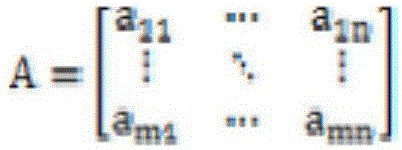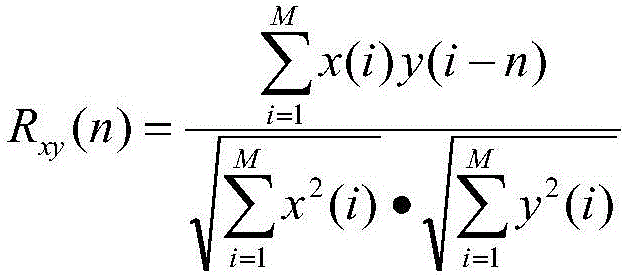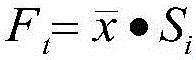Patents
Literature
80 results about "Strategy implementation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Strategy implementation is the activities within a workplace or organisation designed to manage the activities associated with the delivery of a strategic plan.
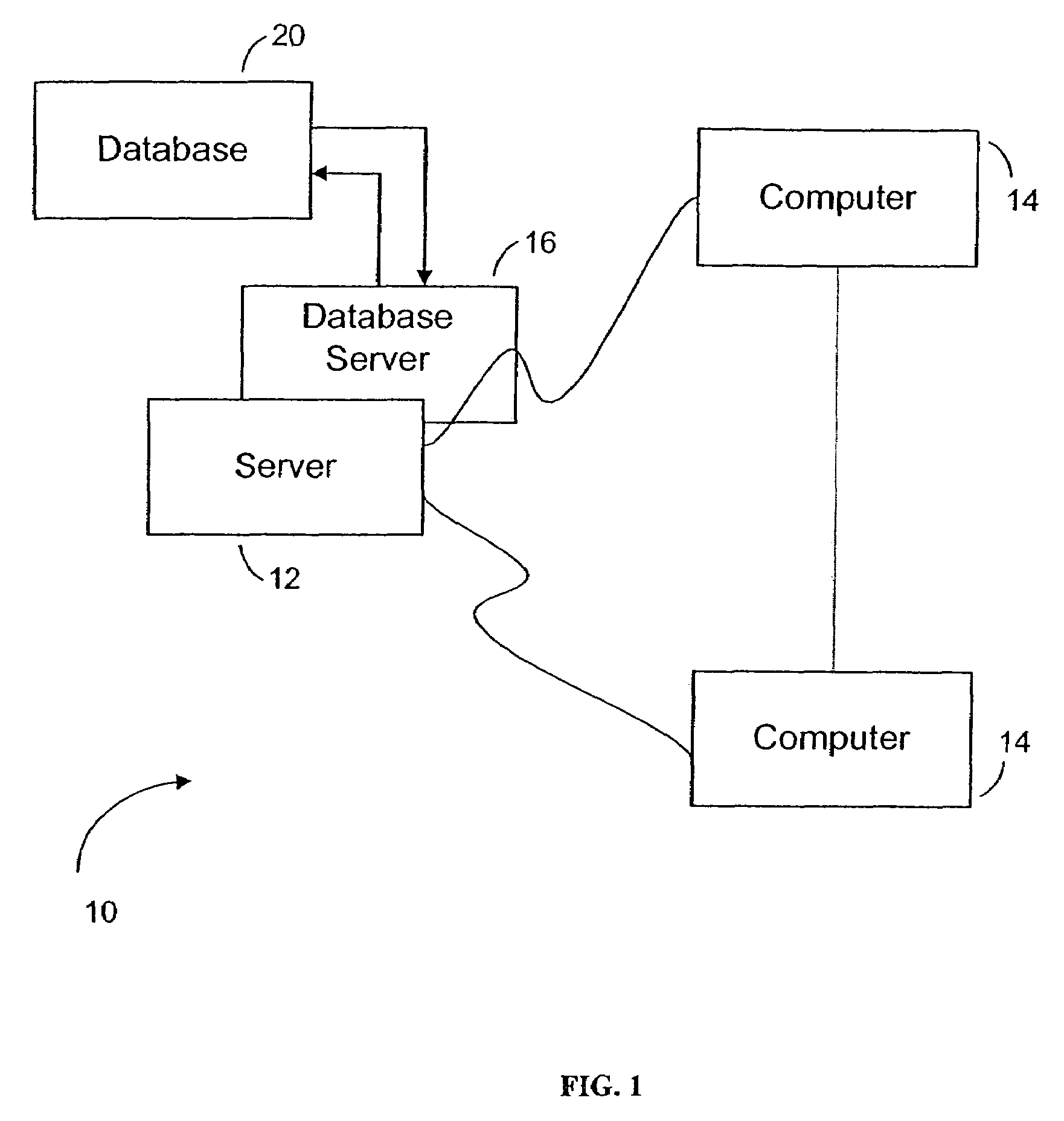
Method and system for load balancing of metadata management in distributed file system
InactiveCN101697526AIncrease profitSmooth expansionData switching networksDistributed File SystemMetadata management
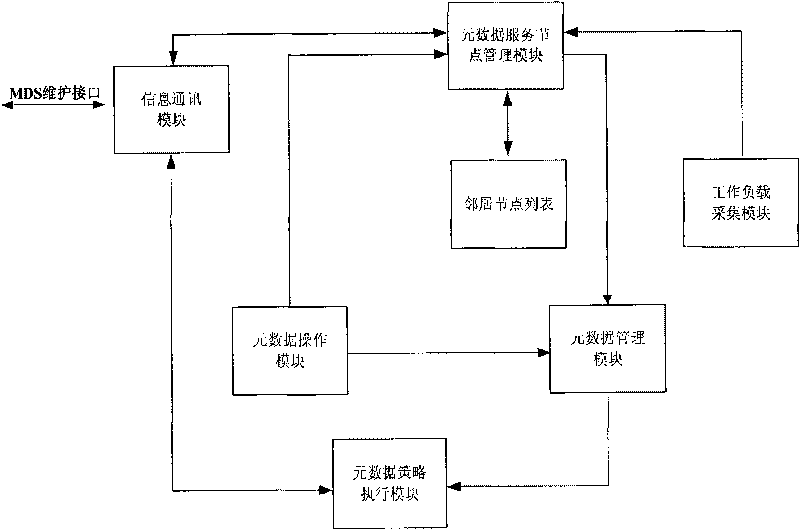
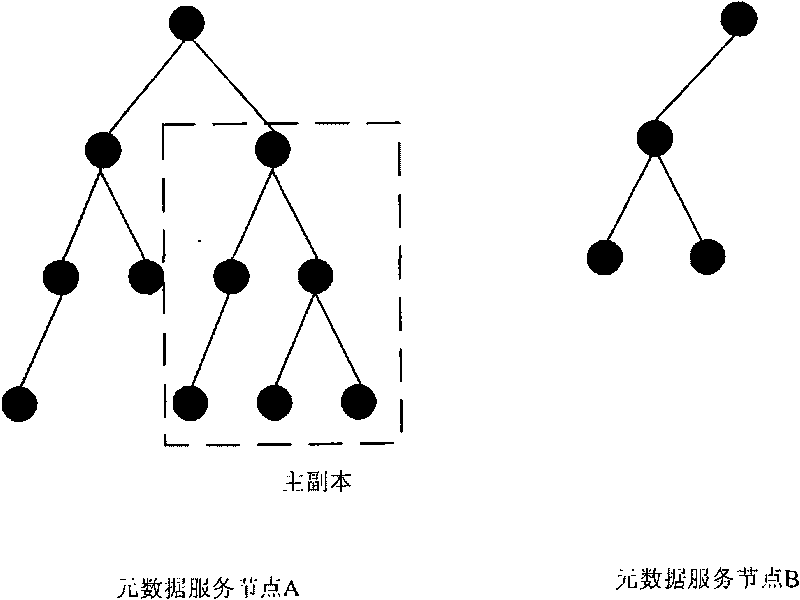
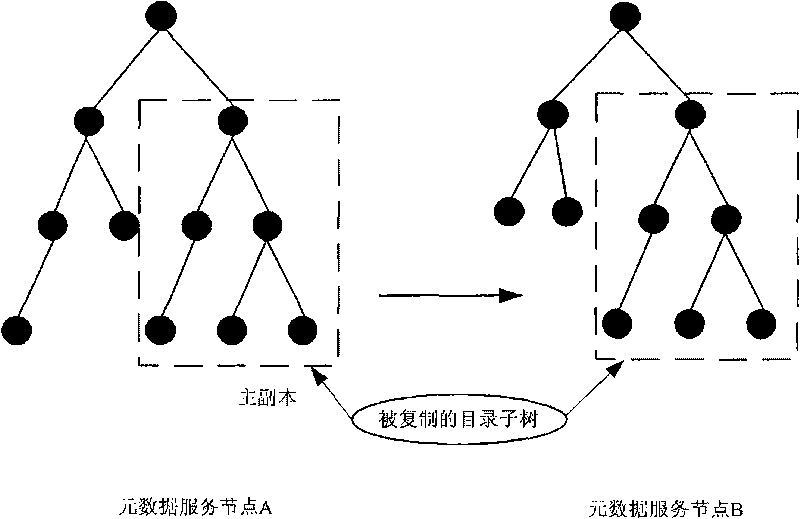
The invention relates to a method and a system for load balancing of metadata management in a distributed file system. When the data structure of metadata, i.e. a directory tree, becomes hotspot metadata, the access heat degree of the directory tree is updated through adopting a mode of copying the metadata; when the load balancing degrees of service nodes of the metadata exceeds a preset value, partial working loads are transferred to underload nodes from overload nodes through adopting a mode of transferring the metadata; and the loading balancing among a plurality of the metadata service nodes is realized through the two modes. The system comprises an information communication module, a metadata operation module, a metadata service node management module, a metadata management module, a metadata strategy implementation nodule and a working load acquisition module. The invention improves the utilization rate of metadata service resources through the two modes of copying and transferring the metadata so as to achieve the purpose of load balancing, thus a metadata service system can be smoothly expanded.
Owner:UNIV OF SCI & TECH OF CHINA
Network based system and method for marketing management
ActiveUS7526434B2Improve business productivityReduce riskDigital data processing detailsSpecial data processing applicationsClient-sideKnowledge management
A marketing management method and a system to manage interactions, develop base line for the current performance, analyzing various marketing strategies and selecting a desirable marketing strategy for implementation are disclosed. In one embodiment of the invention, the method helps clients prepare product and service brands to mitigate risks and maximize profits. The method utilizes a web-based system including a server system coupled to a centralized interactive database and at least one client system. The method further includes the steps of documenting benefits and leading indicator metrics to evaluate an impact of the new marketing strategy and then making iterative improvements after strategy implementation to the new marketing strategy to refine the marketing strategy further to reduce risks and increase profits.
Owner:SHARP LINDA
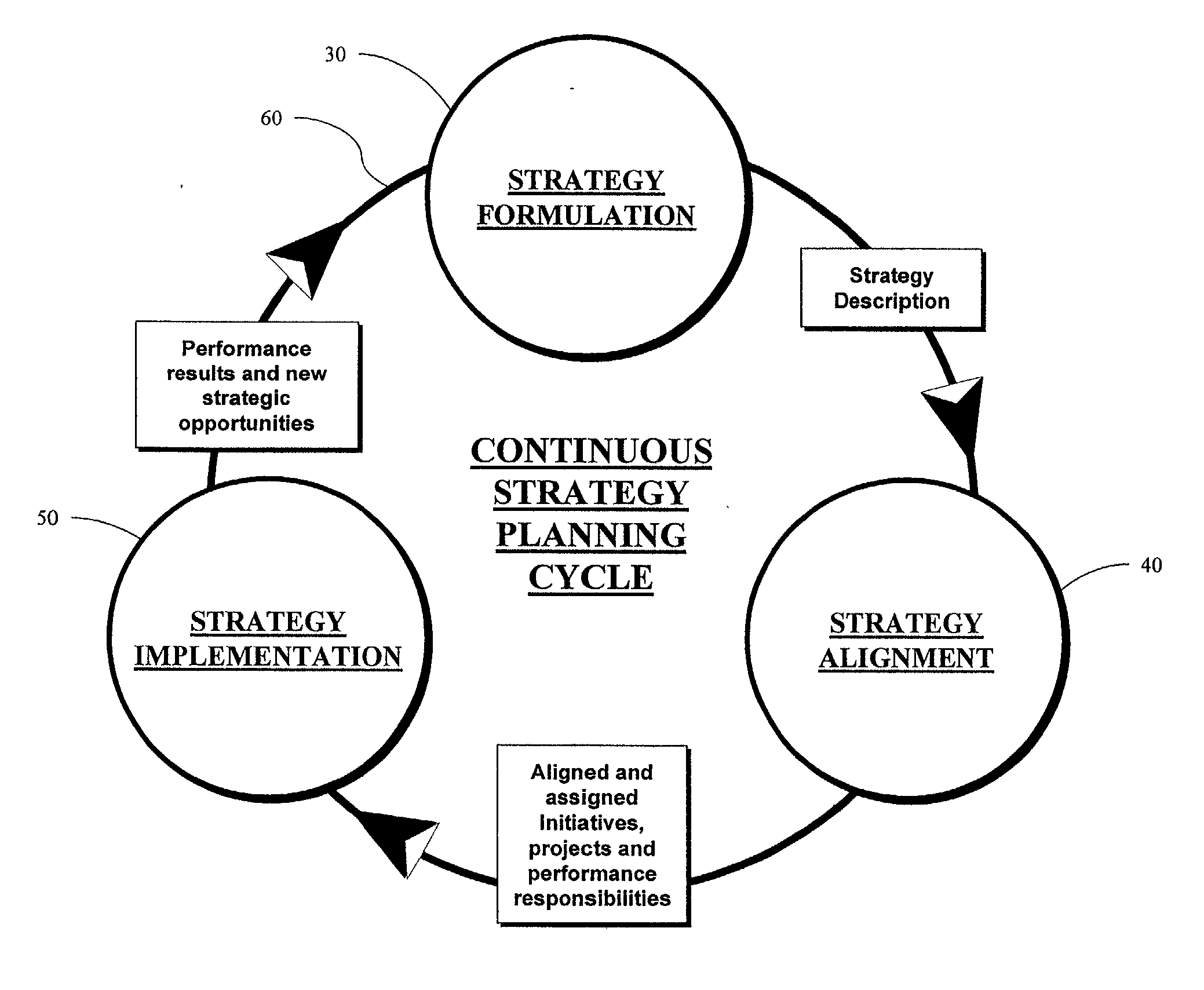
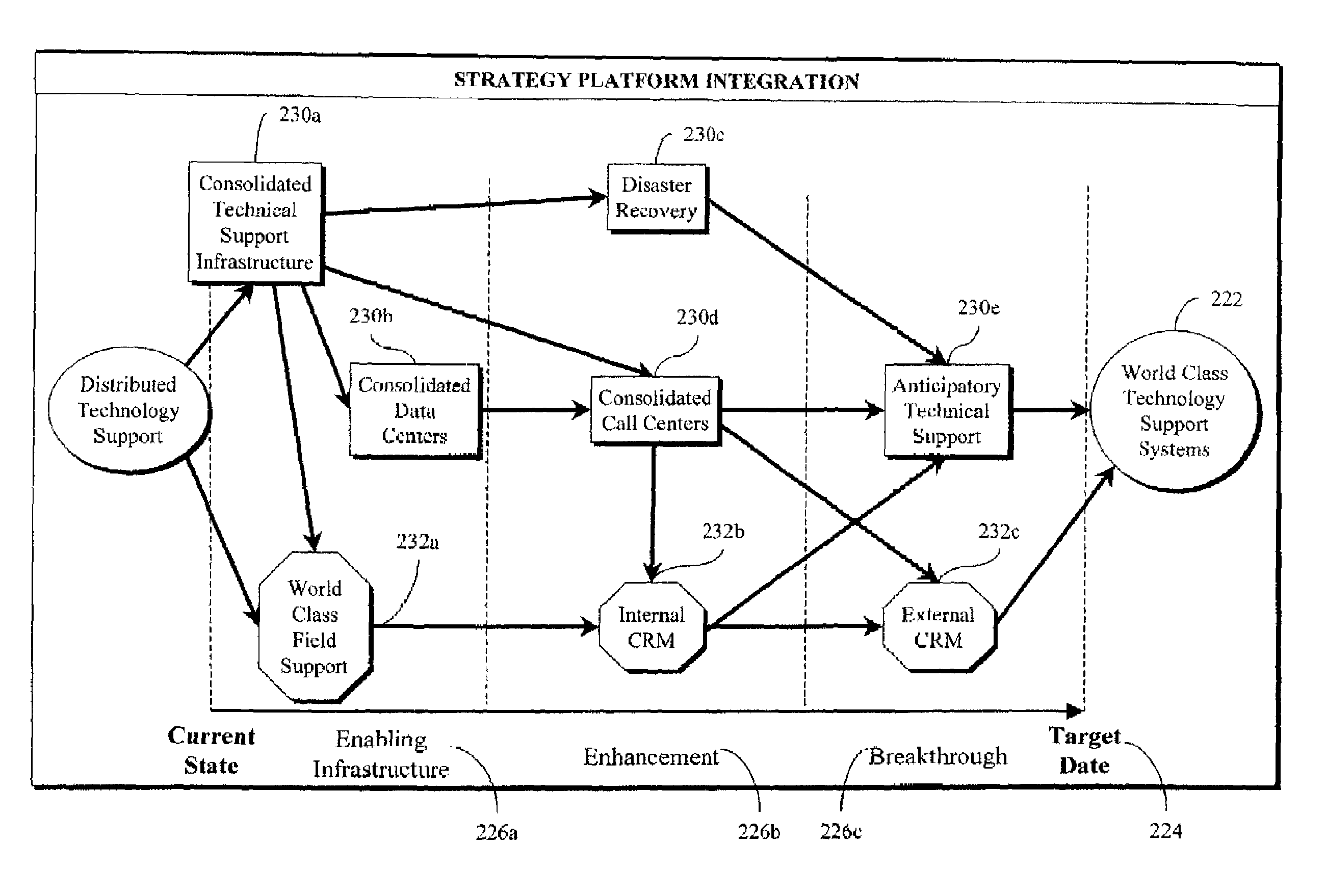
Enterprise strategy alignment framework
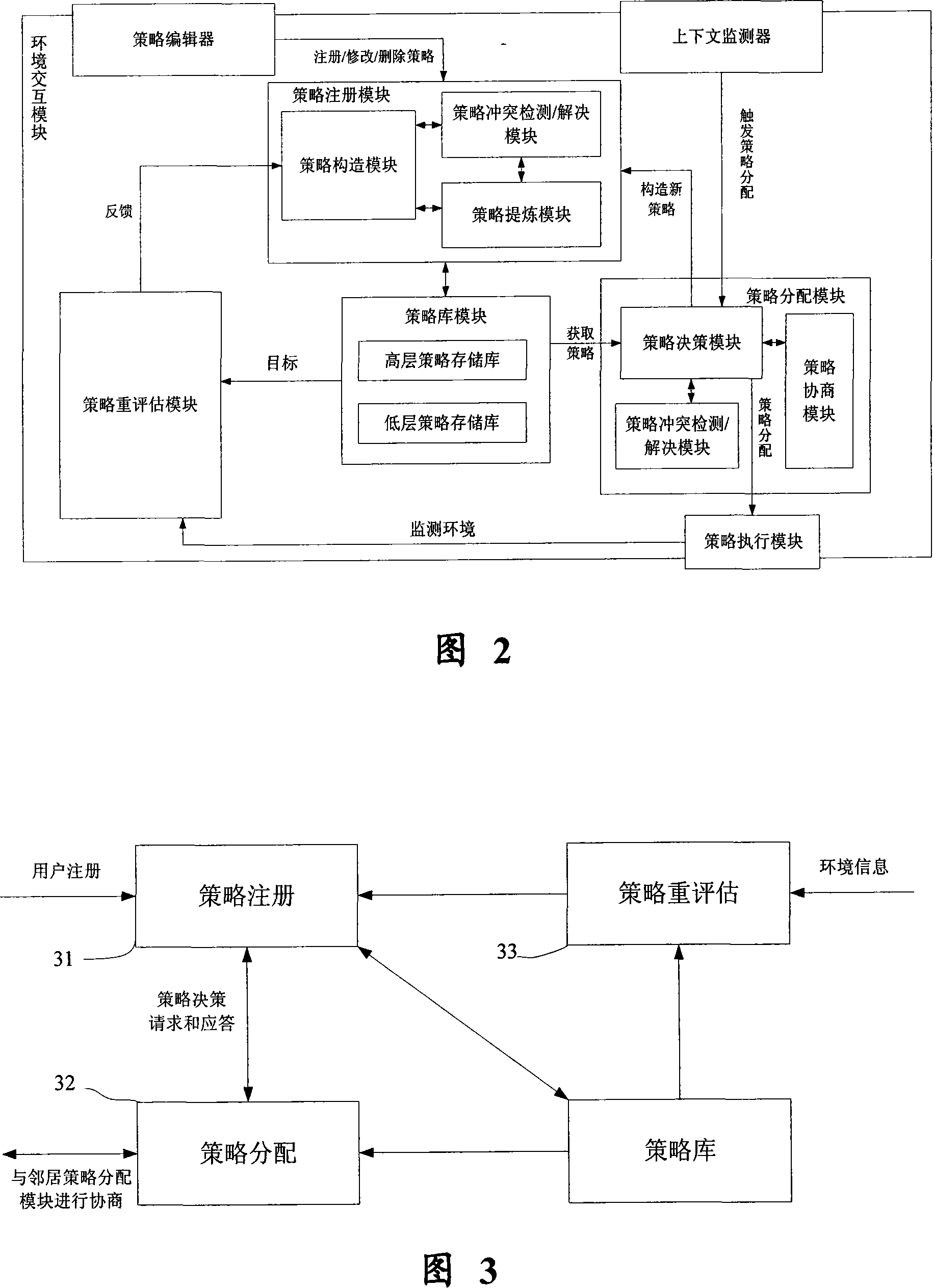
An enterprise strategy management system includes a first software module adapted to formulate a strategy description based on an assessment of environmental data, a second software module adapted to align the strategy description with available enterprise resources and deploy strategy implementation responsibilities, and a third software module adapted to measure the execution of the strategy and identify opportunities to optimize strategic performance. The first, second and third software modules are adapted to implement a continuous strategy management cycle, and may be executed in any order. In one embodiment, the first software module is an STRATEGY FORMULATION module, the second software module is an STRATEGY ALIGNMENT module and the third module is an STRATEGY IMPLEMENTATION module. The STRATEGY FORMULATION module includes software components for assessing environmental data, formulating and analyzing strategic alternatives and determining and approving a final, multi-level strategy description. The STRATEGY ALIGNMENT module includes software components for aligning strategy components, describing and aligning operational strategy components, planning projects, initiatives and performance metrics activity, and deploying implementation responsibilities. The STRATEGY IMPLEMENTATION module includes software components for activating the launch of activities, implementing and measuring the execution of strategy and performance results, and identifying the opportunities to optimize strategic performance.
