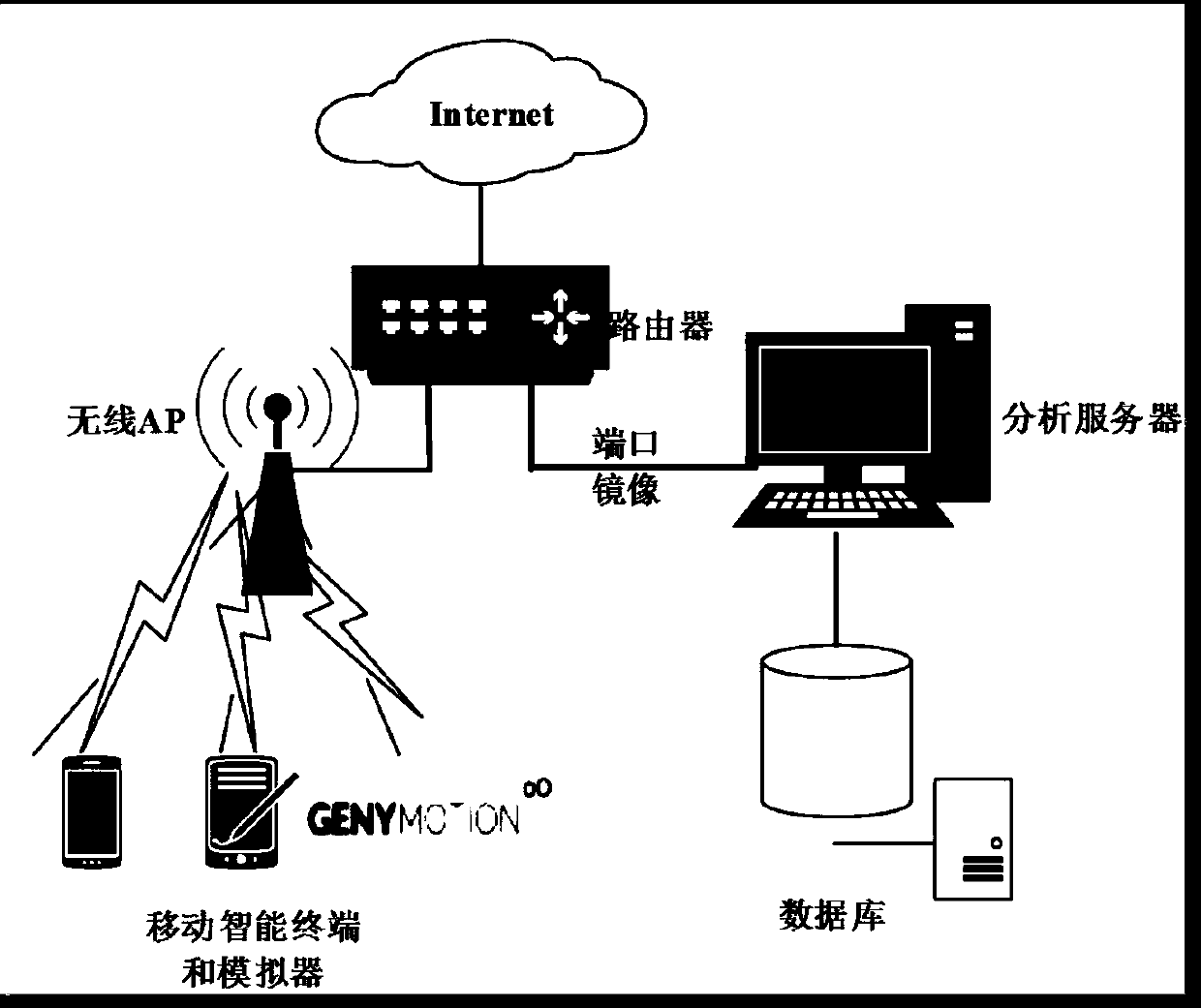
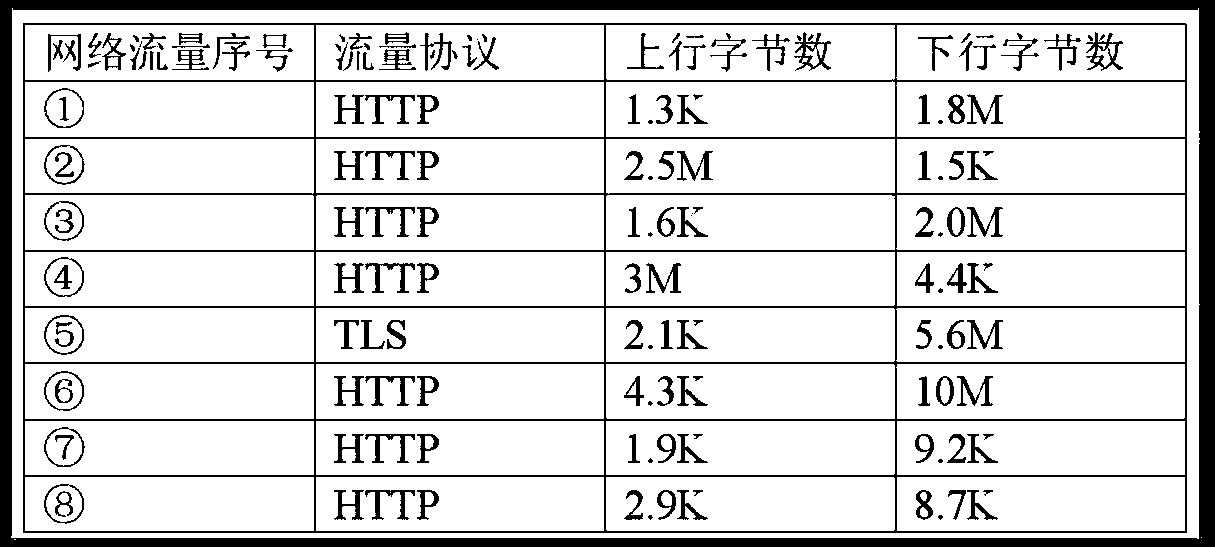
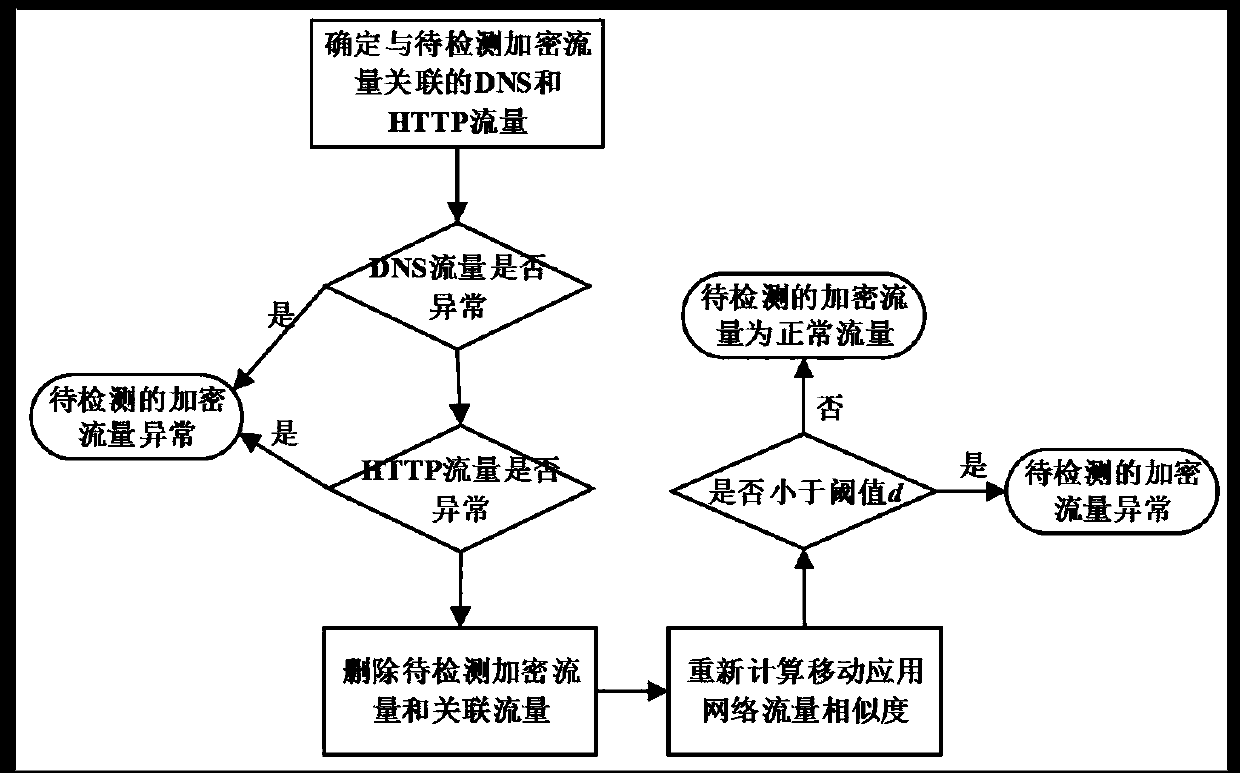
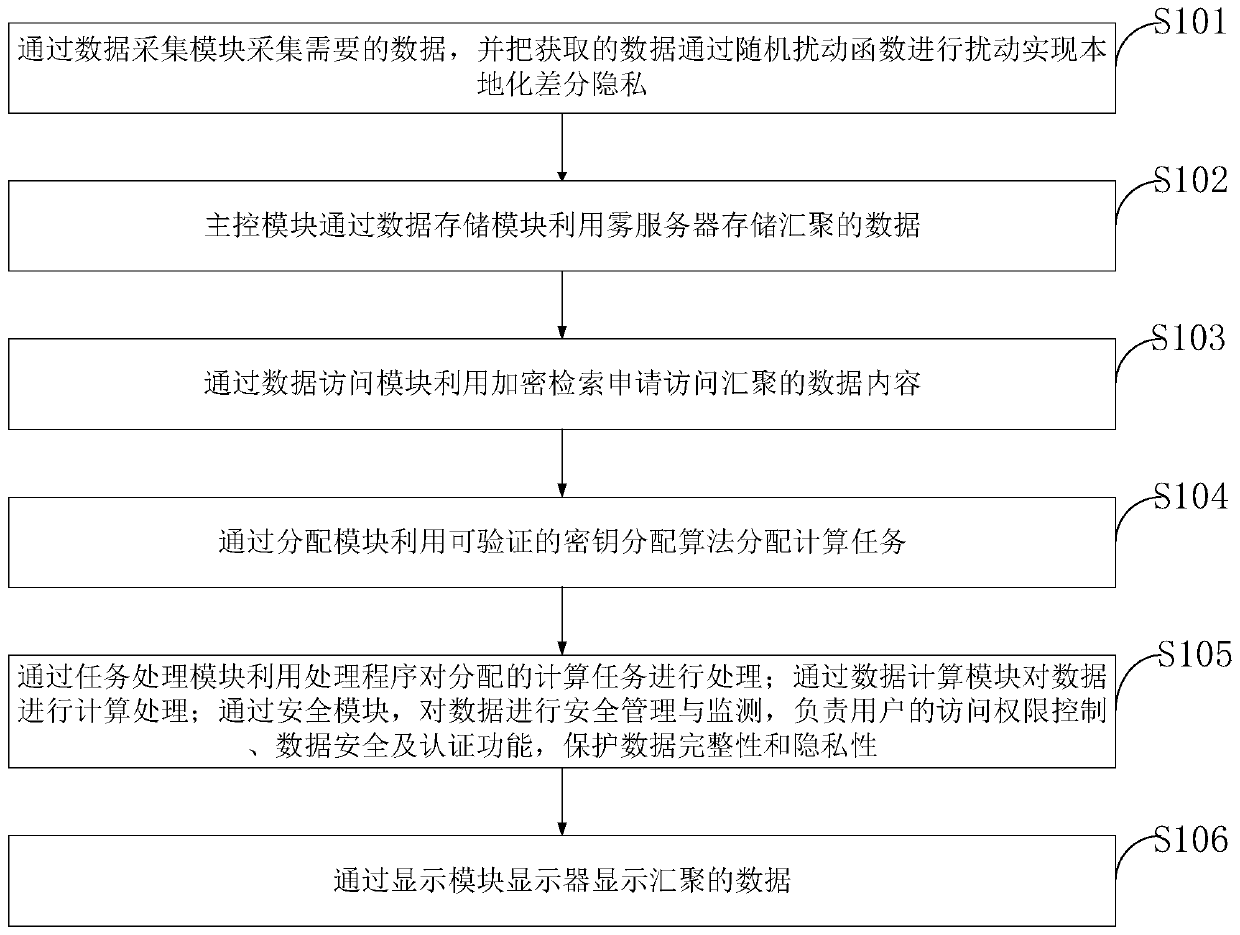
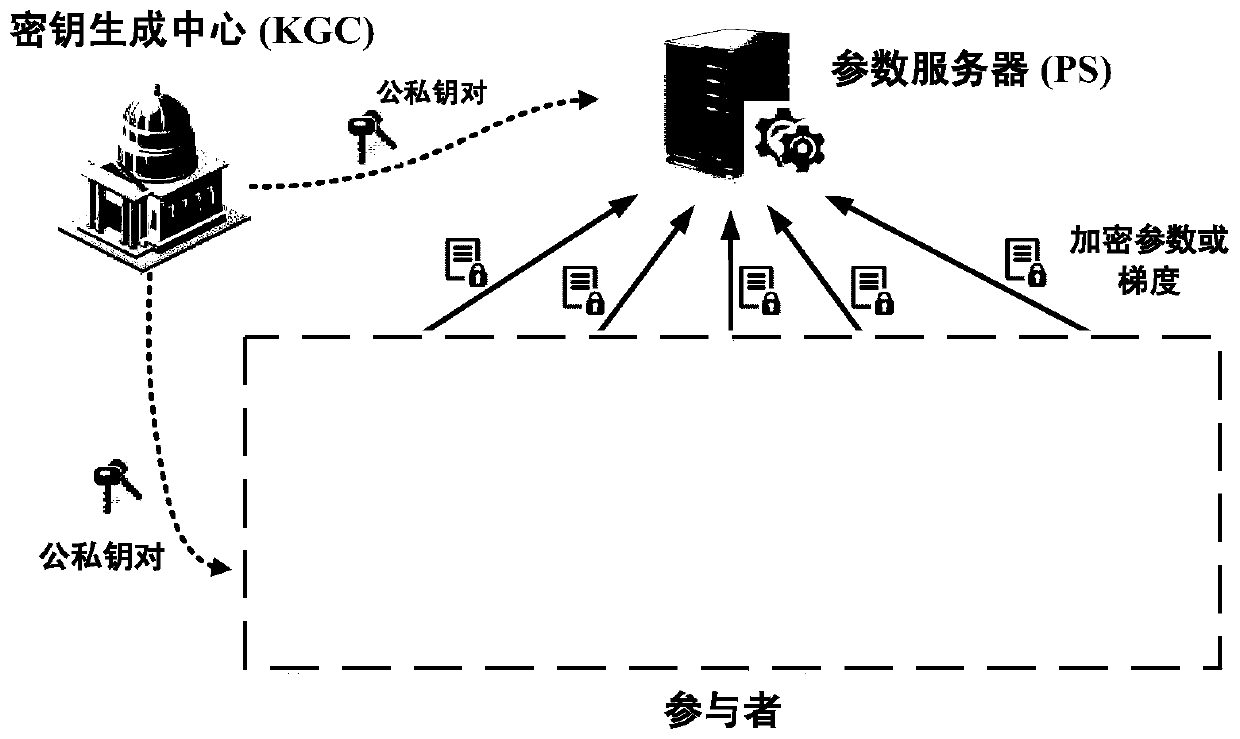
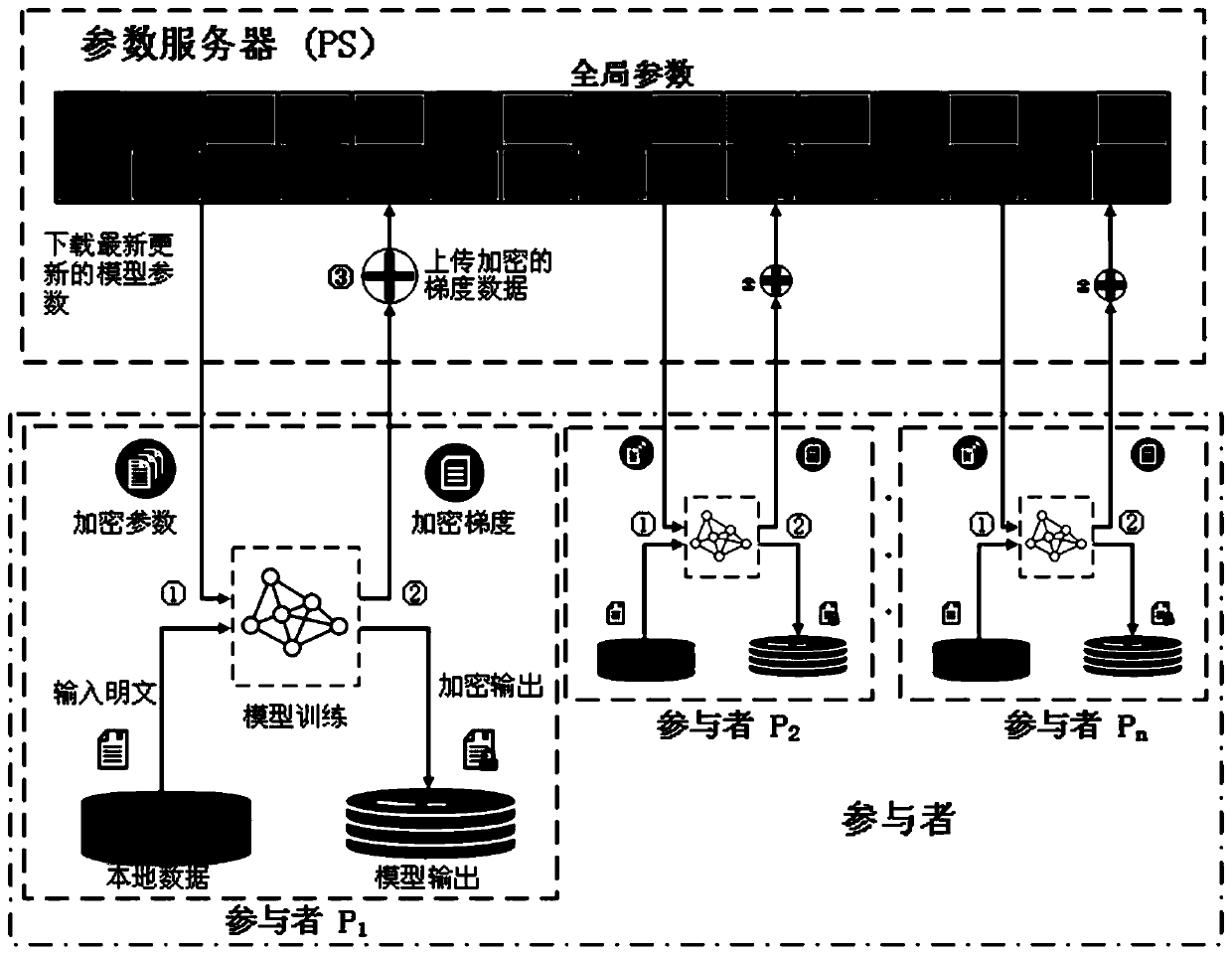
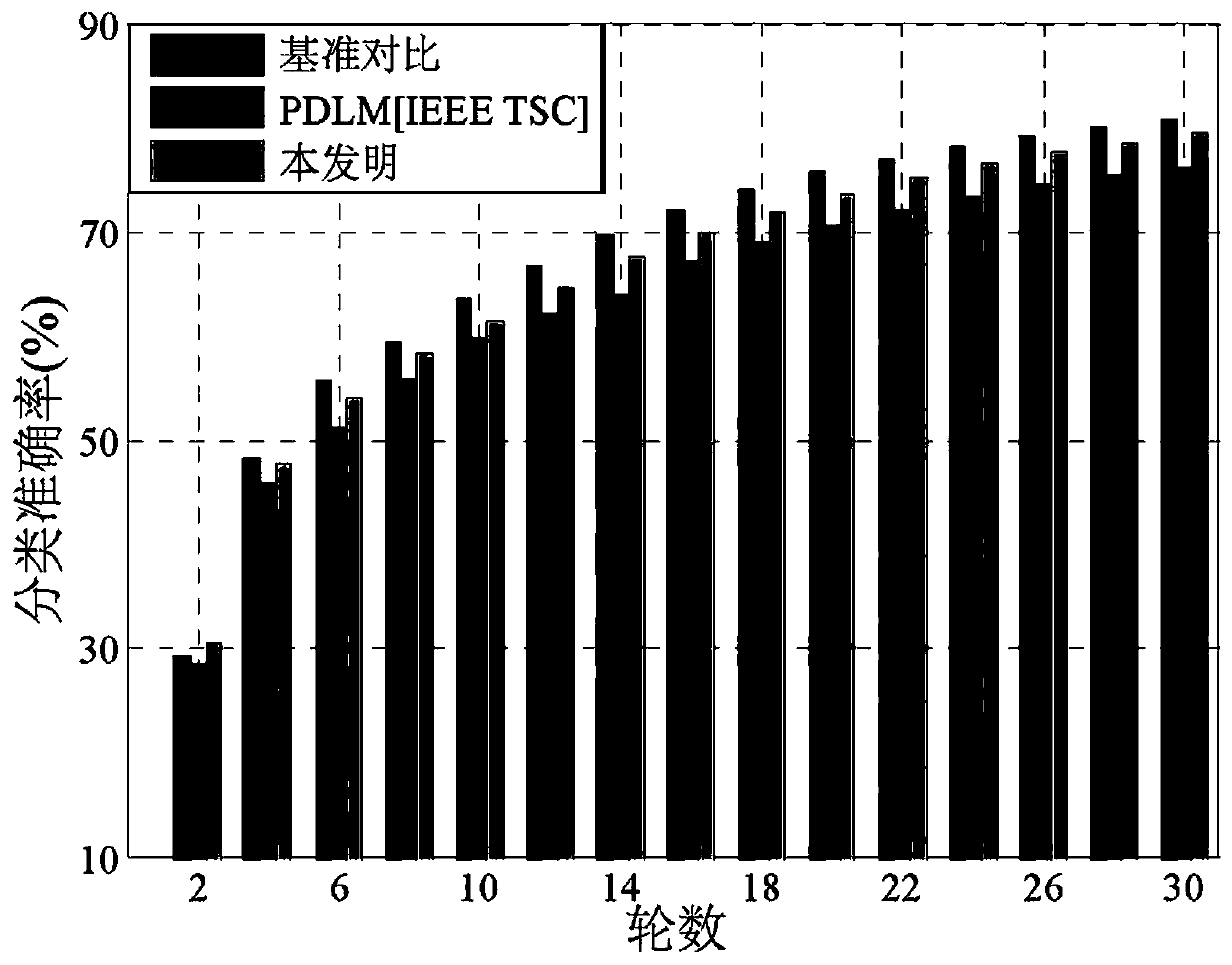
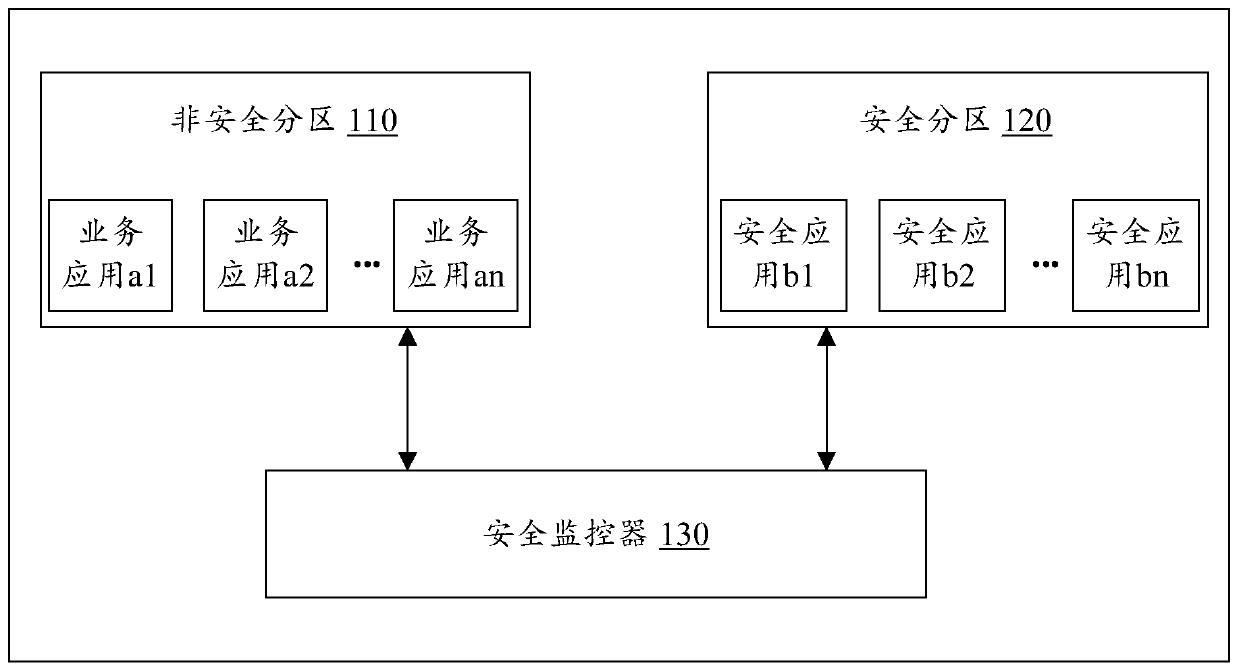
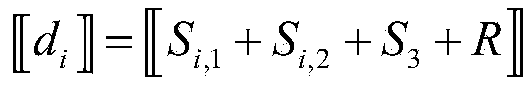Patents
Literature
87results about How to "Guaranteed data privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
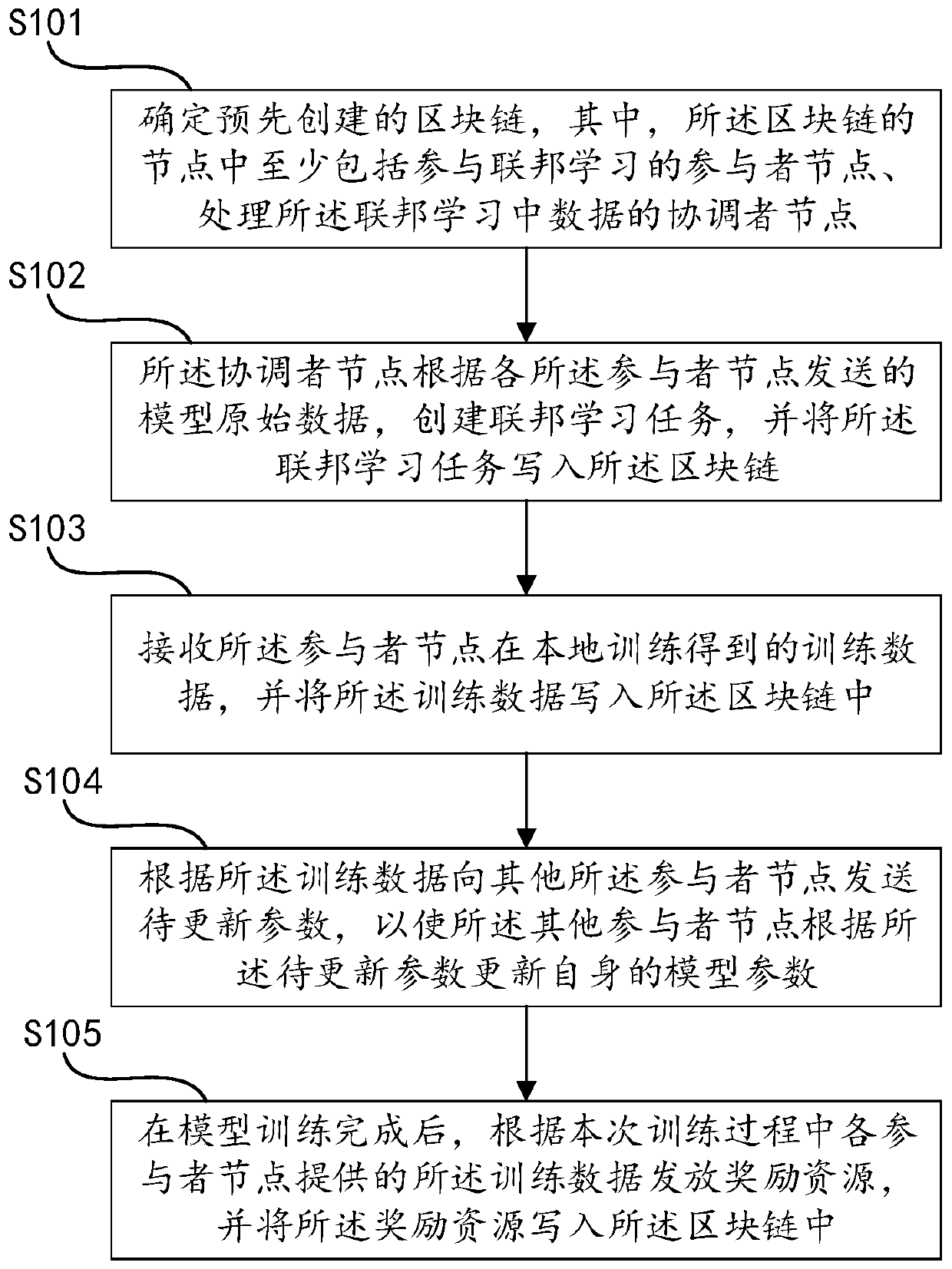
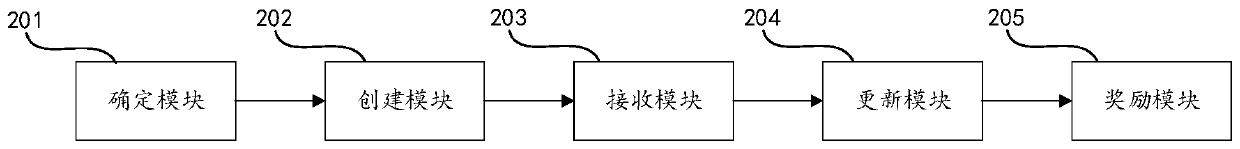
Federated learning method and device based on block chain
InactiveCN111125779ALow costReduce operating costsDigital data protectionMachine learningOriginal dataData operations
The invention discloses a federated learning method and device based on a block chain. The method comprises the steps: determining the block chain; enabling the coordinator node to create a federatedlearning task according to the model original data sent by each participant node; receiving training data obtained by local training of the participant nodes; sending the to-be-updated parameters to other participant nodes according to the training data, so as to enable the other participant nodes to update own model parameters according to the to-be-updated parameters; and after model training iscompleted, issuing reward resources according to training data provided by each participant node in the training process, and writing rewards into the block chain. Compared with a traditional mode, the mutual trust problem of all parties is effectively solved; all parties participating in federated learning negotiate together to generate a coordinator node, so that the transparency of the processis improved; federated learning whole-process data is recorded in a block chain, so that the traceability of data operation is ensured; all parties are encouraged to actively participate through rewarding resources, and the enthusiasm of participants is improved.
Owner:INSPUR ARTIFICIAL INTELLIGENCE RES INST CO LTD SHANDONG CHINA
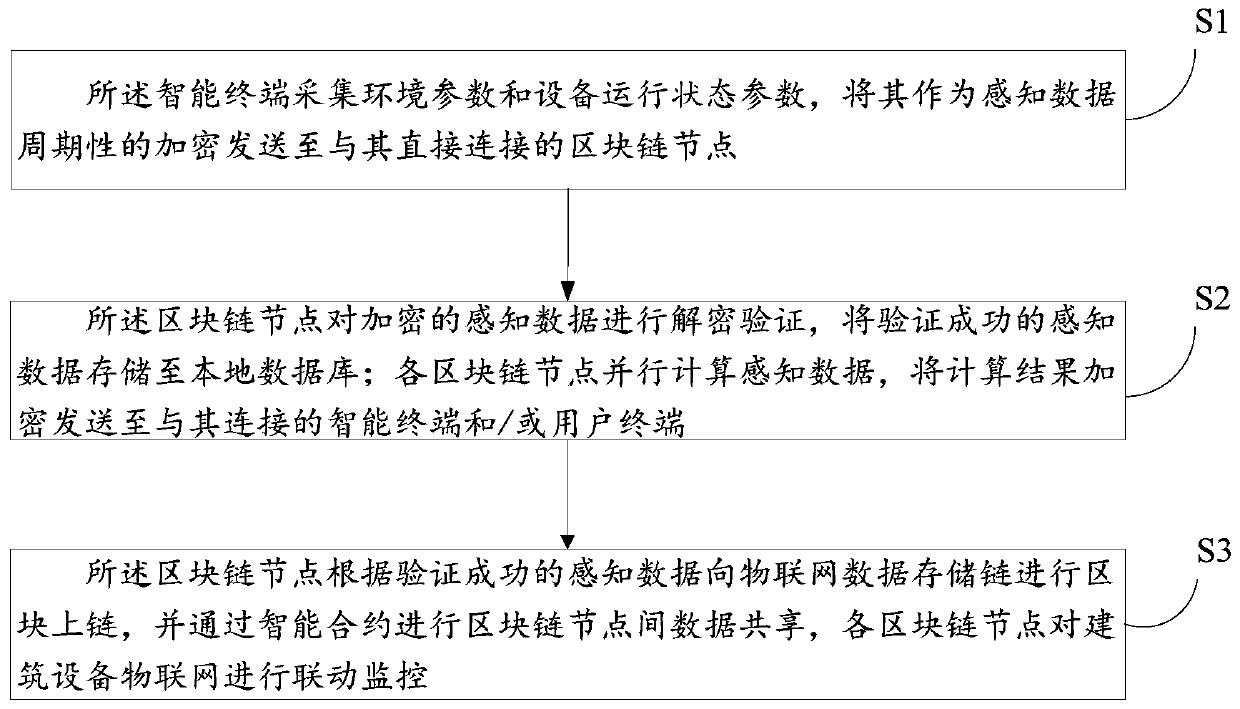
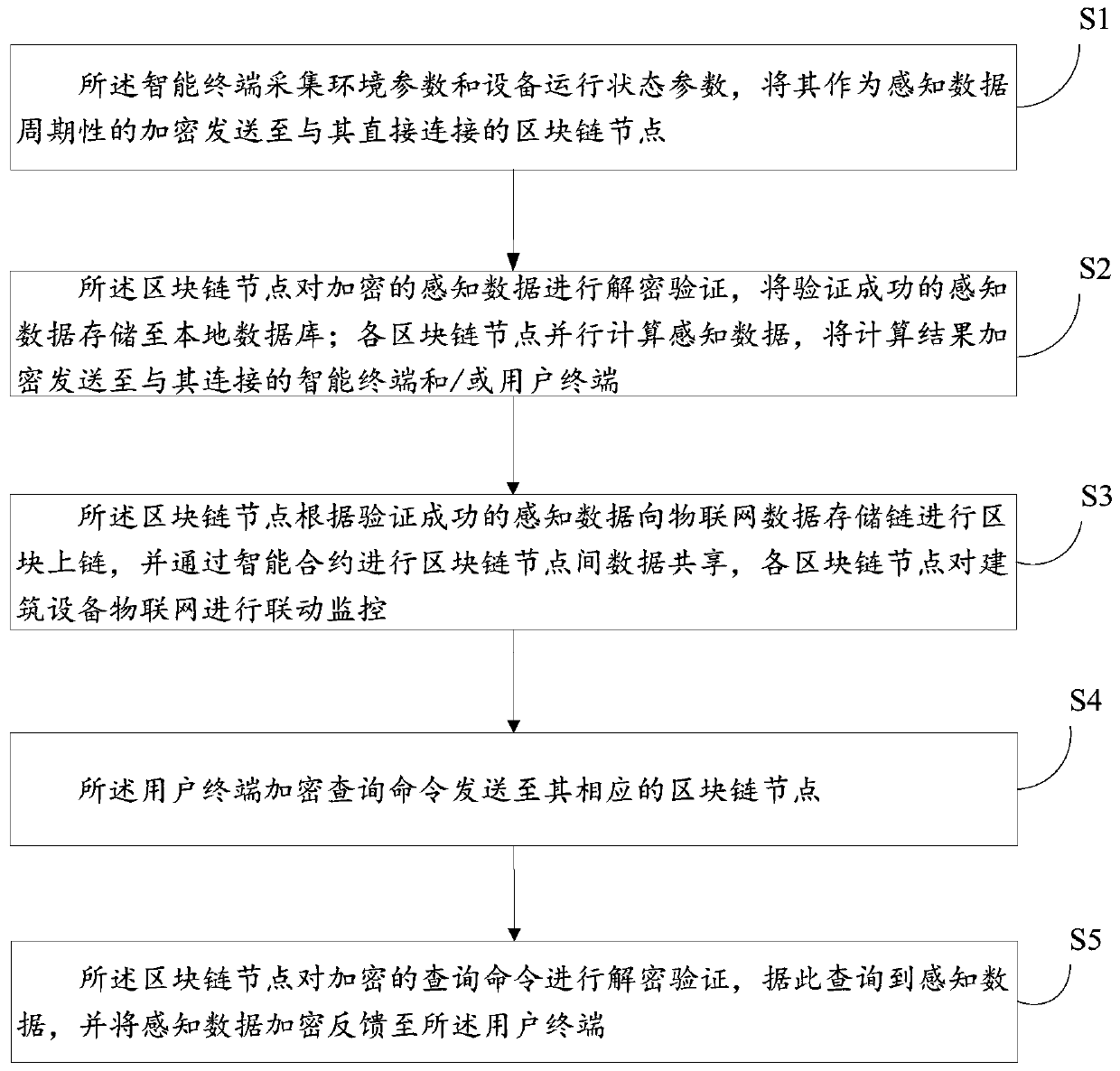
A flattened building equipment Internet of Things monitoring system and method based on a block chain
