5G Internet of Things intrusion detection method and system based on federated transfer learning
A transfer learning and IoT technology, applied in the field of 5G IoT intrusion detection methods and systems based on federated transfer learning, can solve solutions that are difficult to reflect real-world conditions, do not consider the needs of personalized IoT models, and fail to detect new It can achieve the effect of effective unknown attack, detection of unknown attack, and strong generalization ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in further detail below through specific embodiments and accompanying drawings.
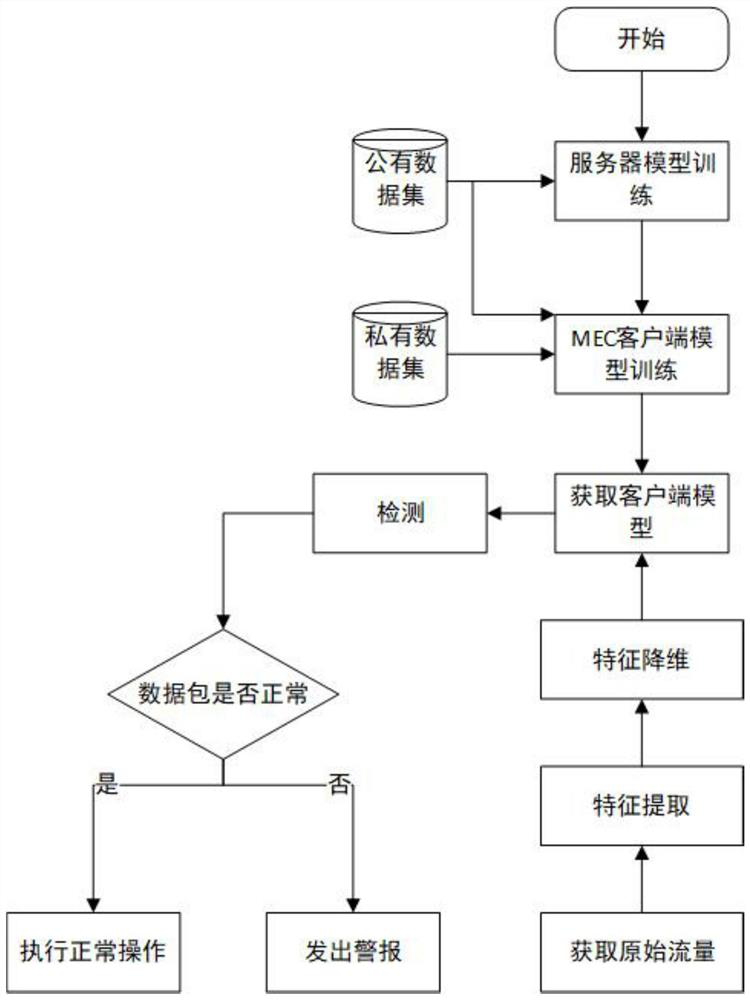
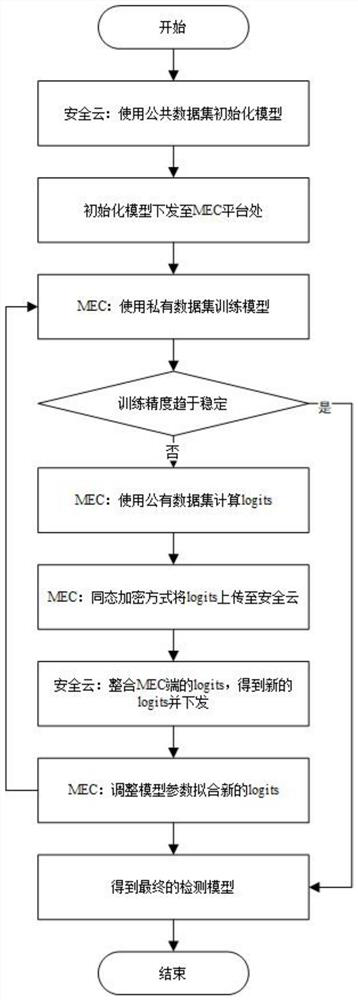
[0049] Such as figure 1 As shown, the federated migration framework proposed by the present invention is based on the federated migration learning algorithm, and the trained model can be used for intrusion detection in the Internet of Things. It mainly includes three modules: data preprocessing, detection model training, and attack detection.
[0050] 1. Data preprocessing
[0051] After obtaining the original data packet, preprocess it to extract basic information such as IP address, data packet size, and arrival time, and then perform feature extraction and feature dimensionality reduction on it.
[0052] 2. Detection model training
[0053] The intrusion detection system architecture designed by this method has three layers. The top layer is a secure cloud platform operated by 5G operators, with a large amount of data and computing resources. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com