Owner:FLORES DAVID R
Derma diagnostic and automated data analysis system
ActiveUS8109875B2Monitor effectivenessDiagnostics using lightDiagnostics using spectroscopyData analysis systemData profiling
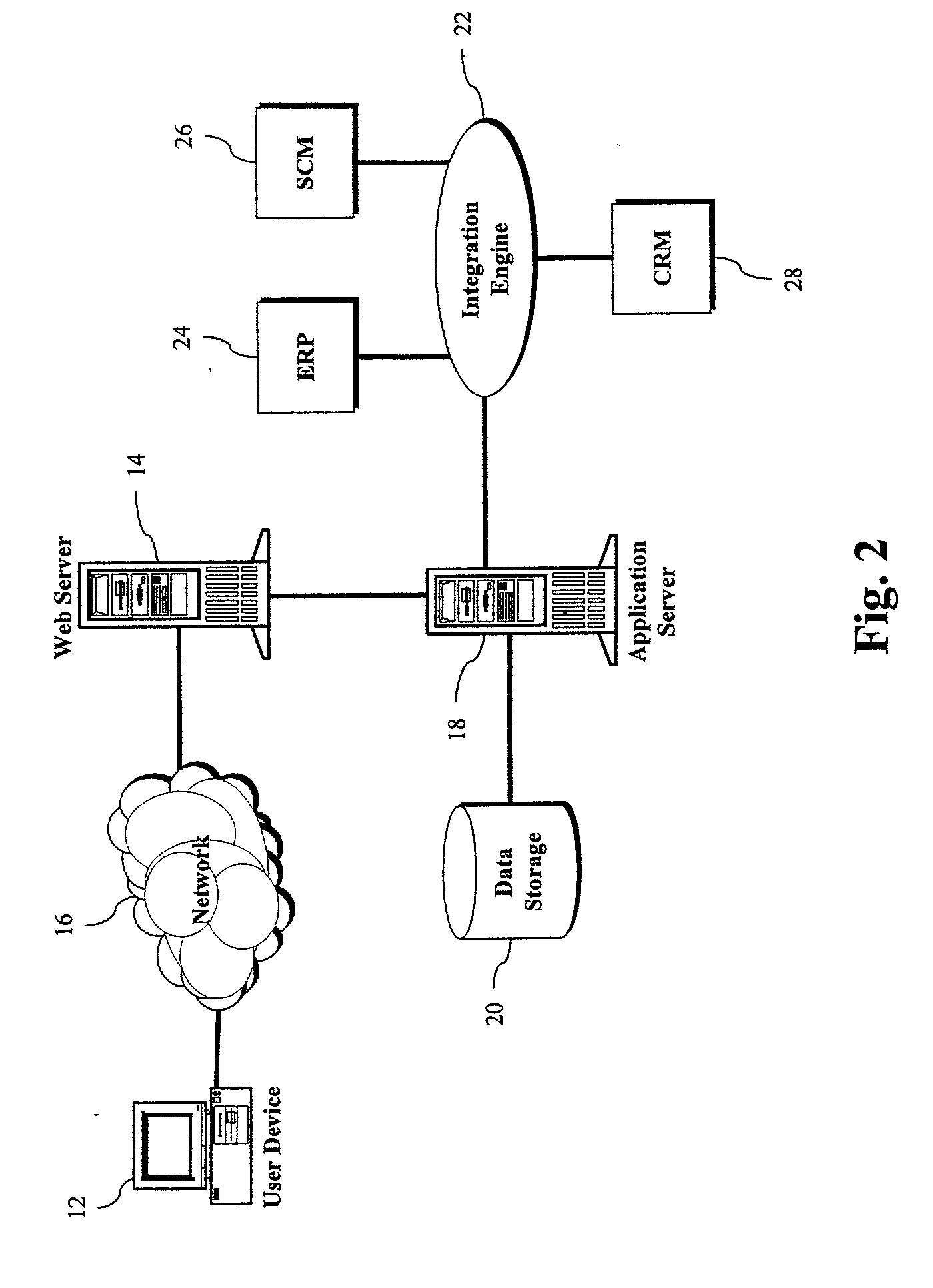
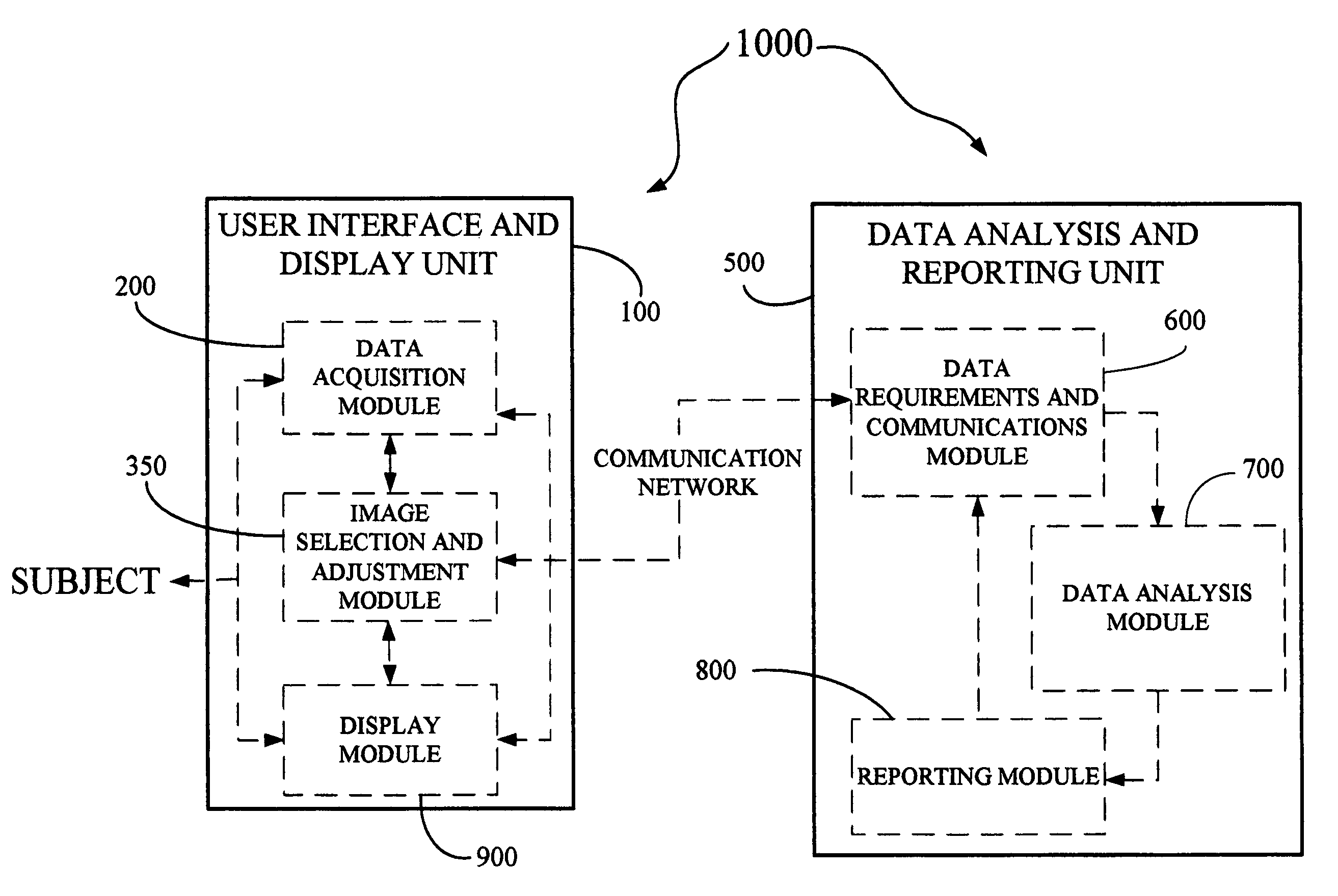
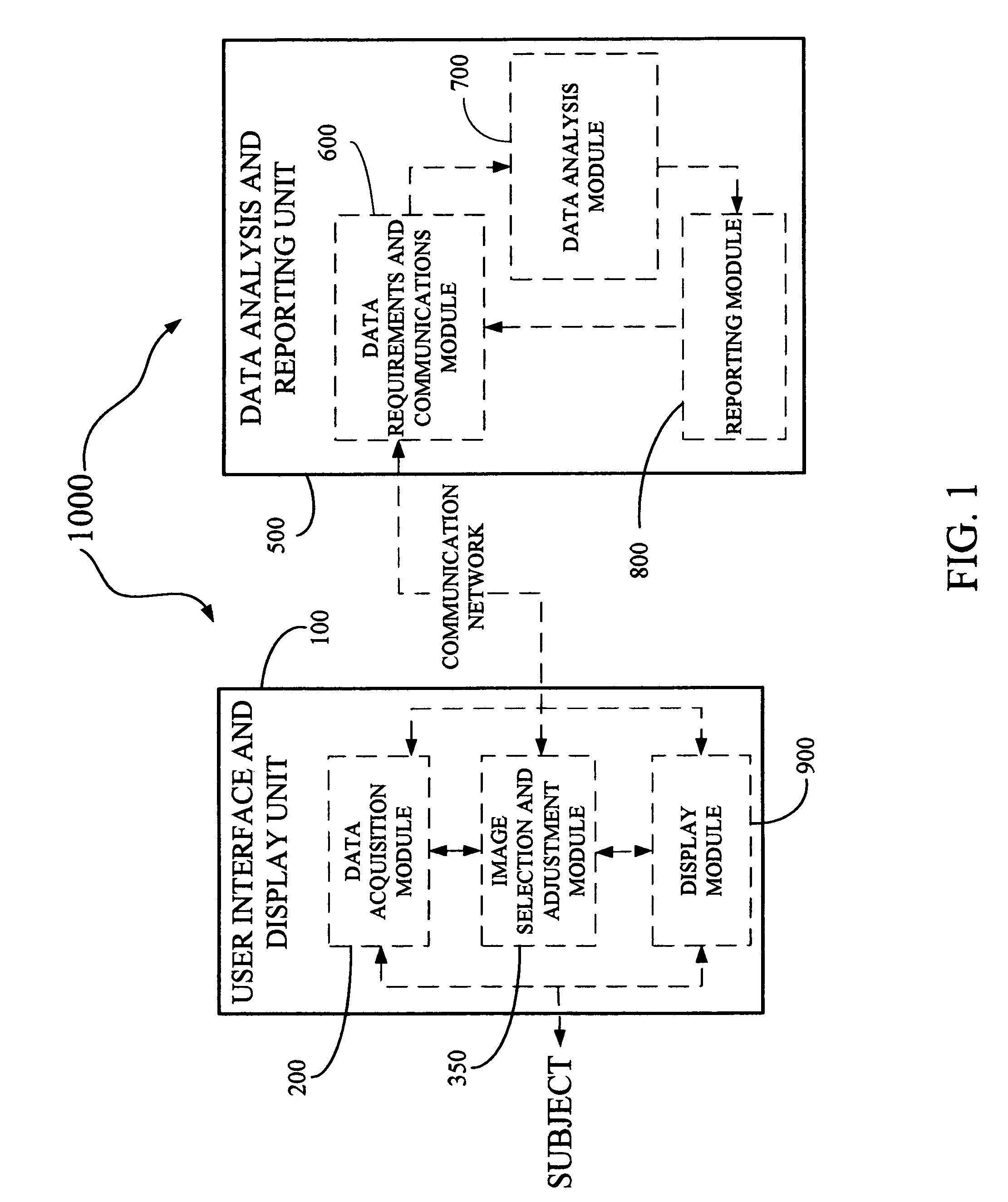
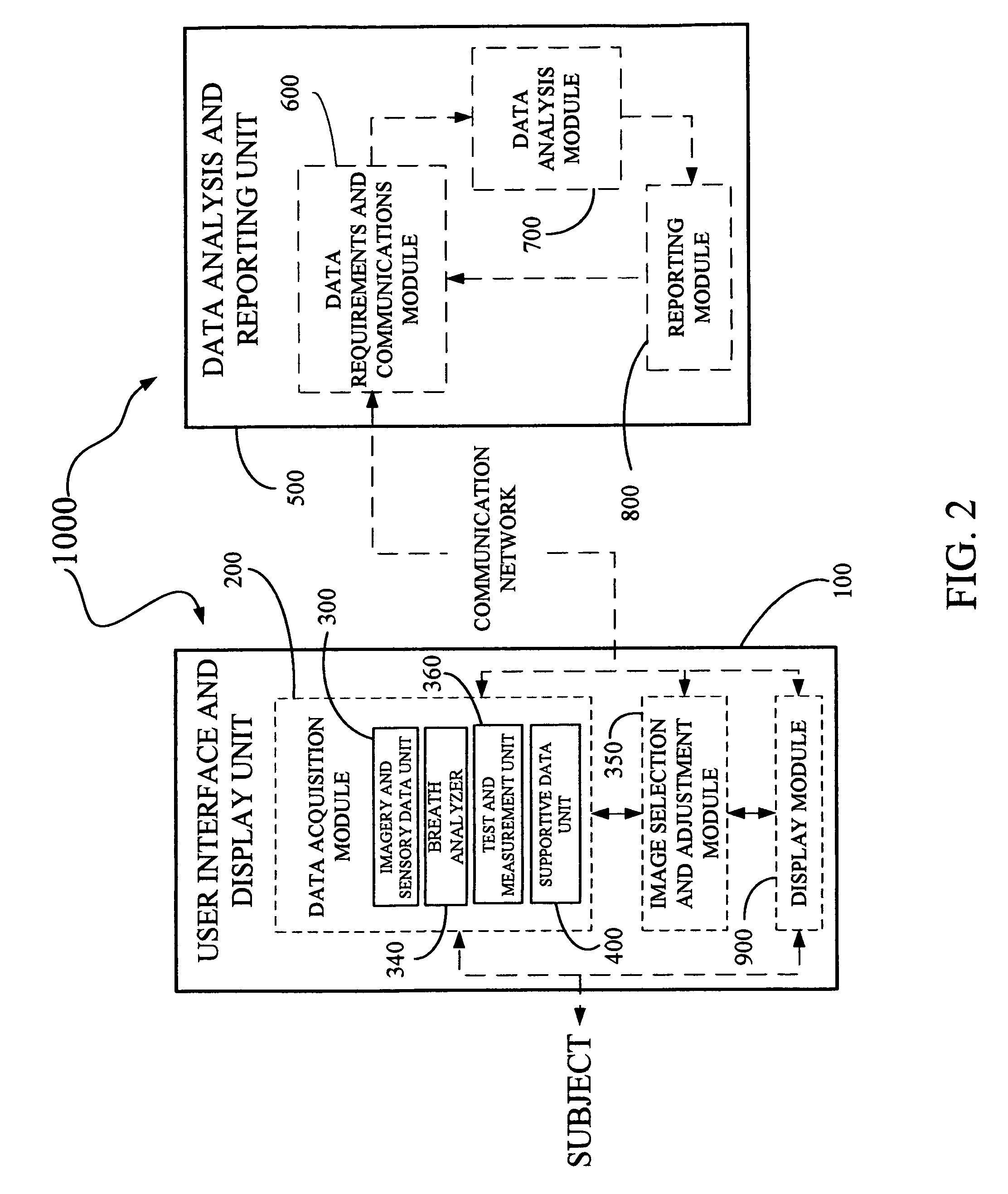
Disclosed is a derma diagnostic and automated data analysis system configured to acquire an array of data pertaining to a subject and their skin disorders. This data is subjected to a comprehensive analysis that culminates in diagnoses, treatments, monitoring activity and health strategy implementation. The derma diagnostic and automated data analysis system comprises a user interface and display unit, capable of acquiring a range of subject data, and communicatively coupled to a remotely located data analysis and reporting unit. The data analysis and reporting unit is capable of receiving and assessing the acquired data, using multiple analytical processes that culminate in a highly probable diagnosis and an effective treatment that is documented in a report and submitted to the subject. The diagnoses, treatments and supporting data are then permanently archived and made available for retrieval.
Owner:GIZEWSKI THEODORE M
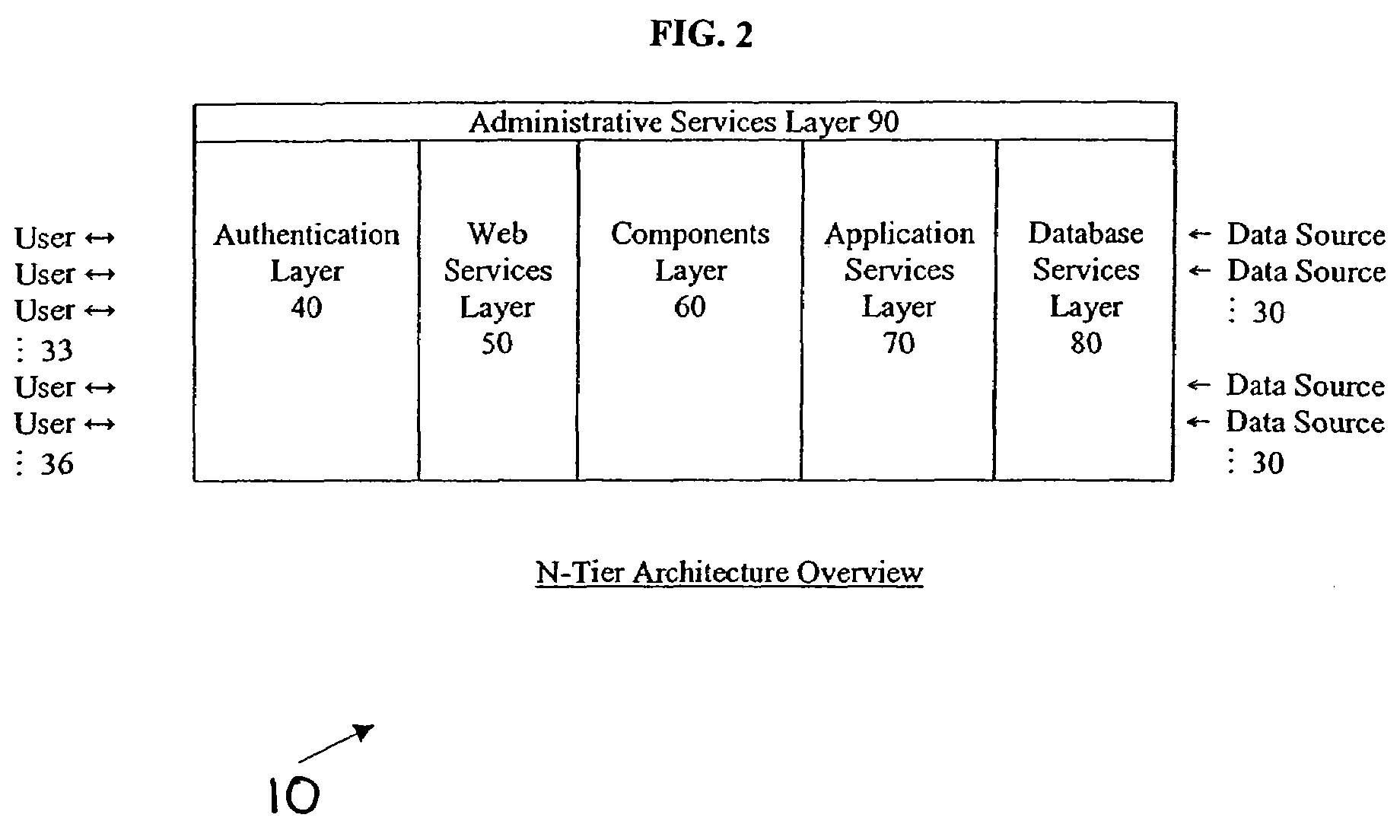
System and method for generating a multi-layered strategy description including integrated implementation requirements
InactiveUS7251613B2Efficiently distributing and executingImprove performanceResourcesOperational strategyPerformance index
An enterprise strategy management system includes a first software module adapted to formulate a strategy description based on an assessment of environmental data, a second software module adapted to align the strategy description with available enterprise resources and deploy strategy implementation responsibilities, and a third software module adapted to measure the execution of the strategy and identify opportunities to optimize strategic performance. The first, second and third software modules are adapted to implement a continuous strategy management cycle, and may be executed in any order. In one embodiment, the first software module is an STRATEGY FORMULATION module, the second software module is an STRATEGY ALIGNMENT module and the third module is an STRATEGY IMPLEMENTATION module. The STRATEGY FORMULATION module includes software components for assessing environmental data, formulating and analyzing strategic alternatives and determining and approving a final, multi-level strategy description. The STRATEGY ALIGNMENT module includes software components for aligning strategy components, describing and aligning operational strategy components, planning projects, initiatives and performance metrics activity, and deploying implementation responsibilities. The STRATEGY IMPLEMENTATION module includes software components for activating the launch of activities, implementing and measuring the execution of strategy and performance results, and identifying the opportunities to optimize strategic performance.