The invention discloses a flat building equipment Internet of Things monitoring system and method based on a block chain. The system comprises a plurality of block chain nodes, a plurality of intelligent terminals and a plurality of user terminals, the block chain nodes are deployed in a building subspace. wherein the blockchain nodes are respectively connected with a user terminal and intelligentterminals arranged in the building subspace, are in one-to-one correspondence with the building subspaces, and are configured to authenticate the intelligent terminals, decrypt the received intelligent terminal data, store and carry out parallel computing, and carry out data sharing among the blockchain nodes through an intelligent contract; the intelligent terminal is configured to collect environment parameters and equipment operation state parameters, and periodically encrypt and send the environment parameters and the equipment operation state parameters as sensing data to the blockchainnode directly connected with the intelligent terminal; and the user terminal is configured to perform data interaction with the block chain node.
Owner:SHANDONG JIANZHU UNIV
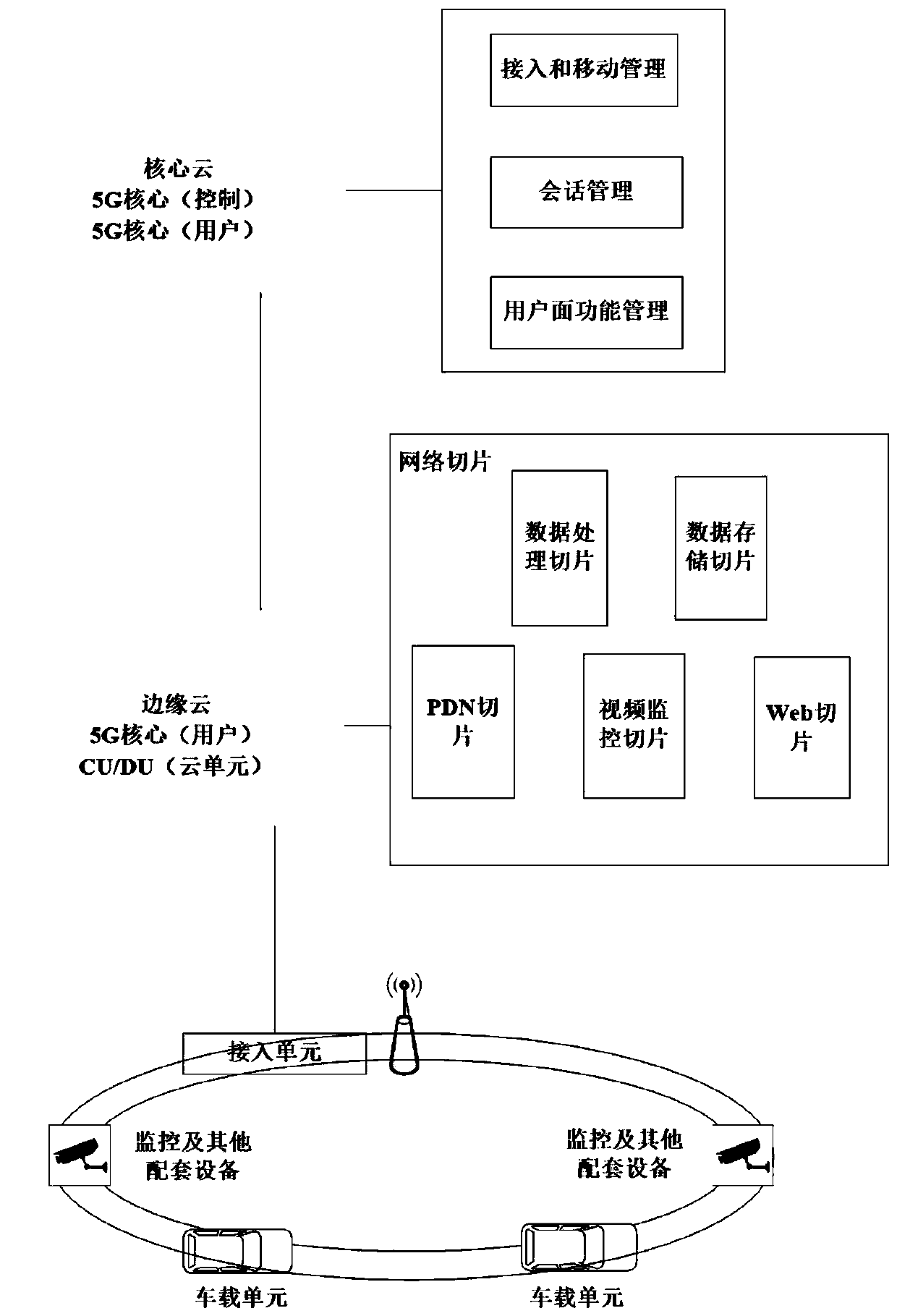
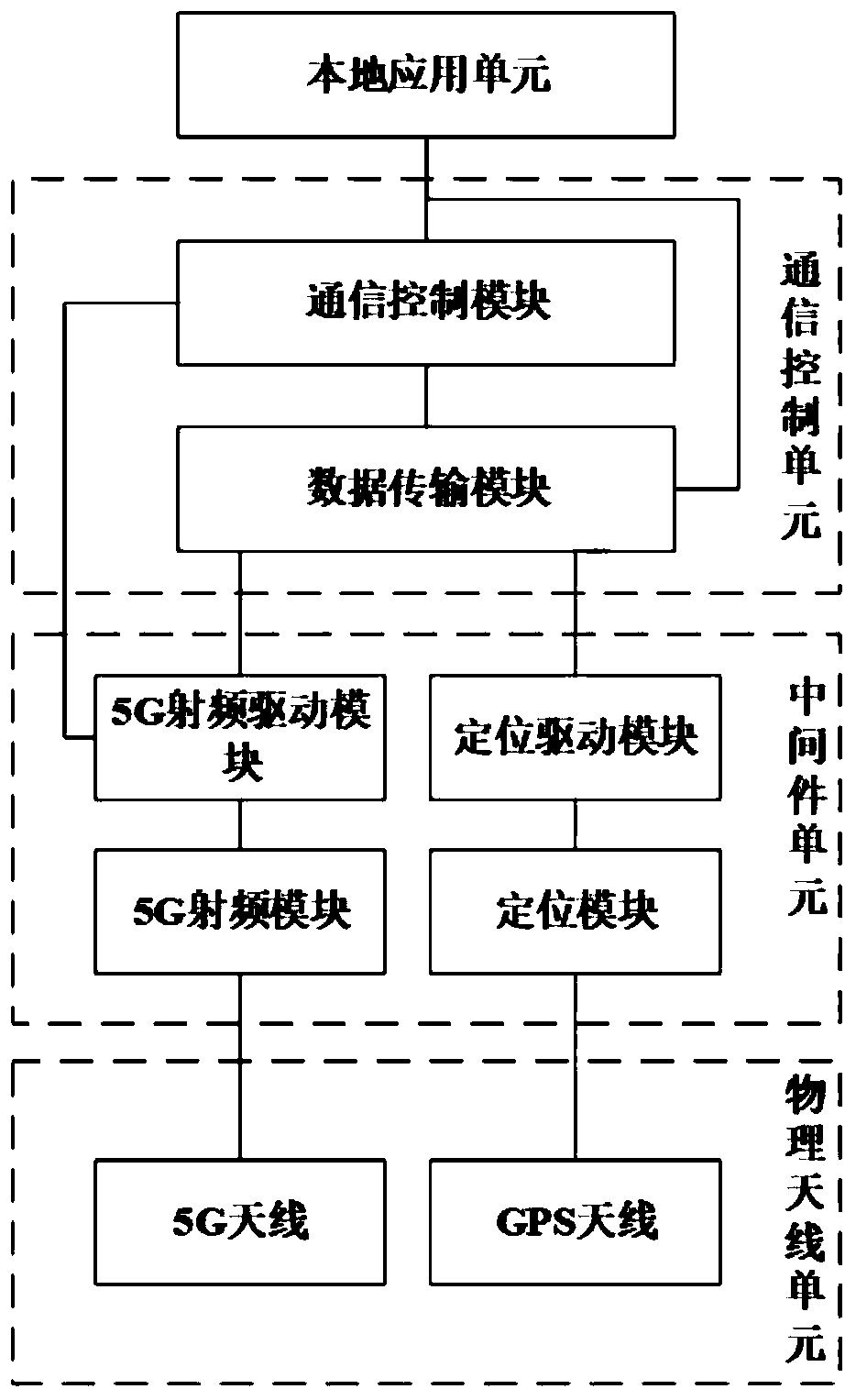
Vehicle-road communication test system and test method on 5G technology
InactiveCN109981771AReduce in quantityRealize data exchangeParticular environment based servicesVehicle-to-vehicle communicationNetwork terminationTime delays
The invention discloses a vehicle-road communication test system based on the 5G technology. A network element function is realized by adopting a virtualization and software mode; the network transmission rate can be obviously improved; concurrent network messages of dense network terminals in the Internet of Vehicles environment are ensured. the requirement of complex and huge Internet of Vehicles application on ultra-low time delay is met; the system cloud server adopts a virtualization technology. the number of servers is reduced; in a security aspect, multiple network slices are divided, asecurity isolation and height self-control special logic network is provided; network security is greatly improved, the information security of the Internet of Vehicles application and the data privacy of the user are ensured; the edge cloud server sinks a part of services to a network edge; the Internet of Vehicles application service processing speed based on roadside equipment can be remarkably increased, lower transmission delay is provided, the test platform can be used for verifying the actual effectiveness of the 5G technology applied to the Internet of Vehicles application, and support is provided for 5G-based Internet of Vehicles equipment layout and network design in a real scene.
