Patents
Literature
100 results about "Boundary crossing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
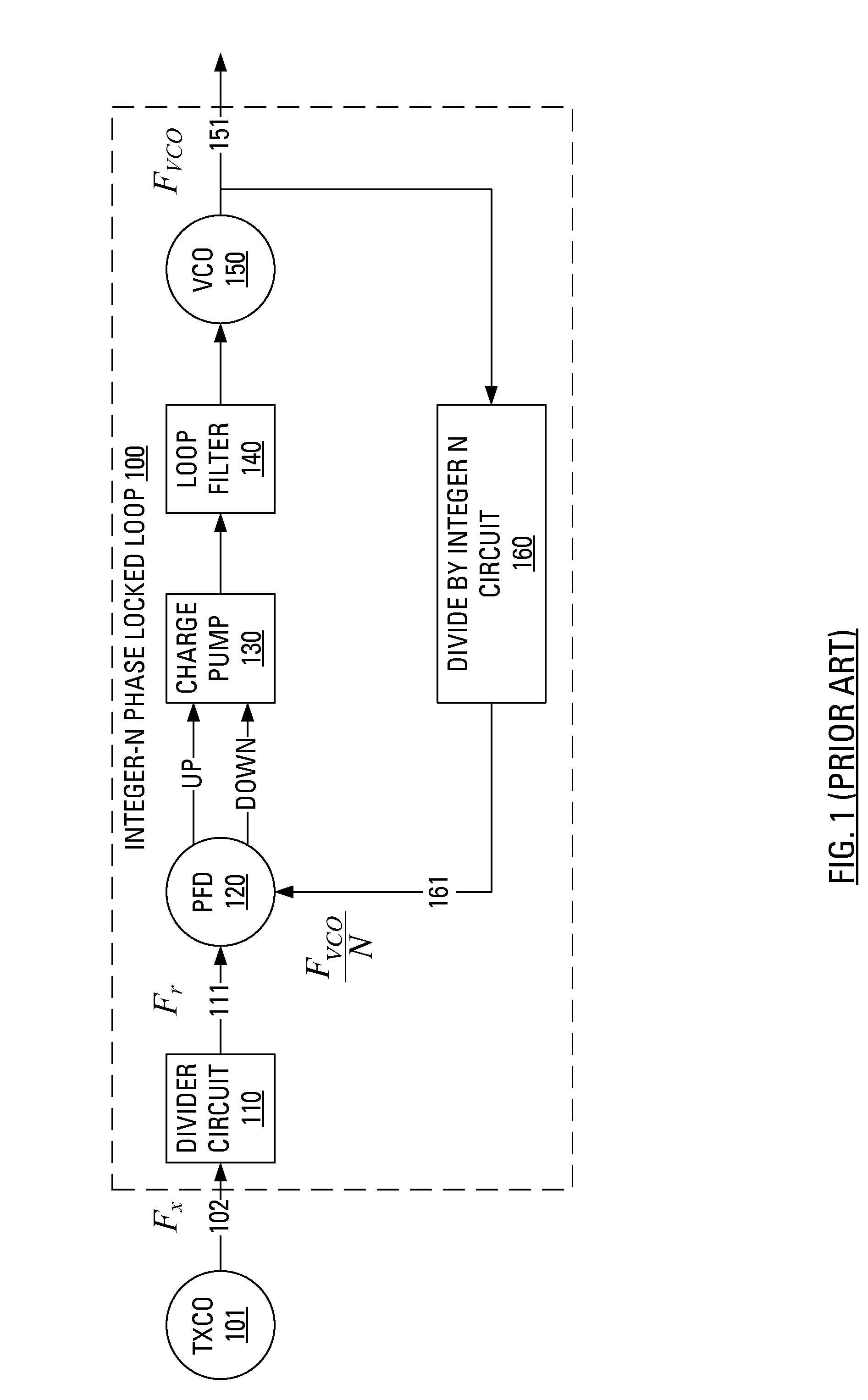
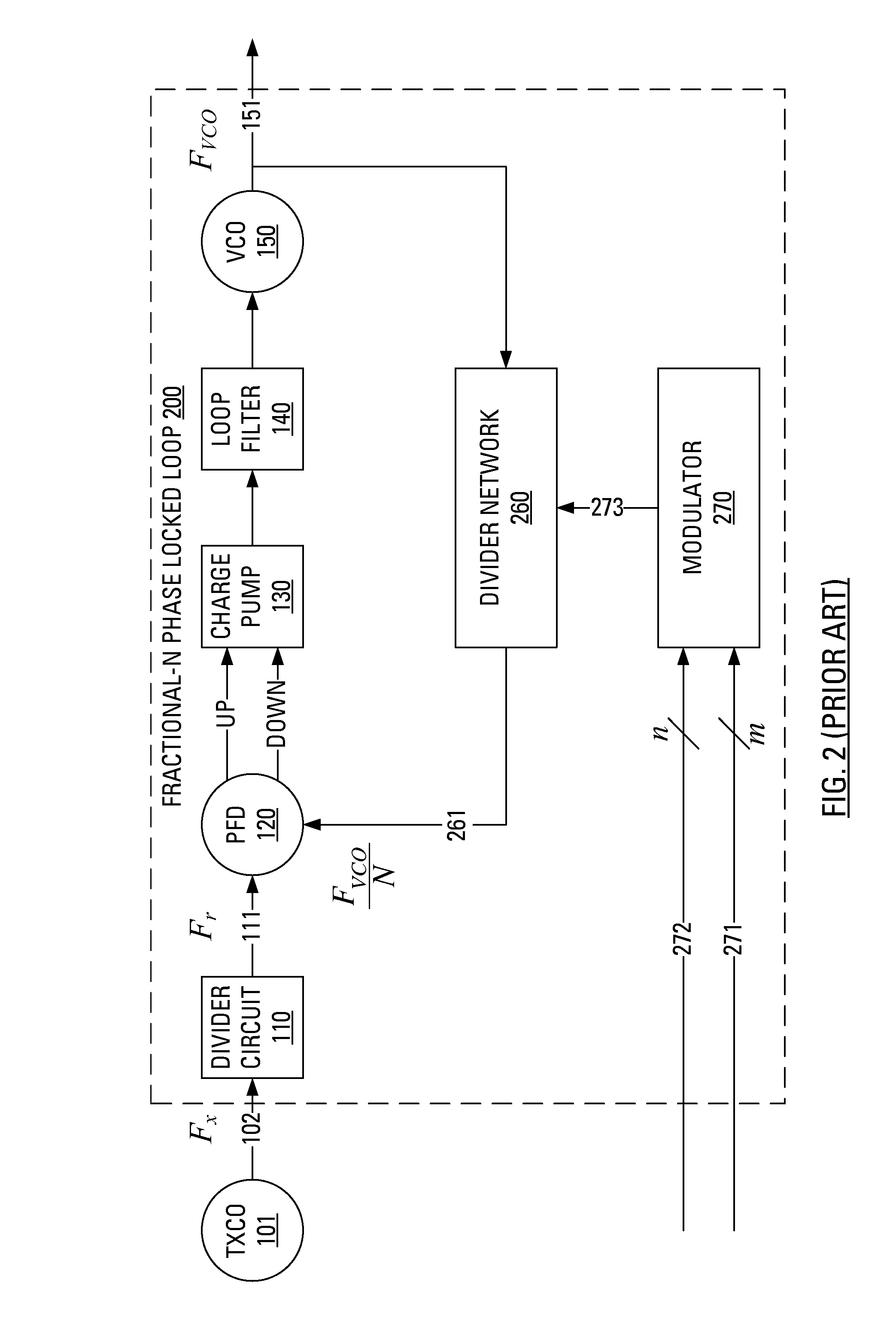
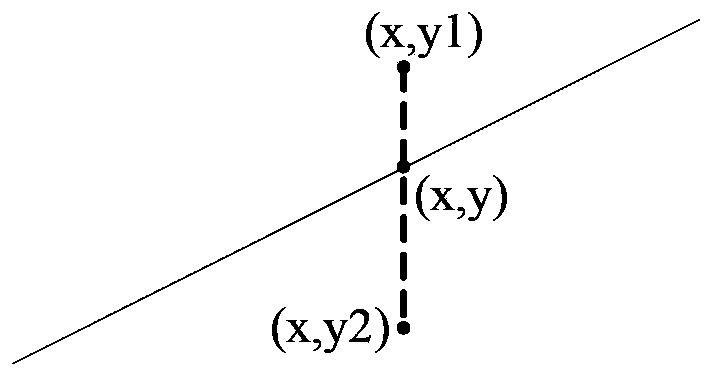
Boundary crossing. Boundary crossing is defined as the efforts made by individuals or groups 'at boundaries' to establish or restore continuity in action or interaction across practices (Bakker & Akkerman, 2013).
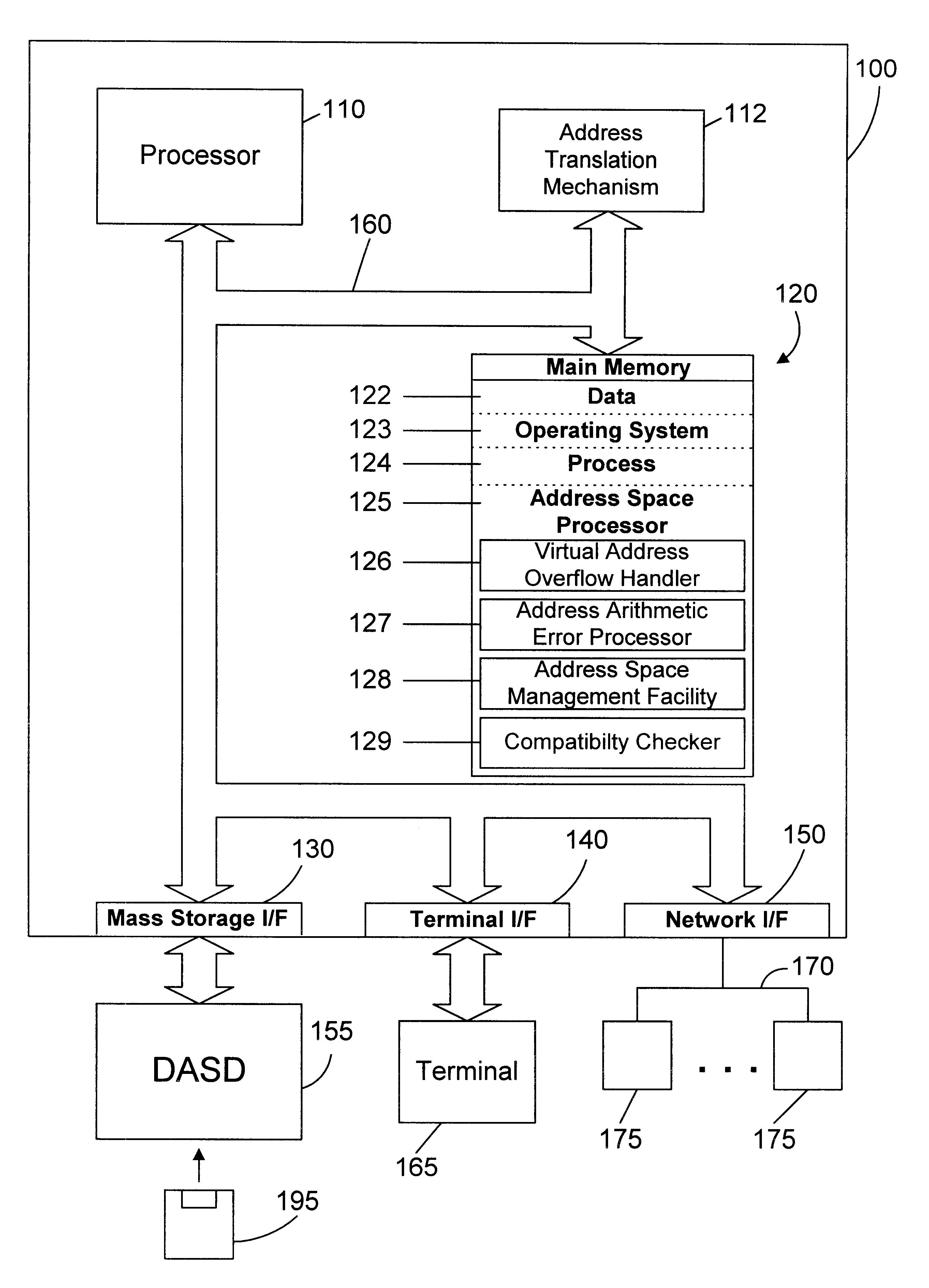
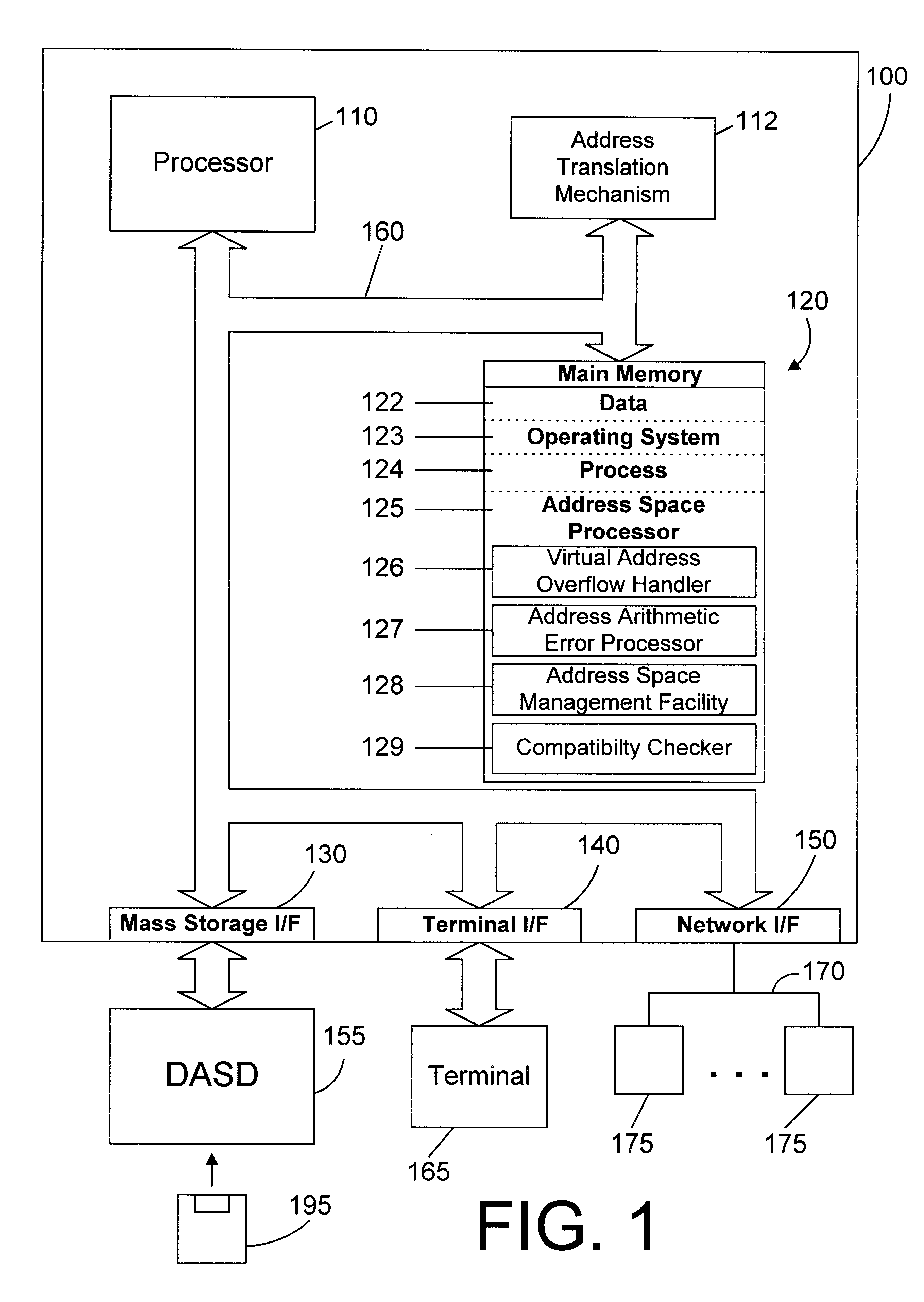
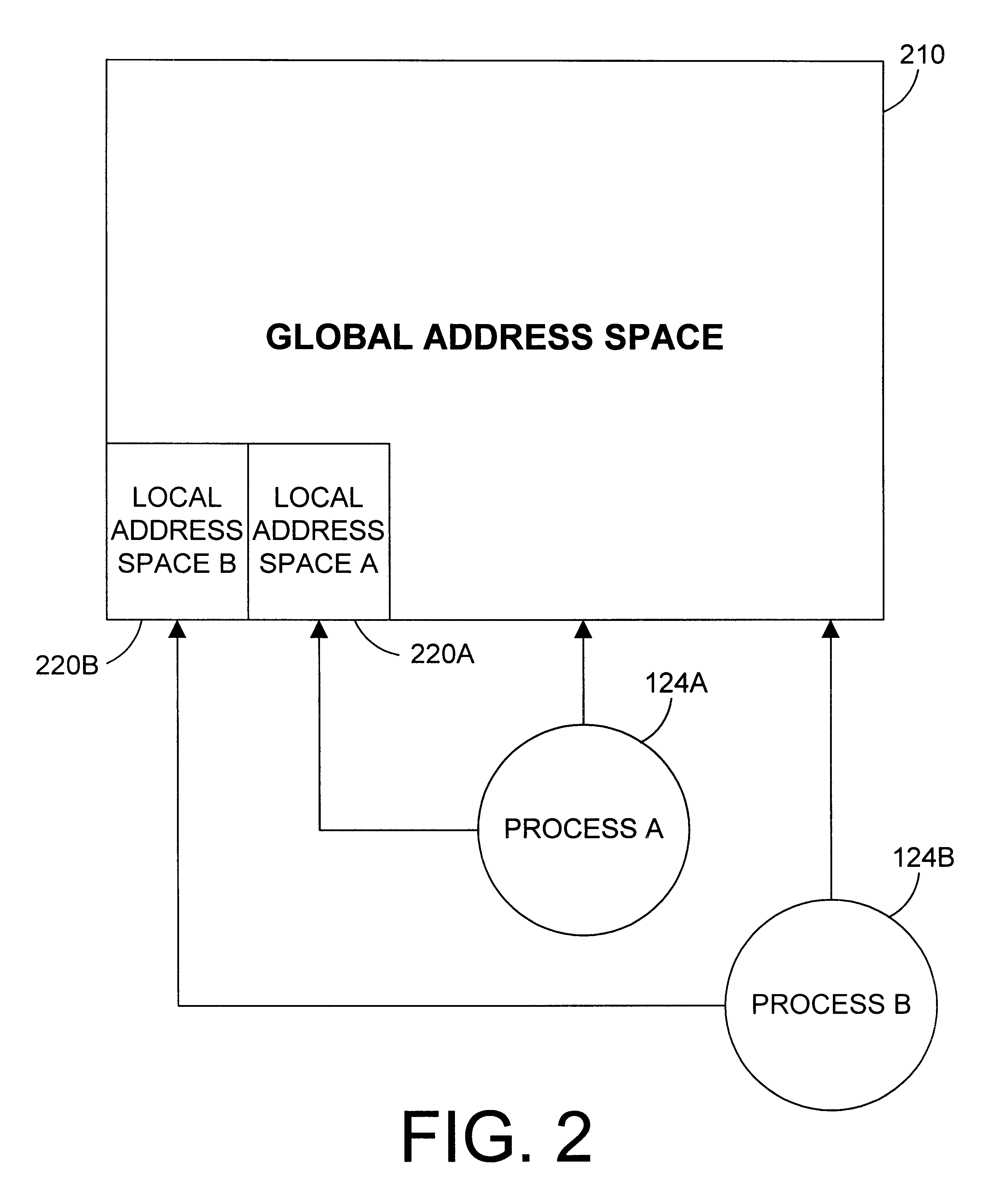
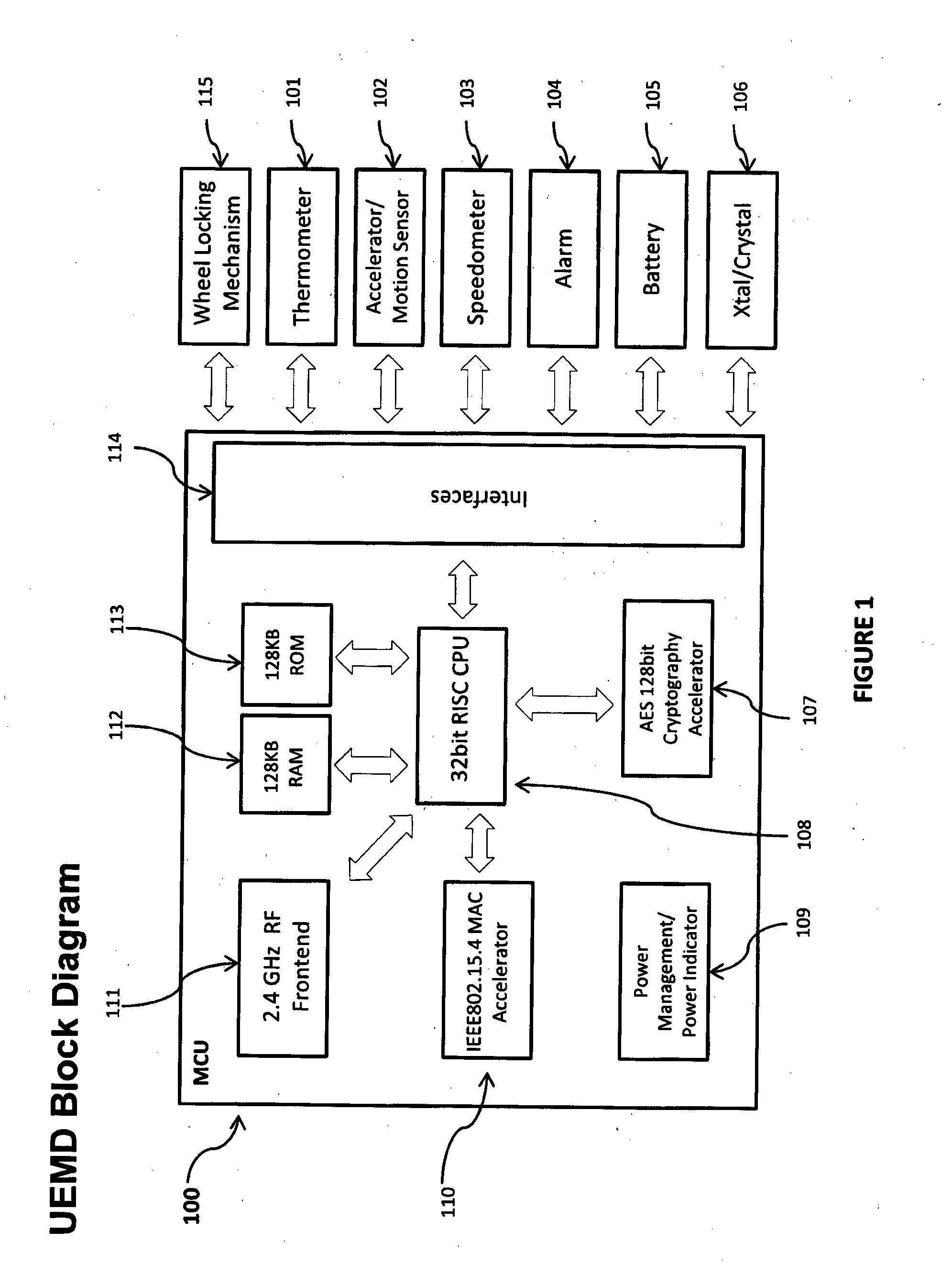
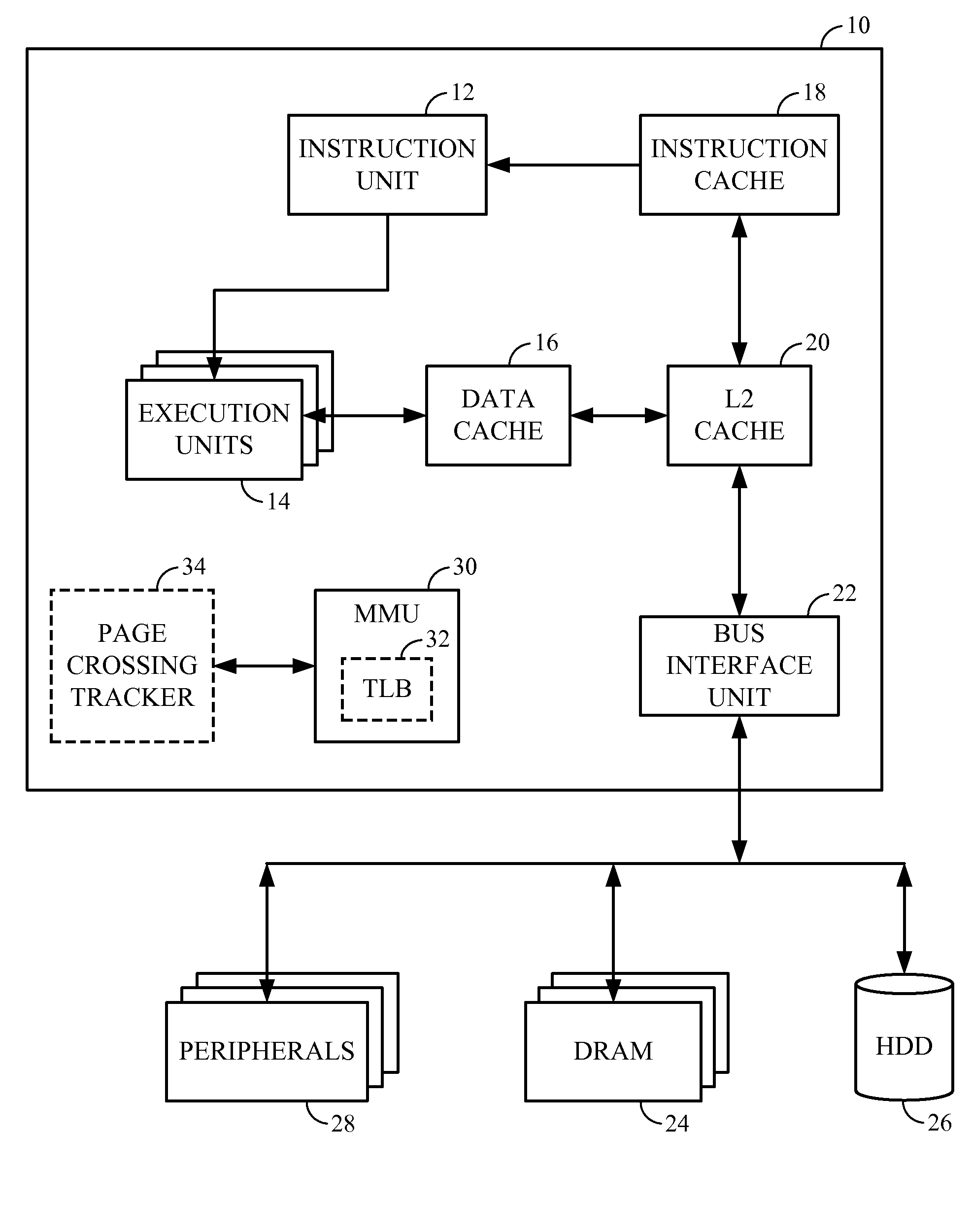
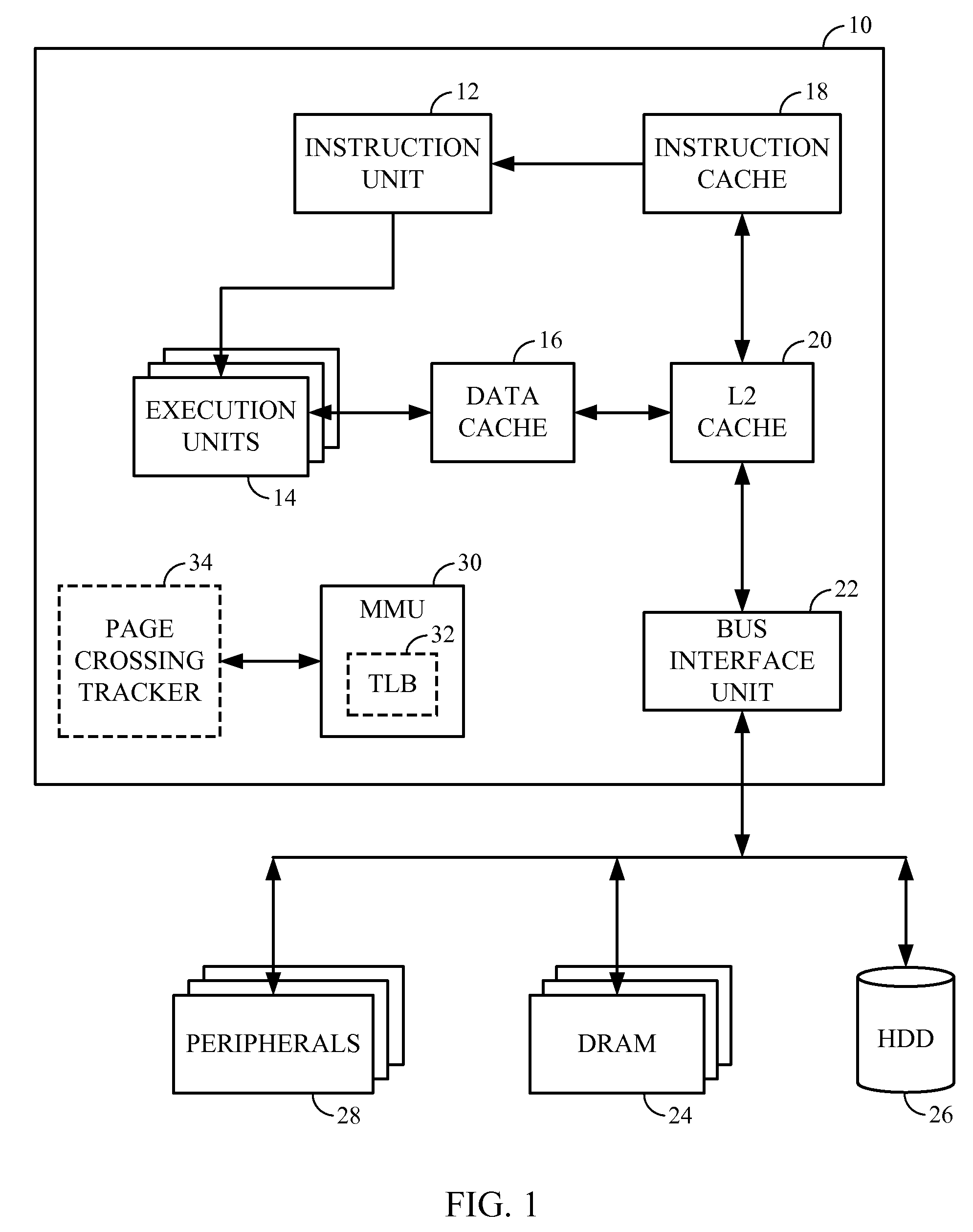
Apparatus and method for providing simultaneous local and global addressing using software to distinguish between local and global addresses
InactiveUS6574721B1Good flexibilityMemory adressing/allocation/relocationMicro-instruction address formationGlobal address spaceComputer compatibility
An apparatus and method provide simultaneous local and global addressing capabilities in a computer system. A global address space is defined that may be accessed by all processes. In addition, each process has a local address space that is local (and therefore available) only to that process. An address space processor is implemented in software to perform system functions that distinguish between local addresses and global addresses. In the preferred embodiments, the local address space has a size that is a multiple of the size of a segment of global address space. When the hardware indicates a page fault, the address space processor determines whether the address being translated is a local address or a global address. If the address is a local address, the address space processor uses a local directory to process the page fault. If the address is a global address, the address space processor uses a global directory to process the page fault. When the hardware indicates an addressing error because a computed address crosses a global segment boundary, the address space processor determines whether the address is a local address or a global address. If the address is a global address, the address space processor indicates an addressing error. If the address is a local address, the address space processor determines whether the address is within the process' local address space, and indicates an addressing error if the address is outside the process' local address space. Instructions are allowed to operate on both local and global addresses because the address space processor handles either type of address whenever software assistance is required, such as for servicing a page fault or checking a segment boundary crossing. In addition, the address space processor dynamically checks the addressing compatibility of called code before passing control to the called code.