Owner:FLORES DAVID
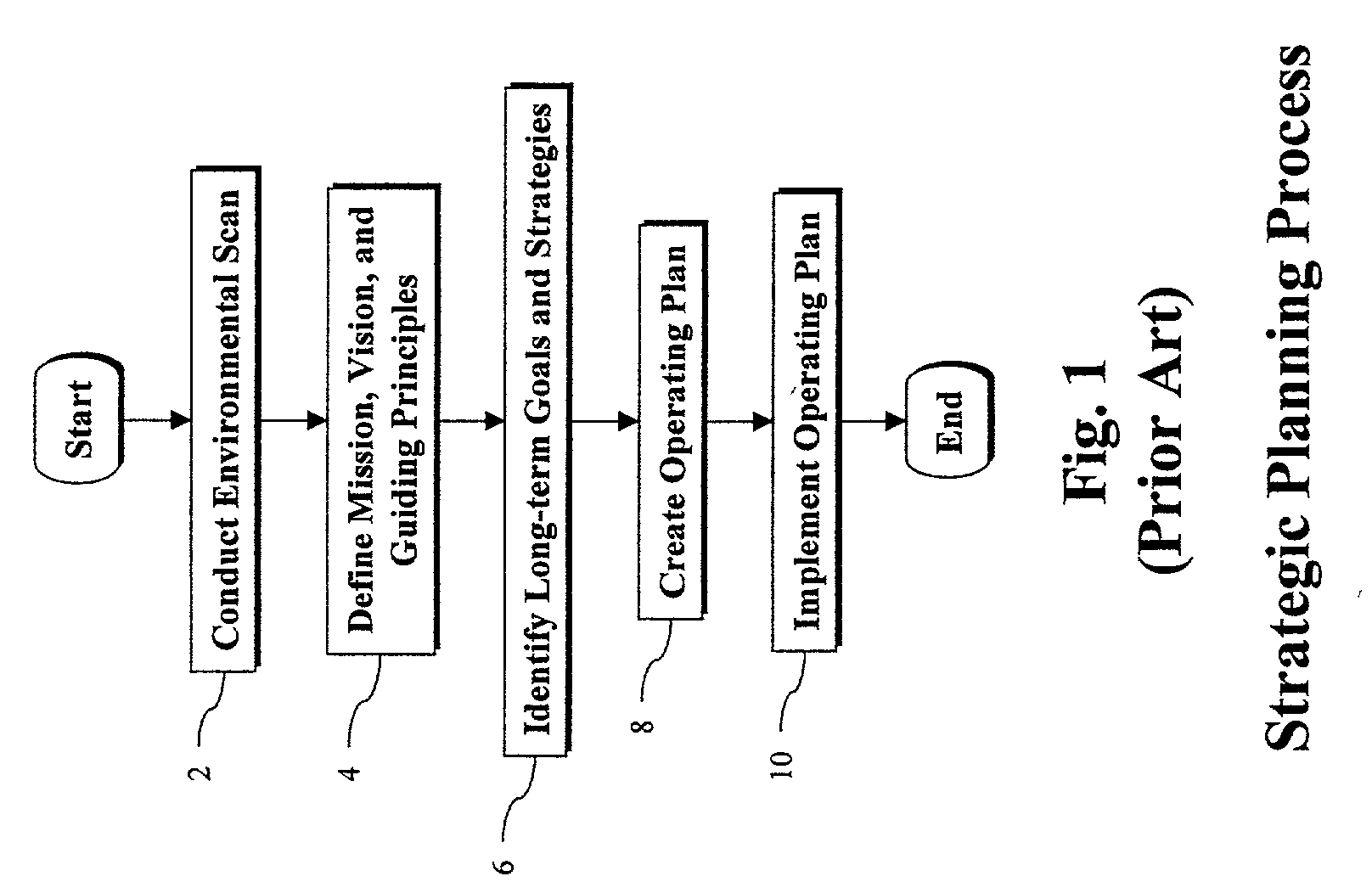
Method for developing an enterprise alignment framework hierarchy by compiling and relating sets of strategic business elements
InactiveUS7346529B2Stable supportEfficiently distributing and executingOffice automationResourcesOperational strategyPerformance index
An enterprise strategy management system includes a first software module adapted to formulate a strategy description based on an assessment of environmental data, a second software module adapted to align the strategy description with available enterprise resources and deploy strategy implementation responsibilities, and a third software module adapted to measure the execution of the strategy and identify opportunities to optimize strategic performance. The first, second and third software modules are adapted to implement a continuous strategy management cycle, and may be executed in any order. In one embodiment, the first software module is an STRATEGY FORMULATION module, the second software module is an STRATEGY ALIGNMENT module and the third module is an STRATEGY IMPLEMENTATION module. The STRATEGY FORMULATION module includes software components for assessing environmental data, formulating and analyzing strategic alternatives and determining and approving a final, multi-level strategy description. The STRATEGY ALIGNMENT module includes software components for aligning strategy components, describing and aligning operational strategy components, planning projects, initiatives and performance metrics activity, and deploying implementation responsibilities. The STRATEGY IMPLEMENTATION module includes software components for activating the launch of activities, implementing and measuring the execution of strategy and performance results, and identifying the opportunities to optimize strategic performance.
Owner:FLORES DAVID R
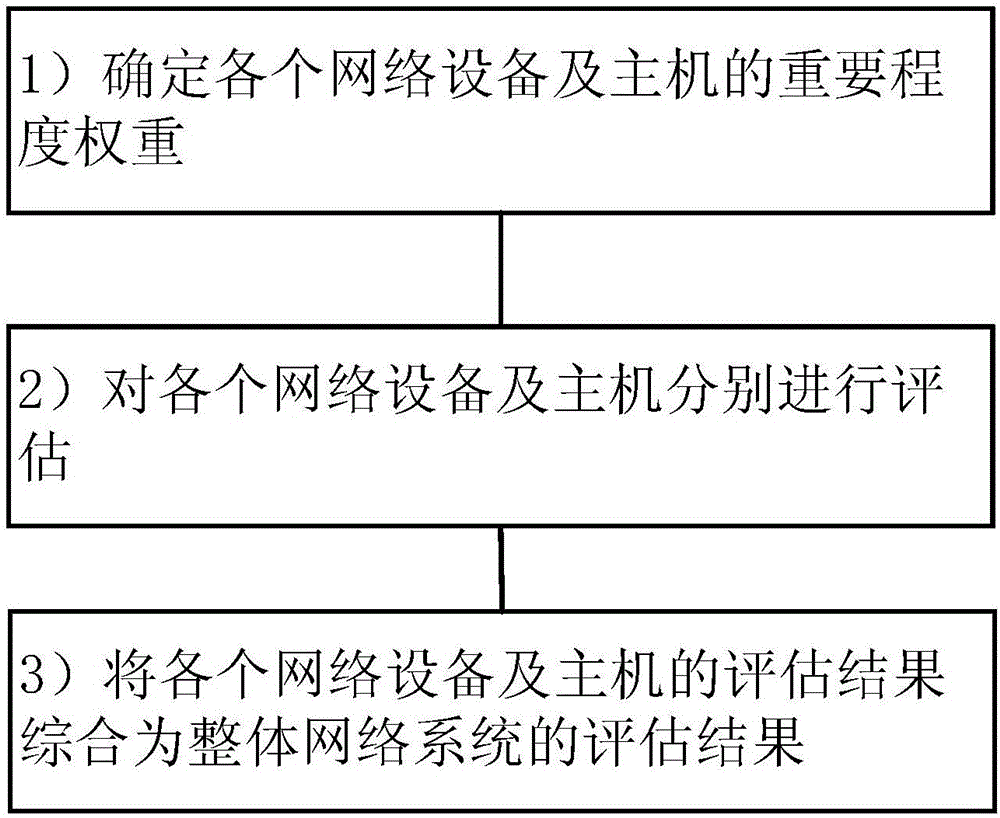
Network security situation evaluation method
The invention discloses a network security situation evaluation method. The method comprises the following steps: 1) determining the importance weights of network devices and hosts; 2) separately evaluating the network devices and hosts; and 3) integrating the evaluation results of the network devices and hosts into an evaluation result of the whole network system. According to the network security situation evaluation method disclosed by the invention, with the device assets as the center, the evaluation process is divided into three stages: the first stage is to determine the importance weights of network devices and hosts; the second stage is to separately evaluate the network devices and hosts; and the third stage is to integrate the evaluation results of the network devices and hosts into the security situation of the whole network. For the evaluation of a single device asset, the evaluation factors are divided into 8 categories, which are attacker capability, attack consequences, vulnerability damages, vulnerability transmission, security measures, security configuration correctness, security strategy and security strategy implementation, and the security situation is quantified from the perspective of threat and defense.
Owner:SHANDONG COMP SCI CENTNAT SUPERCOMP CENT IN JINAN
Lane dynamic partitioning control method for expressway intersection area
ActiveCN103871241AImprove traffic capacitySolve or ease traffic congestionRoadwaysDetection of traffic movementTraffic flowExclusive right
Provided is a lane dynamic partitioning control method for an expressway intersection area. For the expressway intersection area, based on the actual traffic state, lanes of the intersection area are dynamically partitioned into intersection area lanes and non-intersection area lanes through signal indication signs. The intersection of the upper ramp traffic, the lower ramp traffic and the mainline traffic is achieved by means of the intersection lanes; the exclusive right of way is provided for the non-intersection traffic flow of an expressway mainline by the utilization of the non-intersection lanes. The control method comprises the two parts of the dynamic partitioning of the functions of the intersection area lanes and the control over the functions of the intersection area lanes, and the lane function dynamic partitioning model regards the overall through-out capacity maximization as a target, and determines the number of vehicles on the intersection lanes and the non-intersection lanes; the lane function control part comprises a control strategy implementation scheme, information publishing equipment arrangement and an isolation implementation method. The method can provide the exclusive right of way for the expressway mainline traffic in the intersection area, and reduce the interference to straight vehicles of the mainline by the intersection behavior, thereby improving the through-out capacity of the intersection area; under the condition that the vehicles line up and overflow at an off-ramp, the straight vehicles of the mainline can pass through normally, the vehicle average delay is reduced, and the bottleneck problem of the expressway weaving area is solved or relieved.
Owner:TONGJI UNIV
Privacy disclosure monitoring method of android application file
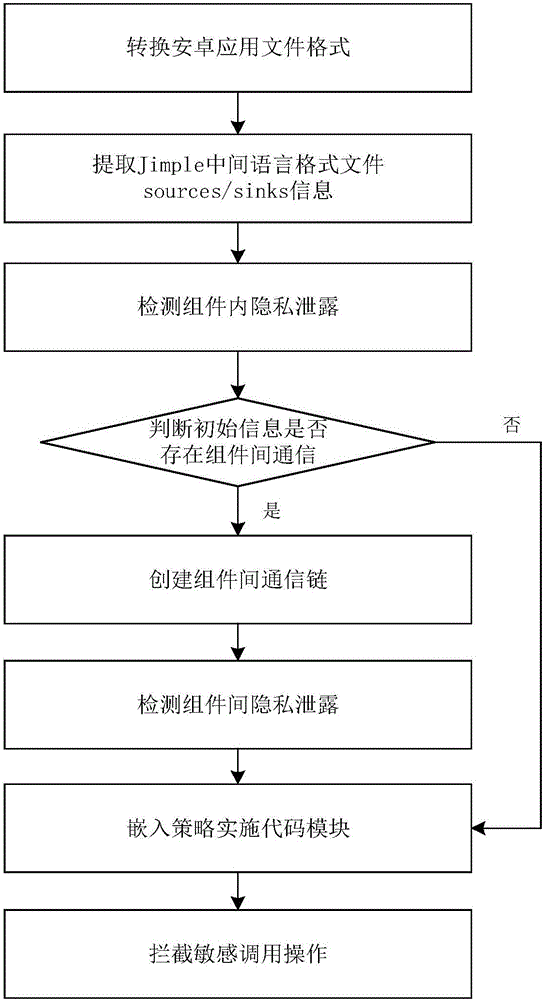
ActiveCN106203113ASimplify the difficulty of workOvercome the problem that multiple entry points are difficult to analyze and detectDigital data protectionPlatform integrity maintainanceControl flowCode module
The invention discloses a privacy disclosure monitoring method of an android application file. The privacy disclosure monitoring method includes: 1, converting a Dalvik byte code file in the android application file to generate a Jimple-format file; 2, parsing the Jimple-format file to generate control flow of a program, and performing privacy disclosure detection in components; 3, detecting Intent in the android file, and performing privacy disclosure detection among the components; 4, embedding a strategy implementation code module together with privacy disclosure detection results into the application program; 5, installing and running embedded application, and dynamically monitoring the application. By the privacy disclosure monitoring method, accuracy of user's privacy disclosure detection is improved, security defense of a system is enhanced, and risk of user's privacy disclosure is reduced to certain extend; the privacy disclosure monitoring method can be used for detection and protection of the android application file.
Owner:XIDIAN UNIV
Transport capacity elevating system based on driver online activity condition
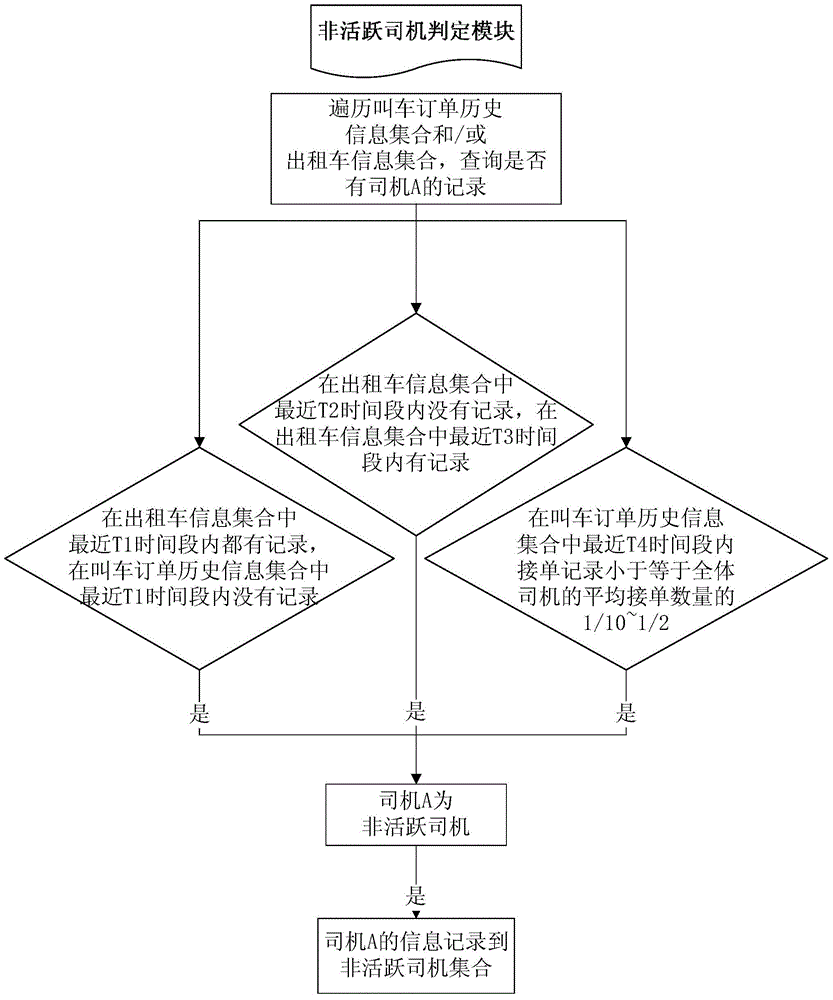
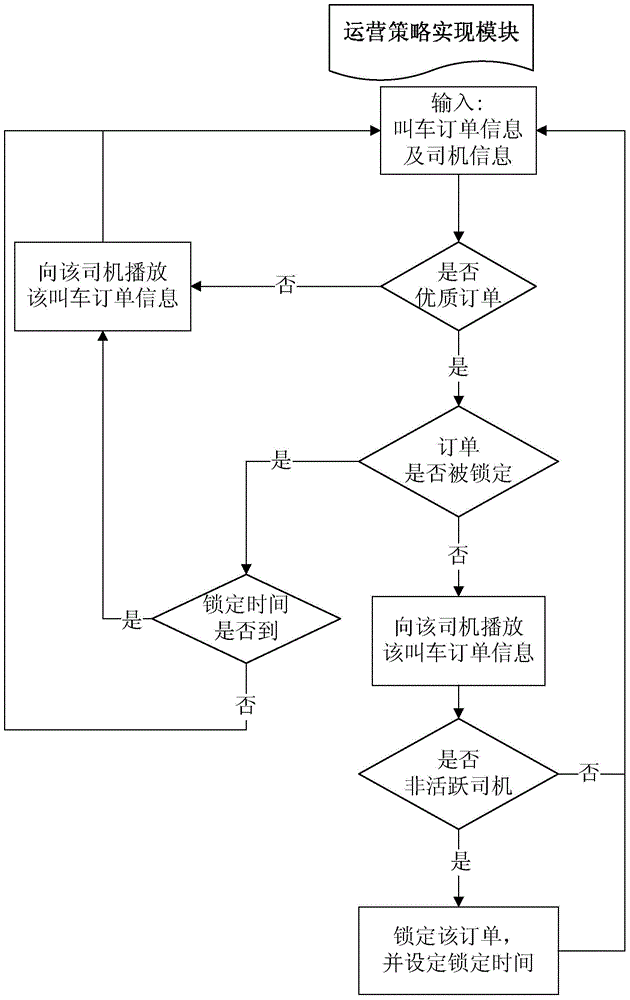
ActiveCN104157133AHigh-quality order pushImprove retentionRoad vehicles traffic controlResourcesOperational strategyOrder form
The invention relates to the technical field of car calling software, particularly relates to the technical field of the enhancement of operation driver activity, and particularly discloses a transport capacity elevating system based on a driver online activity condition. The system comprises a non-active driver judging module and an operation strategy implementation module. The non-active driver judging module is used for judging whether each driver is a non-active driver or not according to the online condition and / or order response condition of each drive during a period of time and recording the information of each non-active driver in a non-active driver set. The operation strategy implementation module is used for playing car calling order information for each online driver and locking high quality car calling order information for a period of time so as to help the non-active driver judging module to obtain the high quality car calling order obtained by the non-active driver in the non-active driver set. According to the system, the activity condition of a driver is judged, the order locking is implemented, thus a non-active driver group with easy loss is activated, and the improvement of the viscosity of a car calling system platform is assisted.
Owner:BEIJING DIDI INFINITY TECH & DEV
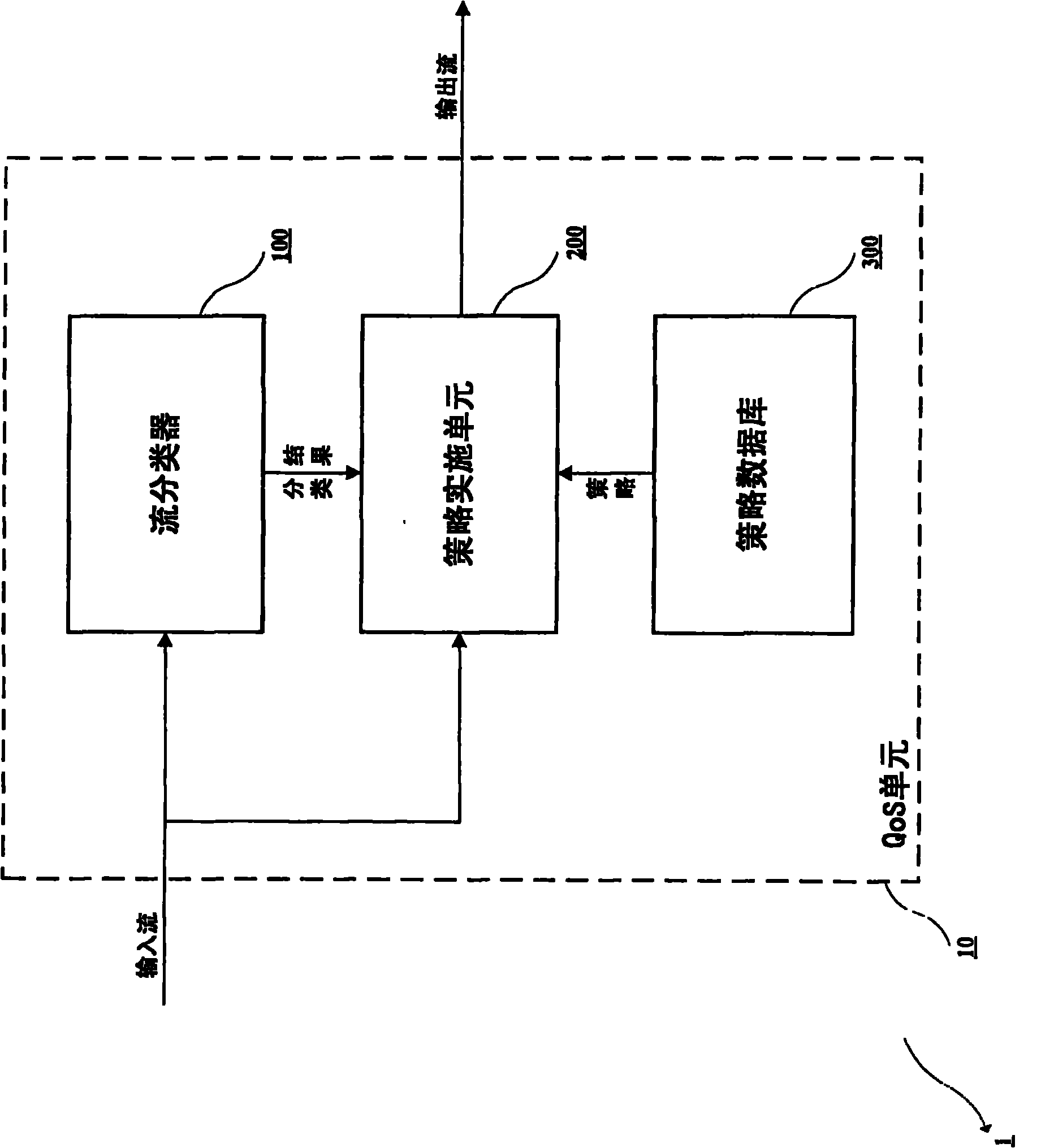
Terminal device, QoS implementation method and flow classifier thereof
The invention provides a terminal device, a QoS implementation method and a flow classifier thereof. The terminal device connected to a network comprises a QoS unit, a strategy database and a strategy implementation unit, wherein the QoS unit comprises the flow classifier which classifies a data flow to be transmitted through the network and outputs a classification result indicating the class of the data flow; the strategy database stores strategies corresponding to each class of one or more classes; and the strategy implementation unit receives the classification result from the flow classifier, searches the strategy database for finding out the strategy corresponding to the class indicating the data flow in the classification result, determines a processing operation to be carried out on the data flow at least based on the found strategy and carries out the determined processing operation on the data flow. The flow classifier can use flow feature information and flow context information. The QoS unit can also comprise a strategy control unit for receiving user input. The strategy implementation unit can use an overlay technology.
