Methods for SN (sensor node) equipment authentication and state authentication, as well as security protocol method
A sensor node and device authentication technology, applied in the field of security protocols of sensor networks, can solve the problems of large network load, inability to know the credit of sensor nodes, insufficient verification of the operating software and status of sensor nodes, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
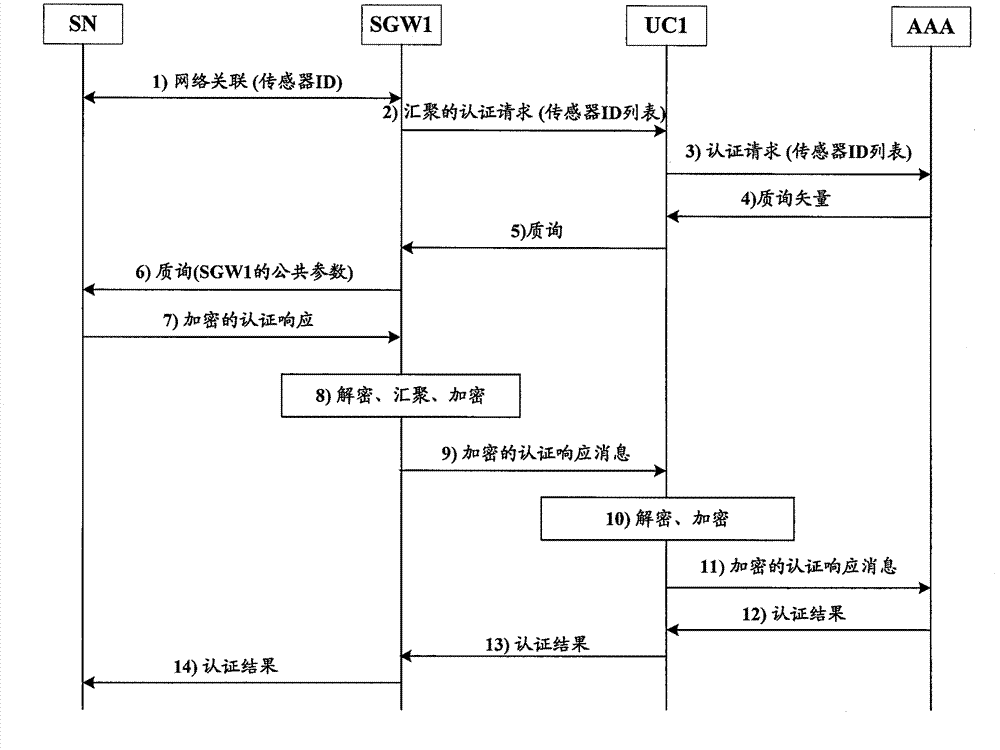
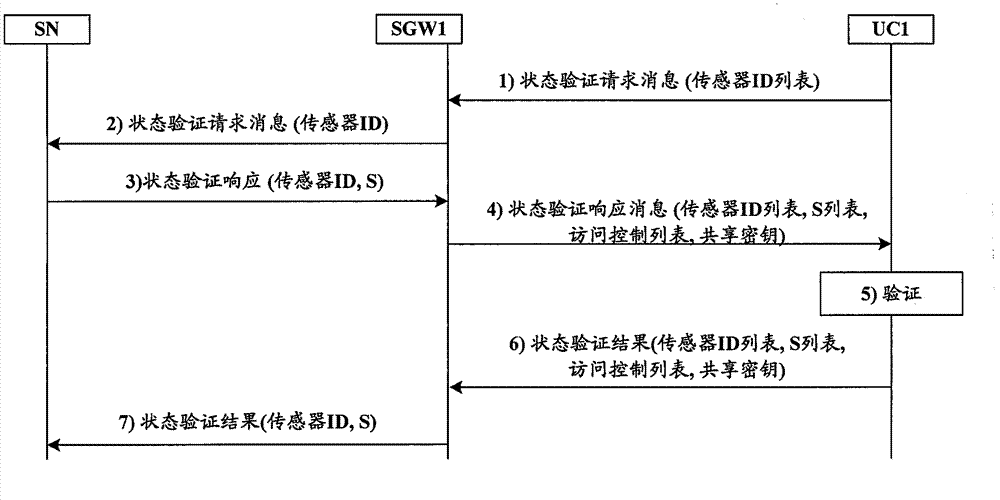
[0075] The following will be described in detail through specific embodiments. It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
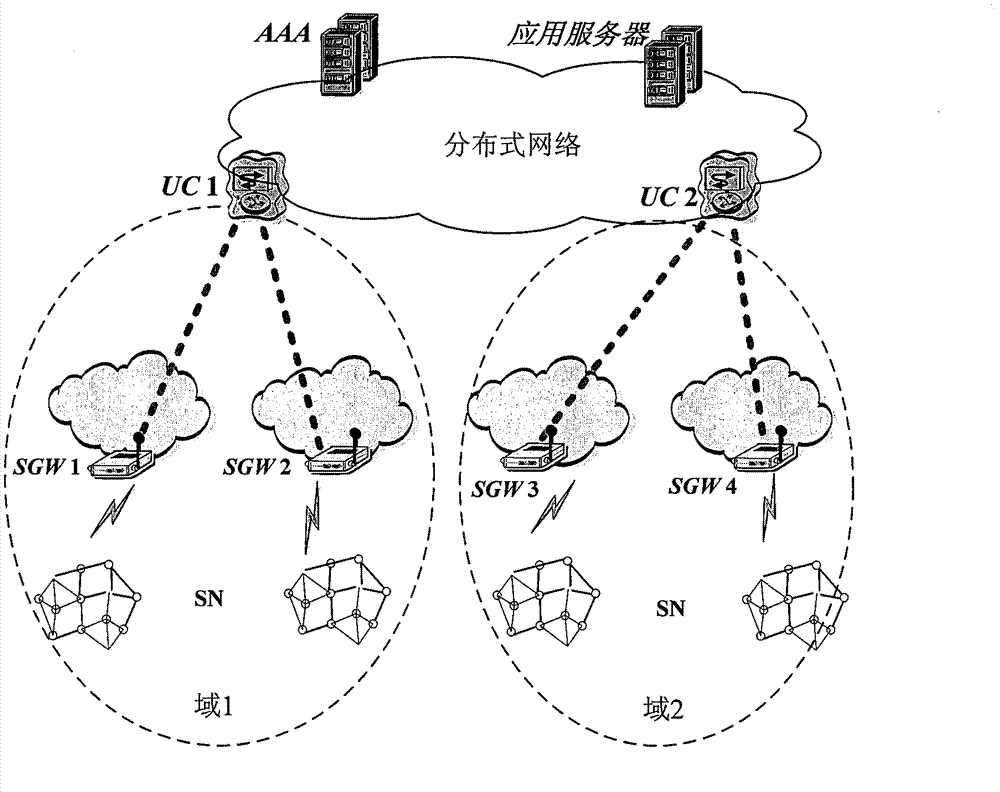
[0076] figure 1 The architecture of the security provisions of the present invention for ubiquitous sensor networks is shown. In addition to the Sensor Node (SN), it includes three main functional elements:
[0077] Sensor Network Gateway (SGW): Responsible for connecting sensor nodes to the Internet. For data forwarding, SGW performs data aggregation function for sensor nodes. For security, the SGW maintains an access control list (controlling which sensor nodes are allowed to join the network). In order to support group authentication for sensor nodes, that is, the aggregation function, the SGW has a cache mechanism to relay authentication data and sensor data.
[0078] USN Controller (UC): Coordinator responsible for managing s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com