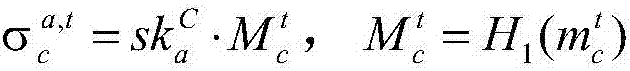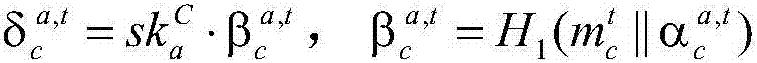Patents
Literature
424results about How to "Ensure information security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
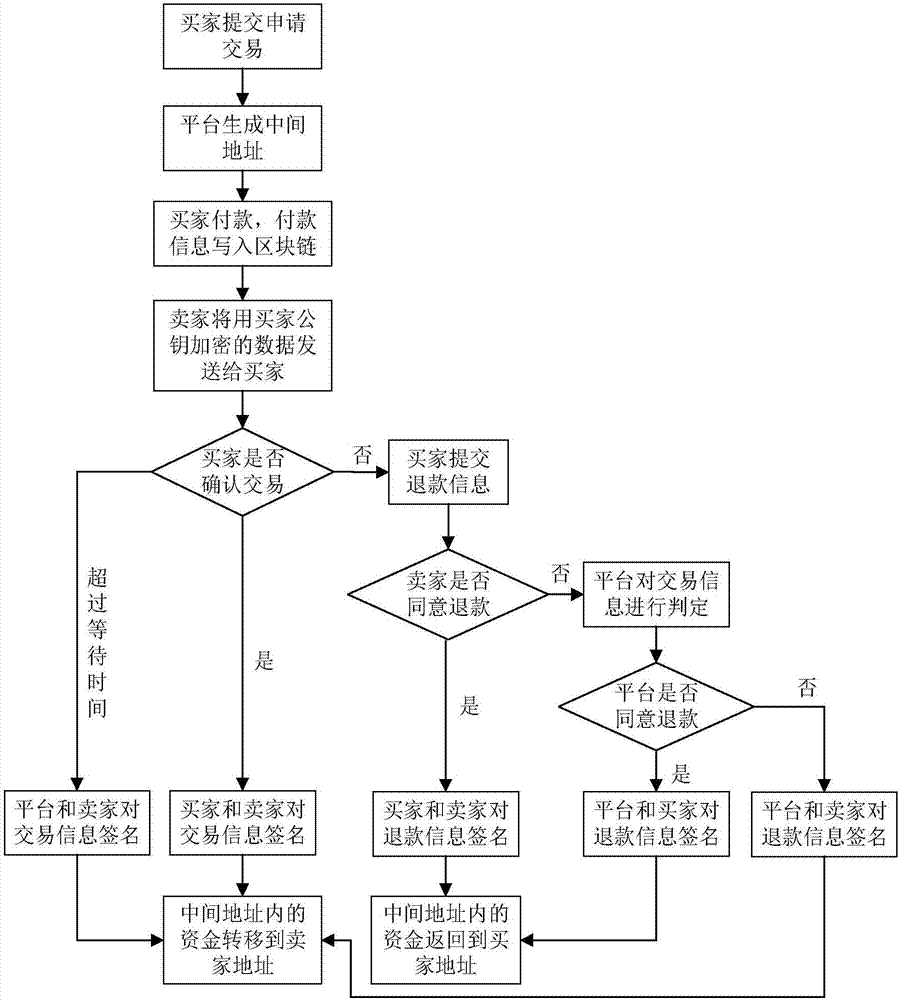
Multi-signature transaction information processing method for data transaction platform based on block chain
ActiveCN107038578AEnsure information securityEnsure safetyPayment protocolsInformation processingPayment
The invention discloses a multi-signature transaction information processing method for a data transaction platform based on a block chain. Each of a buyer and a seller generates a transaction key pair at self client, and the data transaction platform generates and distributes a single transaction key pair for each transaction process; the seller releases data to be transacted on the block chain via the data transaction platform; after the buyer submits a transaction application, an intermediate address is generated according to a three-party public key, money is transferred to the intermediate address after payment, and the seller receives the money, writes the money into the block chain, then encrypts data and sends the encrypted data to the buyer; after the buyer receives the data, if transaction is acknowledged, the double parties sign, and the money is transferred to the address of the seller; and if objection exists, the data transaction platform makes a judgment, and determines to transfer the money to the buyer or the seller according to the judgment result. Data and transaction information during transaction of the double parties are processed in a special regional chain manner, and meanwhile, the data transaction platform cannot embezzle the transaction money, so that the security of digital assets during transaction is further guaranteed.
Owner:浙江数秦科技有限公司
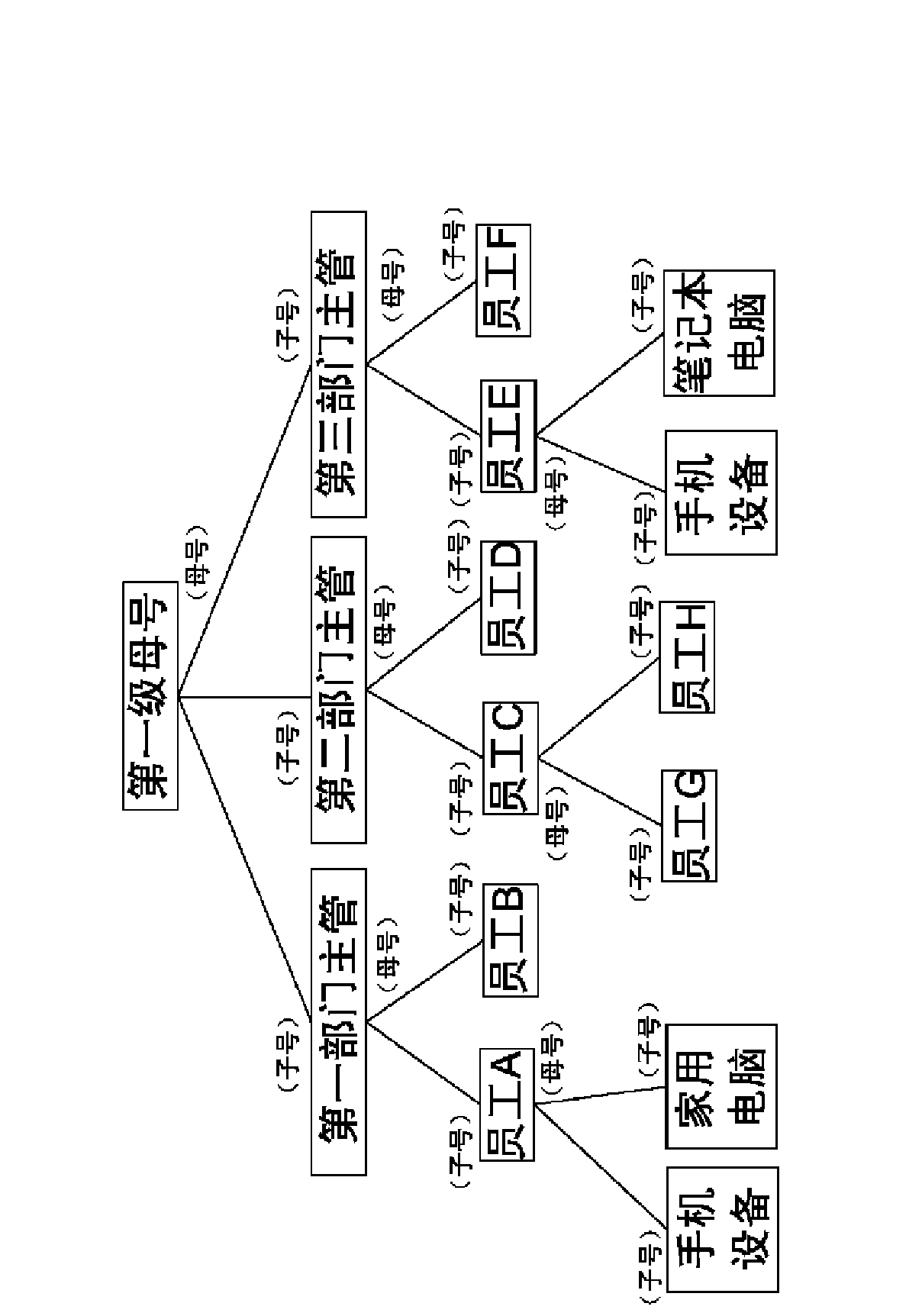
Multiuser system privilege management method and instant messaging system applying same
ActiveCN101834878AAchieve sharingEnsure safetyData switching networksAutomatic controlMultiuser system
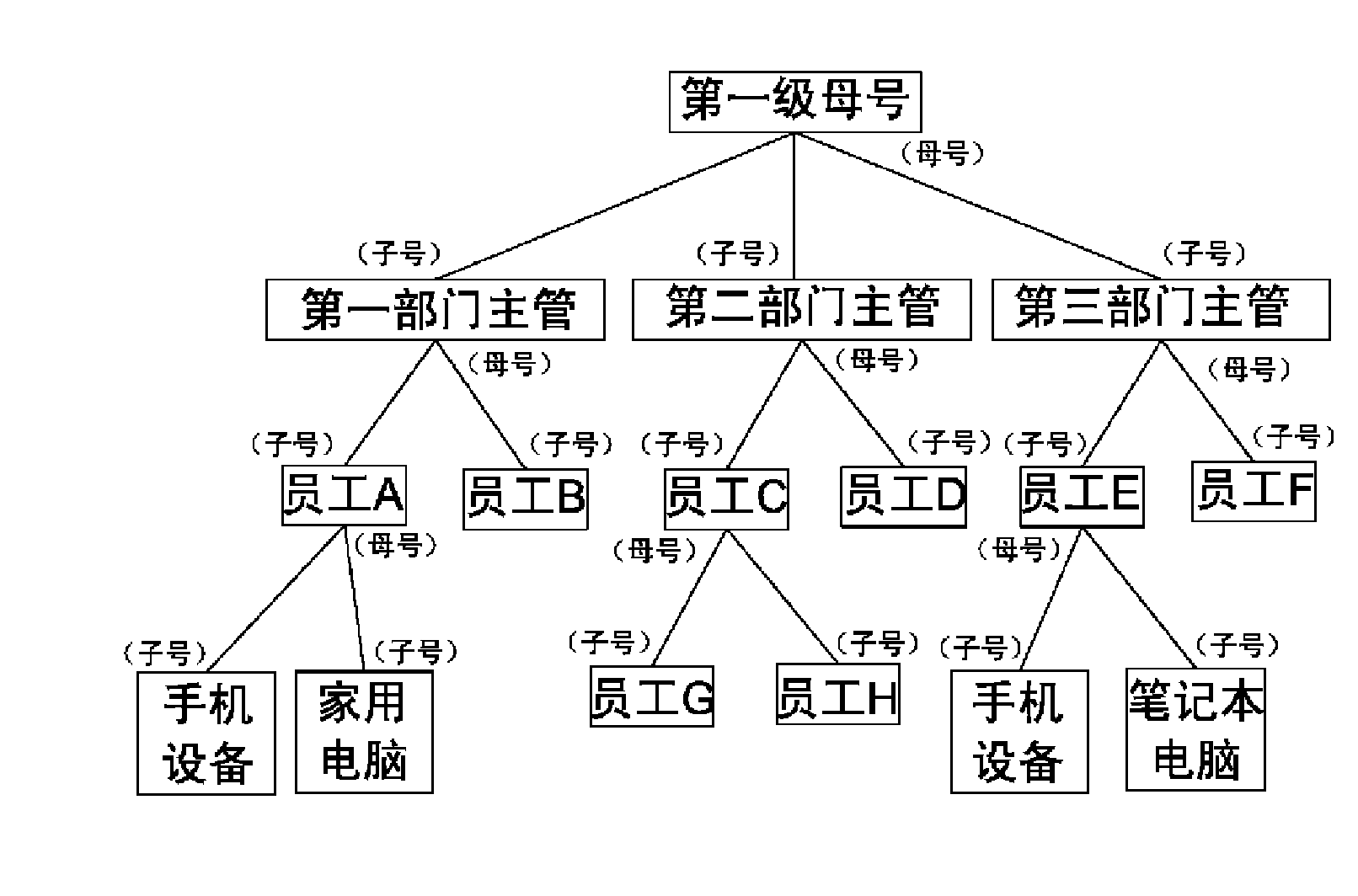
The invention relates to a multiuser system privilege management method which comprises the following steps of: 1, establishing a login account into a mother account; and incorporating the login account except for the mother account by the mother account to enable the login account to be a child account, designating the permission of a holding end of the child account and resources inherited from the holding end of the mother account by the holding end of the mother account. The invention also relates to an instant messaging system for managing function permission and resources of an instant messaging client by applying the multiuser system privilege management method, an instant messaging system which is capable of carrying out inside network communication, outside network communication, private account communication and automatic calling and switching of a communication module according to a sensed network connect state, and a login method for automatically controlling child account, mother account and private account independent login or child account, mother account and private account combined login in a mode of verifying a login device hardware code, a local area network IP address and a special login permission.
Owner:陈时军
Internal threat detection system based on mining of business process model and detection method thereof
ActiveCN106209893AEnsure information securityNormal operation impactTransmissionSpecial data processing applicationsControl flowBusiness activities
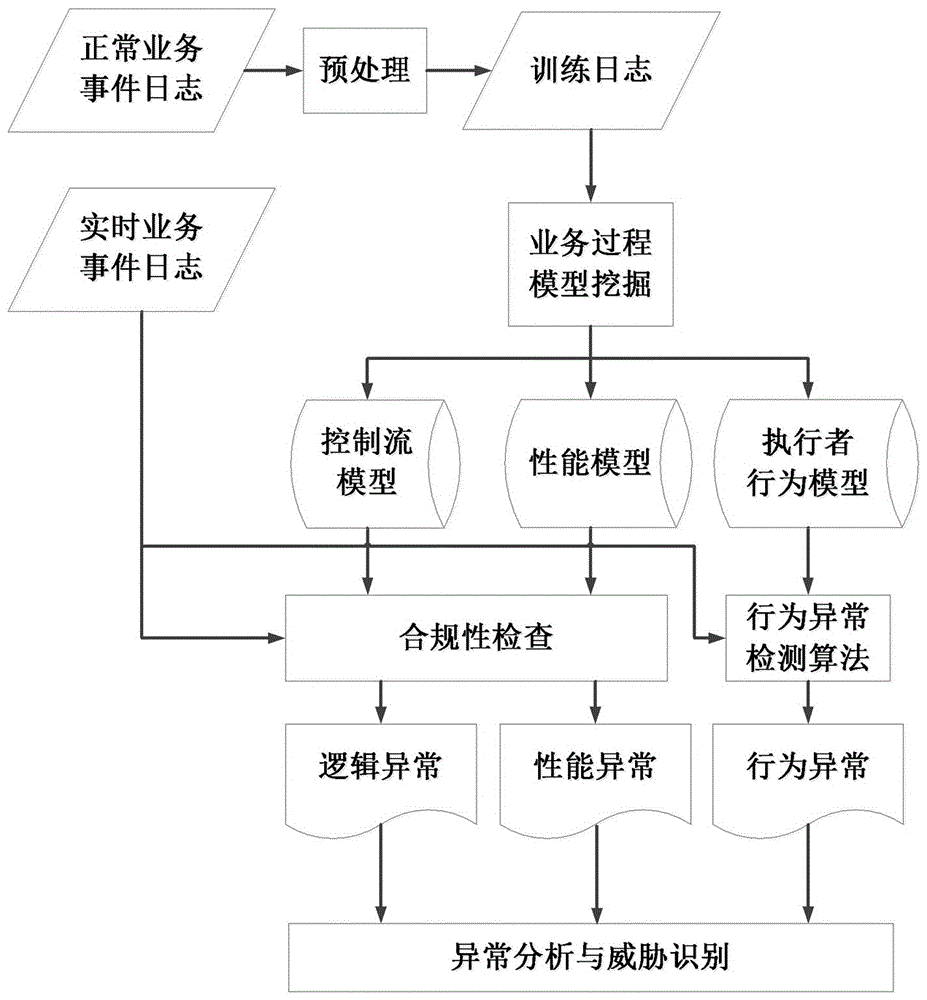
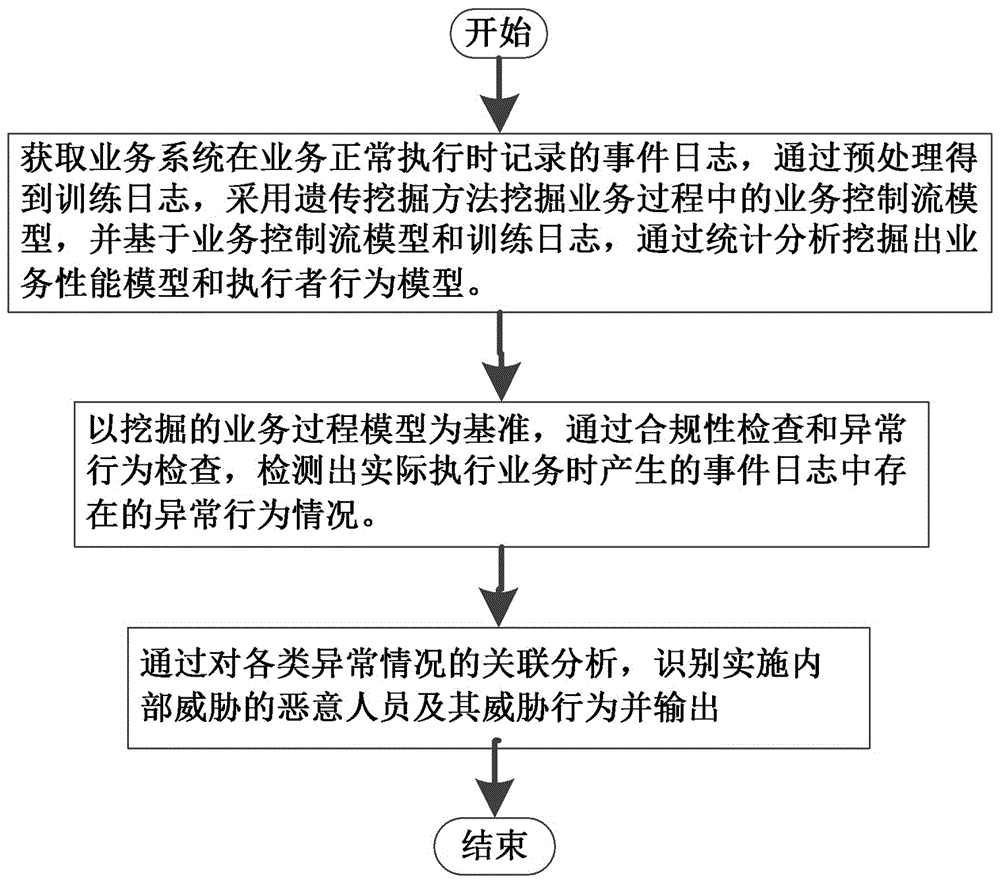
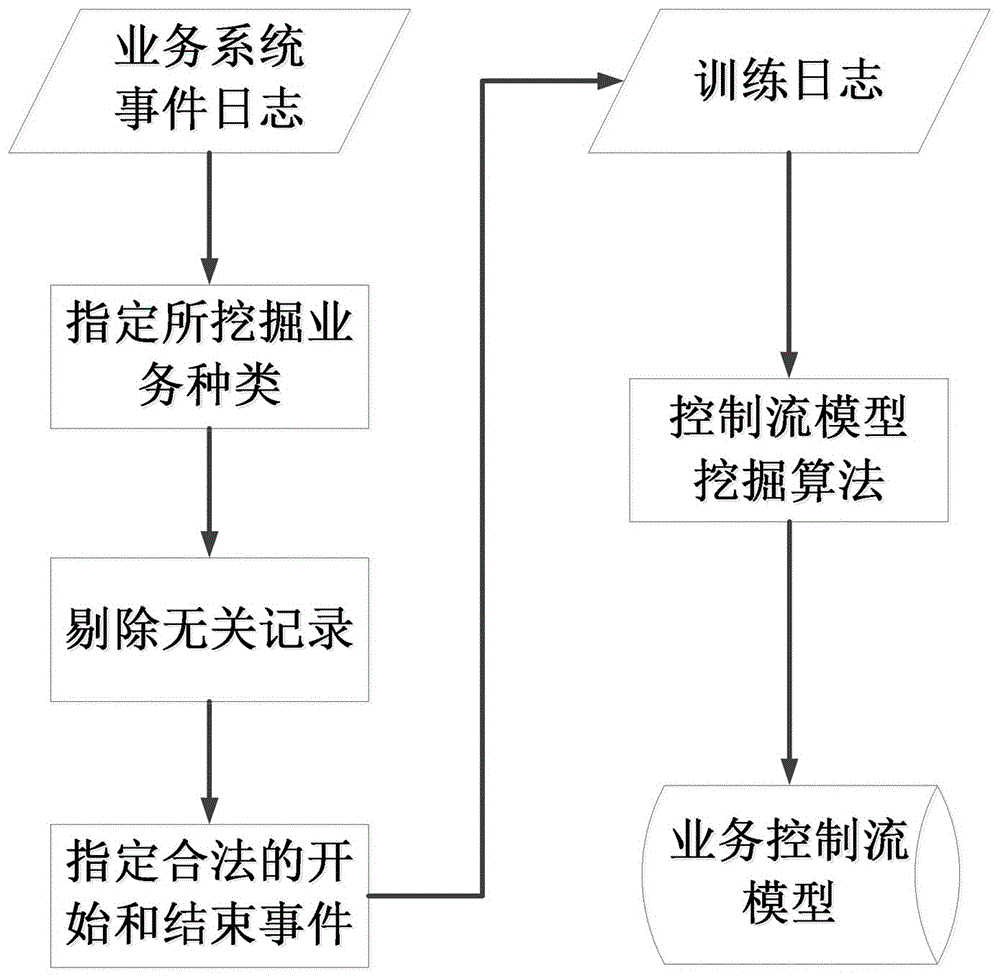
The invention relates to an internal threat detection system based on mining of a business process model and a detection method thereof. The detection system comprises a model mining module, an abnormality detection module and an abnormality analysis model, wherein the model mining module implements model mining according to an event log of each business event in a business system, and thus acquires a business control flow model, a business performance model and an executor behavior model; the abnormality detection module detects logic abnormality, performance abnormality and behavior abnormality of the event log generated during a real-time operation process of a business activity according to the model mining module; and the abnormality analysis model parses a detection result of the abnormality detection module, recognizes execution information about implementation of an internal threat and outputs the information. According to the internal threat detection system based on mining of the business process model established in the invention, the internal threat behavior existing in the business execution process is effectively detected, a powerful support is provided for enterprises and various organizations to prevent the internal threat, and information security of enterprises and organizations is effectively ensured.
