Method, device and electronic equipment for protecting target application
An application and target protection technology, applied in the field of information security, can solve problems such as low security and vulnerable applications, and achieve the effect of improving security, solving vulnerability to attacks, and reducing the probability of being attacked.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
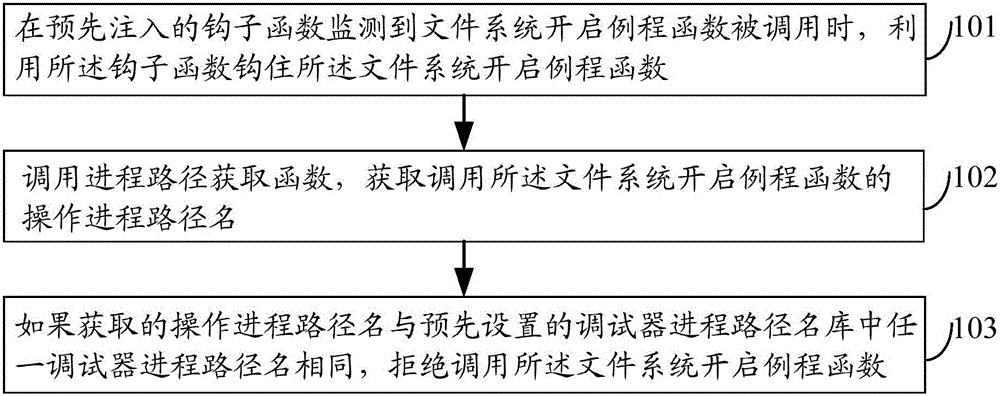
[0050] figure 1 It is a schematic flowchart of a method for protecting a target application program according to an embodiment of the present invention, such as figure 1 As shown, the method of this embodiment may include:
[0051] Step 101, when the pre-injected hook function detects that the file system opening routine function is called, use the hook function to hook the file system opening routine function;
[0052] In this embodiment, when the non-target application program debugs some target application programs, it needs to open the relevant files of the target application program. When the non-target application program opens each file, the non-target application program will request the debugger to call the file. The system opens the routine function for processing, and the file system opens the routine function to read the relevant information of the file to the physical hard disk, thereby realizing the opening of the file.
[0053] In this embodiment, when debuggi...
Embodiment 2
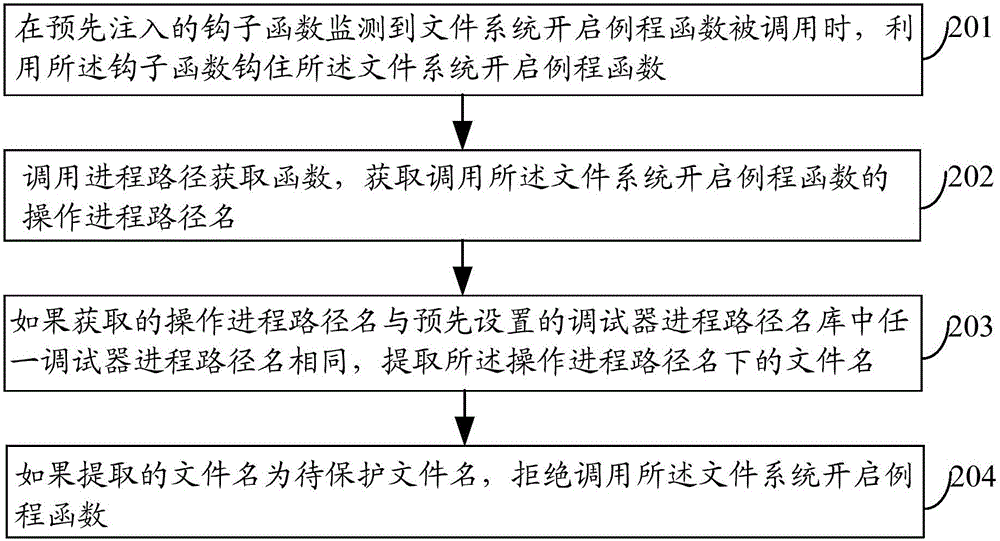
[0074] figure 2 It is a schematic flowchart of a method for protecting a target application program in Embodiment 2 of the present invention, as shown in figure 2 As shown, the method of this embodiment may include:
[0075] Step 201, when the pre-injected hook function detects that the file system opening routine function is called, use the hook function to hook the file system opening routine function;
[0076] Step 202, calling the process path obtaining function to obtain the path name of the operation process that calls the file system opening routine function;
[0077] In this embodiment, the processes from step 201 to step 202 are respectively similar to steps 101 to 102 in the first method embodiment, and will not be repeated here.
[0078] Step 203, if the obtained operation process path name is the same as any debugger process path name in the preset debugger process path name library, extract the file name under the operation process path name;
[0079] Step 20...
Embodiment 3
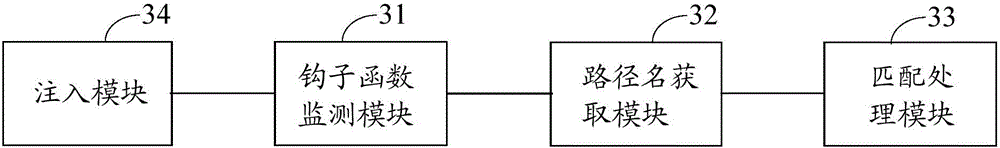
[0088] image 3 It is a schematic structural diagram of a device for protecting a target application program in Embodiment 3 of the present invention, as shown in image 3 As shown, the device of this embodiment may include: a hook function monitoring module 31, a path name obtaining module 32, and a matching processing module 33, wherein,
[0089] A hook function monitoring module 31, configured to use the hook function to hook the file system opening routine function when the pre-injected hook function detects that the file system opening routine function is called;
[0090] In this embodiment, the routine function is a collection of functional interfaces or services provided by the operating system, including but not limited to: API functions, service functions, standard functions provided by Delphi or C++Builder, library functions, and the like.
[0091] In this embodiment, the hook function can be obtained by programming in any language that can realize the corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com