Method and device for controlling debugging ports of terminal equipment
A technology for debugging ports and terminal equipment, applied in the field of communication, can solve the problem of inability to guarantee user information security, and achieve the effect of ensuring security and improving completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
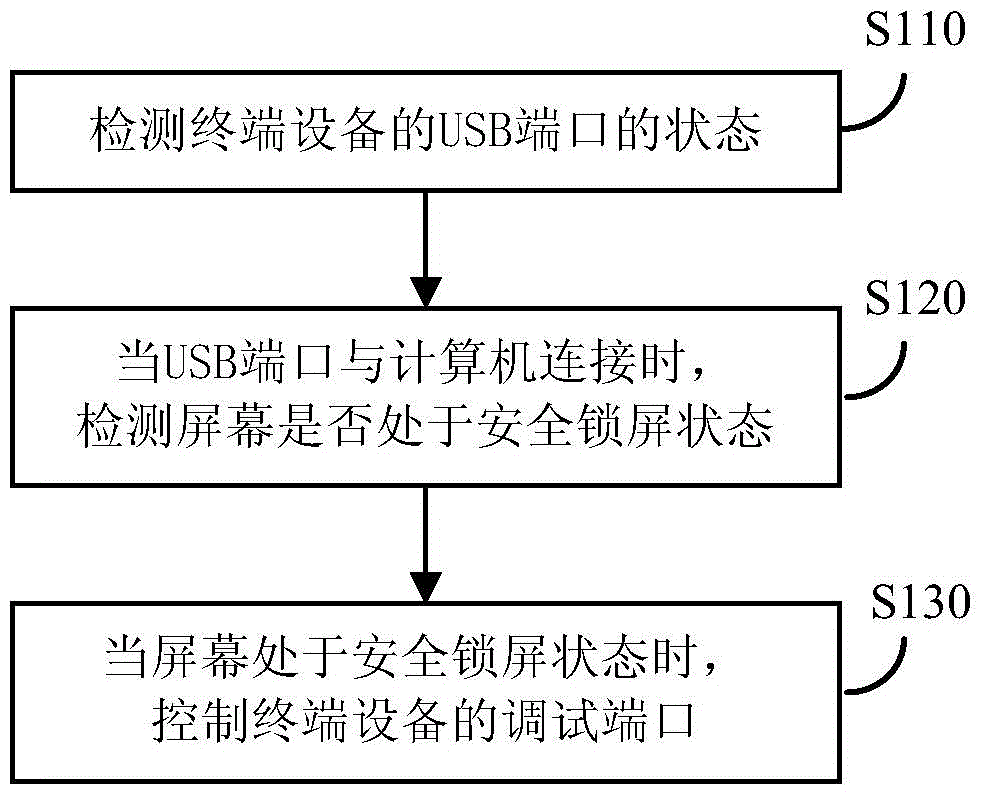
[0027] figure 1 A flowchart showing a method for controlling a debugging port of a terminal device according to an embodiment of the present invention. Such as figure 1 As shown, the debugging port control method mainly includes:
[0028] Step S110, detecting the state of the Universal Serial Bus USB port of the terminal device;
[0029] Step S120, when the USB port is connected to a computer, detect whether the screen of the terminal device is in a secure lock screen state;
[0030] Step S130, when the screen is in the security lock screen state, control the debugging port of the terminal device.
[0031] Specifically, on a device installed with an operating system such as an Andriod system, such as a smart phone or a tablet computer, a set of security policies may be added in front of a debugging port of the terminal device such as an ADB (Andriod Debug Bridge) port. The system can determine whether a USB event occurs by monitoring the USB message of the terminal device,...
