Identification method and system used for identifying personal area network device
A technology of equipment authentication and authentication method, which is applied in the field of authentication to achieve the effect of ensuring safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] Embodiment 1: Key-based authentication.
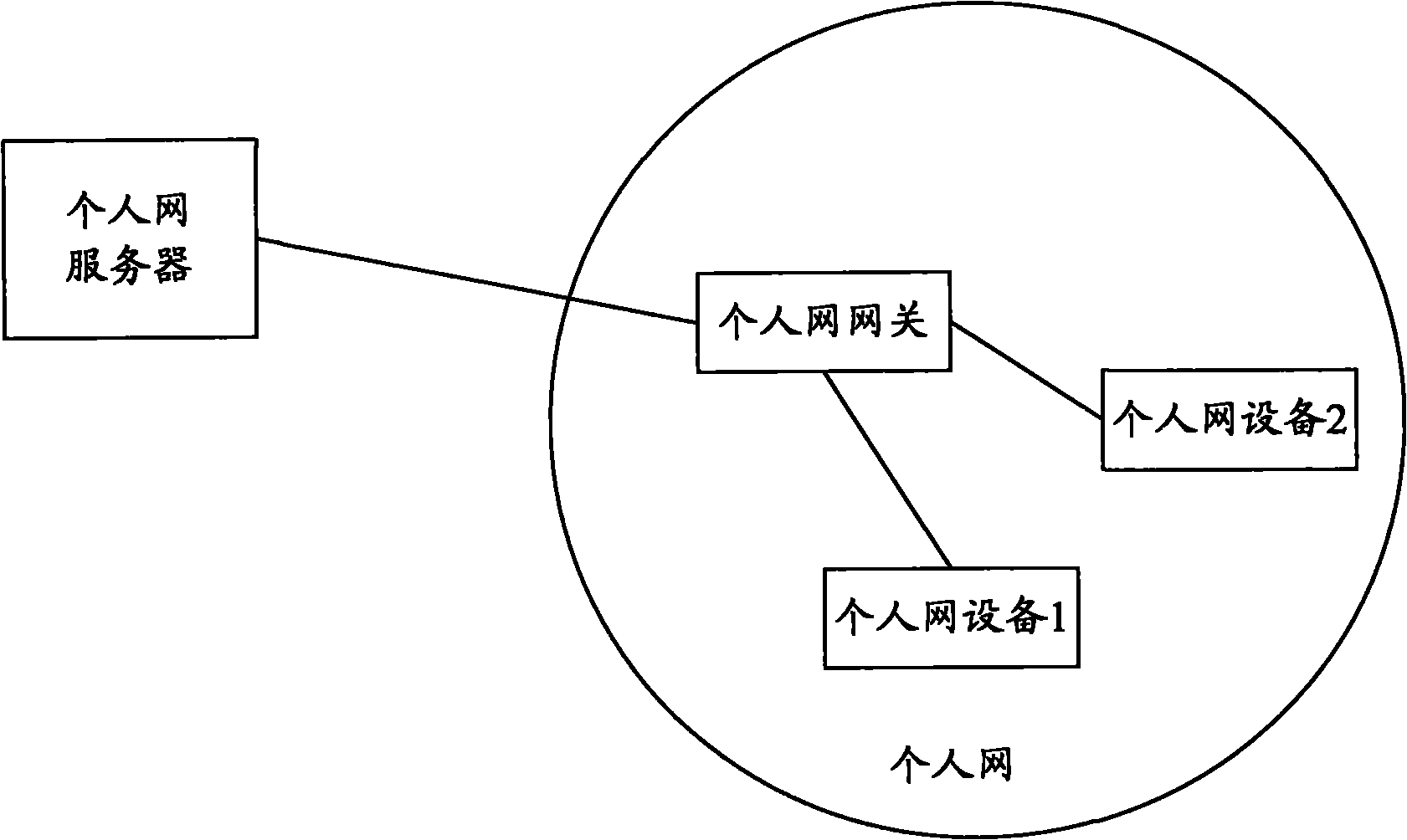
[0055] The networking of this embodiment is as follows figure 2 As shown, the PN is composed of a PN gateway, a PN device 1, and a PN device 2; the PN device 1 and the PN device 2 interact with the PN server through the PN gateway.