Owner:CHANGAN UNIV
5G Internet of Things intrusion detection method and system based on federated transfer learning
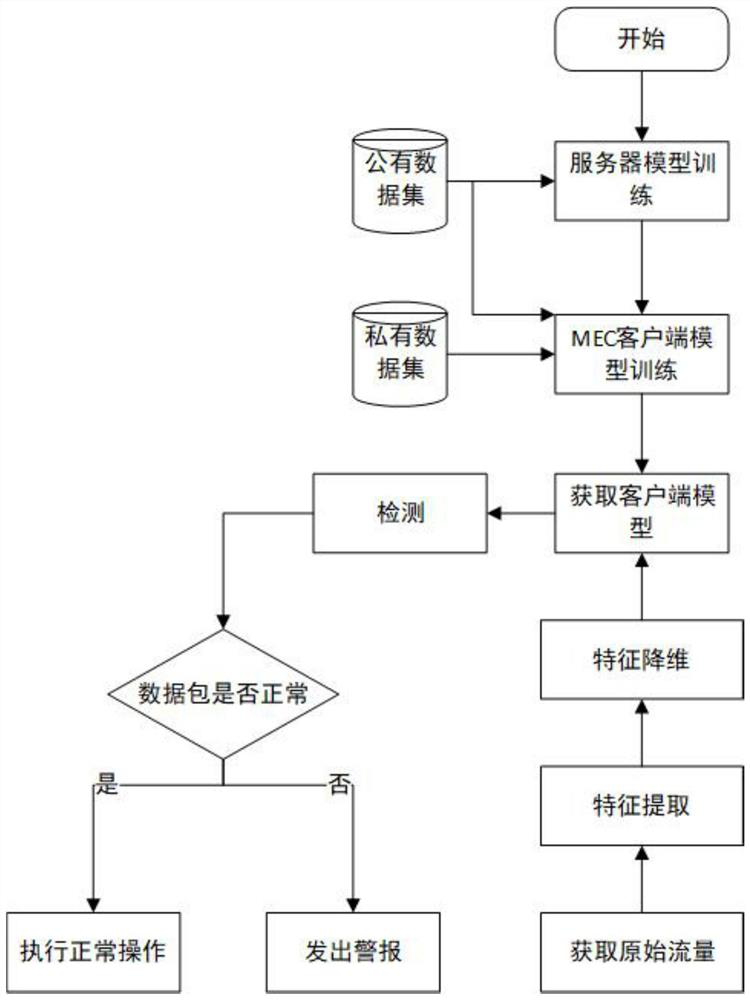
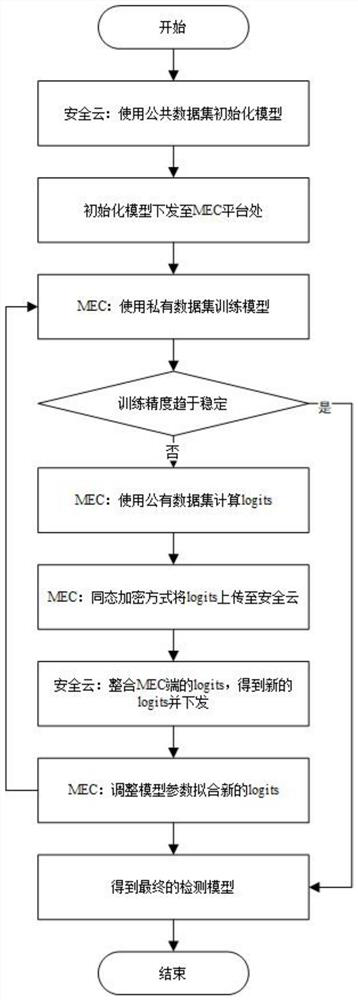
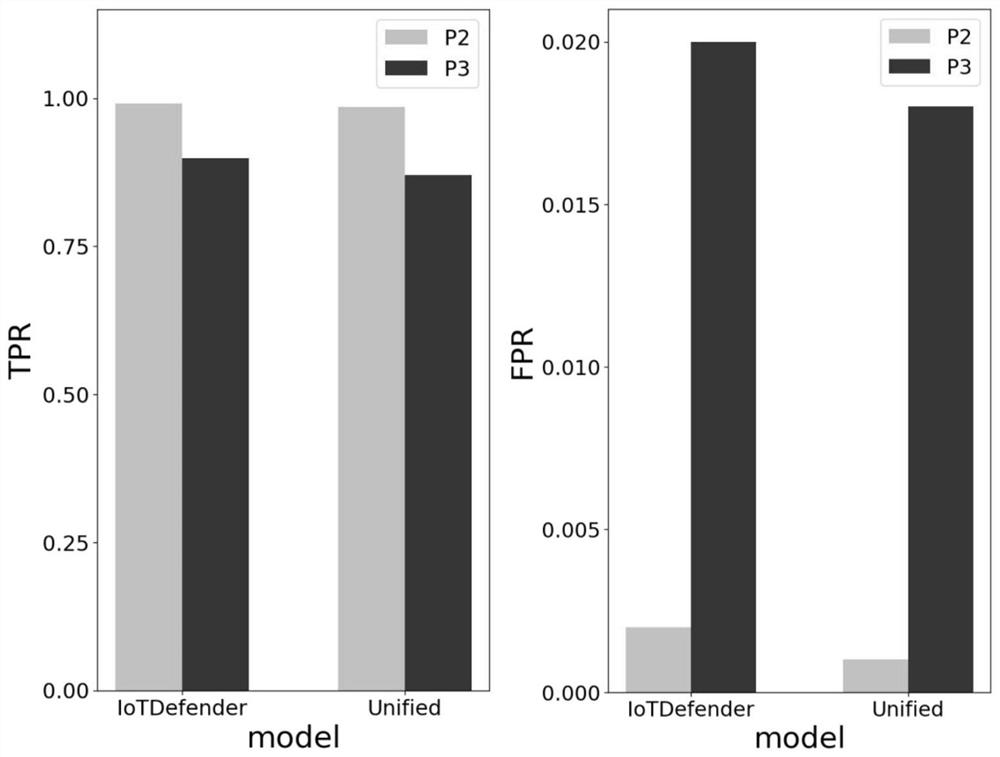
ActiveCN112203282AGuaranteed data privacyHierarchicalClosed circuit television systemsMachine learningData packFeature vector
The invention provides a 5G Internet of Things intrusion detection method and system based on federated transfer learning. The 5G Internet of Things intrusion detection method comprises the steps of:collecting a to-be-detected traffic in the Internet of Things, and acquiring a feature vector of an original data packet; and inputting the feature vector into a corresponding client model fm, k, andjudging whether the to-be-detected traffic is legal or not. According to the 5G Internet of Things intrusion detection, the federation transfer learning method in the 5G Internet of Things IDS is proposed for the first time, data from different Internet of Things can be safely aggregated, a good intrusion detection model for each Internet of Things is realized through knowledge transfer and sharing, the 5G Internet of Things intrusion detection method can be conveniently and safely applied to various different Internet of Things, and the method has very strong generalization ability and is suitable for popularization and application. Compared with an existing method, abnormal traffic can be detected more accurately, and unknown attacks can be detected more effectively.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Mobile malware detection method oriented on network encryption flow
ActiveCN107749859AMalicious Mobile Application Detection PracticalReduce operating loadTransmissionMobile malwareComputer terminal
The invention relates to a mobile malware detection method oriented on network encryption flow. By means of the mobile malware detection method oriented on the network encryption flow, whether the encryption flow generated by a mobile application is attack flow or not can be effectively analyzed; but, the existing method is mainly for plaintext flow to analyze; therefore, the detection method disclosed by the invention is an effective supplement of the existing research method; mobile malware detection of a network layer is relatively practical; simultaneously, according to the detection method disclosed by the invention, only the network flow is used as the input; an additional program does not need to be installed on a mobile terminal; a network flow content also does not need to be deeply analyzed; therefore, the operating load of the mobile terminal is lightened; furthermore, the data privacy of mobile users is ensured; and thus, the mobile malware detection method oriented on thenetwork encryption flow is convenient for practical deployment and use.
Owner:NANJING UNIV OF POSTS & TELECOMM
Security data storage and computing method based on Internet of Things fog computing-edge computing
ActiveCN110213036AProtection securityEnsure safetyKey distribution for secure communicationCommunication with homomorphic encryptionEncryptionData store
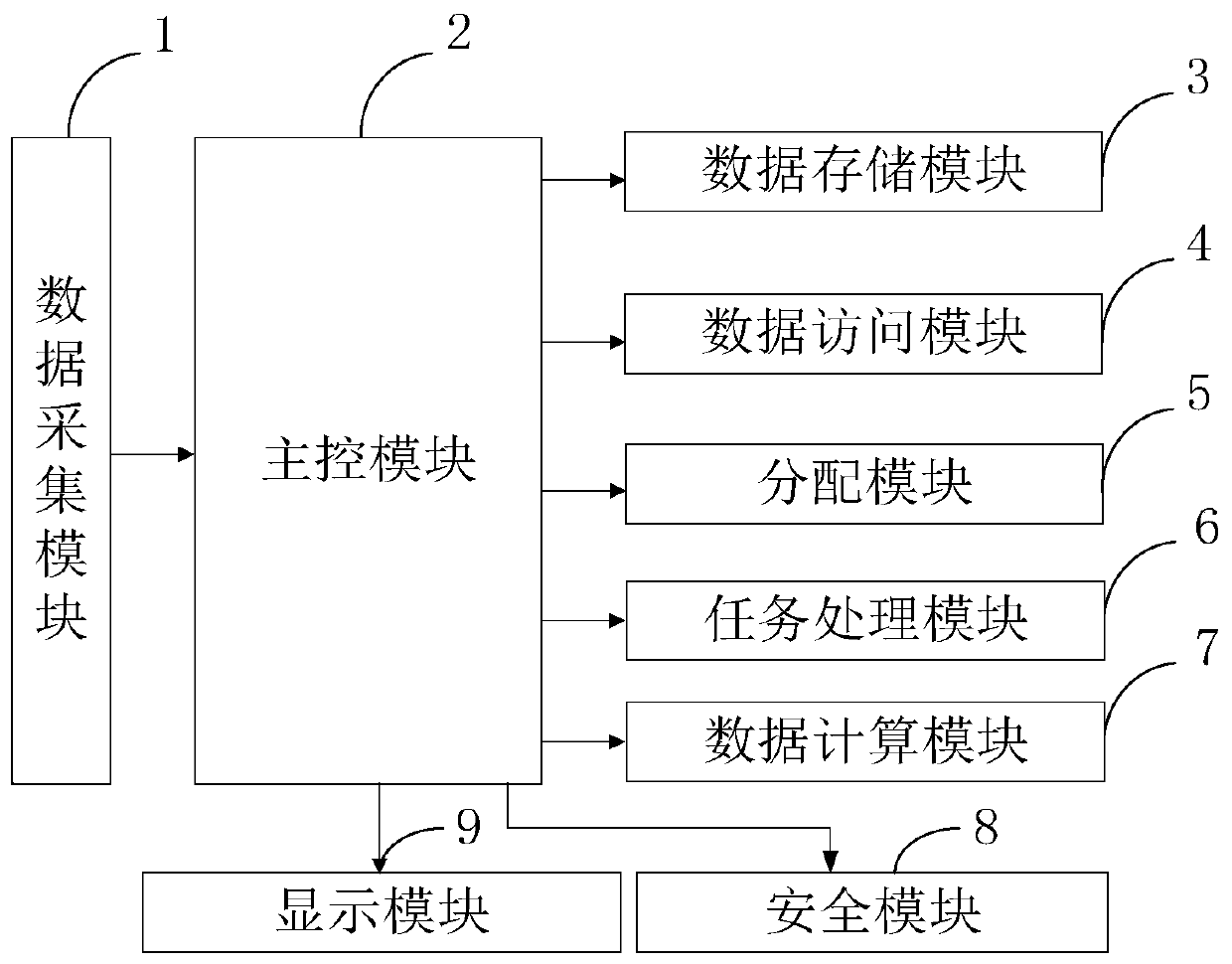
The invention belongs to the technical field of data storage and computing, and discloses a security data storage and computing method based on Internet of Things fog computing-edge computing. Localized Epsilon differential privacy is achieved through the data collection module, data encryption is achieved at fog nodes, and the safety of local area data is protected; the data storage module is used for storing encrypted data and protecting the privacy of the data on the fog server; the data access module is used for realizing data security decryption and protecting data information security sharing; the distribution module uploads own distribution task to the scheduler, so that the privacy of the computing terminal can be effectively protected; meanwhile, the computing tasks are decomposedthrough the task processing module, and parallel computing is conducted on the multiple decomposed computing subtasks. According to the invention, while the processing speed of the computing task isimproved, the data security and data privacy of the whole system are ensured.
Owner:XIDIAN UNIV +1
Private data intersection acquisition method and device, electronic equipment and storage medium
PendingCN112699386AImprove efficiencyImprove securityDigital data protectionMachine learningTheoretical computer scienceComputation process
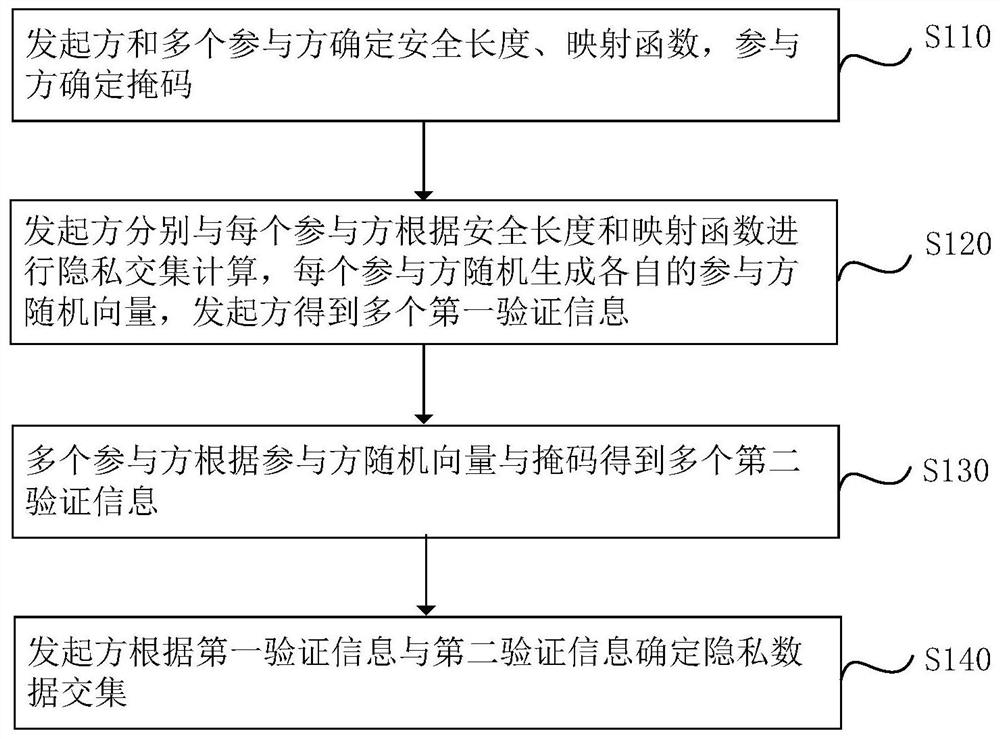
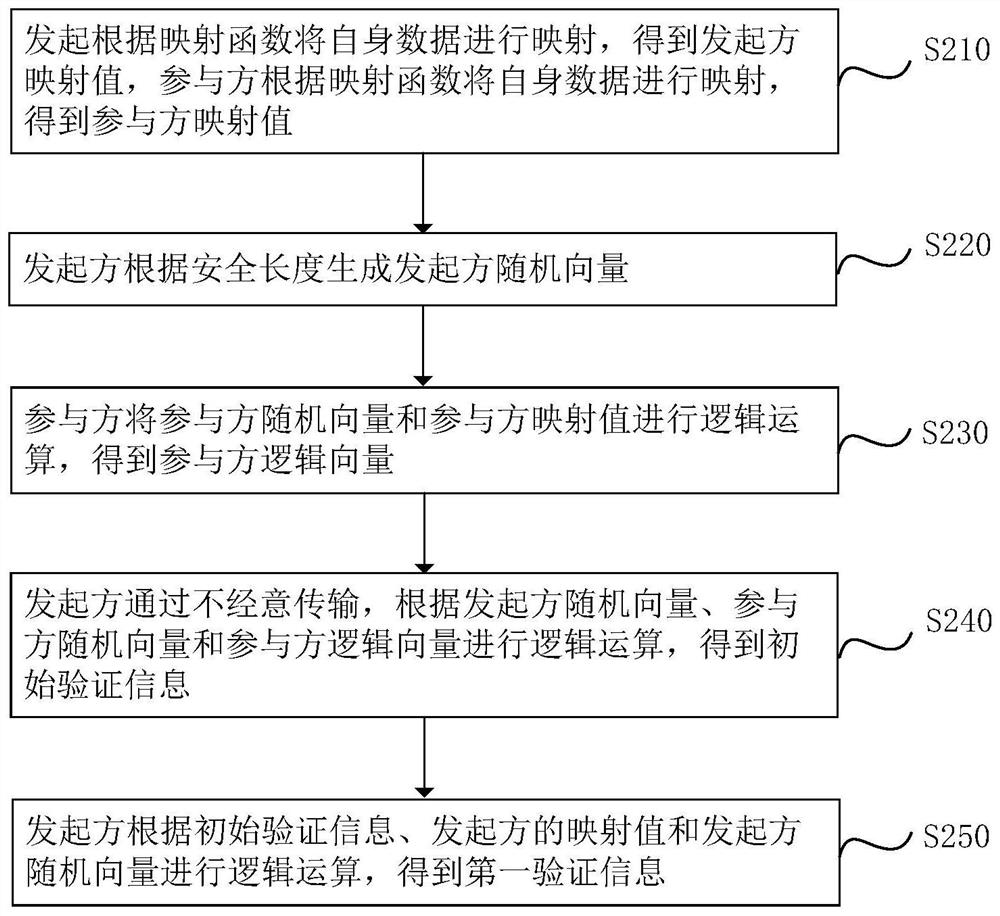
The invention relates to a private data intersection acquisition method and device, electronic equipment and a storage medium, and the method comprises the steps: an initiator and a plurality of participants determine a safety length and a mapping function, and the participants determine a mask; an initiator performs privacy intersection calculation with each participant according to the security length and the mapping function, each participant randomly generates a respective participant random vector, and the initiator obtains a plurality of pieces of first verification information; the plurality of participants obtains a plurality of pieces of second verification information according to the participant random vectors and the masks; and the initiator determines a private data intersection according to the first verification information and the second verification information. The problems of privacy leakage of participants and relatively low data security caused by formation of a multi-party intersection based on pairwise comparison in related technologies are solved, the efficiency and security of a privacy data intersection calculation process are improved, and the data privacy of a user is ensured.
