Patents
Literature
71results about How to "Prevent malicious theft" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
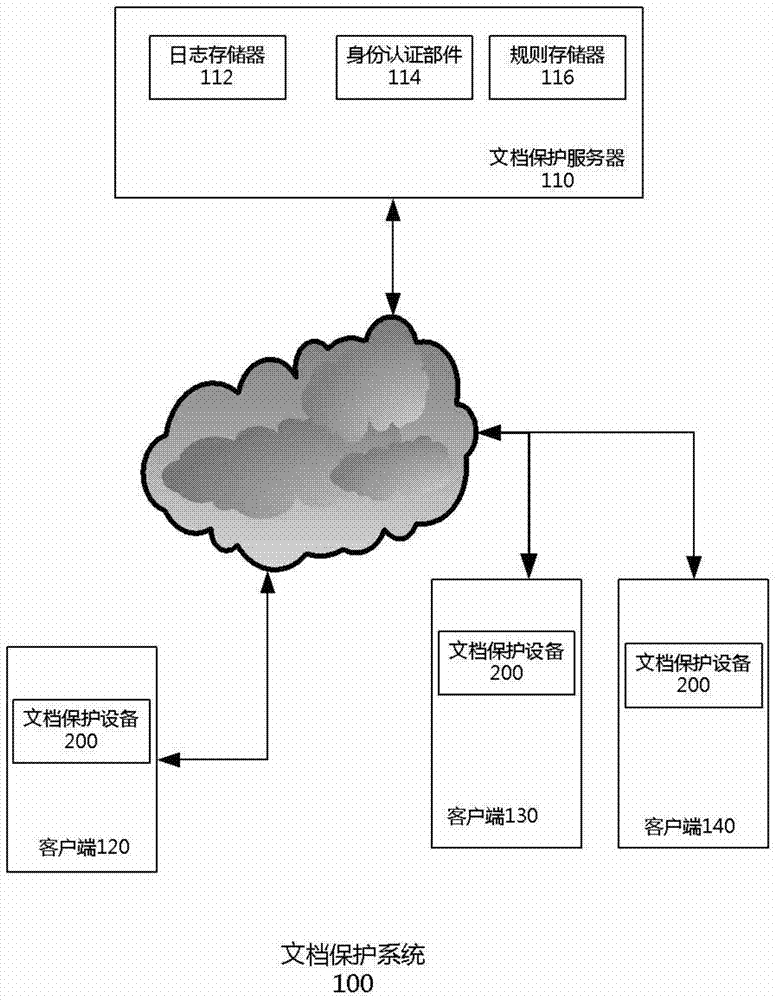
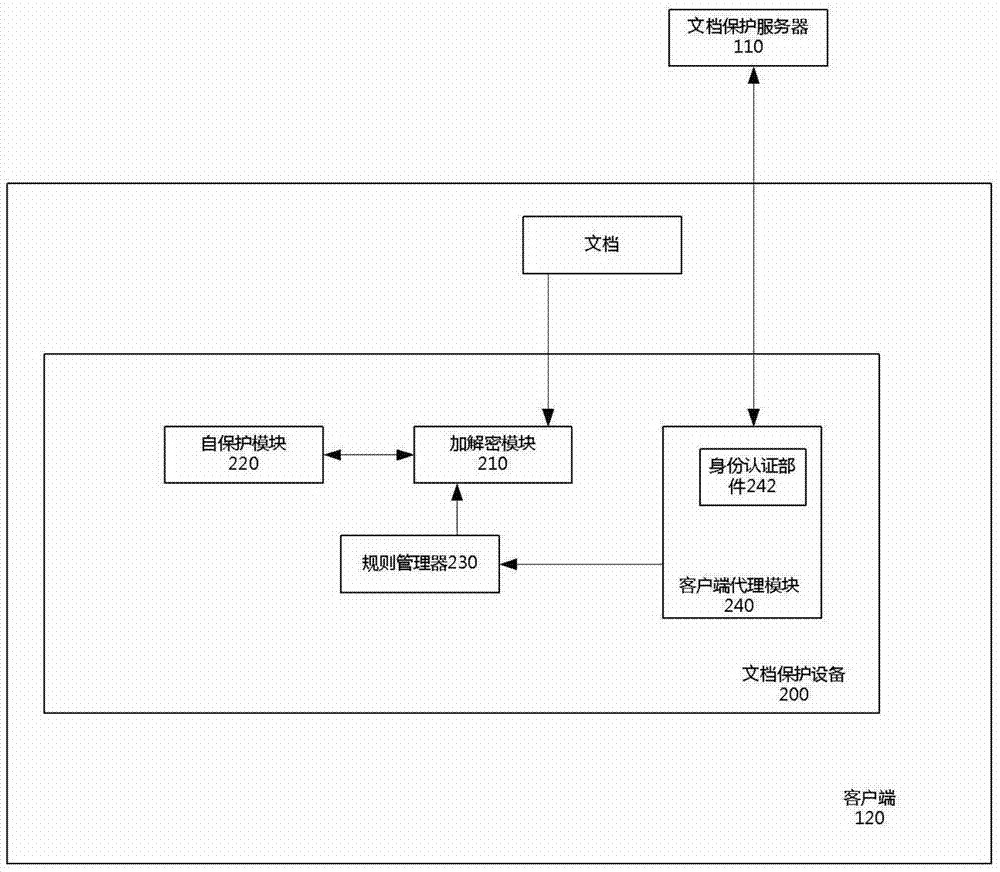
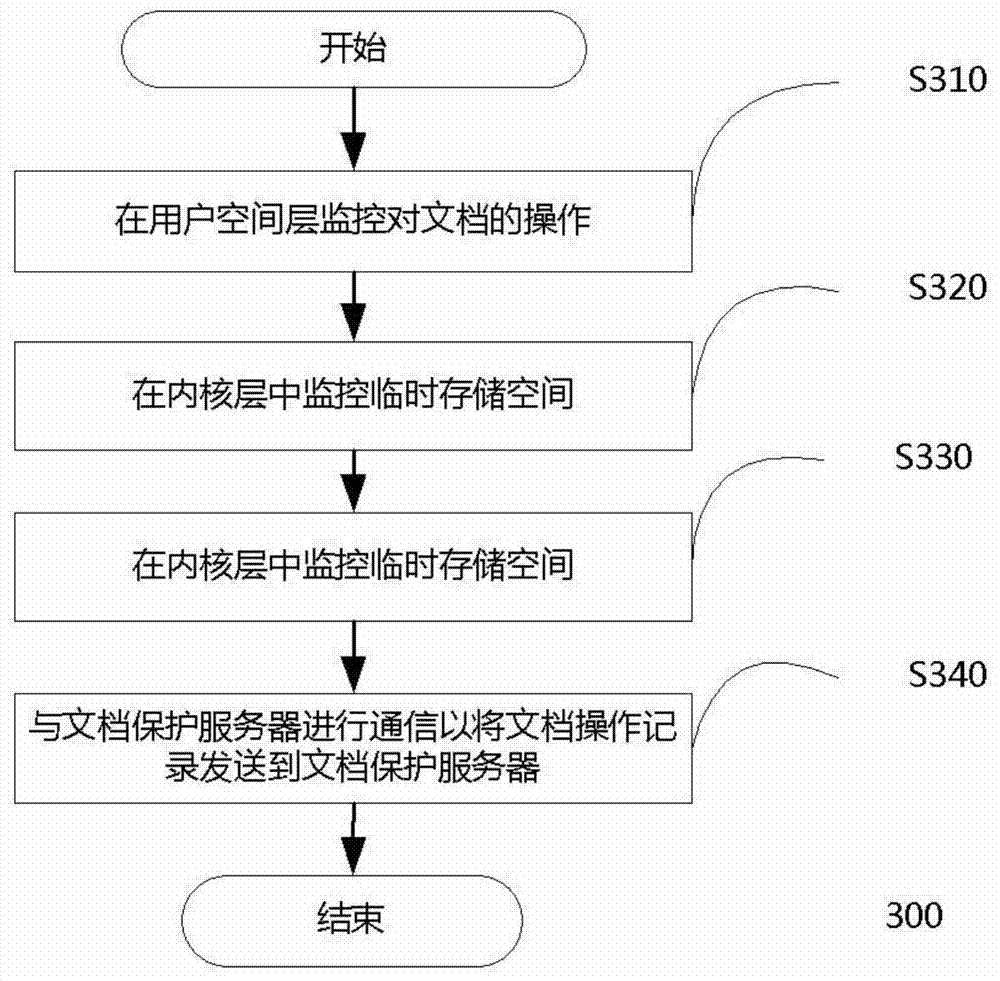
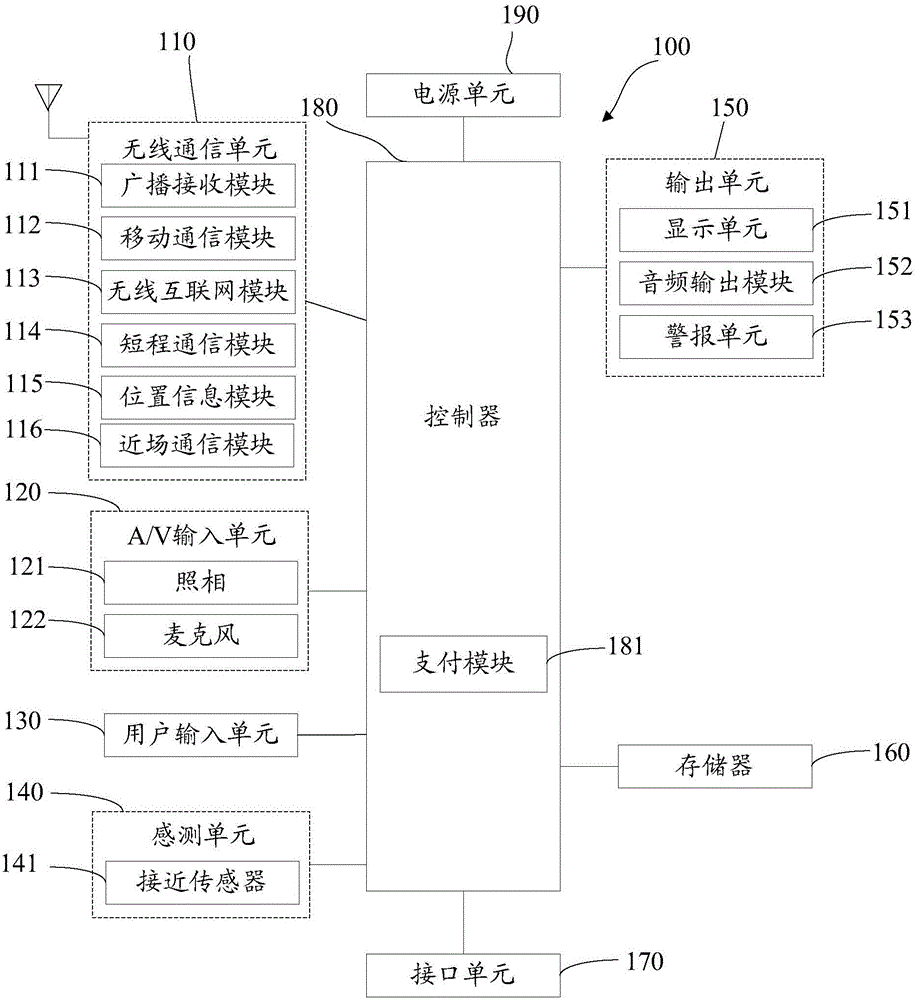
File protection method and system
ActiveCN103763313AShorten the accessible pathReduce complexityDigital data protectionTransmissionOperational systemComputer module
The invention discloses a file protection device which is arranged on a client side. The client side is provided with an operating system. The operating system is divided into a user space layer and a kernel layer. The file protection device comprises an encryption and decryption module and a self-protection module. The encryption and decryption module runs on the user space layer and monitors operation which is conducted on files by an application on the client side. When the file content is read by the application, the encryption and decryption module obtains encrypted file content from the client side, decrypts the encrypted file content, and places the decrypted content into a temporary storage space to be read by the application. When the file content is stored in the application, the encryption and decryption module encrypts the content in the temporary storage space and stores the encrypted file. The self-protection module runs in the kernel layer and monitors the temporary storage space so that other applications except the application can be prevented from having access to the temporary storage space. The invention further discloses a file protection system with the file protection device and a corresponding file protection method.
Owner:深圳市大成天下信息技术有限公司
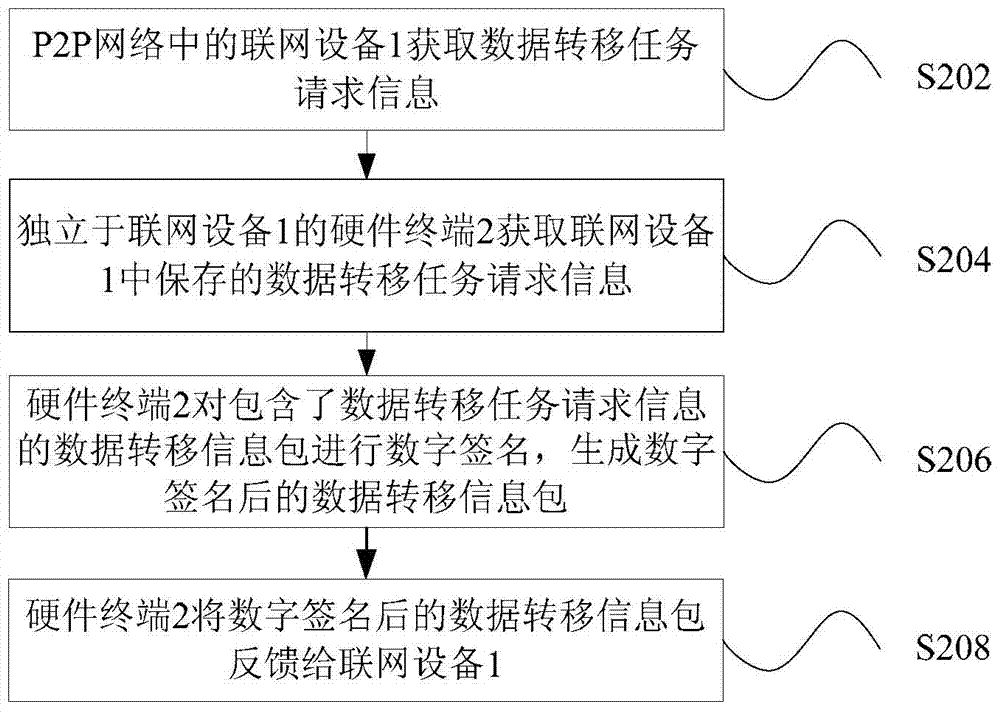
Task data processing method, device and system based on P2P network
InactiveCN103795807AImprove securityPrevent malicious theftUser identity/authority verificationDigital signatureComputer terminal
Owner:徐刚
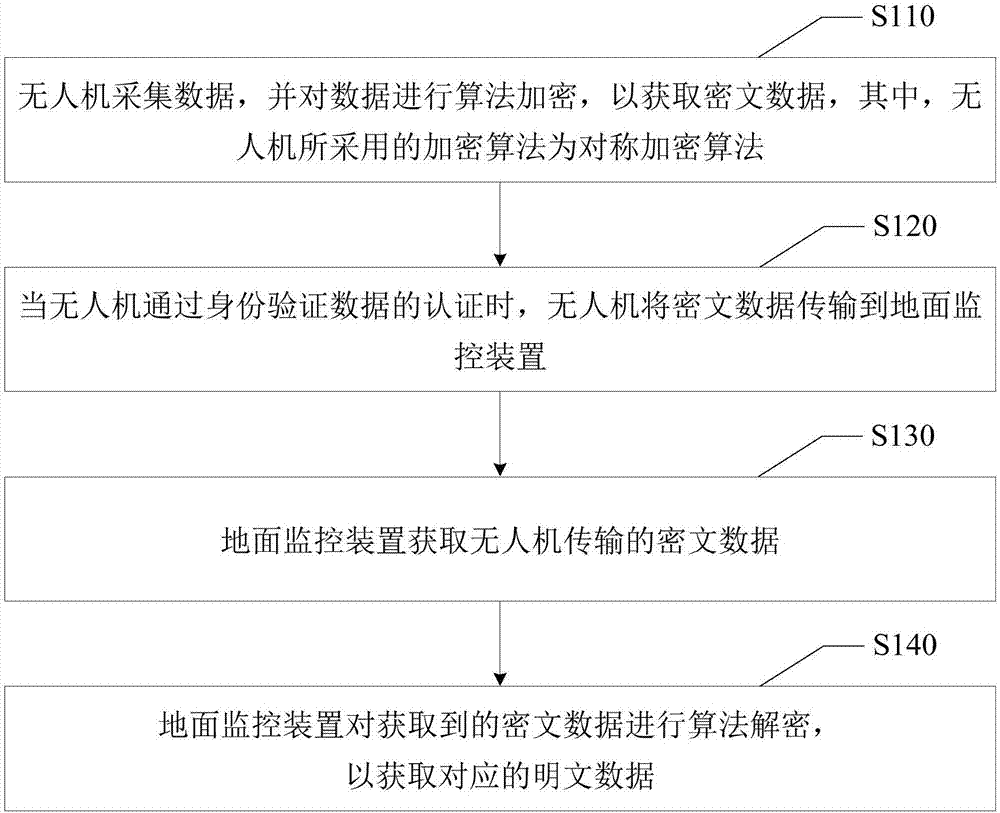
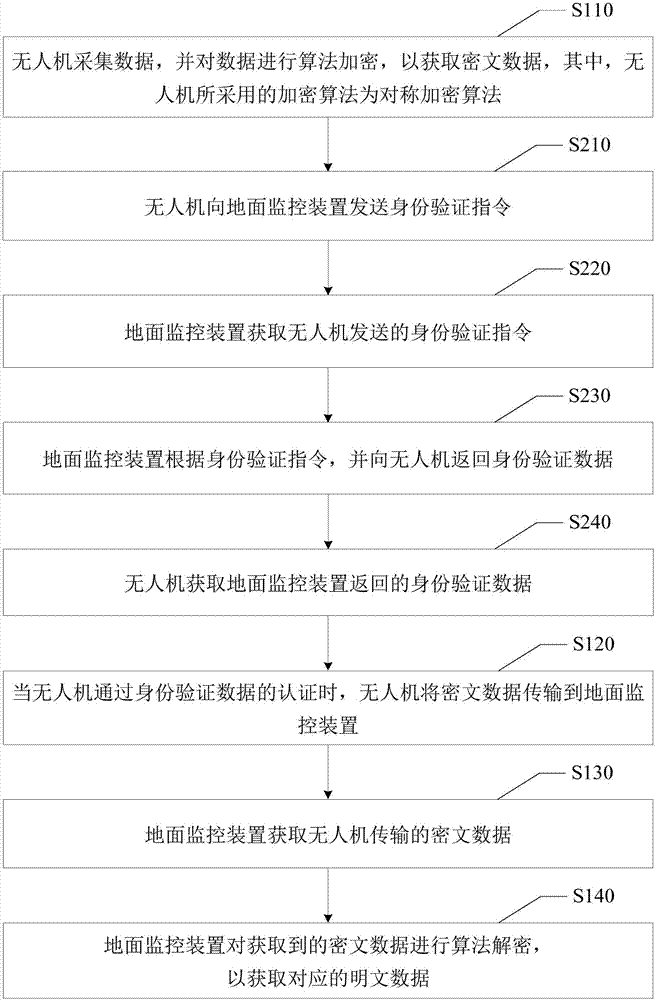
Flying drone data transmission method and flying drone data transmission system
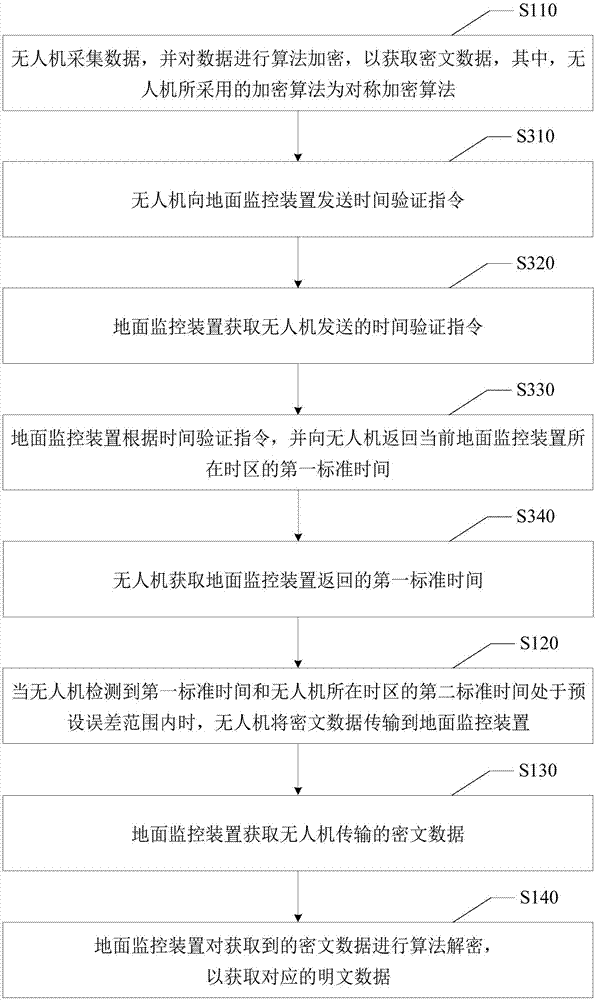
The invention discloses a flying drone data transmission method and a flying drone data transmission system, wherein the flying drone data transmission method comprises: the flying drone acquires data and performs algorithm ciphering to the data to obtain the ciphertext data wherein the ciphered algorithm the flying drone uses is a symmetrically ciphered algorithm; the flying drone transmits the ciphertext data to a ground monitoring device; the ground monitoring device obtains the ciphertext data transmitted from the flying drone; the ground monitoring device performs algorithm deciphering to the obtained ciphertext data to obtain corresponding clear data wherein the deciphering algorithm the ground monitoring device uses is the deciphering algorithm corresponding to the symmetrically ciphered algorithm used by the flying drone. According to the invention, through the manner of data ciphering, the data transmission security of the data transmission system of the flying drone is increased; the reliability of the data transmission is increased; therefore, the data theft or data tamp ering in the transmission process could be prevented, and the phenomenon of data leakage could also be avoided.