Embodiment 2
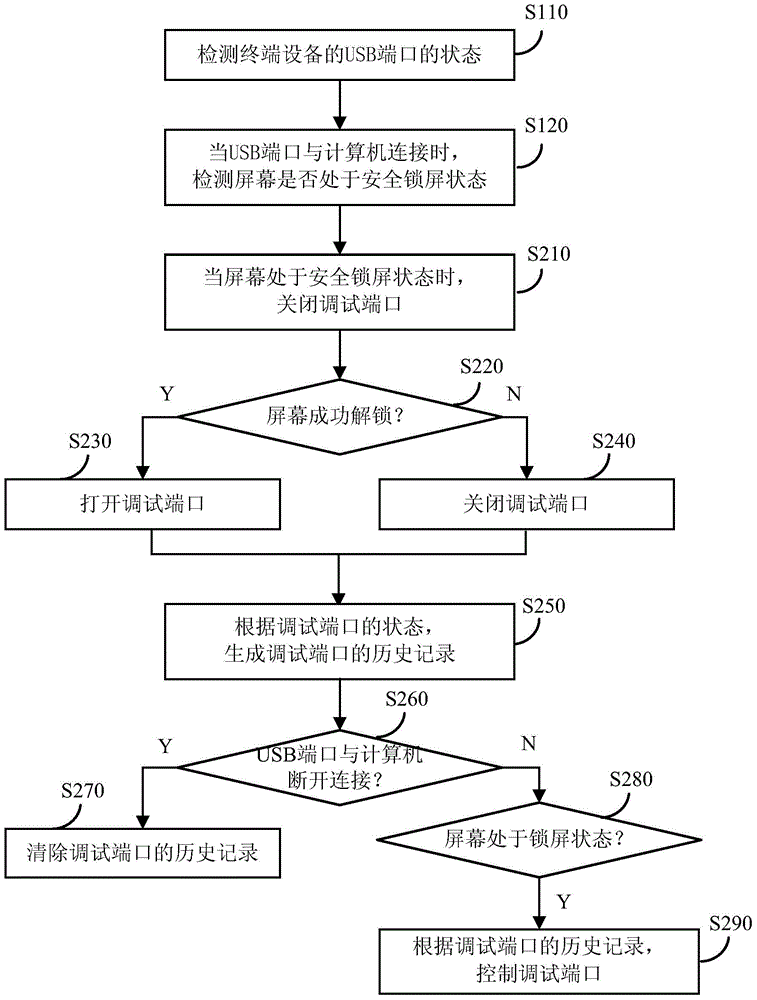
[0036] figure 2 A flowchart showing a method for controlling a debugging port of a terminal device according to another embodiment of the present invention. figure 2 Winning mark and figure 1 The same components have the same functions, and detailed descriptions of these components are omitted for brevity.
[0037] Such as figure 2 as shown, figure 2 The method shown with figure 1 The main difference of the methods shown is that when the screen is in a security lock state, the debug port is closed first, and the debug port cannot be opened until the screen is successfully unlocked.
[0038] Specifically, step S130 may specifically include:
[0039] Step S210, when the screen is in a security lock state, close the debugging port.
[0040] Specifically, the locked screen status refers to a status in which the screen of the terminal device is locked. The screen lock state may include a secure screen lock state and a non-secure screen lock state. For example: in the J ...
Embodiment 3
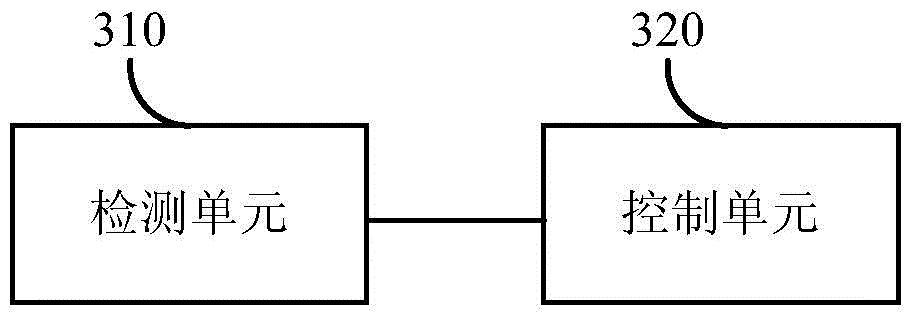
[0060] image 3 A block diagram of an apparatus for controlling a debugging port of a terminal device according to an embodiment of the present invention is shown. Such as image 3 As shown, the debug port control device mainly includes a detection unit 310 and a control unit 320 . Wherein, the detection unit 310 is mainly used to detect the state of the USB port of the terminal device, and when the USB port of the terminal device is connected to a computer, detect whether the screen of the terminal device is in a security lock screen state, wherein the security The lock screen state is preset in the operating system of the terminal device, and the screen can be successfully unlocked only after the user inputs correct unlock information on the locked screen. The control unit 320 is connected with the detection unit 310 and is mainly used for controlling the debugging port of the terminal device when the screen is in the security lock state.
[0061] Regarding the above debu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com