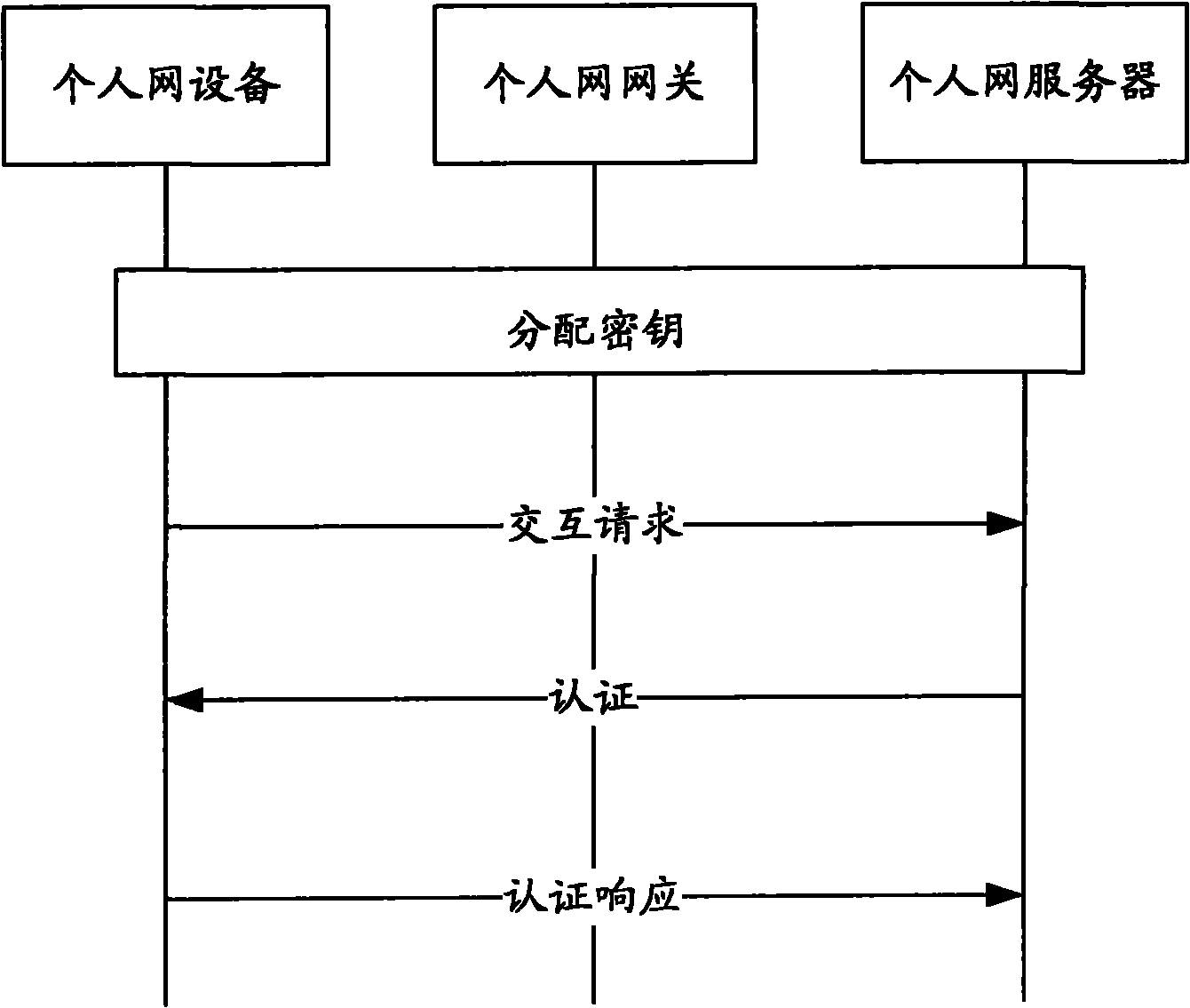
[0056] The key-based authentication process consists of the following steps:
[0057] Step 101, the PN server assigns a 128-bit seed to the PN gateway.
[0058] Step 102, the PN gateway generates random numbers for the PN device 1 and the PN device 2 respectively.
[0059] Step 103, the PN gateway generates a key for the PN device 1 according to the identifier of the PN device 1, the random number of the PN device 1, and the seed.
[0060] Step 104 , the PN gateway sends the key generated for the PN device 1 to the PN device 1 .
[0061] Step 105, the PN gateway generates a key for the PN device 2 according to the identifier of the PN device 2, the random number of the PN device 2, and the seed...
