Data trusted processing method and system fusing trusted computing and block chain
A technology of trusted computing and processing methods, applied in digital transmission systems, transmission systems, secure communication devices, etc., can solve the problem of insufficient design of trusted management methods, difficulty in ensuring data authenticity, lack of trusted data collection and data storage. letter management issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
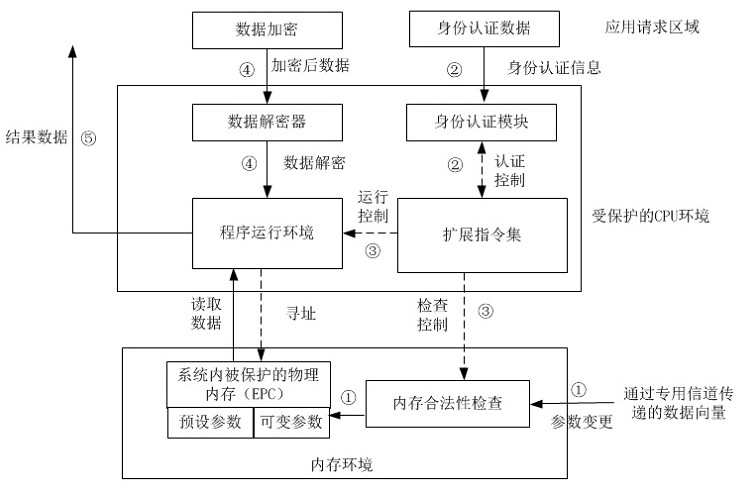
[0169] A trusted data processing method that integrates trusted computing and blockchain,
[0170] Include the following steps:
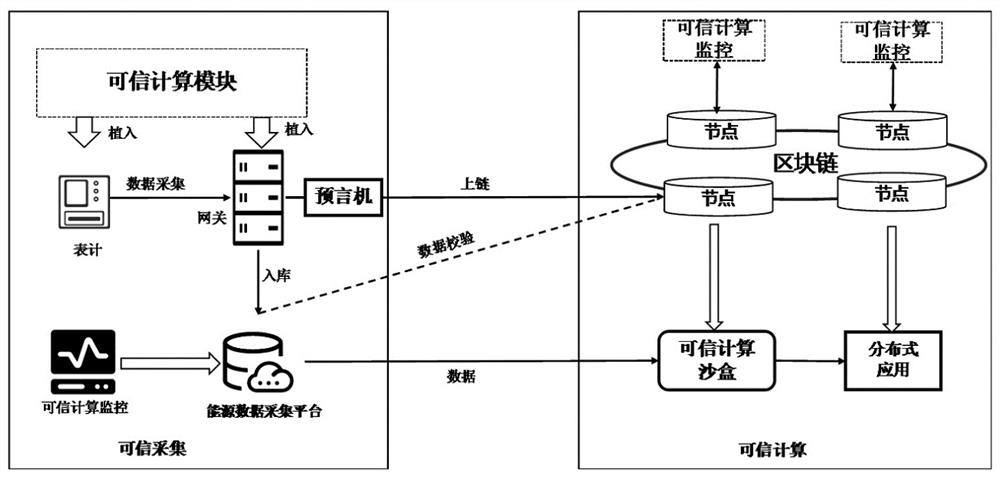
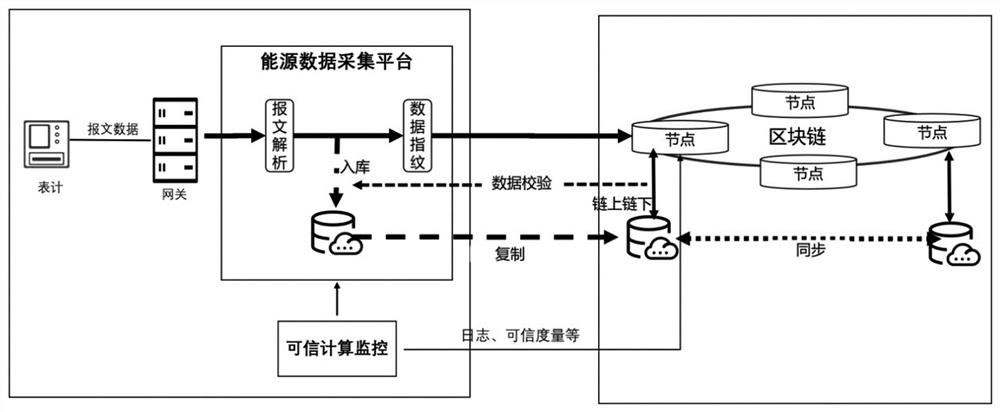
[0171] In the first step, the meter implanted with the trusted computing module generates a message based on the collected energy data according to the protocol rules. The message includes equipment information, time information, and energy data information of the energy sensor, and sends the message through the communication module To the IoT gateway embedded in the Trusted Computing Module;
[0172] In the second step, after the message in the first step is successfully sent, the IoT gateway completes the identity verification of the source of the energy data, and sends the message to the energy data collection platform based on the trusted computing monitoring system;
[0173] In the third step, after the energy data collection platform in the second step receives the message, the energy data collection platform analyzes the message to obtain en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com