Authentication method, device and system
An authentication method and a technology for authenticating data, applied in the field of communication, can solve problems such as data being easily obtained and affecting user information security and experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
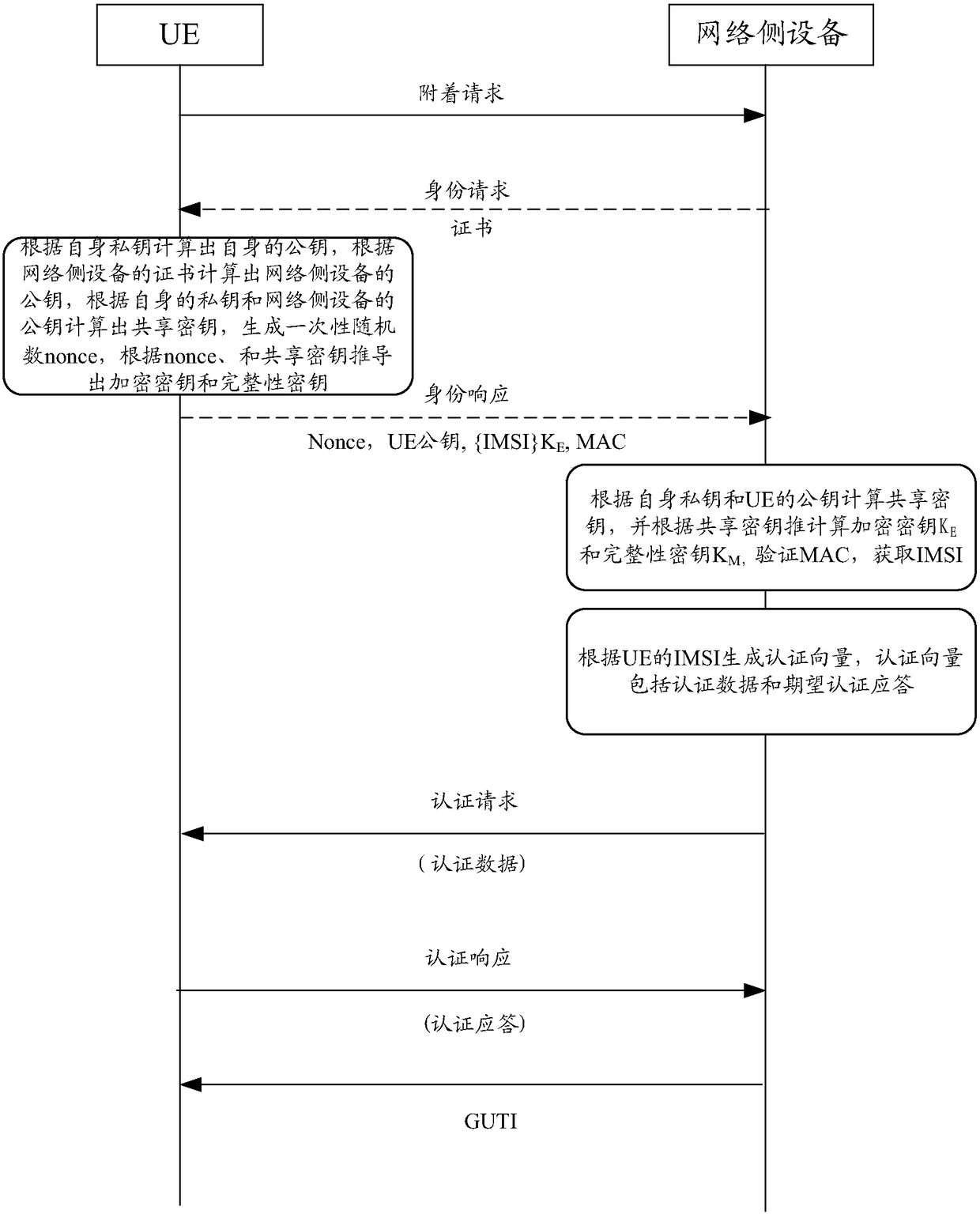
[0106] figure 2 A schematic diagram of an authentication process provided by an embodiment of the present invention, the process includes:
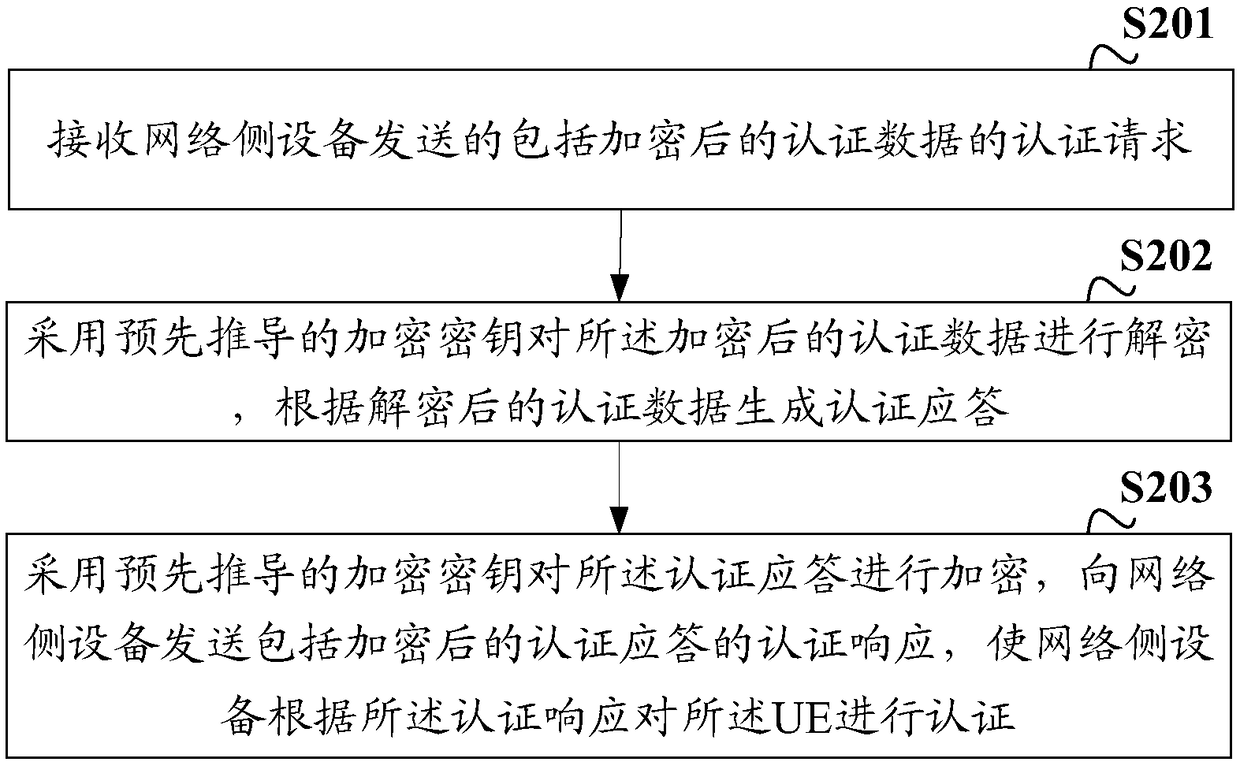
[0107] S201: Receive an authentication request including encrypted authentication data sent by a network side device.
[0108] The authentication method provided by the embodiment of the present invention is applied to UE.
[0109] In this embodiment of the present invention, the UE and the network-side device pre-deduce an encryption key, wherein the pre-derived encryption key may be a shared key generated by the UE and the network-side device using the DHIES protocol. Derived encryption key.
[0110] S202: Decrypt the encrypted authentication data by using a pre-derived encryption key, and generate an authentication response according to the decrypted authentication data.
[0111] Specifically, the UE receives the authentication request including encrypted authentication data sent by the network side device, decrypts the encrypted a...
