Identity authentication method, identity authentication equipment, server and identity authentication-based encryption method
A technology of identity authentication and encryption method, which is applied in the field of authentication and can solve problems such as economic losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
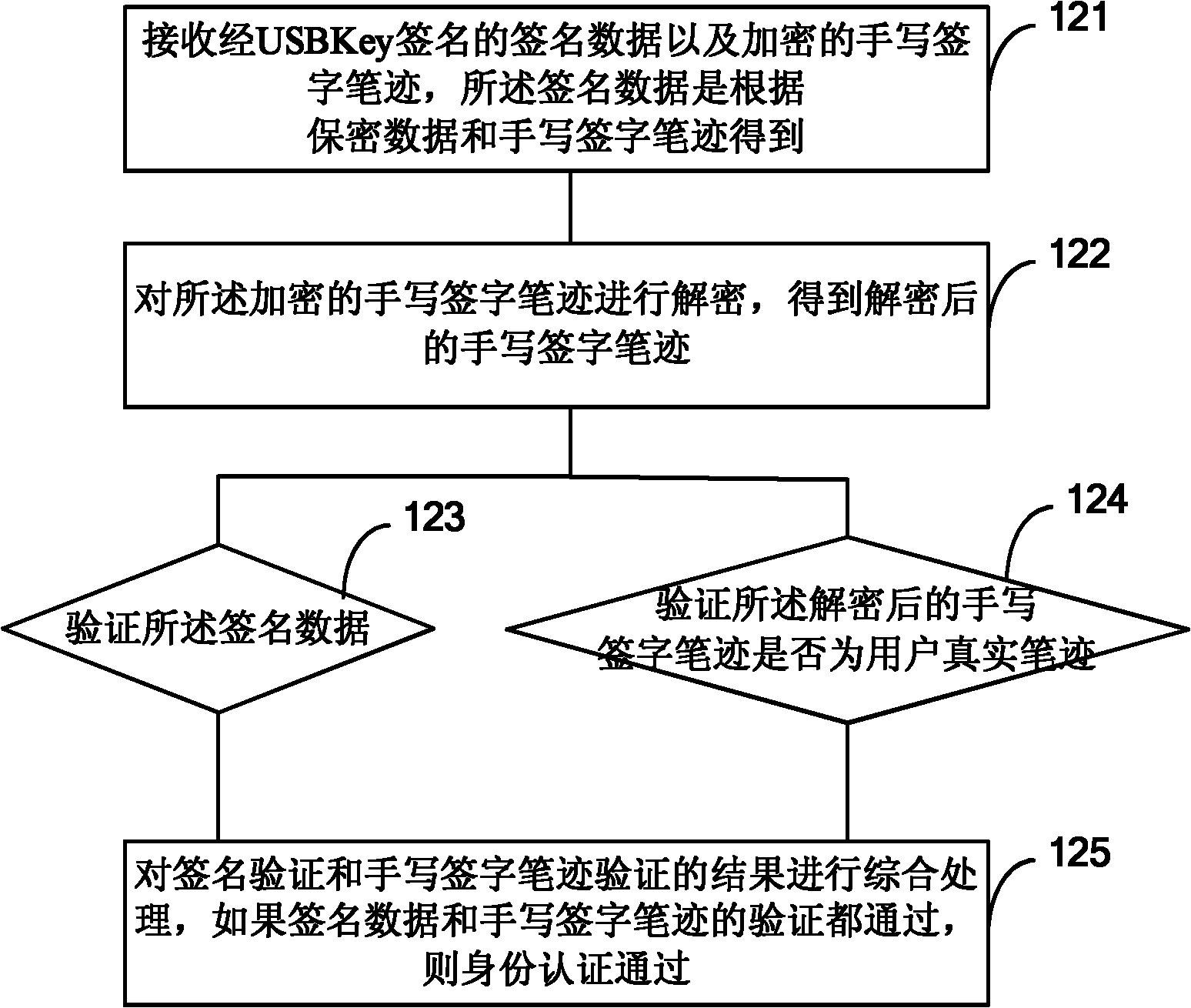
[0052] In this embodiment, the entire user identity authentication process includes two parts: the encryption process performed by the USBKey and the authentication process performed by the verifier. Figure 1A and Figure 1B The process shown is described.
