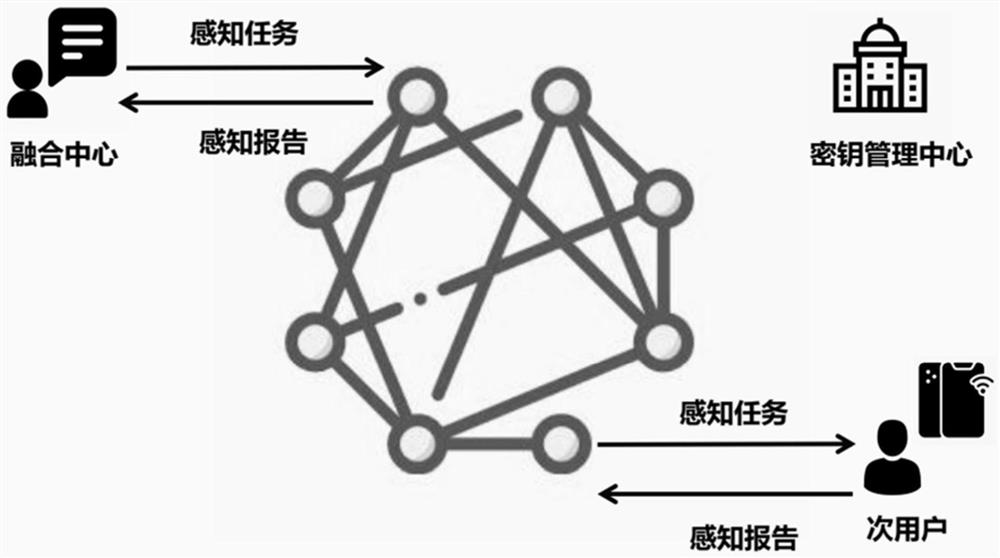
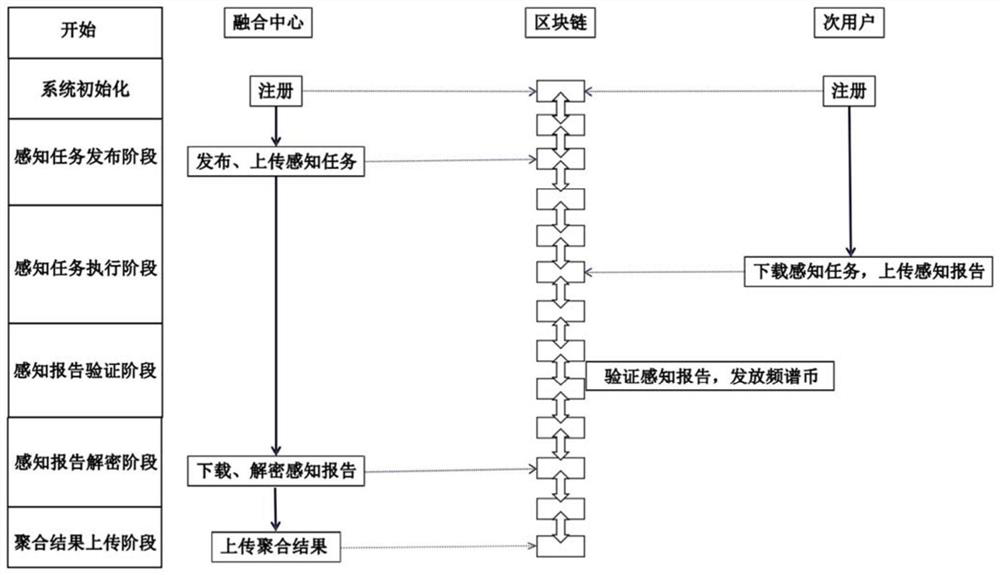
Cooperative spectrum sensing location privacy protection method based on blockchain
A collaborative spectrum sensing and privacy protection technology, applied in the field of blockchain-based collaborative spectrum sensing location privacy protection, can solve problems such as tampering attacks, interference with the normal operation of cognitive wireless networks, and incorrect fusion results of fusion centers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0041] Further, as a preferred embodiment, step 1 specifically includes the following steps:
[0042] Step 1-1, according to the definition of the elliptic curve group, the key management center randomly selects a large prime number p, q, and determines the finite field F p and F p An elliptic curve E(F p ), then select E(F p ) on a P with order q as the base point, and generate a cyclic addition group G, and finally announce the system parameters {p,q,F p ,E(F P ),P,G};
[0043] Step 1-2, the fusion center randomly selects the private key Calculate the public key PK FC =sk FC ·P. where the public key PK FC As the identity ID and transaction address of the fusion center in the blockchain, and made public in the system, the private key sk FC keep secret;
[0044] Steps 1-3, secondary user SU i random private key Calculate the public key PK i ∈sk i ·P. where the public key PK i as secondary user SU i The identity ID and transaction address in the blockchain a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com