Owner:NEC (CHINA) CO LTD
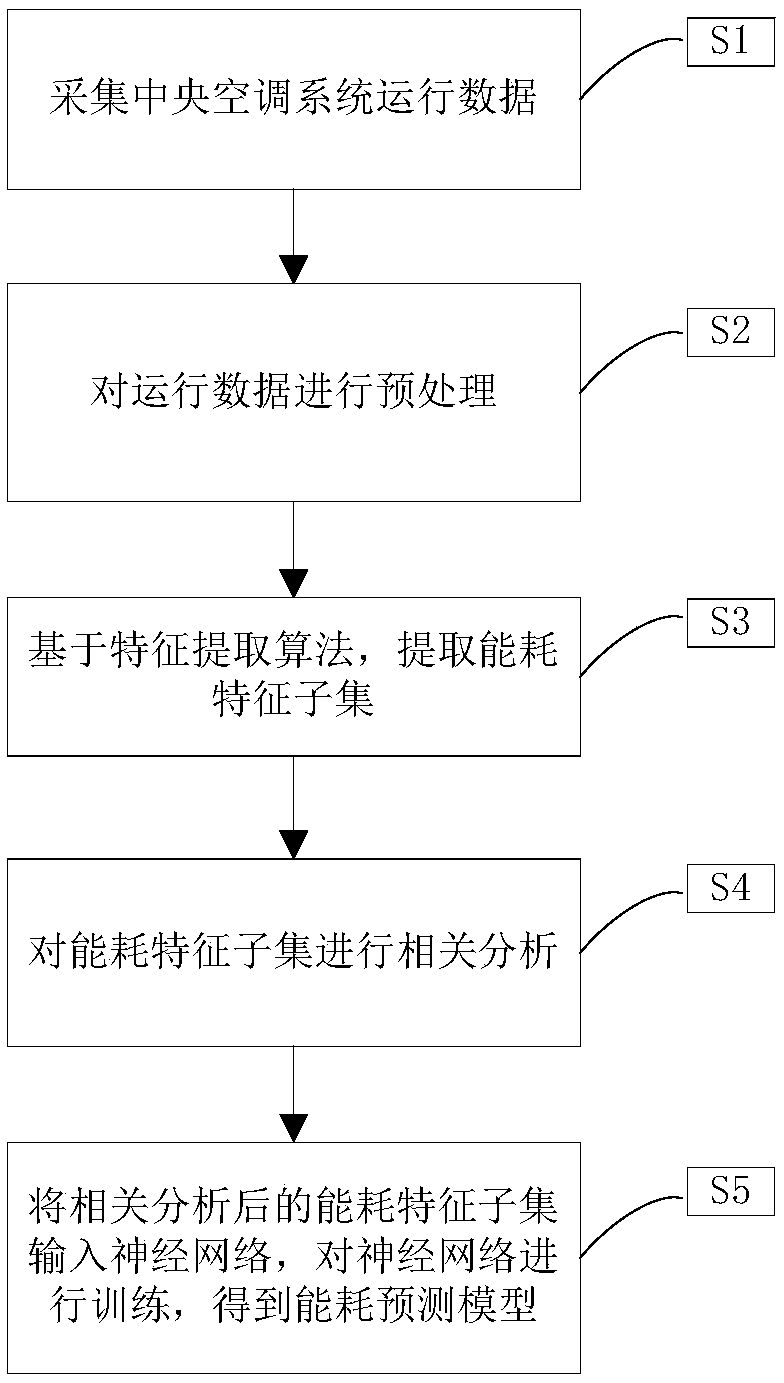
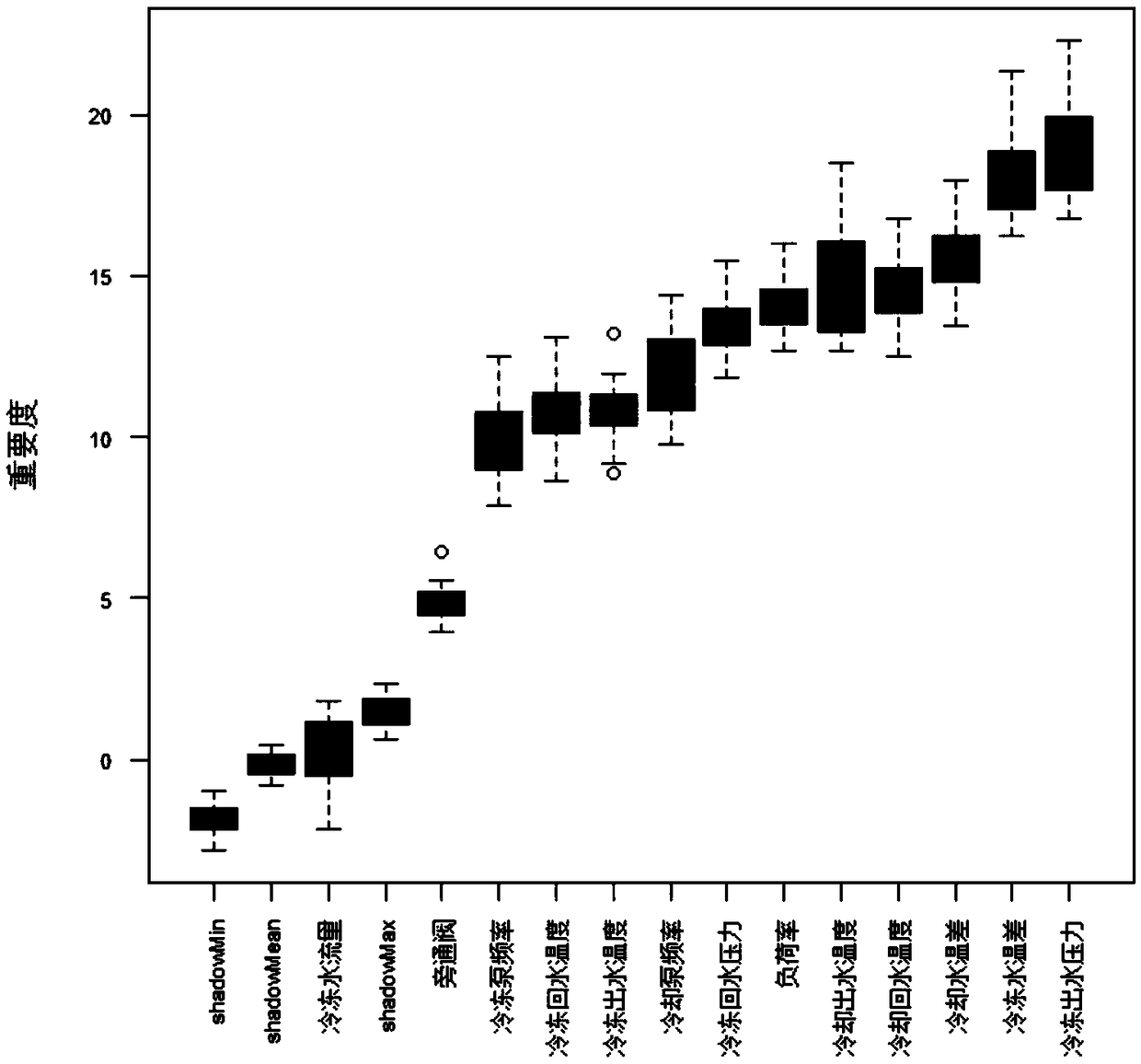
Central air conditioner energy consumption forecasting method based on operation data
InactiveCN108954680ASolve multicollinearityReduce redundancyMechanical apparatusSpace heating and ventilation safety systemsCorrelation coefficientFeature Dimension
The invention provides a central air conditioner energy consumption forecasting method based on operation data, and belongs to the field of central air conditioner modeling research. Aiming at the highly non-linear central air conditioner modeling problem which is difficult to solve through a traditional mechanism analysis method and a system identification method, central air conditioner energy consumption is forecasted through a method combining a Boruta feature selection method with a BP neural network. The operation data is subjected to energy consumption feature selection through the Boruta feature selection method at first, an energy consumption feature subset is obtained, the energy consumption feature dimension of the operation data is reduced, and then, the redundancy rate of theenergy consumption feature subset is decreased through a pearson correlation coefficient method; and finally, the energy consumption feature subset serves as input of a BP neural network energy consumption model, the central air conditioner system total power serves output of the BP neural network energy consumption model, and a training BP neural network energy consumption forecasting model is reliable and pervasive and has important significance to energy saving strategy implementation.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
Intelligent comparison-based online operation and maintenance method and system for secondary equipment of intelligent substation
ActiveCN107706889AReduce complexityReduce uncertaintyEmergency protective circuit arrangementsInformation technology support systemSmart substationSecurity Measure
The invention relates to an intelligent comparison-based online operation and maintenance method and a system for the secondary equipment of an intelligent substation, and provides the high-level application of a soft pressing plate in an intelligent substation. The application comprises the standardization design of the soft pressing plate and the intelligent alarm for the feeding and withdrawingabnormity of the soft pressing plate. Based on the realization of the above functions, the operation and maintenance complexity and the operation and maintenance uncertainty of the intelligent substation can be reduced. Meanwhile, the sequential control operation of a protection device is conducted, so that the one-click type sequential control of feeding and withdrawing protection and security measure isolation is realized. The feeding and withdrawing step of the protection device is immobilized, so that the risk of misoperation in the security measure process is effectively reduced. According to the above technical scheme of the invention, the pilot operation can be carried out in a certain 220 kV intelligent substation, and the running condition is good. Meanwhile, the intelligent level of the substation is improved to a great extent. The configuration of an interval intelligent device during the long-term expansion process is fully considered, and the concept of a replacement device is proposed. The power failure time in the long-term reconstruction and extension process is shortened. Moreover, the modeling is carried out based on the IEC61850 standard, and a theoretical foundation is laid for later strategy implementation.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
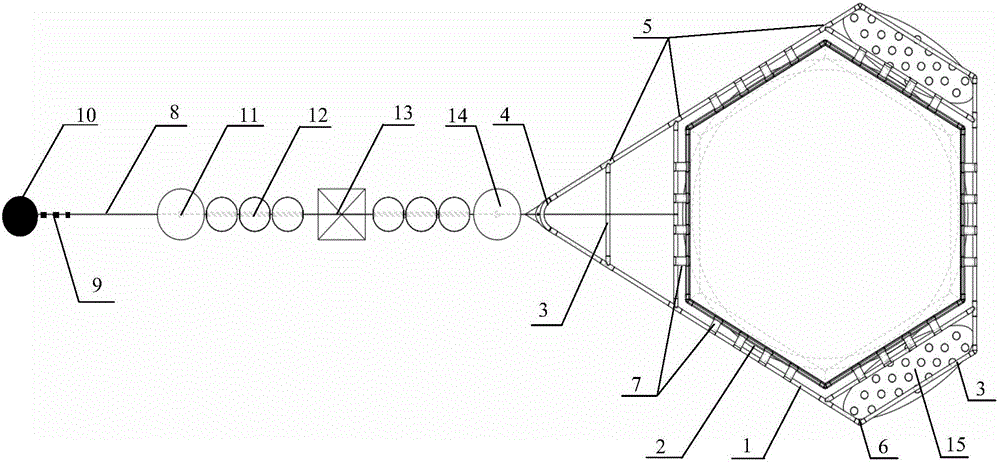
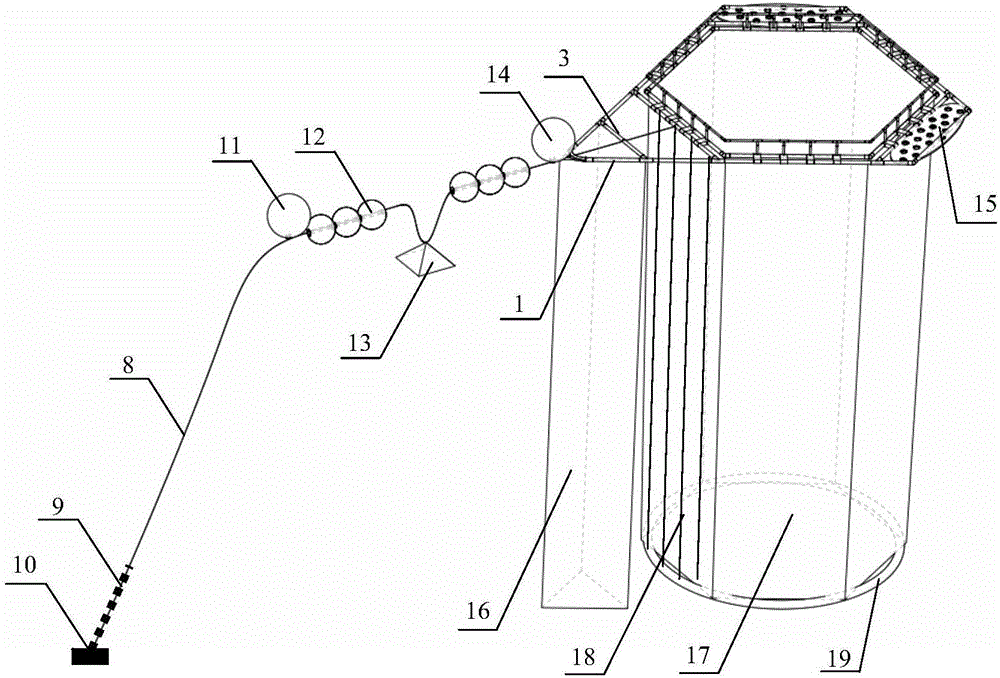
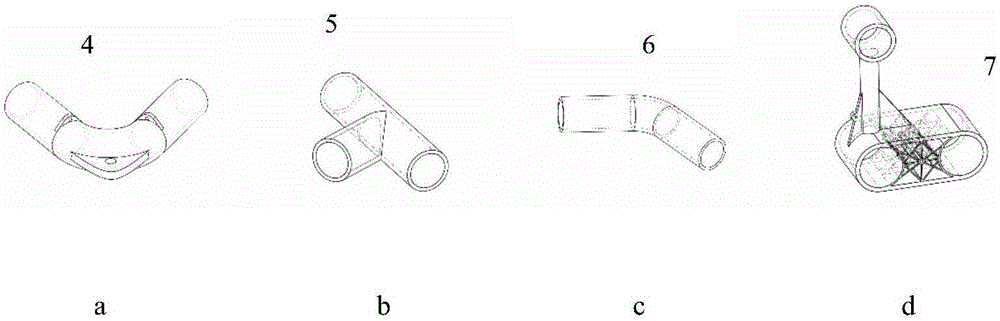
Diamond-shaped wave-resistant and storm-resistant deep-water culture net cage
ActiveCN106804501AIncrease the areaSmall range of motionClimate change adaptationPisciculture and aquariaMaricultureEngineering
A diamond-shaped wave-resistant and storm-resistant deep-water culture net cage is characterized by comprising a net cage frame system which is composed of an outer floating frame, an inner floating frame, a reinforcement pipe, a 60-degree elbow, 60-120-degree lateral tees, 120-degree elbows and floating frame connecting pieces, a mooring system which is composed of a mooring rope, an anchor chain, an anchorage, a front-end buffer floating ball, middle floating balls, a buffer counter weight and a rear-end buffer floating ball, a net cage flow reduction stable structure which is composed of wave stabilizing plates and front-end flow reduction nettings, and a net bag system which is composed of nettings, ground ropes and a bottom frame. The floating frames are of a diamond-shaped structure, and a multi-section buffer single-point mooring system is adopted by the mooring system, through the diamond-shaped frame structure and the multi-section buffer single point mooring system of a net cage, the top of the net cage directly faces wave currents under the action of the wave currents, and a wave breaking effect is achieved, so that the acting force of the waves to the net cage is reduced, and the Chinese Blue granary strategy implementation and the mariculture development tendency from inshore to deep sea are promoted.
Owner:山东深海冷水团海洋开发有限公司
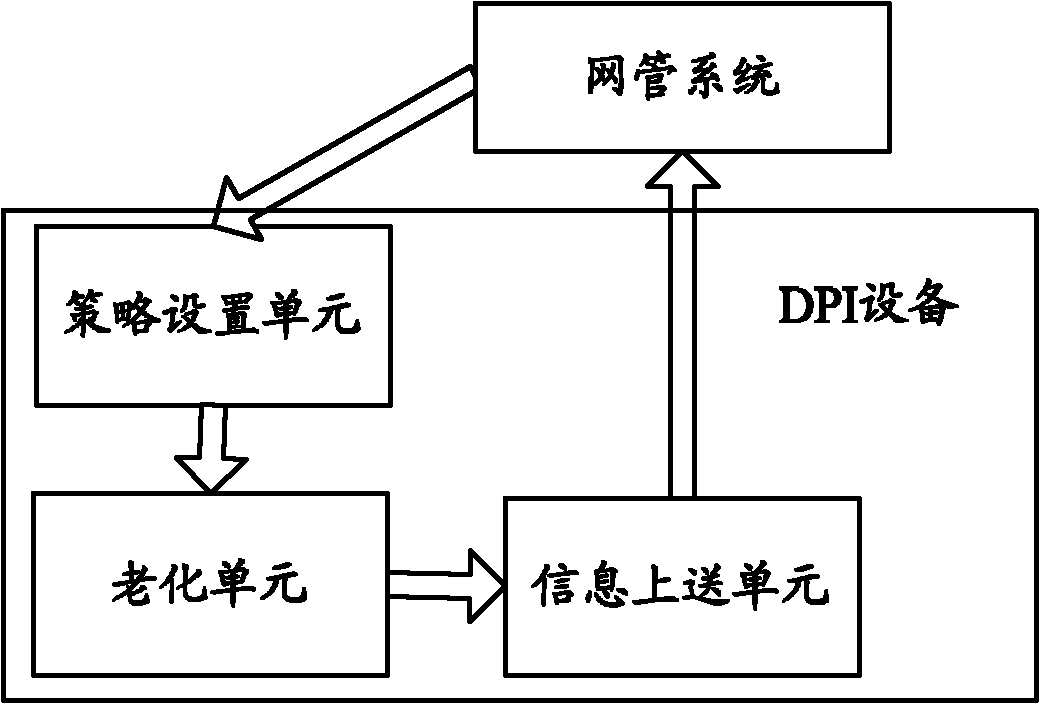
Alarm treating method and DPI (Deep Packet Inspection) device
InactiveCN102035685AGuaranteed real-timeReduce steps to handle alertsData switching networksData treatmentData transmission
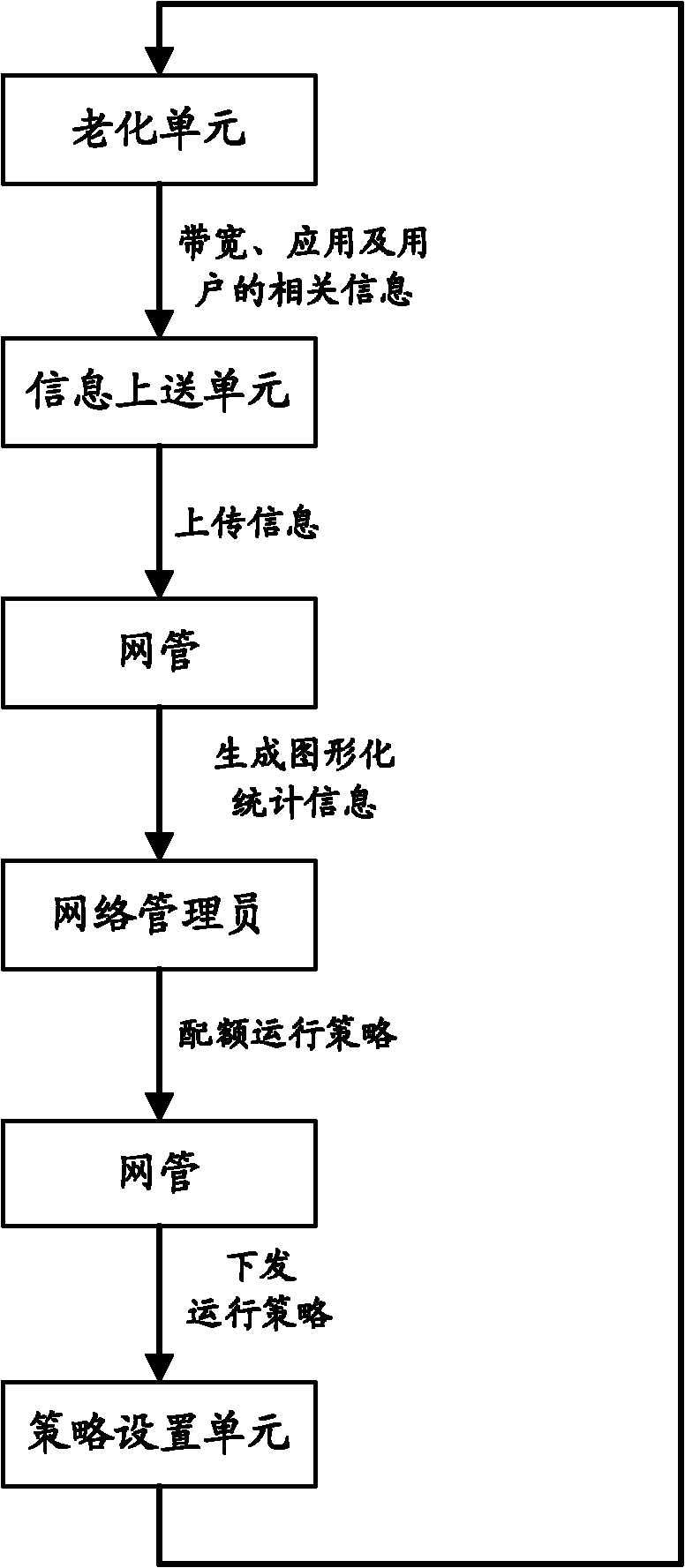
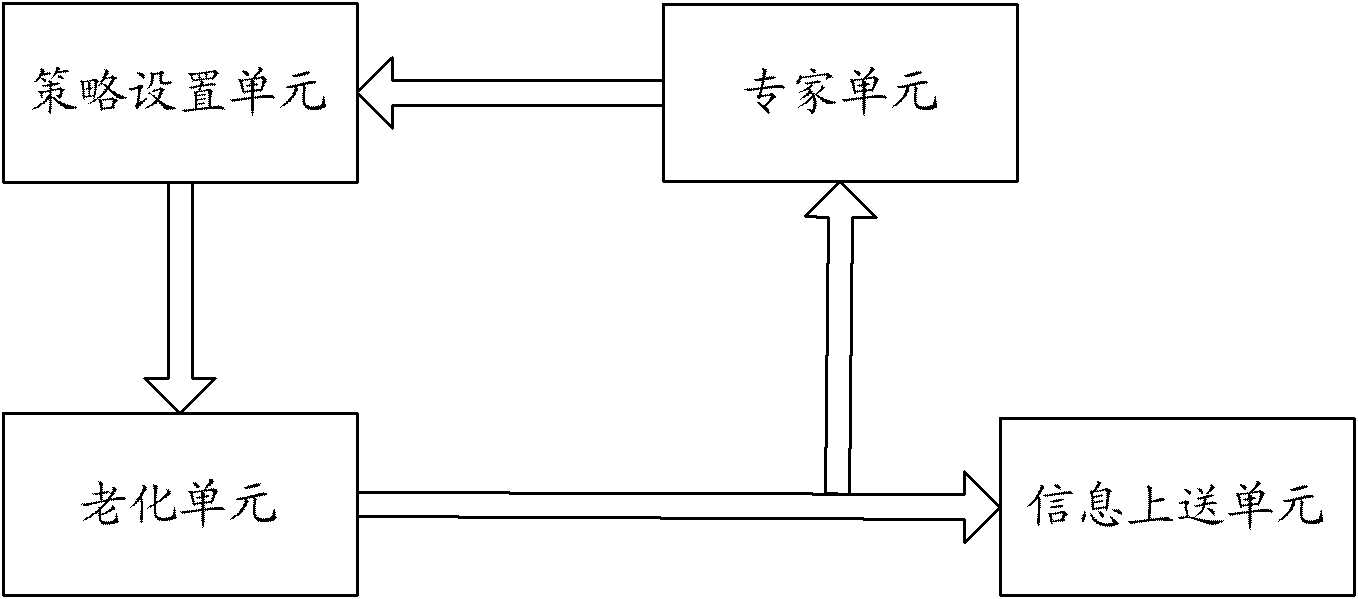
The invention discloses a DPI (Deep Packet Inspection) device for treating alarms, comprising an ageing unit, a strategy setting unit and an expert unit, wherein the ageing unit is used for generating real-time statistic information of the current network and transmitting the generated real-time statistic information to the expert unit; the expert unit is used for analyzing the real-time statistic information transmitted by the ageing unit, generating an alarm when the real-time statistic information is matched with the current configured alarm rule and transmitting an alarm promoting message to the strategy setting unit; and the strategy setting unit is used for regulating the operation strategy of the current network according to the alarm promoting message transmitted by the expert unit. The invention also discloses an alarm treating method. The invention reduces the data transmission quantity of an alarm treating process, shortens an alarm treating period, ensures the real-time performance of data treatment, alarm generation and corresponding strategy implementation, increases the work efficiency of the DPI device and achieves better network managing and controlling effect.