Owner:SHENZHEN ZHOUJI TONGHANG INVESTMENT HLDG CO LTD
Method and system for preventing illegal terminal from accessing as well as terminal
InactiveCN102056169APrevent malicious theftEnsure safetyTransmissionSecurity arrangementDevice typeUniversal subscriber identity module
The invention provides a method for preventing an illegal terminal from accessing, comprising the following steps that: when the terminal requests to access a network, a network side judges whether the equipment type of the terminal and / or equipment access capability is matched with signing data of a user or not; and if not, the network side refuses the terminal to access the network. The invention also provides a system for preventing the illegal terminal from accessing and the terminal for preventing the illegal access. By using the invention, the problem that illegal users maliciously embezzle a universal subscriber identity module (USIM) of MTC (Machine Type Communication) equipment to access to the network can be effectively prevented and the security of MTC communication can be ensured.
Owner:ZTE CORP
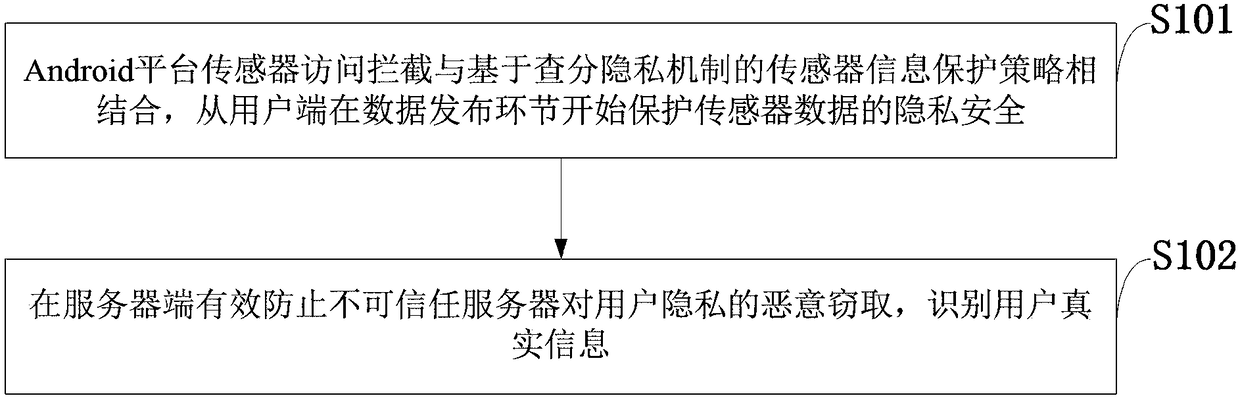
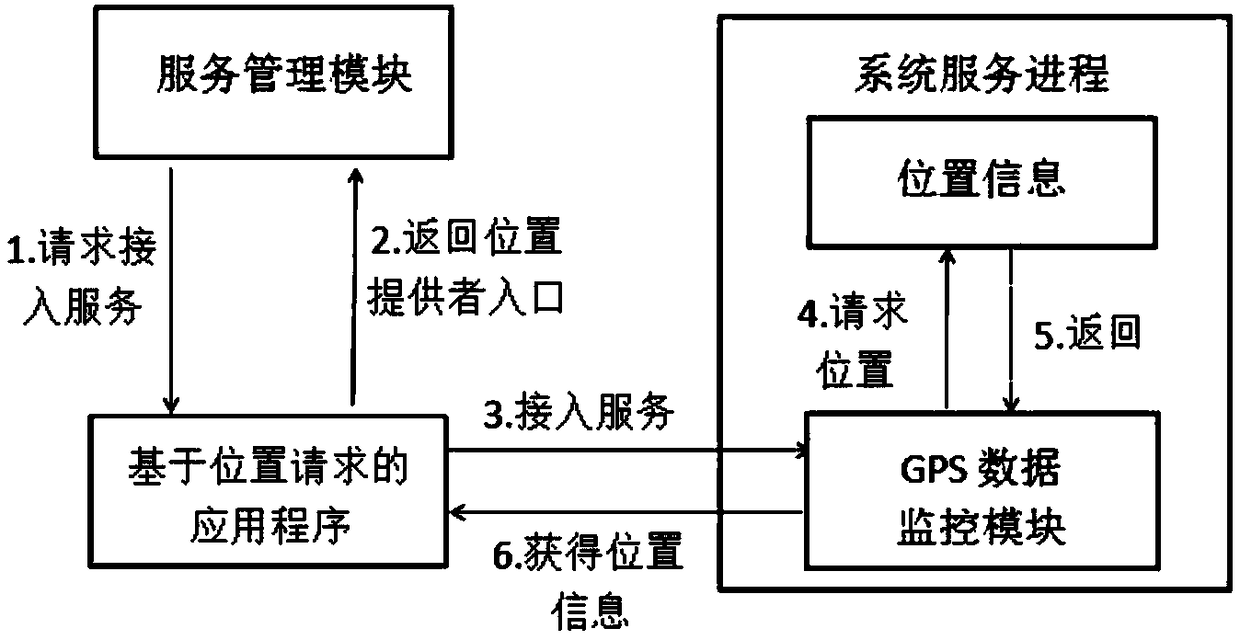
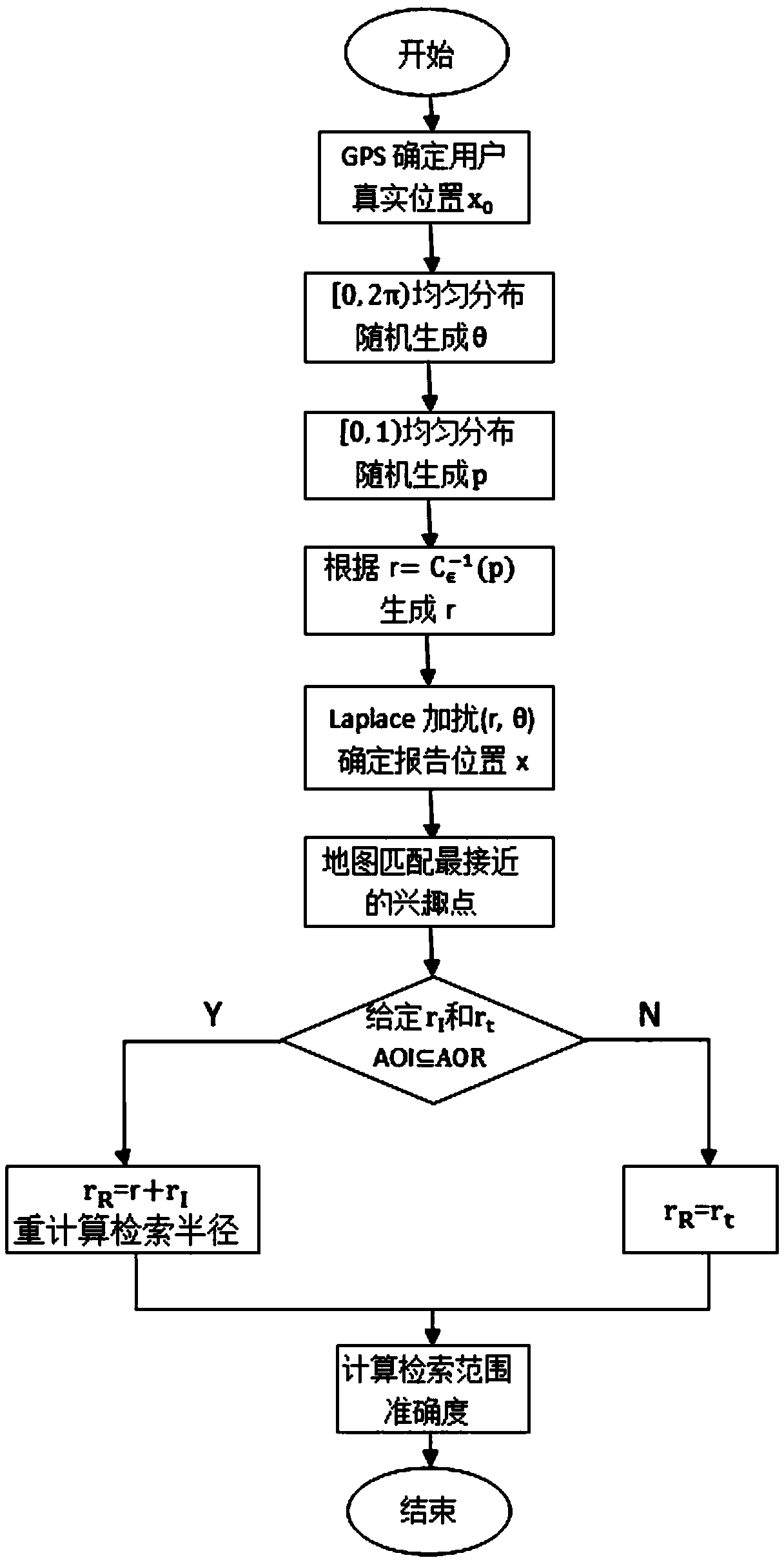
Android terminal sensor information protection method based on differential privacy
ActiveCN108595976AProtect privacy and securityImprove accuracyDigital data protectionSensing dataProtection mechanism
The invention belongs to the technical field of mobile platform privacy protection, and discloses an Android terminal sensor information protection method based on differential privacy. Android platform sensor access interception and a sensor information protection strategy based on a differential privacy mechanism are combined, the privacy security of sensor data can be protected from a user sidein a data release link, and meanwhile, the phenomenon that an untrusted server maliciously steals the user privacy can be effectively prevented at a server side, and real information of a user can beidentified. The differential privacy protection mechanism achieves the privacy protection effect by adding Laplacian noise, and thus the sensitivity of attackers to user background information can beeliminated, and the privacy security can be improved; by remapping random points subjected to noise adding and re-calculating a search area range, the reliability of sensing data and the availabilityof an application program can be guaranteed; and the scheme of the invention has important theoretical values and practical significance for the privacy protection of mobile terminals in the future.
Owner:XIDIAN UNIV
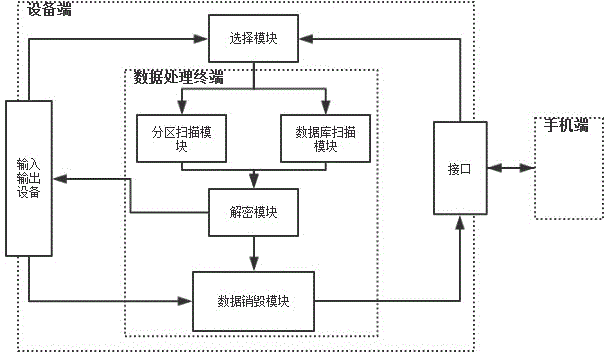
Device and method for destroying Android mobile phone body data
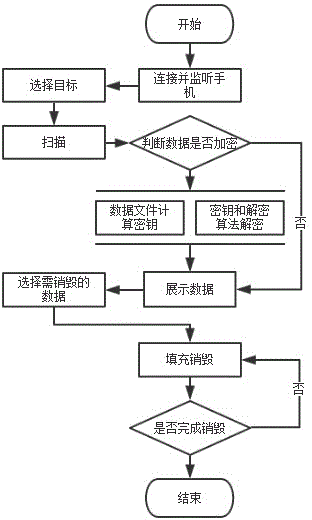
The invention discloses a device for destroying Android mobile phone body data. The device comprises an interface, an input and output device, a selection module and a data processing terminal. The interface is connected with a mobile phone through a USB data line, the interface and the input and output device are connected with the selection module and the data processing terminal at the same time, and the selection module is connected with the data processing terminal. The invention further discloses a method based on the device. The method comprises the steps that (1) the mobile phone is connected; (2) a scanning area is selected; (3) scanning is conducted; (4) encryption is judged and decryption is conducted; (5) the data are displayed; (6) the data are screened; (7) the data are destroyed; (8) whether data destroying is completed or not is judged. According to the device and the method, different areas of the mobile phone can be selected for conducting data scanning and destroying, the data scanned out can be displayed, files in need of destroying can be selected by a user, and the fragmented data in the mobile phone can be removed thoroughly on the condition that the normal data are not destroyed. The safety of the Android mobile phone data is guaranteed and malicious stealing of personal and corporate private data is prevented.
Owner:XLY SALVATIONDATA TECHNOLOGY INC
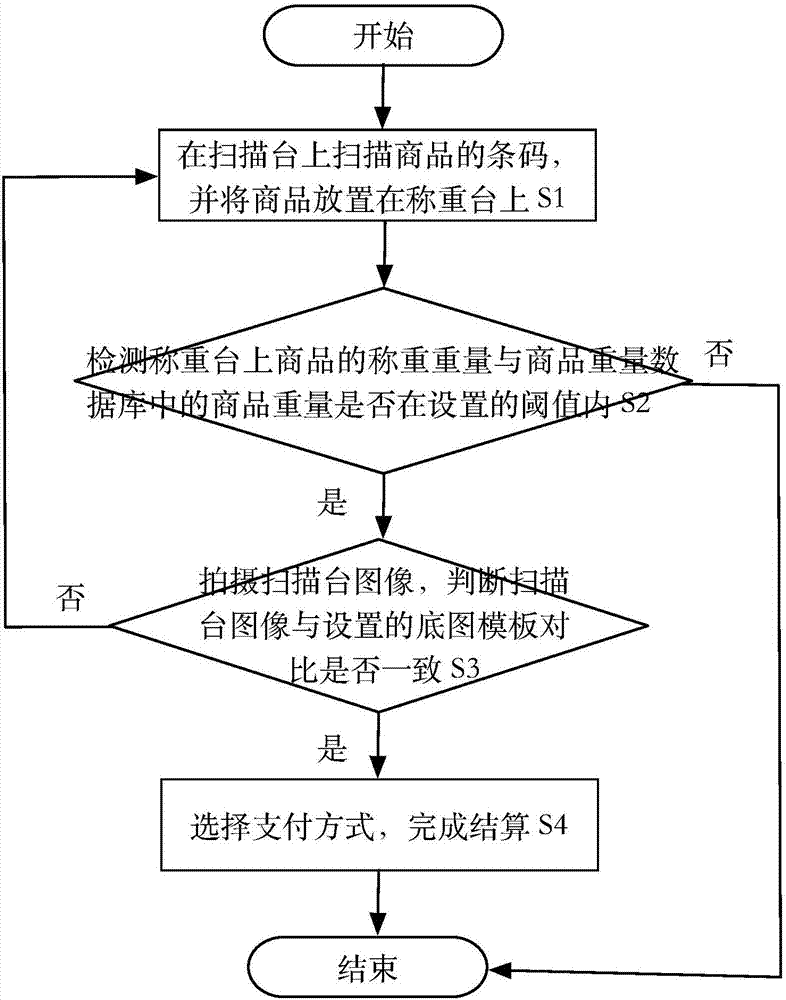
Self-service cashier system and method
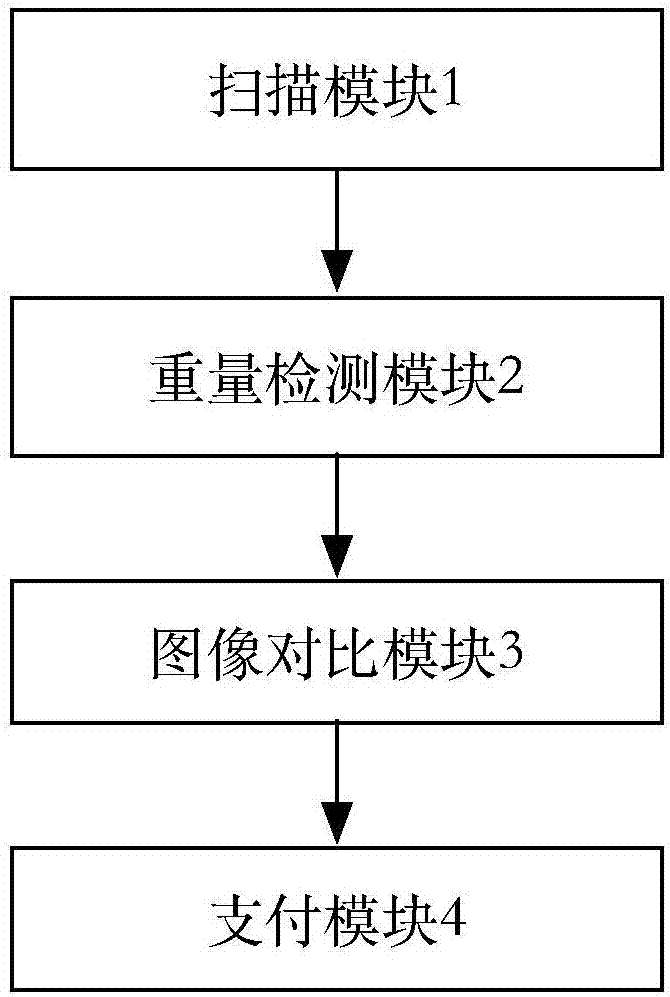
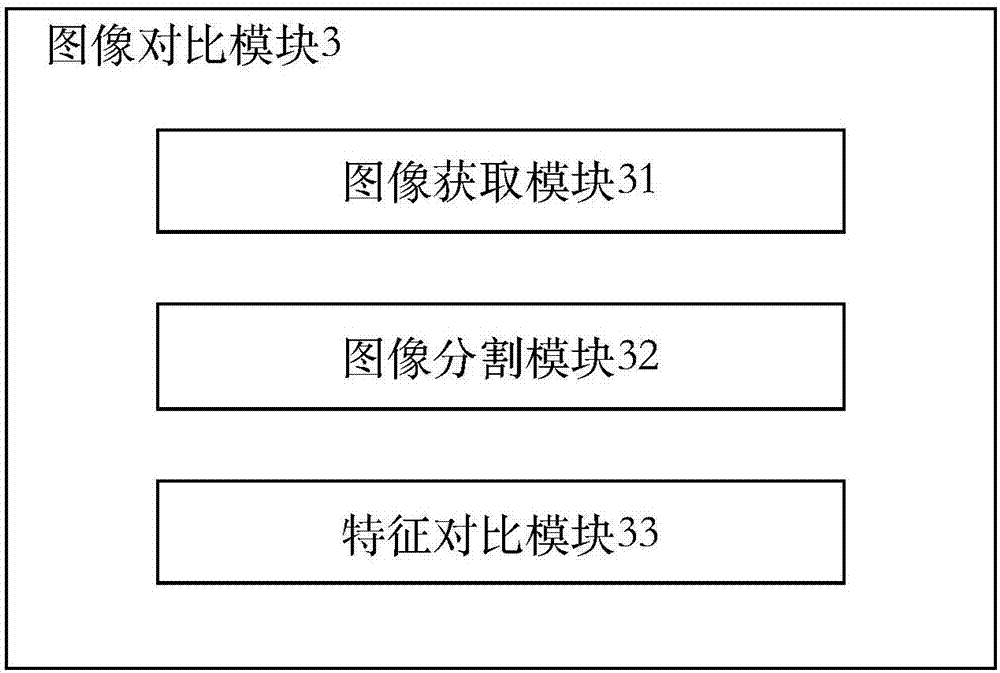
InactiveCN107038822AImprove securityAvoid misleadingCharacter and pattern recognitionCash registersPaymentVideo monitoring
The invention relates to a self-service cashier system and method. The system comprises a scanning module used for scanning bar codes of goods on a scanning table; a weight detection module used for detecting whether weighing weight of the goods and goods weight in a goods weight database are in a set threshold scope; an image comparison module used for shooting scanning table images and comparing the scanning table images with set base map templates; and a payment module provided with multiple payment modes for accomplishing payment. The system is advantaged in that the image shooting comparison technology is added to a self-service cashier system in the prior art, when the goods are on the scanning table, a shopper can not do the following operation, malicious theft can be prevented, misleading video monitors of markets, supermarkets or convenience stores can be avoided, economic loss of the markets, the supermarkets or the convenience stores can be effectively reduced, and safety is improved.