Owner:THE PLA INFORMATION ENG UNIV
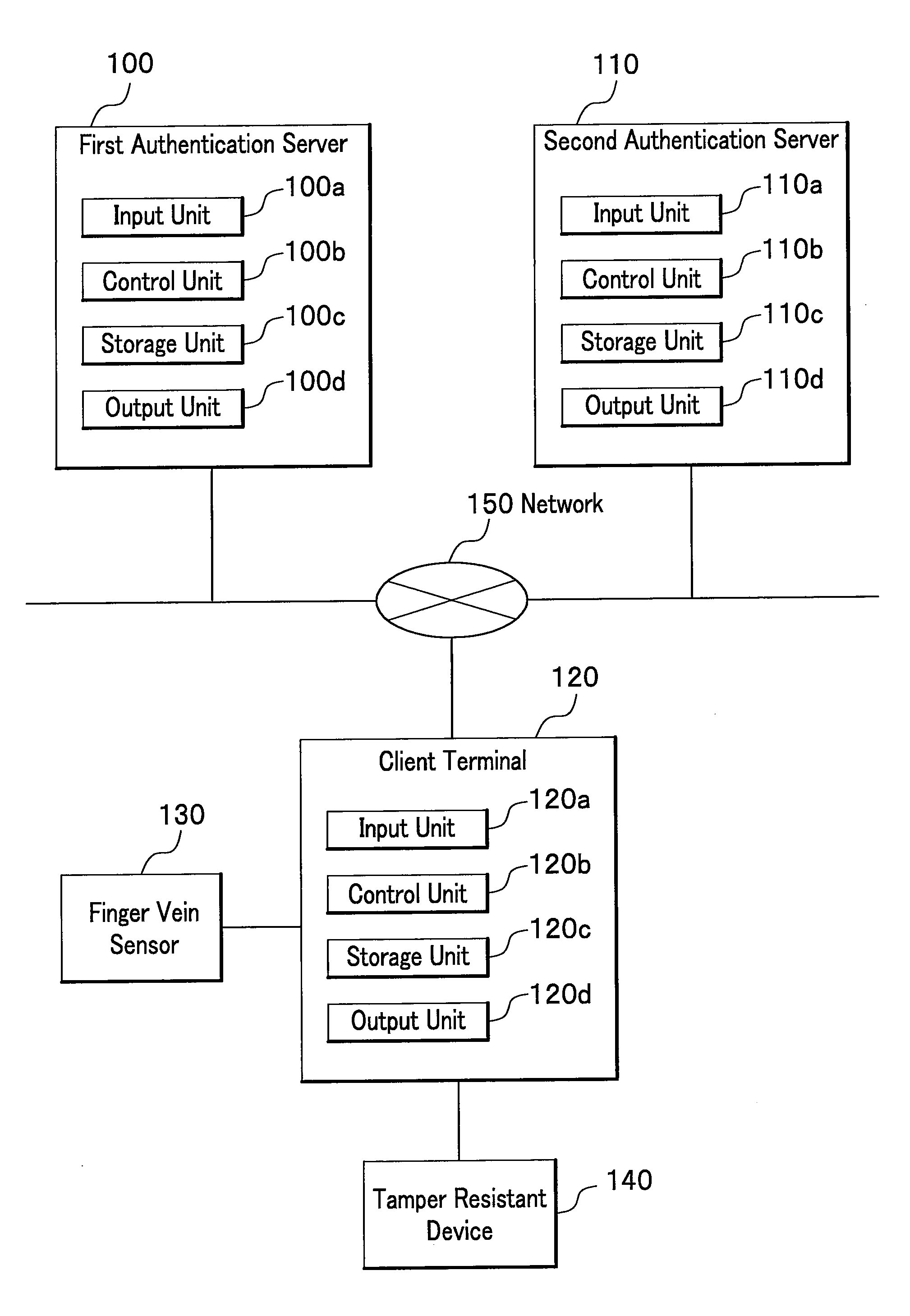
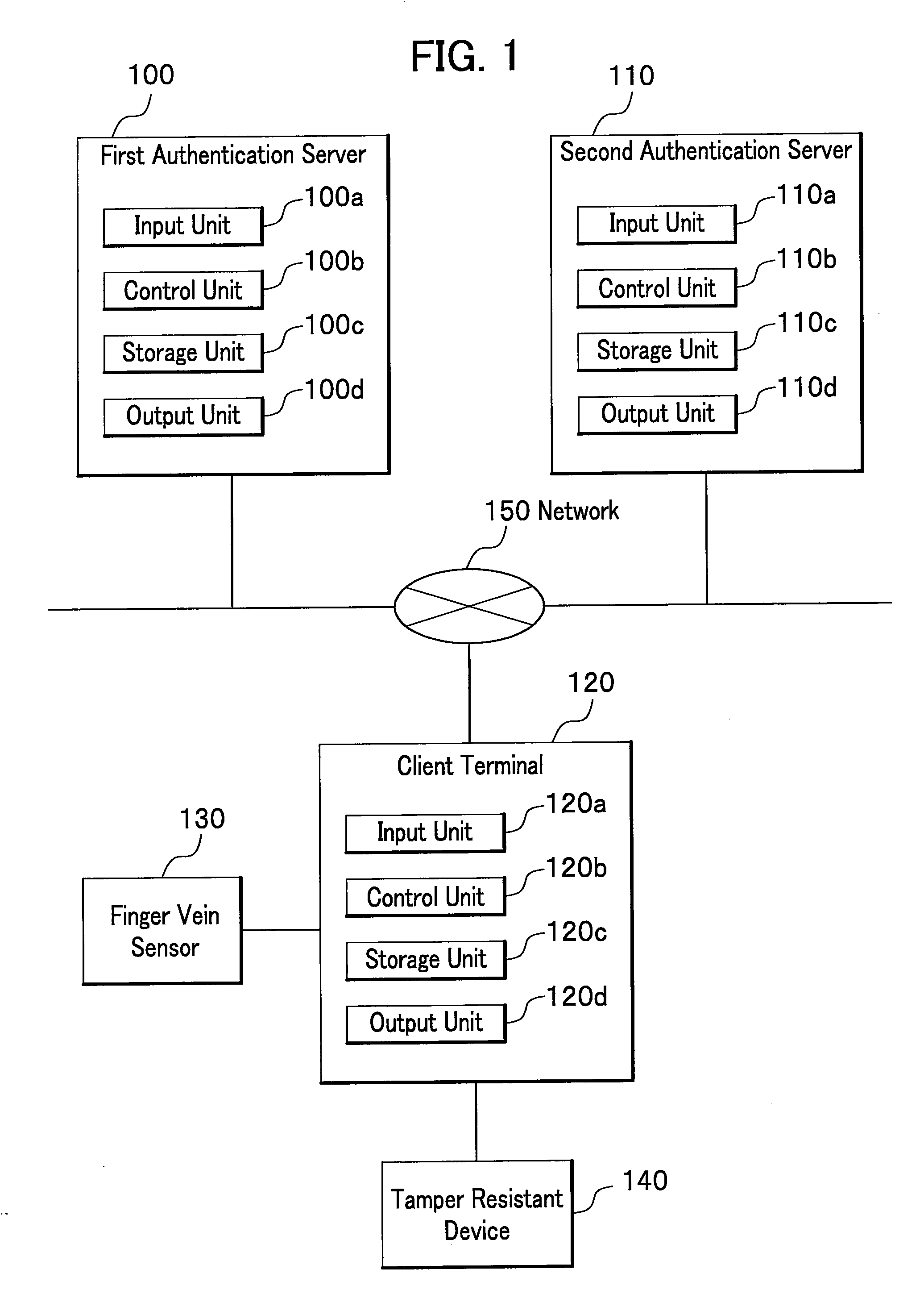
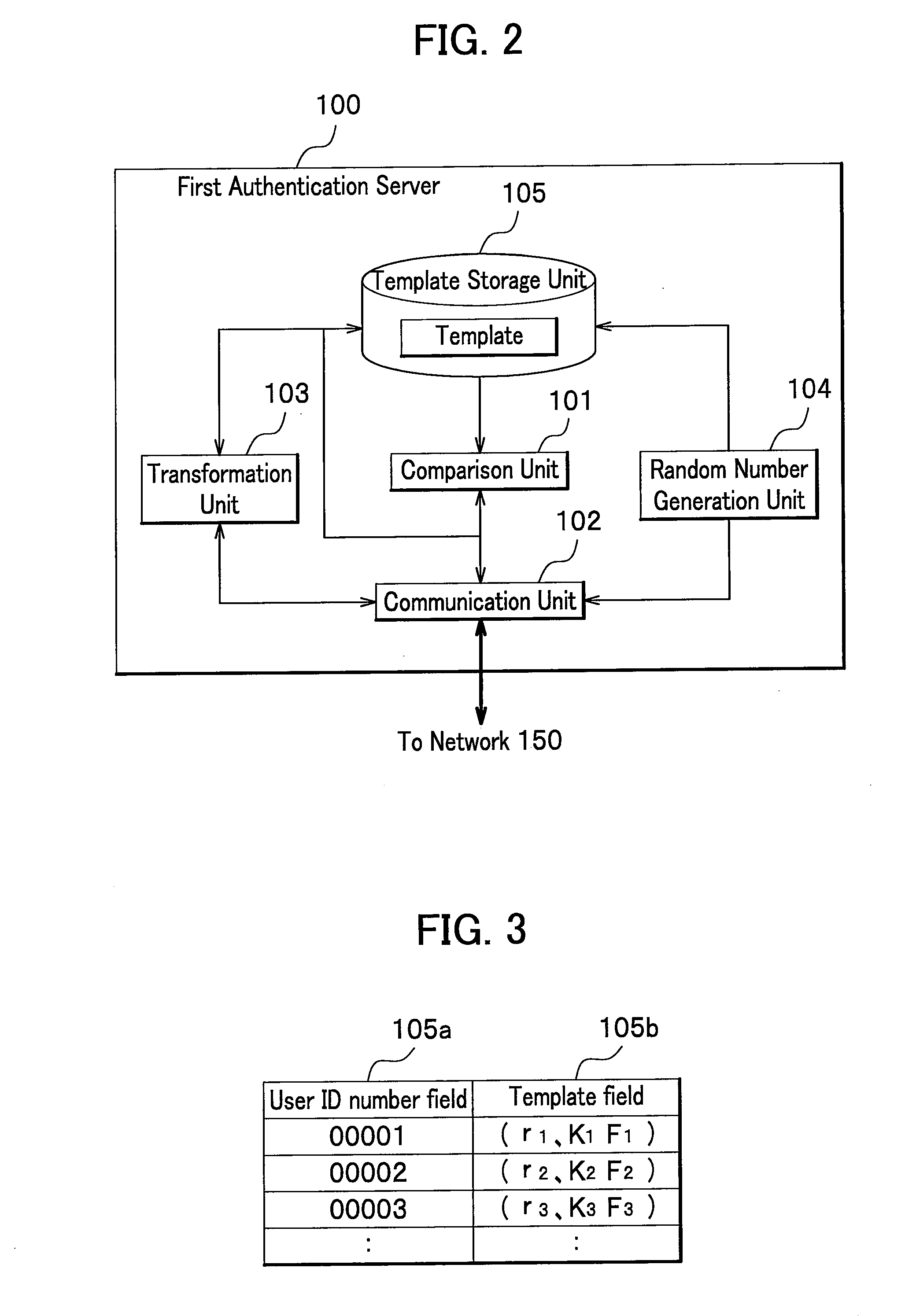
Authentication server, client terminal for authentication, biometrics authentication system, biometrics authentication method, and program for biometrics authentication
InactiveUS20090070860A1Reduce the burden onEnsure information securityDigital data processing detailsUser identity/authority verificationComputer hardwareValidation methods
A template sharing processing is performed between a first authentication server and a second authentication server. A client terminal generates two parameter differences, one of which is sent to the first authentication server, and the other to the second authentication server. The first authentication server transforms an already-registered template with the received parameter difference to create a temporary template and sends the temporary template to the second authentication server. The second authentication server transforms the received temporary template with the already-received parameter difference to create and register therein a further transformed template. A storage medium stores therein only a single master key for generating a parameter.
Owner:HITACHI LTD
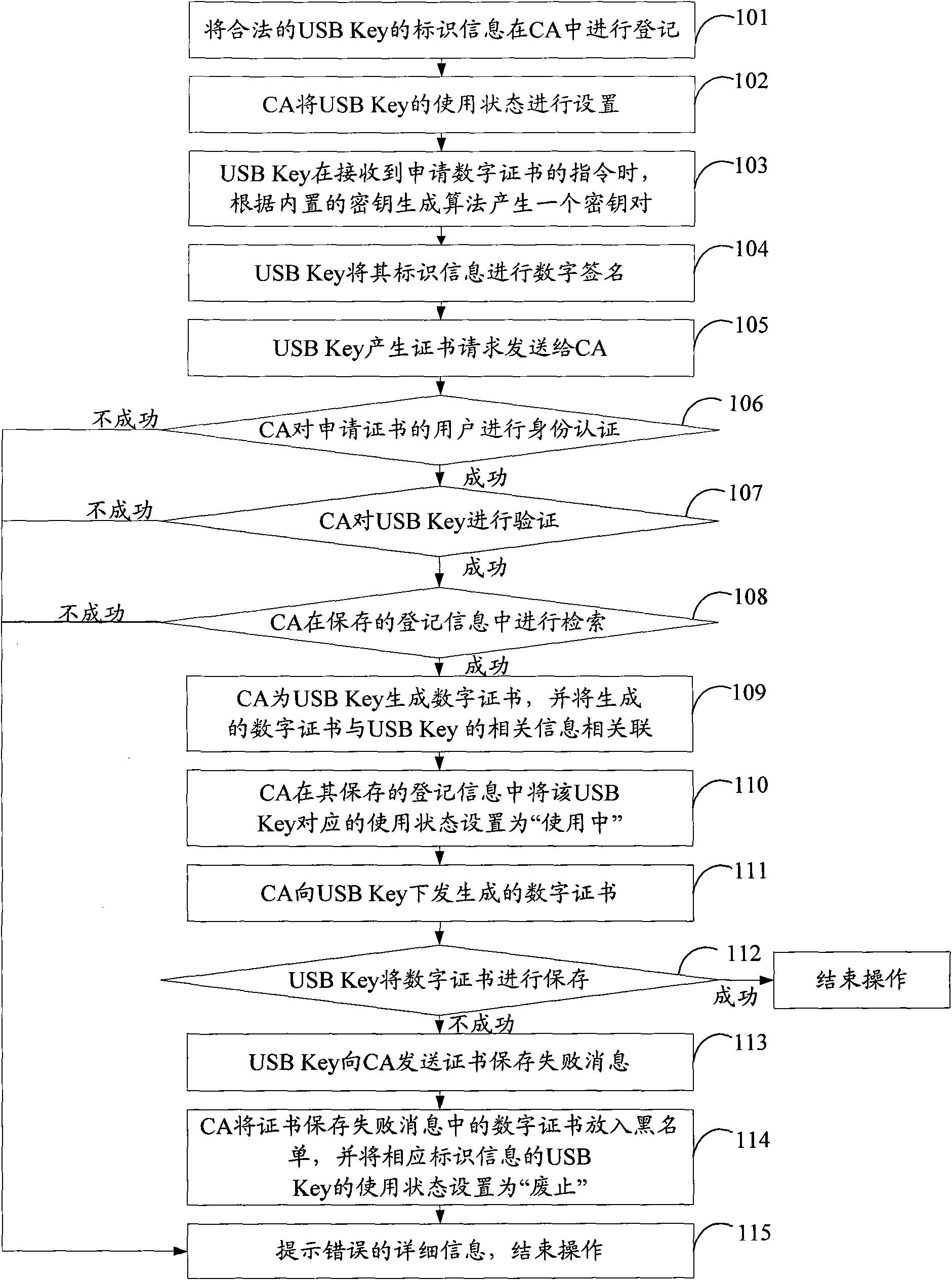
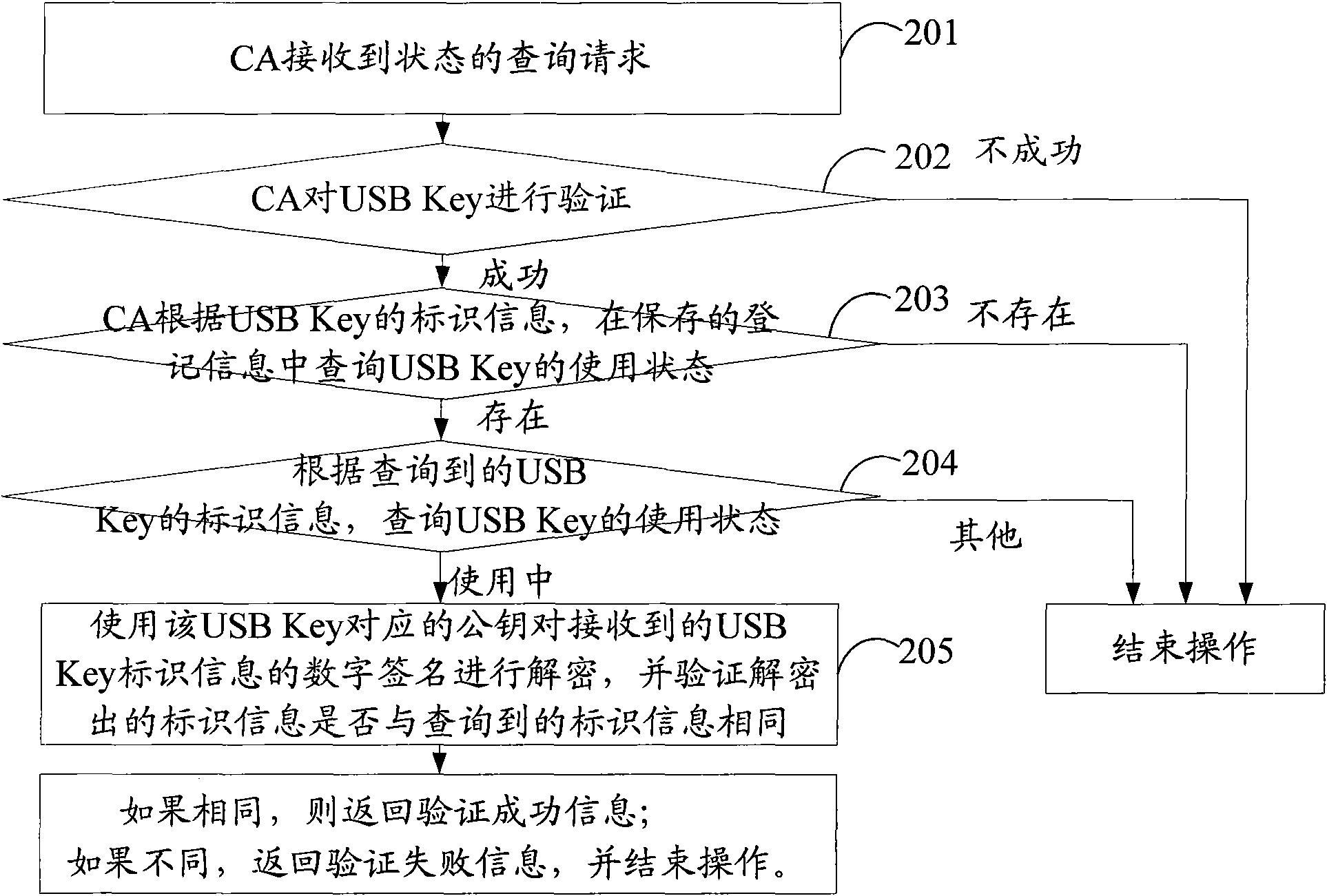
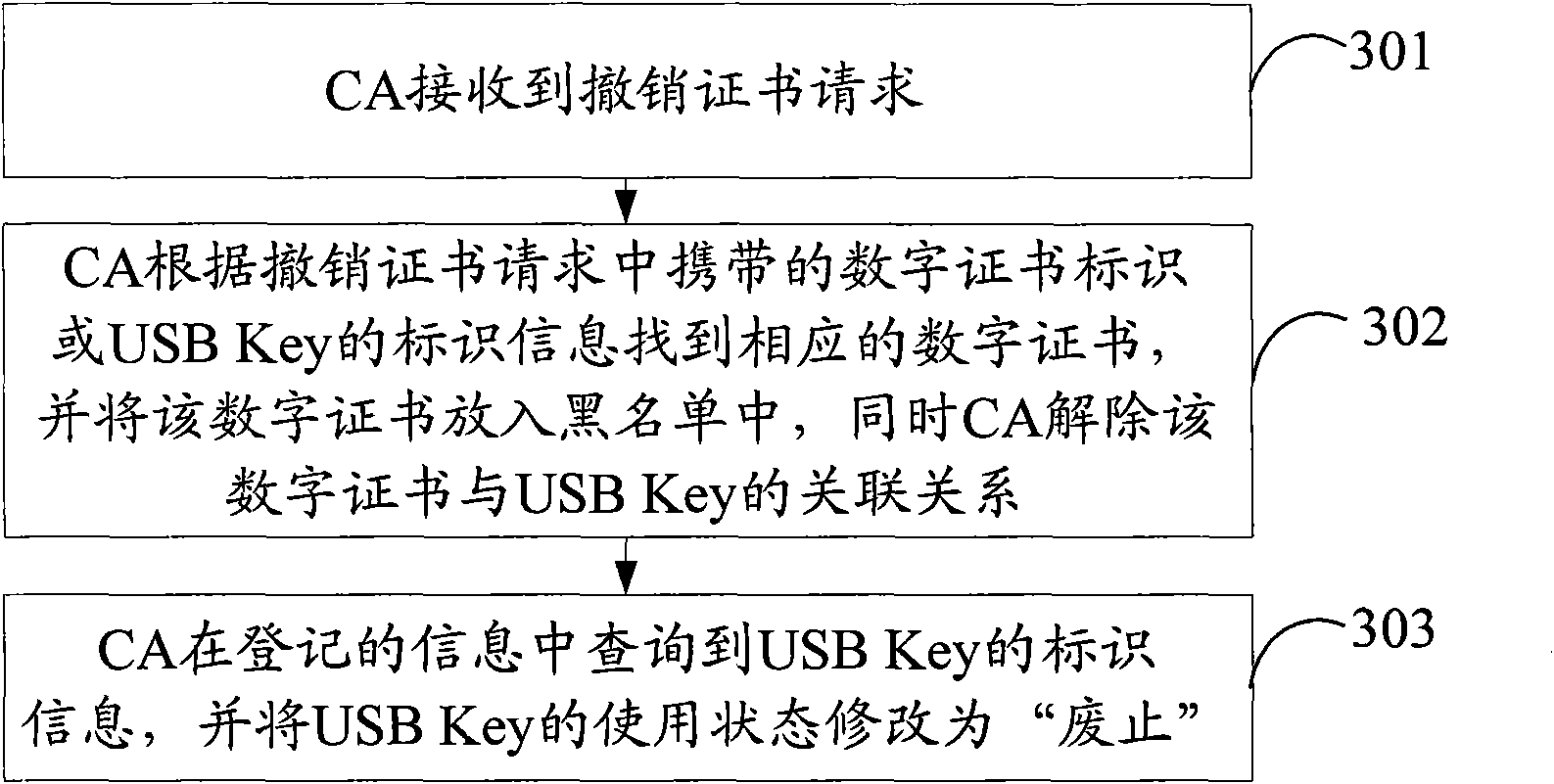
Method for issuing digital certificate
ActiveCN101645889AEasy to manageEnsure information securityUser identity/authority verificationDigital signatureInformation security
The invention discloses a method for issuing a digital certificate, belonging to the information security field. The method comprises the following steps: an authentication center receives a certificate request sent by a USB Key, and the certificate request carries identification information, a digital signature, and a public key of the USB Key; the USB Key is verified according to the identification information, the digital signature, and the public key of the USB Key; the public key of the USB Key is stored in the case of successful verification to generate a digital certificate for the USBKey, and the digital certificate is associated with the USB Key and then sent to the USB Key; and operation is ended in the case of unsuccessful verification. The method helps assure to issue the digital certificate to the legal USB Key.
Owner:FEITIAN TECHNOLOGIES
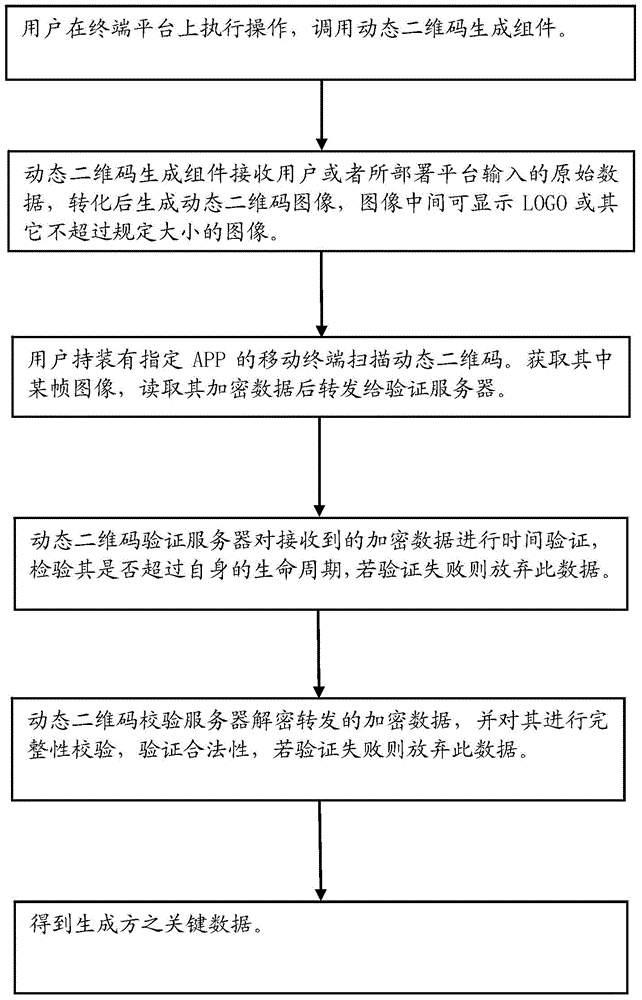
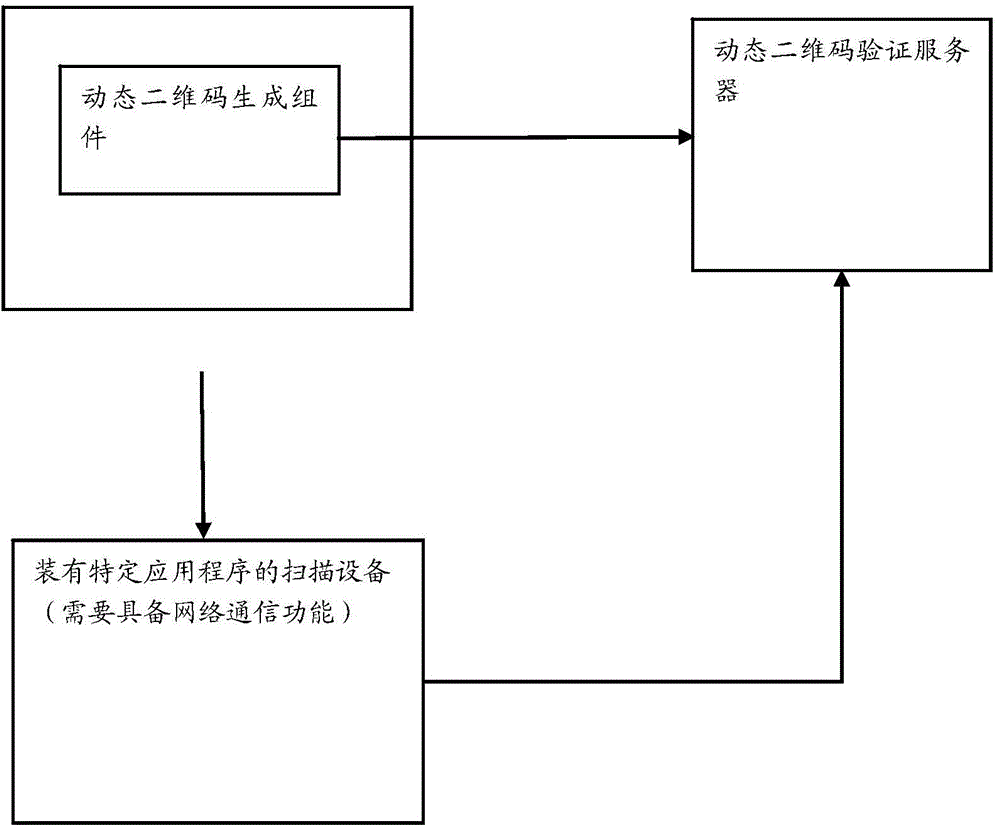
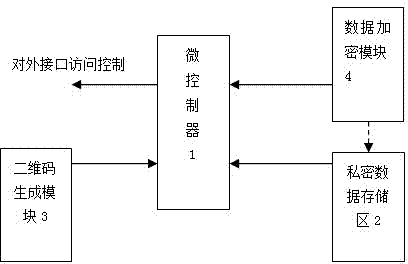
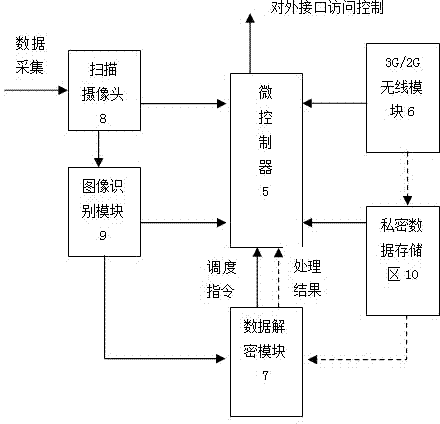
Method and system for generating and verifying dynamic two-dimensional code
InactiveCN104618334AData transmission securityEnsure information securityEncryption apparatus with shift registers/memoriesRecord carriers used with machinesData transmissionData content
The invention refers to the technical field of coding and decoding of a two-dimensional code, and particularly relates to a method for generating and verifying a dynamic two-dimensional code. The method for generating and verifying the dynamic two-dimensional code includes the following steps: generating the dynamic two-dimensional code according to original data input by a user and encrypting the data content of the dynamic two-dimensional code; applying a mobile terminal to scan the dynamic two-dimensional code and performing time verification, data decryption, inspection of data integrity and hardware information matching on one frame of obtained dynamic two-dimensional code data; if the whole inspections are passed, performing subsequent normal flows; otherwise, giving up the data. The dynamic two-dimensional code makes that every two-dimensional code image is dynamically encrypted and generated by using different secrete keys respectively within a period of time on the basis of an original QR Code; its content is encrypted through a security algorithm according with the national password standard and then mixed, so that the data transmission is safer.
