Patents
Literature
221 results about "Exception analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
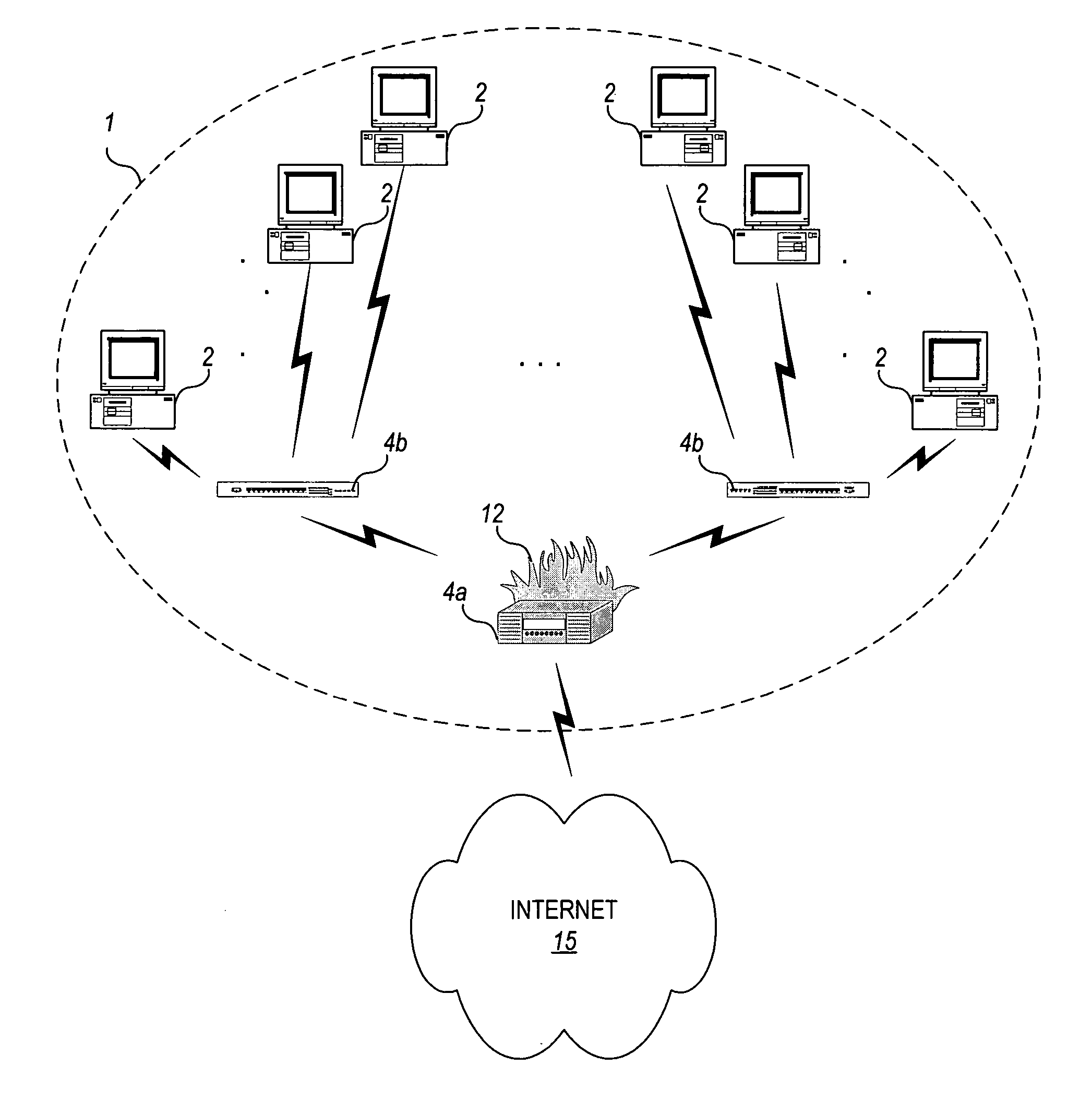
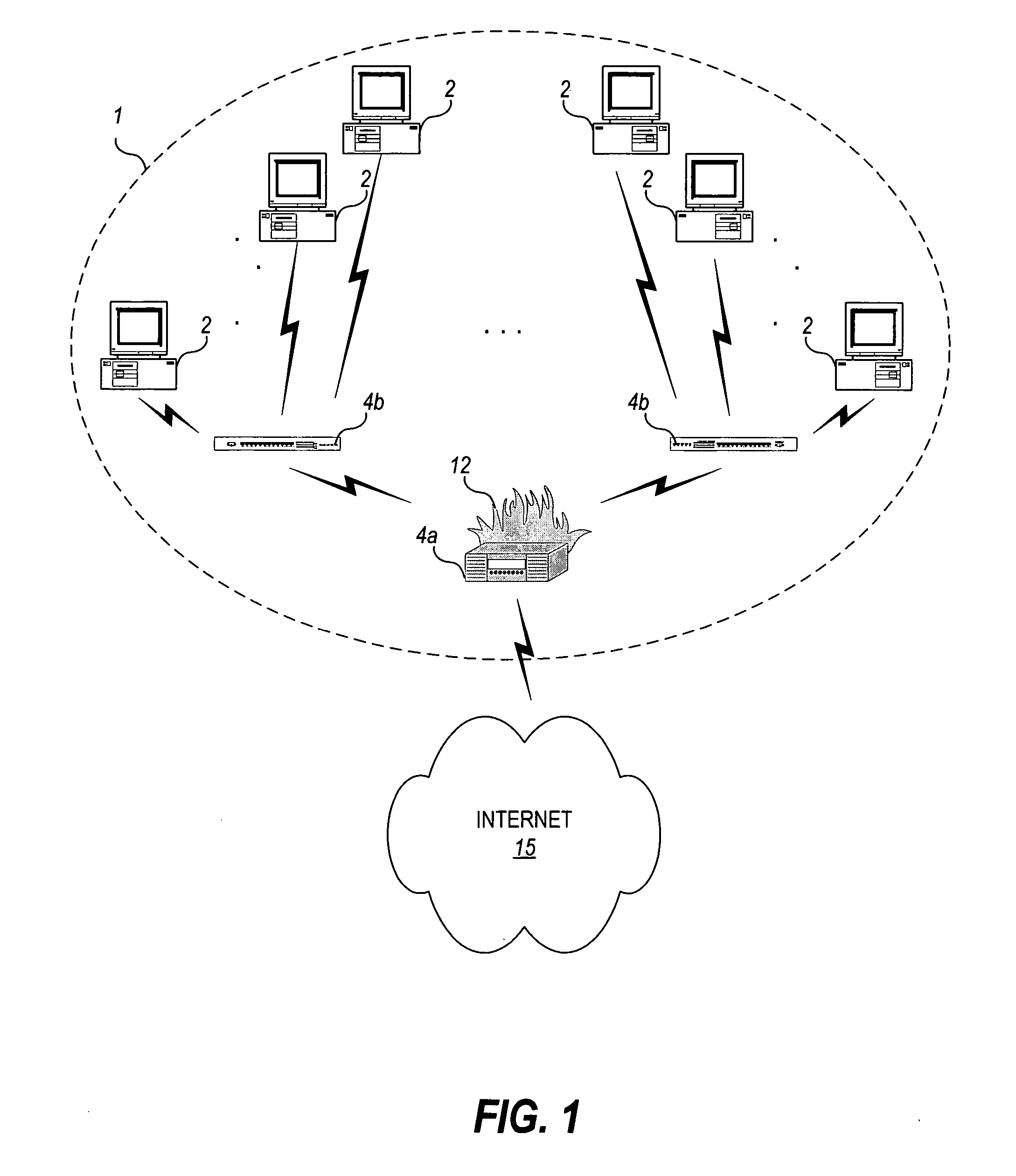
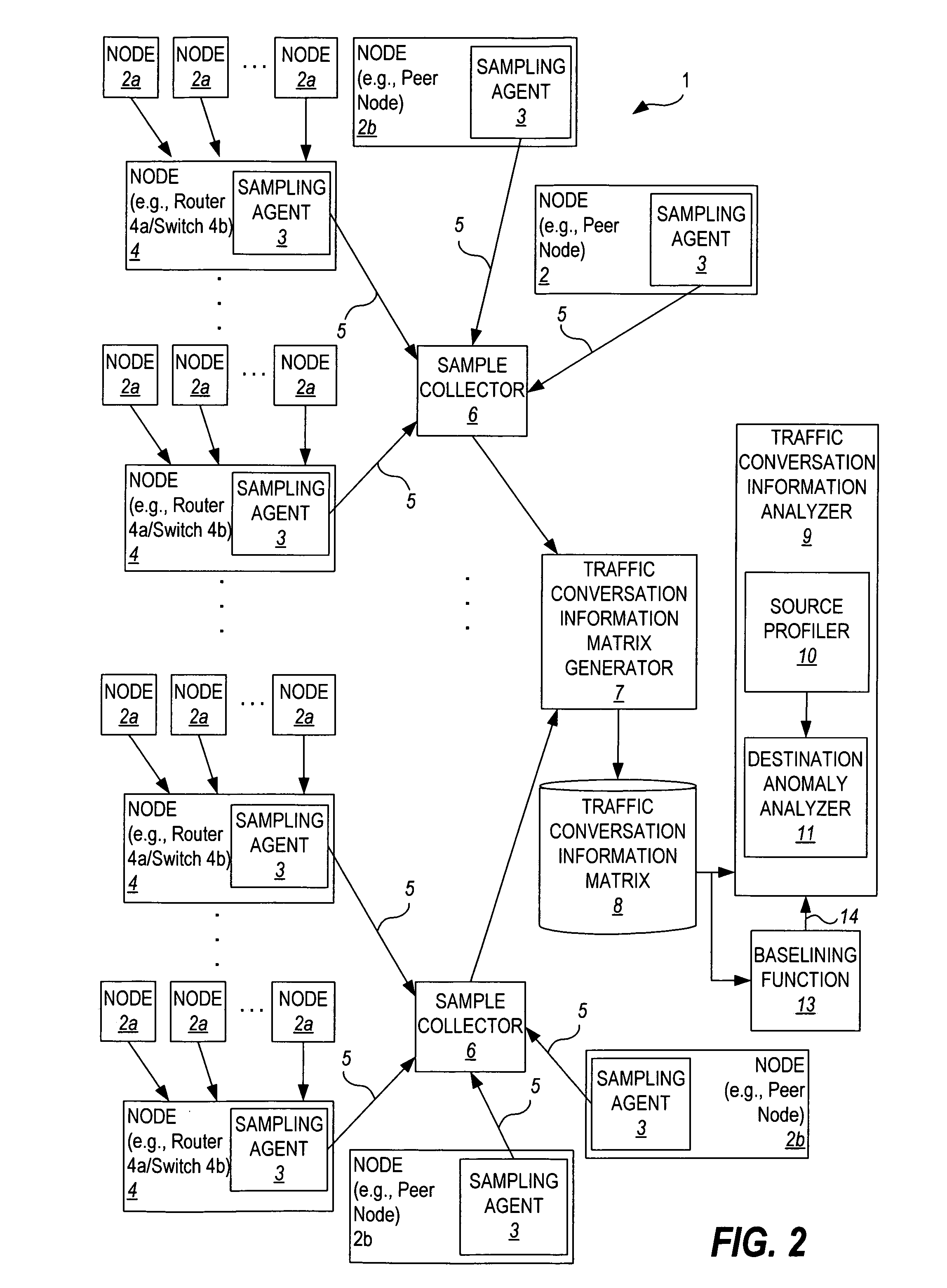
Traffic anomaly analysis for the detection of aberrant network code
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
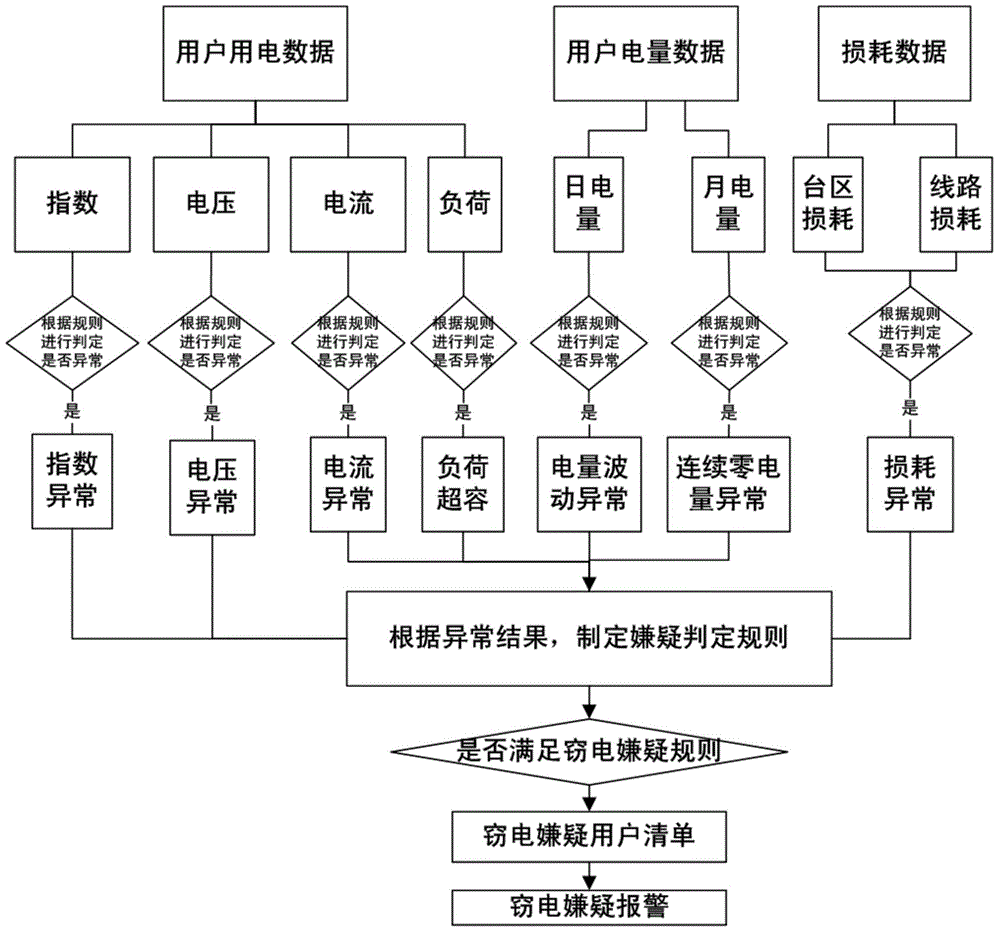
Abnormal electricity utilization judgment method based on abnormal analysis of electric quantity, voltage and current
InactiveCN104407268APrevent and monitor electricity theftReduce line lossCurrent/voltage measurementElectrical testingElectricityPower user
The invention discloses an abnormal electricity utilization judgment method based on abnormal analysis of electric quantity, voltage and current. The abnormal analysis of the electric quantity comprises a fluctuation electric quantity analysis process and a zero electric quantity analysis process, wherein the abnormal analysis of voltage comprises voltage phase-failure abnormal analysis, voltage off-normal abnormal analysis and voltage unbalanced abnormal analysis; the abnormal analysis of current comprises a current loss abnormal analysis and current unbalanced abnormal analysis. By analyzing and comparing abnormal data of electric quantity, voltage and current of the users, real abnormal users or electricity stealing users can be determined. The abnormal electricity utilization judgment method based on the abnormal analysis of the electric quantity, the voltage and the current, disclosed by the invention, has the advantages that electricity information of power users can be timely grasped, the electricity stealing behavior is prevented and monitored, and the reliability of power supply is improved.
Owner:STATE GRID CORP OF CHINA +2
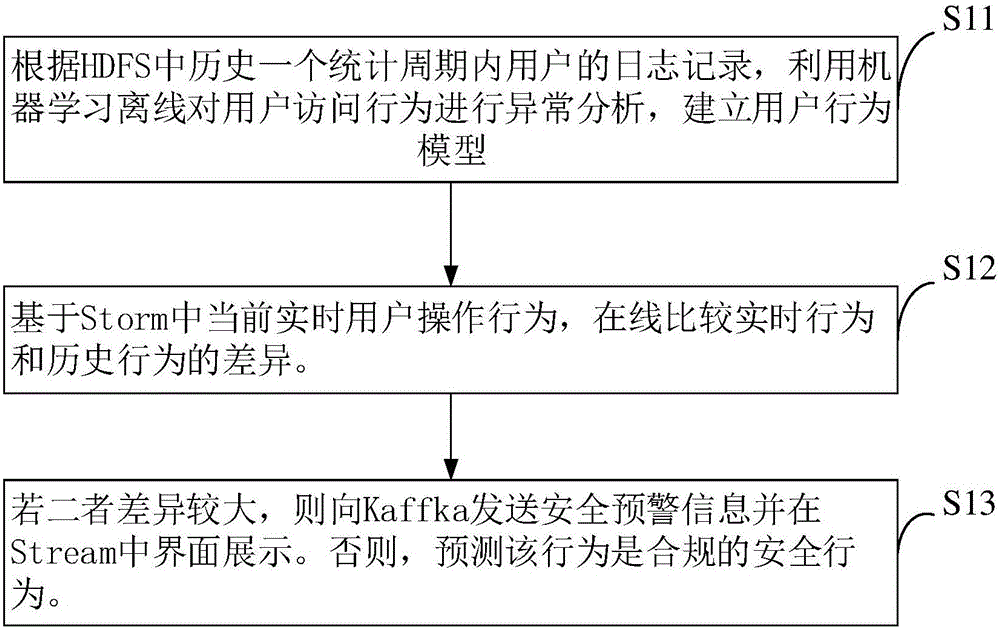
Detection and analysis method for abnormal behaviors of user in big data environment
ActiveCN106789885AAbnormal Behavioral IntelligenceAbnormal behavior intelligent detection intelligenceTransmissionSpecial data processing applicationsGranularityAnomalous behavior
The invention relates to a detection and analysis method for the abnormal behaviors of a user in a big data environment. The method is characterized in that the method comprises the following steps: enabling a user abnormal behavior detection system to carry out the abnormality analysis of user access behaviors in an offline mode through machine learning according to the log record of the user in HDFS in one historical statistical period, and building a user behavior model; enabling the user abnormal behavior detection system to carry out the online comparison of real-time behaviors and historical behaviors based on the current real-time user's operation behavior in Storm; transmitting safety early-warning information to Kaffka and displaying the safety early-warning information at a Stream interface if the difference between real-time behaviors and historical behaviors is big, or else judging that the behavior is a legal safe behavior. Compared with the prior art, the method supports the definition of a behavior mode or a user portrait according to the historical use behavior habit of the user at a Hadoop platform through a machine learning algorithm. A training system updates a model each month in a default manner, and the granularity of the model is one minute.
Owner:STATE GRID CORP OF CHINA +2
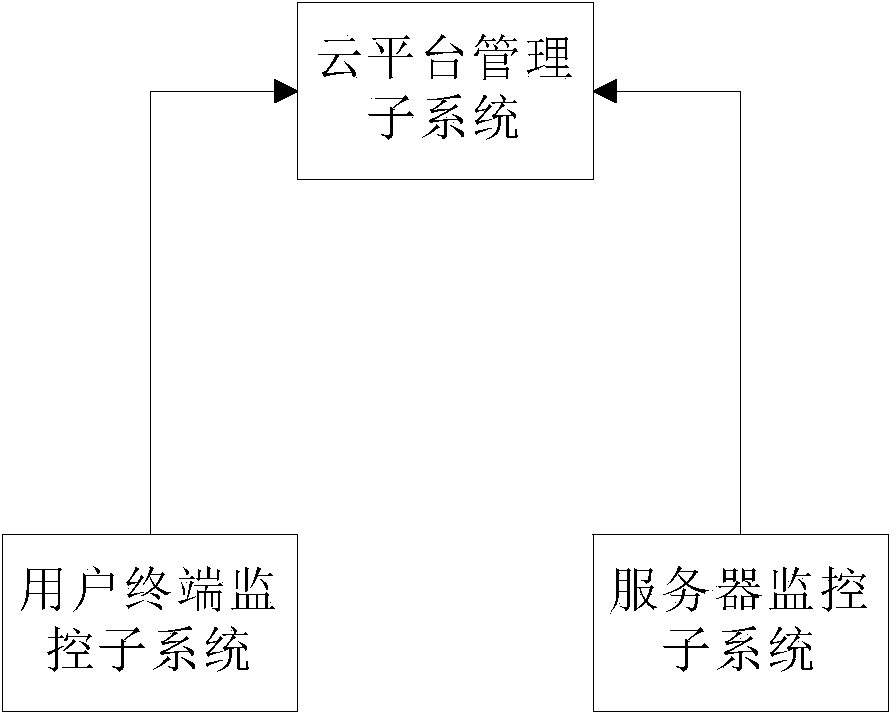
Electric power system interior APT attack detection and pre-warning system based on network architecture
The invention provides an electric power system interior APT attack detection and pre-warning system based on network architecture. The system comprises a user terminal monitoring sub-system, a server monitoring sub-system and a cloud platform management sub-system. According to the characteristic that APT attacks are all pervasive, the APT attack detection and pre-warning system containing a user terminal and a system server is designed. The detection and pre-warning system has the common network security management function, meanwhile conducts analysis of exceptions on logs and events, and excavates and repairs loopholes of the system, after a network system is suffered from the APT attacks, data of attacked equipment can be quickly restored, and the system assists security managers in reversely tracking an attack source.