Owner:杭州赛狐科技有限公司
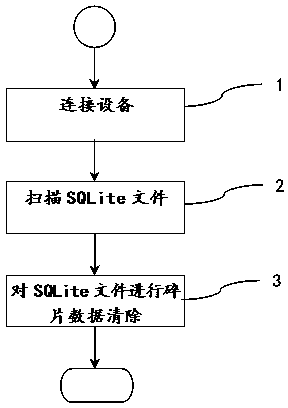
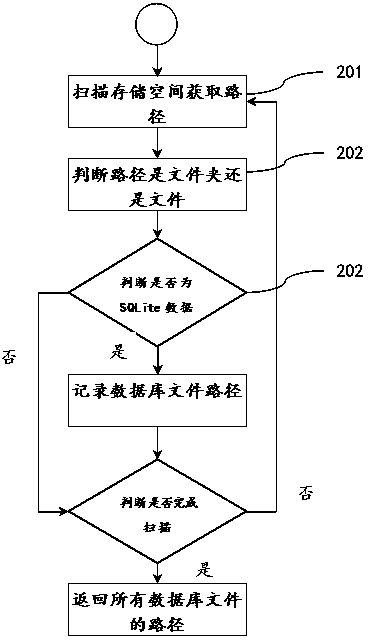
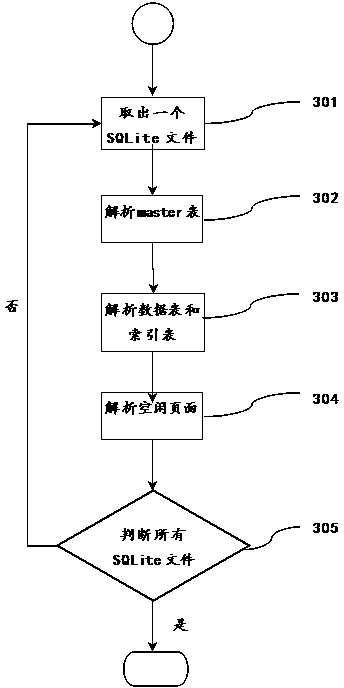
Method for clearing data in SQLite database
ActiveCN104298766AEasy to scanPrevent malicious theftSpecial data processing applicationsDatasheetNonnormal data
The invention discloses a method for clearing data in an SQLite database. The method comprises the following steps that S1, a device comprising the SQLite database is connected to establish a connection channel with the device; S2, all SQLite files in a memory space of the device are scanned to obtain a storage path; S3, the scanned SQLite files are analyzed one by one, and abnormal data clearing is carried out. The method has the advantages that scanning is complete, all the SQLite files in the memory space can be found out, and all areas in the SQLite are scanned and marked; clearing is complete, abnormal data of master tables, data tables, index tables and free pages in the SQLite files are scanned and cleared, malicious steal of privacy data is prevented, and safety of privacy data is protected.
Owner:MWH TECH LLC
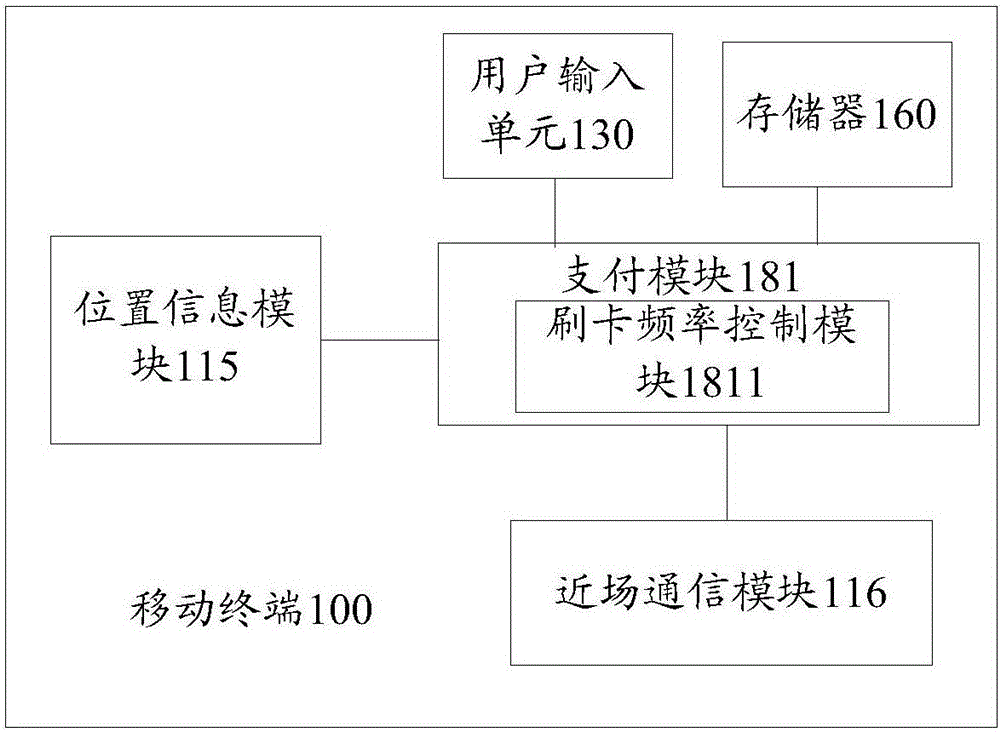
Near field paying method and mobile terminal
InactiveCN105868979AImprove securityPrevent malicious theftProtocol authorisationPaymentComputer terminal
The invention discloses a mobile terminal and a near field payment method. The mobile terminal includes: a near field communication module, a payment module and a position information module. The near field communication module is intended for receiving a payment request which is transmit by a payment reception terminal and transmitting the payment request to the payment module. The payment module is intended for when the payment request is received from the near field communication module, transmitting a position request of current position information of the mobile terminal to the position information module. The position information module is intended for when the position request is received from the payment module, acquiring the current position information of the mobile terminal and transmitting the current position information to the payment module. The payment module is also intended for, when the current position information of the mobile terminal acquired by the position information module belongs to a preset payment area, determining whether the received payment request meets a preset payment condition, and when the determination result is that the received payment request meets the preset payment condition, the payment module starts a payment flow and completes a near field payment. According to the invention, the technical solution can prevent the possibility of malicious unauthorized card using in near field payment.
Owner:NUBIA TECHNOLOGY CO LTD
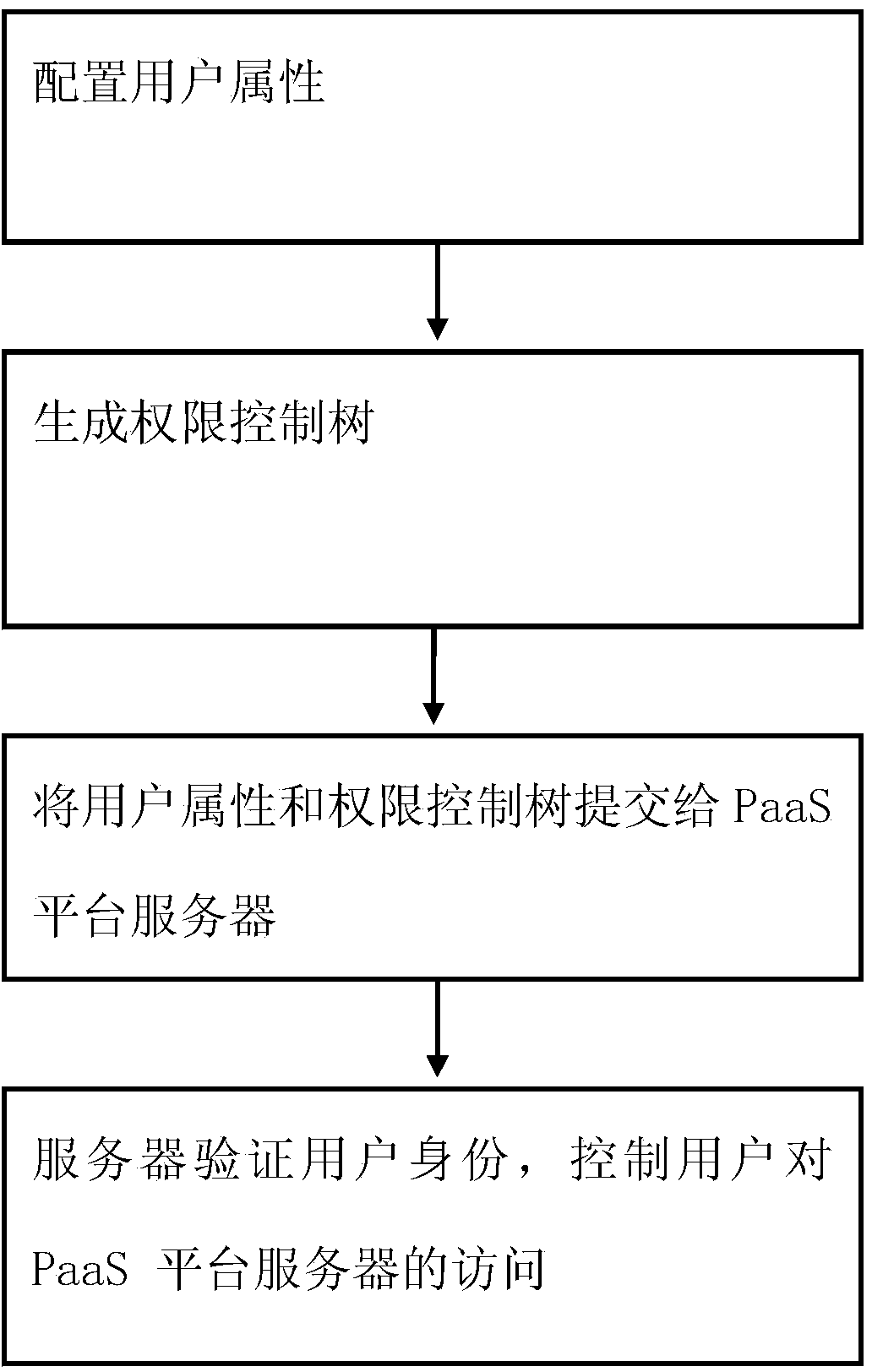
Method and system for safe cloud computing
InactiveCN104184736APrevent malicious theftImprove securityTransmissionClient-sideMobile cloud computing
The invention provides a method and system for safe cloud computing. The method comprises the steps that user property configuration is conducted on the client side; a right control tree is generated and the user role right is controlled; a user logs in a PaaS platform server to submit the user property of the client side and the right control tree to the PaaS platform server; the server verifies the identity of the user when the user requires to have access to the PaaS platform server, and controls the access of the user to the PaaS platform server according to a verification result. According to the method and system for safe cloud computing, a method for property encryption deployment in a PaaS platform is provided, malicious stealing of a database on the PaaS server side is prevented, and the safety of enterprise user data is effectively improved.
Owner:GUANGXI POWER GRID CORP
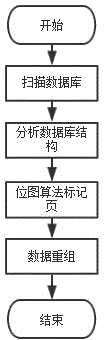
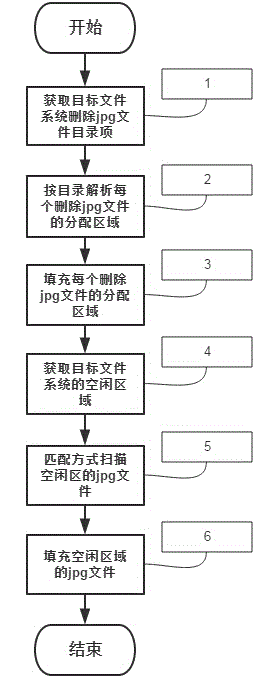
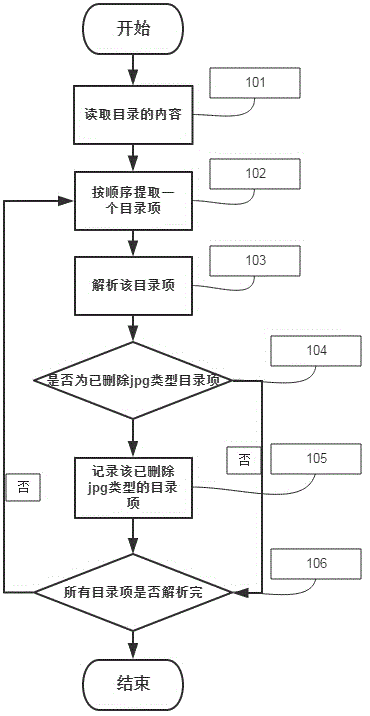
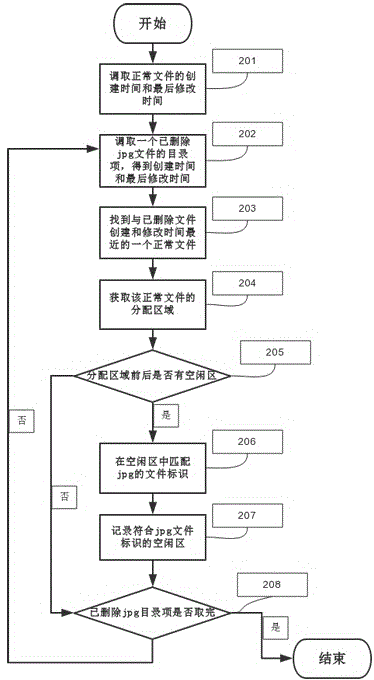
Method for completely removing deleted jpg format in FAT 32 document system
ActiveCN104699794AGuaranteed data privacyPrevent malicious theftSpecial data processing applicationsPP-formatDatabase
The invention discloses a method for completely removing a deleted jpg format in a FAT 32 document system. The method comprises the following steps: S1: Searching all directory entries of the deleted jpg format document; S2: analyzing the directory entries and obtaining a distribution area of the jpg document; S3: writing in and filling empty value in the distribution zone; S4: obtaining a clear area position; S5: scanning and matching the clear area, and finding out fragment data; S6: writing in empty value and filling. Through a bottom layer, the method can analyze the deleted jpg document in the FAT 32 document system by, and find out the fragment data position of the deleted jpg document. The method ensures the safety of the normal jpg document while completely removes the jpg formatted document. Through the jpg document, the jpg document fragments in the clear area are removed for the second time, and thereby all fragment data are removed at the maximum degree, the public privacy is guaranteed, and malicious stealing behavior specific to private data is prevented.