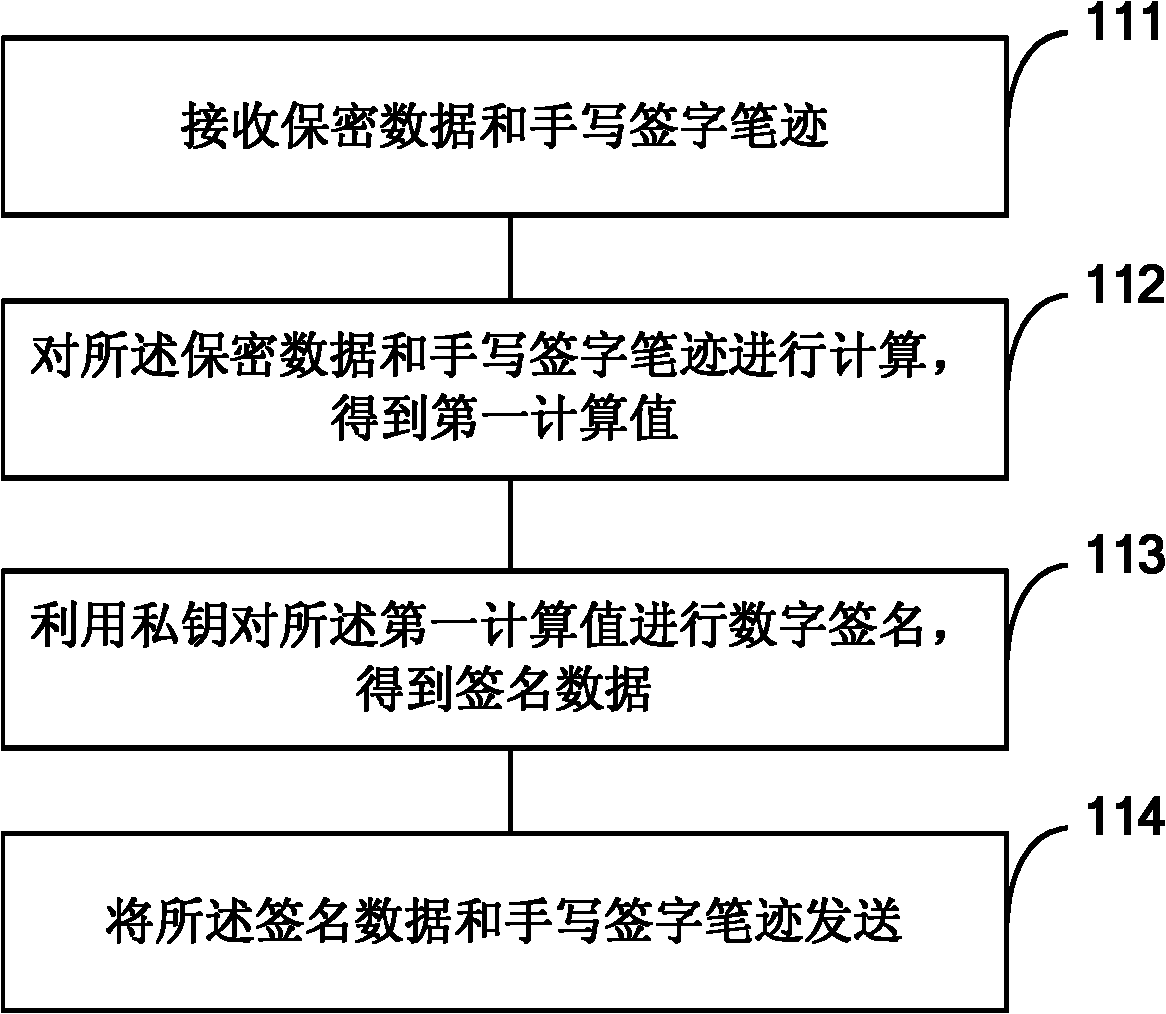
[0053] refer to Figure 1A , is one of the flow charts of the encryption method based on identity authentication described in Embodiment 1 of the present invention.
[0054] The USBKey as an authentication device performs the following steps:
[0055] Step 111, receiving confidential data and handwritten signature handwriting;
[0056] Wherein, the confidential data refers to transaction data, e-commerce data or electronic files, etc., which are transmitted between the USBKey and the verification party, and the verification party refers to the party that needs to authenticate the identity of the user in various fields such as the background program of the online bank .
[0057] The USBKey refers to a USBKey that suppor...