Owner:STATE GRID CHONGQING ELECTRIC POWER CO ELECTRIC POWER RES INST +1
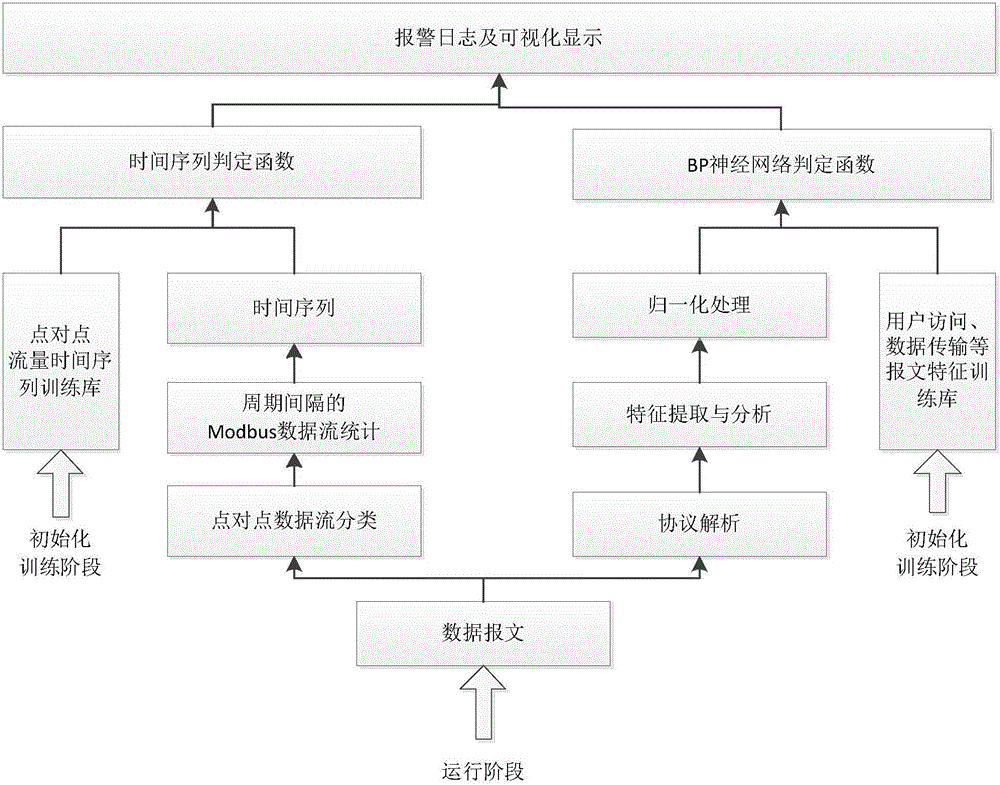
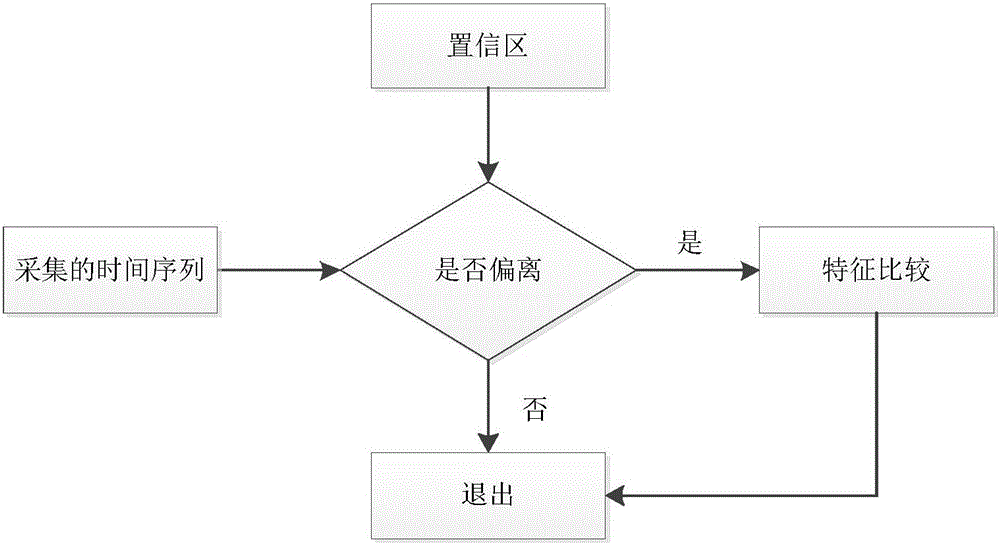
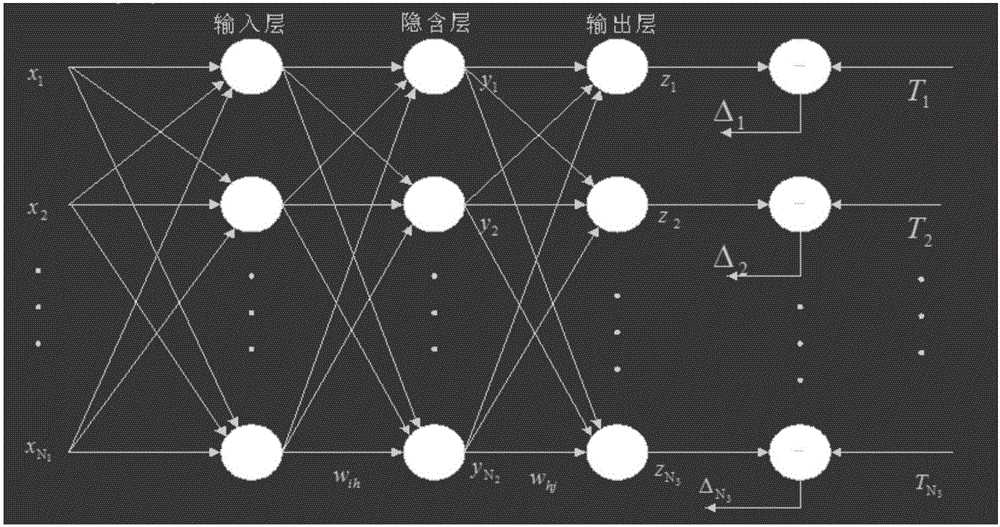
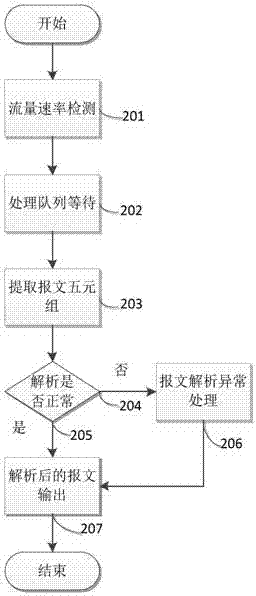
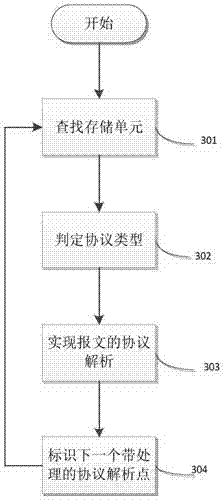
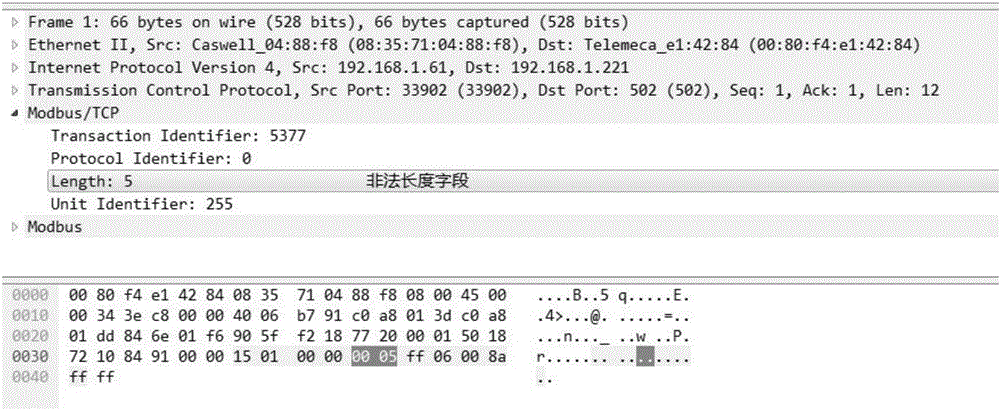
Modbus protocol-oriented data flow anomaly analysis method
The invention discloses an industrial control network Modbus protocol-oriented data flow anomaly analysis method. The method comprises the following steps of 1, an initialization phase, wherein a Modbus protocol data flow anomaly analysis model is generated; 2, an initialization phase, wherein a Modbus protocol self-learning normal behavior model is generated; 3, a run phase, wherein the run state of Modbus protocol data flow is judged; 4, a run phase, wherein the normal / abnormal behavior state of Modbus protocol data messages is judged; 5, representing, wherein the results in the step 3 and the step 4 are visibly represented. The method is designed on the basis of deeply knowing the Modbus protocol and the anomaly analysis technology, good comprehensiveness and practicality are achieved, the efficiency of anomaly analysis can be effectively improved, and Modbus abnormal data flow existing in an industrial control system can be efficiently found through the method.
Owner:工业和信息化部电子工业标准化研究院
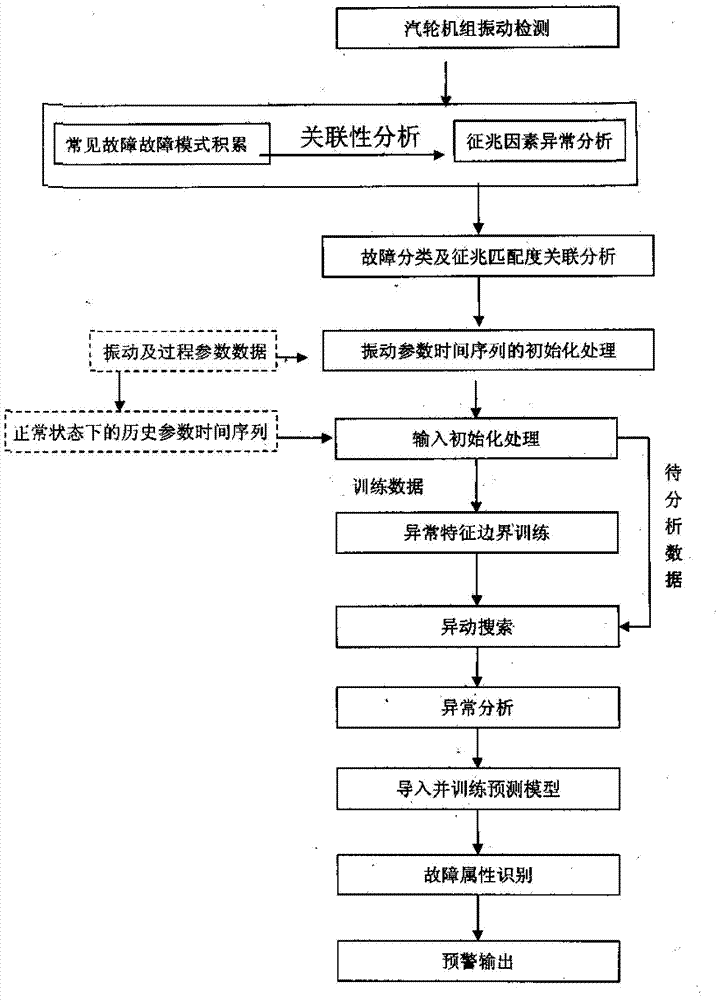
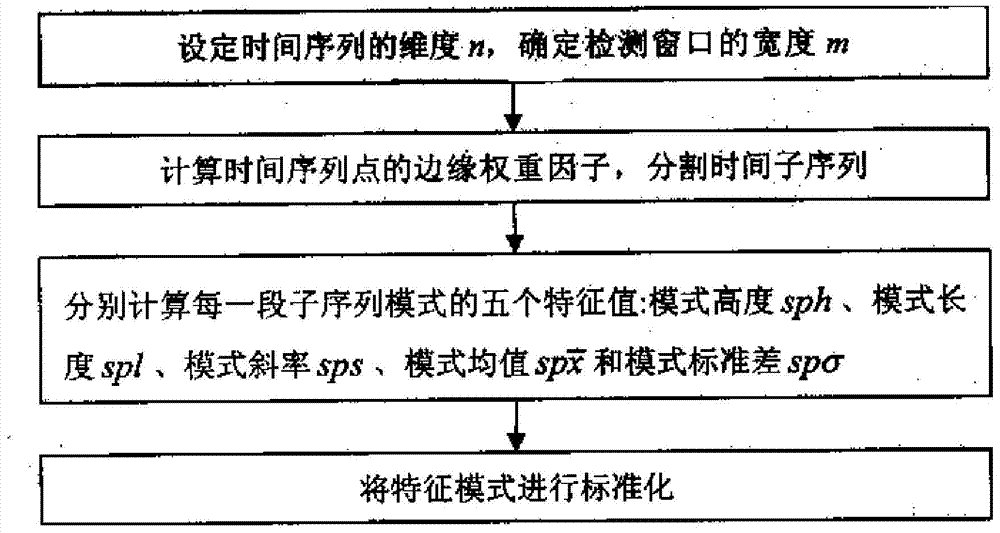
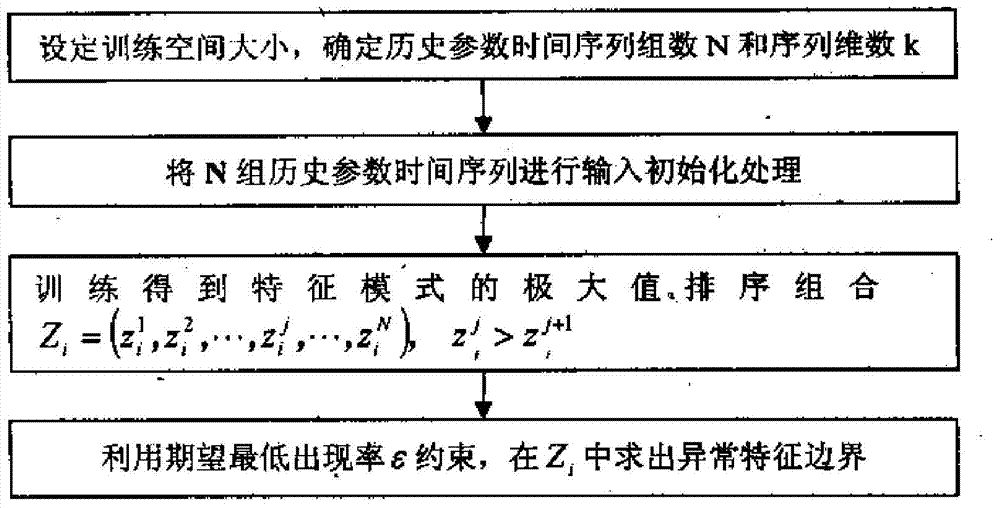
Turbine set online fault early warning method based on abnormality searching and combination forecasting
InactiveCN103793601AImprove the accuracy of early warningDeepen utilizationSpecial data processing applicationsRegression analysisElectric power system
The invention discloses a turbine set online fault early warning method based on abnormality searching and combination forecasting, and belongs to the technical field of electric system early warning. The turbine set online fault early warning method includes the steps of carrying out input initializing processing responsible for segmenting an input parameter time sequence in a standardization mode, and extracting a sequence characteristic mode; carrying out abnormality characteristic boundary training: obtaining an abnormality searching reference standard by training normal state parameters; carrying out abnormality searching: determining an abnormality sequence set by searching characteristic boundary crossing; identifying an abnormality change trend through regression analysis to obtain abnormality analysis of an abnormality distribution change rule; building a forecasting model to carry out trend forecasting on abnormal changes; carrying out early warning output according to the forecasting result in cooperation with the corresponding relation between abnormality parameters and fault symptoms. According to the turbine set online fault early warning method, the defect that in traditional monitoring analysis, only a limiting value theory is used, the abnormality can not be completely identified is overcome, the abnormality early warning accuracy and the abnormality early warning depth are improved, and beneficial evidences are provided for unit fault causes and responsibility ascription.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID +1
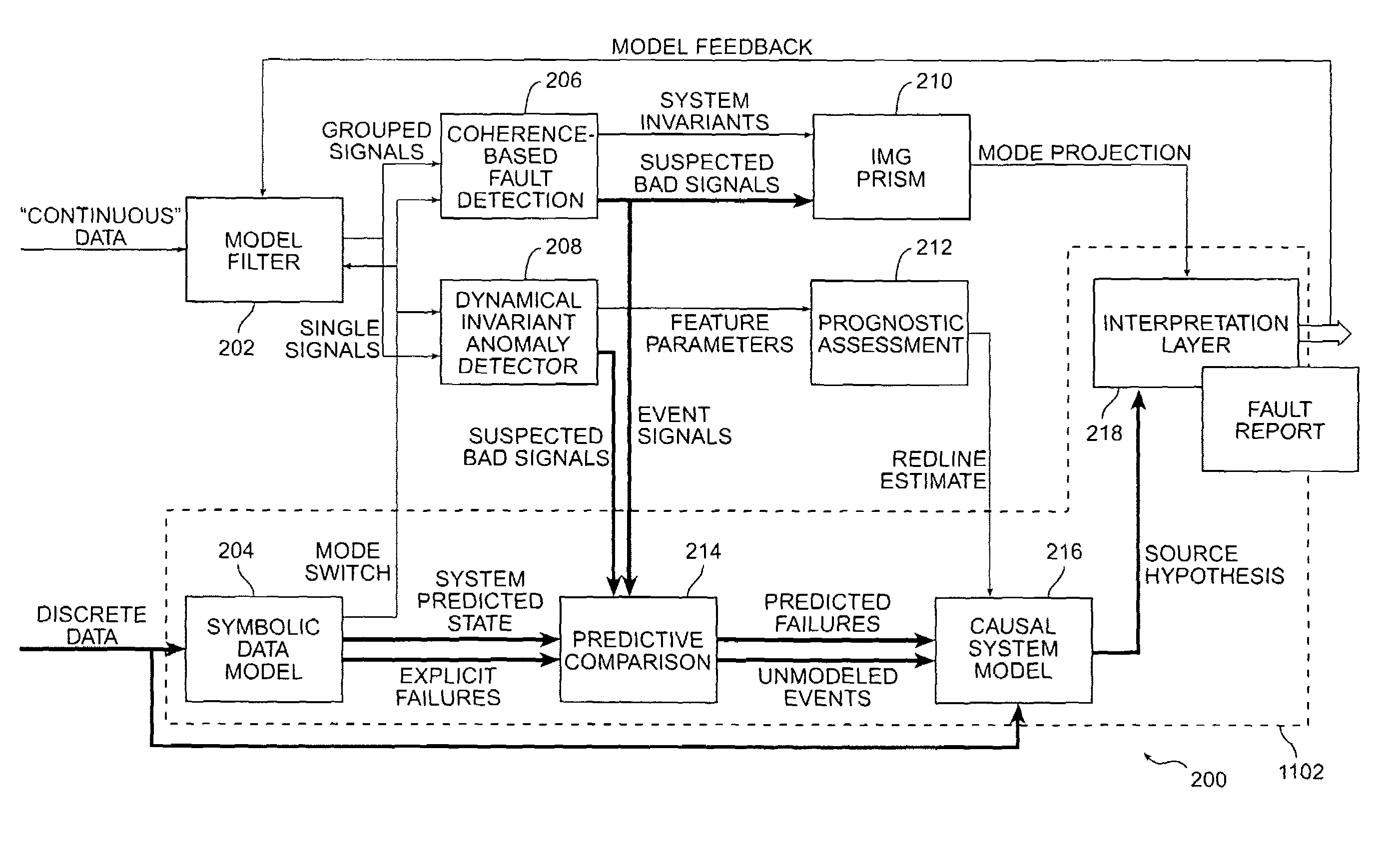
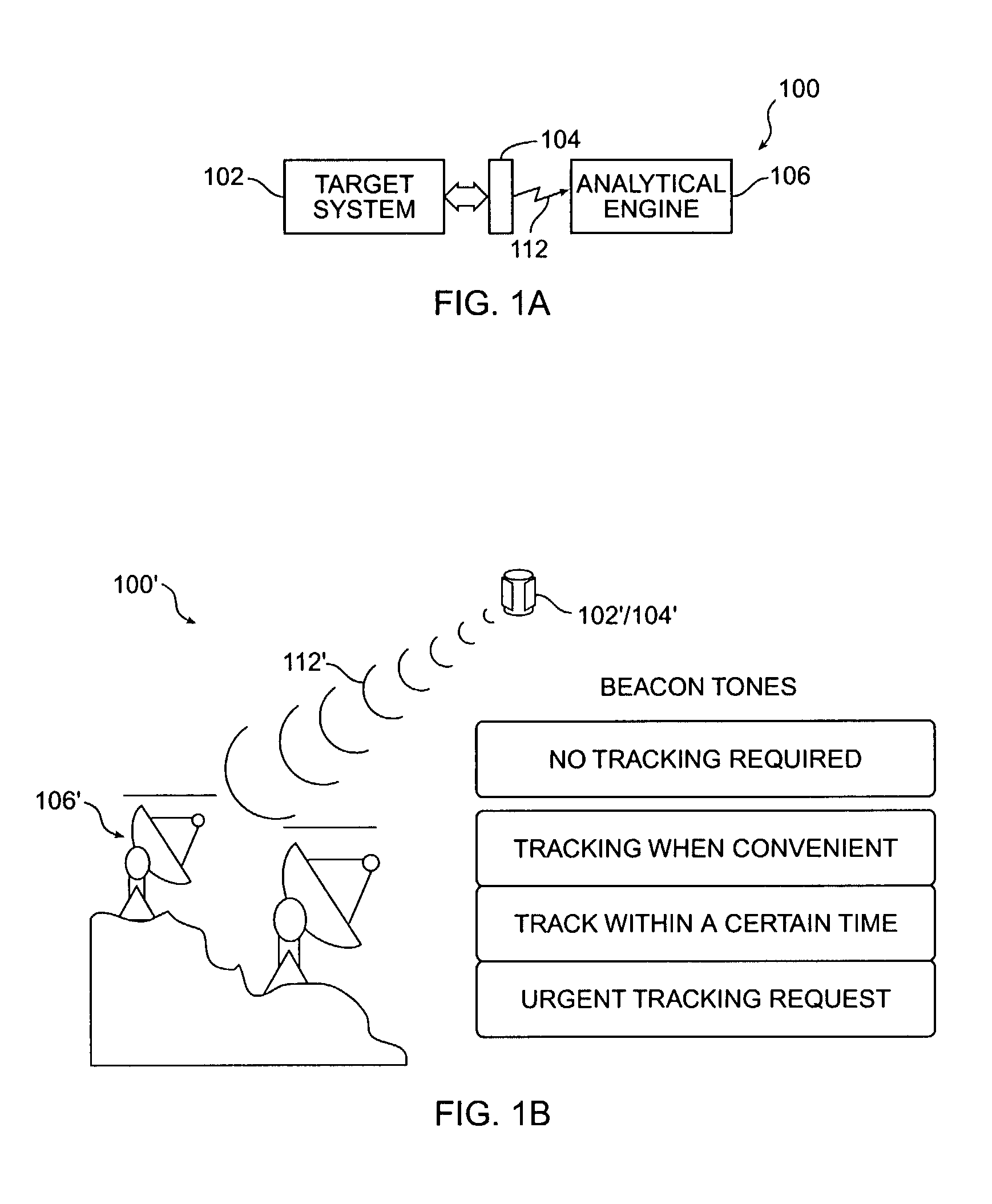
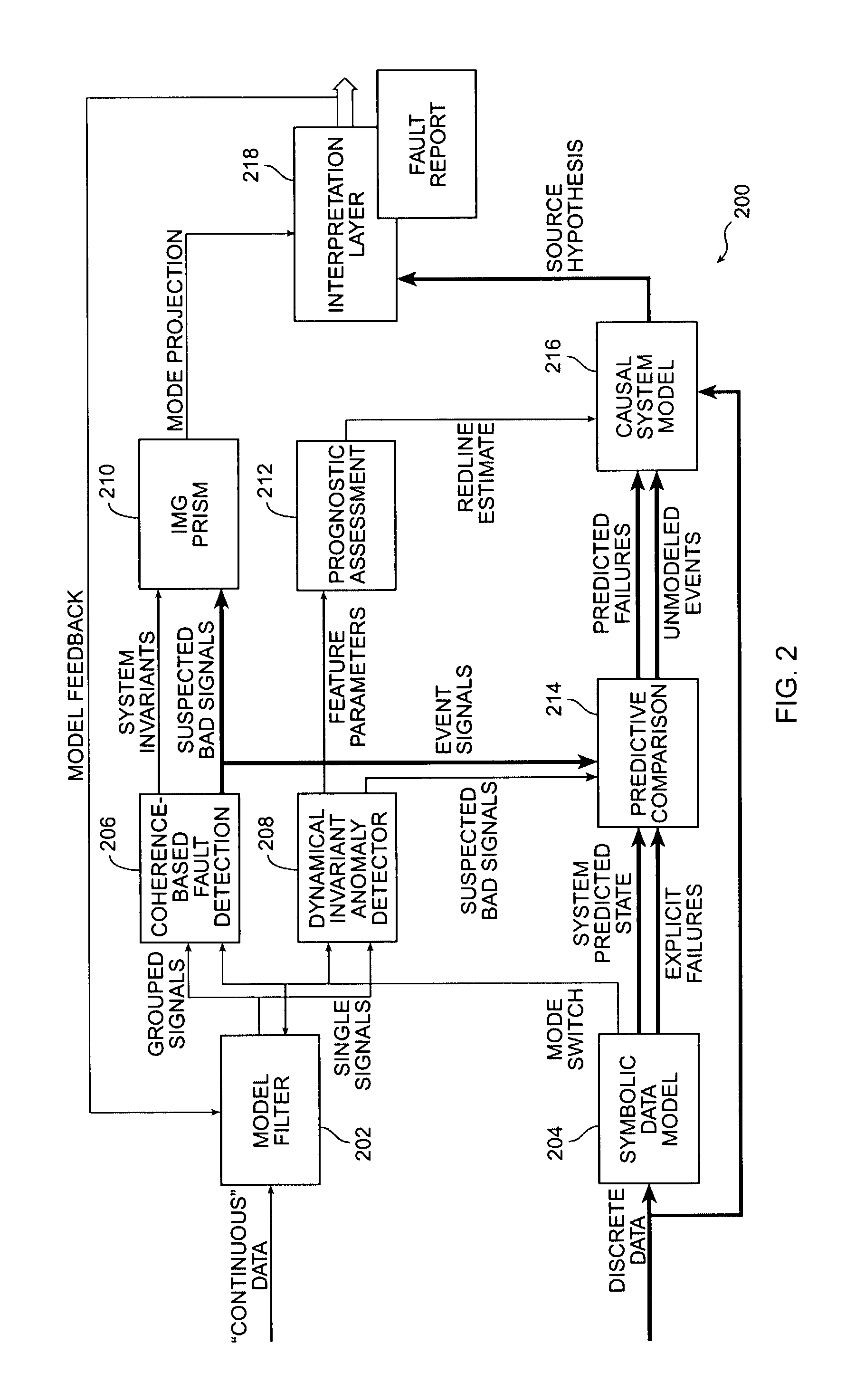
Exception analysis for multimissions
ActiveUS7080290B2Detecting faulty hardware using neural networksSimulator controlOn boardStandard form
A generalized formalism for diagnostics and prognostics in an instrumented system which can provide sensor data and discrete system variable takes into consideration all standard forms of data, both time-varying (sensor or extracted feature) quantities and discrete measurements, embedded physical and symbolic models, and communication with other autonomy-enabling components such as planners and schedulers. This approach can be adapted to on-board or off-board implementations with no change to the underlying principles.
