Two-factor authentication method based on portable TPM (PTPM) and certificateless public key signature for cloud
An authentication method and a certificate-free technology, applied in the field of cloud computing applications, which can solve the problems of complex user operation process, leakage of user privacy, and extension of untrusted path connections, and achieve the effect of improving computing efficiency and ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
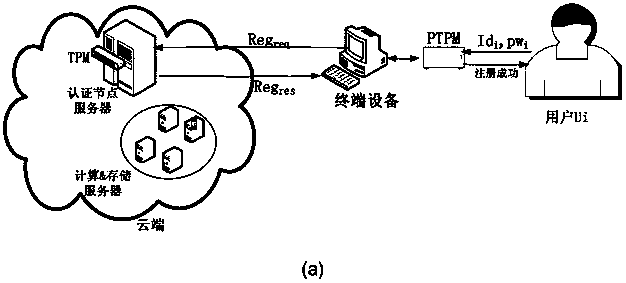
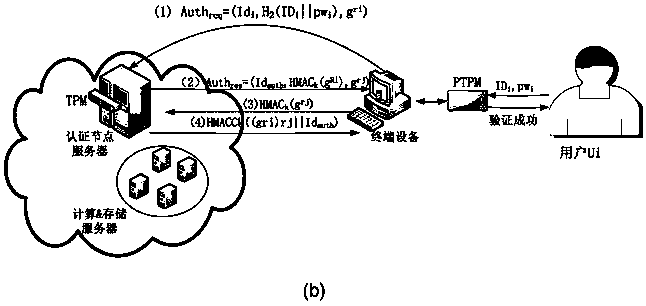
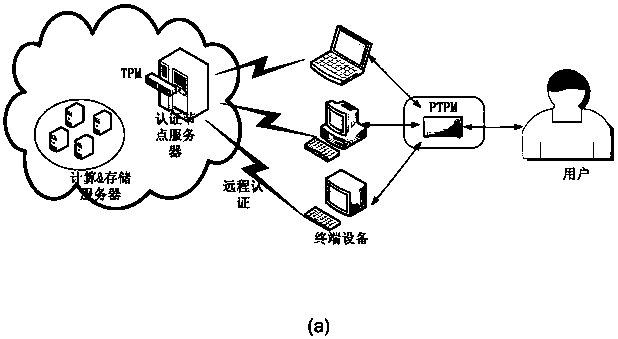
[0046] like figure 2 As shown, the user holds the PTPM hardware module, and the cloud authentication node server embeds the TPM security chip. The two-way authentication process between the user and the cloud includes figure 2 There are two stages of user registration shown in (a) and login authentication shown in Figure 2(b).
[0047] During the registration phase, user u i First enter the password pw i and ID i and other information, and then use PTPM to calculate the registration request information Reg req ;The authentication node server receives the user's registration request information Reg req After, first according to the identity ID i query user u i is registered, then enter KGC and u i 's public key and use the TPM calculation to verify that the i and ID i Check whether the signature value generated by the information is correct, and after verification is correct, the authentication node server stores the user u i registration information, and send the ...
Embodiment 2
[0051] (1) System establishment
[0052] Given a security parameter K, select a large prime p with a length of K bits, assuming G 1 and G 2 are all multiplicative cyclic groups of order p, where g is G 1 generator of . bilinear map e:GG 1 ×→ 1 G 2 , select the collision-resistant hash function H 1 , H 2 , H 1 :{0, 1} * →G 1 , H 2 :{0, 1} * →G 1 ;The system exposes the global parameter params as (G 1 , G 2 , e, p, g, H 1 , H 2 );
[0053] (2) Identity ID generation
[0054] The hierarchical ID tree structure proposed by the present invention defines the identity ID values of roles such as users and cloud servers in the cloud environment. The whole hierarchical structure consists of two layers. The root node is KGC, that is, the third-party key generation center that generates partial private keys of users; the leaf nodes represent end users registered in the cloud and the cloud authentication node server. Obviously, all nodes in the hierarchical ID tree st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com