Owner:ATMU CHINA TECH
Authentication method and system used for wireless payment
ActiveCN102034321AMeet the needs of distance controlAvoid economic lossKey distribution for secure communicationUser identity/authority verificationTelecommunicationsPayment transaction
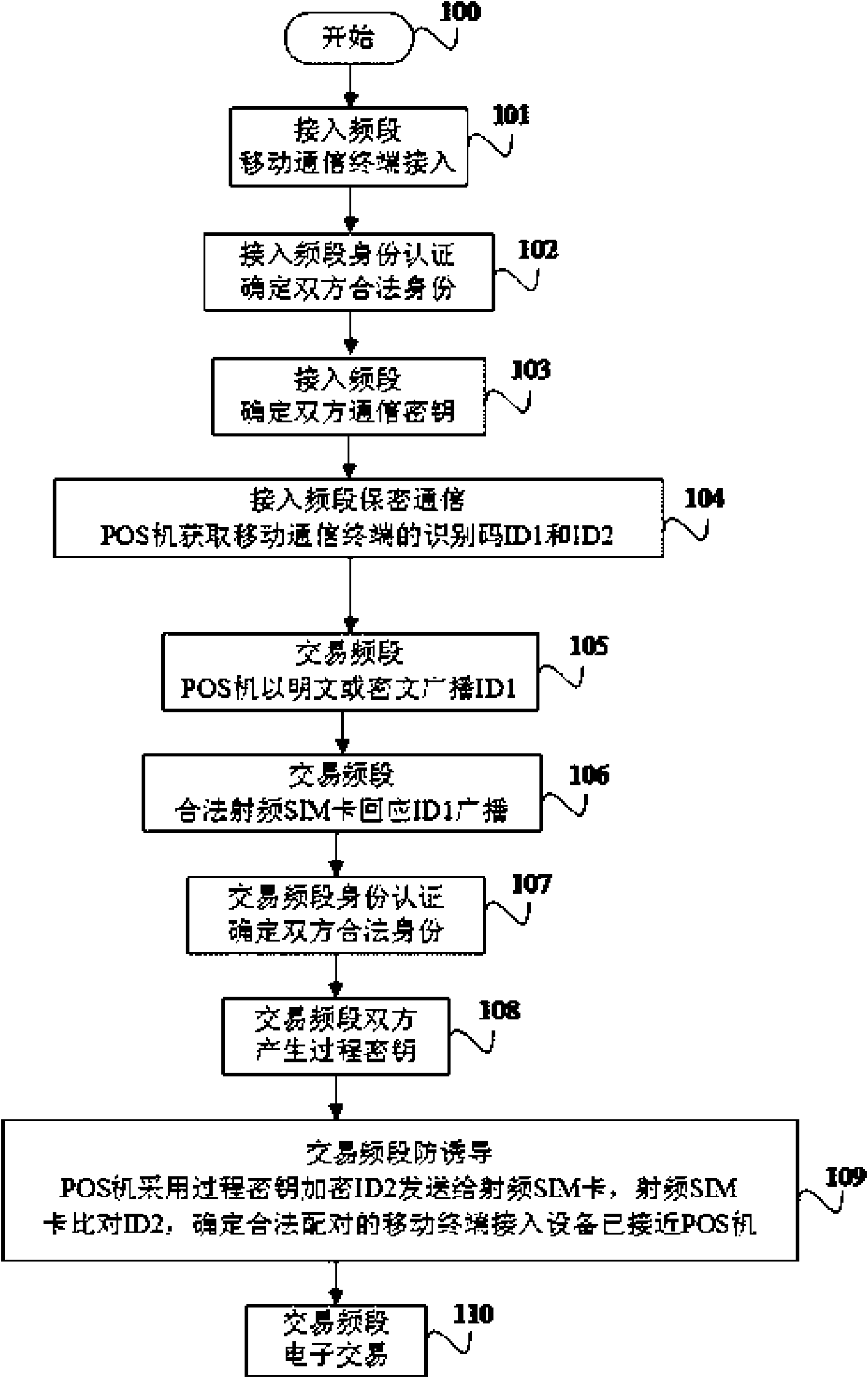
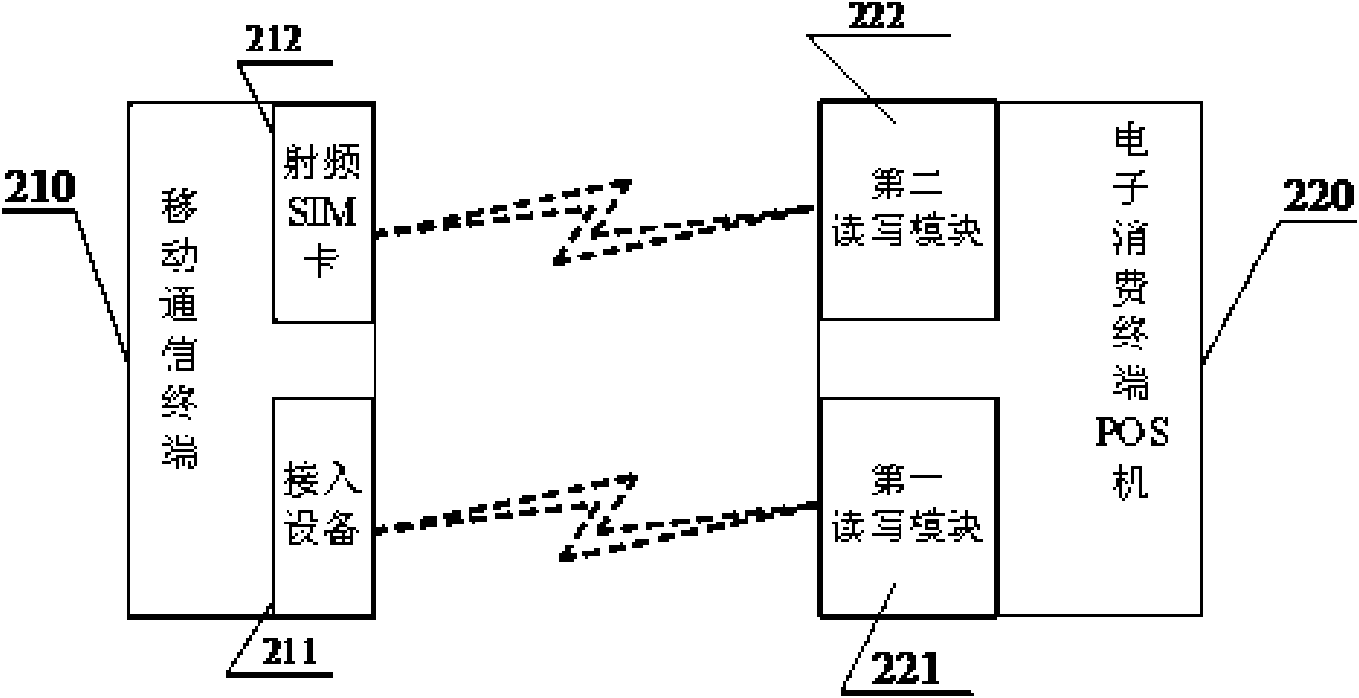
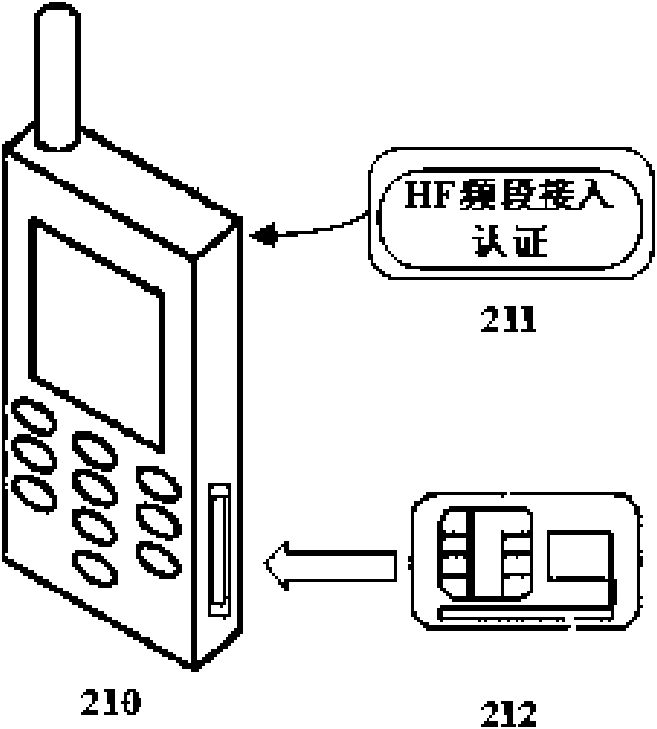
The invention relates to an authentication method for wireless payment. When the distance between a mobile communication terminal (payer) with a radio frequency SIM (subscriber identity module) card and a radio frequency card reading device (payee) of a POS (Point Of Sale) machine and the like meets the distance control requirement, the mobile communication terminal is allowed to be communicated with the POS machine, and identity authentication and safety authentication are first carried out during the communication; and, after the mobile communication terminal confirms that the POS machine is a legal payee, the mobile communication terminal is subjected to wireless payment transaction with the POS machine. The authentication method and system for the wireless payment in the invention accord with the requirement for the wireless payment distance control, ensure the information safety during the wireless payment, eliminate the potential safety hazard, and avoid causing economic loss bythe payer for the wireless payment.
Owner:NATIONZ TECH INC
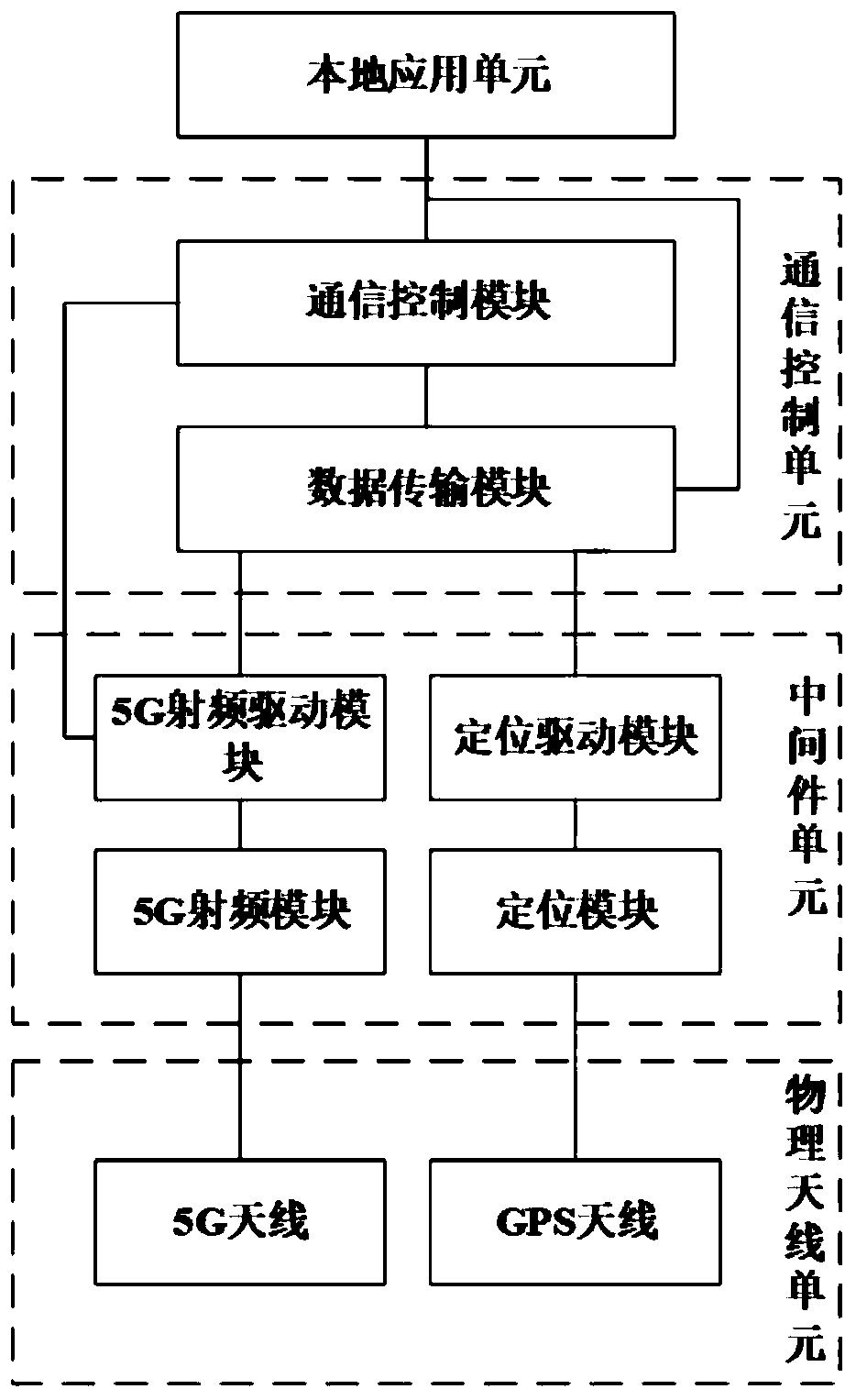
Vehicle-road communication test system and test method on 5G technology
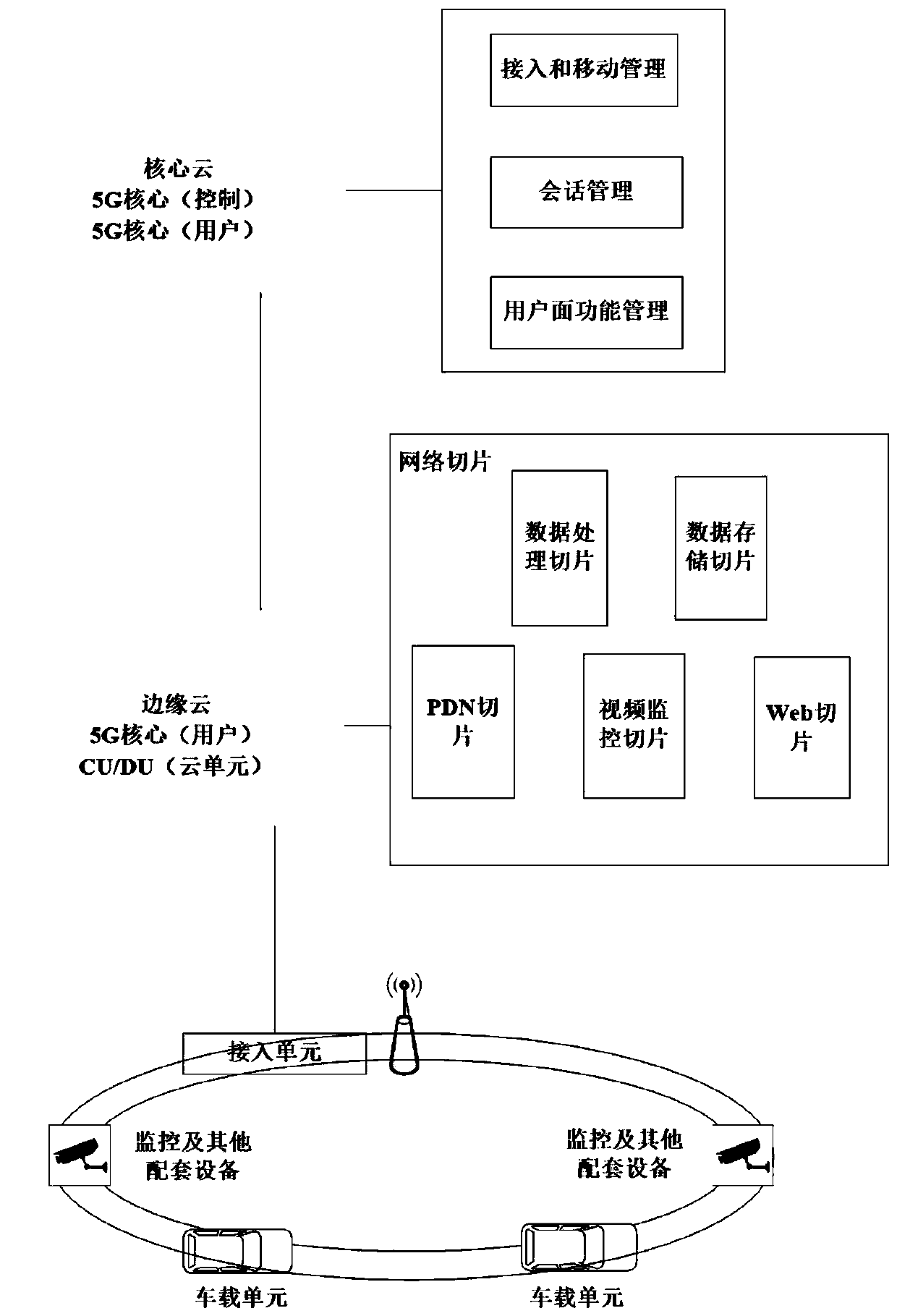
InactiveCN109981771AReduce in quantityRealize data exchangeParticular environment based servicesVehicle-to-vehicle communicationNetwork terminationTime delays
The invention discloses a vehicle-road communication test system based on the 5G technology. A network element function is realized by adopting a virtualization and software mode; the network transmission rate can be obviously improved; concurrent network messages of dense network terminals in the Internet of Vehicles environment are ensured. the requirement of complex and huge Internet of Vehicles application on ultra-low time delay is met; the system cloud server adopts a virtualization technology. the number of servers is reduced; in a security aspect, multiple network slices are divided, asecurity isolation and height self-control special logic network is provided; network security is greatly improved, the information security of the Internet of Vehicles application and the data privacy of the user are ensured; the edge cloud server sinks a part of services to a network edge; the Internet of Vehicles application service processing speed based on roadside equipment can be remarkably increased, lower transmission delay is provided, the test platform can be used for verifying the actual effectiveness of the 5G technology applied to the Internet of Vehicles application, and support is provided for 5G-based Internet of Vehicles equipment layout and network design in a real scene.
Owner:CHANGAN UNIV
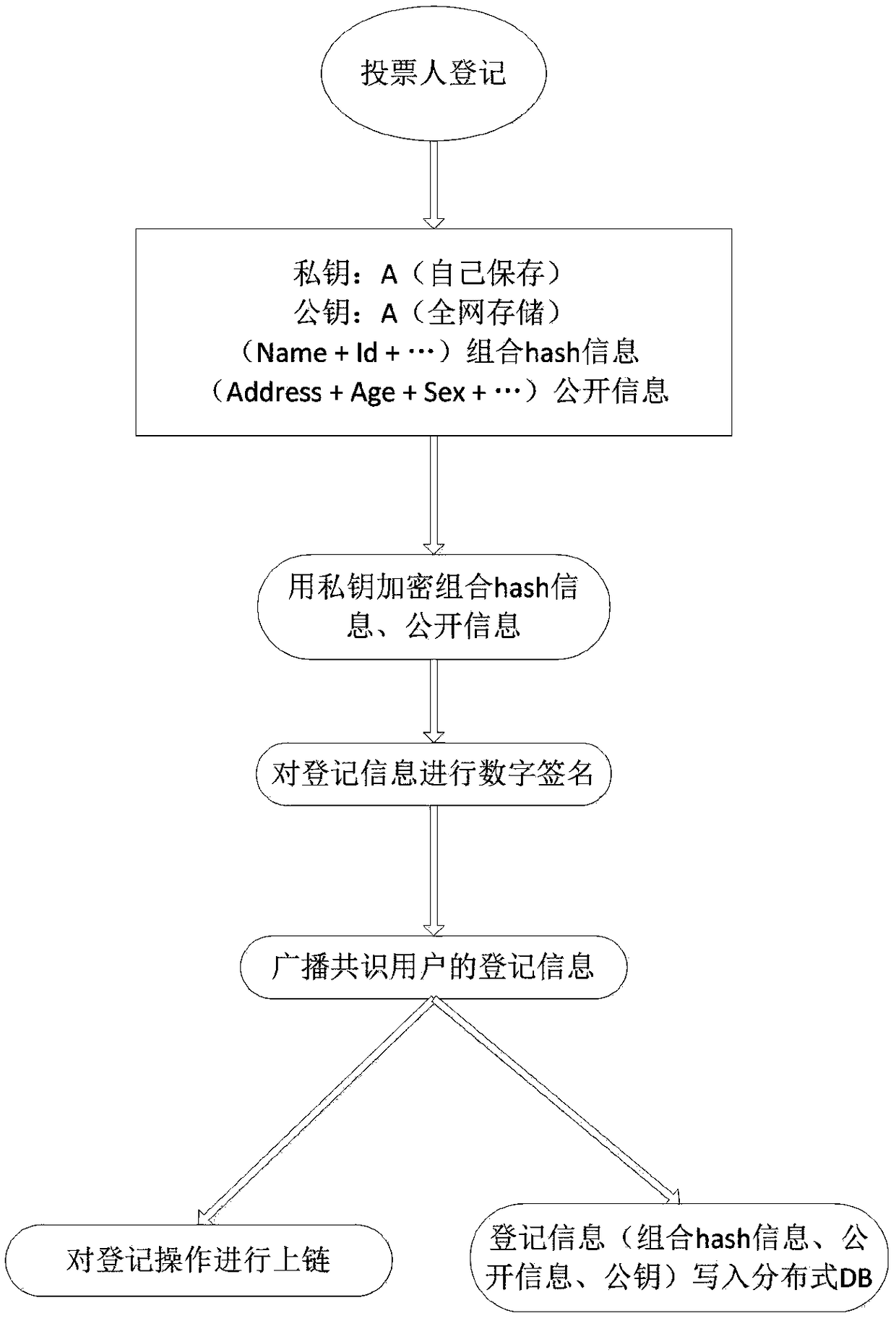
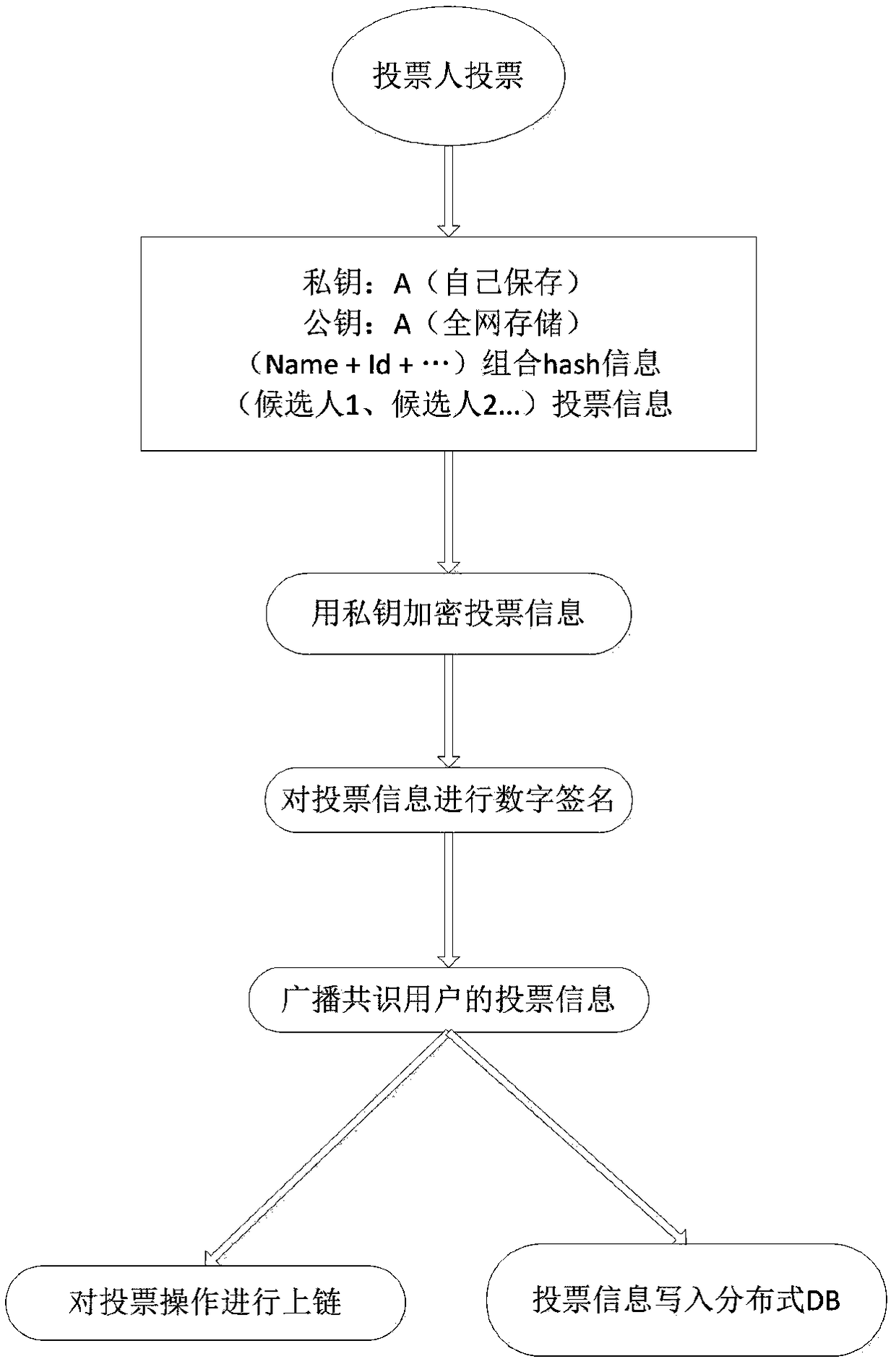
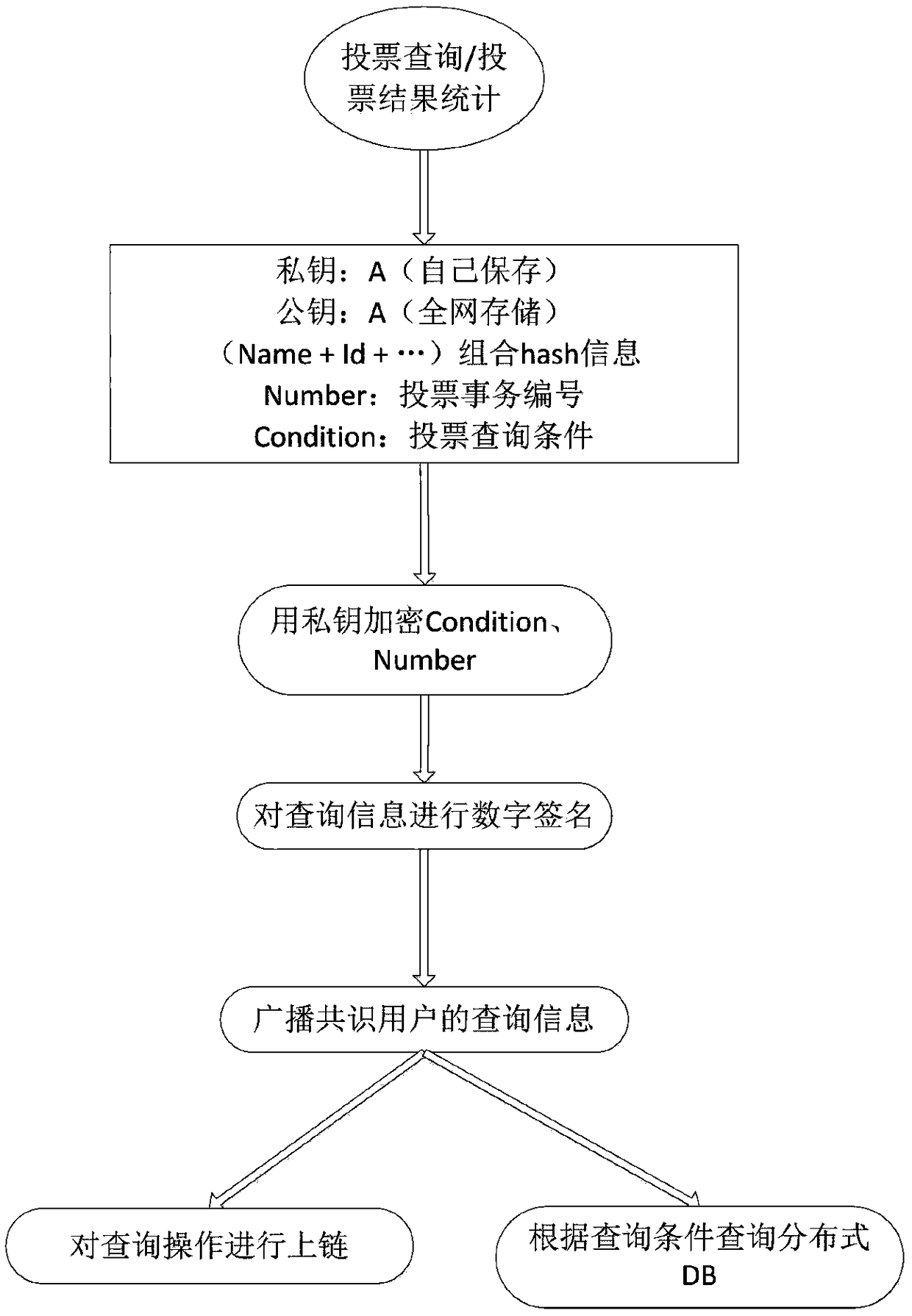
Method for anonymous voting and multi-condition vote counting based on block chain
ActiveCN109286497ANot tampered withEnsure information securityVoting apparatusEncryption apparatus with shift registers/memoriesDigital signatureThe Internet
The invention discloses a method for anonymous voting and multi-condition vote counting based on a block chain, and belongs to the technical field of Internet. The method comprises the steps of voterregistration, voting, voting query and result statistics. Public key encryption and hash are carried out on key and unique identity information of voters to generate unique secret identity informationof the voters, thereby ensuring the identity uniqueness of the voters and the information security, and preventing malicious repeated voting behaviors. The secret identity information of the voters is firstly encrypted by a voter public key and then subjected to hash, so that the information can only be checked by the voters, and anonymous voting is realized. The public information of the votersis encrypted and digitally signed, and the encrypted and signed public information is stored in the database of each network node of the block chain, thereby being capable of achieving multi-conditionvote counting through an intelligent contract in the case of ensuring the voting rights and information security of the voters.