Owner:CALIFORNIA INST OF TECH
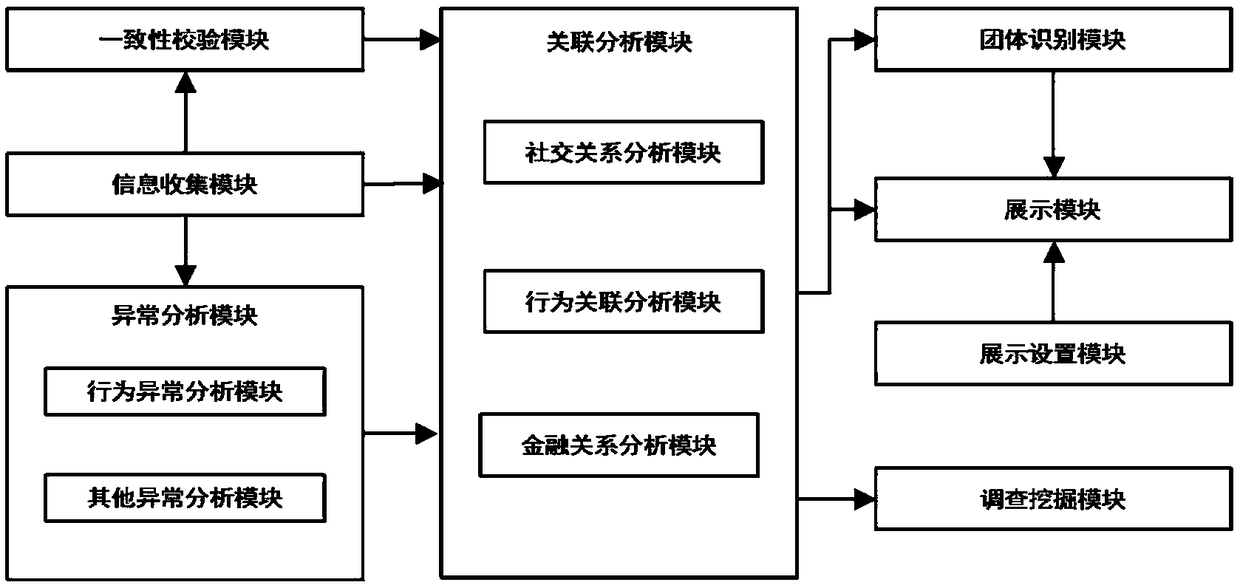
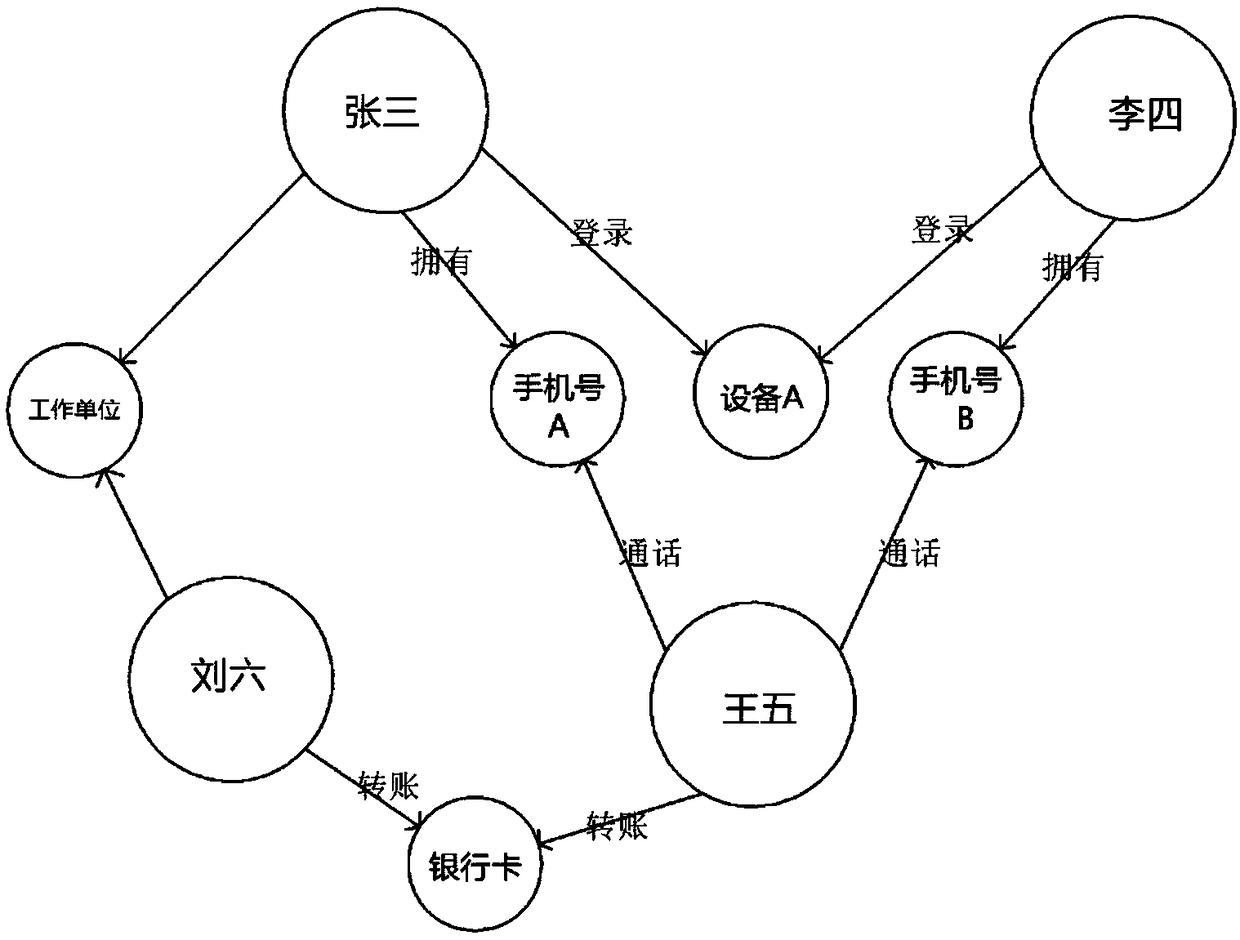
A group fraud identification system based on knowledge map
InactiveCN109191281AAvoid damageAchieving identifiabilityFinanceSemantic tool creationRisk preventionThird party
The invention relates to the technical field of loan risk prevention and control system, in particular to a group fraud identification system based on a knowledge map, which includes an information collection module, an abnormality analysis module, an association analysis module, a group identification module, a display module, a display setting module and a survey and digging module. The information collection module is used for collecting personal information of the borrower. The abnormality analysis module is used for detecting and analyzing abnormal behavior or abnormal data of the borrower, and the association analysis module is used for analyzing the association relationship between the suspected fraudulent user and other borrowers or third-party blacklisted persons. The group identification module is used for finding other suspected fraudulent users related to the suspected fraudulent users according to the association relationship and forming a suspected fraudulent group for the case investigator to judge. The invention provides a group fraud identification system based on a knowledge map, which can identify and evaluate the groups among borrowers, find out the groups thatmay have fraud risk, and reduce unnecessary losses of banks.
Owner:重庆富民银行股份有限公司
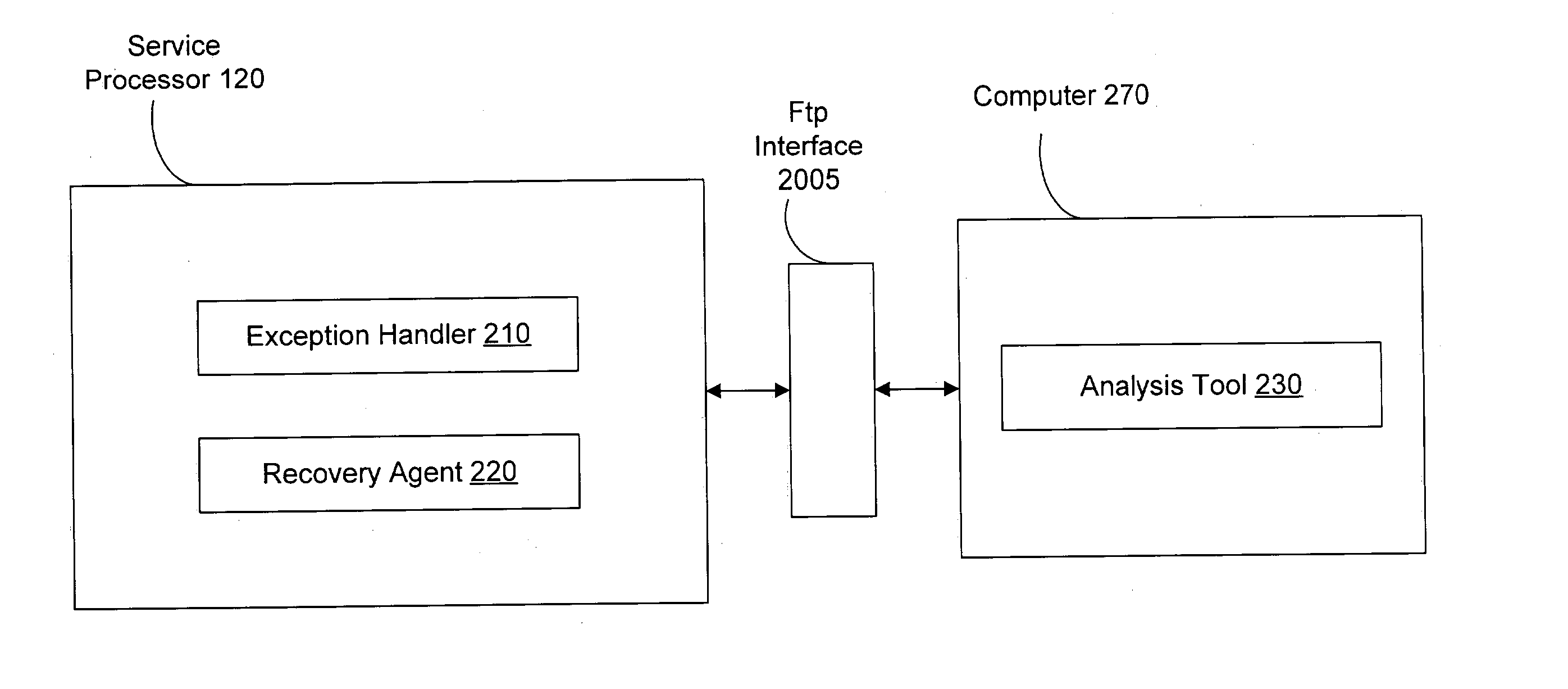
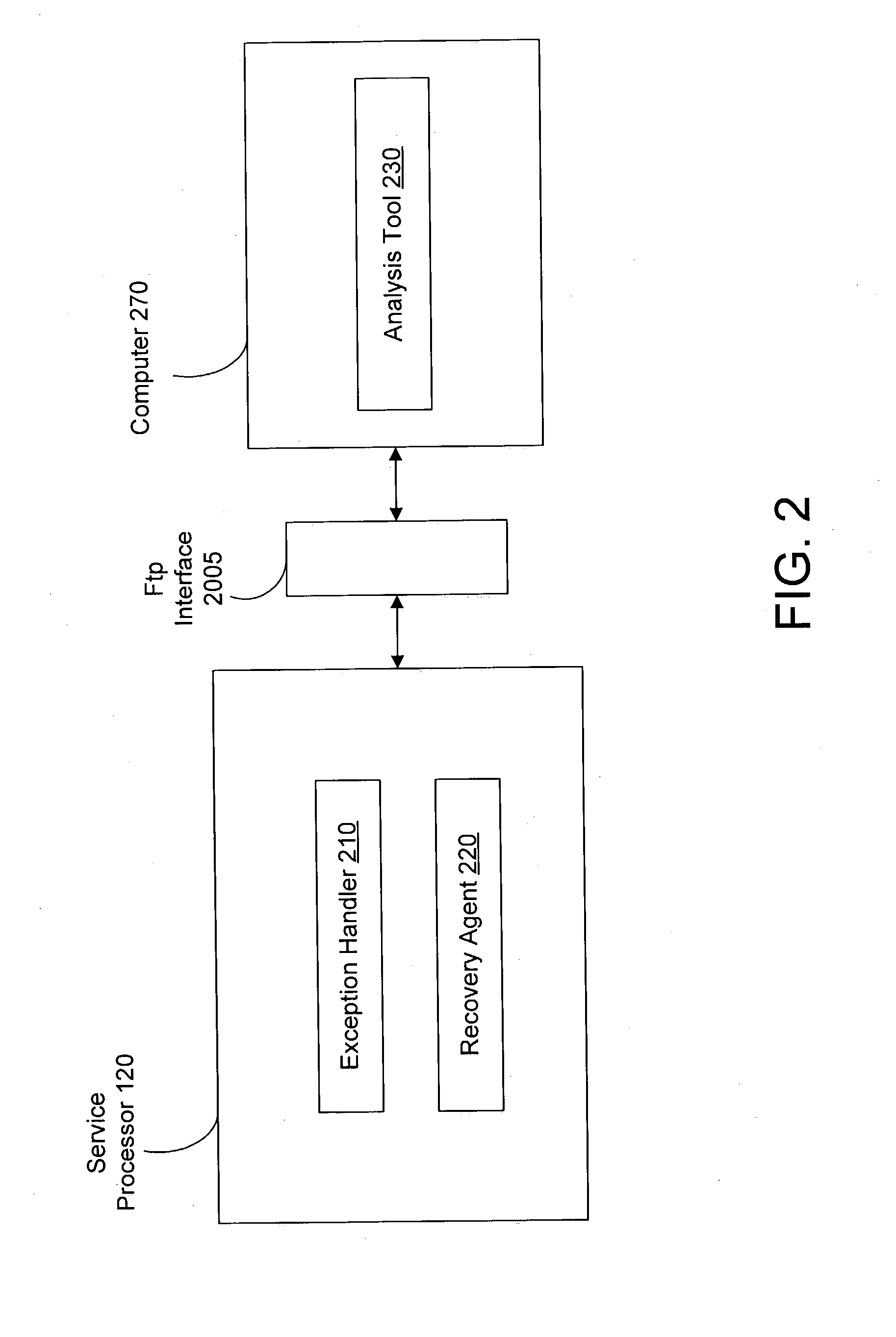
Handling exceptions
InactiveUS20050015579A1Error detection/correctionDigital computer detailsRecovery methodRestoration method
Techniques for handling exceptions are disclosed. In an embodiment, an exception-handling scheme supports an embedded system. An exception handler records information related to the exception. An intelligent recovery agent determines if the erroneous process should be terminated, recovered, etc. The recovery agent also determines the most efficient recovery method, etc. A post-exception analysis tool identifies the cause of the exception.
Owner:HEWLETT PACKARD DEV CO LP
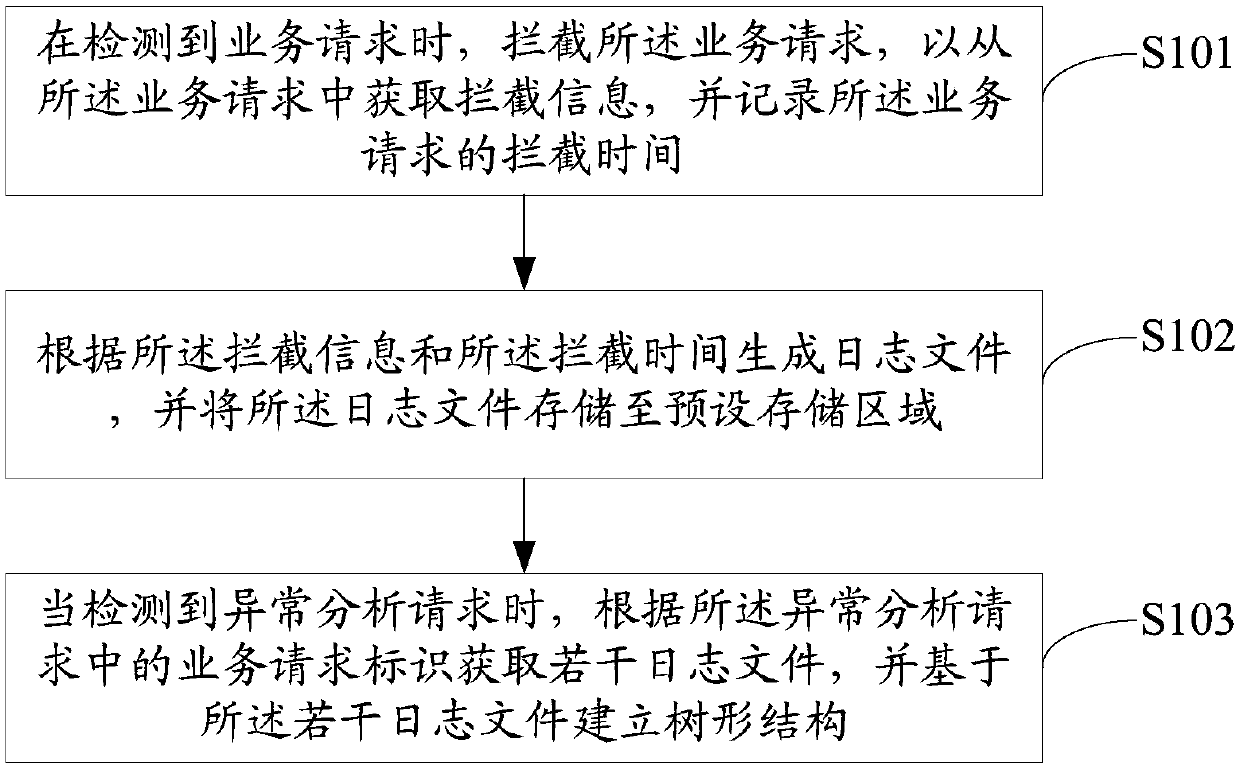
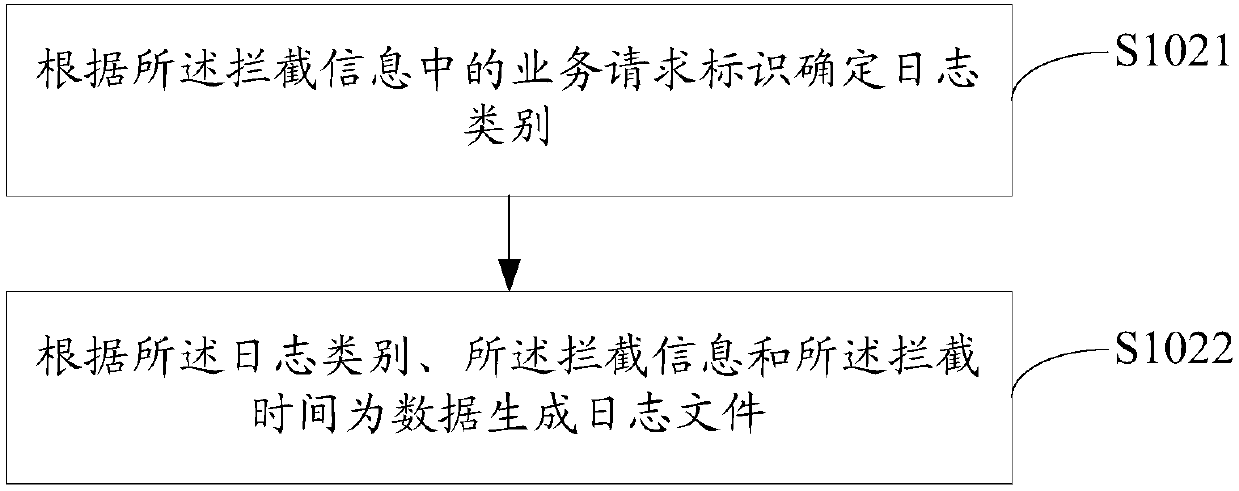
Log generation management method, log generation management device, log generation management equipment and computer-readable storage medium
InactiveCN107678933AFast and accurate analysisFast and accurate positioningHardware monitoringTree shapedDEVS
The invention discloses a log generation management method, a log generation management device, log generation management equipment and a computer-readable storage medium. The log generation management method includes the following steps: when a service request is detected, intercepting the service request to acquire intercepted information from the service request, and recording intercepting timeof the service request, wherein the intercepted information includes a service request identifier and calling chain information; generating a log file according to the intercepted information and theintercepting time, and storing the log file to a preset storage area; and when an abnormality analysis request is detected, acquiring a plurality of log files according to service request identifiersin the abnormality analysis request, and establishing a tree-shaped structure on the basis of the plurality of log files. According to the method, quickly and accurately analyzing and locating key information, of causing a service request abnormality, by a developer are facilitated, costs are greatly reduced, and an accuracy rate of the key information is increased.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
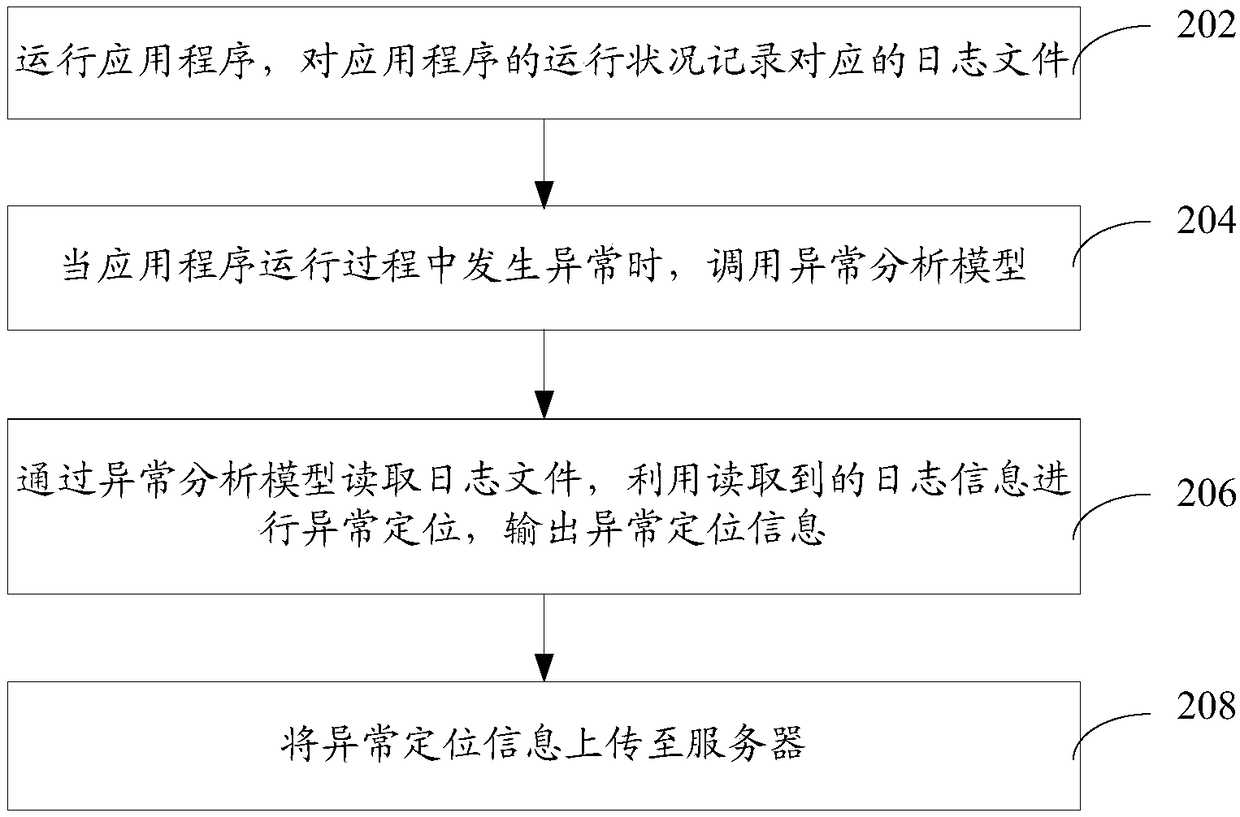
Application program exception analysis method and device, computer equipment and storage medium
InactiveCN108491320AImprove repair efficiencyReduce workloadSoftware testing/debuggingWorkloadApplication software
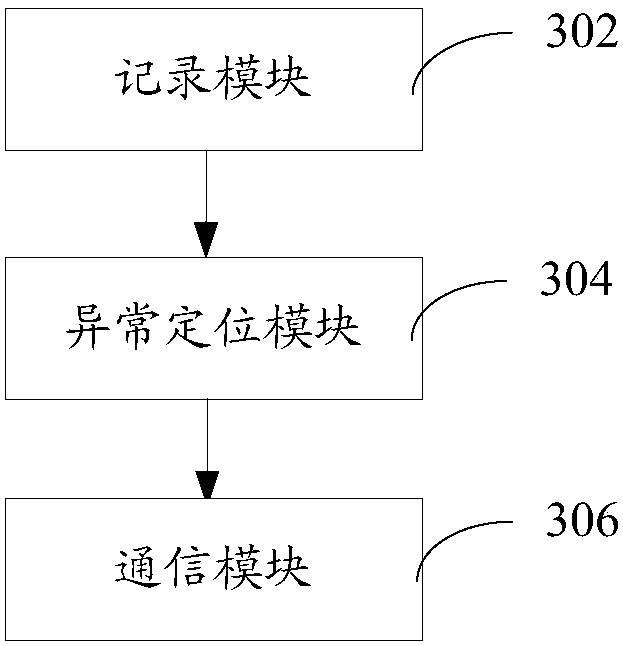
The invention relates to an application program exception analysis method and device, computer equipment and a storage medium. The method comprises the following steps of: operating an application program, and recording a corresponding log file for the operation condition of the application program; when exception occurs in the operation process of the application program, calling an exception analysis model; reading the log file through the exception analysis model, carrying out exception positioning by utilizing read log information, and outputting exception positioning information; and uploading the exception positioning information to a server. By adoption of the method, the workloads of developers can be effectively decreased and the application program recovery efficiency can be improved.
Owner:PINGAN PUHUI ENTERPRISE MANAGEMENT CO LTD
Browser abnormity processing method, device and system
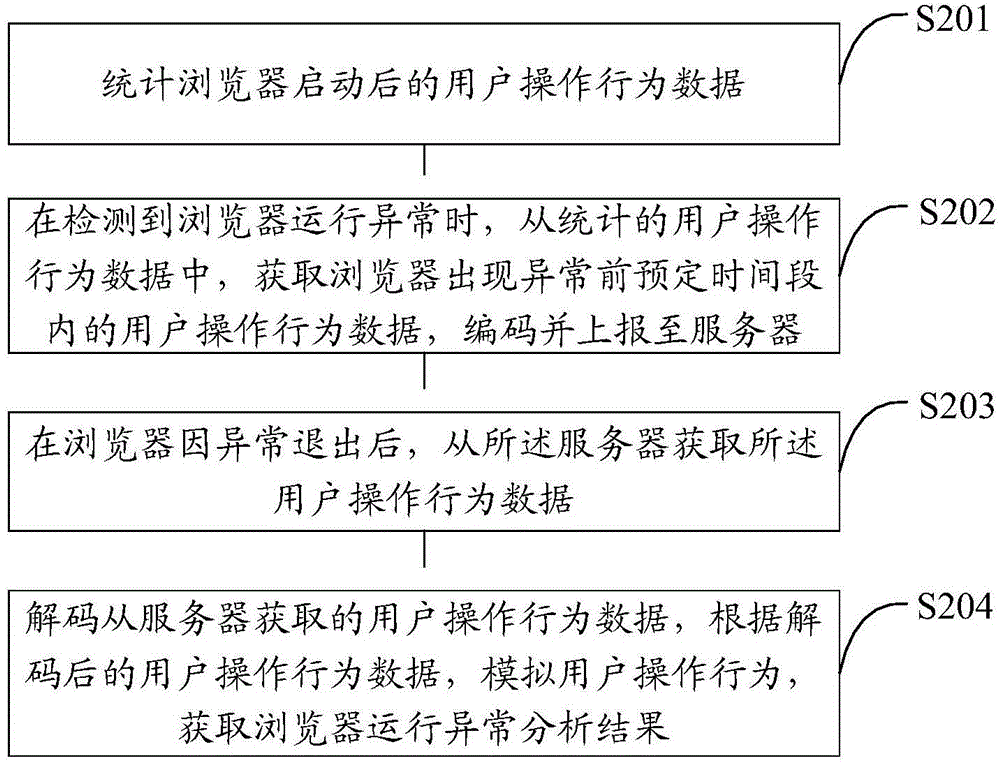
ActiveCN105320572AReduce uncertaintyFacilitate exception repairFault responseOperational behaviorComputer science
The invention relates to a browser abnormity processing method, device and system. The browser abnormity processing method comprises the steps that user operation behavior data after a browser is started are counted; when it is detected that browser operation is abnormal, the user operation behavior data in the predetermined time period before the browser shows an abnormity are acquired from the counted user operation behavior data and reported to a server; after the browser exits due to the abnormity, the user operation behavior data are acquired from the server; a user operation behavior is simulated according to the user operation behavior data to acquire a browser operation abnormity analysis result. According to the browser abnormity processing method, device and system, the user operation process can reappear to the maximum extent to restore the browser environment when the abnormity occurs, and the purposes of quickly reappearing and repairing the browser abnormity problem are achieved.