Owner:MWH TECH LLC
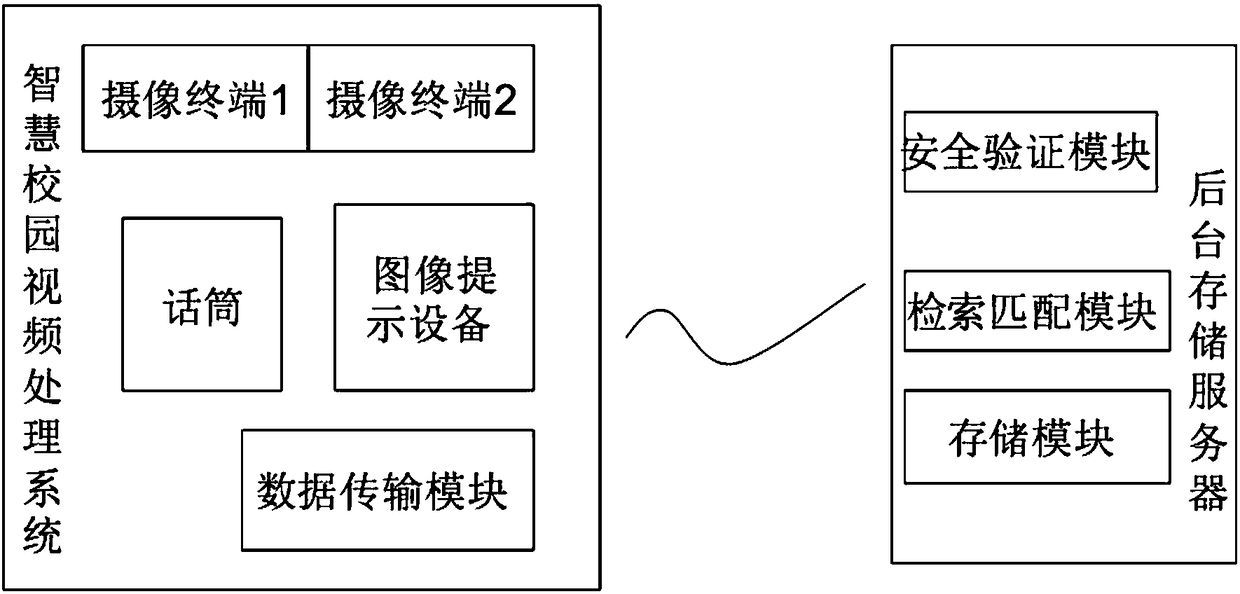
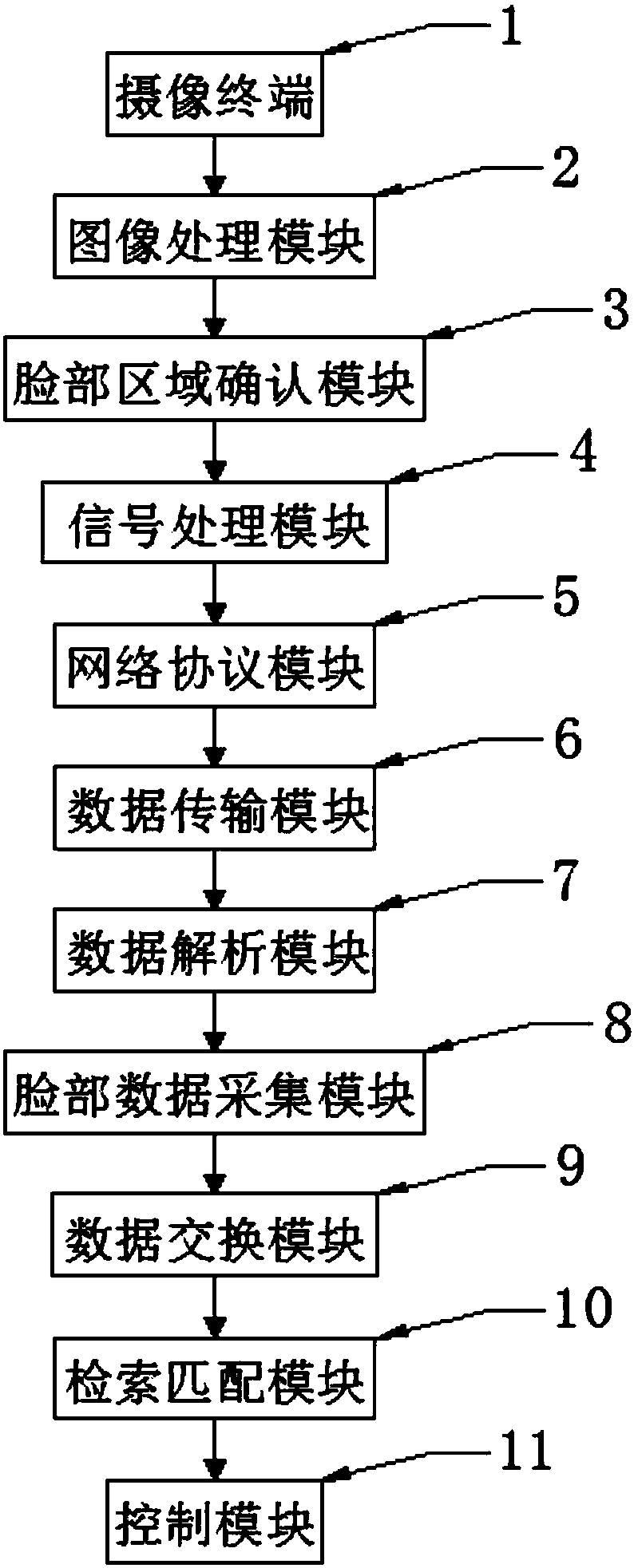
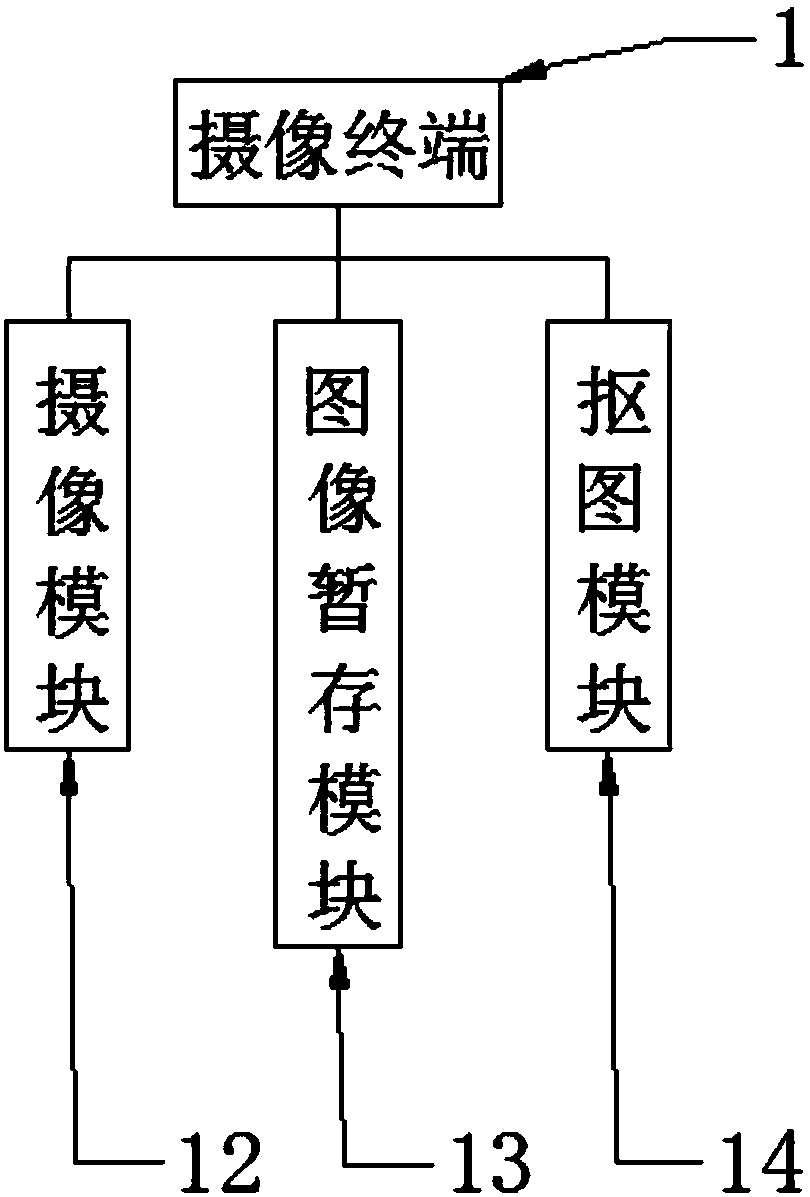
Smart campus video processing system
InactiveCN108600627APrevent malicious misappropriation or theft of informationEnsure safety and stabilityTelevision system detailsCharacter and pattern recognitionData transmissionData analysis
The invention discloses a smart campus video processing system, including an image capturing terminal, wherein the bottom of the image capturing terminal is provided with an image processing module, the bottom of the image processing module is provided with a face region confirming module, the bottom of the face region confirming module is provided with a signal processing module, the bottom of the signal processing module is provided with a network protocol module, the bottom of the network protocol module is provided with a data transmission module, the bottom of the data transmission moduleis provided with a data analysis module, the bottom of the data analysis module is provided with a face data collection module, the bottom of the face data collection module is provided with a data exchange module, the bottom of the data exchange module is provided with a search matching module, and the bottom of the search matching module is provided with a control module. The invention has thebeneficial effects of effectively preventing from malicious theft or information stealing, and ensuring the security and stability of the smart campus.
Owner:DONGGUAN POLYTECHNIC
Remote vehicle locking system of battery electric vehicle and control method thereof
ActiveCN107554481AImprove securityPrevent malicious theftAnti-theft devicesTransmissionComputer terminalBattery electric vehicle
The invention discloses a remote vehicle locking system of a battery electric vehicle. The remote vehicle locking system comprises a vehicle control unit, a monitoring terminal, a combination instrument, a base station, a server and a service terminal. The monitoring terminal and the combination instrument are connected with the vehicle control unit through a CAN bus. The monitoring terminal conducts wireless communication with the base station. The server conducts wireless communication with the base station and the service terminal. The technical problem that as for an existing vehicle locking system, people cannot be informed timely about whether a vehicle is locked successfully or not is solved.
Owner:YANGZHOU YAXING MOTOR COACH
Monitoring method and monitoring system
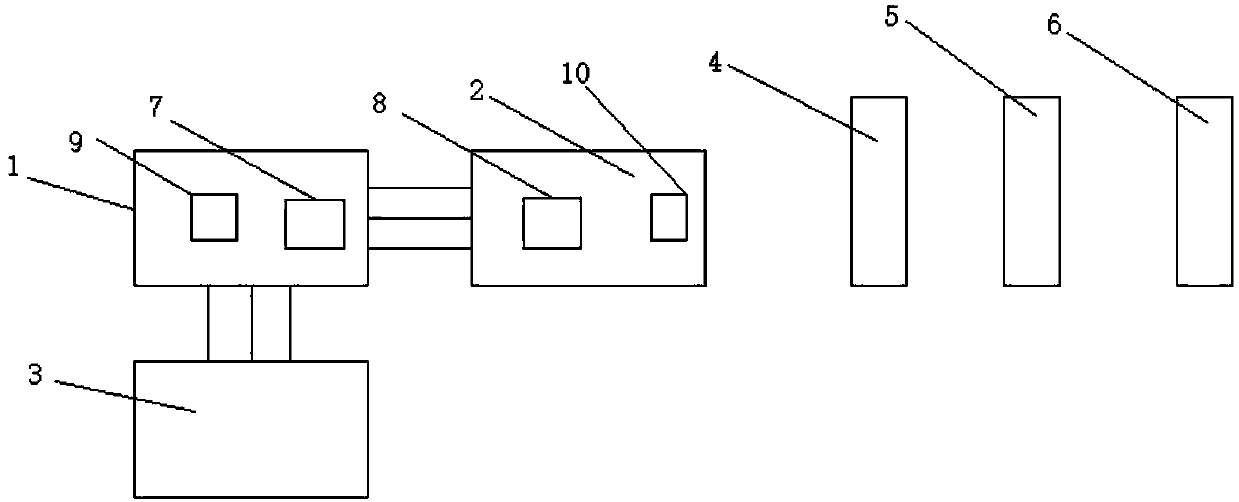
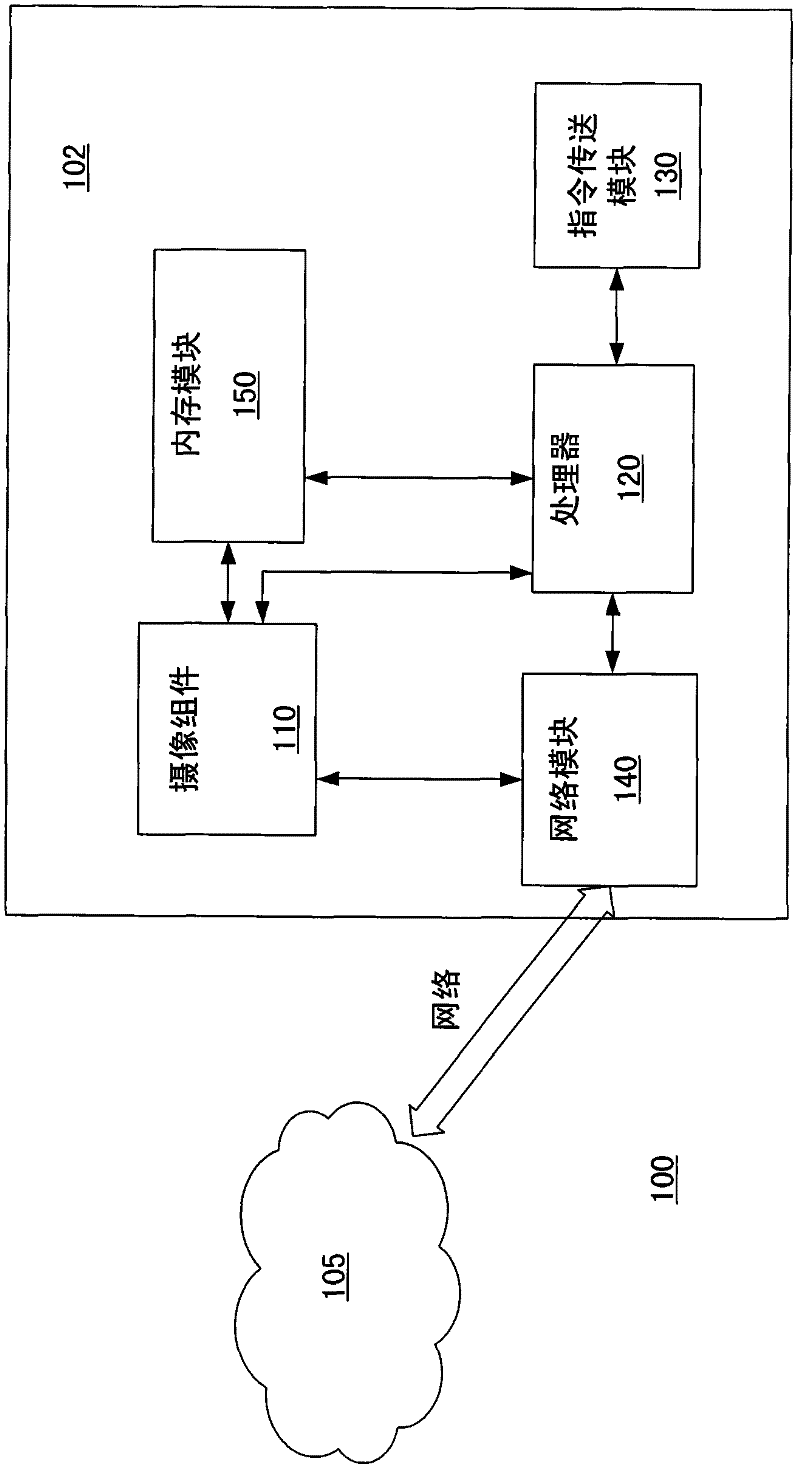
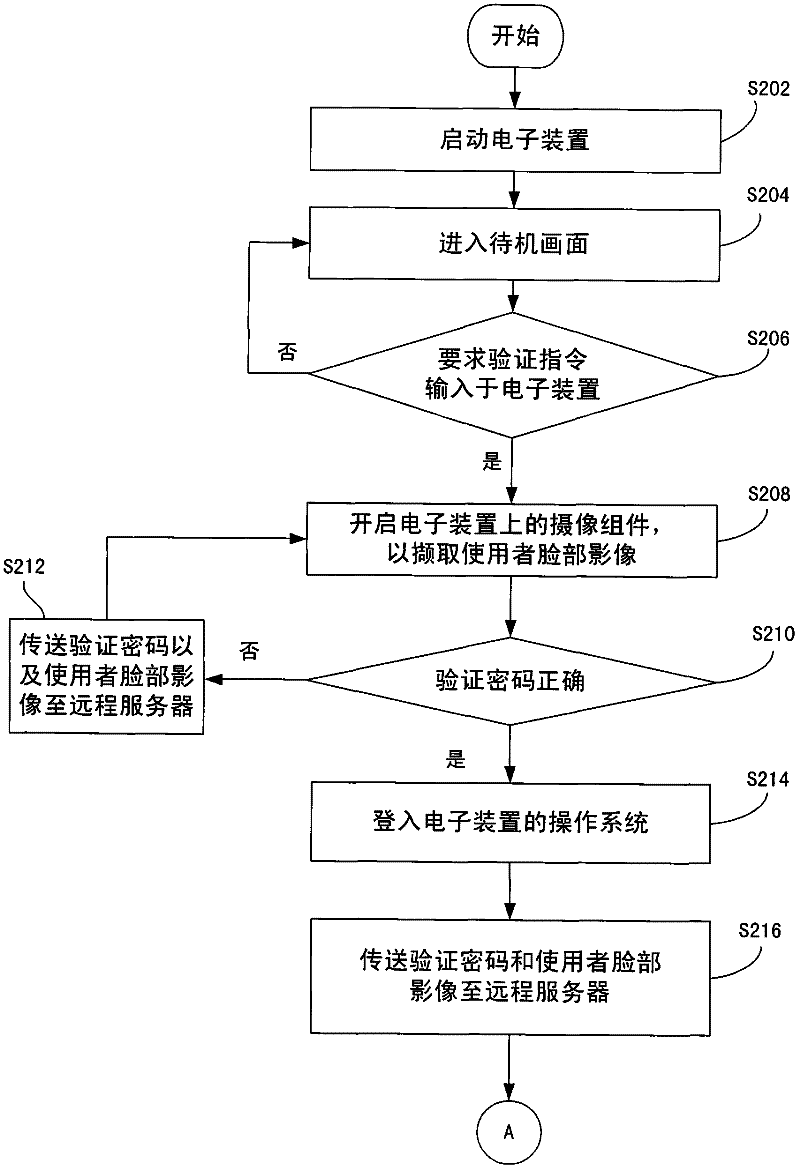
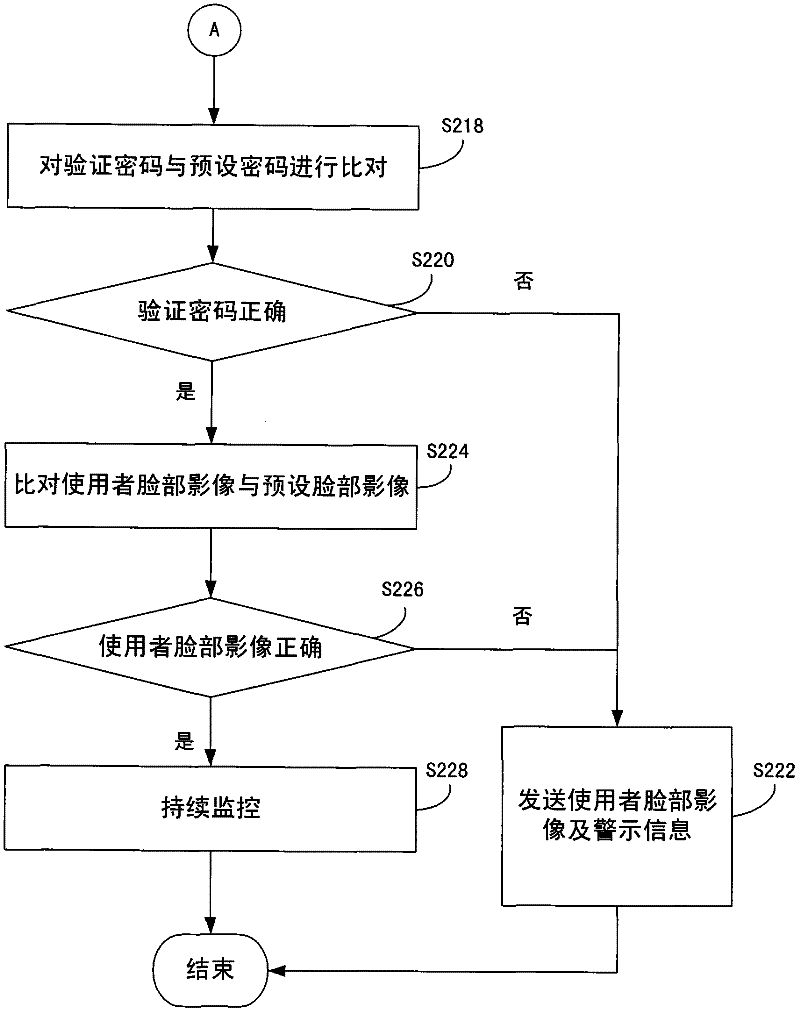
InactiveCN102479299AMonitor usagePrevent malicious theftPlatform integrity maintainancePasswordMonitoring system
The invention discloses a monitoring method and a monitoring system. The monitoring system comprises an electronic device and a remote server. In the electronic device, a processor starts a photographing component after receiving a request verification command output by a command transmitting module, so as to control the photographing component to capture a face image of a user. The processor judges a verification password, and transmits the verification password and the face image of the user when the verification password is incorrect. The remote server is in communication connection with the electronic device via a network, and confirms at least one of the verification password and the image face of the user. When at least one of the verification password and the face image of the user is confirmed to be wrong, the remote server sends the face image of the user and the warning information.