Owner:贵阳信息技术研究院 +1
Method, related device and system for information viewing
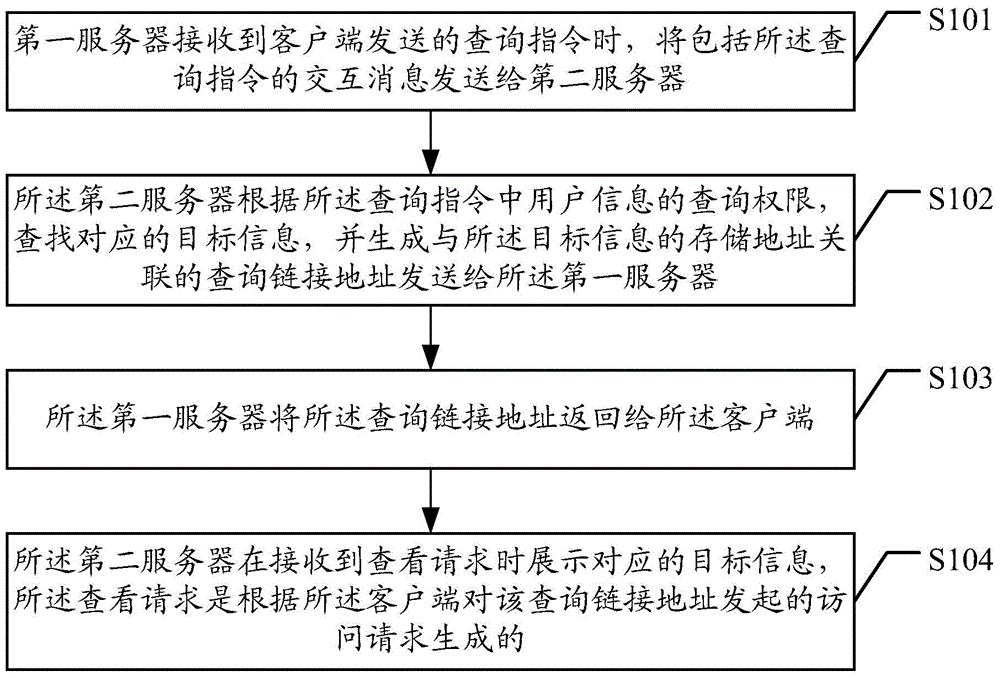
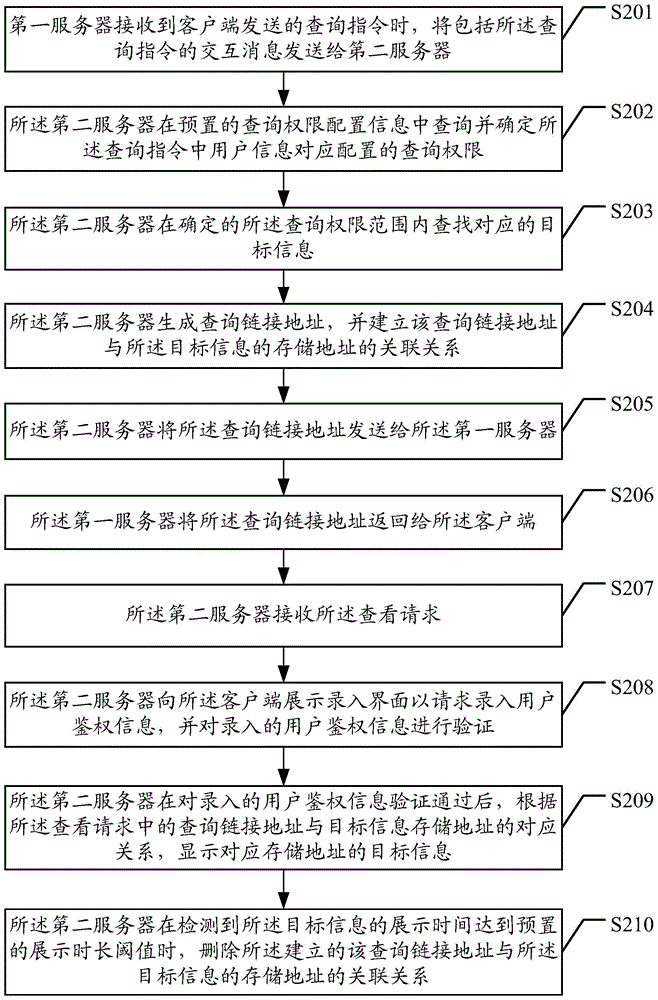
ActiveCN104660562AEfficient managementEnsure information securityServices signallingComputer security arrangementsObjective informationRelevant information
An information viewing method, relative device and system and a storage medium are disclosed by embodiments of the present invention, where the method includes: sending, by a first server, an interactive message comprising a searching instruction to a second server when receiving the searching instruction sent by a client; searching for, by the second server, corresponding target information according to a configured searching permission corresponding to the user information in the searching instruction, generating a searching link address associated with a storage address of the target information and sending the generated searching link address to the first server; returning, by the first server, the searching link address to the client; and presenting, by the second server, the corresponding target information when receiving a viewing request.. In embodiments of the present invention, relative information can be viewed legally, and the information can be managed effectively, which protect internal information of the business entity and personal private information well.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
Password authentication method and system
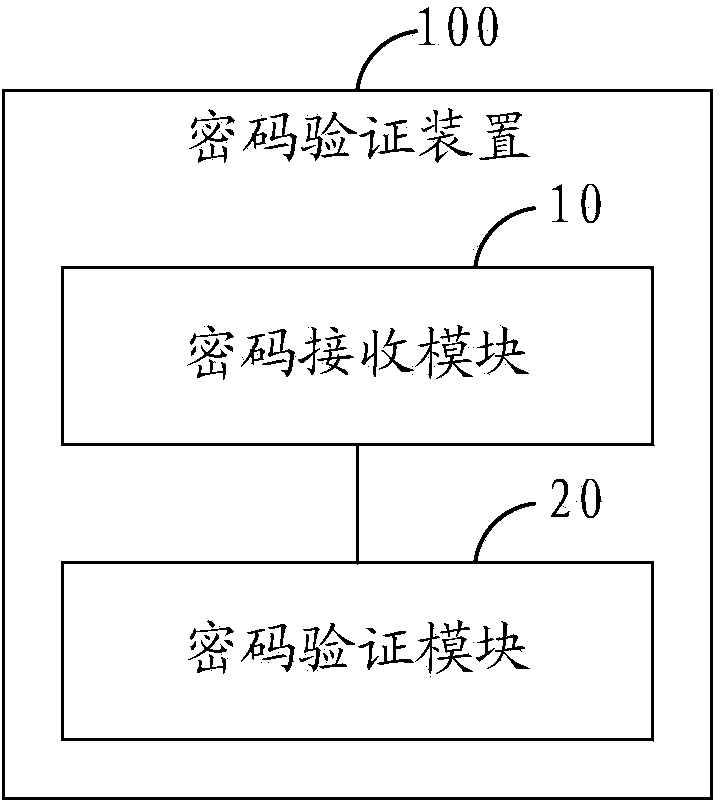
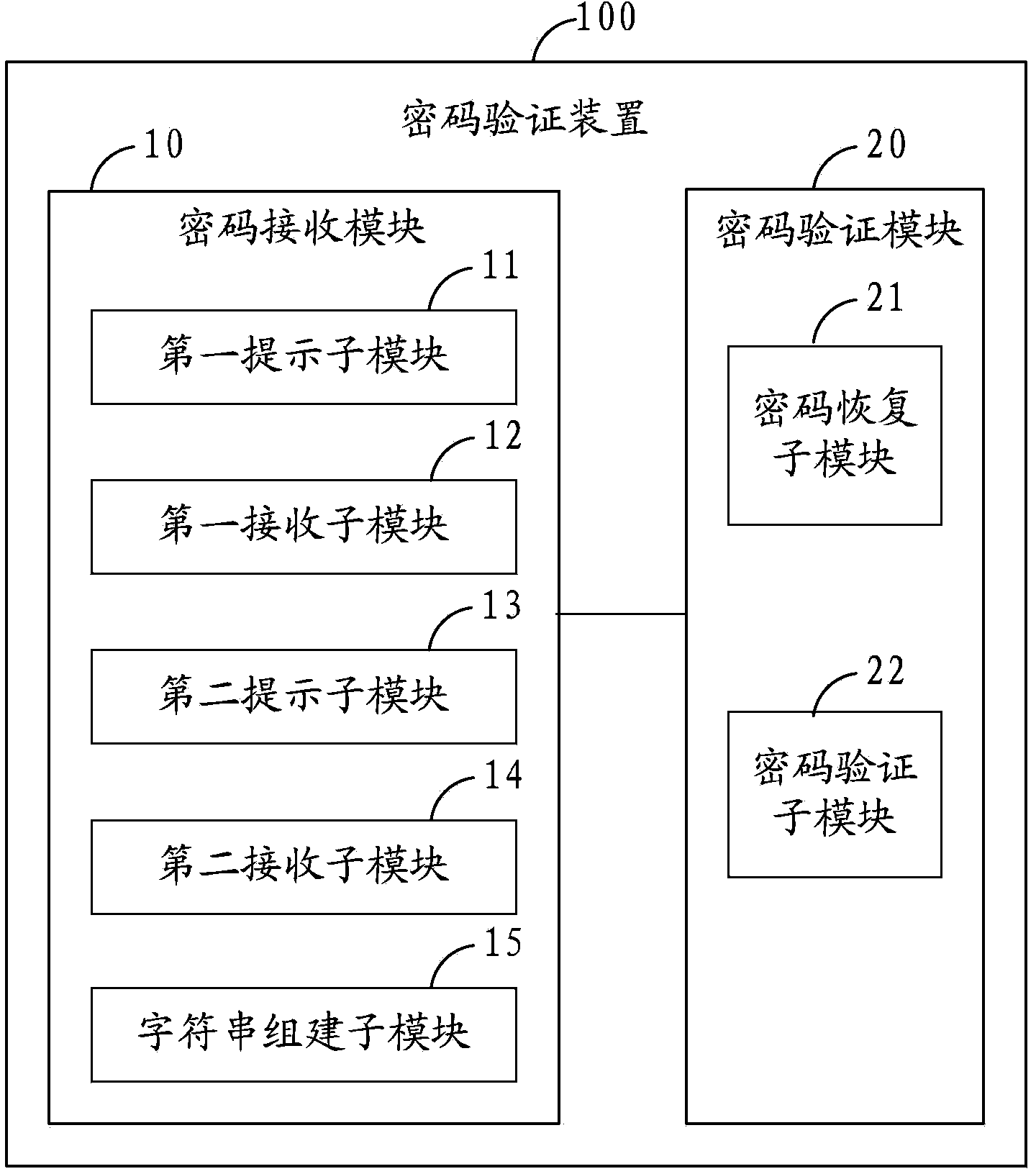
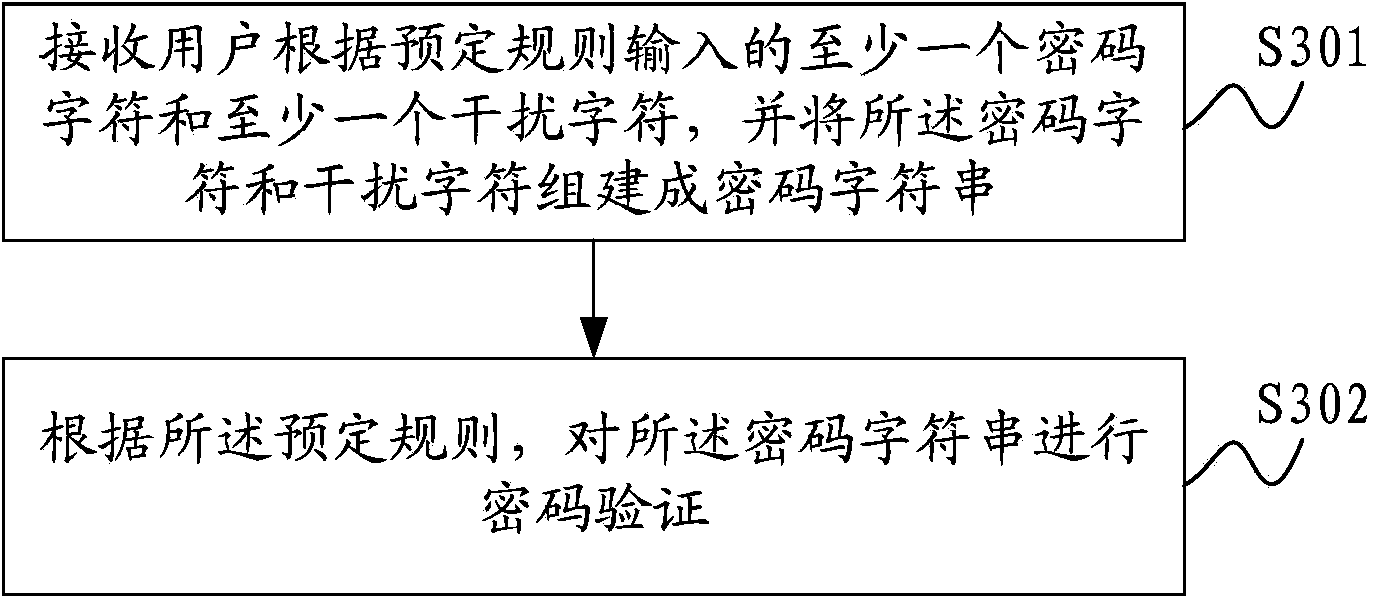
InactiveCN104143068AEnsure information securityGuarantee property securityDigital data protectionDigital data authenticationPasswordInformation security
The invention is applied to the technical field of communication and provides a password authentication method. The method comprises the following steps of receiving a password, namely receiving at least one password character and at least one interference character, which are input by a user according to a preset rule, and establishing a password character string by using the password character and the interference character; authenticating the password, namely performing password authentication on the password character string according to the preset rule. Correspondingly, the invention also provides a password authentication device. Therefore, the invalid interference character is added for interference in the process of inputting and authenticating the password, the password of the user can be effectively prevented from being stolen by a rogue program, and the information safety and the property safety of the user are fully guaranteed.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
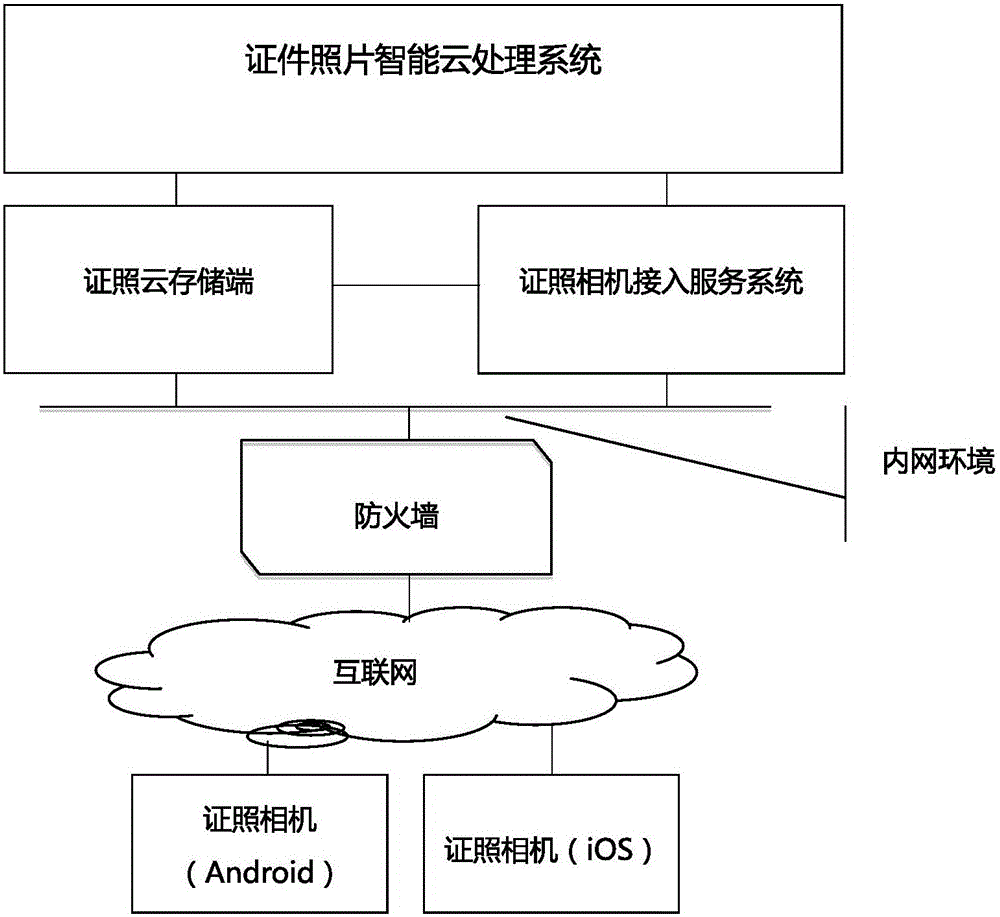
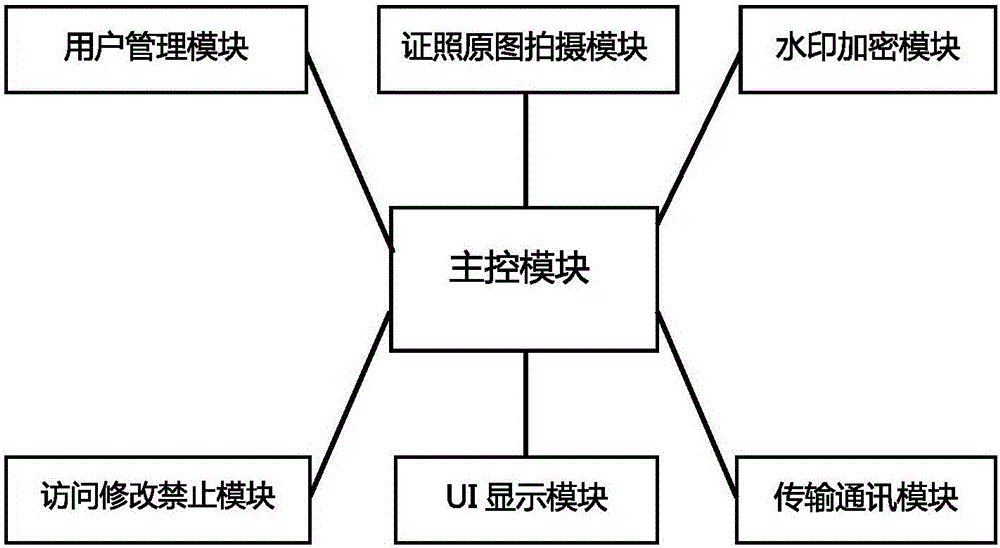
Tamper-proof license camera system and method
ActiveCN105141842APrevent tamperingEnsure information securityTelevision system detailsColor television detailsTamper resistanceAccess modification
The invention discloses a tamper-proof license camera system and method. The tamper-proof license camera system comprises a license camera, a license camera access server and a license cloud storage, wherein the license camera comprises a license original picture shooting module, an access modification prohibition module, a watermark encryption module and a transmission communication module. The tamper-proof license picture shooting method comprises the following steps: shooting license original pictures by the license camera; in the process of shooting and generating the license original pictures, prohibiting users or other software to access the original picture data, and prohibiting users or other software to modify the license original picture data; writing the shot license original pictures into a fragile watermark and encrypting the shot license original pictures; performing compression and secondary encryption on the pictures after being performed watermark encryption, and transmitting the pictures to an independent storage space of a license cloud storage end for conservation. The tamper-proof license camera system and method provided by the invention can guarantee the authenticity and timeliness of pictures in the processes from imaging to generating standard license pictures, submitting and transmitting, prevent pictures from being tampered, and can very conveniently and easily acquire the license pictures.