Owner:深圳市雅阅科技有限公司
Weighted convolutional autoencoder-long short-term memory network-based crowd anomaly detection method
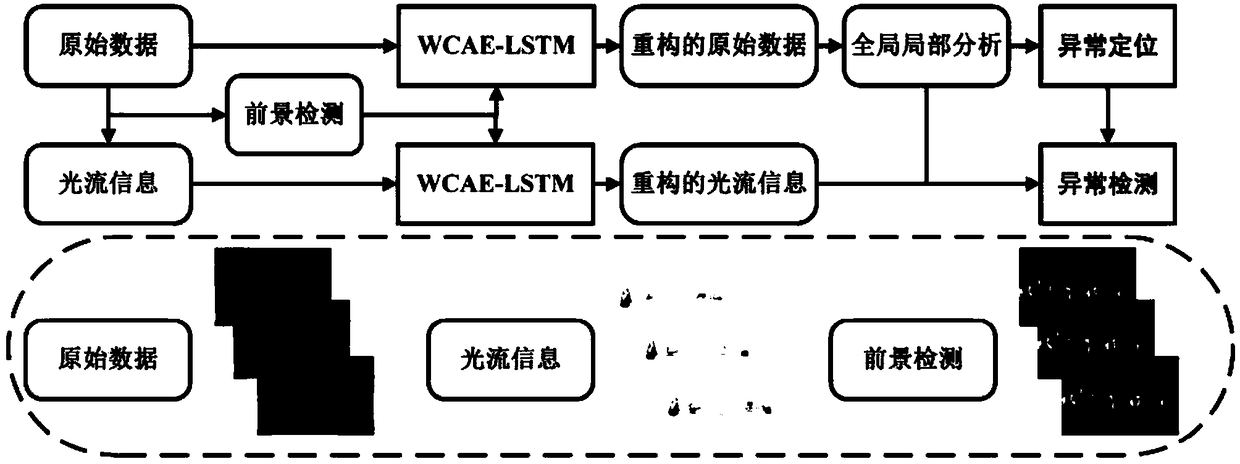
ActiveCN108805015ASuppress interferenceIncrease reconstruction errorCharacter and pattern recognitionNeural architecturesShort-term memoryOriginal data
The invention discloses a method for performing anomaly detection by a weighted convolutional autoencoder-long short-term memory network (WCAE-LSTM network). The method is devoted to perform anomaly detection and positioning by learning a generation model of a mobile pedestrian, thereby guaranteeing the public safety. The invention provides a novel double-channel framework, which learns generationmodes of an original data channel and a corresponding optical flow channel and reconstructs data by utilizing the WCAE-LSTM network, and performs the anomaly detection on the basis of a reconstruction error. In addition, for the problem of complex background, it is proposed that a sparse foreground and a low-rank background are separated by adopting modular robust principal component analysis decomposition; and a weighted Euclidean loss function is designed according to obtained background information, so that background noises are inhibited. The designed WCAE-LSTM network can not only perform the anomaly detection globally but also roughly locate an abnormal region locally; and through the joint consideration of global-local anomaly analysis and optical flow anomaly analysis results, finally robust and accurate detection of abnormal events is realized.
Owner:CHANGZHOU UNIV
Anomaly analysis method and device for network data
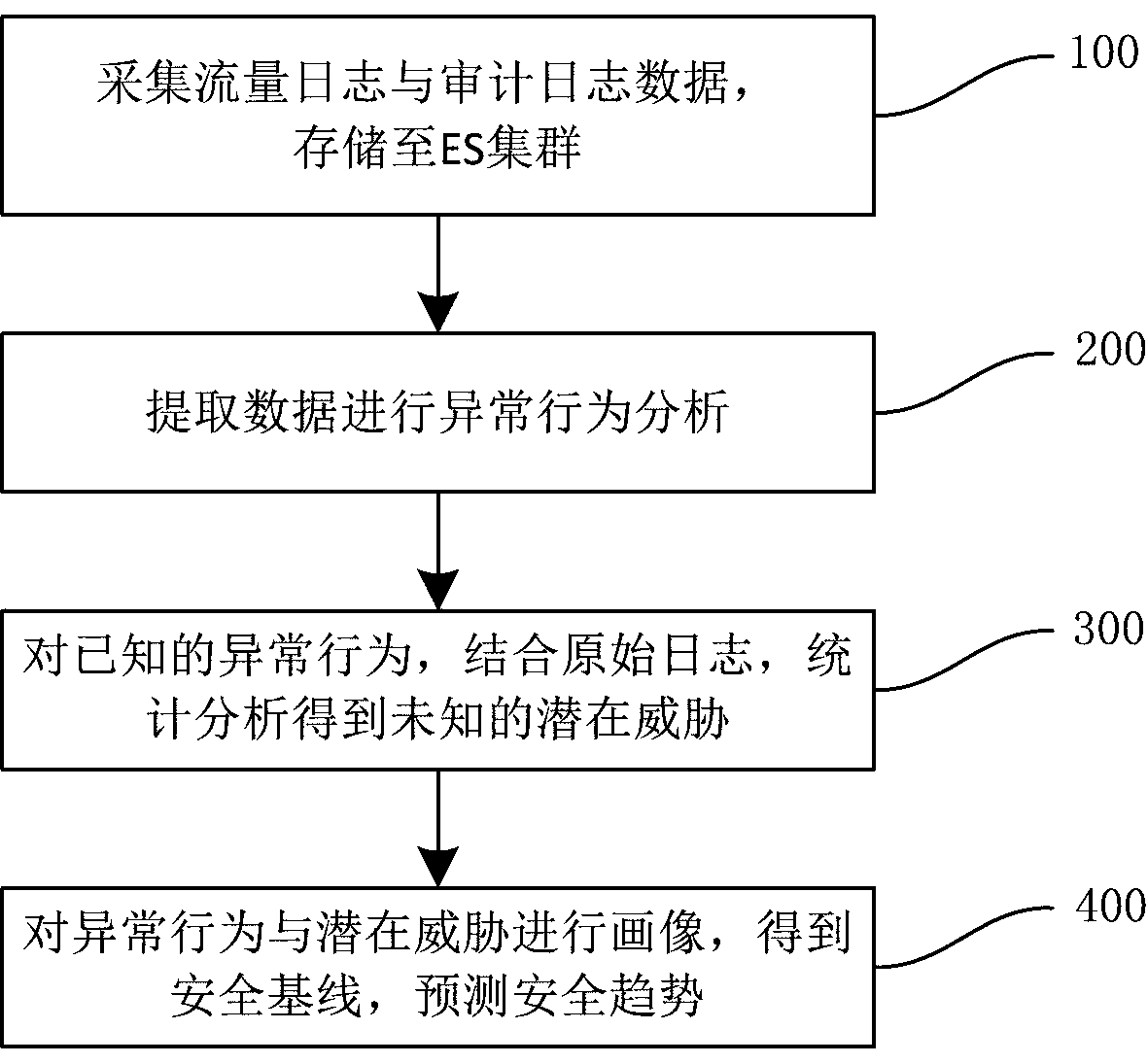
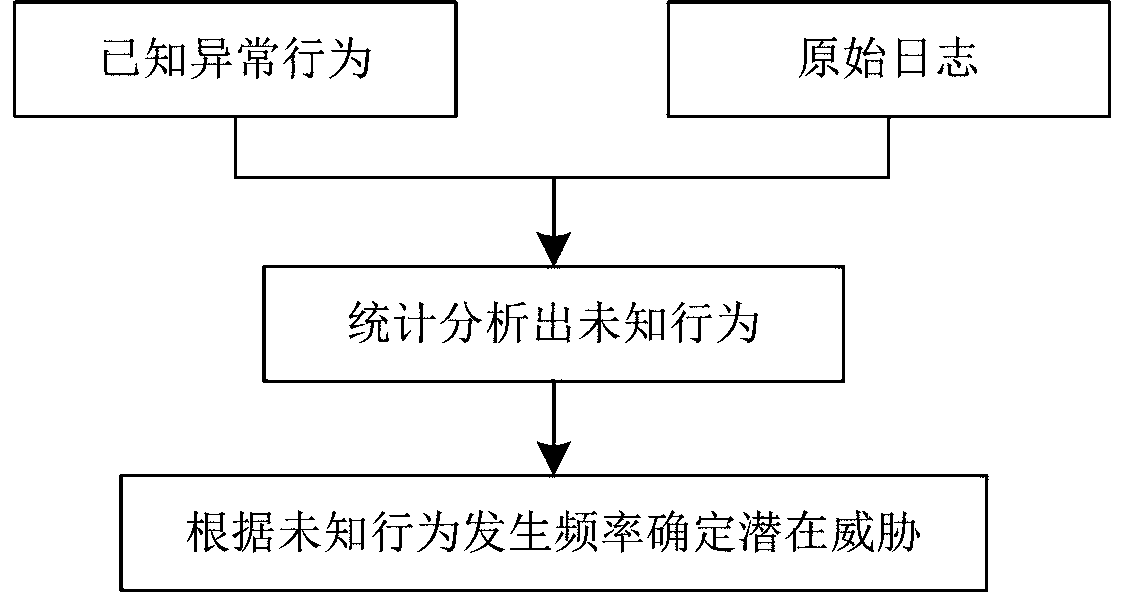
PendingCN111245793AImprove accuracyReduce occupancyCharacter and pattern recognitionTransmissionStatistical analysisEngineering
The invention discloses an anomaly analysis method and device for network data. The method comprises: in a microservice form, starting an exception analysis task in an interface calling or timing scheduling or periodic scheduling mode; obtaining traffic log and audit log data, determining categories of the traffic log and audit log data according to a classification model, executing machine learning or intelligence matching according to the categories to recognize abnormal behaviors, performing statistical analysis to obtain unknown potential threats, performing portrait drawing on the abnormal behaviors and the potential threats to generate a security baseline, and predicting a security trend based on the security baseline. On one hand, the running speed is increased, resource occupationis reduced, and on the other hand, the analysis result accuracy can be improved.
Owner:西安交大捷普网络科技有限公司
Distribution iterative data processing program abnormity detection and diagnosis method
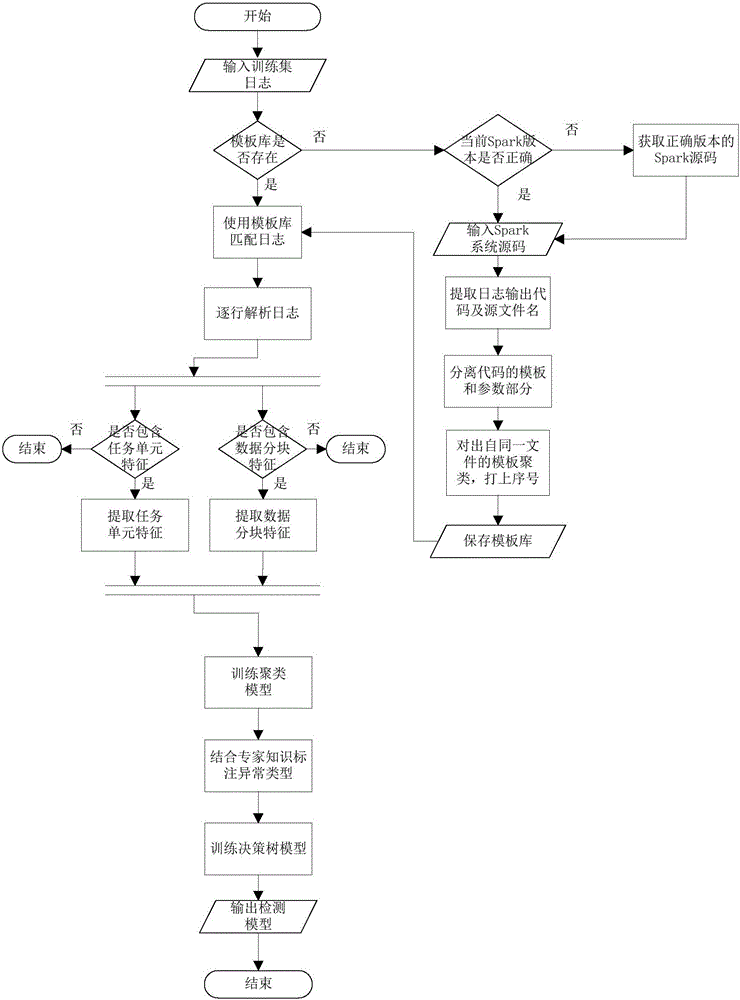
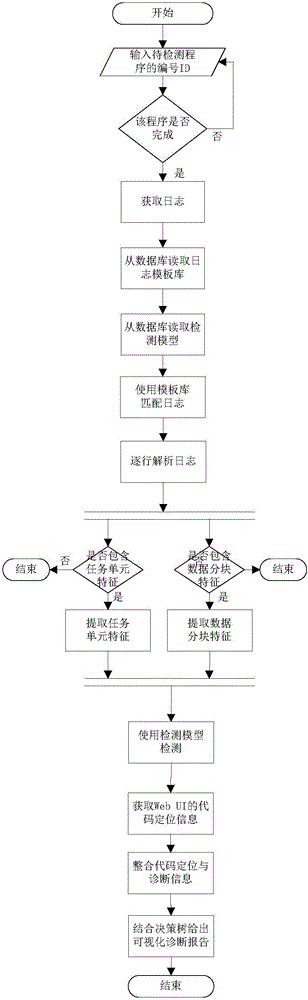
ActiveCN105975604AEfficient matchingEfficient miningFault responseSpecial data processing applicationsFeature vectorAnomaly detection
The invention relates to a distribution iterative data processing program abnormity detection and diagnosis method, and belongs to the computer data management technical field; the method comprises two stages of model training and detection diagnosis; firstly extracting a log template database based on source code analysis, then respectively extracting characteristic vectors corresponding to data partitions and task units from mass log data according to the template database, carrying out abnormity detection model training, then combining field knowledge to tag abnormity types, using trained model to carry out abnormity detection for future calculating tasks, using a visualization interface to display abnormity analysis, associating characteristic units with code positioning information, and finally mapping the abnormal characteristic unit into program codes so as to realize program abnormity detection and diagnosis. The method can detect and diagnose mainly abnormity of the distribution iterative data processing program from multi angles, is direct and easy to use, good in interactivity, thus greatly reducing user time for program abnormity detection and diagnosis.
Owner:TSINGHUA UNIV
Internal threat detection system based on mining of business process model and detection method thereof
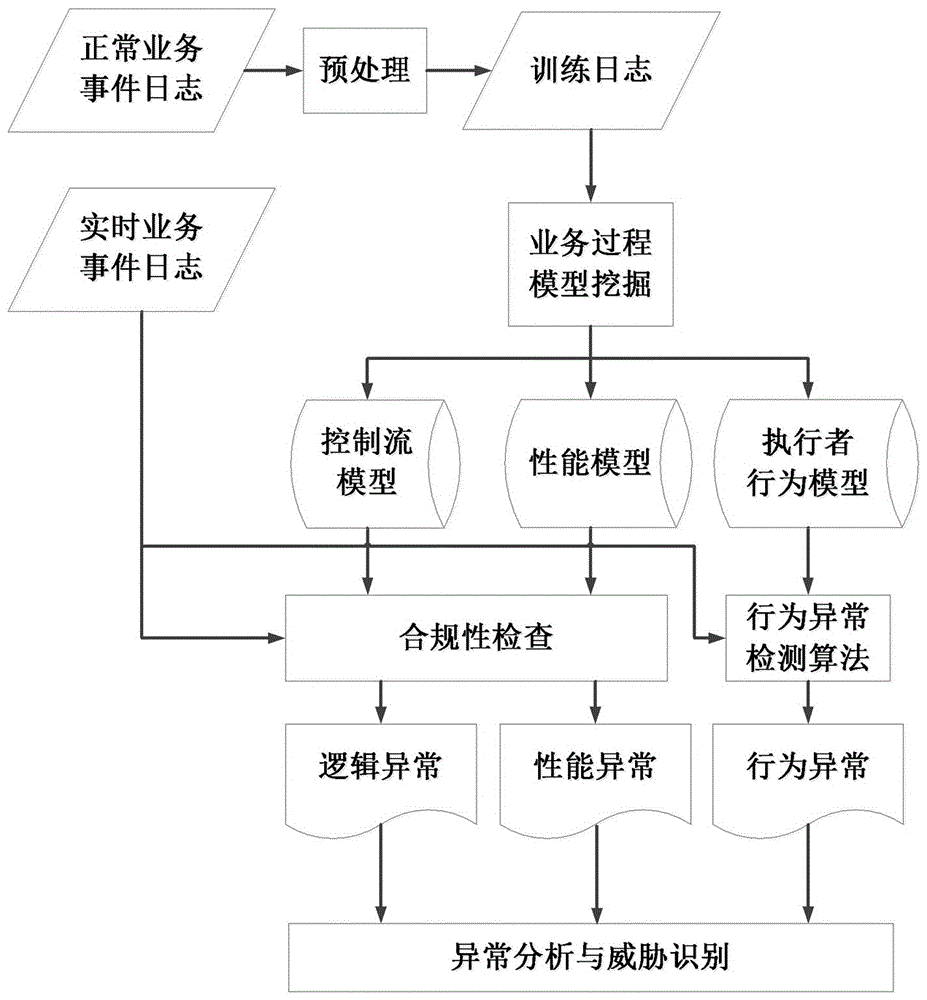
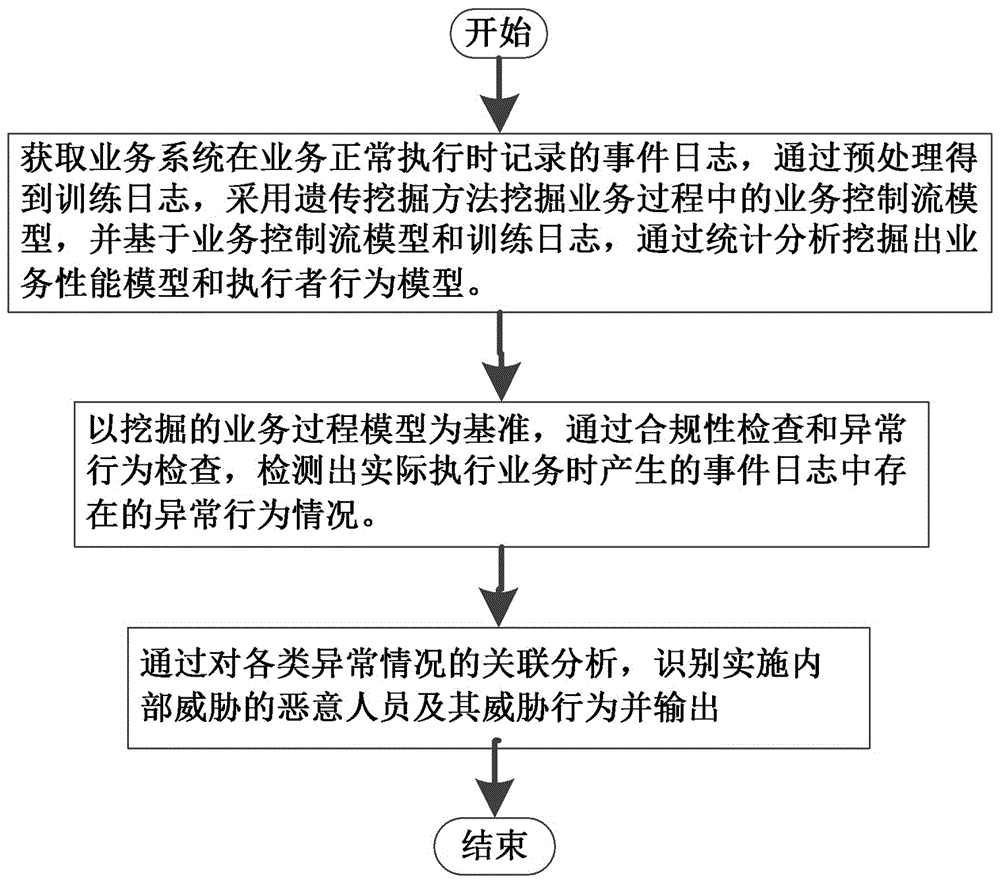
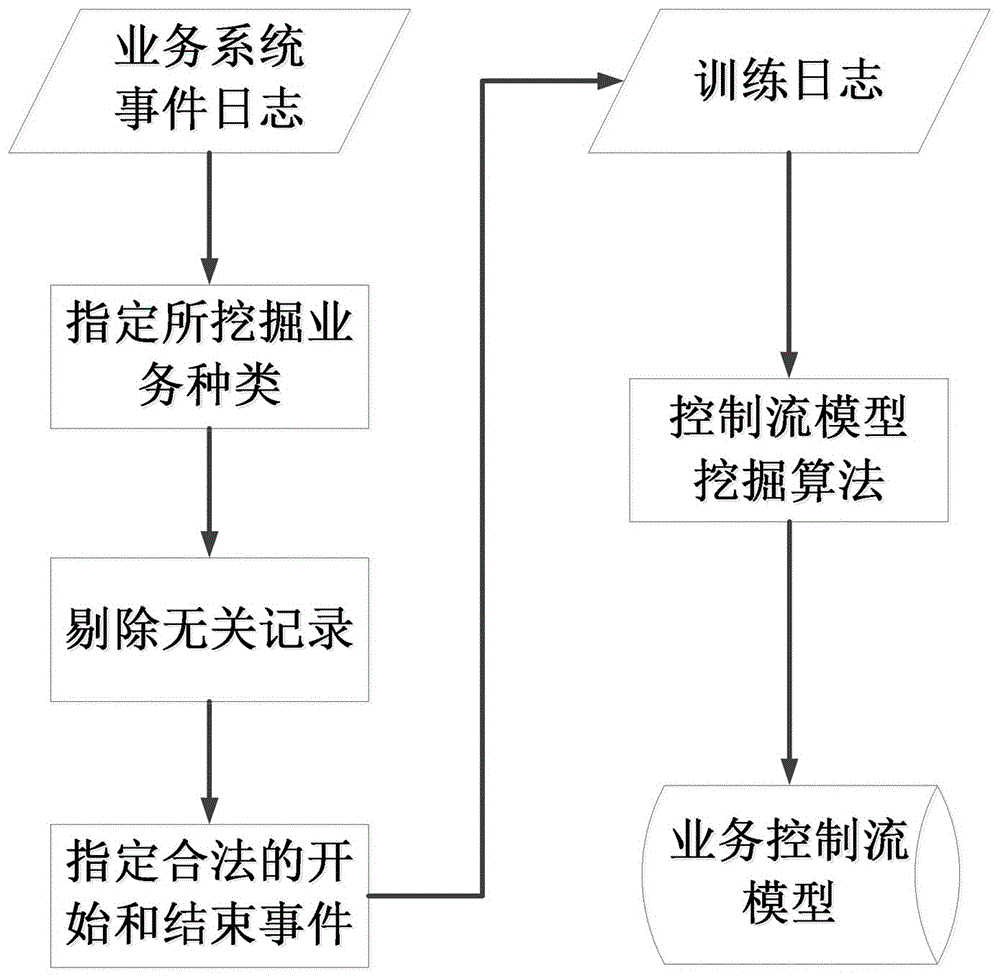
ActiveCN106209893AEnsure information securityNormal operation impactTransmissionSpecial data processing applicationsControl flowBusiness activities
The invention relates to an internal threat detection system based on mining of a business process model and a detection method thereof. The detection system comprises a model mining module, an abnormality detection module and an abnormality analysis model, wherein the model mining module implements model mining according to an event log of each business event in a business system, and thus acquires a business control flow model, a business performance model and an executor behavior model; the abnormality detection module detects logic abnormality, performance abnormality and behavior abnormality of the event log generated during a real-time operation process of a business activity according to the model mining module; and the abnormality analysis model parses a detection result of the abnormality detection module, recognizes execution information about implementation of an internal threat and outputs the information. According to the internal threat detection system based on mining of the business process model established in the invention, the internal threat behavior existing in the business execution process is effectively detected, a powerful support is provided for enterprises and various organizations to prevent the internal threat, and information security of enterprises and organizations is effectively ensured.