Owner:HANGZHOU QULIAN TECH CO LTD
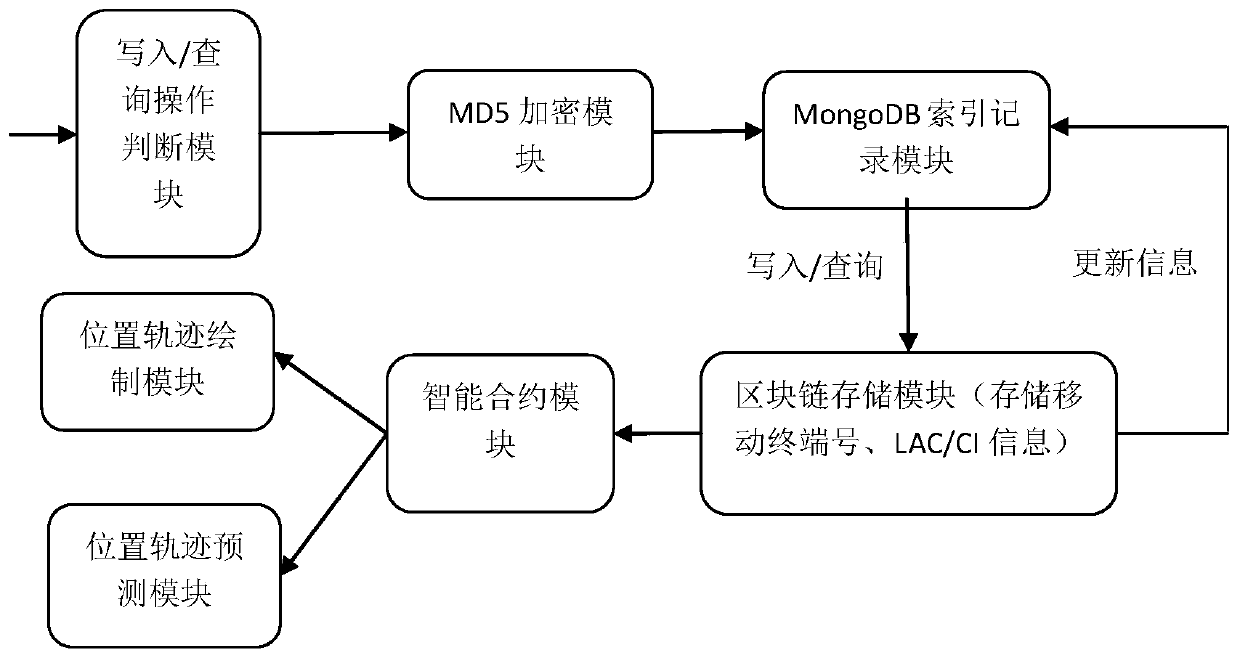
Mobile terminal position track monitoring system and method based on block chain
InactiveCN110210250AGuaranteed data privacyImprove monitoring efficiencyDigital data protectionMonitoring systemMD5
The invention particularly relates to a mobile terminal position track monitoring system and method based on a block chain. The mobile terminal position track monitoring system based on a block chaincomprises a write-in / query operation judgment module, an MD5 encryption module, a MongoDB index recording module, a block chain storage module, an intelligent contract module, a position track drawingmodule and a position track prediction module, wherein the write-in / query operation judgment module is connected to the block chain storage module through the MD5 encryption module and the MongoDB index recording module in sequence, and the block chain storage module is connected to the position track drawing module and the position track prediction module through the intelligent contract module.The method has the advantages that the LAC / CI data generated when the user uses the communication service is accessed based on the block chain technology, the key information such as the number of the mobile terminal of the user is encrypted by combining the MD5 message digest algorithm, and the user position track monitoring efficiency is improved on the premise that the privacy of the user datais effectively guaranteed.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT
Joint training method and device for service model
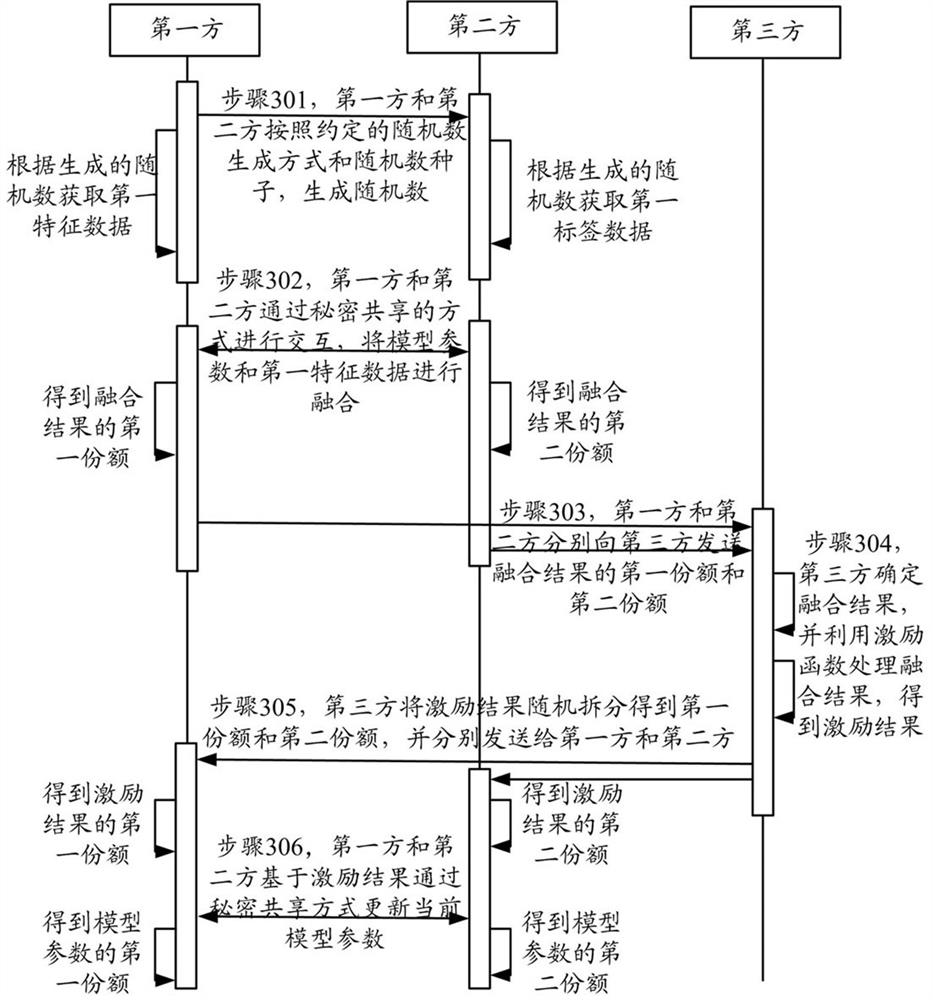
ActiveCN111737755AReduce complexityReduce operational complexityRandom number generatorsDigital data protectionPrivacy protectionFeature data
The embodiment of the invention provides a joint training method and device for a service model, and the method and device enable the nonlinear complex operation to be distributed to a third party forprocessing in multi-party safety calculation, and greatly reduce the complexity of the joint training of a plurality of service parties for a nonlinear model. Meanwhile, each service party holding the feature data or the label data of the training sample generates a preset number of random numbers in an agreed random number generation mode, the sample data of the training samples in one-to-one correspondence in sequence is obtained, the consistency of the data is kept, and since the third party does not participate in the random number generation process, other service parties effectively guarantee data privacy for the third party. And other service parties interact with each other through a secret sharing method, so that data privacy is ensured among the service parties. In conclusion, according to the method, on the basis of privacy protection, the operation complexity of a nonlinear model jointly trained by a plurality of service parties is greatly reduced.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
Privacy protection method and device for Wifi fingerprint positioning
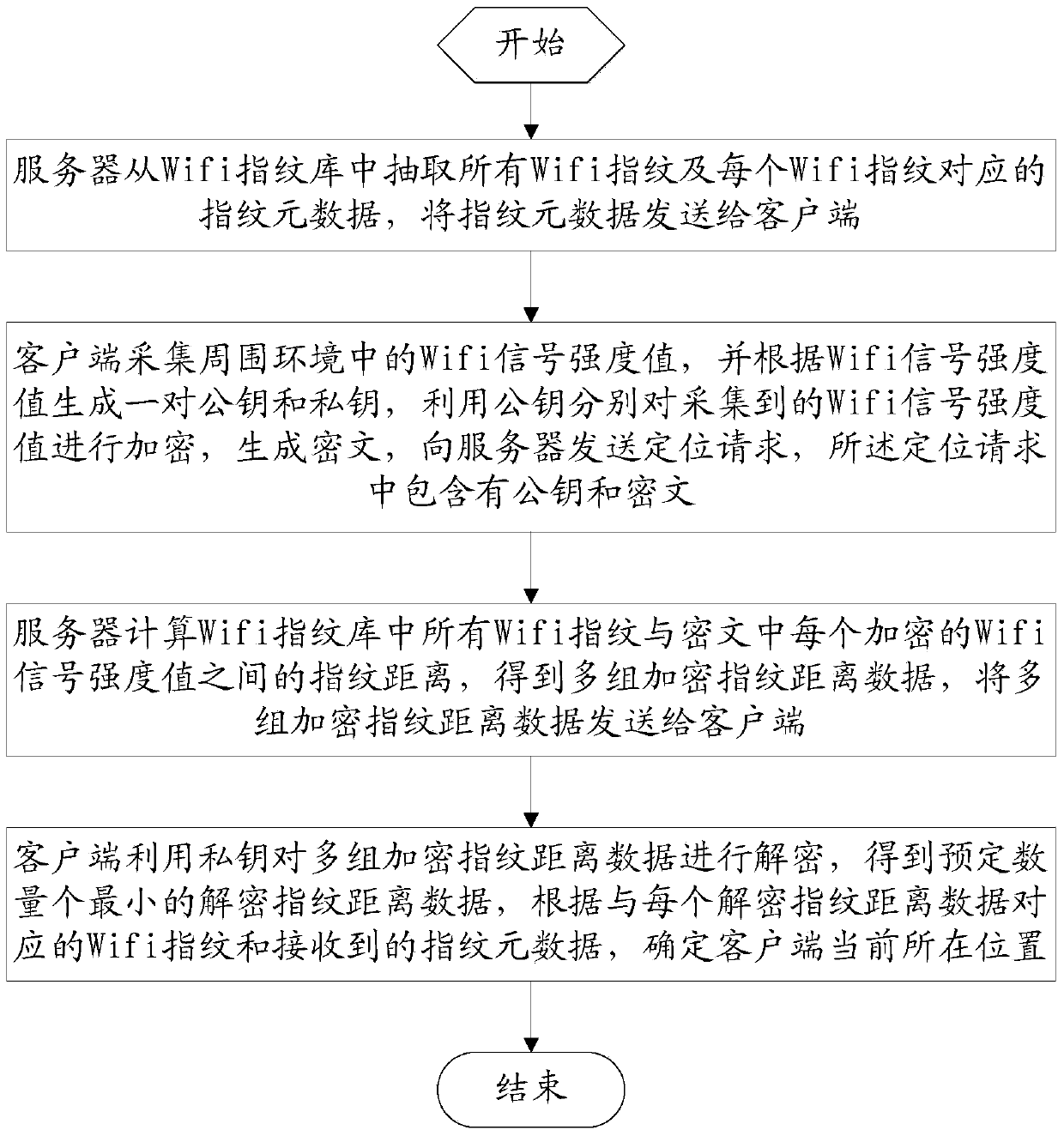
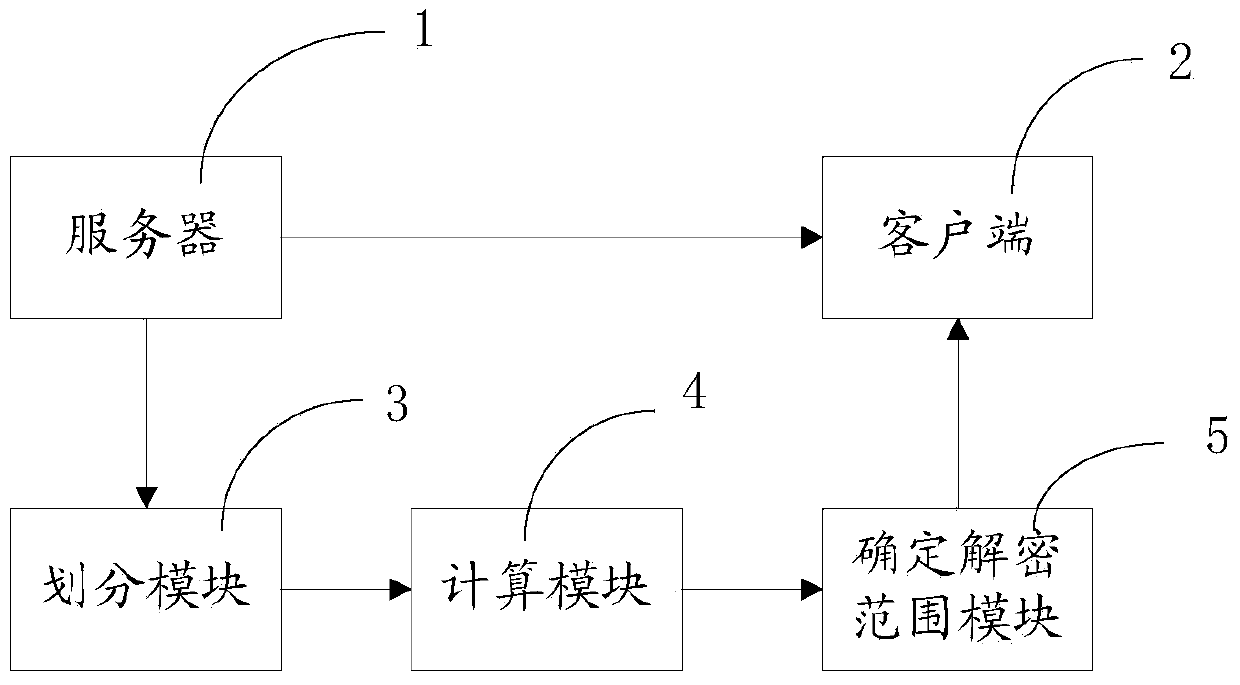
InactiveCN103442335AAvoid privacyGuaranteed positionWireless commuication servicesSecurity arrangementPrivacy protectionEngineering
The invention relates to a privacy protection method and device for Wifi fingerprint positioning. The privacy protection method for Wifi fingerprint positioning comprises the following steps that a server extracts all the Wifi fingerprints and fingerprint metadata; a client terminal collects Wifi signal intensity values in the peripheral environment and generates a public key and a private key according to the asymmetrical encryption algorithm, encryption is respectively conducted on the collected Wifi signal intensity values by the public key and a positioning request is sent to the server; the server calculates the fingerprint distance between all the Wifi fingerprints and each encrypted Wifi signal intensity value and transmits multiple sets of encrypted fingerprint distance data to the client terminal; the client terminal uses the private key to decrypt the multiple sets of the encrypted fingerprint distance data, and determines the current location of the client terminal according to the Wifi fingerprint corresponding to each decrypted fingerprint distance datum and the received fingerprint metadata. The privacy protection method and device for Wifi fingerprint positioning solves the privacy problem in an existing WiFi fingerprint positioning technology, and can protect the location privacy of a user and the data privacy of a service provider.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
Secure transaction execution method based on smart contract
ActiveCN113222606AGuaranteed legal effectSolve financial problemsPayment protocolsTransaction dataFinancial transaction
The invention discloses a secure transaction execution method based on a smart contract. The method comprises the following steps: deploying a blockchain node service; receiving the original transaction voucher information for uplink storage; enabling each transaction processing node to sign a smart contract and deploy the smart contract to the blockchain; recording the encrypted transaction voucher information on a transaction data alliance chain based on the smart contract; judging whether a contract is deployed on a blockchain for a current smart contract, analyzing transaction parameters corresponding to the smart contract, checking the identity compliance, security and authority of the transaction parameters of the smart contract, packaging the smart contract, and enabling an execution end to call the smart contract and execute the smart contract; sending the effective consensus information to other transaction processing nodes, determining that the smart contract is effective, and performing uplink evidence storage. According to the invention, the information security is ensured, the requirements of the bank for transaction checking and account checking and clearing are met, the processing efficiency of each link in the transaction process is improved, the default risk caused by human factors is reduced, and the cost reduction and benefit increase of an industrial chain are promoted.
Owner:中企链信(北京)科技有限公司
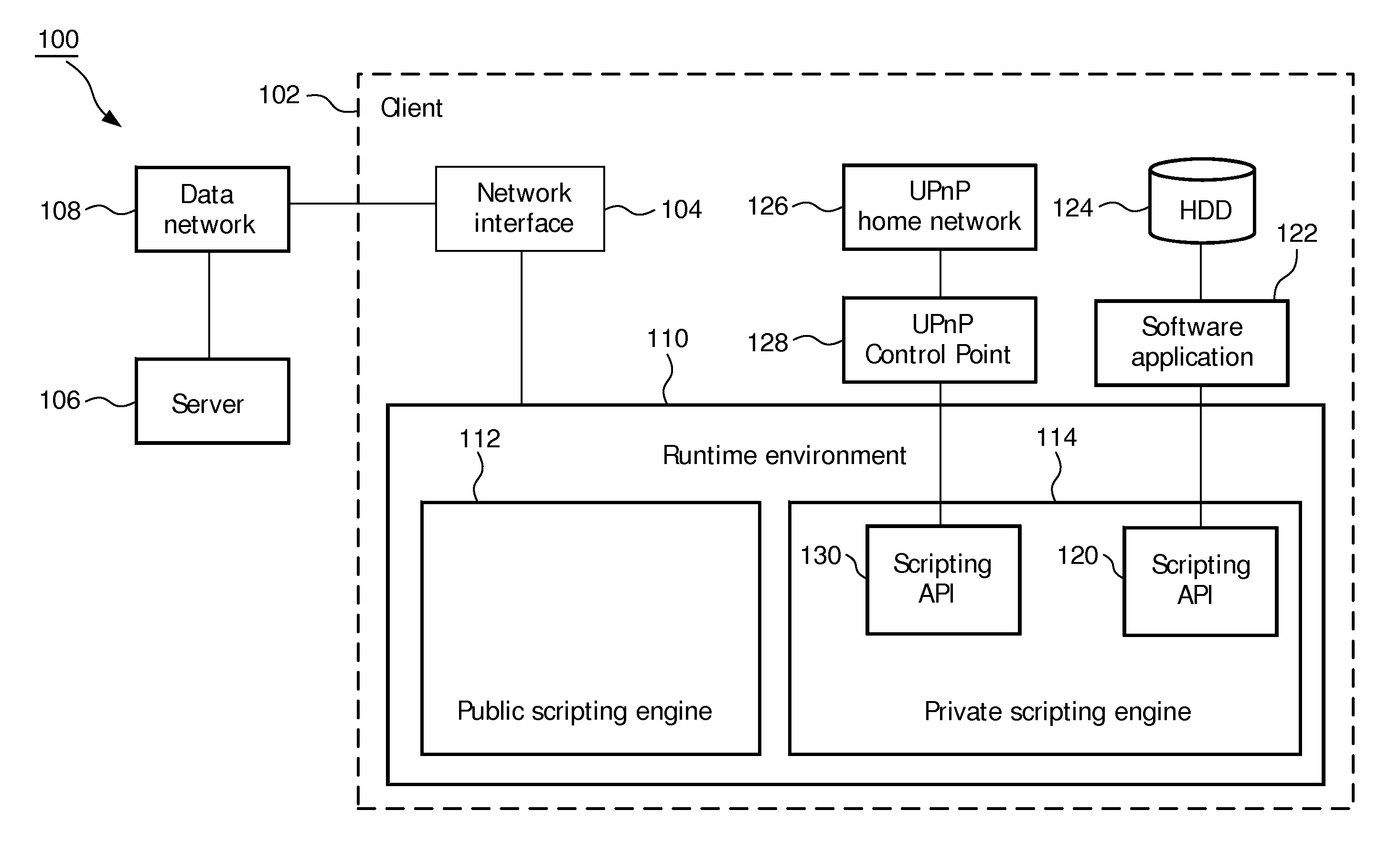
Browser with dual scripting engine for privacy protection
ActiveUS9258136B2Guaranteed data privacyGuaranteed privacyDigital data processing detailsAnalogue secracy/subscription systemsData processing systemPrivacy protection
A data processing system has a browser with scripting engine means for executing a script. The scripting engine means implements a public scripting engine and a private scripting engine. The browser is configured to have the script executed by the public scripting engine if the script does not require access to a pre-determined resource at the system. The browser is configured to have the script executed by the private scripting engine if the script requires access to the pre-determined resource. Only the private scripting engine has an interface for enabling the script to access the predetermined resource. The scripting engine means is configured to prevent the private scripting engine from communicating data to the public scripting engine or to a non-approved server external to the data processing system.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
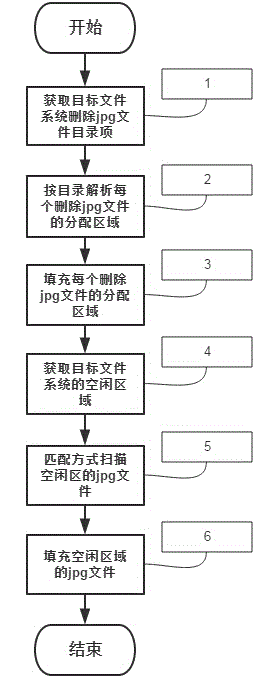
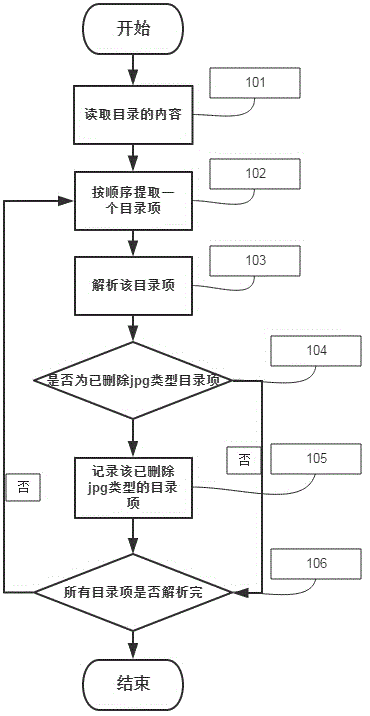
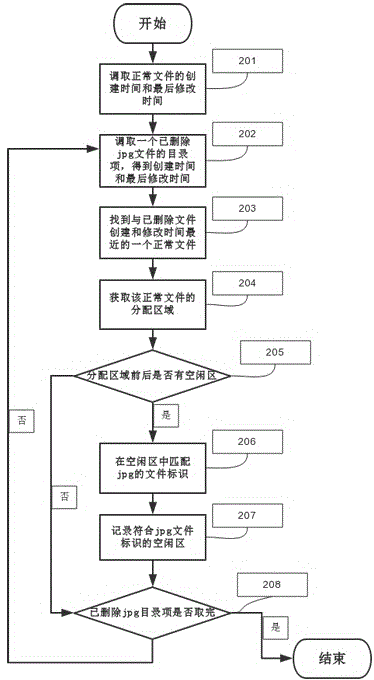
Method for completely removing deleted jpg format in FAT 32 document system
ActiveCN104699794AGuaranteed data privacyPrevent malicious theftSpecial data processing applicationsPP-formatDatabase
The invention discloses a method for completely removing a deleted jpg format in a FAT 32 document system. The method comprises the following steps: S1: Searching all directory entries of the deleted jpg format document; S2: analyzing the directory entries and obtaining a distribution area of the jpg document; S3: writing in and filling empty value in the distribution zone; S4: obtaining a clear area position; S5: scanning and matching the clear area, and finding out fragment data; S6: writing in empty value and filling. Through a bottom layer, the method can analyze the deleted jpg document in the FAT 32 document system by, and find out the fragment data position of the deleted jpg document. The method ensures the safety of the normal jpg document while completely removes the jpg formatted document. Through the jpg document, the jpg document fragments in the clear area are removed for the second time, and thereby all fragment data are removed at the maximum degree, the public privacy is guaranteed, and malicious stealing behavior specific to private data is prevented.