Owner:ZTE CORP
Method and device for deleting strategy session
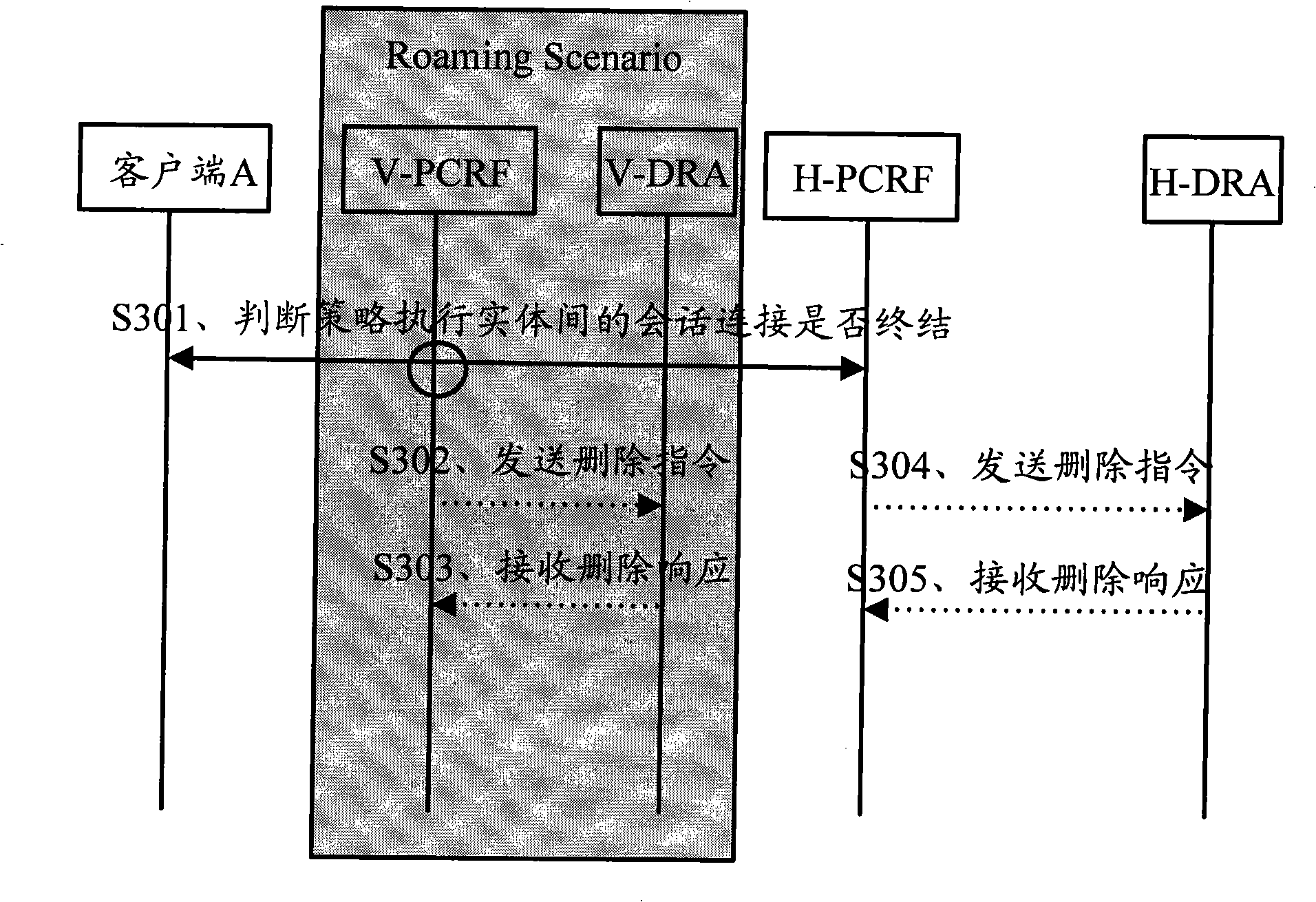
InactiveCN101541100AReduce adverse effectsImprove transmission qualityWireless network protocolsTransmissionQuality of serviceKnowledge management
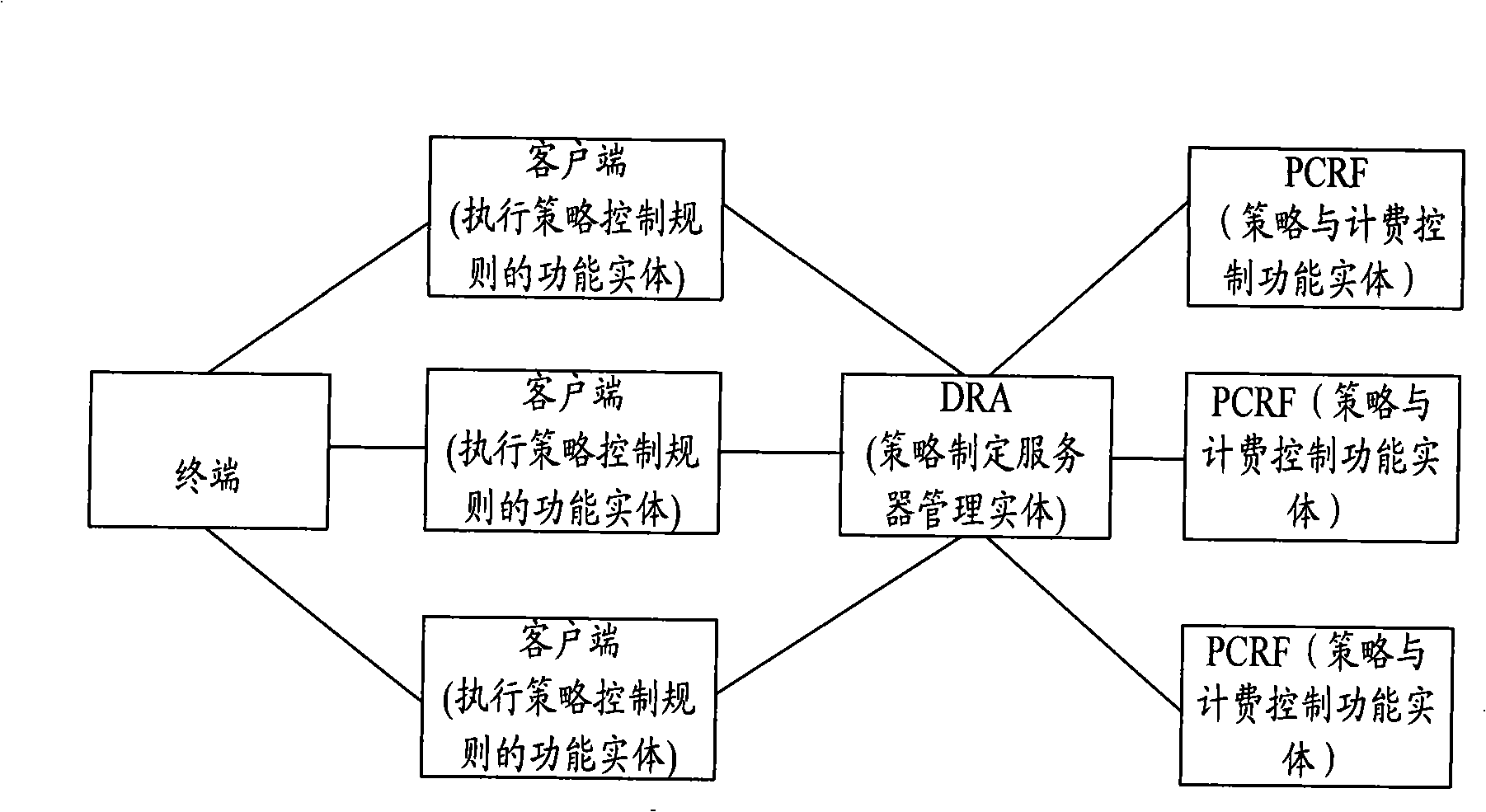
The embodiment of the invention discloses a method and a device for deleting strategy session. The method comprises the following steps: judging whether strategy session connection between strategy implementation entities is ended or not; sending a strategy session information instruction corresponding to the strategy session connection deleting to the Diameter domain routing agent DRA when the strategy session connection is ended; and receiving the response that the DRA deletes the strategy session information. By the invention, the DRA can delete the useless strategy session information and connection relation information in time so as to avoid adverse influence on normal strategy connection by useless redundant information and improve the communication service quality.
Owner:HUAWEI TECH CO LTD
Data center network flow balancing method and device oriented to software definition
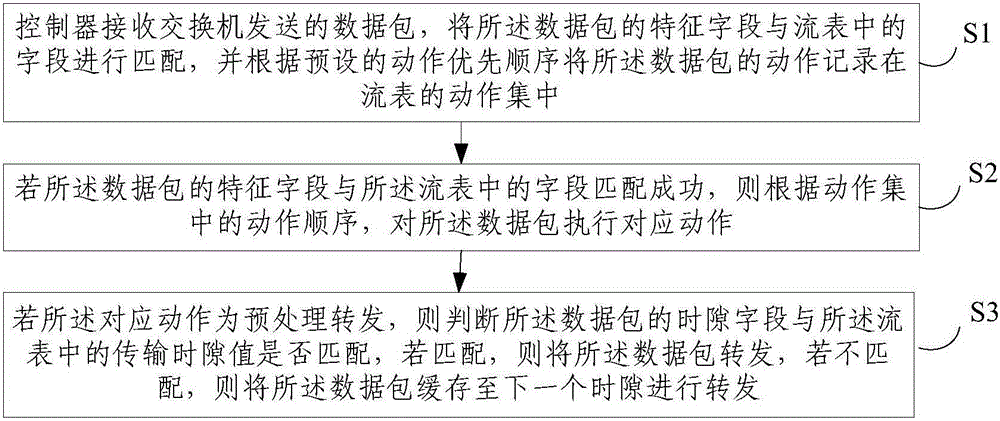
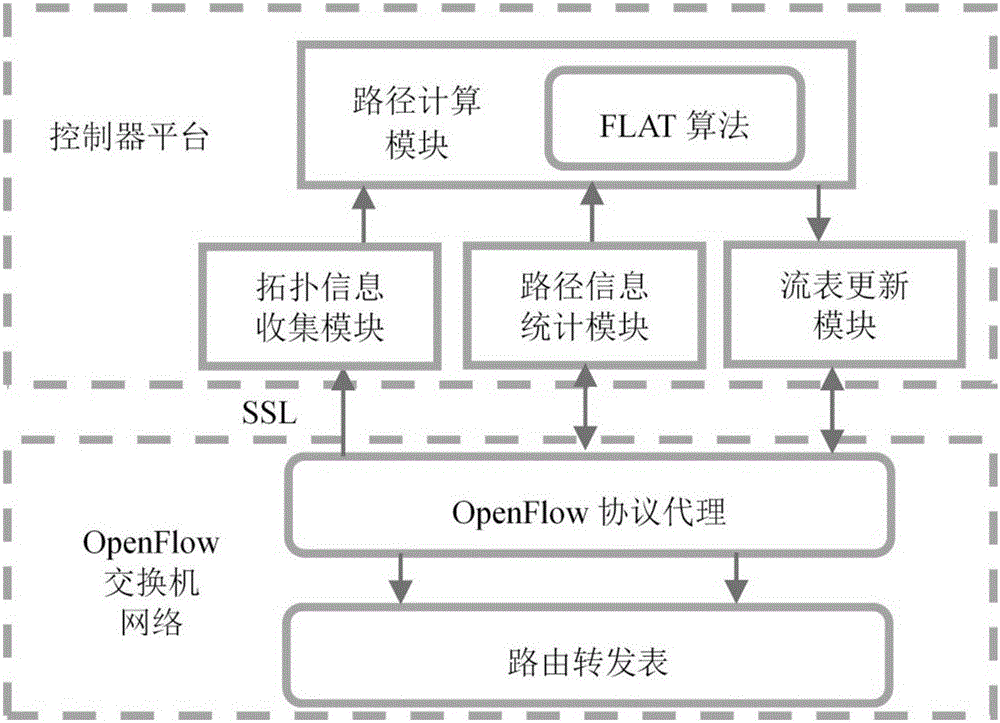
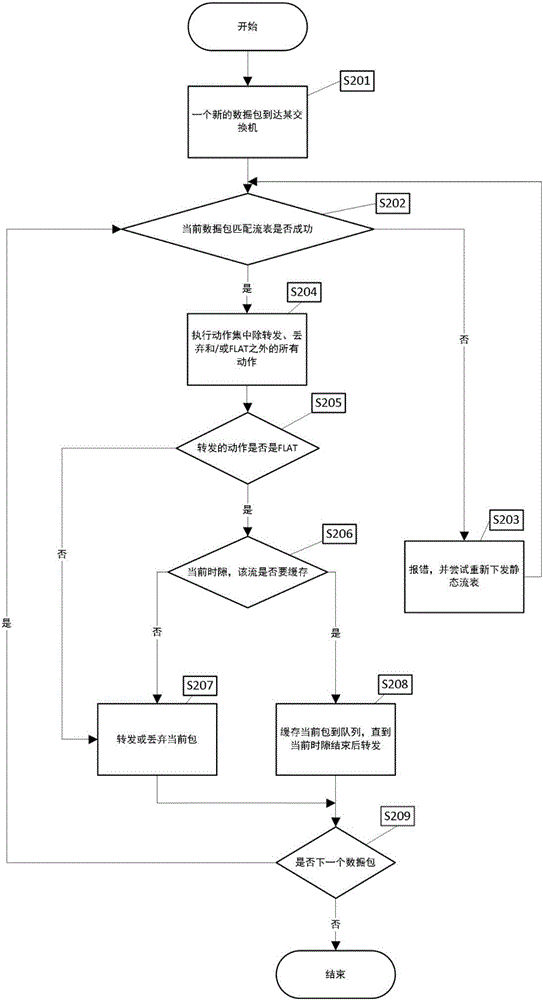
ActiveCN105915467AAvoid disorderImprove scalabilityData switching networksExtensibilityTraffic capacity
The invention discloses a data center network flow balancing method and a data center network flow balancing device oriented to software definition. The data center network flow balancing method comprises the steps that: a controller receives a data packet transmitted by a switch, matches feature fields of the data packet with fields in a flow table, and records actions of the data packet in an action set of the flow table according to a preset action priority; a corresponding operation is carried out on the data packet according to the action sequence in the action set if the feature fields of the data packet are successfully matched with the fields in the flow table; and whether a time slot field of the data packet is matched with a transmission time slot value in the flow table is judged if the corresponding operation is pretreatment forwarding, if so, then the data packet is forwarded, and if not, the data packet is cached to a next time slot for forwarding. The data center network flow balancing method and the data center network flow balancing device simplify deployment, enhance network expandability, and solve the problems of data flow packet loss during the strategy implementation process and disorder of data packets which may occur at a receiving end.
Owner:TSINGHUA UNIV +1
Application-oriented dynamic resource allocation method for IaaS (Infrastructure As A Service) layer
ActiveCN104679595AImplement dynamic resource allocationMeet multiple management goalsResource allocationSpecial data processing applicationsDynamic resourceResource utilization
The invention discloses an application-oriented dynamic resource allocation method for an IaaS (Infrastructure As A Service) layer. The method comprises the following steps: generating a message for triggering resource allocation by virtue of a system or a user; matching the generated message, and searching a strategy database for a matched strategy; for the matched strategy, communicating with resource monitoring service according to a constraint condition self-defined by the user, and judging whether the constraint condition is met or not; for the strategy consistent with the constraint condition, communicating with the resource monitoring service and strategy implementation service according to a behavior self-defined by the user, and implementing the specific resource allocation strategy. According to the method, the user can formulate a corresponding dynamic resource allocation strategy according to characteristics of an application, so that the utilization rate of resources is increased, and the multi-target management requirements of the user can be met.
Owner:山东中创软件商用中间件股份有限公司
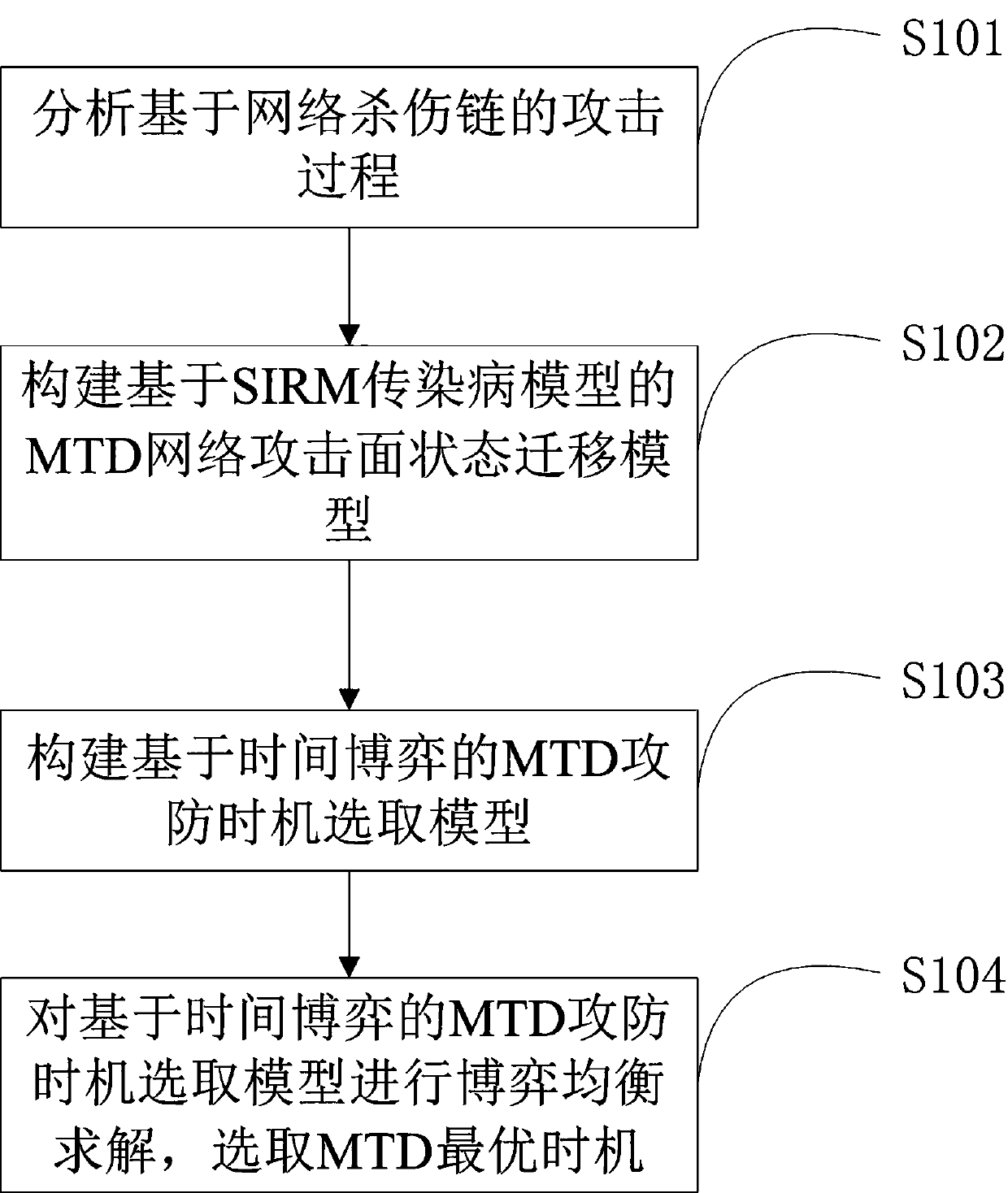
Moving target defense opportunity selection method and device based on covert confrontation
ActiveCN111385288APractical guidance is of good valueGame equilibrium solutionData switching networksQuality of serviceAttack
The invention belongs to the field of network security, and particularly relates to a moving target defense opportunity selection method and a moving target defense opportunity selection device basedon covert confrontation. The moving target defense opportunity selection method comprises the steps of: analyzing an attack process based on a cyber kill chain; constructing an MTD network attack surface state migration model based on a SIRM infectious disease model; constructing an MTD attack and defense opportunity selection model based on time game; and performing game equilibrium solution on the MTD attack and defense opportunity selection model based on the time game, and selecting the optimal opportunity of the MTD. According to the moving target defense opportunity selection method, theoptimal equilibrium point of strategy implementation opportunities of an attacker and a defender is analyzed in a time game theory framework in accordance with a real network attack and defense scene, so that the MTD implementation opportunity is guided for the defender, and the SDN service quality and MTD decision income are balanced.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Comprehensive electricity consumption measurement and control management terminal
InactiveCN105652754AChange wasteAvoid wastingProgramme controlComputer controlLonWorksStatistical analysis
The invention discloses a comprehensive electricity consumption measurement and control management terminal and belongs to the technical field of electric use safety and energy conservation. The terminal comprises a microcontrol unit and an illumination intensity acquisition module, a human body induction module, an electric quantity acquisition module, a data storage module, a real-time clock module, a Lonworks intelligent receiving and transmitting device, an RS485 communication interface and a man-machine interaction interface platform which are all connected with the microcontrol unit. By means of the terminal, energy consumption conditions of electric appliances in a building can be accurately monitored, statistical analysis of the energy consumption conditions and energy consumption charging are facilitated, the terminal has various energy-saving control modes and can be conveniently set, bases are provided for flexible control strategy implementation of a comprehensive energy management system, and the effects of reasonably using energy and reducing energy consumption are achieved. Consumption reduction indexes can be sent through the system in the electricity use peak hours, the set temperature is automatically adjusted through a temperature controller, and the aim of reducing consumption is achieved. The terminal can be widely applied to energy-saving systems of an air conditioner, an illumination device and other electric appliances of the building.