Owner:THE PLA INFORMATION ENG UNIV
Remote data acquisition and analysis system for filling production line and abnormity analysis method thereof
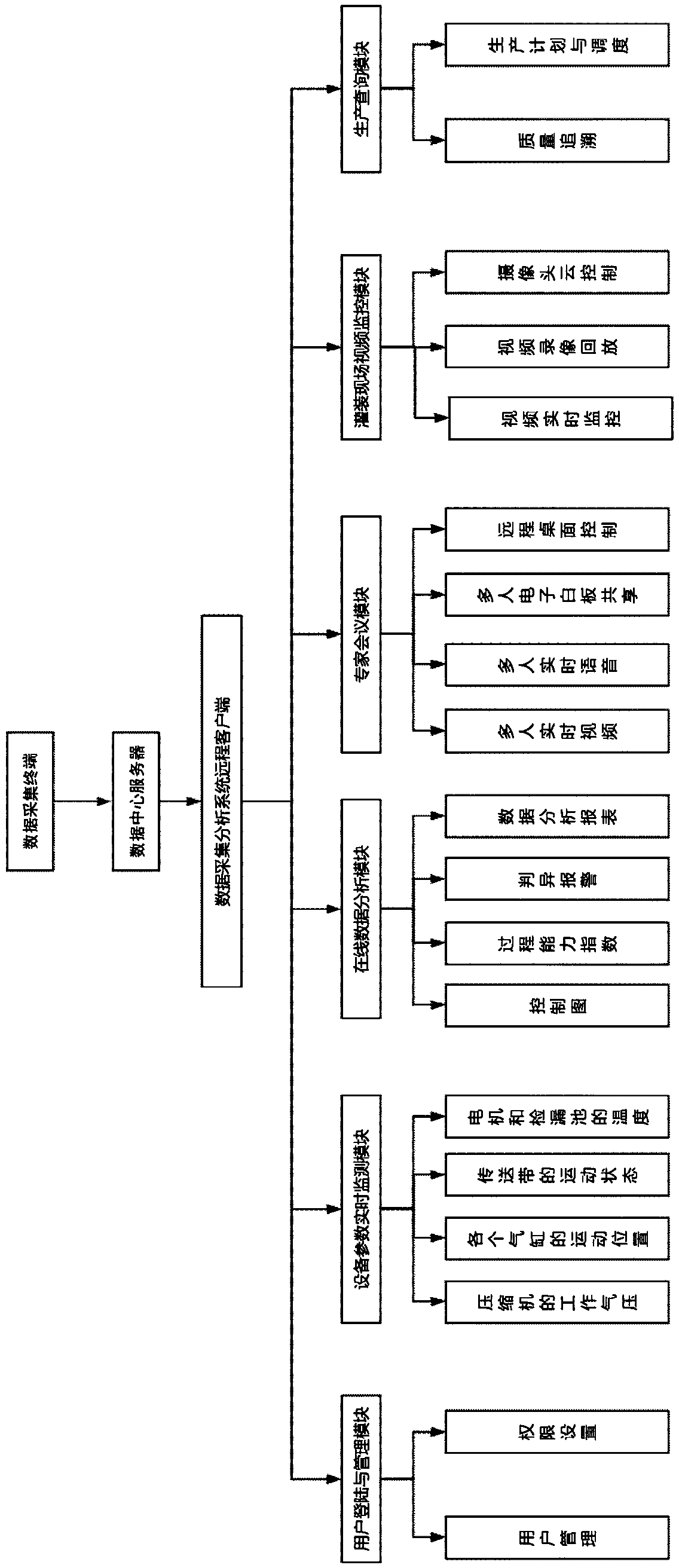
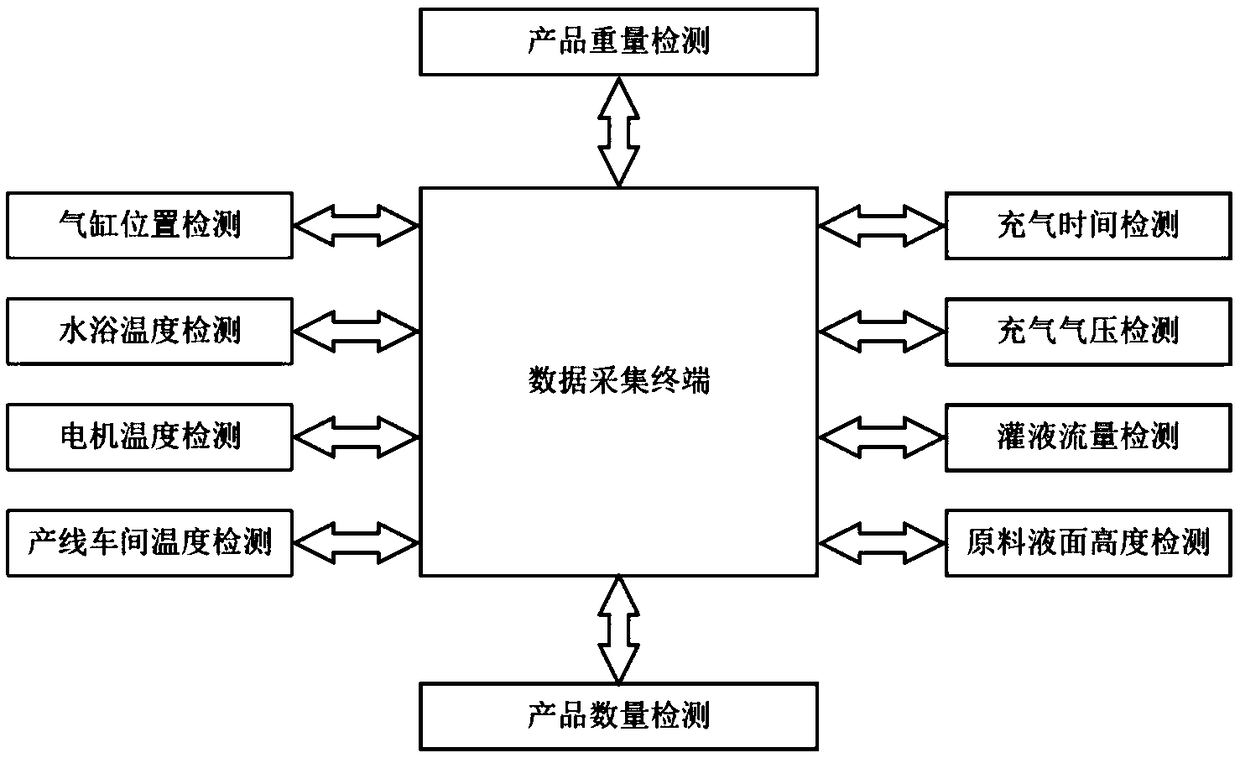
ActiveCN109086999ARealize analysisRealize evaluationResourcesNeural learning methodsProduction lineVideo monitoring
The invention discloses a remote data acquisition and analysis system for a filling production line, including a data acquisition terminal for real-time on-line acquisition of production characteristic data, a data center server for transmitting and storing production characteristic data and a remote client of a data collection and analysis system for processing the production characteristic data,wherein the remote client of the data collection and analysis system reads the production characteristic data from the data center server and analyzes the production characteristic data; The remote client of the data acquisition and analysis system comprises a user login and management module, a device parameter real-time monitoring module, an on-line data analysis module, an expert meeting module, a filling scene video monitoring module and a production inquiry module. The remote client comprises a user login and management module, a device parameter real-time monitoring module, an on-line data analysis module, an expert meeting module, a filling scene video monitoring module and a production inquiry module. The system can collect the data of every working link of the filling productionline, monitor the production process of the filling production line in real time and remotely, and analyze the quality of the filling product on-line, which is helpful to improve the qualified rate and quality of the product and save the cost of fault diagnosis.
Owner:SOUTHEAST UNIV +1
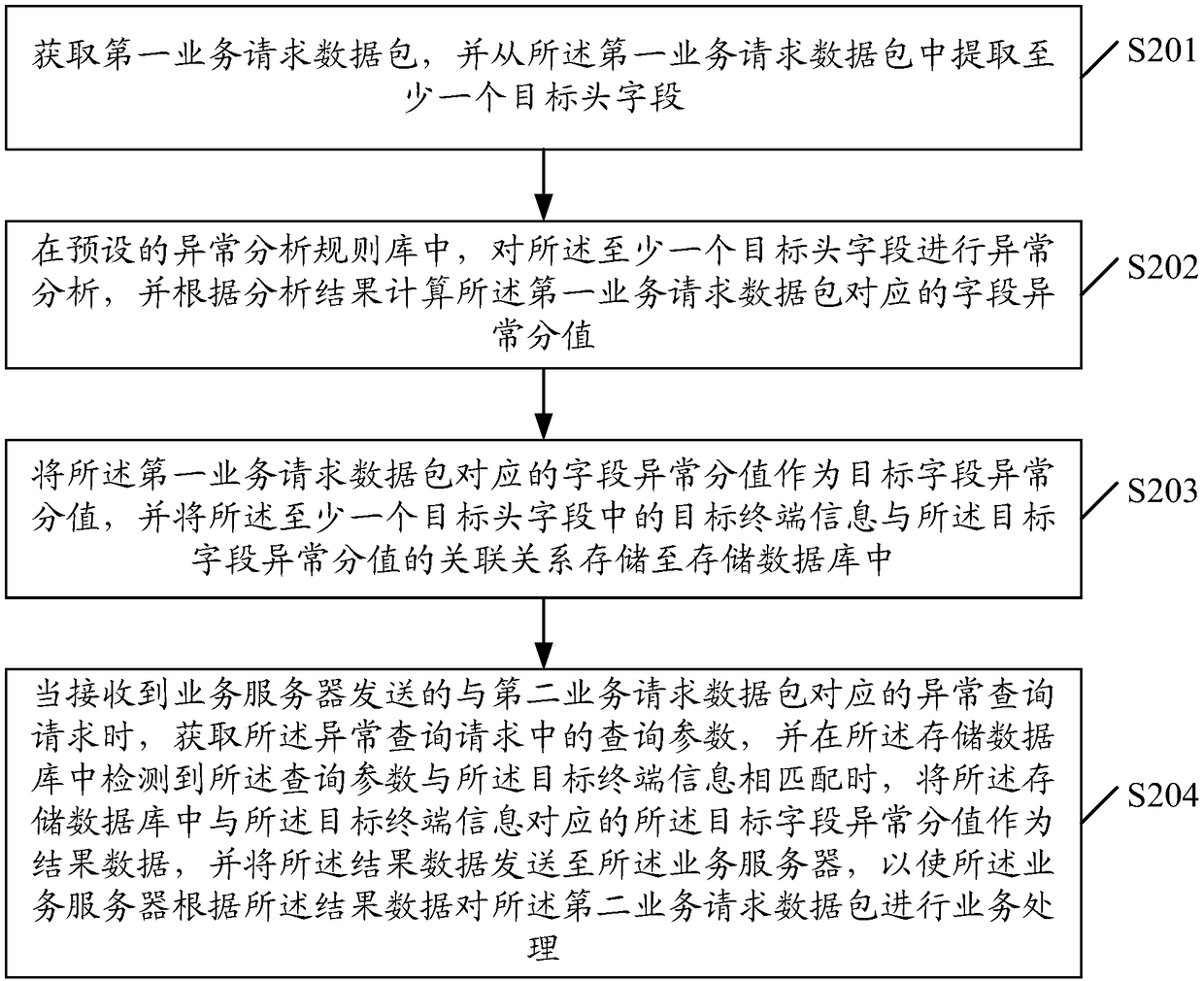
Data detection method and device
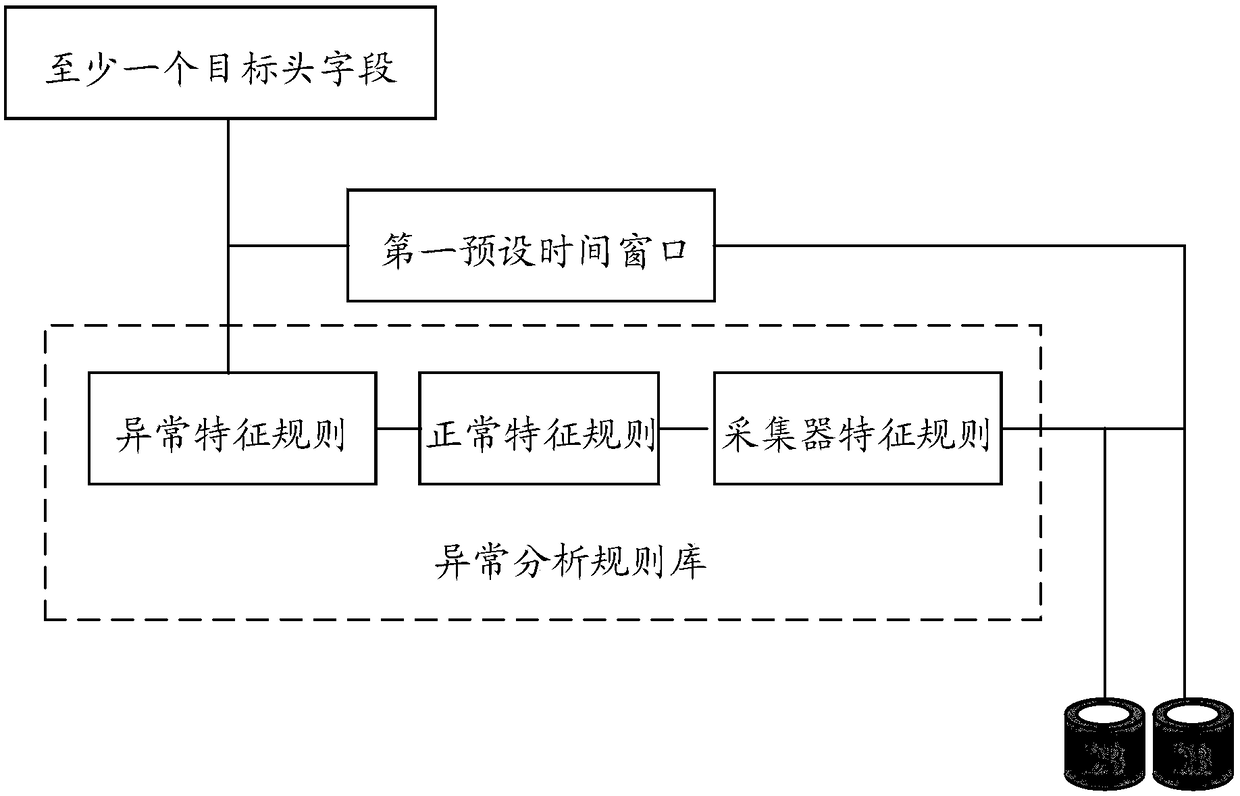
ActiveCN108737333AReduce false positive rateReduce the probability of misjudgmentTransmissionNetwork packetData mining
The embodiment of the invention discloses a data detection method and a data detection device. The method comprises the steps of extracting at least one target head field from a first service requestdata packet, performing exception analysis in a preset exception analysis rule library, computing a field exception score corresponding to the first service request data packet according to an analysis result to serve as a target field exception score, and storing an association relation between target terminal information in each target head field and the target field exception score into a storage database; and when an exception query request sent by a service server is received, acquiring a query parameter in the exception query request, and when the query parameter is detected to be matched with the target terminal information in the storage database, using the target field exception score corresponding to the target terminal information as result data to be sent to the service server.By using the method and device provided by the invention, the misjudgment rate and the missing rate of malicious crawlers can be reduced, and network request interruption during the normal service process in the service server is avoided.
Owner:TENCENT TECH (SHENZHEN) CO LTD
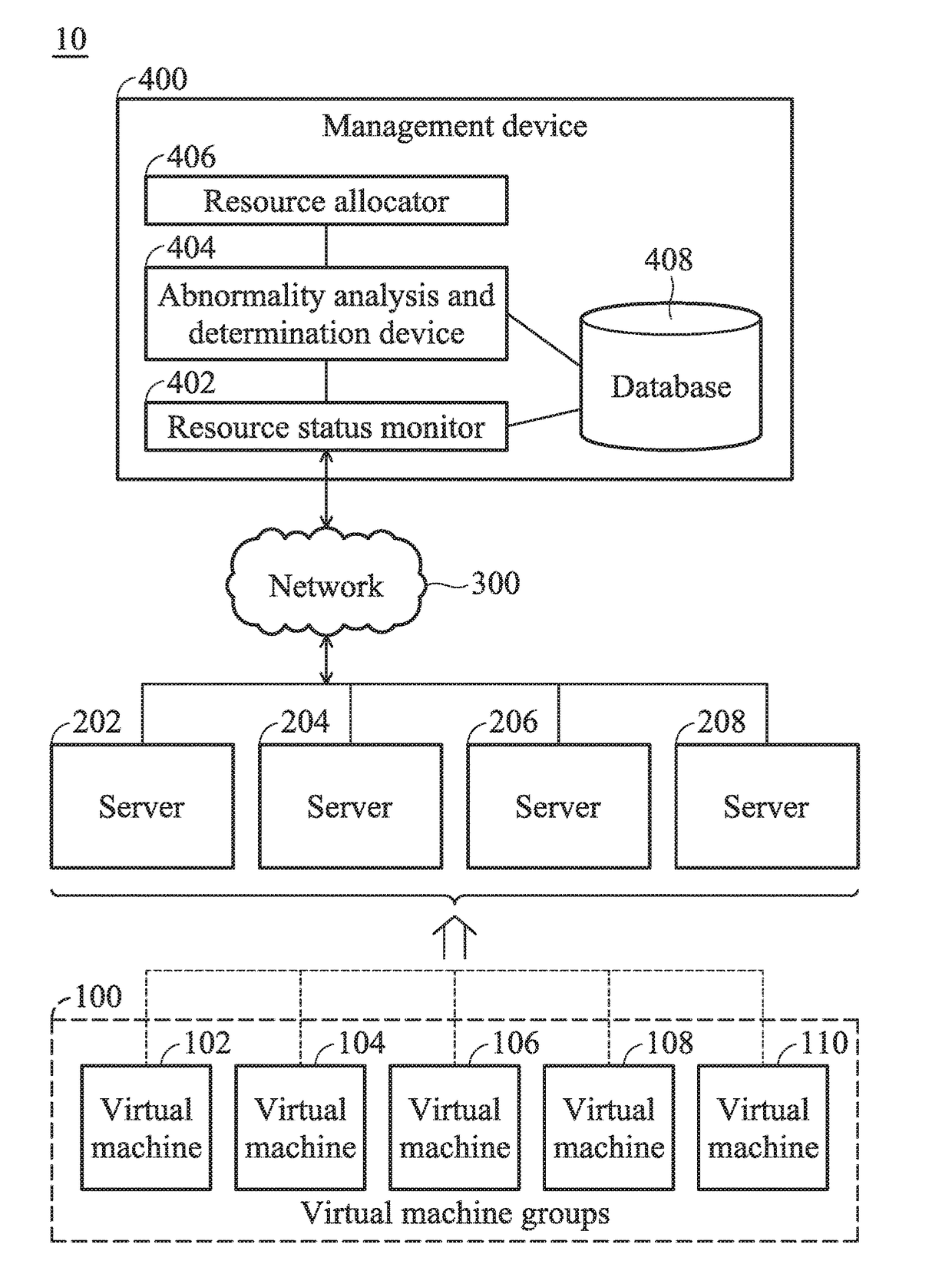
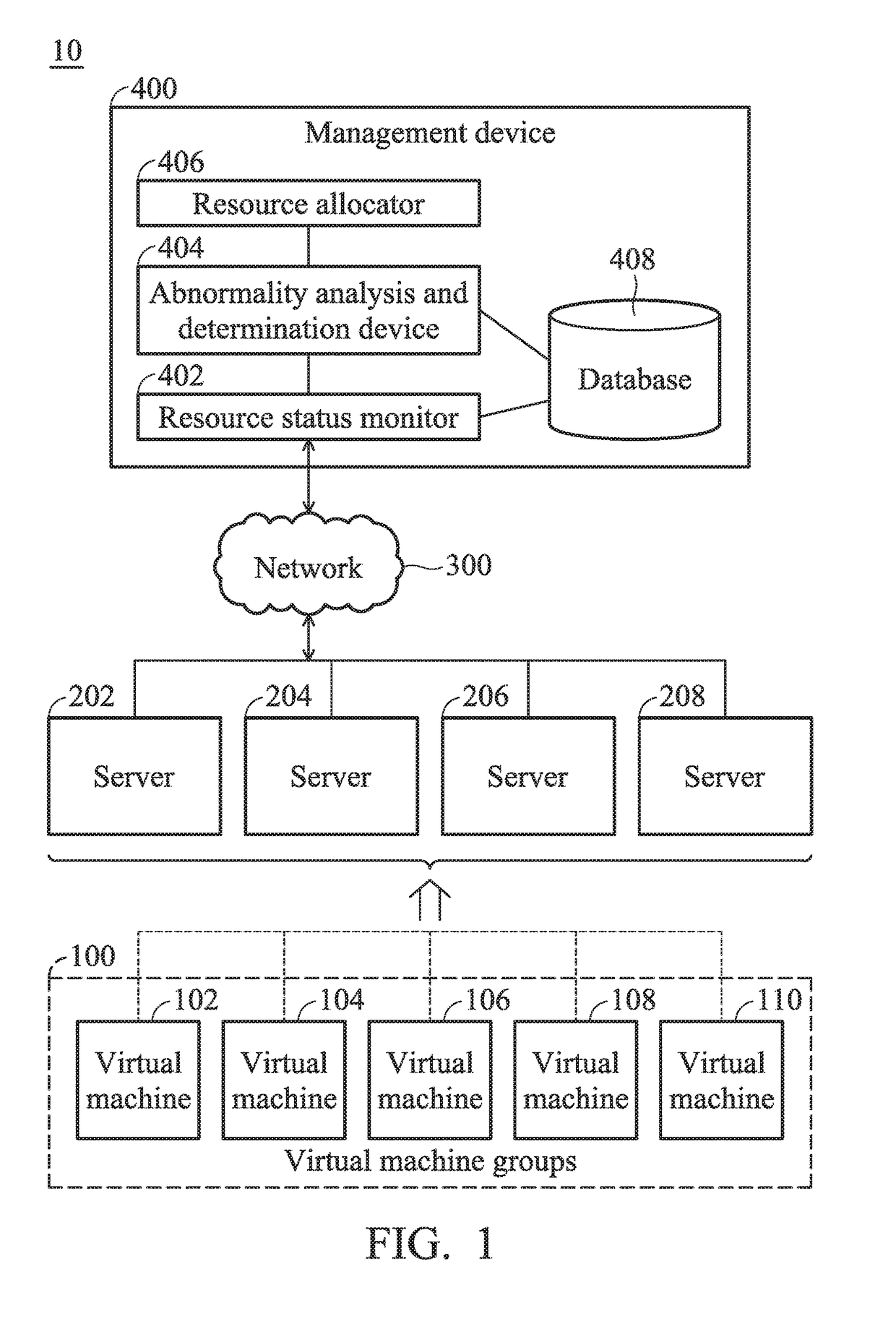
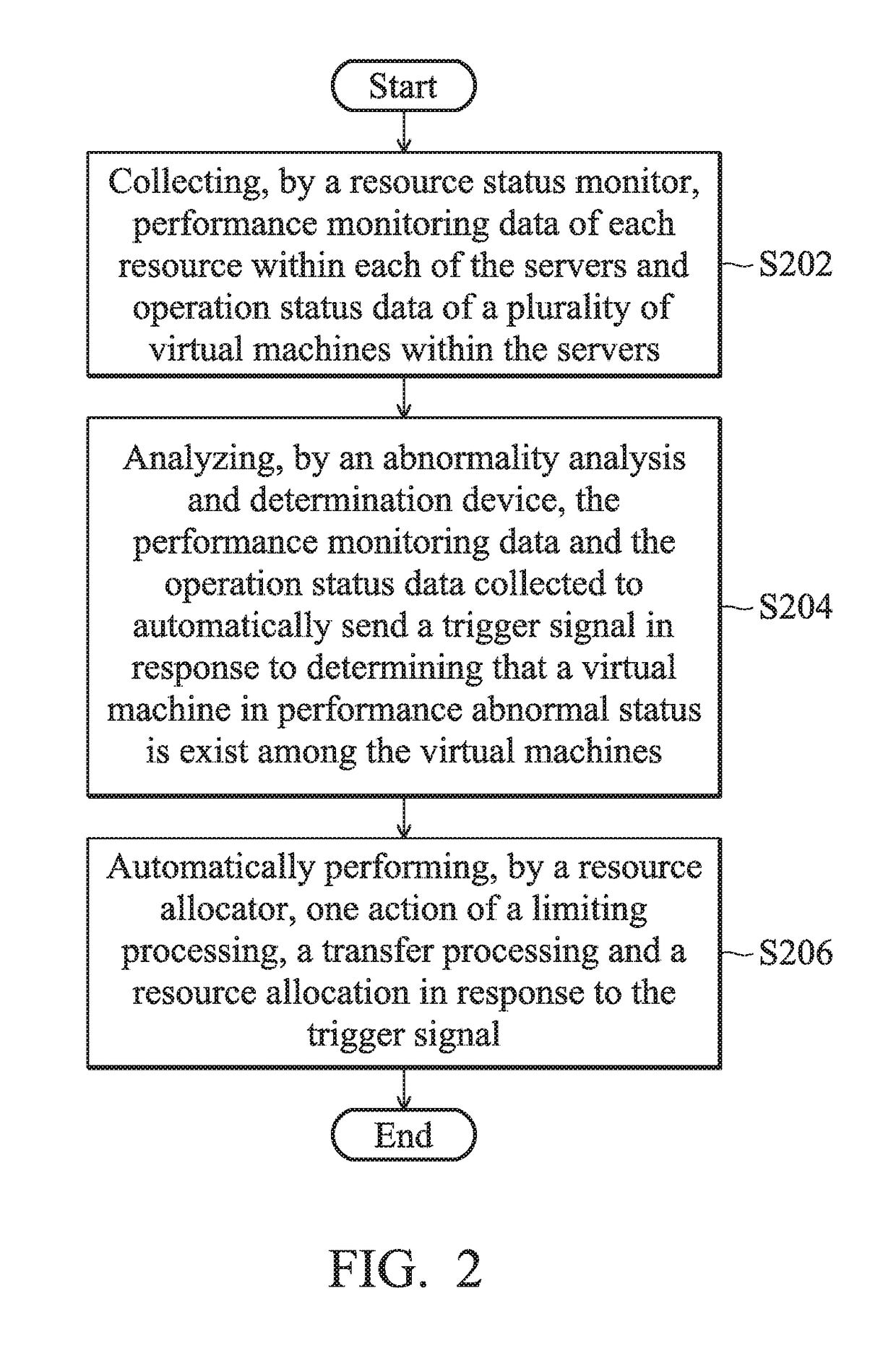
Management systems for managing resources of servers and management methods thereof
A management method for management of resources of servers is provided, the method including the step of: collecting, by a resource status monitor, performance monitoring data of each resource within each of the servers and operation status data of a plurality of virtual machines within the servers; analyzing, by an abnormality analysis and determination device, the performance monitoring data and the operation status data collected to automatically send a trigger signal in response to determining that a virtual machine in performance abnormal status is exist among the virtual machines; and automatically performing, by a resource allocator, a processing on the virtual machine in performance abnormal status in response to the trigger signal, wherein the processing is at least one action of a limiting processing, a transfer processing and a resource allocation.
