Threat level-based multi-factor identity authentication method
An identity authentication and threat level technology, applied in the field of identity authentication, can solve the problems of inflexible authentication methods, hidden dangers, endangering system security, etc., to achieve a good user experience, user convenience, and flexible authentication process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
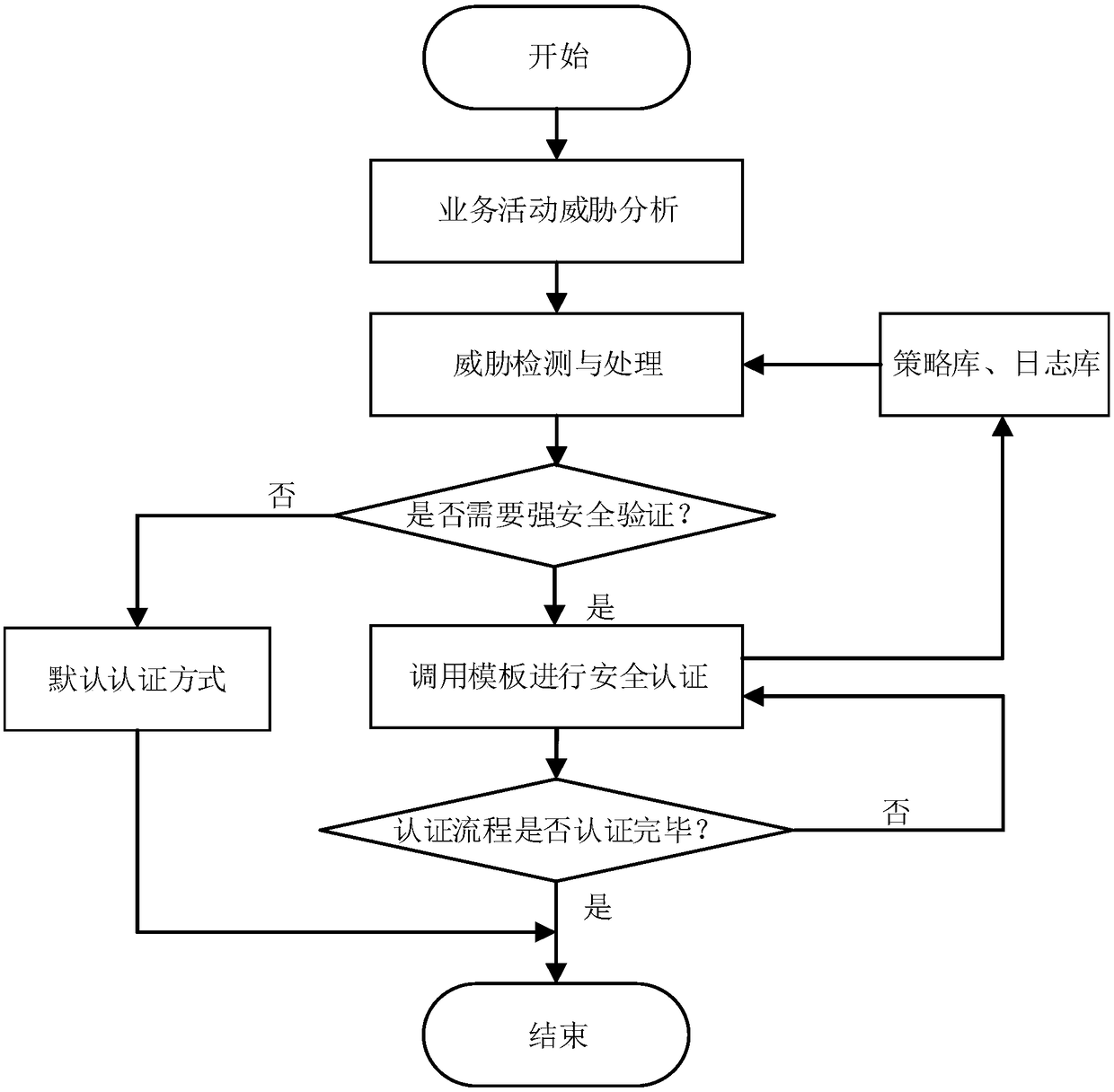
[0033] A multi-factor identity authentication method based on threat level, the following steps are performed:
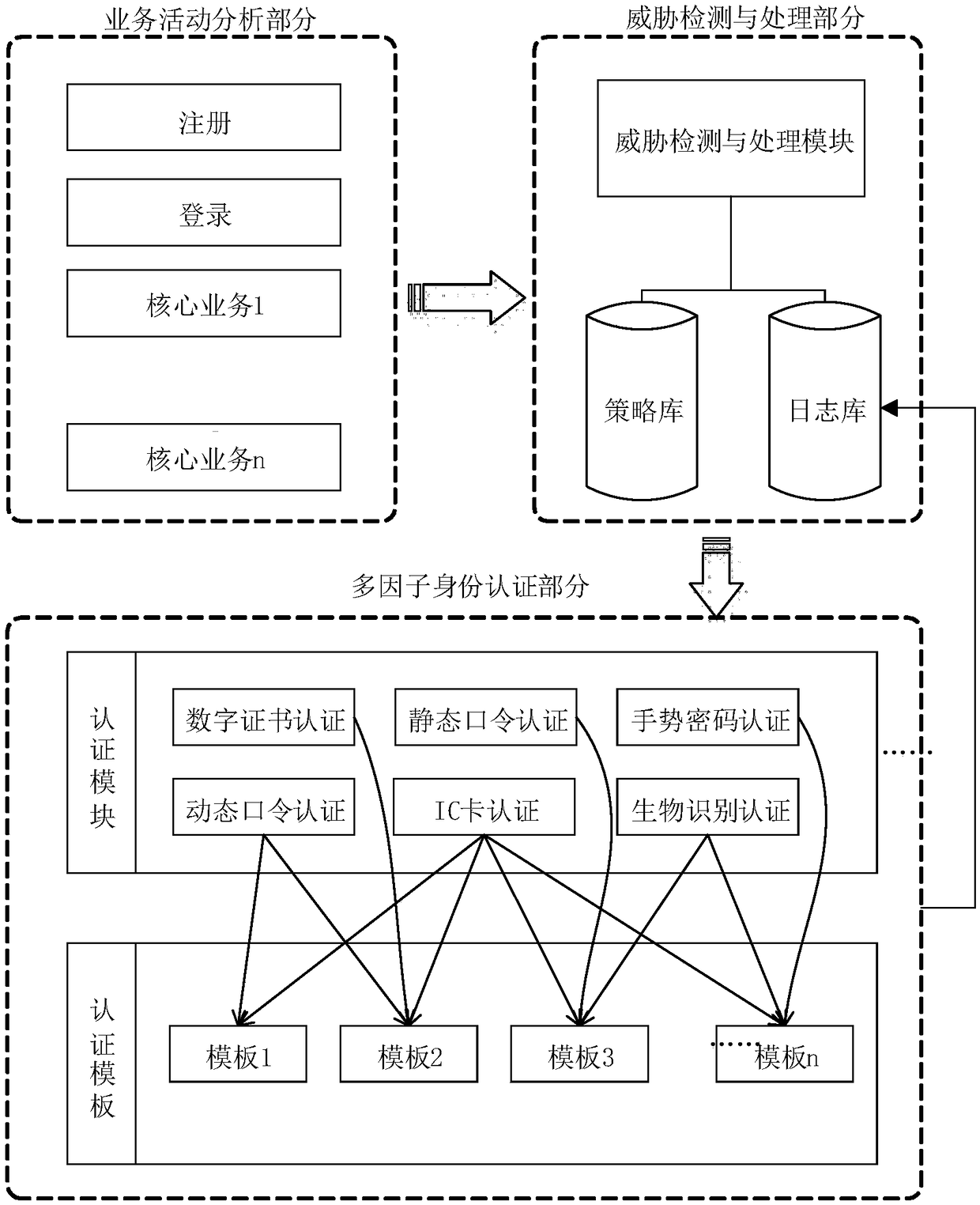
[0034] A. Establish an identity authentication model, which includes a business activity part, a threat detection and processing part, and a multi-factor identity authentication part, such as figure 1 As shown, it is a schematic diagram of the composition of the identity authentication model based on the threat level. The model is mainly composed of the business activity part, the threat detection and processing part, and the multi-factor identity authentication part. The main functions of each part are as follows:
[0035]The business activity part is used to analyze system architecture, security boundaries, business processes, and key modules, formulate evaluation methods, identify functional modules that require identity authentication, perform threat identification, threat level classification, and threat quantification on modules, and provide The threat detecti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com