Embodiment 2
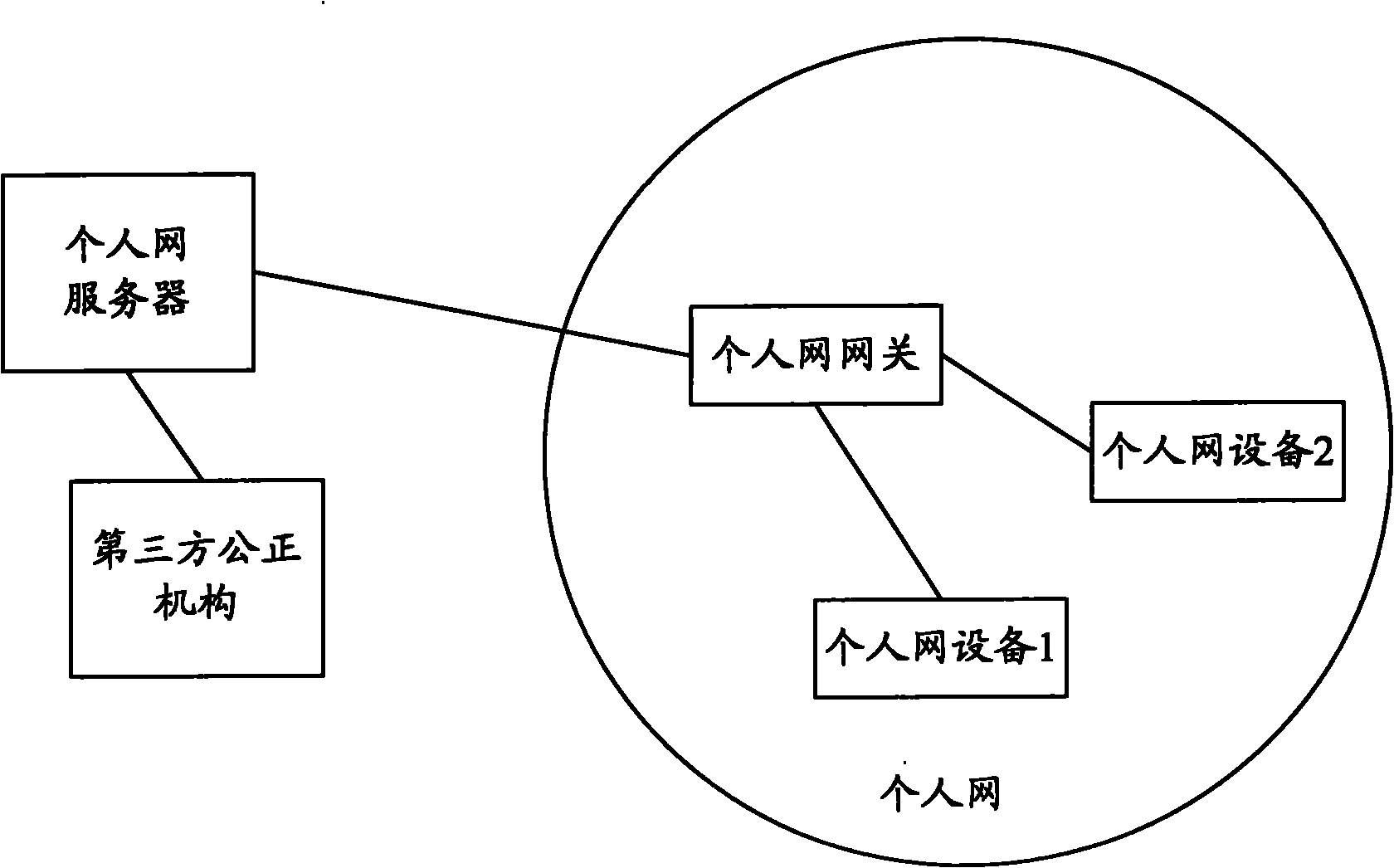
[0069] Embodiment 2: Authentication based on digital certificates.
[0070] The networking of this embodiment is as follows image 3 shown. Such as image 3 As shown, the PN is composed of PN gateway, PN device 1, and PN device 2; PN device 1 and PN device 2 interact with the PN server through the PN gateway; the PN server is connected to a third-party impartial agency , which is used to issue digital certificates.
[0071] The authentication process based on digital certificates includes the following steps:
[0072] Step 201, the device manufacturer builds a public key and a private key into the PN device 1 when producing it.
[0073] Step 202, the device manufacturer builds a public key and a private key into the PN device 2 when producing it.
[0074] Step 203, PN device 1 sends its public key to a third-party notary organization through the PN gateway and PN server to apply for a digital certificate.
[0075] Step 204, the third-party notary organization sends the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com