Security data storage and computing method based on Internet of Things fog computing-edge computing
An edge computing and secure data technology, applied to secure communication devices and key distribution, can solve problems such as inability to guarantee data security, slow computing task processing speed, and large data volume
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0095] In order to further understand the content, features and effects of the present invention, the following examples are given, and detailed descriptions are given below with reference to the accompanying drawings.
[0096] The structure of the present invention will be described in detail below in conjunction with the accompanying drawings.
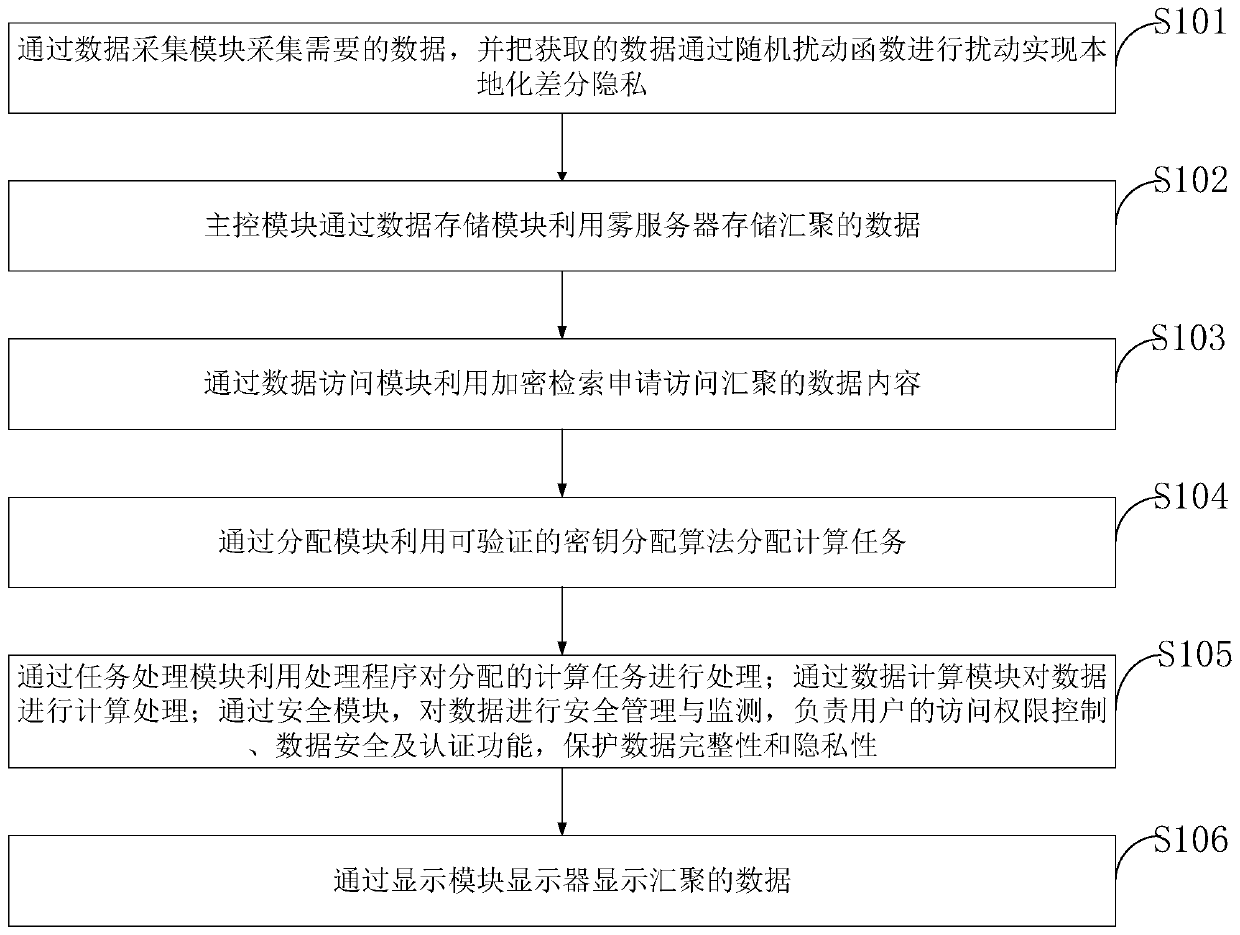