Owner:江苏联宏智慧能源股份有限公司
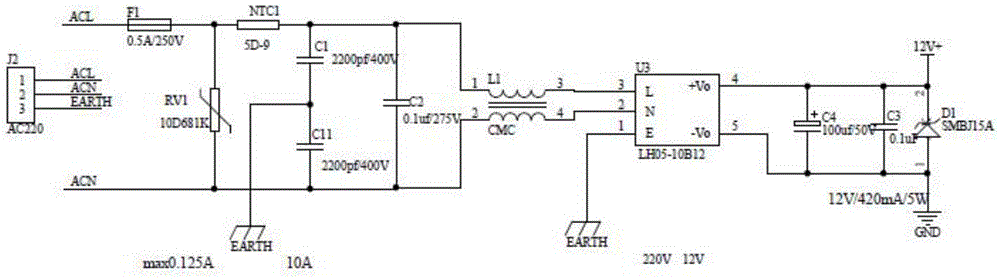
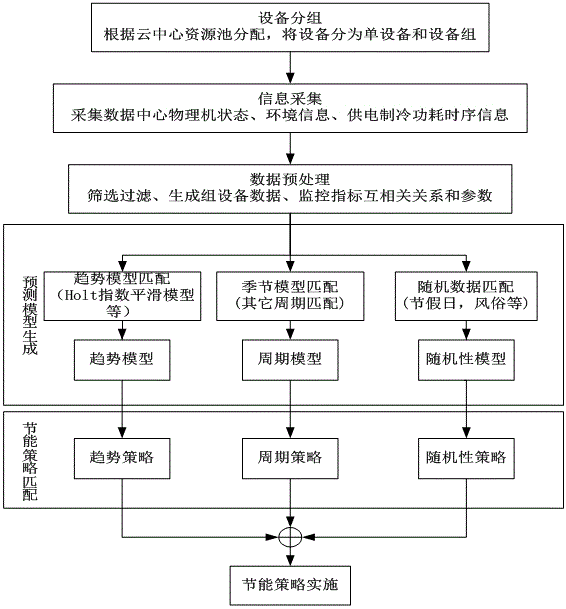
Data center energy saving strategy implementation method based on time series analysis
InactiveCN105868073AReduce energy consumptionEffective energy saving strategyHardware monitoringPower supply for data processingAnalysis dataData center
The invention particularly relates to a data center energy saving strategy implementation method based on time series analysis. The data center energy saving strategy implementation method based on time series analysis comprises the steps that firstly, equipment group configuration is conducted, and data collection is conducted through an information collection module; secondly, the collected data is stored in a database and then preprocessed; thirdly, time series analysis is conducted on the preprocessed data to obtain a predicted model; lastly, energy saving strategy matching is conducted according to the predicted model, and a matched energy saving strategy is selected and then implemented by a strategy implementation module. According to the data center energy saving strategy implementation method based on time series analysis, the self-correlation relation and mutual-correlation relation of the data in time dimension are analyzed through a time series analysis method to obtain the tendency, period and random variation laws of the data, model matching is conducted to generate the more effective data center energy saving strategy, energy saving control is conducted on a data center from multiple directions and multiple dimensions in the time domain, and therefore the data center energy consumption is effectively reduced.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
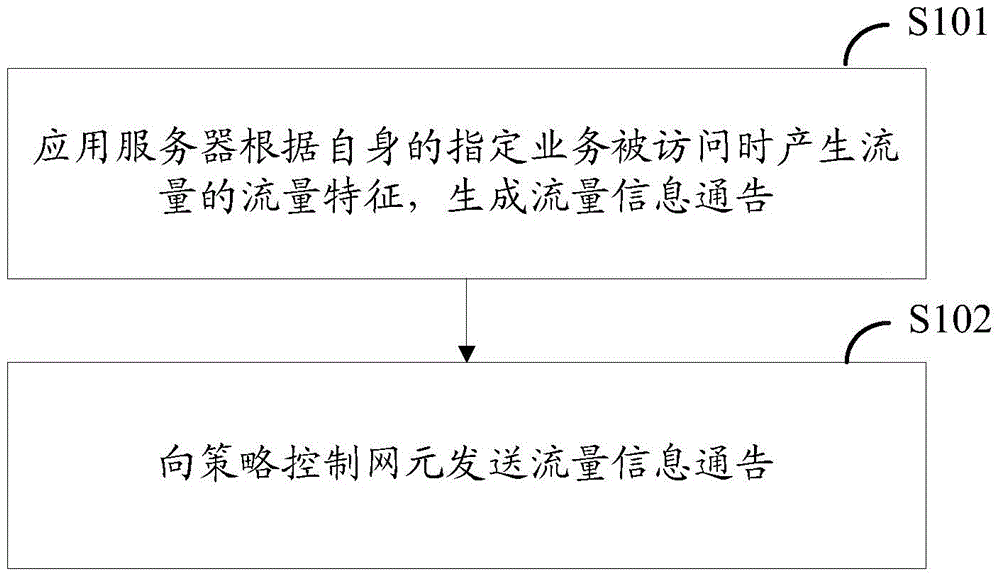
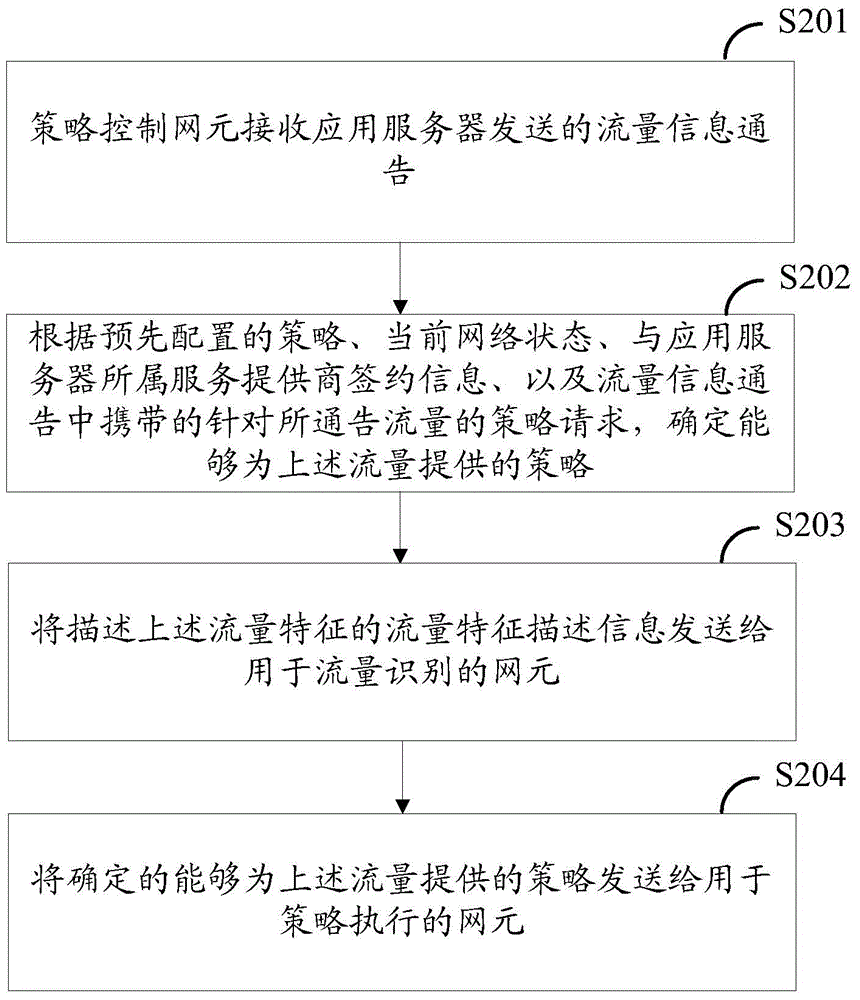
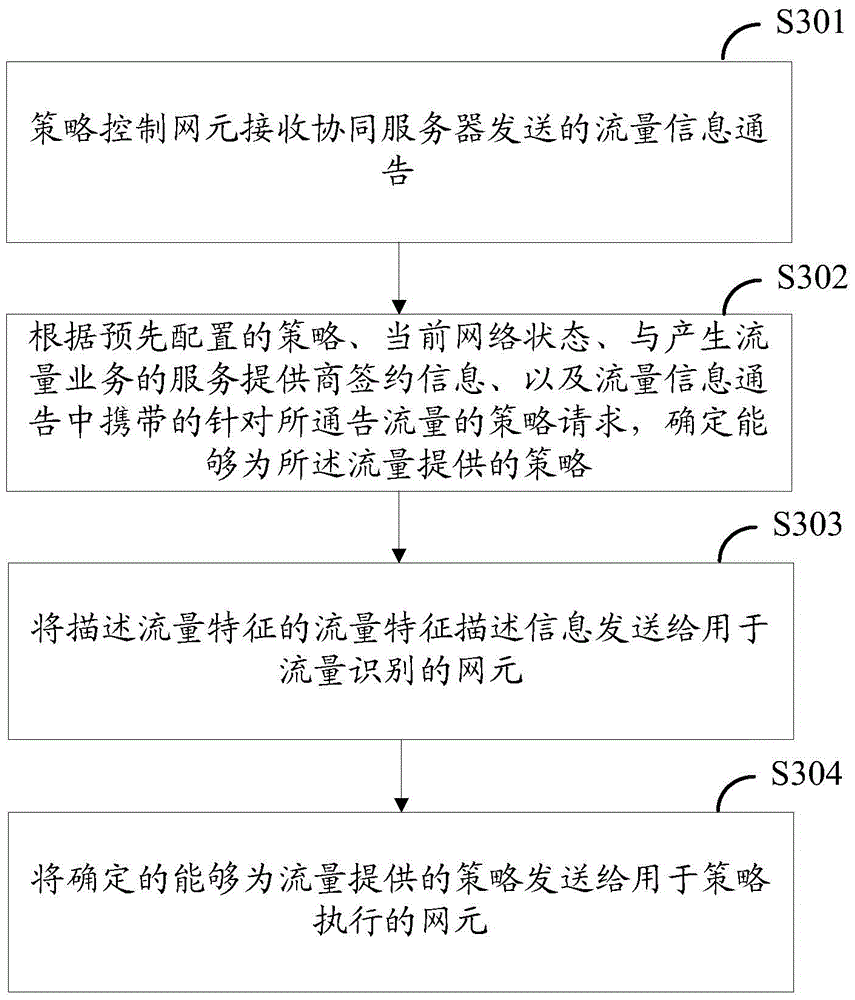
Traffic identification method, application server, and network element equipment
ActiveCN105099803AThe recognition granularity is flexible and accurateData switching networksTraffic characteristicControl network
The embodiment of the invention provides a traffic identification method, an application server, and network element equipment. The application server generates a traffic information notification according to the traffic characteristic of the traffic generated during the access to designated business; the traffic information notification is sent to a strategy control network element; the strategy control network element determines the strategy provided for the notified traffic according to the pre-configured strategy, the current network state, subscription information with a service provider which the application server belongs to, and a strategy request for the notified traffic carried by the traffic information notification after receiving the traffic information notification; and the determined related information is sent to the network element used for traffic identification and strategy implementation. According to the traffic identification method, the application server, and the network element equipment, the identification of the traffic is more flexible and accurate. The invention relates to the field of mobile communication.
Owner:CHINA MOBILE COMM GRP CO LTD
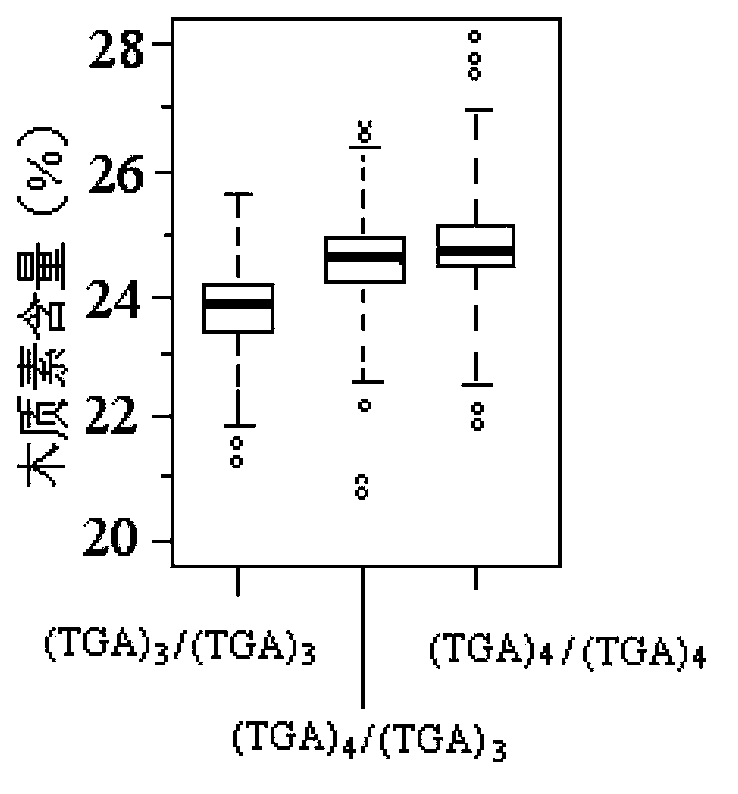
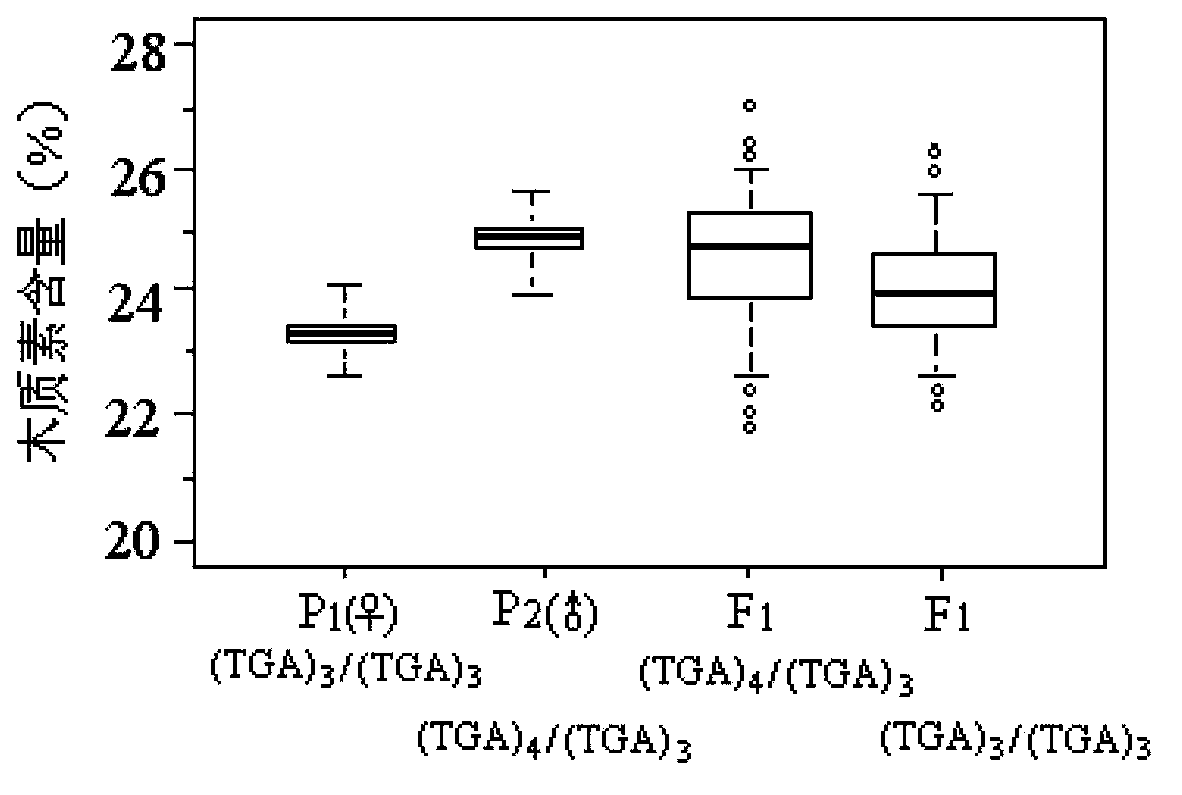
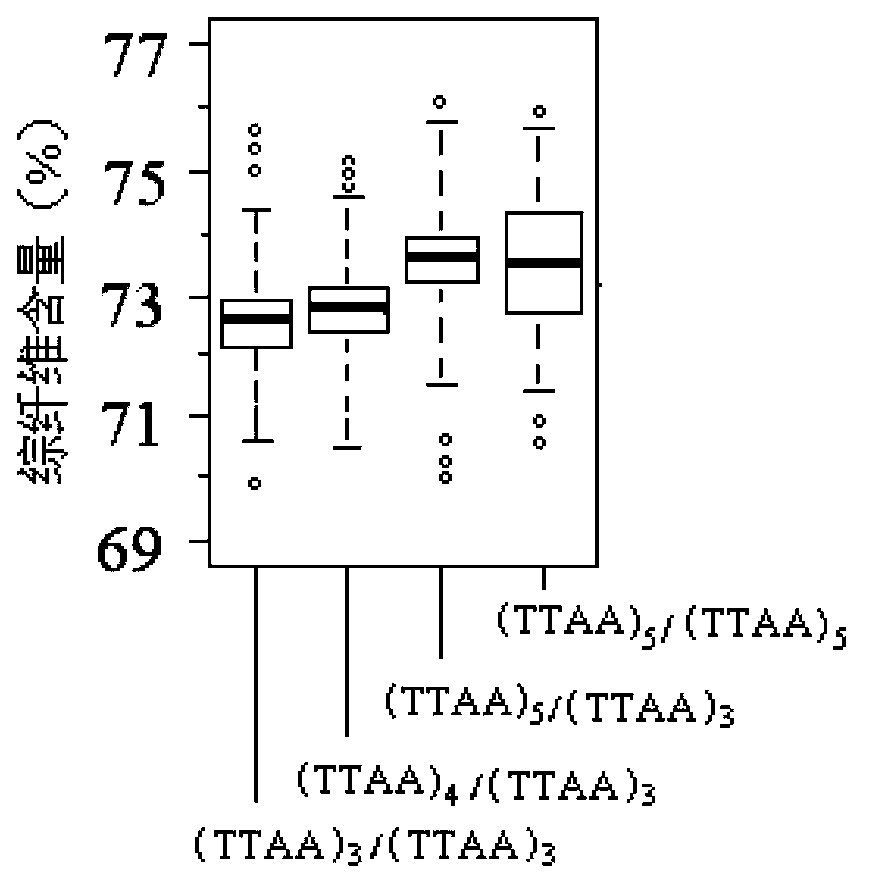
Functional SSR labels obviously related with wood quality characters in populus CesAs gene, and applications and kit thereof
InactiveCN104293774AShorten the breeding cycleMicrobiological testing/measurementPlant genotype modificationGermplasmExon
Functional SSR labels obviously related with wood quality characters in a populus CesAs gene, and applications and a kit thereof are disclosed. The functional SSR labels comprise 7A-SSR2 and 7B-SSR1. The 7A-SSR2 is in the exon 3 zone of populus CesA7-A and is (TGA)n. The 7B-SSR1 is in the intron 4 zone of populus CesA7-B and is (TTAA)m. The determined functional SSR labels provide new technical means for early-period screening of breeds with high-quality and for shortening the breeding cycle of forest trees, provide genetic evidences for molecular research for improvement of wood quality characters, and have important significance for improving development of forest genetic breeding engineering in China and for forest breeding strategy implementation at present.
