Method and device for intercepting network attack based on cloud
A network attack and cloud technology, applied in the field of network communication and information security, can solve problems such as user loss and theft, and achieve the effect of preventing attacks and ensuring information security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
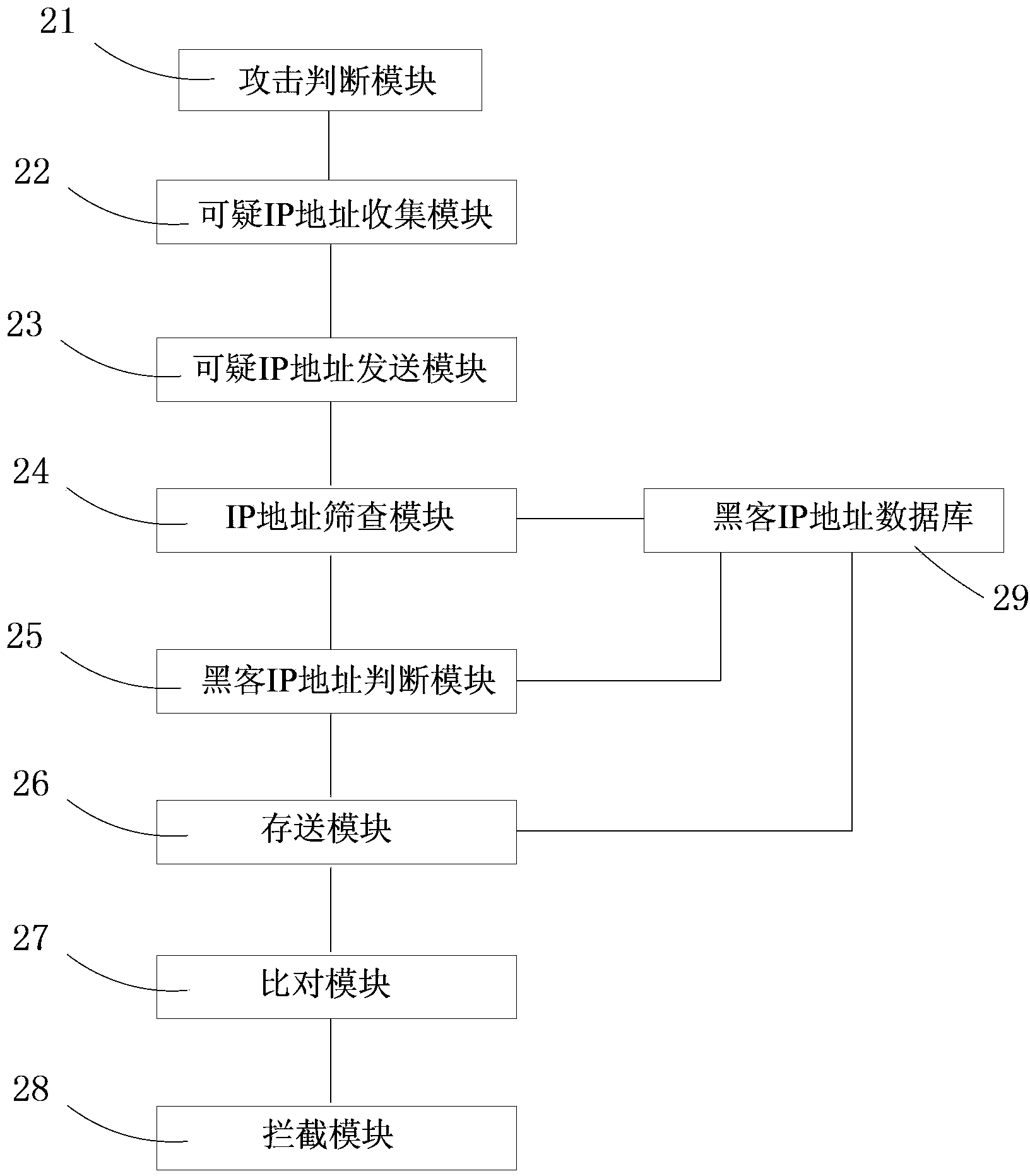
Image
Examples
Embodiment Construction
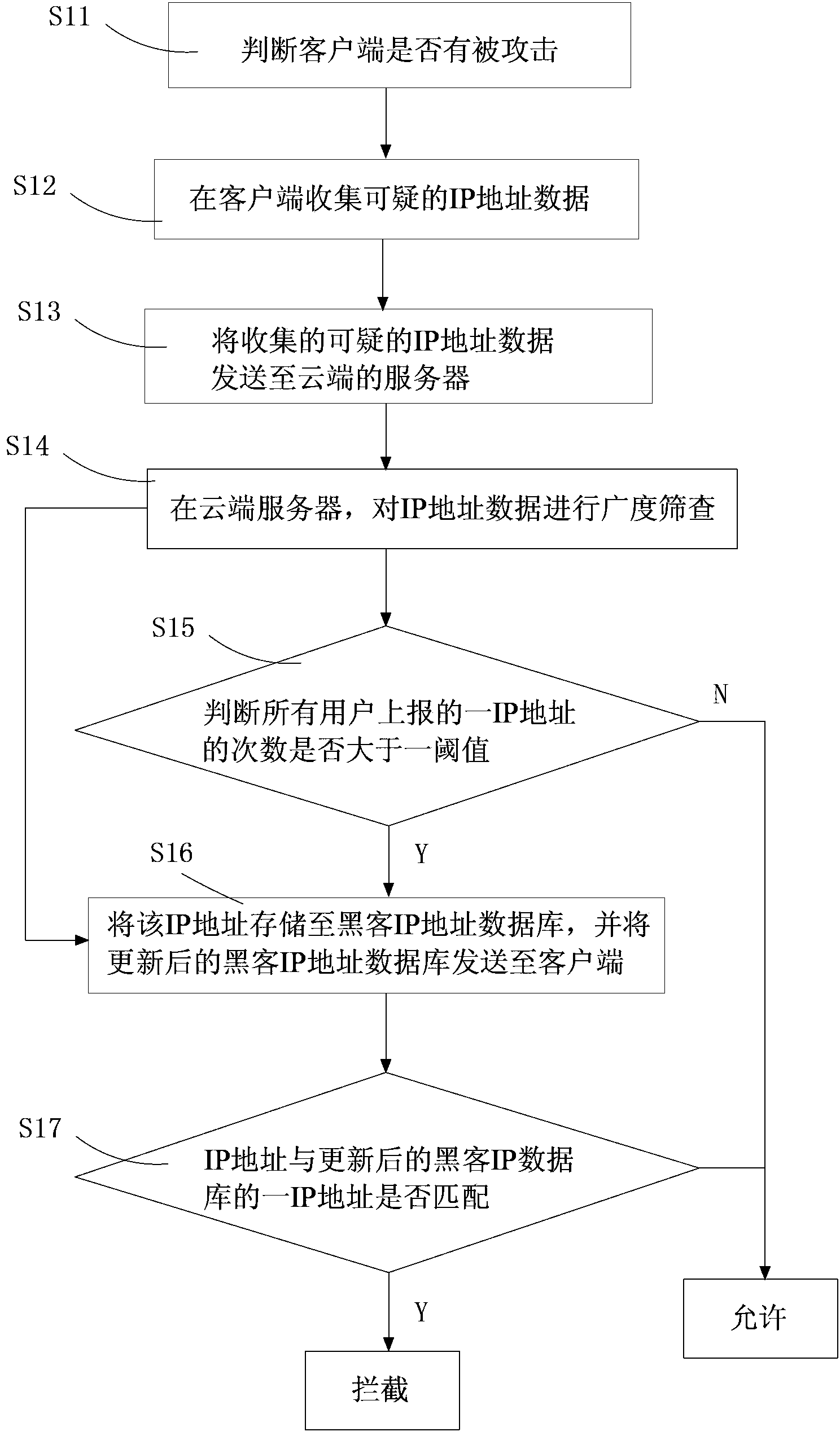
[0024] see figure 1 , which is a flow chart of the cloud-based method for intercepting network attacks of the present invention. The cloud-based method for intercepting network attacks includes the following steps:
[0025] Step S11: Determine whether the client has been attacked. Usually, after a hacker attack is successful, a script file, such as FTP or Wscript, will be run to download the virus. Therefore, when an FTP or Wscript program is detected to be downloaded, it can be judged as being attacked.
[0026] Step S12: collecting suspicious IP address data on the client side. The IP address data is the target address of the malicious download.
[0027] Step S13: Send the collected suspicious IP address data to the cloud server.
[0028] Step S14: Extensive screening is performed on the IP address data on the cloud server. The IP address is compared with a hacker IP address database, if the IP address matches an IP address in the hacker IP database, it is judged to be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com