Owner:QUANTA COMPUTER INC
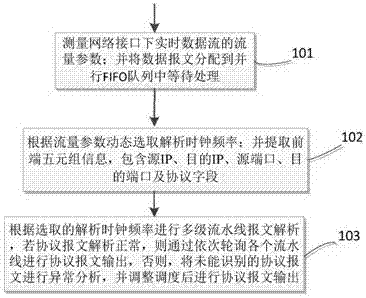
Message analysis method and device based on FPGA hardware parallel pipelines
ActiveCN106961445AEasy constructionFast transferData switching networksStructure of Management InformationOperating frequency
The invention relates to a message analysis method and device based on FPGA hardware parallel pipelines. The method comprises the steps of measuring traffic parameters of real-time data streams under network interfaces; allocating data messages to parallel FIFO queues for processing; dynamically selecting analysis clock frequencies according to the traffic parameters; extracting front end quintuple information; and carrying out multilevel pipeline message analysis according to the selected analysis clock frequencies, if the protocol message analysis is normal, polling each pipeline in sequence for protocol message output, otherwise, carrying out abnormality analysis on the unidentified protocol messages, adjusting scheduling and then carrying out protocol message output. According to the method and the device, on the basis of a high-speed parallel pipeline structure, a message analysis rate is improved; working frequencies are dynamically changed through traffic detection; the system power consumption cost is greatly reduced; a solidified and sealed mode of a traditional network is broken through; a utilization rate of link resources is improved; and the basic network construction cost is reduced.
Owner:THE PLA INFORMATION ENG UNIV
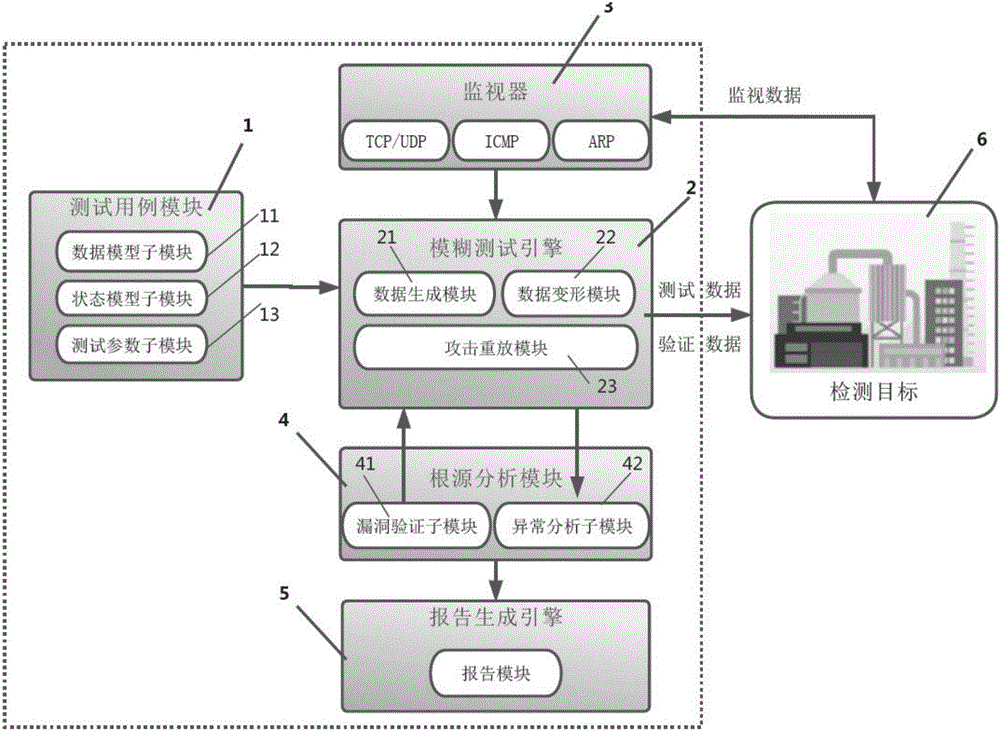
Industrial control network security detection system and detection method
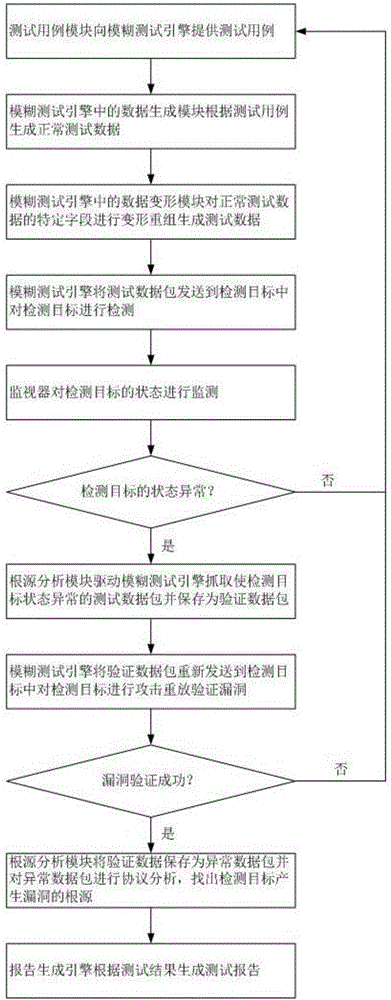
PendingCN106487813AImprove the protective effectImprove applicabilityData switching networksControl networkSecurity bug
The invention relates to the field of industrial control network security vulnerability detection. In order to achieve thorough and comprehensive detection of industrial control network security vulnerabilities, effectively discover unknown security vulnerabilities, and find out a root cause of the industrial control network security vulnerabilities, the invention provides an industrial control network security detection system, wherein a test case module provides test cases for a fuzzy test engine; the fuzzy test engine generates a test data packet and performs security detection on a detection target, and obtains test results including "normal", "other" and "suspected vulnerabilities"; a monitor monitors the state of the detection target in real time; a root cause analysis module drives the fuzzy test engine to perform attack replay, after the vulnerability verification is successful, performs abnormality analysis on an abnormal data packet, and obtains the root cause of the security vulnerabilities; and a report generation engine generates a test report. The industrial control network security detection system provided by the invention is used for carrying out security detection, and the detection is thorough and comprehensive, which can effectively find the unknown security vulnerabilities and obtain the root cause of the security vulnerabilities.
Owner:BEIJING KUANGEN NETWORK TECH
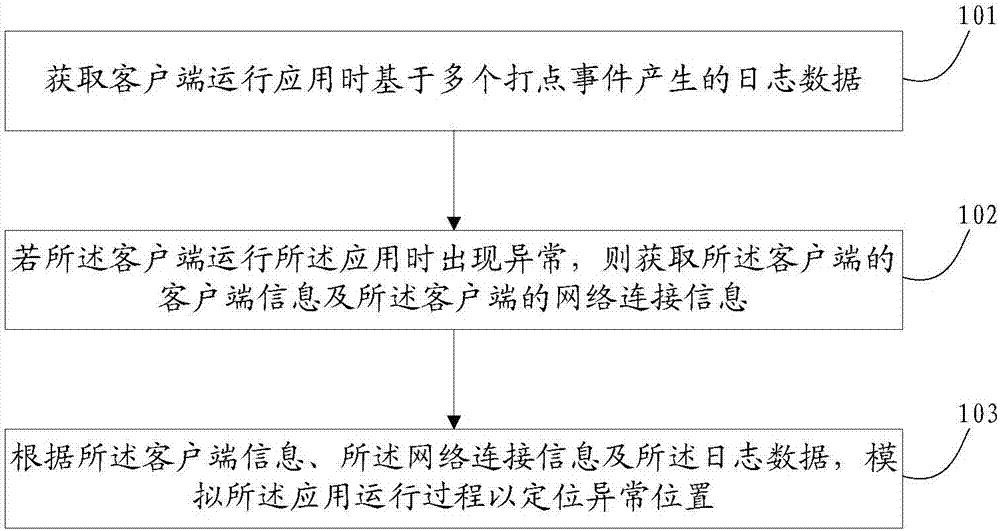
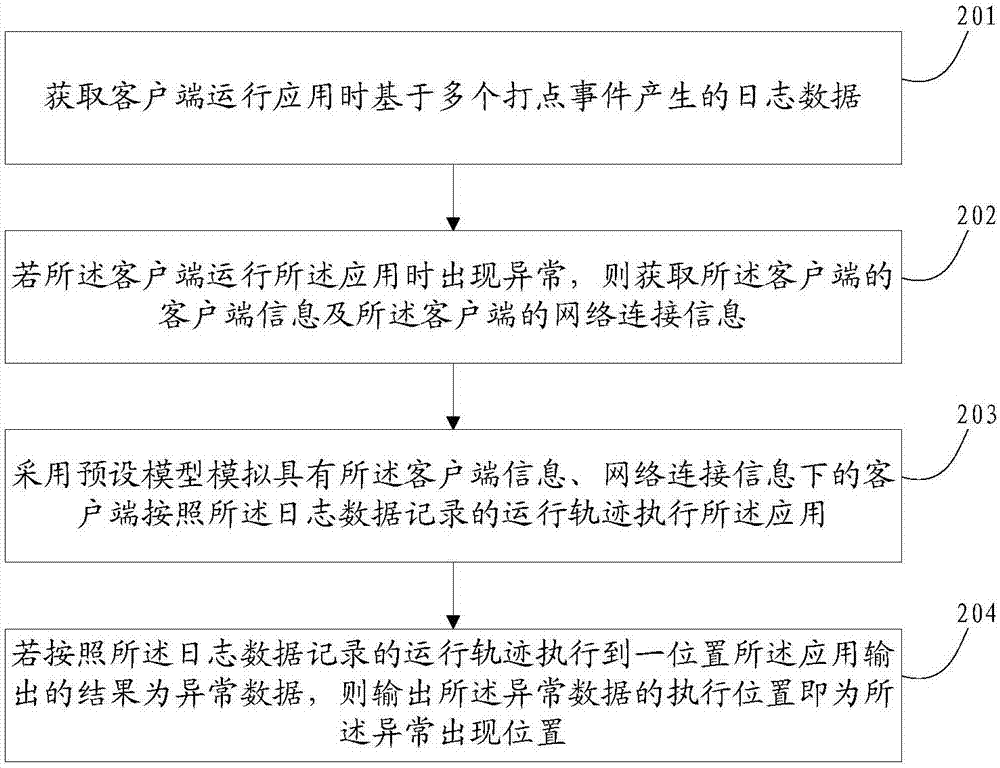
Method and device for analyzing operation anomaly of client application
ActiveCN107040816AImprove accuracyHigh precisionSelective content distributionData switching networksAbnormal positionsNetwork connection
The invention discloses a method and device for analyzing operation anomaly of a client application, and belongs to the technical field of Internet broadcast live. The method comprises the following steps: acquiring log data generated based on multiple dotting events when a client runs the application; if the anomaly occurs when the client runs the application, then acquiring client information of the client and network connection information of the client; and simulating the application running process to locate an abnormal position according to the client information, the network connection and the log data. The embodiment of the invention can locate a fault position of the client and analyze the cause of the fault, so as to solve the problem subsequently specifically.
Owner:北京龙之心科技有限公司
Business monitoring method and device
InactiveCN101562540AEffectively locate impactReduce the difficulty of positioningData switching networksLocation EquipmentOperating system
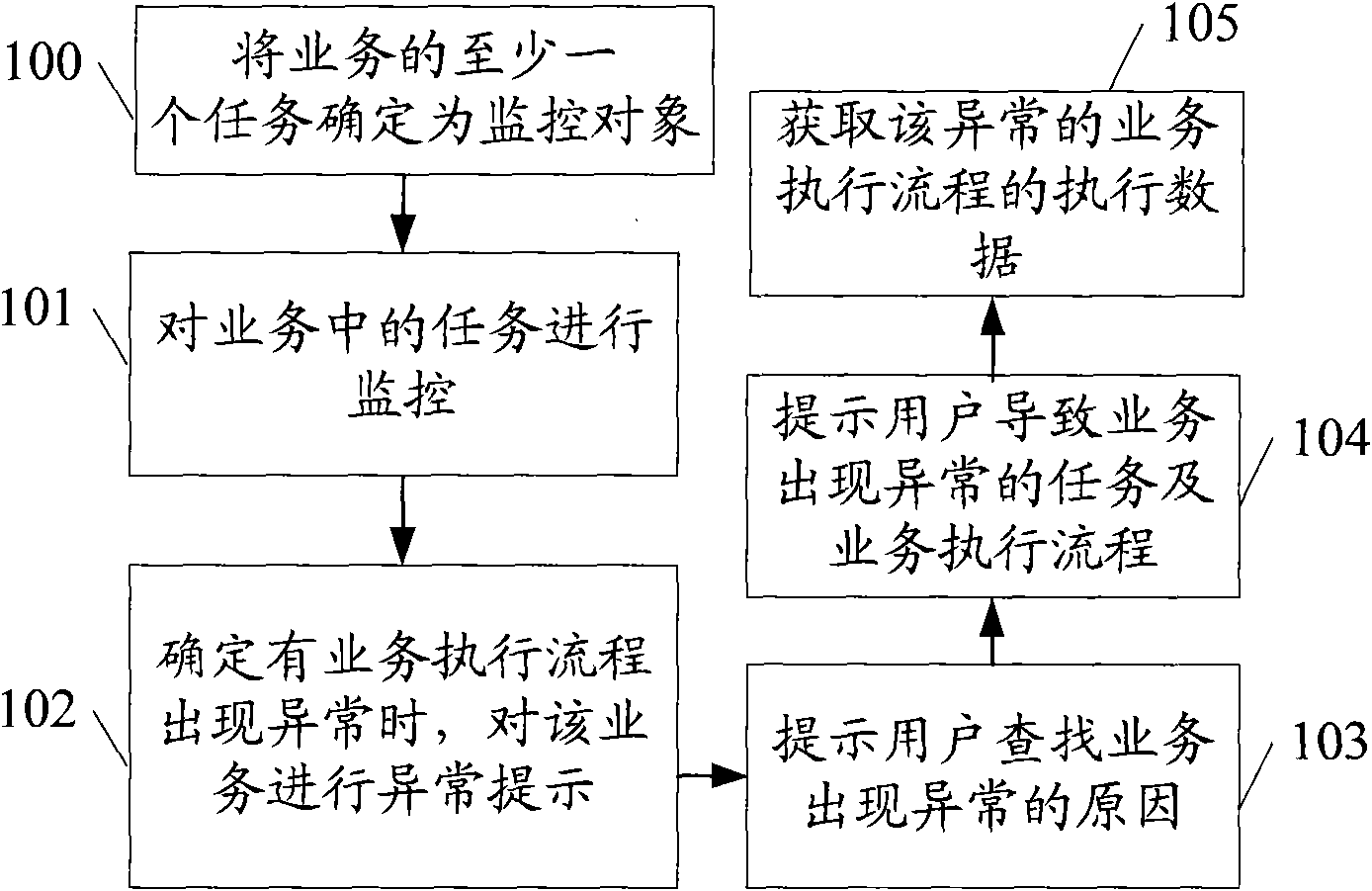
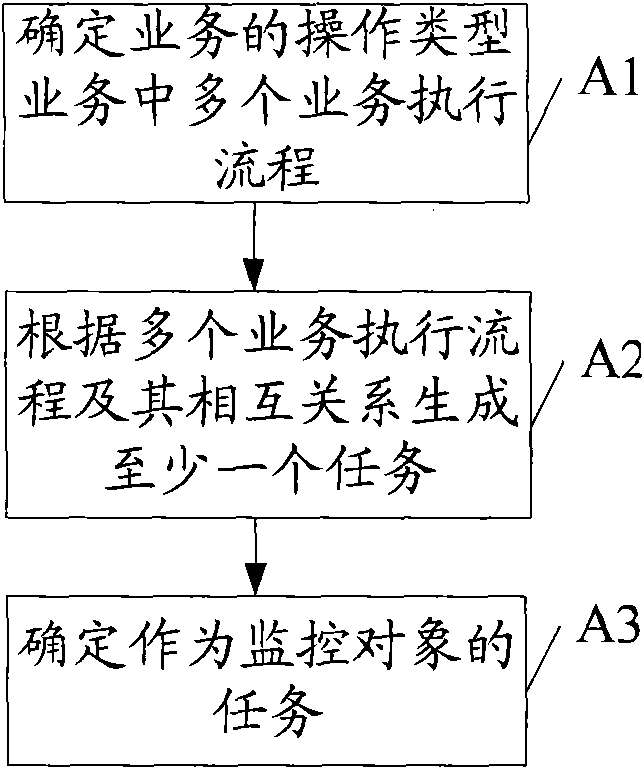
Owner:HUAWEI TECH CO LTD
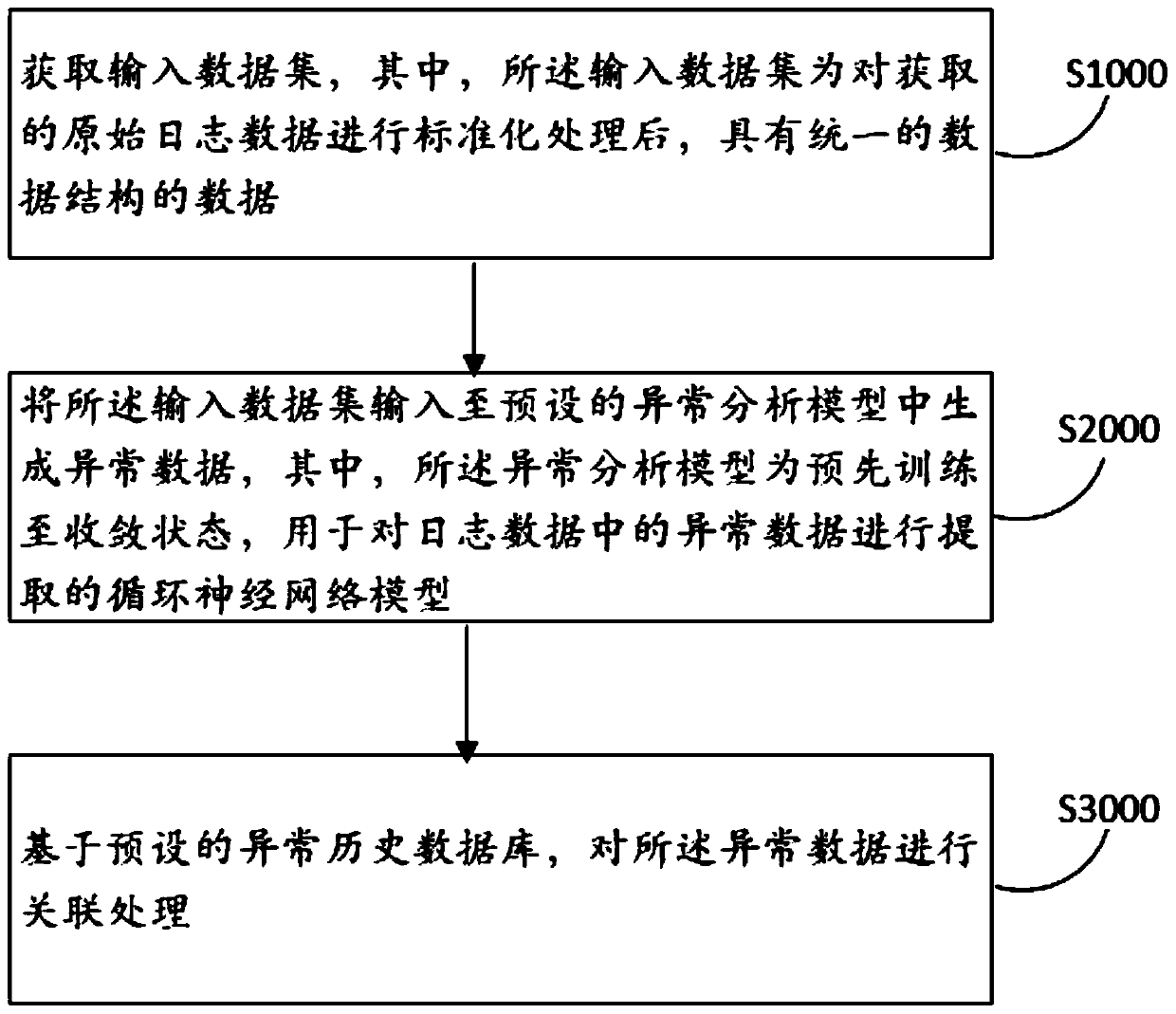
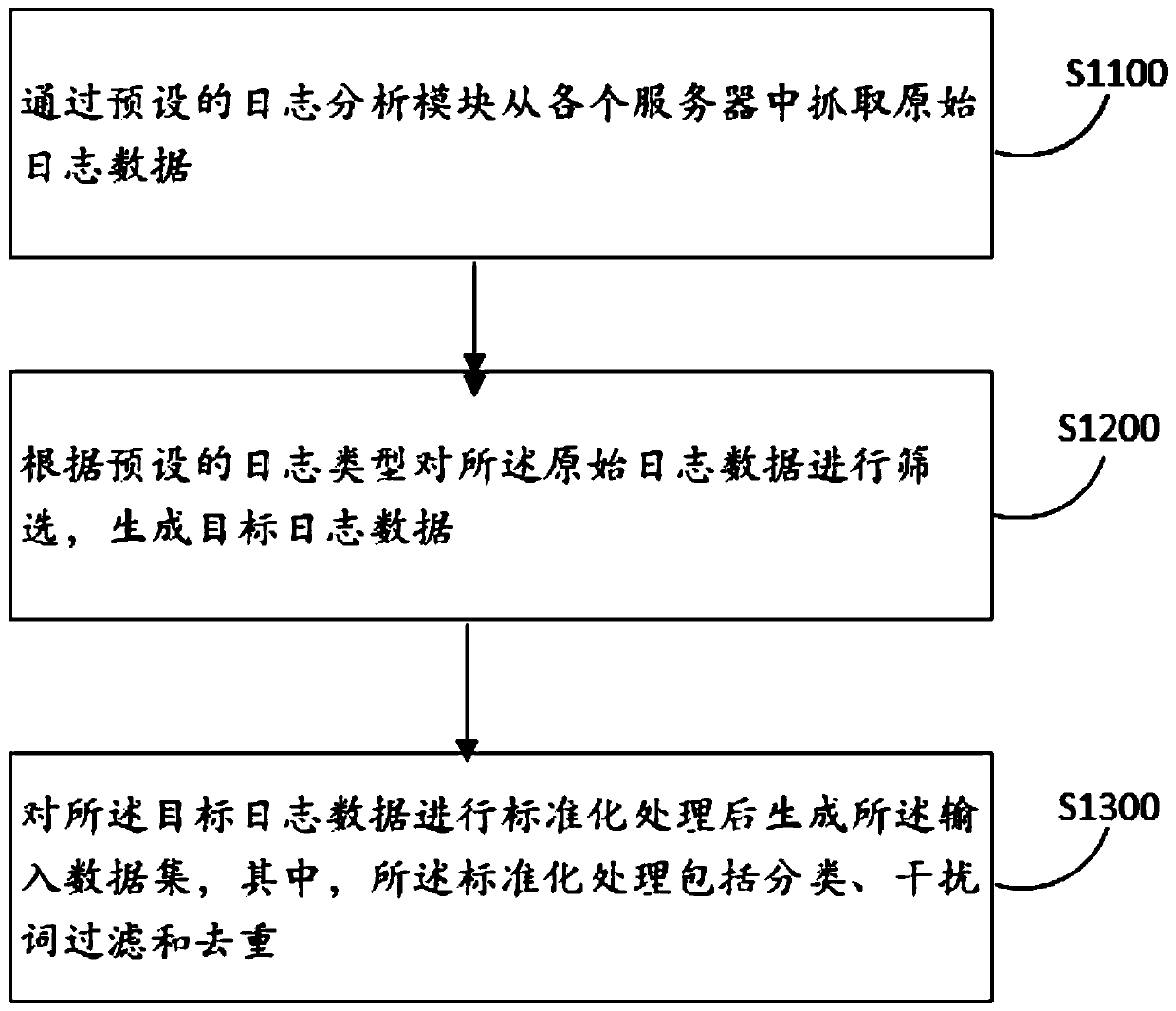
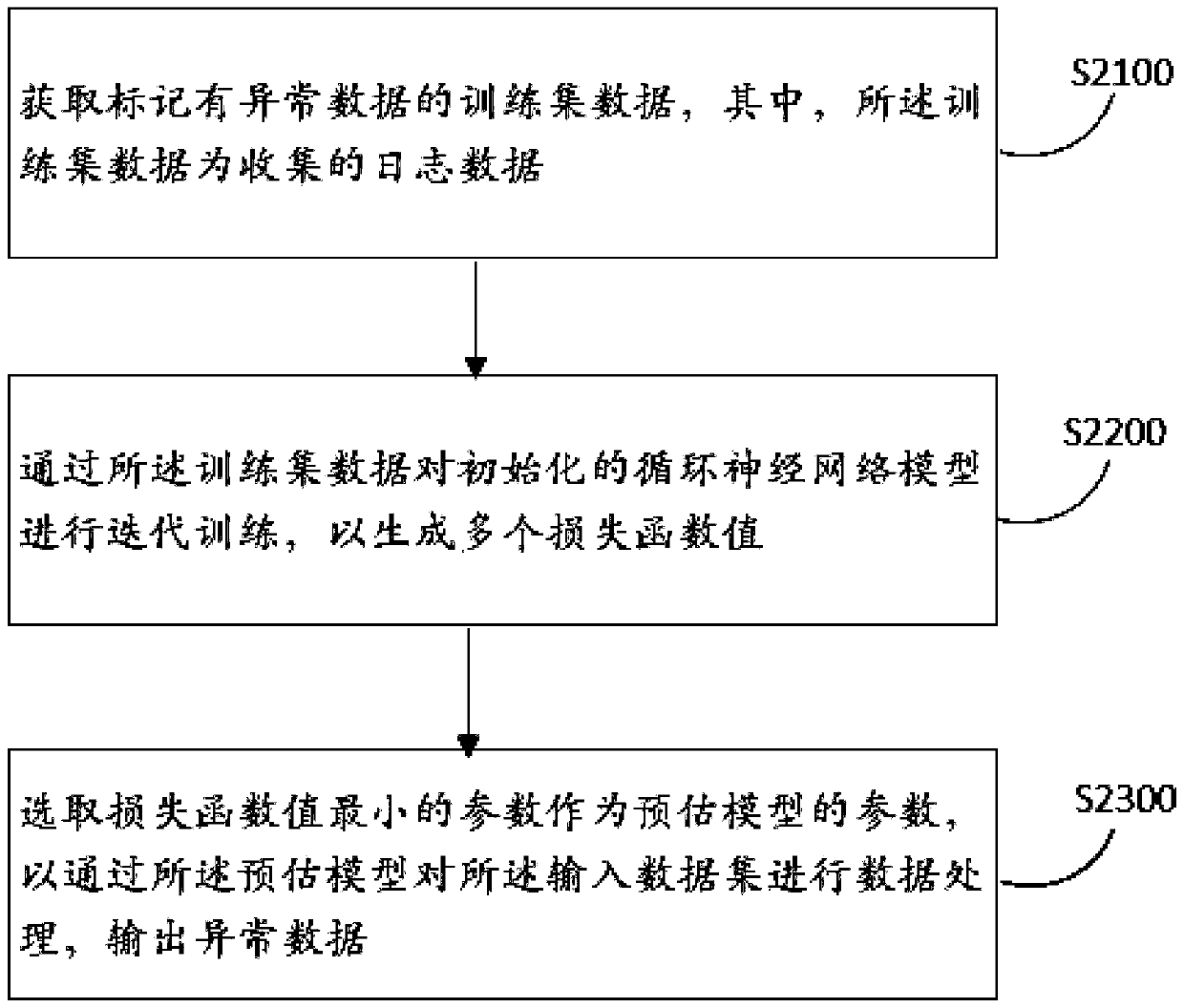
Log analysis method and device, computer equipment and storage medium
PendingCN111177095AImplement auto-scalingImprove adaptabilityHardware monitoringNeural learning methodsAnalytic modelData set
The invention discloses a log analysis method and device, computer equipment and a storage medium, and the method comprises the steps: obtaining an input data set which is data with a unified data structure after the standardization of the obtained original log data; inputting the input data set into a preset exception analysis model to generate exception data, the exception analysis model being arecurrent neural network model which is trained to a convergence state in advance and is used for extracting the exception data in the log data; and performing association processing on the abnormaldata based on a preset abnormal historical database. According to the method, the original log data from different servers can be quickly acquired; the log data is subjected to standardization processing to have the same data structure, and then the log data is subjected to anomaly identification by adopting the recurrent neural network model, so that even if the data volume is huge, the log datacan be rapidly identified, and the abnormal data is subjected to correlation processing to accelerate the abnormal data processing speed and improve the abnormal data processing accuracy.