Owner:INVENTEC CORP
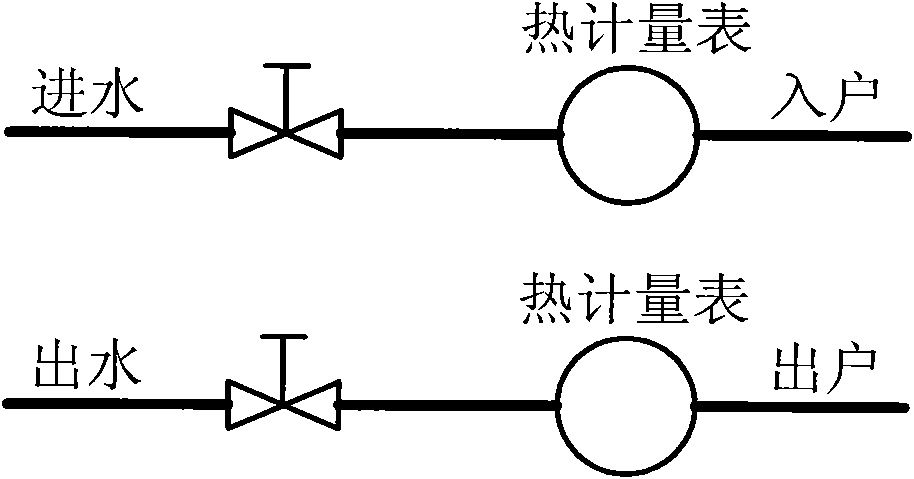
Wireless heat meter based on ZigBee technology
InactiveCN101799335AExtended service lifeImprove reliabilityTransmission systemsCalorimeterHigh humidityLiquid-crystal display
The invention discloses a heat metering device for cold water and hot water, which realizes that bidirectional flow for water inflow and backwater is detected, a temperature signal and a flow signal are wirelessly transmitted without external connection leads, and operations of wireless charging and wireless meter reading can be carried out. The wireless heat meter is suitable for cold water and hot water. The heat metering device is provided with a reflection ultrasonic flow meter, a temperature sensor, a Zigbee controller and an LCD liquid crystal display device. The reflection ultrasonic flow meter is connected in series in a water inlet (or backwater) pipeline; the temperature sensor is arranged inside the flow meter; the Zigbee controller is arranged on the upper part of the flow meter; and the LCD liquid crystal display device is arranged on the top of the flow meter. Hardware, circuits and software of two devices which are matched to use are all same, the software firstly automatically sets a device connected with a high-temperature pipe to be a master node mode, and sets a device connected with a low-temperature pipe to be an auxiliary node mode when the two devices are used, the two modes can be regularly switched, the faults are automatically switched and a double-controller is simultaneously operated in parallel. The heat metering device for cold water and hot water is suitable for severe environment, such as strong electromagnetic interference, high voltage, high temperature, high humidity and the like, and is widely applied to a cold water / hot water concentrated air-conditioner heating system, thereby realizing separate metering for one meter each household.
Owner:陈建明 +6
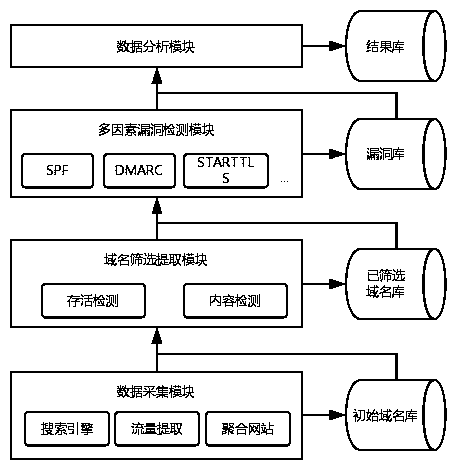
Email security protection detection technology based on multiple factors
InactiveCN109474611ASolve the defect of relay transmissionGuaranteed confidentialityData switching networksDomain nameInternet privacy
The invention relates to an email security protection detection technology based on multiple factors, and designs an email security detection model based on the multiple factors aiming at the problemthat the email with a Chinese domain name is lack of security detection. The technology comprises the steps of extracting different types of true and effective domain name data based on a data collection and domain name screening module; and then, detecting implementation conditions of email security extension protocols such as SFP, DMARC and STARTTLS based on a multi-factor vulnerability detection and data analysis module.
Owner:SICHUAN UNIV
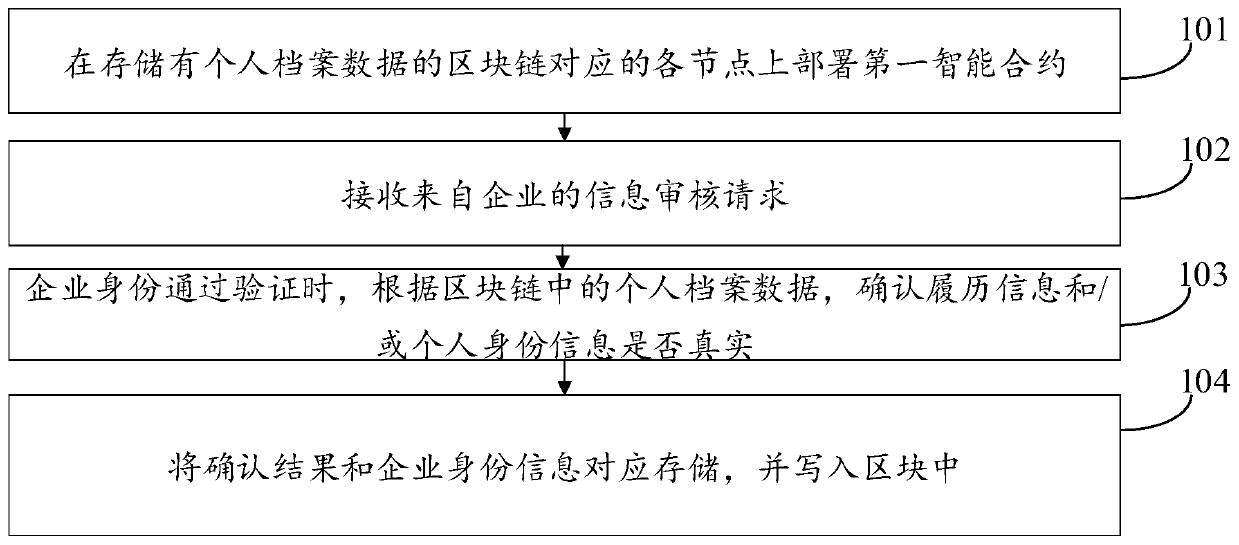
Resume record management method and device based on block chain, and medium
PendingCN111008821AAccurate identificationGuarantee authenticityDatabase distribution/replicationOffice automationBusiness enterpriseEngineering
The invention discloses a resume record management method and device based on a block chain and a medium. The method comprises the following steps of deploying a first smart contract on each node corresponding to the block chain storing personal file data, wherein the triggering condition of the first smart contract is that an information auditing request sent by an enterprise is detected andthe enterprise identity information of the enterprise passes the verification, and the information auditing request comprises the enterprise identity information, the resume information of a job seeker andthe personal identity information of the job seeker; when contract execution is set in the first smart contract, determining whether the record information and / or the personal identity information are / is true or not according to personal archive data in the block chain; and correspondingly storing a confirmation result and the enterprise identity information, and writing the confirmation result and the enterprise identity information into a block. According to the invention, a resume can be accurately identified, so that the operation risk and the labor cost of enterprises are reduced.
Owner:浪潮云洲工业互联网有限公司
Product packing structure with invisible identification code and code recognition method of product packing structure
ActiveCN106005743ASimple structureEasy to manufactureContainer decorationsLevel indicationsPattern recognitionIdentity theft
The invention discloses a product packing structure with an invisible identification code and a code recognition method of the product packing structure. The product packing structure comprises a packed product and a packing body. The identification code is marked on the packing body. The color of the identification code is lighter than the background color of the packed product, so that a reverse contrast is formed. The packing body is transparent or semi-transparent in the identification code area. The corresponding code recognition method comprises the following steps that the packing body is separated from the packed product; and the identification code on the packing body is scanned in the backlighting environment. The product packing structure and the code recognition method have the advantages that the structure is simple; manufacturing is convenient; malicious identity theft can be effectively prevented in the manufacturing, circulating and selling links of a product; and most of packing materials are directly coded, so that the processing technology is simplified, and the manufacturing cost is reduced.
Owner:上海凌脉网络科技股份有限公司
Method and system for running application software on intelligent terminal as well as related equipment
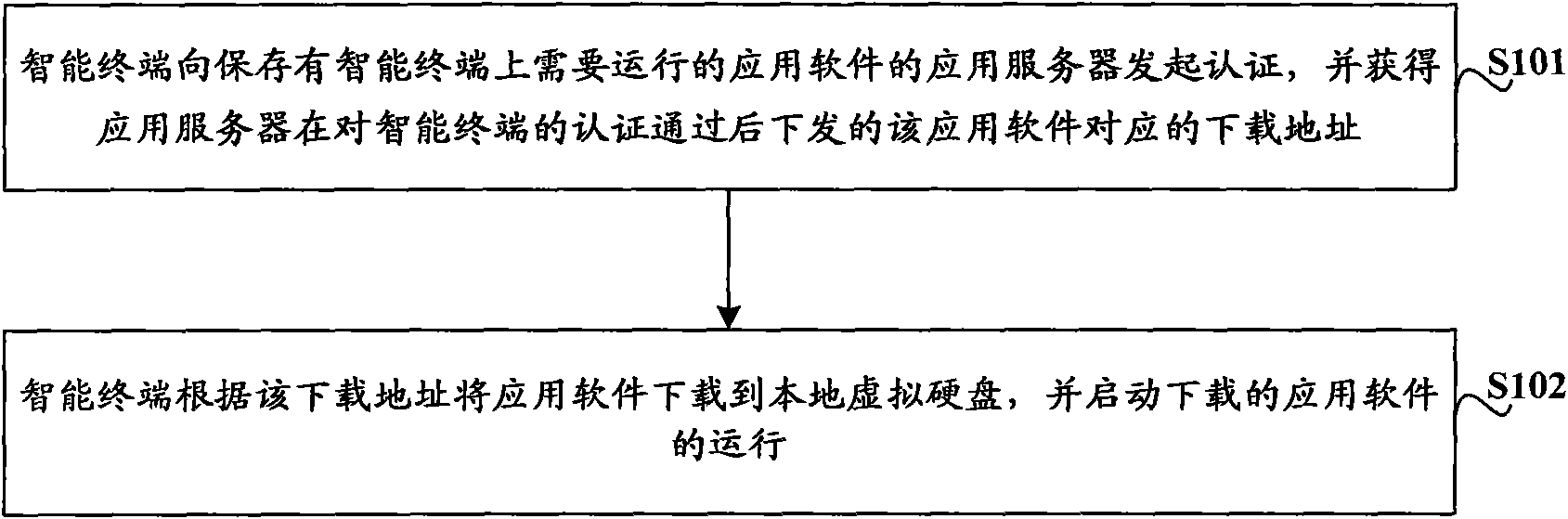
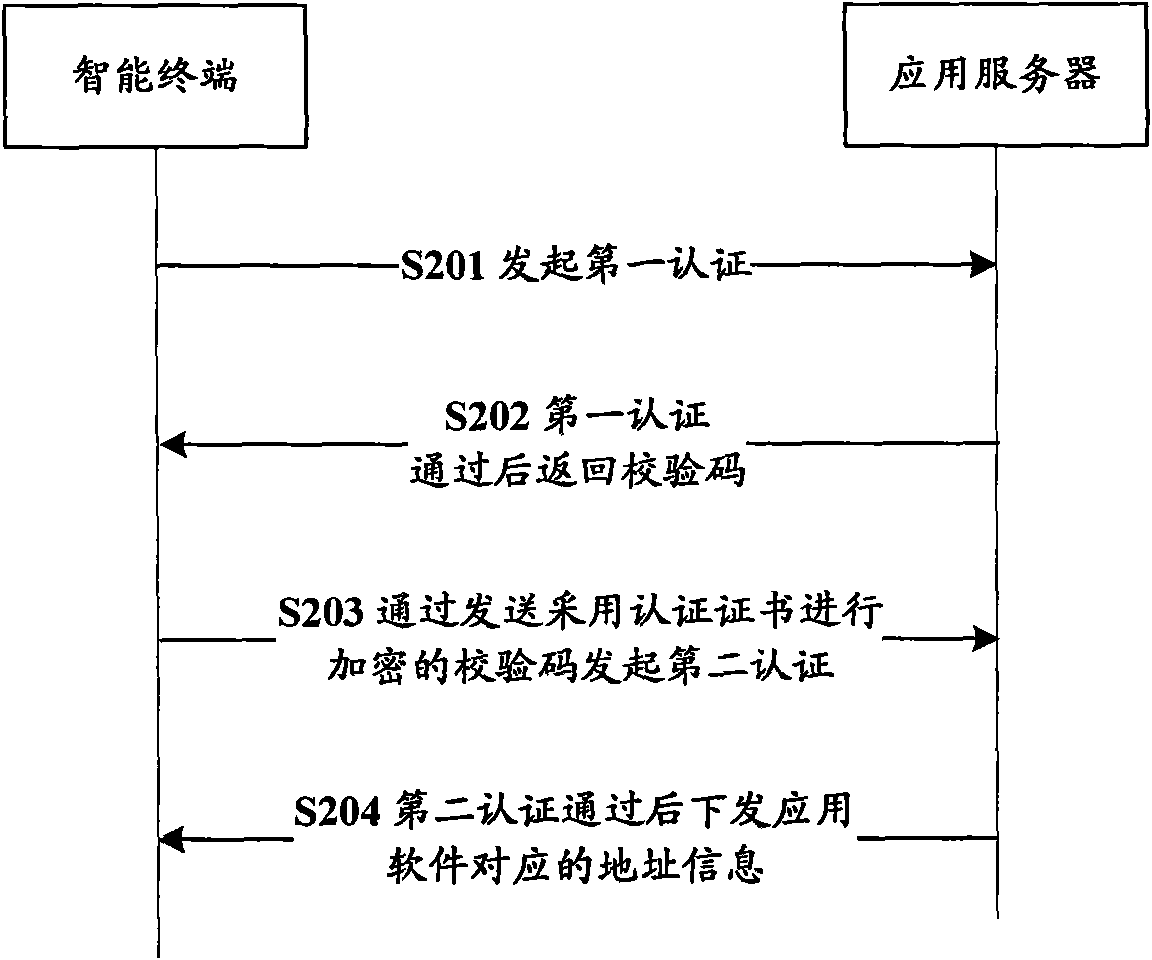
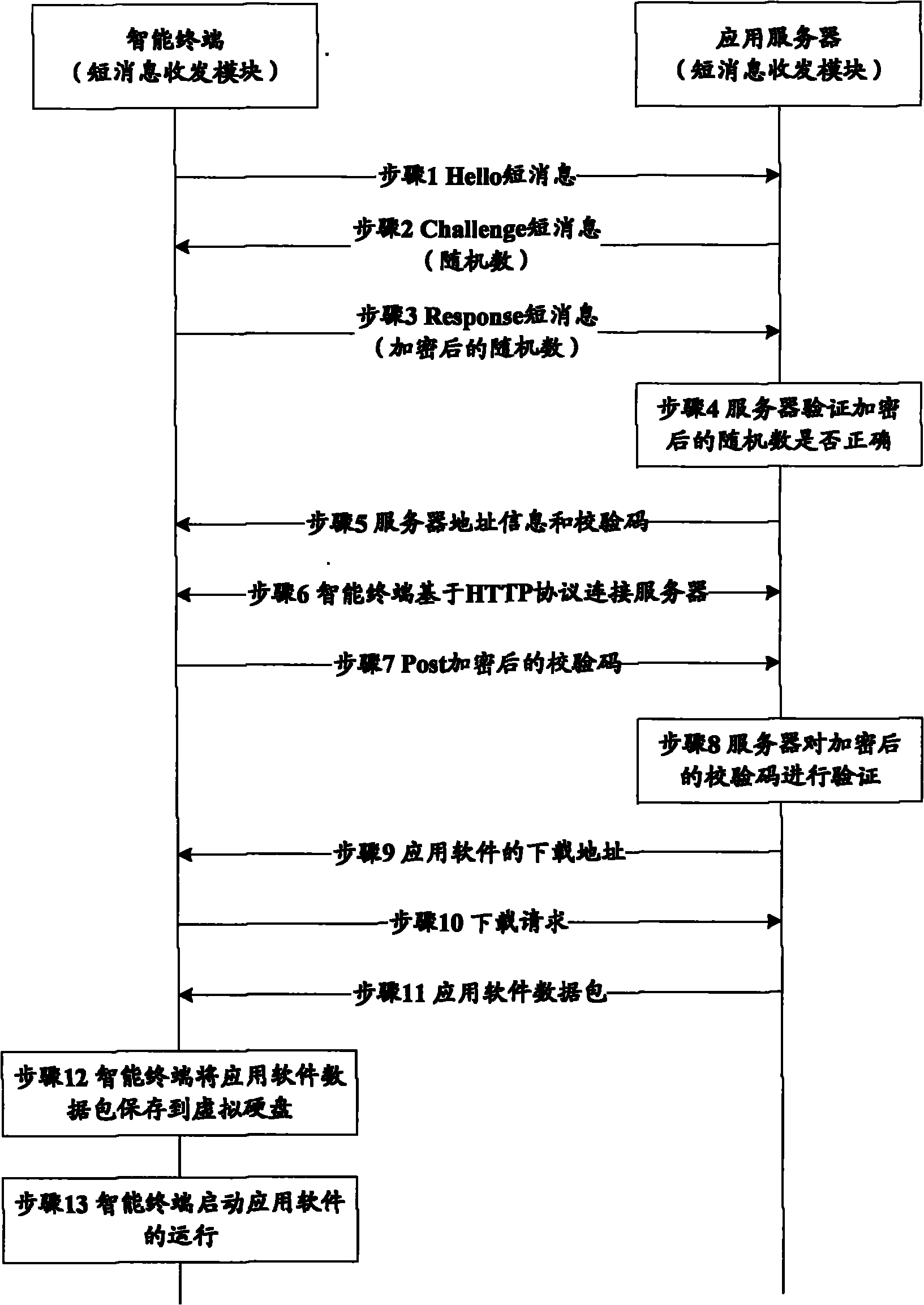
ActiveCN102075933AGuaranteed uptimePrevent malicious theftSecurity arrangementApplication serverSoftware engineering
The invention discloses a method and system for running application software on an intelligent terminal, used for improving the security of the application software on the premise of ensuring the normal operation of the intelligent terminal. The method for running the application software on the intelligent terminal comprises the following steps of: issuing an authentification to an application server by the intelligent terminal and acquiring an issued download address corresponding to the application software after the authentification of the server to the intelligent terminal is passed, wherein the application server stores the application software to be run on the intelligent terminal; and downloading the application software to a local visual hard disk by the intelligent terminal according to the download address and starting to run the downloaded application software. The invention also provides the intelligent terminal and the application server.