Owner:IBM CORP
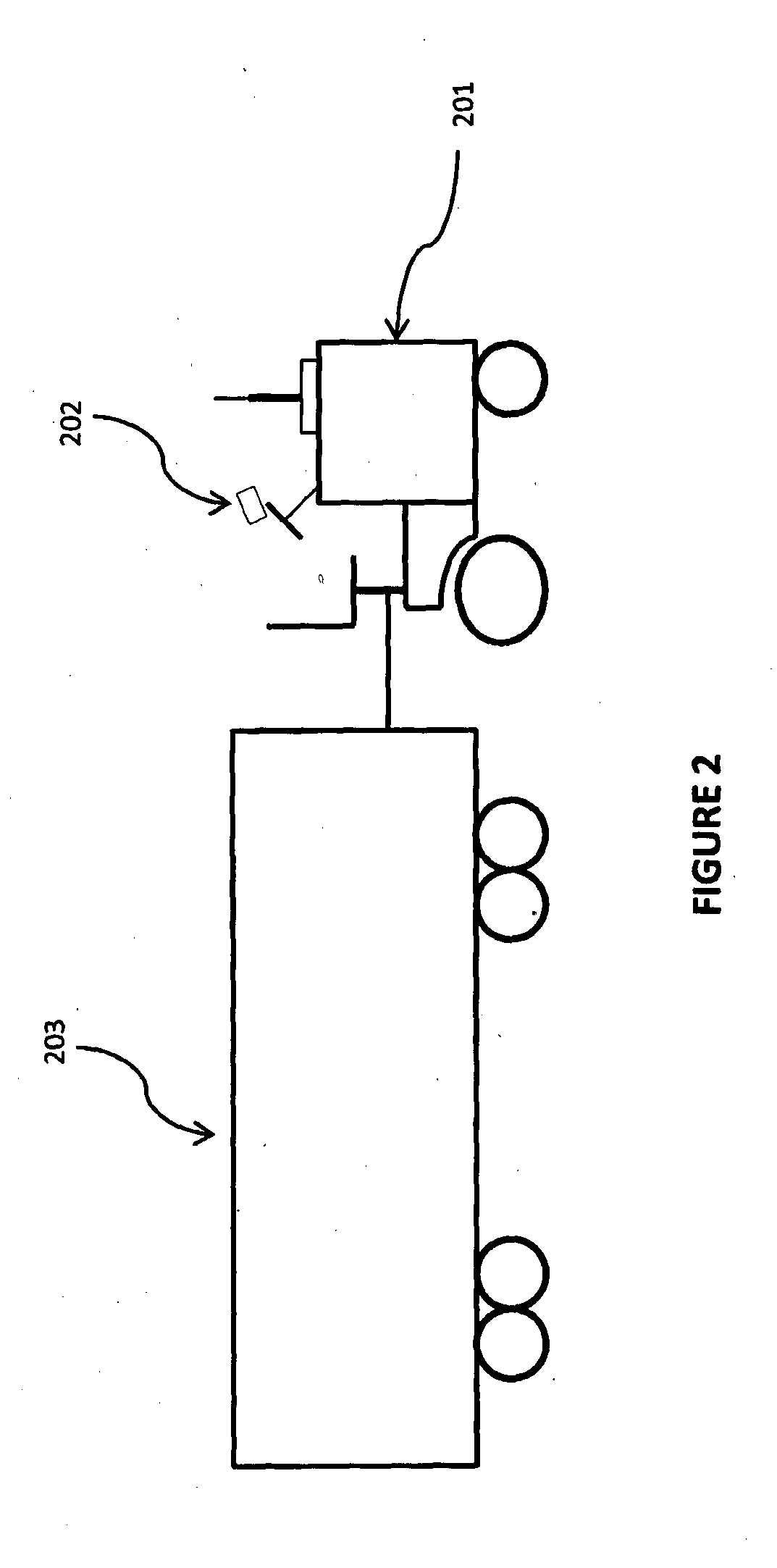
Monitoring and tracking of trolleys and other transporting units
InactiveUS20150325103A1Easy to detectShortens trolley retrieval processData processing applicationsNetwork topologiesData storingBoundary crossing
The present invention provides a system for monitoring and tracking transporting units. The system utilizes a monitoring device fitted to a transporting unit to collect data pertaining to the transporting unit and transferring the data along with a unique ID for monitoring device it to a reader device for a particular geographical area. Each reader device for a geographical area transfers data collected for a plurality of monitoring devices in its geographical area to a centralized server. The server stores the data in a database. The data server uses algorithms to calculate positions of transporting units, load managing for the reader devices, boundary crossing occurrences by a transporting unit, triggering alarm and / or locking wheels for the transporting unit when the device is out-of-range or stolen, and for searching the transporting unit. A user can view the data stored, data computed via. Algorithms and alerts are generated by the data server.
Owner:NGYEUN MARK VUONG TOAN +1
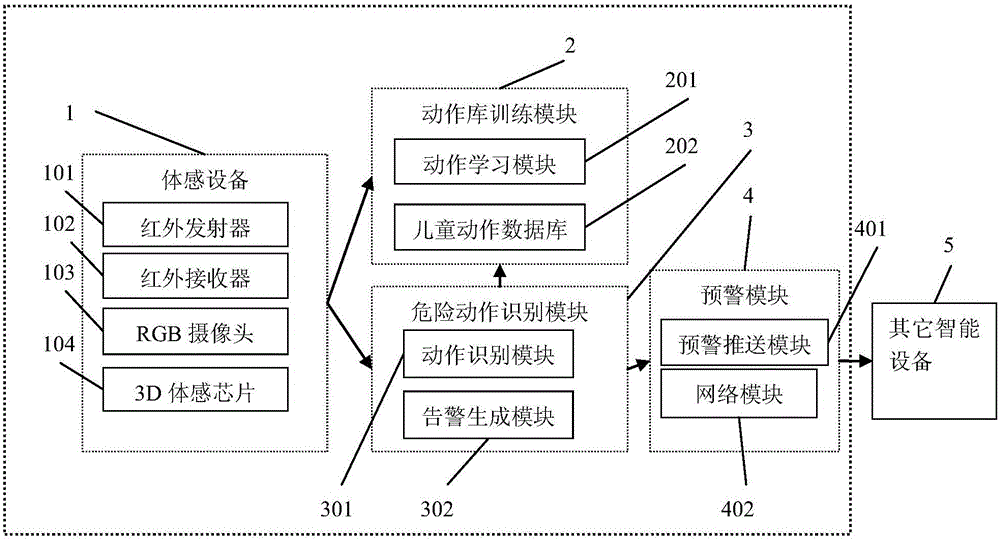
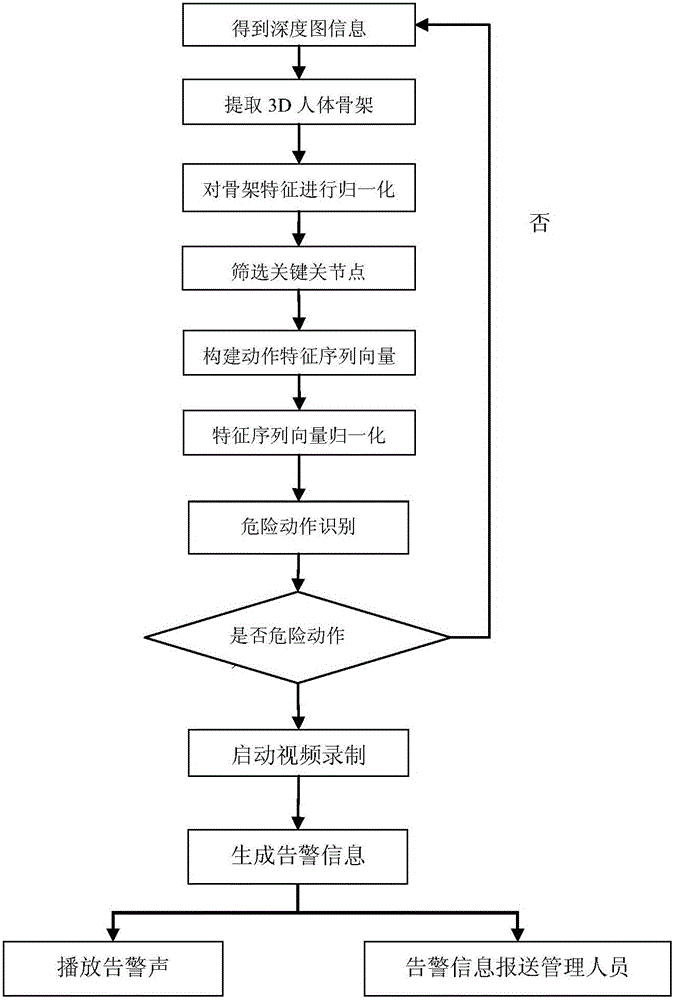
Motion-sensing technology based kindergarten intelligent monitoring method
InactiveCN106056035AScalableMeet the needs of different scenariosImage enhancementImage analysisHuman bodyFeature vector
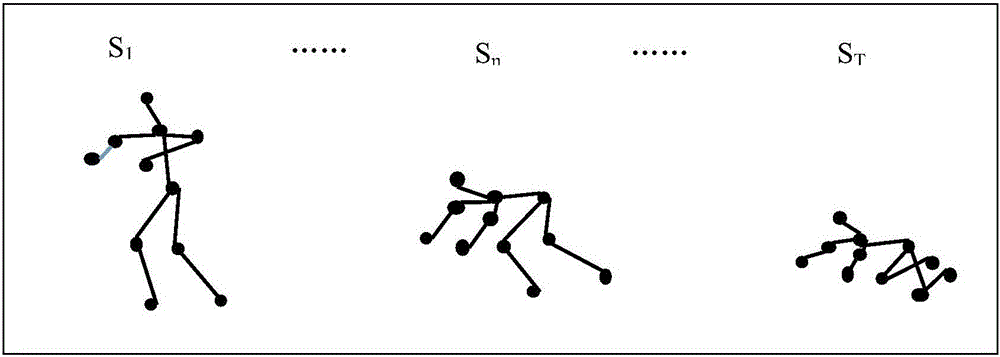
The invention relates to a motion-sensing technology based kindergarten intelligent monitoring method, which comprises the steps of installing 3D motion-sensing equipment in a kindergarten, capturing 3D human body skeleton images of children in real time, extracting key joint feature vectors, inputting the feature vectors into a motion classifier so as to carry out motion classification, and finding out motions with the highest matching degree, wherein motion classification is trained in advance through a machine learning method. The method provided by the invention can realize detection, analysis and tracking for human body motion postures and figure motion trails through a three-dimensional visual perception technology, and motions of the children are captured dynamically in real time, so that dangerous behaviors such as fighting, tumbling and boundary crossing can be predicted, and a warning is given out in advance so as to reduce occurrence of kindergarten accidents.
Owner:NANJING HUAJIE IMI TECH CO LTD
Border-crossing detection method and border-crossing monitoring system based on video monitoring
InactiveCN104680555AReduce work intensityImprove monitoring proactivenessImage analysisClosed circuit television systemsVideo monitoringBorder crossing
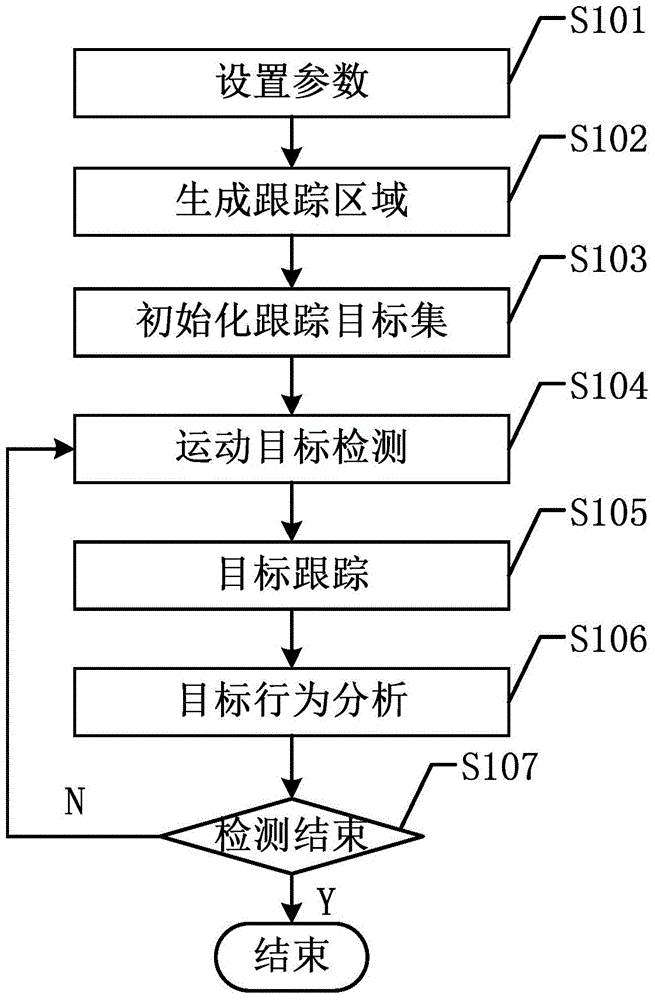
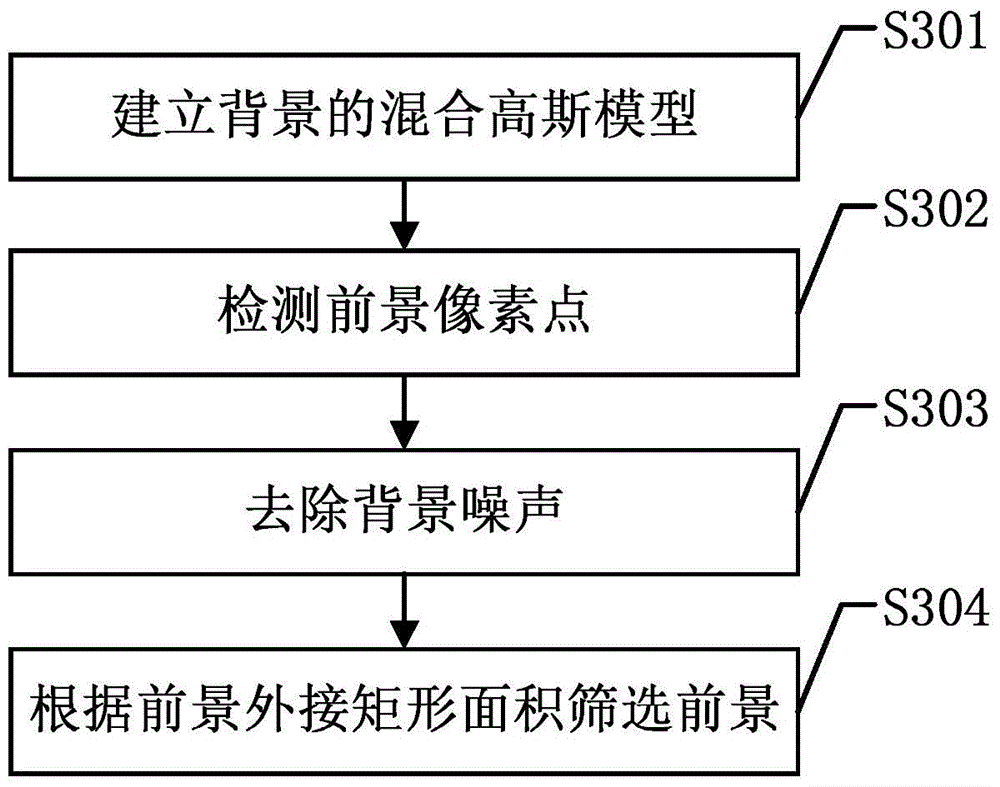
The invention discloses a border-crossing detection method and a border-crossing monitoring system based on video monitoring. The border-crossing detection method comprises the following steps: obtaining a closed boundary line and a safe passage line according to an endpoint of the top safe passage line of a boundary line set by a user; obtaining a tracking region through expansion and reduction of the closed boundary line; detecting a moving object of each frame of video monitoring image, to screen out a moving object region in the tracking region; performing matching tracking on the screened moving object region and a tracking object, to obtain a coordinate queue of the tracking object; performing object behavior analysis on the tracking object; judging whether a border-crossing risk exists; if no border-crossing risk exists, doing nothing; if a great border-crossing risk exists, warning; otherwise, judging whether an early warning for the current abnormal situation is required according to a security identifier; when warning or early warning, marking a target track according to the target coordinate queue. According to the invention, the border-crossing detection is performed according to the set boundary, the border-crossing detection for large regions and complex sites can be implemented, and the scope of application is wide.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
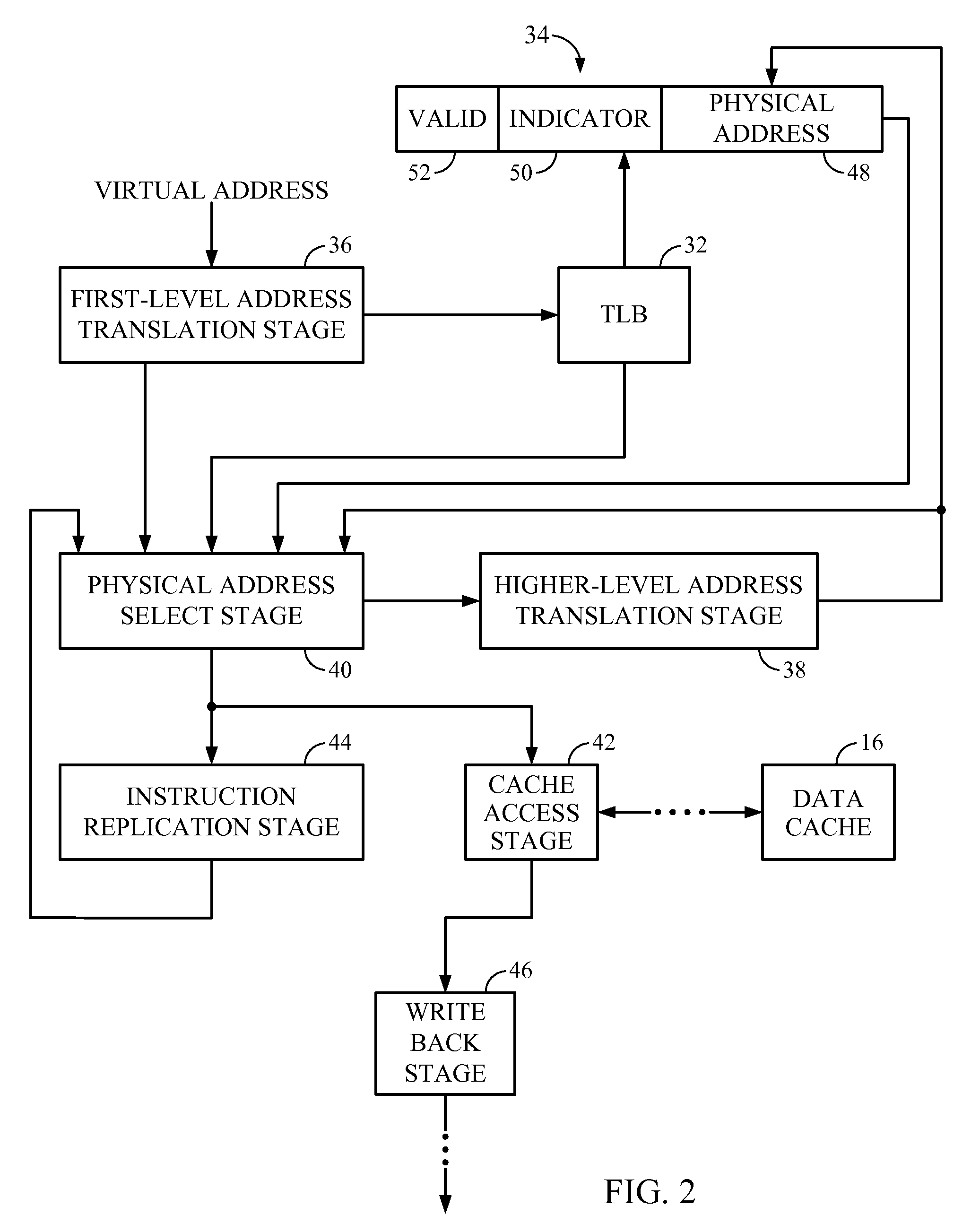
Address Translation Method and Apparatus
ActiveUS20080189506A1Address performance requirementsMultiple address translationMemory architecture accessing/allocationEnergy efficient ICTBoundary crossingOperating system
Address translation performance within a processor is improved by identifying an address that causes a boundary crossing between different pages in memory and linking address translation information associated with both memory pages. According to one embodiment of a processor, the processor comprises circuitry configured to recognize an access to a memory region crossing a page boundary between first and second memory pages. The circuitry is also configured to link address translation information associated with the first and second memory pages. Thus, responsive to a subsequent access the same memory region, the address translation information associated with the first and second memory pages is retrievable based on a single address translation.