Owner:CHINA MOBILEHANGZHOUINFORMATION TECH CO LTD +1
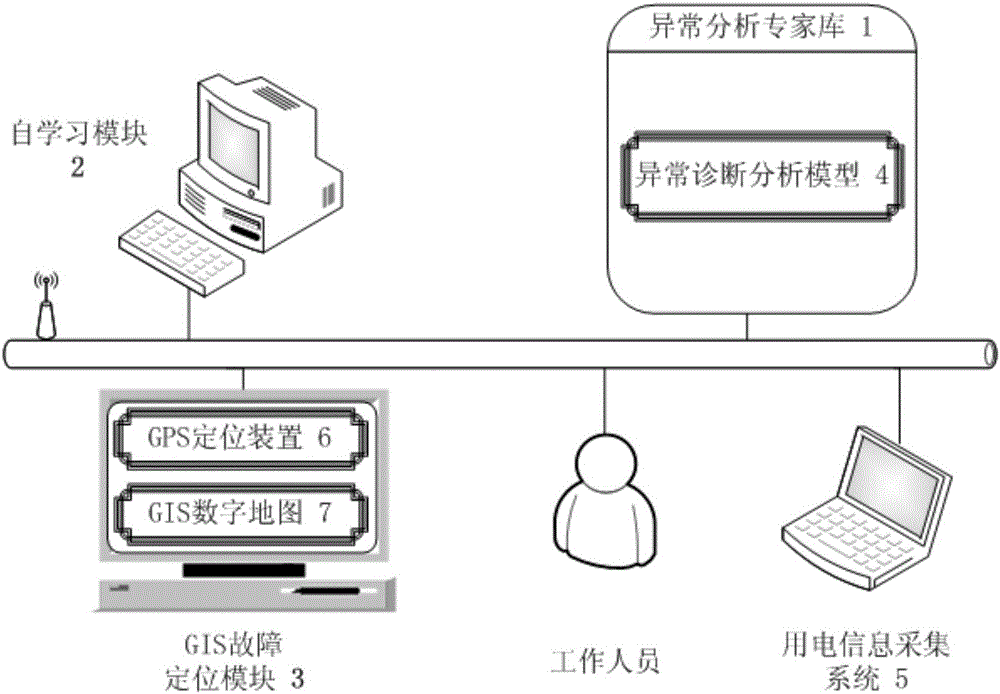
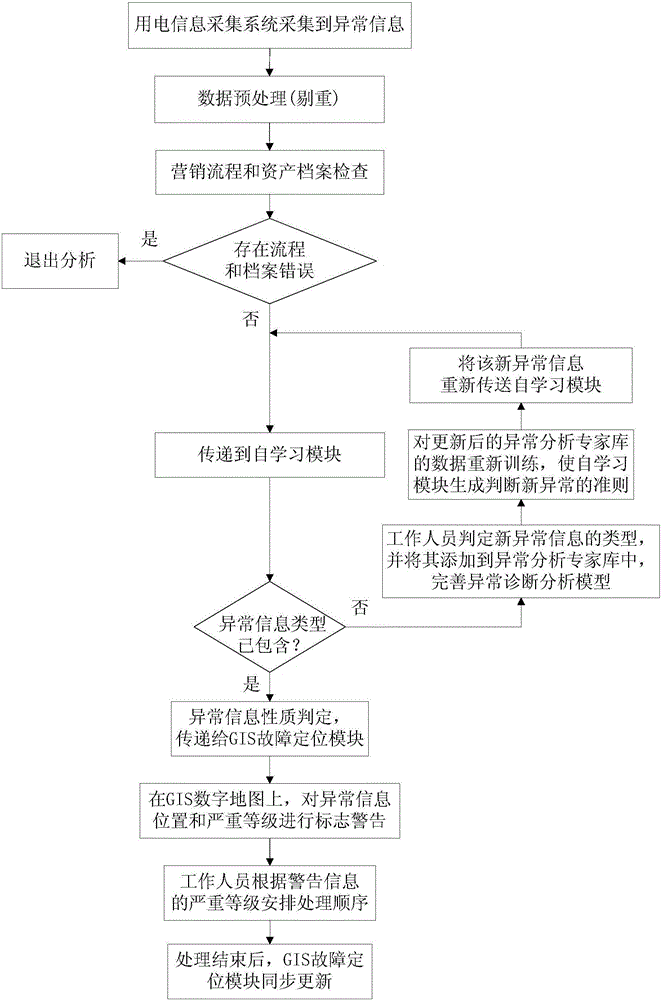
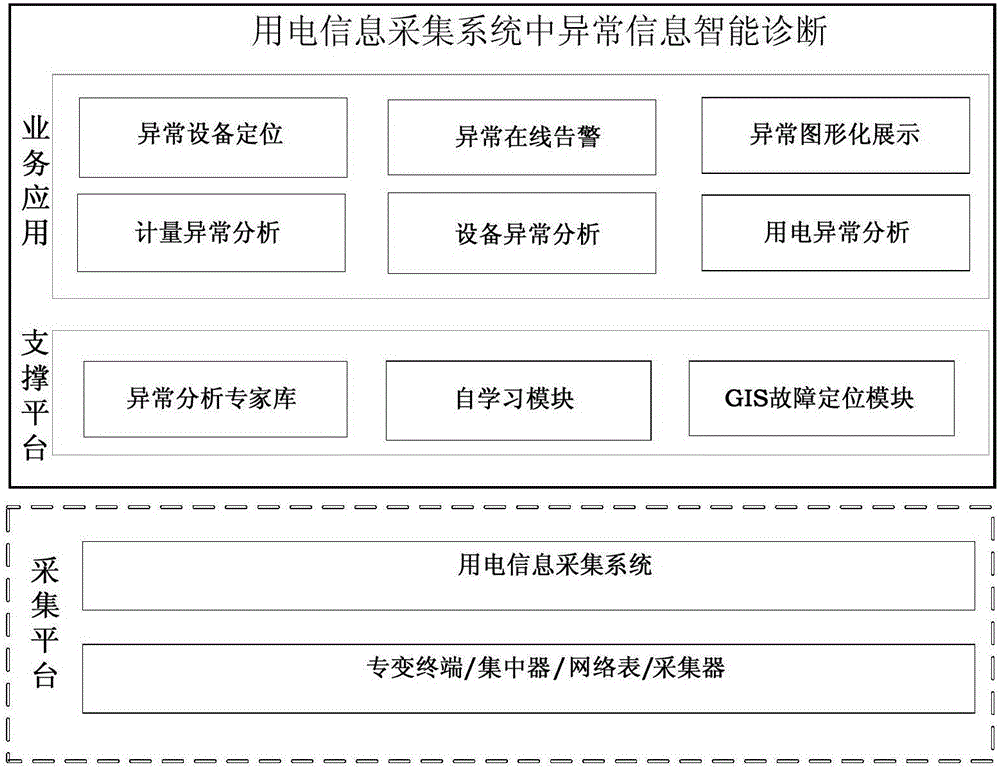
Intelligent diagnosis system and method for abnormal information in electric information acquiring system
ActiveCN106199276AImprove accuracyImprove troubleshooting efficiencyElectric connection testingSeverity/IntensityProcess efficiency
The invention discloses an intelligent diagnosis system and method for abnormal information in an electric information acquiring system. The system comprises an anomaly analysis expert database, a self-learning module and a GIS fault location module which cooperate with one another to enhance a capability of monitoring the operation of the electric information acquiring system. The system and method use the data acquired by the electric information acquiring system as a basis, count, analyze and diagnose t various kinds of electric data acquired by the abnormally analysis expert database and the self-learning module, determines an abnormity type and a serious degree, lock the specific location of a fault by the GIS fault location module quickly and accurately, and improve fault monitoring accuracy and fault processing efficiency to a great extent.
Owner:NARI TECH CO LTD +4
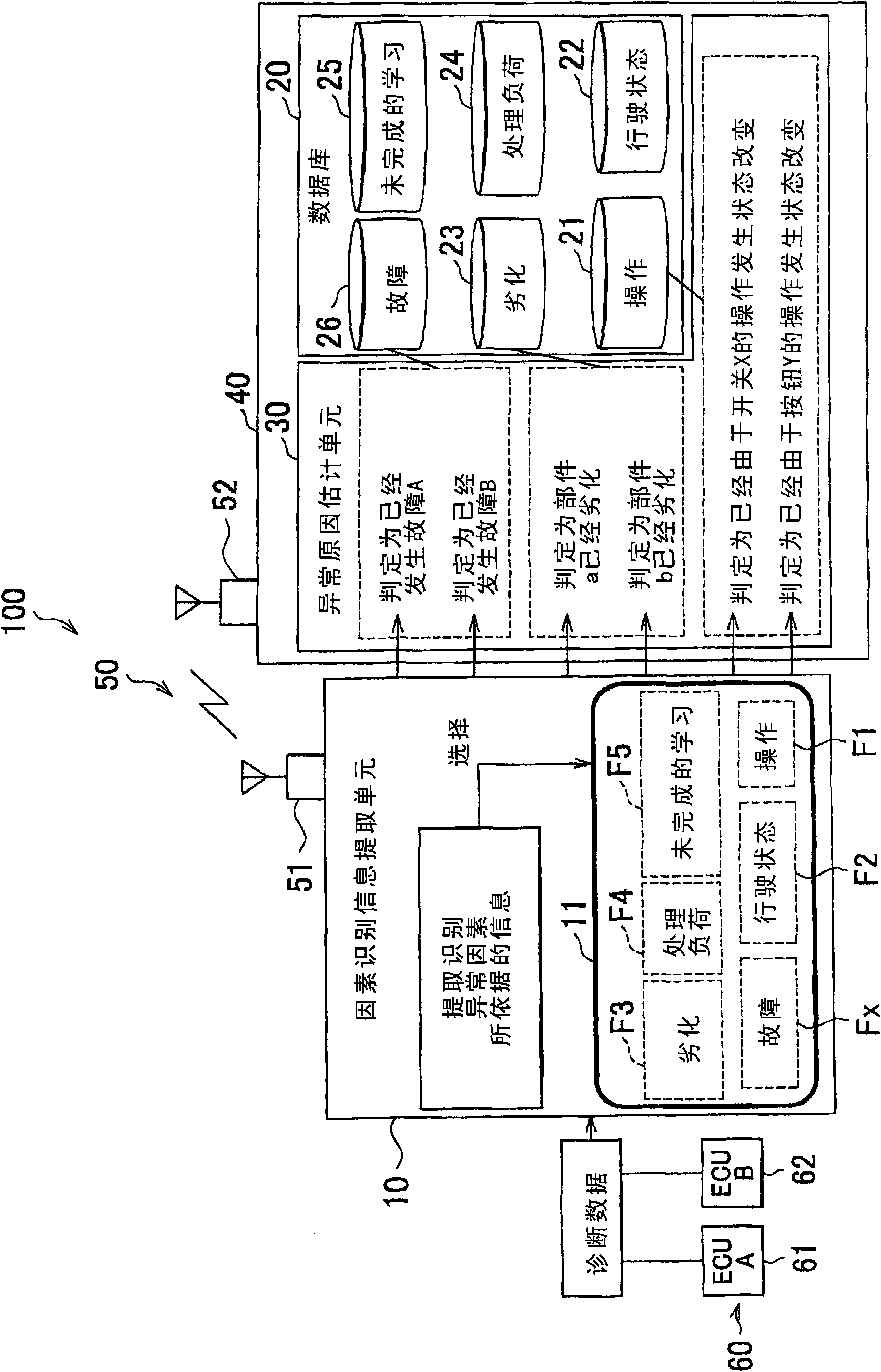
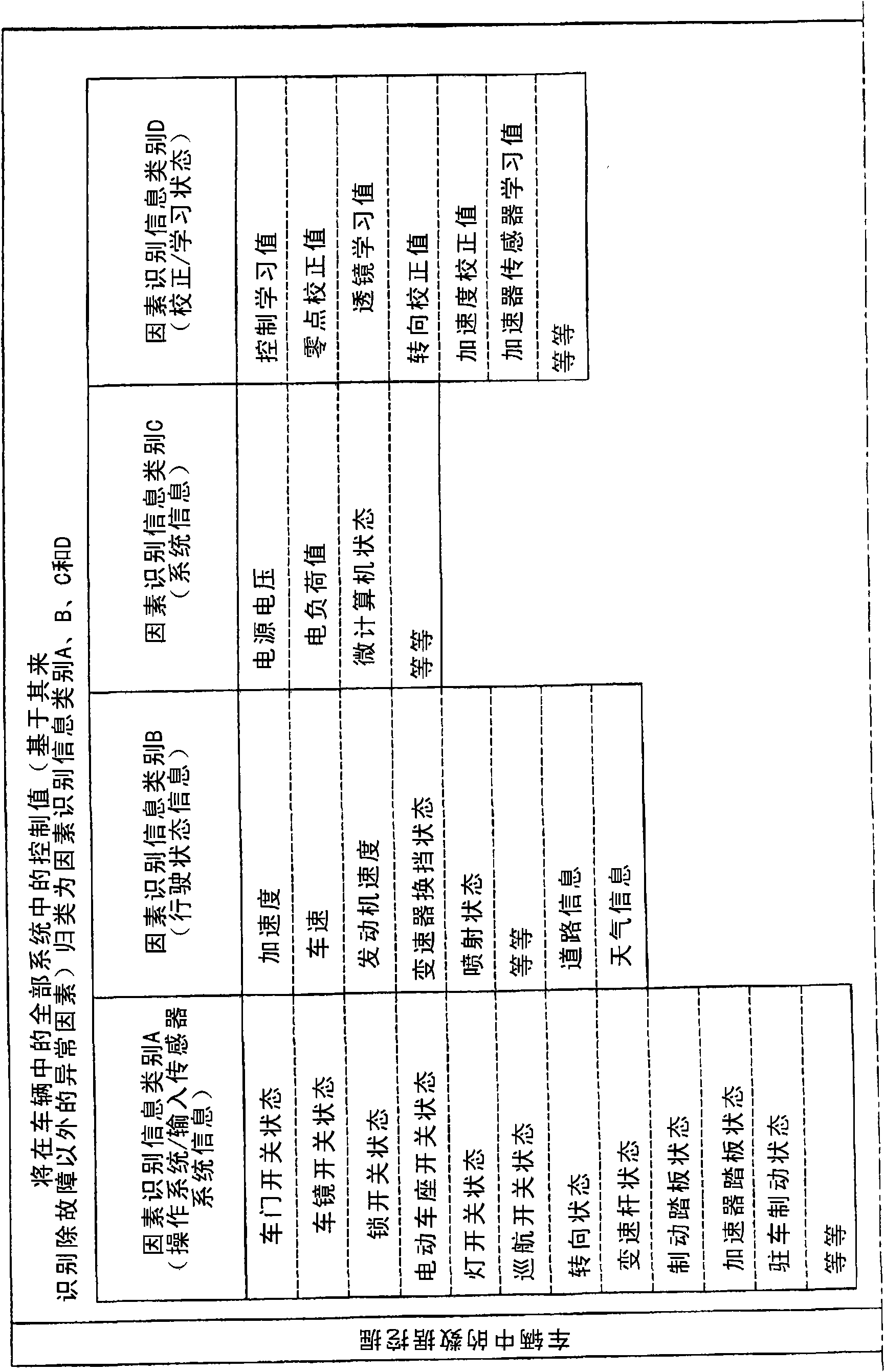
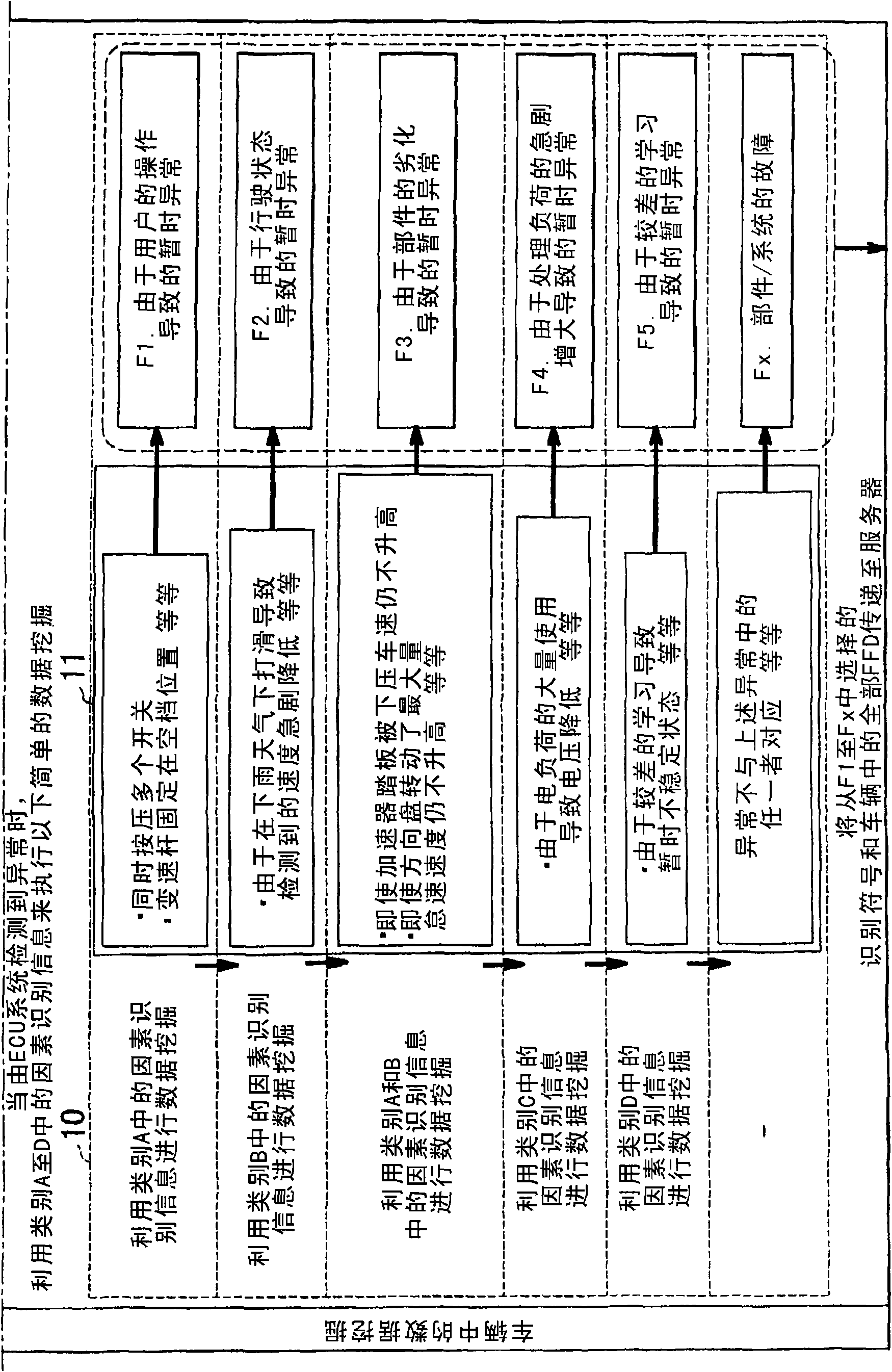
Abnormality analysis system for vehicle and abnormality analysis method for vehicle
InactiveCN101660974AReduce processing loadImprove judgment accuracyVehicle testingData processing applicationsAnalysis methodComputer science
Owner:TOYOTA JIDOSHA KK
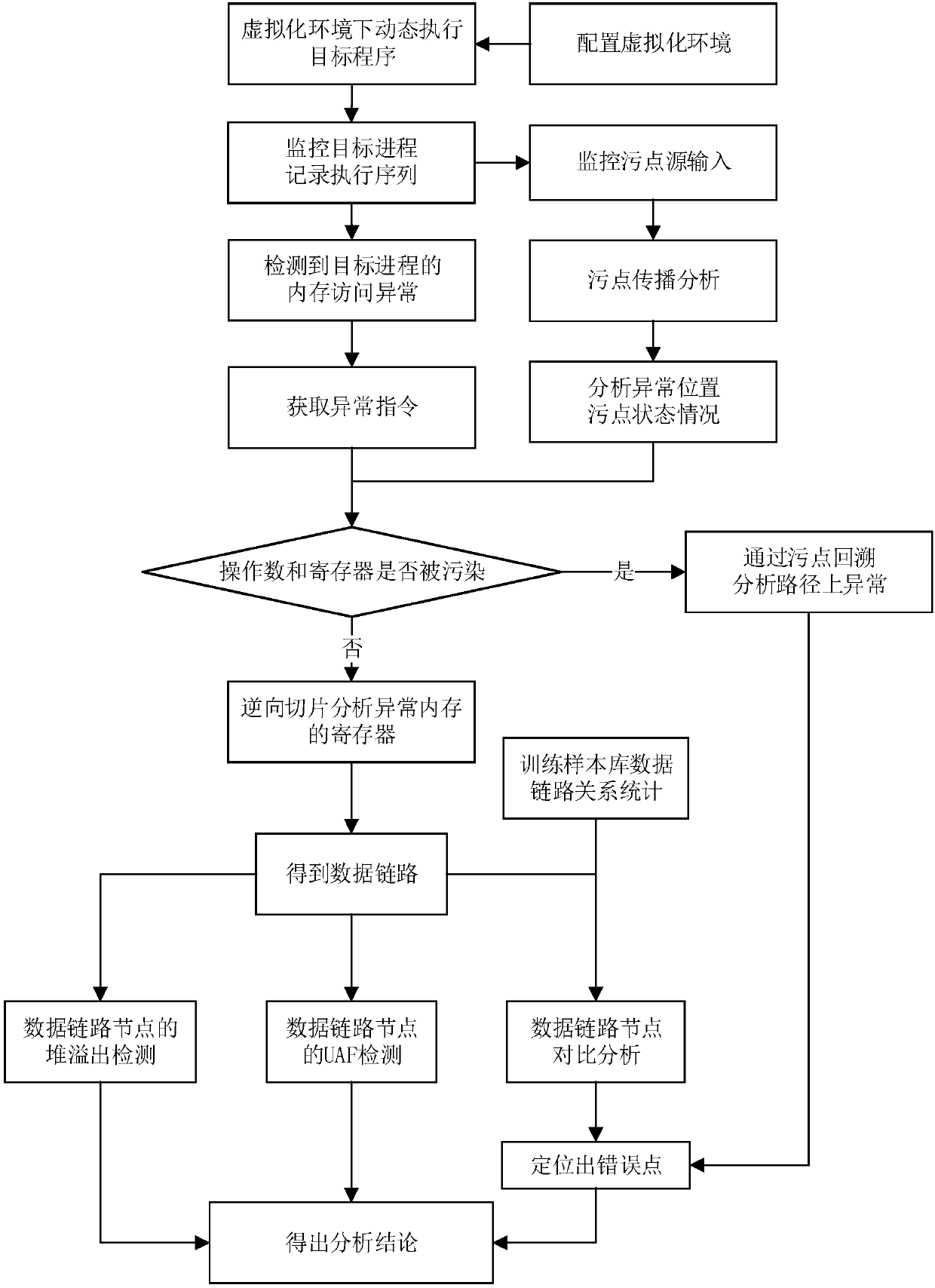
Program exception analysis method based on dynamic stain propagation
ActiveCN109583200AAccurate analysisPrecise positioningPlatform integrity maintainanceVirtualizationHeap overflow
The invention provides a program exception analysis method based on dynamic stain propagation, which comprises the following steps of: dynamically running a target program in a virtualization environment, monitoring a target process of the target program and recording execution sequence information; Marking the input data causing the abnormity of the target program as a stain source, and performing stain propagation analysis according to the instruction semantics of the instruction executed by the target process to obtain stain state information of a memory; Identifying a memory access exception in the running process of the target program, extracting an exception position of an exception instruction, and detecting an operand of the exception position and a stain state of a register according to stain state information of the memory; If the operands and the registers are polluted, positioning error points through stain backtracking; And otherwise, carrying out reverse slice analysis onthe register, finding out a related data link, carrying out heap overflow detection and UAF detection on each node on the data link, and positioning an error point through comparative analysis.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
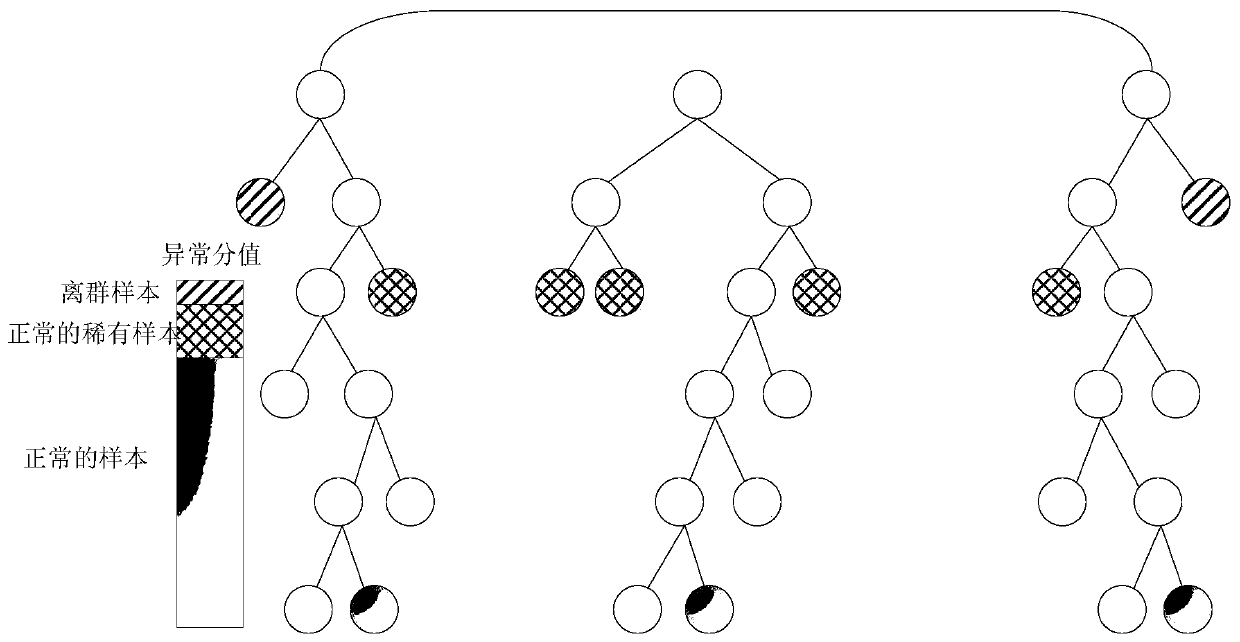
Electricity consumption information acquisition data exception analysis method based on isolated forest algorithm
PendingCN110189232AImprove processing efficiencyEasy to handleData processing applicationsData dredgingData set
The invention discloses an electricity consumption information acquisition data exception analysis method based on an isolated forest algorithm, and the method comprises the steps of building a transformer area line loss management index based on an electricity consumption information acquisition system, and formulating a transformer area line loss management method based on the electricity consumption information acquisition system; for the line loss type transformer areas, adopting a cloud storage technology to realize acquisition, classification and processing of the power utilization information data of the line loss type transformer areas; analyzing and summarizing the type of the dirty data, eliminating the noise according to the representation form of the dirty data, and removing the dirty data; converting the cleaned and screened data into a form beneficial to data mining through data conversion; establishing a data analysis model by applying the isolated forest algorithm; andperforming model evaluation by applying the ROC curve and the area AUC under the curve and the cumulative recall ratio curve and the P-R curve of the subject, applying the model to a plurality of lineloss type transformer area power consumption information data sets, performing data mining on the screened data, and screening the power consumption abnormal users. According to the method, the dataabnormal users are effectively mined by adopting the isolated forest algorithm, the line loss reasons are analyzed, and the line loss management of the transformer areas is enhanced.
