Cross-domain authentication and key agreement method based on block chain in Internet of Things environment
A technology of key agreement and blockchain, which is applied in the field of cross-domain authentication and key agreement, which can solve problems such as inability to resist man-in-the-middle attacks, reduced scalability, and high communication costs, so as to avoid single point of failure and reduce network burden , Calculate the effect of small amount of data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0073] The utility model will be further described below with reference to the accompanying drawings and embodiments.
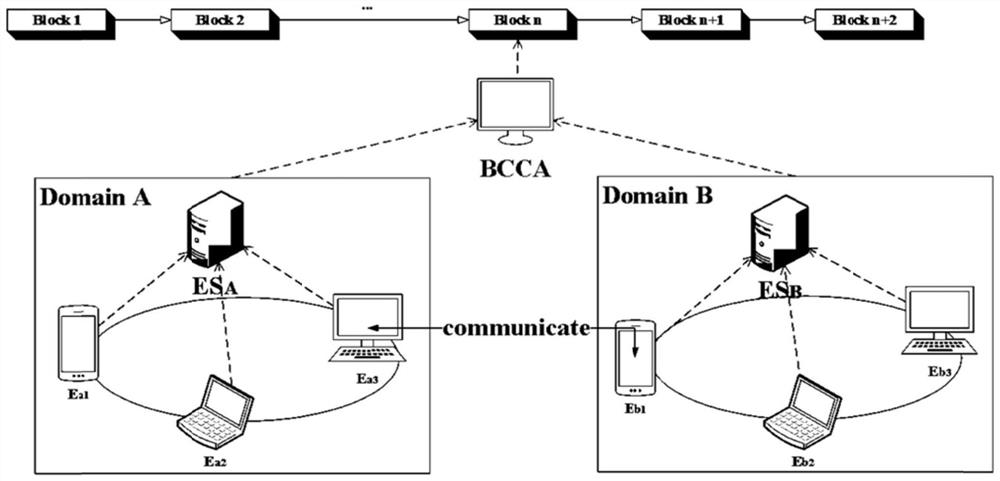
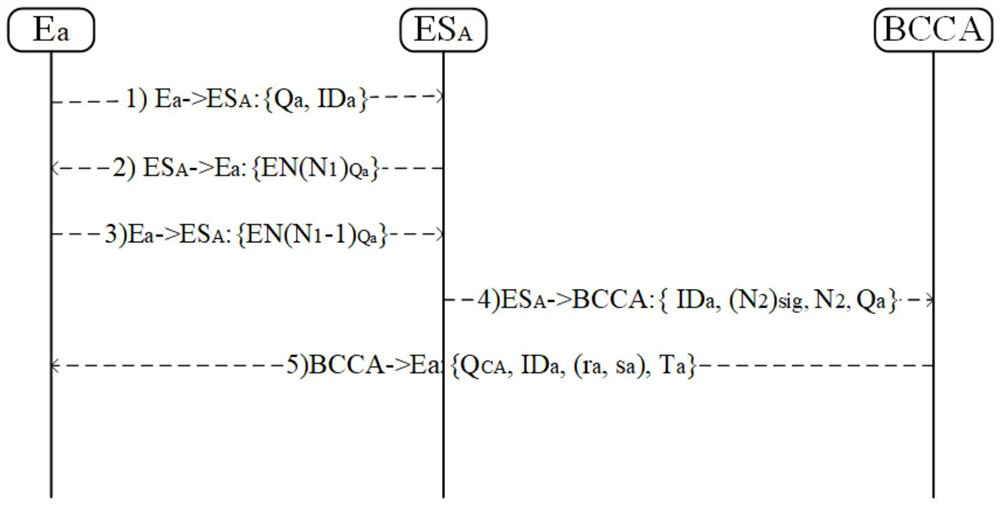
[0074] like figure 2 shown, figure 2 is the system frame diagram of the present invention, ES A As an edge server, it manages the devices in the trusted domain A (Domain A) and acts as a bridge between the end entity E and the Blockchain Certificate Authentication (BCCA). BCCA uploads the received information to the blockchain, and uses the immutability and traceability of the blockchain to ensure the authenticity and accuracy of the information. Edge entity E a After registration, it can communicate with post-authentication entities in the domain, and can also access cross-domain devices.
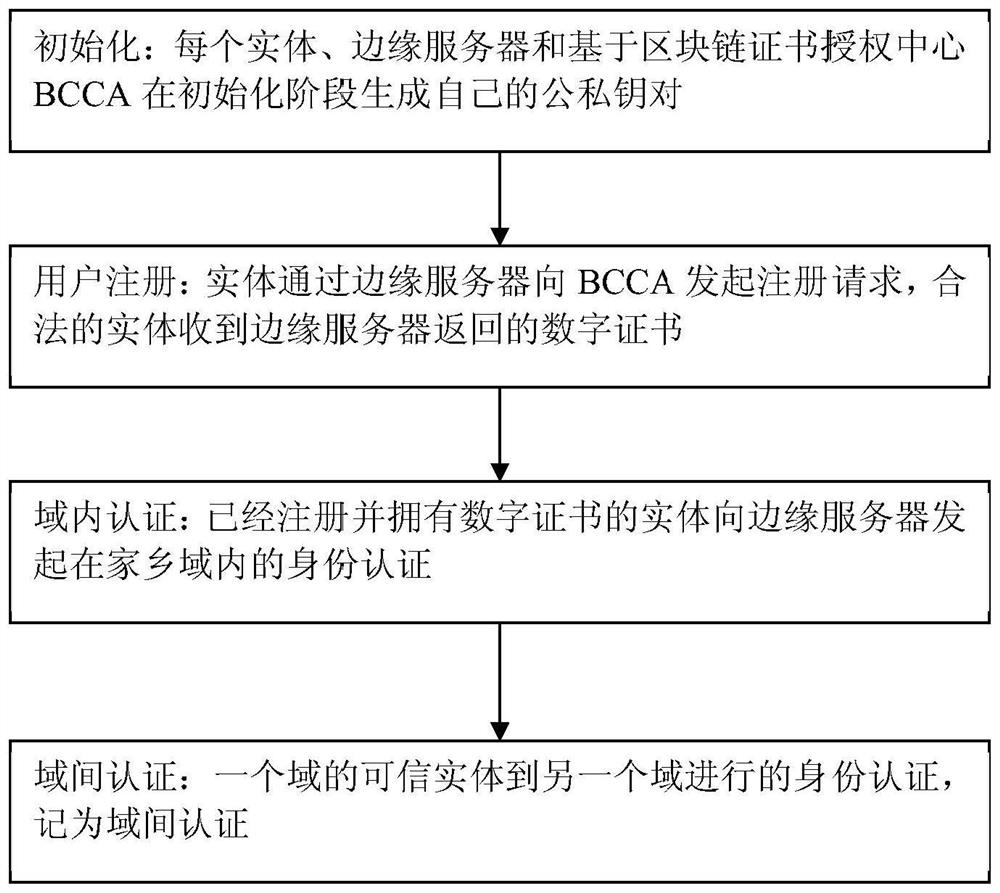
[0075] like figure 1 As shown, a blockchain-based cross-domain authentication and key agreement method in the Internet of Things environment includes the following steps:
[0076] (1) Initialization: Each entity, edge server and blockchain-based certificate author...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com