Owner:MWH TECH LLC
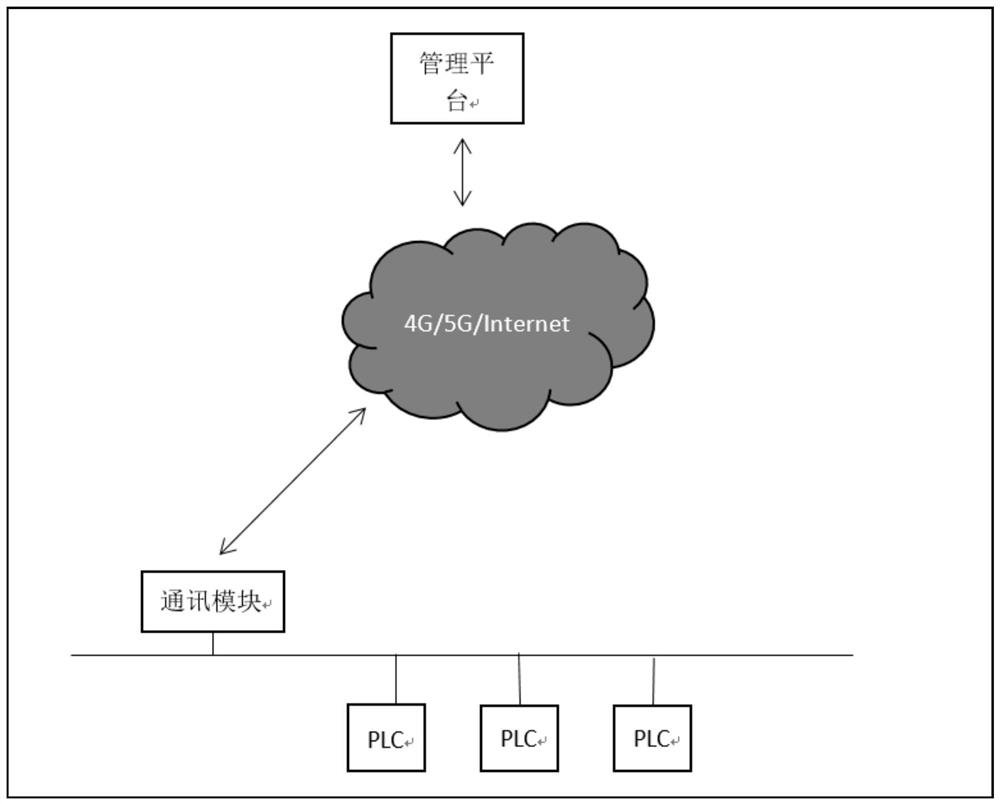
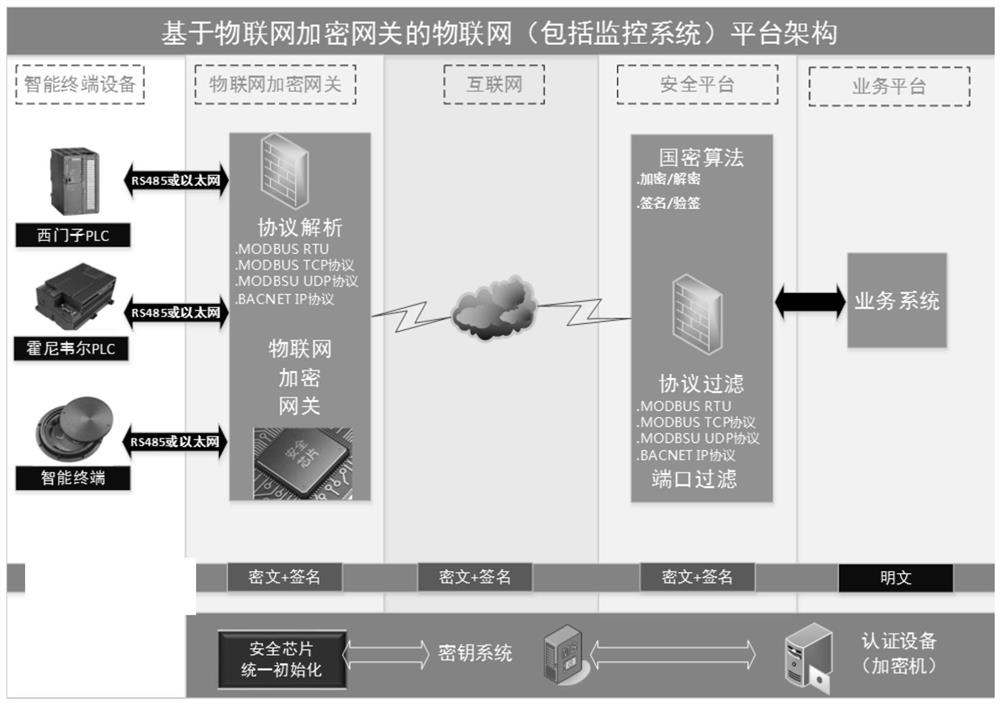
Internet of Things system based on Internet of Things encryption gateway
PendingCN112954048AGuaranteed data privacyGuaranteed secure data transmissionParticular environment based servicesUser identity/authority verificationProtocol for Carrying Authentication for Network AccessData security
The invention provides an Internet of Things system based on an Internet of Things encryption gateway. The Internet of Things system comprises an intelligent terminal device used for sending to-be-transmitted data to the Internet of Things encryption gateway; the Internet of Things encryption gateway is used for judging whether a protocol supported by the intelligent terminal equipment is an unsafe protocol, if the protocol is the unsafe protocol, refusing to accept data sent by the intelligent terminal equipment, and if the protocol is the safe protocol, analyzing the data sent by the intelligent terminal equipment by using the protocol supported by the intelligent terminal equipment to obtain to-be-transmitted data, sending the to-be-transmitted data to the Internet, or encrypting and signing the to-be-transmitted data, generating processed data, and sending the processed data to the Internet. The Internet is used for transmitting data to be transmitted or processed data; the security platform is used for receiving the to-be-transmitted data or performing signature verification operation on the processed data, performing decryption operation on the processed data to obtain the to-be-transmitted data after the signature verification is passed, and sending the to-be-transmitted data to the service platform; and the service platform is used for processing to-be-transmitted data.
Owner:BEIJING GAS GRP
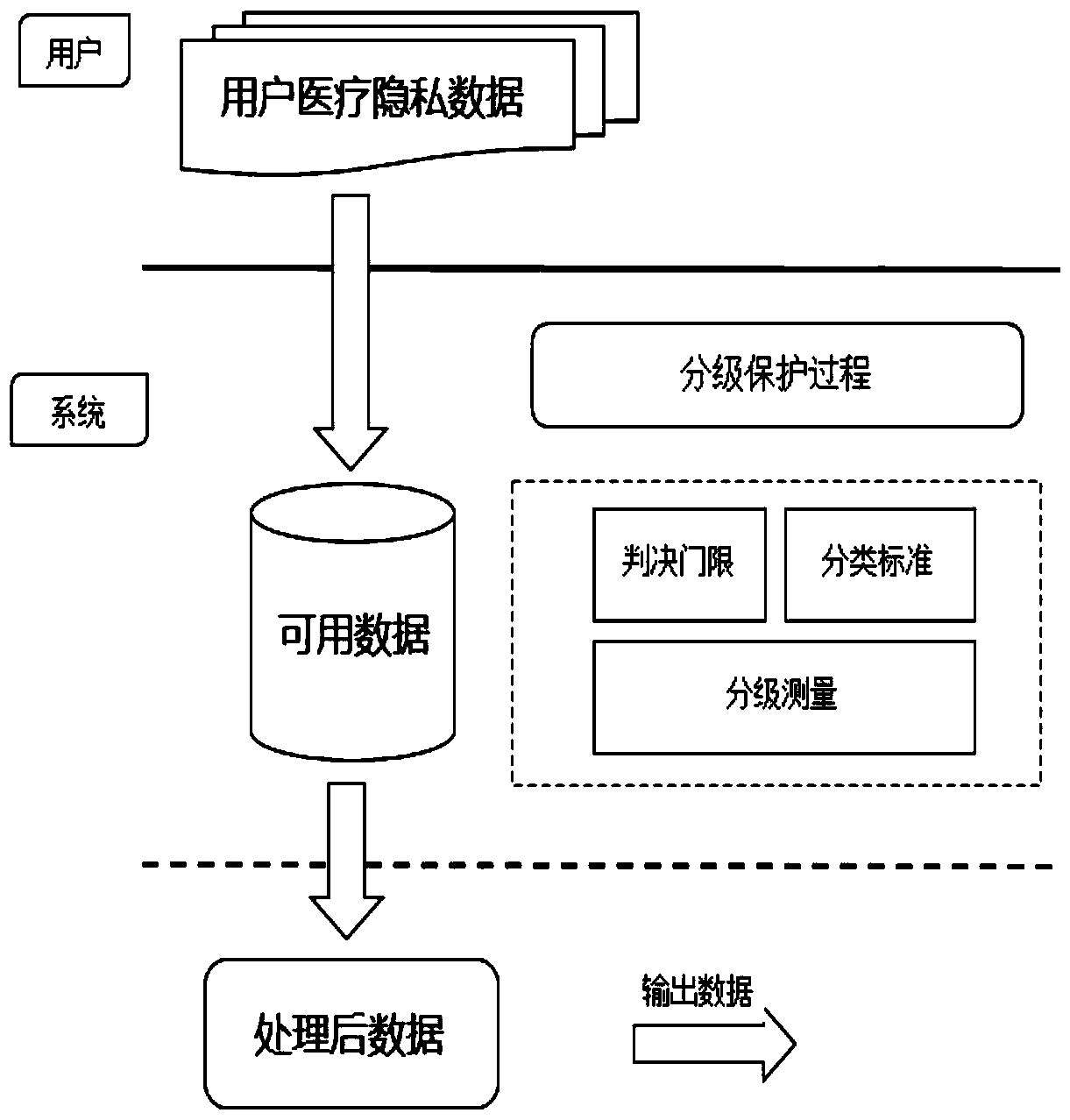
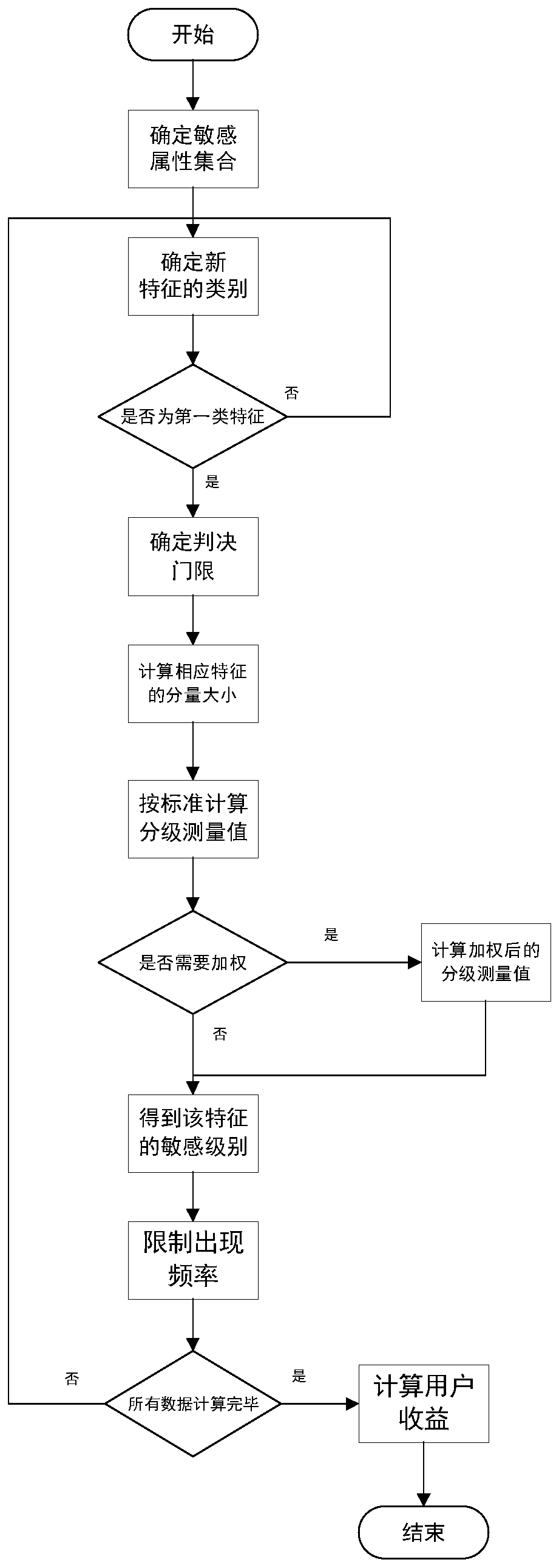
Privacy data hierarchical protection method
ActiveCN110020546ARealize hierarchical protectionGuaranteed data privacyDigital data protectionPrivacy protectionService quality
The invention provides a privacy data hierarchical protection method. Most of existing models are similar to all private data, the problem of privacy sensitivity degree is not considered, the privacydegree is regarded as a measure in the privacy protection process, the sensitivity level of the privacy data is calculated, and the occurrence frequency of the data with the high sensitivity degree islimited to a low value, so that higher-degree protection is provided for the privacy data with the high sensitivity degree. Furthermore, starting from the perspective of the user, the income which can be obtained by the user is directly calculated after the privacy is protected in a grading manner, and the grading protection result of the privacy is associated with the service quality and privacyloss of the user, so that the user can obtain satisfactory service from the system, and meanwhile, the data privacy of the user is guaranteed.
Owner:NANJING UNIV OF POSTS & TELECOMM
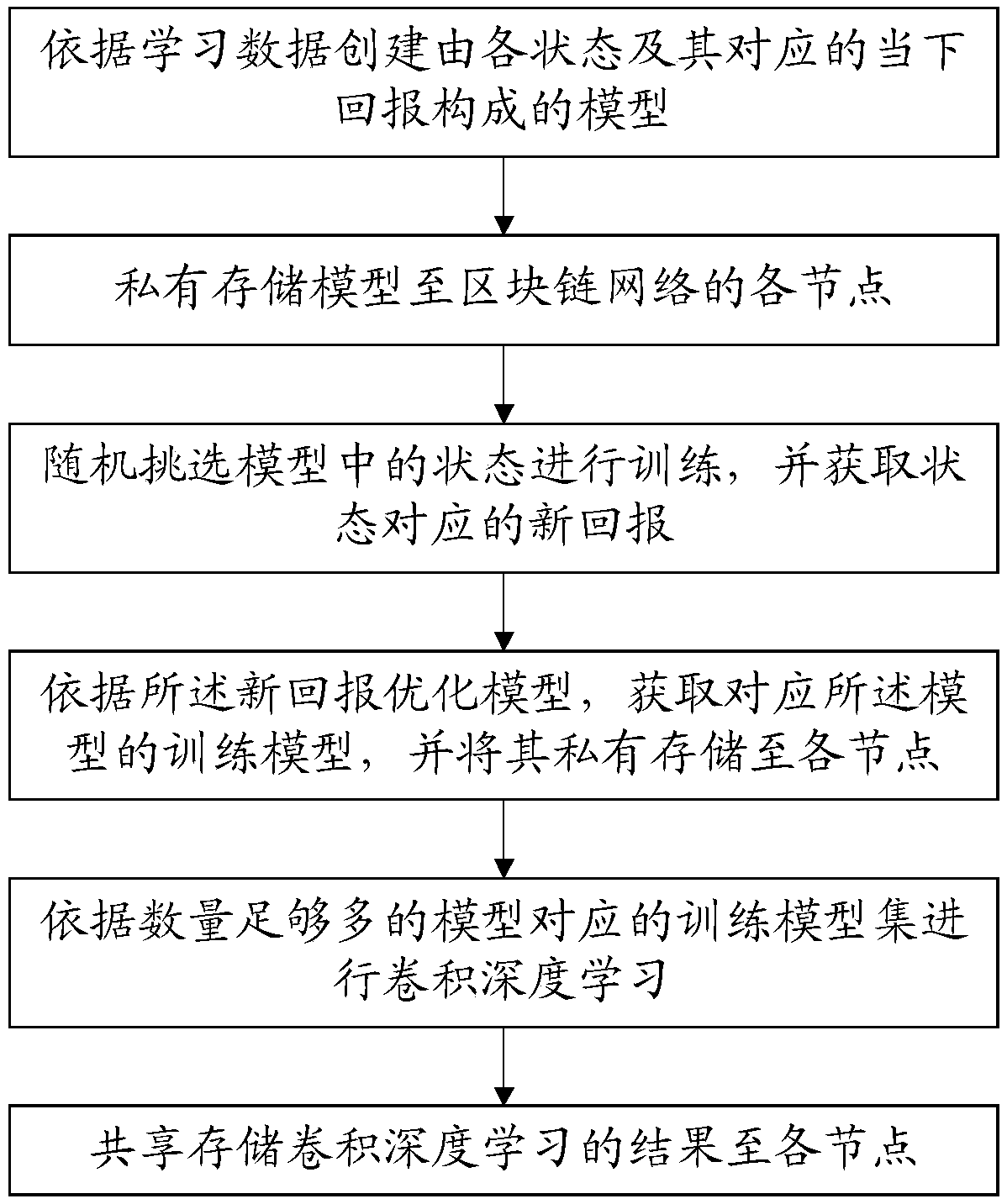
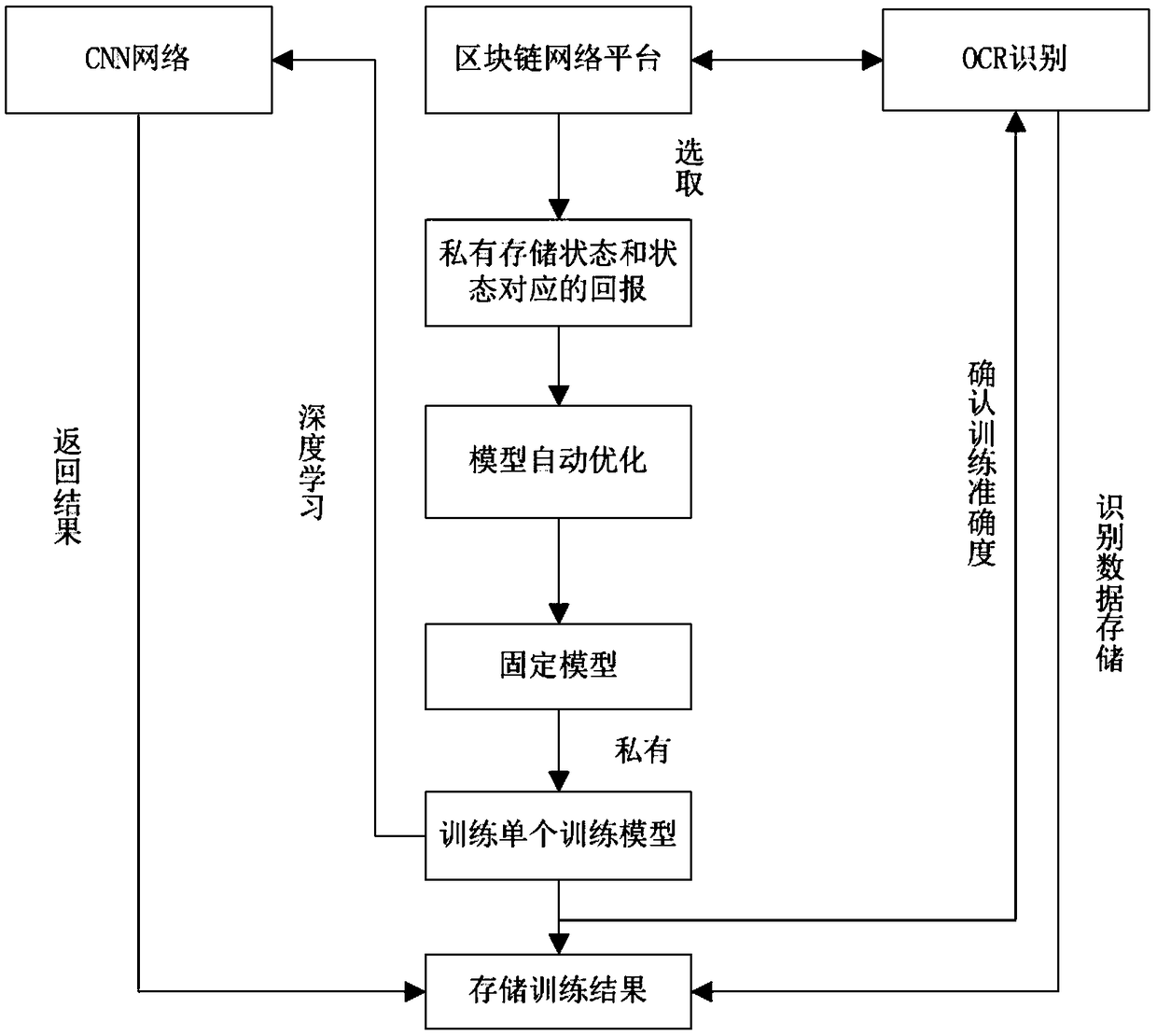
OCR depth learning method based on block chain mechanism, storage medium
ActiveCN109344823AGuaranteed privacyGuaranteed data privacyCharacter recognitionLearning dataStorage model
The invention provides an OCR depth learning method based on a block chain mechanism. The storage medium comprises: a model composed of each state and its corresponding immediate return is created according to the learning data. The states correspond to each sub-learning data in the learning data. Private storage model to the nodes of the block chain network; The states in the model are randomly selected for training, and the new returns corresponding to the states are obtained. Obtaining a training model corresponding to the model according to the new reward optimization model; Convolution depth learning is carried out according to the training model set corresponding to a sufficient number of models. Share the results of convolutional depth learning to each node. The invention can realize resource sharing of learning data. It can effectively protect the self-learning results, improve the learning value, and help to accelerate the progress of research and development; But also guarantees user data privacy.
Owner:福建天晴在线互动科技有限公司
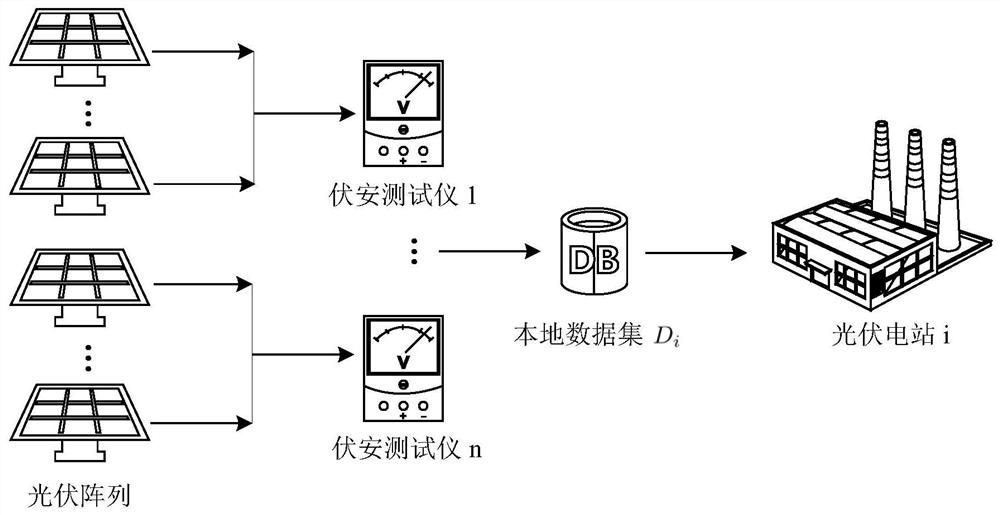
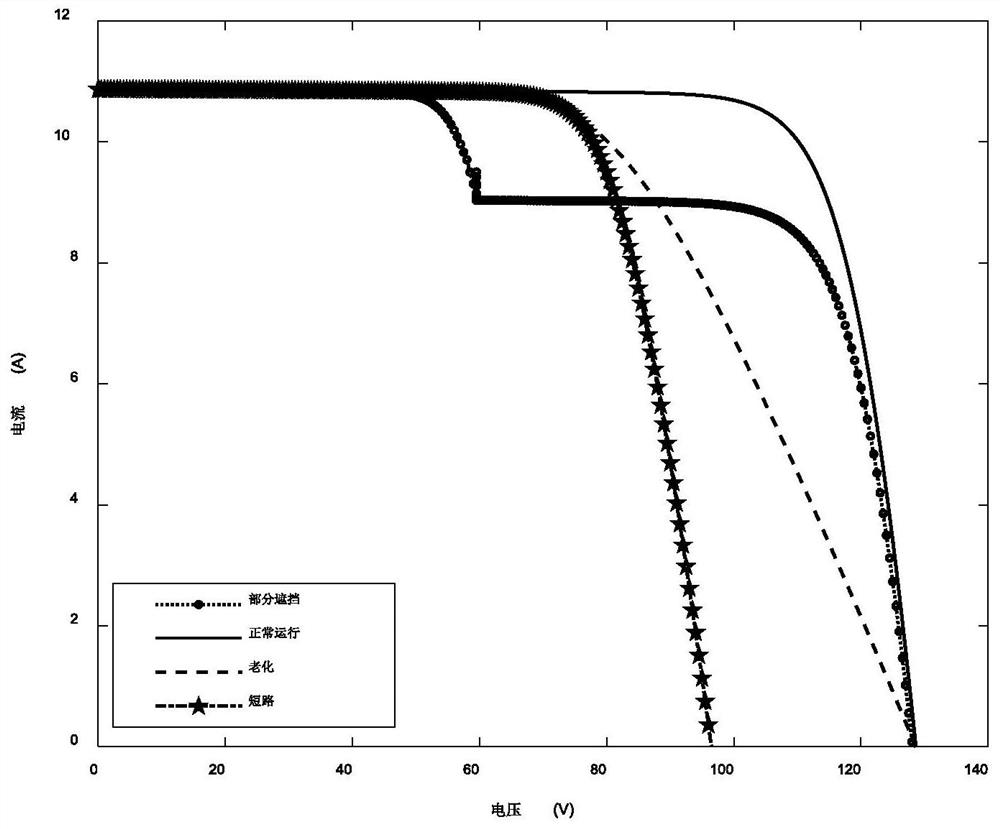
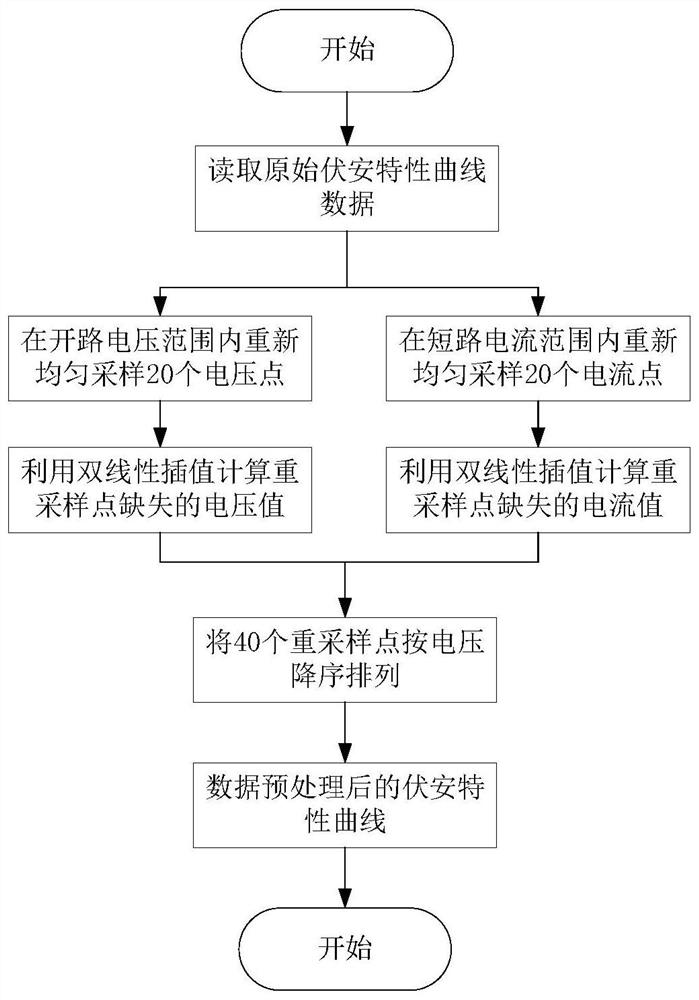
Photovoltaic power station joint fault diagnosis method based on asynchronous decentration federated learning
ActiveCN113283175AImprove generalization abilityTake advantage ofDesign optimisation/simulationNeural architecturesData setEngineering
The invention discloses a photovoltaic power station combined fault diagnosis method based on asynchronous decentralized federated learning, and relates to the field of fault diagnosis. The method includes: constructing an original local data set; preprocessing the data; building a CNN (Convolutional Neural Network) for training a local fault diagnosis model; carrying out joint fault diagnosis modeling of multiple power stations based on asynchronous decentration federated learning; and finally, evaluating the fault diagnosis accuracy, the communication efficiency and the model training efficiency of the combined fault diagnosis model. The generalization ability of the model is effectively improved; local data of a plurality of power stations are fully utilized under the condition that data privacy is guaranteed; aggregation of the global model does not need participation of a central server but is completely distributed, so that the communication and training efficiency of the model is effectively improved; and high-precision fault diagnosis of the photovoltaic module can be realized only by adopting a simple CNN (Convolutional Neural Network).
