Mobile CA node electing method based on MD5 hash information abstract
An information summary and node technology, applied in wireless communication, energy-saving ICT, encryption device with shift register/memory, etc., can solve the problems that CA nodes cannot continue to provide certificate services, other nodes provide certificate services, and authentication mechanism risks , to avoid providing certificate services, reduce the probability of being attacked, and save energy consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
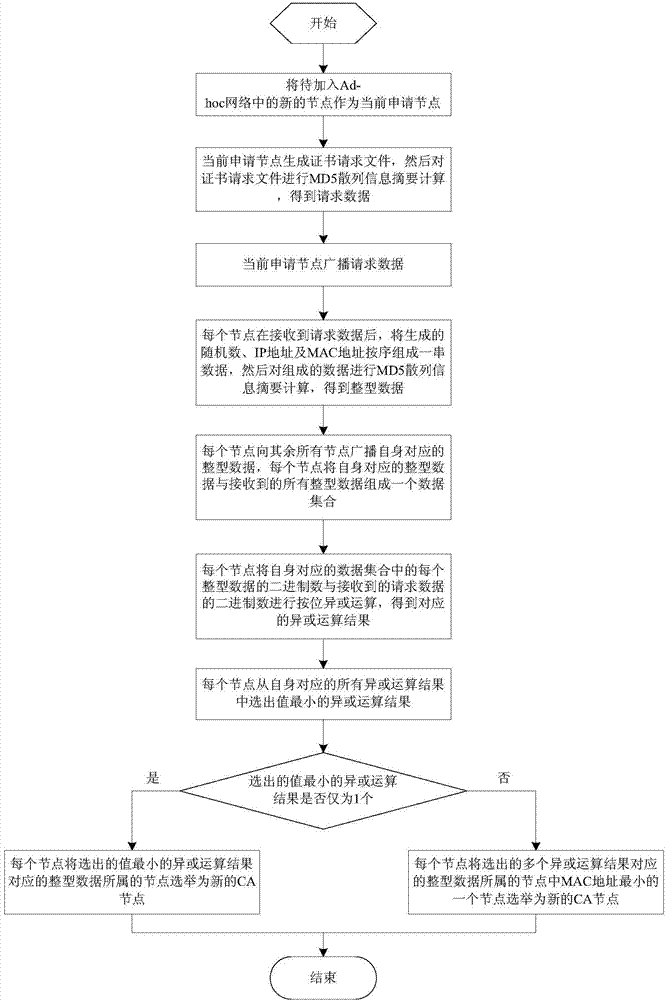
[0019] A kind of mobile CA node election method based on MD5 hash information abstract that the present invention proposes, its flow chart is as follows figure 1 As shown, it includes the following steps:
[0020] 1) Assuming that there is a new node to be added to the Ad-hoc network, this new node is the current application node.
[0021] 2) The current application node generates a certificate request file, and then the current application node performs MD5 hash information digest calculation on the generated certificate request file, and obtains a string of 16-byte request data representing the certificate request file. The data is integer data expressed in hexadecimal.
[0022] 3) The current application node broadcasts the request data obtained in step 2) to all nodes in the Ad-hoc network.
[0023] 4) After each node in the Ad-hoc netw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com