Owner:CHINA MOBILE GROUP JILIN BRANCH
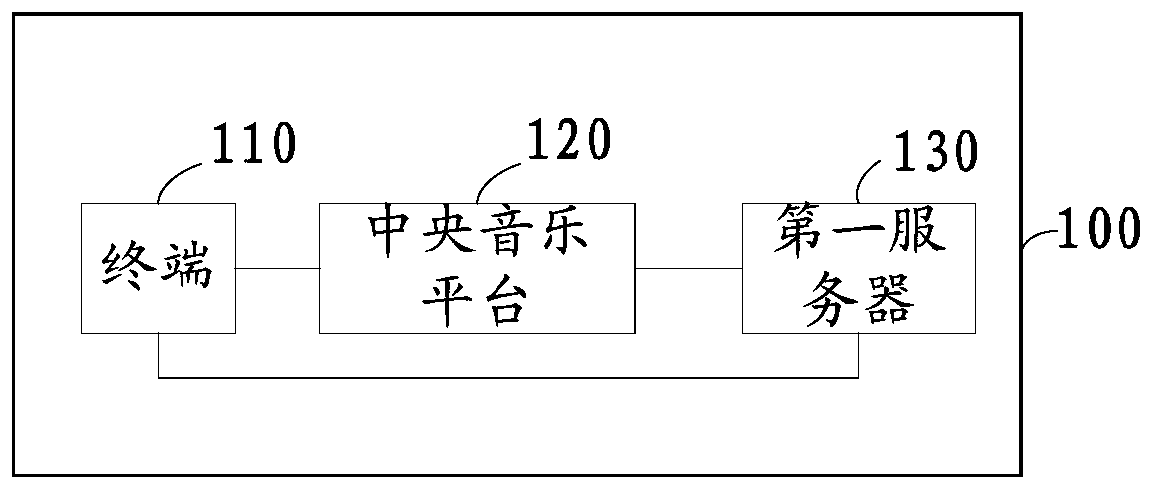
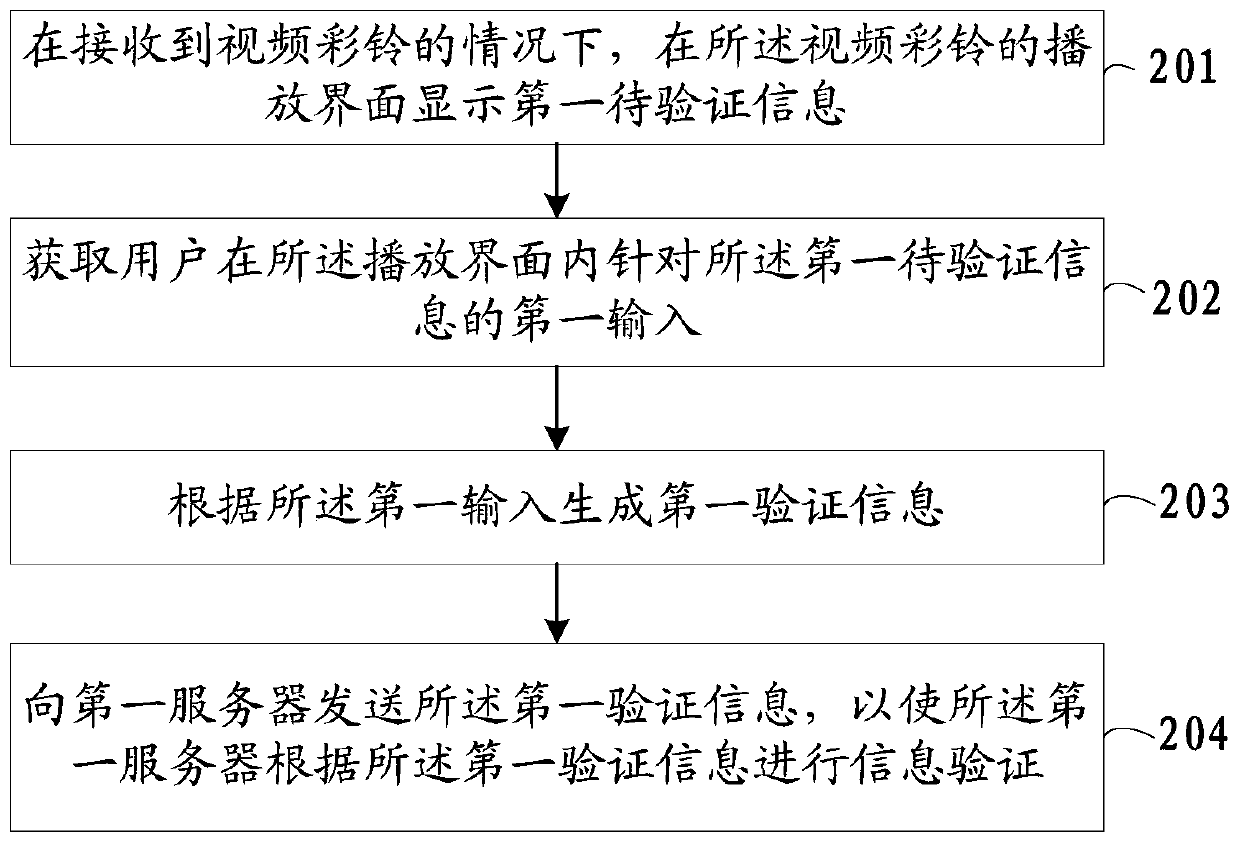
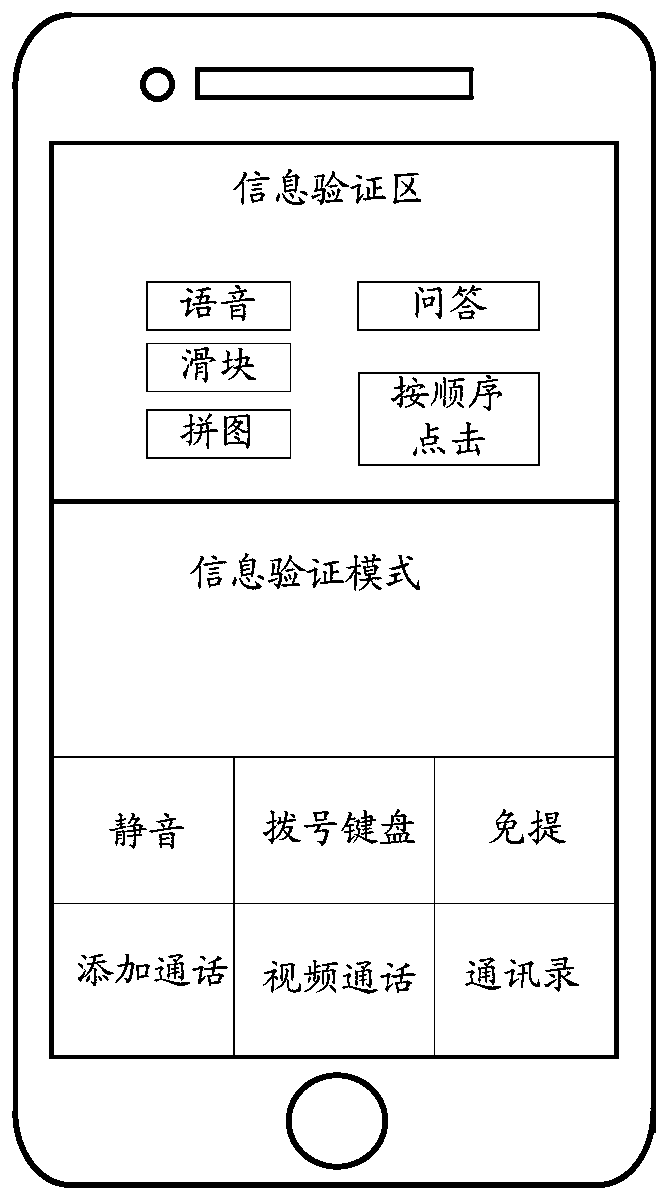
Information verification method and system, communication equipment and computer readable storage medium
ActiveCN110620786AReduce waiting timeSimplify verificationSpecial service for subscribersSubstation equipmentRisk ControlDynamic data
The invention provides an information verification method and system, communication equipment and a computer readable storage medium. The method comprises the following steps: displaying first to-be-verified information on a play interface of a video polyphonic ringtone under the condition that the video polyphonic ringtone is received; acquiring a first input of a user for the first to-be-verified information in the playing interface; generating first verification information according to the first input; and sending the first verification information to a first server, so that the first server performs information verification according to the first verification information. According to the embodiment of the invention, the information verification mode of the risk control behavior is carried out through the video polyphonic ringtone, a user completes information verification on the playing interface of the video polyphonic ringtone, the verification link is simplified, and the waiting time of the user is shortened; verification information is presented in a dynamic data mode in the transmission and presentation process, malicious stealing and peeping can be effectively prevented, and the safety of information verification is improved.
Owner:MIGU COMIC CO LTD +1
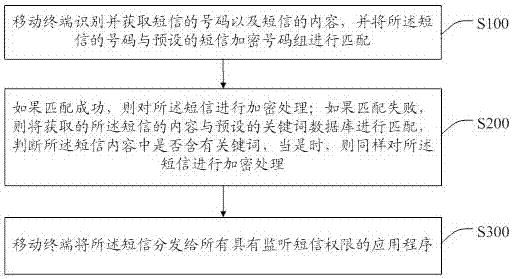
Method for automatically encrypting short messages, storage equipment and mobile terminal
ActiveCN107509180APrevent malicious theftGuarantee information securityMultiple keys/algorithms usageMessaging/mailboxes/announcementsComputer terminalInformation security
The invention discloses a method for automatically encrypting short messages, storage equipment and a mobile terminal. The method comprises the following steps: before distributing the received messages to an application, separately matching the number and contents of the short messages with a preset short message encrypted number group and a keyword database, when the match is successful, encrypting the short messages, and then distributing the short messages to the application with short message monitoring permissions. Thereby, the contents of the short messages can be encrypted before the application receives the short messages, the phenomenon that the important information in the short messages is maliciously stolen by the application can be prevented, the information security of users can be ensured, and the loss caused by the leakage of the important information can be avoided.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
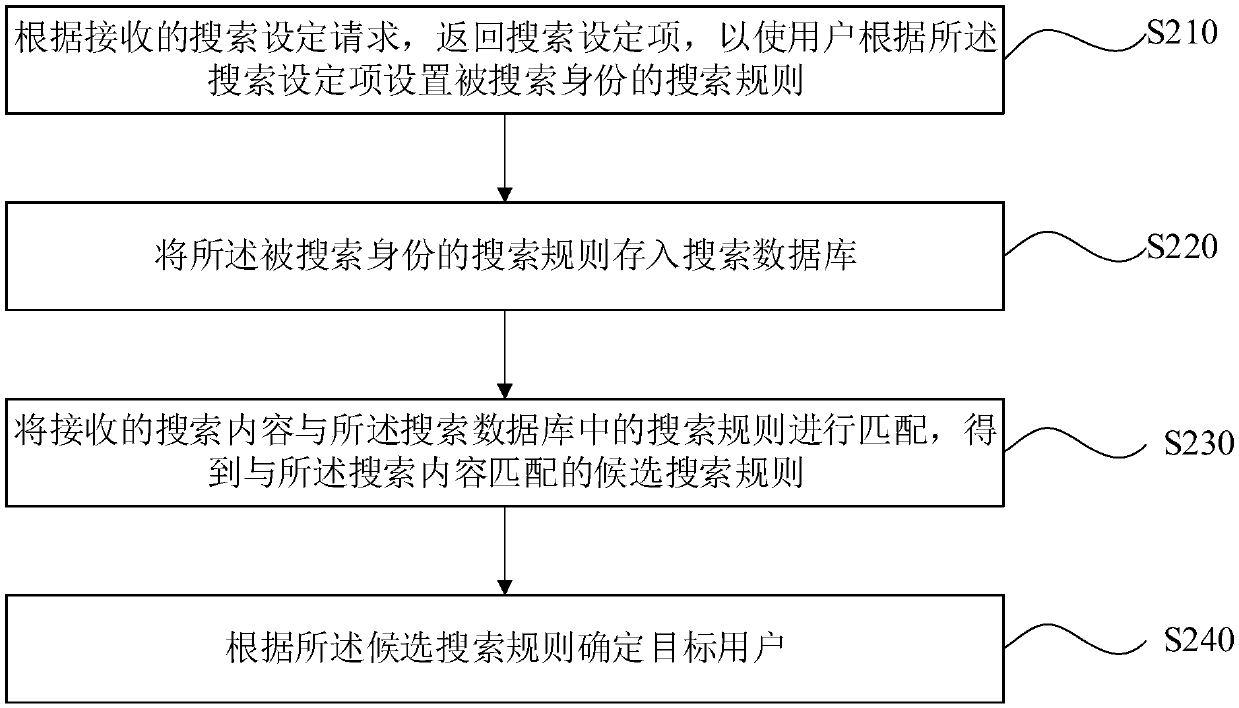
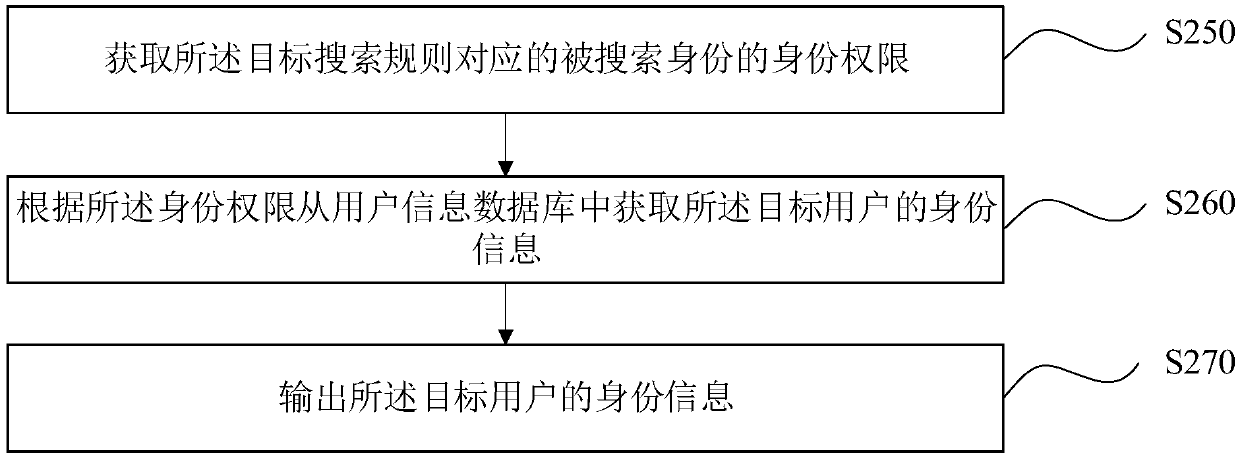
Method, device, computer device and storage medium for searching people based on social network
ActiveCN108875083AProtection of personal informationPrevent malicious theftData processing applicationsDigital data protectionSocial circleCrowds
The invention relates to a method, device, computer device and storage medium for searching people based on a social network. Firstly, the method is based on a search database which is established byusing the self-defined identity by a user, and the search database does not contain the personal information of the user, then, the user sends the search content to a server through a terminal and performs the search operation, the searched content is matched with the content in the search database to obtain a candidate search rule, and the user corresponding to the searched identity is obtained.As the search rule in the search database in the method is set based on the search intention when the user sets the searched identity, the user can automatically control the population in the social circle (namely, the particular population that can search him) by the user. Furthermore, the search database which does not contain the personal information of the user is used in performing the searchrule matching, the personal information of the user can be effectively protected, and the personal information of the user can be prevented from being maliciously stolen by using a method of a largeamount of searching and splicing.
Owner:重逢(北京)科技有限公司
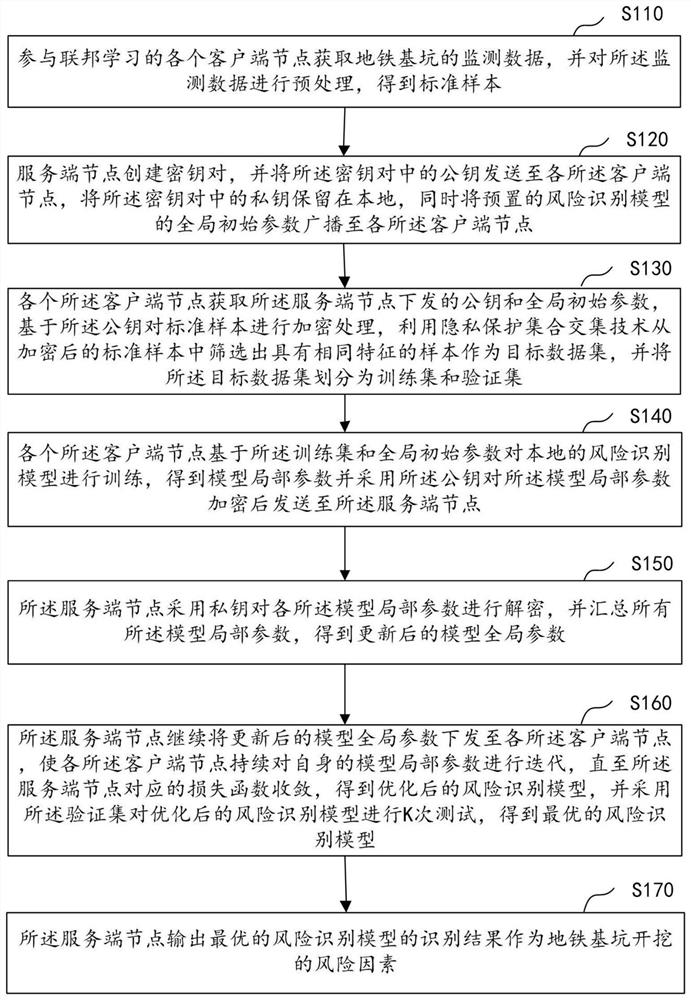
Subway foundation pit excavation risk identification method and device based on federated learning
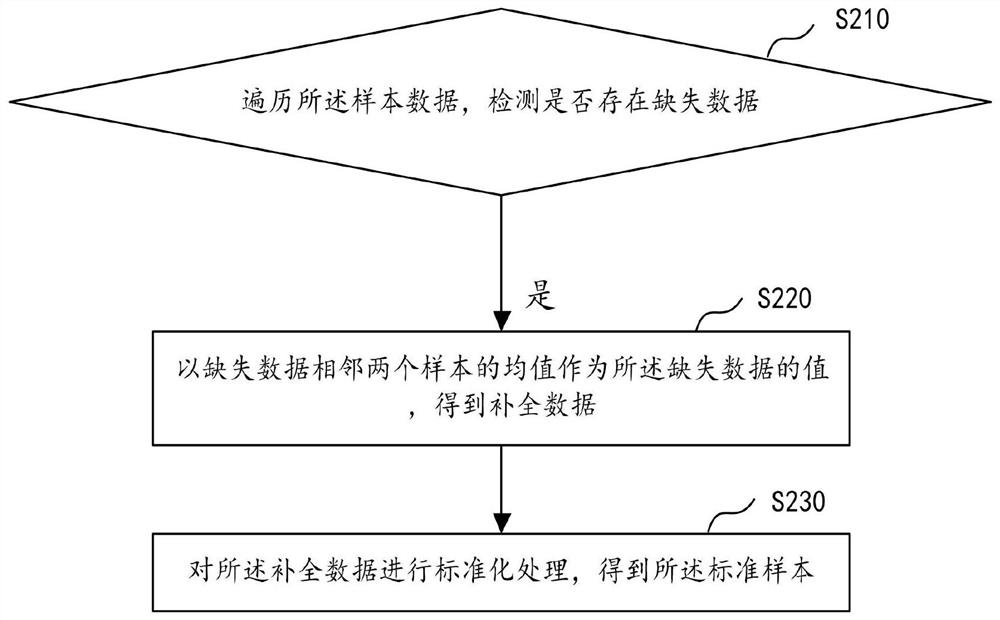
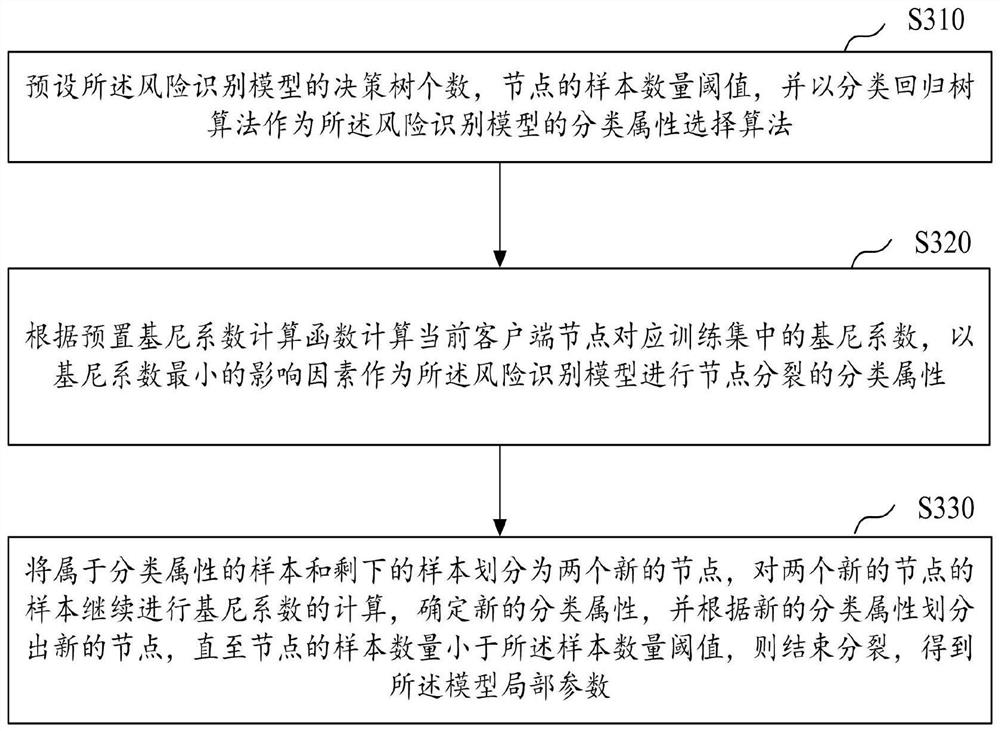
ActiveCN114021168AImprove accuracyImprove efficiencyDigital data protectionData setRisk identification
Embodiments of the invention disclose a subway foundation pit excavation risk identification method and device based on federated learning. The method comprises the following steps: each client node participating in federated learning acquires monitoring data of a subway foundation pit and obtains a standard sample; each client node performs encryption alignment processing on the local standard sample, and screens out a target data set from the encrypted standard sample; each client node trains a risk identification model based on the target data set to obtain local model parameters; a server node summarizes all local model parameters to obtain updated global model parameters, and feeds back the updated model global parameters to each client node; each client node continuously iterates, uploads and receives local parameters of the model until a loss function corresponding to the server node converges, and an optimized risk identification model is obtained; the optimized risk identification model is tested by adopting a verification set to obtain an optimal risk identification model; and a recognition result is determined by using the optimal risk recognition model. The method is higher in accuracy.
