Mobile ad hoc authentication method, network and system
A mobile self-organization and authentication method technology, applied in the field of communication, can solve the problems of high output bits of Hash function, reduce network reliability and security, synchronization attacks, etc., to solve the synchronization problem within the cluster, speed up processing, and ensure security. degree of effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
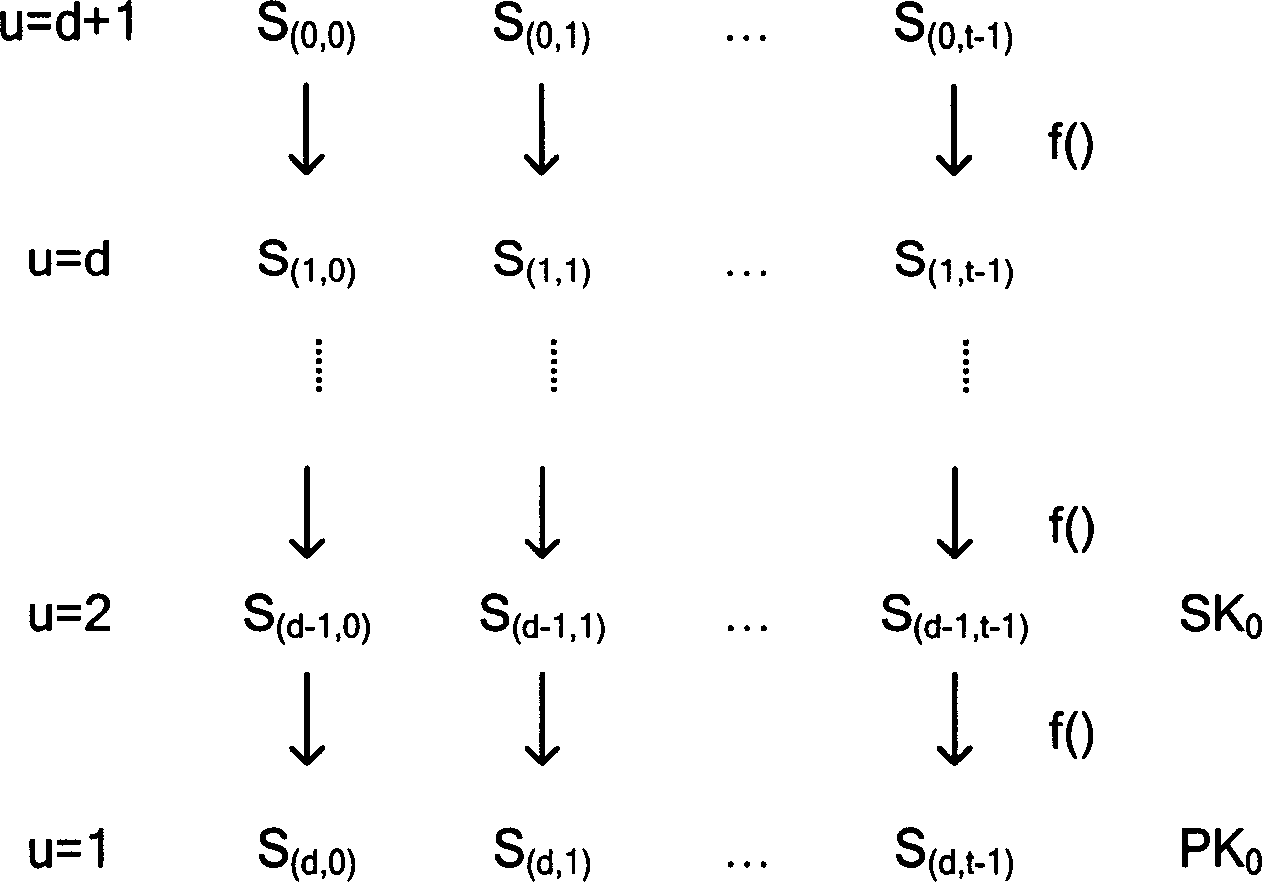
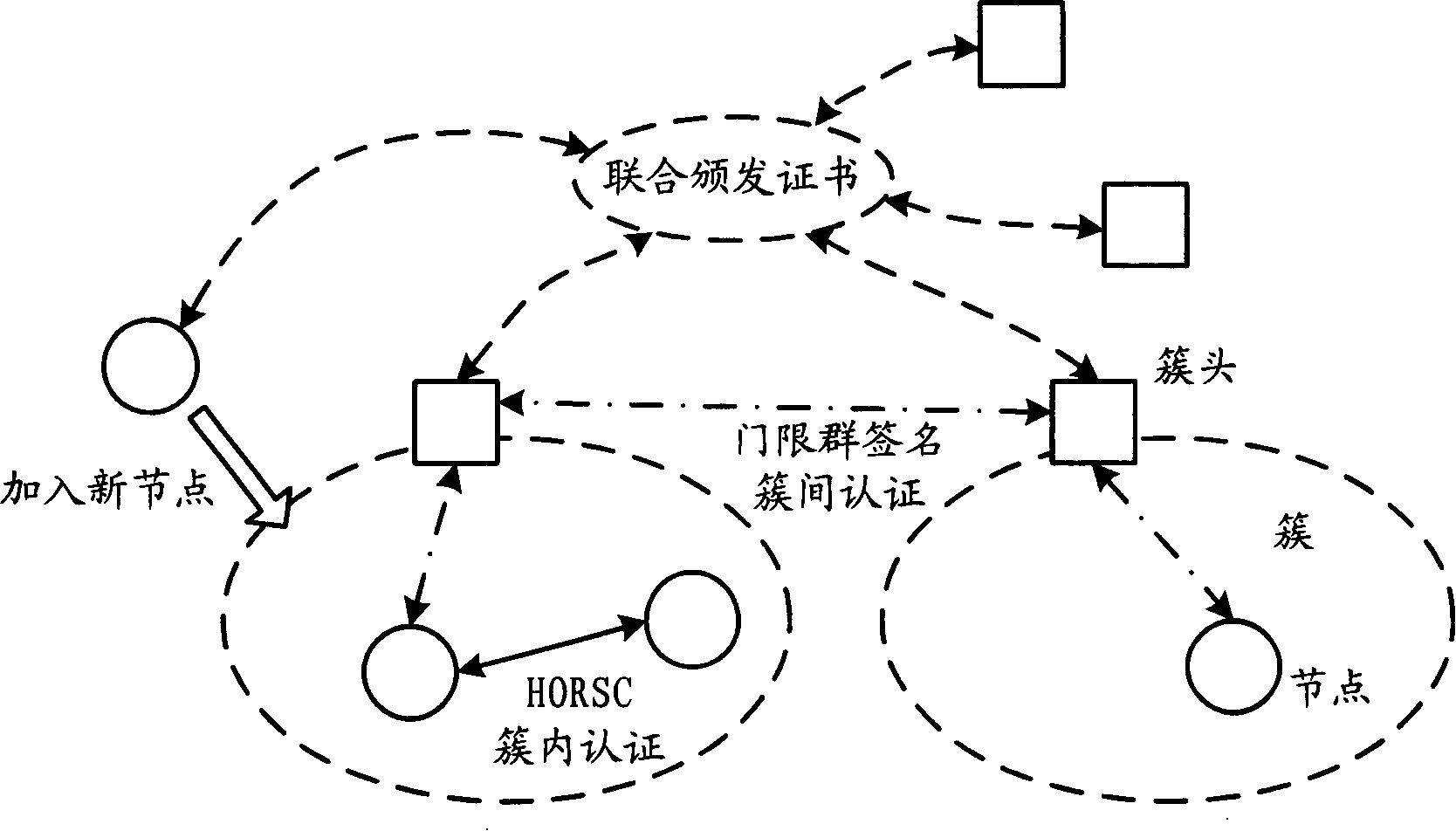
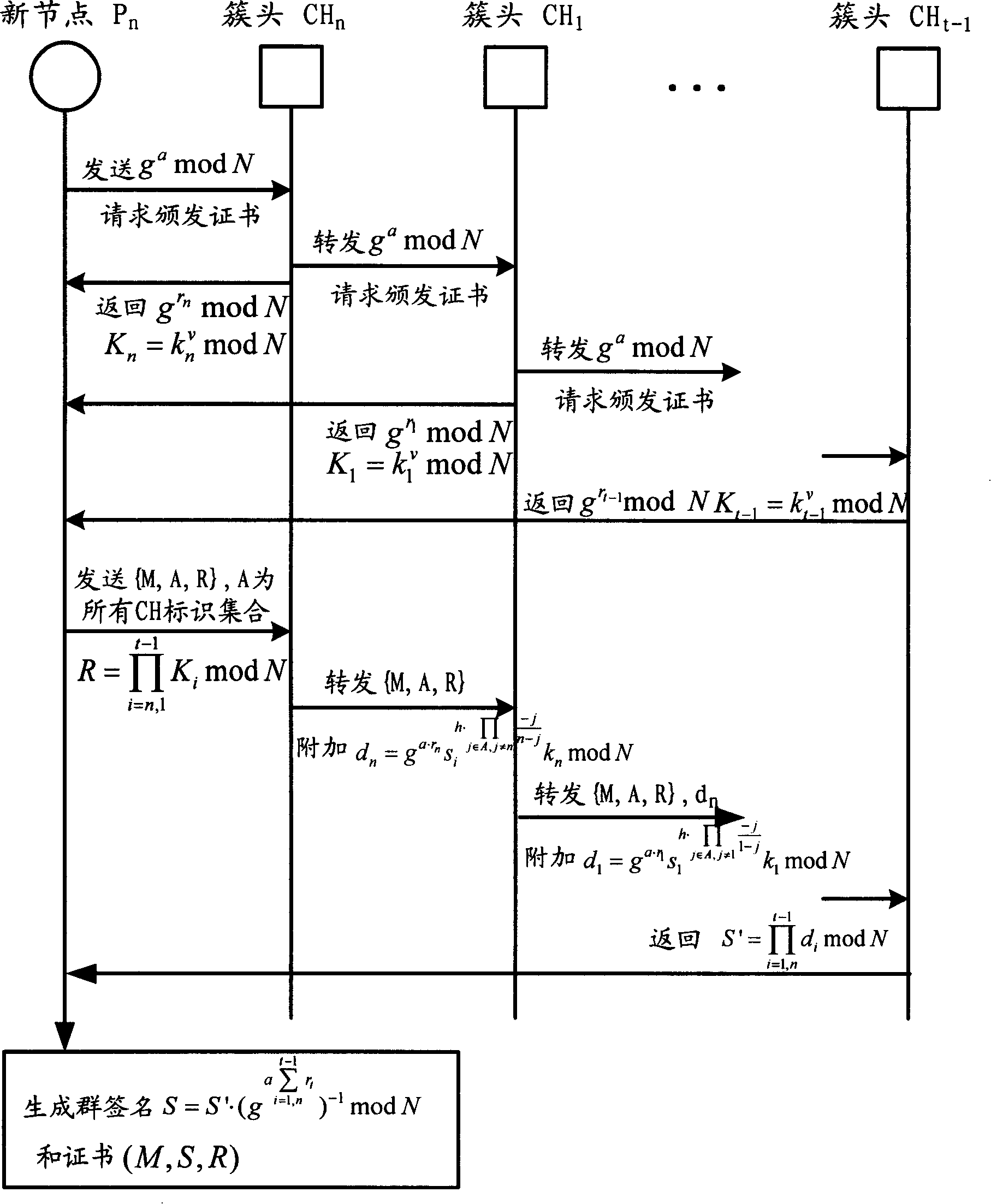
[0069] The most basic networking method of mobile ad hoc networks is flat networking. The defects of this method prevent it from being promoted and developed, and clustered networking is widely recognized. Especially when the scale of the mobile ad hoc network is relatively large, the network needs to be managed hierarchically. The authentication mechanism of a simple flat network can no longer meet the authentication requirements of the network. Hierarchical distributed authentication is a good solution. Based on this starting point, the present invention proposes a hierarchical distributed authentication solution, which respectively uses an improved new threshold group signature protocol to achieve inter-cluster authentication, and uses a Hash chain-based HORSC...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com