Embodiment 2
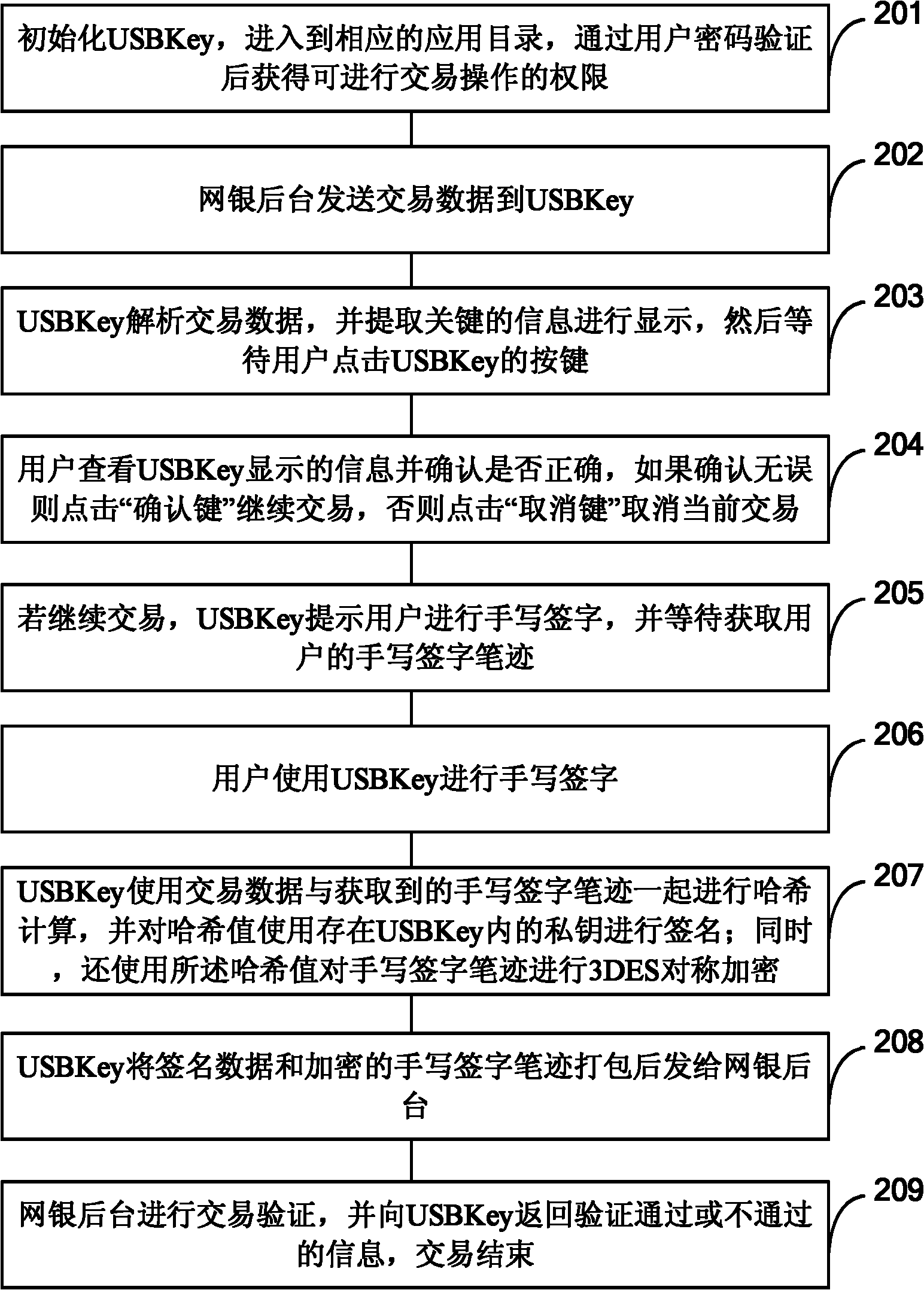
[0092] Based on the content of the first embodiment above, the following will take online banking transactions as an example, through figure 2 and image 3 The flow shown is described in more detail.
[0093] refer to figure 2 , is a transaction flow chart based on USBKey described in Embodiment 2 of the present invention.
[0094] Step 201, initialize the USBKey, enter the corresponding application directory, and obtain the permission to perform transaction operations after passing the user password verification;
[0095] That is, when the user conducts online banking transactions, he uses the USBKey to enter the user password, and after the online banking background verification of the user password is passed, the user can obtain the transaction authority.
[0096] Step 202, the online banking background sends the transaction data to the USBKey;
[0097] The transaction data includes bank name, user name, transaction account number, transaction password and other data....
Embodiment 3
[0115] This embodiment provides an identity authentication device applied to the first and second embodiments above. The identity authentication device supports handwritten signatures. The specific structure is as follows Figure 4 shown.
[0116] refer to Figure 4 , is a structural diagram of an identity authentication device supporting handwritten signatures according to Embodiment 3 of the present invention. The identity authentication device may be a USBKey or other devices with the same function.
[0117] The identity authentication device includes a communication interface 41, a touch screen 42, an analog / digital converter 43, a touch screen controller 44 and a main controller 45, wherein:
[0118] The communication interface 41 is used to receive confidential data and send it to the main controller 45; the confidential data refers to data such as transaction data, e-commerce data or electronic files; the communication interface 41 can be a USB interface or Bluetooth ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com