Owner:QUALCOMM INC
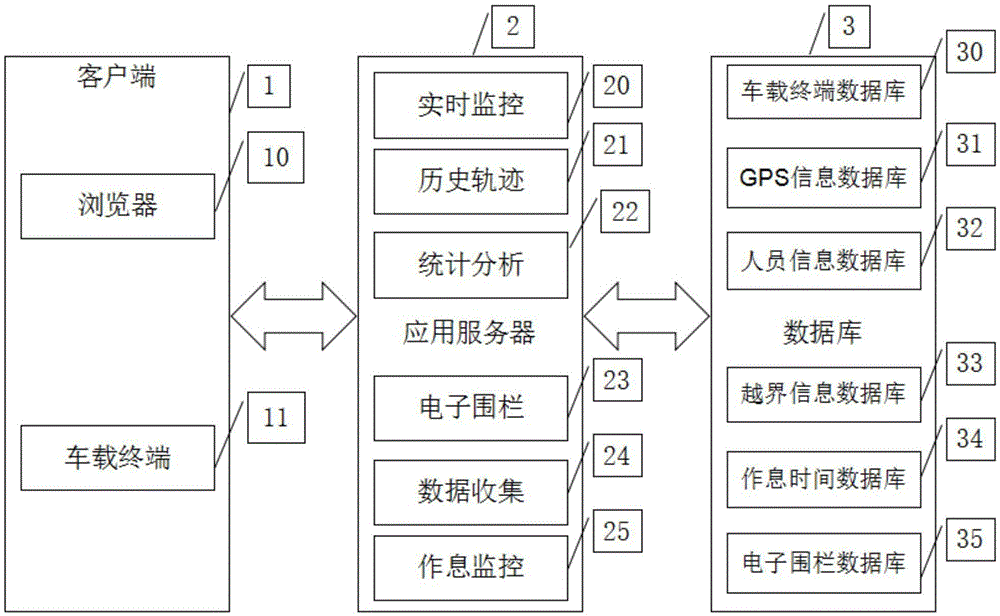
GIS-based smart city management special vehicle monitoring system
ActiveCN105575110ARealize real-time monitoringEasy to monitorRoad vehicles traffic controlInformatizationStatistical analysis
The invention relates to a GIS-based smart city management special vehicle monitoring system, which takes an LBS system as a framework and a browser as a display platform. The system comprises a real-time monitoring service module, which provides positioning parameters for a historical track service module and a work and rest monitoring service module; the historical track service module, which can present the historical driving tracks of special vehicles on a digital map; a statistical analysis module, which can search historical boundary-crossing information of the special vehicles; and an electronic fence service module, which can carry out driving restriction on the special vehicles in some area, and can manage the special vehicles conveniently. The GIS-based smart city management special vehicle monitoring system realizes real-time monitoring of the special vehicles, facilitates to carry out basic data monitoring and command and dispatch on the special vehicles during city management, can present and display the historical driving tracks of the special vehicles, can trigger an alarm when the special vehicles cross boundaries, and can improve level of informatization of a supervision department and reduce management cost.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
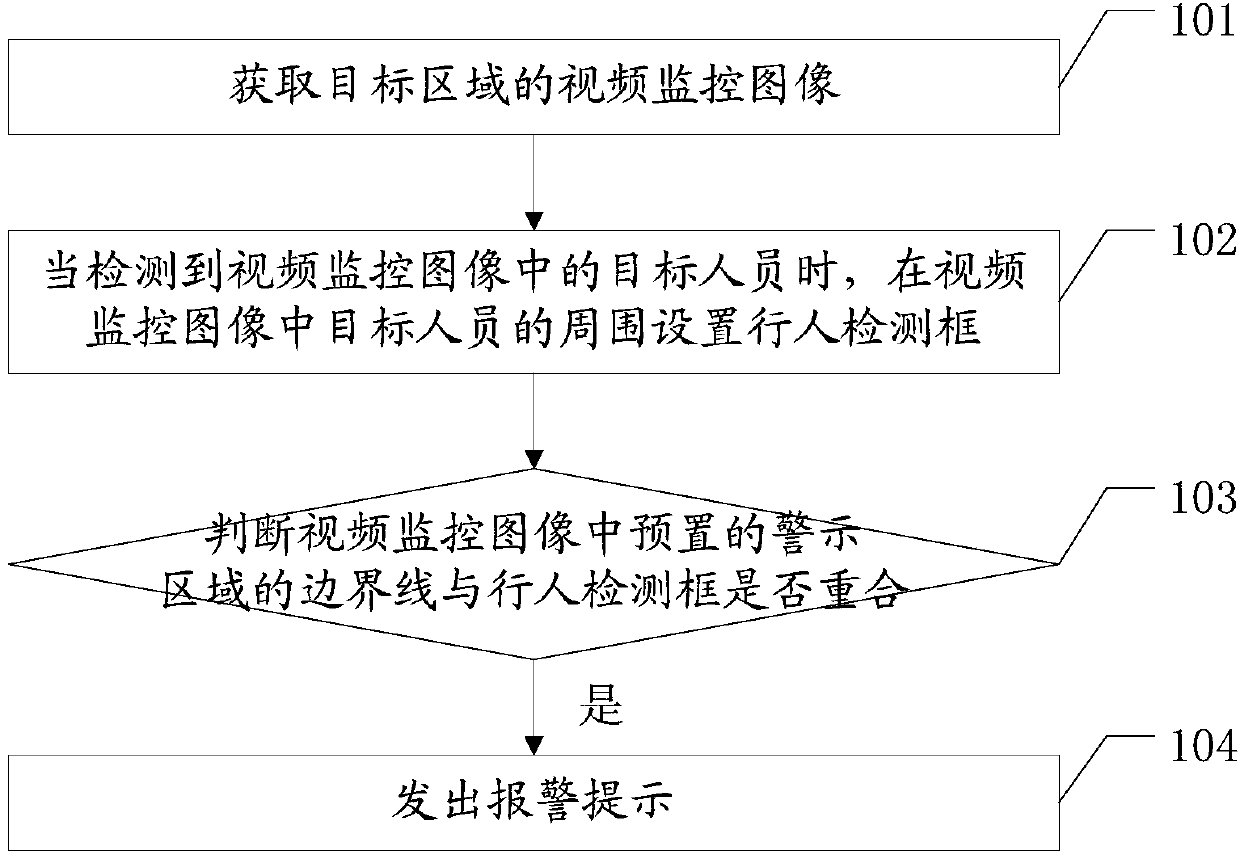
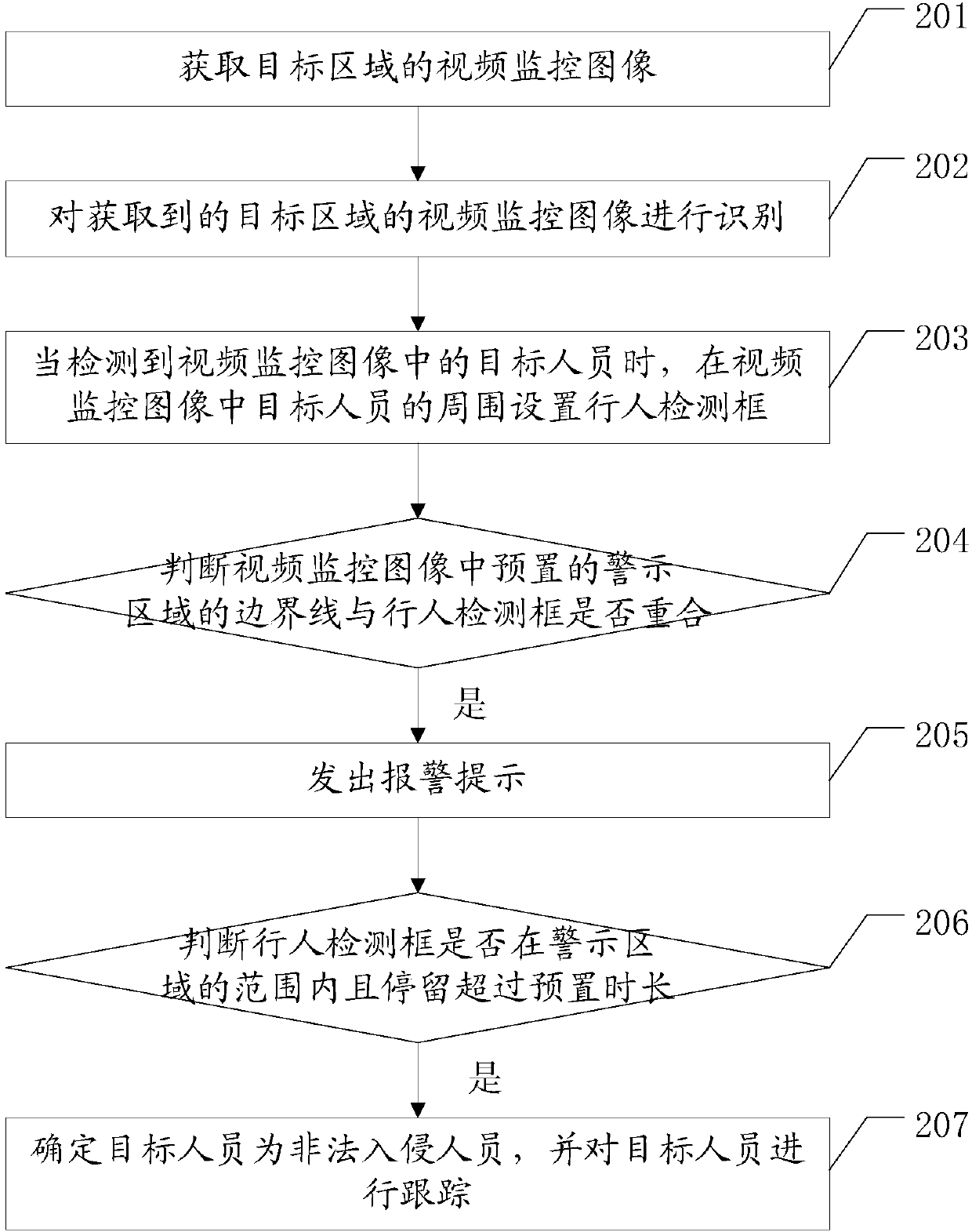
Alarm method and device for illegal boundary crossing based on video monitoring
InactiveCN107818651AReal-time accurate automatic analysisReduce security risksImage enhancementImage analysisVideo monitoringComputer vision
The embodiments of the application disclose an alarm method and device for illegal boundary crossing based on video monitoring. The method and the device are used to make a real-time, accurate and automatic analysis of vide pictures and automatically give an alarm for potential safety risks, so as to reduce potential safety hazard and avoid disasters. The method disclosed by one embodiment of theapplication includes the following steps: acquiring a video monitoring image of a target area; when detecting a target person in the video monitoring image, setting a pedestrian detection box around the target person in the video monitoring image; determining whether the boundary line of a preset warning area in the video monitoring image coincides with the pedestrian detection box; and if the pedestrian detection box coincides with the boundary line, giving an alarm.
Owner:华润电力技术研究院有限公司 +1
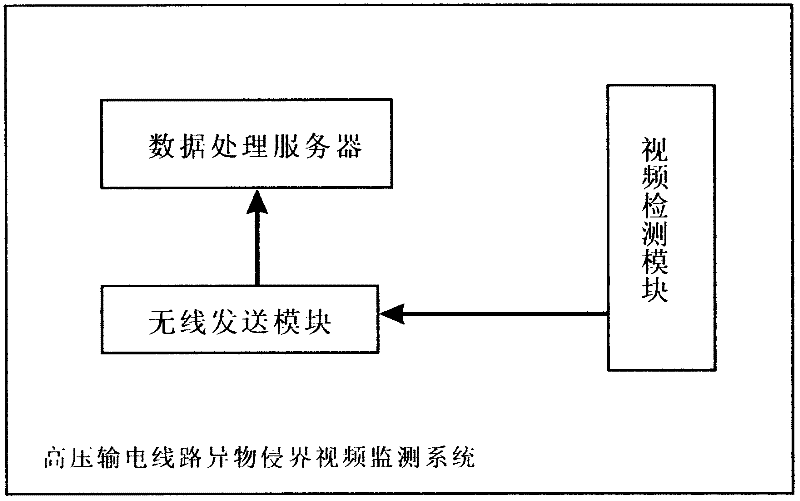
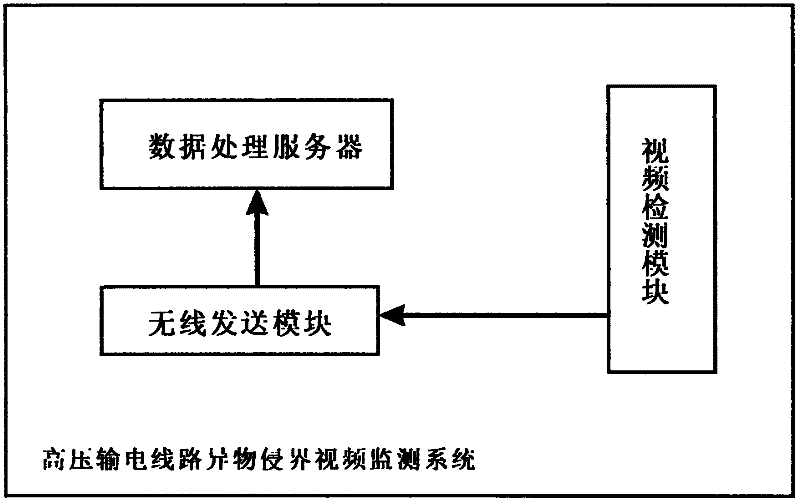
Video monitoring system for monitoring boundary crossing of foreign matter in high voltage power transmission line
InactiveCN102404555AReal-time monitoring and detection of security conditionsMonitor and detect security conditionsCharacter and pattern recognitionClosed circuit television systemsForeign matterVideo monitoring
The invention aims to provide a video monitoring system for monitoring boundary crossing of a foreign matter in a high voltage power transmission line based on a wireless video sensor network with high availability and effectiveness, which comprises a video detecting module, a wireless sending module and a data processing server. The system is characterized in that the video detecting module takes pictures in the area close to an electric wire tower and transmits the image data to the data processing server by the wireless sending module. Then the data processing server processes the images, detects the connecting area of a horizontal projection and a vertical protection of the images, judges if a foreign matter comes into a communicating area, displays the concrete coordinate of the foreign matter and gives an alarm in case of detecting the foreign matter.
Owner:XIAN RADIO OFCAM INFORMATION TECH CO LTD
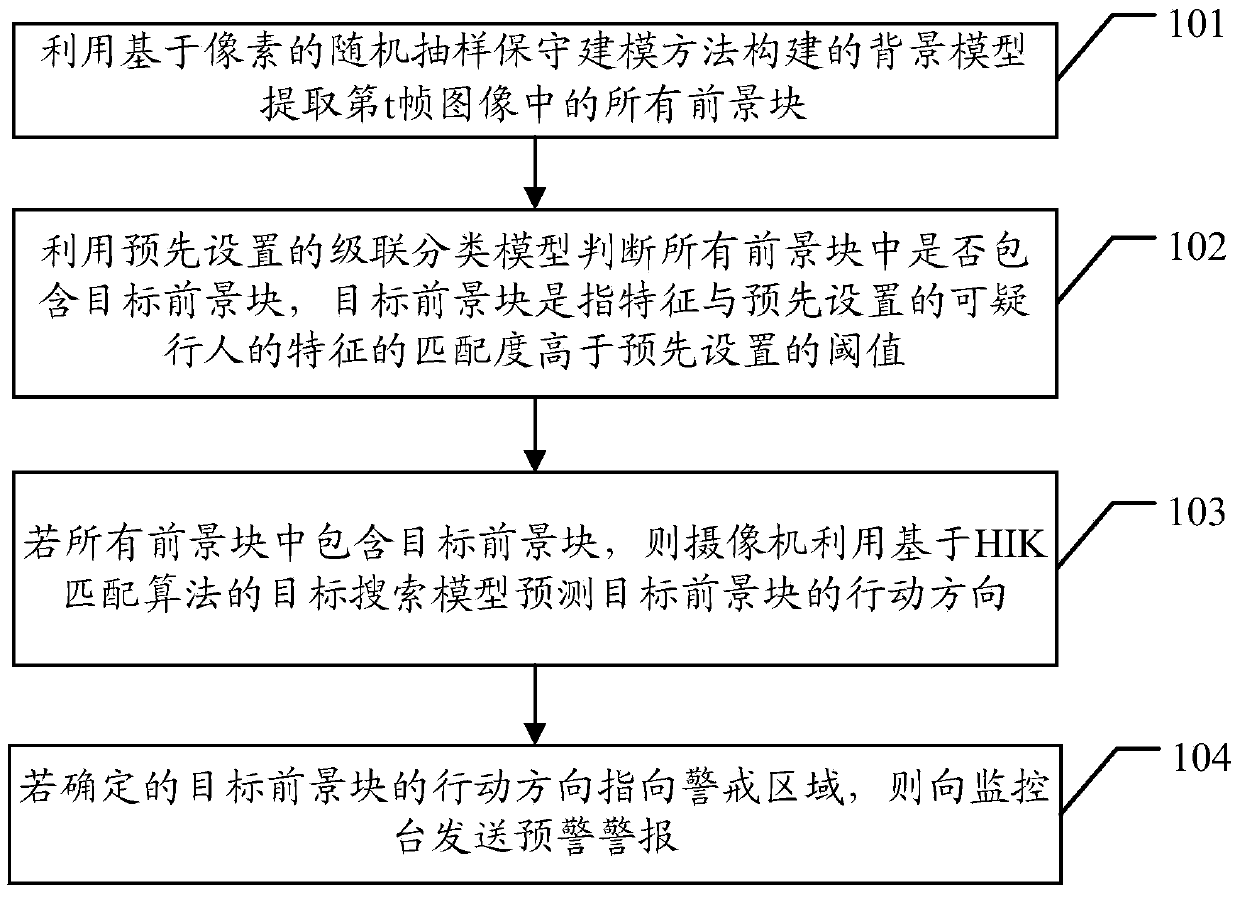
Early warning method and camera
ActiveCN104200466ARealize real-time trackingImage analysisClosed circuit television systemsMatch algorithmsPixel based
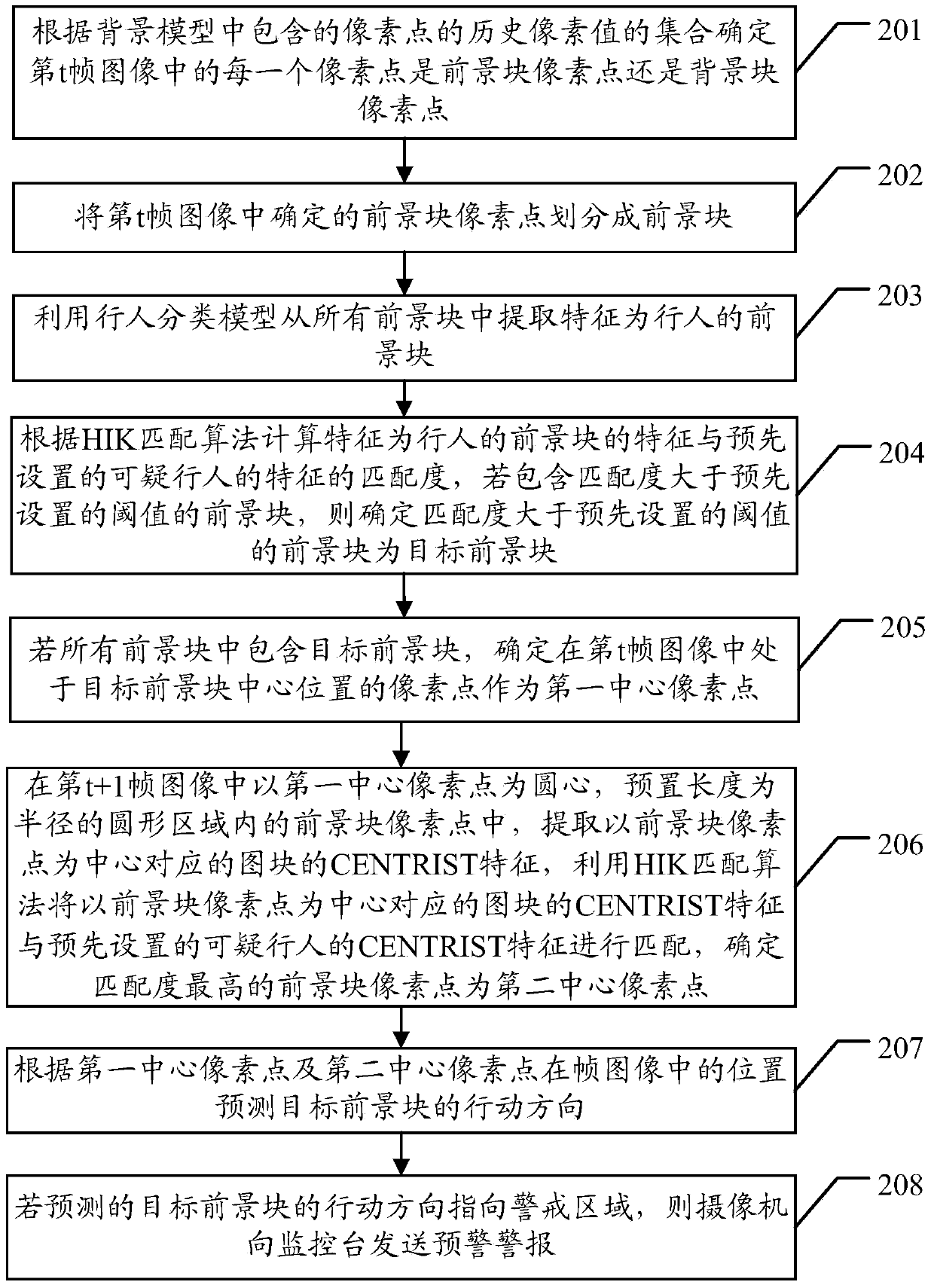
The embodiment of the invention discloses an early warning method and a camera. The early warning method and the camera solve the problem that the boundary crossing time cannot be early warned by the camera. According to the early warning method and the camera, the method comprises the following steps: extracting all foreground blocks in a t-th frame image by utilizing a background model constructed with a pixel-based random sampling conserved modeling method by the camera, and judging whether target foreground blocks are contained in all the foreground blocks by utilizing a preset cascade classification model, if the target foreground blocks are contained in all the foreground blocks, predicting the action orientation of the target foreground blocks by utilizing the target search model based on a histogram intersection kernel (HIK) matching algorithm, if the action orientation of the determined target foreground blocks point to a warning region, sending an early warning alarm to a monitoring station by the camera. By predicting the action orientation of the target foreground blocks, real-time tracking of the target foreground blocks can be effectively realized, and early warning can be effectively performed.
Owner:DONGGUAN ZKTECO ELECTRONICS TECH
Cleaning robot and block selection method and device for same
ActiveCN107913039AAvoid repeated cleaningAvoid Uncleaned SituationsCarpet cleanersFloor cleanersCross-linkEngineering
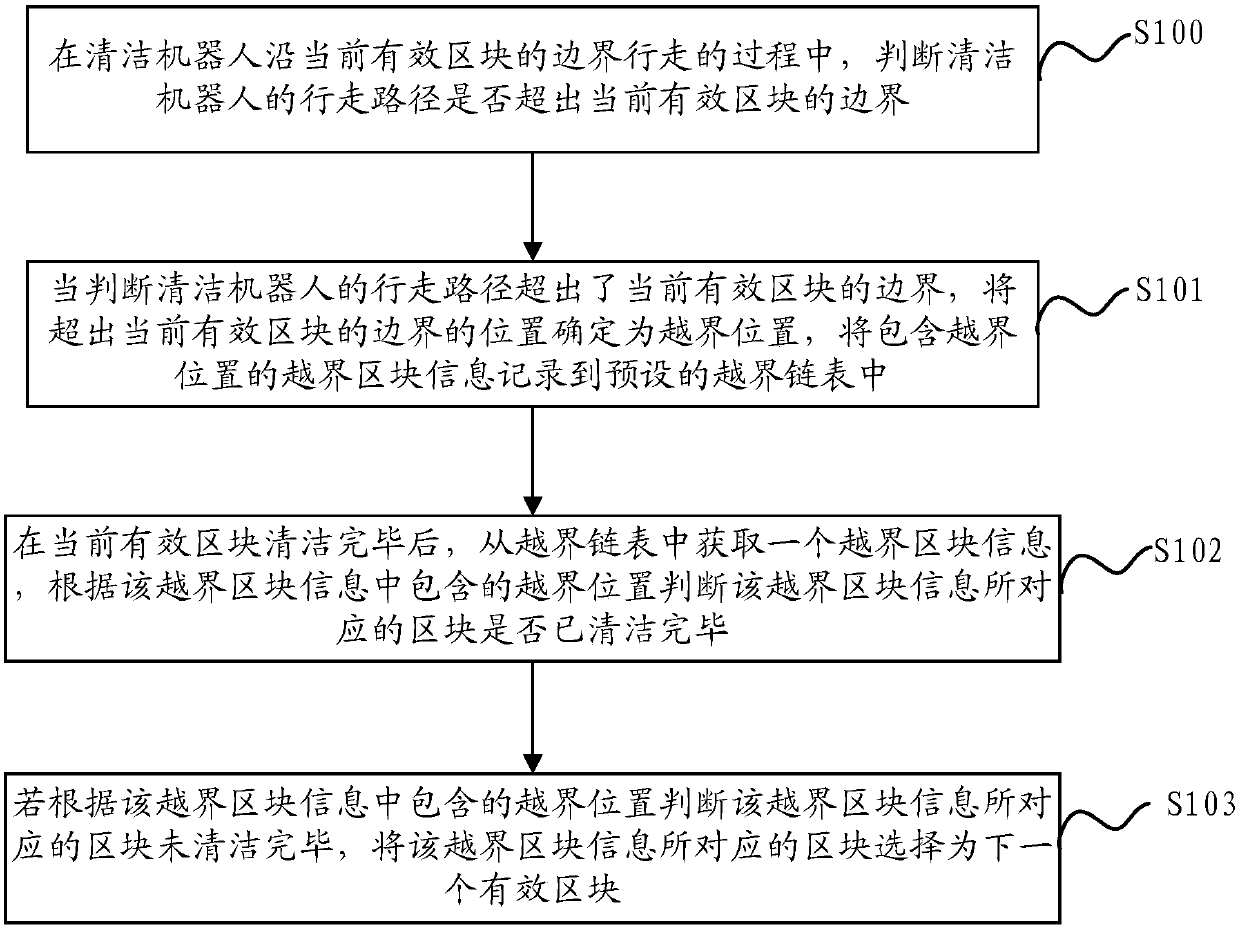
The invention discloses a cleaning robot and a block selection method and a block selection device for the cleaning robot. The block selection method includes judging whether the walking path of the cleaning robot exceeds the boundary of the current effective block or not when the cleaning robot walks along the boundary of the current effective block; if so, then determining the position out of the boundary of the current effective block as a boundary-crossing position according to the judgement result, and recording boundary-crossing block information containing the boundary-crossing positionto a preset boundary-crossing linked list; after finishing cleaning of the current effective block, acquiring one boundary-crossing information from the boundary-crossing linked list, and judging whether the block corresponding to the boundary-crossing block information is cleaned or not according to the boundary-crossing position contained in the boundary-crossing block information; if no, thendetermining the block corresponding to the boundary-crossing block information as the next effective block. By the method, repeated cleaning of the block can be avoided, cleaning efficiency can be improved, omission of cleaning of the block can be avoided, and cleaning quality can be guaranteed.