Embodiment 2
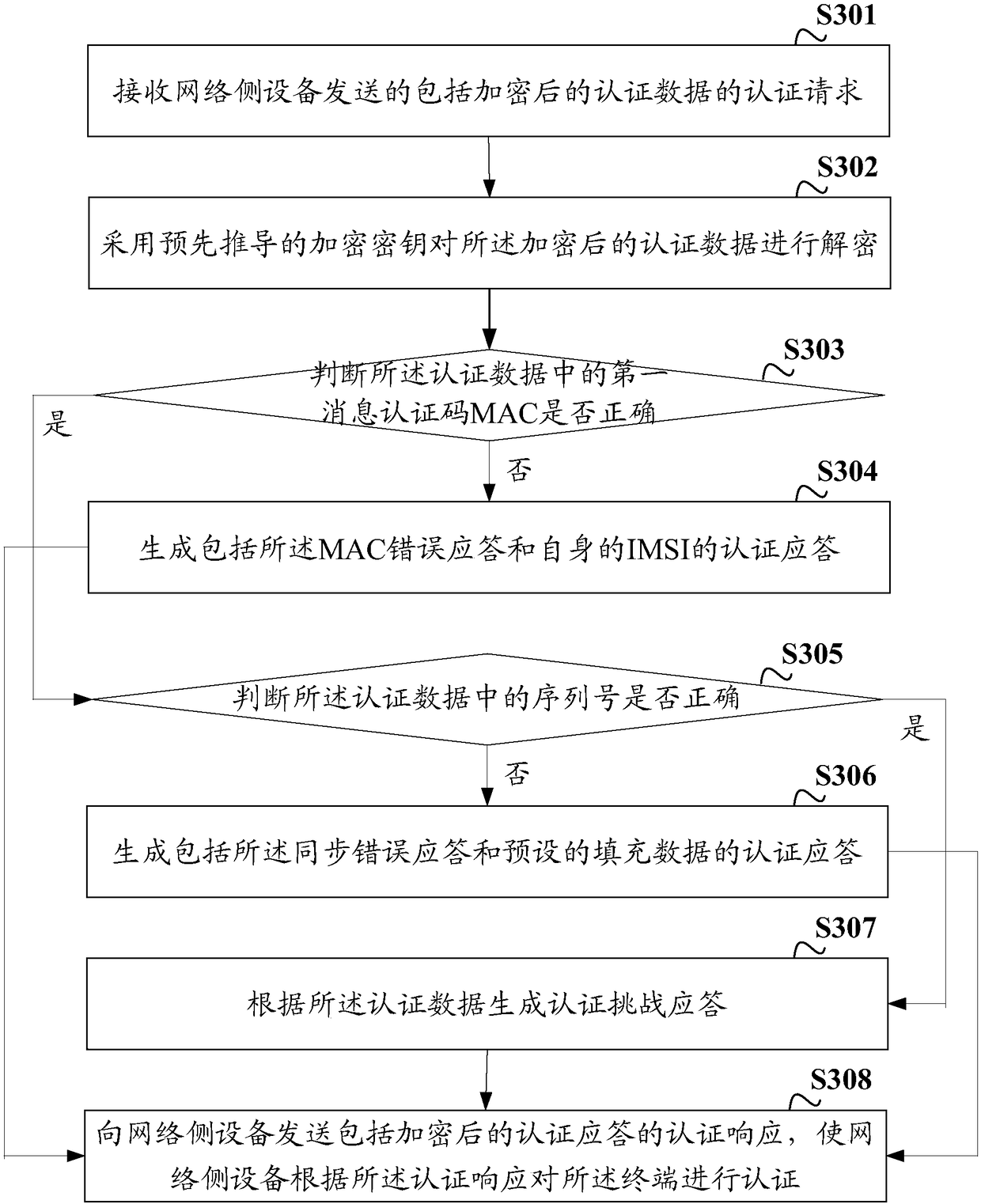
[0116] In order to improve the accuracy of authentication, on the basis of the above-mentioned embodiments, in the embodiment of the present invention, the generation of the authentication response according to the decrypted authentication data includes:
[0117] judging whether the first message authentication code (Message Authentication Code, MAC) in the authentication data is correct;
[0118] If not, generate a first authentication response;
[0119] If yes, determine whether the serial number in the authentication data is correct;
[0120] If the serial number in the authentication data is incorrect, generate a second authentication response, and if the serial number in the authentication data is correct, generate a third authentication response.
[0121] Specifically, the authentication information carries the information of the first MAC and the serial number. After the encrypted authentication data is decrypted, in order to further ensure the security of data transmi...
Embodiment 3
[0141] In order to improve the authentication efficiency, on the basis of the above-mentioned embodiments, in the embodiment of the present invention, before receiving the authentication request including the encrypted authentication data sent by the network side device, the method further includes:
[0142] Judging whether the network side device has a globally unique temporary user identity (Globally Unique Temporary User Equipment Identity, GUTI);
[0143] If so, generate a one-time random number Nonce, and generate an encryption key and an integrity key according to the Nonce and the pre-derived shared key for the network side device, and send to the network side device including the Attachment request for Nonce and GUTI.
[0144] In this embodiment of the present invention, the UE stores a shared key and GUTI for each network-side device that has successfully authenticated itself before this authentication, where the shared key is the UE and the network-side device when t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com