Operation method and device for network device software
A technology of network equipment and operating methods, applied in the direction of electrical components, internal/peripheral computer component protection, transmission systems, etc., can solve problems such as low security and difficulty in protecting user privacy, so as to improve security and prevent malicious theft Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
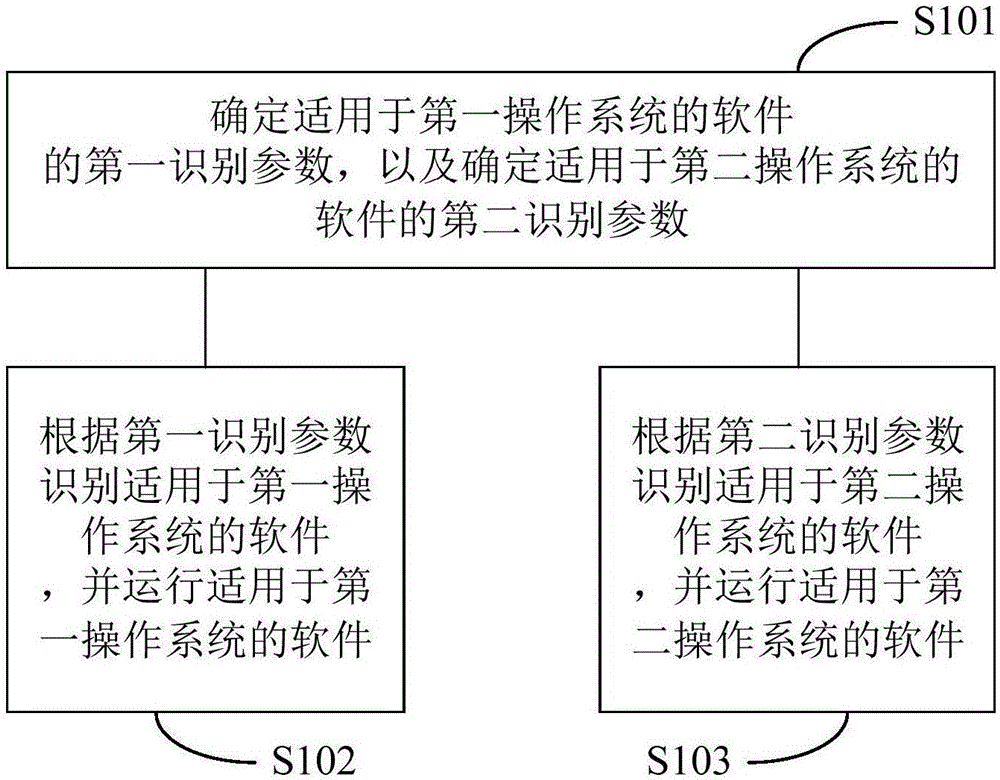
[0023] figure 1 It shows the implementation flow of the network device software operation method provided by Embodiment 1 of the present invention, which is used to realize the operation of the software applicable to the operating system running in the security architecture of the network device, and is described in detail as follows:
[0024] First, explain the network device security architecture:
[0025] In this embodiment, the network device security architecture includes a first hardware architecture for running a first operating system and identifying and running software applicable to the first operating system, for running a second operating system and identifying and running software applicable to The second hardware architecture of the software of the second operating system.
[0026] Wherein, the first hardware architecture and the second hardware architecture respectively include at least one application processor and a storage device connected to the application...
Embodiment 2
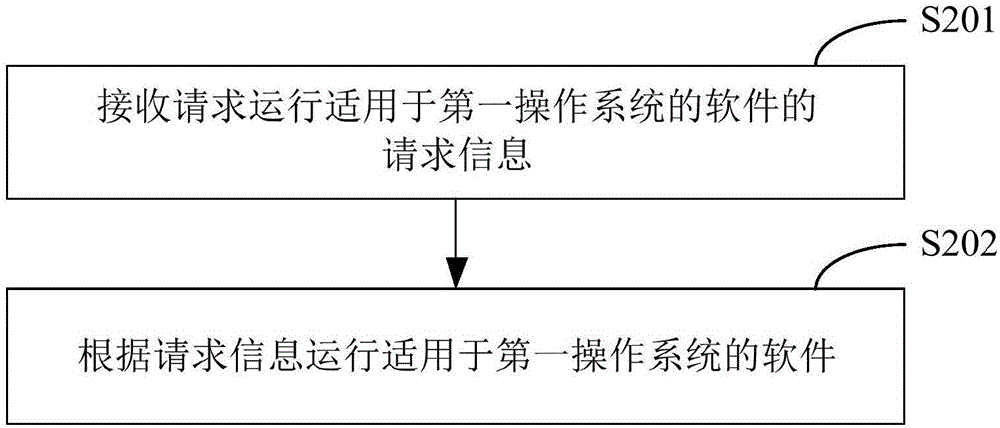
[0050] figure 2 The flow of running the software applicable to the first operating system in the embodiment of the present invention is shown, and the details are as follows:
[0051] In step S201, a request message requesting to run software applicable to the first operating system is received.
[0052] Wherein, the request information may be request information sent by a user. For example, the user sends request information to the first operating system to run software suitable for the first operating system through a relevant input device according to the user's needs. The first operating system receives request information requesting to run software suitable for the first operating system. In this embodiment, one or more pieces of software may be selected from the identified software applicable to the first operating system, and then request information is generated according to the selected software. In addition, one or more softwares may be selected from the software...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com