Owner:BEIJING QIHOO TECH CO LTD
Liquid crystal display and manufacturing method thereof
ActiveUS20050018111A1Solve the real problemOptical filtersNon-linear opticsResistLiquid-crystal display
A method of manufacturing a liquid crystal display panel is provided, which includes: coating a negative organic photoresist on a substrate; performing divisional light exposure with a plurality of shots including first and second shots adjacent to each other; and developing the photoresist to form a light blocking member having a plurality of openings, wherein the first and the second shots have a boundary crossing the openings.
Owner:SAMSUNG DISPLAY CO LTD
Circuit and method for glitch correction
InactiveUS20080258835A1Easy to operateEfficient detectionAngle modulation detailsBoundary crossingGlitch
Correction of glitches output from a delta-sigma modulator is accomplished using an integer boundary crossing detector and a FIR filter. The detector monitors a portion of an input to the modulator. The detector recognizes a transition from an all 1's bit pattern to an all 0's bit pattern or vice versa as representative of potential for a glitch to be present on the output of the modulator. The detector responsively generates condition detection output. Receipt of such condition detection output triggers the generation of a correction signal by the filter. The correction signal is, at least substantially similar, in magnitude but opposite in sign from to the expected glitch at the output of the modulator. The correction signal is added to the output of the modulator to substantially eliminate the glitch.
Owner:CONVERSANT INTPROP MANAGEMENT INC
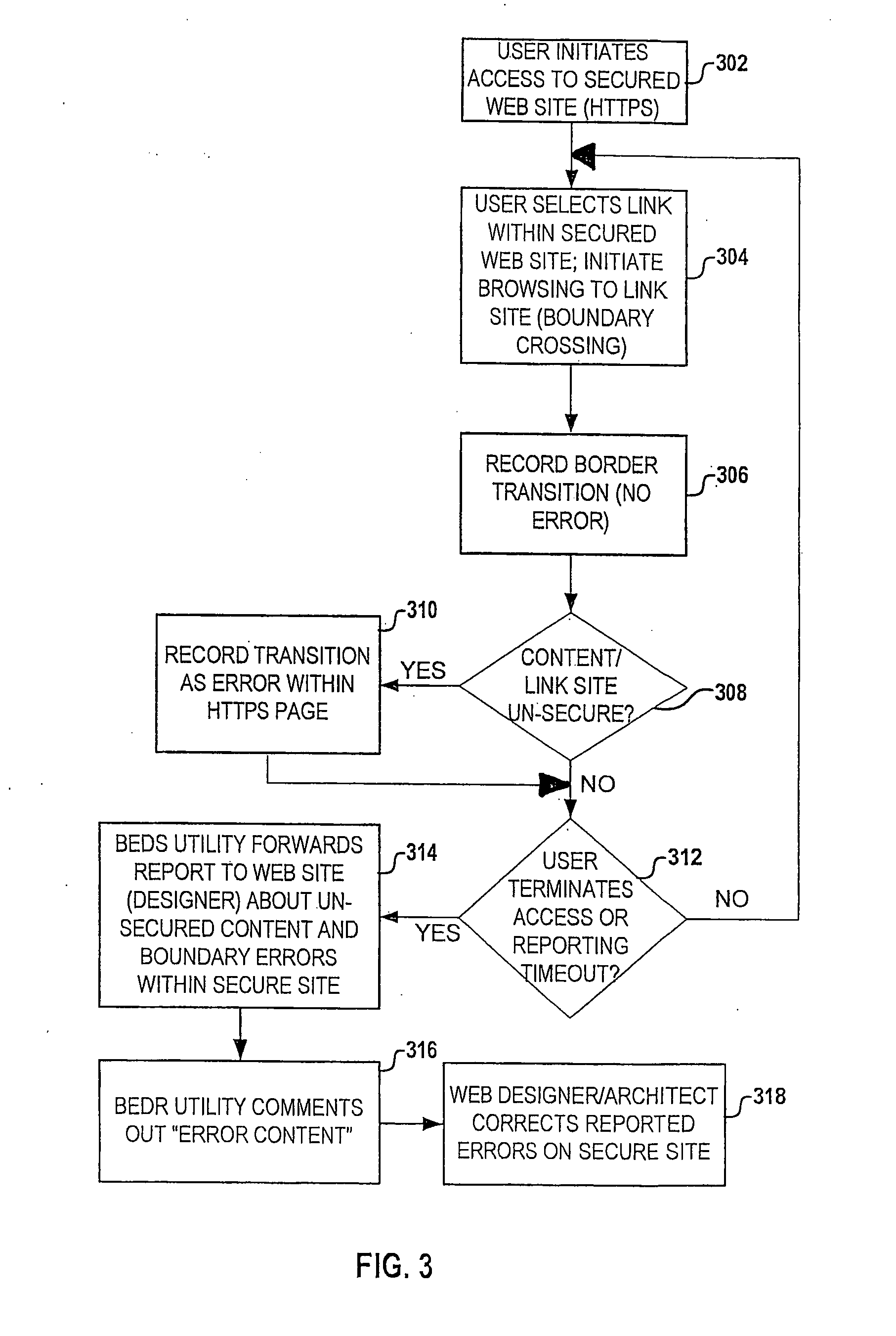
Architecture for automatic HTTPS boundary identification
InactiveUS20070240225A1Quick identificationMemory loss protectionError detection/correctionWeb siteWeb application
A method, system, and computer program product that enables a web designer / architect to be dynamically notified of the presence of unsecured content within a secure web site based on testing or users browsing activities. A boundary error detection and reporting (BEDR) utility is added to the web browser, web application server, or both. The BEDR utility provides / activates a function that tracks a user's movements on the secure web site. Whenever a link crosses an HTTP-to-HTTPS boundary, the BEDR utility records the transition as informational. The utility also records any HTPS-to-HTTP boundary crossings and any objects not from the same HTTPS source as an error. The BEDR utility automatically addresses the boundary problem, such as through stripping out code or objects, and also automatically reports these boundary crossings to a Web designers and / or architects, who may utilize this reported data to correct these errors on the secure site.
Owner:IBM CORP
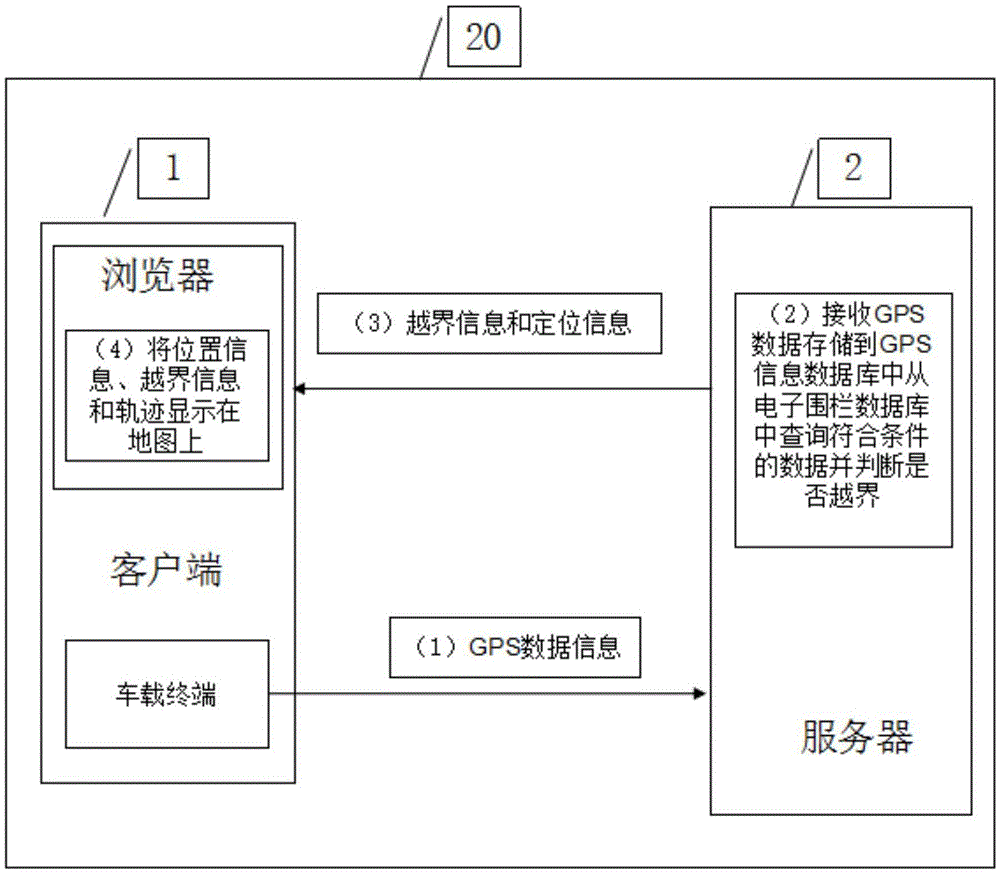
Method of determining whether dynamic position of monitoring terminal exceeds virtual fence
InactiveCN108303719AAccurate judgmentOvercome deficienciesSatellite radio beaconingEarly warning systemComputer science
The invention discloses a method of determining whether dynamic position of a monitoring terminal exceeds a virtual fence. The method of determining whether dynamic position of a monitoring terminal exceeds a virtual fence establishes a virtual fence by means of a virtual fence defining module in a virtual fence early warning system, and utilizes the monitoring terminal in the virtual fence earlywarning system to obtain the dynamic positional information of the monitoring terminal. The method of determining whether dynamic position of a monitoring terminal exceeds a virtual fence includes thesteps: when the virtual fence is a closed figure which is formed through enclosure of parallel edges, and when the virtual fence is a closed figure which is formed through enclosure of curves, and when the virtual fence is a non-closed figure, respectively performing the corresponding judgment of boundary crossing, thus solving the problem that the prior art cannot judge whether the dynamic position of the monitoring terminal exceeds the virtual fence, and realizing the technical effect of being able to accurately judge whether the dynamic position of the monitoring terminal exceeds the virtual fence.
Owner:SHANGHAI UNIVERSITY OF ELECTRIC POWER
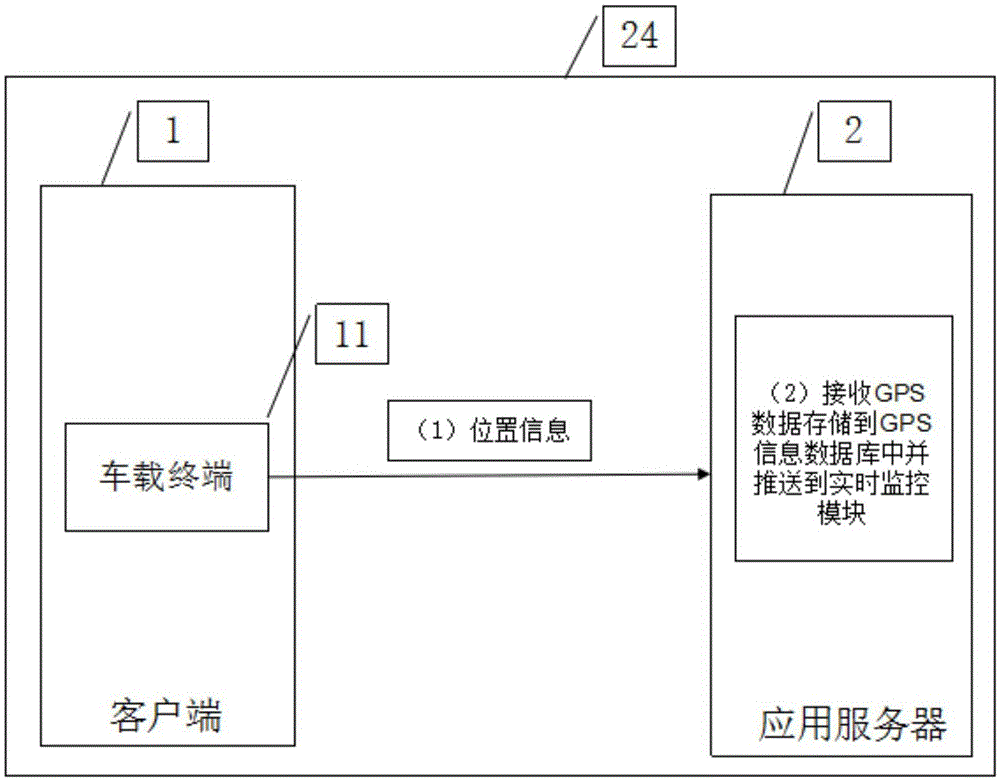
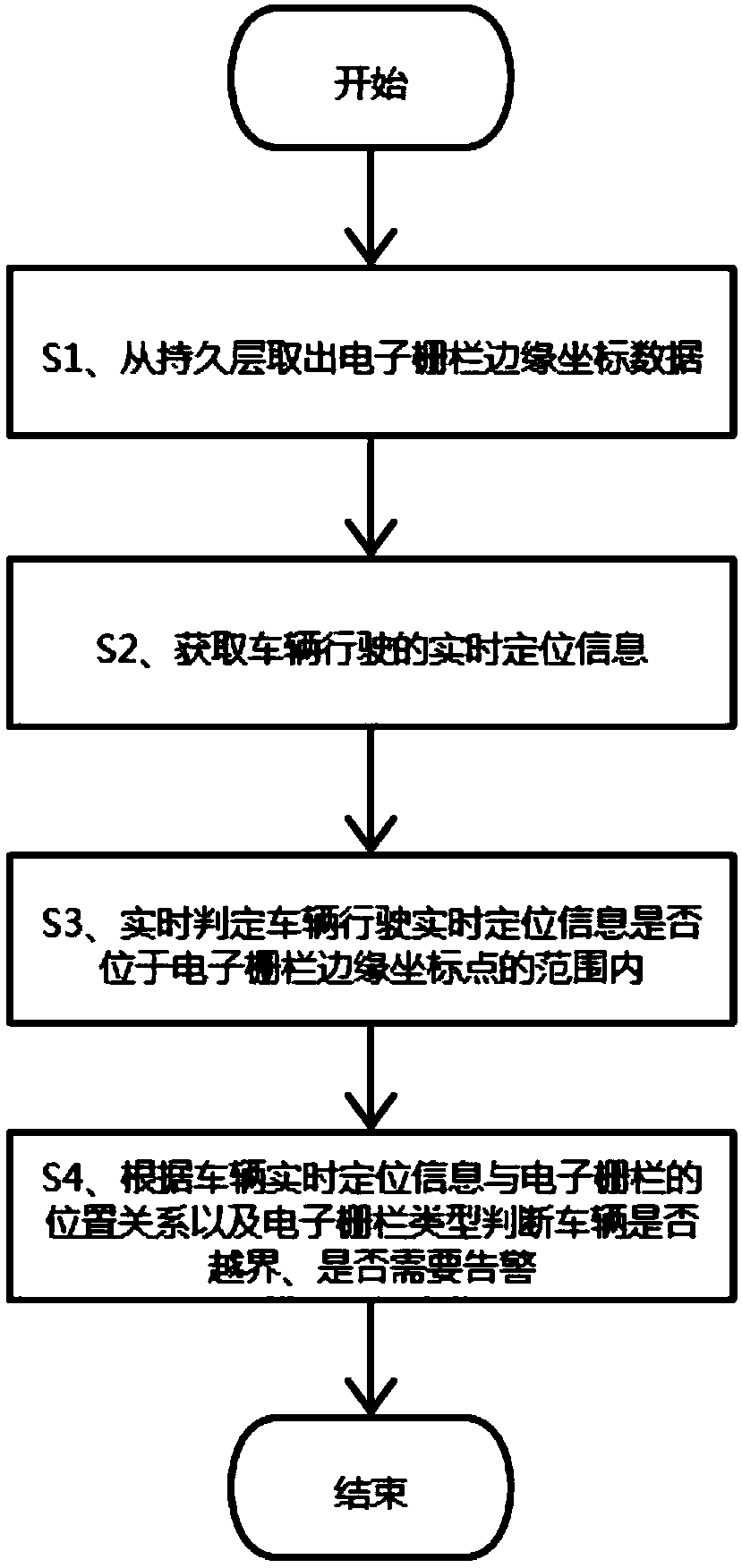
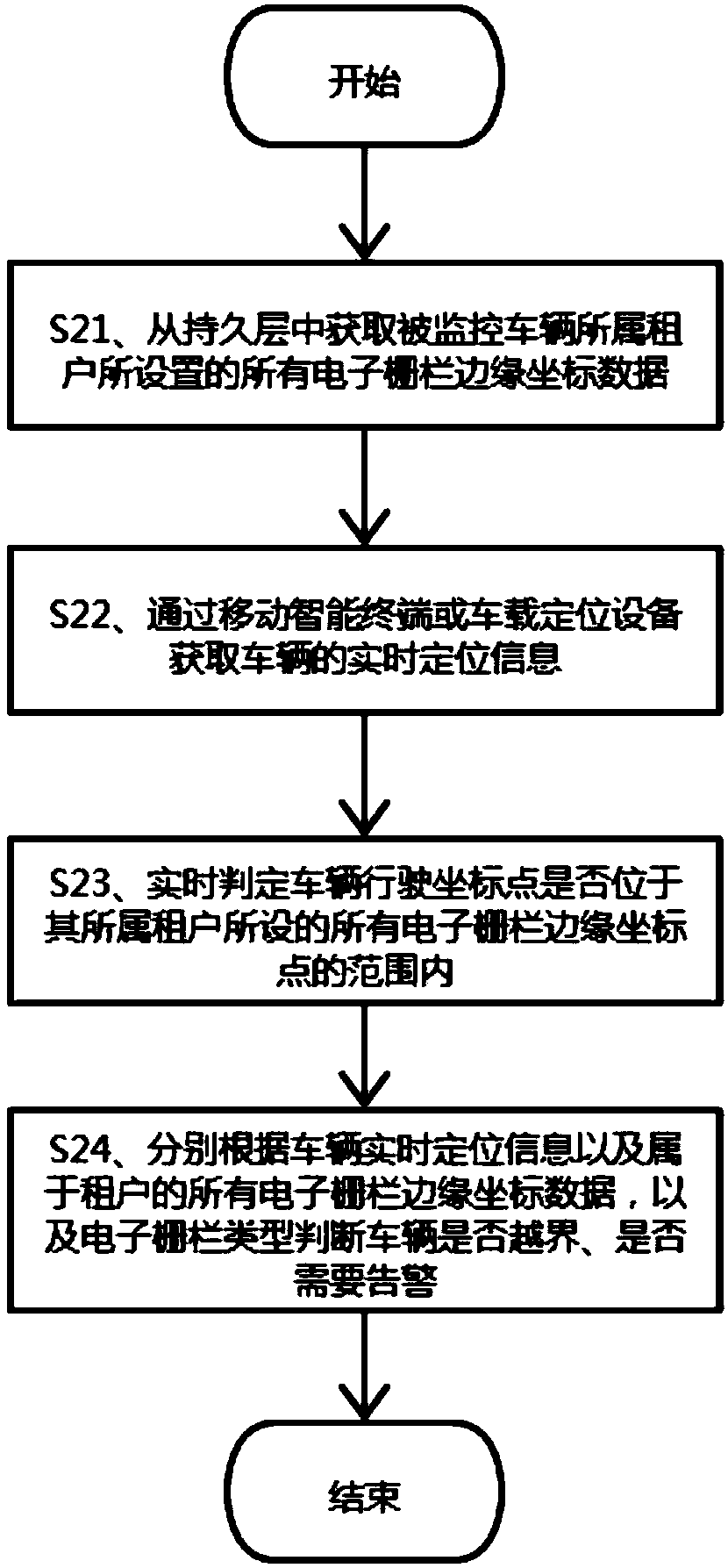
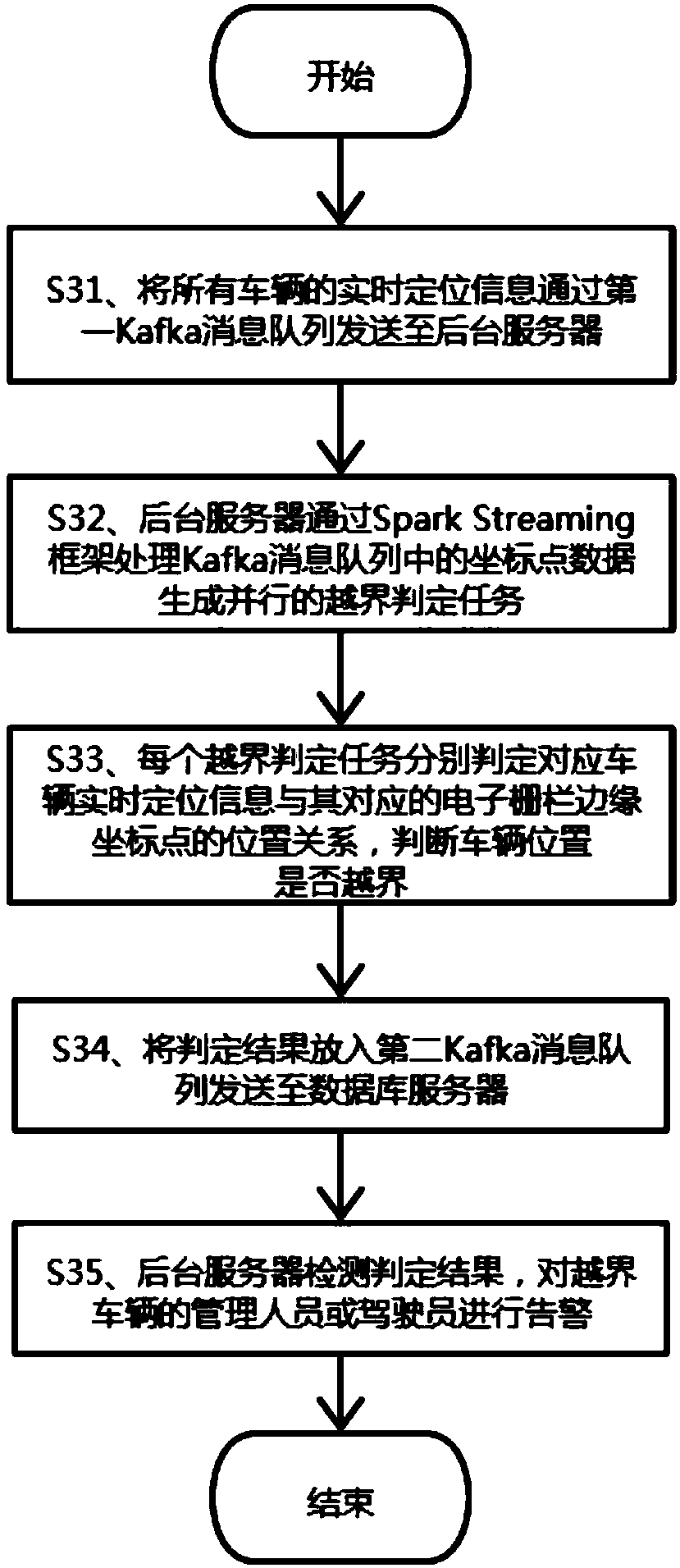
Vehicle boundary crossing recognition and alarm method and system based on electronic fence
InactiveCN109413581AHigh economic valueParticular environment based servicesVehicle wireless communication serviceDatabase serverTime-sharing
The invention discloses a vehicle boundary crossing recognition and alarm method and system based on an electronic fence. The method comprises the following steps: extracting edge coordinate point data of the electronic fence from a persistent layer; acquiring real-time running location information of a vehicle; judging whether the real-time running location information of the vehicle is within the range of edge coordinate points of the electronic fence or not in real time; and judging whether the vehicle crosses a boundary or not and whether alarm needs to be made or not according to a position relationship between the real-time location information of the vehicle and the electronic fence. The system comprises a vehicle location unit, a background server and a database server. The methodand the system can process vehicle boundary crossing recognition and alarm events under various complex conditions in real time, can be applied to the aspects of determination of return areas of time-sharing leased vehicles, restriction of the use areas of the leased vehicles, statistics of the running area data of vehicles and the like, and have a wide application range and relatively high economical value.
