Cloud computing access method based on cross domain identity authentication
An identity authentication and access method technology, applied in the field of identity authentication and cloud computing technology, can solve the problems of complex data, inconvenient management of cross-domain identity authentication, etc., and achieve the effect of ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
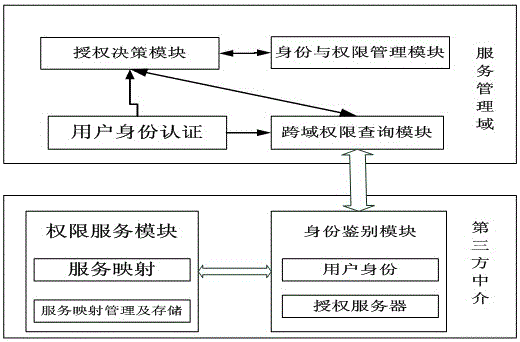
[0030] Configure the cloud computing access system based on cross-domain authentication:
[0031] The system consists of a local identity authentication module, a local authorization decision-making module, a local identity and authority management module, a cross-domain authority query module, a third-party identity authentication module, and a third-party authority service module.
[0032] The local identity authentication module completes the identity authentication function of the visited entity, if the entity belongs to the management domain, then directly identify the identity and authority of the entity; if the entity is an entity of other management domains, it needs to pass The cross-domain permission query module performs cross-domain identity authentication and authorization.
[0033] The local identity and rights management module manages user identities and their access rights, including changes in user identities and changes in user rights.
[0034] The local au...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com