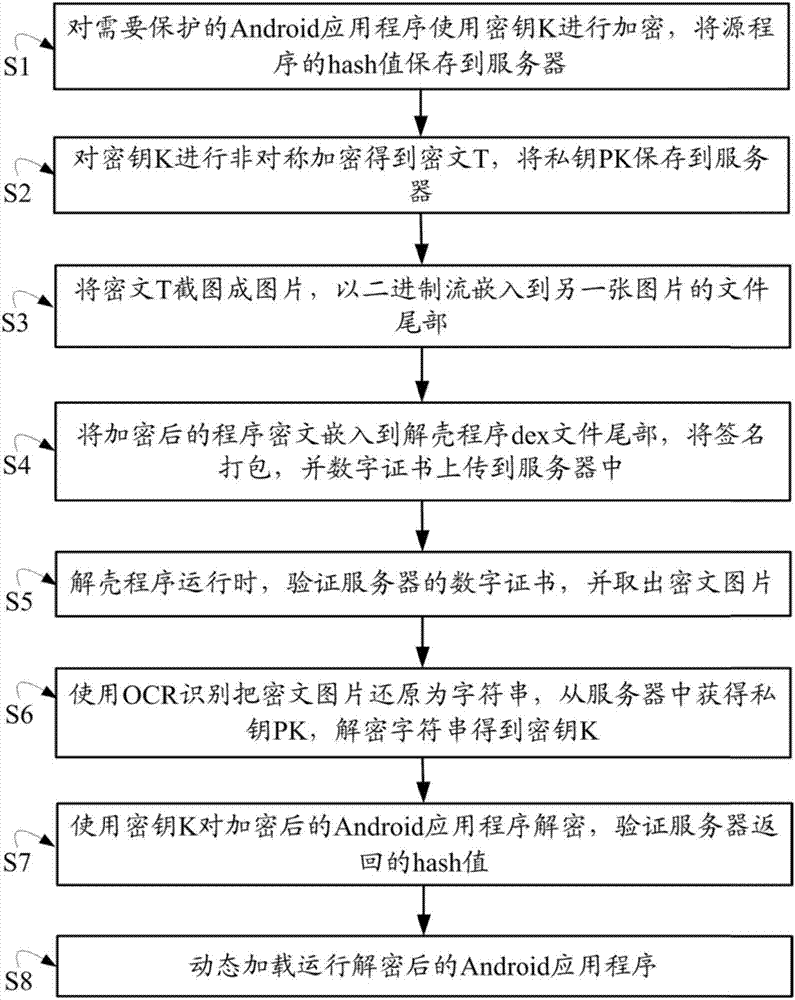
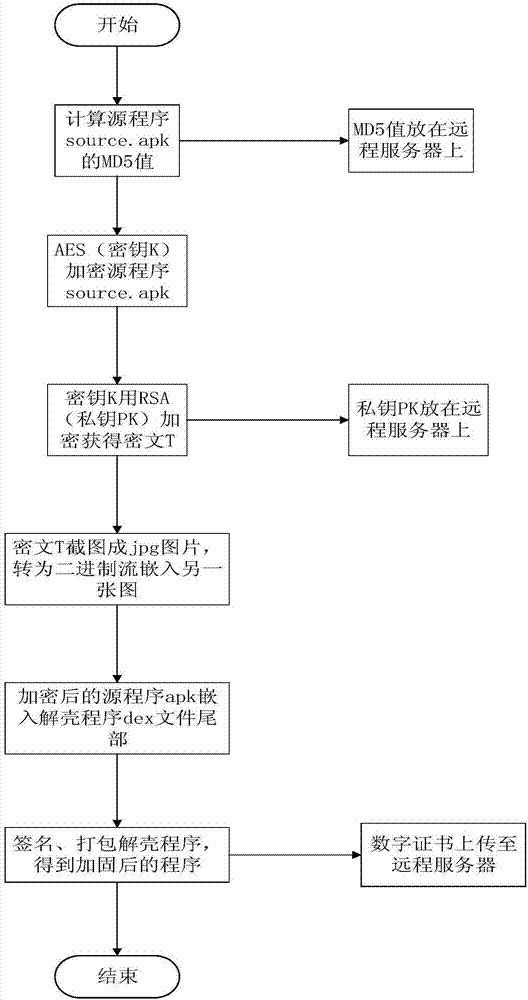
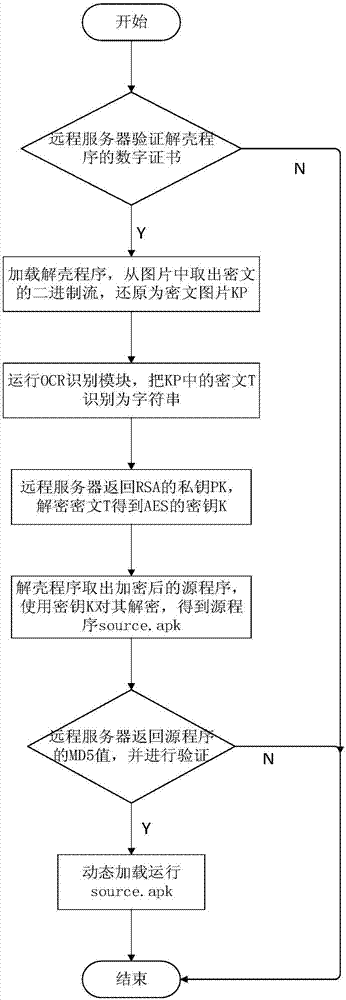
The invention discloses an Android application program strengthening method. The method comprises the following steps of: encrypting a to-be-protected Android application program by using a secret key; asymmetrically encrypting the secret key to obtain a ciphertext; carrying out screenshot on the ciphertext to obtain a picture and embedding the picture into the tail part of a file of another picture via a binary stream; embedding the encrypted program ciphertext into the tail of a file of an deshell program; when the deshell program is operated, validating a digital certificate of a server and taking out a ciphertext picture; restoring the ciphertext picture into a character string by using OCR identification, obtaining a private key from the server, and decrypting the character string to obtain a secret key; decrypting the encrypted Android application program by using the secret key; and dynamically loading and operation the decrypted Android application program. According to the method, key codes of mobile application programs are encrypted, and a remote server is combined to ensure that programs are not tampered, so that the aim of protecting Android application programs is achieved.
