Intrusion detection system facing cloud calculating environment
A technology of intrusion detection system and cloud computing environment, applied in the direction of transmission system, electrical components, etc., can solve the problem of no technology and its solution, security protection, resource safety multiplexing without too much involvement, no solution to dynamic splitting of resources Security monitoring management and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
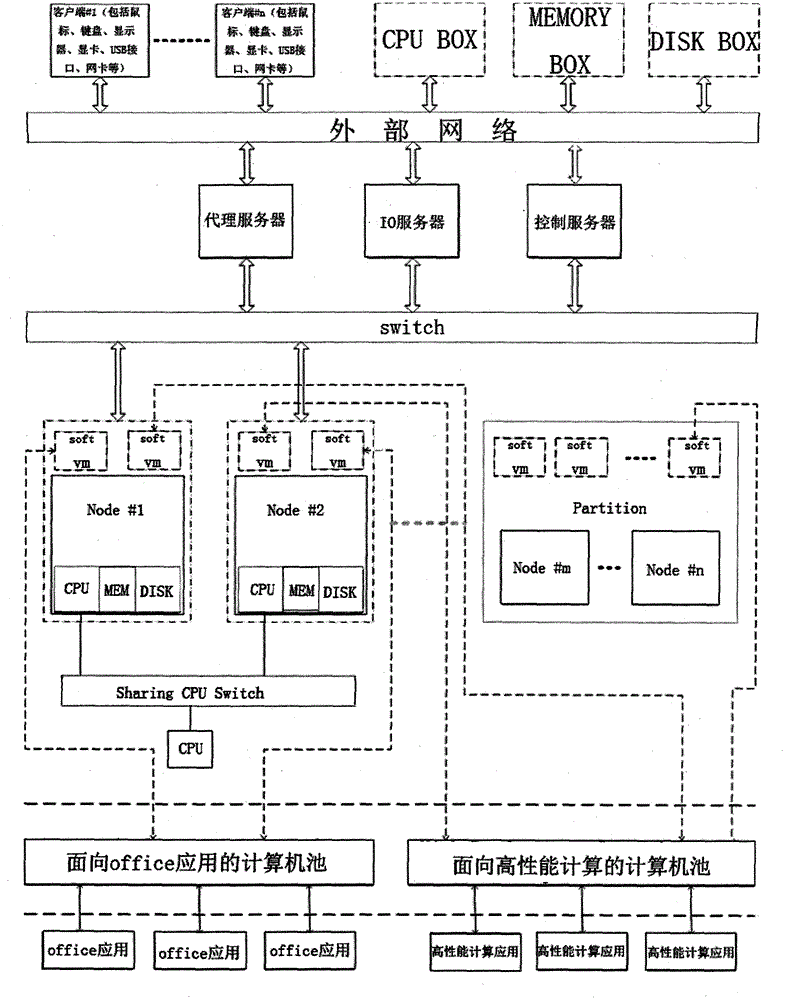
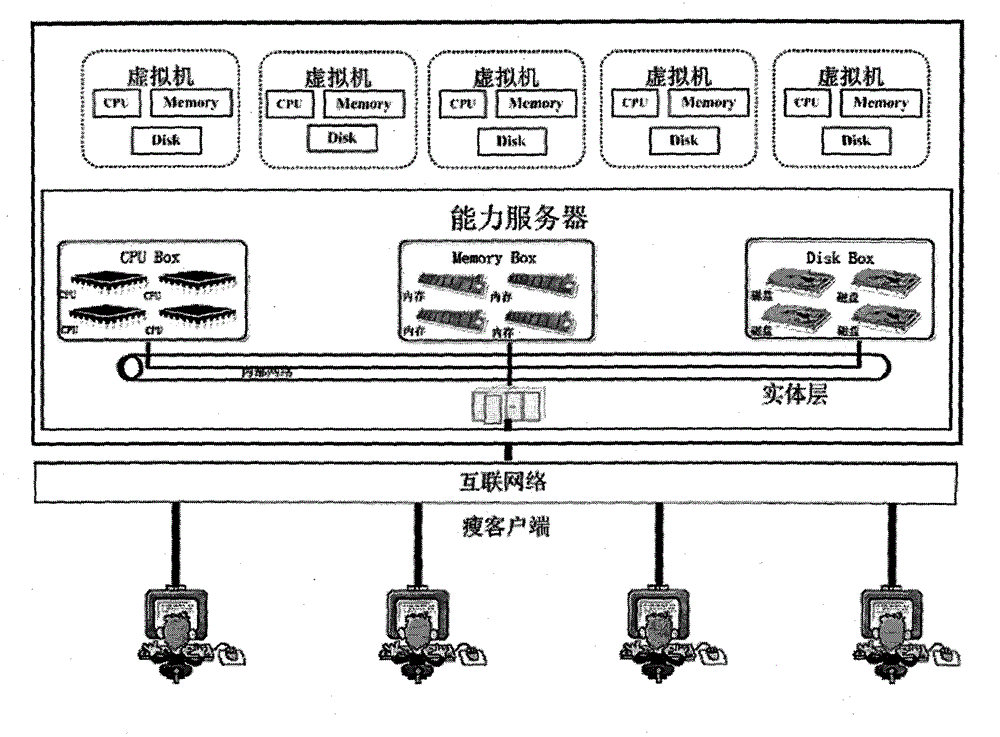
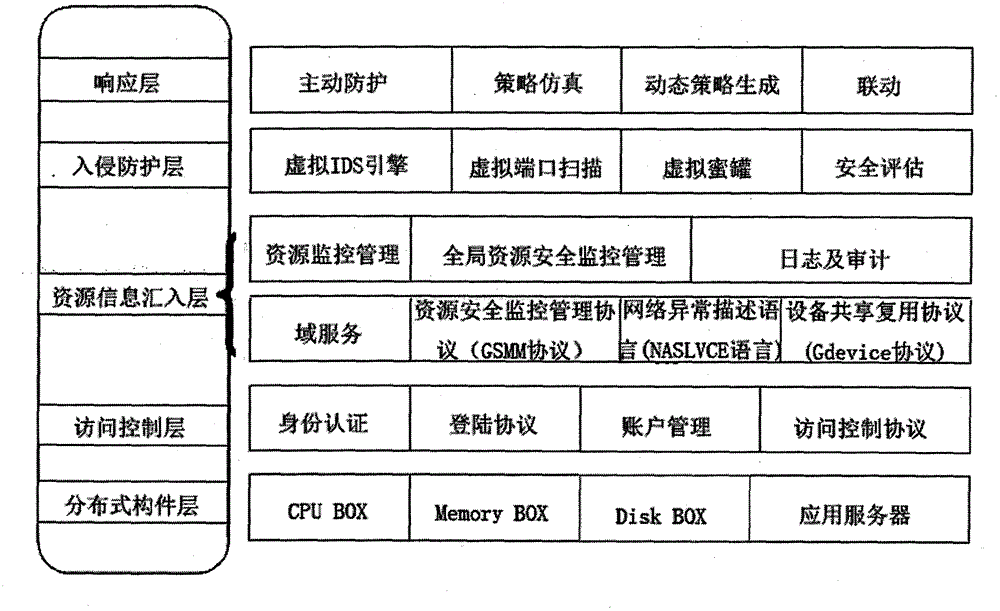
[0037] The ability server architecture for virtual computing environment has large-scale sharing of resources, low cost, ease of use, configuration flexibility, easy management, security, scalability and high availability. main guiding principles. Among them, the security architecture is a very important aspect in the design of the capability server, which involves issues such as identity authentication, authorization, credit, integrity, confidentiality, service and information availability, auditing and accounting, and service protection of the capability server. Its main content is to provide safe and reliable identity authentication, virtual distributed and scalable intrusion detection, safe and intelligent resource monitoring and management, and safe and reliable resource aggregation multiplexing access protocol for the capability service domain in the virtual computing environment. Scale Distributed Security Infrastructure (SDSI) for capability servers in virtual computin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com