[0097] Such as figure 1 As shown, the method for secure data storage and computing based on fog computing-edge computing provided by the present invention comprises the following steps:
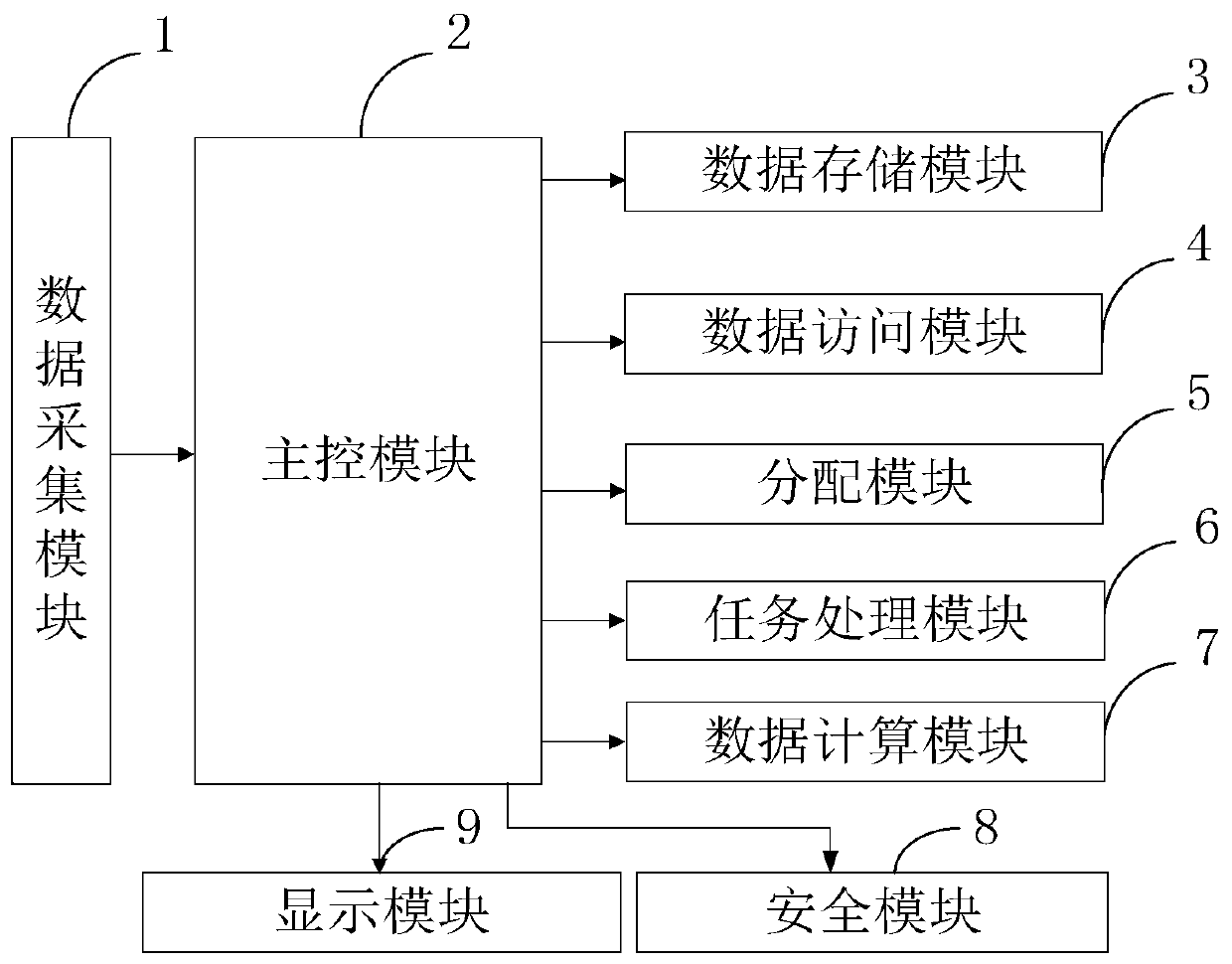
[0098] S101, collect the required data through the data collection module, and perturb the acquired data through a random perturbation function to realize localized differential privacy, and realize data security in the local area by encrypting at the fog node;
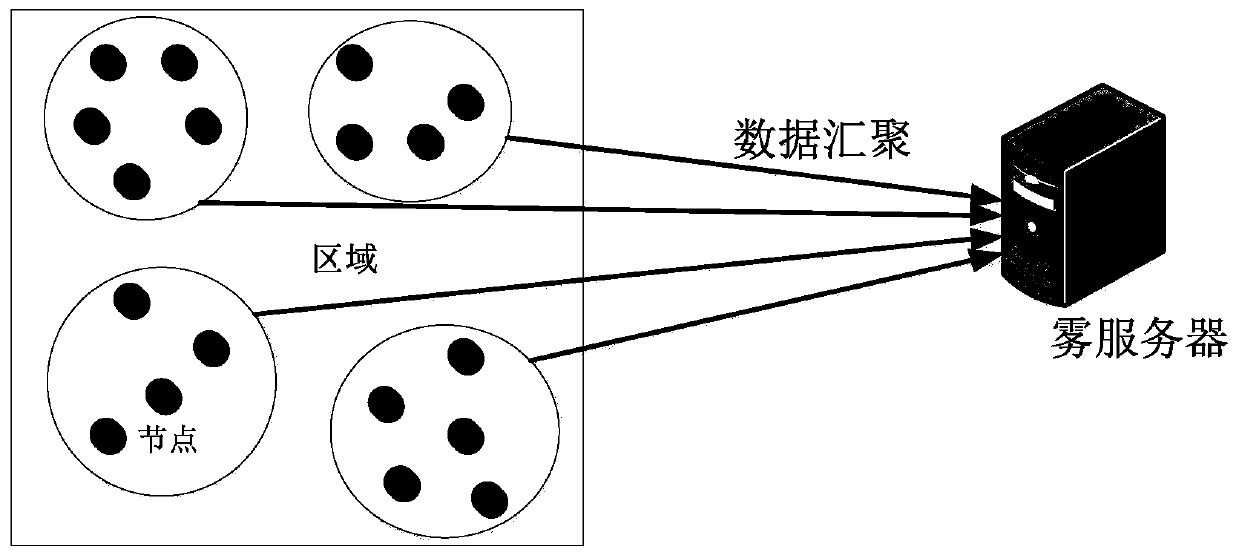
[0099] S102, the main control module uses the fog server to store the aggregated data through the data storage module;
[0100] S103, using the encrypted retrieval application to access ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com