Owner:GUANGZHOU XINGFU NETWORK TECH
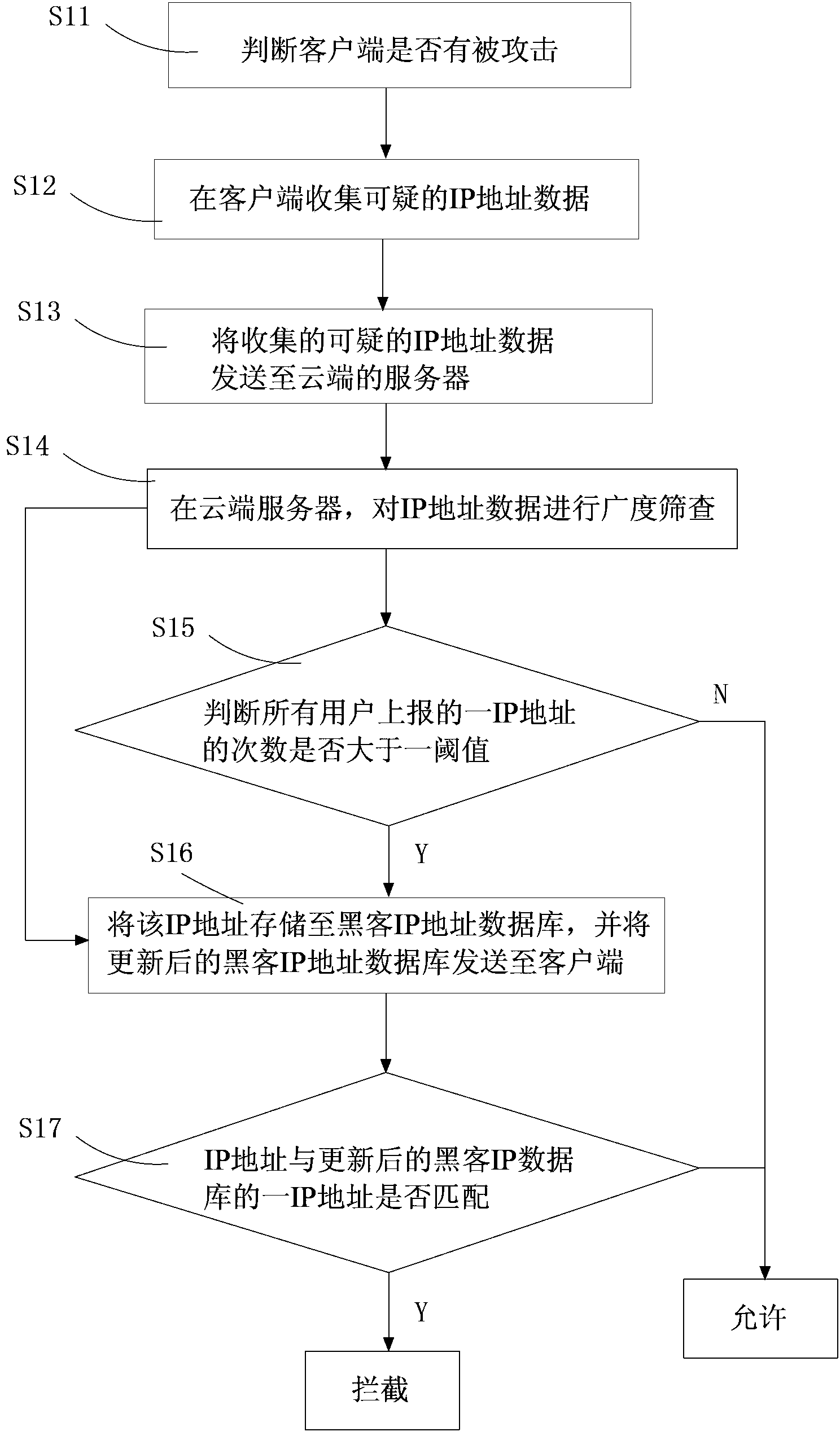
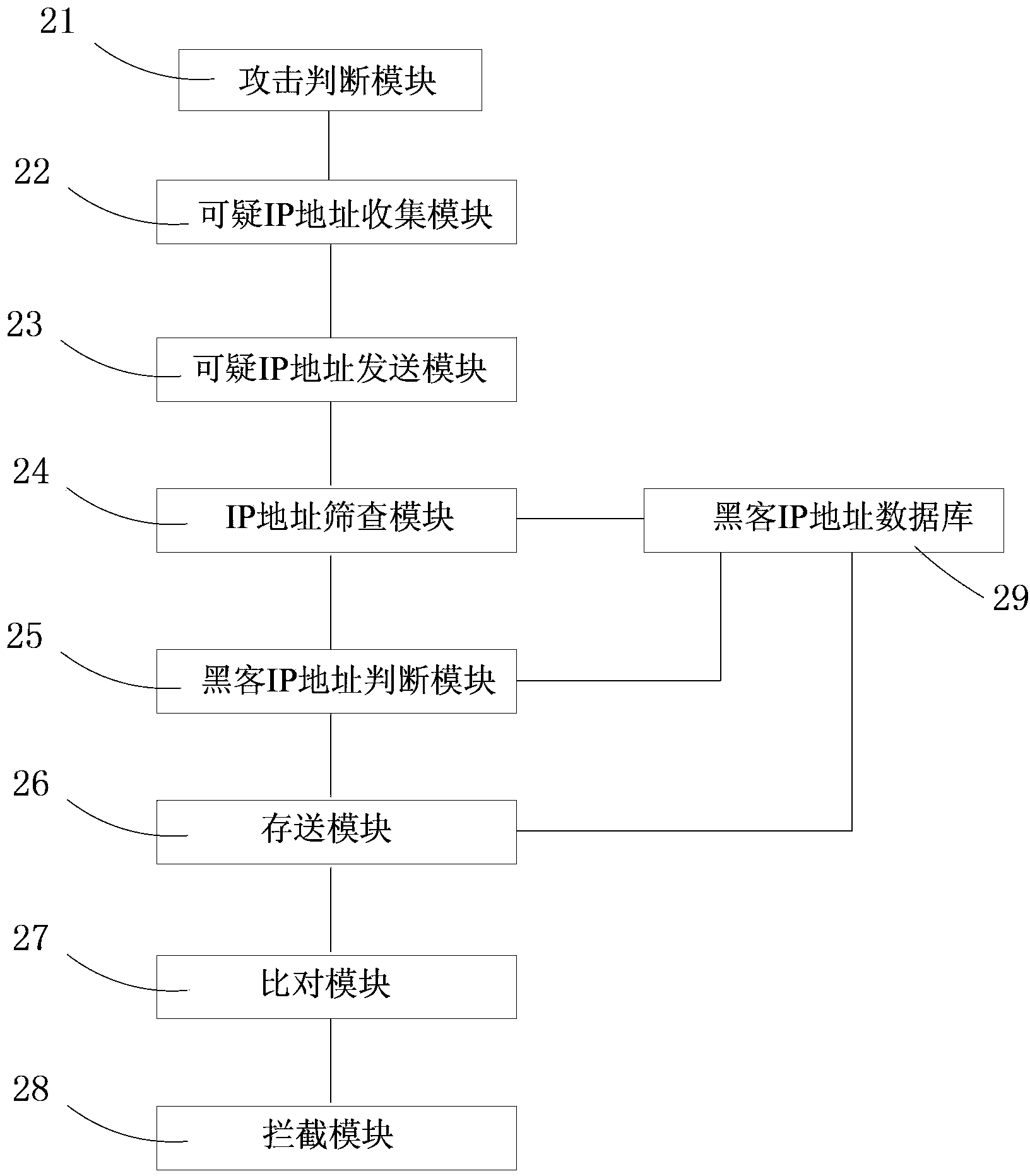
Method and device for intercepting network attack based on cloud
A method for intercepting network attack based on cloud comprises the following steps: step 1, whether a client is attacked is judged; step 2, suspicious IP address data is collected at the client; step 3, the collected suspicious IP address data is sent to a cloud server; step 4, breadth screening is carried out on IP address data at the cloud server; step 5, whether the number of times of reporting of an IP address by all users is greater than a threshold value is judged, the IP address is judged as a hacker IP address if the number of times of reporting of the IP address by all users is greater than the threshold value, or downloading is allowed; step 6, the IP address is stored in a hacker IP address database, and the updated hacker IP address database is sent to the client; and step 7, a suspicious IP address is compared with the updated hacker IP address database at the client, the IP address is intercepted if the IP address is matched with an IP address in the hacker IP address database, or downloading is allowed. Hacker IP addresses are identified, checked and judged at the cloud, and attack of hackers is effectively prevented.
Owner:ZHUHAI BAOQU TECH CO LTD
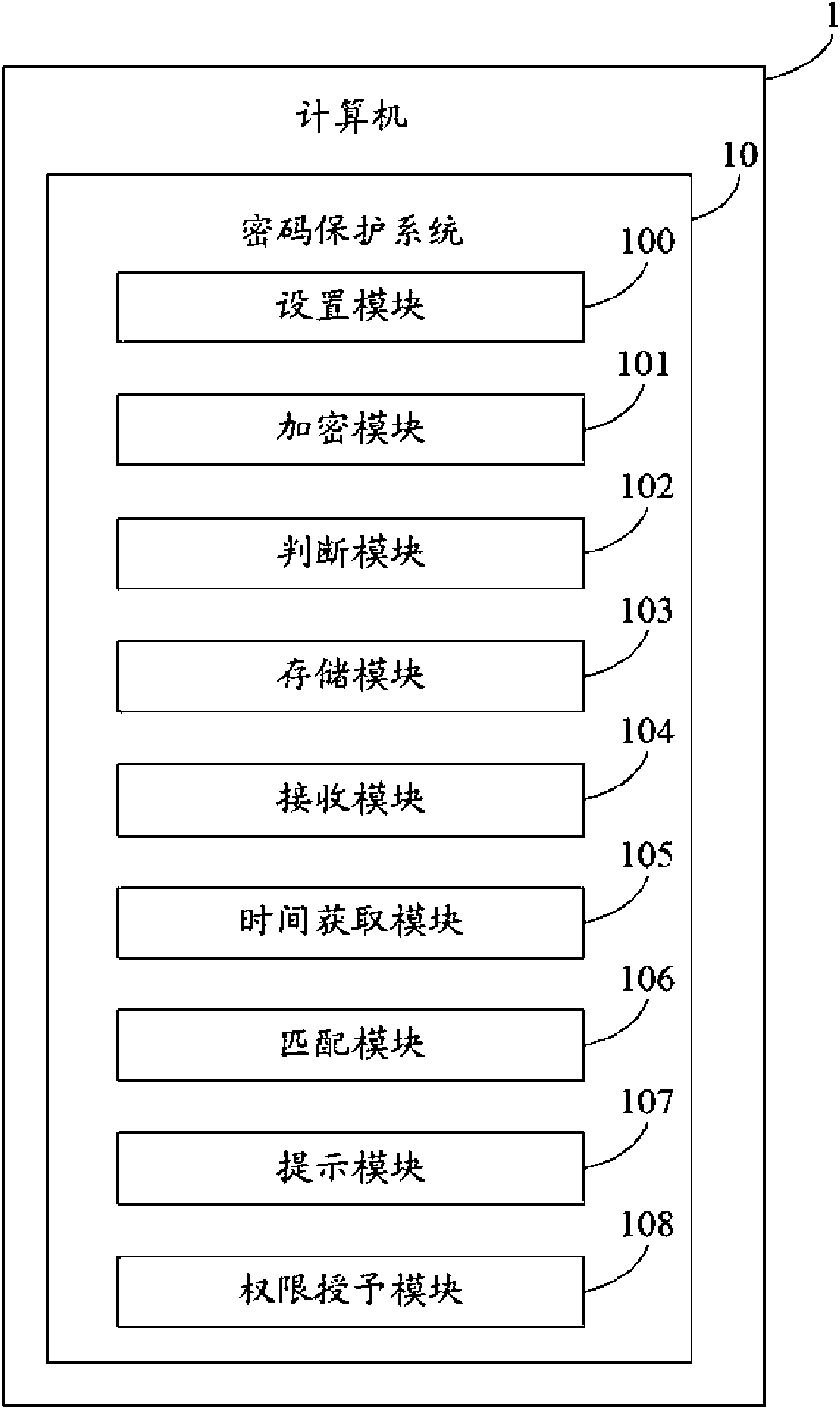
Password-protecting system and method
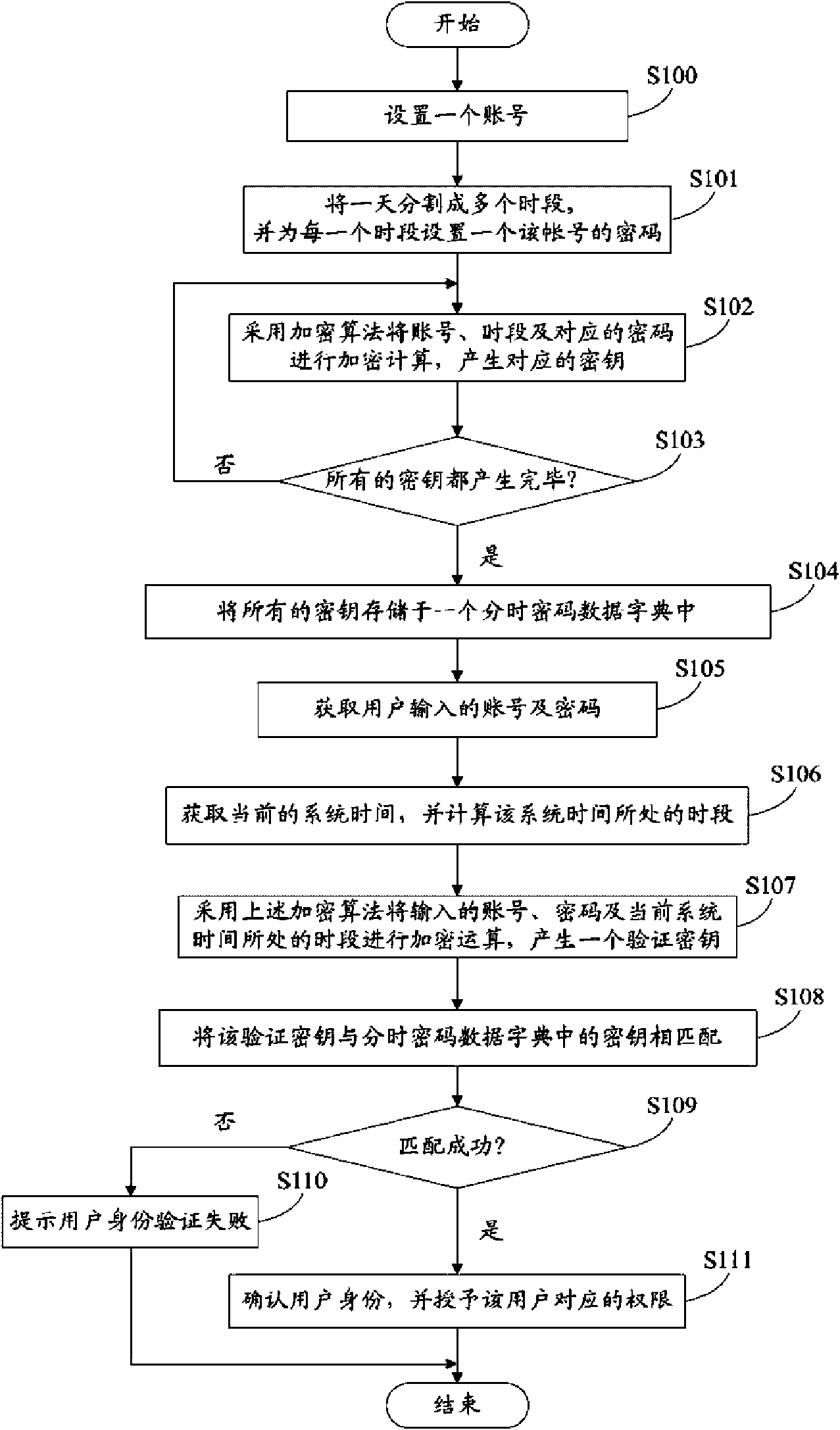
InactiveCN101616003AImplement passwordImplementation timeUser identity/authority verificationPasswordSystem time
The invention provides a password-protecting system comprising a setting module, an encrypting module, a storing module, a receiving module, a time-obtaining module, a matching module, a prompting module and a right-granting module. The setting module is used for setting an account and a plurality of passwords thereof, wherein the passwords correspond to a plurality of periods of time; the encrypting module is used for encrypting and calculating the account, the periods of time and the corresponding passwords to generate keys; the storing module is used for storing the keys to a time-sharing password data dictionary; the receiving module is used for receiving the input account and the passwords; the time-obtaining module is used for obtaining system time and calculating a period of time corresponding to the system time; the matching module is used for encrypting and calculating the input account, the passwords and the calculated periods of time to generate a verification key and matching the verification key with the keys in the data dictionary; the prompting module is used for prompting the verification failure of a user identity in case of unsuccessful match; and the right-granting module is used for confirming the user identity in case of successful match. The invention also provides a password-protecting method, can more effectively protect the account and the passwords of a user and ensures the information security of the user.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
Multi-user multi-parameter wireless detection, diagnosis, service and monitoring system
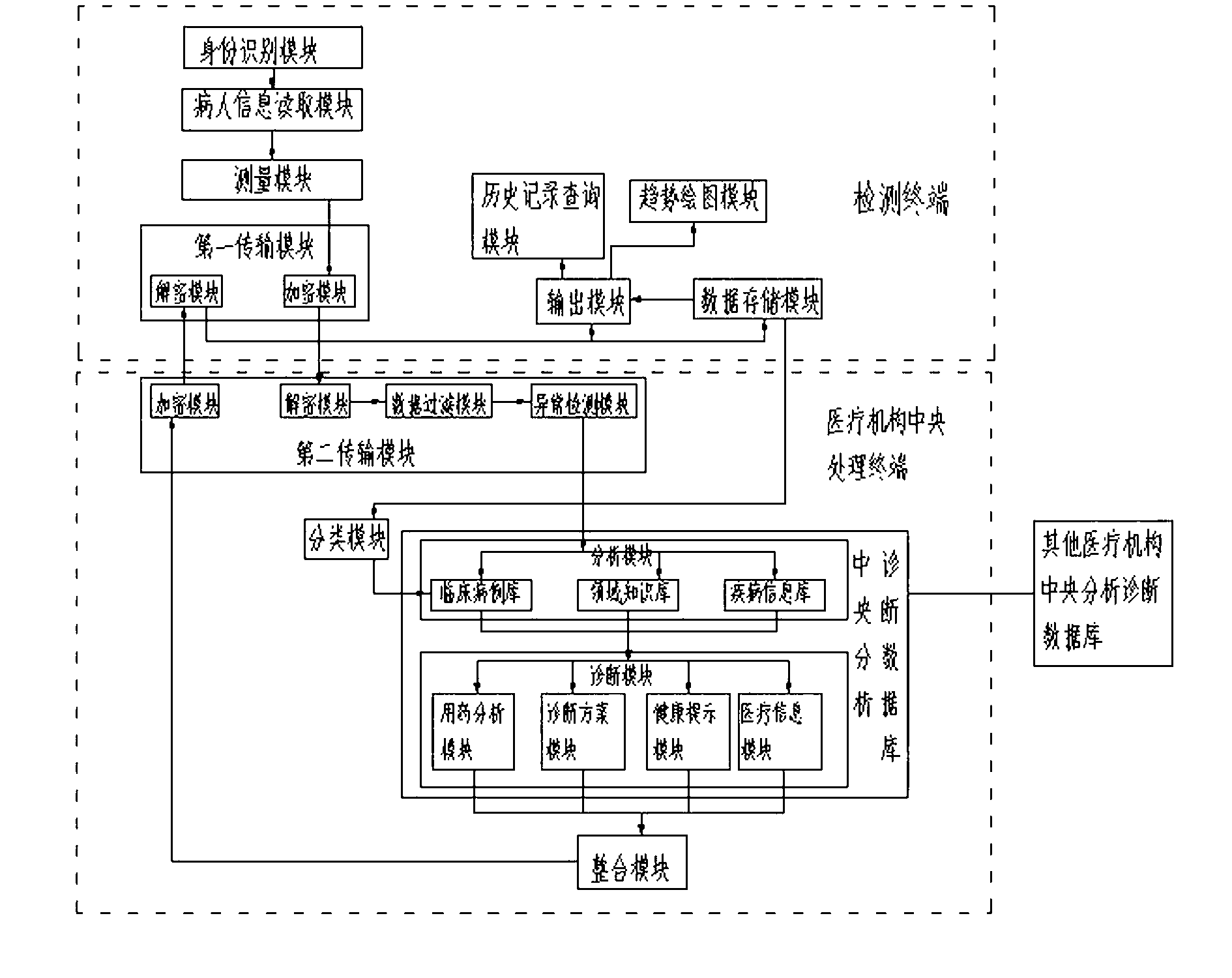
InactiveCN103268422AConvenient to enjoyFlexible timeSpecial data processing applicationsDiagnostic dataNetwork connection
The invention relates to a multi-user multi-parameter wireless detection, diagnosis, service and monitoring system which comprises a detection terminal and a medical establishment central processing terminal connected to the detection terminal through a network, wherein the detection terminal comprises a patient information reading module, a measuring module and a first transmission module. The first transmission module transmits patient physiological data measured by the measurement module to the medical establishment central processing terminal through the network. The medical establishment central processing terminal comprises a central analysis and diagnosis database and a second transmission module, and the second transmission module transmits data between the first transmission module and the central analysis and diagnosis database. The detection terminal further comprises an output module which is at least used for outputting inspection reports. According to the multi-user multi-parameter wireless detection, diagnosis, service and monitoring system, data transmission between the detection terminal and the medical establishment central processing terminal is utilized to achieve remote medical service, so people can more conveniently enjoy the medical service, and time and places for the medical service are more flexible.
Owner:MAYHAP IND SUZHOU
Invoice true check system based on cloud computing and encrypted two-dimensional codes
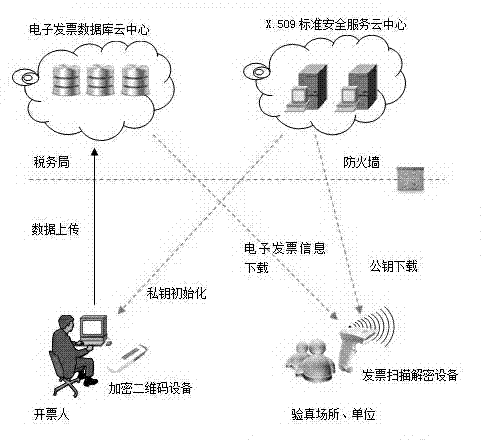
ActiveCN102930634AMeet the needs of invoice verificationEnsure information securityPaper-money testing devicesCharacter and pattern recognitionComputer hardwareInvoice
The invention discloses an invoice true check system based on cloud computing and encrypted two-dimensional codes and belongs to a tax invoice true check system. The invoice true check system comprises a tax office cloud computing platform, an encrypted two-dimensional code device and an invoice scanning decrypting device. The tax office cloud computing platform is used for managing the encrypted two-dimensional code device and the invoice scanning decrypting device. The encrypted two-dimensional code device is used for printing the encrypted two-dimensional codes on physical invoices when invoicing invoices for drawers. The invoice scanning decrypting device is used for scanning, decrypting and comparing the invoices needing true check and outputting processing results according to grades to serve as true check basis. Compared with the prior art, the invoice true check system based on cloud computing and the encrypted two-dimensional codes can solve the problems of trust issue and data safety of the existing invoice true check results, and restrains invoice counterfeiting and false invoice using to a certain extent.
Owner:INSPUR SOFTWARE TECH CO LTD
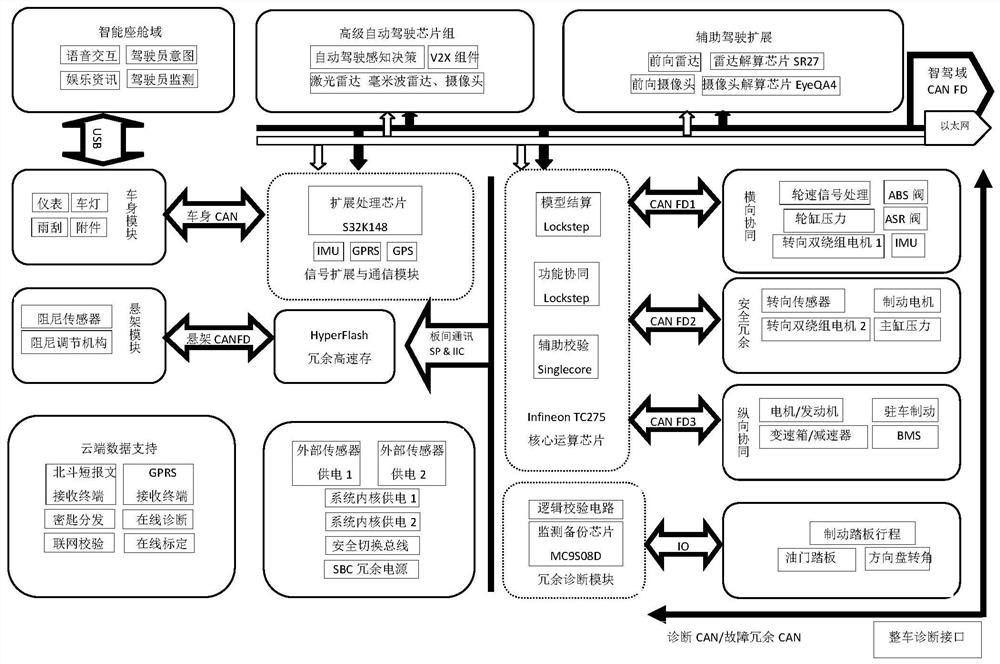
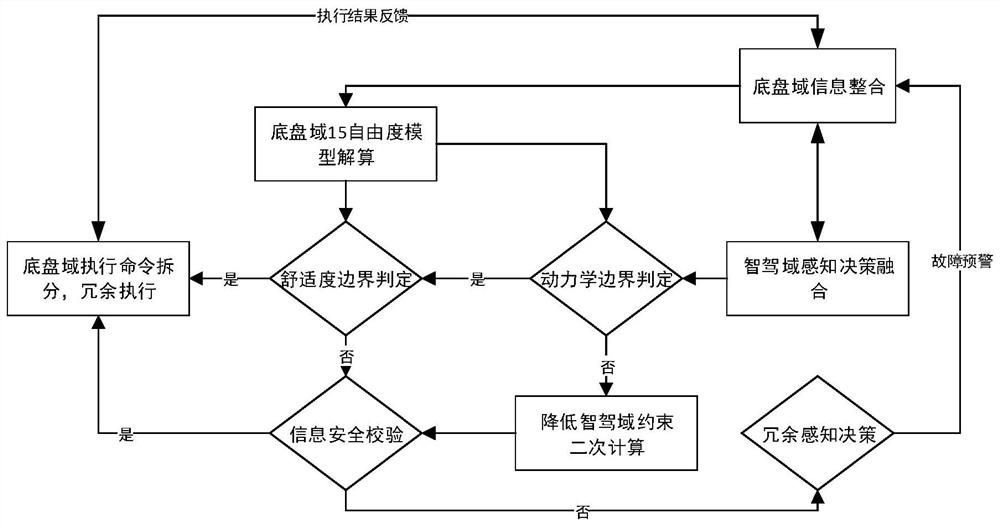
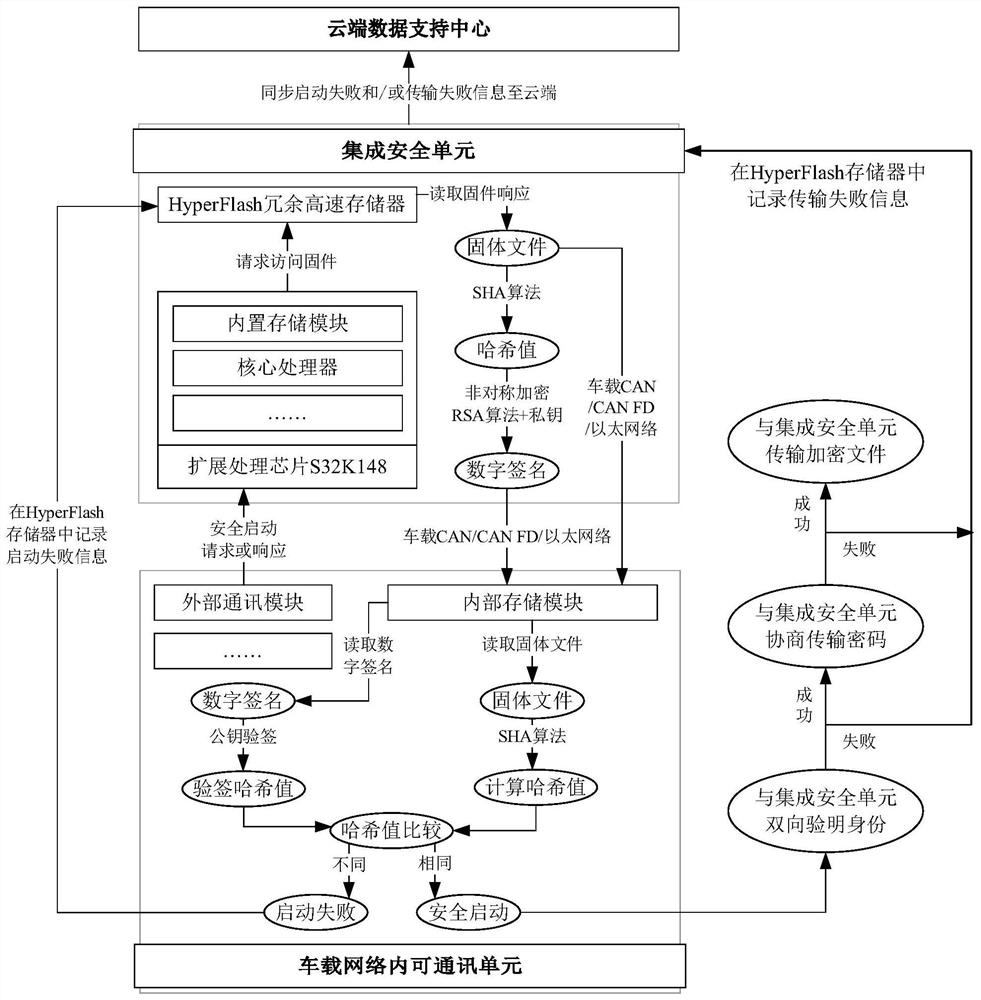
Intelligent automobile information flow redundancy safety control system based on chassis domain controller
ActiveCN112849055ARealize hierarchical managementRealize the signal verification mechanismAnti-theft devicesElectric/fluid circuitControl systemControl engineering
The invention provides an intelligent automobile information flow safety redundancy control system based on a chassis domain controller. The chassis domain controller realizes interaction with external information flow through a redundancy signal channel, and the redundancy signal channel comprises a transverse cooperative control unit, a longitudinal cooperative control unit, a safety redundancy unit and diagnosis / fault redundancy, wherein the transverse cooperative control unit, the longitudinal cooperative control unit and the safety redundancy unit are directly linked to a main control chip of a core operation unit. According to the system, information flow on a chassis is re-integrated based on the concept of chassis dynamics domain control, meanwhile, a redundant interaction interface of chassis information and intelligent driving related information is re-defined for a future intelligent automobile framework, and through a high-reliability domain controller and a redundant safety information flow channel, and by combining encryption and verification technologies, redundant control of each execution mechanism of the chassis is realized, hierarchical management and signal verification of an automatic driving function module, redundant control of a whole vehicle signal and whole vehicle information flow verification work are realized, and the information safety of the whole vehicle is ensured.