Owner:HAINAN YILE IOT TECH CO LTD
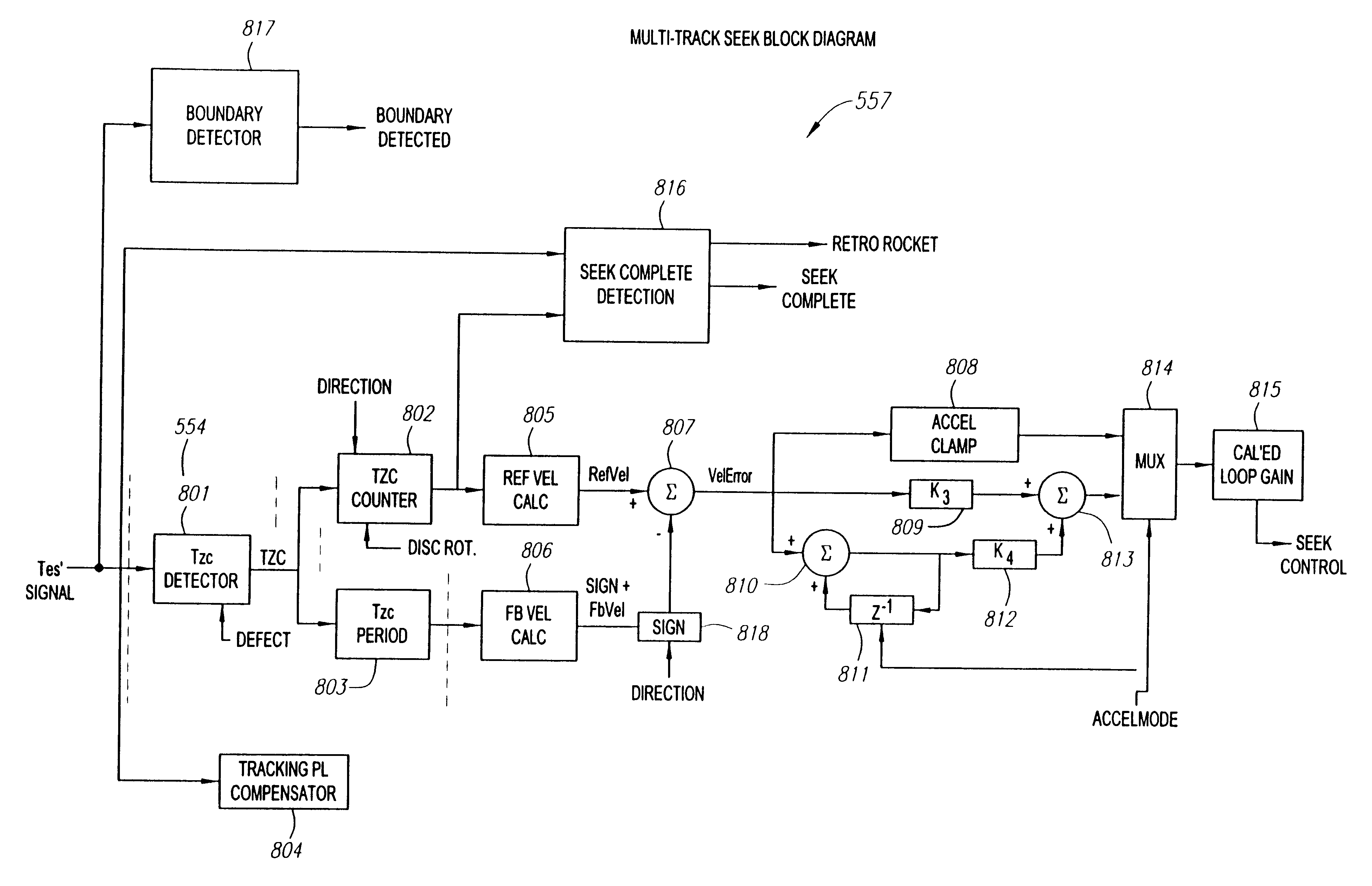
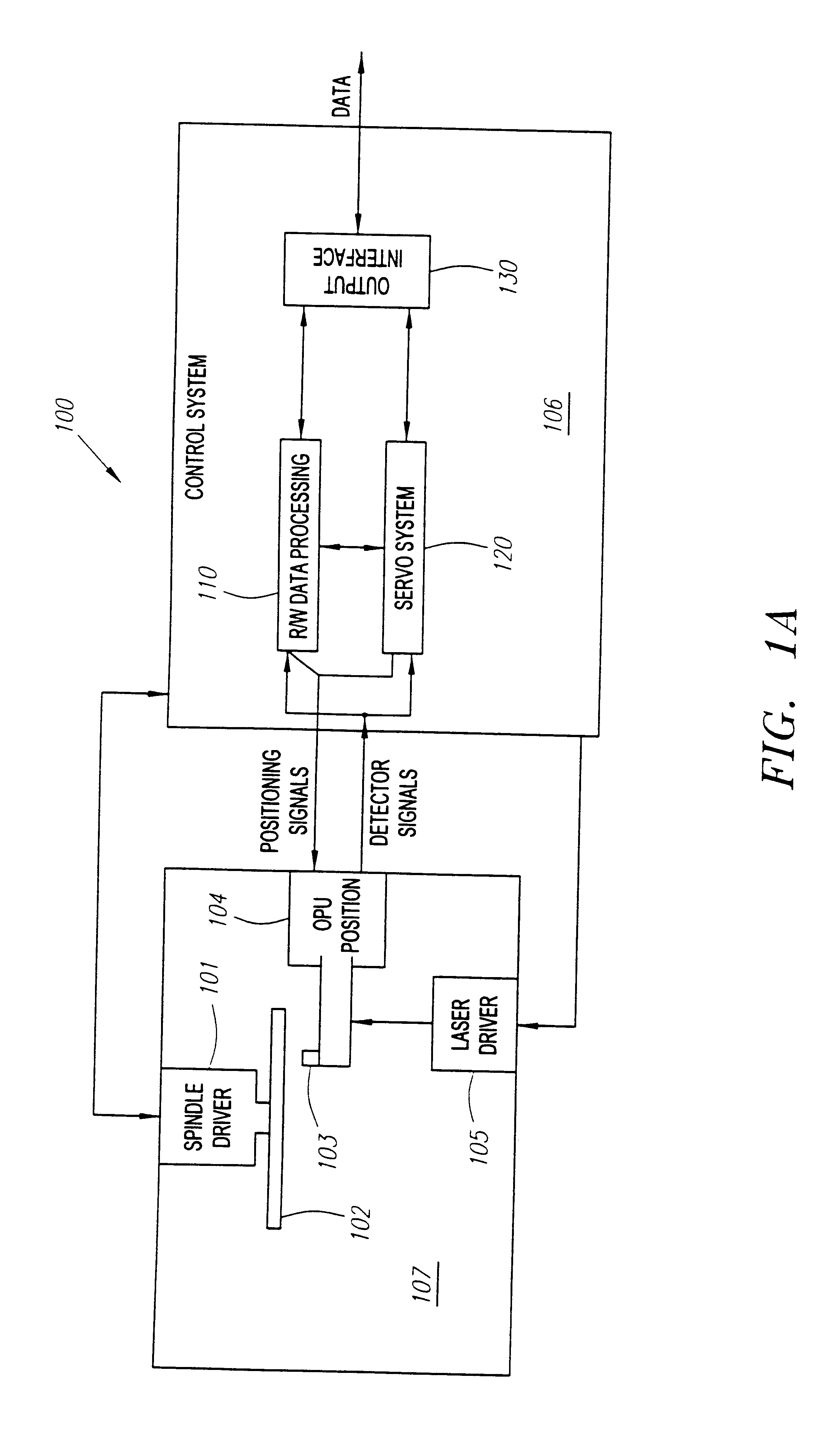
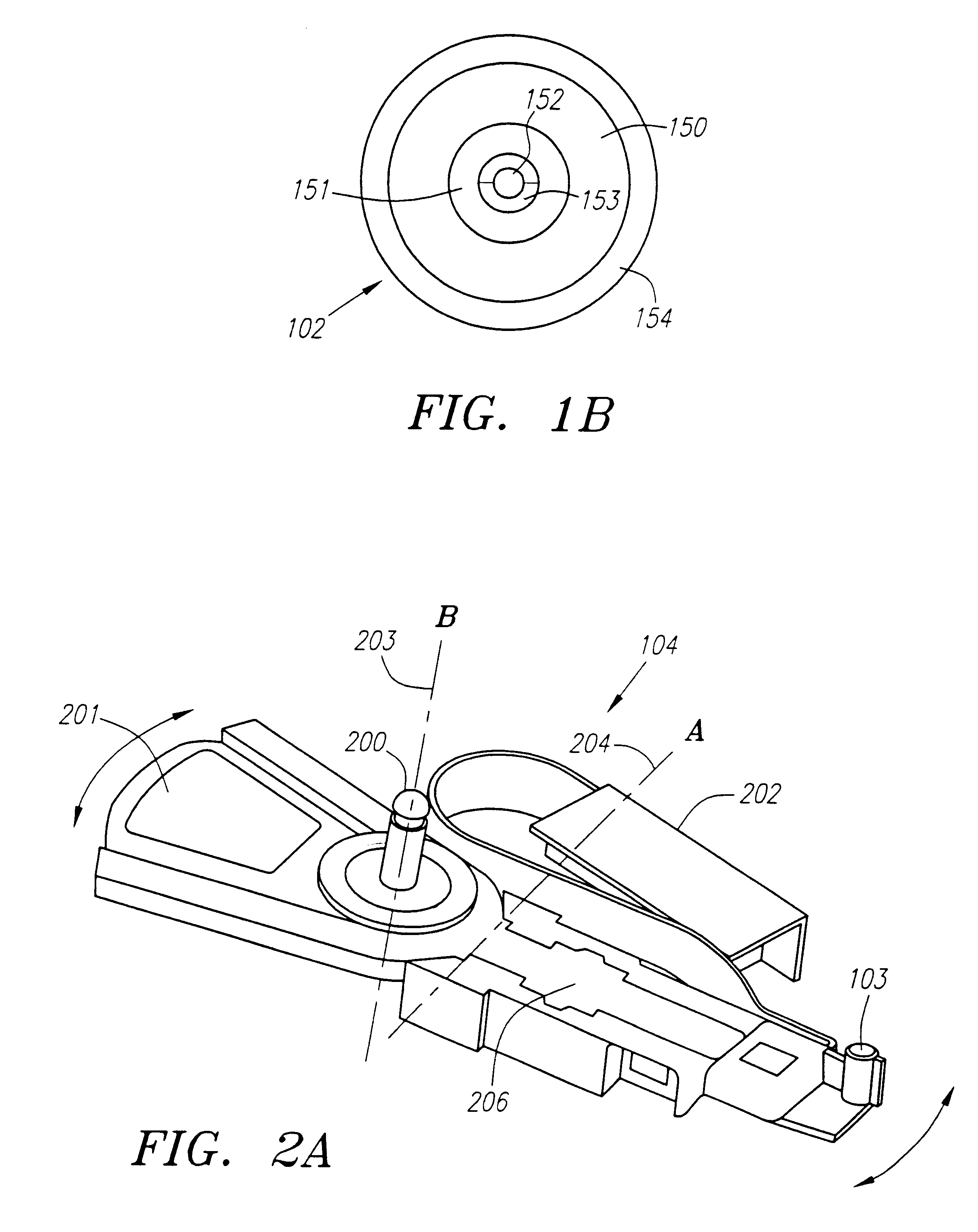
Tracking and focus servo system with a media type boundary crossing detector
A boundary crossing detector in a tracking and focus servo system of an optical disk drive is presented. A tracking error signal can be monitored as an optical pick-up unit of the optical disk drive is allowed to move across an optical media in the optical disk drive. If a peak-to-peak value of the tracking error signal changes by a threshold value, than the boundary crossing can be indicated.
Owner:RPX CORP
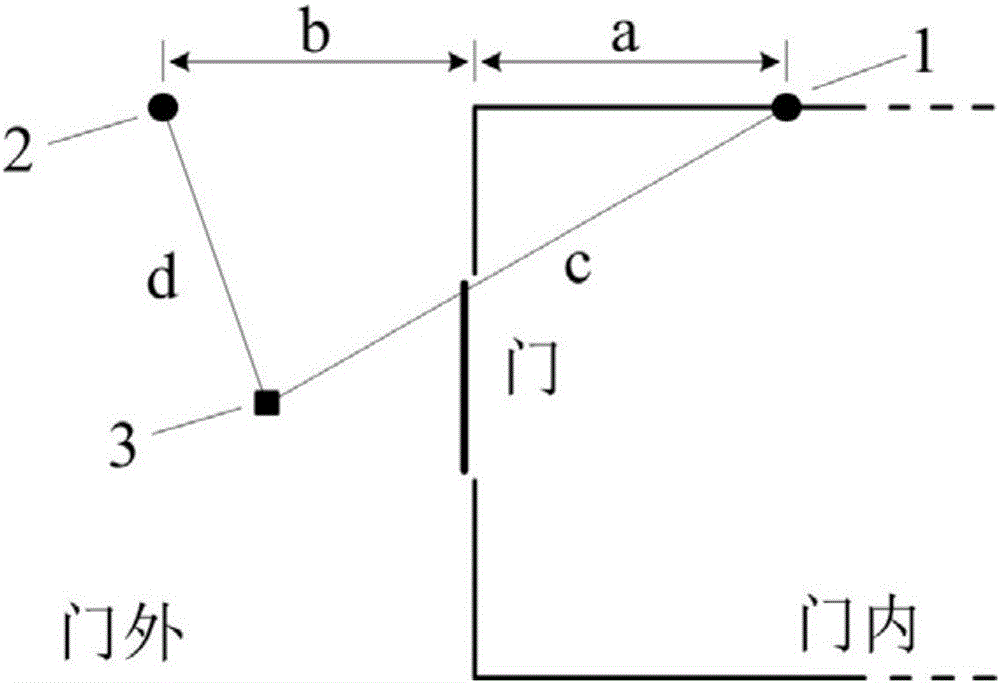
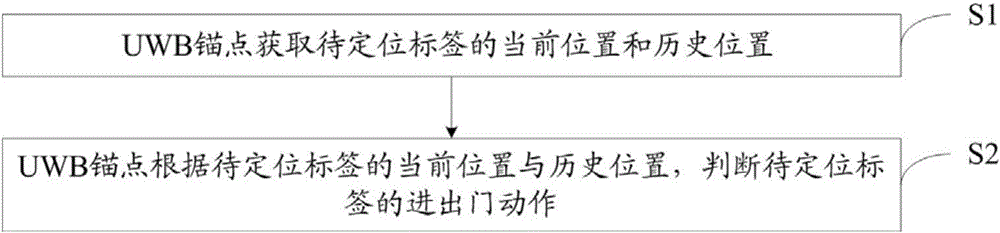
Personnel entering and leaving management system and boundary crossing judgment method thereof
The invention discloses a personnel entering and leaving management system and a boundary crossing judgment method thereof, and belongs to the field of communication. The personnel entering and leaving management system comprises a UWB anchor point and multiple tags to be located which can perform data communication with the UWB anchor point. The UWB anchor point is connected with a first antenna which is used for being arranged at the internal side of the door and a second antenna which is used for being arranged at the external side of the door. The first antenna and the second antenna are symmetrically arranged at the internal and external sides of the door. The advantages of the personnel entering and leaving management system and the boundary crossing judgment method thereof are that only the UWB anchor point having double antennas is required so that equipment cost is low; the system is not influenced by the environment so that the locating accuracy is high; debugging of the signal range is not required so that the debugging work amount is low; and the extensibility of the arrangement position is high and construction is easy and convenient. Besides, the system has high locating accuracy so that the system has the characteristics of being low in equipment cost, low in debugging work amount, easy and convenient to construct and high in locating accuracy in comparison with the systems in the prior art.
Owner:BEIJING YONGANXINTONG TECH CO LTD
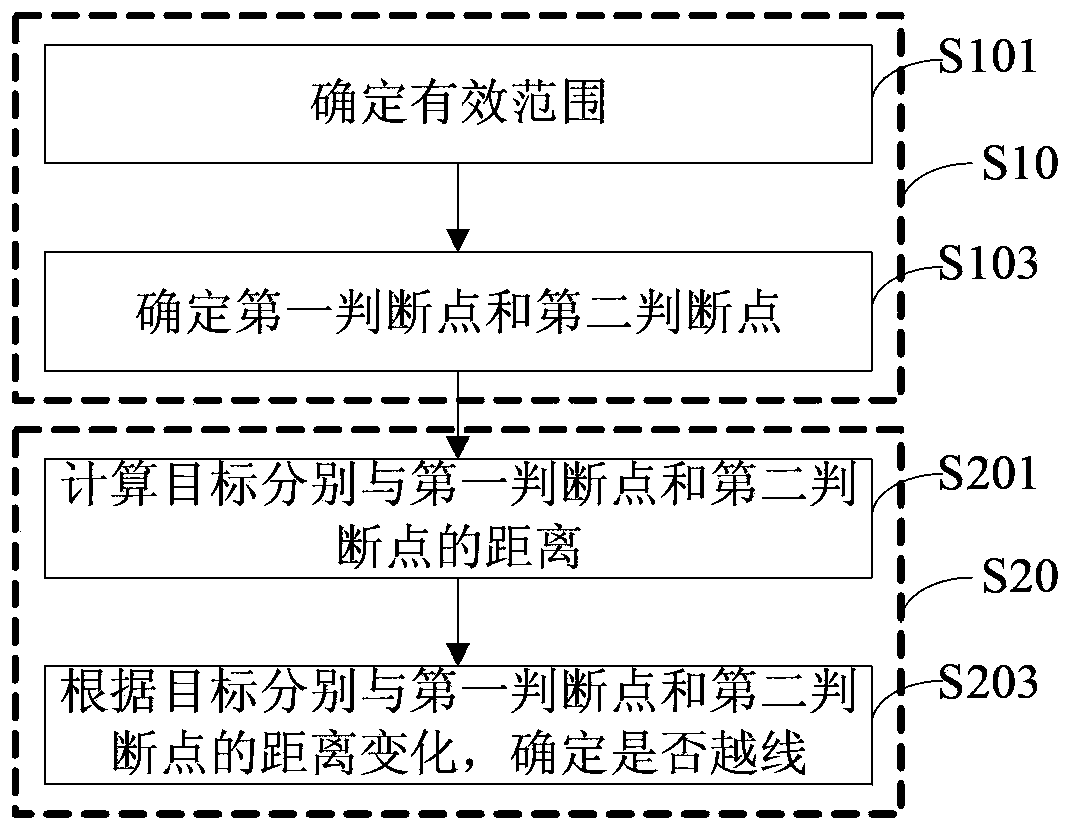
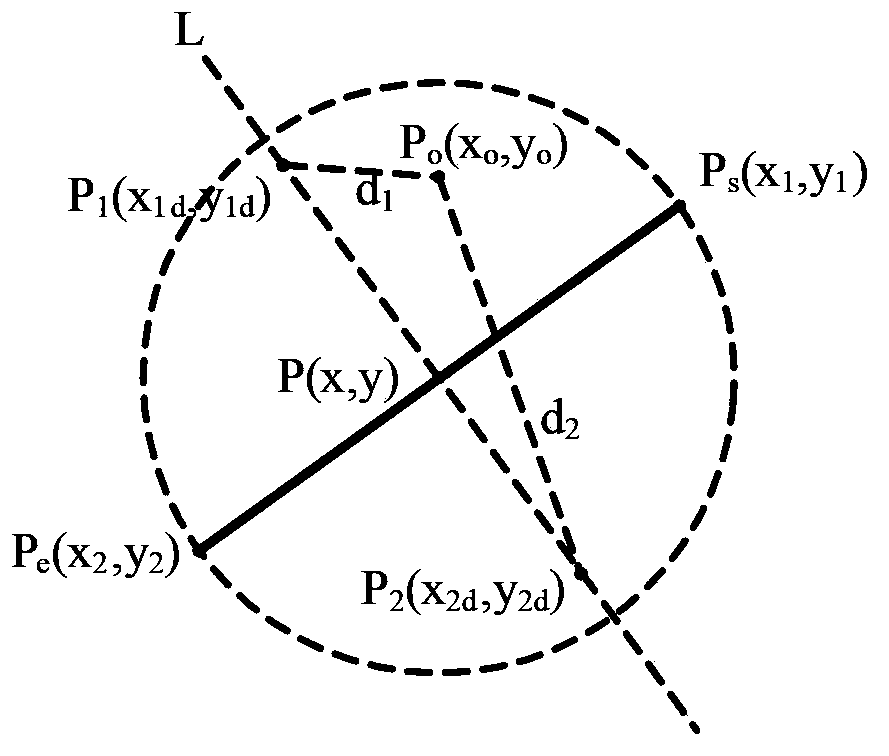
Detection method and device for tripwire crossing of object and video monitoring system
InactiveCN103473528AAvoid crossing the lineImprove accuracyCharacter and pattern recognitionClosed circuit television systemsPattern recognitionVideo monitoring
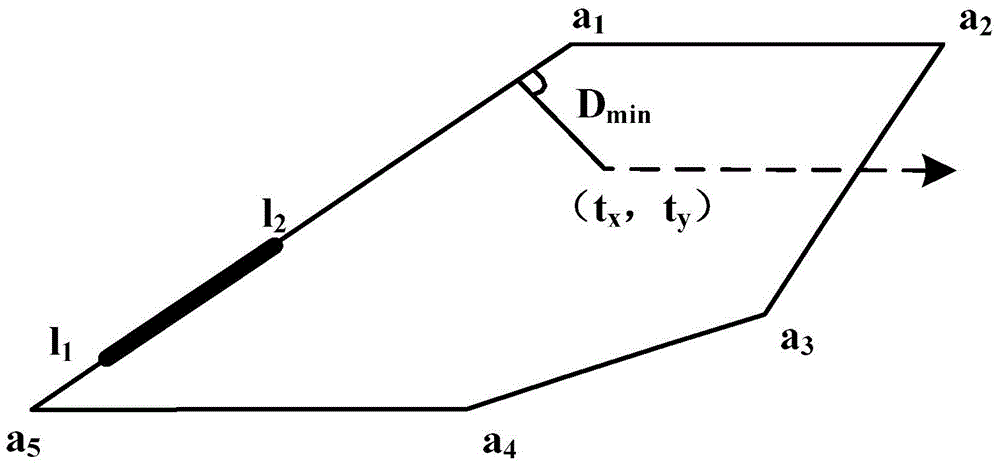
The application relates to a detection method and device for tripwire crossing of an object and a video monitoring system. The method includes a range-point determination step: according to a received tripwire which is drawn on a video image by an operator, determining an effective range used for detecting tripwire crossing by a moving object and selecting two points, which are at the two sides of the tripwire respectively, in the effective range as a first judgment point and a second judgment point; and an tripwire crossing judging step: detecting the position of the moving object and according to changes of distances between the position of the moving object and the first judgment point and the second judgment point respectively, determining that the moving object crosses the tripwire. Through determination of the effective range, it is prevented that when the object passes by outside the tripwire, the behavior is also regarded as a boundary-crossing behavior and at the same time, in judging whether the object is boundary-crossing, not only is a front and rear coordinate position relation of the moving object judged, but the two points at the two sides of the tripwire are also selected in the effective range as a judgment basis to determine whether the moving object is boundary-crossing so that accuracy in judging whether the tripwire is crossed is improved.
Owner:SHENZHEN WISION TECH HLDG
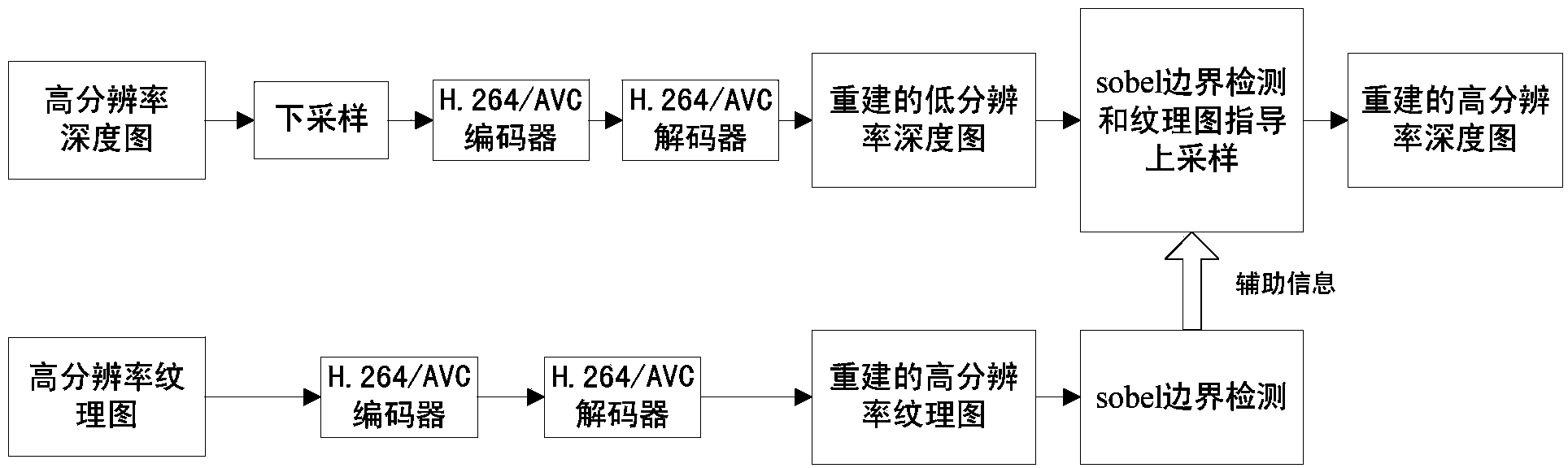
Texture/depth combination up-sampling method
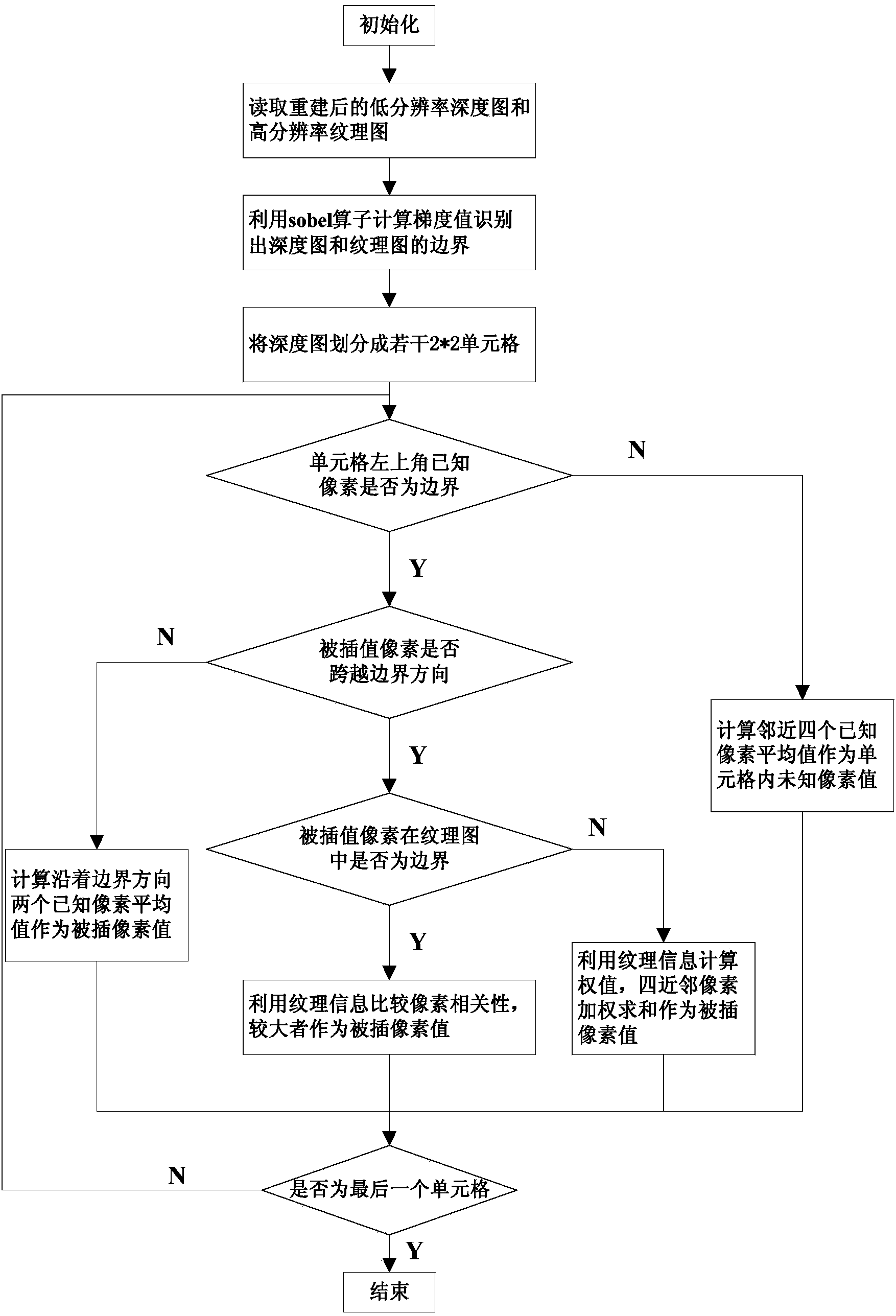
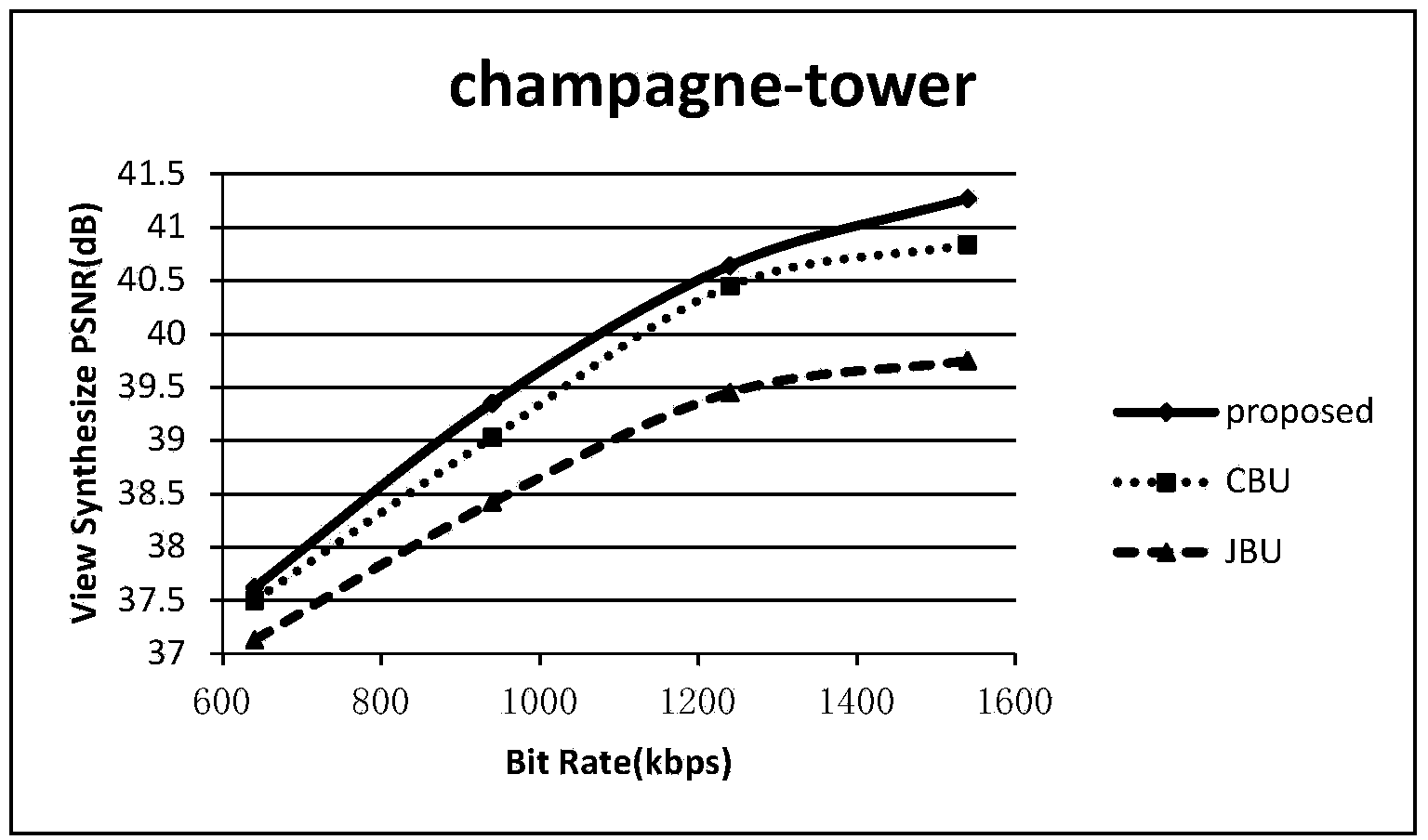
InactiveCN103905812AImprove composite qualityBorder protectionImage analysisSteroscopic systemsImage resolutionBoundary crossing
The invention discloses a texture / depth combination up-sampling method. A boundary can be well protected, coding efficiency is improved, and the synthesis quality of a virtual view is improved. The method comprises the steps that (a) the boundary of a low-resolution depth image and a high-resolution texture image is identified at a decoding end, and the whole low-resolution depth image is divided into three parts, namely a horizontal boundary, a vertical boundary and a non-boundary zone; and (b) the structure similarity of the low-resolution depth image and a high-resolution depth image and the boundary similarity of the depth images and corresponding texture images are used, and according to the fact that depth values in the boundary direction are partially even and depth values in the boundary-crossing direction can change suddenly and severely, a high-resolution depth image is reestablished.
