Confidential active type strategy linkage method
A proactive and strategic technology, applied in the field of information security, can solve the problems of unreliable security event alarm information, high false alarm rate and false alarm rate, and achieve the effect of ensuring consistency, improving accuracy, and reducing risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
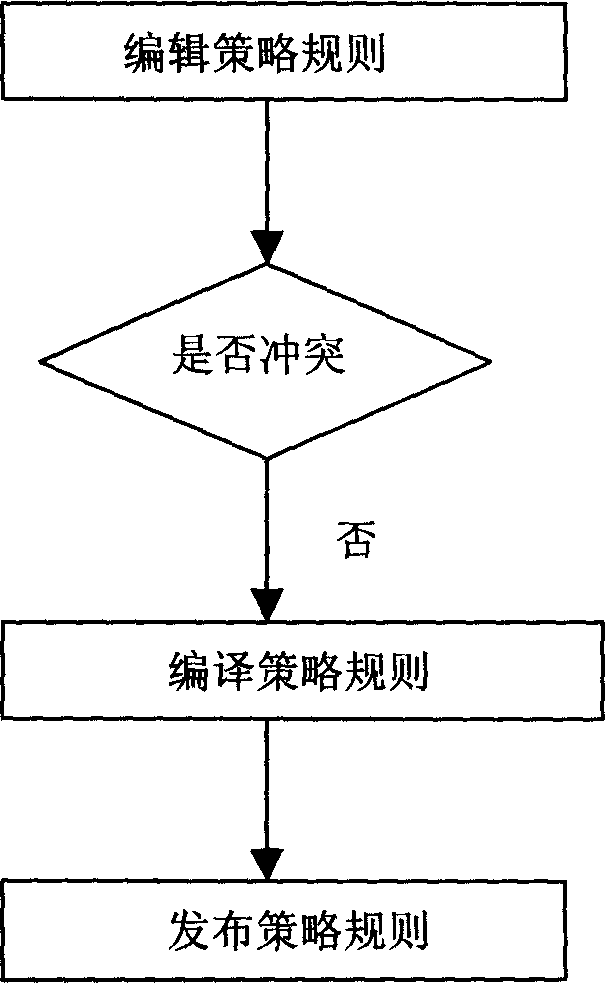
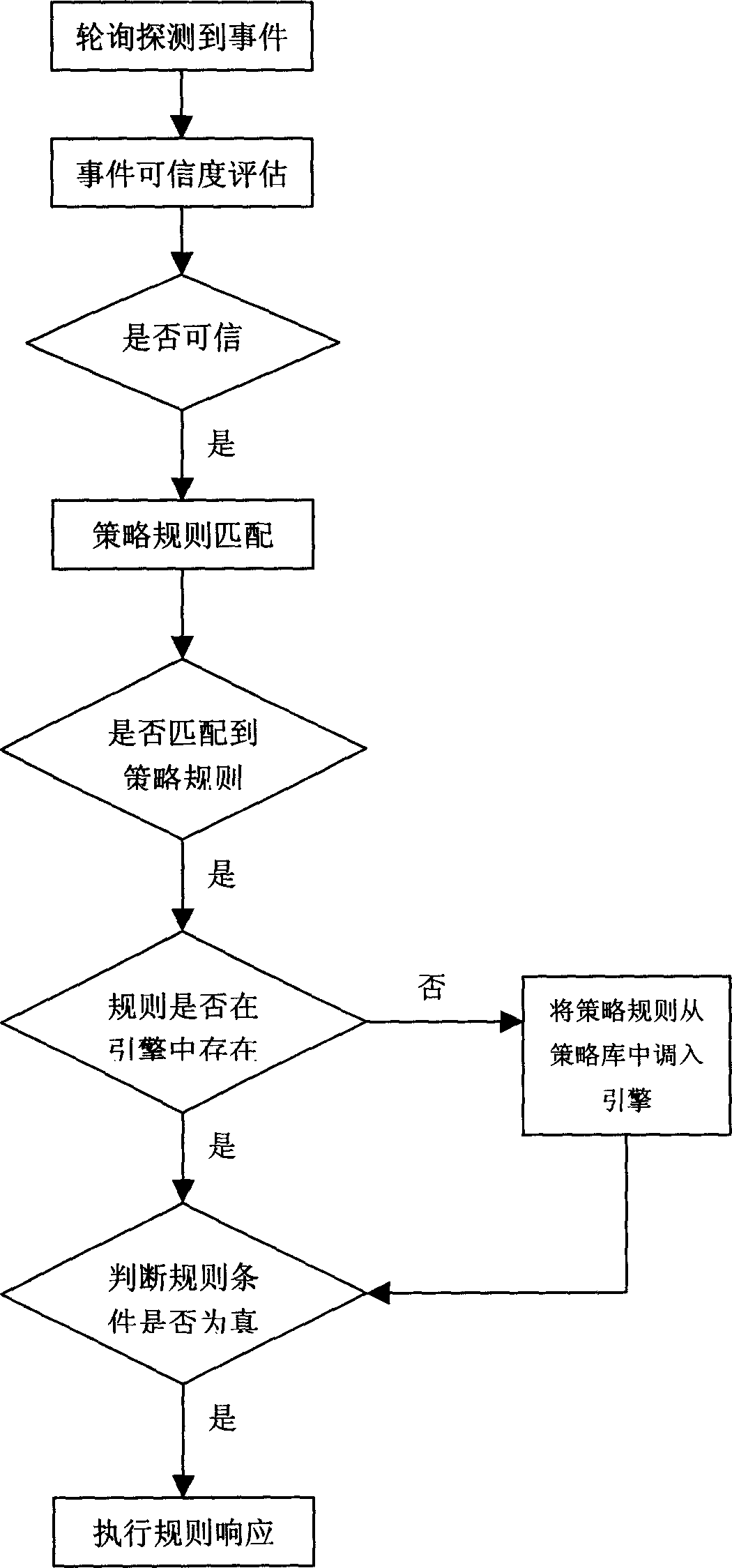
[0017] The following examples are provided in conjunction with the content of the method of the present invention:
[0018] The linkage policy engine is arranged on a PC, which can be located anywhere in the network, but must be able to allow the policy manager to access and issue linkage policies through an existing physical network such as a public data network. At the same time, the linkage policy engine must be able to access the LDAP policy library through the existing physical network; the policy manager is deployed at any location on the network, but must be able to access the policy engine through the existing physical network. Construct a Bayesian network of security events according to the user's policy linkage requirements, and develop a security event adapter based on the Bayesian network, and then deploy the security event adapter at the bottom of the linkage policy engine. Develop corresponding conditional adapters and corresponding adapters for different securit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com