Owner:TSINGHUA UNIV
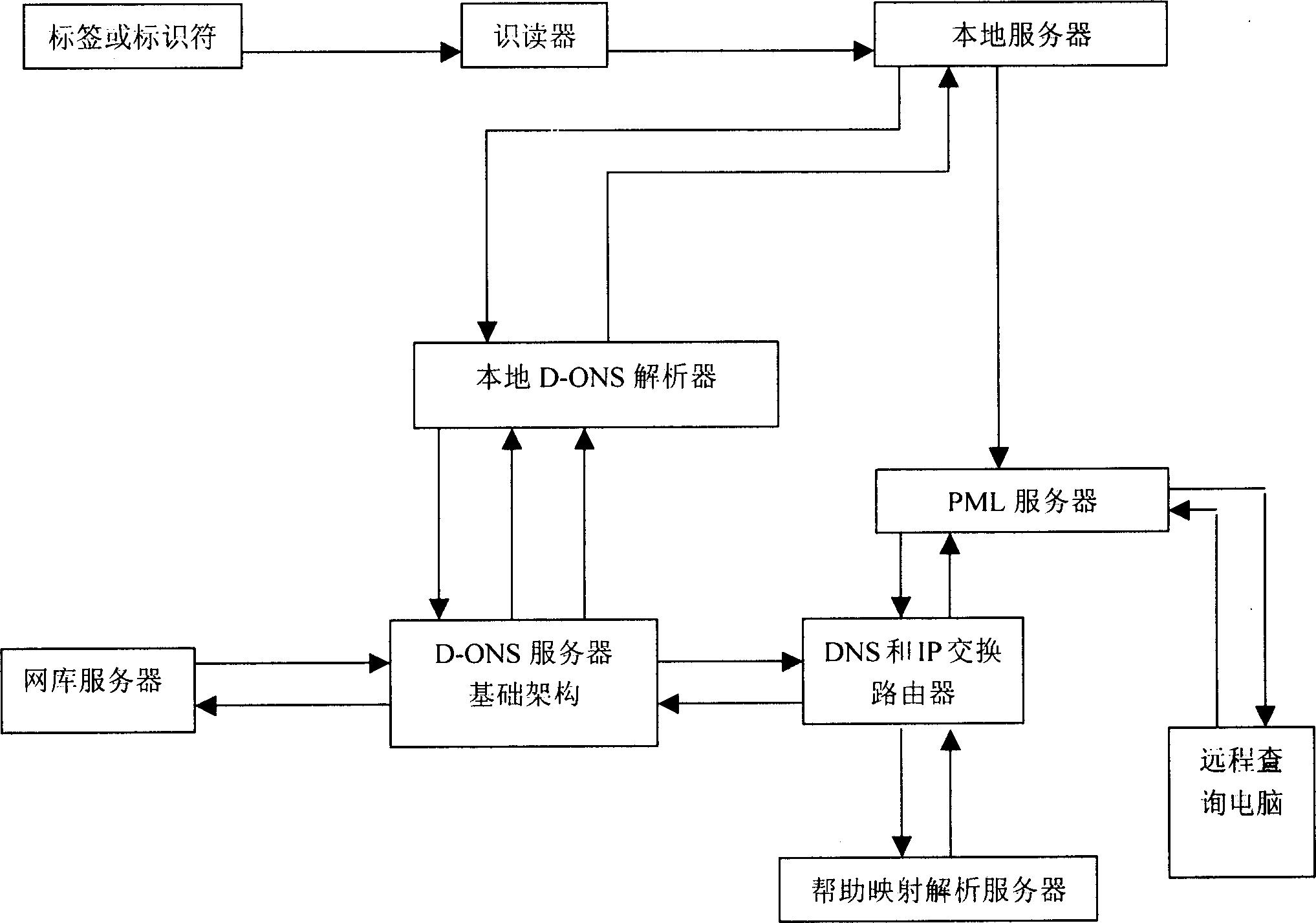
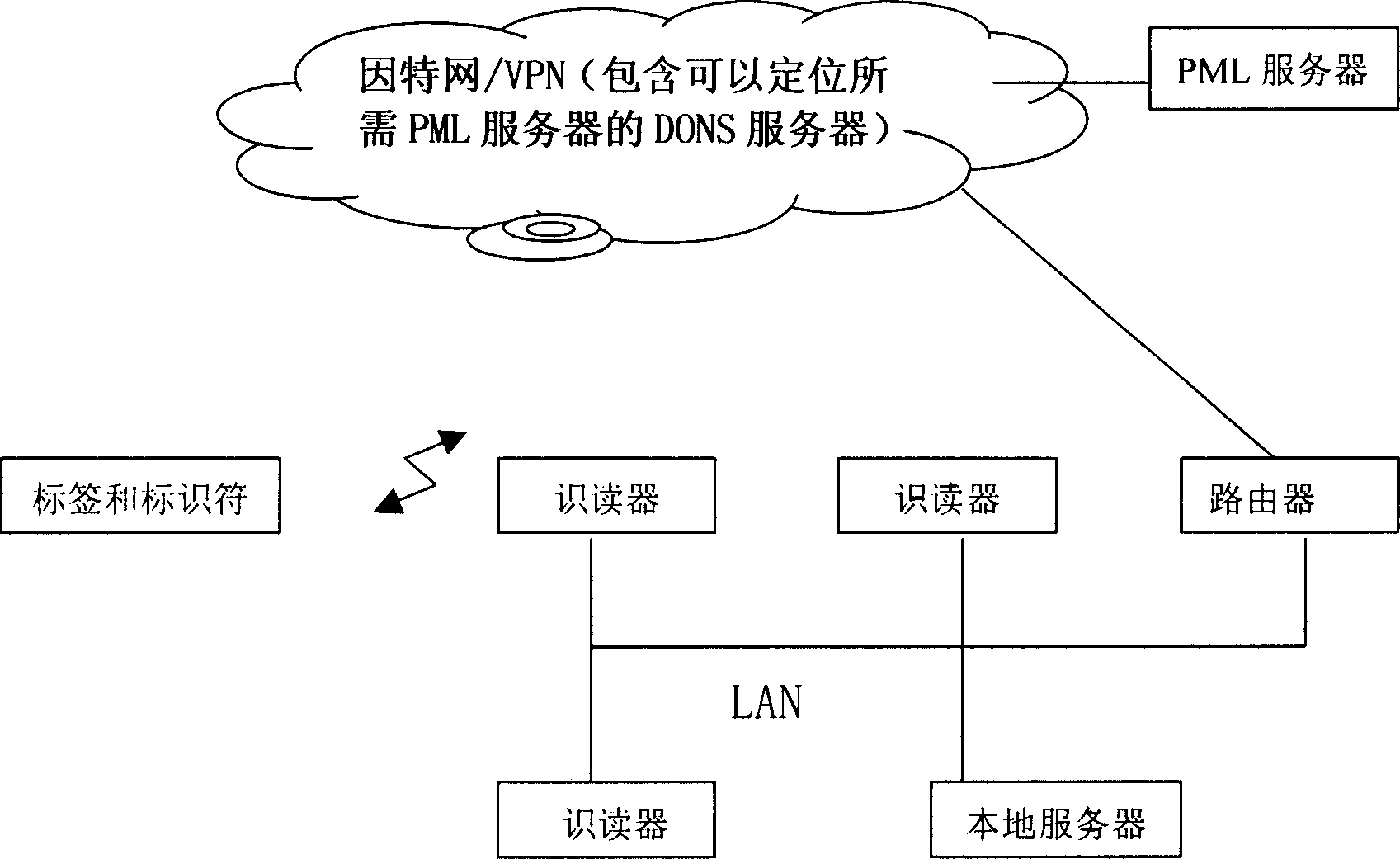
Guiding code used for object and commodity coding netowrk joining and its application system
InactiveCN1719458ARealize transparent managementEnsure safetyData processing applicationsRecord carriers used with machinesProgramming languageIntellectual property
The present invention relates to a guiding code for coding and networking articles and commodities. When it is used in the electronic or digital identification code and additional plane identification code or bar code for making network transmission an identification symbol formed from digital symbol or character symbol or ideographic symbol or their combination, for example country code in ITU-T-E164 and area code defined by every country or article and commodity class code as digital code or character code with specific definition of guiding code can be embedded so as to solve various problems of global trade process.
Owner:上海通用化工技术研究所
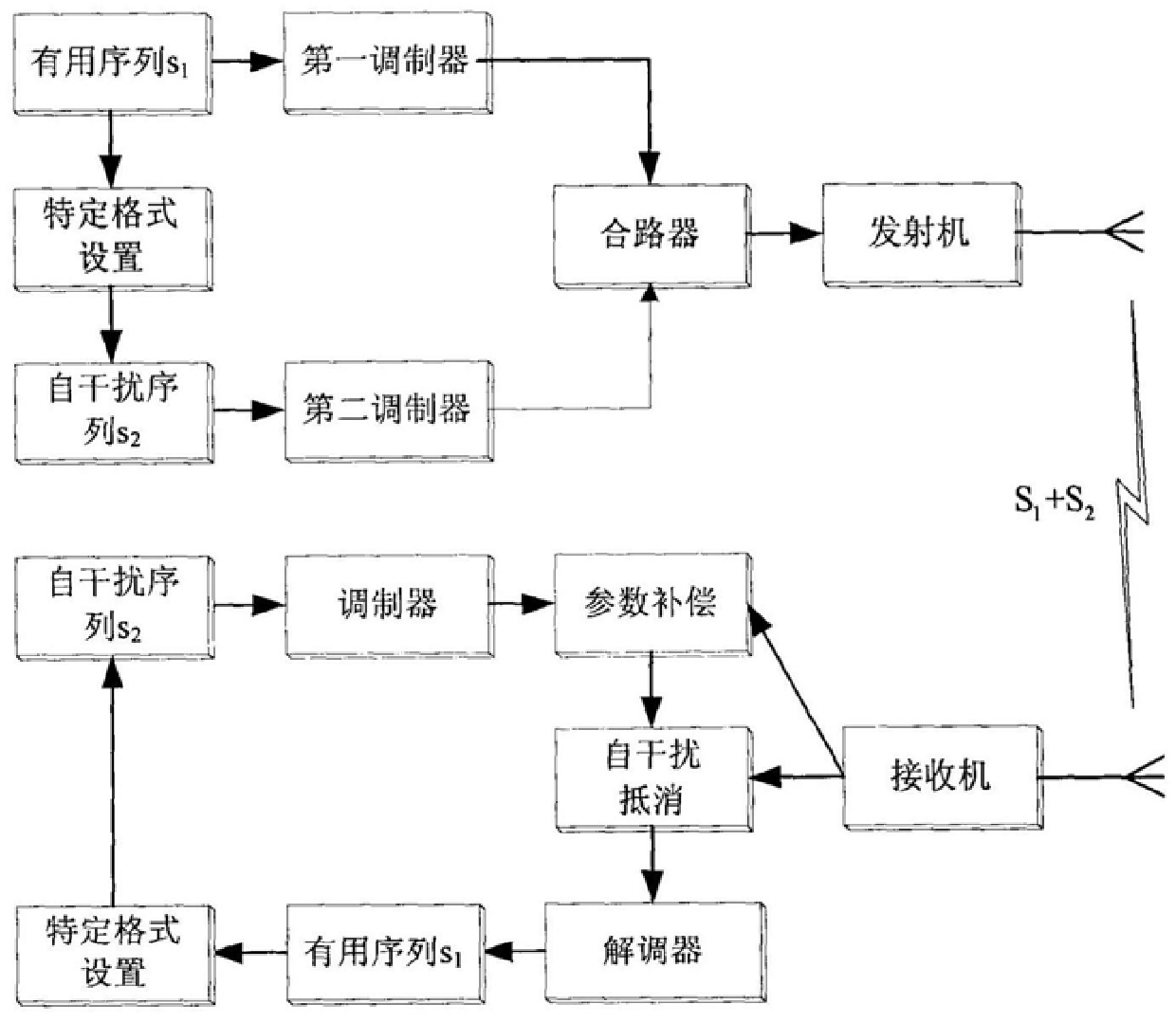
A self-interference communication method and system
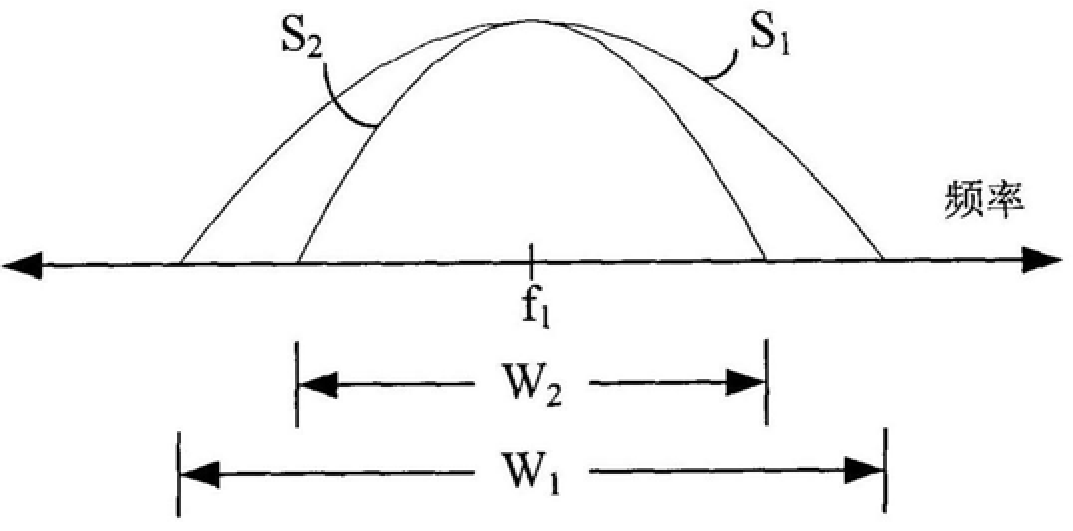
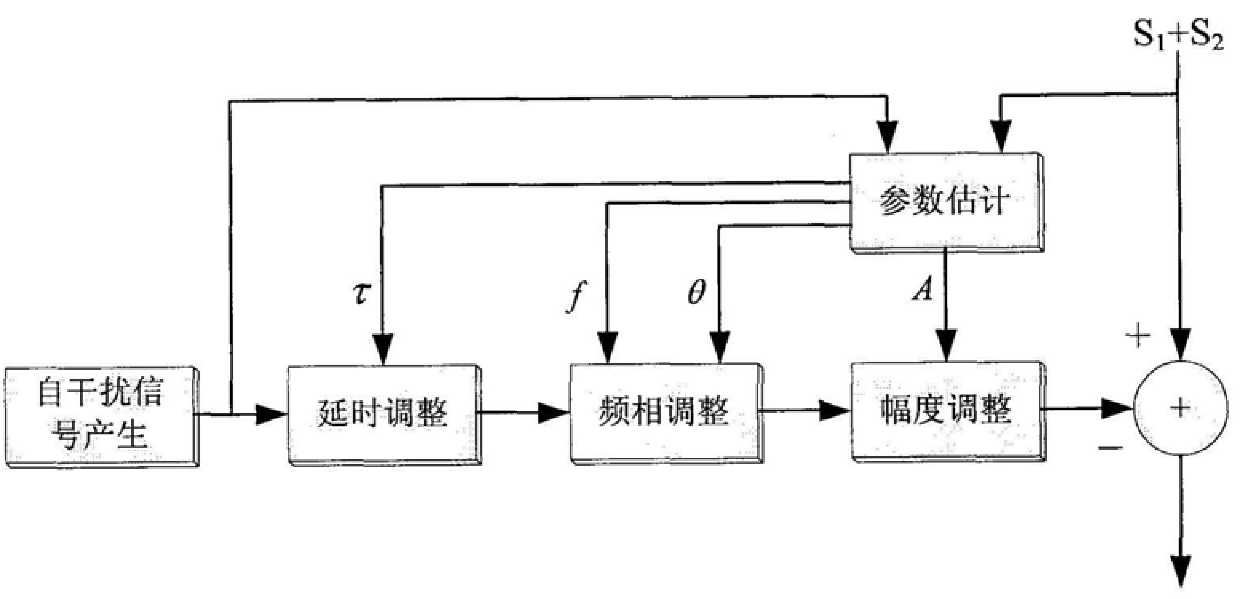
InactiveCN106508102BImprove anti-intercept performanceEnsure information securitySecuring communicationSelf interferenceSecure communication
A self-interference communication method and system belong to the technical field of communication. The sender converts the useful sequence to be sent into a specific format and modulates it to generate a self-interference signal, linearly superimposes the useful signal and the self-interference signal into a mixed signal, and sends it on the same channel. According to the known self-interference signal generation format, the cooperative receiver estimates the channel parameters of the self-interference signal for the received mixed signal, reconstructs the self-interference signal, and then subtracts the reconstructed self-interference signal from the received mixed signal Demodulate to get the useful sequence. In the whole communication process from the transmitting party to the cooperating receiving party in the present invention, part of the transmission is a mixed signal, which has great anti-interception performance. Since the non-cooperating party does not know the format of the self-jamming signal and cannot reconstruct the self-jamming signal, there is no way to extract useful information from the mixed signal and ensure the information security of communication. Compared with the PCMA technology, the invention can enhance the security of the whole communication process and widen the application scope.
Owner:西南电子电信技术研究所
Device and method for destroying secret electronic information carriers
ActiveCN103611607ASignificant application advantagesEnsure information securityMagnetic bodiesGrain treatmentsComputer moduleElectronic information
The invention discloses a device for destroying secret electronic information carriers. The device is provided with a hard disk demagnetization module, a selenium drum cut-off module and a carrier crushing module; the device for destroying the carriers is provided with a plurality of feeding holes, so that the multiple electronic information carriers can be destroyed at the same time. The device can be used for destroying most secret electronic information carriers such as a selenium drum, a hard disk, an optical disk, a USB flash disk, a chip, an integrated circuit (IC) card, a secure digital (SD) card, a compact flash (CF) card, a T-flash (TF) (Micro SD) card, a multi media card (MMC), and a mini SD card in a physical way; the device is simple in structure, efficient, and low in noise and has an energy-saving effect, thus being completely suitable for the office environment.
Owner:北京瑞翔恒宇科技有限公司
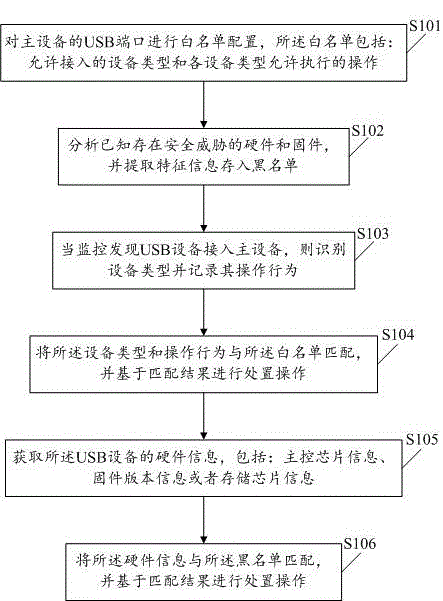
Method and device for detecting malicious USB equipment
ActiveCN105718825AEfficient identificationIdentify in timeInternal/peripheral component protectionDevice typeFirmware version
The invention discloses a method and a device for detecting malicious USB equipment. The method comprises the steps as follows: white list configuration is carried out on a USB port of primary equipment, wherein a white list comprises access-allowed equipment types and execution-allowed operations of the equipment types; known hardware and firmware with a security threat are analyzed; feature information is extracted and stored into a black list; when the condition that the USB equipment is accessed to the primary equipment is monitored and found, the equipment type is identified and the operation behavior is recorded; the equipment type and the operation behavior are matched with those in the white list; processing operation is carried out on the basis of the matching result; hardware information of the USB equipment is obtained and comprises main control chip information, firmware version information or storage chip information; the hardware information is matched with that in the black list; and the processing operation is carried out on the basis of the matching result. According to the technical scheme, the USB equipment for implementing an attack by known hardware bug and firmware bug can be effectively identified.
Owner:HARBIN ANTIY TECH
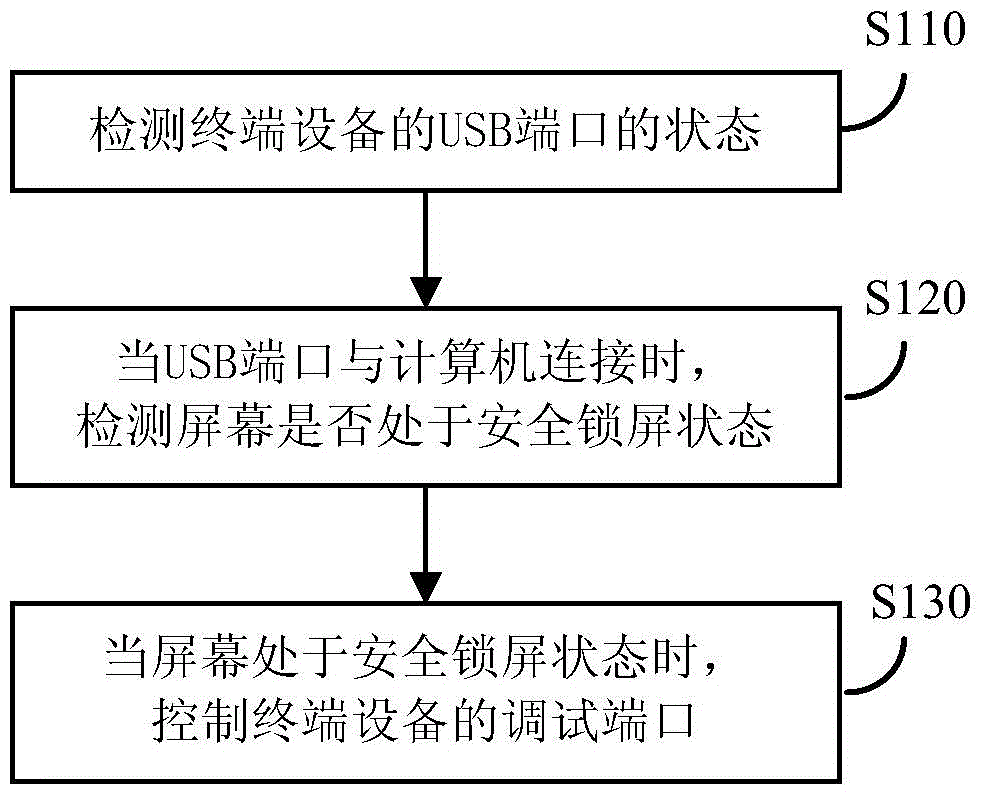
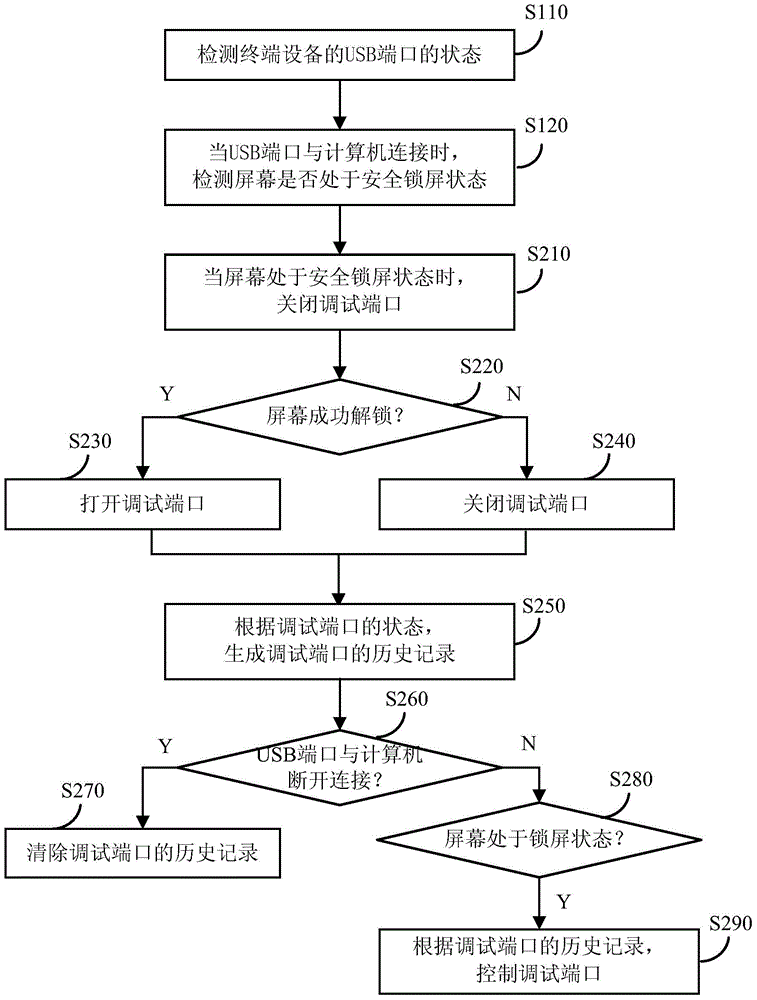
Method and device for controlling debugging ports of terminal equipment
ActiveCN103559435AImprove completenessEnsure safetyInternal/peripheral component protectionDigital data authenticationTerminal equipmentEngineering
The invention discloses a method and a device for controlling debugging ports of terminal equipment. The method for controlling the debugging ports includes the steps: detecting the state of a universal serial bus port of the terminal equipment; detecting whether a screen of the terminal equipment is in a safety screen locking state or not when the universal serial bus port is connected with a computer; controlling the debugging ports of the terminal equipment when the screen is in the safety screen locking state. By the aid of the method and the device for controlling the debugging ports, the completeness of safety strategies of the terminal equipment can be improved, and safety of user information on the terminal equipment is effectively ensured.