Owner:SHANGHAI JIAO TONG UNIV
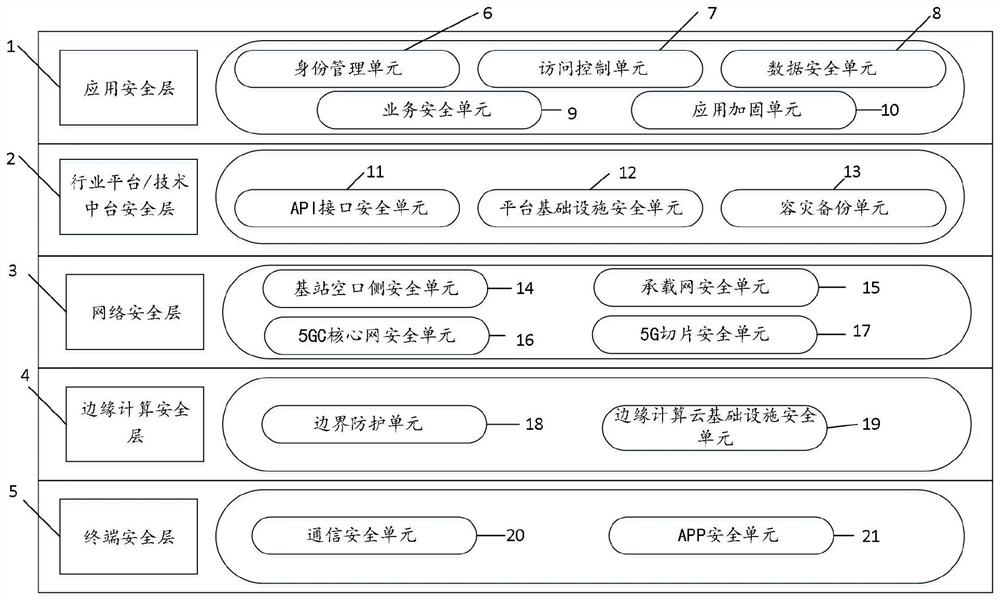
5G smart city security architecture
InactiveCN113079163AAvoid physical attackNot easy to captureTransmissionCommunications securityEdge computing
The invention discloses a 5G smart city security architecture. The 5G smart city security architecture is a five-layer architecture. The five-layer architecture comprises an application security layer, an industry platform / technology platform security layer, a network security layer, an edge computing security layer and a terminal security layer. The application security layer is used for guaranteeing the security of an application account and application software; the industry platform / technical platform safety layer is used for guaranteeing safe and stable operation of the industry platform and the technical platform; the network security layer is used for protecting the security of the network; the edge computing security layer is used for preventing an edge computing network from being invaded and damaged by an external network; and the terminal security layer is used for guaranteeing communication security. By adopting the 5G smart city security architecture provided by the invention, the security problem of a 5G smart city system can be reduced, and the data security and privacy of users and enterprises are effectively protected.
Owner:安徽长泰科技有限公司
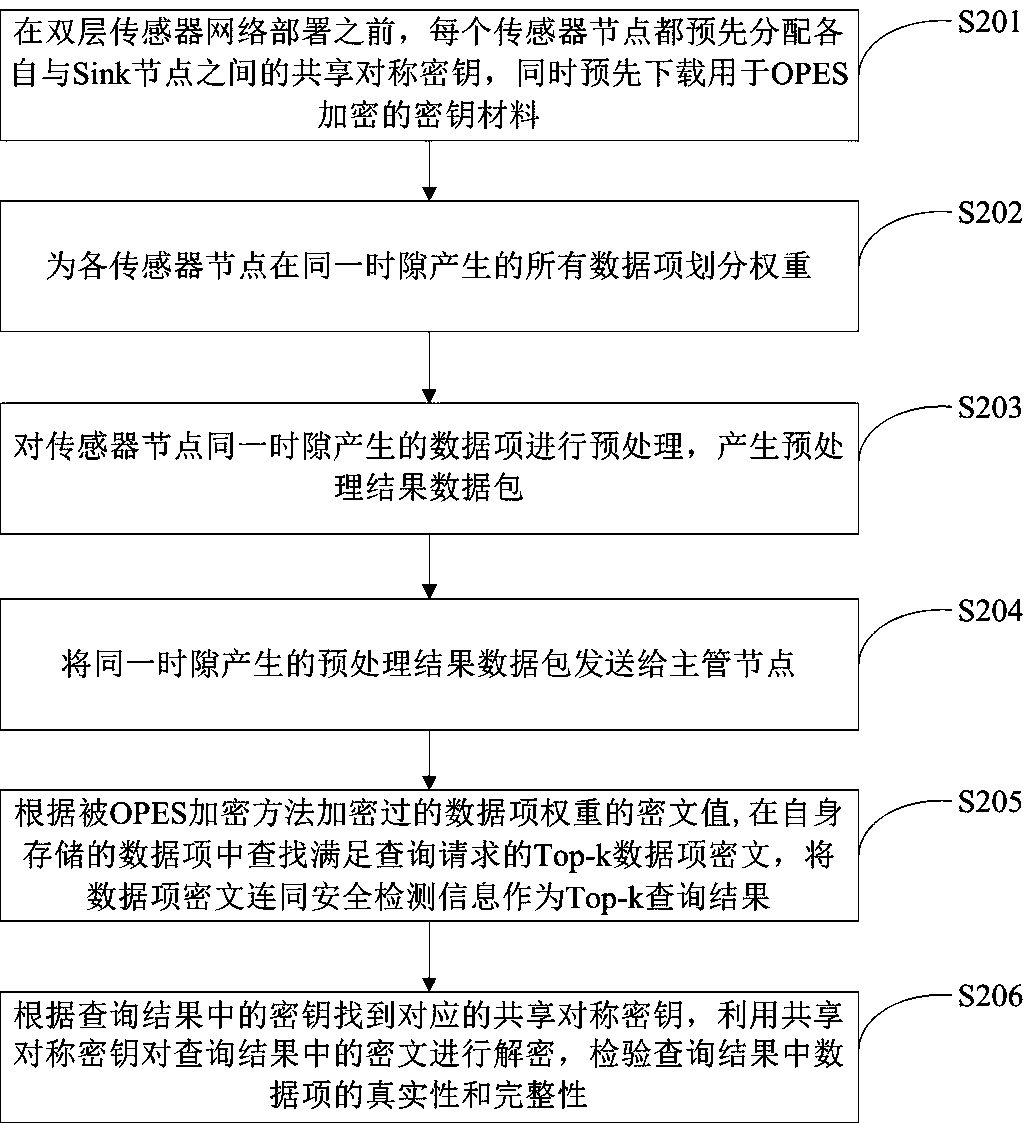
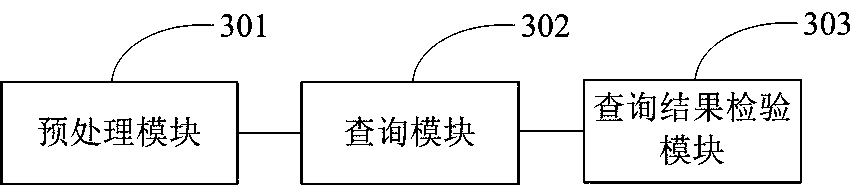
Safety Top-k query method facing to double-layered sensing network and device
ActiveCN107609425AGuaranteed data privacyReduce communication costNetwork topologiesDigital data protectionHigh probabilitySensor node
The invention relates to the technical field of security defense of a double-layered sensing network. The safety Top-k query method facing to the double-layered sensing network includes steps that a data item generated in the same time slot of a sensor node is pretreated; a main pipe node searches Top-k data item ciphertext in accordance with the query request from the stored data item according to a ciphertext value of the data item weight, and uses these data item ciphertexts along with a part of security detection information as the Top-k query result; a Sink node finds out a sharing symmetric key according to the key in the query result, decodes the ciphertext in the query result, and detects the data item authenticity and integrity in the query result. The safety Top-k query device facing to the double-layered sensing network comprises a pretreatment module, a query module and a query result inspection module. The safety Top-k query method and the device can ensure the data privacy of the Top-k query and detect the Top-k query result which is not possessed of the data integrity by high probability.
Owner:XINYANG NORMAL UNIVERSITY
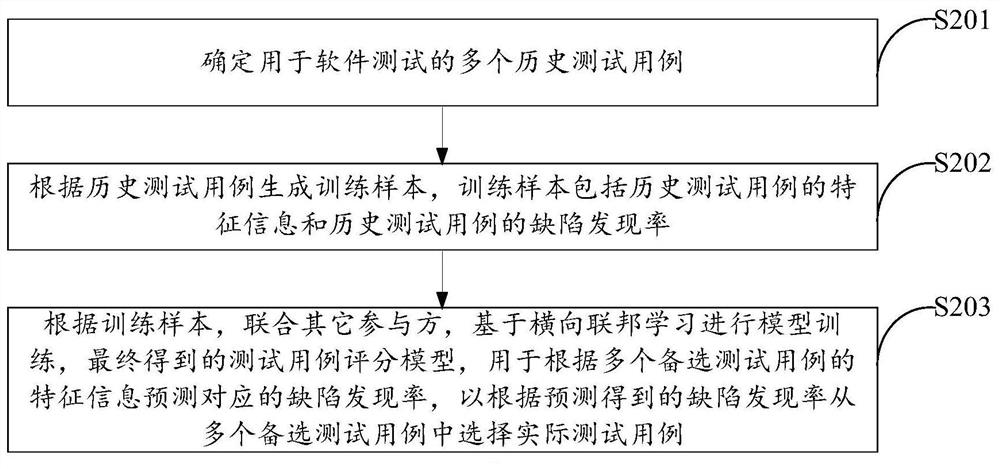
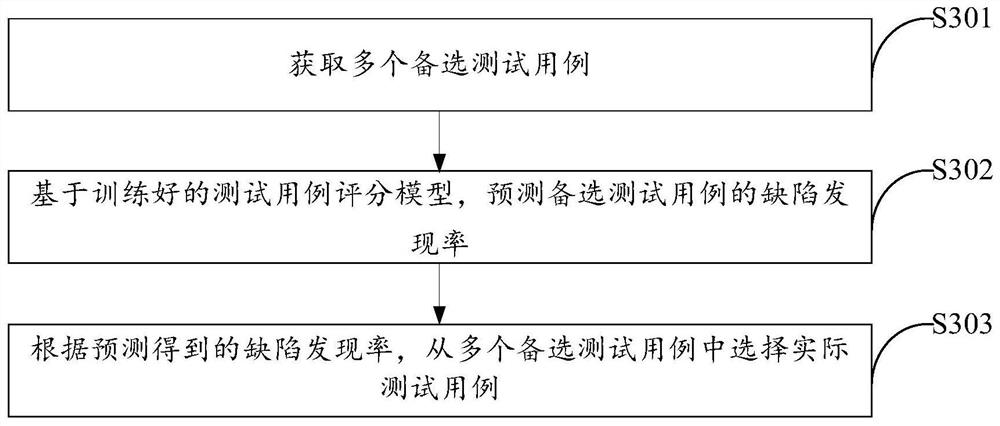
Test case scoring model training method and test case selection method
PendingCN112948274AImprove selection efficiencyImprove test efficiencySoftware testing/debuggingTest efficiencyEngineering
The invention discloses a test case scoring model training method and a test case selection method. The test case scoring model training method comprises the following steps: determining a plurality of historical test cases for software testing; generating a training sample according to the historical test case, wherein the training sample comprises feature information of the historical test case and a defect discovery rate of the historical test case; according to the training sample, in combination with other participants, performing model training based on transverse federated learning, wherein a finally obtained test case scoring model is used for predicting a corresponding defect discovery rate according to feature information of a plurality of alternative test cases, and selecting an actual test case from the plurality of alternative test cases according to the predicted defect discovery rate. The model is trained based on a large amount of sample data by combining a plurality of participants, the method can be used for predicting the defect discovery rate of the test case, effective reference is provided for selection of the test case, the test case selection efficiency is improved, and the software test efficiency is improved.
Owner:WEBANK (CHINA)
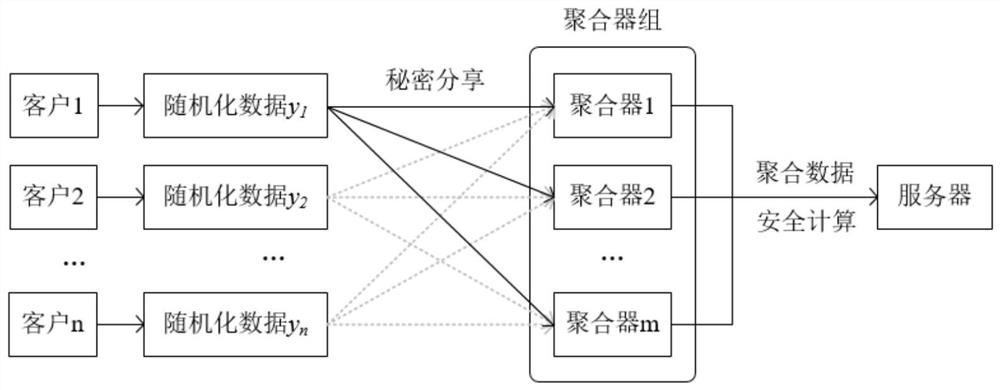
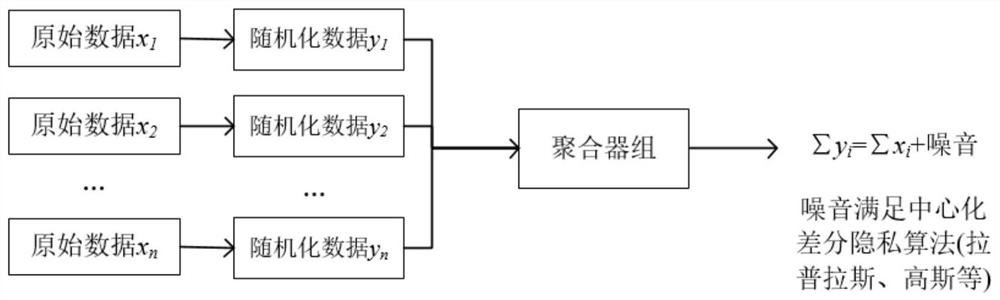
Distributed differential privacy aggregation method
ActiveCN113300828AHigh precisionGuaranteed data privacyPlatform integrity maintainanceCommunication with homomorphic encryptionComputer networkDifferential privacy
The invention belongs to the technical field of data collection of distributed privacy protection, and particularly relates to a distributed differential privacy aggregation method. The method comprises the following steps: distributed implementation is performed on a centralized differential privacy algorithm in a mode of adding noise at a user side on the basis that the centralized differential privacy algorithm obeys the additive property of the distribution; in the process that a user sends data and aggregates the data, by using a secure multi-party computing method, the user sends data randomized through a differential privacy algorithm to all aggregators in a secret sharing mode, and then all the aggregators interact to obtain a final randomized aggregation result. According to the accurate and efficient distributed differential privacy aggregation method provided by the invention, a differential privacy algorithm is realized in a distributed manner, so that the collection accuracy of distributed privacy protection data is improved, and under the trust hypothesis that a data collection party is not trusted, the security of intermediate data of a user is ensured through secure multi-party calculation, and the security data aggregation efficiency is improved.
Owner:NANKAI UNIV
Inference attack resistant distributed multi-task learning privacy protection method and system
ActiveCN112118099AAddress safety training issuesEnsure safety trainingKey distribution for secure communicationDesign optimisation/simulationKey (cryptography)Privacy protection
According to an inference attack resistant distributed multi-task learning privacy protection method and system, model training is carried out through various task nodes based on local data, and jointmodel training is realized through a knowledge sharing mode. According to the method, a privacy protection model training mechanism based on homomorphic cryptography is provided, so that task nodes realize multi-task learning model training on the premise of ensuring the privacy of training data, the model training efficiency is independent of a sample data volume, and the machine learning modeltraining efficiency is improved. A model publishing method based on differential privacy is designed, and an identity inference attack initiated can be resisted when a model user accesses a machine learning model . The system comprises a key generation center, a central server, a task node and a model user. According to the method, the data privacy of the task nodes in the model training process and after the release of the model can be ensured, and large-scale application of multi-task machine learning is promoted.