Owner:CHINA THREE GORGES UNIV
Method, apparatus and system for GSM system service tracking and exception management
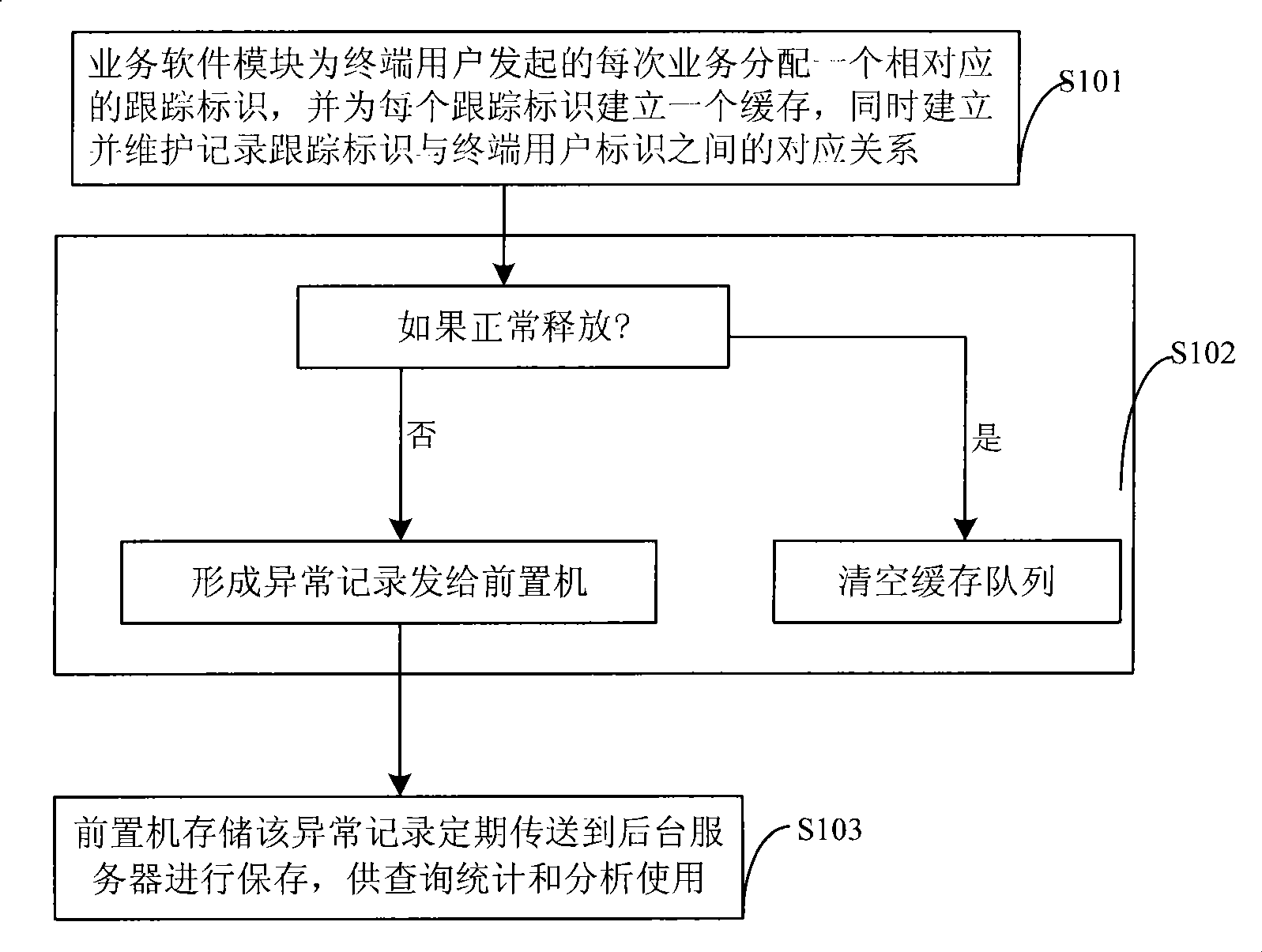
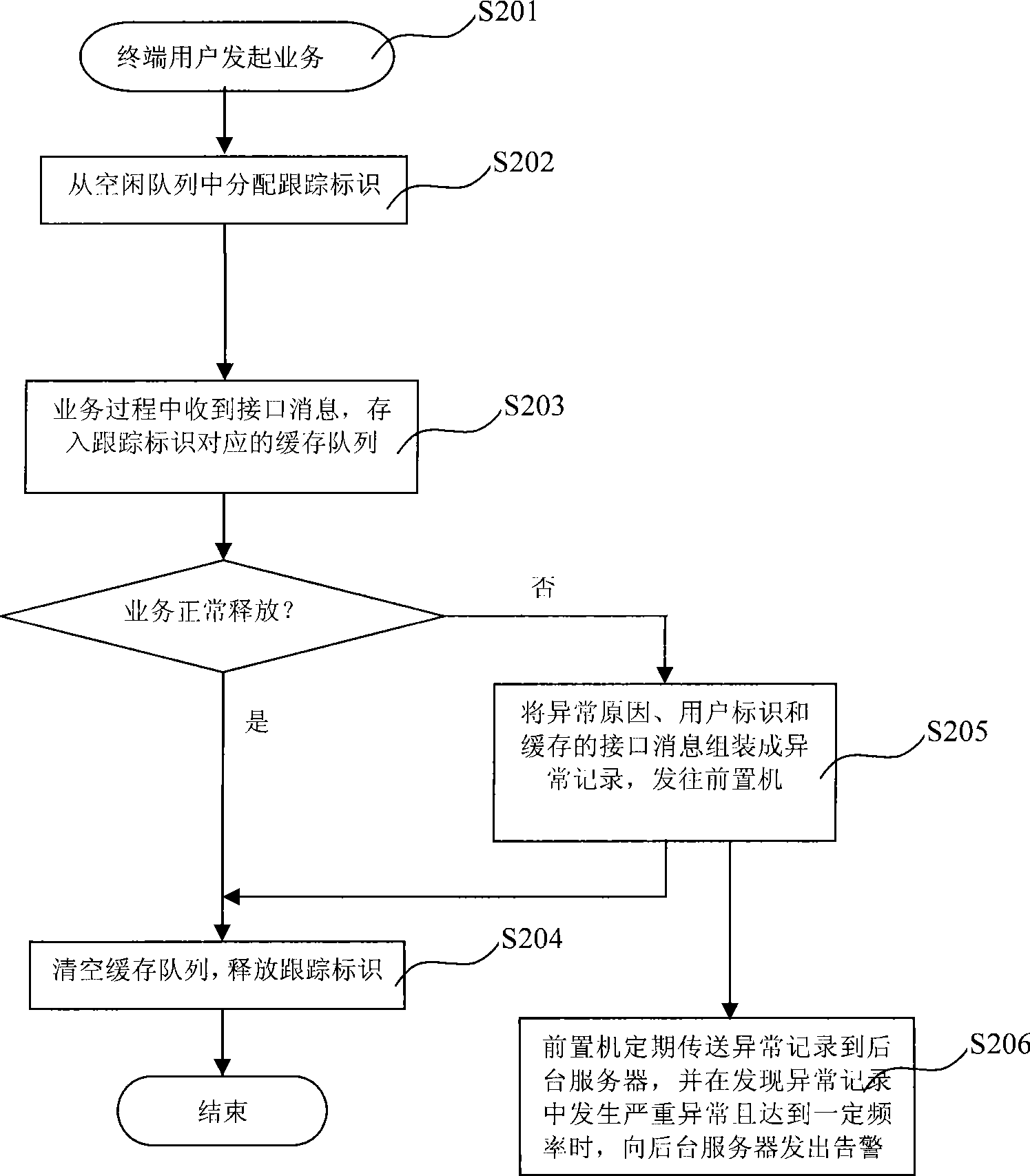
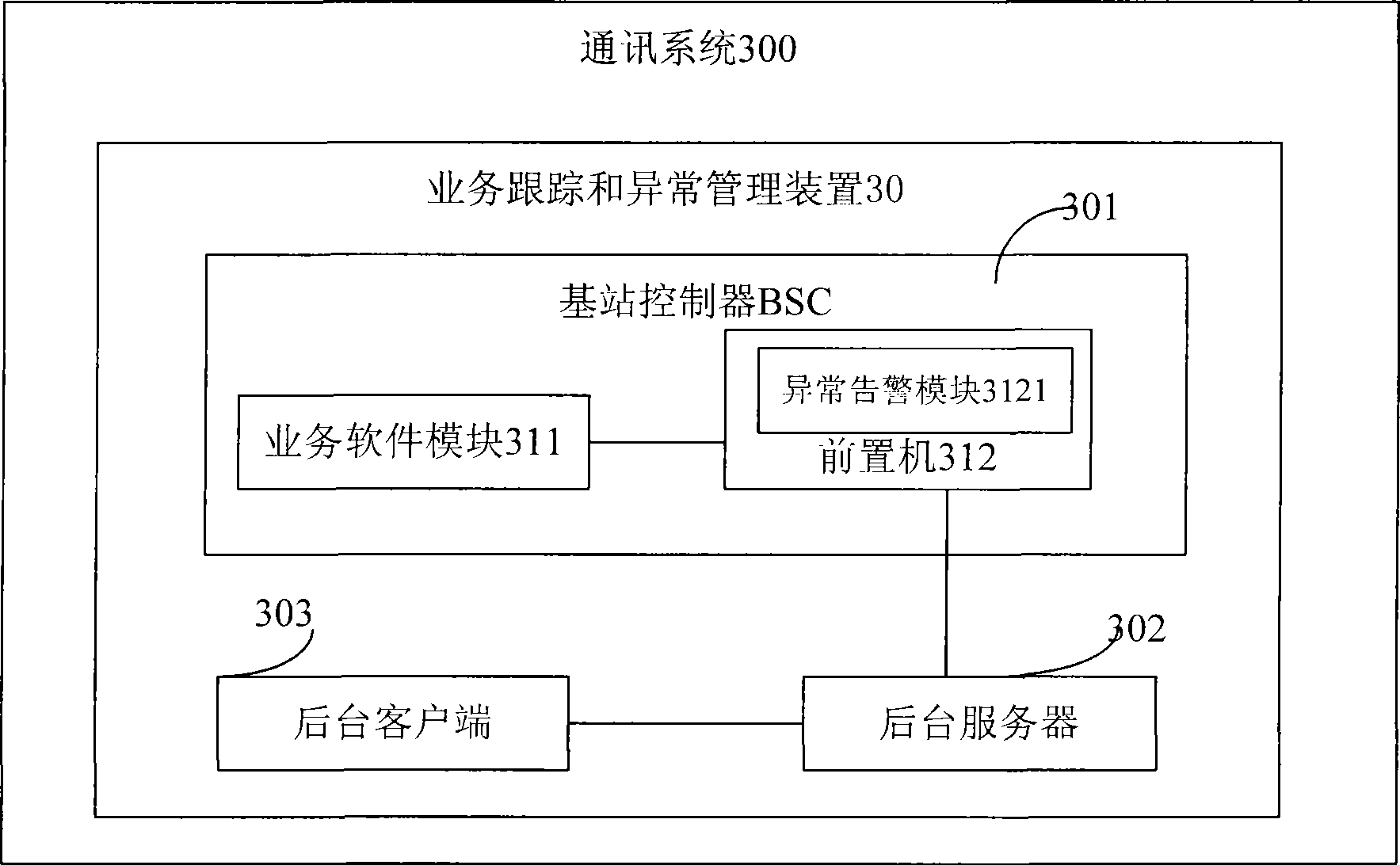
InactiveCN101459924AEasy to detectImprove analytical performanceNetwork traffic/resource managementConnection managementCommunications systemUser identifier
The invention discloses a method and a device for a GSM system business tracking and exception management, and a communication system employing same, wherein the method comprises firstly allocating a corresponding tracking identifier to per business promoted by terminal users through a business soft module, establishing every tracking identifier with a buffer memory for storing interface information between element locations received from business in operation, and simultaneously establishing, maintaining and recording the corresponding relationship between the tracking identifiers and terminal user identifiers. Secondly, releasing the corresponding tracking identifiers after the business is over, emptying a buffer memory queue if the release is normal, and forming and sending an abnormal record to a front-end processor if the release is abnormal. Thirdly, utilizing the front-end processor to store and periodically send the abnormal record to a background server for storing. The method, device and communication system of the invention solves the problem that data quantity is too large to position network fault, and provides a means for network state detecting, alarming, and abnormal analysis of special users.
Owner:ZTE CORP
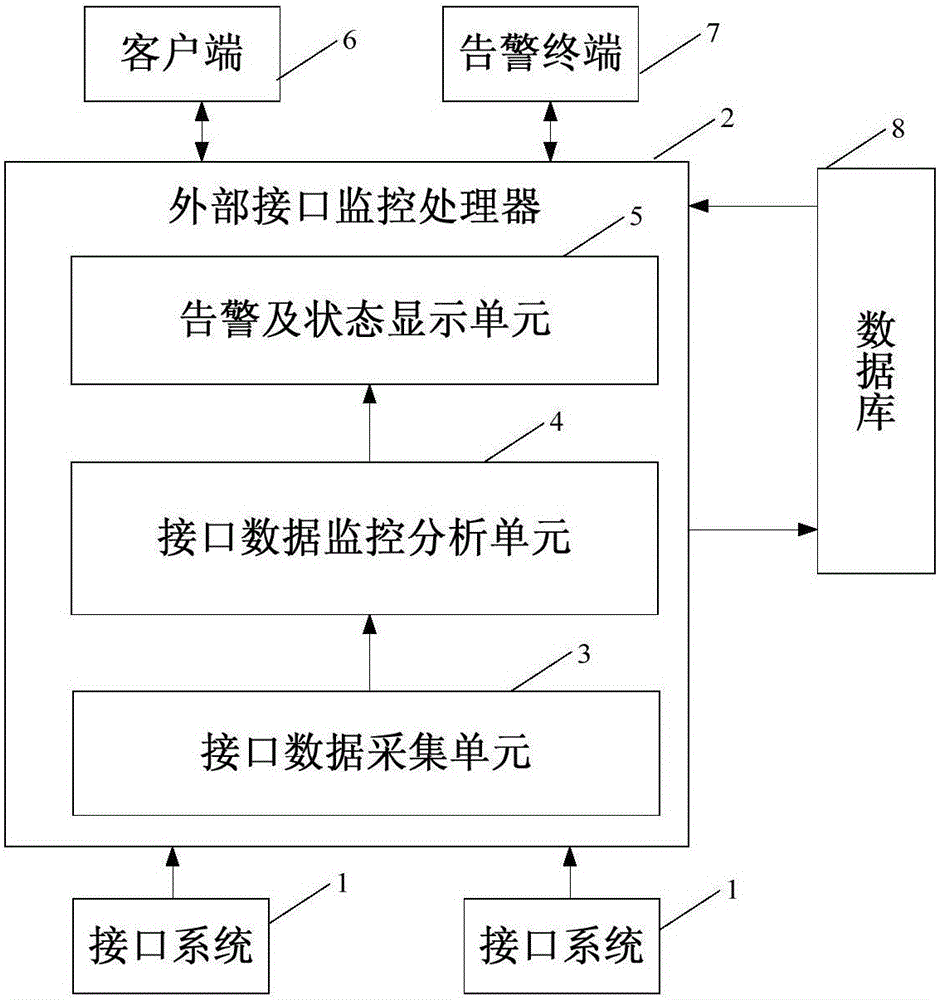
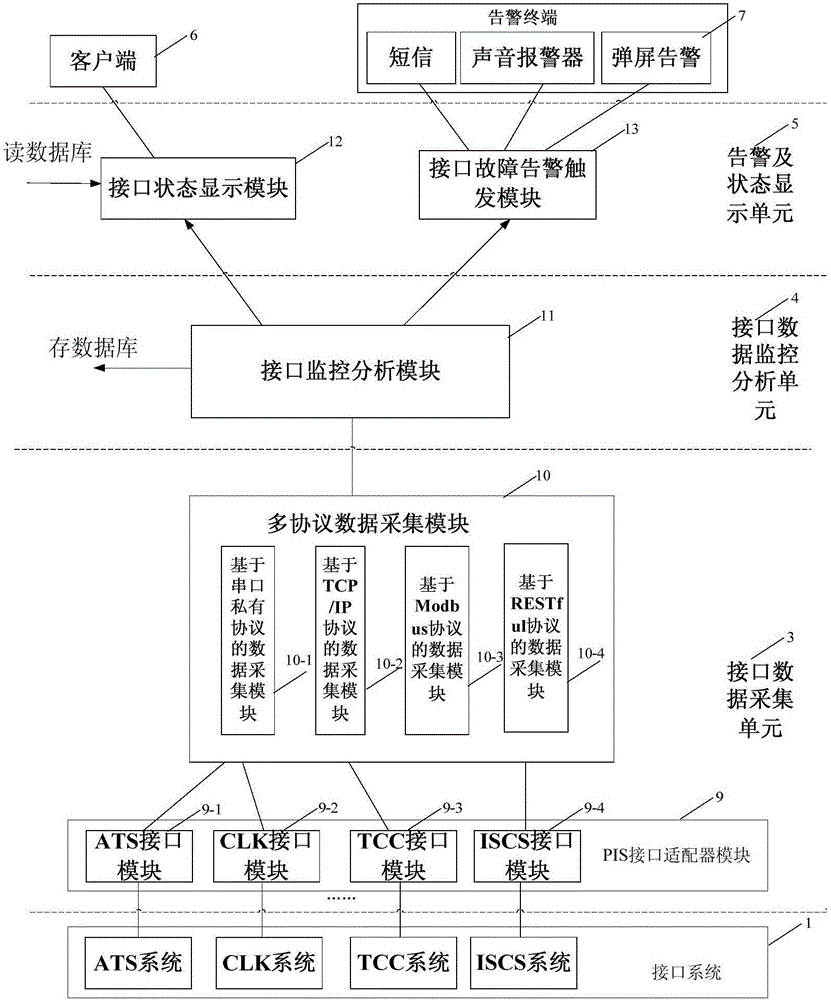
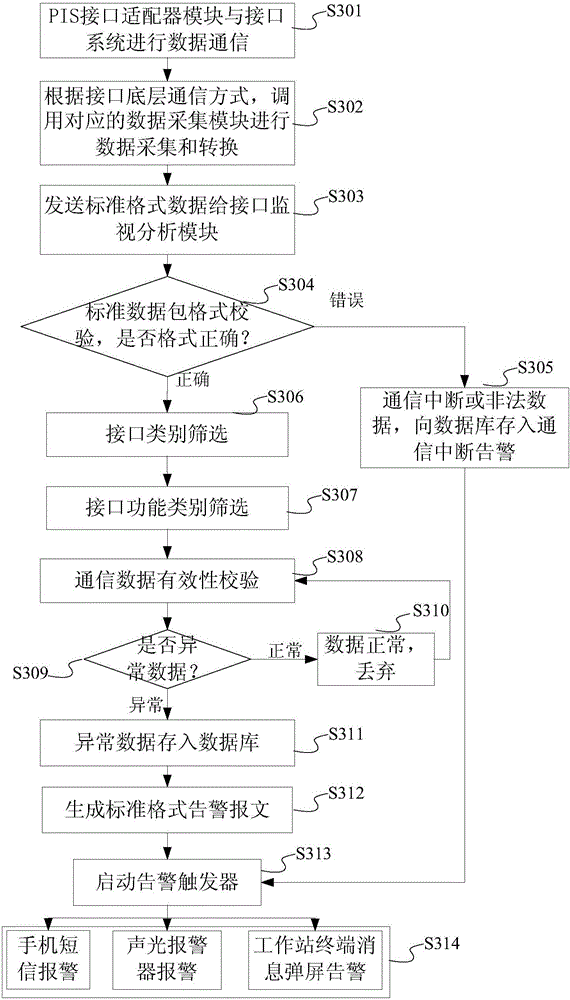
PIS (Passenger Information System) external interface monitoring system and method
The invention discloses a PIS (Passenger Information System) external interface monitoring system and method, which can perform real-time monitoring on a data communication state of a PIS external interface and give an abnormal alarm timely. The system comprises an external interface monitoring processor, a client, an alarm terminal and a plurality of interface systems; the external interface monitoring processor is connected with the plurality of interface systems, so as to realize acquisition and exception analysis of communication data between a PIS system and the interface systems, and generate an alarm message in the presence of abnormal communication data; the client is communicated with the external interface monitoring processor, and acquires a communication state of the PIS external interface; and the alarm terminal is communicated with the external interface monitoring processor, acquires the alarm message generated by the external interface monitoring processor, and gives an alarm.
Owner:INST OF COMPUTING TECH CHINA ACAD OF RAILWAY SCI +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com