Owner:BEIJING FORESTRY UNIVERSITY
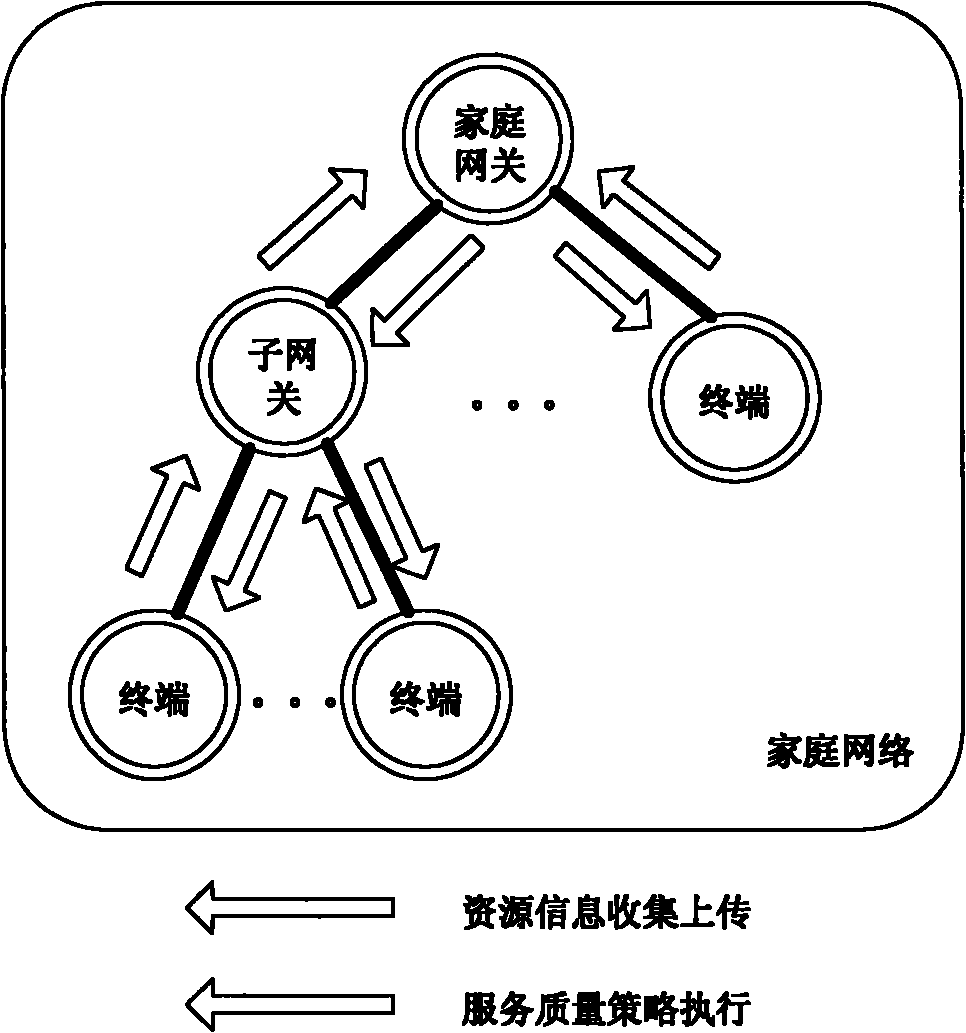
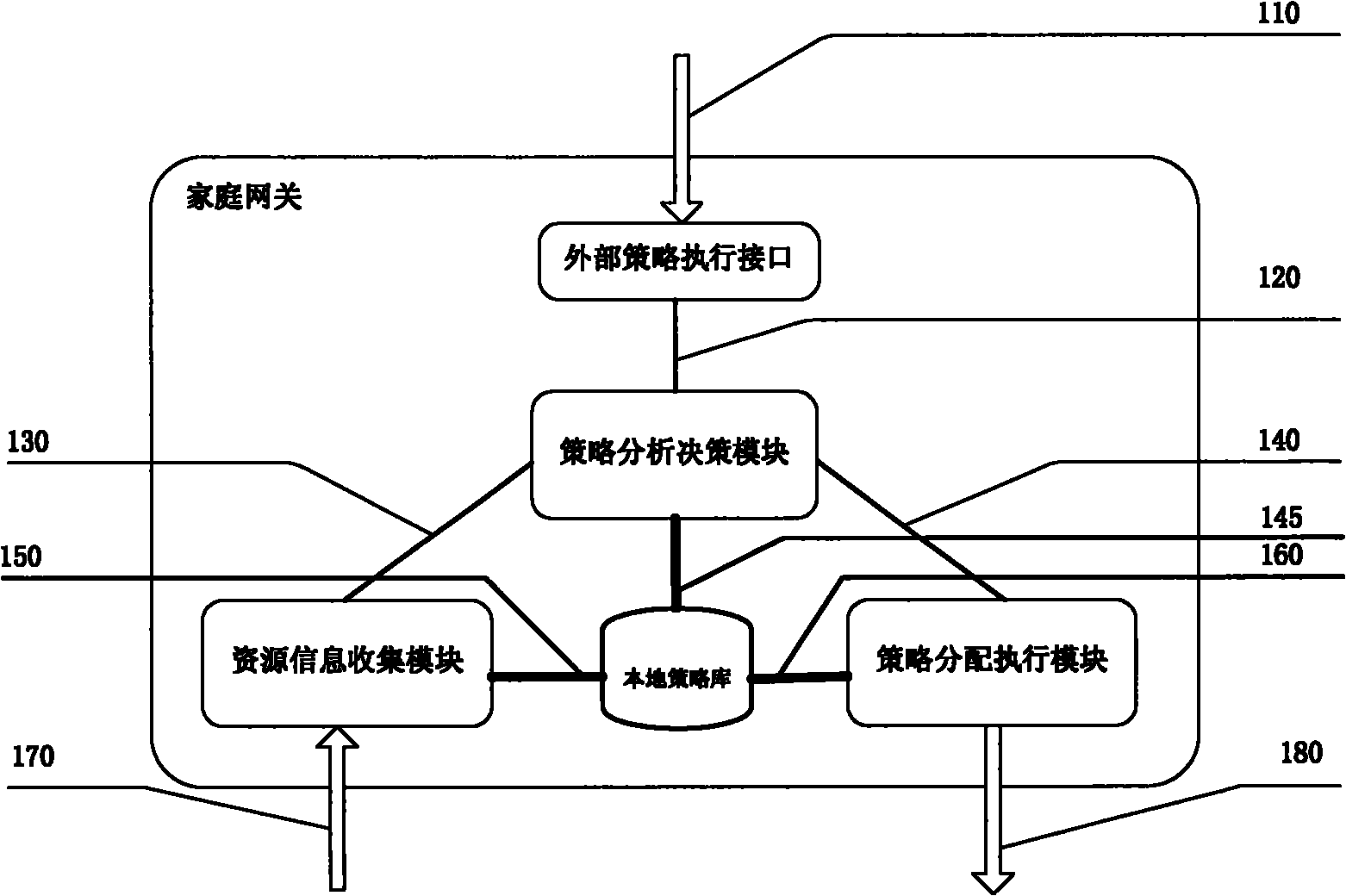
Dynamic service quality strategy method and system of home network
ActiveCN101997746AEffective distributionDynamic Policy Expansion CapabilityData switching by path configurationNetwork connectionsInformation strategiesQuality of service
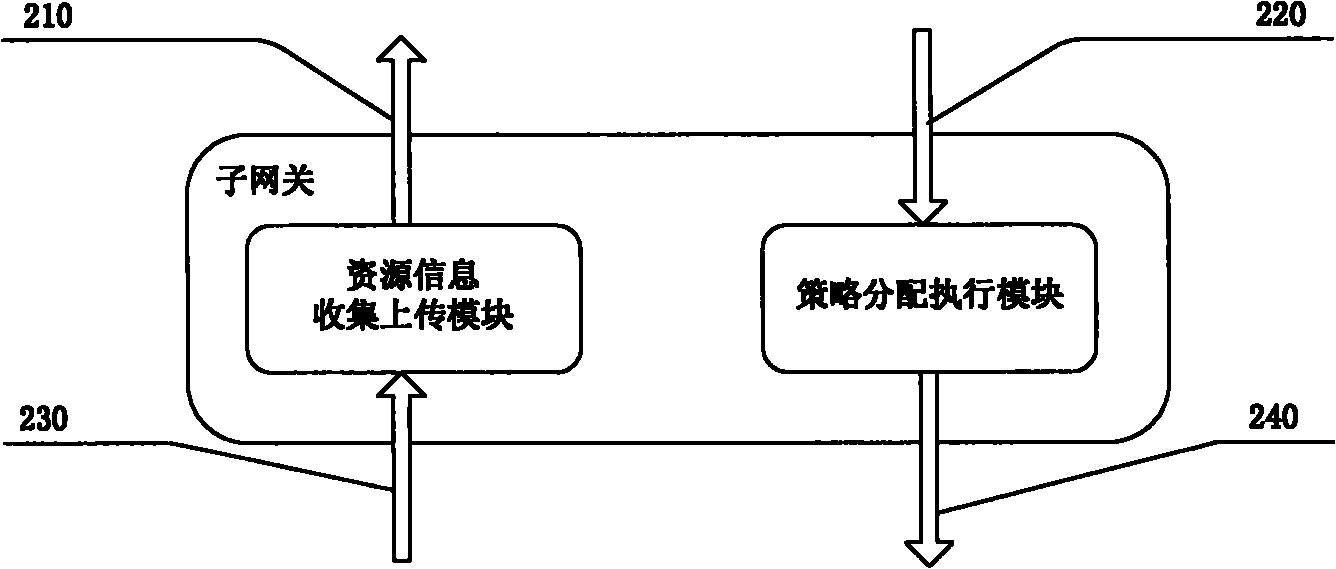
The invention provides a dynamic service quality strategy system of a home network. The strategy system is a service quality strategy system which comprises a home gateway, a sub-gateway and a terminal, wherein the home gateway comprises an external strategy implementation interface, a resource information acquisition module, a strategy analysis and decision module, a strategy distribution and implementation module and a local strategy library, wherein the external strategy implementation interface is used for externally providing a uniform external service quality strategy implementation interface which acquires a service quality strategy of an external network; the resource information acquisition module is used for acquiring resource information reported by the sub-gateway and the terminal; the strategy analysis and decision module is used for generating new local service quality strategy map by using the resource information and the service quality strategy of the external network and saving the new local service quality strategy map in a local strategy library; the strategy distribution and implementation module is used for distributing and allocating a generated global service quality strategy to the sub-gateway and the terminal managed by the home gateway; and the local strategy library is used for storing the global service quality information strategy of the home network and dynamic variation of the home network resource information. Through the method and the system, dynamic generation and implementation of an internal service quality strategy of the home network are realized.
Owner:ZHENGZHOU SEANET TECH CO LTD
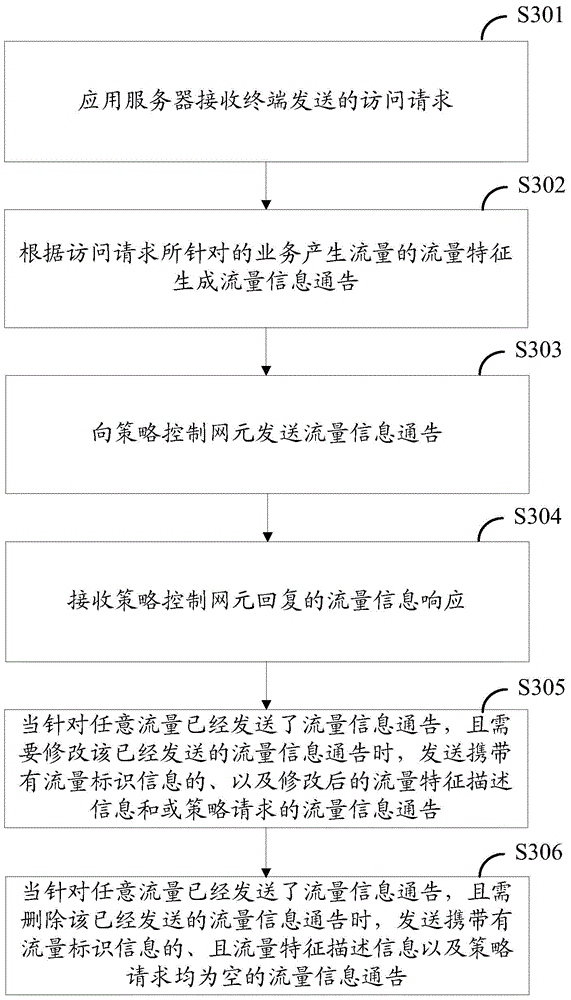
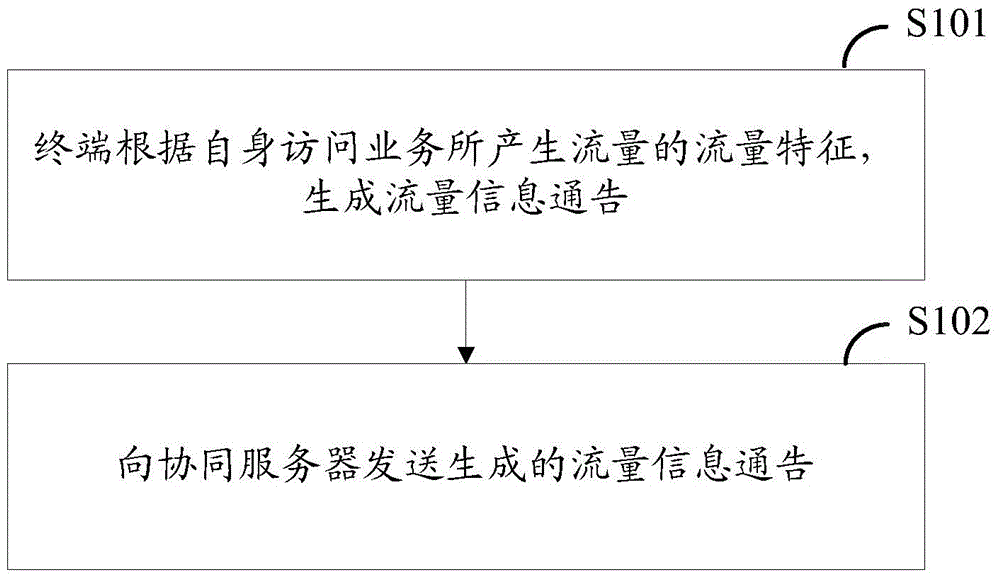
Traffic identification method, terminal, and network element equipment
ActiveCN105099802AThe recognition granularity is flexible and accurateData switching networksTraffic characteristicTraffic capacity
The embodiment of the invention provides a traffic identification method, a terminal, and network element equipment. A terminal side generates a traffic information notification according to the traffic characteristic of the traffic generated during the access to business; the traffic information notification is sent to a cooperative server; the cooperative server employs a communication protocol supported by a designated network element to send the traffic information notification to the designated network element via protocol conversion after receiving the traffic information notification sent by a plurality of terminals; the designated network element determines the strategy provided for the traffic according to the pre-configured strategy, the current network state, subscription information with a service provider which generates traffic business, and a strategy request for the notified traffic carried by the traffic information notification; and traffic identification and strategy implementation are realized according to the determined strategy. According to the traffic identification method, the terminal, and the network element equipment, the identification of the traffic is more flexible and accurate. The invention relates to the field of mobile communication.
Owner:CHINA MOBILE COMM GRP CO LTD
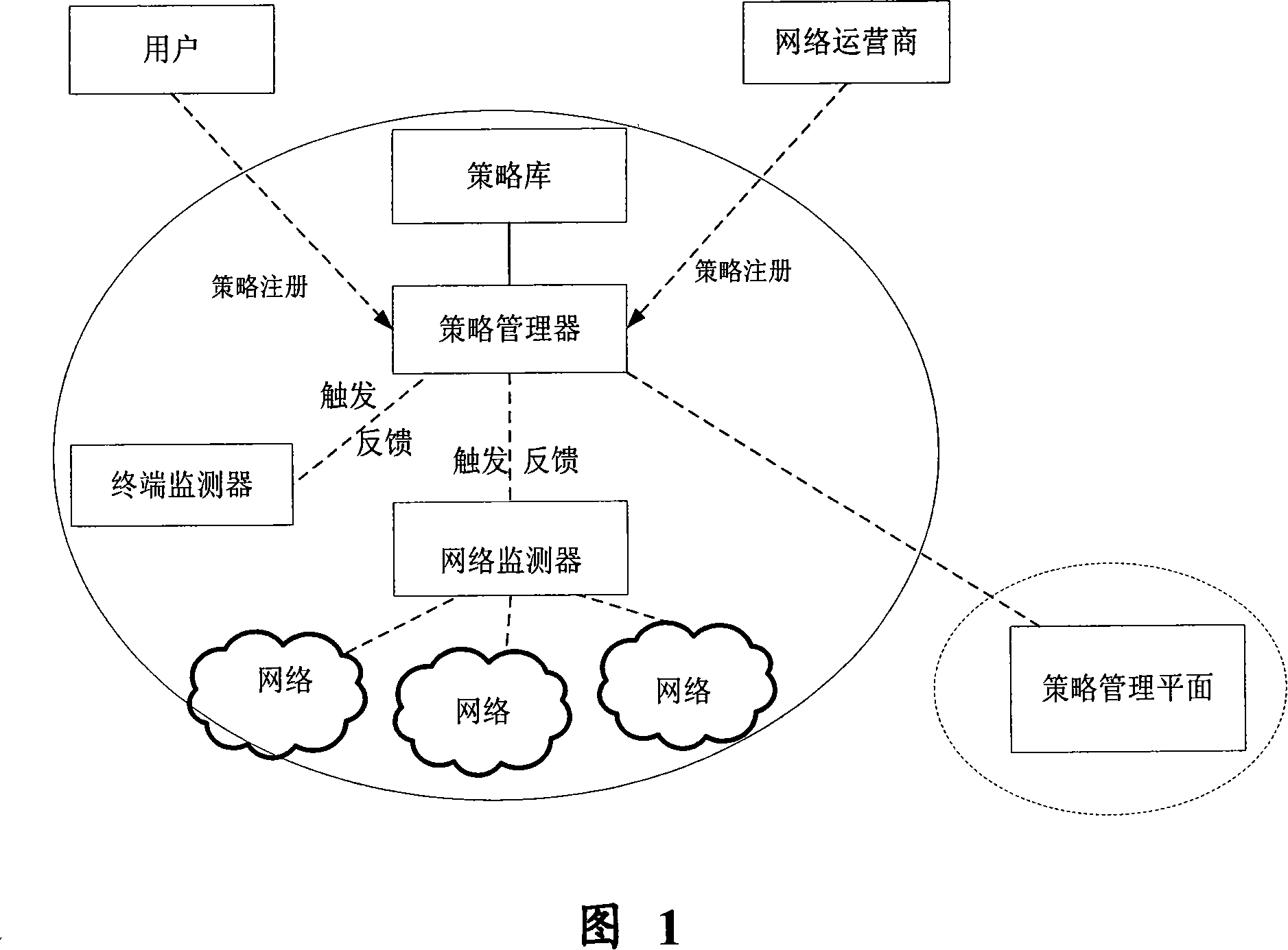
Tactical management based method and architecture used for communication system
InactiveCN101141307AImplement dynamic configurationManagement Complexity ReducedRadio/inductive link selection arrangementsData switching networksCommunications systemComputer science
The utility model discloses a strategy management-based system architecture which is used for the communication system. The system architecture is characterized in that the strategy management device is connected with a strategy base, a network monitor and a terminal monitor via the network, so as to realize the strategy management; the strategy base is connected with the strategy management device via the network to store the strategy; the network monitor is connected with the strategy management device via the network to monitor the network information. Thus, the strategy management device can be triggered to distribute the appropriate strategy and the strategy implementation result can be returned to the strategy management device for updating or generating the strategy; the terminal end monitor is connected with the strategy management device via the network to monitor the termination message and trigger the strategy management device to distribute appropriate strategy and the strategy implementation result can be returned to the strategy management device for updating or generating the strategy.