Owner:SHENZHEN UNIV
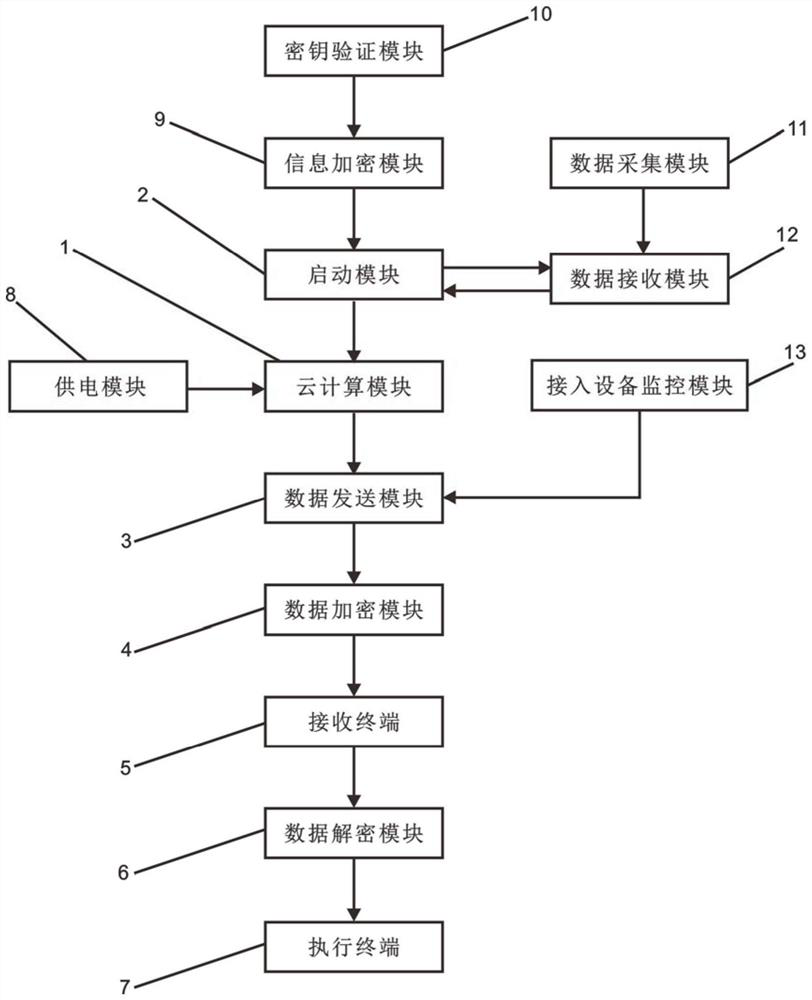
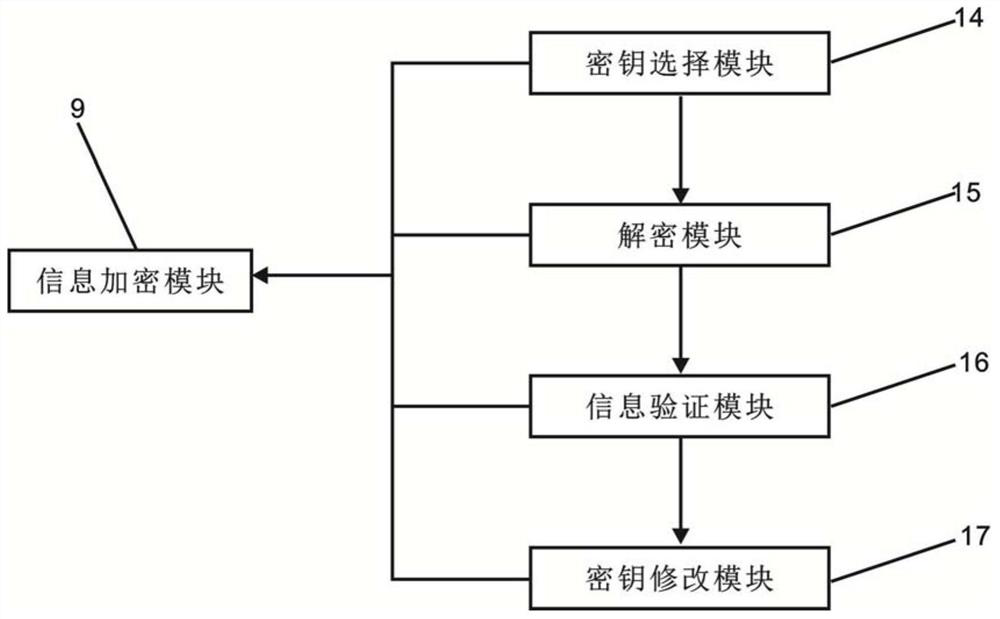
Smart home gateway system information encryption processing method based on cloud computing
PendingCN112910916APrevent malicious theftImprove securityDigital data protectionHome automation networksEmbedded systemCloud computing
The invention relates to the field of smart home, and discloses a smart home gateway system information encryption processing method based on cloud computing. According to the system, the output end of a secret key verification module is connected with the input end of an information encryption module, the output end of a starting module is connected with the input end of the information encryption module, and an access equipment monitoring module is fixedly installed at a data external interface of a cloud computing module; the output end of the cloud computing module is connected with the input end of the data sending module, and the output end of the data sending module is connected with the input end of the data encryption module; and a key selection module, a decryption module, an information verification module and a key modification module are arranged in the information encryption module, so that a plurality of encryption modules are matched for use to encrypt data information stored in the starting module and the cloud computing module, the internal information is prevented from being maliciously stolen, and the security of the method is improved.
Owner:内江佳路云网络科技有限公司
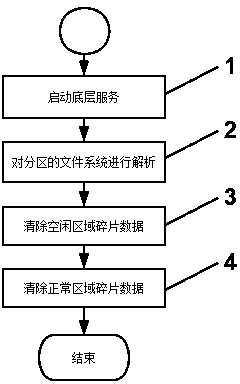
Method of clearing fragmented data of Android phone
InactiveCN104407822AGuaranteed data privacyPrevent malicious theftInput/output to record carriersComputer security arrangementsFile systemInternet privacy
The invention discloses a method of clearing fragmented data of Android phone. The method comprises the following steps: S1, starting an Android underlying service; S2, paring file systems of partitions; S3, clearing all fragmented data of idle areas; S4, clearing all fragmented data of normal areas; The method of clearing fragmented data of Android phone is able to distinguish normal areas, idle areas and fragmented areas in partitions, thoroughly clear all fragmented data in idle areas and data of the fragmented areas in the normal areas, thereby ensuring data privacy of the public, and preventing baleful stealing of privacy data.
Owner:MWH TECH LLC
Intelligent antitheft system, network intrusion preventing method, and burglar alarming method
InactiveCN106981152APrevent functionAnti-theft alarm functionBurglar alarm with fastening tamperingCommunication with homomorphic encryptionPasswordComputer terminal
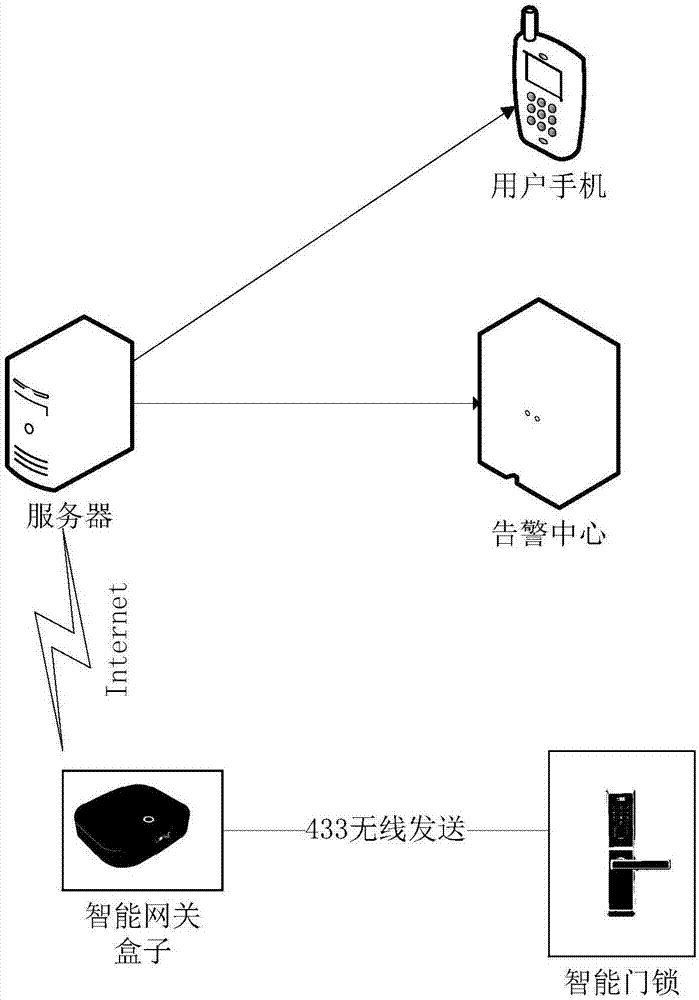
The invention discloses an intelligent antitheft system which comprises an intelligent door lock, an intelligent gateway box, a mobile terminal and a server. The intelligent door lock is provided therein a transmitter module and is in one-way communication connection to the intelligent gateway box through the transmitter module. The intelligent gateway box is in communication connection to the server. Information is synchronized between the intelligent door lock and the server by using a synchronous encryption method. The mobile terminal is communication connection with the server. The intelligent antitheft alarm system has functions of preventing network intrusion and burglar alarming, and improves a home security index. The function of preventing network intrusion can prevent the password of the intelligent door lock from being maliciously stolen. The burglar alarming function can give an alarm to an owner and a network alarm platform when the password is cracked violently or the intelligent door lock is broken violently in order that the owner and / or a security worker can timely take measures to avoid more serious damage to property safety.
Owner:深圳市前海洛克智慧安防科技股份公司
Intelligent lockset with internal RFID reader-writer and anti-theft function
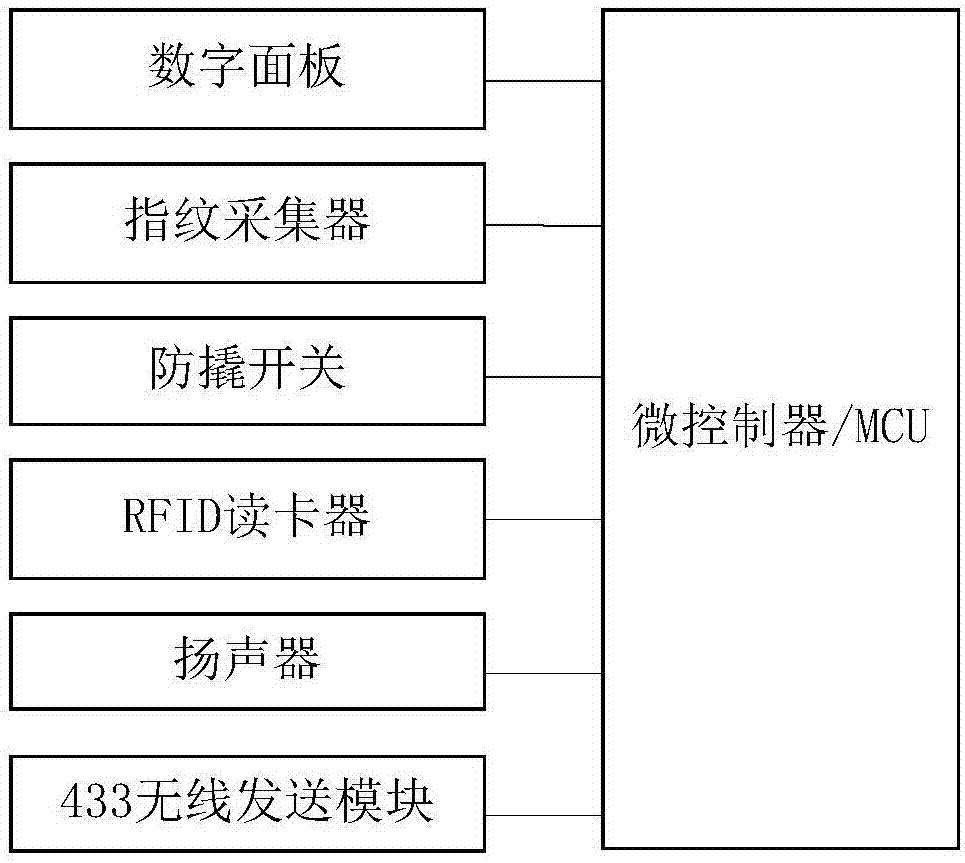
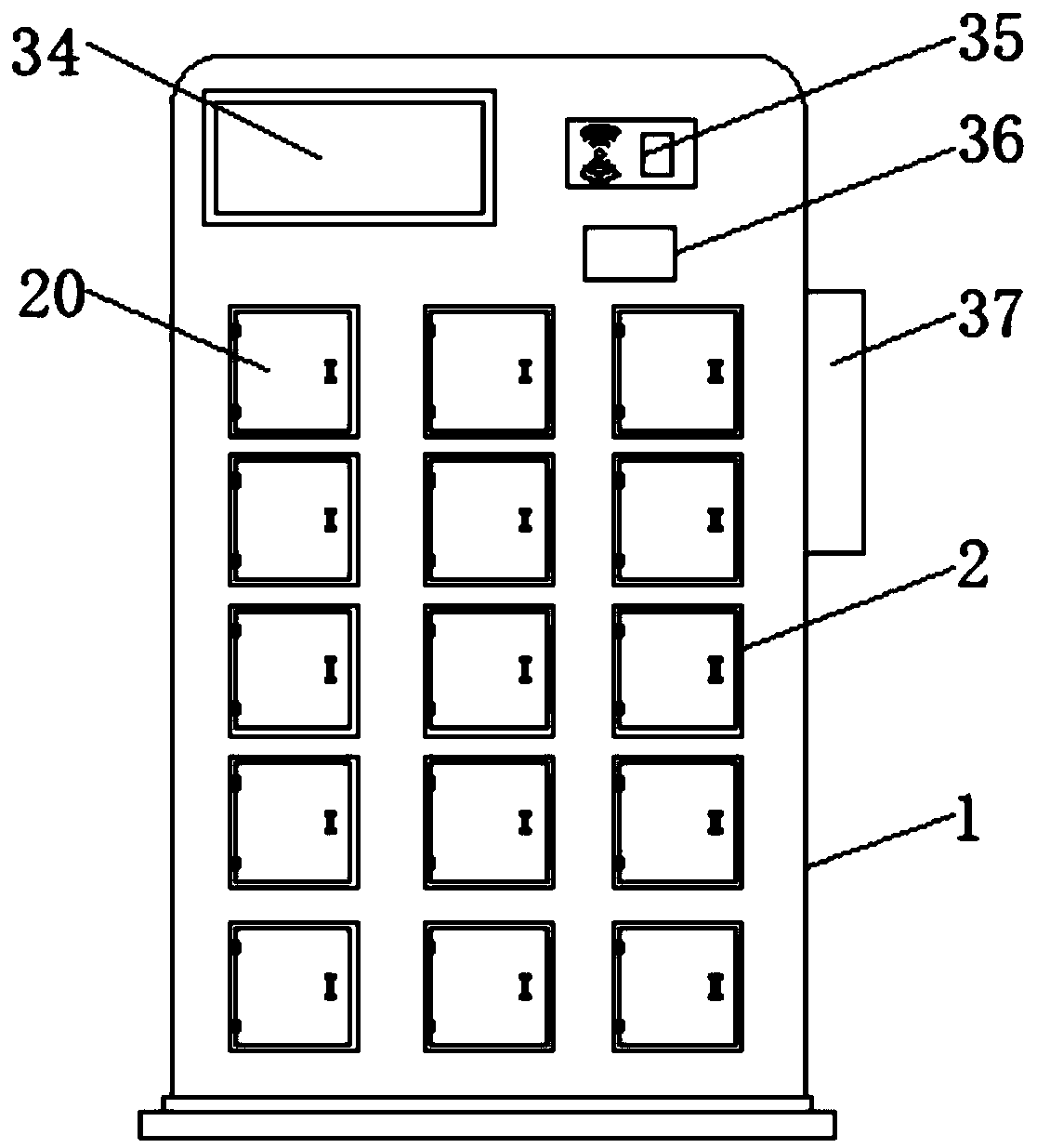
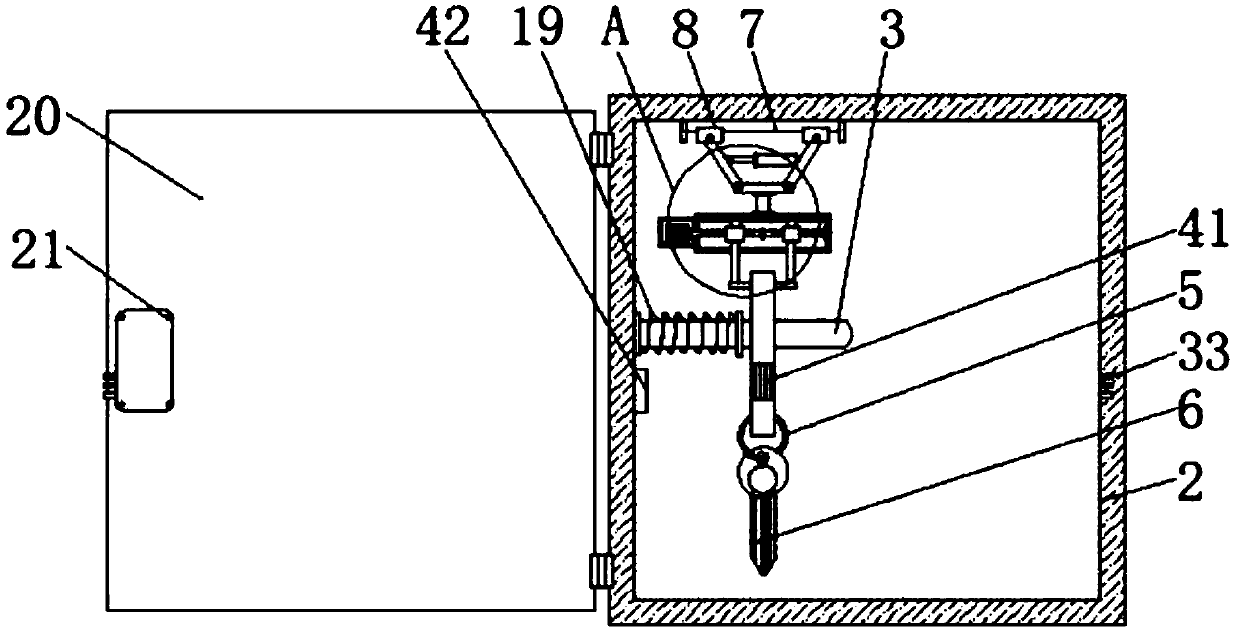
ActiveCN109598864AImplement access managementGuaranteed normalizationApparatus for meter-controlled dispensingSlide plateInductor
The invention discloses an intelligent lockset with an internal RFID reader-writer and an anti-theft function and relates to the technical field of intelligent locks. The lockset comprises a key cabinet, wherein a storage cabinet is fixedly connected to the inside of the key cabinet, a cross bar is fixedly connected to one side of the inner wall of the storage cabinet, key signs are connected to the surface of the cross bar in a sliding mode, a lantern ring is movably connected to the bottom of each key sign, and a key is movably connected to the surface of each lantern ring. According to theintelligent lockset with the internal RFID reader-writer and the anti-theft function, an RFID inductor is fixedly connected to the inside of each key sign, one intelligent key sign is arranged for each key, code information of an RFID chip arranged in each key sign serves as a unique electronic identifier of the corresponding key, and therefore storage and taking management of the keys can be realized; and since sliding blocks are connected to the two sides of the bottom of a sliding plate respectively in a sliding mode, after the keys are returned and recognized, the corresponding signs can be fixed, malicious theft by someone is prevented, and the safety of the keys is improved.
