Trusted two-dimensional code generation method and device, electronic equipment and storage medium
A two-dimensional code and two-dimensional code information technology, applied in the field of communication, can solve the problems of unauthorized access, leakage of user private information, increase of two-dimensional code security problems, etc., and achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
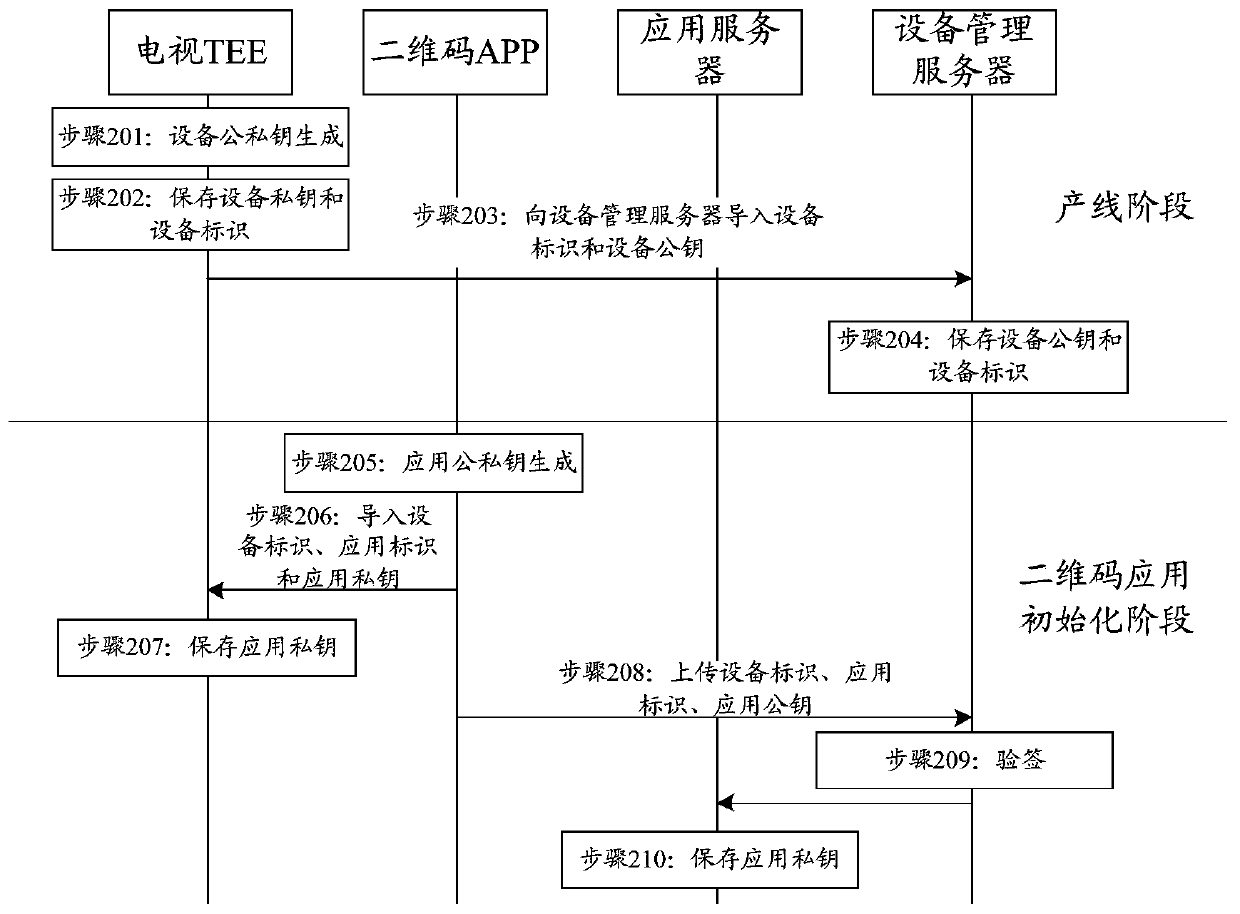
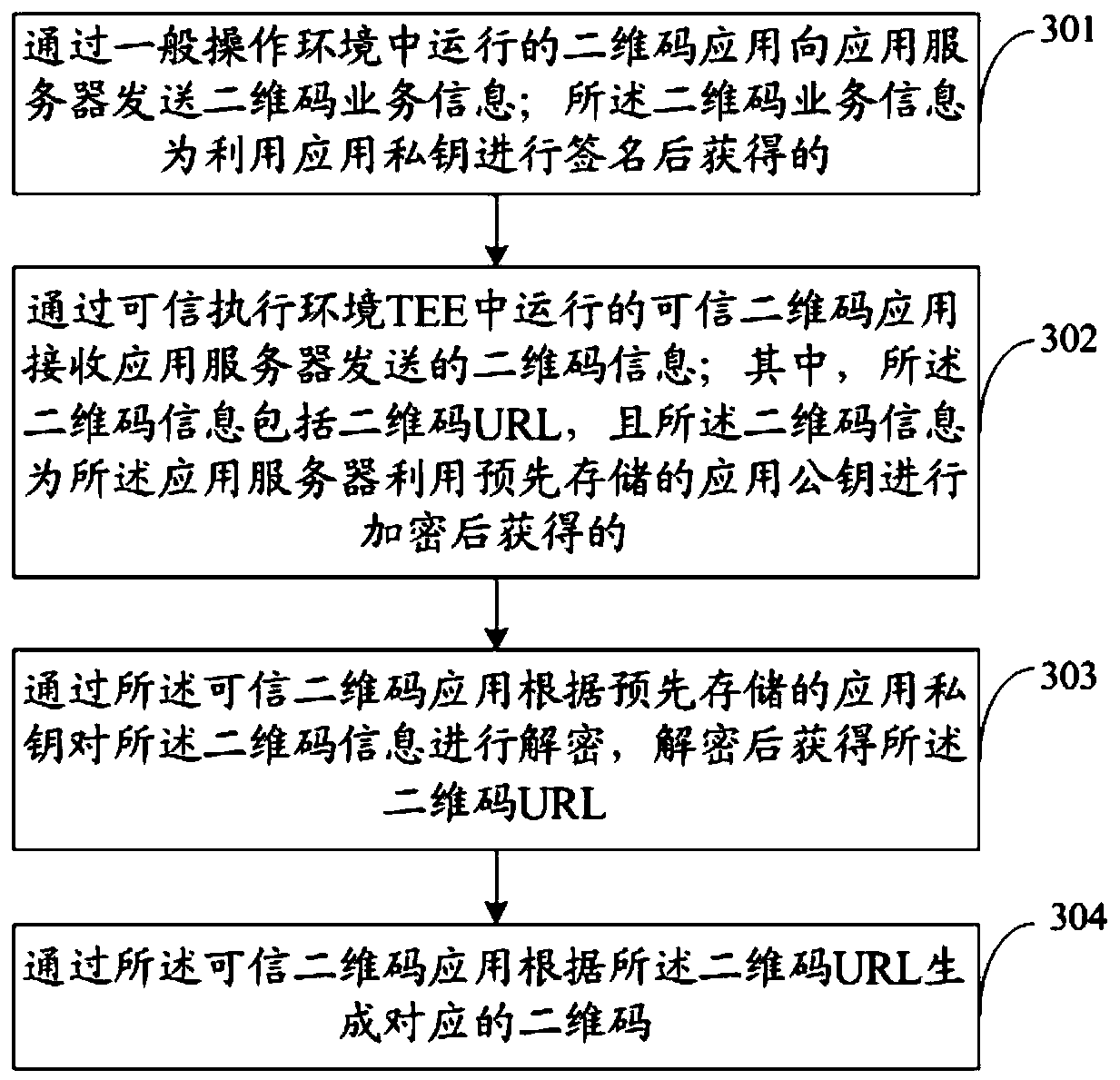