Owner:HUAWEI TECH CO LTD
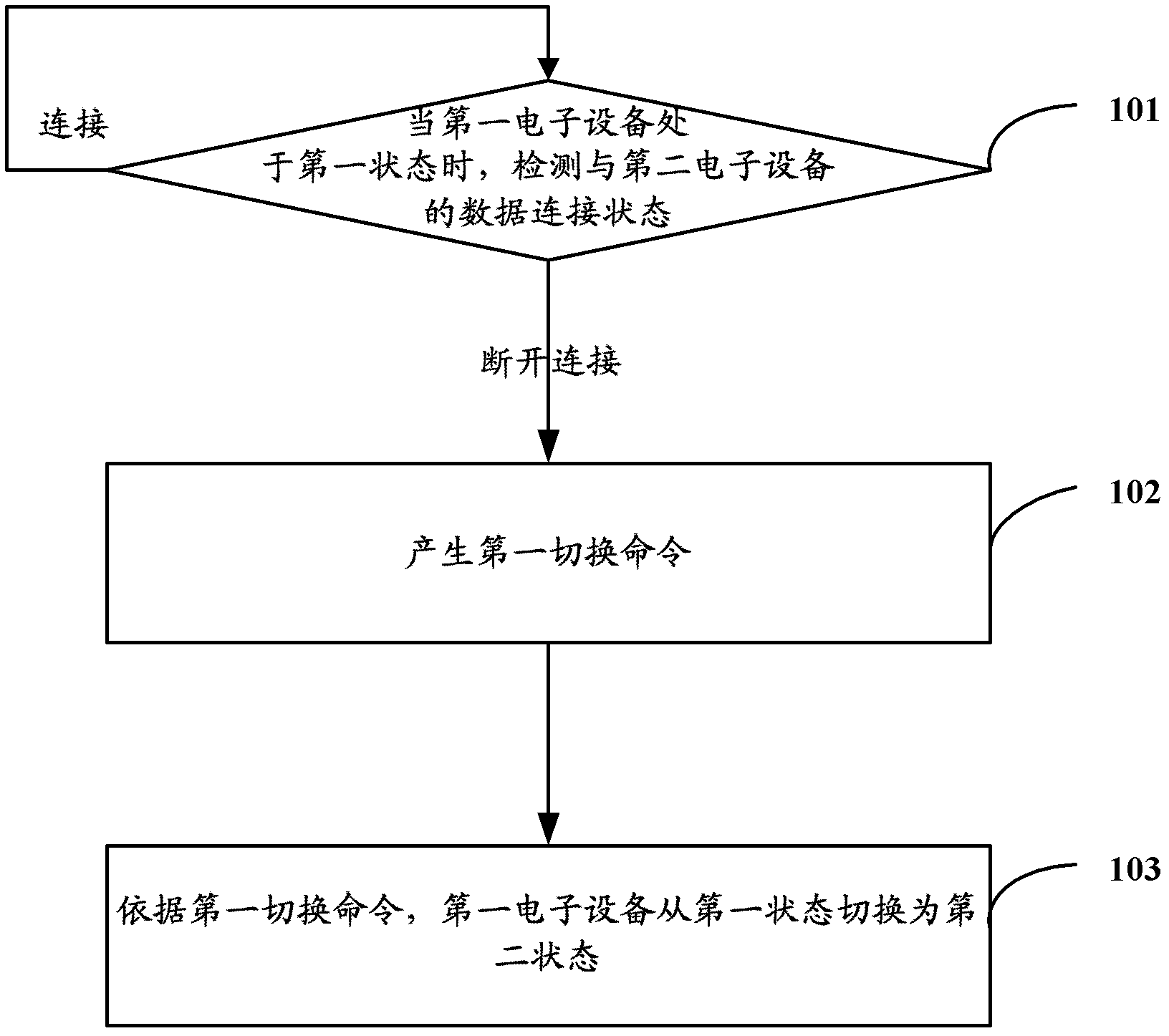
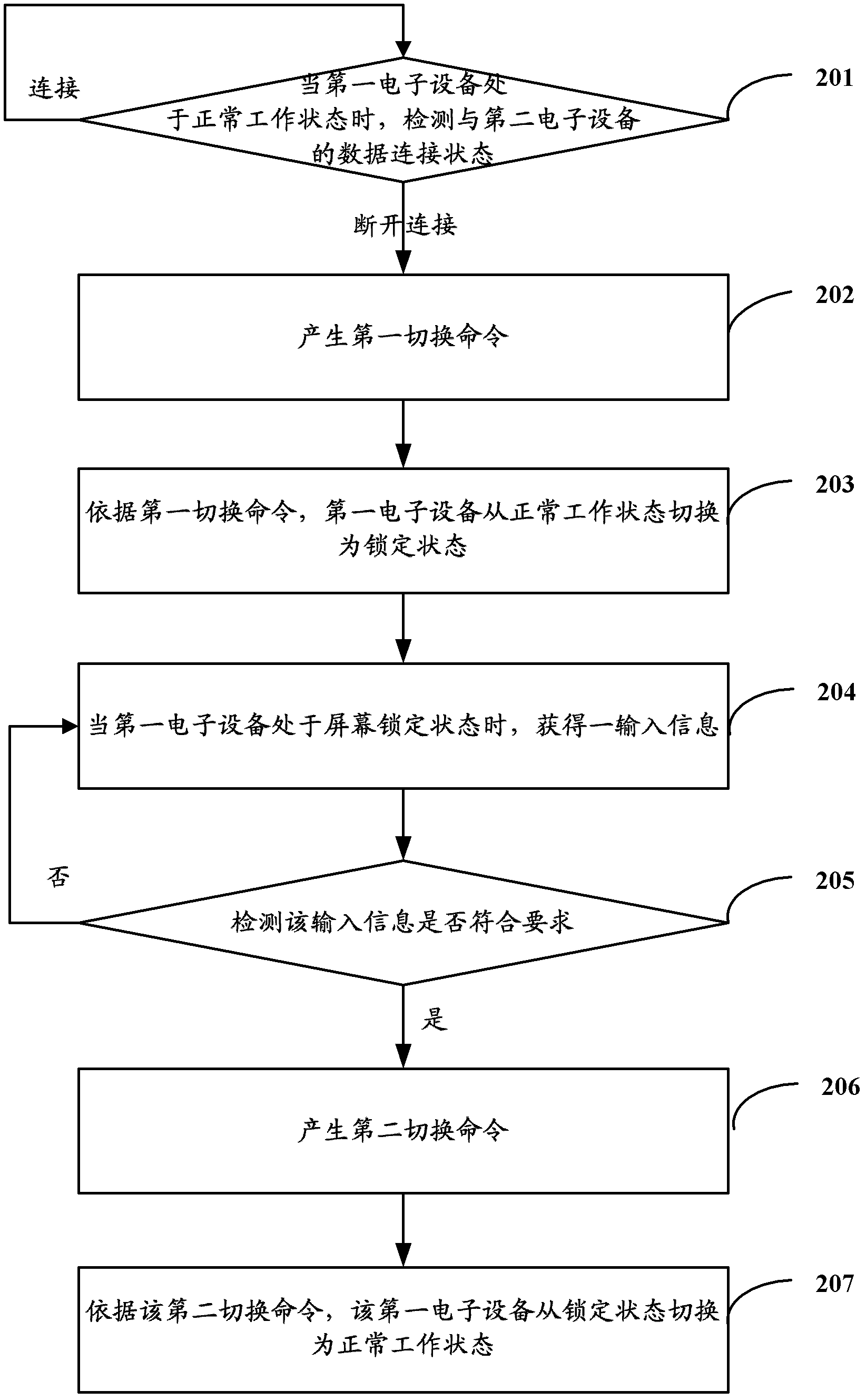
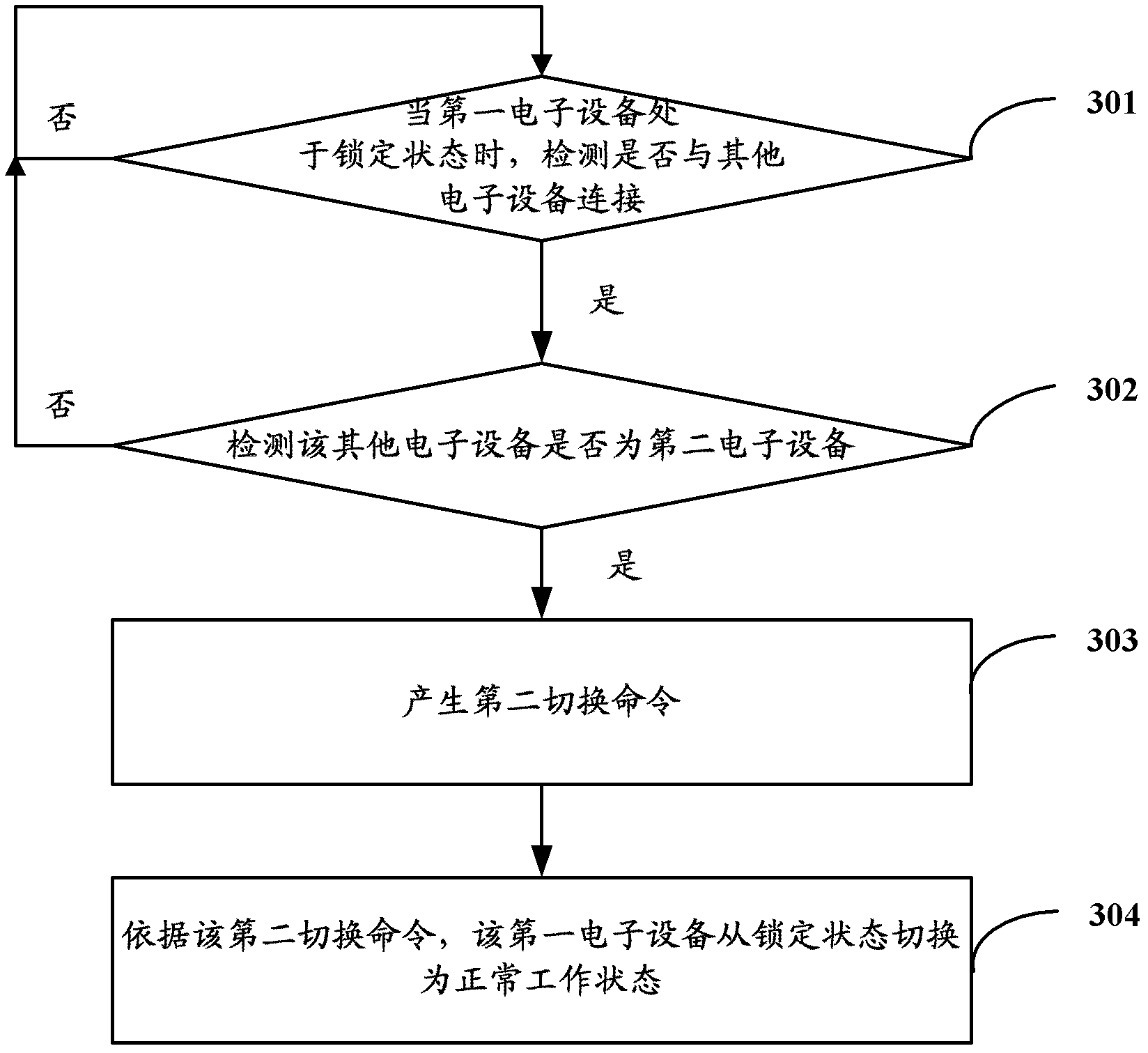
State switching method and electronic equipment
ActiveCN103019836AEnsure safetyReduce power consumptionProgram initiation/switchingPower supply for data processingData connectionState switching
The invention discloses a state switching method and electronic equipment. The switching method is applied to first electronic equipment which is engaged in data connection with second electronic equipment. The first electronic equipment has a first state and a second state; when the first electronic equipment is in the first state, the electronic equipment can execute a first amount of instructions; and when the first electronic equipment is in the second state, the first electronic equipment can execute a second amount of instructions, wherein the second amount is less than the first amount. The state switching method includes the steps that: the data connection state of the first electronic equipment with the second electronic equipment is detected to obtain a first detection result when the first electronic equipment is in the first state; a first switching command is generated when the first detection result shows that the data connection between the first and second electronic equipment is cut out; and according to the first switching command, the first electronic equipment switches from the first state to the second state. With the state switching method, when the data connection of the electronic equipment with other electronic equipment is cut out, the electronic equipment can rapidly switch to the second state so as reduce power consumption of the system and / or to guarantee the security of the user information.
Owner:LENOVO (BEIJING) LTD
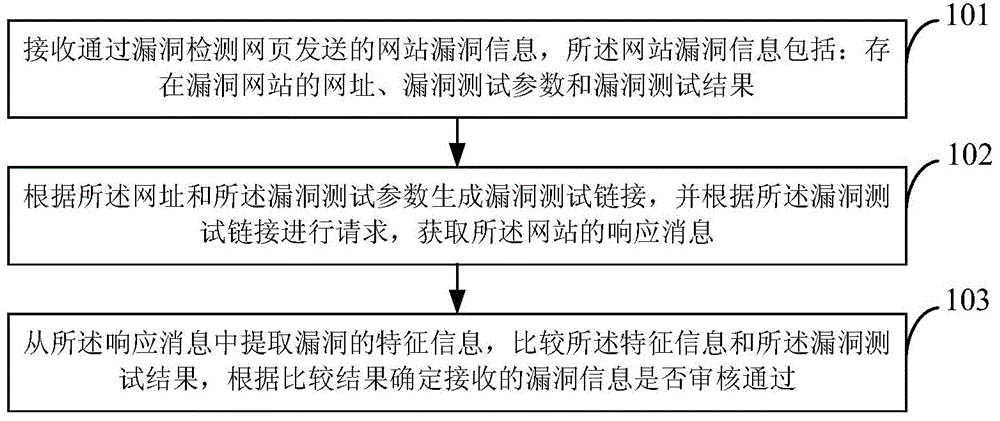
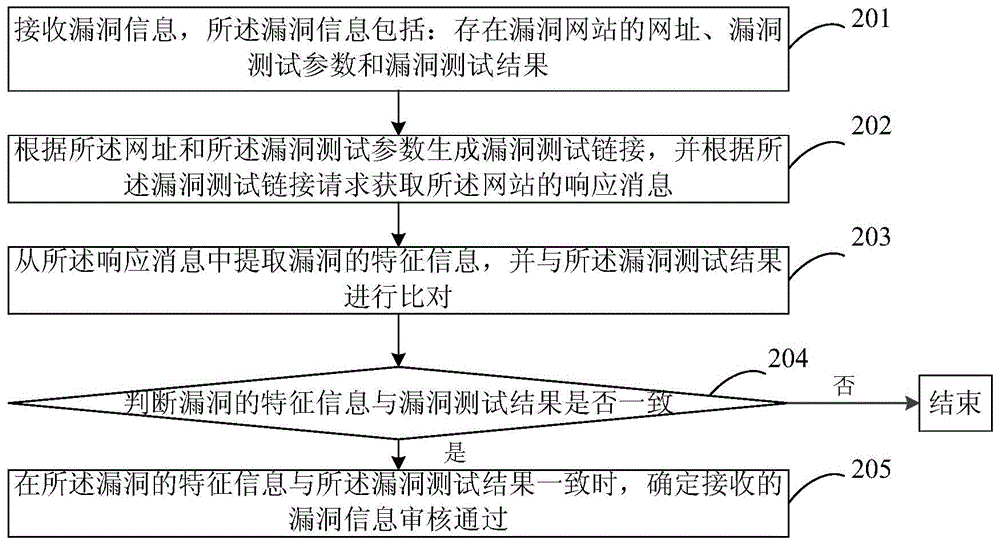
Website bug examination method and device
InactiveCN104618177AEnsure information securityReduce false alarm rateData switching networksUniform resource locatorInformation security
The invention discloses a website bug examination method and device. The method comprises receiving website bug information sent by bug detection webpage, wherein the website bug information comprises uniform resource locators with bug websites, bug test parameters and bug test results; generating bug test links according to the uniform resource locators and the bug test parameters and performing requirement according to the bug test links to obtain uniform resource locator response information; extracting bug characteristic information from the response information, comparing the characteristic information with the bug test results and determining whether the received bug information passes the examination. By the aid of the method and the device, the bug information is received, bugs mentioned in the bug information are subjected to bug test verification, the bug information is sent to website managers, and accordingly, the bug false alarm rate is reduced, and the website information security is guaranteed.
Owner:BEIJING QIANXIN TECH
Intelligent ammeter management system and method
InactiveCN104123674AEnsure information securitySave human effortData processing applicationsCo-operative working arrangementsEmbedded systemRadio frequency
The invention discloses an intelligent ammeter management system and method. An ammeter RFID (radio frequency identification) tag is arranged on an ammeter and the ammeter RFID tag is provided with a radio frequency chip stored with identification information for ammeter management. An ammeter read-write device is cooperated with the ammeter RFID tag, reads the ammeter identification information stored in the radio frequency chip of the ammeter RFID tag, and can write relevant information into the radio frequency chip of the ammeter RFID tag; finally, a remote management center is in data connection with the ammeter read-write device, obtains the ammeter identification information read by the ammeter read-write device and stores and manages the information; and the remote management center transmits the processed relevant information to the ammeter read-write device, and the ammeter read-write device writes the information into the radio frequency chip of the ammeter RFID tag of the corresponding ammeter. The intelligent ammeter management system and method are based on the RFID technology and can realize safe, reliable and convenient intelligent management on the ammeter.
Owner:SHANGHAI CHANGFENG SMART CARD
Application program login method, computer side, mobile terminal, system and storage medium
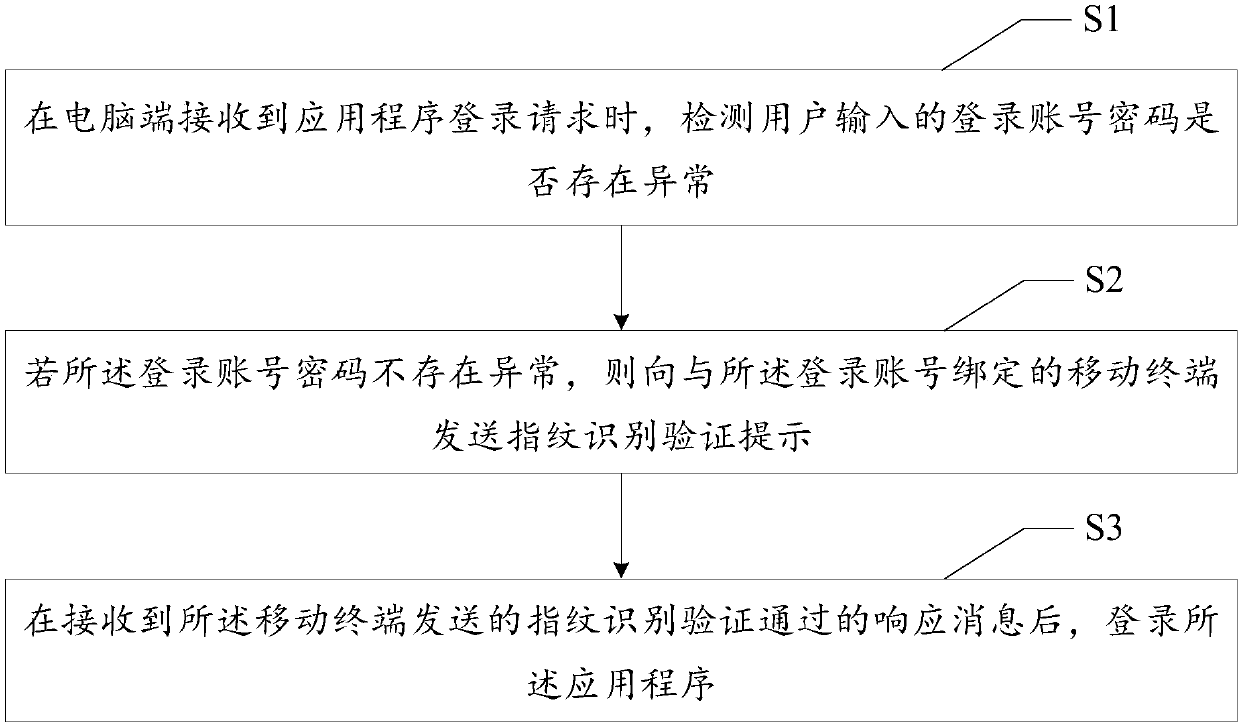
PendingCN109558718AEnsure information securityImprove login securityDigital data authenticationPasswordApplication software
The invention discloses an application program login method, a computer end, a mobile terminal, a system and a readable storage medium, and the method comprises the steps: detecting whether a login account password input by a user is abnormal or not when the computer end receives an application program login request; if the login account password is not abnormal, sending a fingerprint identification verification prompt to a mobile terminal bound with the login account; and logging in the application program after receiving a response message which is sent by the mobile terminal and passes thefingerprint identification verification. Through double verification of password verification and fingerprint verification, the identity and login safety of the user are authenticated, so that the login safety coefficient is improved, and the information safety of the user is ensured.
Owner:NUBIA TECHNOLOGY CO LTD
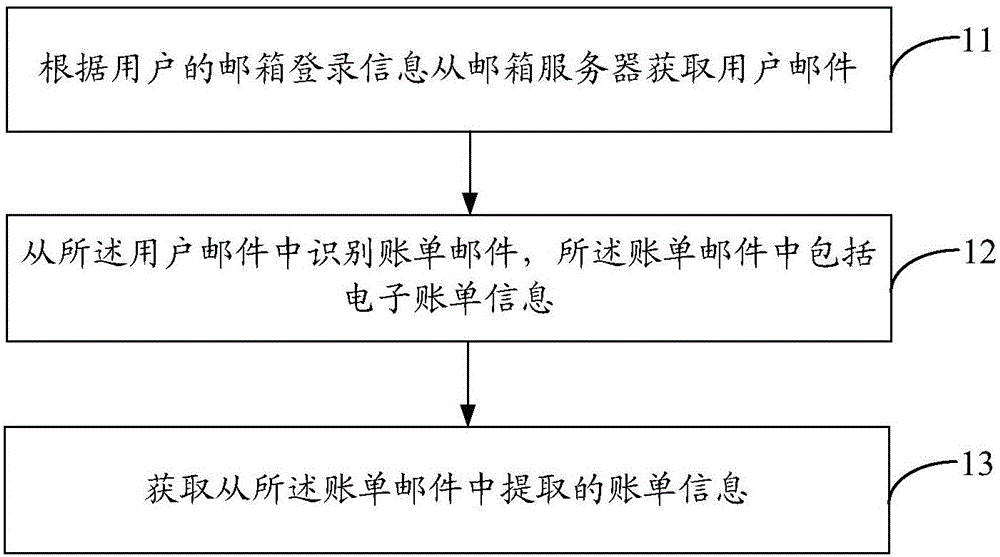
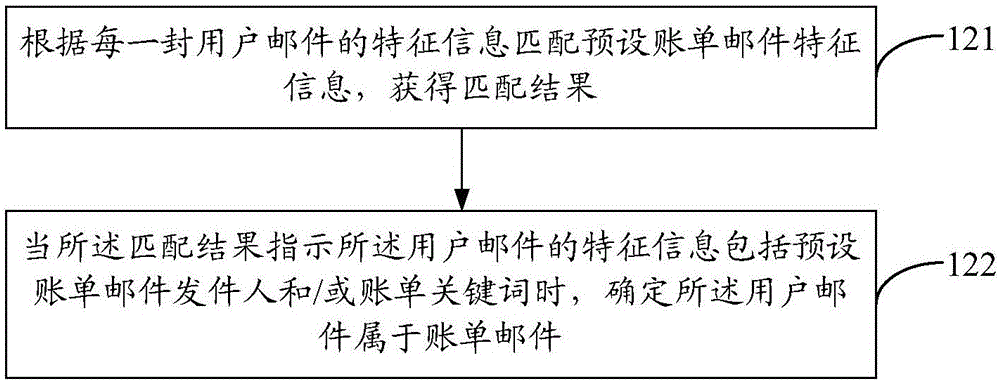
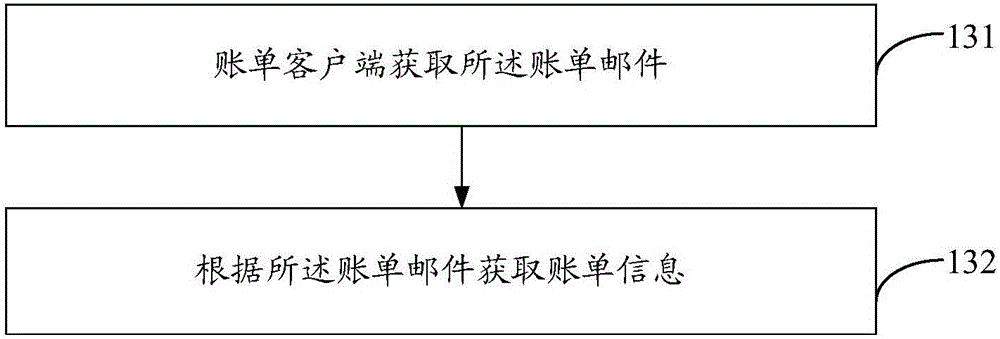
Method and apparatus for obtaining billing information
InactiveCN106341313APrevent leakageEnsure safetyFinanceSubstation equipmentComputer terminalInformation security
The present discloses a method and apparatus for obtaining billing information. The method includes the following steps that: user mails are obtained from a mail server end according to the mailbox login information of a user; a billing mail is identified from the user mails, wherein the billing mail contains electronic billing information; and the billing information is extracted from the billing mail. According to the method for obtaining the billing information of the invention, in a whole billing information obtaining process, the mailbox login information of the user is not uploaded to a billing server and is only stored on a user terminal, and therefore, user information leakage caused by attacks to the database of the billing server performed by criminals can be effectively prevented, and the information security of the user can be effectively ensured.