Owner:GUANGDONG UNIV OF TECH
Data trusted processing method and system fusing trusted computing and block chain
ActiveCN114499895ARealize trusted acquisitionRealize computingUser identity/authority verificationInstrumentsPrivacy protectionData acquisition
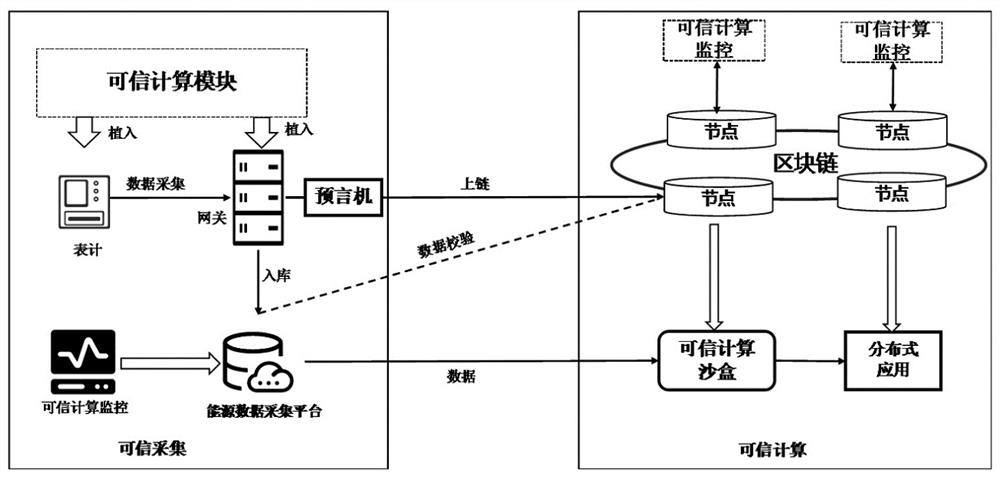
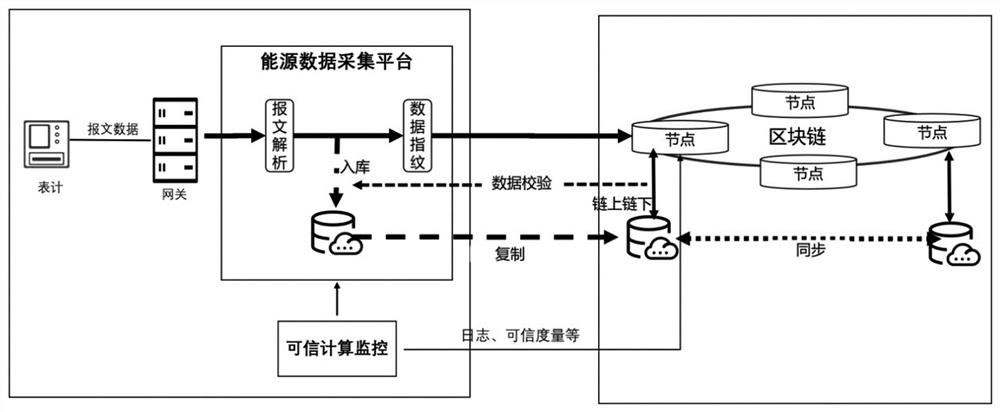
The invention discloses a data trusted processing method and system fusing trusted computing and a block chain, and belongs to the technical field of energy data processing. The invention discloses a data trusted processing method and system fusing trusted computing and a block chain. The data trusted processing method and system are mainly used for solving the energy data trust problem before energy data is chained in the current block chain application process and the environment trusted problem of service computing. Aiming at the problem of credibility of uplink energy data, starting from two aspects of an Internet of Things acquisition end or an Internet of Things energy data acquisition platform, a method of fusing a credible computing technology and a block chain technology is adopted, and Internet of Things acquisition equipment, an oracle machine and an on-chain and off-chain energy data credible verification model are embedded through credible computing; the credibility of energy data collection, transmission and storage processes is realized, and the credibility of energy data collection is ensured in combination with security monitoring of credible computing. In order to solve the problem of a service computing environment, the invention provides a computing architecture combining trusted computing and a state channel, so that service computing is carried out on energy data under the condition of privacy protection.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com