Attack identification method, device and apparatus and computer readable storage medium
An attack identification, computer technology, applied in the field of network security, can solve problems such as system breach, achieve the effect of improving accuracy, improving system security, and reducing the probability of system being attacked
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
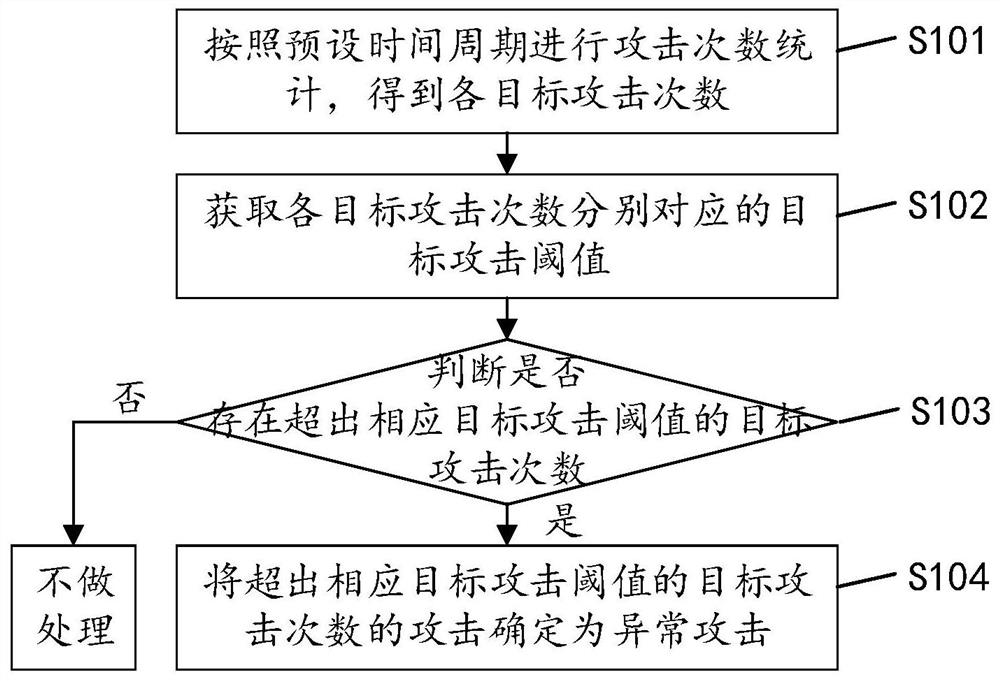
[0047]Seefigure 1 ,figure 1 This is an implementation flow chart of the attack identification method in the embodiment of the present invention, and the method may include the following steps:
[0048]S101: Count the number of attacks according to a preset time period to obtain the number of attacks of each target.
[0049]The time period for counting the number of attacks is preset, and the attack mutation recognition engine performs statistics on the number of attacks according to the preset time period to obtain the number of attacks for each target.
[0050]It should be noted that the time period for counting the number of attacks can be set and adjusted according to actual conditions, which is not limited in the embodiment of the present invention, for example, it can be set to every minute.
[0051]S102: Acquire target attack thresholds corresponding to the number of target attacks.
[0052]Each acquired number of target attacks has its corresponding target attack threshold. After the number...
Embodiment 2
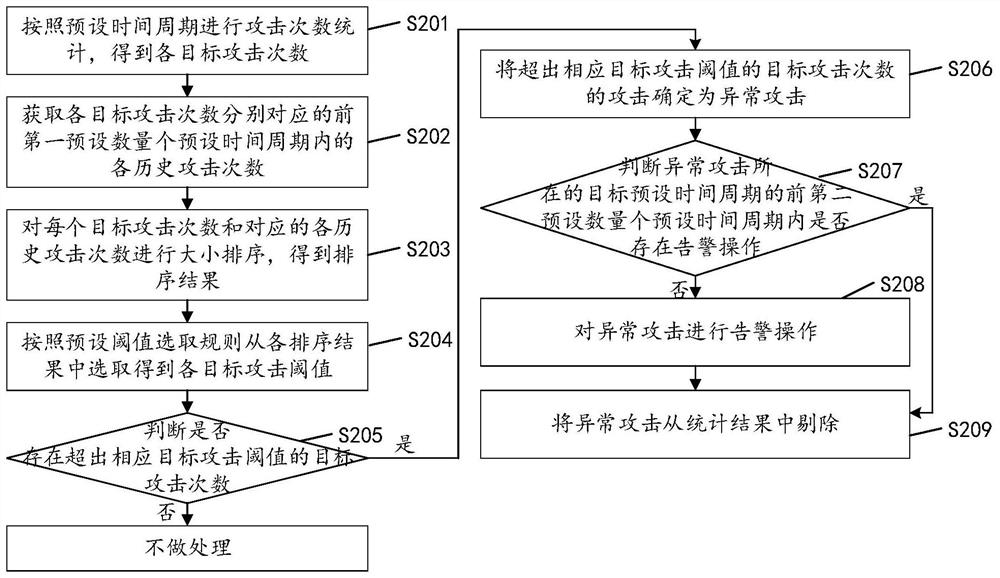
[0061]Seefigure 2 ,figure 2 This is another implementation flowchart of the attack identification method in the embodiment of the present invention. The method may include the following steps:
[0062]S201: Count the number of attacks according to a preset time period to obtain the number of attacks of each target.
[0063]S202: Acquire each historical attack count in the first preset number and preset time periods corresponding to each target attack count.
[0064]Pre-set the number of preset time periods that need to be referred to when determining the target attack threshold. After the number of attacks on each target is counted, the first preset number corresponding to the number of target attacks are obtained for each historical attack number in the preset time period. .
[0065]It should be noted that the number of preset time periods that need to be referred to when determining the target attack threshold can be set and adjusted according to actual conditions, which is not limited in the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com