Owner:BEIJING XIAOMI PAYMENT TECH CO LTD
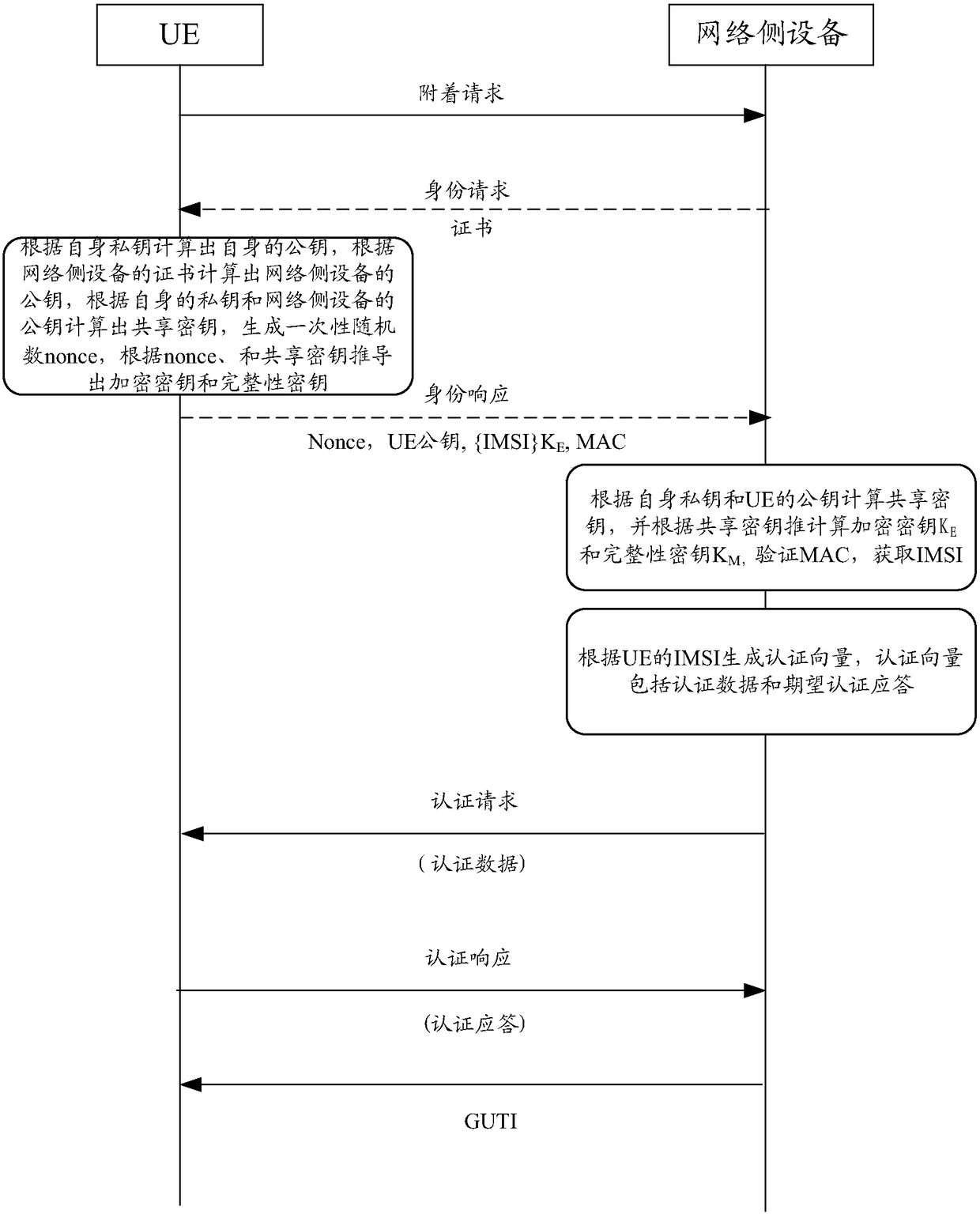
Authentication method, device and system
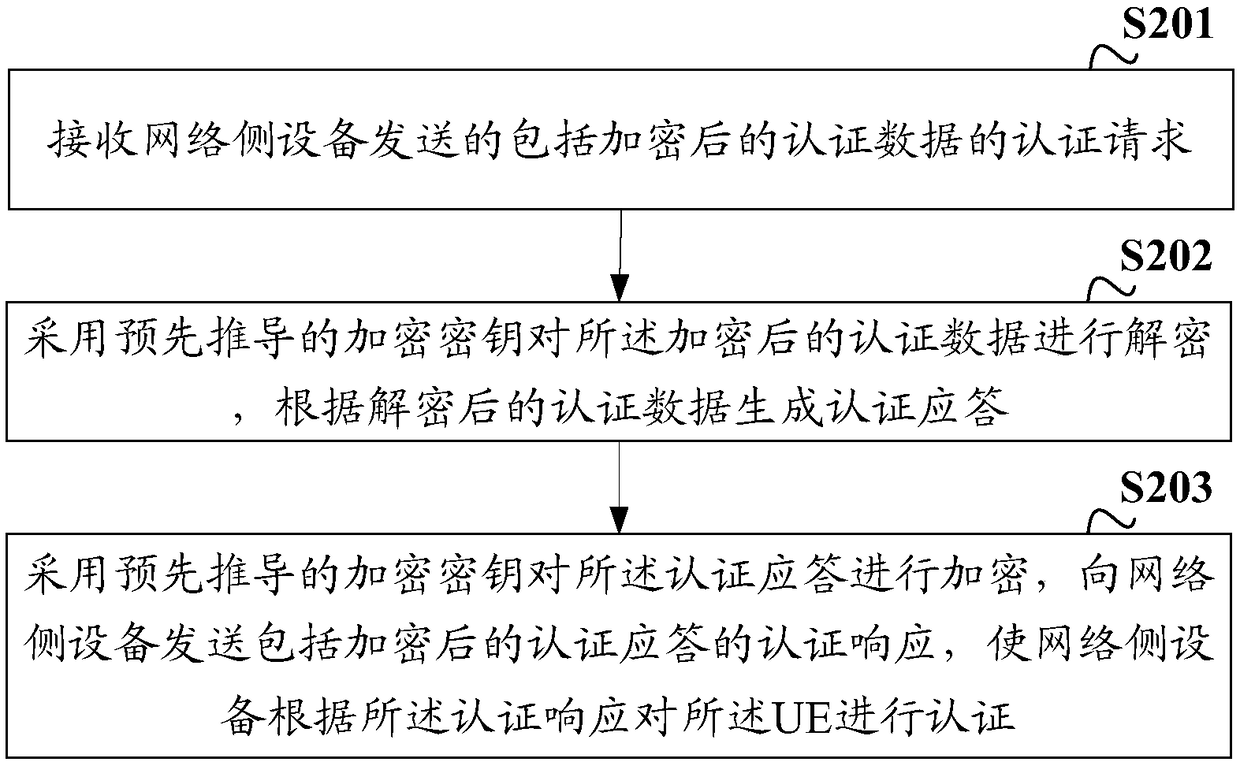
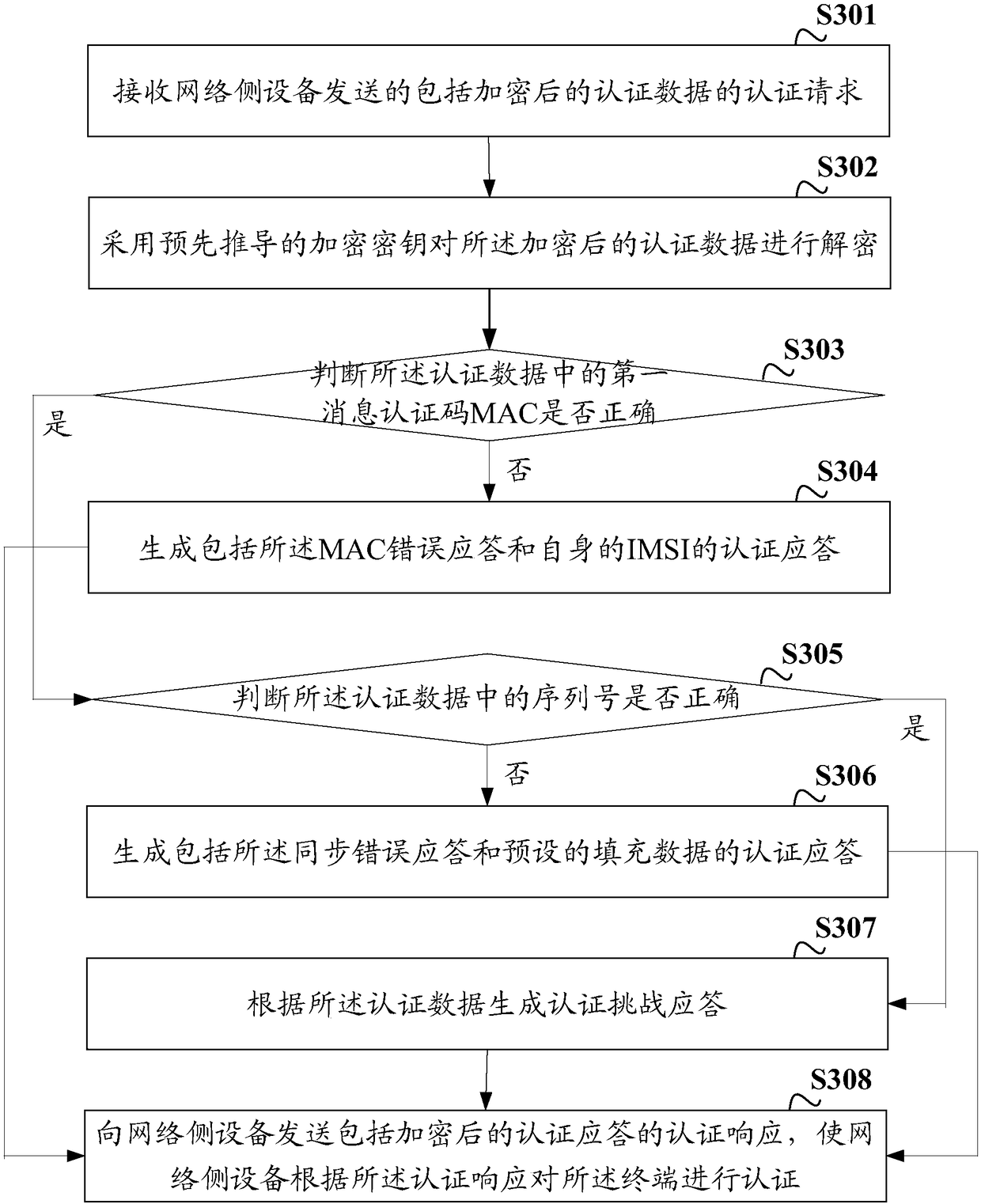
ActiveCN108809903AImprove experienceAvoid Correlation AttacksUser identity/authority verificationSecurity arrangementThird partyInformation security
The invention discloses an authentication method, device and system. The method comprises the following steps of receiving an authentication request which is sent by network side equipment and comprises encrypted authentication data; decrypting the encrypted authentication data by adopting a pre-derived encryption key, and generating an authentication response according to the decrypted authentication data; and encrypting the authentication response by adopting the pre-derived encryption key, and sending an authentication response comprising the encrypted authentication response to the networkside equipment. In the embodiments of the invention, UE decrypts the encrypted authentication data sent by the network side equipment according to the pre-derived encryption key and encrypts the generated authentication response according to the pre-derived encryption key, and the UE and the network side equipment transmit the encrypted authentication data and the authentication response during an authentication process, so that a third-party malicious attacker is prevented from acquiring the authentication data and the authentication response to carry out correlation attack on the UE and thenetwork side equipment, the information safety of the user is guaranteed, and the user experience is improved.
Owner:CHINA MOBILE COMM LTD RES INST +1
Image Forming Device and Image Forming Program
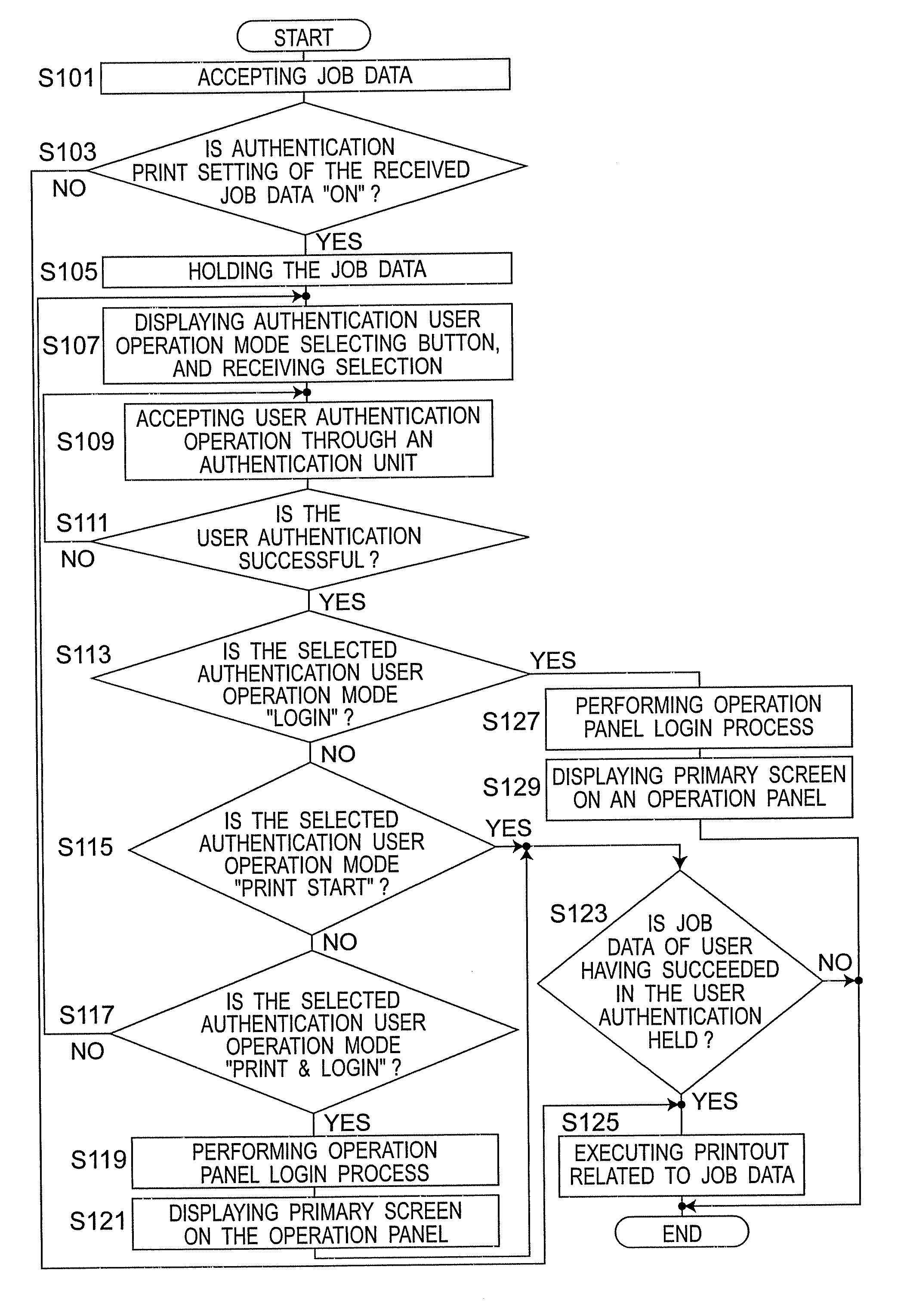
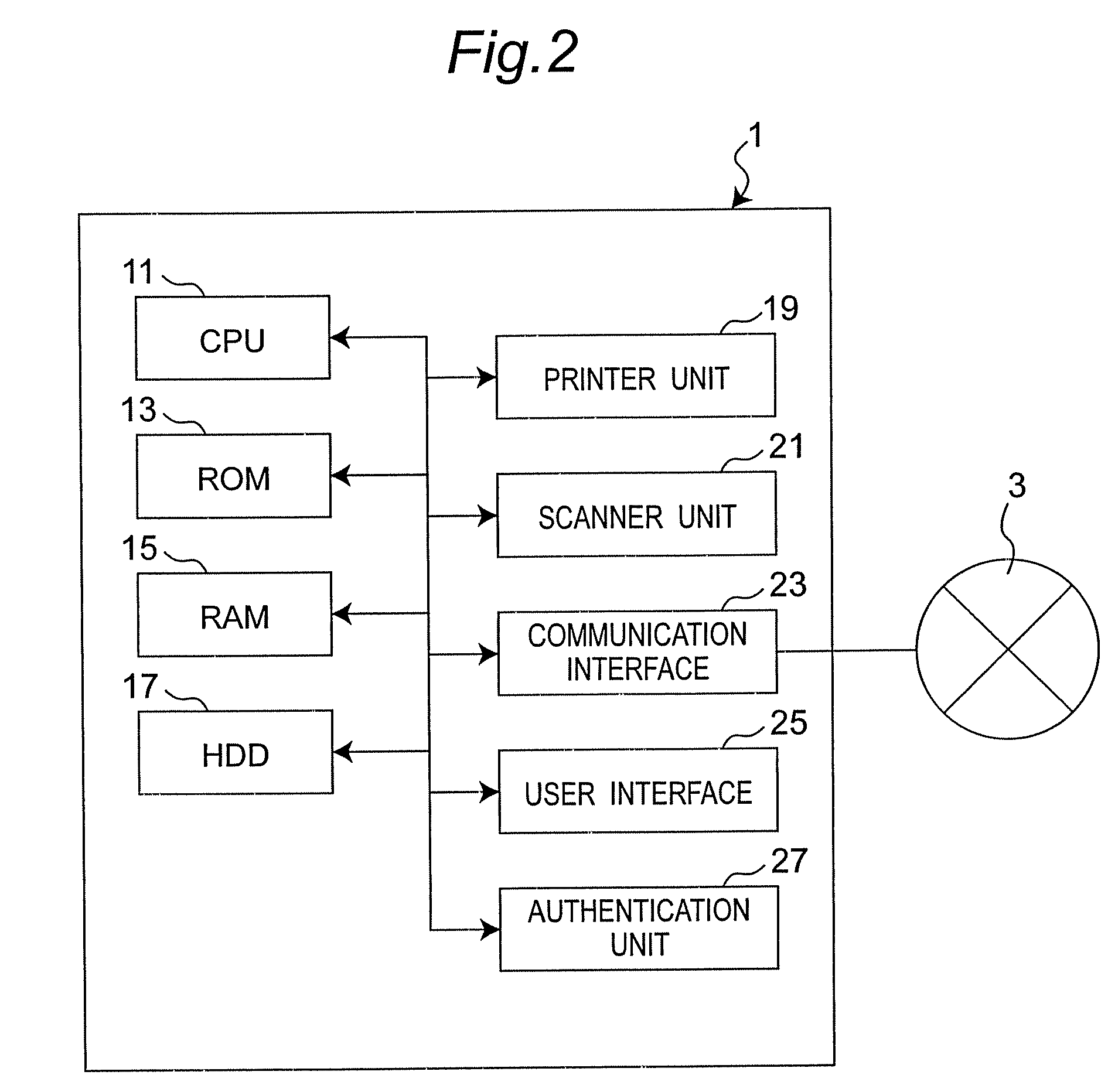
ActiveUS20090158422A1Easy to operateImprove productivityDigital data processing detailsUser identity/authority verificationImage formationUser authentication
The present invention is an image forming device capable of executing an authentication print printing. The image forming device includes: an authentication print detecting unit which detects whether to execute a job as the authentication print printing by referencing predetermined data; an authentication unit; a user authentication unit which outputs the result of the user authentication; a job executing unit; a user interface; and a user interface input mode switching unit which switches an information input / output mode of the user interface, wherein, an instruction to execute a first process can be received, and wherein the first process includes processes in which: the execution of the authentication print printing starts based on the result of the user authentication output by the user authentication unit; and the result of the user authentication is invoked so that the information input / output mode of the user interface is switched to a login mode.
Owner:KONICA MINOLTA BUSINESS TECH INC
Data processing method, related device and computer storage medium
ActiveCN109302466ASolve problems such as low securityImprove securityNetworks interconnectionComputer hardwareInformation leakage
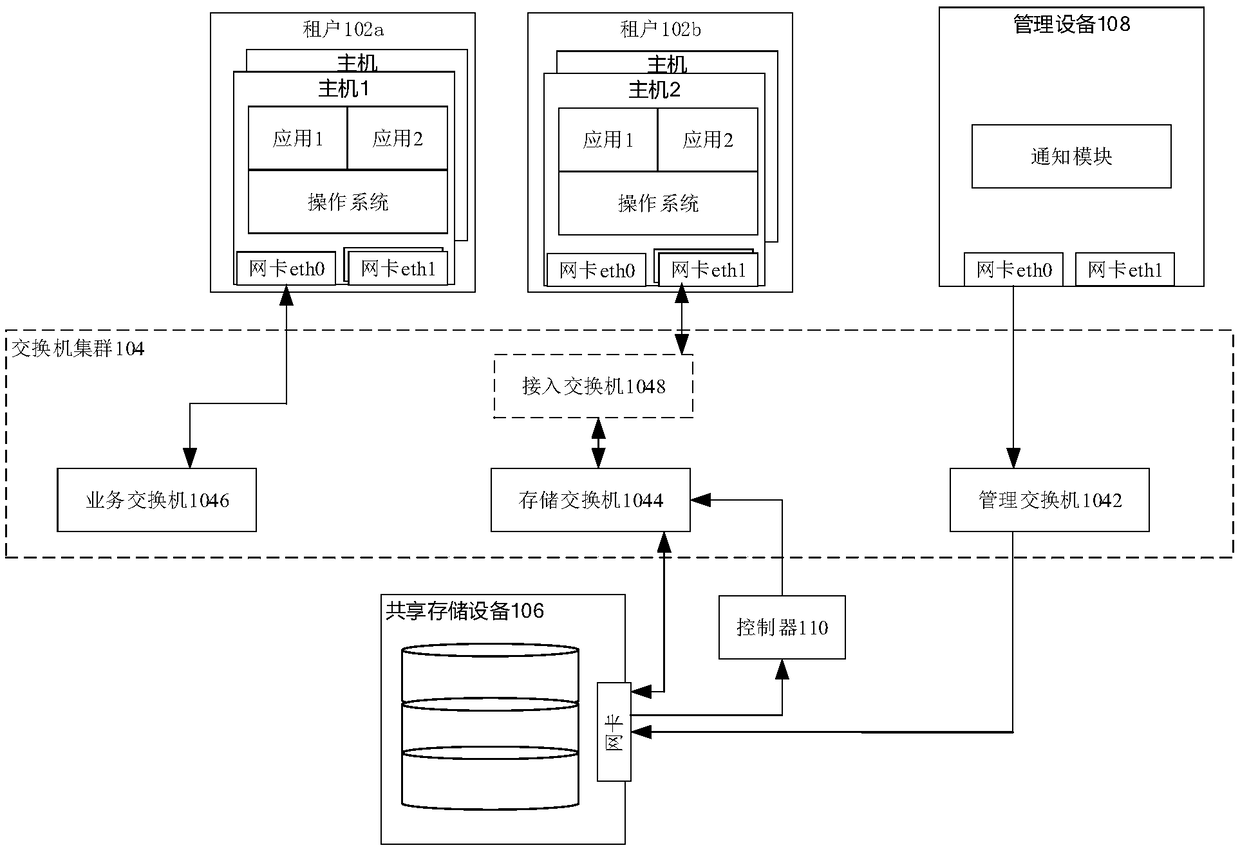
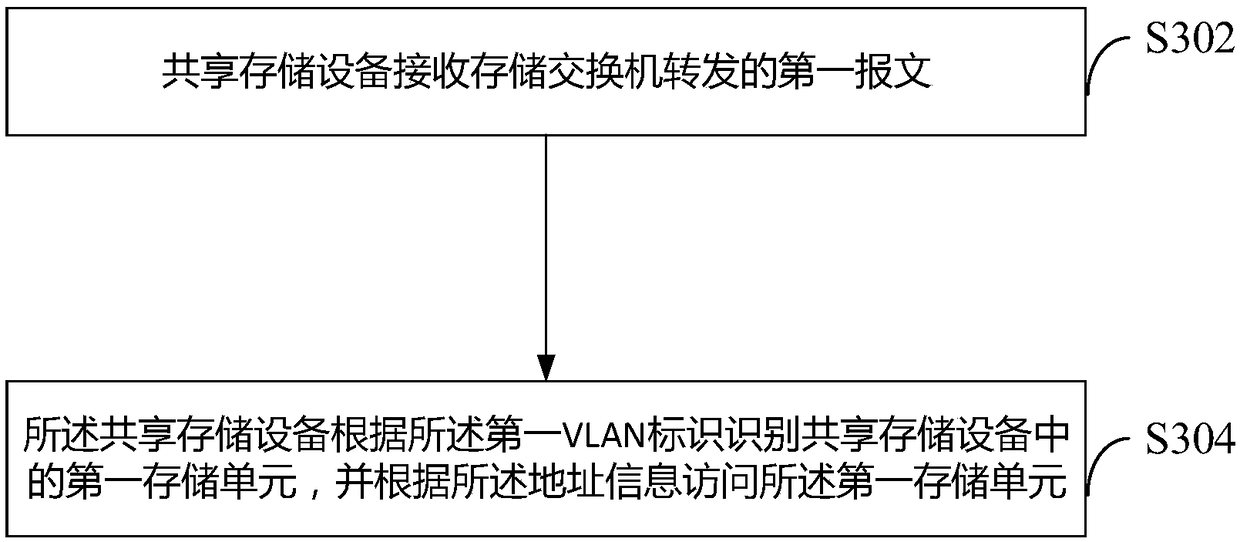
The embodiment of the invention discloses a data processing method. The method comprises the following steps: a shared storage device receives a first message forwarded by a storage switch, wherein the first message carries a virtual local area network VLAN identifier and address information; and the shared storage device identifies a storage unit occupied by a host in the shared storage device according to the VLAN identifier, and accesses the storage unit according to the address information. By adoption of the embodiment of the invention, the problems of tenant information leakage, tenant information insecurity and the like in the prior art can be solved, thereby improving the security of information.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com