Owner:BEIJING UNIV OF TECH
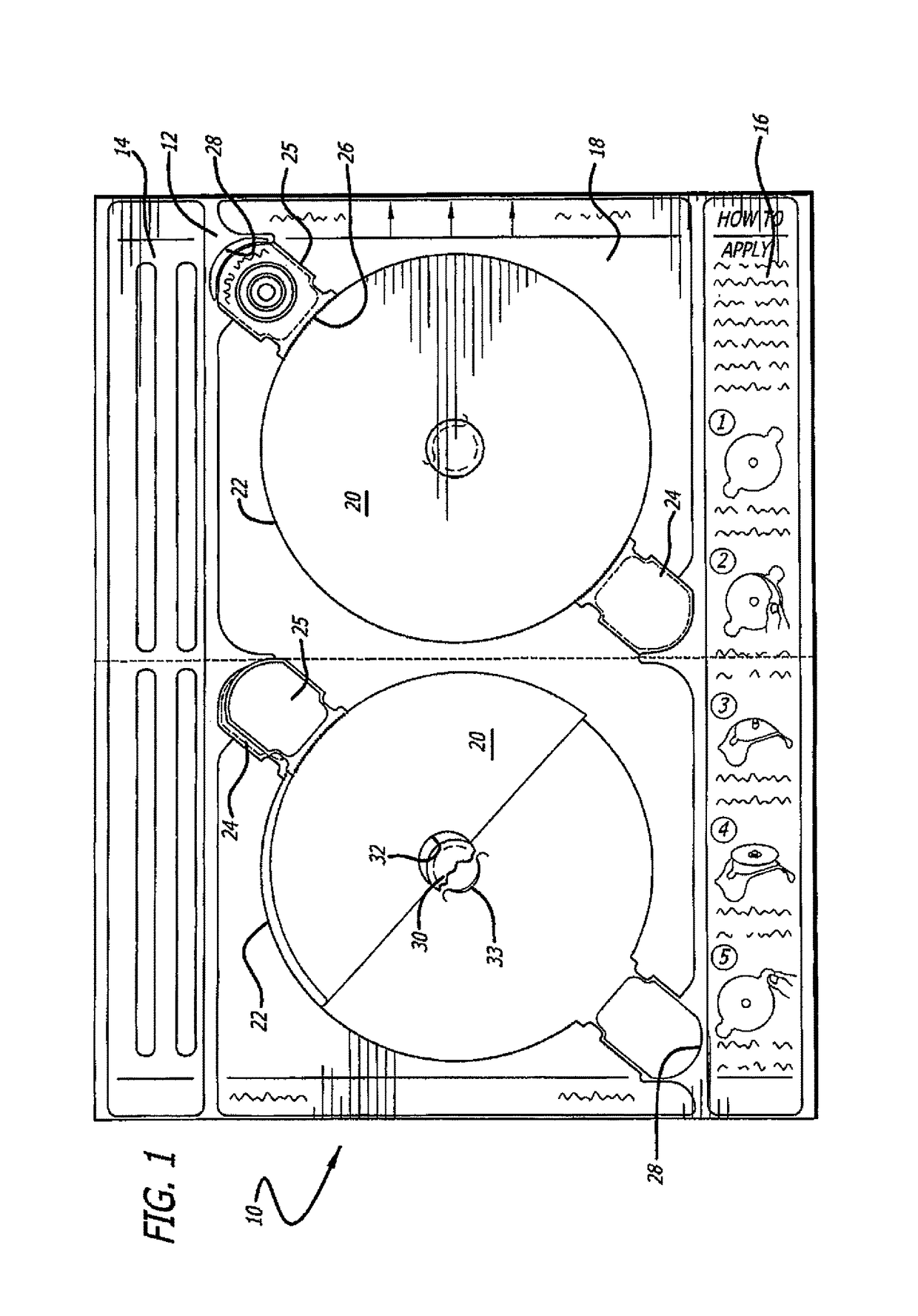
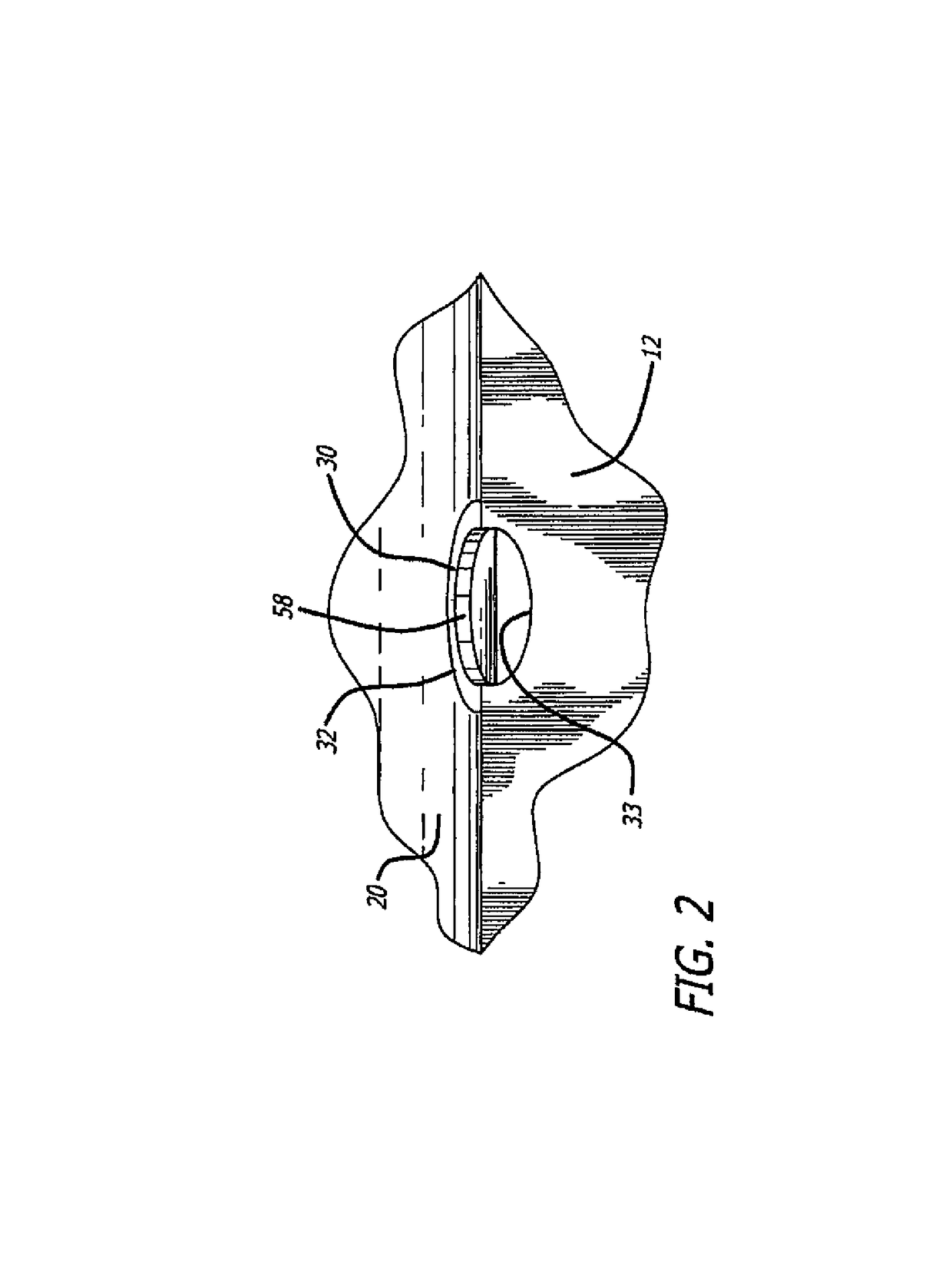
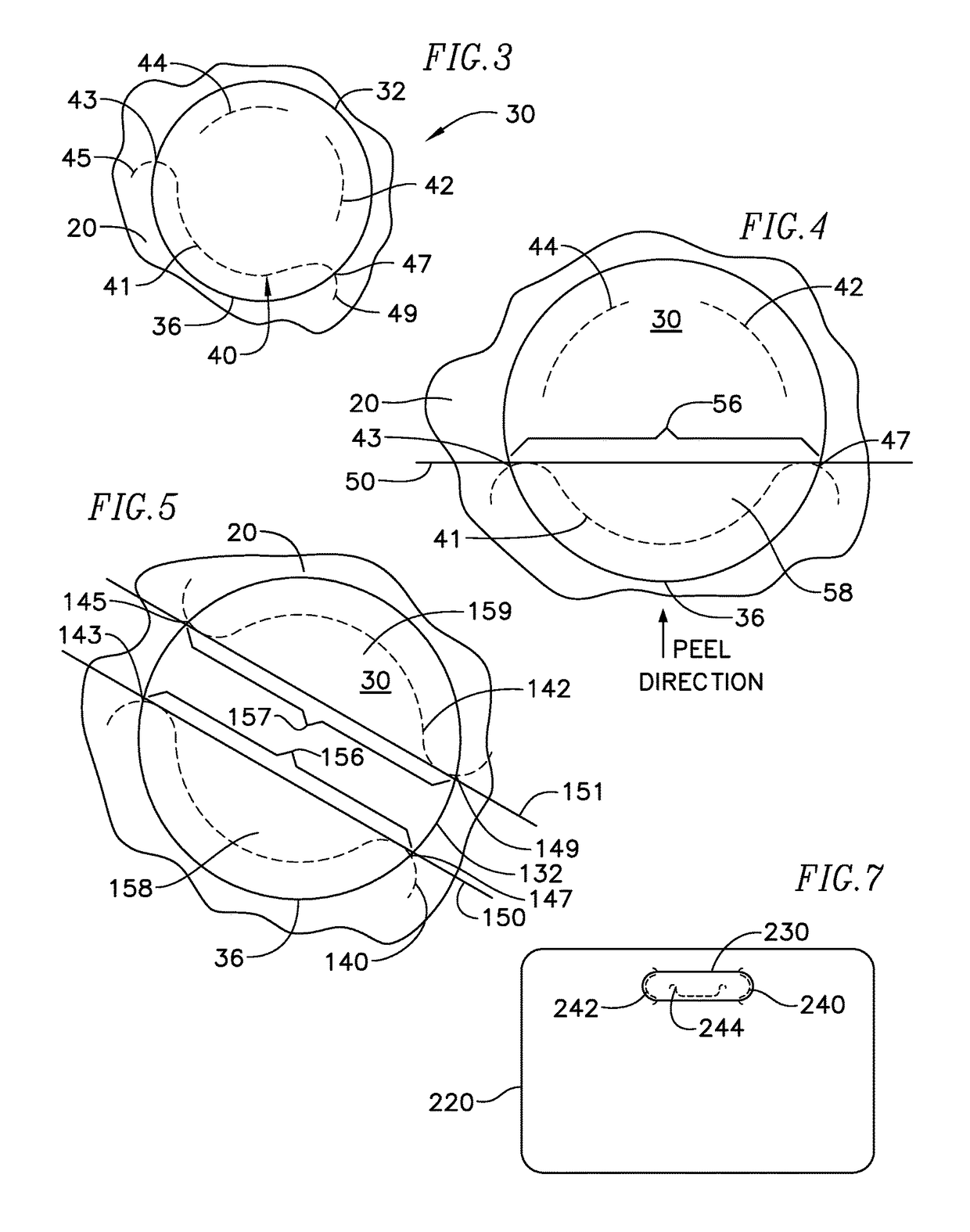
Adhesive label liner sheet modifications for retaining unneeded label sections on liner
One or more cuts is provided in a label liner sheet near the area of a cutout within the label, such as the center hole in a CD label, in order to facilitate reliable separation of the cutout from the label and retention of the cutout on the liner sheet as the label is peeled from the liner. The majority of the cut runs generally parallel to the cutout boundary underneath the cutout, and the ends of the cut cross the boundary at two separate boundary crossing points on either side of the portion of the cut running parallel to the boundary. The cut first causes a flap to be created in the liner sheet and partially lifted as the label is beginning to be peeled away. Thereafter, as the peel line passes the flap area, the cutout experiences the full retentive strength of the label's pressure sensitive adhesive primarily at the two boundary crossings, and the cutout is pulled from the label and retained on the liner sheet as the adhesive force overcomes the cohesive force.
Owner:CCL LABEL INC
Campus border-crossing automatic early warning method based on face recognition
InactiveCN112530116AAvoid out-of-bounds situationsSave human resourcesData processing applicationsDigital data information retrievalBorder crossingEngineering
The invention discloses a campus border-crossing automatic early warning method based on face recognition, and relates to the technical field of face recognition. The method specifically comprises thefollowing operation steps of: A, data collection and input; B, campus border-crossing monitoring; C, face recognition and judgment; D, border crossing automatic early warning; ad E, later-period datamanagement. According to the campus border-crossing automatic early warning method based on face recognition, firstly, identity input can be carried out on personnel in a campus through the data collection and input step, so that identity information of border-crossing personnel is conveniently judged subsequently, and the situation of border crossing of students is avoided; through the campus border-crossing monitoring step, a monitoring device can be used for automatically monitoring a campus border position monitoring area, capturing faces and extracting face features, so that border-crossing personnel face images of the monitoring area can be obtained, the monitoring efficiency is improved, campus human resources are saved, identity information of border-crossing personnel can be intelligently judged through face recognition judgment, and strange visitors can be recognized.
Owner:上海天健体育科技发展有限公司
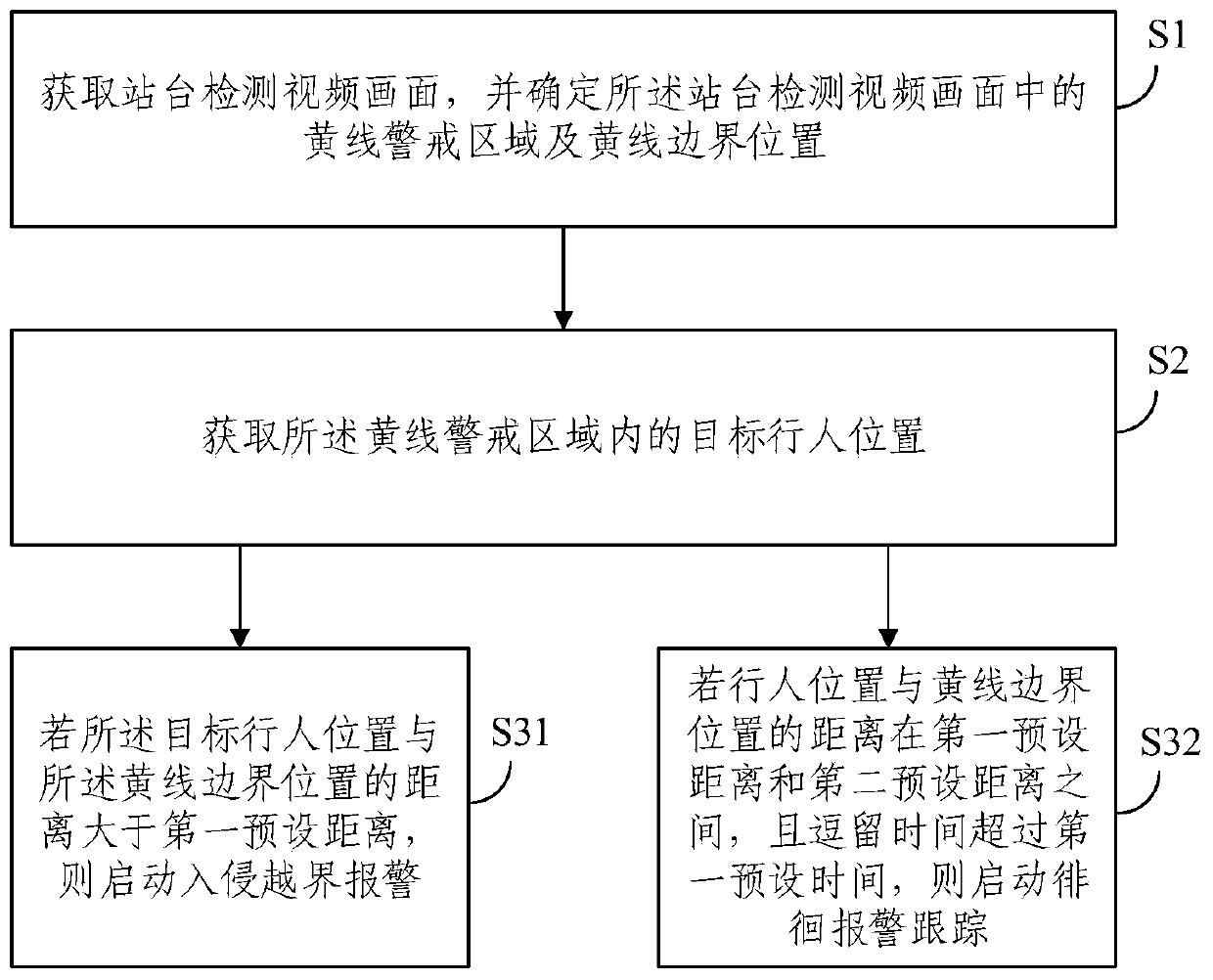
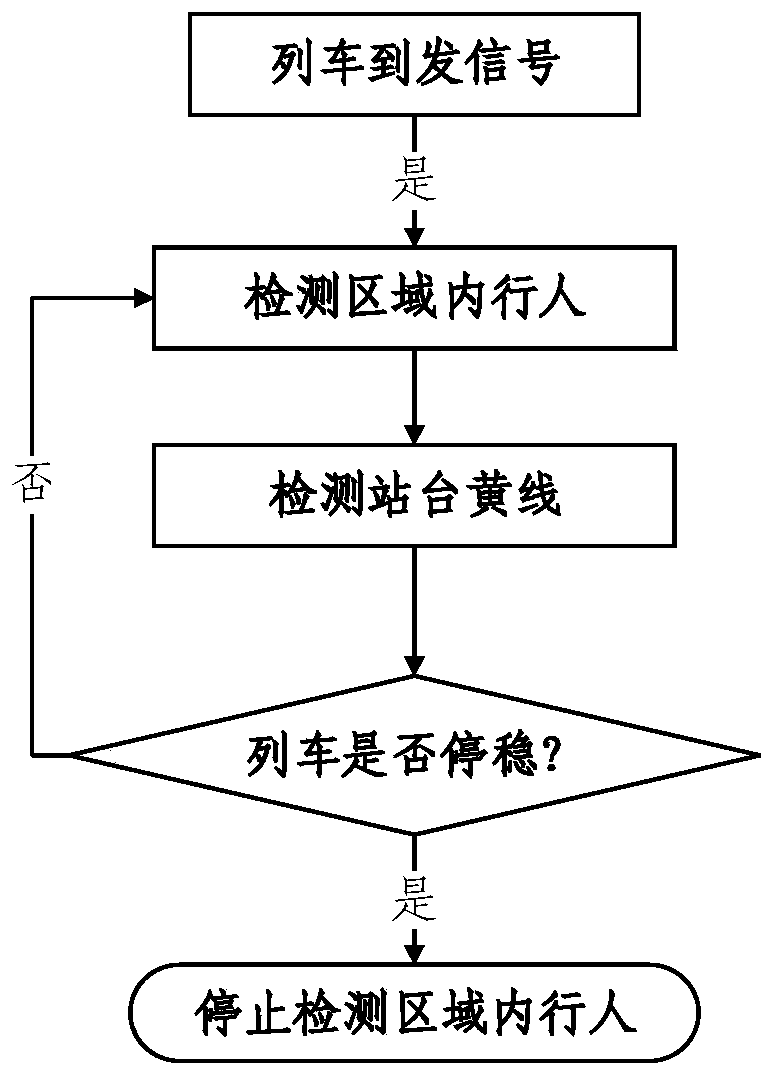
Detection method and system for boundary-crossing person invading to yellow line of platform
ActiveCN110796819AEnsuring the safety of entering the stationPrecise positioningCharacter and pattern recognitionClosed circuit television systemsEngineeringVideo image
The embodiment of the invention provides a detection method and system for a boundary-crossing person invading to a yellow line of a platform. The method comprises the steps of acquiring a platform detection video image, and determining a yellow line warning region and a yellow line boundary position in the platform detection video image; acquiring a target pedestrian position in the yellow line warning region, and starting an invasion boundary-crossing warning if a distance between the target pedestrian position and the yellow line boundary position is larger than a first preset distance; andstarting wandering warning tracing if the distance between the pedestrian position and the yellow line boundary position is between the first preset distance and a second preset distance and stay time exceeds first preset time. With the detection method and system for the boundary-crossing person invading to the yellow line of the platform, provided by the embodiment of the invention, and a trainis guaranteed to enter a station safely; and meanwhile, accurate positioning and real-time tracing of a suspicious person in the yellow line warning region can be achieved, the automatic level of thestation is improved, and the operation efficiency of a relevant worker of the station is improved.