Owner:XIDIAN UNIV +1
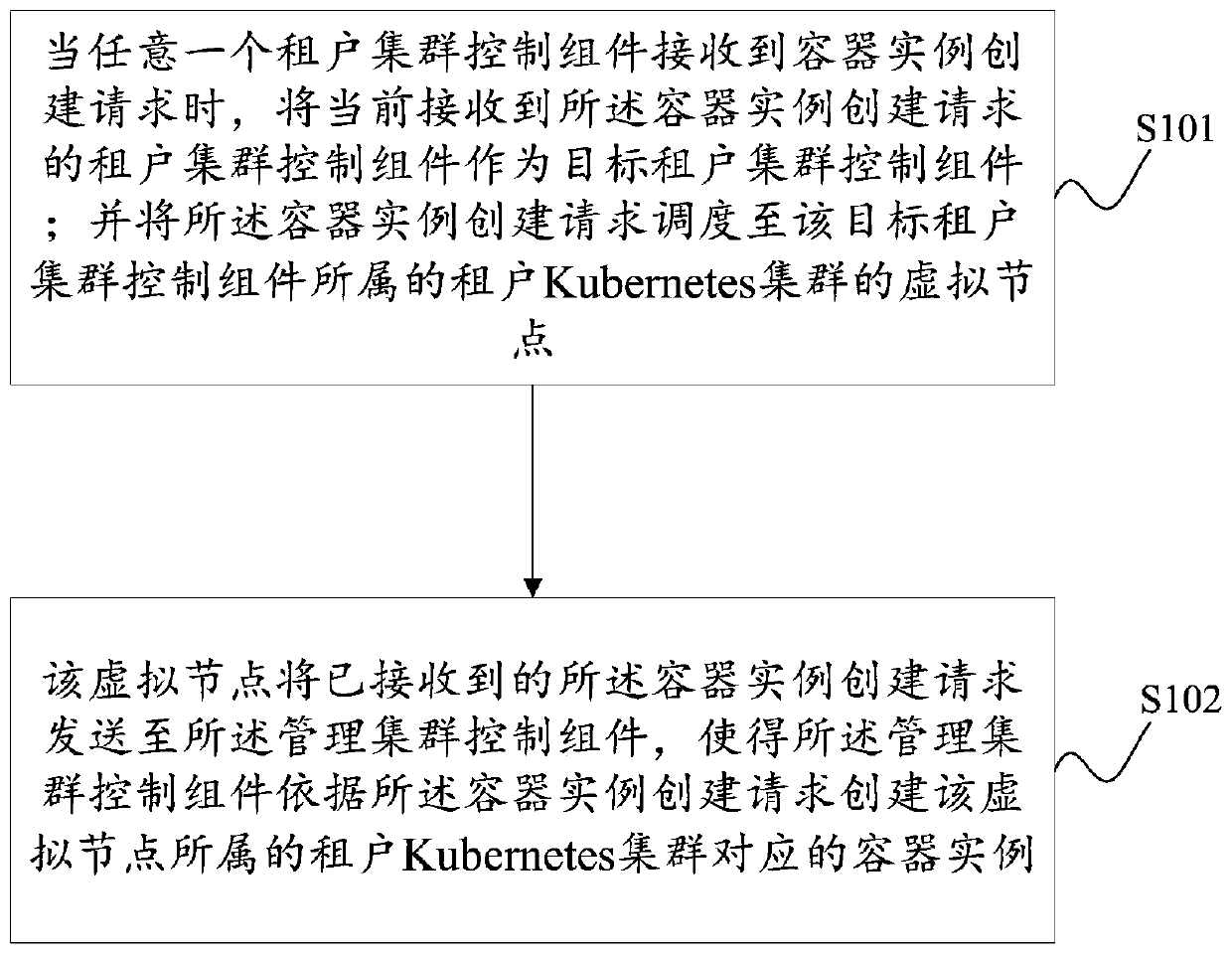
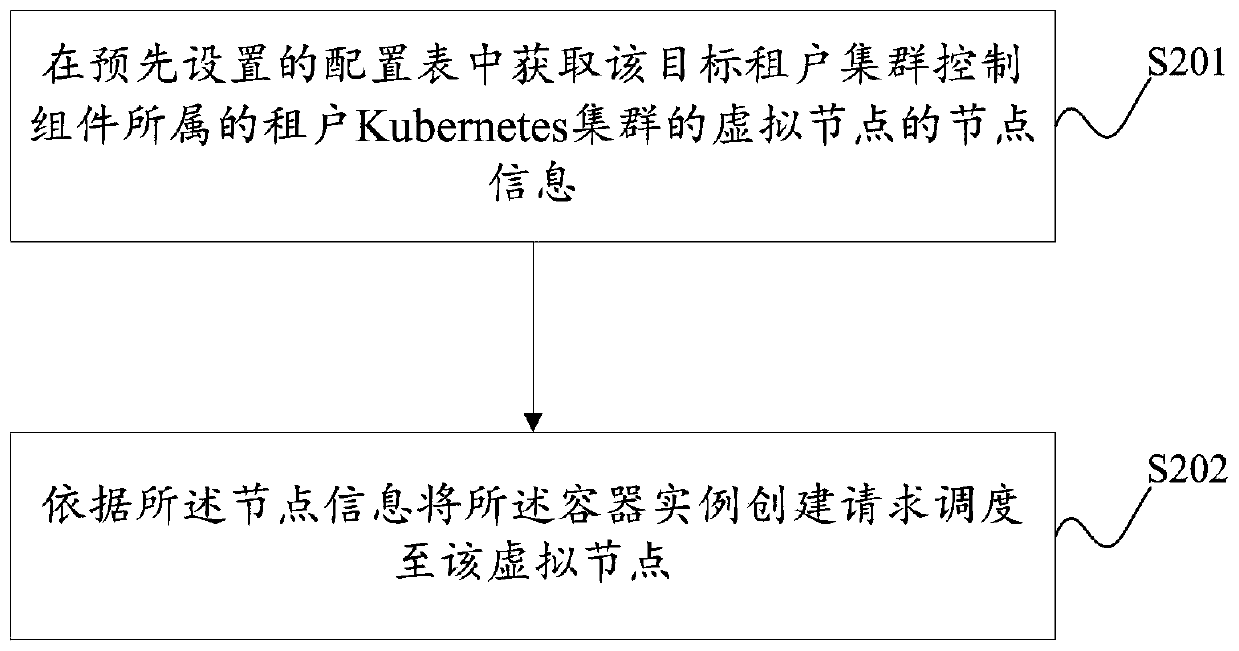
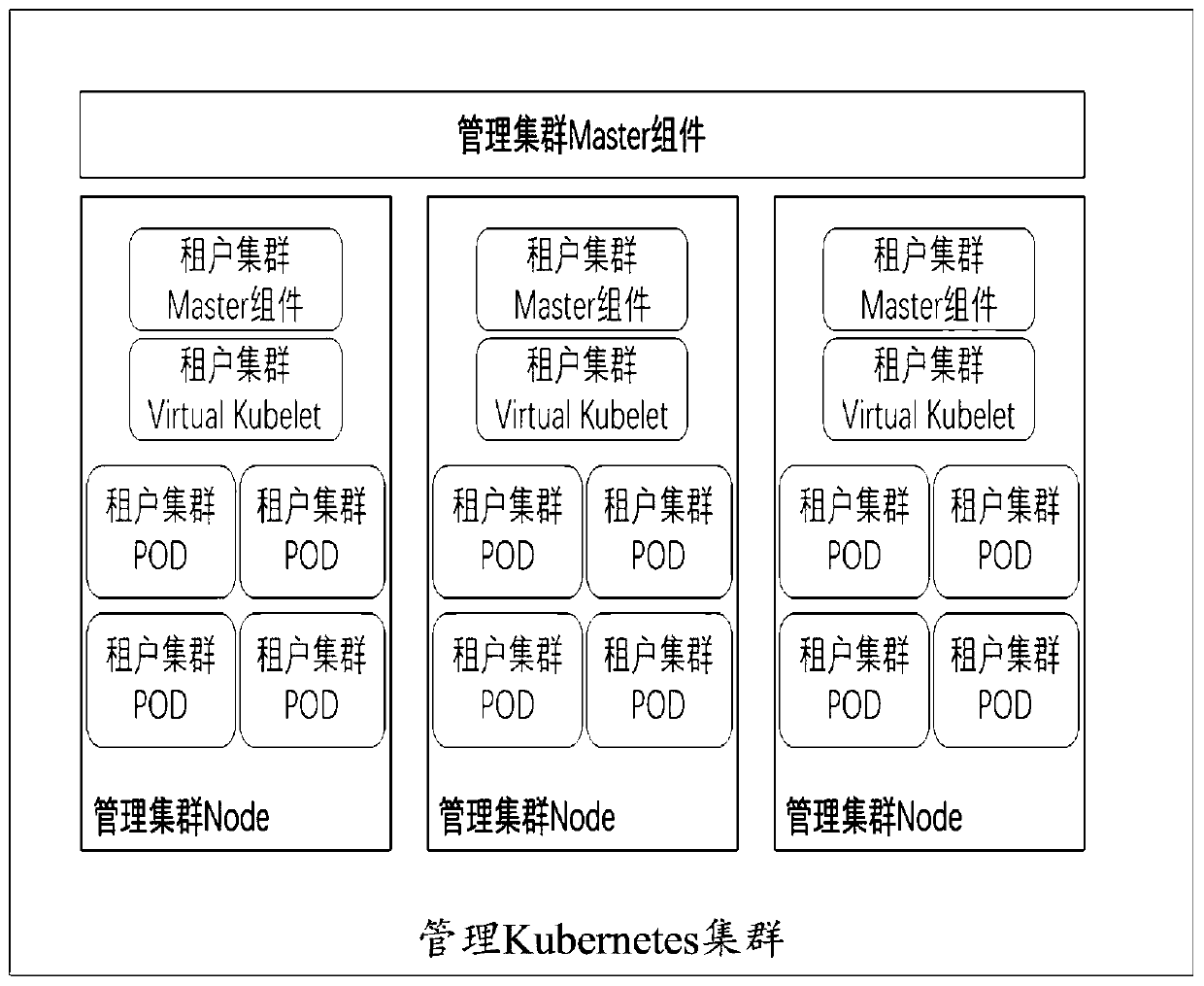
Container instance creation method and device based on multi-tenant management cluster
ActiveCN111309448AAchieve isolationGuaranteed data privacyDigital data protectionTransmissionComputer securityCluster Node
The invention provides a container instance creation method and device based on a multi-tenant management cluster. The method and the device are applied to management of a Kubernetes cluster. The management Kubernetes cluster comprises a management cluster control assembly and a plurality of management cluster nodes. Wherein each management cluster node deploys a tenant Kubernetes cluster corresponding to the management cluster node in advance, each tenant Kubernetes cluster comprises a tenant cluster control assembly and a virtual node, and when the target tenant cluster control assembly receives a container instance creation request, the container instance creation request is scheduled to the virtual node; and the virtual node sends the container instance creation request to the management cluster control component, so that the management cluster control component creates a corresponding container instance according to the container instance creation request. According to the invention, the isolation of multiple tenants can be realized under the condition of not influencing the service logic of the tenants, and the tenants do not need to care about the server information, so thatthe tenants can manage the tenant cluster conveniently.
Owner:UCLOUD TECH CO LTD
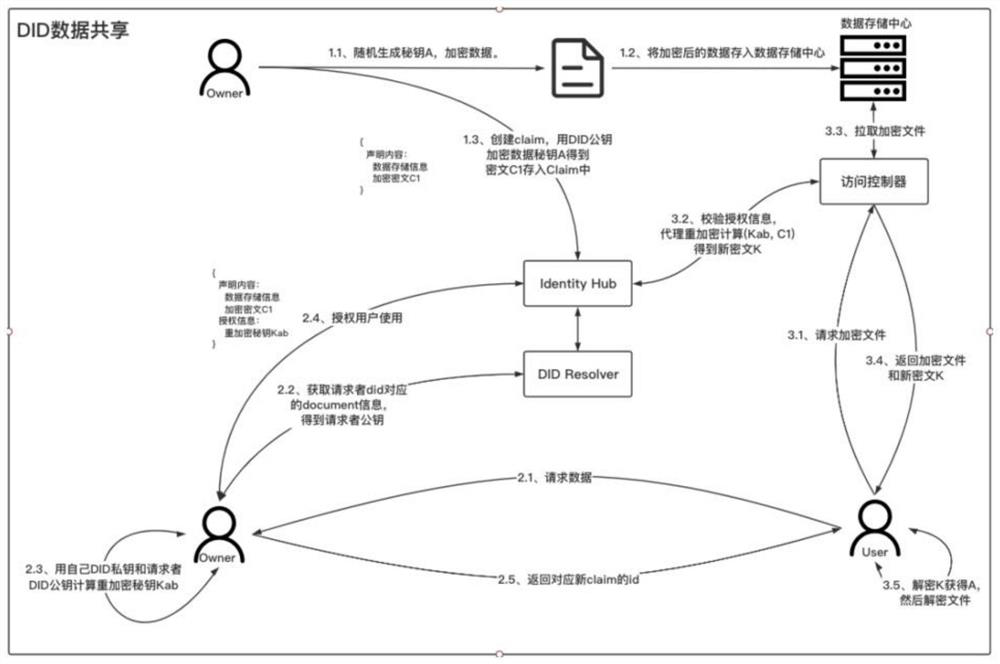
Data sharing method based on decentralized identity and proxy re-encryption
PendingCN112861157AProtect absolute controlGuaranteed data privacyDigital data protectionOriginal dataCiphertext
The invention discloses a data sharing method based on decentralized identity and proxy re-encryption. The method comprises the following steps: a data owner randomly generates a secret key A, encrypts original data R by using the secret key A to obtain encrypted data D, and pushes the encrypted data D to a data storage center for storage; then, the data owner encrypts the secret key A by using the own DID public key, generates an encrypted ciphertext C1, generates claim-1, and stores the claim-1; the data user sends a data use request to the data owner, the data owner authorizes the data user, and claim-2 authorization information is generated; the data user requests data specified by the corresponding claim from the access controller, and after it is confirmed that the data user has the access permission to the data, the data user obtains the original data R through decryption. According to the method, the absolute control right of the user on the data is strictly protected while the data is shared, and the data privacy of the user is ensured to the greatest extent.
Owner:奥科塞尔控股公司
Privacy protection method for collaborative deep learning model training
ActiveCN111460478AImplement collaborative model trainingGuaranteed data privacyDigital data protectionNeural architecturesPrivacy protectionEngineering
The invention discloses a privacy protection method for collaborative deep learning model training, and the method comprises the steps: proposing a collaborative distributed deep learning model training method, wherein a participant makes model parameter gradient calculation locally through existing training data, transmitting the gradient data obtained through calculation to a parameter server,and updating model parameters ; proposing a privacy protection mechanism based on a double-trap-door public key cryptographic algorithm so that participants can realize safety training of a deep learning model on the premise of ensuring the privacy of respective training data; and designing a fine-grained deep learning model release method to ensure that only the data owners participating in training can obtain the model, so that the model training fairness is ensured. A simulation test result shows that the method can provide accurate model training service on the premise of ensuring data privacy of participants. Privacy protection can be provided for artificial intelligence and other new-generation computer technologies.
Owner:XIDIAN UNIV +1
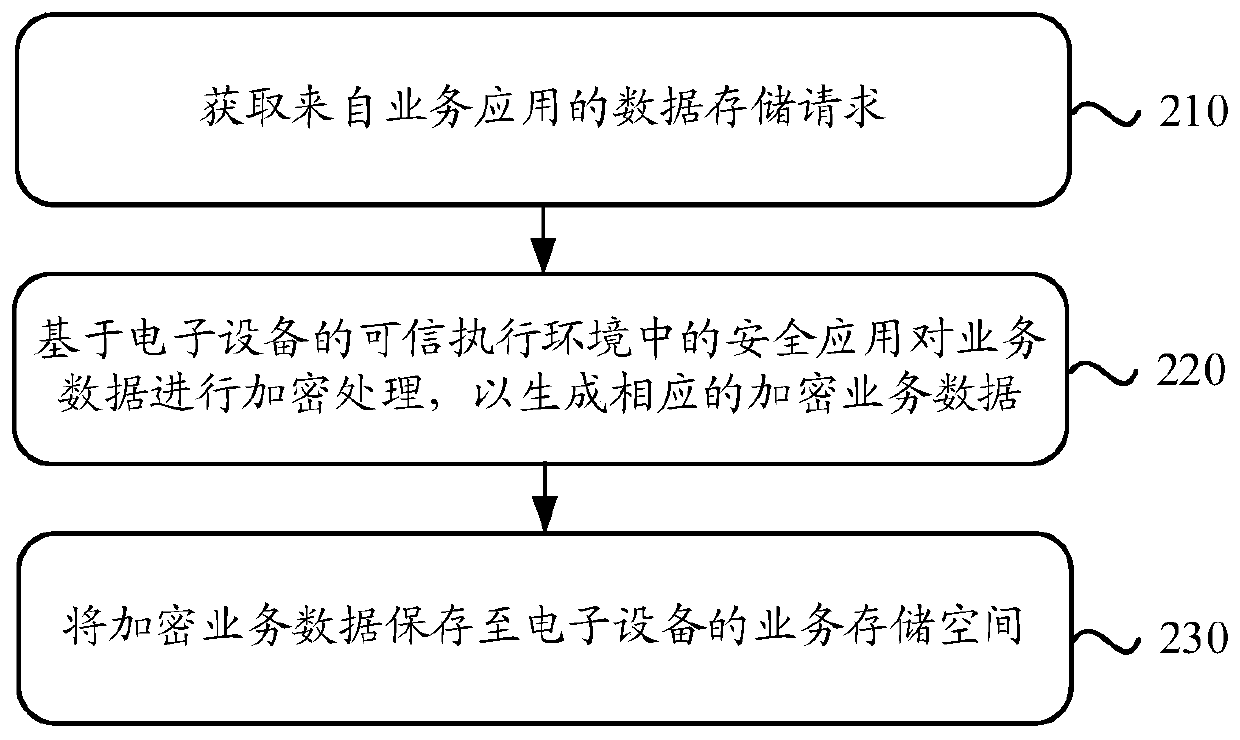
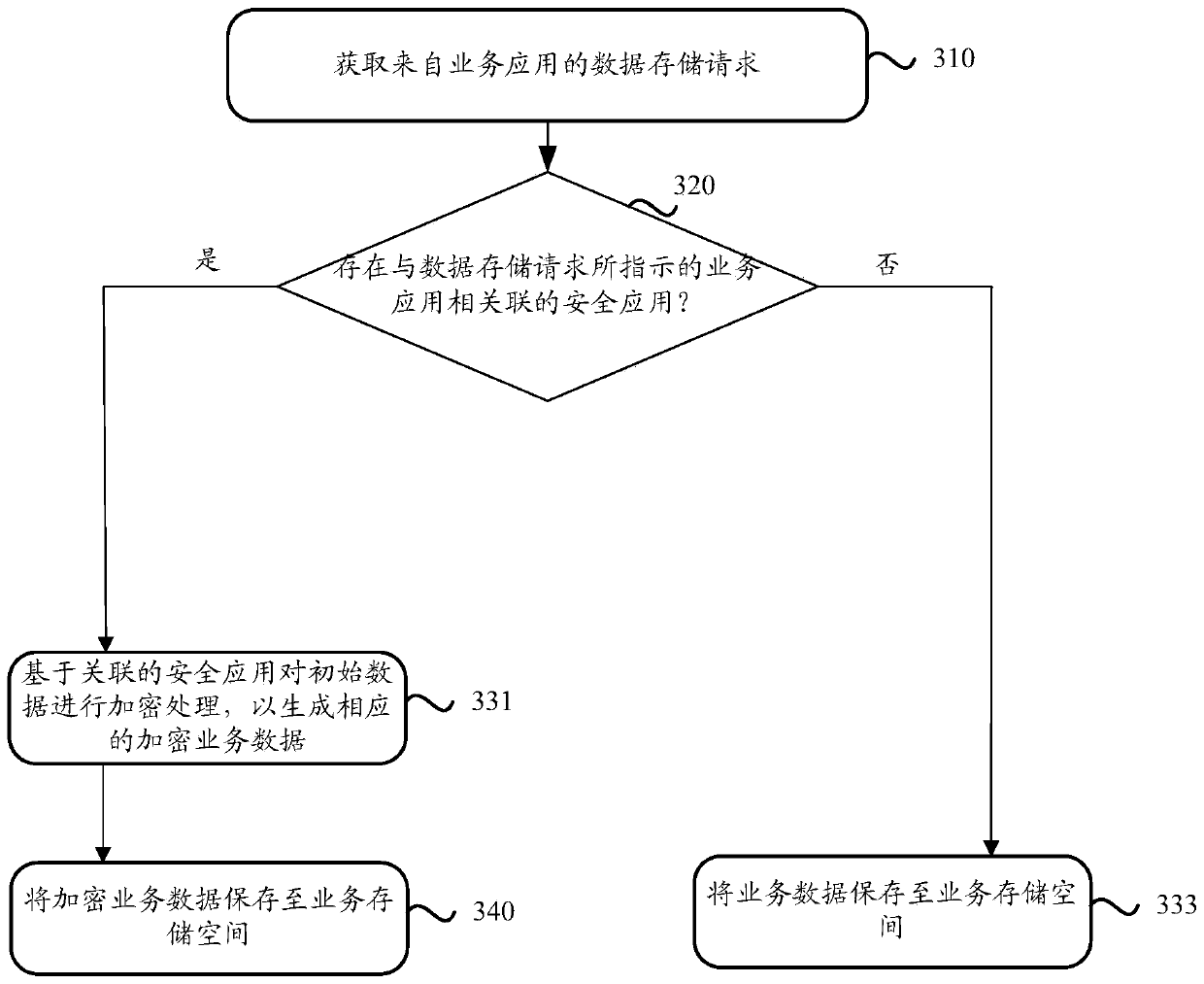
Data storage method and device and electronic equipment
ActiveCN111538995AImprove securityGuaranteed data privacyDigital data protectionPlatform integrity maintainanceEngineeringData store
The embodiment of the invention discloses a data storage method, a device and electronic equipment. The electronic device is configured with a trusted execution environment. At least one safety application is running in the trusted execution environment. In this method, firstly, a data storage request from a service application is obtained; wherein the data storage request comprises service data to be stored; according to the method, the service data is encrypted based on the safety application in the trusted execution environment of the electronic equipment to generate the corresponding encrypted service data, and then the encrypted service data is stored in the service storage space of the electronic equipment, so that the safety storage of the terminal data can be realized, and the safety of user data or privacy can be protected.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