[0057] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
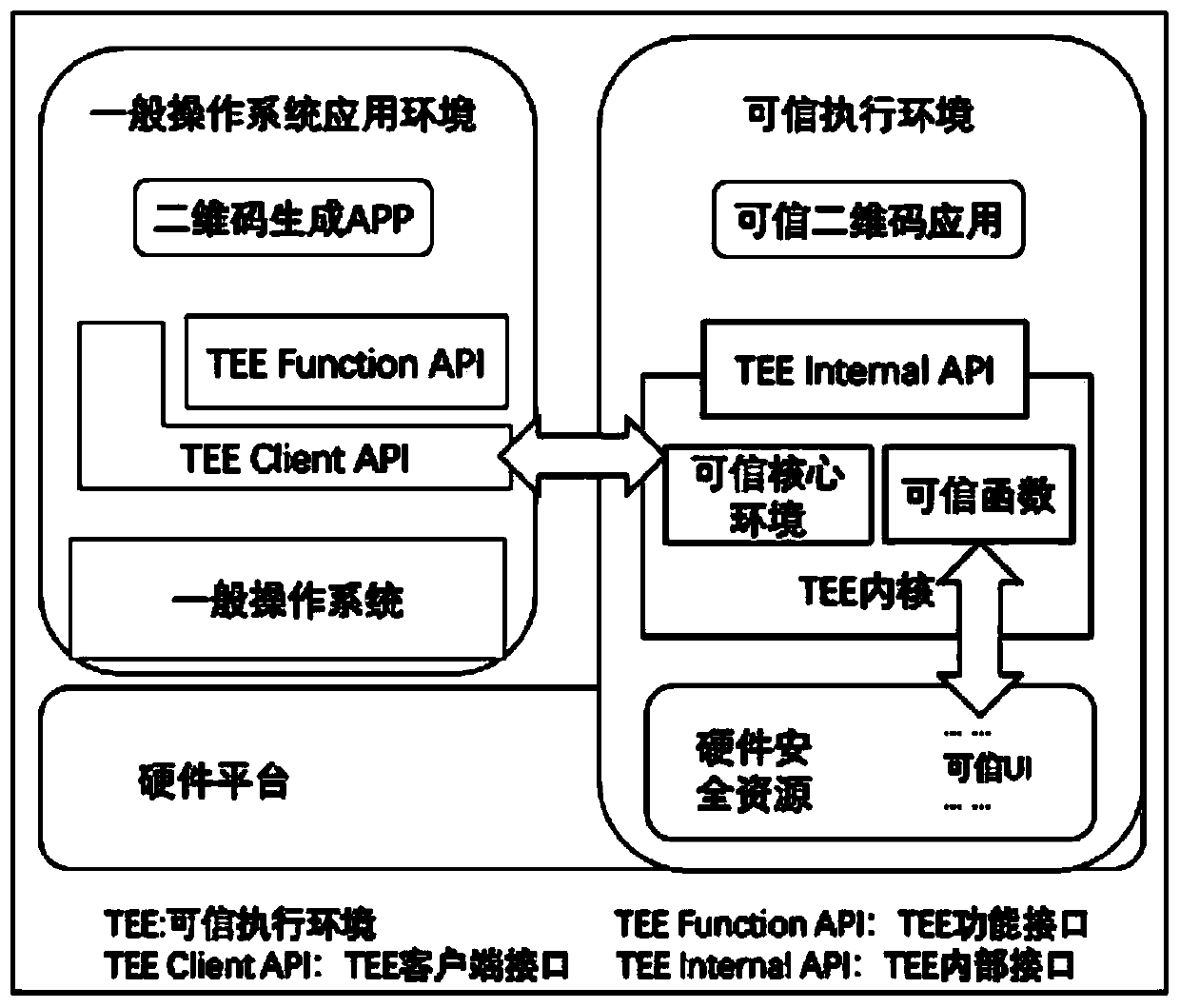
[0058] figure 1 The trusted two-dimensional code TV terminal architecture diagram provided for the embodiment of this application, such as figure 1 As shown, a general operating system application environment (Rich Execution Environment, REE) and a trusted execution environment (Trusted Execution Environment, TEE) are simultaneously running in the TV terminal. A common environment in IEDs is REE. In the embodiment of this application, the two-dimensional code application runs in the REE, and the trusted two-dimensional code application runs in the TEE. For example, the third-party communication application WeChat, its online chat function is executed in the REE WeChat application, and its online payment The functions of TEE are executed in the trusted WeChat application in TEE.
[0059] TEE is an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com