Owner:INST OF COMPUTING TECH CHINA ACAD OF RAILWAY SCI +3
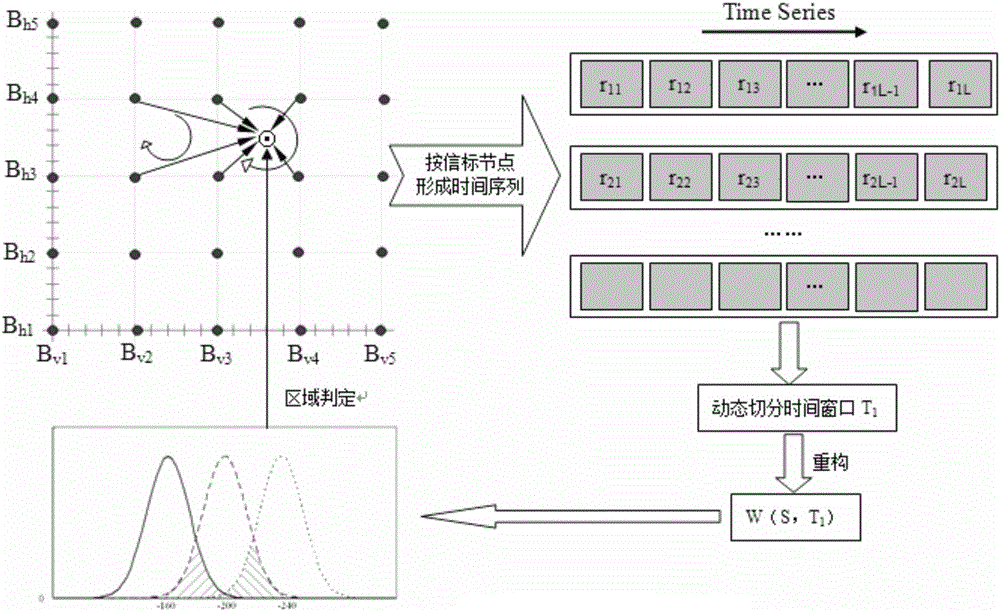
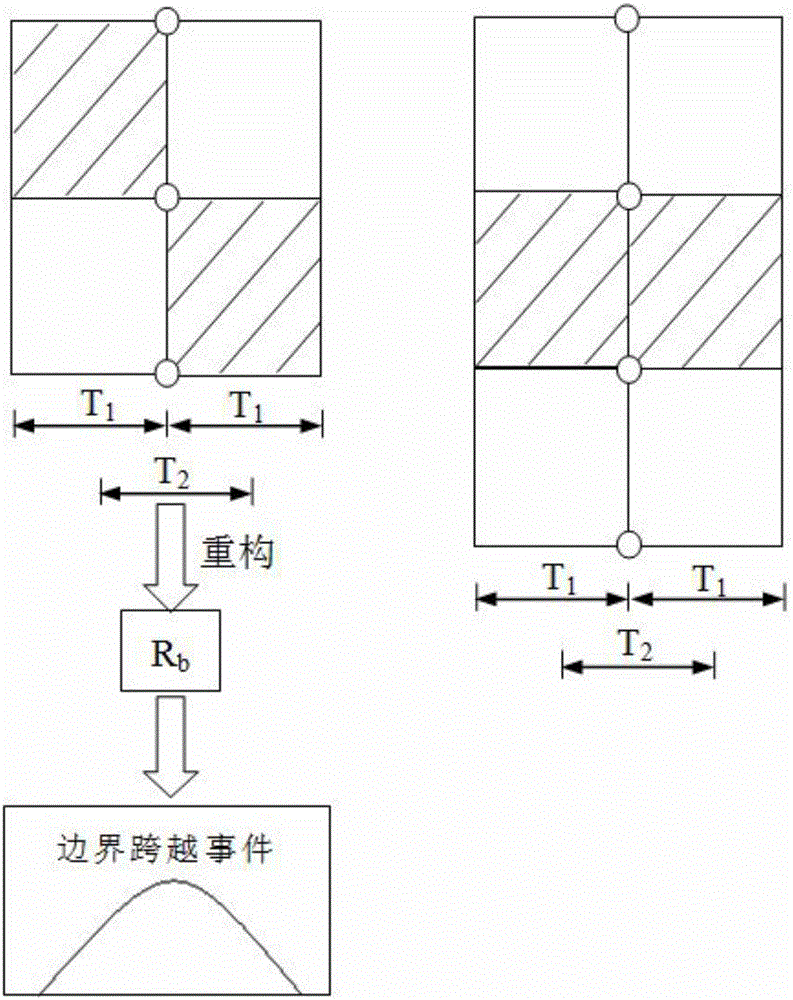
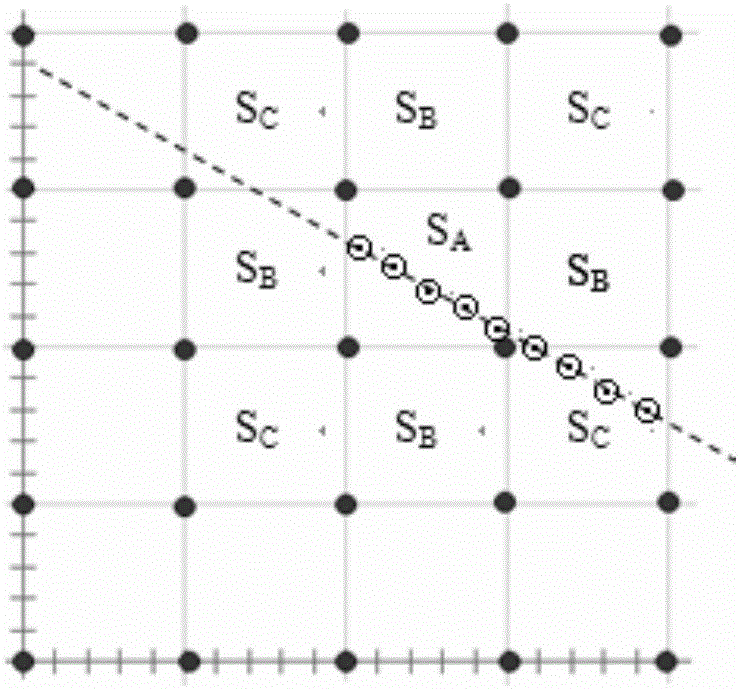
Distributed space-time correlation model trajectory tracking method based on statistical inference
InactiveCN106257301ARealize trajectory trackingImprove accuracyPosition fixationTracking modelDistribution characteristic
The invention relates to a distributed space-time correlation model trajectory tracking method based on statistical inference. Beacon nodes are deployed in the shape of an equidistant grid in a locating space according to longitudinal and transverse directions, and beacon node information is saved in each unknown node; the beacon nodes receiving notification information transmitted by the unknown nodes emit locating signals at a fixed frequency, and the unknown nodes receive and form multiple time sequences according to the beacon nodes; each unknown node constructs a boundary time sequence to detect a boundary crossing event and determine a corresponding time point; each unknown node constructs regional time window statistical quantity and infers the current region; the position of the intersection points of the trajectories and the boundary is inferred; and the trajectories are formed and the result is uploaded to aggregation nodes. According to the method, RSSI locating information probability distribution characteristics in the trajectory tracking problem and space-time data mining are overall considered, and the boundary crossing event and regional information are discovered through the method of time-space information statistical inference so that trajectory tracking can be realized.
Owner:INNER MONGOLIA UNIV OF TECH
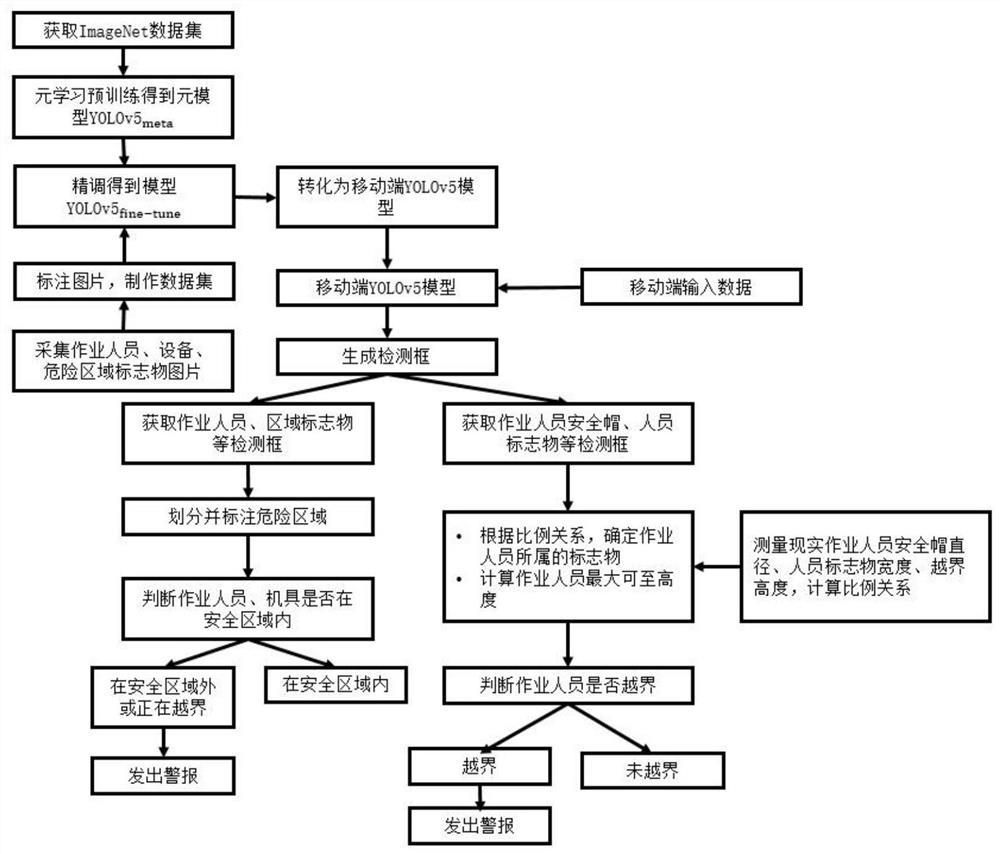
Substation reconstruction and extension violation behavior intelligent identification method based on meta-learning
ActiveCN112818768AImprove training effectImprove playbackCharacter and pattern recognitionInformation technology support systemData setMobile end
The invention discloses a transformer substation reconstruction and extension violation behavior intelligent identification method based on meta-learning, and the method comprises the steps: firstly, collecting a picture, constructing a difficult sample, completing the marking of a scene, forming a small sample data set, pre-training a YOLOv5 model on an ImageNet data set through employing a meta-learning method, and carrying out the fine adjustment on the collected small sample data set, and obtaining a final YOLOv5 model; secondly, deploying the trained YOLOv5 model to a mobile terminal, and completing the recognition of detection objects such as operating personnel, construction equipment, power transmission and transformation equipment and the like; and finally, setting a virtual electronic fence in a self-adaptive manner according to construction operation requirements, and carrying out intelligent recognition and alarm on boundary-crossing violation behaviors of personnel and machines based on the set virtual fence. The method is different from traditional physical fence and other types of virtual electronic fence technologies, not only can ground violation behaviors be effectively identified, but also high-altitude border-crossing violation behaviors can be identified, and the method is flexible in deployment, simple in operation, high in real-time performance and good in reusability.
Owner:NANJING UNIV OF POSTS & TELECOMM
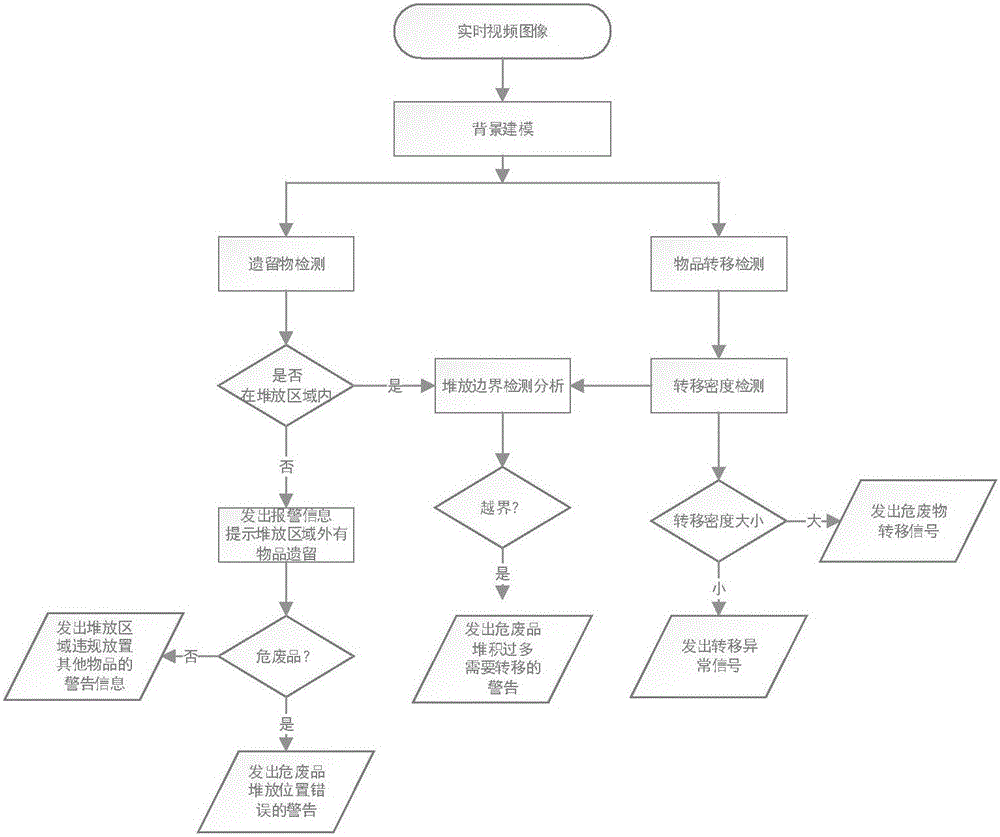
Method for determining storage states of solid waste and hazardous waste by using video analysis
The invention discloses a method for determining storage states of solid waste and hazardous waste by using video analysis. The method comprises the following steps: analyzing a video of a solid waste and hazardous waste storage site in real time, once abandoned materials are stored outside the stacking area, comparing the abandoned materials with the hazardous waste in the stacking area to generate alarm information, and carrying out intervention on the abnormity through workers; detecting hazardous waste transfer behaviors in the stacking area, once a transfer behavior occurs, recording the transfer time and immediately giving a transfer signal so that the monitoring personnel can check and monitor the transfer behavior; and carrying out boundary detection on the stacking area, and once the stacking crosses the boundary, generating a boundary crossing signal to prompt that the hazardous waste needs to be transferred.
Owner:重庆扬讯数字科技股份有限公司
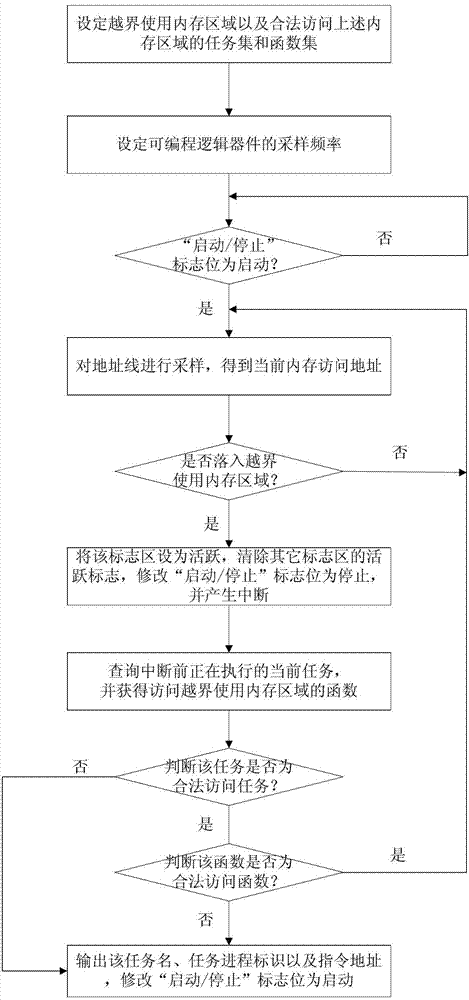
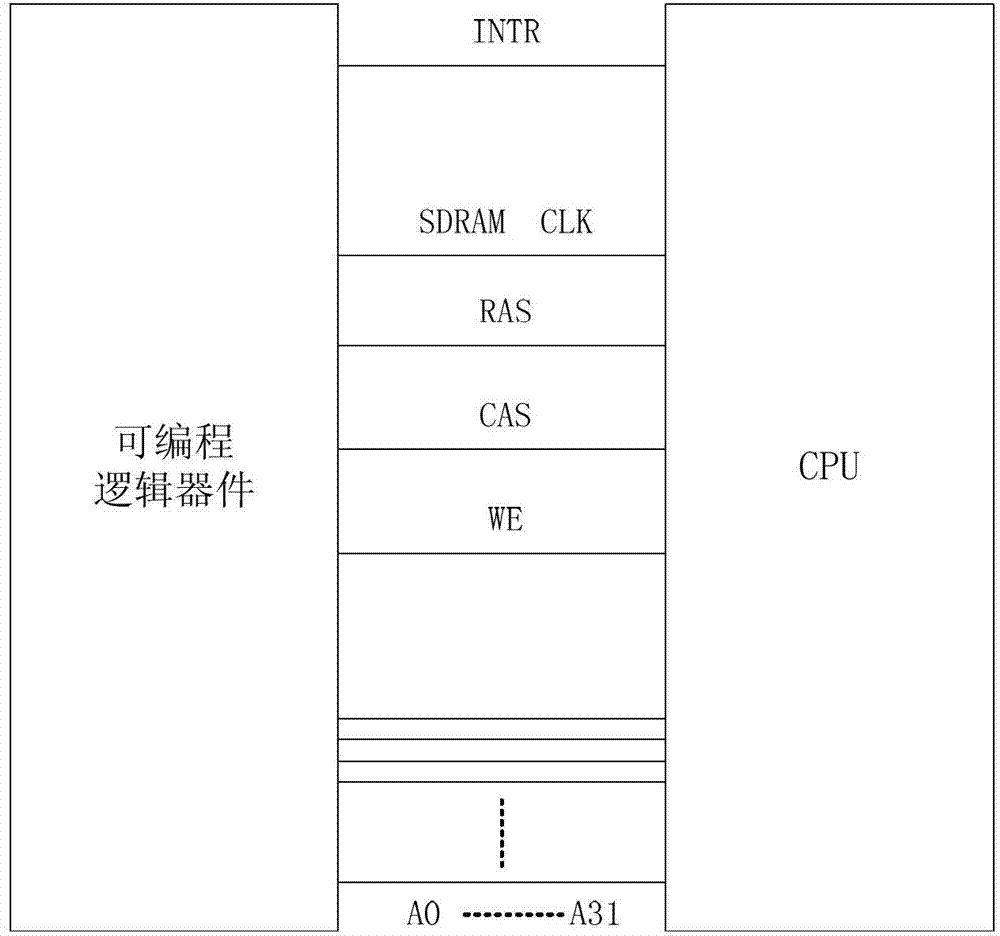
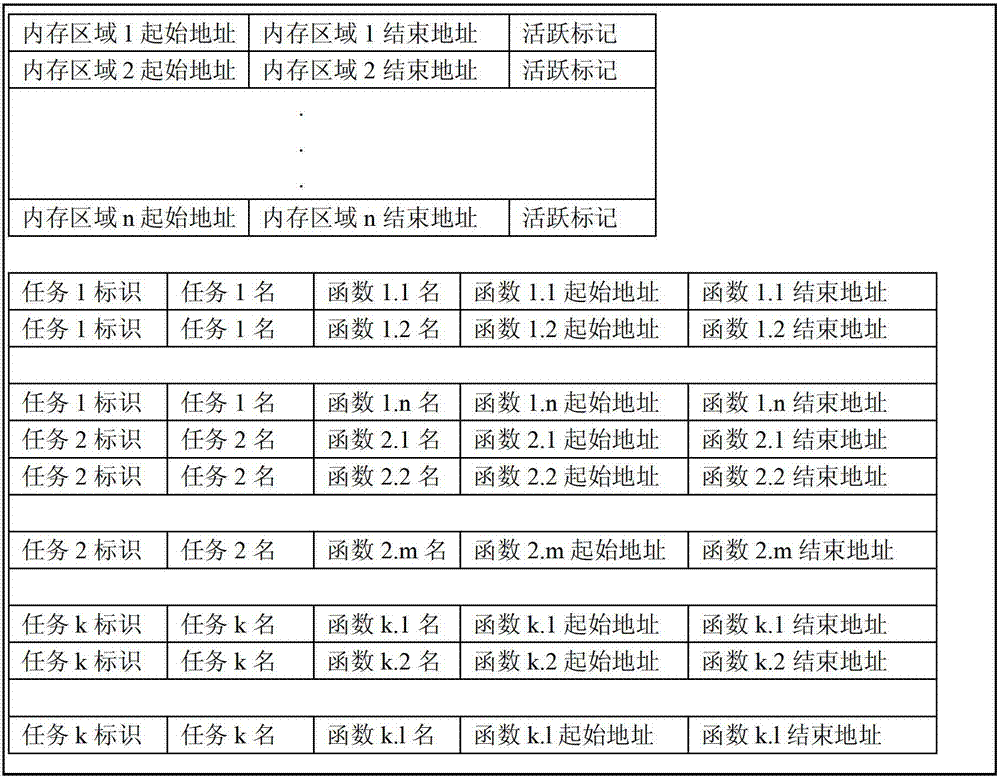
Rapid positioning method of internal storage boundary crossing errors of embedded system
ActiveCN102866951AShorten the timeImprove debugging efficiencySoftware testing/debuggingSpecific functionProgrammable logic device
The invention discloses a rapid positioning method of internal storage boundary crossing errors of an embedded system, which comprises the following steps of: monitoring several boundary crossing use internal storage areas through the programmable logic device, and producing interruption when the boundary crossing use internal storage areas are visited, wherein the internal storage areas are configured on a programmable logic device; querying the executing current task before interruption through a central processing unit (CPU), and obtaining a function for visiting the boundary crossing use internal storage areas; and determining whether the function causes the internal storage boundary crossing or not according to a legal visit task set and a legal visit function set configured on the programmable logic device, and outputting the task of the function causing the internal storage boundary crossing and an instruction address. The rapid positioning method can fast determine the task which causes the internal storage boundary crossing errors and the specific function which is directly called by the task to cause the internal storage boundary crossing errors, therefore, the time for troubleshooting the concealed errors of the embedded system can be reduced, and the efficiency of the system debugging can be improved.
Owner:FENGHUO COMM SCI & TECH CO LTD
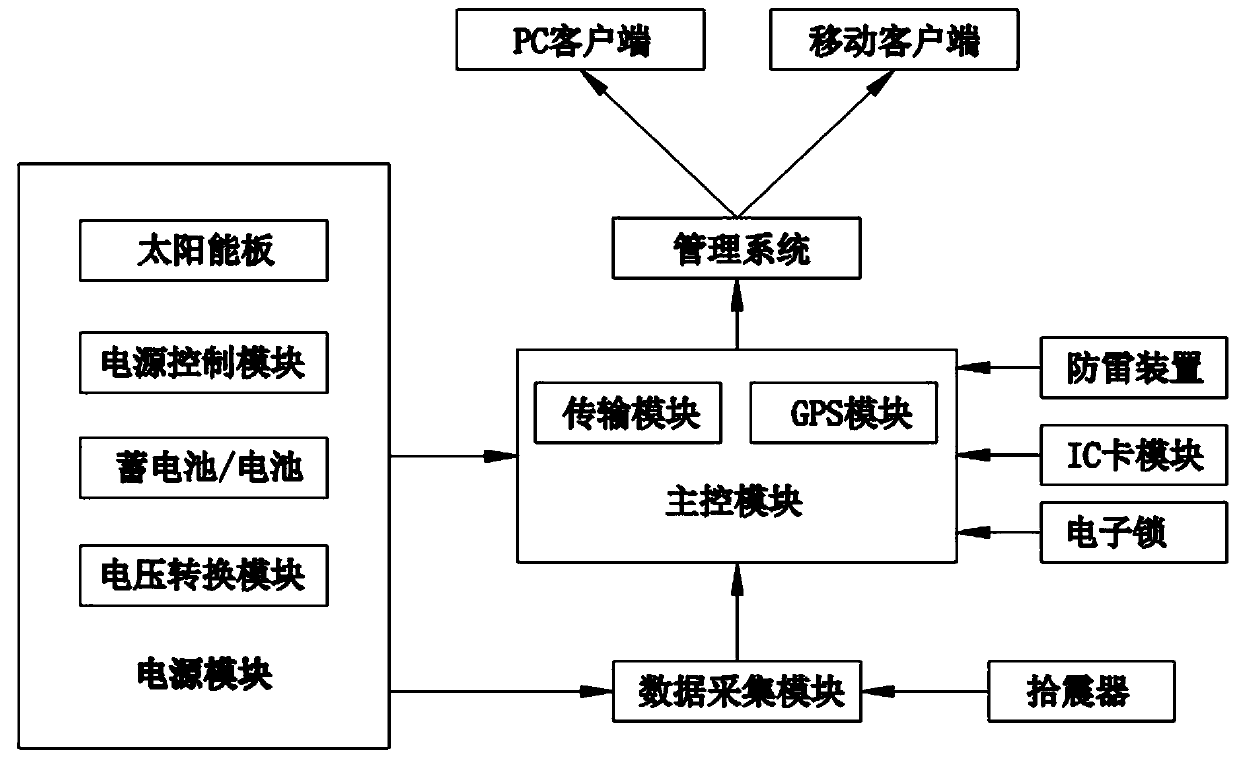
Monitoring and early-warning method and system for preventing boundary-crossing illegal mining in mining area
ActiveCN111009087AProtection securityAccurately calculate actual geographic coordinatesBurglar alarm mechanical vibrations actuationMonitoring siteShock wave
The invention discloses a monitoring and early warning method and a system for preventing boundary-crossing illegal mining in a mining area. The system comprises a seismometer, a data acquisition module, a main control module, a transmission module, a GPS module, a power supply module, an IC card module, an electronic lock, a lightning protection device, a management system and a user terminal. According to the method, the blasting point shock wave information uploaded by the monitoring points is analyzed and processed through the management system; the actual geographical coordinates of the blasting point can be accurately calculated by processing the integrity and effectiveness of the information, the detection range is wide, the actual geographical coordinates are compared with the mining range approved by the mining area for judgment, whether boundary-crossing illegal mining behaviors exist can be effectively judged, and the safety of the mining area is protected.