Owner:BEIJING UNIV OF POSTS & TELECOMM
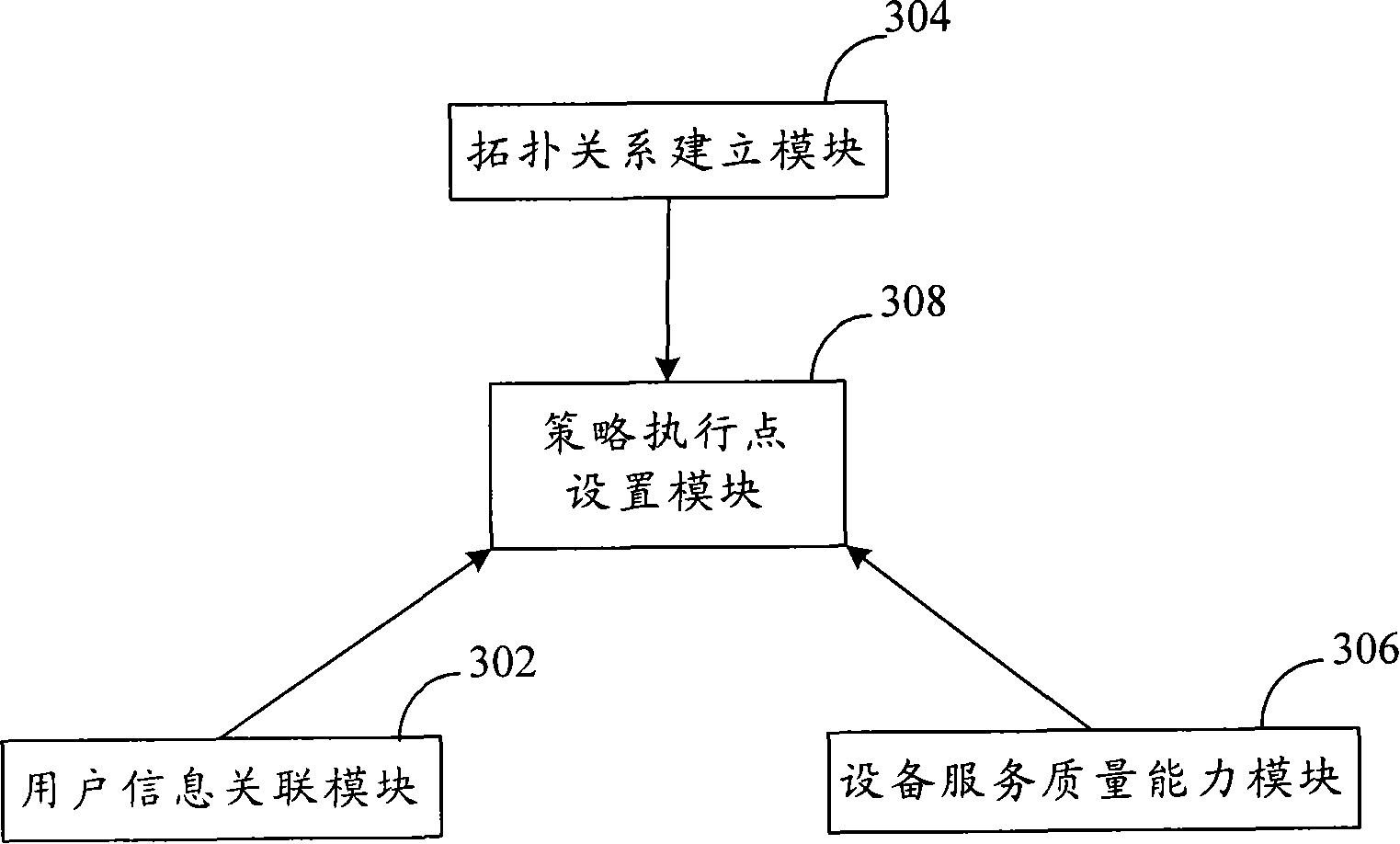
Method and apparatus for choosing policy executing point
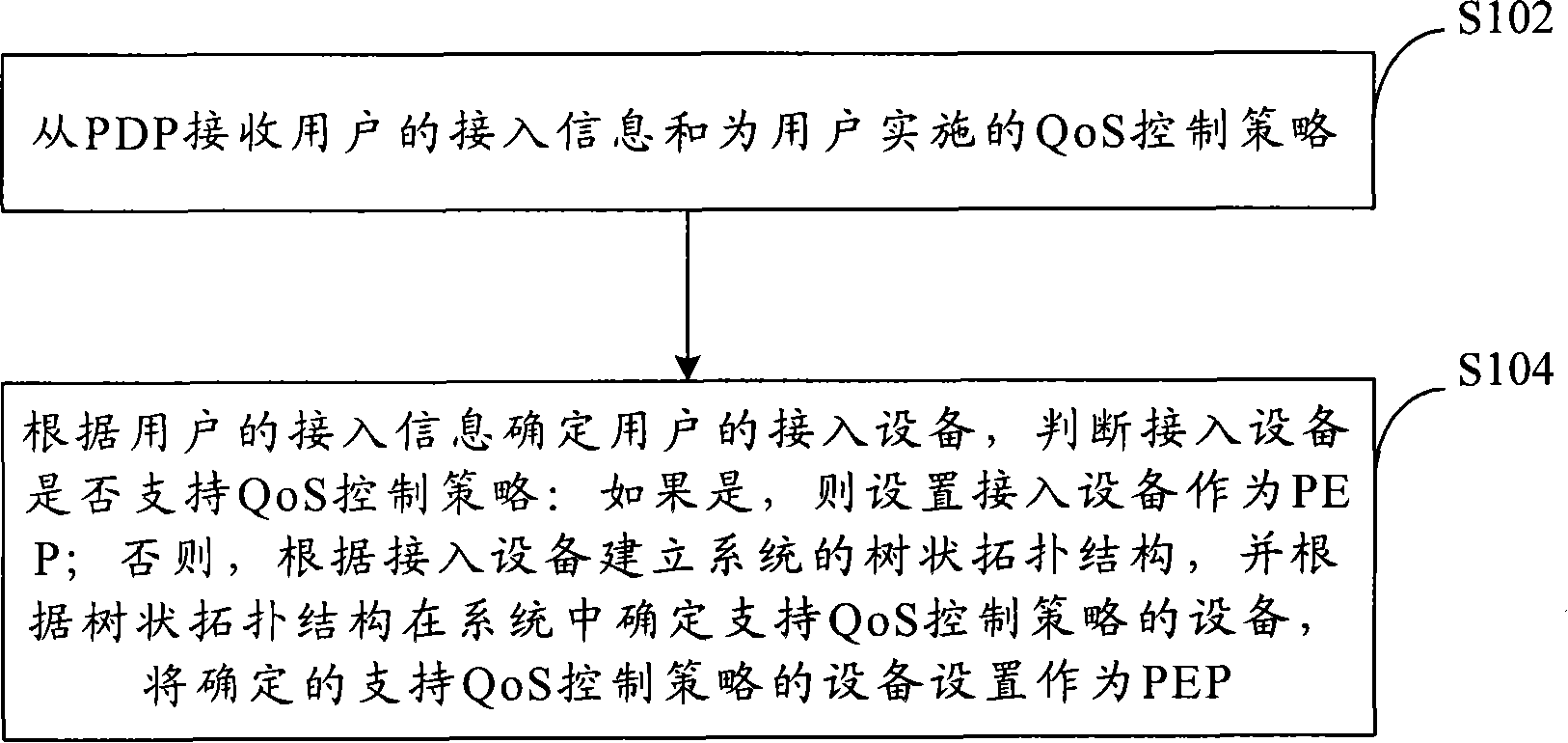
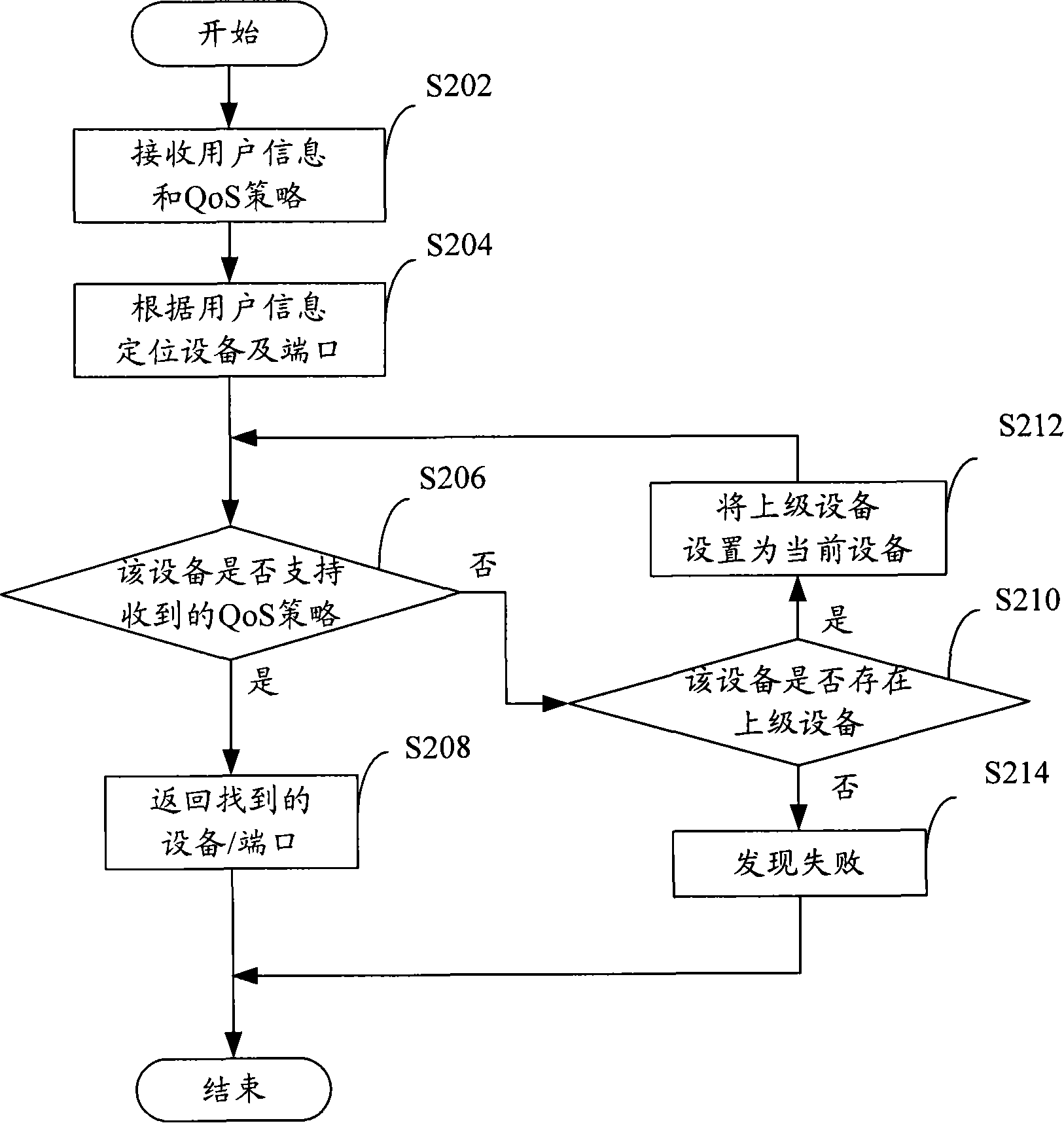
ActiveCN101252779AReduce manual operation costsReduce error rateRadio/inductive link selection arrangementsData switching networksQuality of serviceAccess network
The invention provides a strategy implementation point selection method used for a service quality strategy control system and the equipment thereof. The method comprises the following steps: access information of the users and service quality control strategy implemented for the users are received form the strategy implementation point; access equipment of the users is determined according to the access information of the users, and whether the access equipment supports the service quality control strategy is judged; if the access equipment supports the service quality control strategy, the access equipment is set as the strategy implementation point; otherwise, a tree-like topological structure of the system is established according to the access equipment, equipment for supporting the service quality control strategy is determined in the system according to the tree-like topological structure, and the determined equipment for supporting the service quality control strategy is set as the strategy implementation point. Through the technical proposal of the invention, the strategy implementation point can be automatically searched on the established equipment tree, both the manual operating cost and the error probability are effectively reduced, the QoS strategy control can be implemented in a complex network and especially in a access network system, and the application range of the relevant QoS strategy control system is expanded.
Owner:ZTE CORP
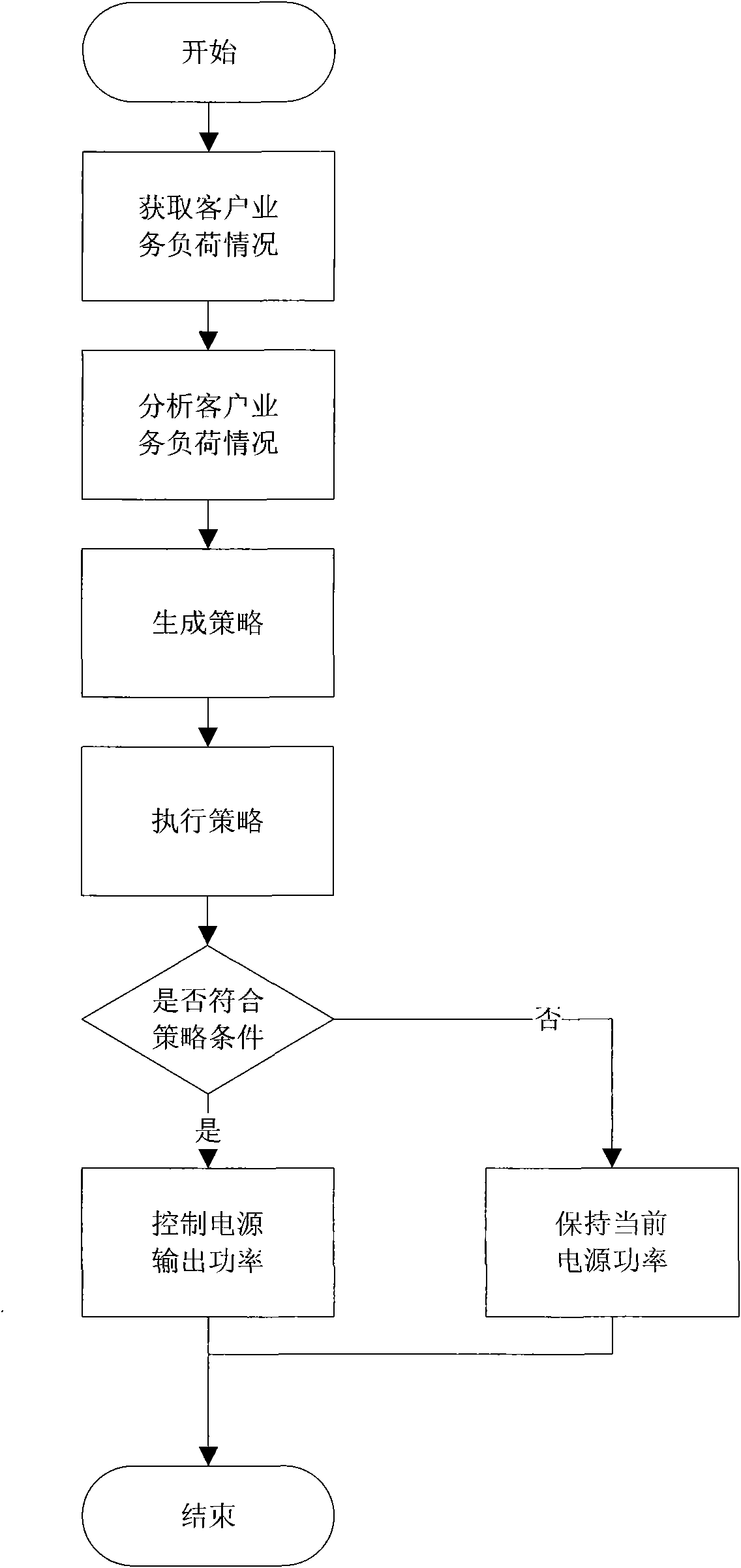
Method for dynamically distributing power of computer power supply based on strategy
ActiveCN101615065AAutomatic load monitoringControl output powerPower supply for data processingComputer monitorComputer monitoring
The invention discloses a method for dynamically distributing power of a computer power supply based on a strategy, which belongs to the computer monitoring management field, formulates a corresponding working strategy according to the customer business load condition and controls the output power of the power supply according to the set strategy. A system comprises a customer business load monitoring unit, an embedded power control unit arranged at the power supply, and a strategy analyzing and implementing unit, wherein the customer business load monitoring unit mainly charges the monitoring and the statistic of customer business loads; the embedded power control unit arranged on the power supply is the carrier of the method and charges the control of the power supply based on the strategy specification; and the strategy analyzing and implementing unit is the center of the method and takes charge of the strategy analysis, the strategy formulation and the strategy implementation. The method for dynamically distributing power of the computer power supply based on a strategy achieves the purpose of saving energy through forcedly controlling the output power of the power supply and has the characteristics of reasonable design, convenient use, energy and resources saving, and the like.
Owner:烟台浪潮云计算有限公司
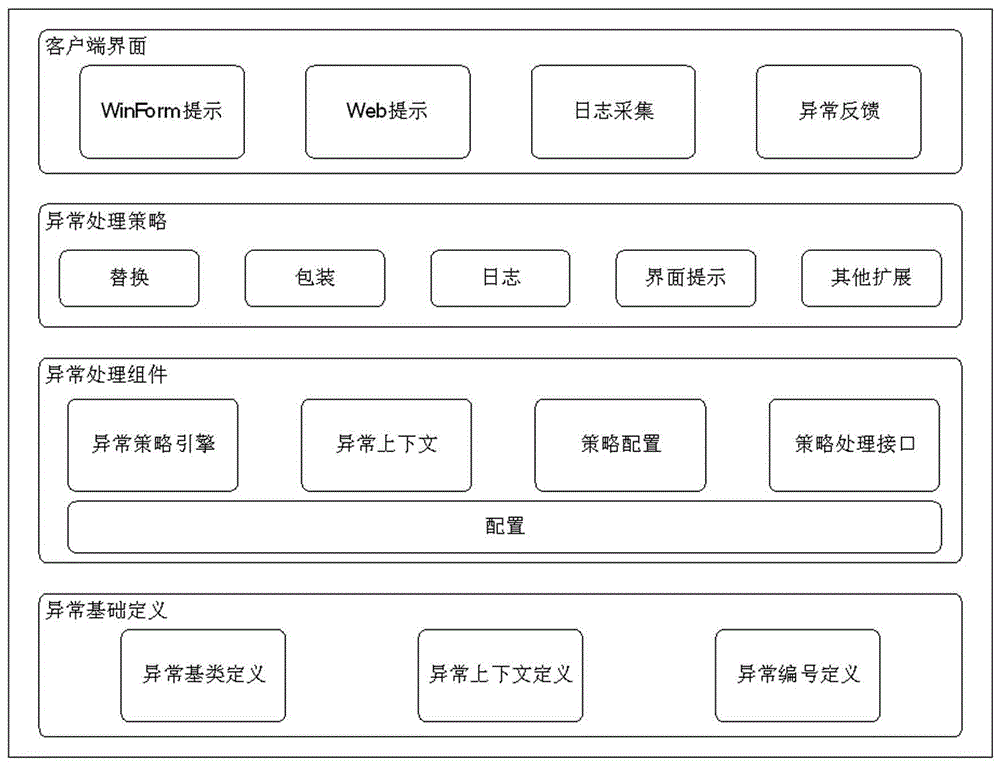
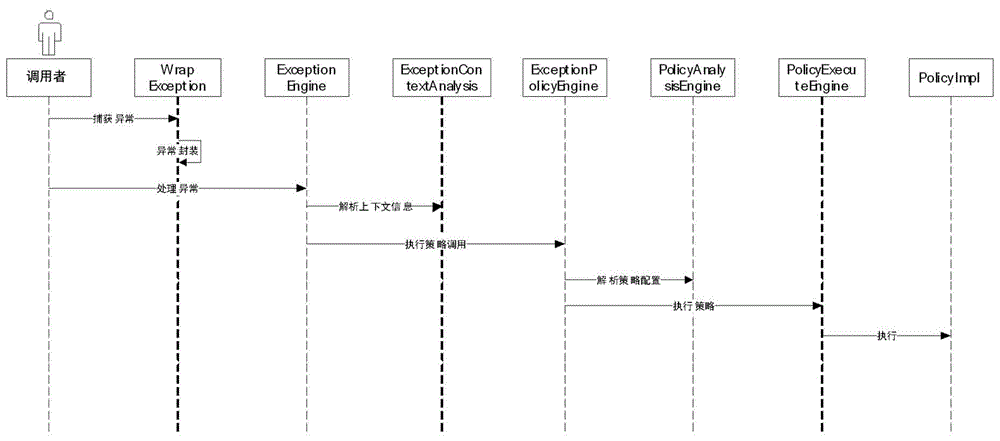
Exception handling method based on strategy configuration
ActiveCN106484425AFlexible handlingEasy to handleSoftware designSpecific program execution arrangementsStrategy executionConfiguration analysis
The invention discloses an exception handling method based on strategy configuration. The method comprises the following steps: encapsulating the exception into context information for exception handling when a service caller captures the exception; transmitting the encapsulated context information to an exception handling engine to performing the exception handling; handing the exception context to an exception analysis engine when the exception handling engine receives the exception context, thereby analyzing the context information; after the analysis is finished, the exception handling strategy engine calling different strategy implementations to realize the handling according to the introduced strategy name; calling a strategy configuration analysis engine to analyze the configured strategy configuration when the strategy implementation is handled, and returning the result; calling a strategy execution engine to execute the corresponding exception handling according to a structure returned by the strategy analysis engine. Compared with the prior art, the exception handling method based on strategy configuration is used for dynamically matching and processing the captured exception and the handling strategy, the exception handling process is simplified, the exception handling flexibility is improved, and the practicability is strong.
Owner:INSPUR COMMON SOFTWARE
Anti-crawler method and system based on operation environment feature identification
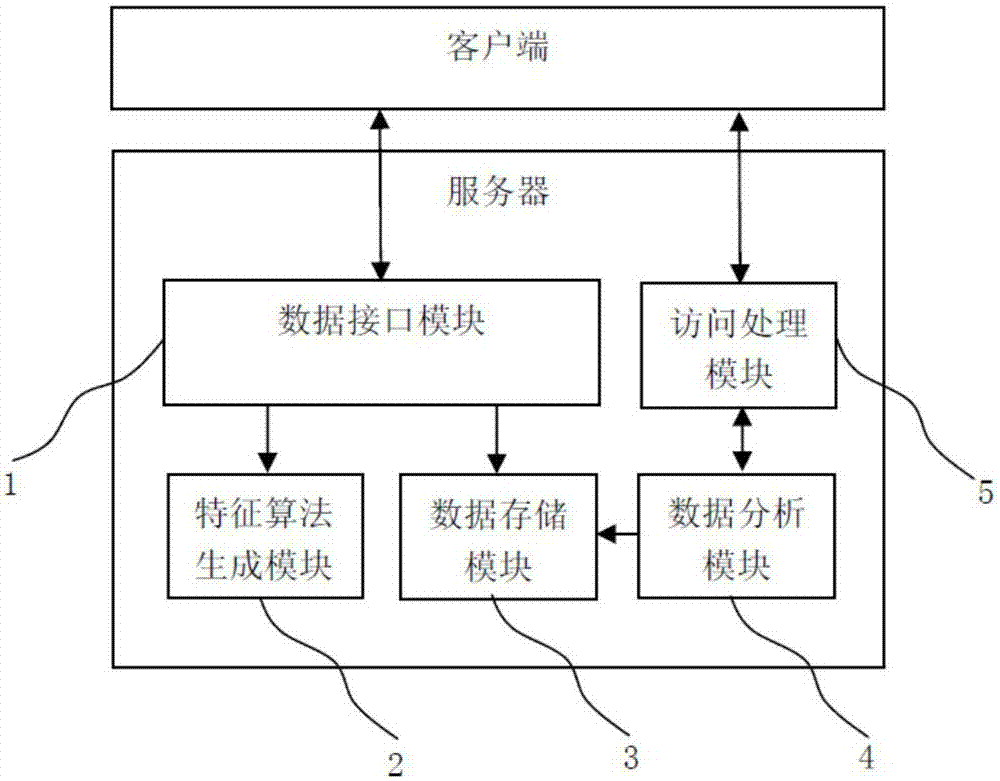
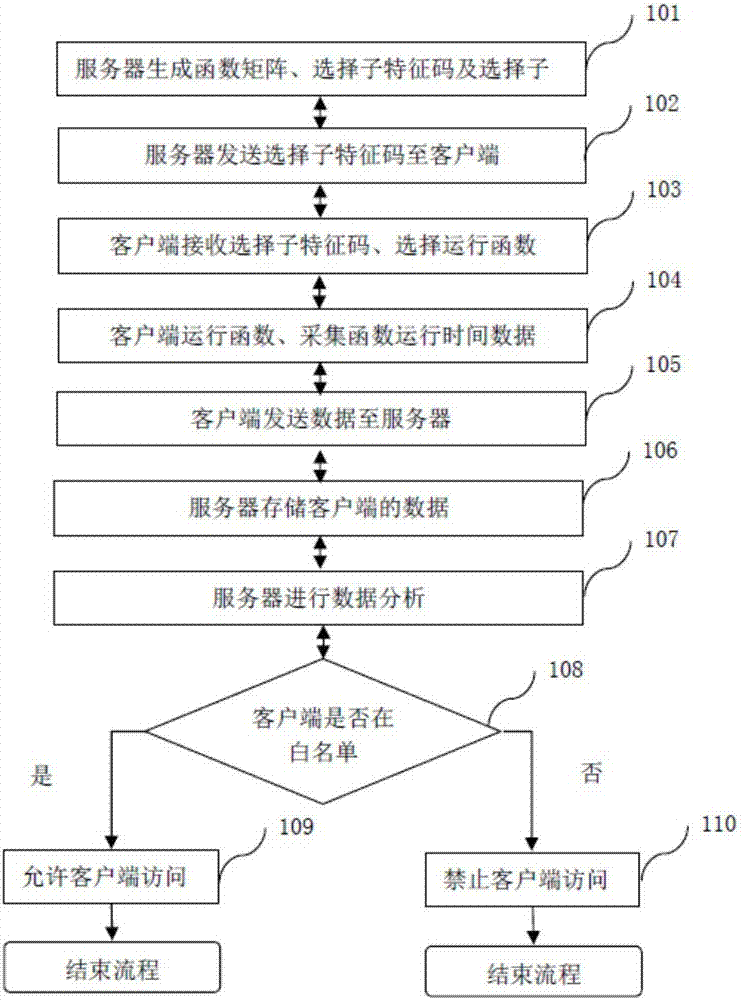
ActiveCN107426148AReduce false positive rateRaise the possibilityTransmissionFeature dataAccess control
The invention discloses an anti-crawler method and system based on operation environment feature identification, and relates to the field of anti-crawler technology, and addresses the technical problems of crawler program identification and anti-crawling strategy implementation. The method herein includes the following steps: generating a new strategy packet and an option code which is for operating the new strategy packet, using the new strategy packet to update the current strategy packet of a server and establishing a feature type white list about the operation feature data of the new strategy packet; transmitting the option code to a client, then transmitting a response request to the client; the client, based on the option code, optionally operating the strategy packet for performing responding by the server, acquiring the feature data corresponding to the option code and returning the feature data to the server; analyzing the option code and the feature data corresponding to the option code, computing the feature type of the client and determining whether the feature type is on the feature type white list, and performing access control on the client which is not on the feature type white list.
Owner:成都优易数据有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com