Owner:WUHAN RUILAIBAO ENERGY TECH +1
Experimental data management system
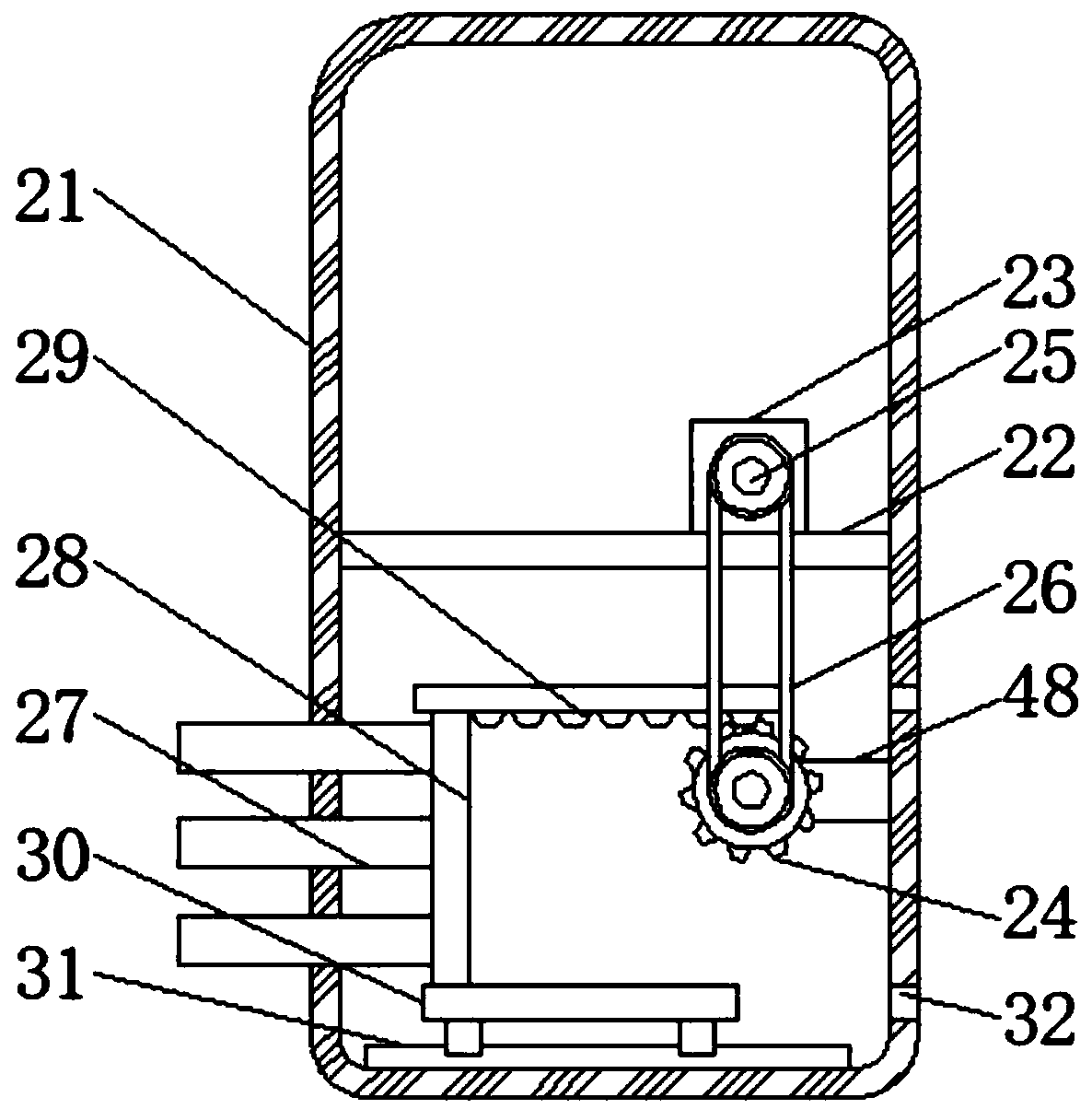
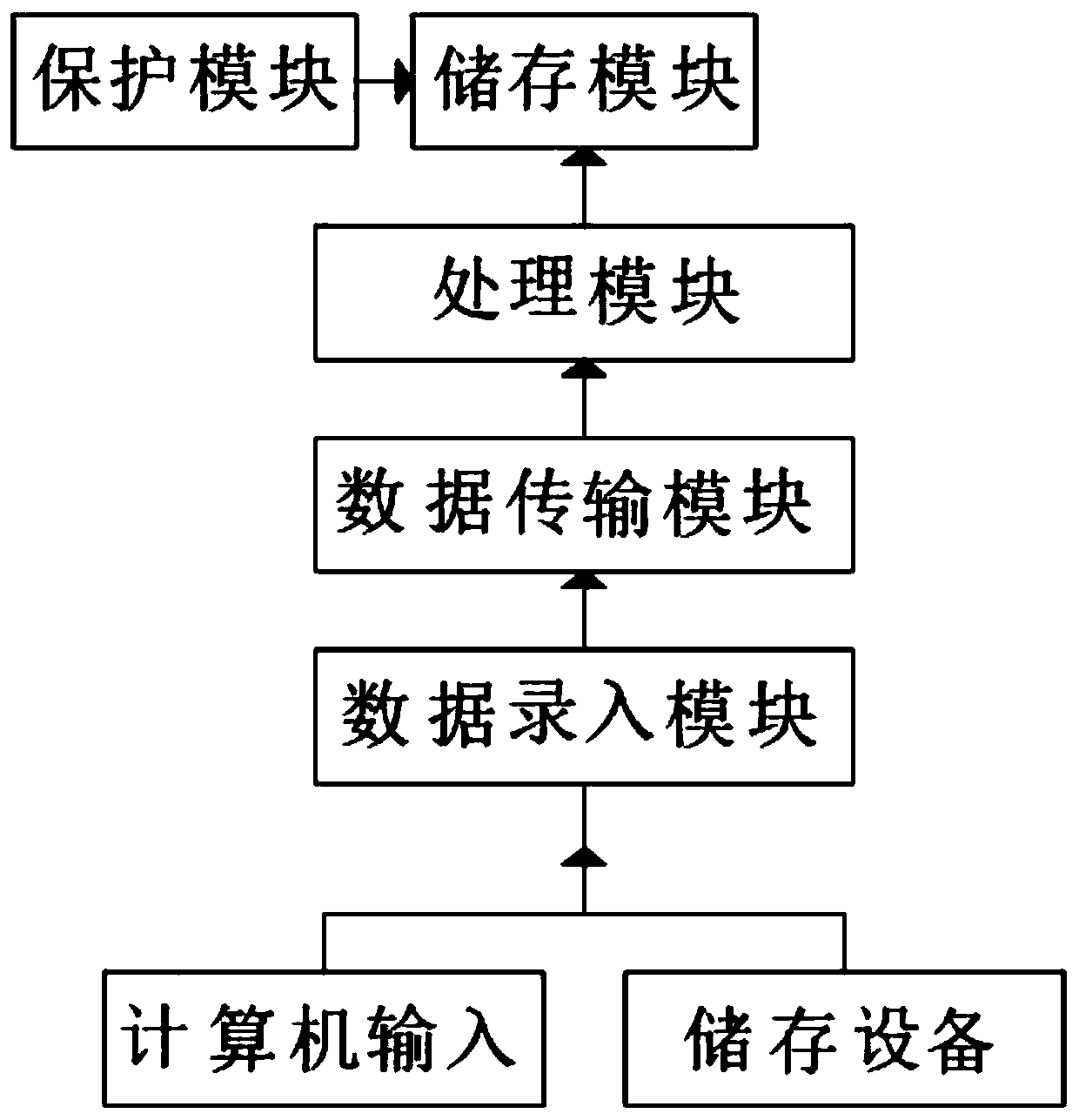
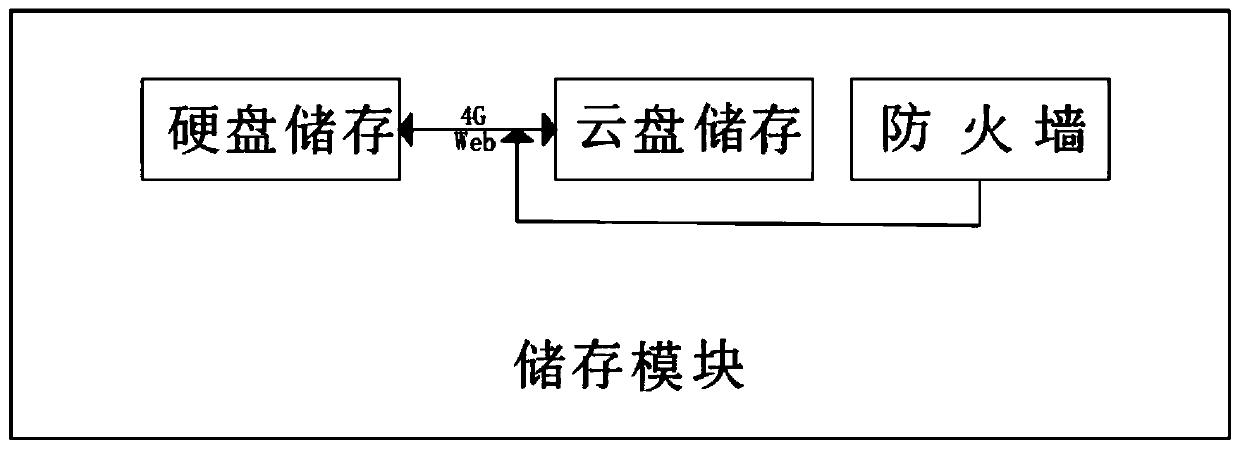
PendingCN111190972AImprove securityAvoid destructionDatabase management systemsRelational databasesData storeData terminal equipment
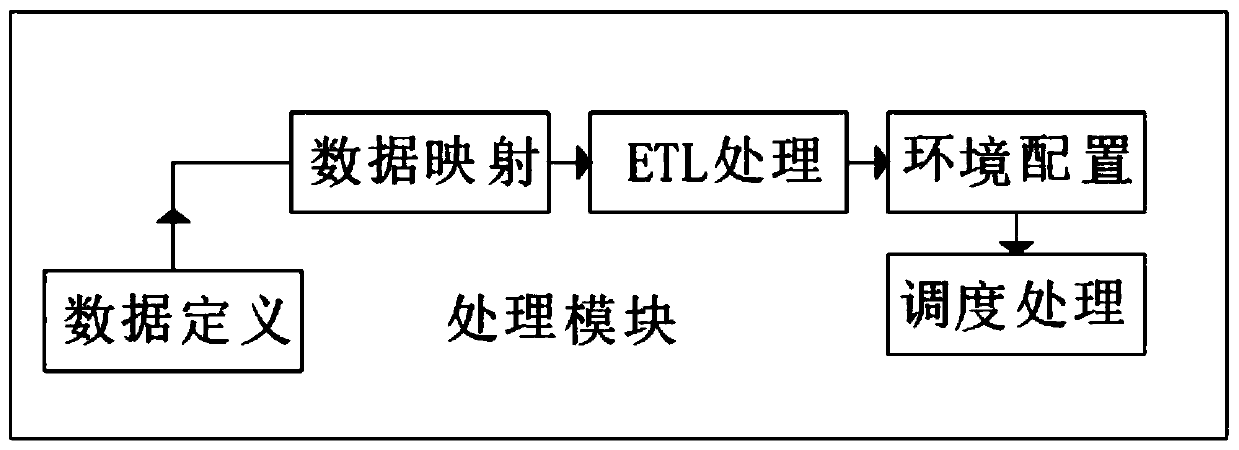
The invention discloses an experimental data management system, which is characterized in that a data input module is used for manually inputting text data into a computer, or equipment such as a mobile hard disk, a memory card and an optical disk are directly inserted into the computer for data input; a data transmission module receives the input data, carries out proper format conversion on thedata and then transmits the data to a processing module; the processing module carries out a series of algorithm processing on the data, classifies and integrates the data; and the processed data is transmitted to a storage module. According to the experimental data management system, the data transmission module directly transmits binary '1' or '0' electric signals transmitted by data terminal equipment (DTE) to a circuit of the data processing module; data mapping is applied to the data after data definition processing, the safety degree and the persistence degree of data storage are increased, the secret key and the antivirus form of the module are protected, the safety degree of data storage is increased, and viruses are prevented from damaging the processed data.
Owner:武汉俊楚信息科技有限公司
Novel contactless metal shielding information data card and production method thereof
The invention relates to the field of shielding cards, in particular to a novel contactless metal shielding information data card capable of effectively protecting credit cards, financial IC (integrated circuit) cards, smart cards, identification cards, driving licenses and bank cards to avoid unnecessary losses caused by risks such as data stealing by RFID (radio frequency identification) electronic scanners. The novel contactless metal shielding information data card comprises a first shielding layer, a second shielding layer and an accommodating space. The accommodating space formed by the first shielding layer and the second shielding layer is used for holding a card physically. The first shielding layer and the second shielding layer are metal sheets. Characters, patterns or combinations of characters and patterns can be printed on front and back surfaces of each metal sheet according to customers' needs. The novel contactless metal shielding information data card has the advantage that the credit cards, the financial IC cards, the smart cards, the identification cards, the driving licenses and the bank cards can be protected effectively to avoid the unnecessary losses caused by the risks such as data stealing by the RFID electronic scanners.
Owner:张敏
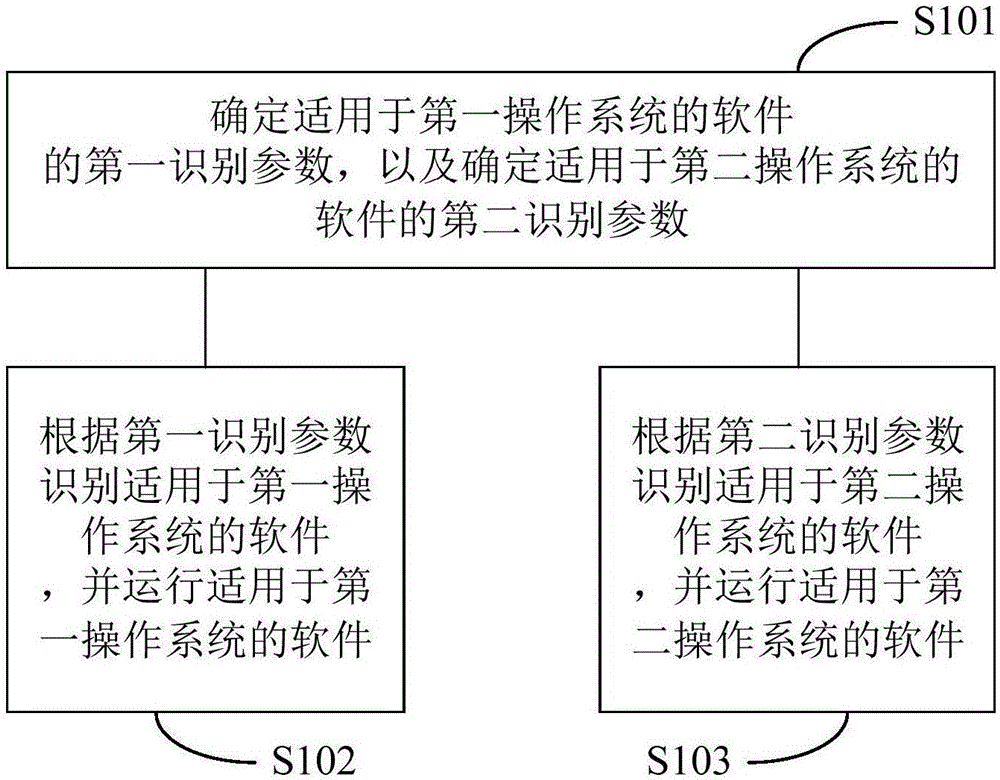
Operation method and device for network device software
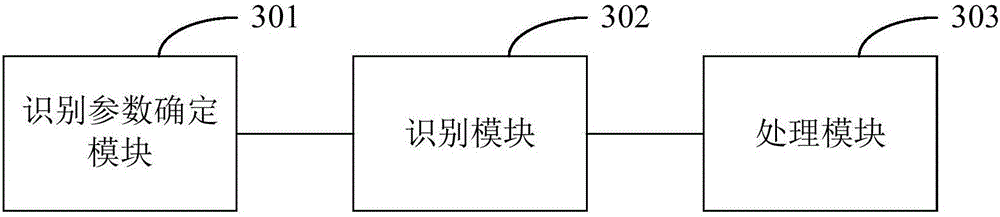
InactiveCN106548097AGuaranteed uptimePrevent malicious theftInternal/peripheral component protectionTransmissionUser privacyOperating system
The invention is applicable to the technical field of a network device and provides an operation method and device for network device software. The method comprises the steps of determining a first identification parameter of software applicable to a first operating system and a second identification parameter of the software applicable to a second operating system; identifying the software applicable to the first operating system according to the first identification parameter and operating the software applicable to the first operating system; and identifying the software applicable to the second operating system according to the second identification parameter and operating the software applicable to the second operating system. According to the method, the software operation security can be improved, and important information such as user privacy can be prevented from being leaked.
Owner:SHENZHEN TRANZDA TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com