Owner:GUILIN SAIPU ELECTRONICS TECH
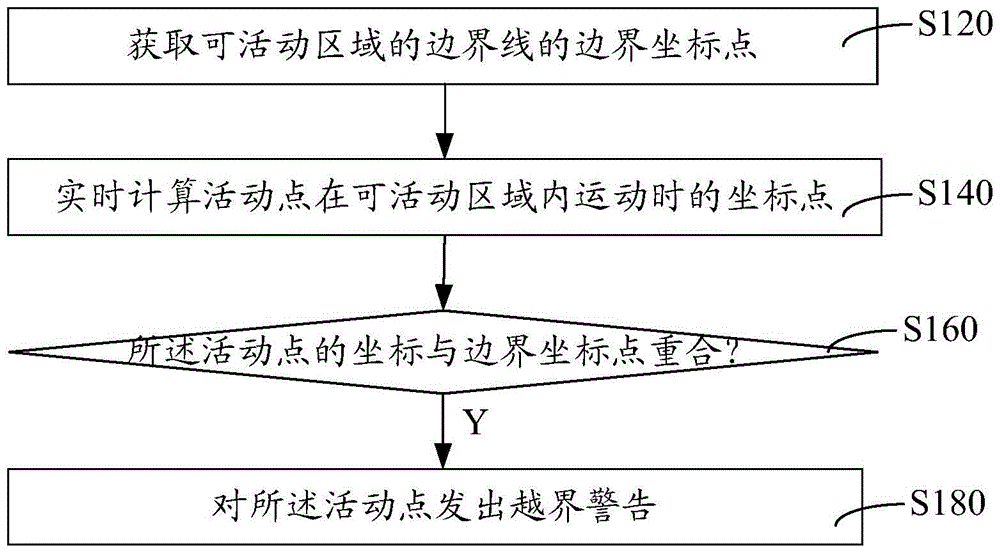
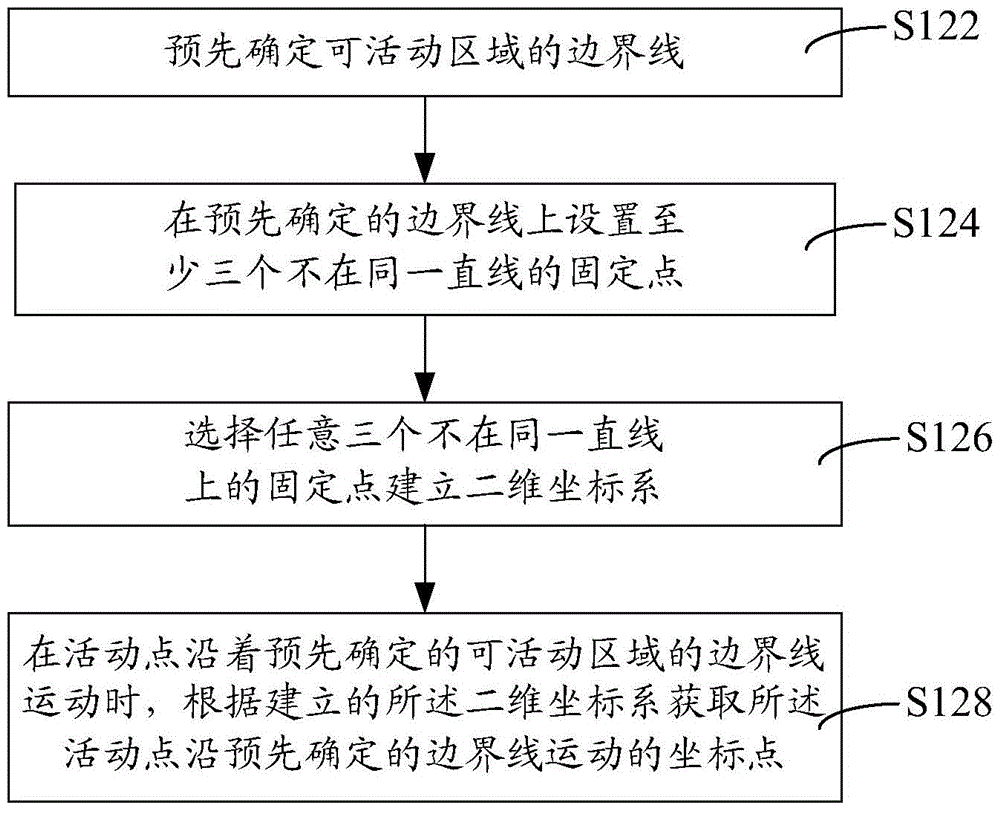
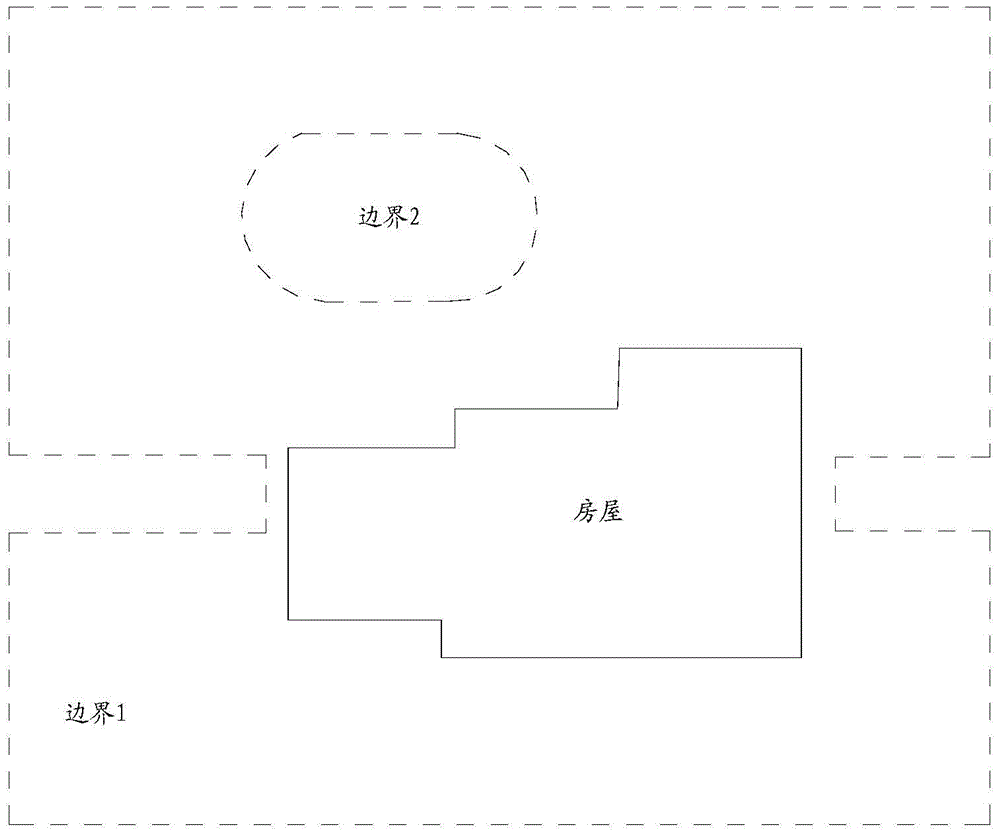
Method and system for realizing real-time automatic identification of virtual boundary
The invention relates to a method and a system for realizing real-time automatic identification of a virtual boundary. The method comprises the steps of acquiring a boundary coordinate point of a border line of a movable area; performing real-time calculation on a coordinate point of a moving point in motion in the movable area; judging whether the calculated coordinate point of the moving point in motion in the movable area is superposed with a boundary coordinate point; and on the condition that the coordinate point of the moving point in motion in the movable area is superposed with the boundary coordinate point, transmitting a boundary crossing alarm to the moving point. The system comprises a boundary module, a calculation module, a judging module and an alarm module. The method and the system can perform effective management on a pet and prevent an accident which is caused by motion range exceeding of the pet.
Owner:POSITEC POWER TOOLS (SUZHOU) CO LTD
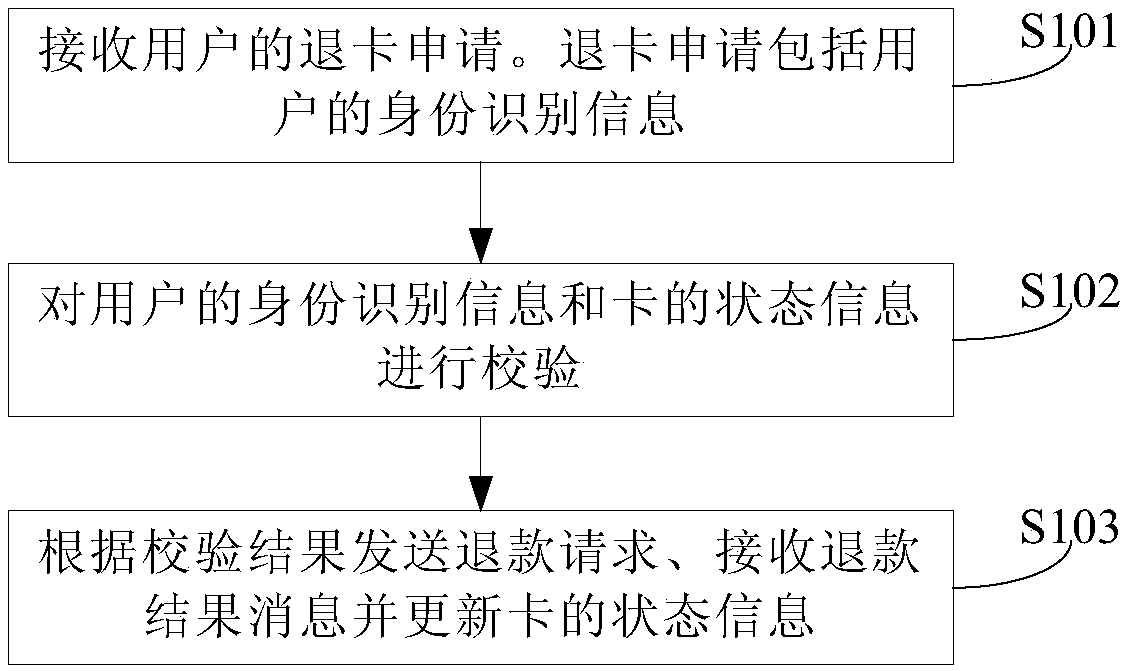
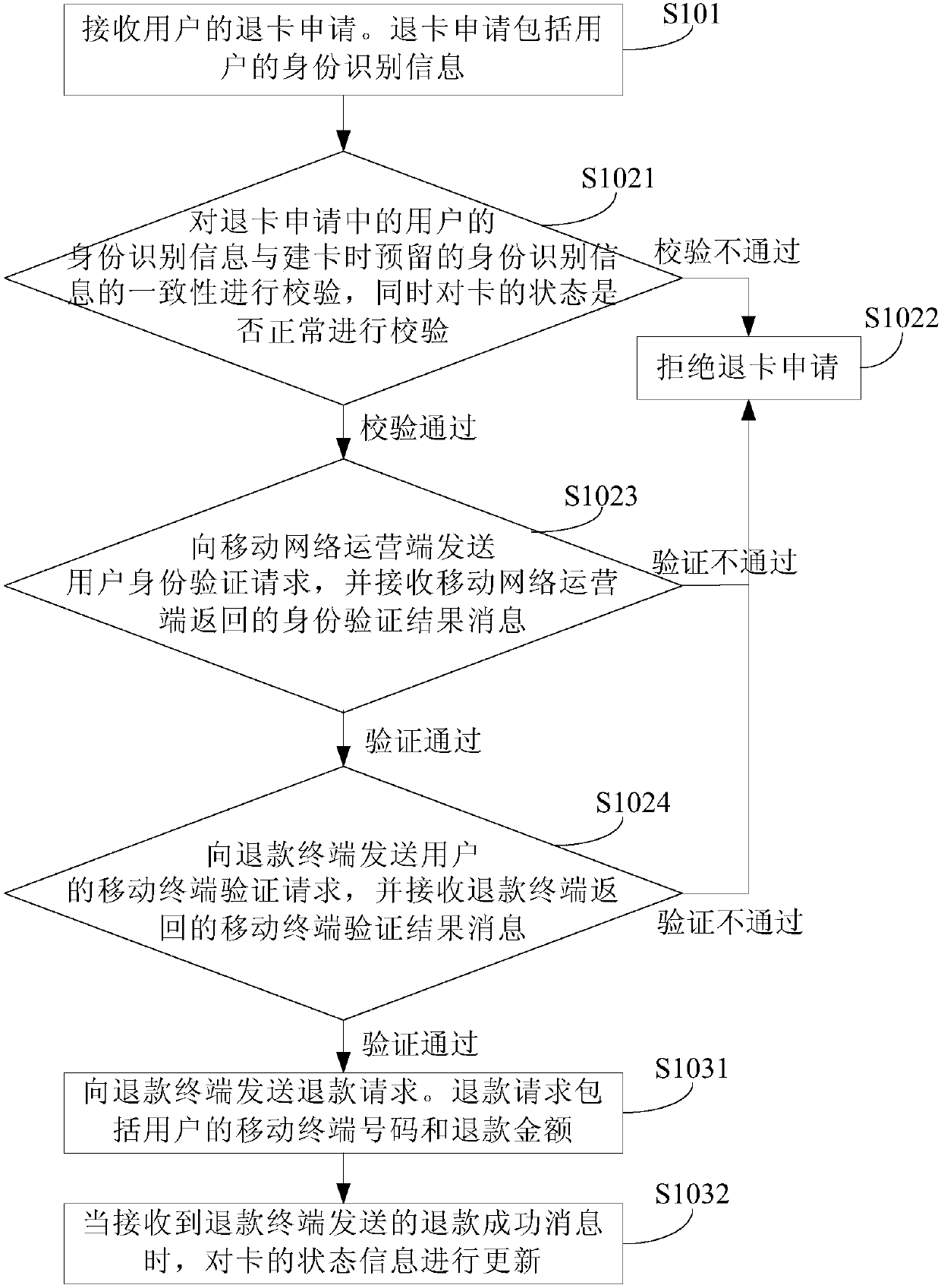
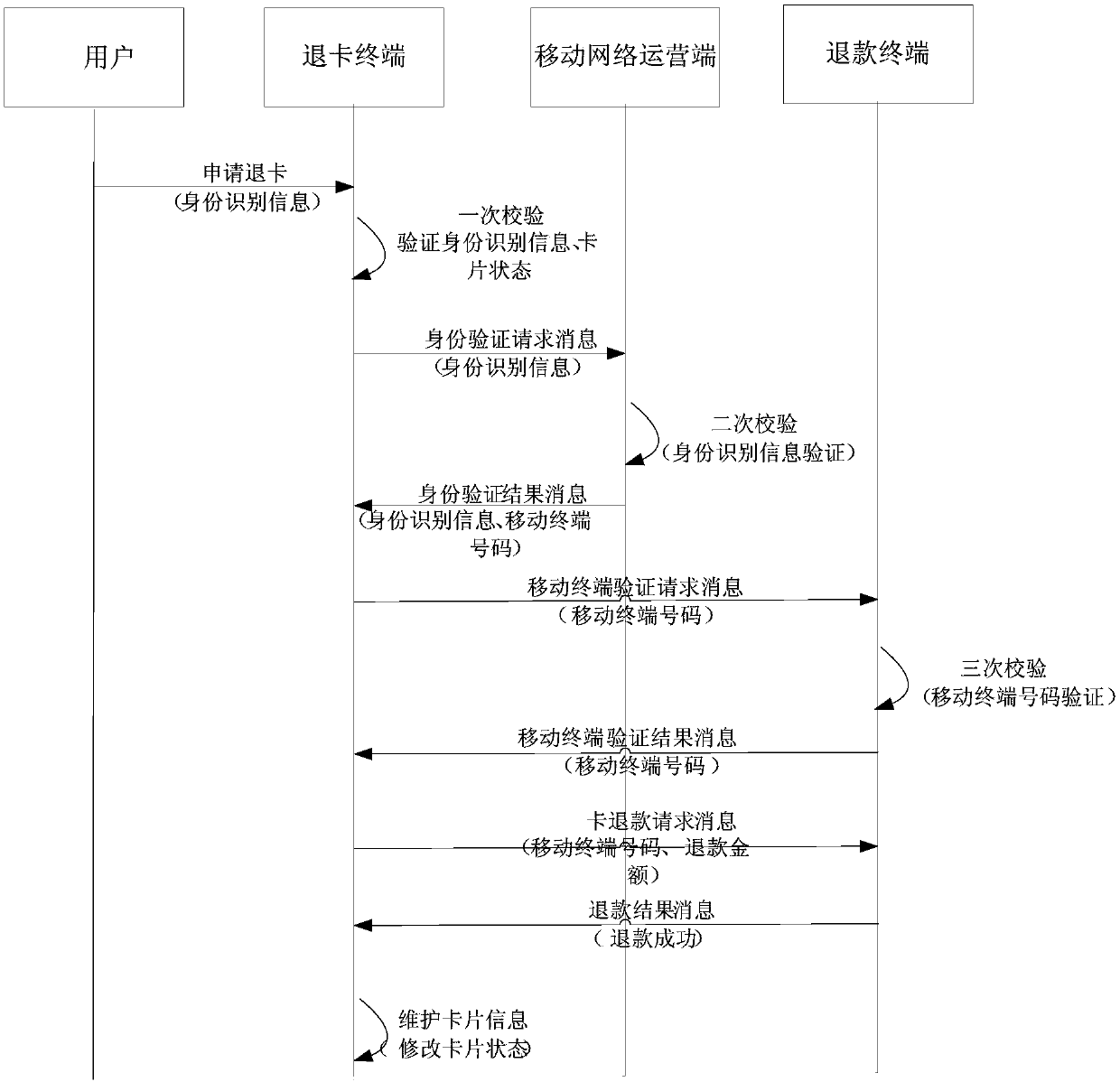
Card returning method, card returning terminal, mobile network operation terminal and refunding terminal
InactiveCN107564175AEasy card withdrawalImprove card refund experienceCoded identity card or credit card actuationProtocol authorisationComputer hardwareBoundary crossing
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Electrical time measuring system or device indicating time intervals by regioned concentric arciforms that indicate the time of duration of particular events
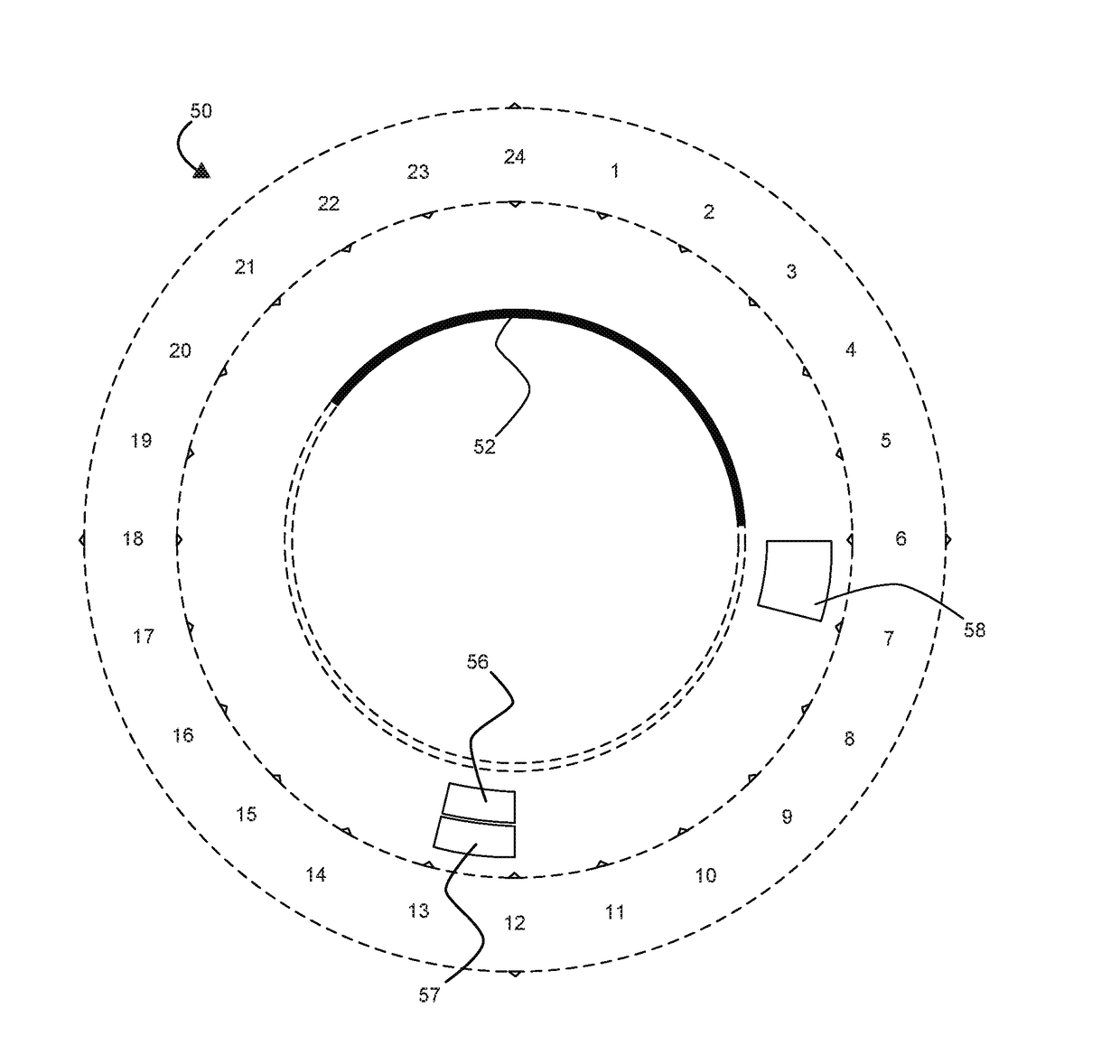
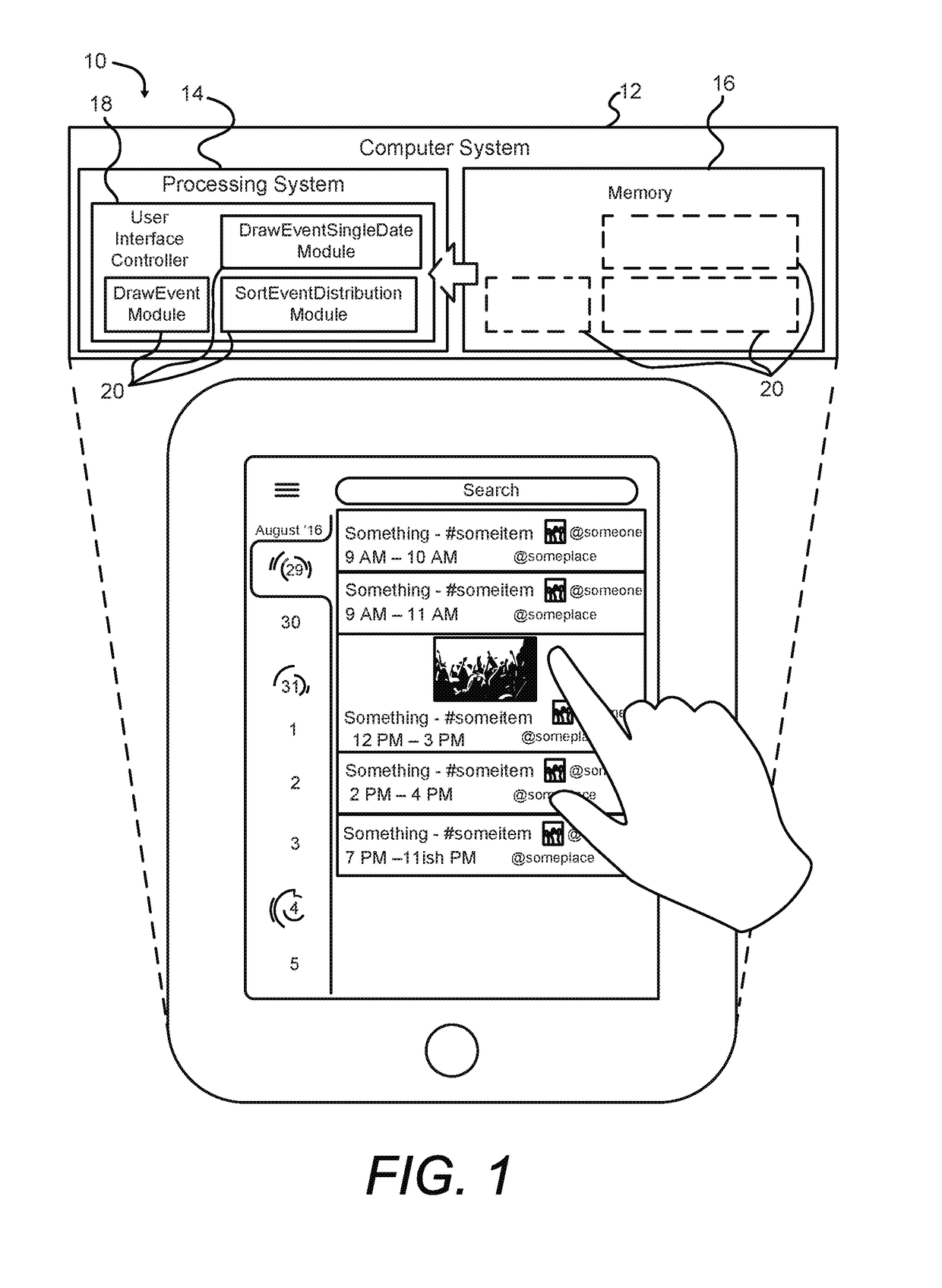
ActiveUS20180101142A1ConserveReduce processor cycleVisual indicationsLocation information based serviceElectricityDisplay device
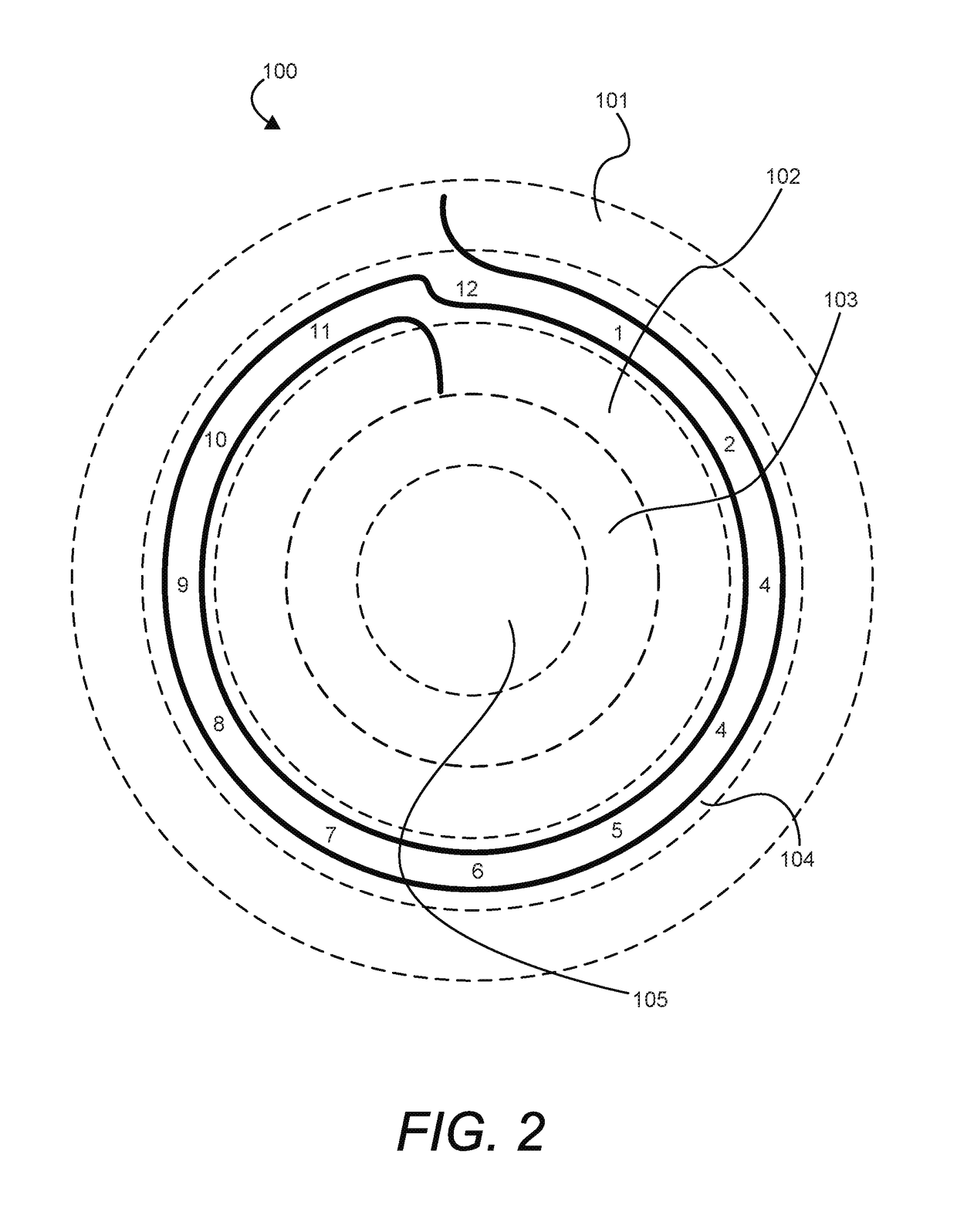
An electrical time measuring device, intended to conserve processor cycles and memory when used in indicating time interval durations, includes a computer system with a processing system having a hardware processor and a memory accessible to the processing system, a user interface controller under control of the processing system, and logic, under control of the processing system. Various embodiments include nested concentric regions in a clockface display, an ante meridiem events region, a post meridiem events region, and / or a following-day events or tasks region. Events or time interval durations are represented as arciform. For events that cross from morning to afternoon, or from evening to the following day, arciforms are displayed with a start point in one of the nested concentric regions and an end point in a different one of the nested concentric regions. The parts of such arciforms are joined by an integral boundary-crossing transition indicator.
Owner:SAMRAT SOLUTIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com