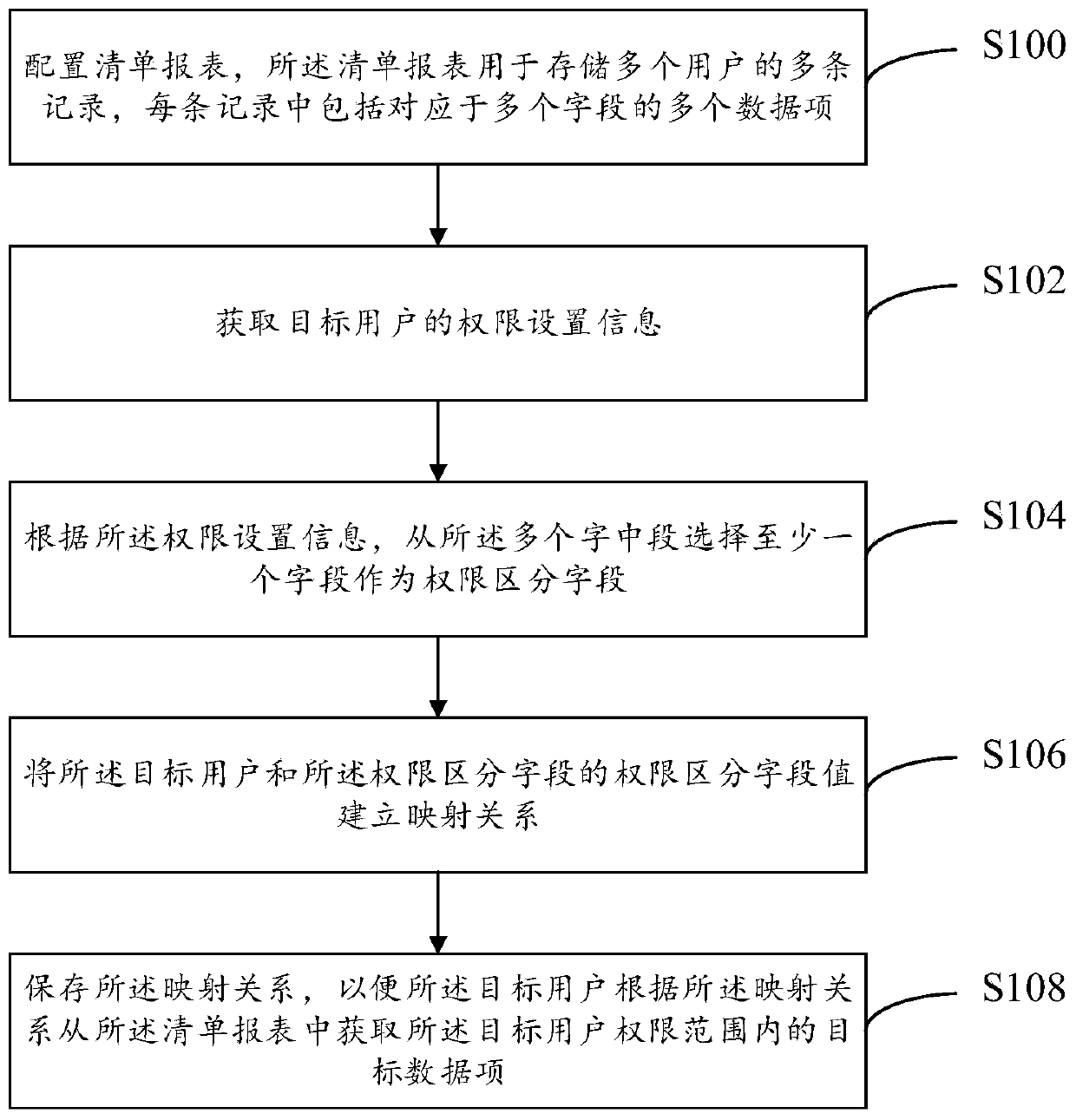
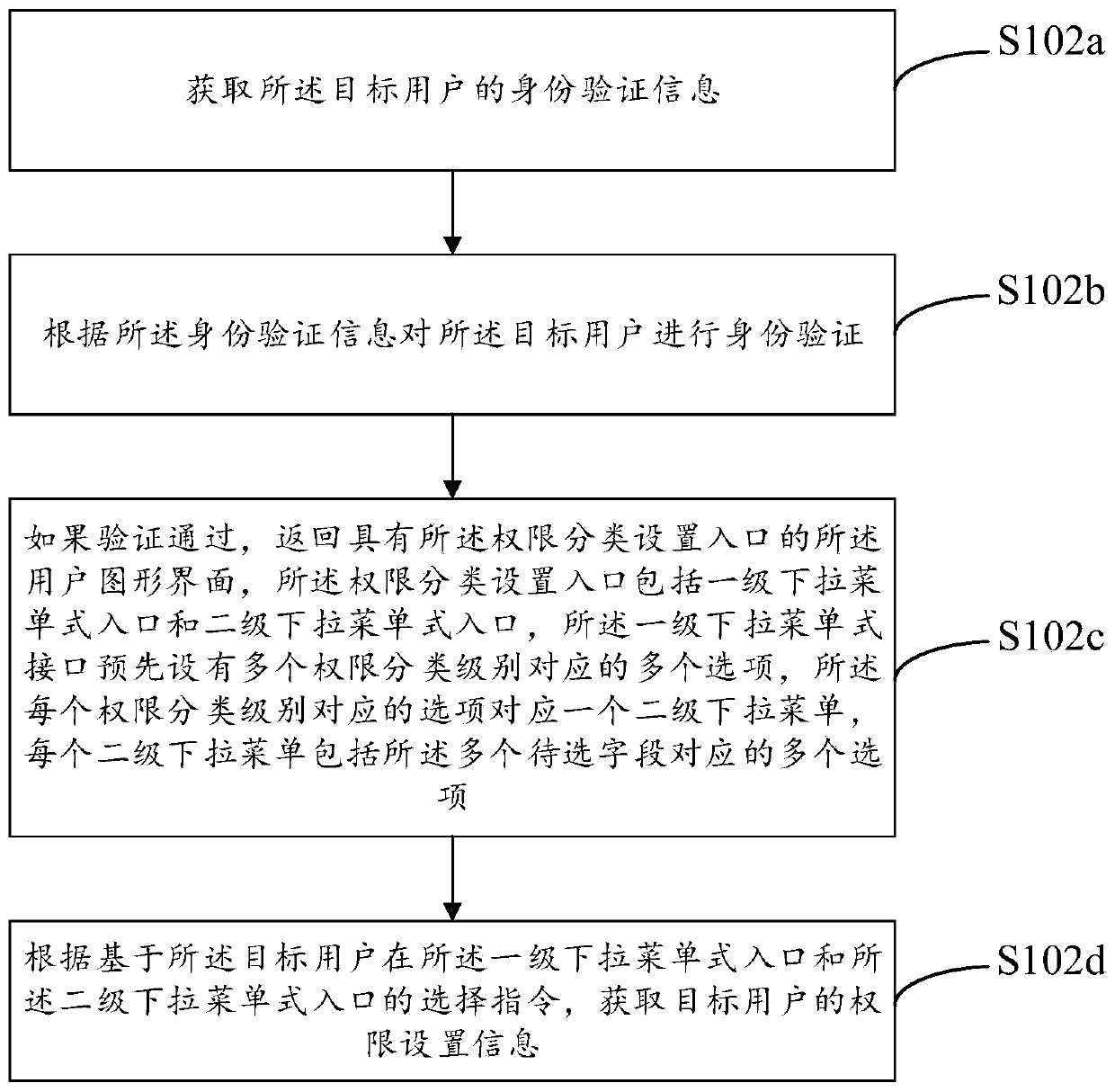
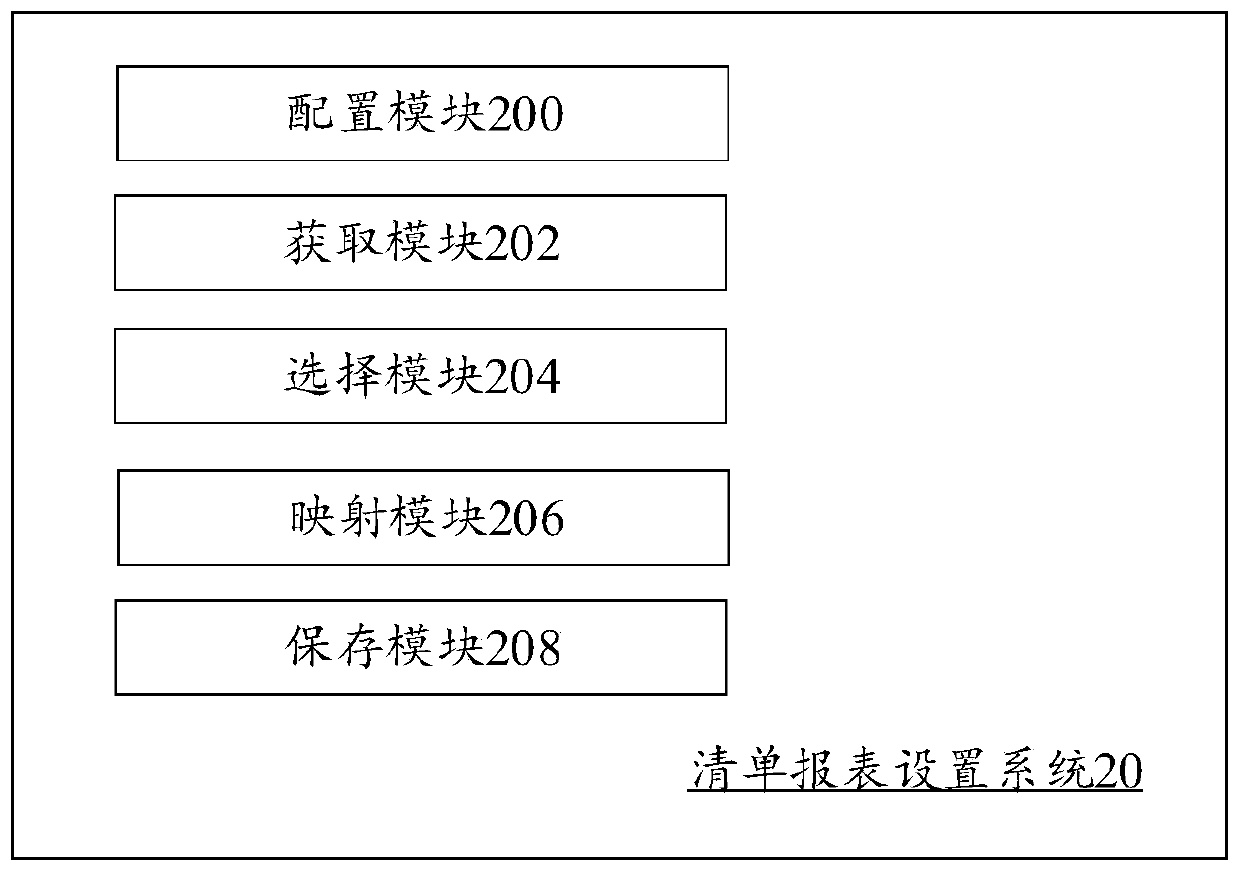
Manifest report setting method and system and manifest report obtaining method
PendingCN110618990AReduce download burdenGuaranteed data privacyRelational databasesDigital data protectionData mining
The embodiment of the invention provides a manifest report setting method, which comprises the following steps: configuring a manifest report which is used for storing a plurality of records of a plurality of users, and each record comprising a plurality of data items corresponding to a plurality of fields; obtaining permission setting information of a target user; according to the permission setting information, selecting at least one field from the plurality of field middle sections as a permission distinguishing field; establishing a mapping relationship between the target user and the authority distinguishing field values of the authority distinguishing fields; and storing the mapping relationship, so that the target user obtains a target data item in the permission range of the targetuser from the list report according to the mapping relationship. According to the embodiment, the list report is configured by the list with the same logic, so that the configuration efficiency and the subsequent maintenance efficiency are improved. Meanwhile, the data downloading burden is reduced, unnecessary links such as screening are removed, and the data privacy of other institutions is effectively guaranteed.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
Matrix QR decomposing method based on matrix privacy protection
InactiveCN103997499AGuaranteed data privacyEasy recovery of correct resultsDigital data protectionTransmissionQR decompositionMatrix decomposition
The invention discloses a matrix QR decomposing method based on matrix privacy protection. The method comprises the steps that an original matrix is preprocessed, the processed matrix is sent to a service provider, QR decomposing is conducted on the matrix by the service provider, the decomposed matrix is returned to a user, and after the user conducts certain operation, the matrix after decomposition of the original matrix is restored. Through above mode, according to the matrix QR decomposing method based on matrix privacy protection, due to the fact that the matrix is preprocessed, the service provider can not acquire any information of the original matrix, and the safety of the information and the transmission safety are improved.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
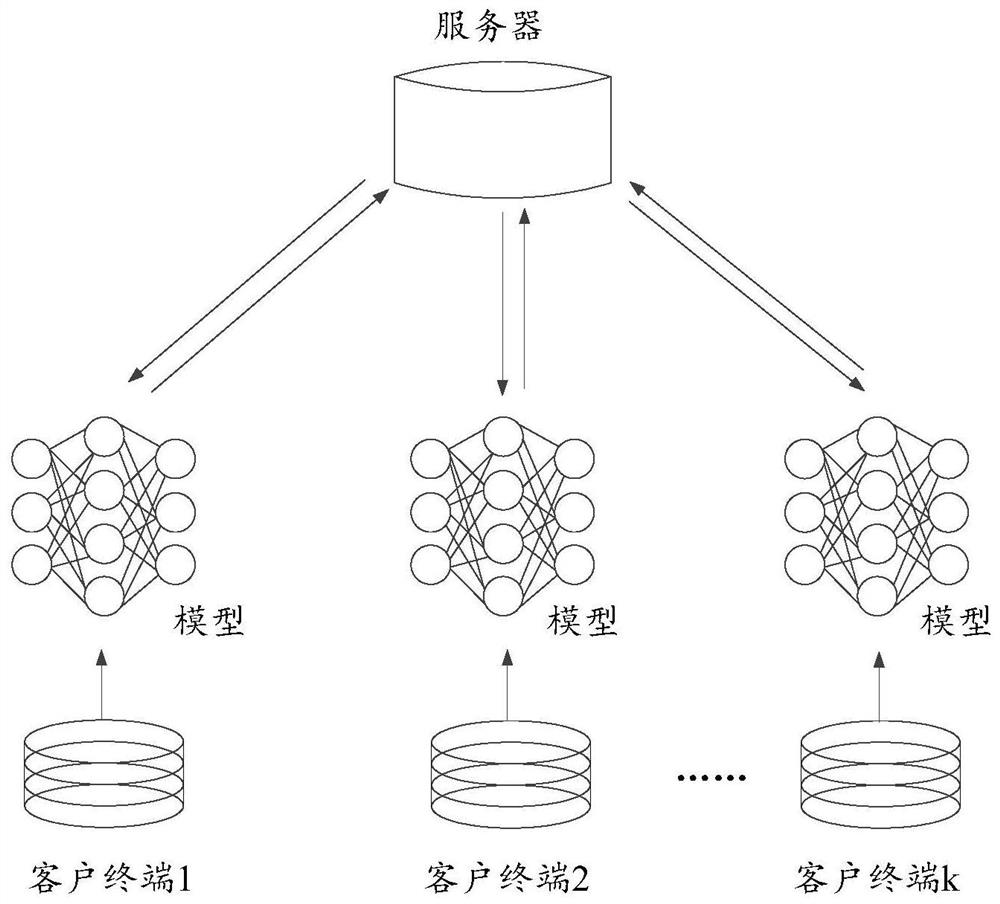
A model training method and system based on federated learning
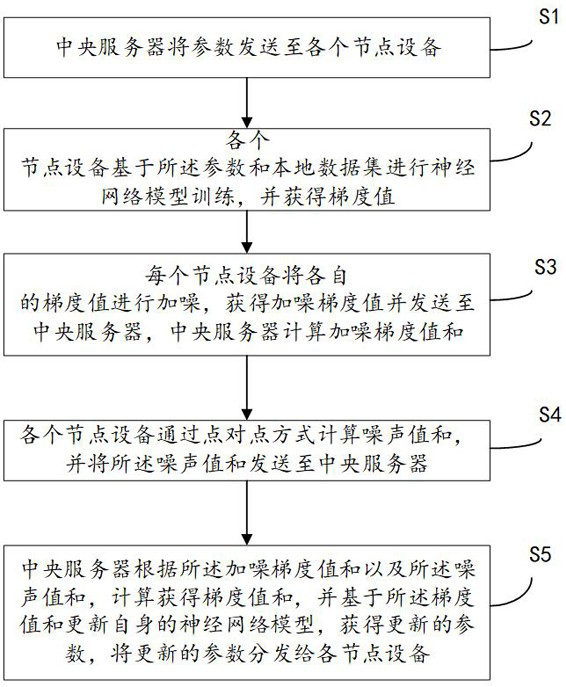
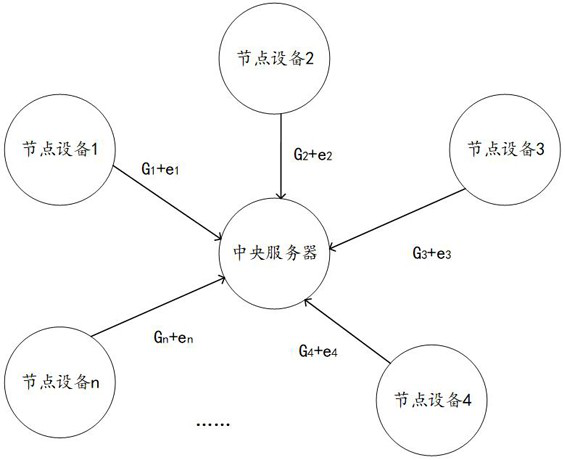
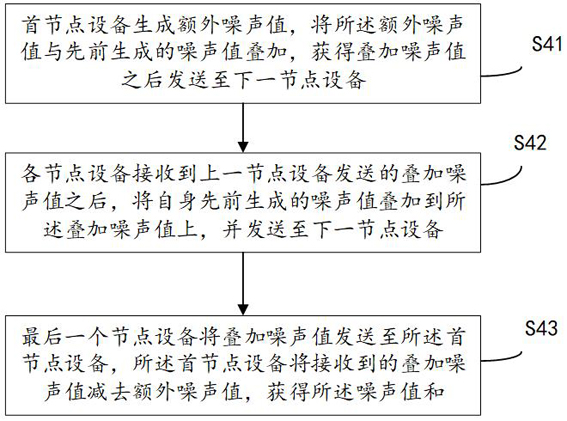
ActiveCN112333216BGuaranteed privacy dataGuaranteed accuracyEnsemble learningTransmissionData setEngineering
The invention discloses a model training method and system based on federated learning. The method includes: a central server sends parameters to each node device; each node device performs neural network model training based on the parameters and a local data set, and obtains a gradient value; Each node device adds noise to their respective gradient values, obtains the noised gradient value and sends it to the central server, and the central server calculates the sum of the noised gradient values; Sent to the central server; the central server calculates and obtains the sum of gradient values according to the sum of the noise-added gradient values and the sum of the noise values, and obtains updated parameters based on the sum of the gradient values and updates its own neural network model. The parameters are distributed to each node device; this method can ensure the model training accuracy while protecting the private data of the participants.
Owner:深圳索信达数据技术有限公司
Data sharing method, system and device and computer readable storage medium
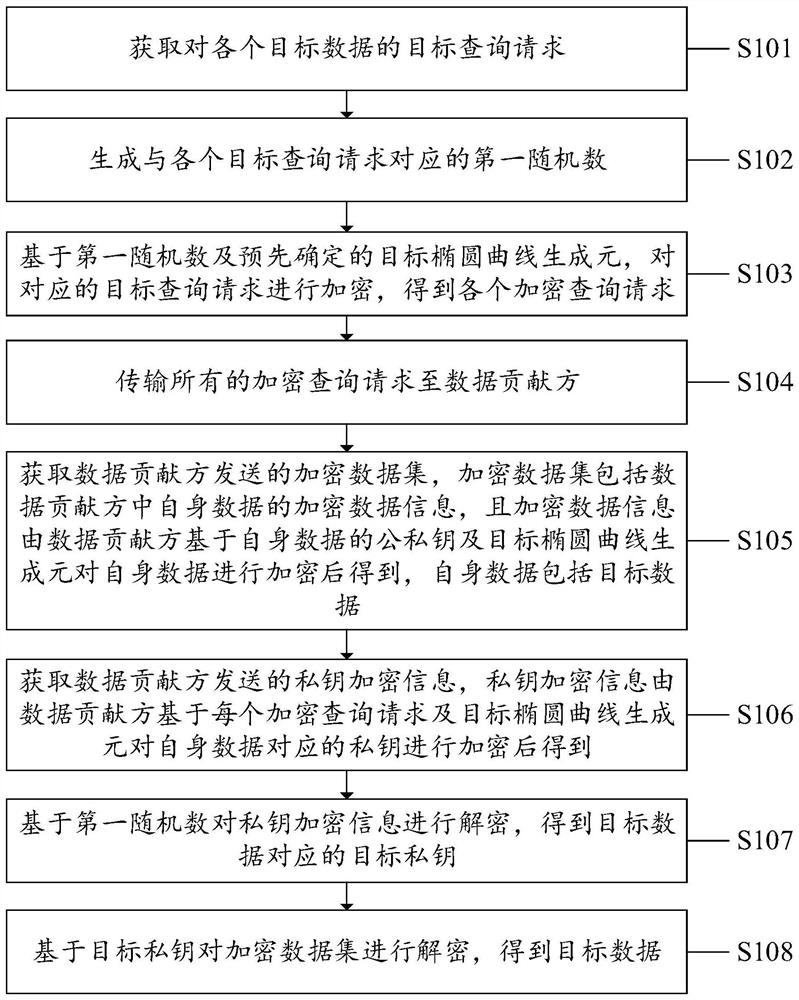
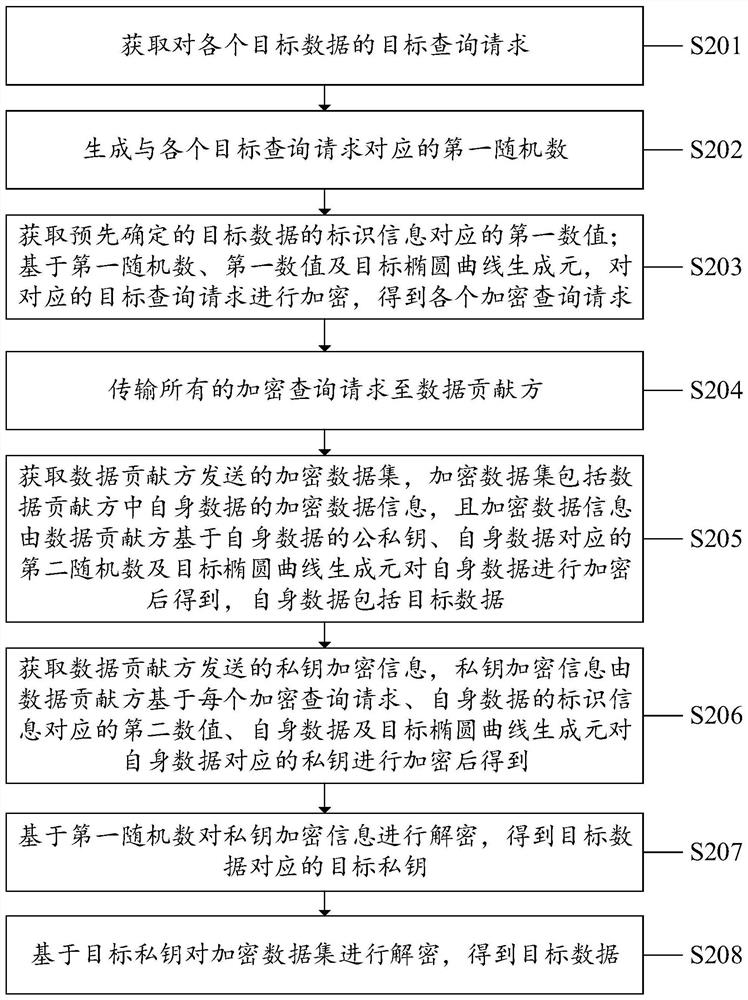
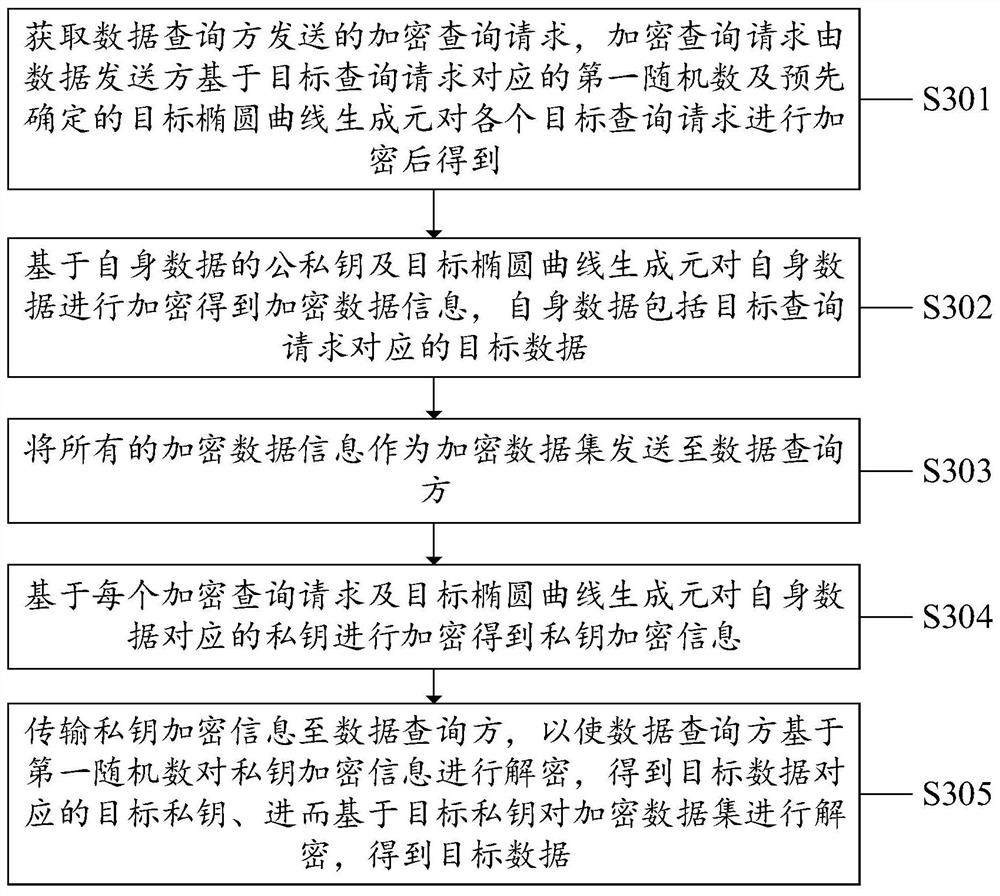
PendingCN113569259AProtect query privacyImprove privacyDatabase queryingDigital data protectionData setData query
The invention discloses a data sharing method, system and device and a computer readable storage medium, and is applied to a data query party. The method includes: obtaining a target query request for each piece of target data; generating a first random number corresponding to each target query request; based on the first random number and a predetermined target elliptic curve generator, encrypting the corresponding target query request to obtain each encrypted query request; transmitting all encrypted query requests to a data contributor; acquiring an encrypted data set sent by a data contributor; acquiring private key encryption information sent by the data contributor; decrypting the private key encryption information based on the first random number to obtain a target private key of the target data; and decrypting the encrypted data set based on the target private key to obtain target data. According to the method, system and device, the query privacy of the data query party is protected by encrypting the query request; the data privacy of the data contributor is ensured through the encrypted data set and the private key encryption information, and the utilization rate of the data can be improved.
Owner:SHENZHEN SECURITIES INFORMATION
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com